Patents
Literature
51 results about "Threat perception" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Threat perception is defined as a deep sense of vulnerability that is assumed to be negative, likely to result in loss, and largely out of one's control (Dutton & Jackson, 1987; Jackson & Dutton, 1988) -- Glibert, 2005, 742. Threat perception is commonly viewed as a requirement to change organizational inertia.
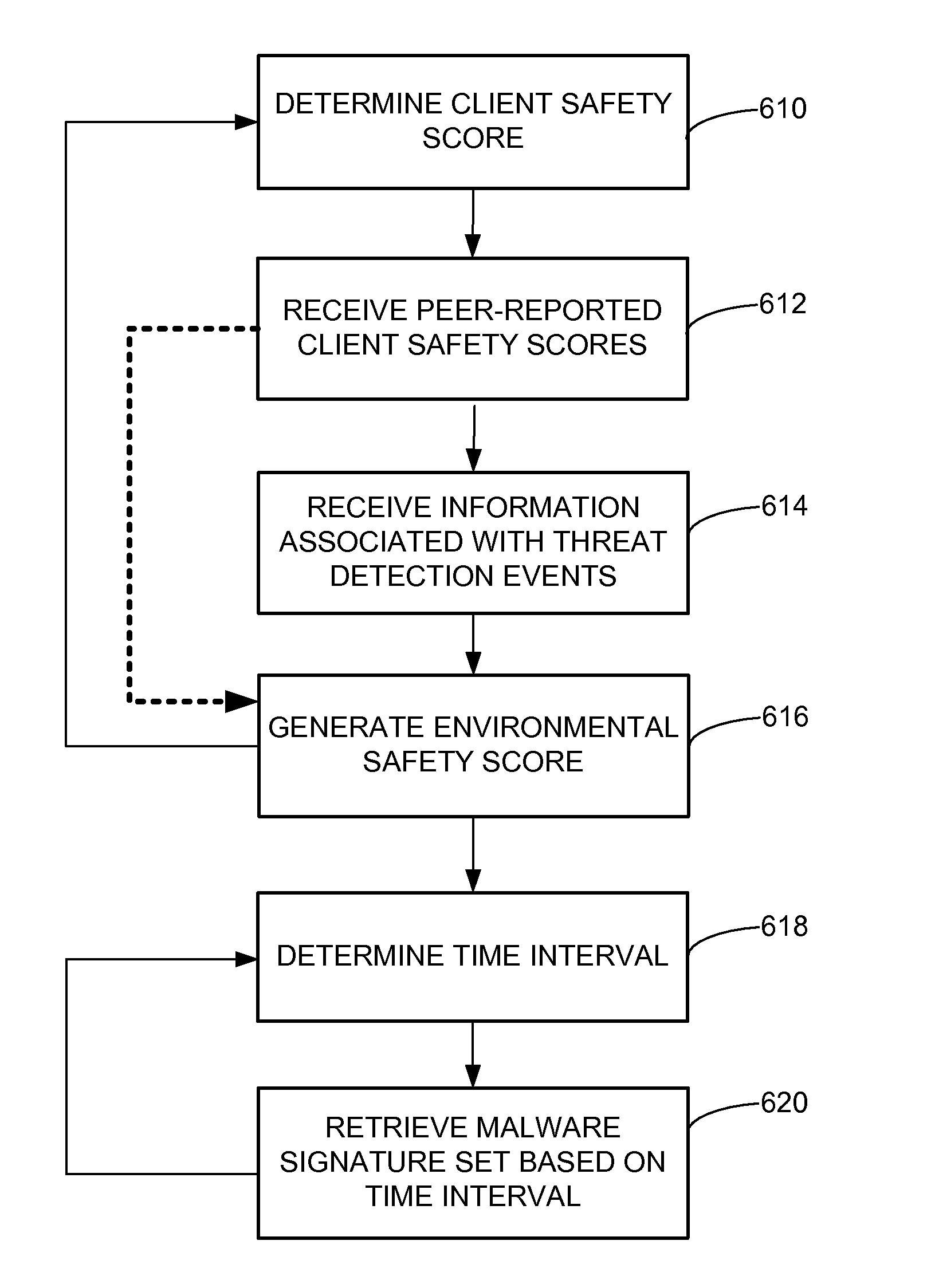
Scheduling malware signature updates in relation to threat awareness and environmental safety
Information is received from a set of peer clients associated with a client, the information indicating likelihoods of peer client exposure to malware threats. An environmental safety score associated with the client is determined based, at least in part, on the information received from the set of peer clients, wherein the environmental safety score indicates a likelihood that the client is exposed to malware threats. A set of malware signatures is retrieved from the server at a time determined responsive to the environmental safety score and stored.
Owner:NORTONLIFELOCK INC
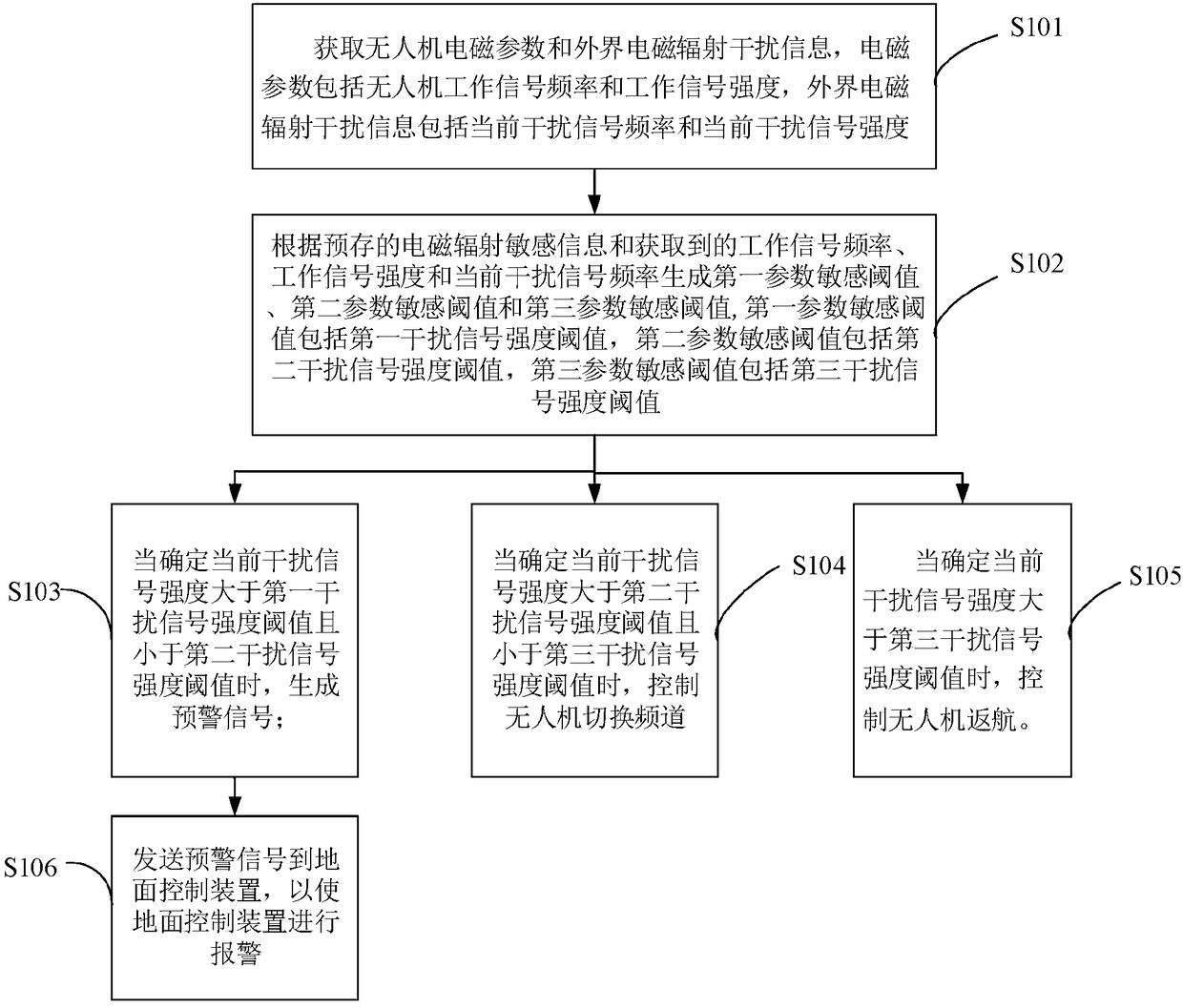
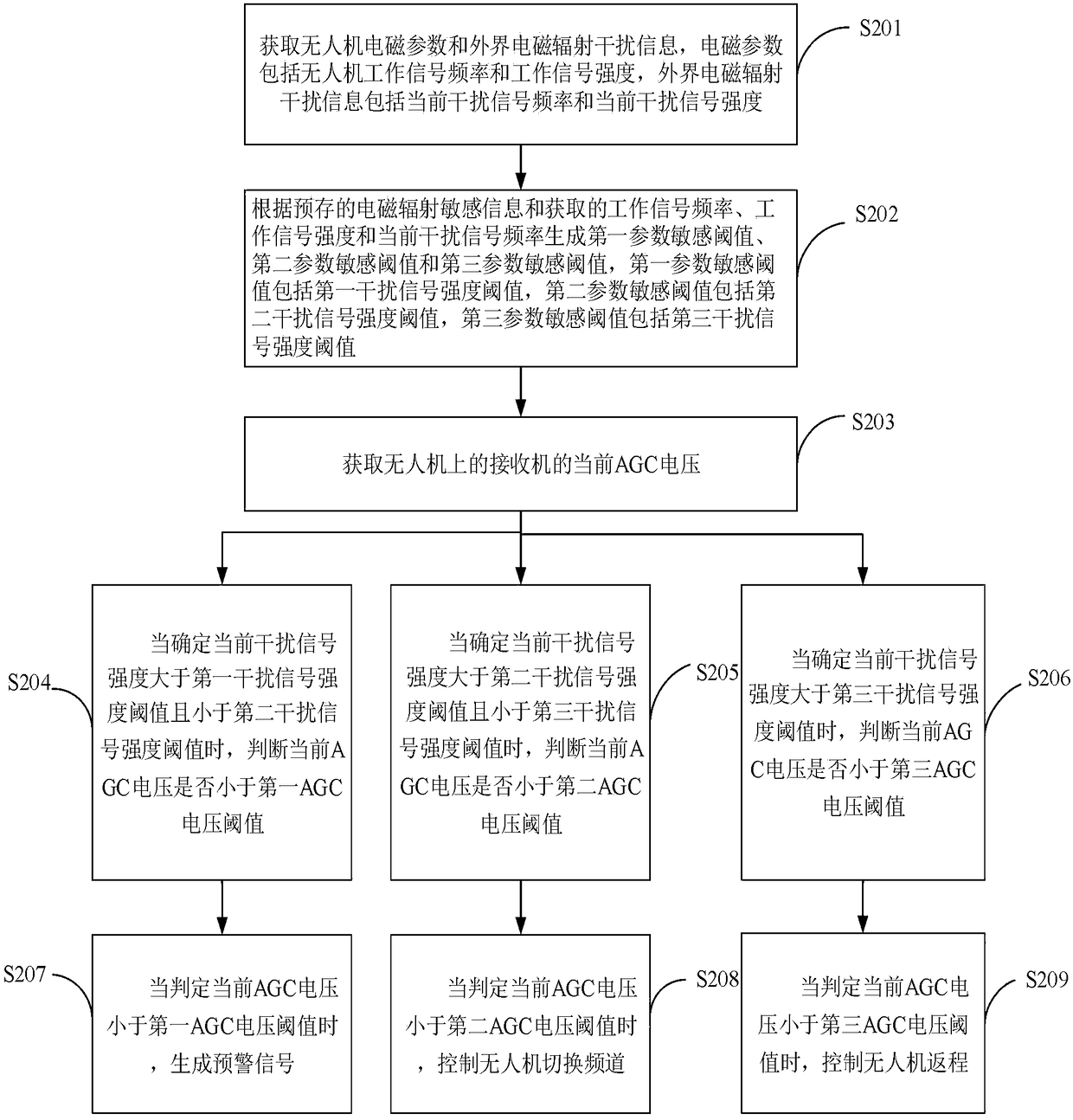
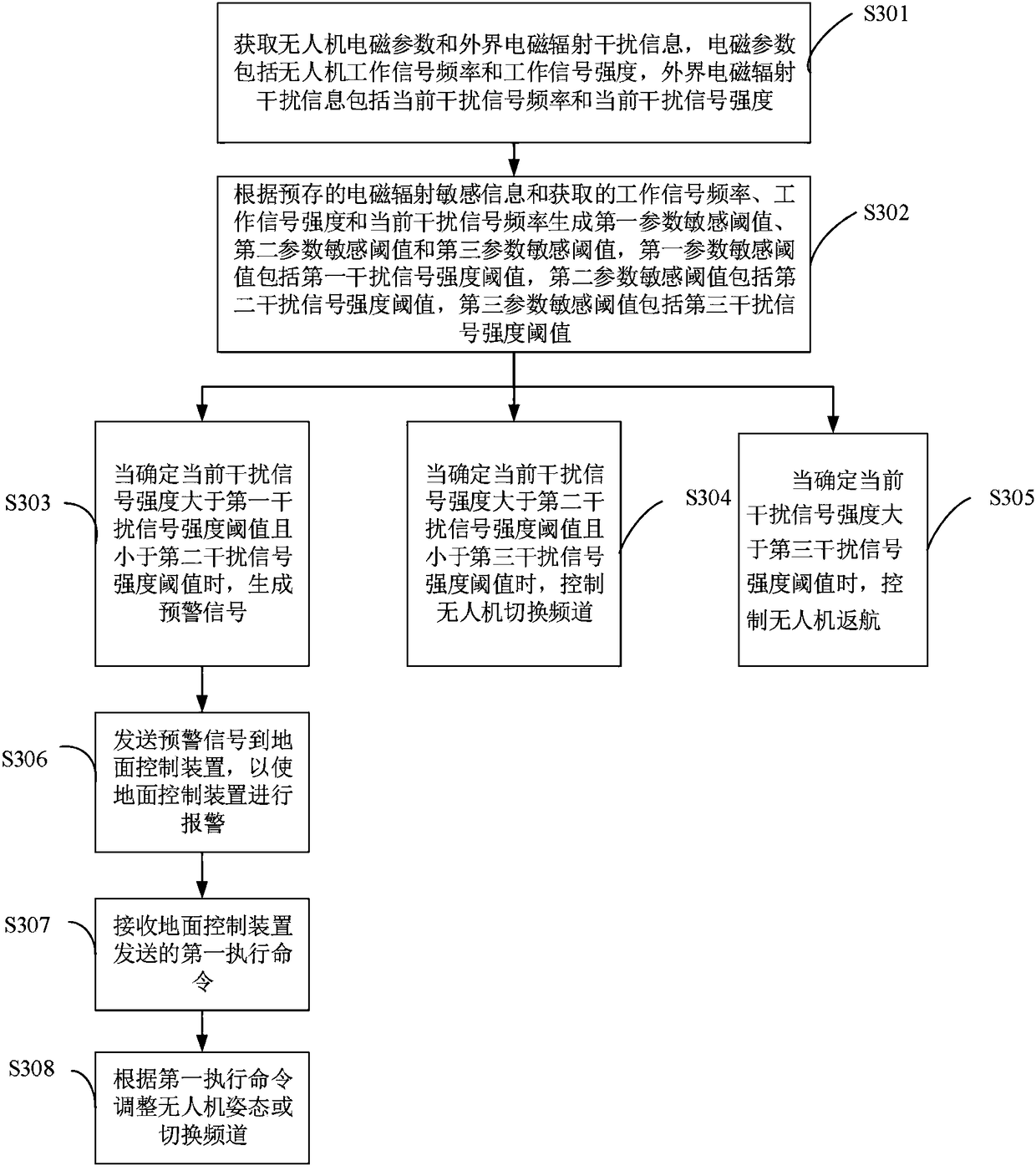
Electromagnetic radiation interference resisting method and device for information link of unmanned aerial vehicle
ActiveCN108153321AReduce the degree of impactAvoid unexpected situationsAttitude controlPosition/course control in three dimensionsElectromagnetic interferenceContinuous wave
The invention provides an electromagnetic radiation interference resisting method and device for an information link of an unmanned aerial vehicle. The electromagnetic radiation interference resistingmethod comprises the steps that unmanned aerial vehicle electromagnetic parameters and external electromagnetic radiation interference information are obtained, and a first parameter sensitive threshold, a second parameter sensitive threshold and a third parameter sensitive threshold are generated according to electromagnetic radiation sensitive information; an early warning signal is generated if the current interference signal intensity is greater than a first interference signal intensity threshold and less than a second interference signal intensity threshold; the unmanned aerial vehicleautomatically switches the channel if the current interference signal intensity is greater than the second interference signal intensity threshold and less than a third interference signal intensity threshold; and the unmanned aerial vehicle automatically executes a return instruction if the current interference signal intensity is greater than the third interference signal intensity threshold. According to the invention, the unmanned aerial vehicle can be avoided from being trapped in a strong electromagnetic interference area suddenly or having a sudden unexpected situation, the electromagnetic threat perception ability of the unmanned aerial vehicle is improved, the degree of influences imposed on unmanned aerial vehicle equipment by external continuous wave in-band electromagnetic radiation interference is reduced, and the intelligent development level of the equipment is improved.
Owner:ARMY ENG UNIV OF PLA
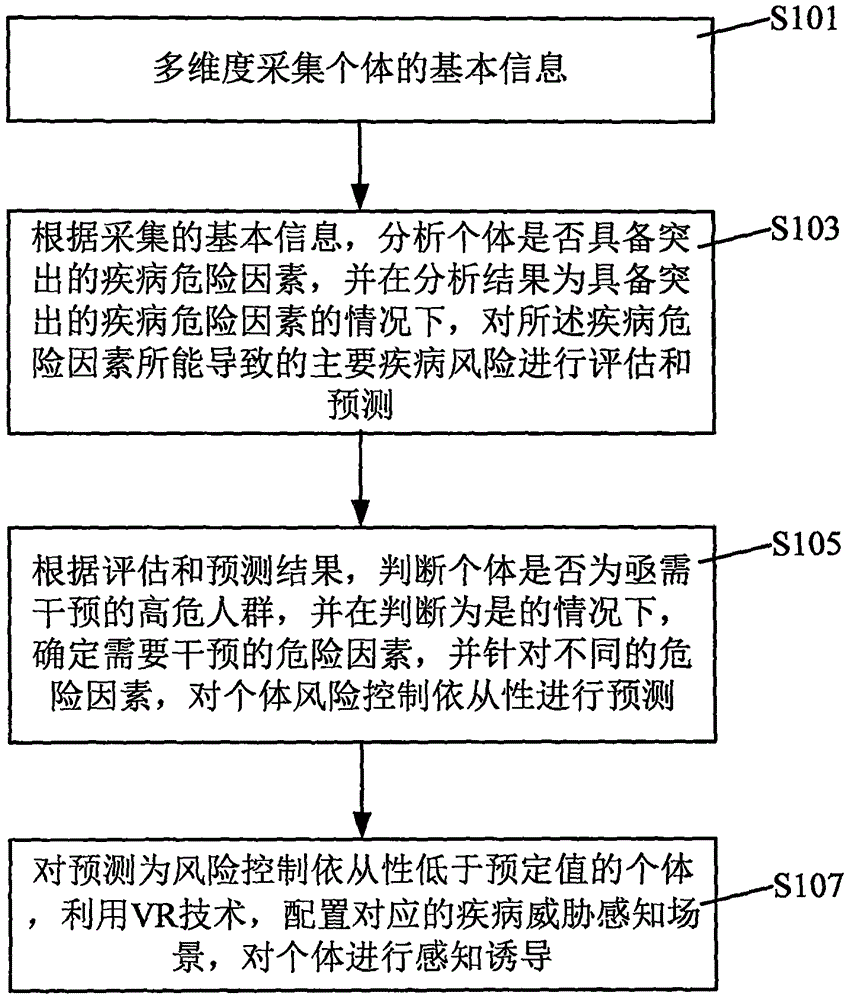
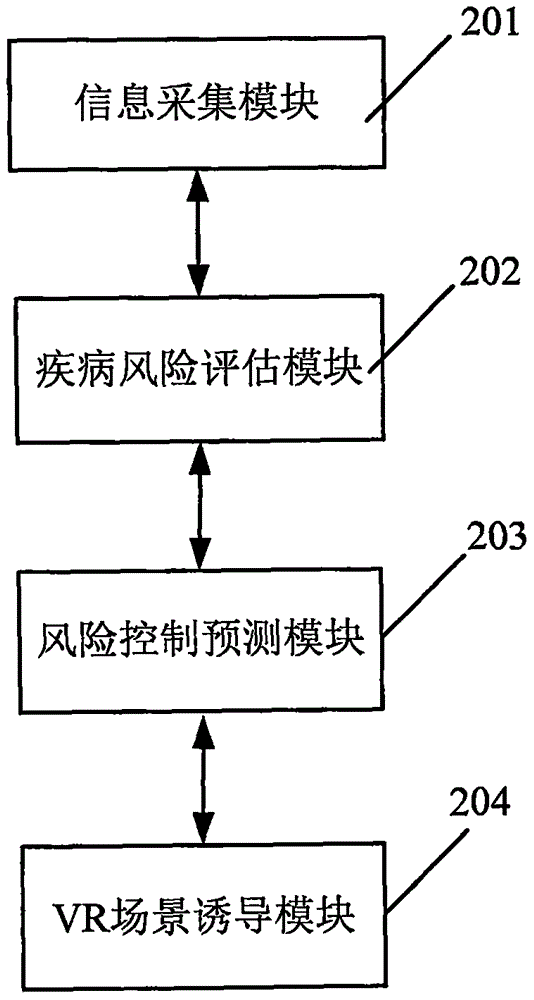
Disease prevention and health management method and system
ActiveCN106066938AAchieve preventionRealize health managementMedical automated diagnosisSpecial data processing applicationsDisease riskHigh risk populations
The invention discloses a disease prevention and health management method and system; the method comprises the following steps: multi-dimensionally collecting individual basic information; analyzing whether the individual has protruding disease danger factors or not according to collected basic information, and evaluating and predicting main disease risks caused by the disease danger factors if the analysis result is yes; determining whether the individual belongs to high risk population needing intervention or not according to the evaluation and prediction result, determining the danger factors needing intervention if the individual belongs to the high risk population, and predicting individual risk control compliance according to different danger factors; using VR technology to configure a corresponding disease threat perception scene for the individual with the predicted risk control compliance lower than a preset value, thus carrying out perception induction for the individual. The method and system can use VR scene technology to carry out disease danger perception induction for individuals, thus promoting behavior correction, and realizing disease prevention and health management.
Owner:贡京京
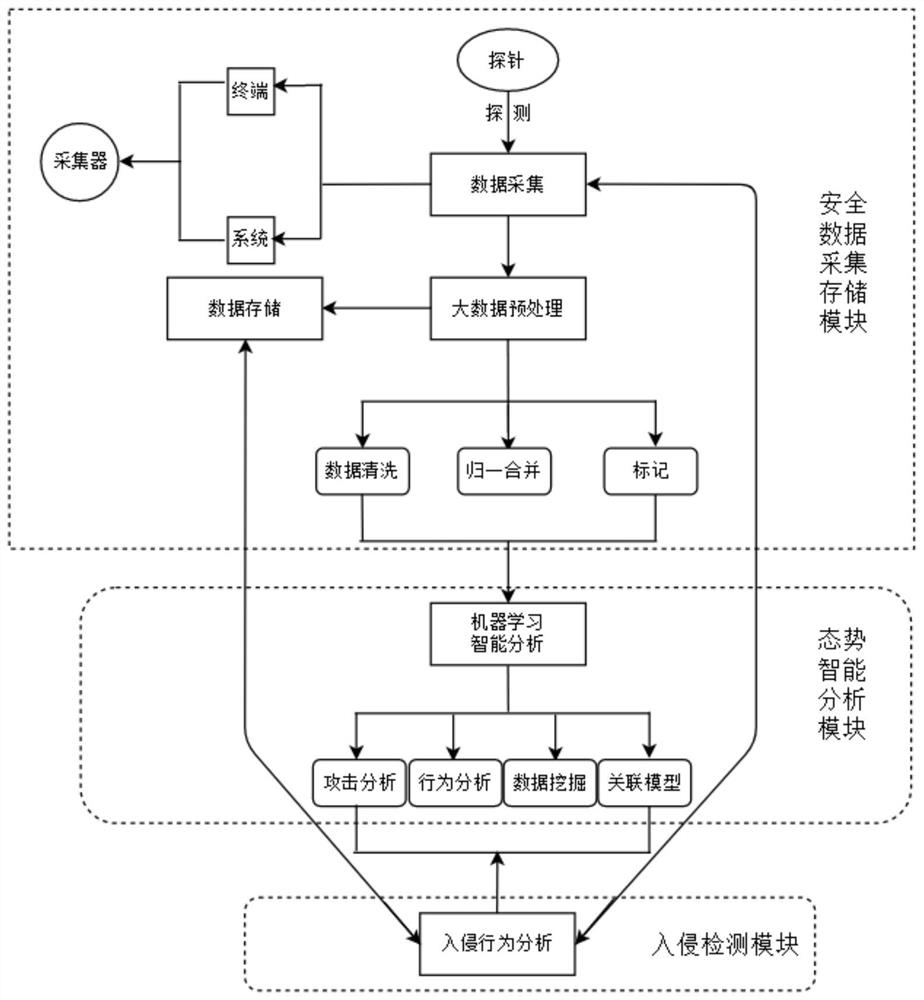
Power grid security situation awareness platform architecture
PendingCN112651006AAttack detected in timeAccurate predictionCharacter and pattern recognitionDigital data authenticationAttackData acquisition
The invention provides a power grid security situation awareness platform architecture. The power grid security situation awareness platform architecture comprises a security data acquisition and storage module, an intrusion detection module, an intelligent situation analysis module and a situation visualization module, through technologies of active monitoring, flow analysis, enterprise side collection and the like, power Internet of Things security threat perception, attack discovery, violation behavior monitoring, threat alarm and the like are formed, and security situation perception service is provided for the power industry aiming at the characteristics of multiple perception nodes, different types, diversified connections, dynamic and changeable information and the like in the power Internet of Things environment. An electric power Internet of Things security situation awareness solution is formed.
Owner:CHINA ELECTRIC POWER RES INST
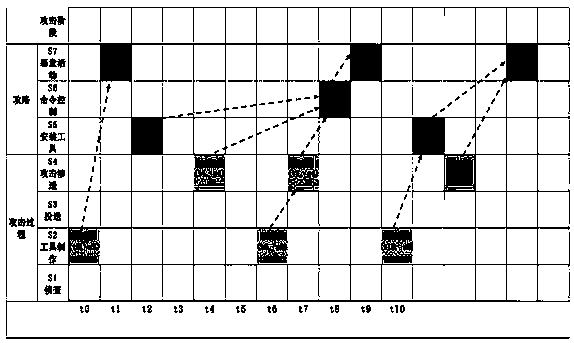
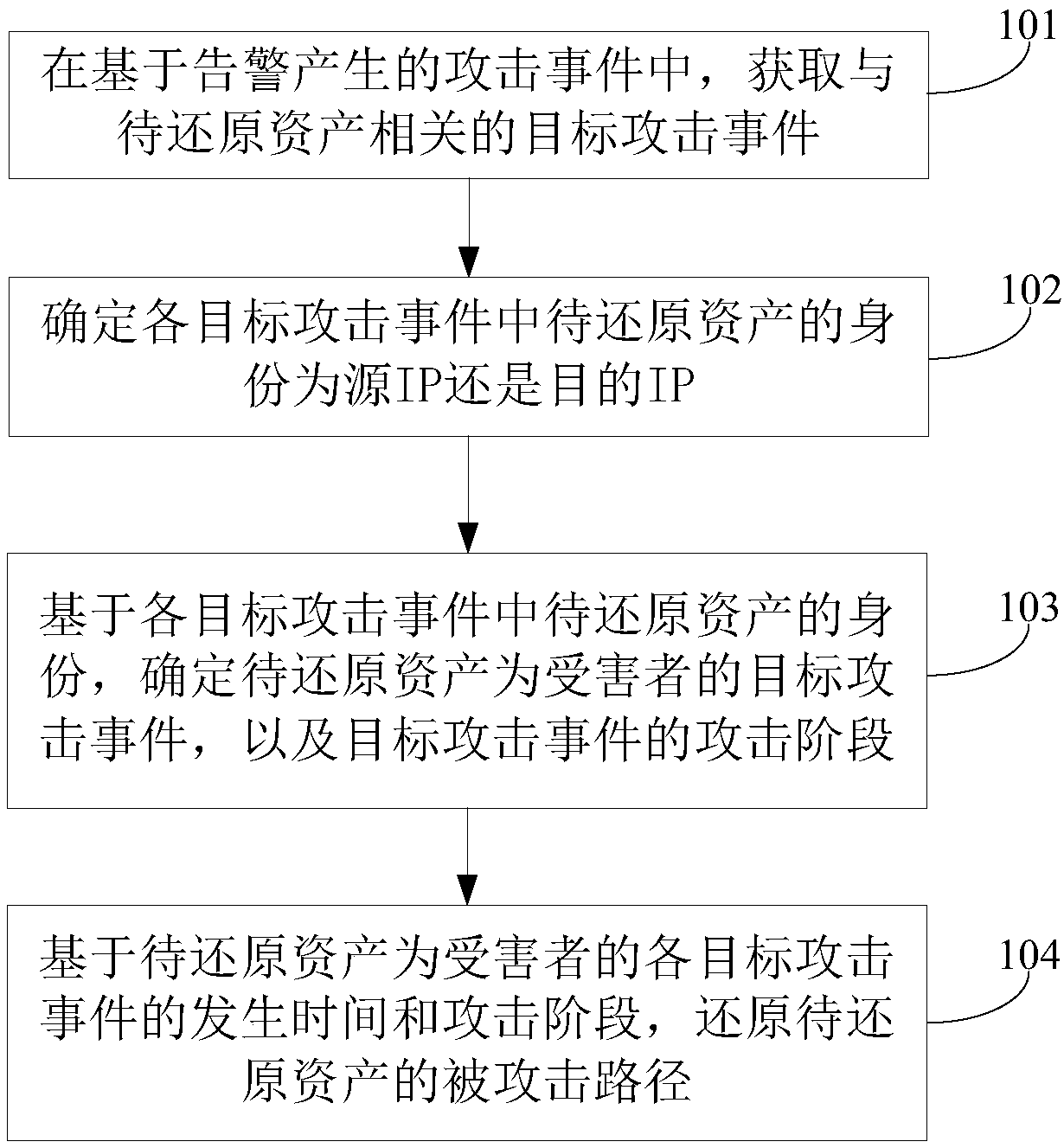
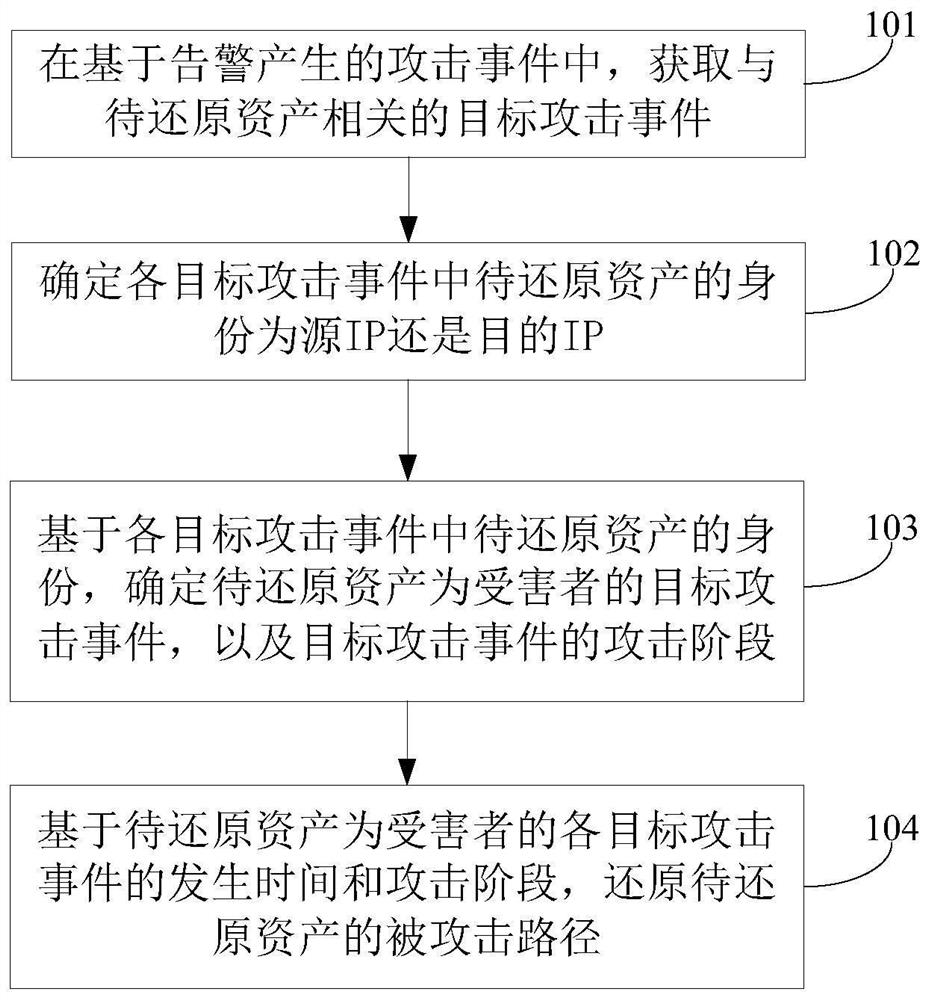
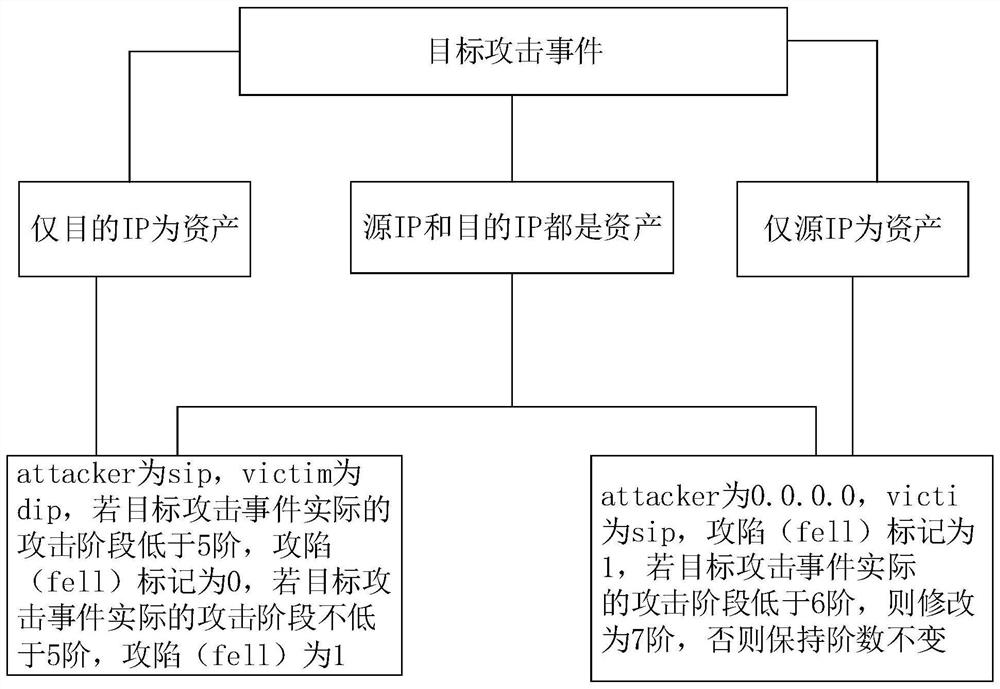
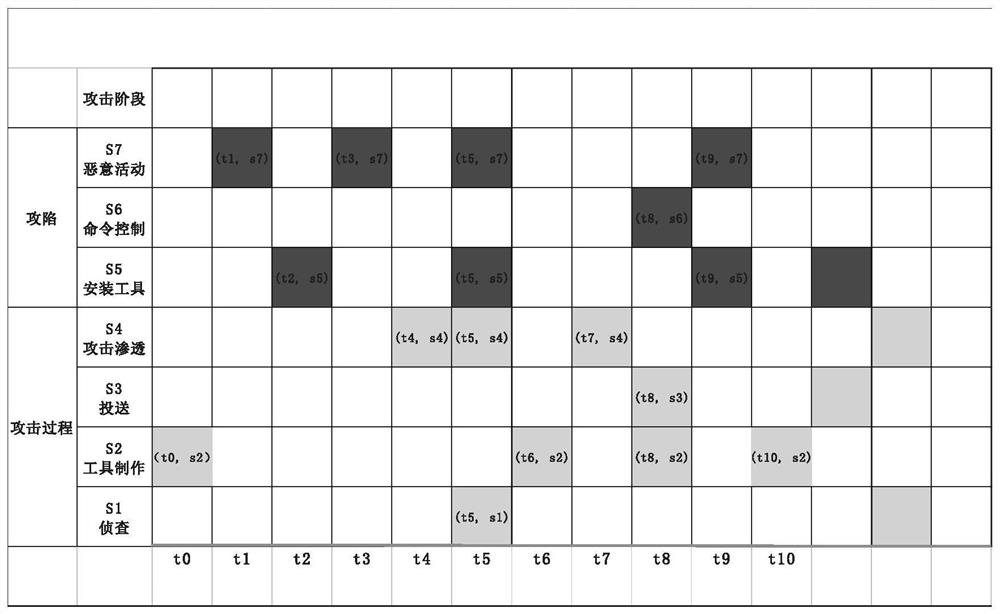
Attacked path reduction method, electronic device and computer readable storage medium
The invention discloses an attacked path reduction method, an electronic device and a computer readable storage medium. By acquiring target attack events related to to-be-reduced assets in attack events generated on the basis of alarms and determining whether an identity of the to-be-reduced asset in each target attack event is a source IP or a target IP, target attack events in which the to-be-reduced assets are victims and attack stages of the target attack events are determined; and then on the basis of occurrence time and the attack stage of each target attack event in which the to-be-reduced asset is the victim, an attacked path of the to-be-reduced asset is reduced. Based on the description above, it can be known that according to the application, the attacked paths are reduced on the basis of roles of the assets in the target attack events and the occurrence time and the attack stages of the target attack events; and in consideration of a case that the target attack events occurin a period of time, the reduced attacked paths can reflect laws of attacks from which the assets suffer in a certain time so as to benefit for improving the threat perception ability and the prediction ability of a network.
Owner:中国移动通信集团海南有限公司
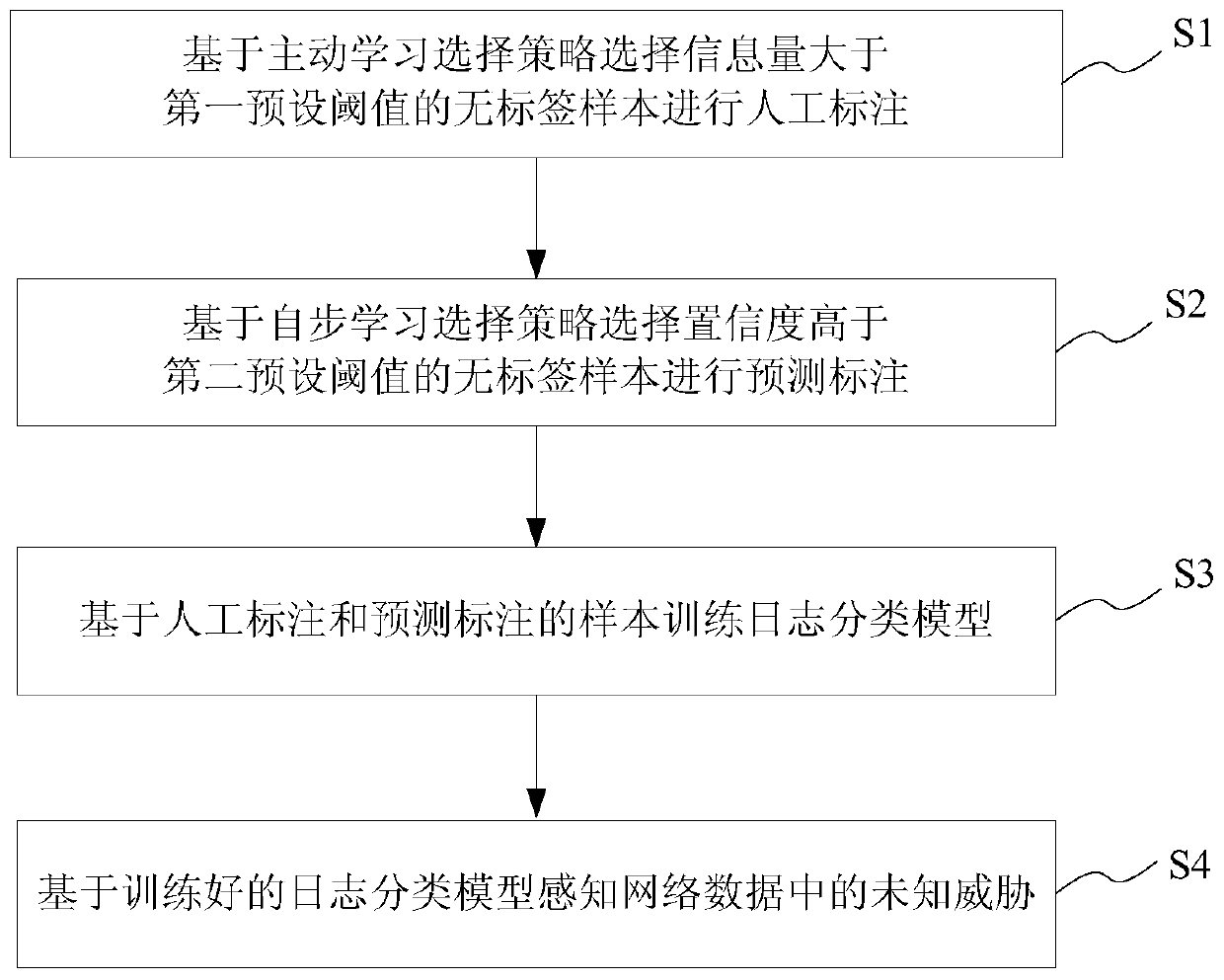
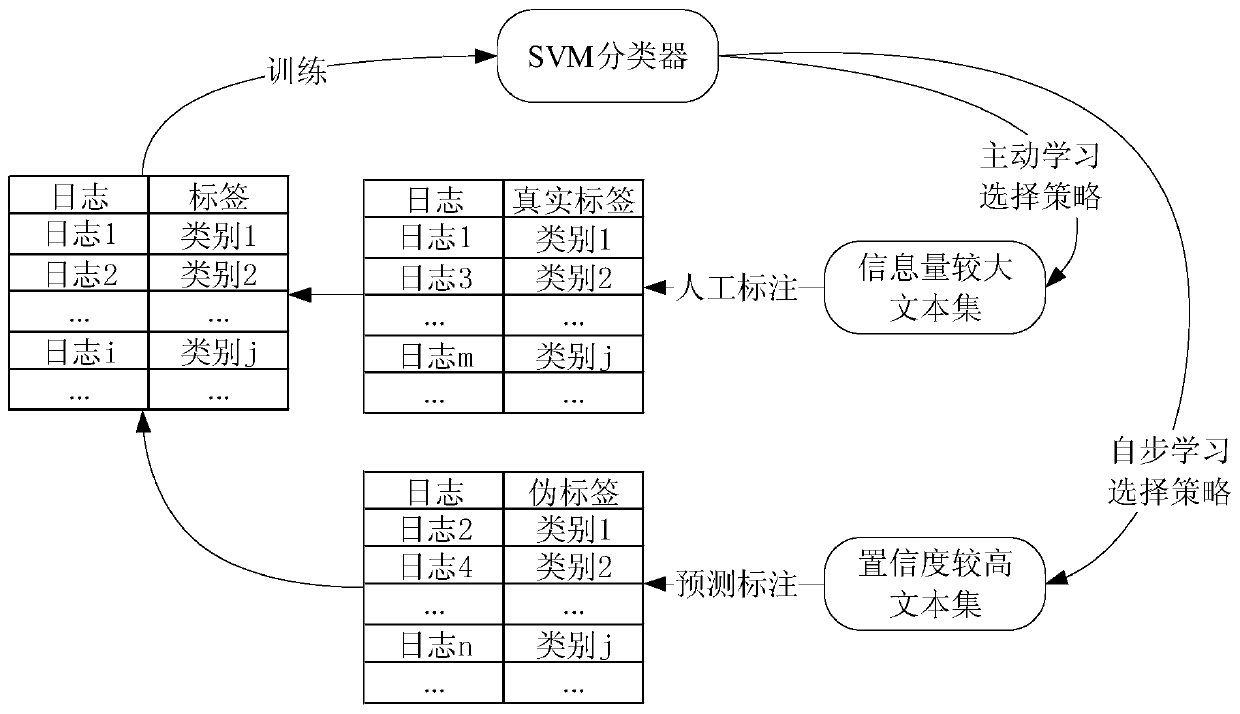
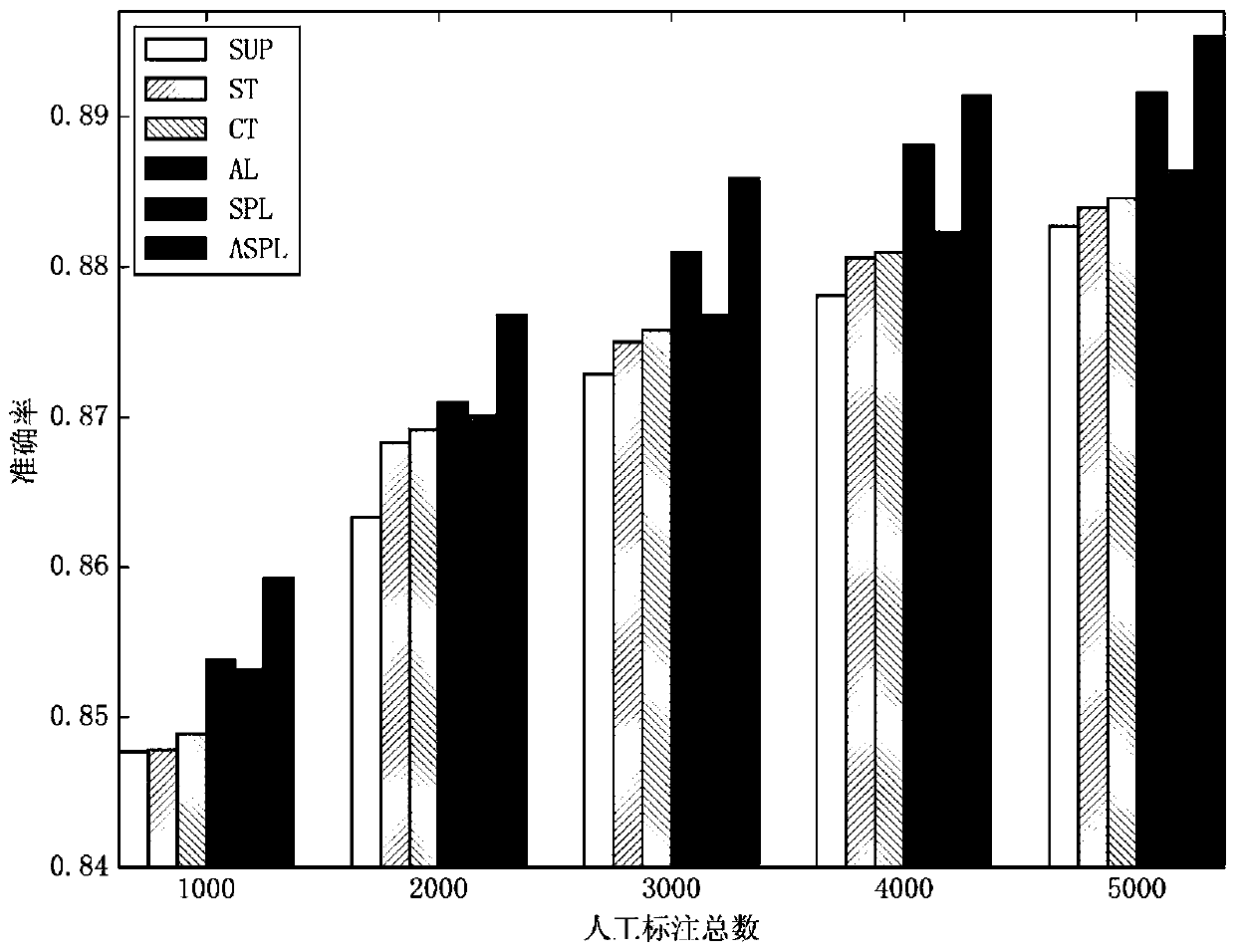
Unknown threat perception method and system based on active self-paced learning, storage medium and terminal
InactiveCN109818929AImprove accuracyMeet training needsCharacter and pattern recognitionTransmissionPattern recognitionManual annotation
The invention provides an unknown threat perception method and system based on active self-paced learning, a storage medium and a terminal. The unknown threat perception method comprises the followingsteps: selecting a label-free sample with the information amount greater than a first preset threshold value for manual labeling based on an active learning selection strategy; Selecting a label-freesample with the confidence higher than a second preset threshold based on a self-learning selection strategy to carry out prediction labeling; Training a log classification model based on samples ofmanual annotation and predictive annotation; And sensing unknown threats in the network data based on the trained log classification model. According to the unknown threat perception method and systembased on active self-paced learning, the storage medium and the terminal, the accuracy of network threat recognition is improved through a mode of combining manual annotation and predictive annotation, and an unknown network can be recognized.
Owner:TIANYI ELECTRONICS COMMERCE
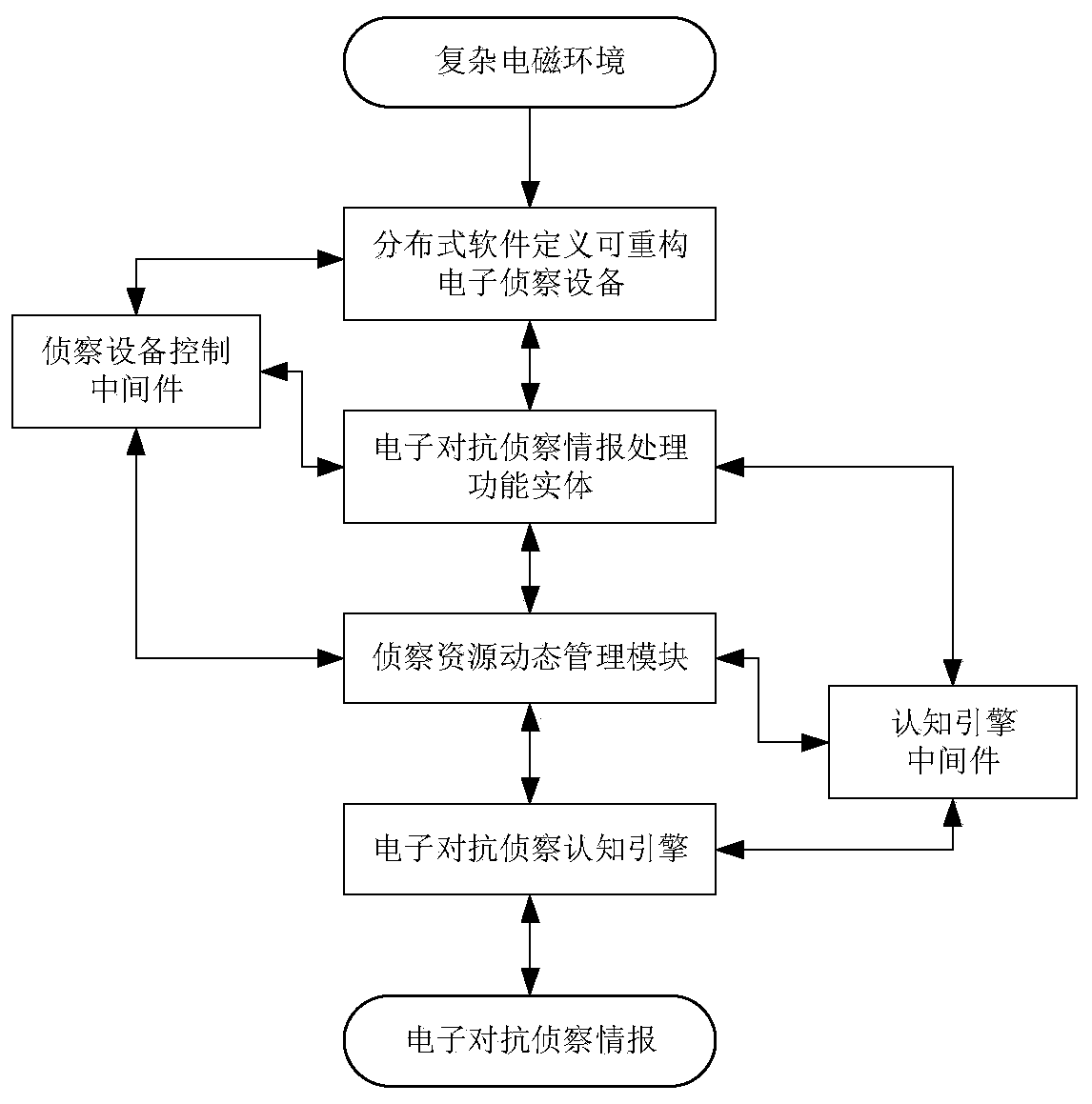
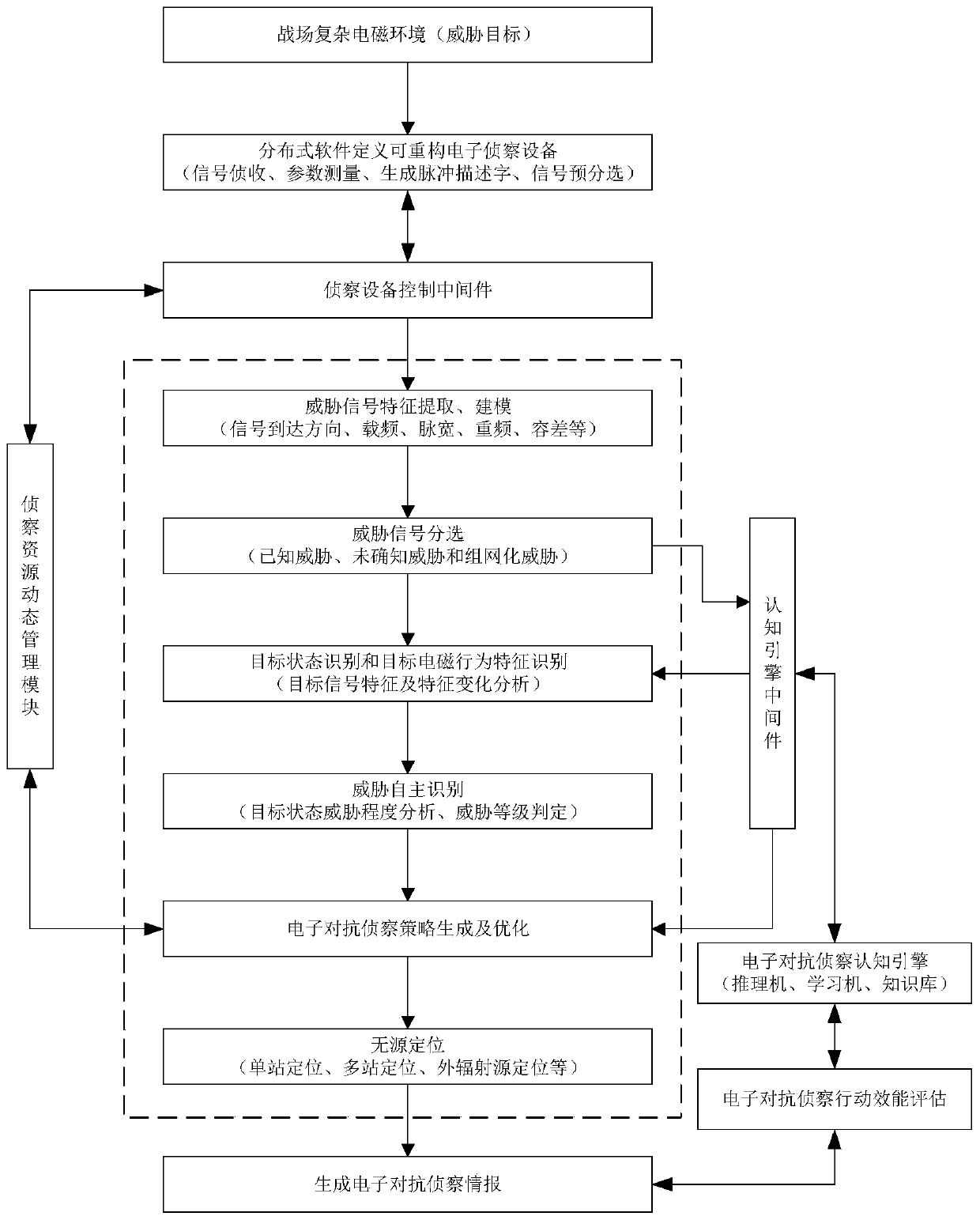
Electronic countermeasure reconnaissance system architecture based on heterogeneous cognitive sensor network
PendingCN111490848AImprove threat awareness and identification capabilitiesIncrease flexibilityCommunication jammingFeature extractionTarget signal
The invention discloses an electronic countermeasure reconnaissance system architecture based on a heterogeneous cognitive sensor network. Distributed software-defined reconfigurable electronic reconnaissance equipment performs threat perception on a complex electromagnetic environment; a threat signal feature extraction module performs feature extraction and modeling on the target signal; a target state and behavior characteristic recognition module is used for recognizing a target state and target electromagnetic behavior characteristics; a threat signal sorting module sorts the threat signals according to known threats, unascertained threats and networking threats; a threat autonomous identification module performs threat identification and threat level judgment on the known threat based on a knowledge base; an electronic countermeasure reconnaissance cognitive engine identifies and deduces unascertained threats and networking threats based on an inference engine; and a backbone node reconnaissance resource dynamic management module carries out functional parameter dynamic reconstruction and optimal scheduling on the sensing nodes, so that the threat sensing identification capability of the electronic countermeasure reconnaissance system and the utilization efficiency of reconnaissance resources are improved.
Owner:NAVAL AVIATION UNIV
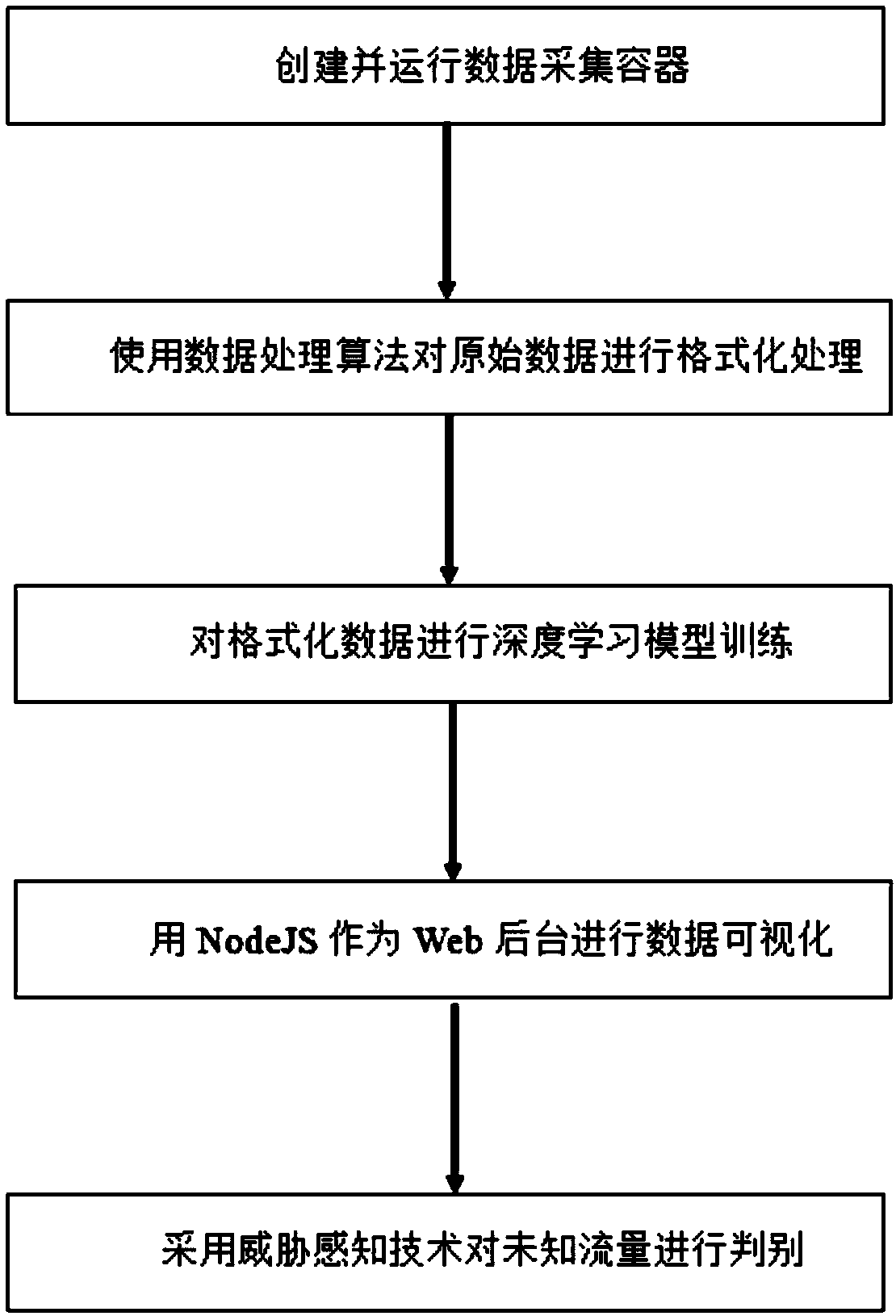
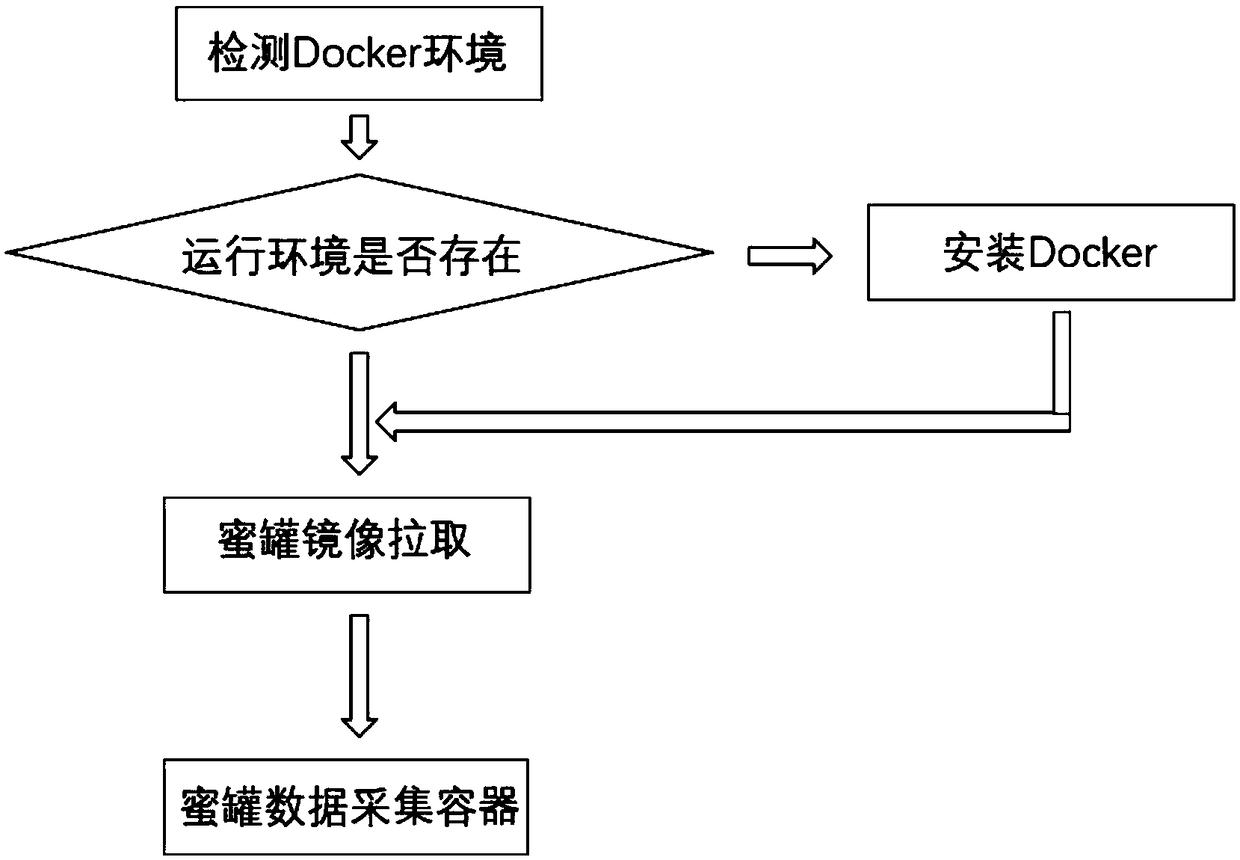
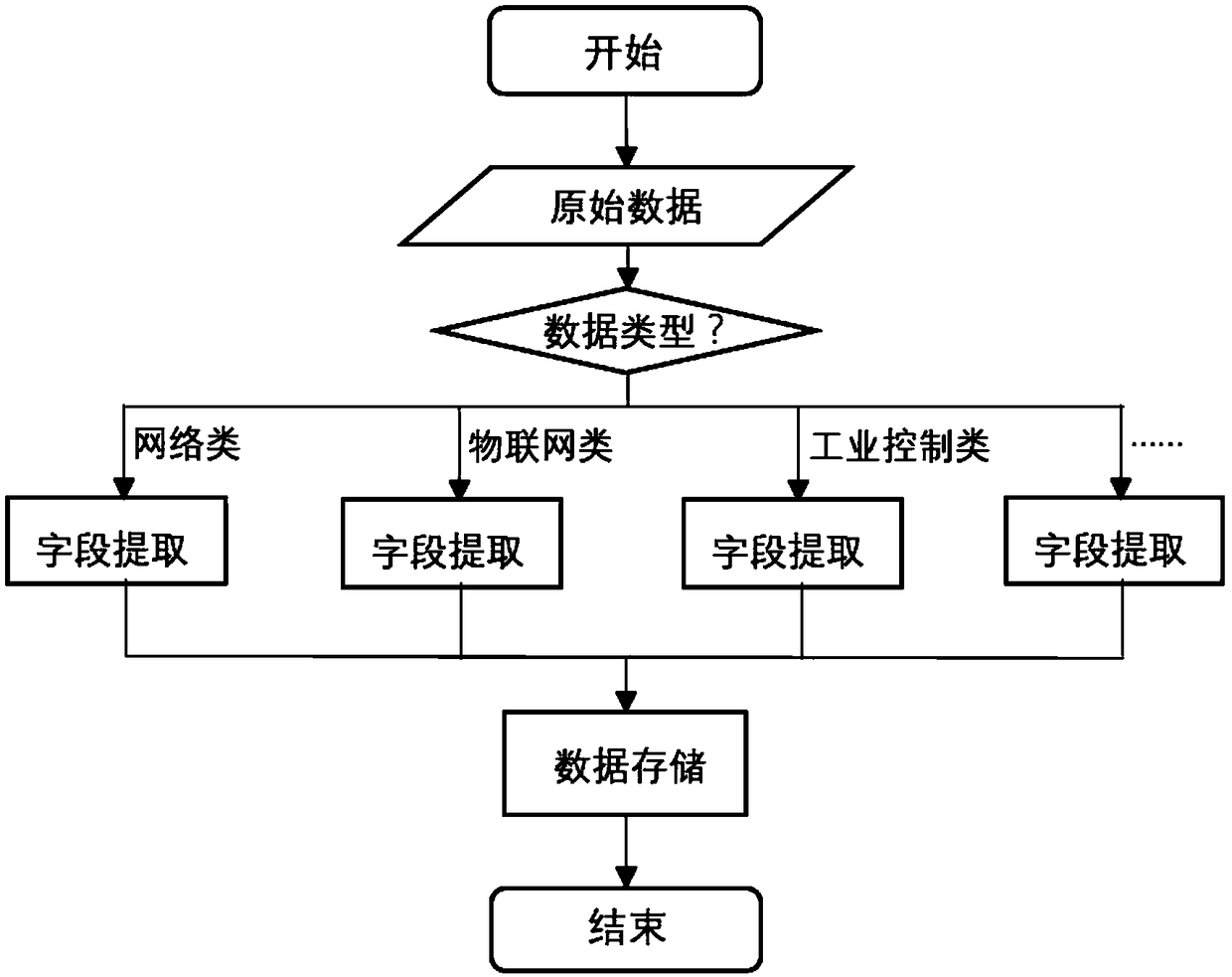
Docker-based automated honey pot construction and threat perception method
ActiveCN108900467AReduce hardware costsReduce economic lossTransmissionOriginal dataData acquisition
The invention discloses a Docker-based automated honey pot construction and threat perception method. The method comprises: step one, creating and running a data collection container; step two, carrying out formatting processing on original data according to a data processing algorithm; step three, carrying out depth model training on the formatted data; step four, carrying out data visualizationby using NodeJS as a web background; and step five, determining an unknown flow by using a threat perception technology. Therefore, functions of data collection, data processing, data visualization and the like can be completed automatically; and parameters for model training need to be adjusted manually, so that the model becomes stable and accurate.
Owner:EAST CHINA NORMAL UNIVERSITY
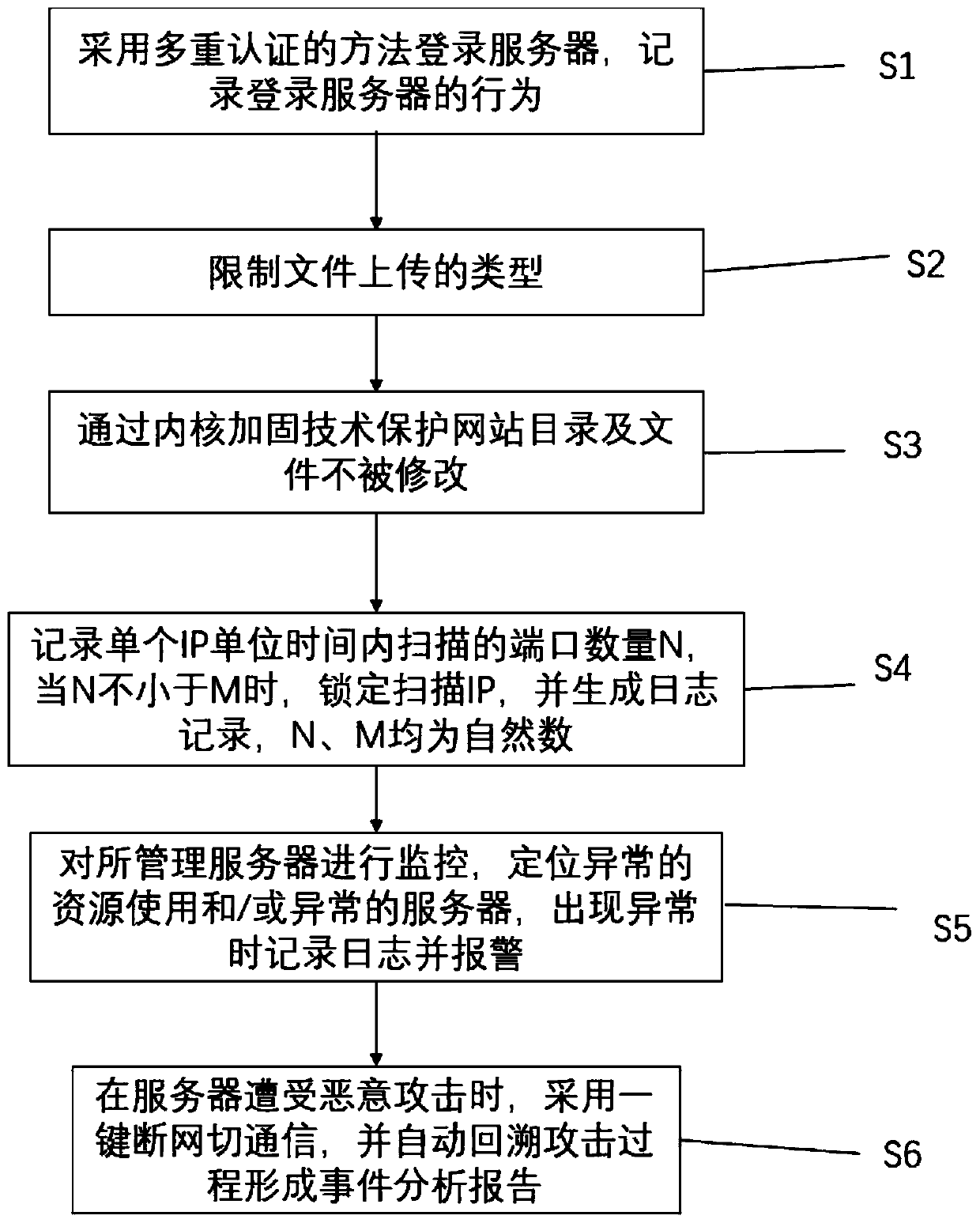
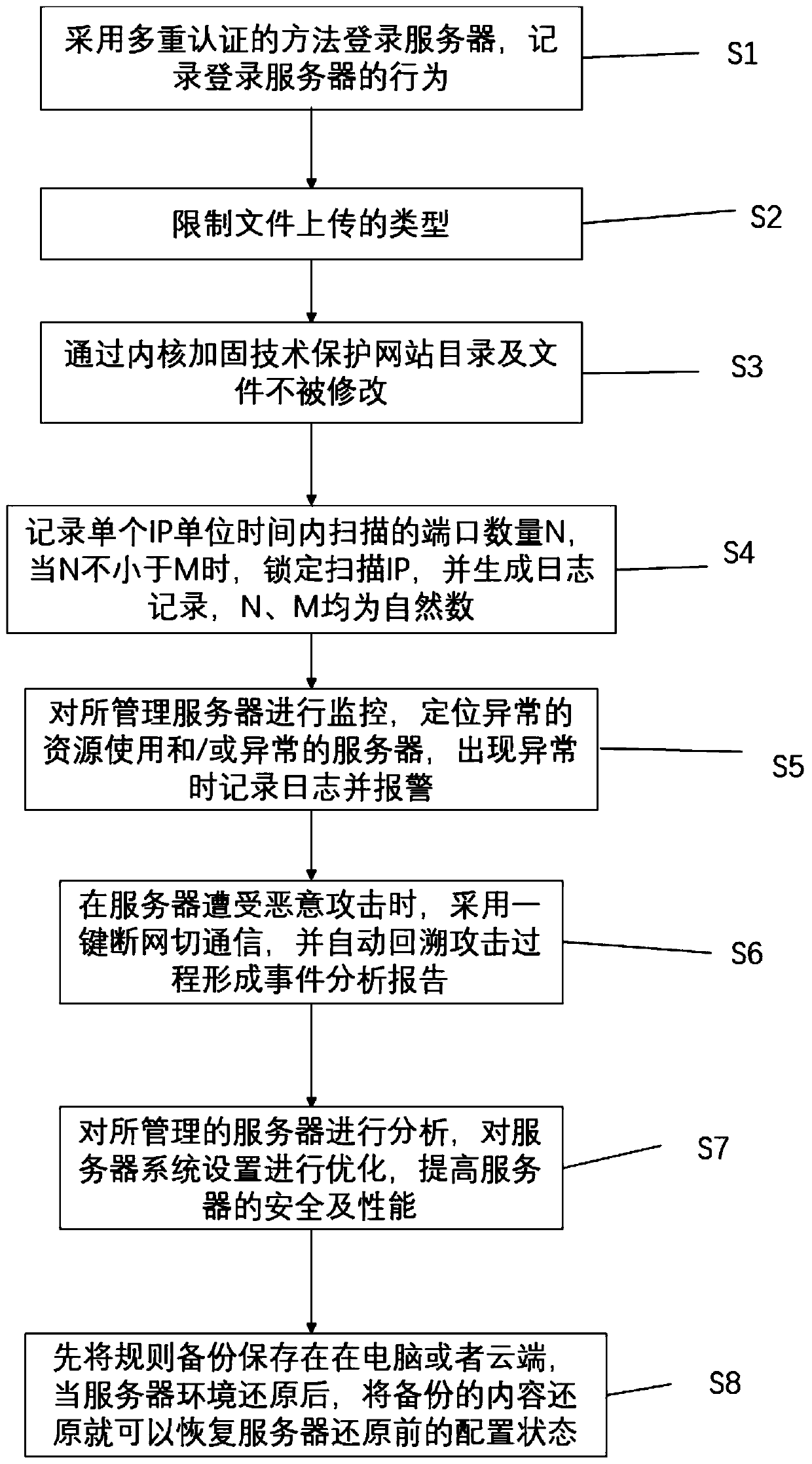
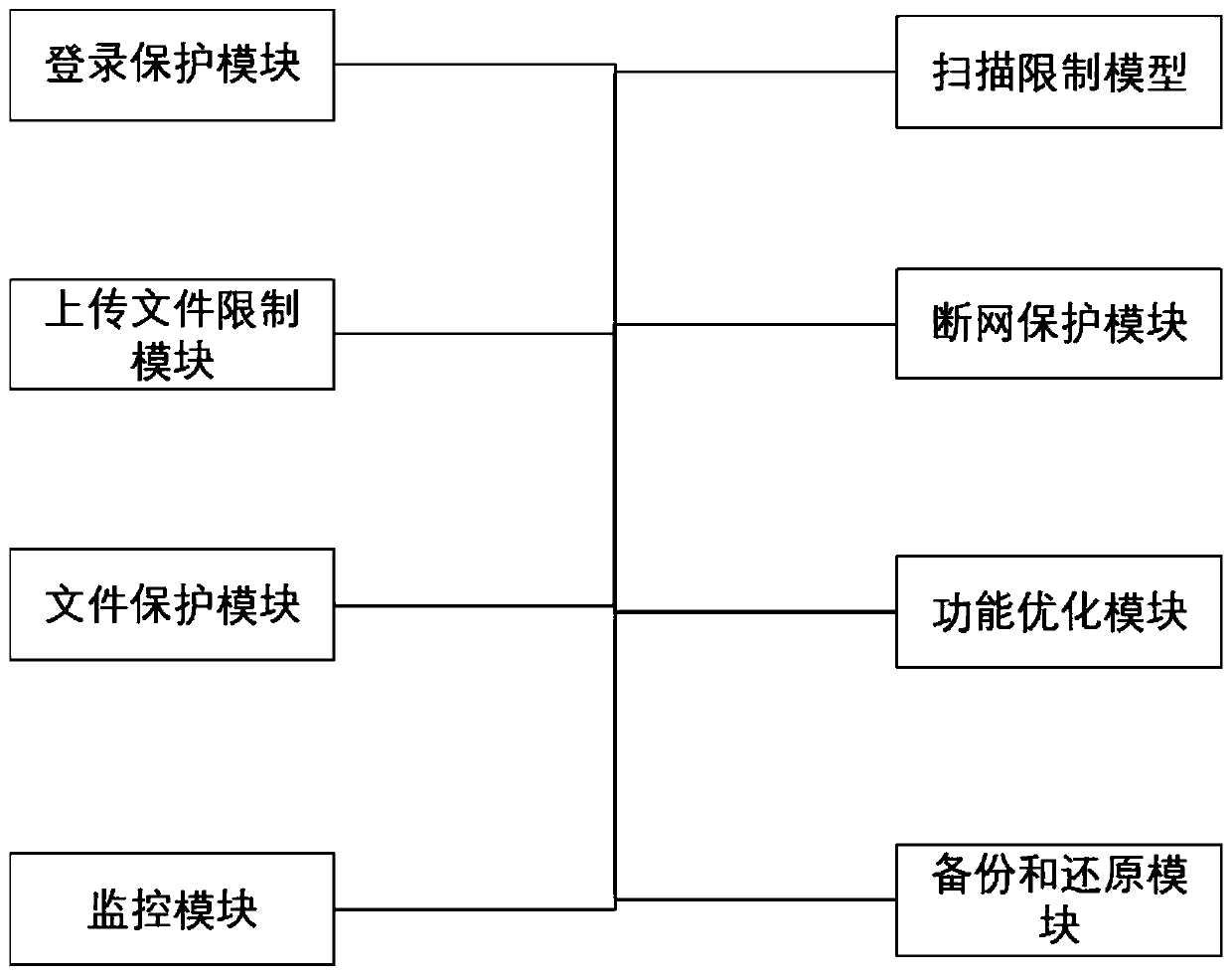
Network information security protection method and system
InactiveCN110099060AImprove securityImprove security levelTransmissionTamper resistanceRisk identification
The invention belongs to the technical field of network security, and particularly relates to a network information security protection method and system. According to the method, real-time monitoringand active protection can be carried out on data in a network system, and when external invasion is monitored, protection measures can be actively adopted to protect the server and the information security on the server. According to the method and system, comprehensive resource supervision, login behavior recording, attack recording, file tamper-proofing, emergency supervision and security supervision can be conveniently and intensively carried out on various information systems, and operation conditions, security situations, risk identification, threat perception and security disposal-attack event traceability of all the information systems can be fully grasped..
Owner:瑞森网安(福建)信息科技有限公司
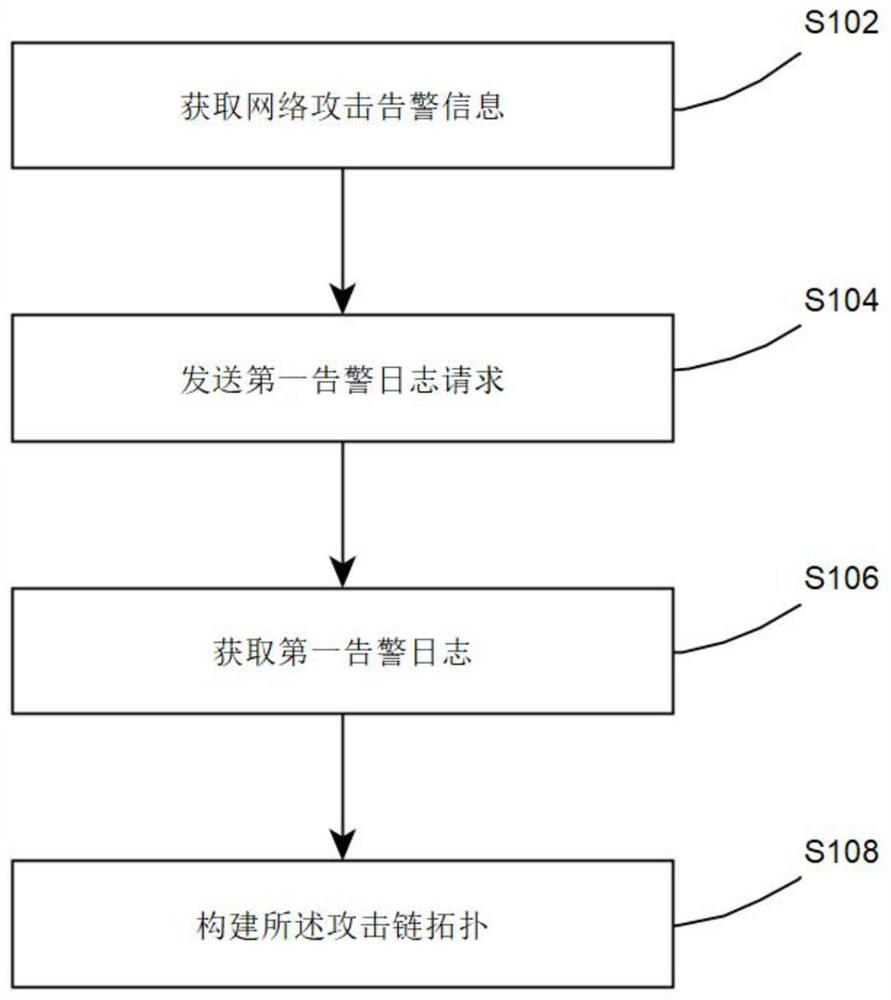
Attack chain topology construction method and device
The invention discloses an attack chain topology construction method and device, and the method comprises the steps: obtaining network attack alarm information which comprises a first alarm identification; sending a first alarm log request, wherein the first alarm log request comprises the first alarm identifier; obtaining a first alarm log, wherein the first alarm log comprises the first alarm identifier, a first source IP, a first target IP, a first trigger alarm condition and first trigger alarm time; and constructing the attack chain topology according to the first alarm log. According to the method, the attack chain topology is established, so the whole process of the security event can be visually known, the visual feeling of the attack process is improved, and the method is suitable for threat perception changes in a new normal state.
Owner:中能融合智慧科技有限公司
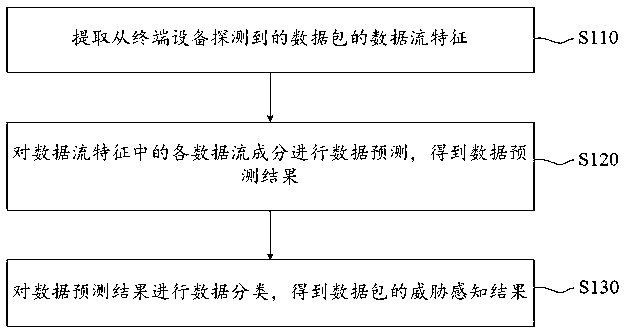
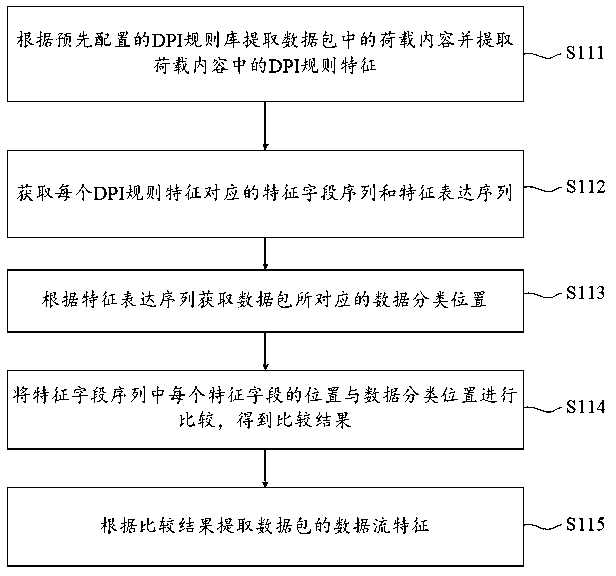
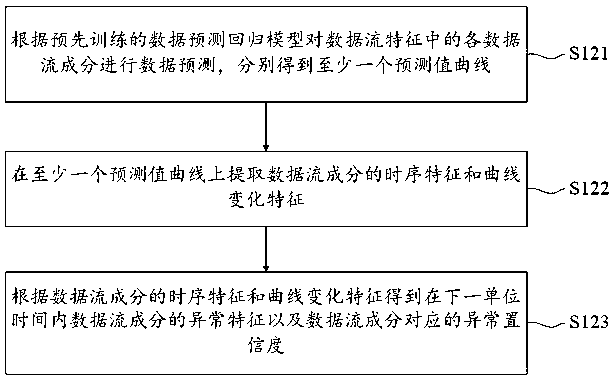
Depth data packet detection method and device and readable storage medium
ActiveCN110995769AReduce security impactRespond in a timely mannerData switching networksData packData stream
The embodiment of the invention provides a depth data packet detection method and device and a readable storage medium. Data prediction is carried out on each data stream component in data stream characteristics of a detected data packet, therefore, the threat perception situation of the data stream characteristics in the future unit time can be predicted and classified, so that the threat perception detection can timely respond to the change of the data packet, and the influence of the computer security when the data packet is quickly changed can be reduced.
Owner:上海飞旗网络技术股份有限公司
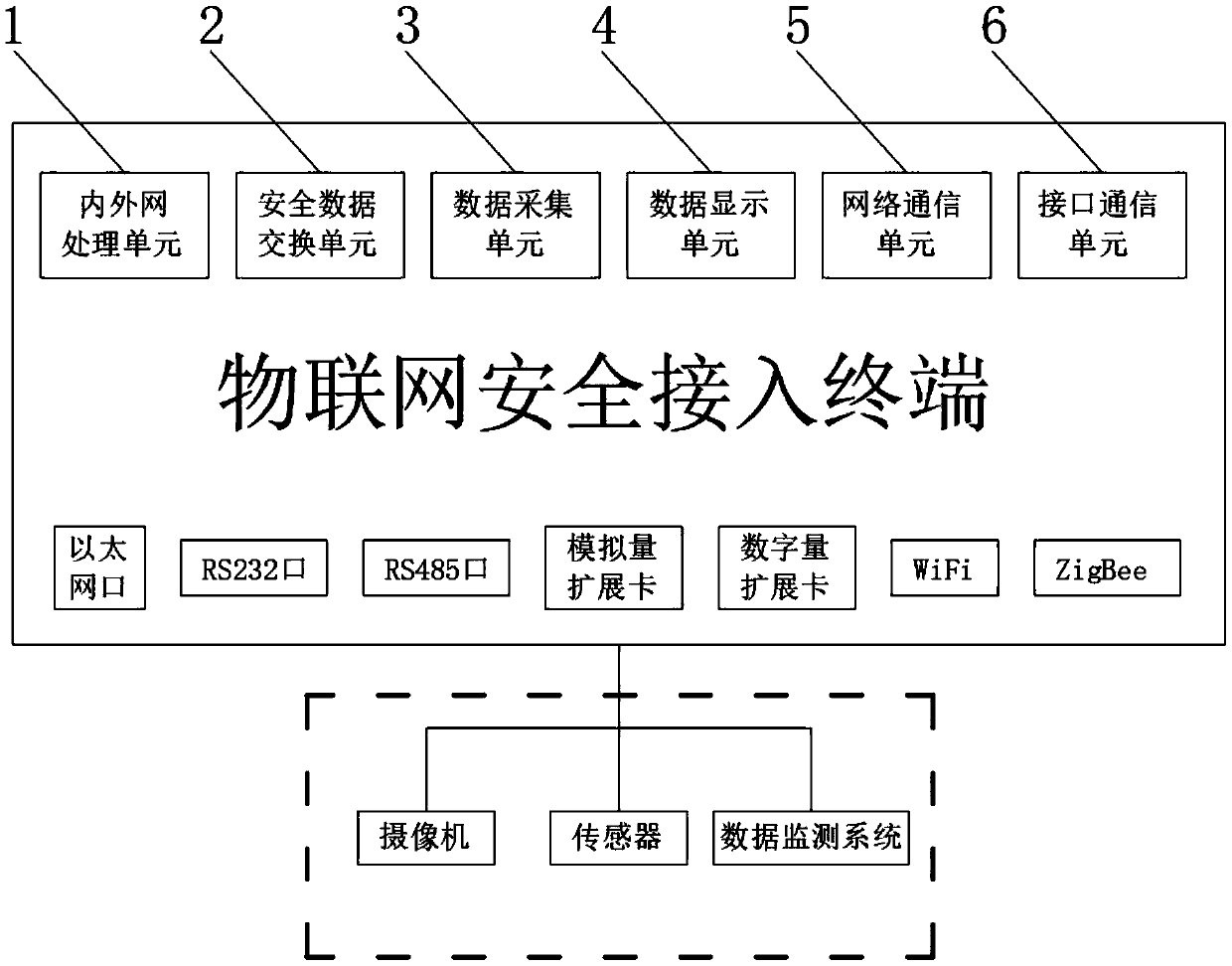
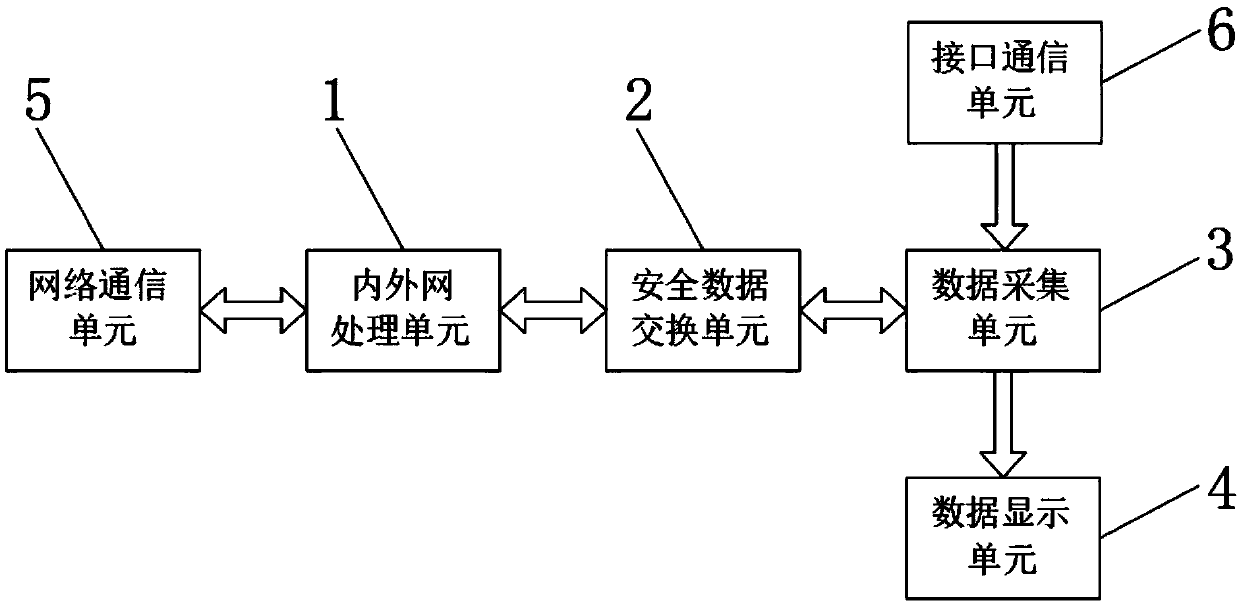
Secure access terminal to internet of things based on enterprise data acquisition
The invention discloses a secure access terminal to an internet of things based on enterprise data acquisition, which comprises an internal and external network processing unit, a secure data exchangeunit, a data acquisition unit, a data display unit, a network communication unit and an interface communication unit. The secure access terminal to the internet of things provides rich software and hardware interfaces. The secure access terminal to the internet of things can have the capabilities of secure access, safe management and threat perception of various sensor terminal devices and industrial control systems of an enterprise front end, realizes the exchange between an internal network and an external network and the physical isolation, and also realizes the protocol isolation, therebyavoiding the occurrence of an inter-network transmission event and a compromise event with security risk in a real sense.
Owner:ANHUI HEXIN TECH DEV
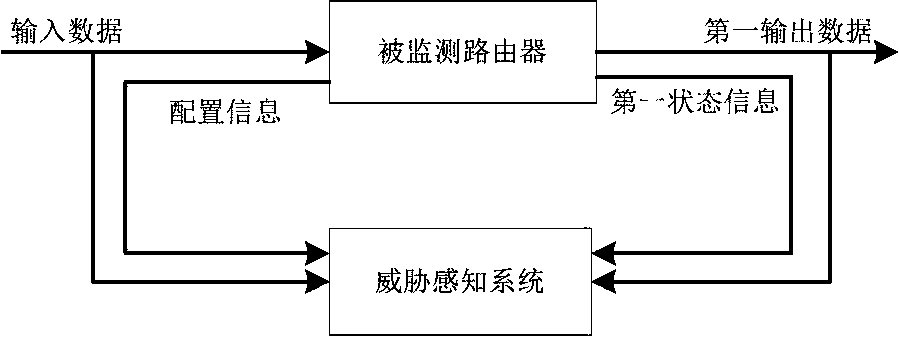
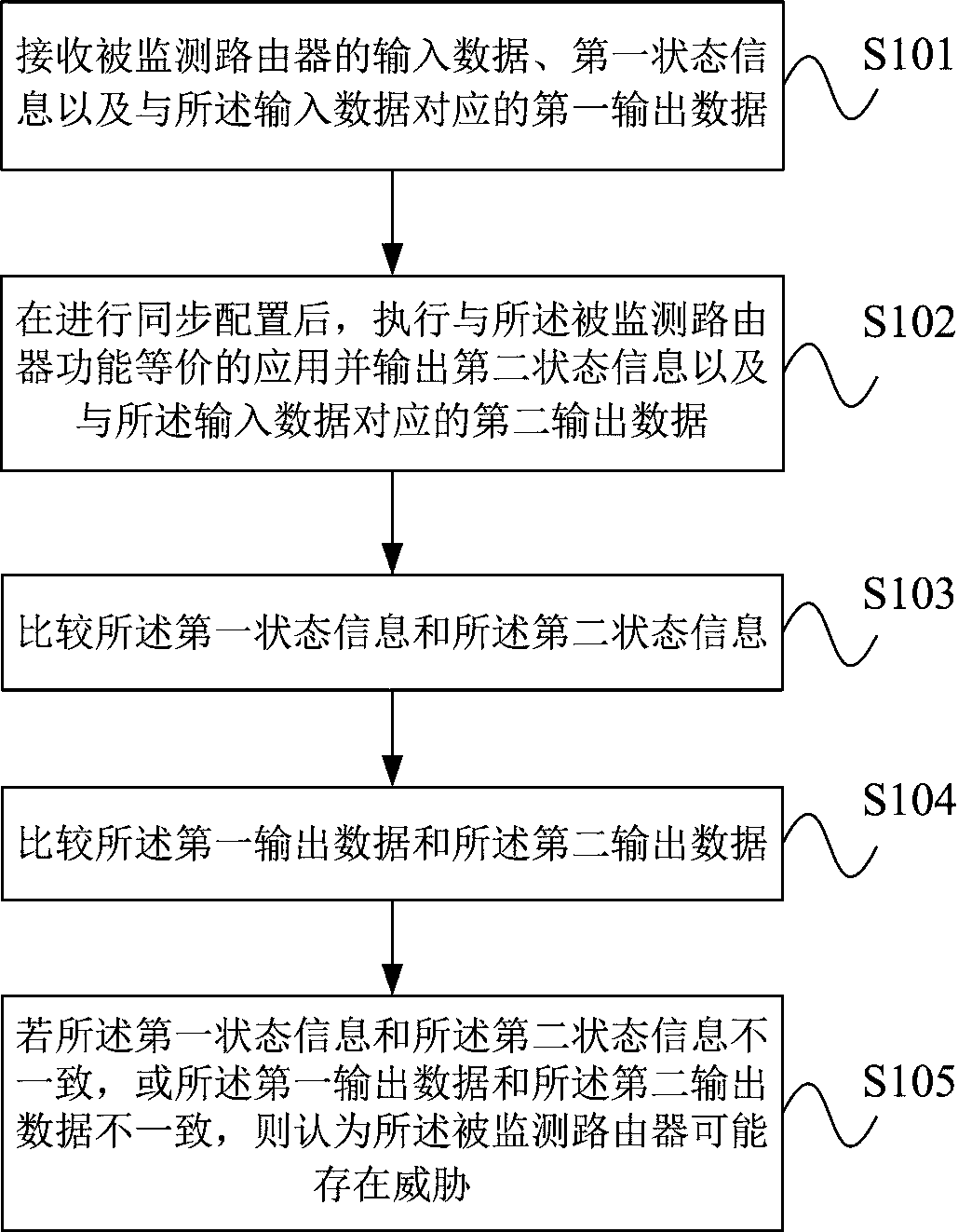
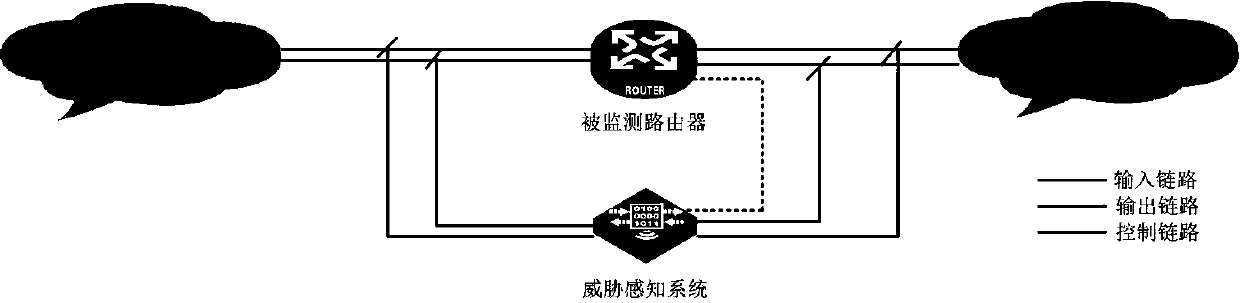
Router threat perception method and system
The invention provides a router threat perception method and system. The method comprises the following steps that: the threat perception system is consistent with the input of a monitored router; theoutput data of the monitored router is sent to the threat perception system at the same time; wherein the configuration information of the monitored router needs to be synchronously configured to thethreat perception system; and the state information of the monitored router needs to be timely collected to the threat perception system. The output data and state of the monitored router are compared with the output data and state of the threat sensing system, if the output data or state of the monitored router is inconsistent with the output data or state of the threat sensing system, the monitored router may have a threat, and alarm information is sent to a management system. The threat perception system comprises an input processing unit, a function equivalent actuator unit, a state comparison unit, an output comparison unit and an analysis alarm unit. According to the method, the problem of high difficulty in judging router threats caused by various vulnerability and attack technicalmeans can be solved, and unknown vulnerabilities and zero-day attacks can be perceived.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Network security operation management platform
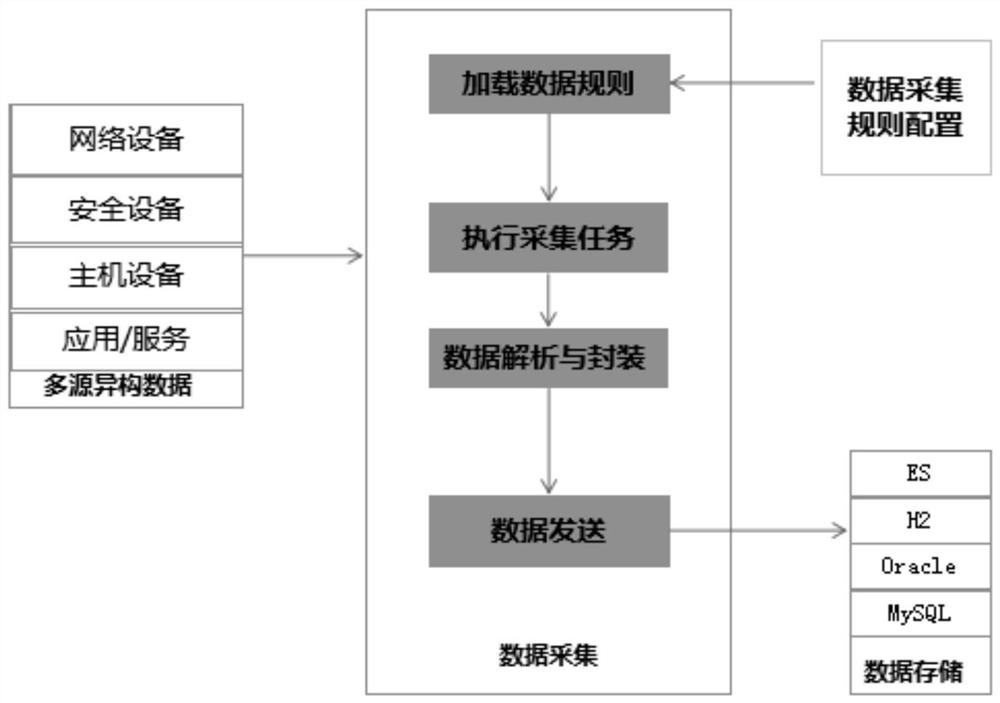
PendingCN114090374ARich data supportReduce alarm redundancyDatabase management systemsHardware monitoringMulti source dataCorrelation analysis
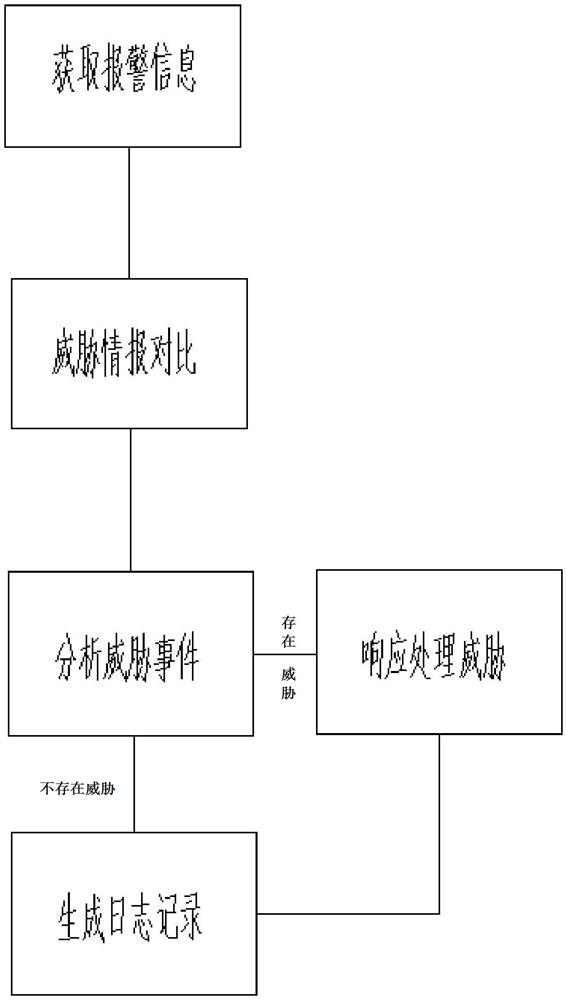
The embodiment of the invention provides a network security operation management platform. The network security operation management platform comprises a data acquisition and treatment module, a threat perception and analysis module, a monitoring alarm module and a response processing module. The technical scheme has the beneficial technical effects that the data acquisition technology adopted by the invention can comprehensively obtain multi-source security information, and provides rich data support for discovery of security threats. The threat perception and analysis technology is adopted, multi-source data are fused for correlation analysis, alarm redundancy can be effectively reduced, and the threat identification accuracy is improved. According to the asset management technology, network risks are analyzed from the aspect of assets, and digital management of the assets is achieved. By adopting a security event response technology, customization of an event disposal process and tracking of the disposal process are realized, and network security is improved to realize disposal efficiency.
Owner:BEIJING XJ ELECTRIC
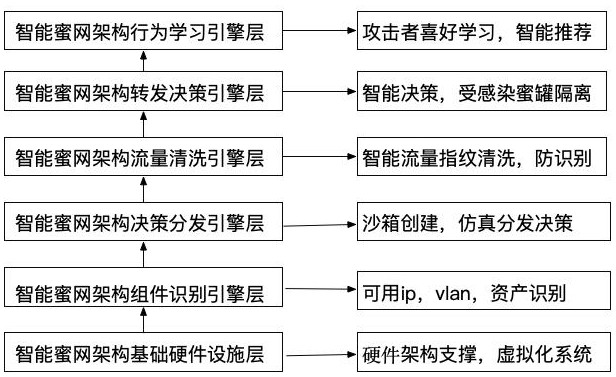
Implementation method of dynamic intelligent self-adaptive honeynet
The invention discloses an implementation method of a dynamic intelligent self-adaptive honeynet, which comprises a dynamic intelligent self-adaptive honeynet architecture. The dynamic intelligent self-adaptive honeynet architecture comprises an intelligent honeynet architecture basic hardware facility layer, an intelligent honeynet architecture component recognition engine layer, an intelligent honeynet architecture decision distribution engine layer, an intelligent honeynet architecture flow cleaning engine layer, an intelligent honeynet architecture forwarding decision engine layer and an intelligent honeynet architecture behavior learning engine layer. Through mutual configuration and cooperation of multiple engines, the flexibility of the honeynet is improved, and the score of the attacker connection activity, the self-adaptive attack and the network environment are calculated according to the algorithm weight. Aiming at the problems of a traditional honeypot, resources are reasonably called and a honeynet most suitable for a client is deployed according to the actual situation of the client and the strength degree of an attack technique, and a balance point is achieved between the threat perception effect and the resource utilization efficiency.
Owner:江苏天翼安全技术有限公司
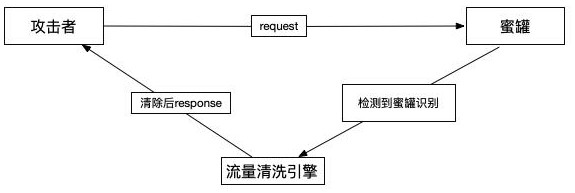
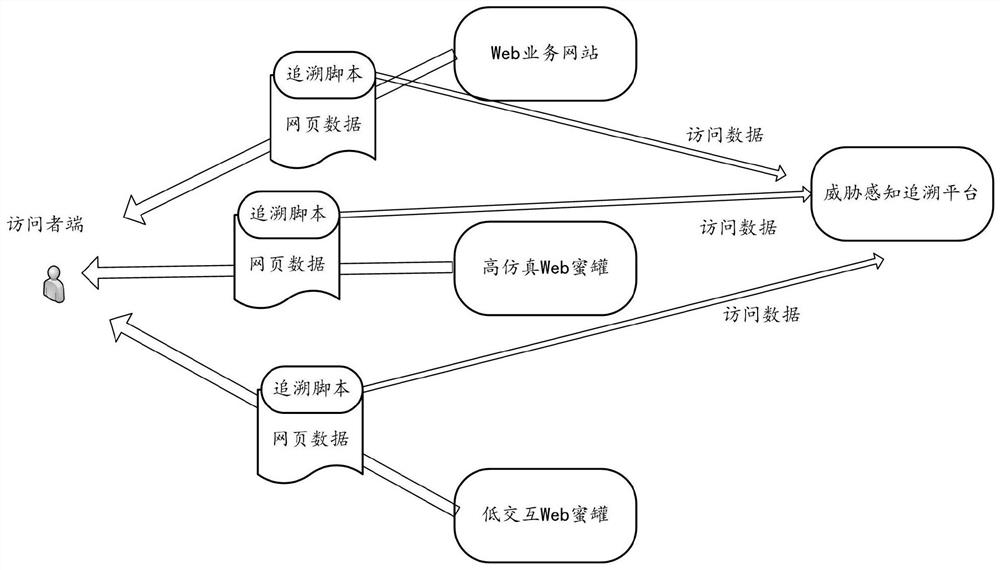
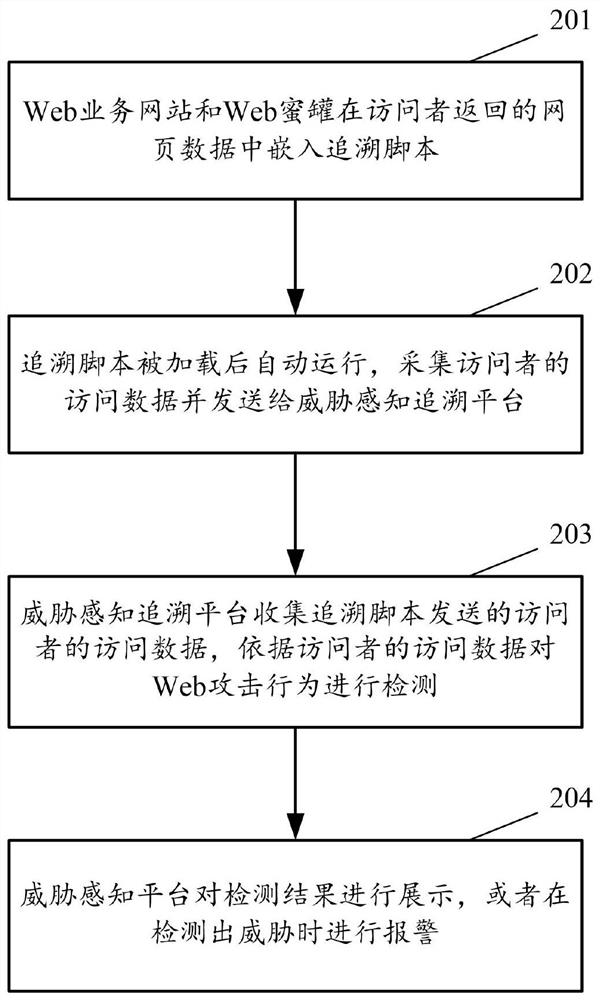
Web attack behavior detection method and system
The invention provides a Web attack behavior detection method and system. The system comprises a Web service website, a Web honeypot and a threat perception tracing platform. The Web service website and the Web honeypot are used for embedding a tracing script into webpage data returned to a visitor; the tracing script automatically runs after being loaded and is used for collecting access data ofa visitor and sending the access data to the threat perception tracing platform; and the threat perception tracing platform is used for collecting the access data of the visitor sent by the tracing script and detecting the Web attack behavior according to the access data of the visitor. According to the invention, the detection effect of Web attack behaviors can be effectively improved.
Owner:RIVER INFORMATION TECH SHANGHAI CO LTD
Defense honeypot-based security threat active sensing method
ActiveCN108446557AThe same threat perception and identification capabilitiesImprove efficiencyPlatform integrity maintainanceTransmissionActive perceptionAutomaton
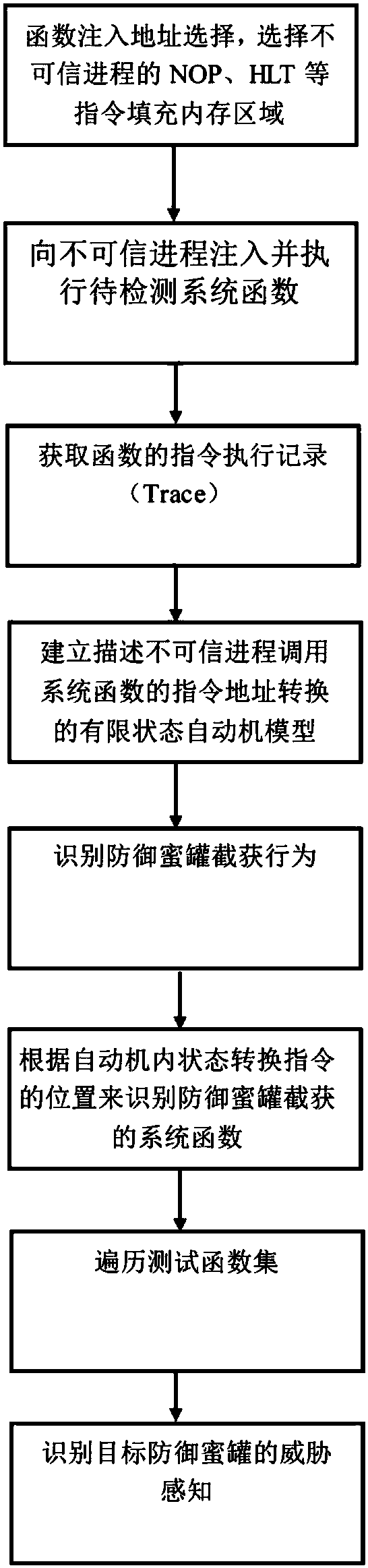
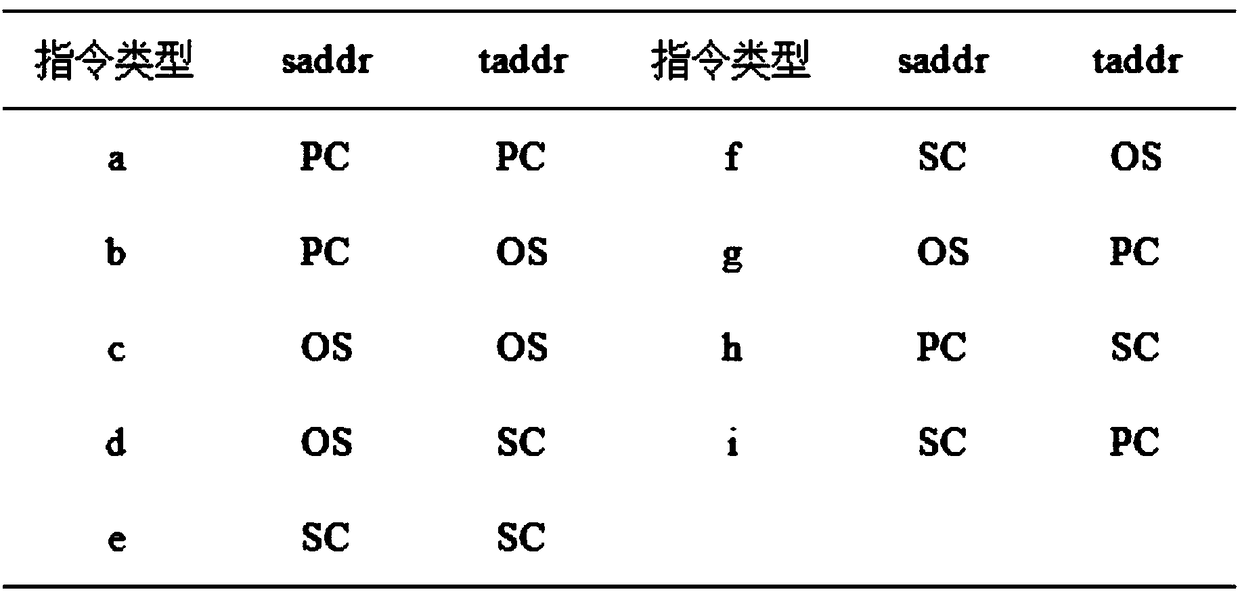
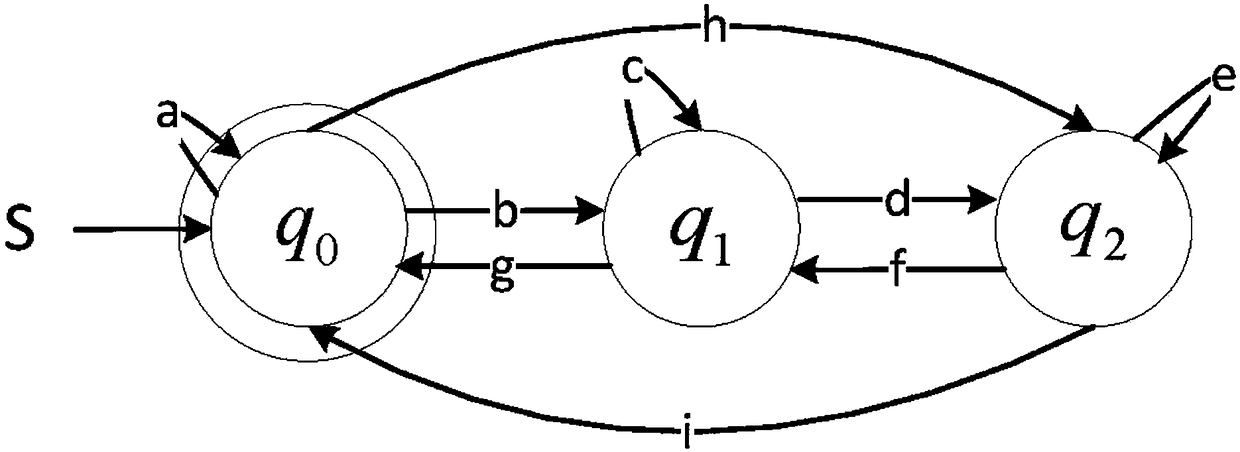
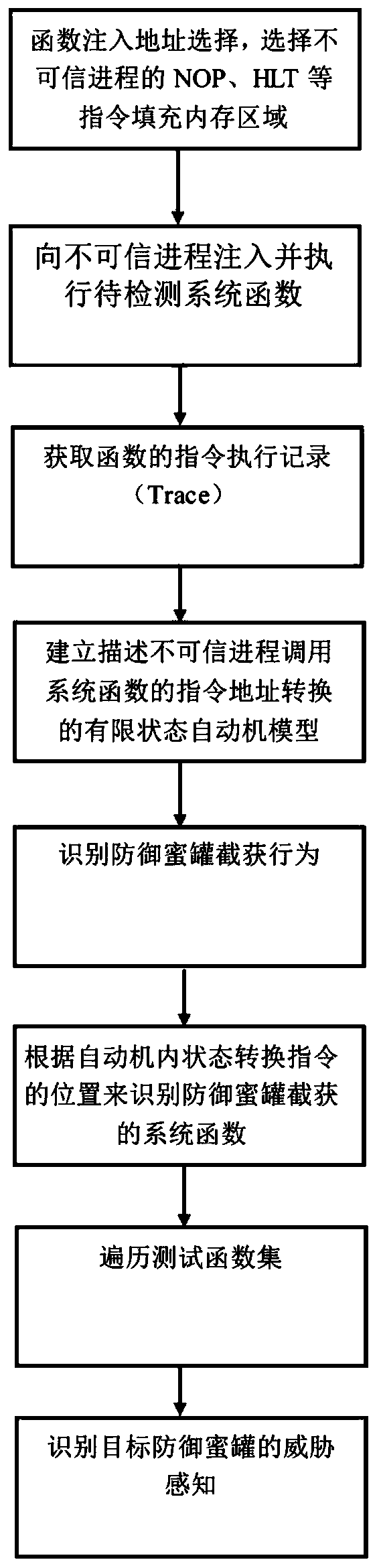
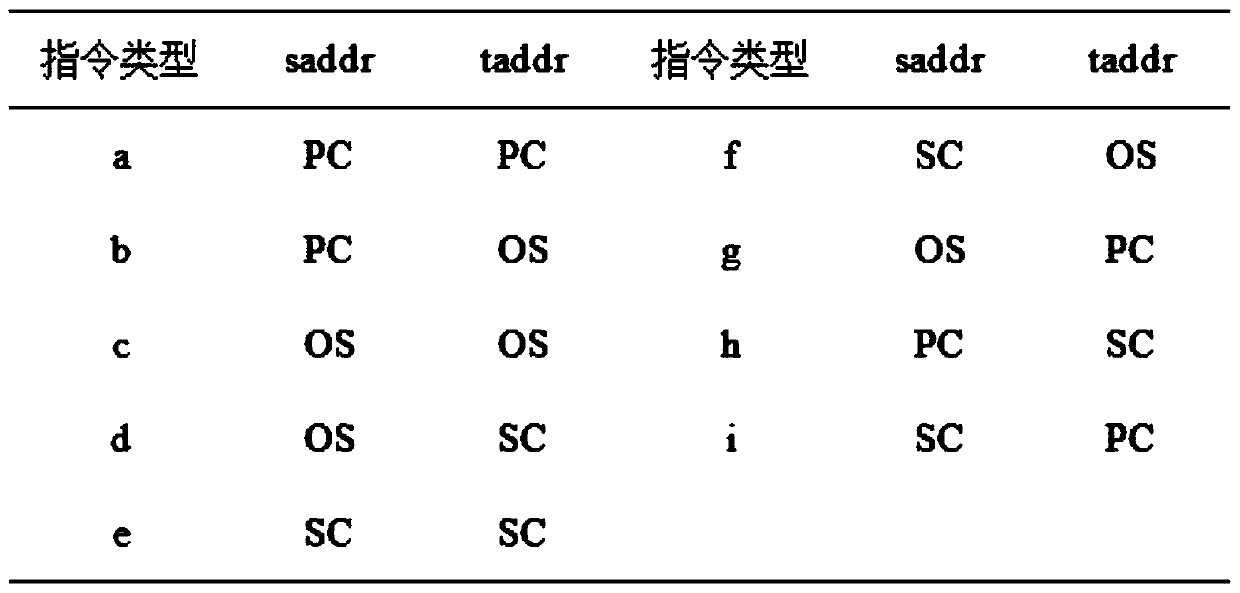
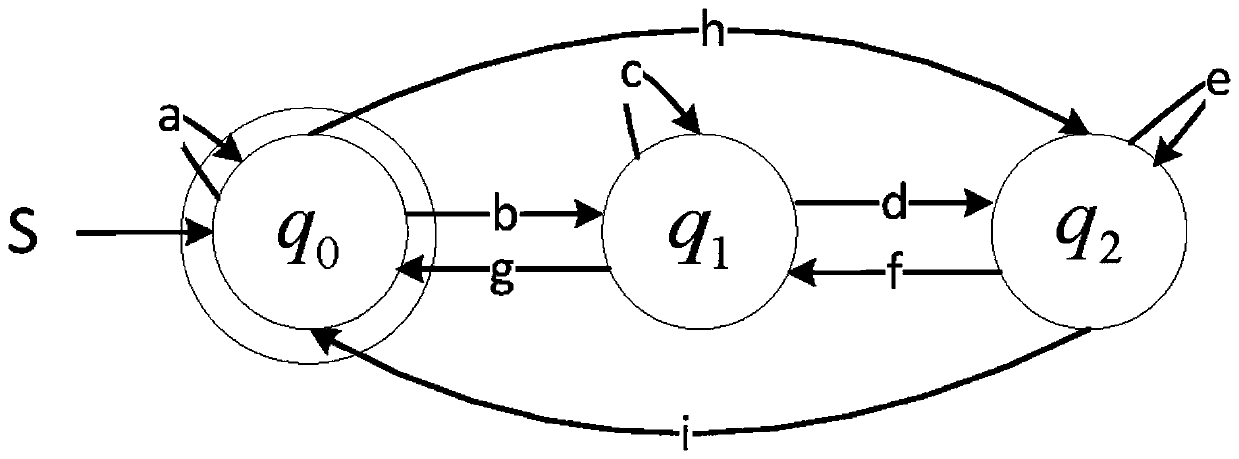
The invention discloses a defense honeypot-based security threat active sensing method. Based on understanding of a Hook technology, whether a defense honeypot intercepts and captures a test functionor not is judged by analyzing an execution Trace of a system function; firstly the to-be-detected system function is injected into an untrusted process and is executed to obtain an instruction execution record (Trace) of the function; further according to a characteristic that the defense honeypot intercepts and captures the Trace of the system function, an address space finite state automata is designed, and the obtained Trace is analyzed in the automata to judge the system function intercepted and captured by the defense honeypot; and finally, a test function set is traversed to identify threat sensation of the target defense honeypot. The threat sensation of the target defense honeypot can be identified; and compared with an existing threat sensation identification method, the method has the same defense honeypot-based threat sensation identification capability, and is more automatic and more efficient.
Owner:江苏中天互联科技有限公司
Network attack monitoring system based on multi-source information analysis
PendingCN112511387AAccurately identify potential safety hazardsSensitive Threat AwarenessData switching networksInformation analysisNetwork security management
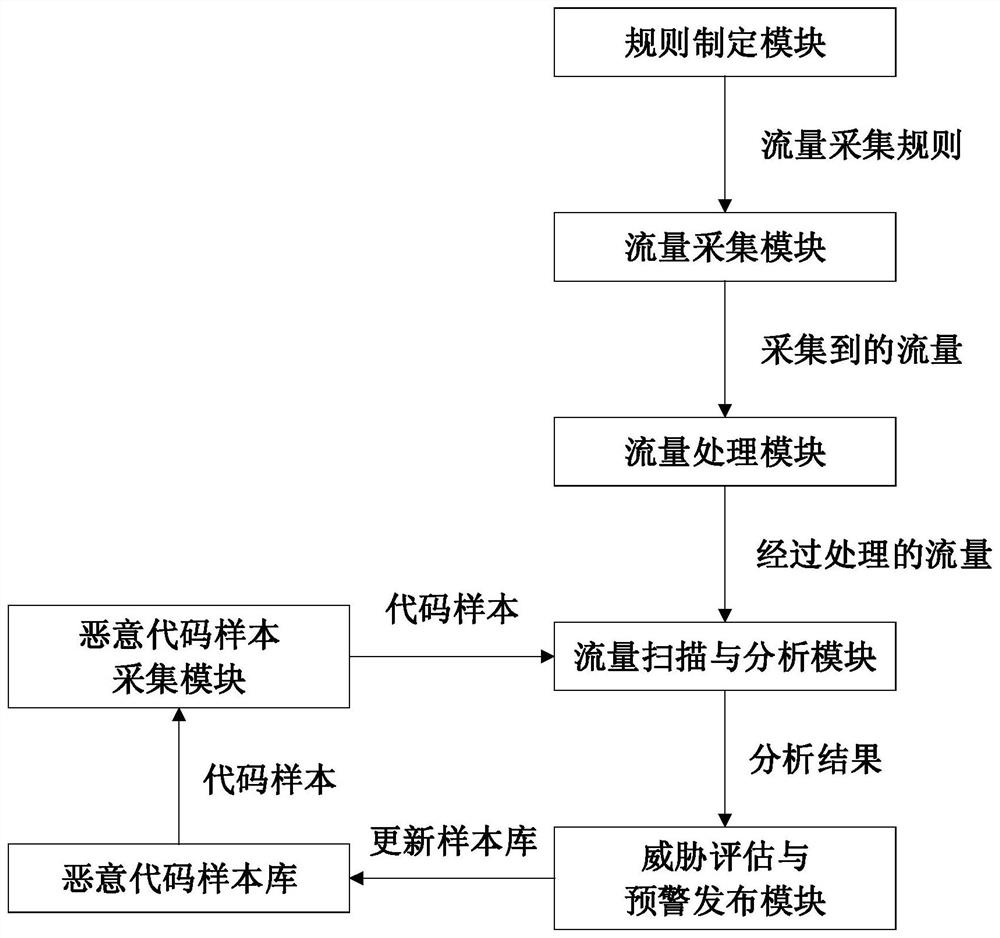
The invention belongs to the technical field of computers, and particularly relates to a network attack monitoring system based on multi-source information analysis. The system comprises a rule makingmodule, a flow acquisition module, a flow processing module, a malicious code sample acquisition module, a flow scanning and analysis module and a threat assessment and early warning release module.The method has the technical effects that the network threats are comprehensively perceived, specifically, based on flow analysis, network potential safety hazards are accurately recognized, sensitivenetwork threat perception capacity is constructed, and the comprehensive network security situation is displayed. Timely loss stopping and quick response: providing a network security threat assessment report through network attack security analysis, assisting network security management personnel to take corresponding treatment measures in time, and preventing the situation from continuing to develop.
Owner:北京京航计算通讯研究所
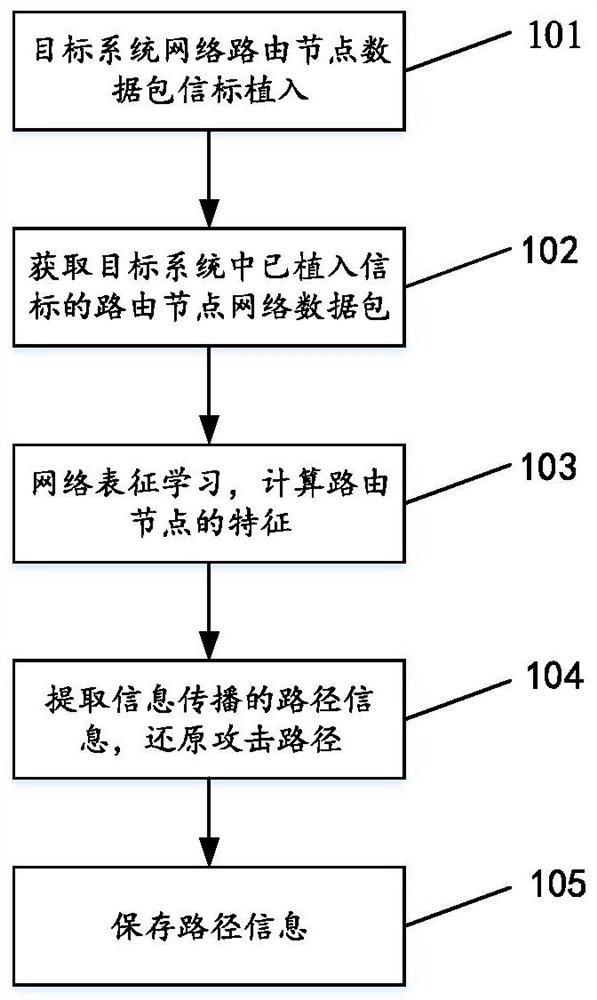
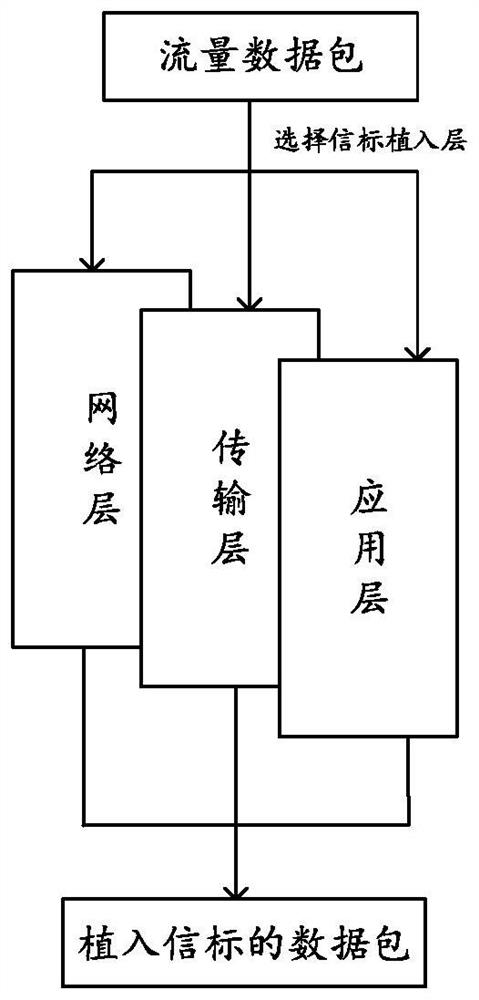
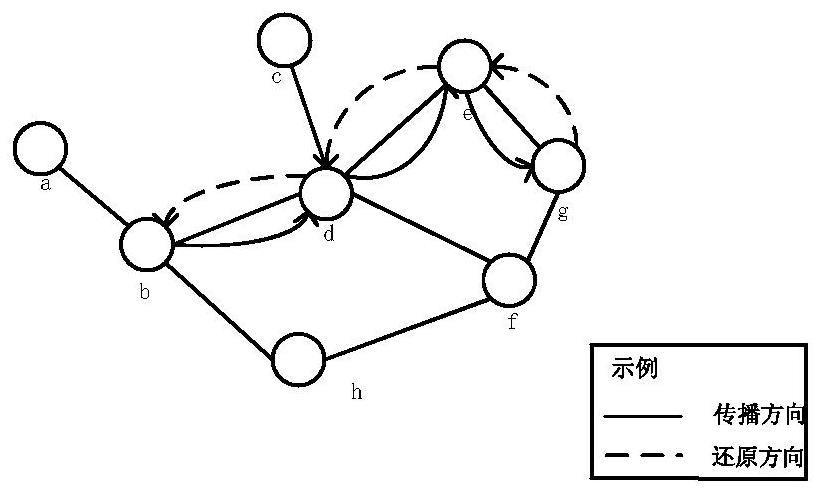
Multilayer fusion beacon detection and path restoration method and device
ActiveCN114650171AReduce in quantityDistinct Routing Node FeaturesNeural architecturesNeural learning methodsPathPingData pack
The invention discloses a multi-layer fusion beacon detection and path restoration method and device. The method comprises the following steps: implanting a multi-layer fusion beacon in a target system network routing node data packet; obtaining a routing node network data packet of an implanted beacon in a target system; network characterization learning is carried out on the network data packet with the implanted beacons, and the features of routing nodes are calculated; extracting path information of information propagation according to the characteristics of the routing node, and restoring an attack path; and storing the restored path information. Therefore, according to the method, the network representation learning model is introduced, the network routing nodes are vectorized, and the characteristics of different routing nodes are considered, so that the obtained vector form can have representation and reasoning capabilities in the vector space, and then the reduced attack path is calculated by using the graph convolutional neural network; the threat perception and prediction capability of the network can be improved, and the security of the network is improved.
Owner:NO 15 INST OF CHINA ELECTRONICS TECH GRP +2
Threat-driven network attack detection and response method
PendingCN112039865AQuick Response Processing CapabilityCharacter and pattern recognitionTransmissionAttackProtection mechanism
The invention relates to a threat-driven network attack detection and response method, and belongs to the technical field of information security. Aiming at the defects of a traditional static defensetechnology system and an emergency threat response protection mechanism, the invention designs a threat-driven security response method according to a PPDR model starting from the attack thought andprocess of an attacker on the basis of research and analysis of a universal network attack process. The invention designs a threat-based attack detection and response method, so as to establish a threat dynamic response system which is linked internally and externally, is mainly used for prevention and has overall threat perception and rapid response processing capabilities in the near future.
Owner:BEIJING INST OF COMP TECH & APPL
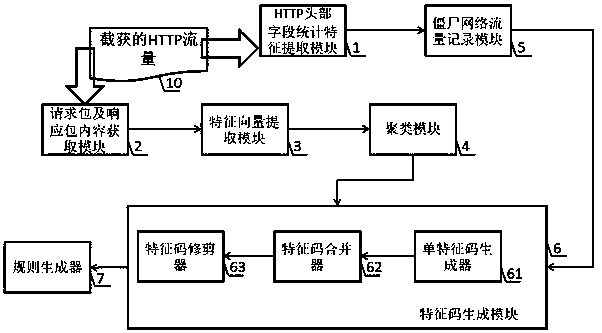
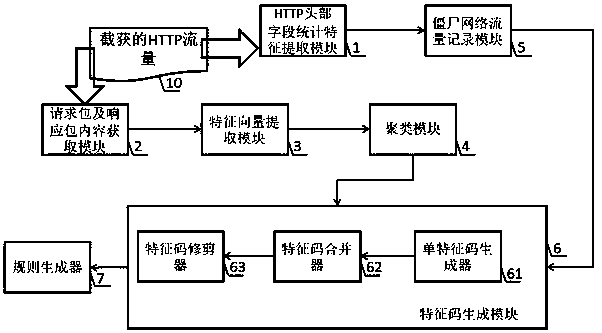
Botnet detection device based on HTTP first question and answer packet clustering analysis
InactiveCN111182002AReduce overheadExtensive and accurate detectionTransmissionFeature extractionInternet traffic
The invention discloses a botnet detection device based on HTTP first question and answer packet clustering analysis, and relates to the field of information technology. The botnet detection device iscomposed of an HTTP head field statistical feature extraction module, a botnet traffic recording module, a request packet and response packet content acquisition module, a feature vector extraction module, a clustering module, a feature code generation module and a rule generator, wherein the feature code generation module consists of a single feature code generator, a feature code combiner and afeature code trimmer. The botnet detection device does not depend on priori knowledge, does not need a large amount of manual intervention, and can automatically extract and generate high-quality feature codes from HTTP botnet traffic. The feature code detection can be added into an intrusion detection system to be used for rapid and wide botnet threat perception and botnet family classification,and wide and rapid botnet host discovery is achieved.
Owner:BEIJING ACT TECH DEV CO LTD
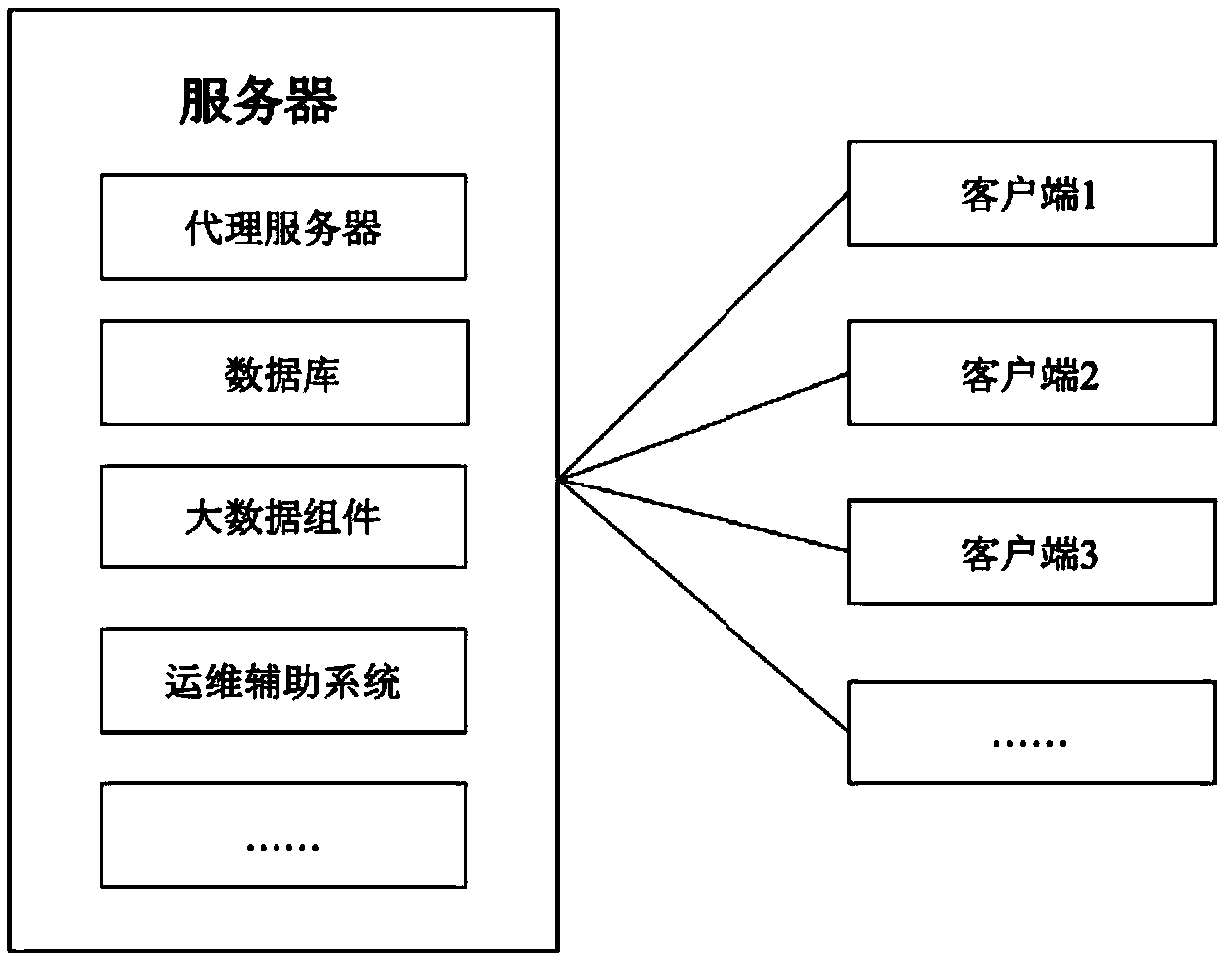
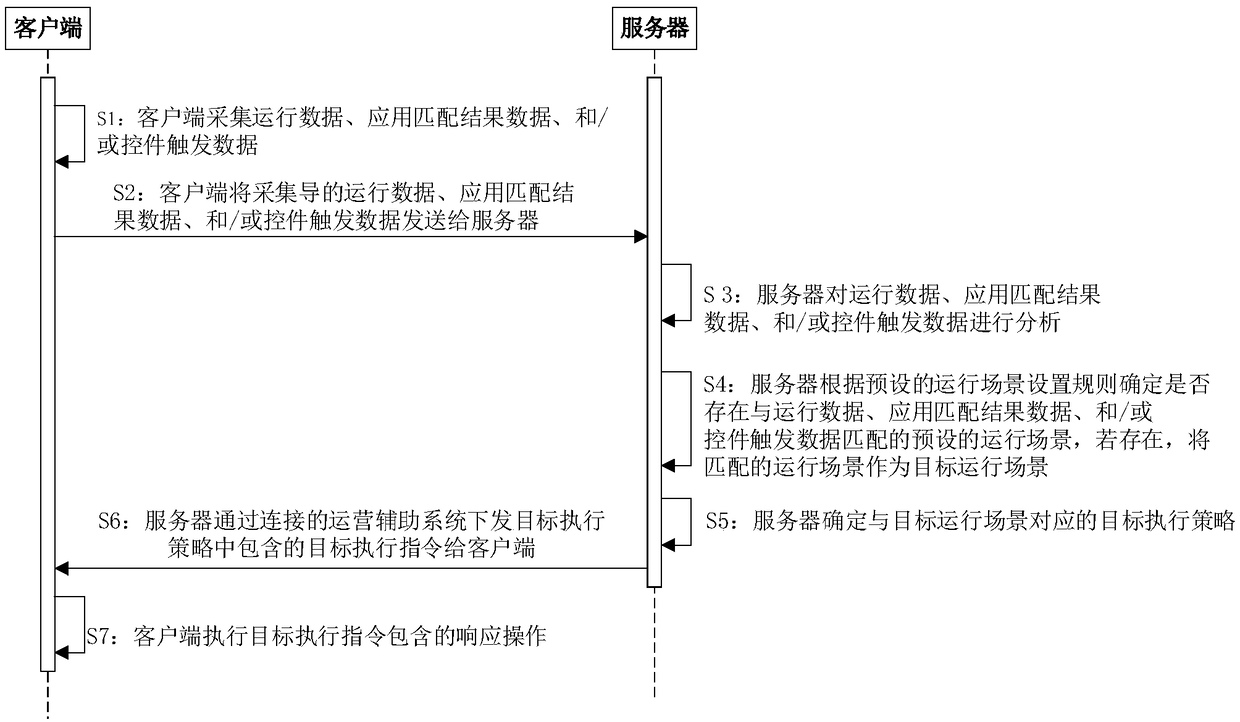
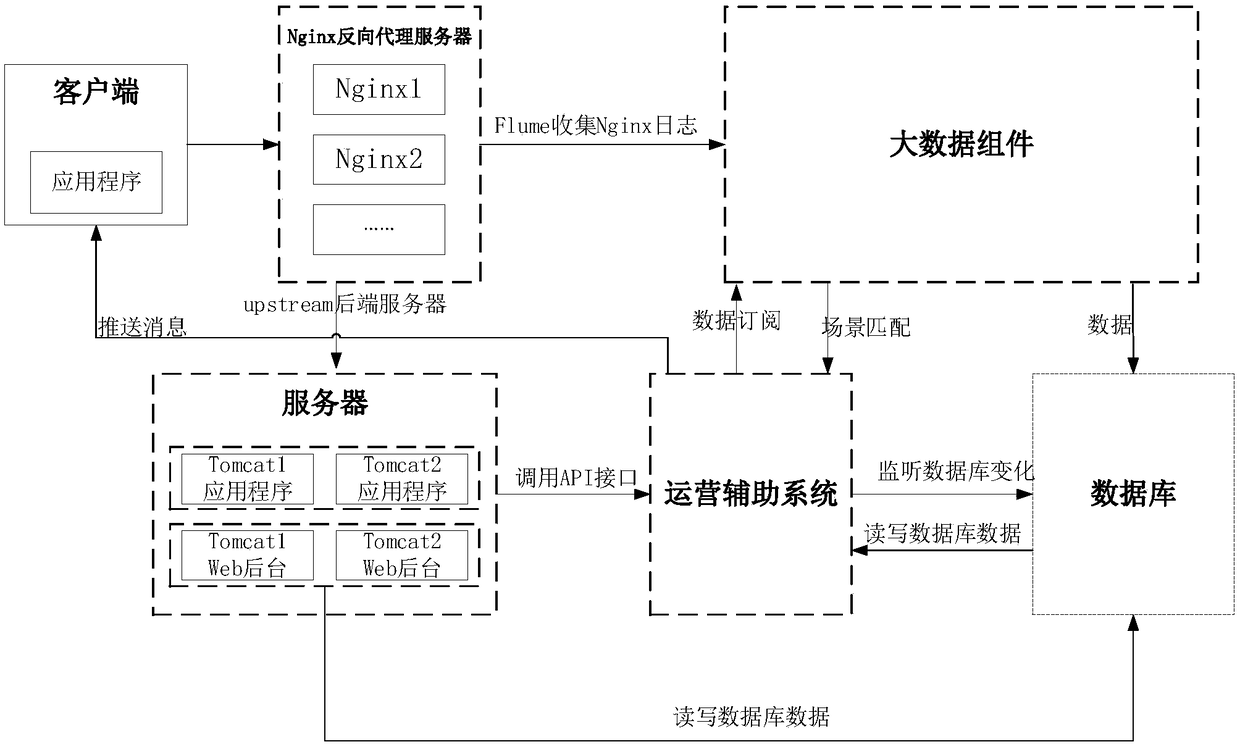
Threat perception method and system based on operating scenario analysis
ActiveCN109327433AImprove experienceEasy to identifyPlatform integrity maintainanceTransmissionData matchingClient-side
The embodiments of the invention disclose a threat perception method based on operating scenario analysis, based on a system comprising at least one client and a server. The method comprises: the server receiving operating data, application matching result data and / or control trigger data uploaded by the client, analyzing the operating data, the application matching result data and / or the controltrigger data to determine whether a preset operating scenario that matches the operating data, the application matching result data and / or the control trigger data is present, using the matching operating scenario as a target operating scenario, determining a target execution strategy corresponding to the target operating scenario, and transmitting a target execution instruction included in the target execution strategy to the client by an operation assistance system; and the client executing a response operation included in the target execution instruction after receiving the target executioninstruction. The method and the system can improve the recognition efficiency of the security risk of an application during use, and improve the defense ability against the unknown threat.
Owner:北京智游网安科技有限公司
Big data processing method and system based on threat perception, and cloud platform
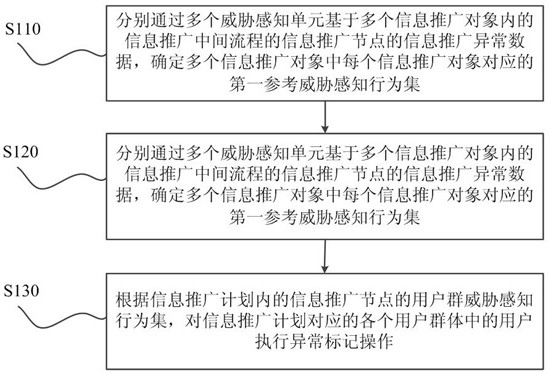
InactiveCN112950439ACutting costsShort processData processing applicationsDigital data information retrievalOperations researchData science
The embodiment of the invention provides a big data processing method and system based on threat perception, and a cloud platform. An information promotion plan occupied by operation is divided into scattered information promotion objects, and the number of information promotion intermediate flows in one information promotion object is smaller than the number of information promotion intermediate flows in the whole information promotion plan, so the process of determining a first reference threat perception behavior set corresponding to one information promotion object through a threat perception unit is faster, and the determination of first reference threat perception behavior sets corresponding to the plurality of information promotion objects is synchronously processed through different threat perception units, so that the cost of threat perception can be reduced, the cost of determining the user group threat perception behavior set of the information promotion node in the information promotion plan is reduced, the efficiency of generating the user group threat perception behavior set is improved, and the reliability of information promotion service operation is improved.
Owner:林燕东
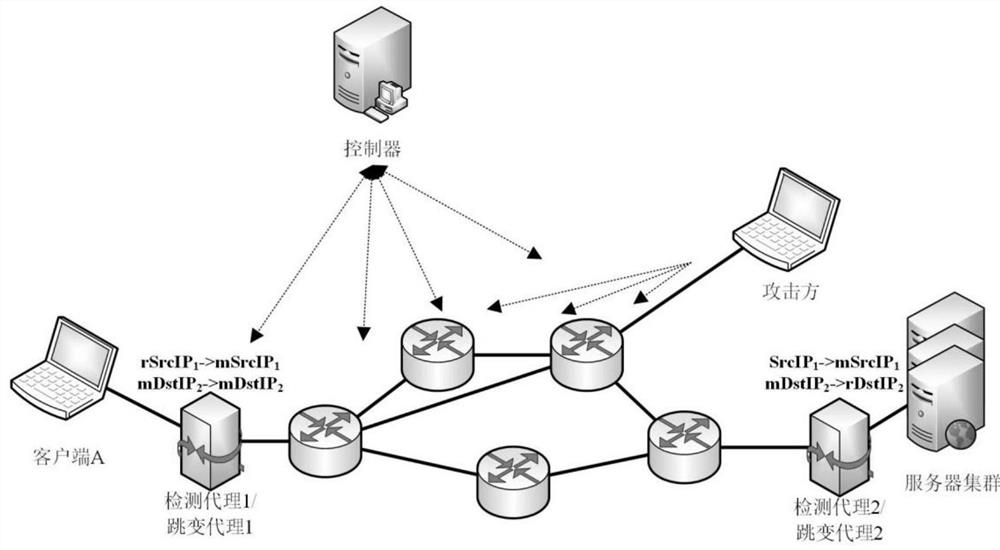
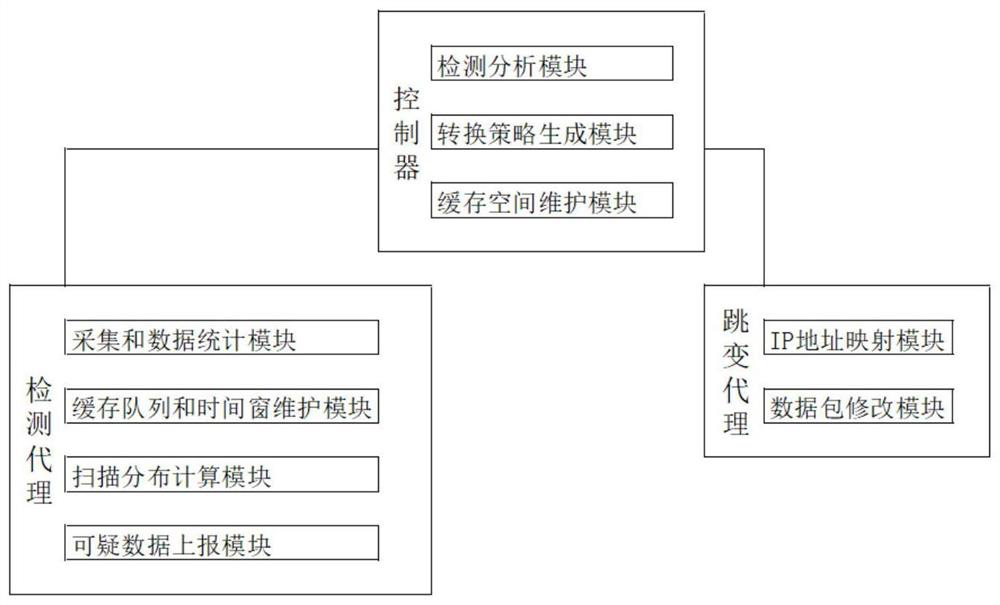
Multi-attribute self-adjusting network transformation system and method based on SDN
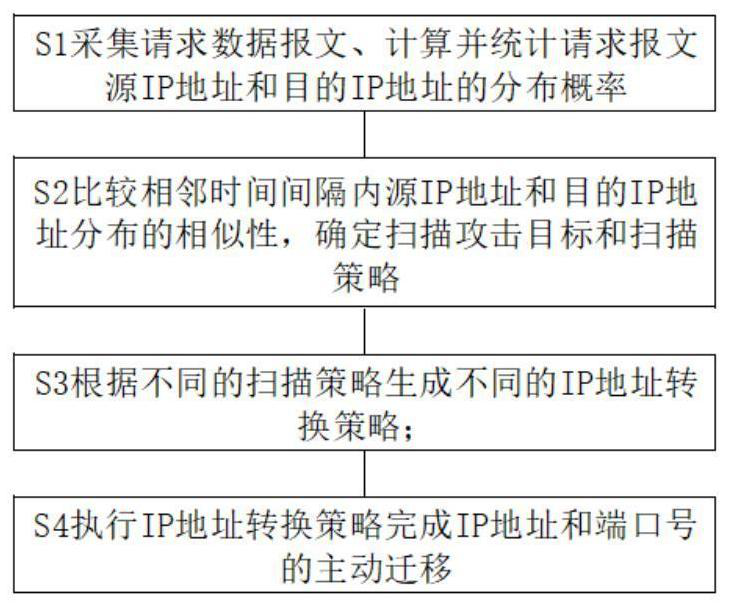
PendingCN113938458AImprove targetingAchieving Moderate ProtectionSecuring communicationIp addressAttack
The invention discloses a multi-attribute self-adjusting network transformation system and method based on an SDN. The method comprises the following steps: collecting a request data message, and carrying out calculation and statistics on distribution probabilities of a source IP address and a destination IP address of the request message; comparing similarity of distribution of the source IP address and the destination IP address in adjacent time intervals, and determining a scanning attack target and scanning strategies; generating different IP address conversion strategies according to different scanning strategies; and executing the IP address conversion strategies to complete active migration of the IP address and a port number. According to the invention, a jump strategy is triggered based on threat perception, so that the pertinence of network jump strategy selection is improved; and moderate protection of end nodes is realized by adaptively adjusting jump end information and a jump period.
Owner:佳缘科技股份有限公司
Data processing method based on threat perception big data and artificial intelligence, and AI system
InactiveCN113434869AAvoid causingIncrease the number of featuresCharacter and pattern recognitionPlatform integrity maintainanceSensing dataEngineering
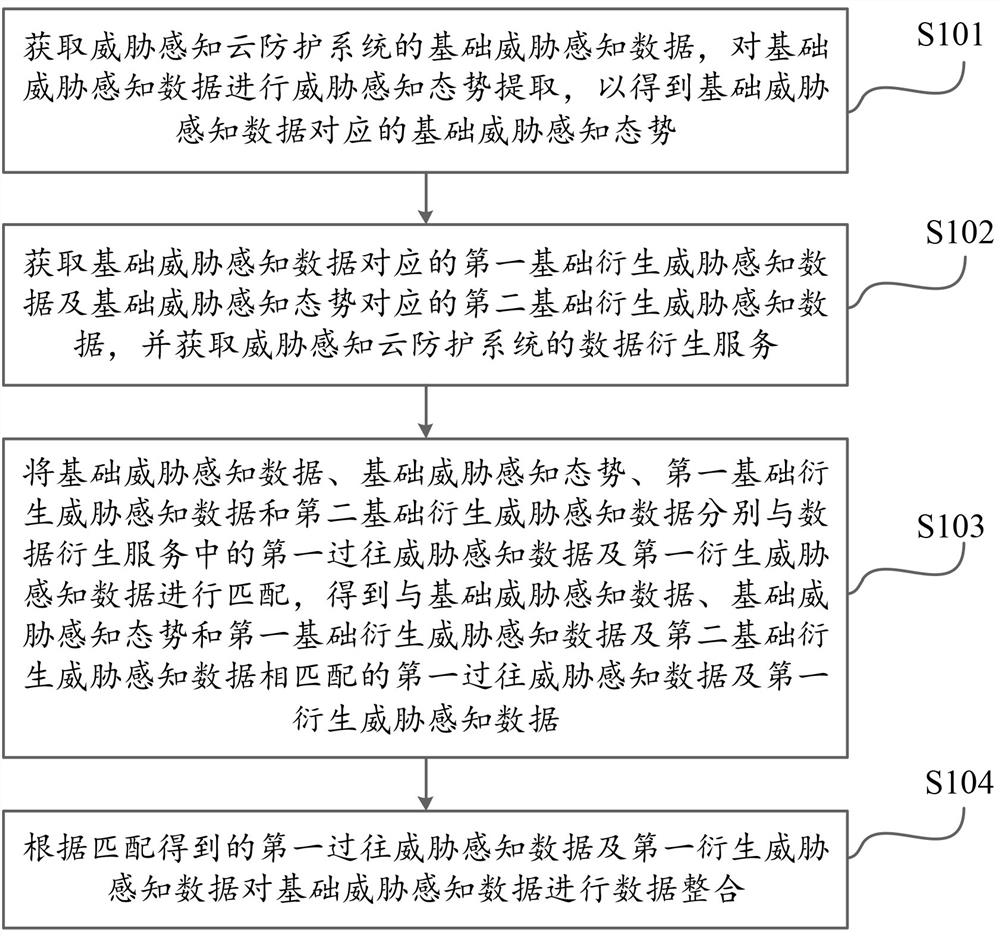
The embodiment of the invention provides a data processing method based on threat perception big data and artificial intelligence and an AI system, and the method comprises the steps: carrying out the matching of a data derivation service through employing first basic derived threat perception data and second basic derived threat perception data corresponding to basic threat perception data, and a basic threat perception situation; therefore, the first previous threat perception data and the first derived threat perception data which are matched with each other are obtained, and data integration is carried out. According to the method, data islands caused in an AI training process can be avoided, and threat sensing data related to basic threat sensing data, namely matched first previous threat sensing data and first derived threat sensing data, can be more abundantly derived, so that the basic threat sensing data is subjected to data integration; and the number of features of subsequent data mining is increased.
Owner:广州天悦科技信息有限公司
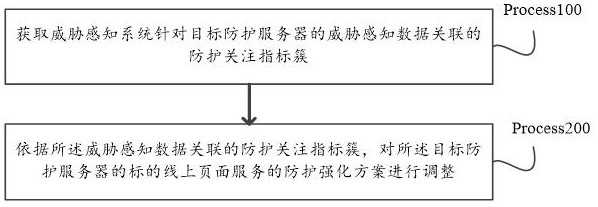
Threat attack protection decision-making method adopting AI and big data analysis and AI system
The embodiment of the invention provides a threat attack protection decision-making method adopting AI and big data analysis and an AI system, and the method comprises the steps: obtaining a protection attention index cluster related to threat perception data of a threat perception system for a target protection server, and carrying out the protection attention index cluster according to the protection attention index cluster related to the threat perception data, and the protection enhancement scheme of the target online page service of the target protection server is adjusted, so that protection enhancement adjustment is performed on the related online page on the basis of the protection attention index, and compared with global unified protection enhancement adjustment in the related technology, the method has higher pertinence and accuracy.
Owner:深圳微言科技有限责任公司
Information generation method based on threat perception big data, and artificial intelligence perception system
InactiveCN113434868ACharacter and pattern recognitionPlatform integrity maintainanceSafety propertyEngineering
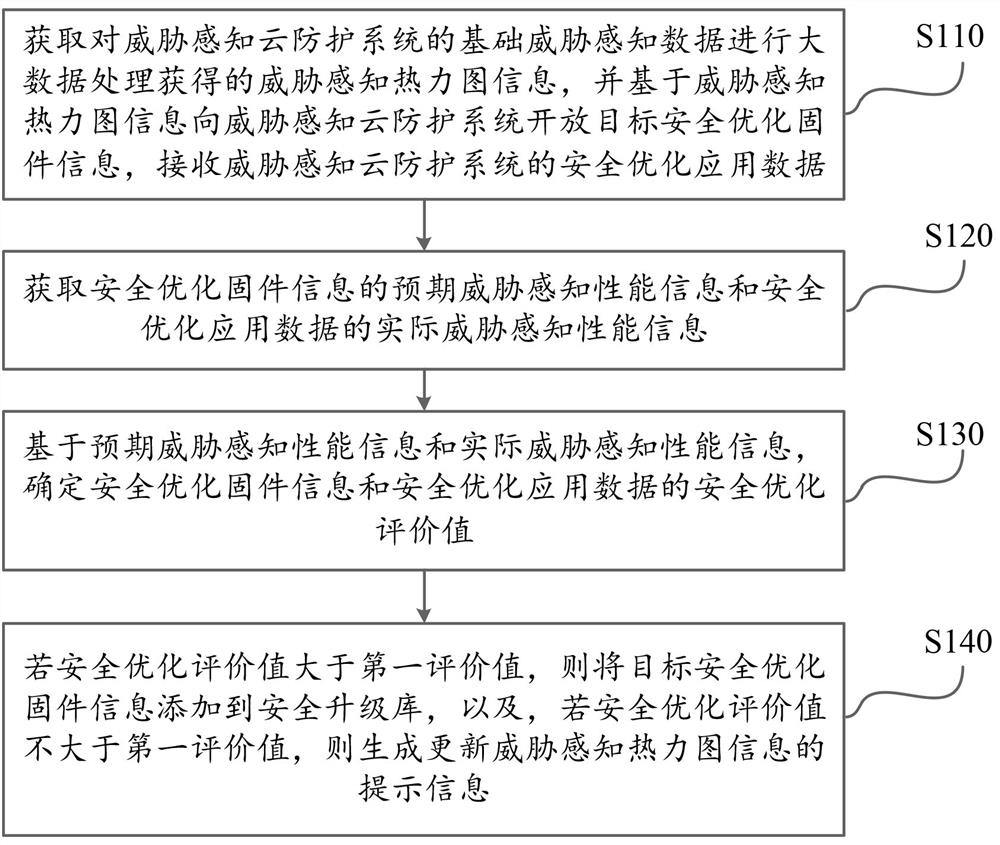
An embodiment of the invention provides an information generation method based on threat perception big data, and an artificial intelligence perception system. According to the information generation method based on the threat perception big data, and the artificial intelligence perception system provided by the embodiment of the invention, after the security optimization application data is obtained, the security optimization performance evaluation is performed on the security optimization firmware information and the security optimization application data, whether the safety optimization application data are matched with the optimization performance of the safety optimization firmware information is judged by judging whether the safety optimization application data is matched with the optimization performance of the safety optimization firmware information, so that whether the safety performance optimization meets the safety performance optimization condition can be determined, and if yes, the target safety optimization firmware information can be added to a safety upgrading library to carry out upgrading basic resource recording. Therefore, high-reliability security upgrade library resources are continuously formed, and prompt information for updating the threat perception thermodynamic diagram information of a security optimization firmware information pushing basis is generated when the security upgrade library resources do not accord with the threat perception thermodynamic diagram information so as to prompt that the current threat perception thermodynamic diagram information needs to be updated.
Owner:广州天悦科技信息有限公司
An attack path restoration method, electronic device and computer-readable storage medium
Owner:中国移动通信集团海南有限公司
Security Threat Active Sensing Method Based on Defensive Honeypot
ActiveCN108446557BThe same threat perception and identification capabilitiesImprove efficiencyPlatform integrity maintainanceTransmissionHoneypotAutomaton
The invention discloses a defense honeypot-based security threat active sensing method. Based on understanding of a Hook technology, whether a defense honeypot intercepts and captures a test functionor not is judged by analyzing an execution Trace of a system function; firstly the to-be-detected system function is injected into an untrusted process and is executed to obtain an instruction execution record (Trace) of the function; further according to a characteristic that the defense honeypot intercepts and captures the Trace of the system function, an address space finite state automata is designed, and the obtained Trace is analyzed in the automata to judge the system function intercepted and captured by the defense honeypot; and finally, a test function set is traversed to identify threat sensation of the target defense honeypot. The threat sensation of the target defense honeypot can be identified; and compared with an existing threat sensation identification method, the method has the same defense honeypot-based threat sensation identification capability, and is more automatic and more efficient.
Owner:江苏中天互联科技有限公司
Security analysis method based on original message
PendingCN113518067AImprove perceptionReduce construction costsTransmissionComputer networkEngineering
The invention aims to overcome the defects in the background technology, provides a security analysis method based on an original message, can simultaneously solve the self-security problem of the equipment terminal in the network, and is quick and effective in response. Meanwhile, the whole process can be recorded in time, so that later analysis and solution popularization are facilitated. In order to achieve the technical effect, the invention adopts the following technical scheme: the security analysis method based on the original message is matched with a probe arranged at an application end to use IDS and WAF double engines, and supports traditional threat detection and advanced threat detection in combination with threat intelligence, malicious file analysis, WEBshell detection and abnormal behavior detection, so that the security of the original message is improved, and the threat perception capability of the user is comprehensively improved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD JINHUA POWER SUPPLY CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com