Defense honeypot-based security threat active sensing method
A honeypot, active technology, applied in computer security devices, instruments, computing, etc., to achieve high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described in detail below in conjunction with the accompanying drawings and examples. The following examples are explanations of the present invention and the present invention is not limited to the following examples.
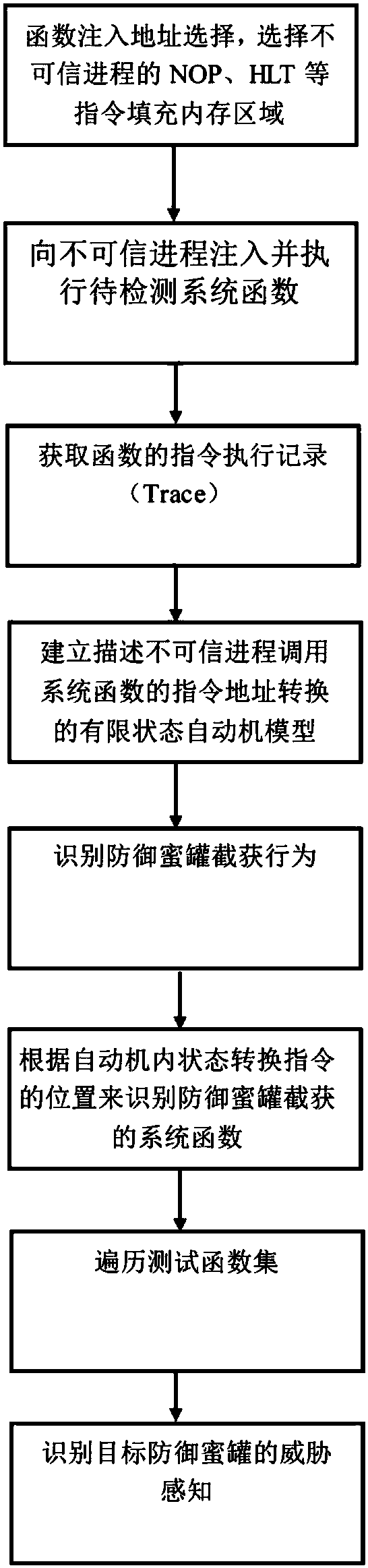
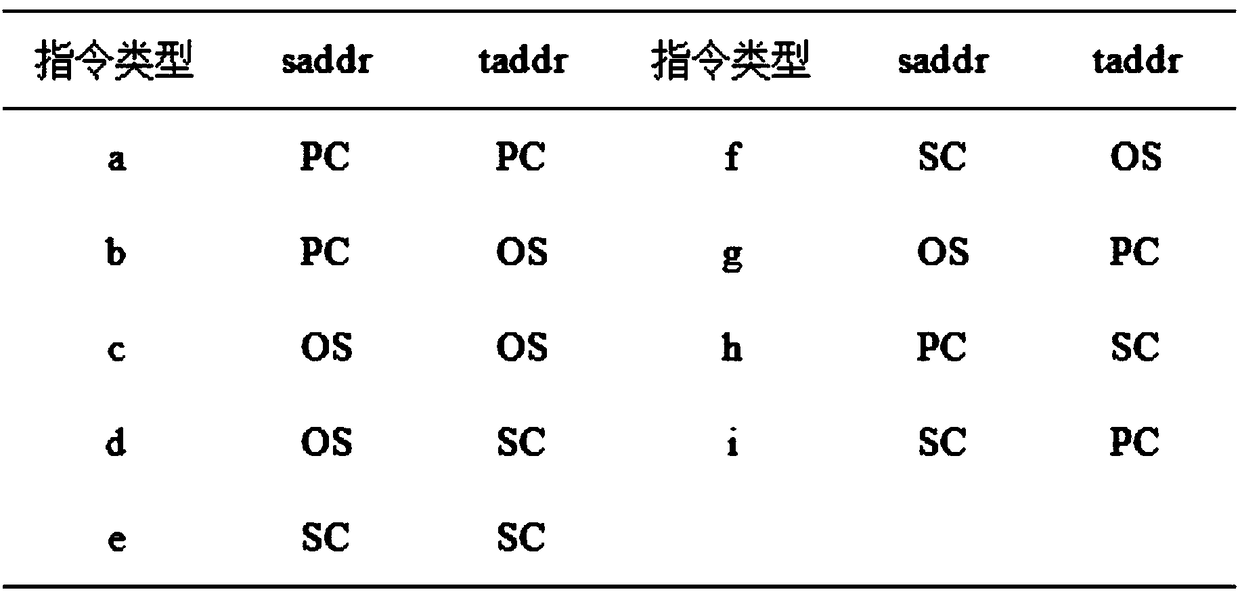
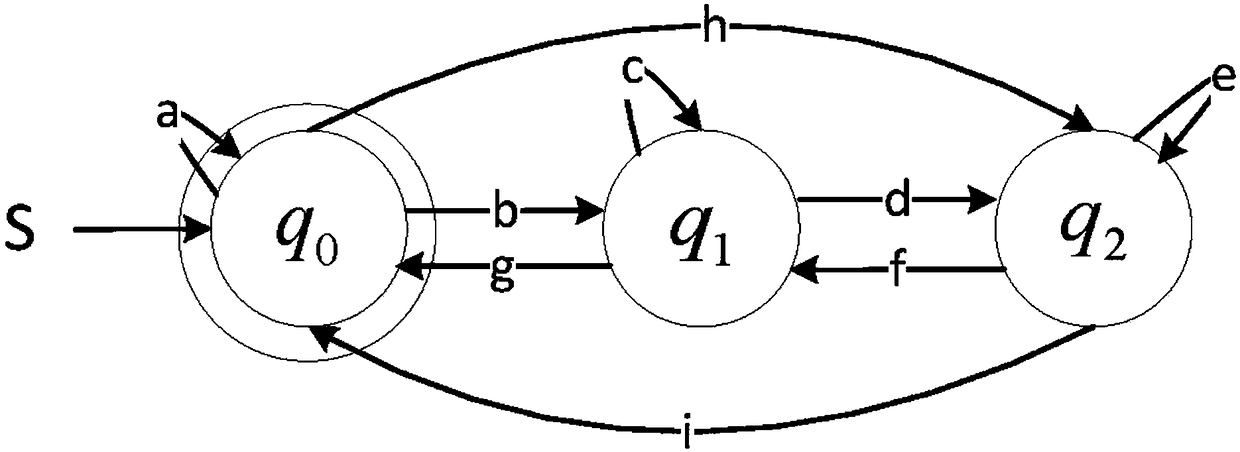
[0034] like figure 1 As shown, a kind of security threat active perception method based on defense honeypot of the present invention, concrete steps are as follows:
[0035] Step 1, function injection address selection, select NOP, HLT and other instructions of the untrusted process to fill the memory area. In the Windows system, since the program uses NOP and HLT instructions to fill the code segment of the program to ensure instruction alignment, in order not to destroy the function code of the untrusted process itself, the area filled with NOP and HLT instructions is selected as the injectable address area ms.
[0036] Step 2: Inject and execute the system function to be detected into the untrusted process. Sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com