Method for locating the attack source of multimedia subsystem network, system and anti-attack system
A multimedia subsystem and network attack technology, applied in the field of communication, can solve the problems of being unable to eliminate the attack from the root cause, and unable to locate the physical location of the user by IP address, so as to achieve the effect of solving network attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
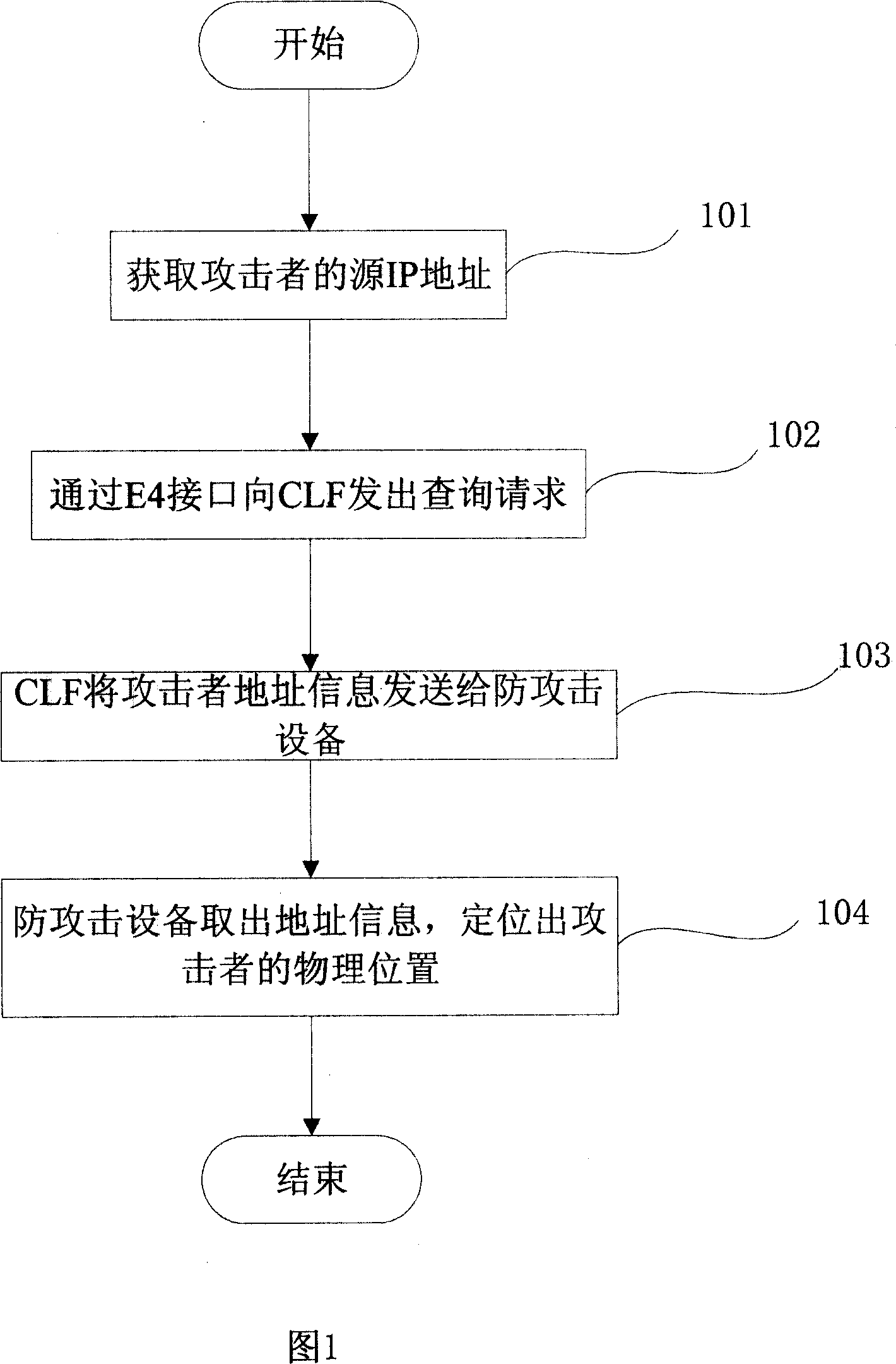
[0027] Referring to FIG. 1 , the embodiment of the present invention proposes a method for locating the source of an attack in an IMS network. Implement the E4 interface on the anti-attack device, and realize the physical location of the attacker through the interaction between the anti-attack device and the CLF. The method is as follows:
[0028] Step 101: the anti-attack device starts the attack detection function, if the anti-attack device detects an attack, obtains the source IP address of the attacker through the source IP address of the attack message, and records the source IP address of the attacker;
[0029] Step 102: the anti-attack device sends a query request to the CLF through the E4 interface, that is, constructs a query request message according to the requirements of the ETSI ES 282 035 standard, and the content of the request includes at least the attacker's source IP address information recorded in step 101;
[0030] Step 103: After the CLF receives the quer...
Embodiment 2
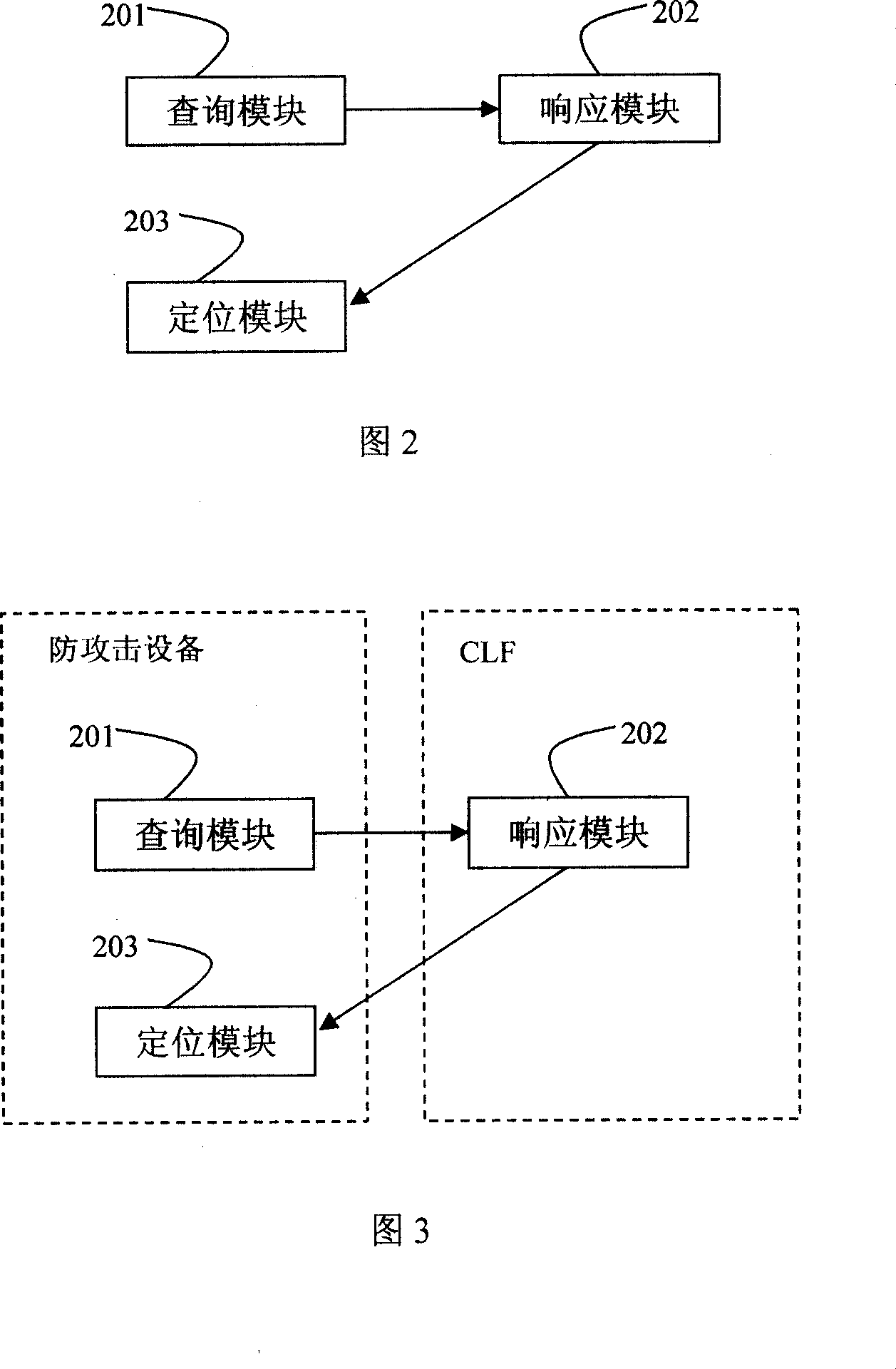
[0036] Referring to FIG. 2 , an embodiment of the present invention provides a system for locating the source of an IMS network attack. The system includes a query module 201 , a response module 202 , and a location module 203 . The output signal of the query module 201 is input to the response module 202 , and the output signal of the response module 202 is input to the positioning module 203 .
[0037] The query module 201 is configured to send a query request to the CLF when the attack prevention device detects that an attack occurs, and the content of the request includes at least source IP address information of the attacker.
[0038] The response module 202 is used for searching the address information corresponding to the source IP address information of the attacker in the database after the CLF receives the query request sent by the query module 201, and sending a response message to the attack defense device, which includes the above address information.
[0039] The ...
Embodiment 3
[0048] Referring to FIG. 3 , the present embodiment provides an attack prevention system, the system includes an attack prevention device and a CLF, the attack prevention device includes a query module 201 and a positioning module 203, and the CLF includes a response module 202;
[0049] The query module 201 is configured to send a query request to the CLF when the attack prevention device detects that an attack occurs, and the content of the request includes at least source IP address information of the attacker.
[0050] The response module 202 is used to search the database for the address information corresponding to the source IP address information of the attacker when the CLF receives the query request sent by the query module 201, and send a response message to the anti-attack device, the response message includes above address information.
[0051] The response module may specifically be a physical address response module or a logical address response module.
[0052...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com