Method for detecting security of Java open source component
A security detection and component technology, applied in the field of network security to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
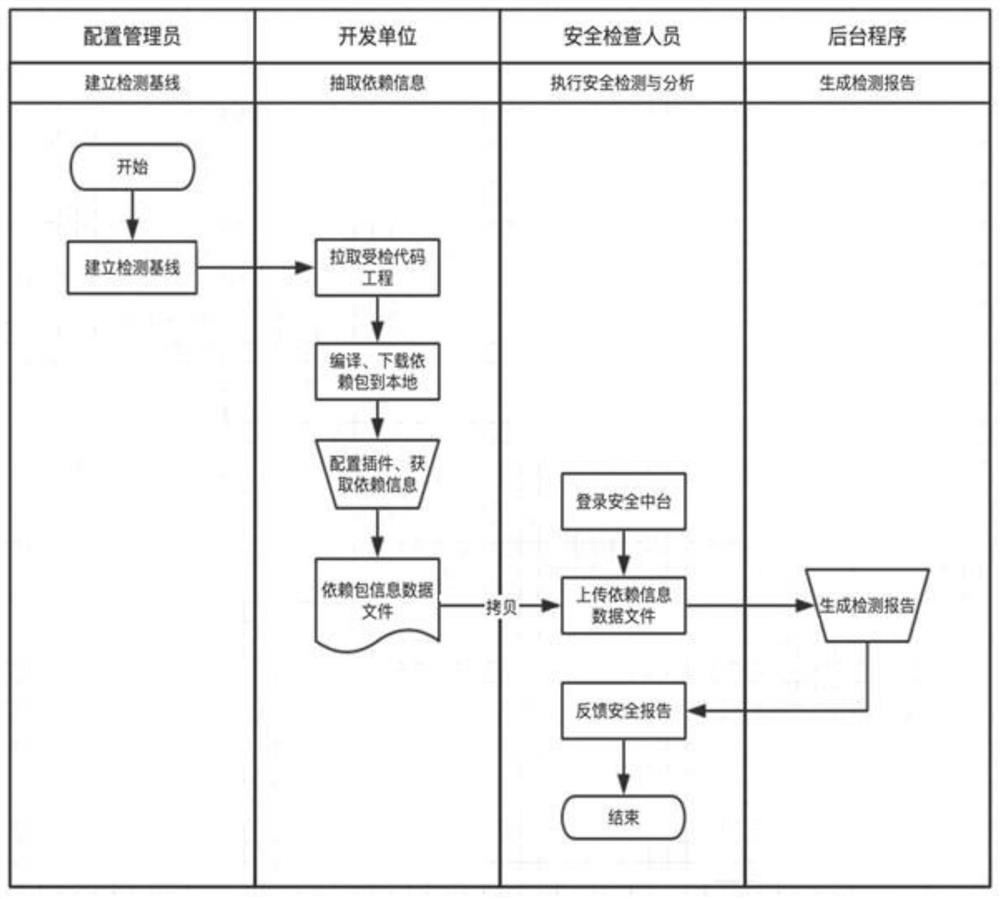
[0028] combined with figure 1 As shown, a method for security detection of Java open source components includes:
[0029] Step S100: use Maven to build a private warehouse, mark the security risk level of the open source components stored in the private warehouse, and store them as the first open source component;
[0030] Step S200: Upload the system project file, and analyze the system project file by configuring the maven dependency package information extraction plug-in in the maven project pom file to obtain a list of second open source components that the project file depends on; the step S200 specifically includes:
[0031] Step S210: the configuration administrator establishes a baseline for the maven code project file to be detected;
[0032] Step S220: The developer extracts the source code corresponding to the baseline version from the source code library on site;
[0033] Step S230: The developer compiles the source code project file, and downloads the dependency...
Embodiment 2
[0059] Furthermore, the security risk level in the step S100 is marked with three dimensions, and the three dimensions are authorization verification, virus Trojan horse detection and security vulnerability detection;
[0060] The method for the authorization (License) verification is: obtain the authorization information of the open source component, and carry out security risk classification according to the authorization information;
[0061] Risks are categorized as follows:
[0062] MIT-Low Risk-The developer of the program retains the original author's license information in the modified source code;
[0063] Apache1.0-medium risk-open source components and open source software adopt the Apache1.0 license, and the developer does not retain the original author's license information in the modified source code;
[0064]Apache2.0-low risk-open source components and open source software adopt the Apache2.0 license, and the developer does not retain the original author's lic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com