Safety processing method, device and apparatus based on user behaviors
一种用户、行为的技术,应用在基于用户行为的安全处理领域,能够解决降低黑产破解图片或文字验证码难度、黑产攻击防御失败、降低网站安全性等问题,达到避免训练集污染、增加验证难度、降低黑产攻击的风险的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Hereinafter, the present application will be described in detail with reference to the drawings and embodiments. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
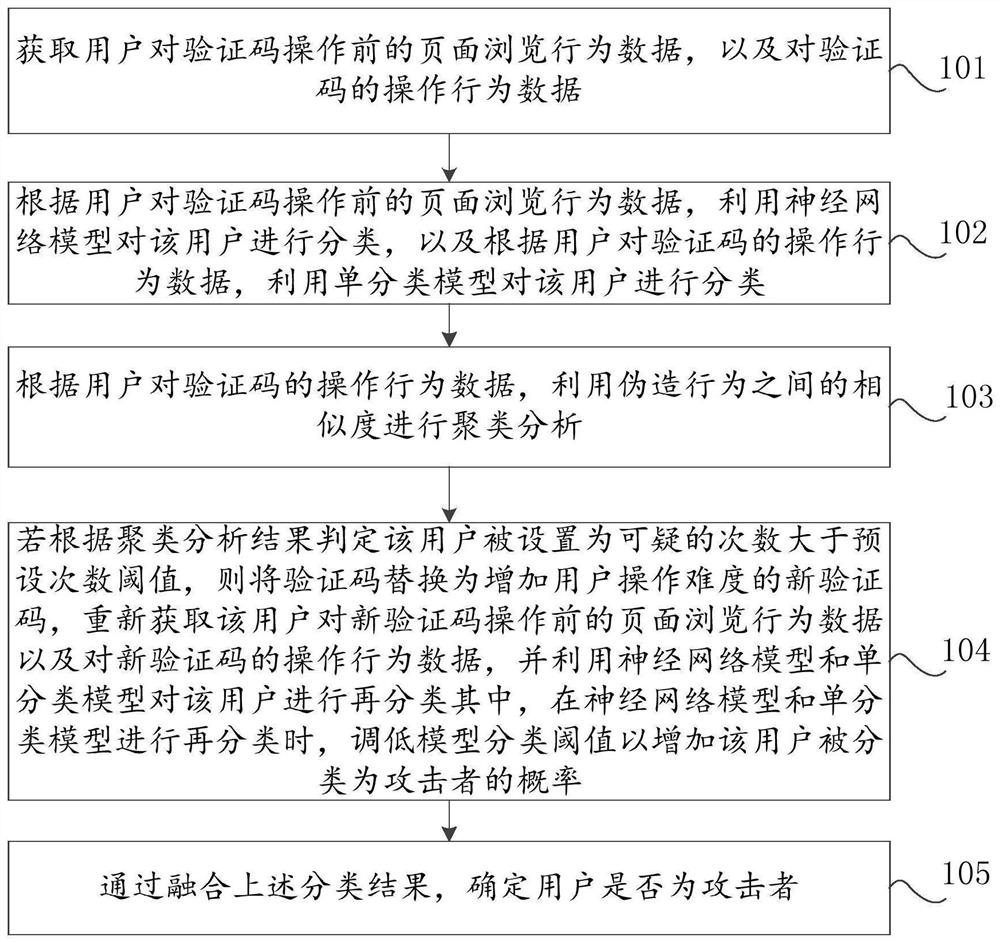
[0032] Aiming at improving the current technical problem that attackers can automatically identify the verification code of the website through the computer, it is easy to make the defense of black production attacks fail, thereby reducing the security of the website. This embodiment provides a security processing method based on user behavior, such as figure 1 As shown, the method includes:
[0033] 101. Obtain the page browsing behavior data before the user operates the verification code, and the operation behavior data on the verification code.
[0034] Wherein, the page browsing behavior data before the verification code operation may include: the user's mouse operation sequence and keyboa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com