Network attack monitoring system based on multi-source information analysis
A technology of network attack and monitoring system, applied in the computer field, can solve the problems of intrusion, powerlessness, loss assessment, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
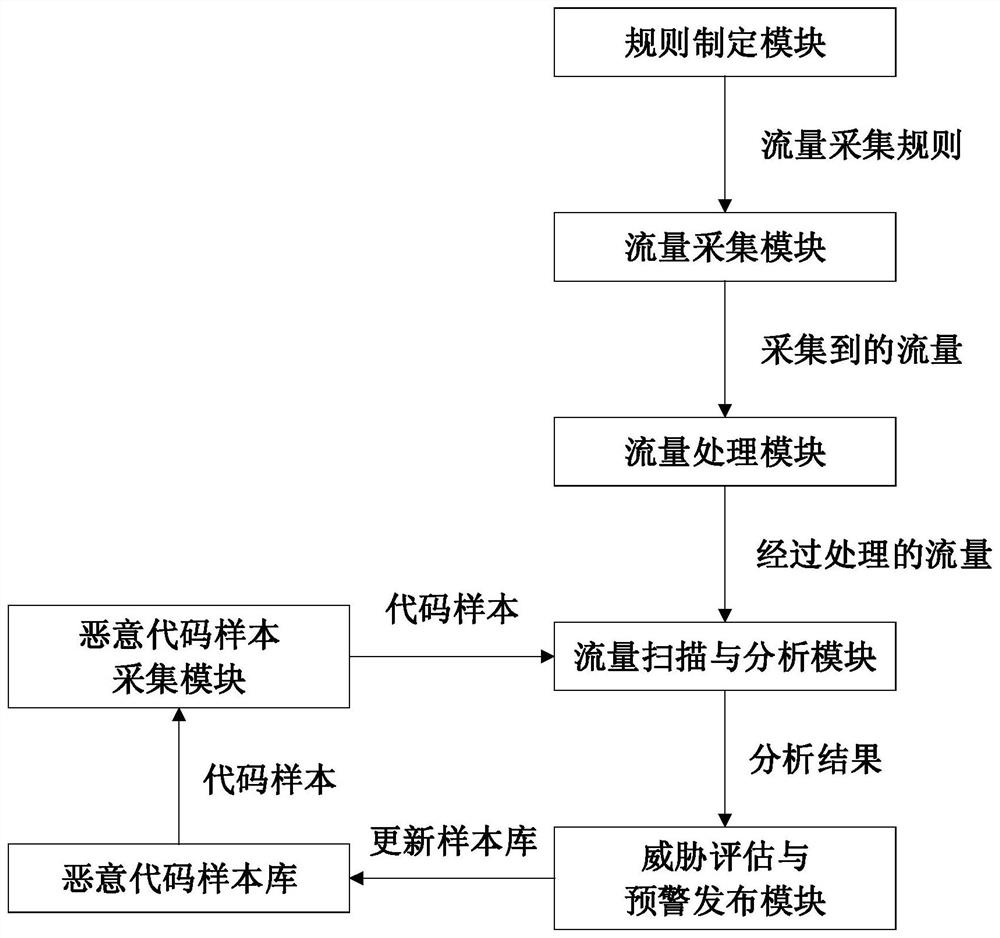
[0048] This embodiment provides a network attack monitoring system based on multi-source information analysis, which includes a traffic monitoring and collection module, a network attack analysis module, a malicious code analysis module, a threat assessment and early warning release module, and the like.
[0049] The workflow of the network attack monitoring system based on traffic analysis is as follows:
[0050] (1) Flow monitoring acquisition module
[0051] a) Collect and restore, collect and restore suspicious original traffic data monitored by network security monitoring probe equipment, standardize and store traffic data, and realize functions such as retrieval, traffic restoration, and file extraction.
[0052]b) Collection rules, for IP quintuples, fixed and floating location keywords, application protocols, etc., define in a visual way and deliver traffic collection rules to network security monitoring probe devices.
[0053] 1) IP quintuple refers to source IP addr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com