Multi-attribute self-adjusting network transformation system and method based on SDN
A network transformation and self-adjustment technology, applied in the field of network security, can solve the problems of poor hopping timeliness, reduced hopping unpredictability, and poor hopping defense effectiveness, so as to maximize defense benefits, ensure timeliness and pertinence Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to enable those skilled in the art to better understand the technical solutions of the present invention, the present invention will be further described in detail below in conjunction with specific embodiments.
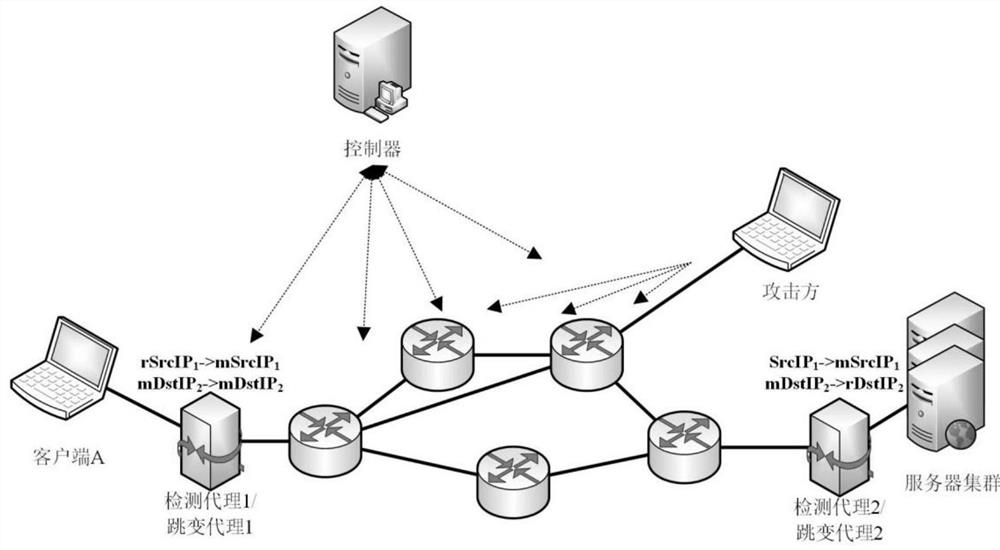
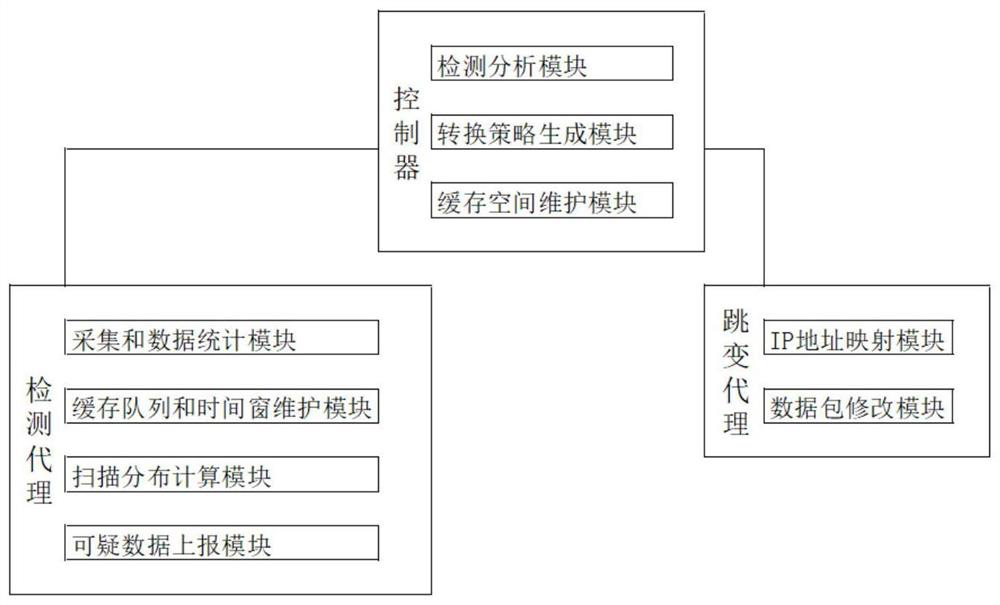
[0029] Such as figure 1 , figure 2 As shown, the present invention provides a multi-attribute self-regulating network conversion system based on SDN, specifically including: deployed in SDN (Software Defined Network):
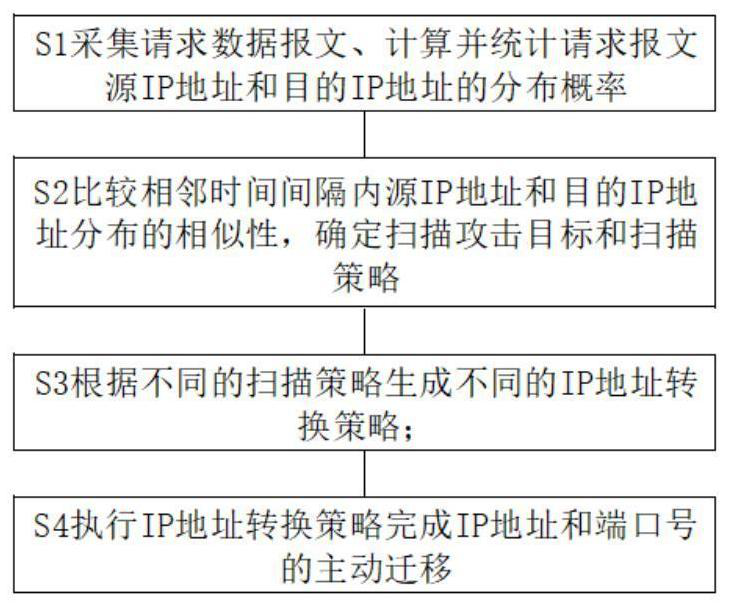
[0030] The detection agent is used to collect request data packets, calculate and count distribution probabilities of source IP addresses and destination IP addresses of request packets.
[0031] The controller includes a detection and analysis module, a conversion strategy generation module and a cache space maintenance module; the detection and analysis module is used to compare the similarity of the distribution of source IP addresses and destination IP addresses in adjacent time intervals, and determine scanning attack targets an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com