Threat-driven network attack detection and response method
A network attack and intelligence technology, applied in the field of information security, can solve the problems of lack of diversity and single processing space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
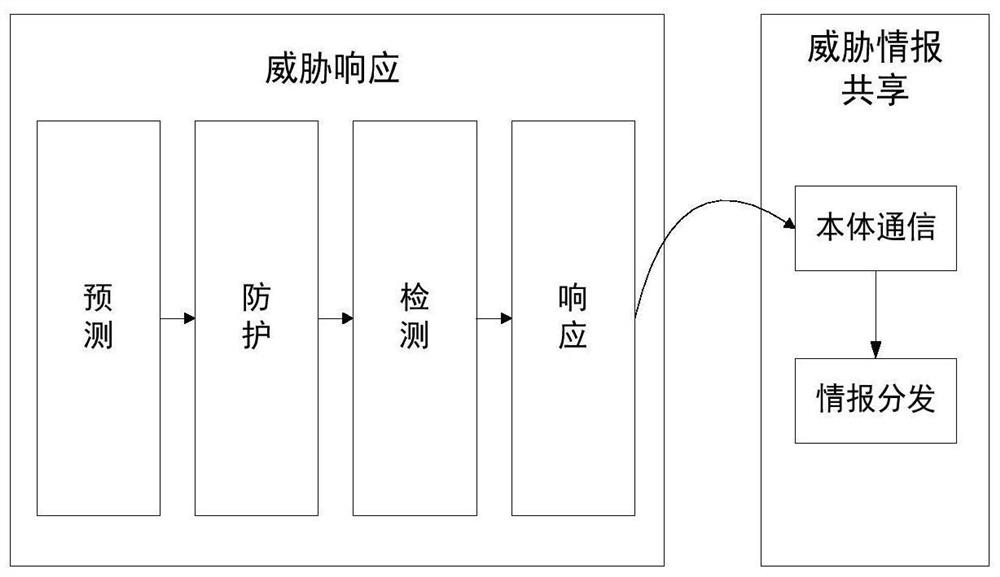
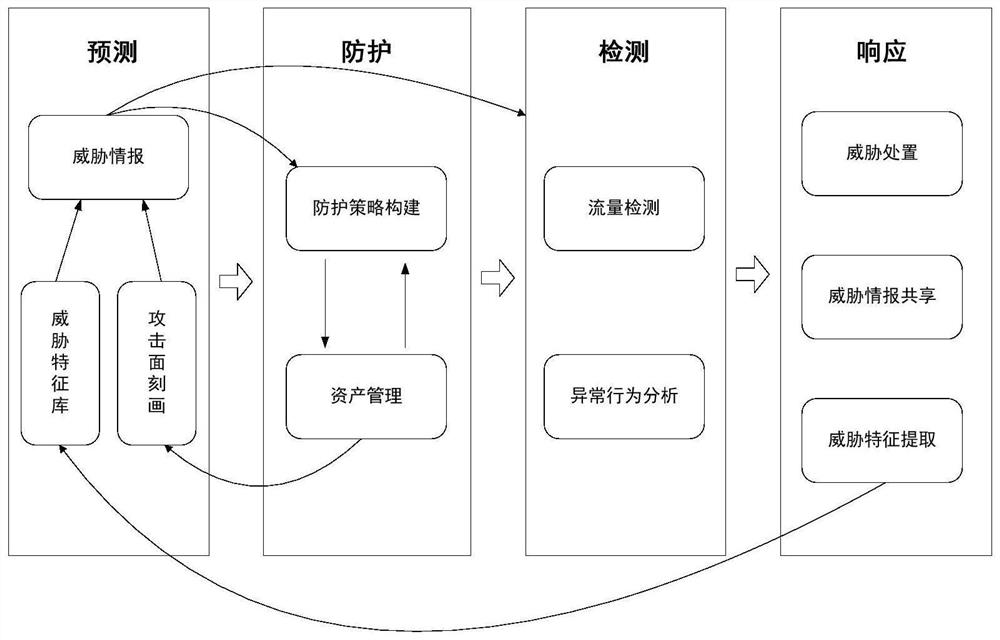
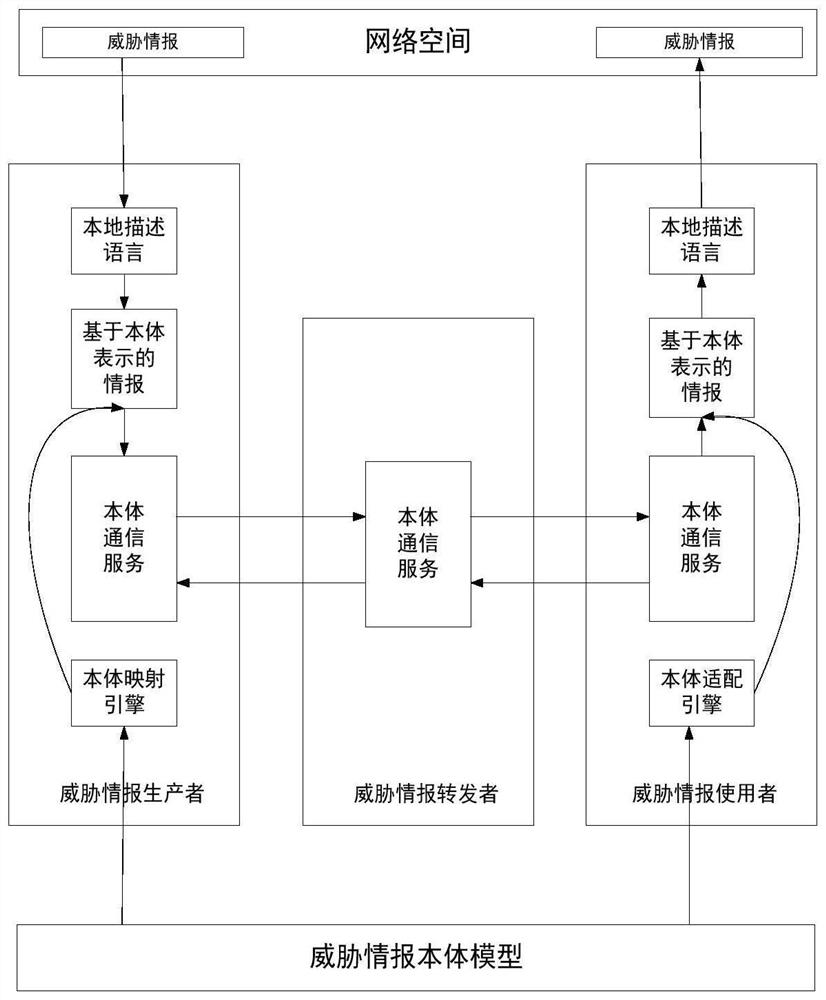
[0048] The attacking and defending parties have been in a dynamic game under the condition of information asymmetry for a long time, and the defender knows far less about the attacker than the attacker knows about the defender. Traditional attack detection methods not only cannot meet the current security detection requirements, but also do not analyze the attacker's relevant information deeply enough. Therefore, on the basis of the research and analysis of the general network attack process, the present invention designs a threat-based attack detection and response method based on the attacker's attack idea and process, mainly including threat response based on the attack life cycle and ontology communication-based Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com