Security analysis method based on original message
A technology of security analysis and original message, applied in the field of security analysis based on original message, can solve the problems of information security work lagging behind the development of information technology, imperfect regulations and standards, etc., and achieve the goal of improving perception ability and reducing construction cost Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
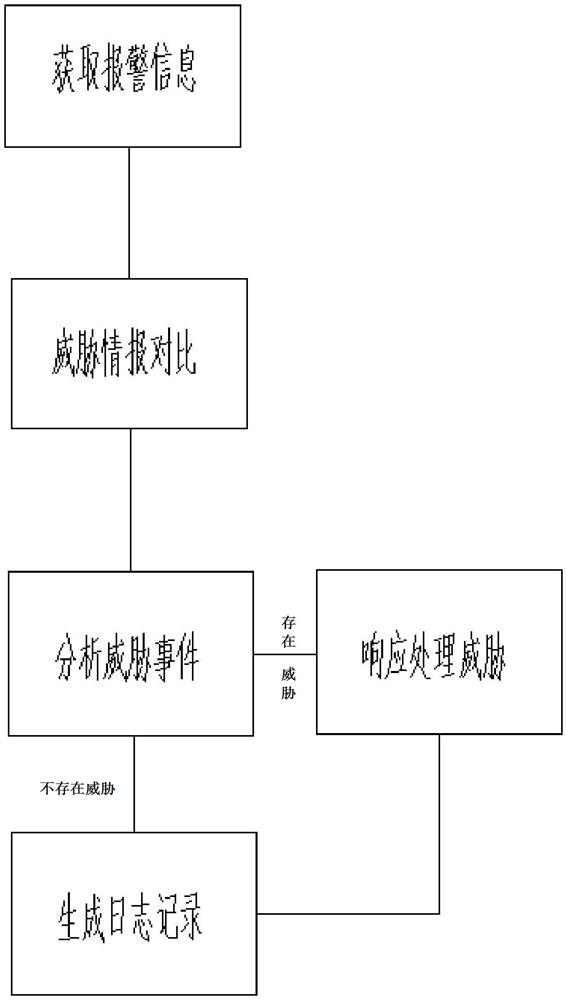
[0041] Example 1: Abnormal traffic audit scenario: perform the following steps in sequence:
[0042] A. The probe performs full traffic collection, and after obtaining the message, enable the intrusion detection system and the WEB application firewall at the same time;
[0043] B. Perform intrusion behavior detection, WEB application detection, threat intelligence detection, malicious file detection, webshell detection, DDOS detection, and abnormal behavior detection on the data stream through threat intelligence comparison in sequence.
[0044] C. Carry out judgment and analysis on the test results; if the analysis result is safe, it will be directly recorded in the log. Otherwise retrospective analysis of metadata, pcap, and:
[0045]D: The application side responds: enable the bypass blocking function, and automatically block and start threats after the attack behavior is found; the specific process is: when the user accesses the server, the traffic is mirrored to the prob...
Embodiment 2
[0047] Example 2: Situation awareness / security operation / data governance scenario. Follow the steps in sequence:
[0048] A. The probe performs full traffic collection, and after obtaining the message, enable the intrusion detection system and the WEB application firewall at the same time;
[0049] B. Perform intrusion behavior detection, WEB application detection, threat intelligence detection, malicious file detection, webshell detection, DDOS detection, and abnormal behavior detection on the data stream through threat intelligence comparison in sequence.
[0050] C. Carry out judgment and analysis on the test results; if the analysis result is safe, it will be directly recorded in the log. Otherwise retrospective analysis of metadata, pcap, and:
[0051] D: The application side responds: enable the bypass blocking function to block the attack IP and malicious domain name traffic.
[0052] E. Record the event flow in step D into the log, which can be called up for evidenc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com