Docker-based automated honey pot construction and threat perception method
A honeypot and algorithm technology, applied in the field of visualization technology, can solve the problems of high resource occupation, high deployment cost of honeypot system, and inability to make full use of computer storage and computing resources, so as to achieve a high degree of automation, reduce economic losses, and ease operation burden effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described in detail in conjunction with the following specific embodiments and accompanying drawings.
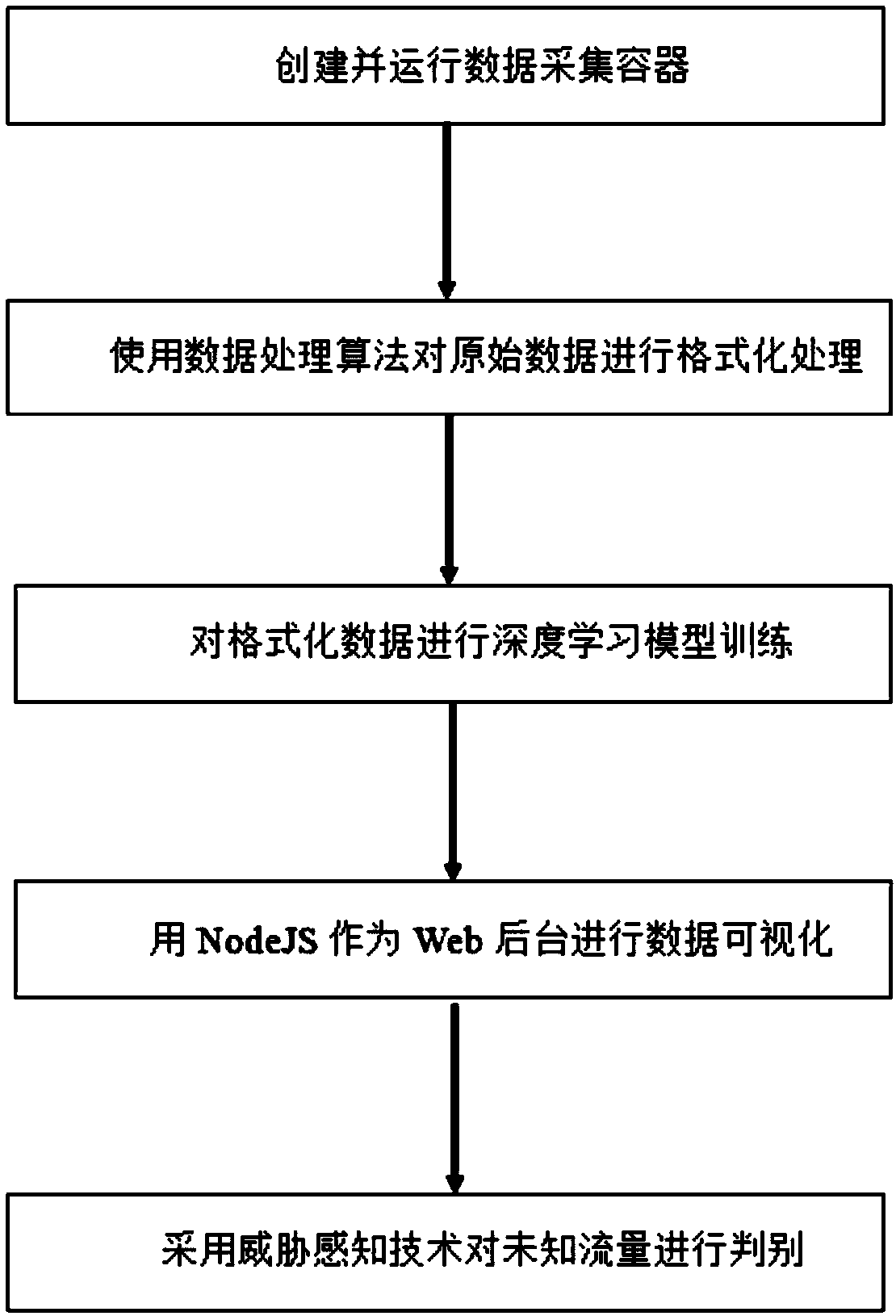
[0031] refer to figure 1 , the present invention provides a kind of method based on Docker automatic honeypot construction and threat awareness, comprising the following steps:
[0032] Step 1: Create and run the honeypot data collection container;
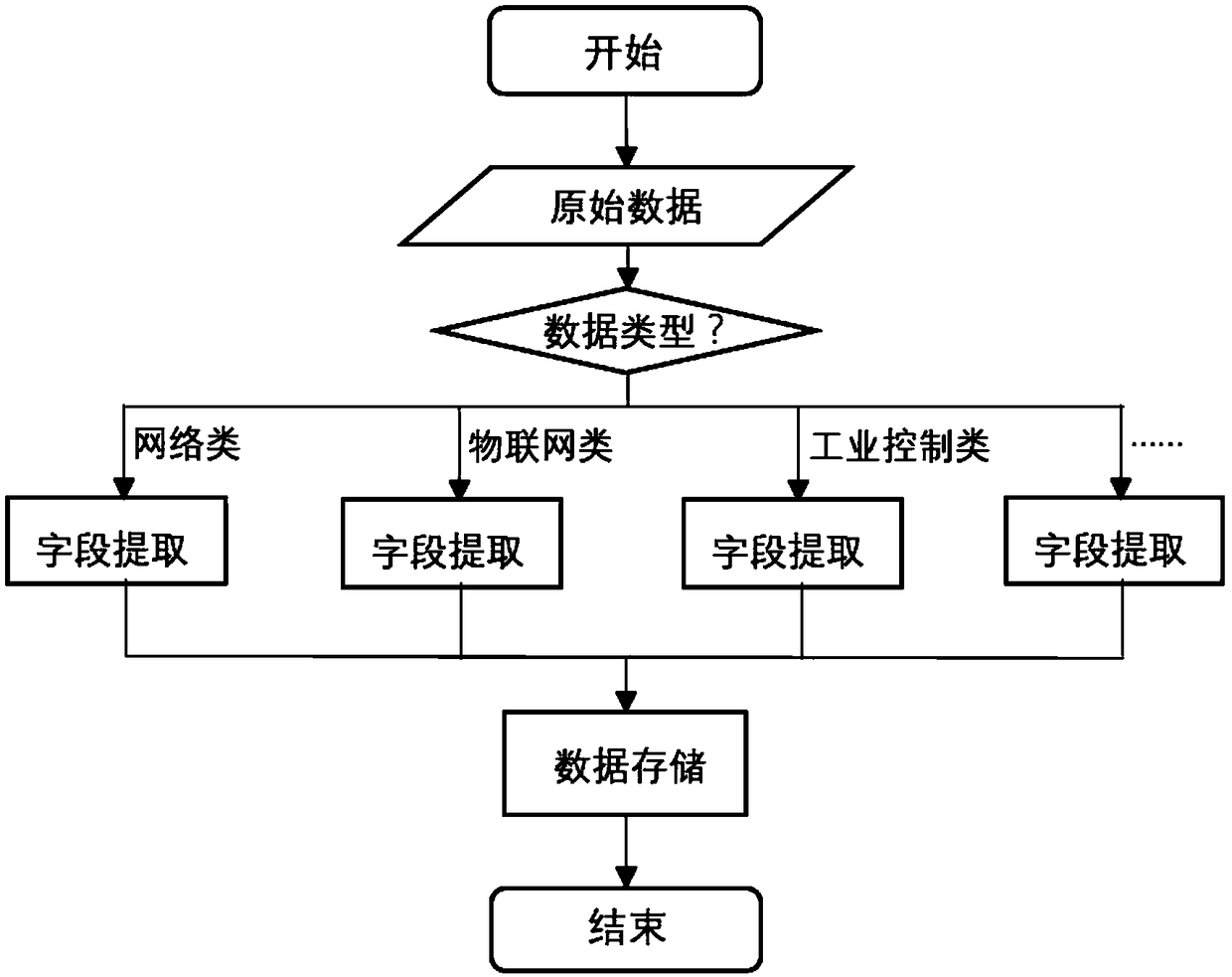
[0033] Step 2: Use data processing algorithms to format the original data;
[0034] Step 3: Perform deep model training on the formatted data;
[0035] Step 4: Use NodeJS as the Web background for data visualization;
[0036] Step 5: Use the deep model obtained in step 3 to discriminate the unknown traffic.
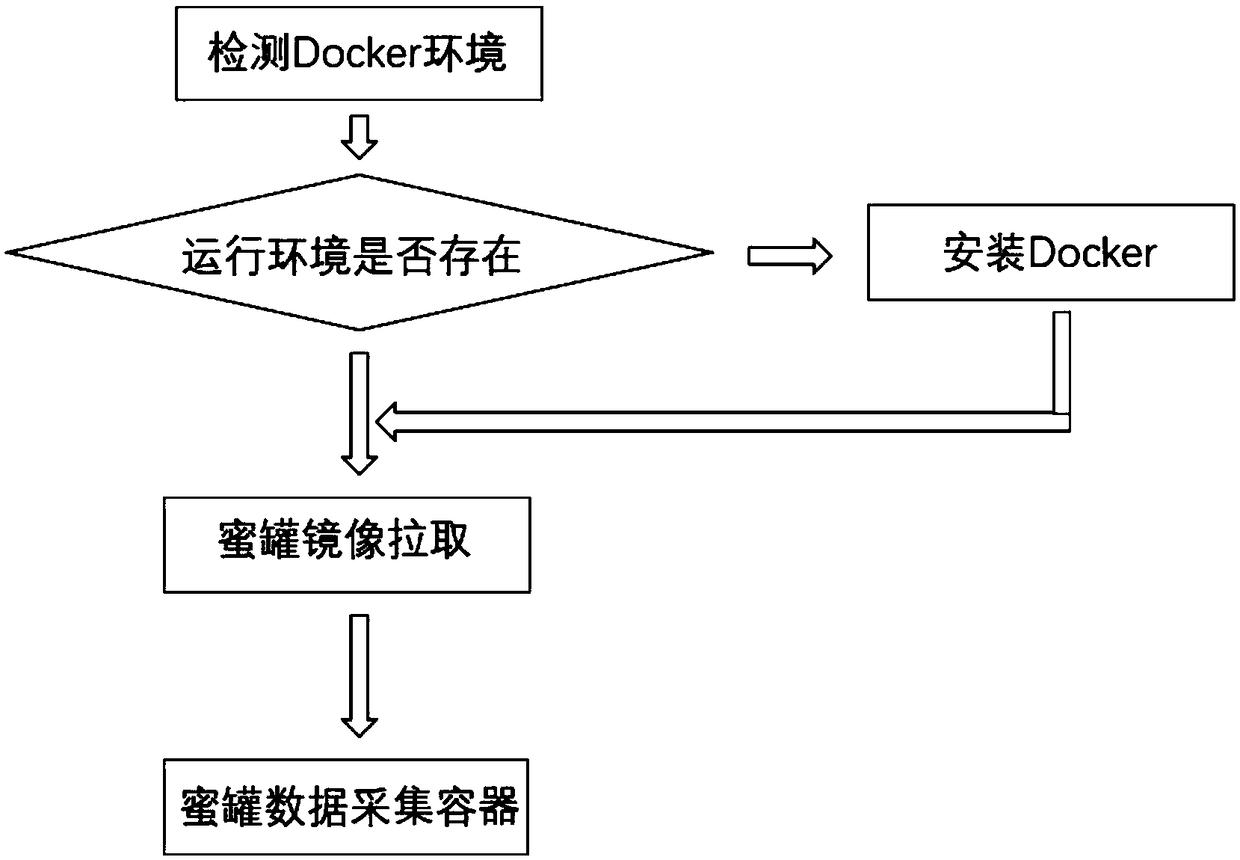
[0037] refer to figure 2 , when creating and running the data acquisition container step, the present invention first judges whether there is a Docker operating environment in the system to be deployed, if there is an operating environment, then starts to pull the Docker ho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com