Attack chain topology construction method and device
A construction method and topology technology, applied in the field of attack chain topology construction, which can solve the problems of inability to assess the attack risk of similar assets, inability to obtain attack surface data, and lack of attack stage division.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
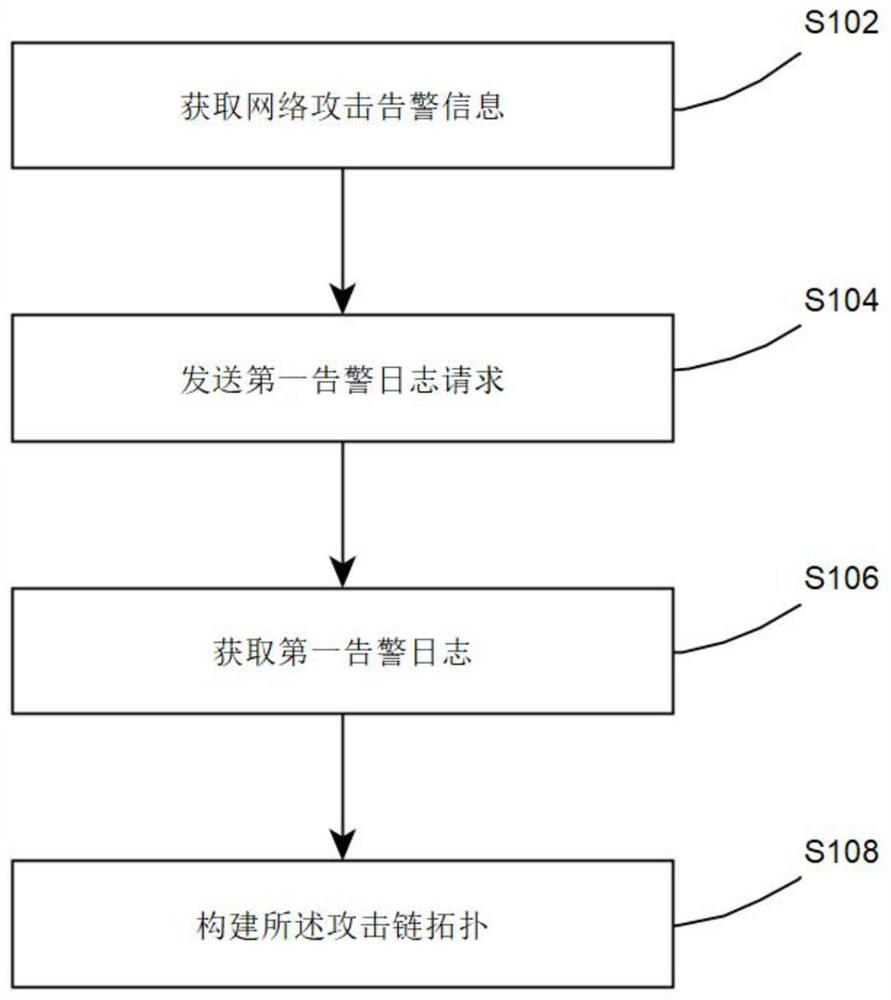
[0029] As a preferred implementation, the method for constructing the attack chain topology also includes:
[0030] S110. Send a first asset information request, where the first asset information request includes the first target IP;
[0031] S112. Obtain first asset information, where the first asset information includes the first target IP, the first asset identifier, the first sensitive data, the first login account and its authorization status;
[0032] S114. Improve the attack chain topology according to the first asset information.
[0033] This preferred implementation mode obtains asset information through target IP and improves the attack chain topology, thereby helping to combine and analyze asset information and attack information, thereby knowing asset risks in a timely manner, and early screening or eliminating security threats.
[0034] As a preferred implementation, the method for constructing the attack chain topology also includes:
[0035]S116. Send an asso...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com