Botnet detection device based on HTTP first question and answer packet clustering analysis
A botnet and cluster analysis technology, applied in electrical components, transmission systems, etc., can solve problems such as time-consuming and labor-intensive work, undetectable botnets, etc., achieve high accuracy, prevent and contain attacks, and reduce the number of analysis objects and the effect of storage overhead on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
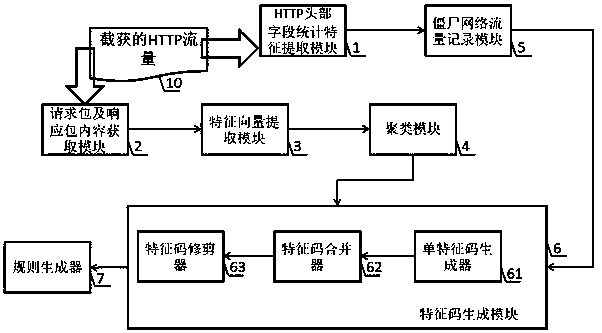
[0031] see figure 1, realizing the botnet detection device based on the first HTTP question-and-answer packet clustering analysis of the present invention, comprising an HTTP header field statistical feature extraction module 1, a botnet traffic recording module 5, a request packet and a response packet content acquisition module 2, and a feature vector Extraction module 3, clustering module 4, signature generation module 6 and rule generator 7 are made up; Wherein signature generation module 6 is made up of single signature generator 61, signature merger 62 and signature trimmer 63;
[0032] HTTP header field statistical feature extraction module 1, input intercepted HTTP traffic 10, compare four kinds of parameters in the HTTP request packet and HTTP response packet identified by IP quadruple, four kinds of parameters include: request line path length , request parameters, number of path layers, and number of parameters; HTTP traffic with four completely consistent paramete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com