Multilayer fusion beacon detection and path restoration method and device
A multi-layer fusion and beacon detection technology, applied in the field of network security, can solve problems such as the inability to build a network attack path, the difficulty in path reconstruction, and the inability to collect data packets.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
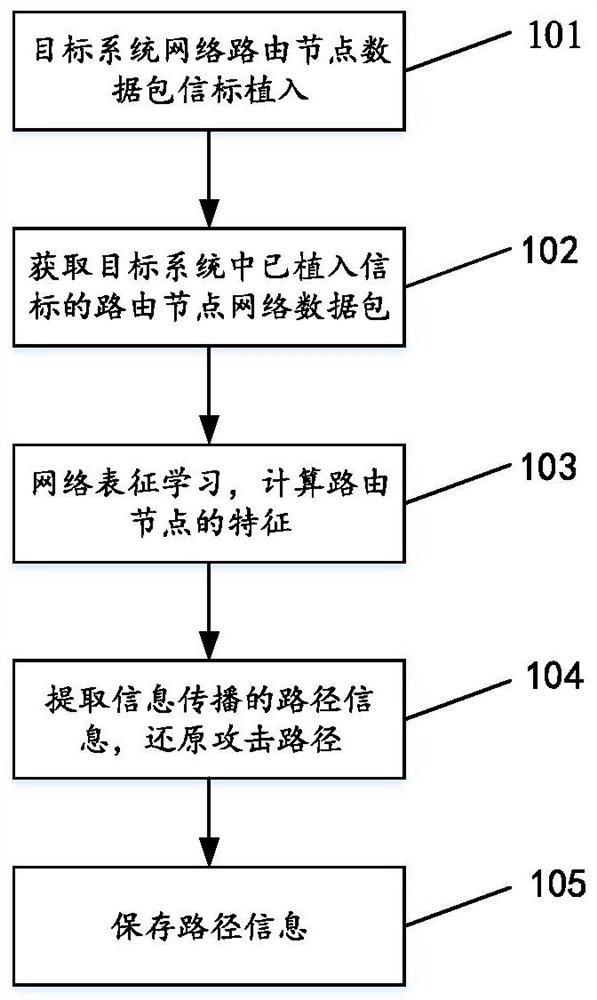
[0082] see figure 1 , figure 1 It is an overall block diagram of a multi-layer fusion beacon detection and path restoration method disclosed in the embodiment of the present invention, including the following operations:
[0083] 101. The target system network routing routing node data packet beacon implantation;
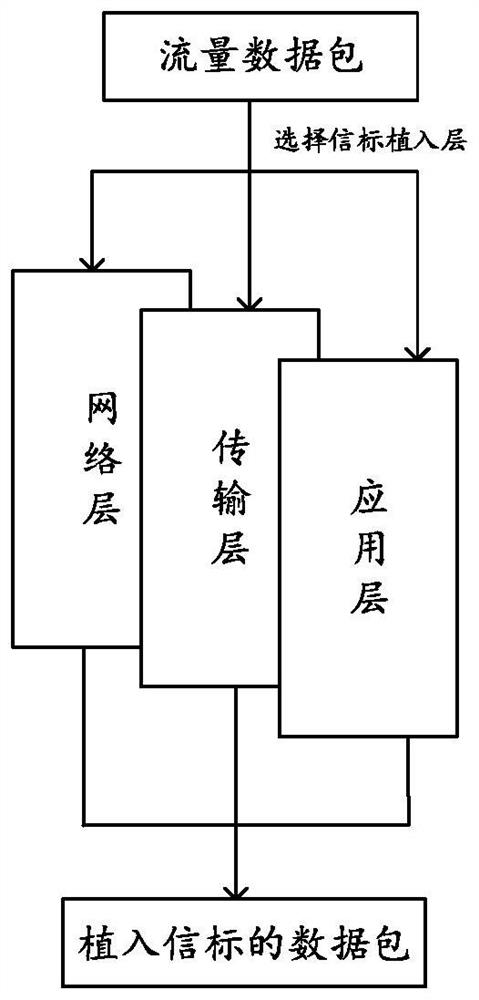
[0084] The beacon is implanted in a multi-layer fusion method. When the beacon identification field in the network data packet is marked by the routing node, it is inserted according to the insertfield old =insertfield+ID old Rules are implanted, where insertfield represents the identification field of the current routing node, and insertfield old Indicates the identification field of the previous routing node, ID old Indicates the ID of the IP protocol in the data packet of the previous routing node. like figure 2 As shown, a beacon is implanted in a specific position of the application layer protocol, an optional field of the transport layer in TCP, and an ...
Embodiment 2
[0105] Scenario: When an enterprise accesses the network in the local area network, if there is an attacker attacking the users using the network, the network security management personnel can restore the attack path of the attacker through the method mentioned in the present invention, and can take measures Improve the security of your own network.
[0106] The overall thinking of embodiment two is as follows:
[0107]Step 1. Select the routers for network traffic in and out of the enterprise, and add beacon implantation devices to these routers; select network border entry and exit gateway routers, and add beacon detection devices to them.
[0108] Step 2: When the intranet of the enterprise is attacked by the network, the beacon is extracted from the data packets flowing through the router.
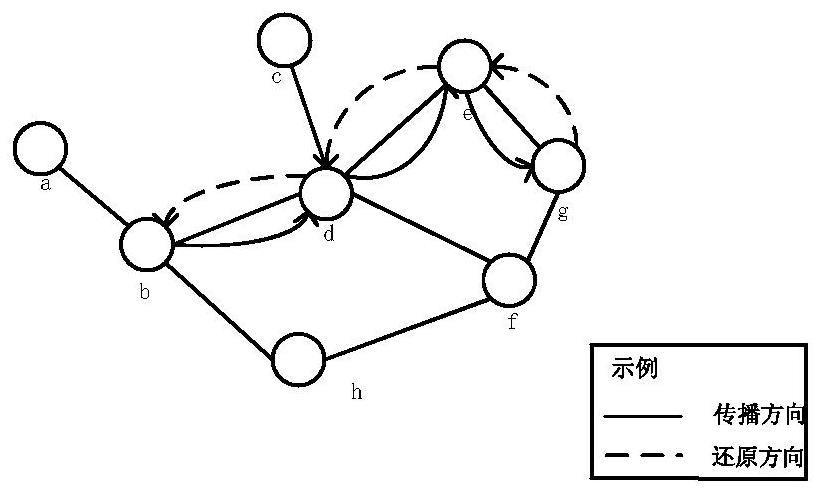
[0109] Step 3. Starting from the data packet of the first routing node, calculate the transition probability, search deviation and the probability of the data packet pointing to the n...
Embodiment 3
[0122] see Figure 4 , Figure 4 It is a schematic diagram of a multi-layer fusion beacon detection and path restoration device based on representation learning, wherein, Figure 4 The described device can be applied to a multi-layer fusion beacon detection and path restoration method based on representation learning, such as Figure 4 As shown, the device may include:
[0123] 401. Beacon implantation module, used to implement multi-layer fusion beacon implantation;
[0124] 402. The routing node feature calculation module uses a random walk-based network representation learning model to calculate the features of the routing node;
[0125] 403. The path restoration module extracts the path information of information propagation from the information of each routing node in the network, so as to find the order of routing node restoration;
[0126] 404. The storage module stores the restored attack path in a database, so as to enhance network security later.
[0127] It can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com