Patents
Literature
681 results about "Multitenancy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The term "software multitenancy" refers to a software architecture in which a single instance of software runs on a server and serves multiple tenants. Systems designed in such manner are often called shared (in contrast to dedicated or isolated). A tenant is a group of users who share a common access with specific privileges to the software instance. With a multitenant architecture, a software application is designed to provide every tenant a dedicated share of the instance - including its data, configuration, user management, tenant individual functionality and non-functional properties. Multitenancy contrasts with multi-instance architectures, where separate software instances operate on behalf of different tenants.
Custom entities and fields in a multi-tenant database system
ActiveUS20050223022A1Digital data processing detailsObject oriented databasesObject storageData value
Systems and methods for hosting variable schema data such as dynamic tables and columns in a fixed physical database schema. Standard objects, such as tables are provided for use by multiple tenants or organizations in a multi-tenant database system. Each organization may add or define custom fields for inclusion in a standard object. Custom fields for multiple tenants are stored in a single field within the object data structure, and this single field may contain different data types for each tenant. Indexing columns are also provided, wherein a tenant may designate a field for indexing. Data values for designated fields are copied to an index column, and each index column may include multiple data types. Each organization may also define custom objects including custom fields and indexing columns. Custom objects for multiple tenants are stored in a single custom object data structure. The primary key values for the single custom object table are globally unique, but also include an object-specific identifier which may be re-used among different entities.
Owner:SALESFORCE COM INC
Query optimization in a multi-tenant database system
ActiveUS20050065925A1Great semantic knowledgeBroaden their knowledgeDigital data information retrievalData processing applicationsDatabase indexQuery optimization
More efficient querying of a multi-tenant database using dynamic tuning of database indices. A layer of meta-data associates data items with tenants, e.g., via tags, and the meta-data is used to optimize searches by channeling processing resources during a query to only those pieces of data bearing the relevant tenant's unique tag.
Owner:SALESFORCE COM INC
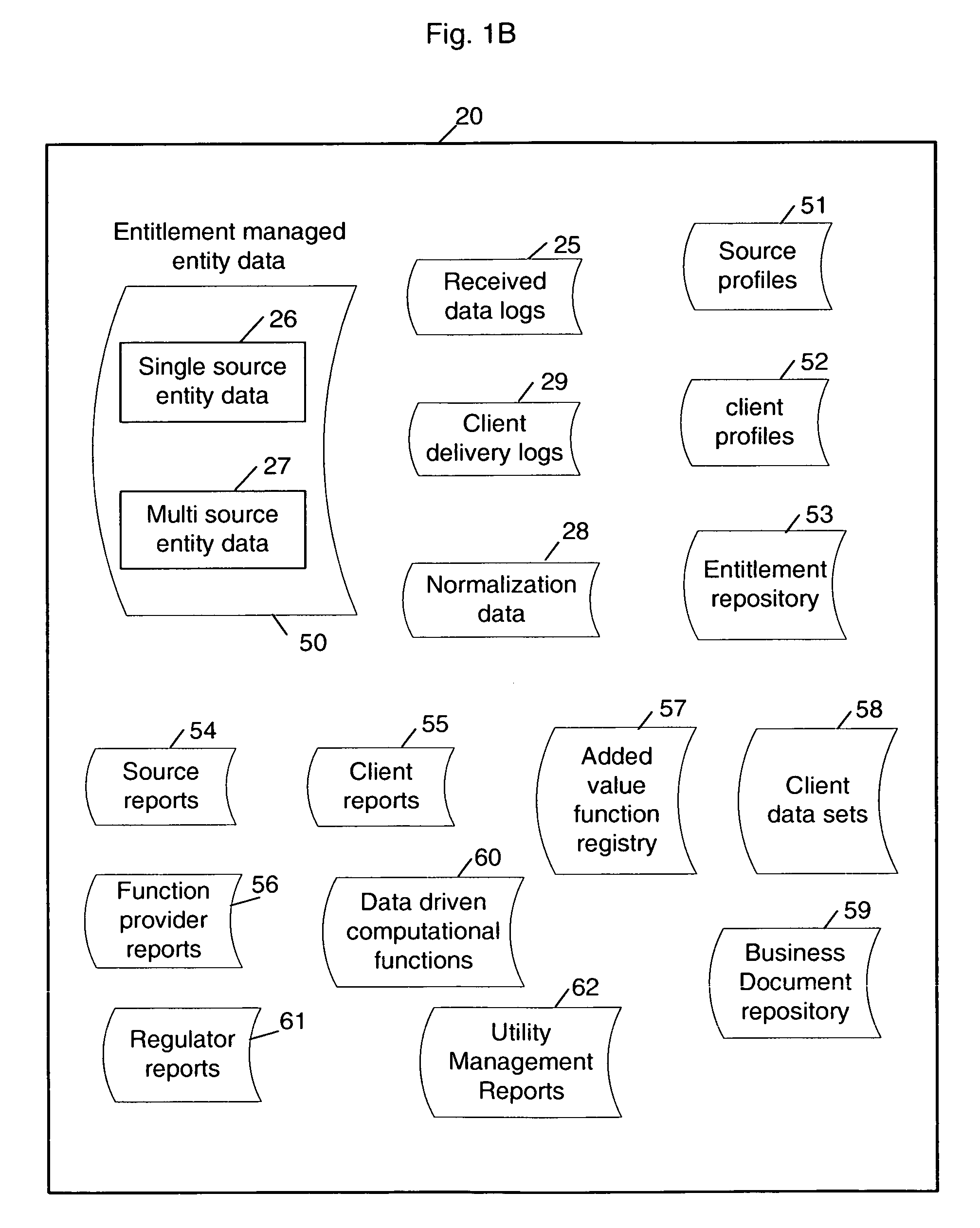
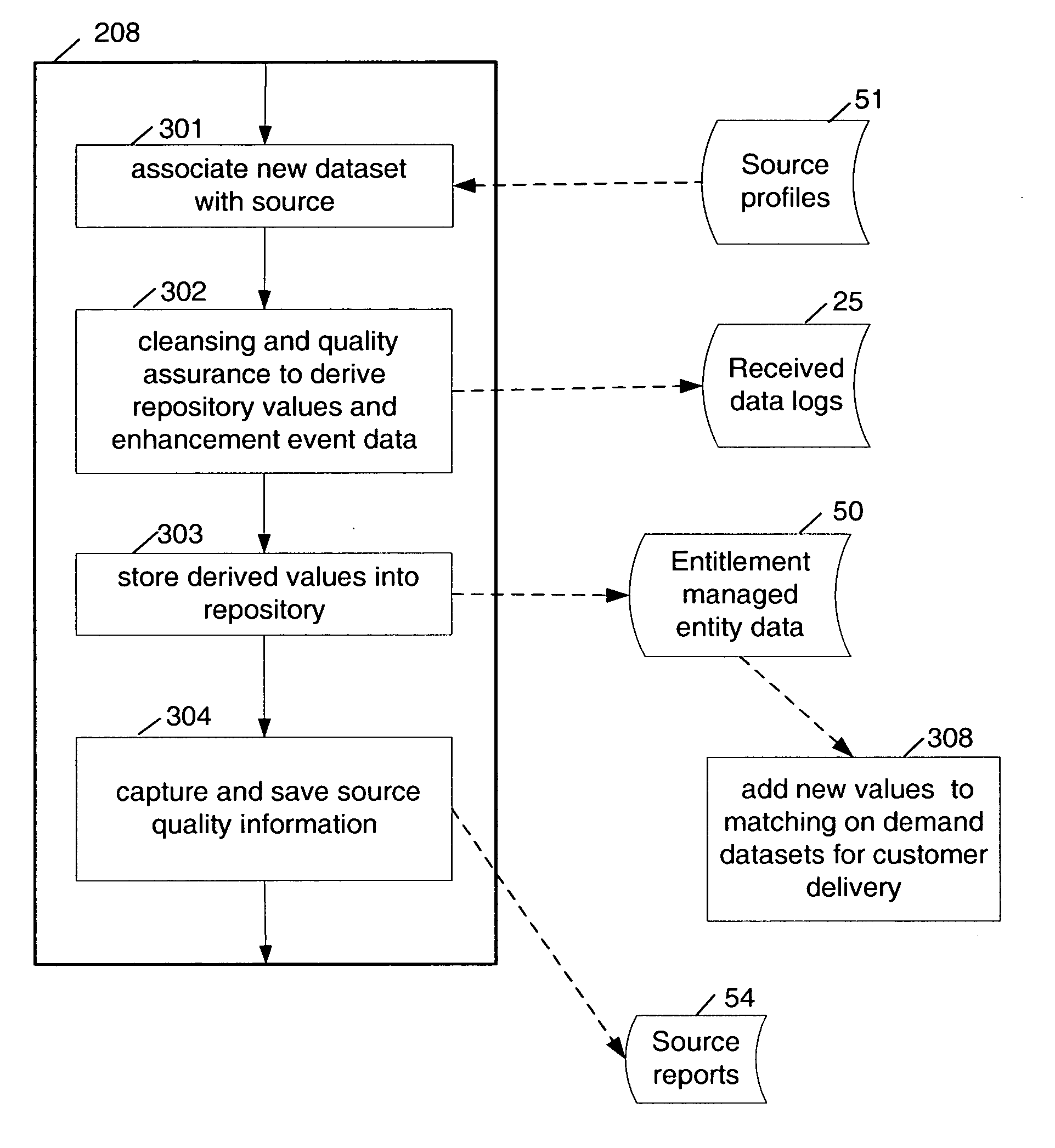
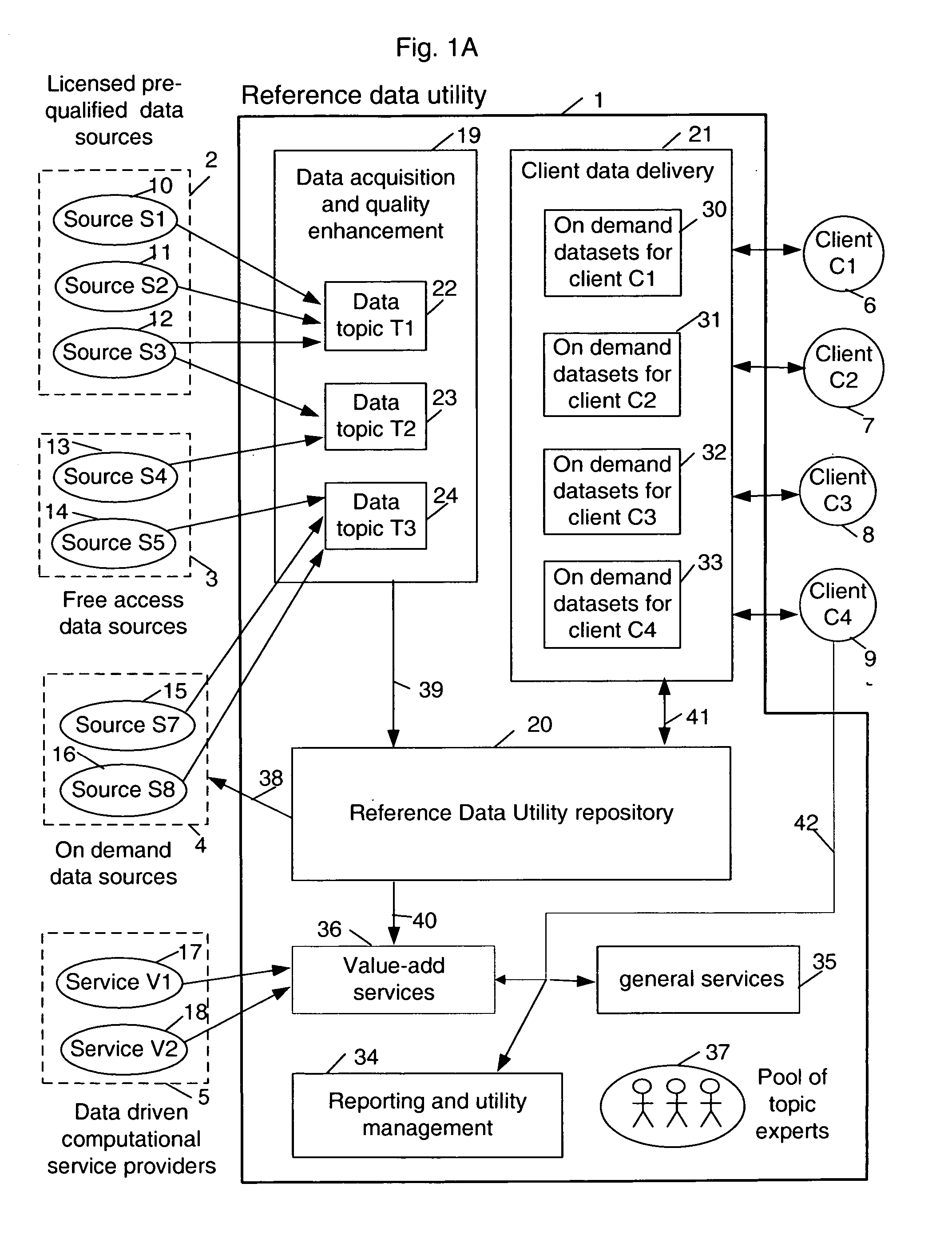
Multi-source multi-tenant entitlement enforcing data repository and method of operation
InactiveUS20060235831A1Easy to optimizeLow costFinanceSpecial data processing applicationsData qualityData store
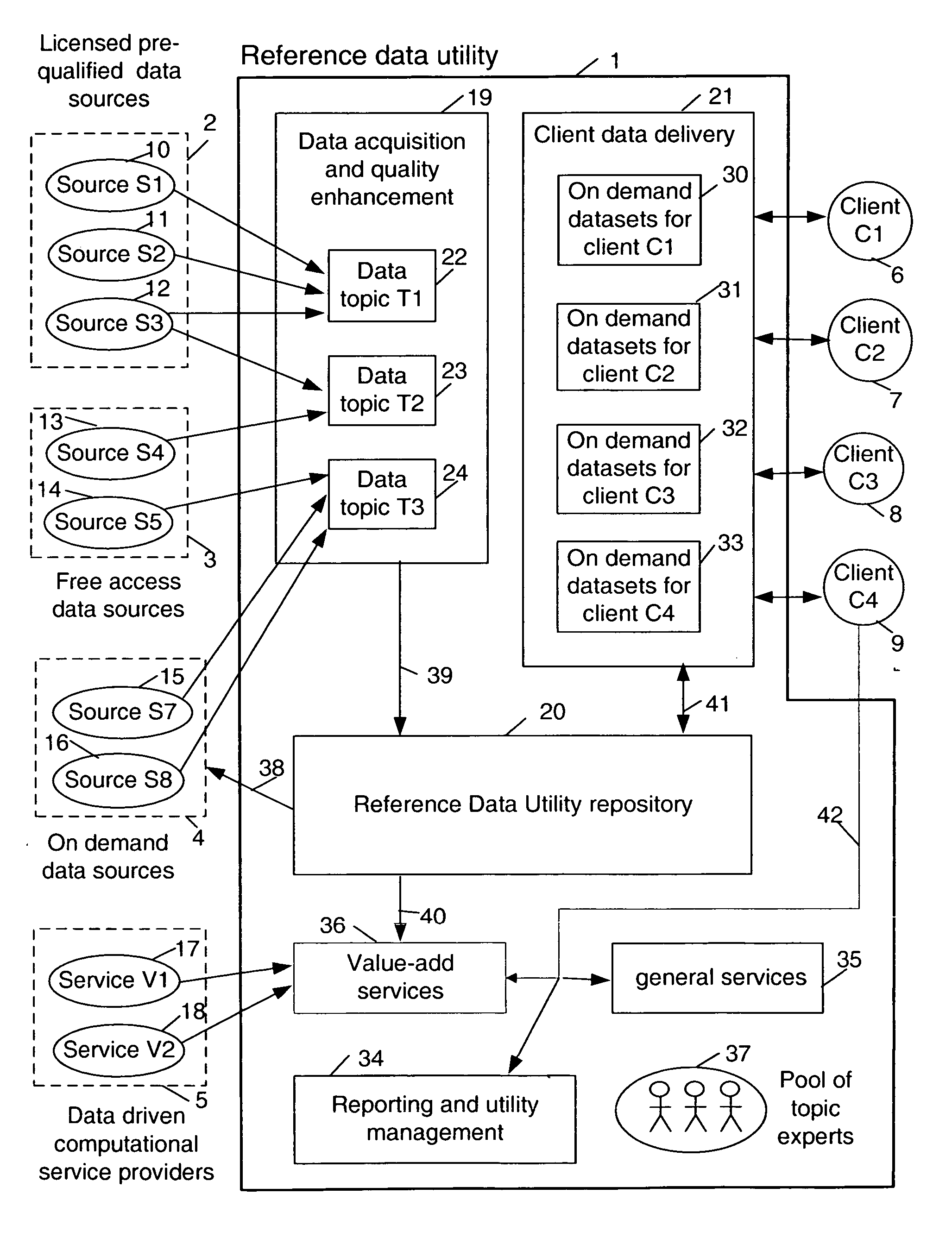
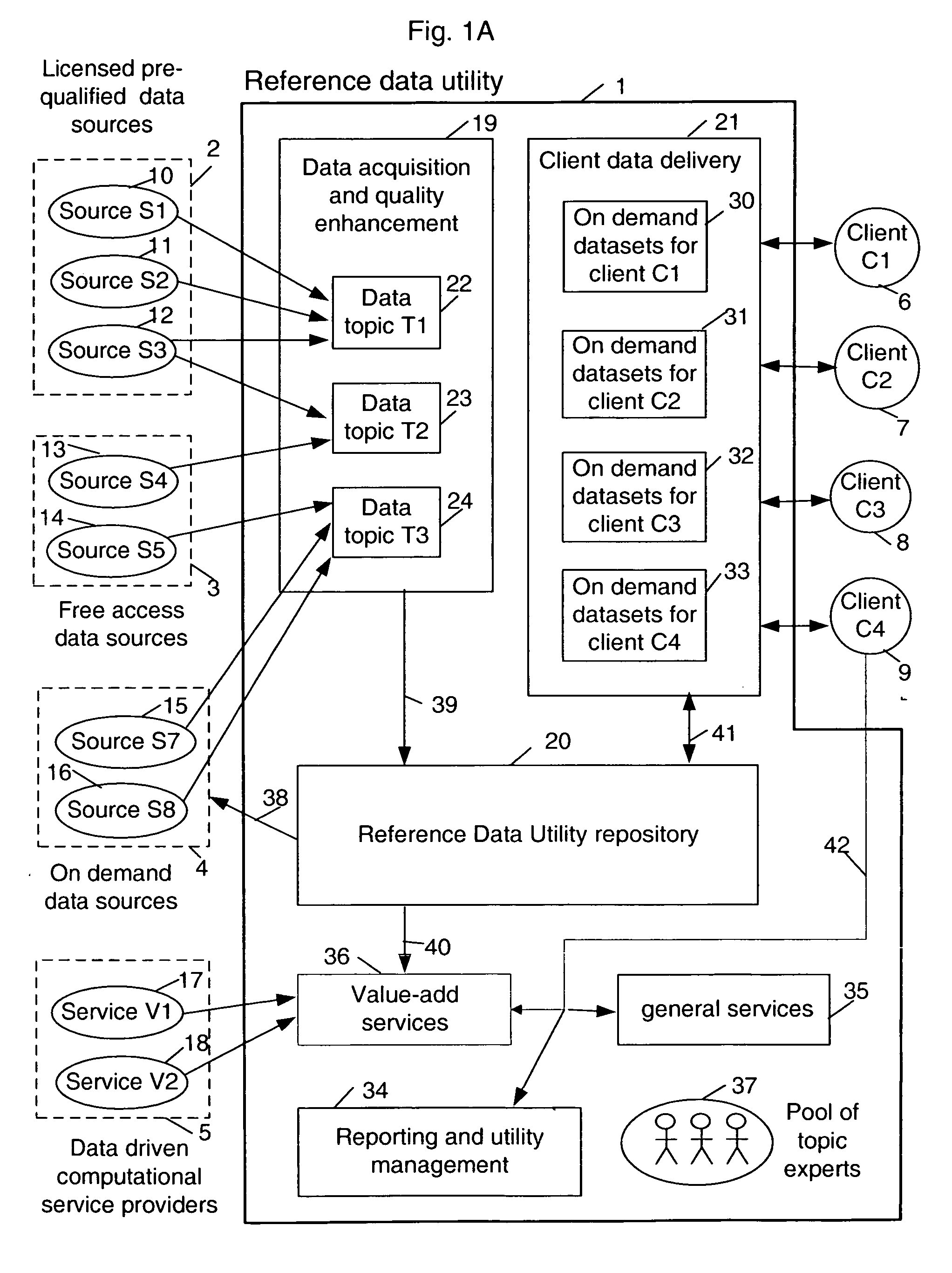
Forming and maintaining a multi-source multi-tenant data repository on behalf of multiple tenants. Information in the multi-source multi-tenant data repository is received from multiple sources. Different sources and different data quality enhancement processes may yield different values for attributes of the same referred entity. Information in the multi-source multi-tenant data repository is tagged with annotations documenting the sources of the information, and any data quality processing actions applied to it. Tenants of the multi-source multi-tenant data repository have entitlement to values from some sources and to the results of some quality enhancement processes. Aspects of the method maintain this entitlement information; employ evolutionarily tracked source data tags; receive requests for information, locate the requested information, apply any sourcing preference, enforce entitlements and return entitled values to the requester. An outsourced reference data utility is one context where such a multi-source multi-tenant data repository is useful.
Owner:ADINOLFI RONALD EMMETT +9
Multi-tenant audit awareness in support of cloud environments
ActiveUS20120179646A1Facilitate compliance analysisEasy to analyzeDatabase management systemsDigital data processing detailsData miningComputer science
A cloud enablement aggregation proxy (CEAP) receives and processes audit data from audited resources before such data is stored in a database. The CEAP manages log data for resources hosted in a multi-tenant shared pool of configurable computing resources (e.g., a compute cloud). A method for managing log data begins by the proxy aggregating and normalizing log information received from a plurality of the resources. The aggregated and normalized log information is then parsed to identify a tenant associated with each of a set of transactions. For each of the set of transactions, the CEAP annotates log data associated with the tenant and the particular transaction to include a tenant-specific identifier. An optional tenant separation proxy (TSP) separates the annotated log data on a per tenant basis prior to storage, and the tenant-specific log data may be stored in per tenant data structures or dedicated tenant log event databases to facilitate subsequent compliance or other analysis.
Owner:IBM CORP
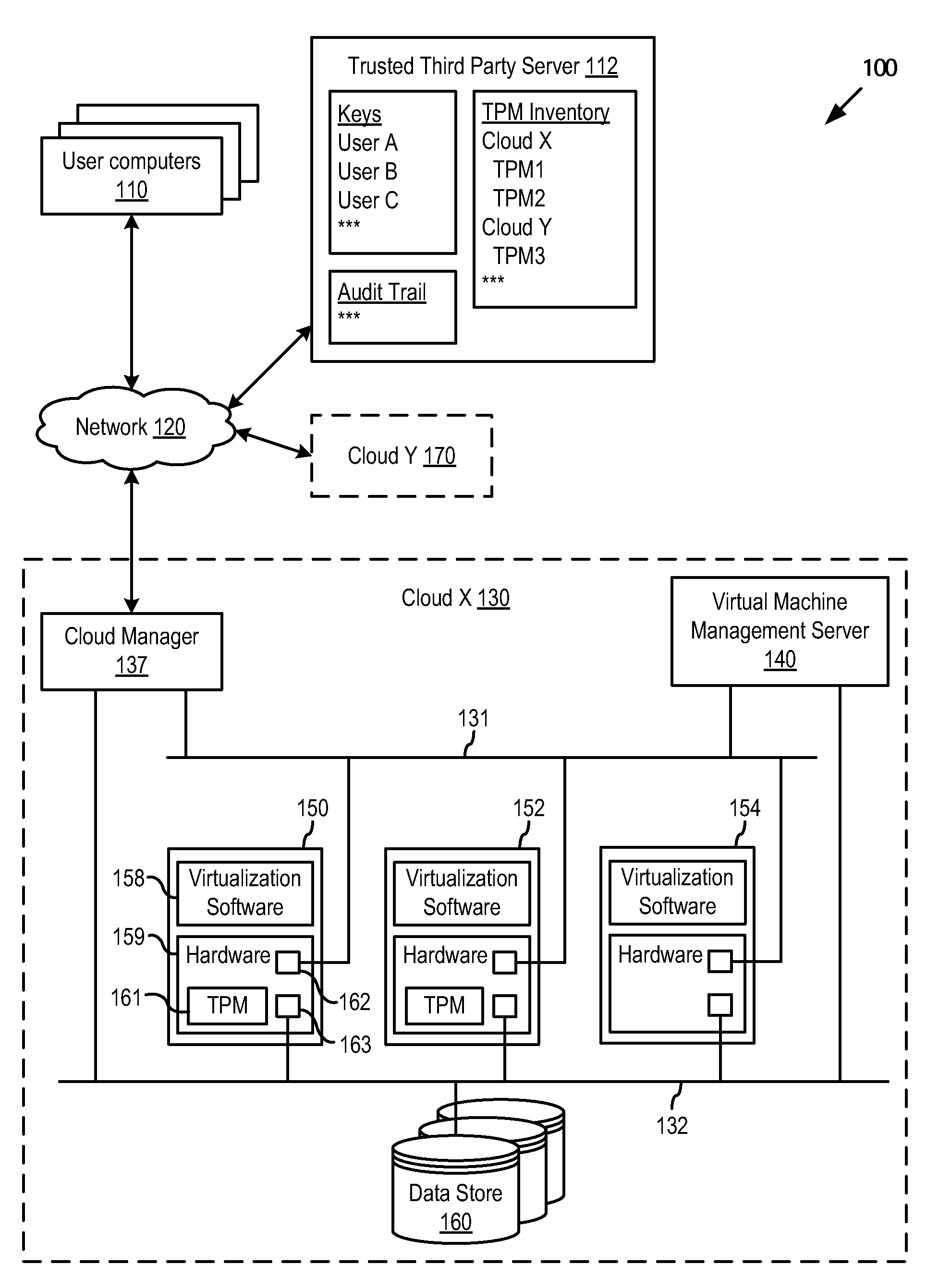
Securing customer virtual machines in a multi-tenant cloud
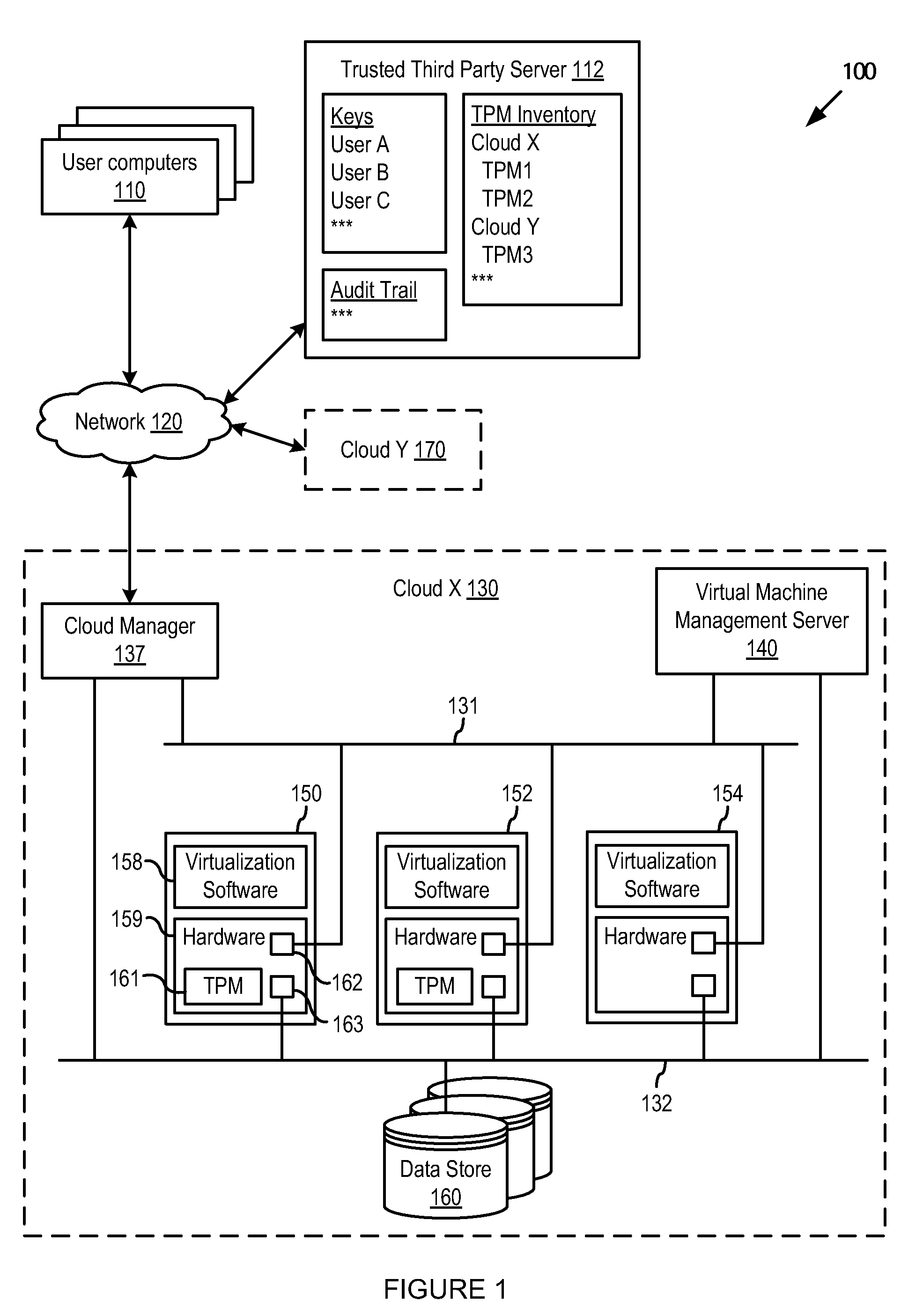
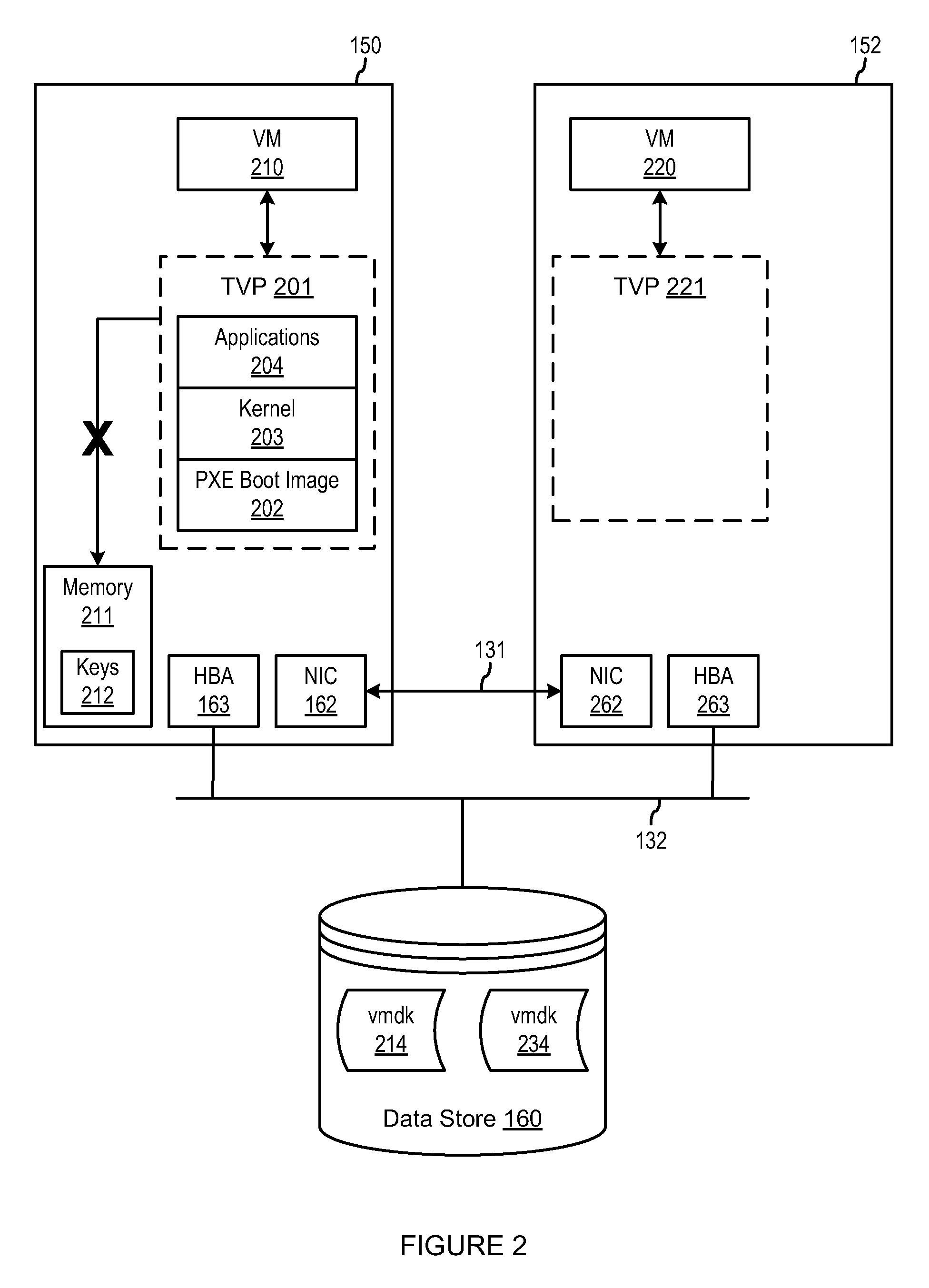
ActiveUS20110302415A1Limited accessKey distribution for secure communicationUser identity/authority verificationVirtualizationThird party
A trusted virtualization platform protects sensitive customer data during operation of virtual machines in a multi-tenant cloud computing center. The trusted virtualization platform limits administrator access to the data and state of the virtual machines running thereon, reports any changes made thereto, and requires keys provided by the customer or a trusted third party of the customer to perform management operations on the virtual machines. By requiring cloud computing centers to use such trusted virtualization platforms, customers uploading their virtual machines into the cloud computing center can be assured that cloud administrators will not be able to access or tamper with their private data. Furthermore, customers can directly audit all important state or configuration changes for their virtual machines as the trusted virtualization platform can be configured to report all such changes according to a security policy set by the customer.
Owner:VMWARE INC
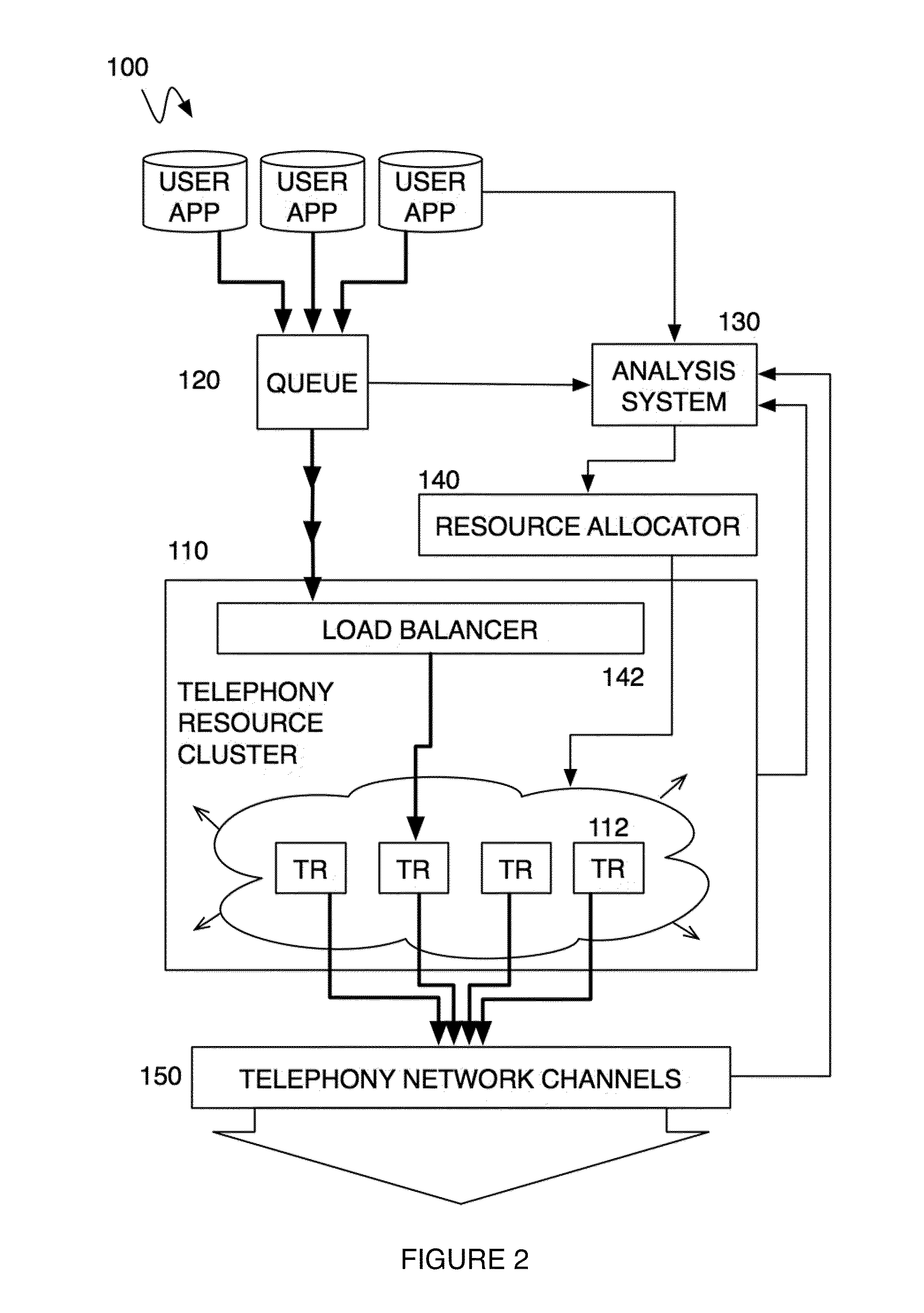
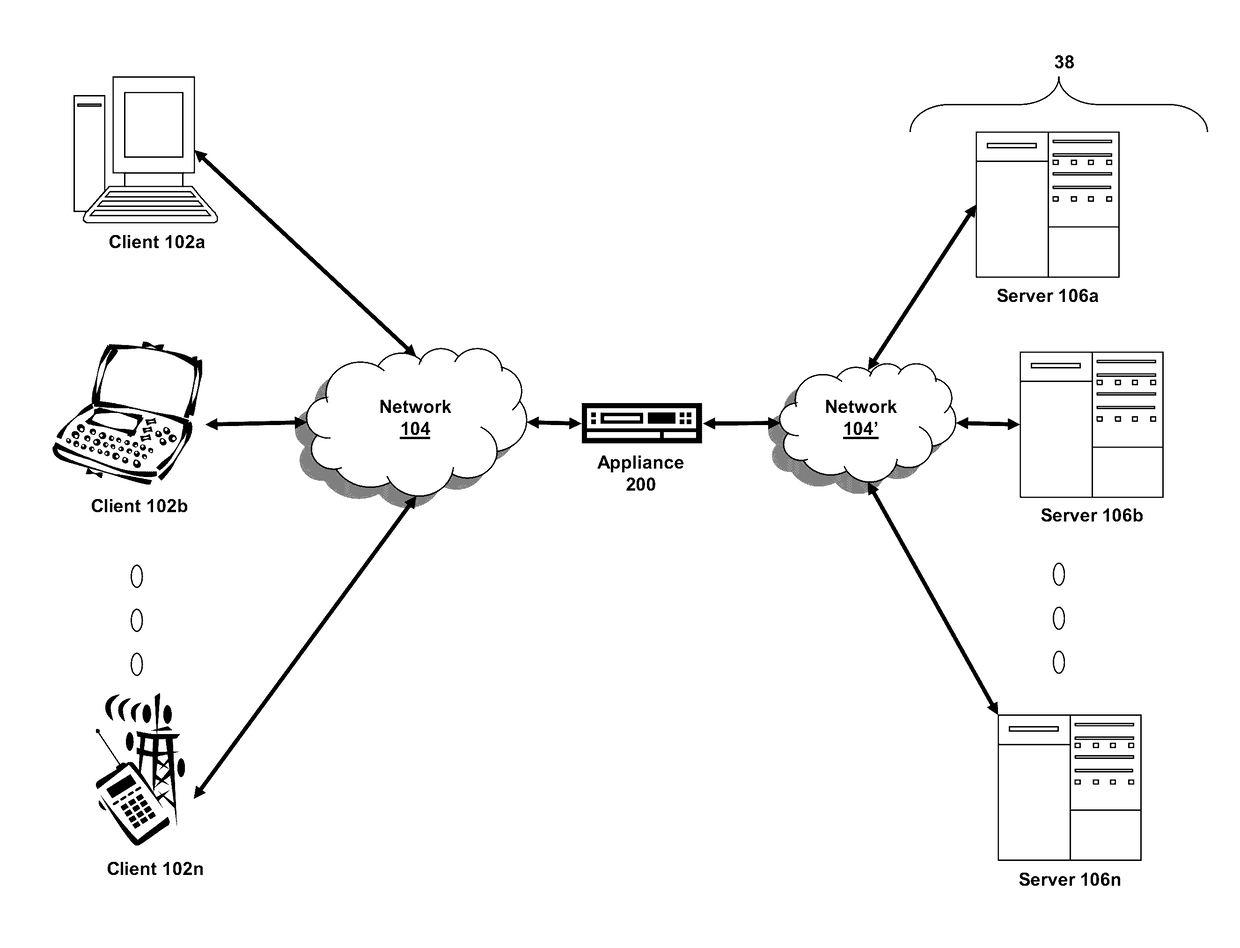
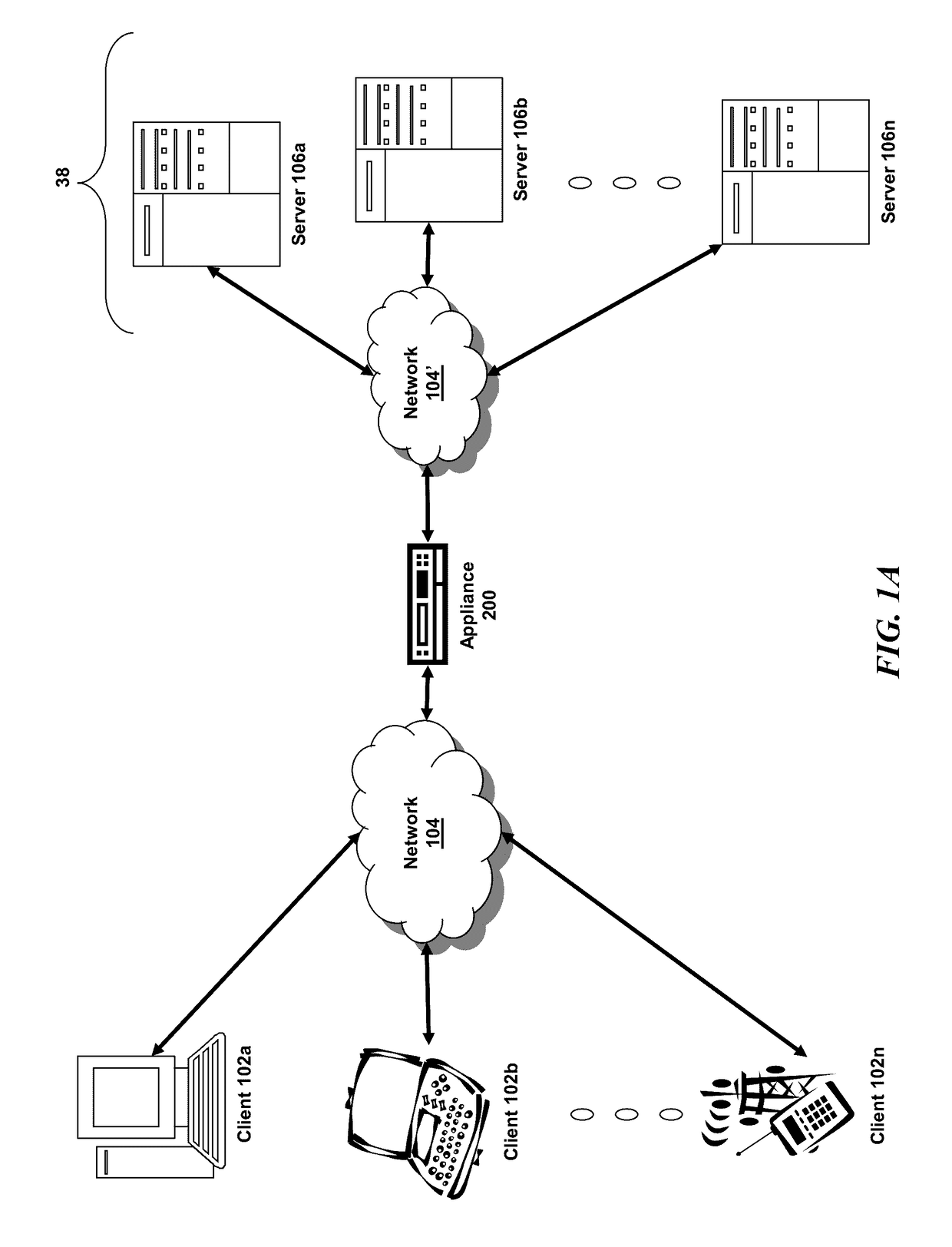
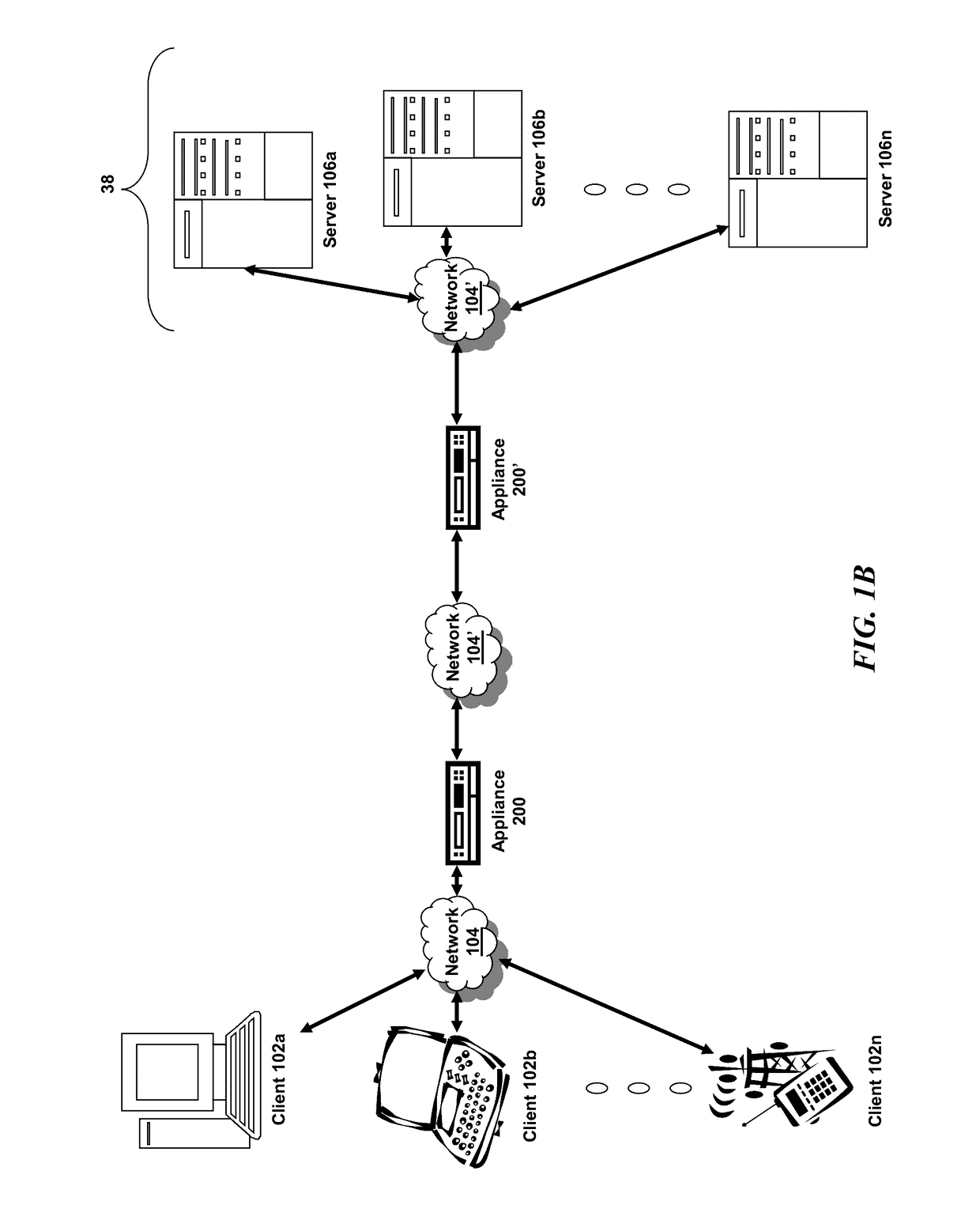
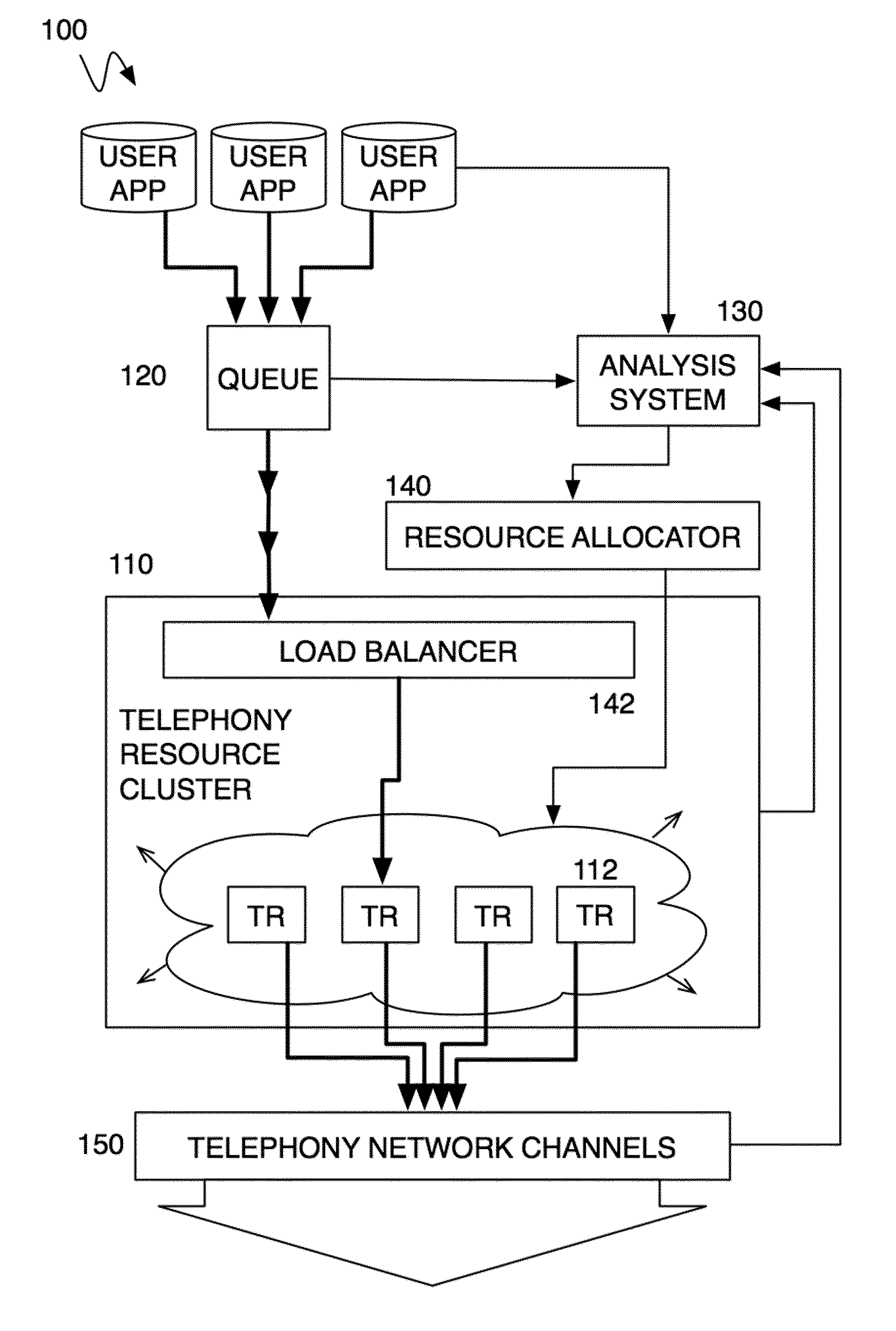
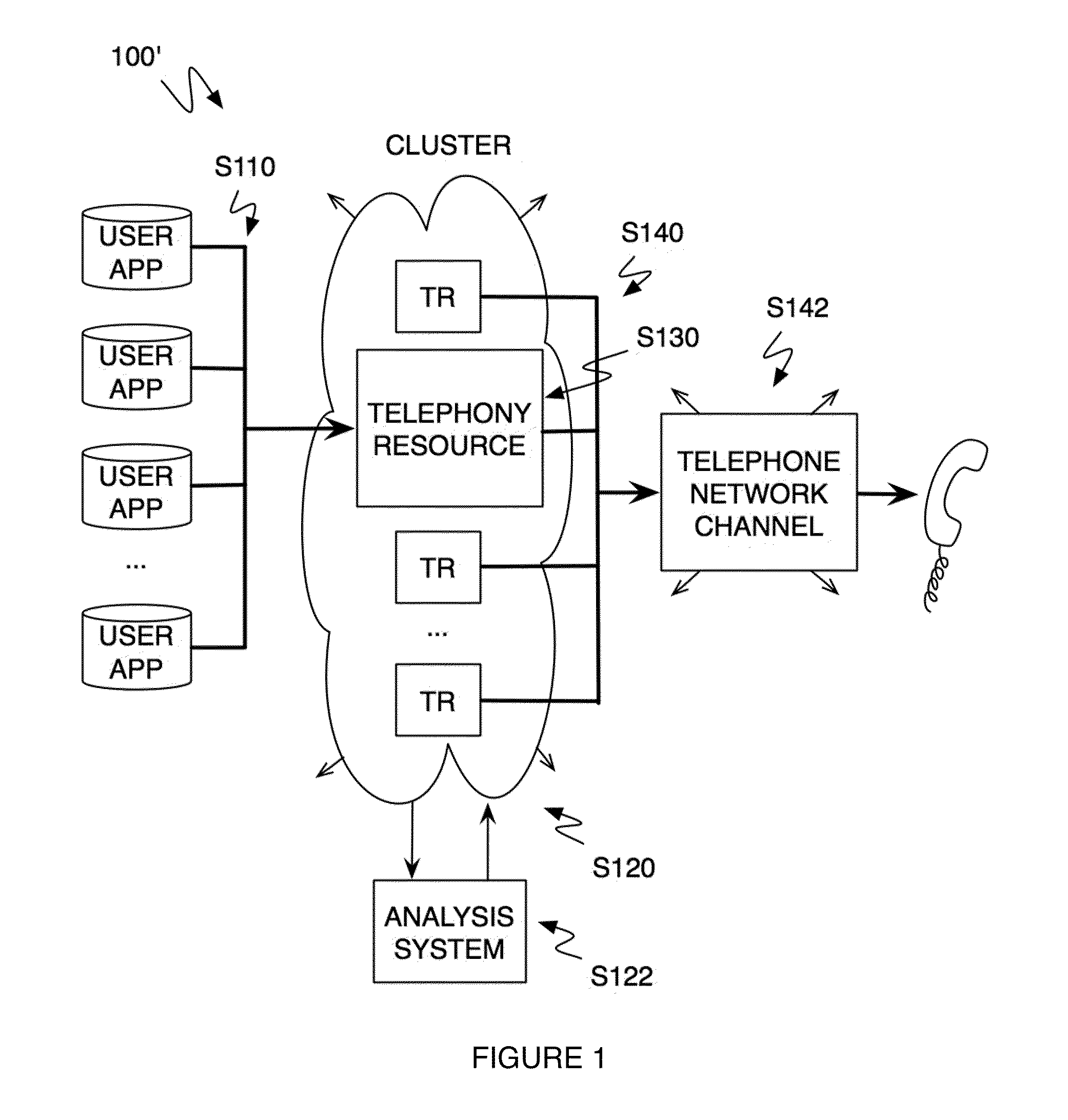
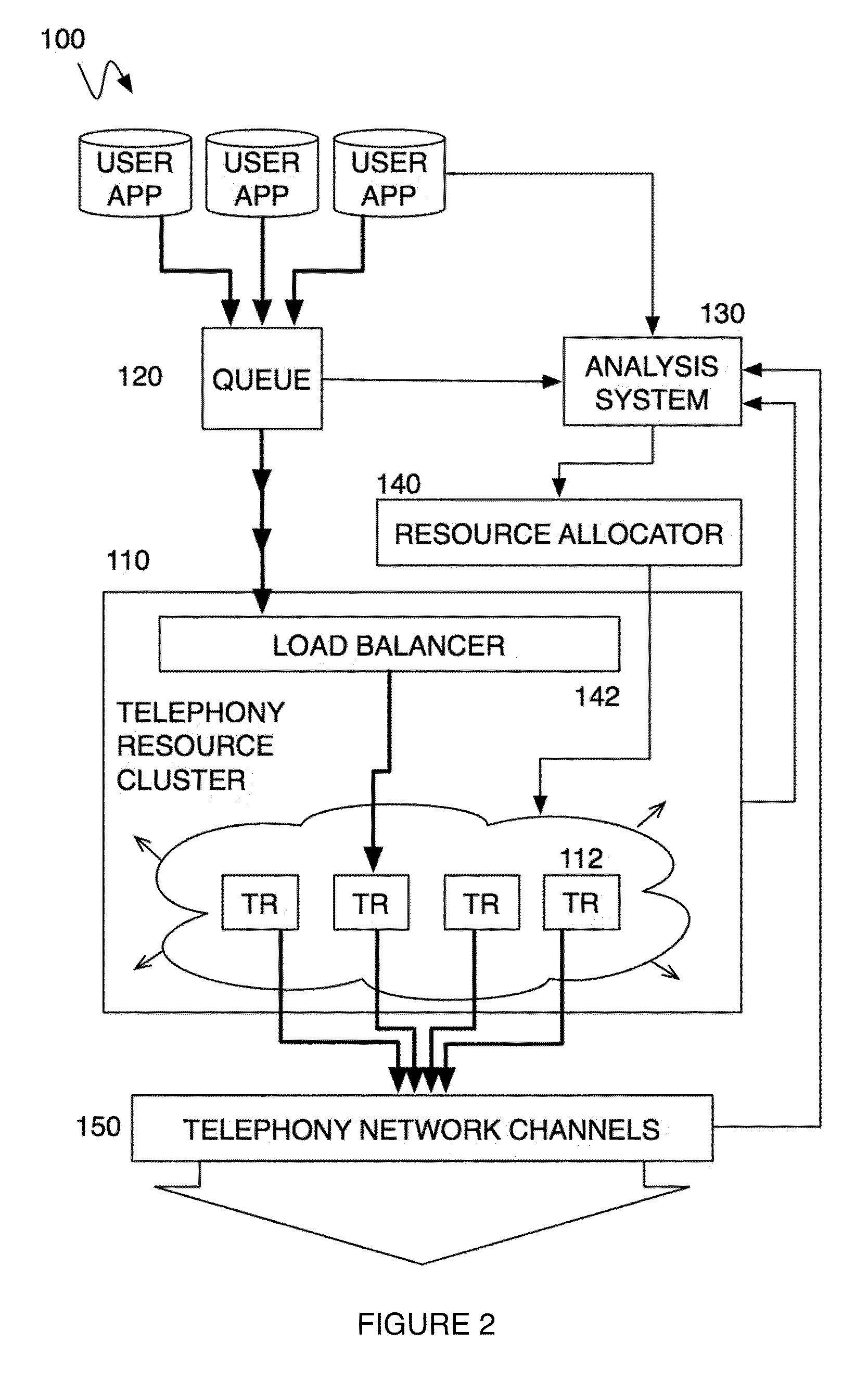
Method and system for a multitenancy telephone network
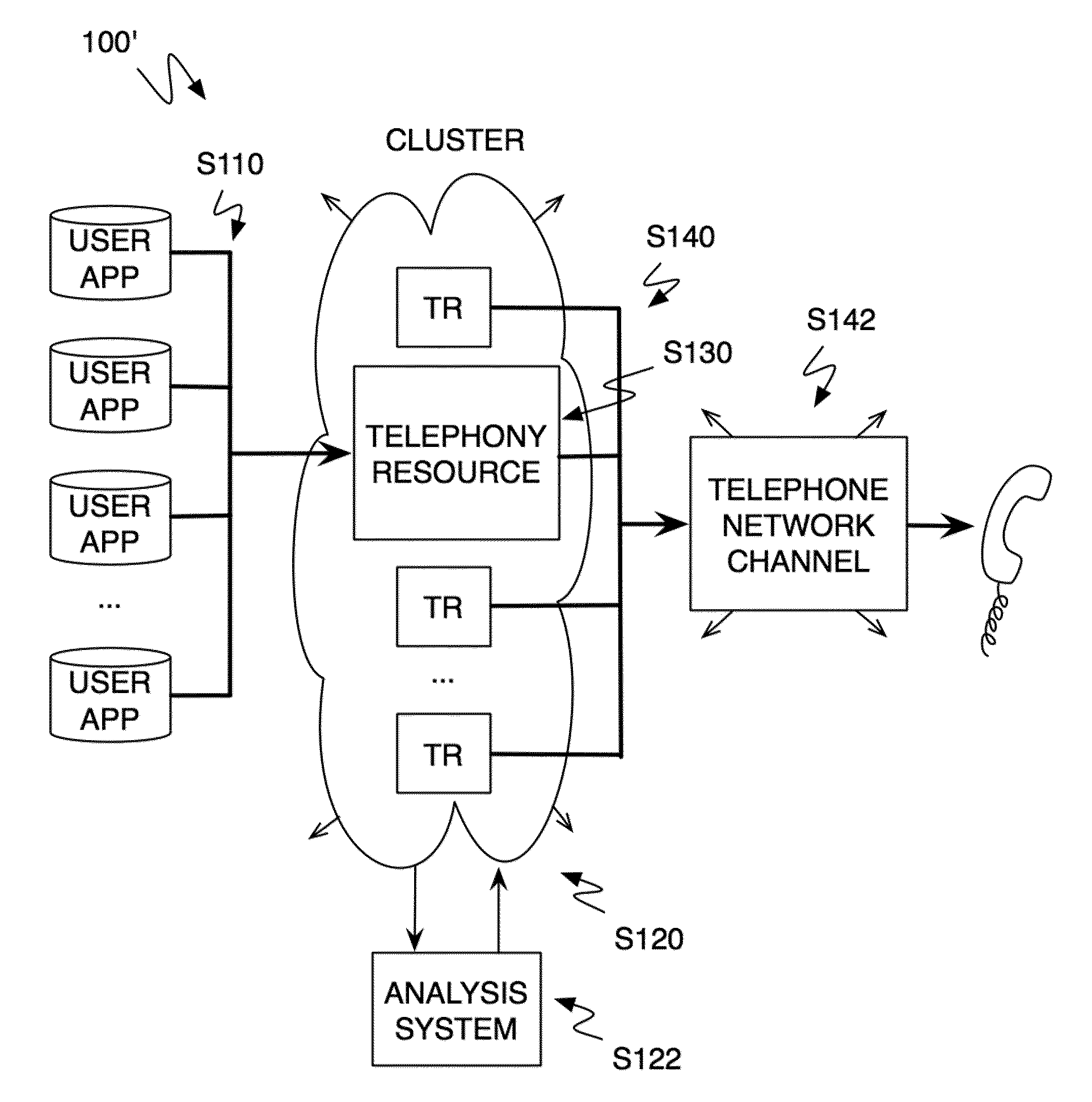
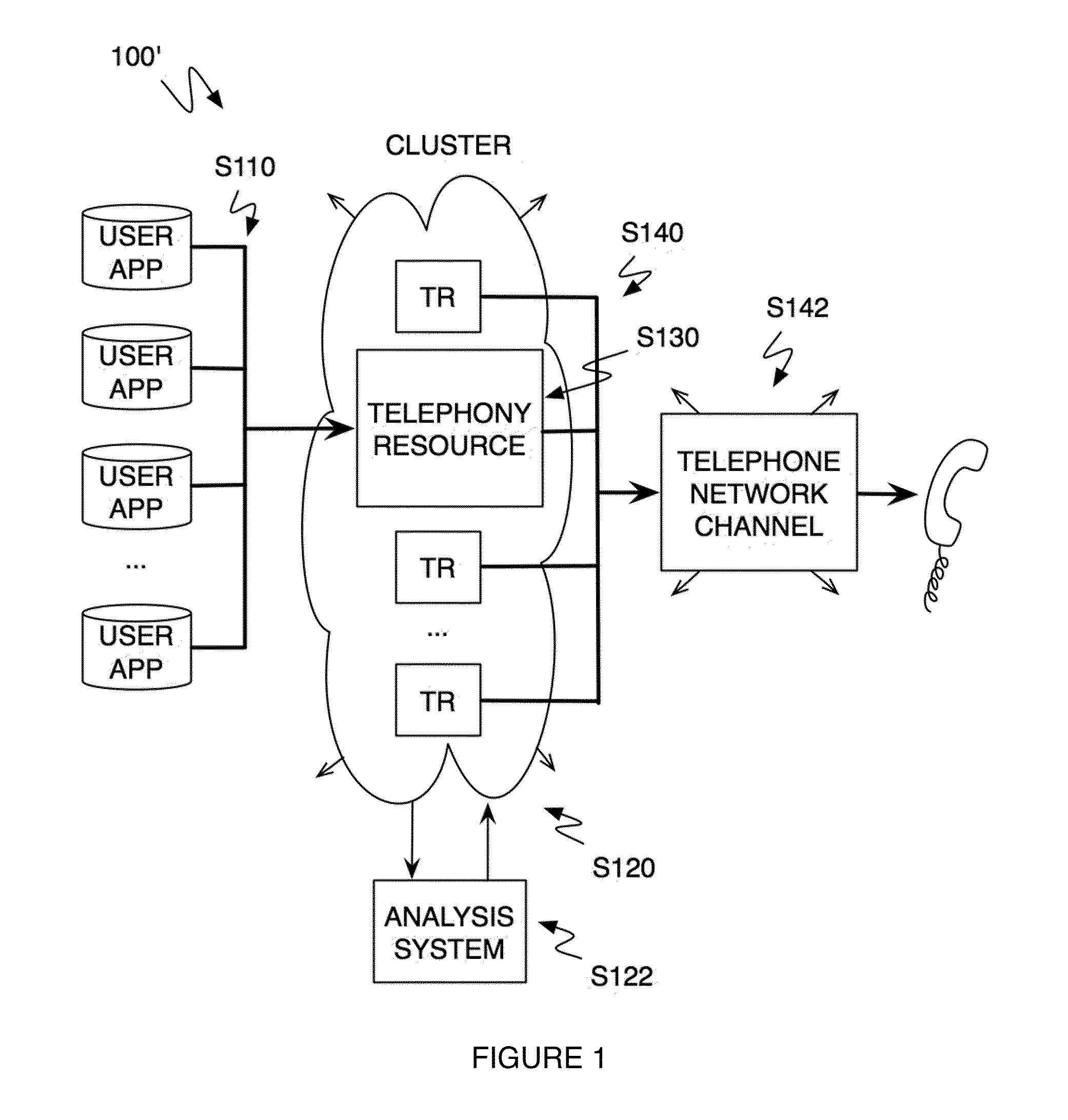
ActiveUS20100232594A1Energy efficient ICTSpecial service for subscribersTelephone networkMultitenancy
A method and system for operating a multitenancy telephony system including a call queue that stores call requests received from a plurality of users; an expandable and contractible telephony resource cluster that establishes call sessions for call requests; a analysis system that calculates capacity requirements of the system; a resource allocator that manages the scaling and operation of the telephony resource cluster; and a plurality of telephony network channels that are used as telephony communication channels for call sessions.
Owner:TWILO INC
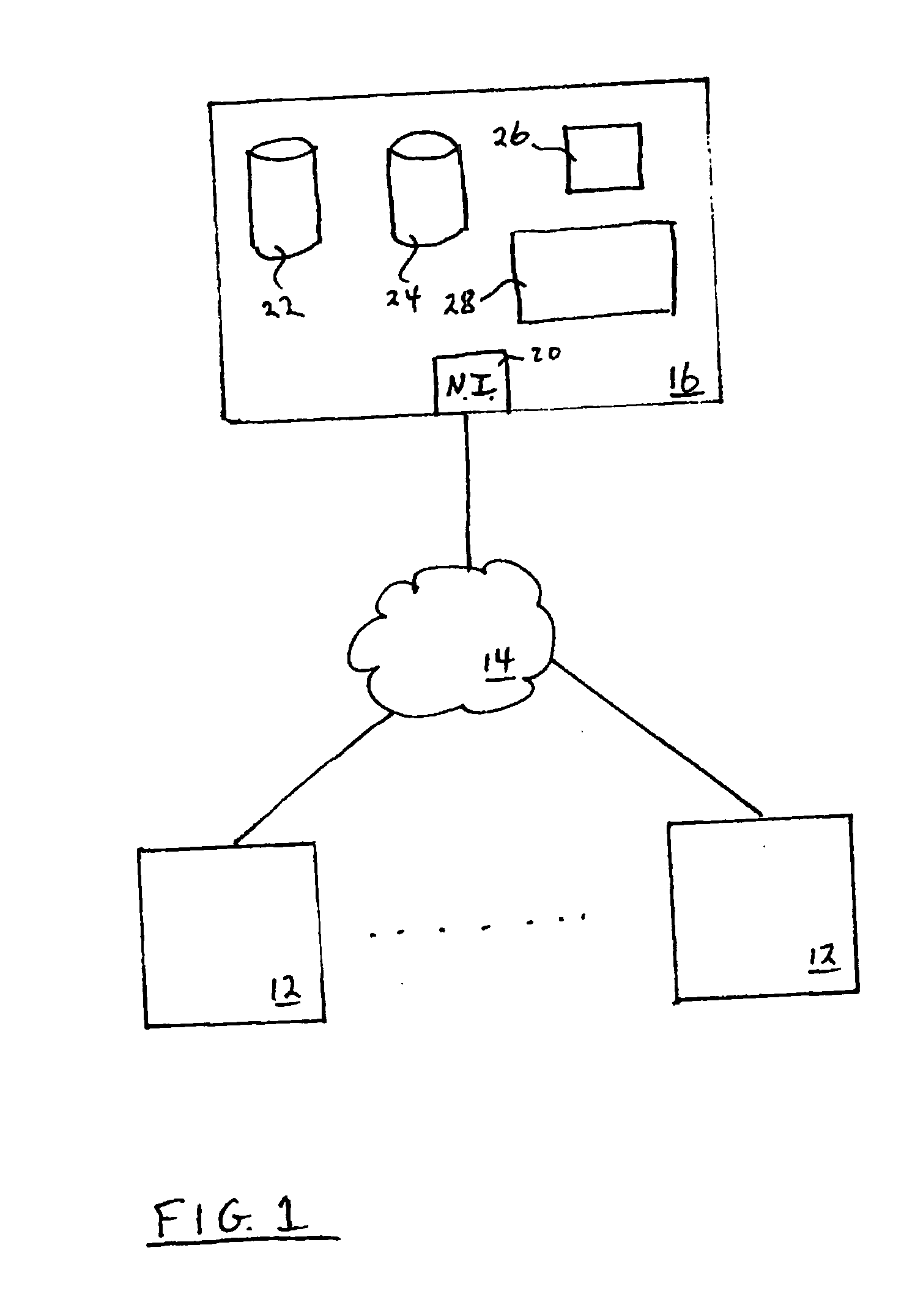
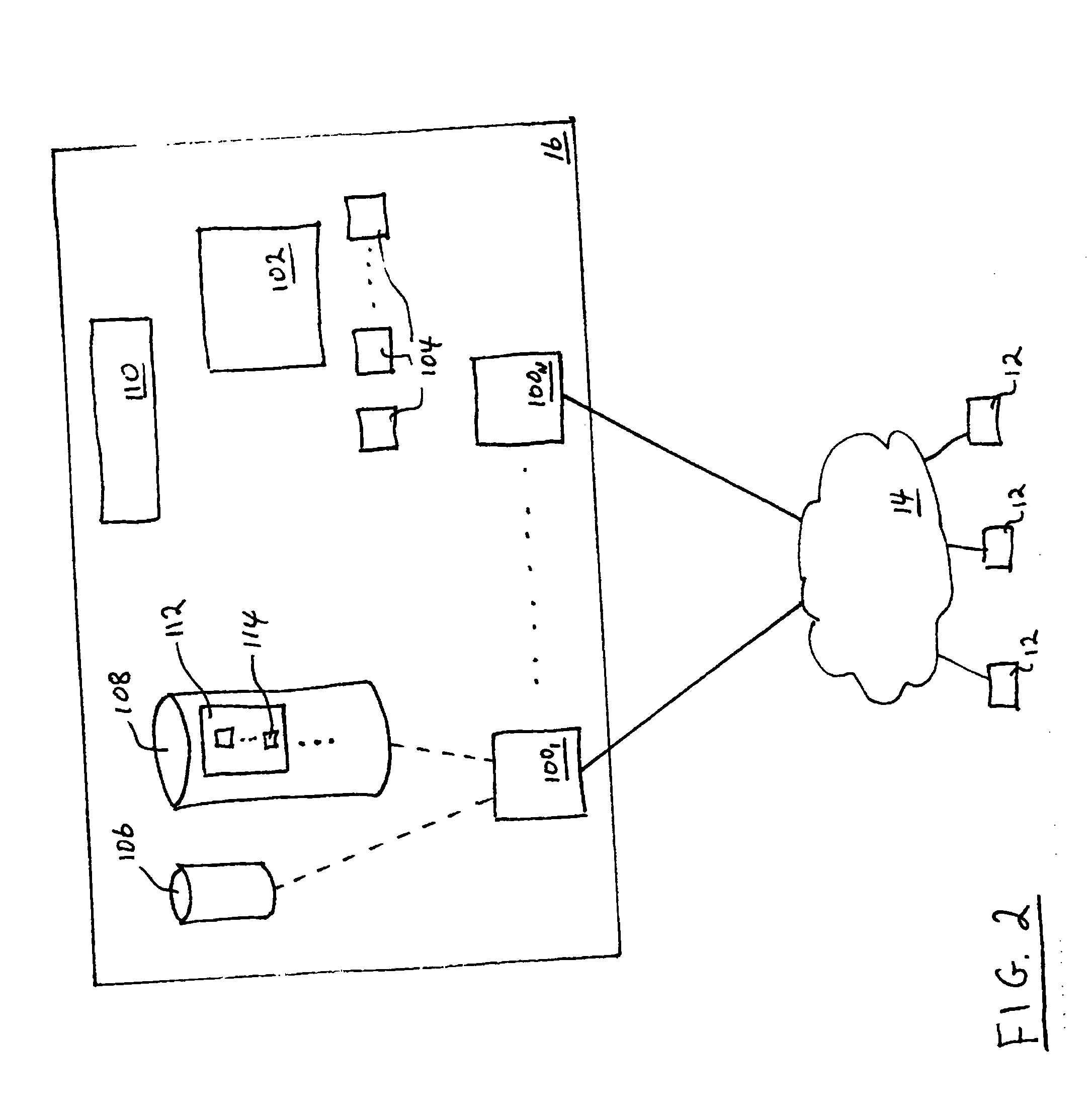
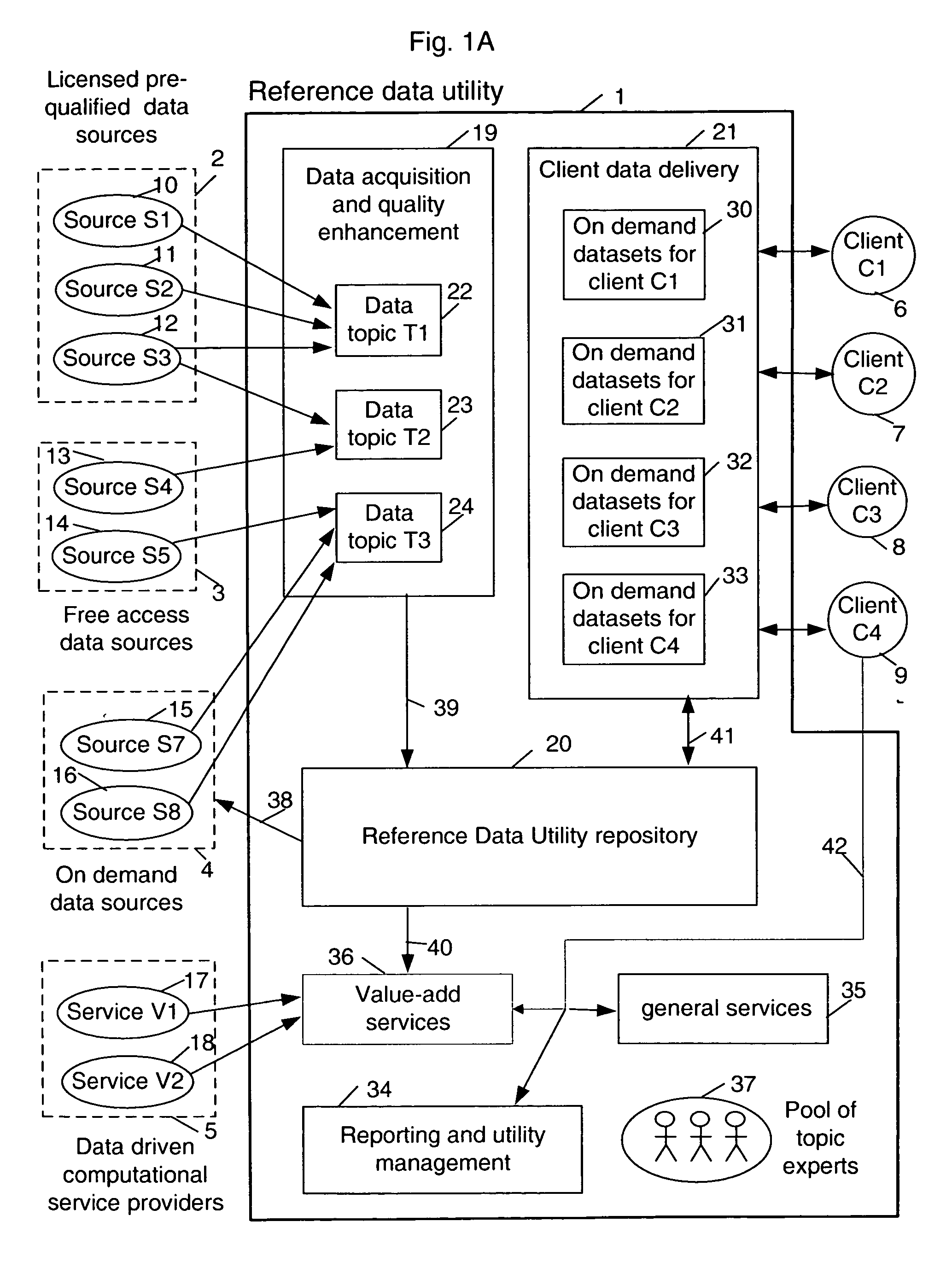
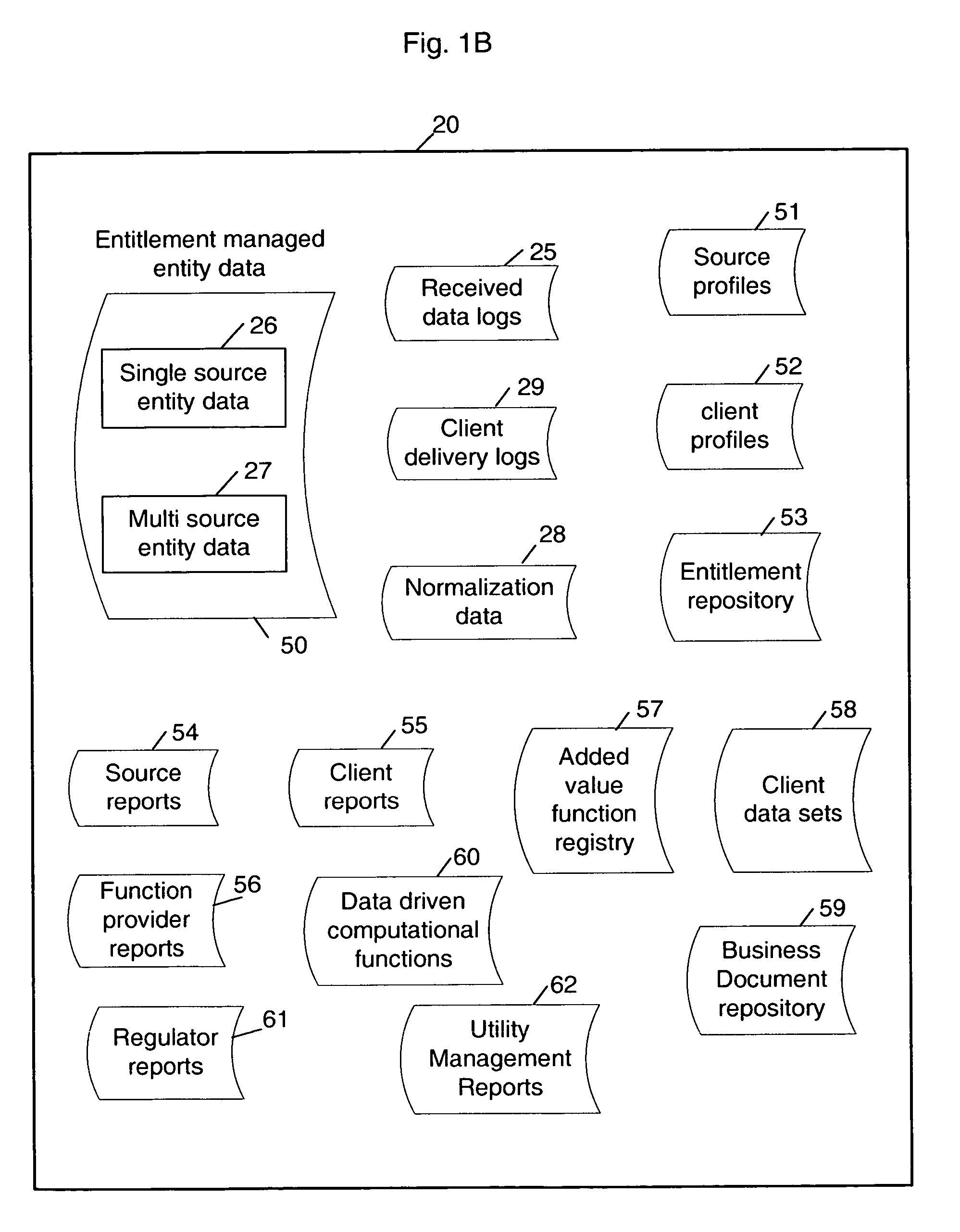
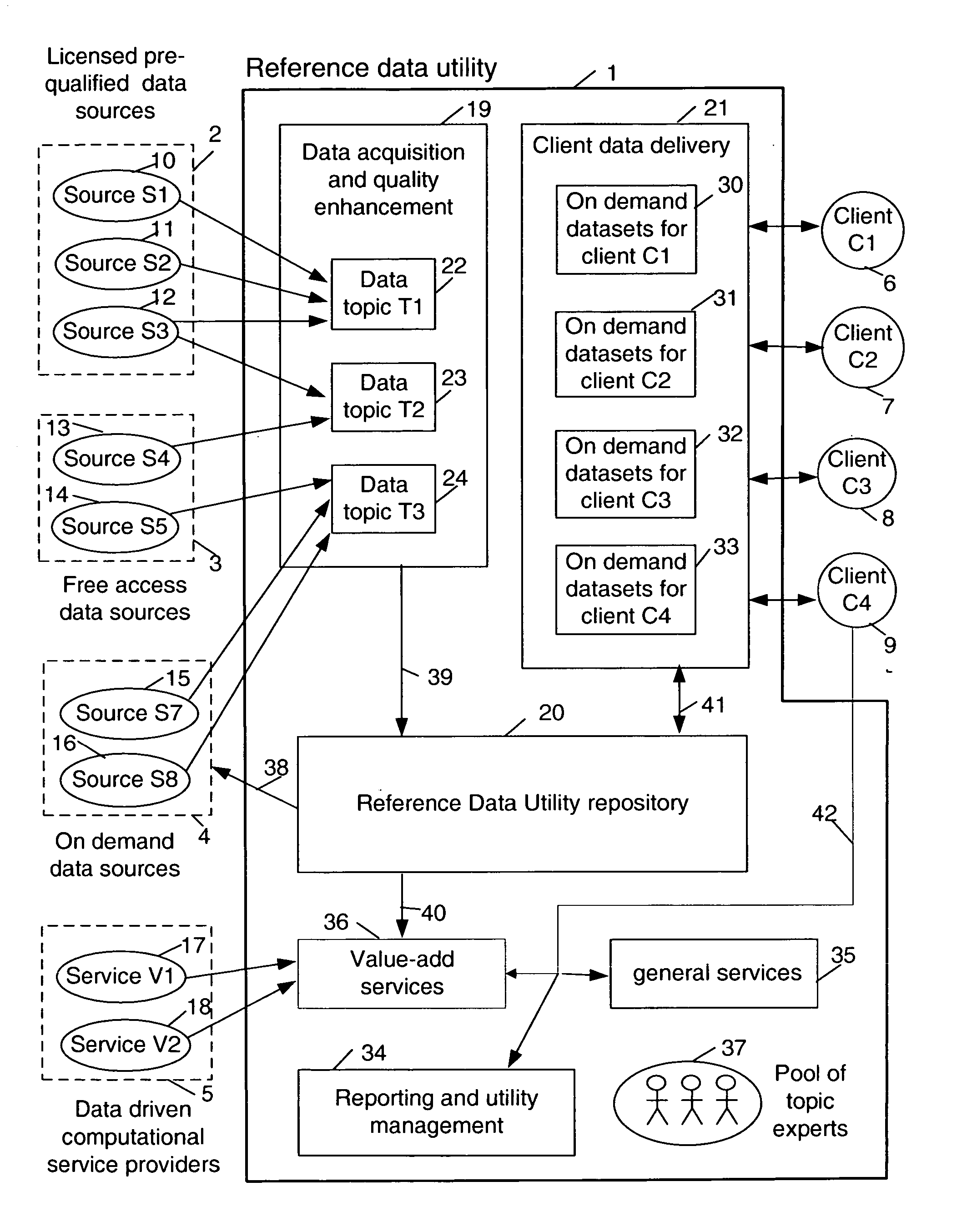
Sharable multi-tenant reference data utility and methods of operation of same
A multi-source multi-tenant reference data utility and methods for forming and maintaining the same, delivering high quality reference data in response to requests from clients, implemented using a shared infrastructure, and also providing added value services using the client's reference data. Included are data cleansing and quality assurance of the received data with full tracking of the sourcing of each value, storage of resulting entity values in a repository which allows retrievals and enforces source based entitlements, and delivery of retrieved data in the form of on demand datasets supporting a wide range of client application needs. An advantageous implementation has additional services for reporting on data quality and usage, a selection of value adding data driven computations and business document storage. By using a shared infrastructure and amortizing the costs of data quality assurance across a plurality of clients, while ensuring that clients only receive values from data sources to which they are licensed, better quality data at lower cost is delivered.
Owner:IBM CORP
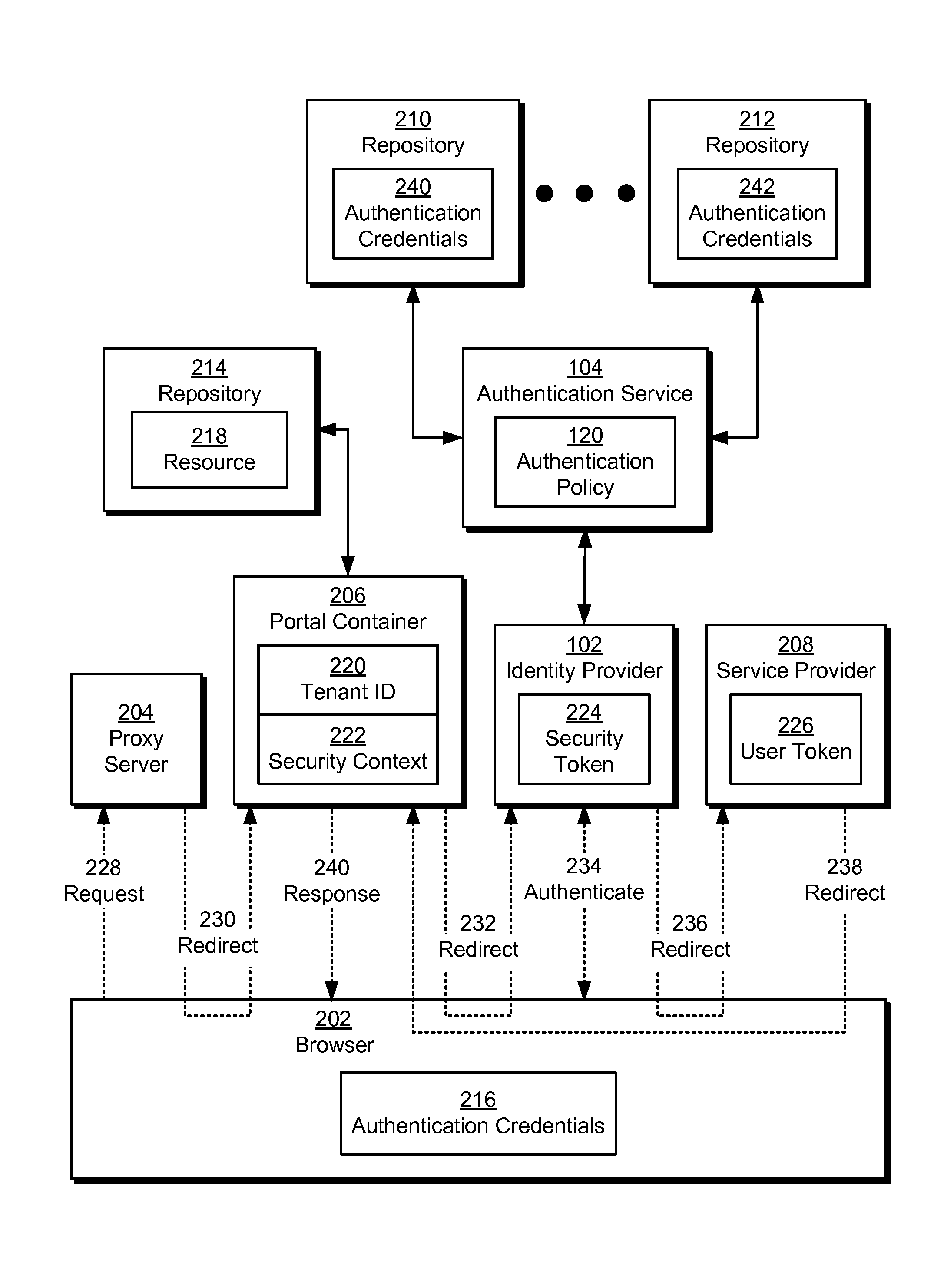
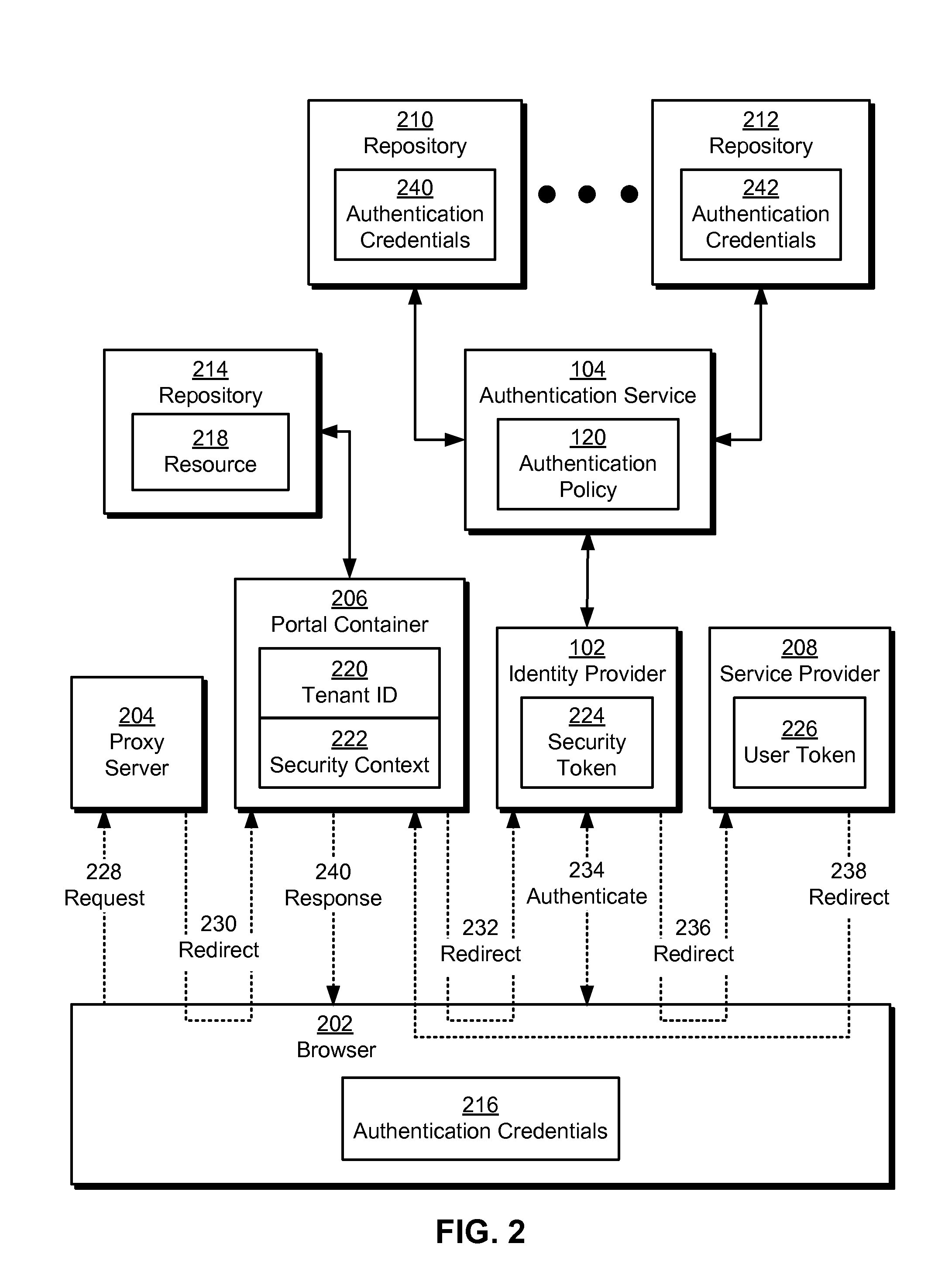
Single sign-on in multi-tenant environments
ActiveUS20140090037A1Digital data processing detailsMultiple digital computer combinationsInternet privacySystem usage
The disclosed embodiments provide a system that authenticates a user. During operation, the system identifies a first tenant associated with a first request for a first resource from the user and obtains an authentication policy for the first tenant. Next, the system uses an authentication mechanism associated with the authentication policy to authenticate the user. Upon authenticating the user, the system provides a first security token for enabling access to the first resource by the user.
Owner:INTUIT INC
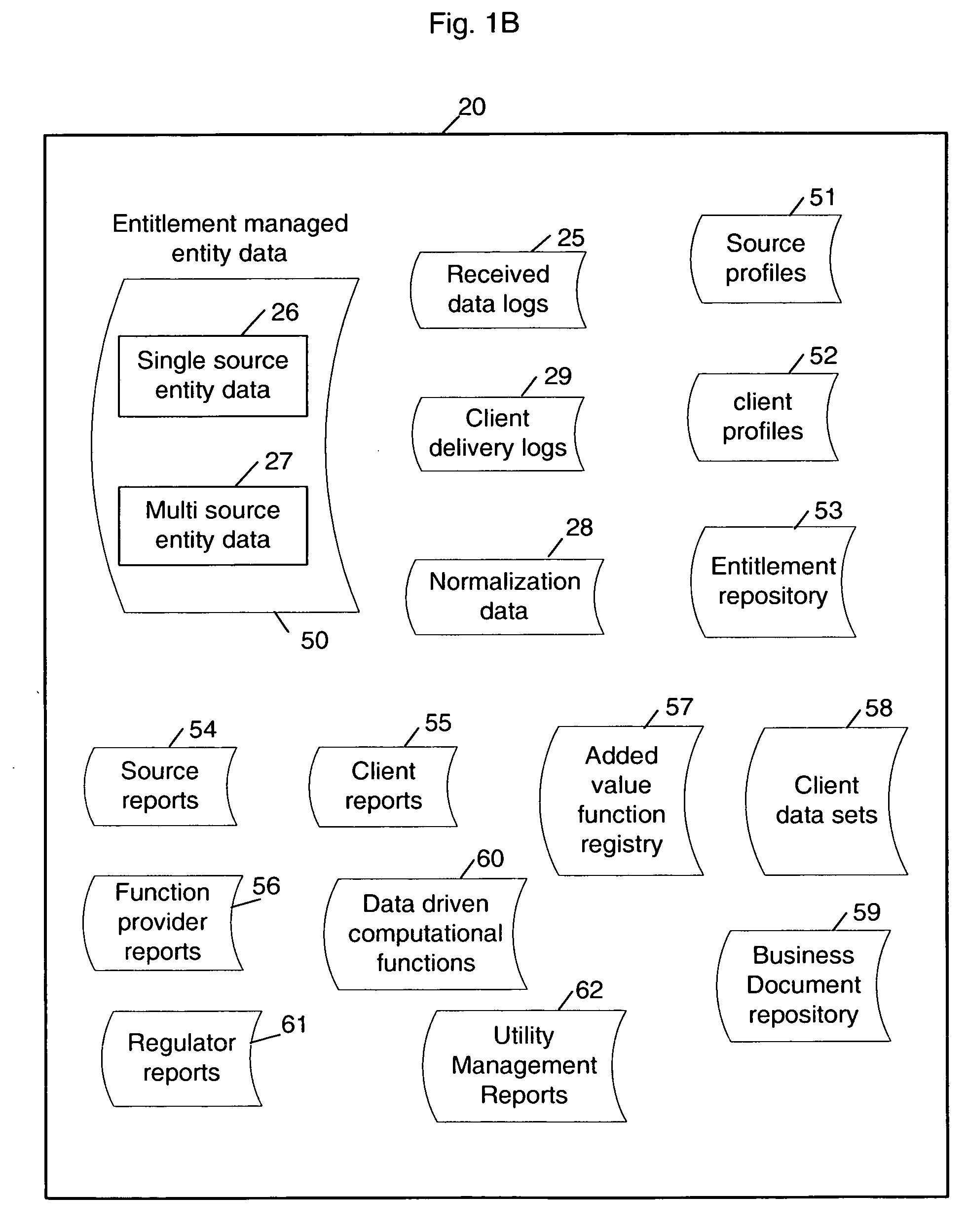
Enabling value enhancement of reference data by employing scalable cleansing and evolutionarily tracked source data tags
Provision for scalable cleansing and value enhancement of data in the context of a multi-source multi-tenant data repository. The source data comes from multiple sources and on multiple topics. Evolutionarily tracked source data tags are used to hold tracking information reflecting the nature and sources of each change to the data, as it is affected during the various stages of data processing. The stages of processing include validation, normalization, single-source cleansing and cross-source processes. Various rules are applied during these stages, and evolutionarily tracked source data tags are used to record sources and agents of all changes to the data. As information is processed, transformed, and added to the repository, corresponding evolutionarily tracked source data tags are stored in association with the various information elements. The information contained in these tags can be used to enforce data entitlements in a multi-tenant data repository environment.
Owner:CALUSINSKI EDWARD PATRICK JR +9
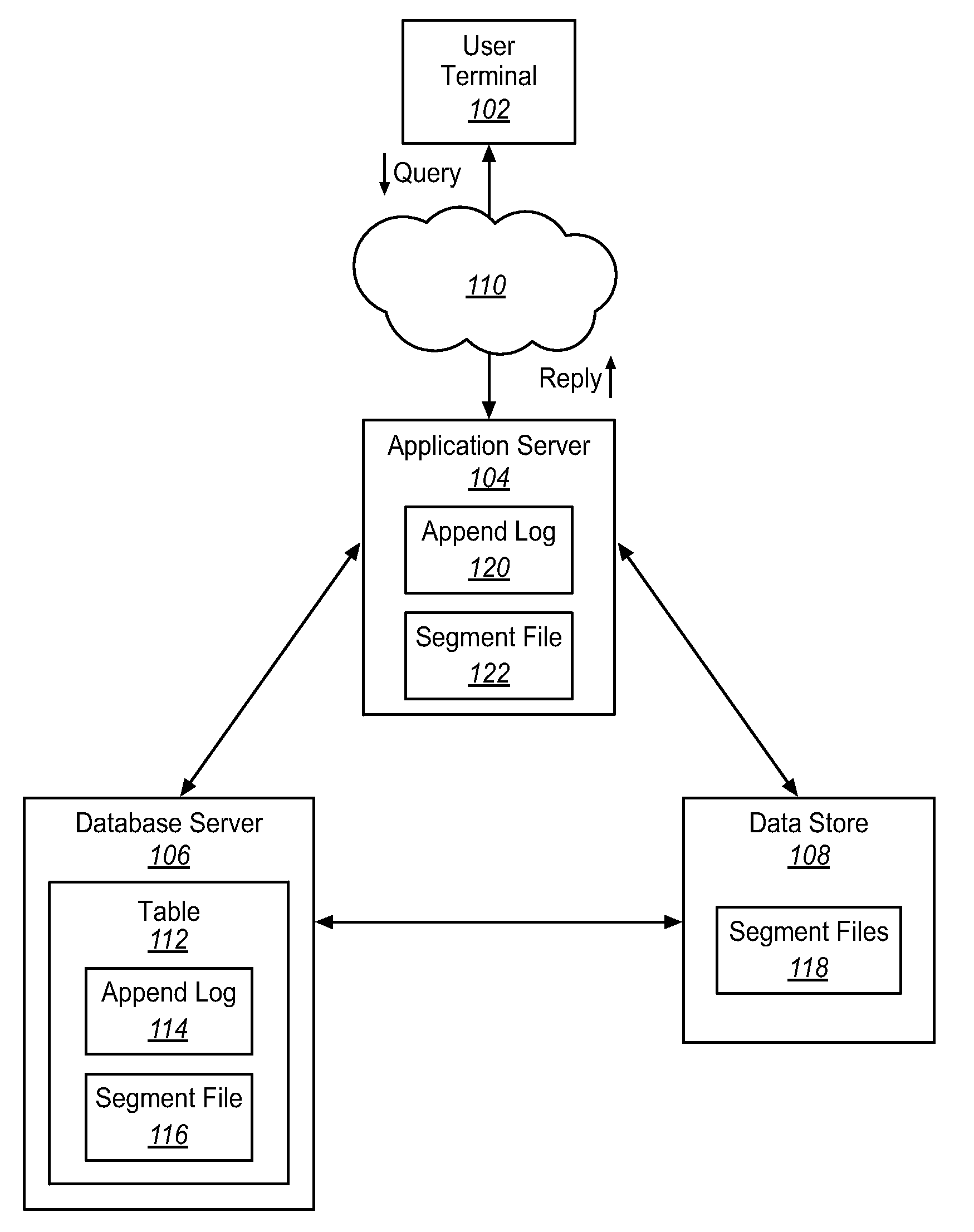
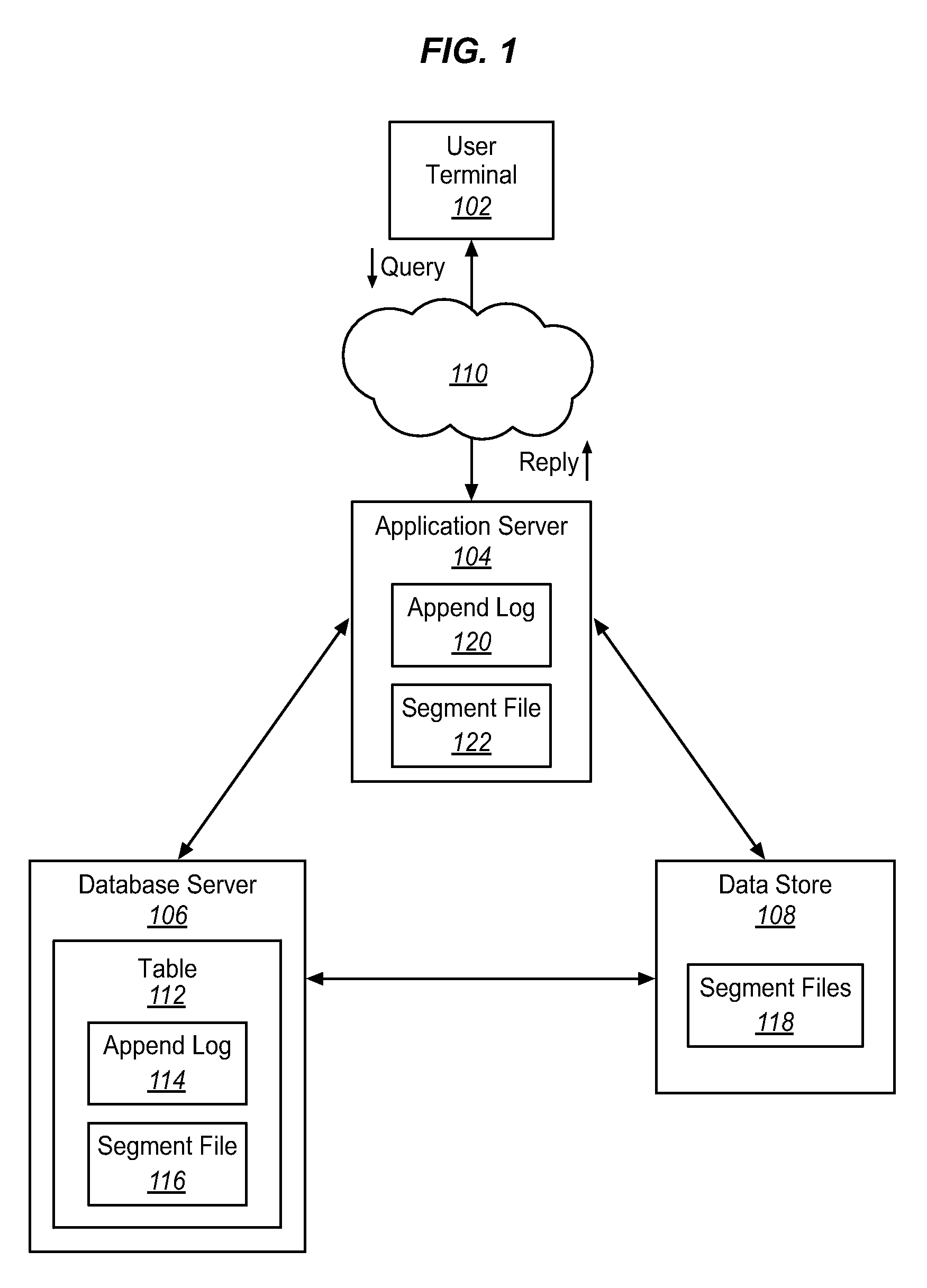
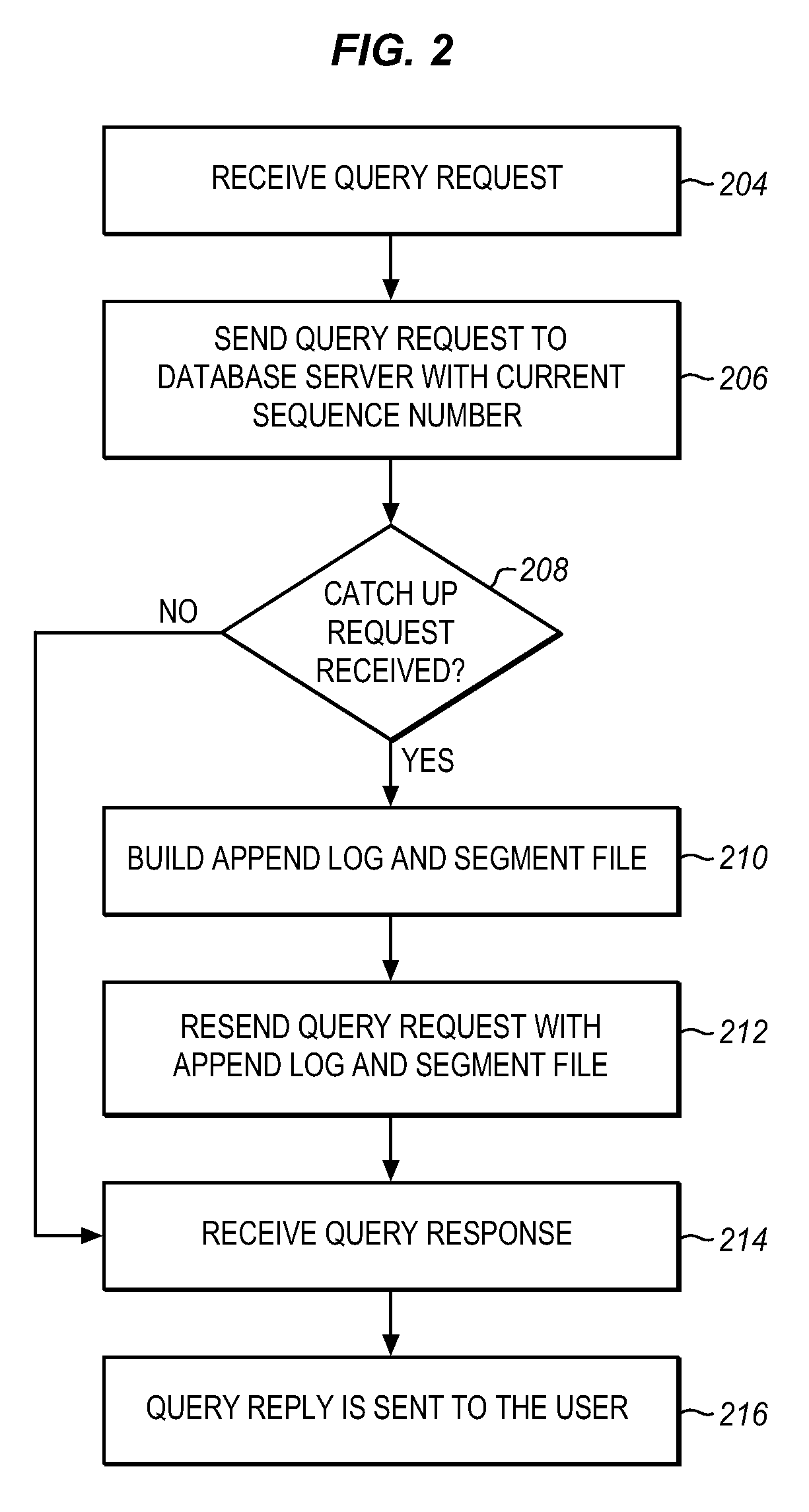
Methods and systems for appending data to large data volumes in a multi-tenant store
ActiveUS20110258242A1For quick maintenanceMore reliableDigital data information retrievalSpecial data processing applicationsMultitenancyData store
In accordance with embodiments, there are provided mechanisms and methods for appending data to large data volumes in a multi-tenant store. These mechanisms and methods for appending data to large data volumes can enable embodiments to provide more reliable and faster maintenance of changing data. In an embodiment and by way of example, a method for appending data to large data volumes is provided. The method embodiment includes receiving new data for a database. The new data is written to a temporary log. The size of the log is compared to a threshold. Then the log is written to a data store, if the size of the log is greater than the threshold.
Owner:SALESFORCE COM INC
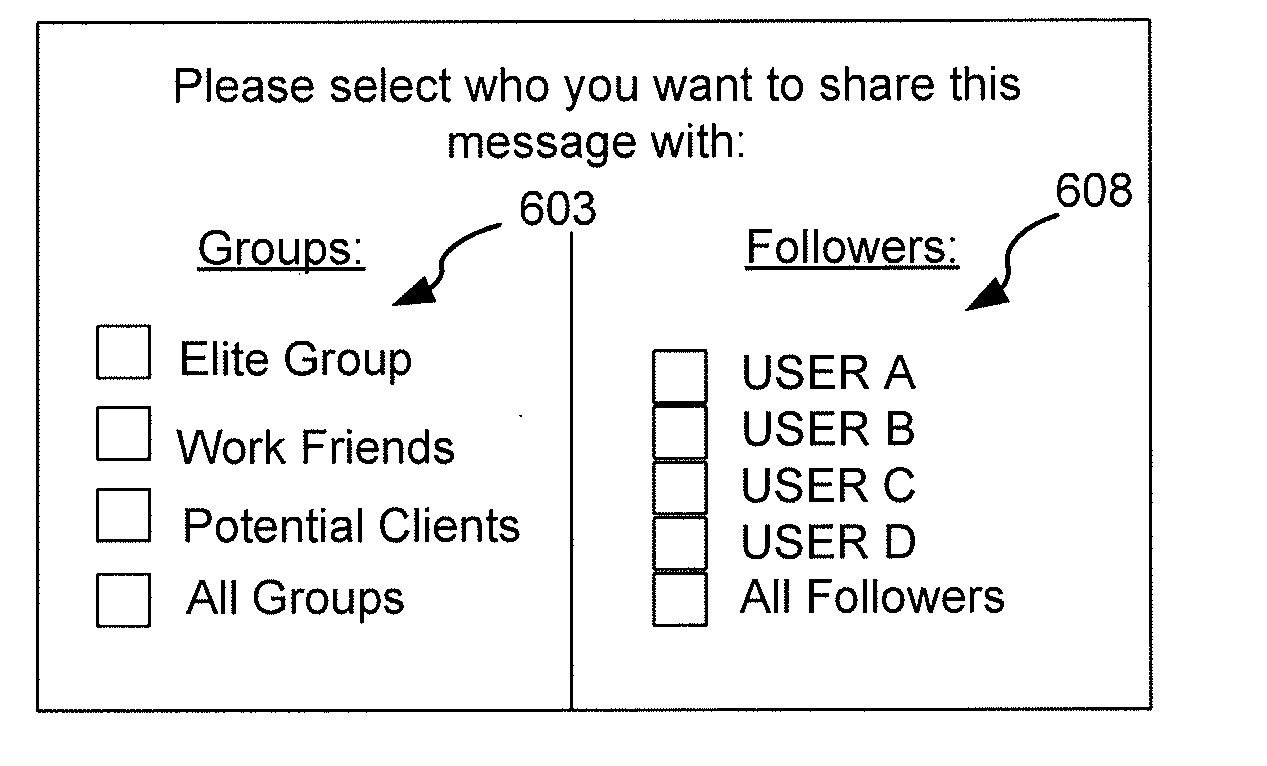
Methods and systems for providing a secure online feed in a multi-tenant database environment
InactiveUS20110307695A1Digital data information retrievalUser identity/authority verificationInternet privacyPassword
Embodiments of the present invention provide systems, apparatus, and methods for securing information shared between users of a database system. A message in a feed on a multi-tenant database can be securely shared when a user marks the message as private. Users of the database can selectively decide on which recipient and / or group of recipients have access rights to view the message. The messages are secured through cryptography, such as by a key shared between two or more users. The user can additionally have a private key that is used to decrypt the secure (e.g., encrypted) messages. This private key can be further protected by the user's password used to log into the database system. The secure message can appear in either encrypted form or be absent from the feed to which the secure message is posted. Secure messages can be transparently encrypted and decrypted by the system. In some embodiments, sharing rules can be pre-defined by the user to determine how messages are secured. Furthermore, the secured messages are stored in encrypted fomi on the multi-tenant database and only accessible by users with whom the messages are shared.
Owner:SALESFORCE COM INC
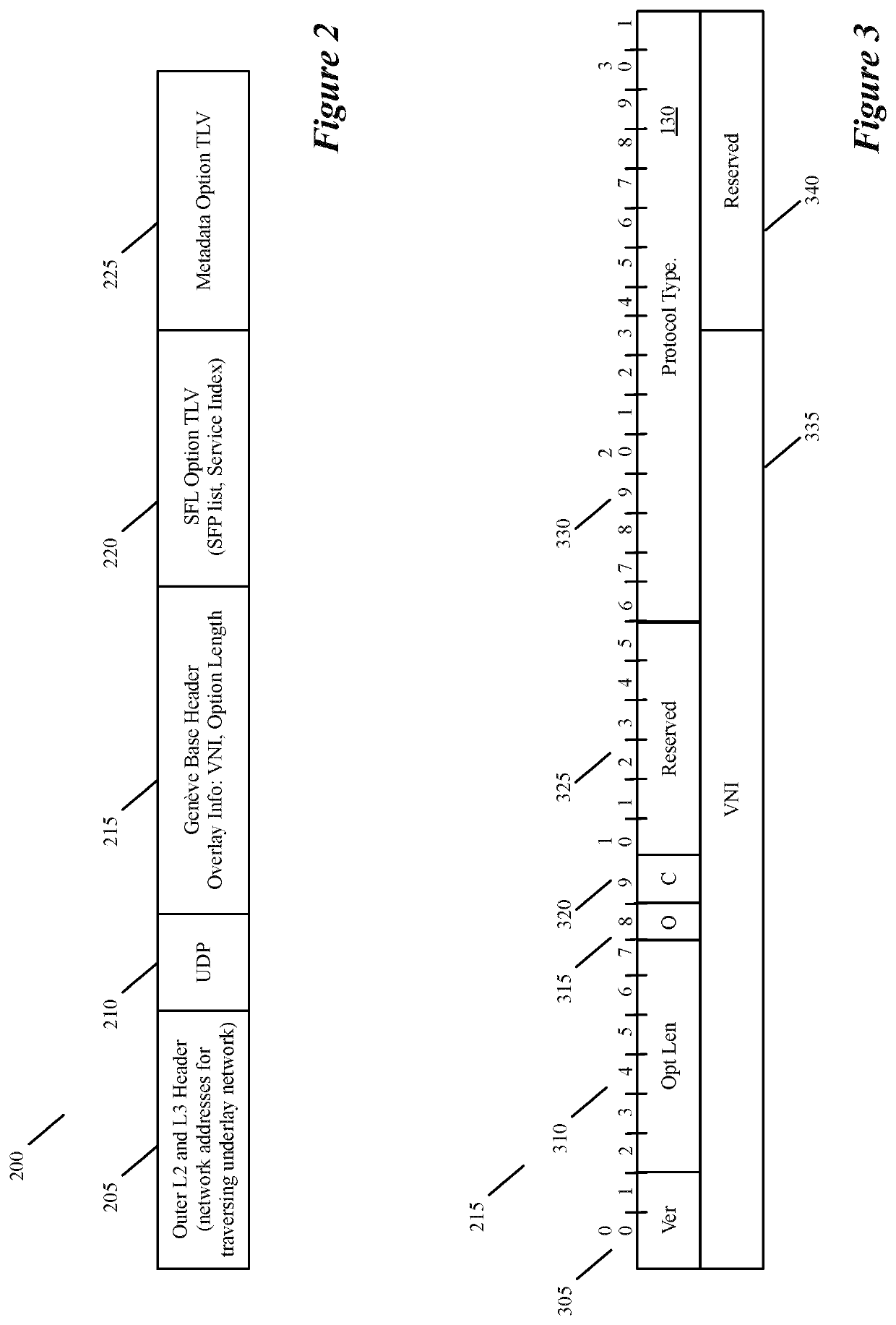
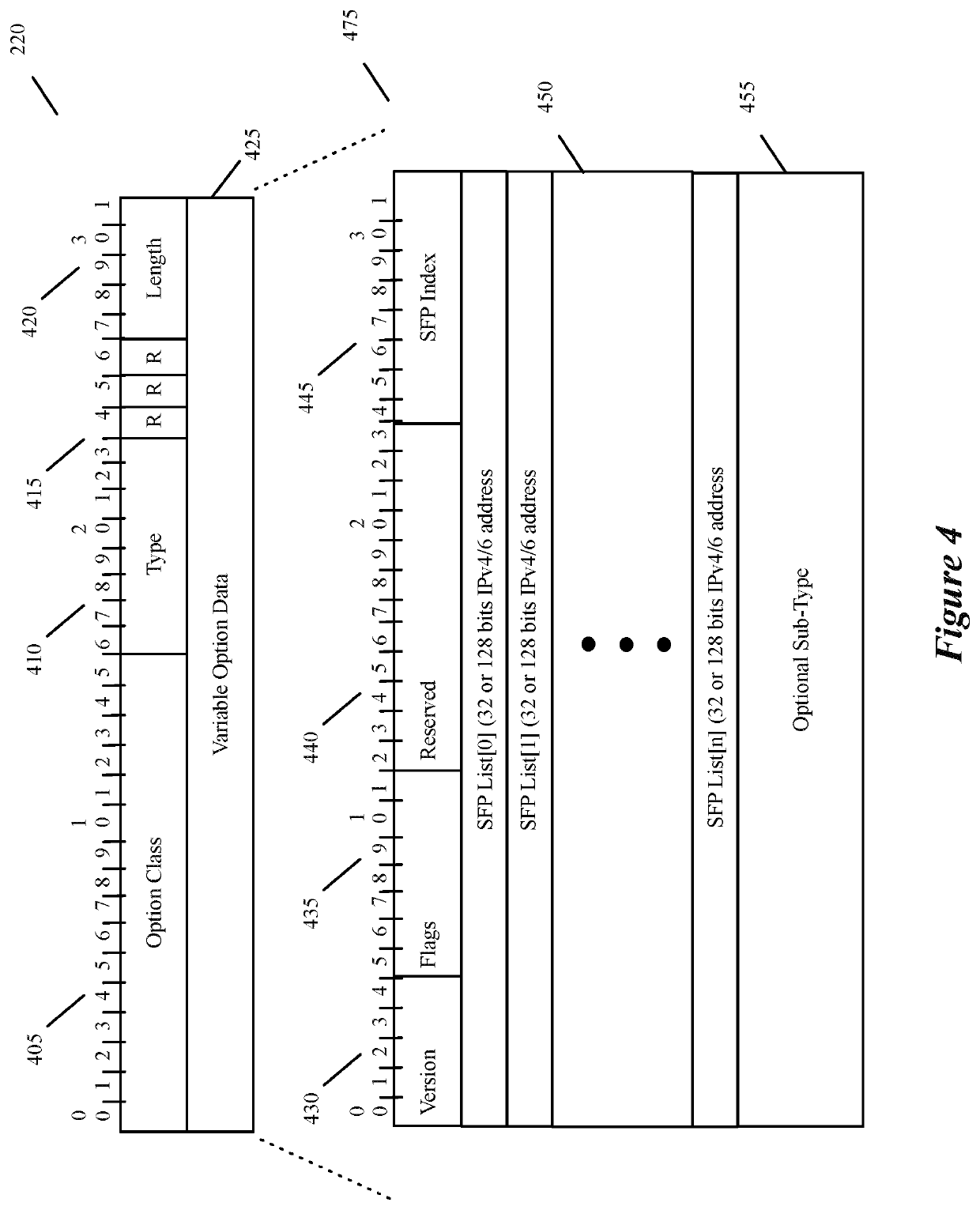
Systems and methods to support vxlan in partition environment where a single system acts as multiple logical systems to support multitenancy
The present disclosure is directed towards systems and methods for supporting virtual extensible local area network (VXLAN) in a network environment in which a single system is partitioned to establish multiple logical systems to support multi-tenancy.
Owner:CITRIX SYST INC
Method and system for a multitenancy telephone network
A method and system for operating a multitenancy telephony system including a call queue that stores call requests received from a plurality of users; an expandable and contractible telephony resource cluster that establishes call sessions for call requests; a analysis system that calculates capacity requirements of the system; a resource allocator that manages the scaling and operation of the telephony resource cluster; and a plurality of telephony network channels that are used as telephony communication channels for call sessions.
Owner:TWILO INC
Service operation chaining
ActiveUS10805181B2Networks interconnectionSoftware simulation/interpretation/emulationMessage flowIp address
Owner:NICIRA INC
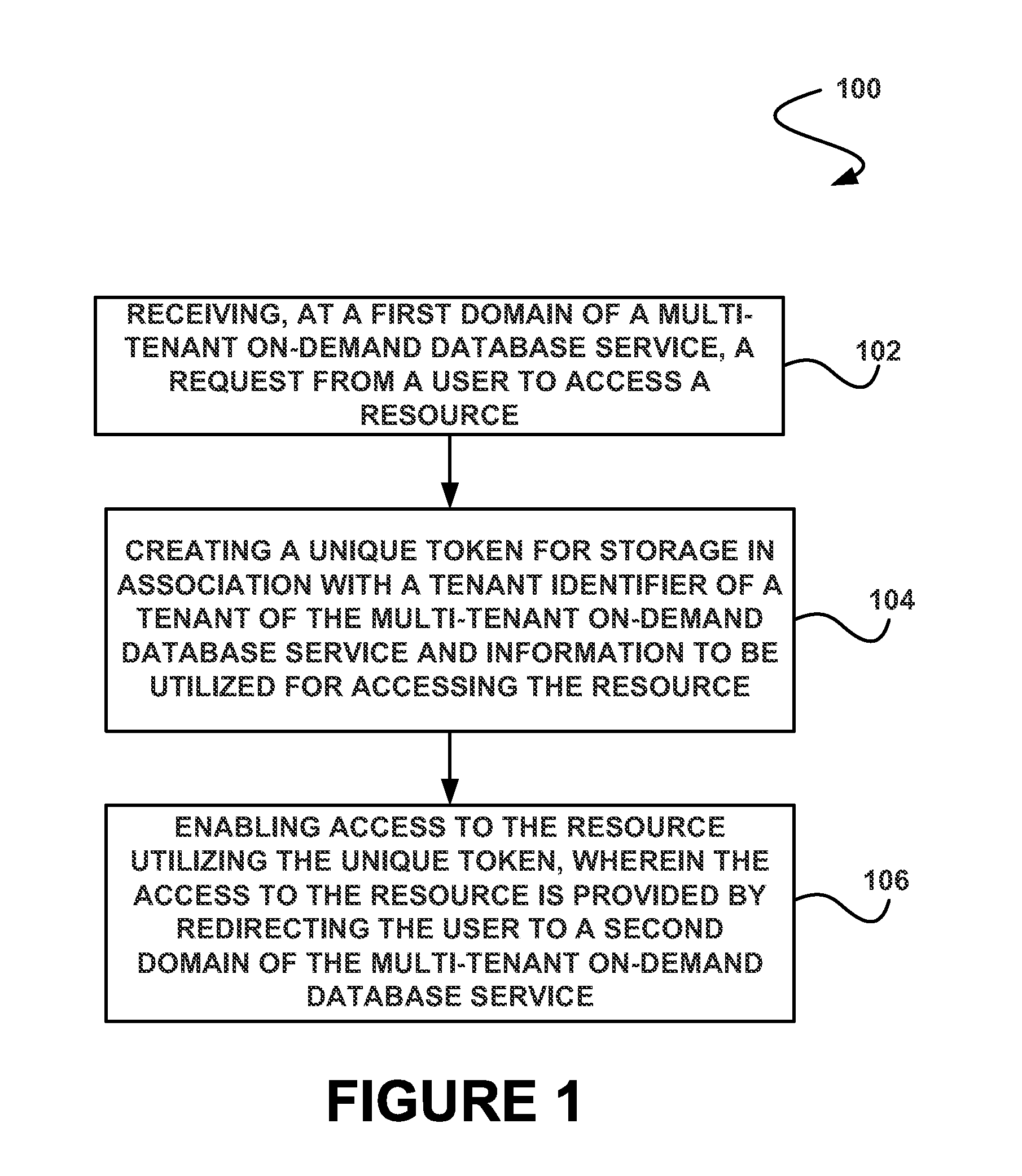
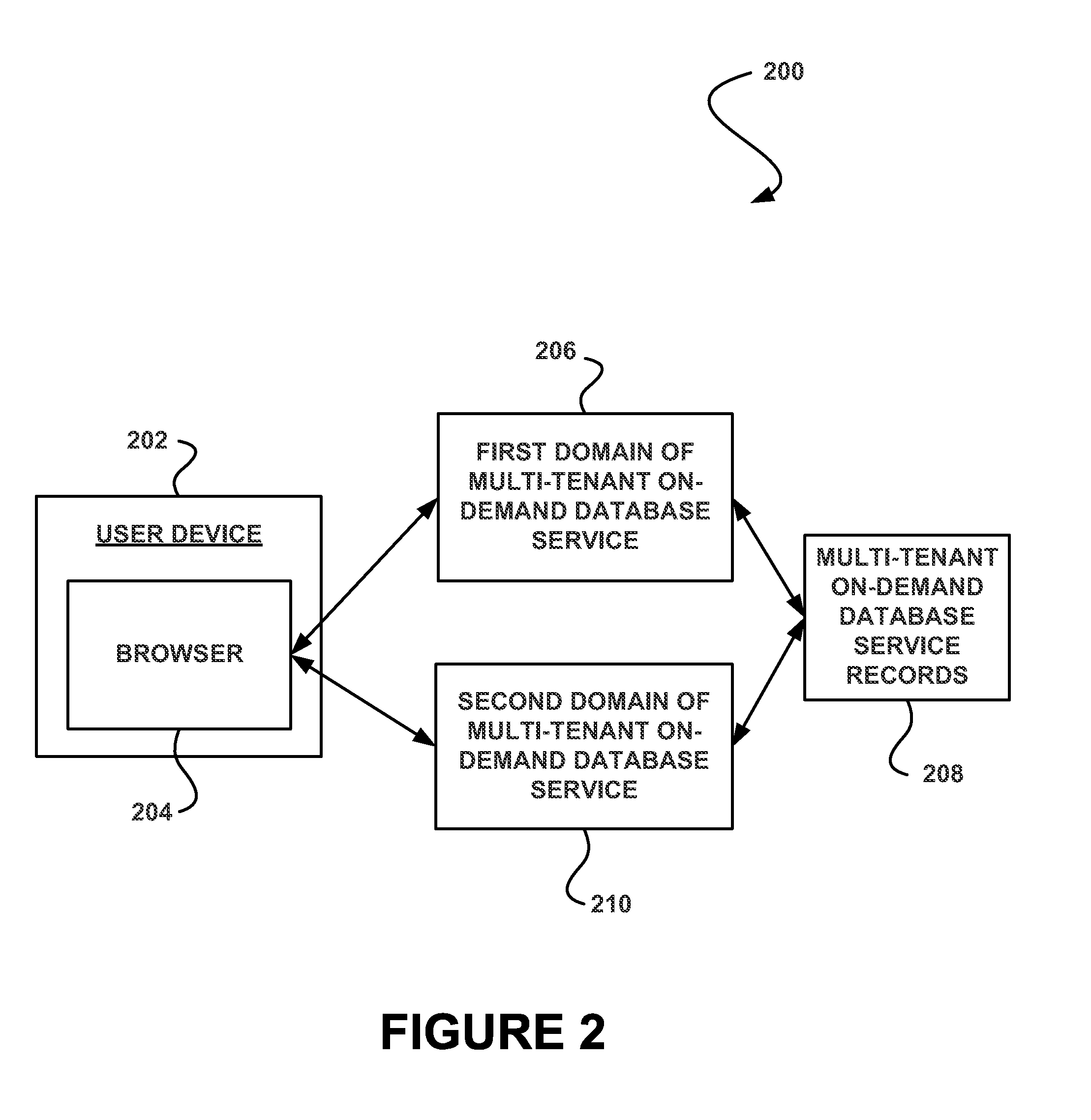
System, method and computer program product for enabling access to a resource of a multi-tenant on-demand database service utilizing a token
ActiveUS20130198236A1Avoid identificationUnwanted useWeb data indexingDigital data processing detailsDatabase servicesOn demand
In accordance with embodiments, there are provided mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token. These mechanisms and methods for enabling access to a resource of a multi-tenant on-demand database service utilizing a token can be utilized to prevent identification of a user attempting to access the resource, and thus unwanted use of the user's identity.
Owner:SALESFORCE COM INC
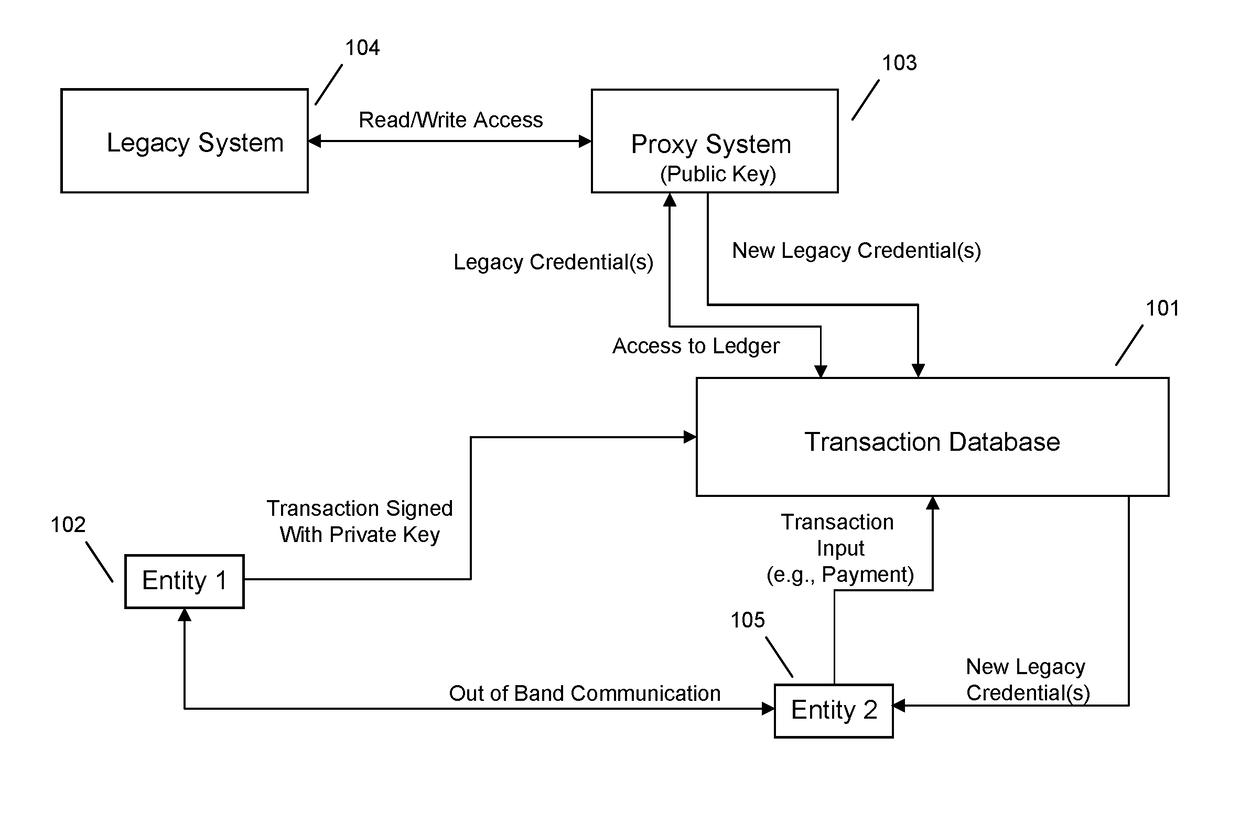
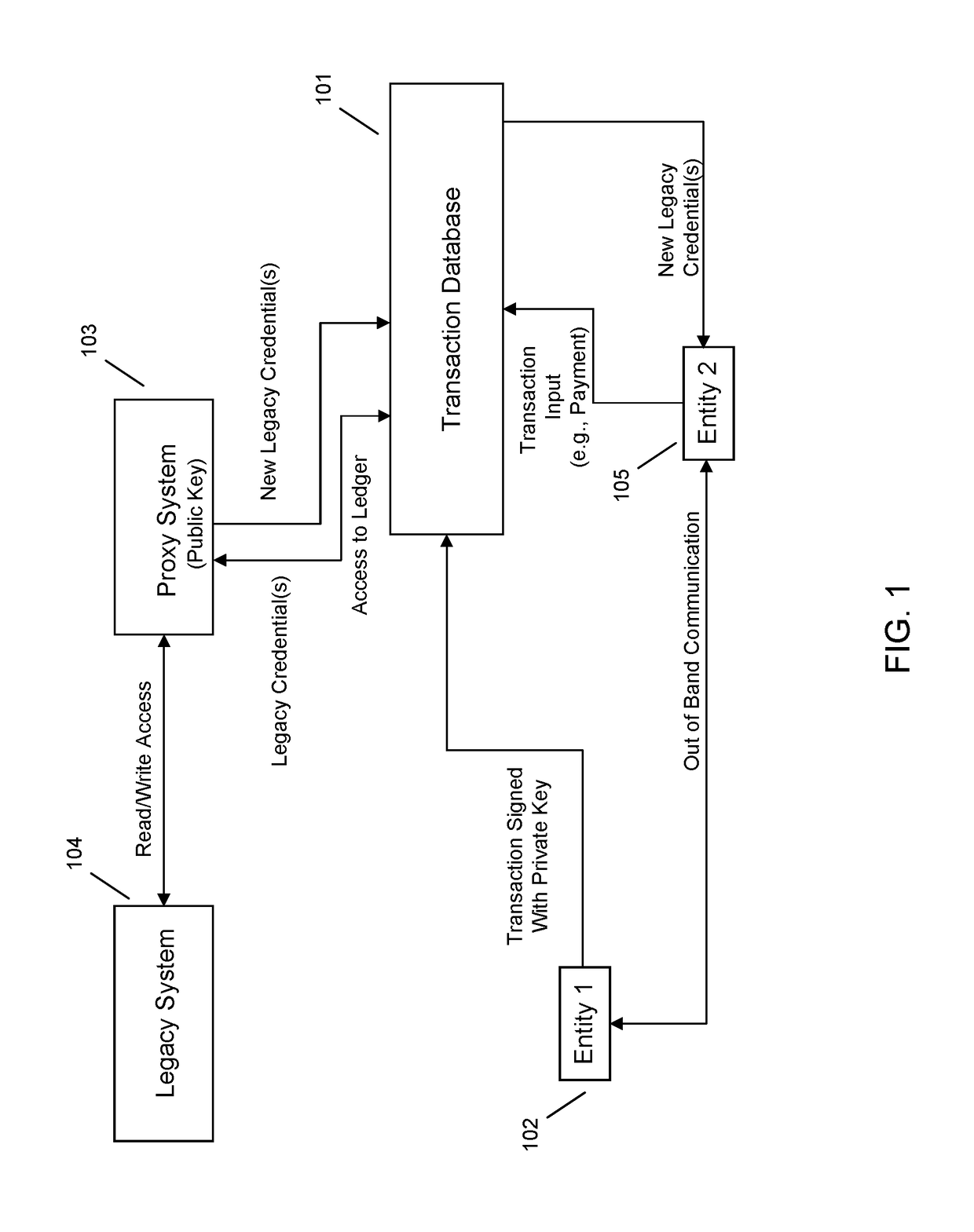
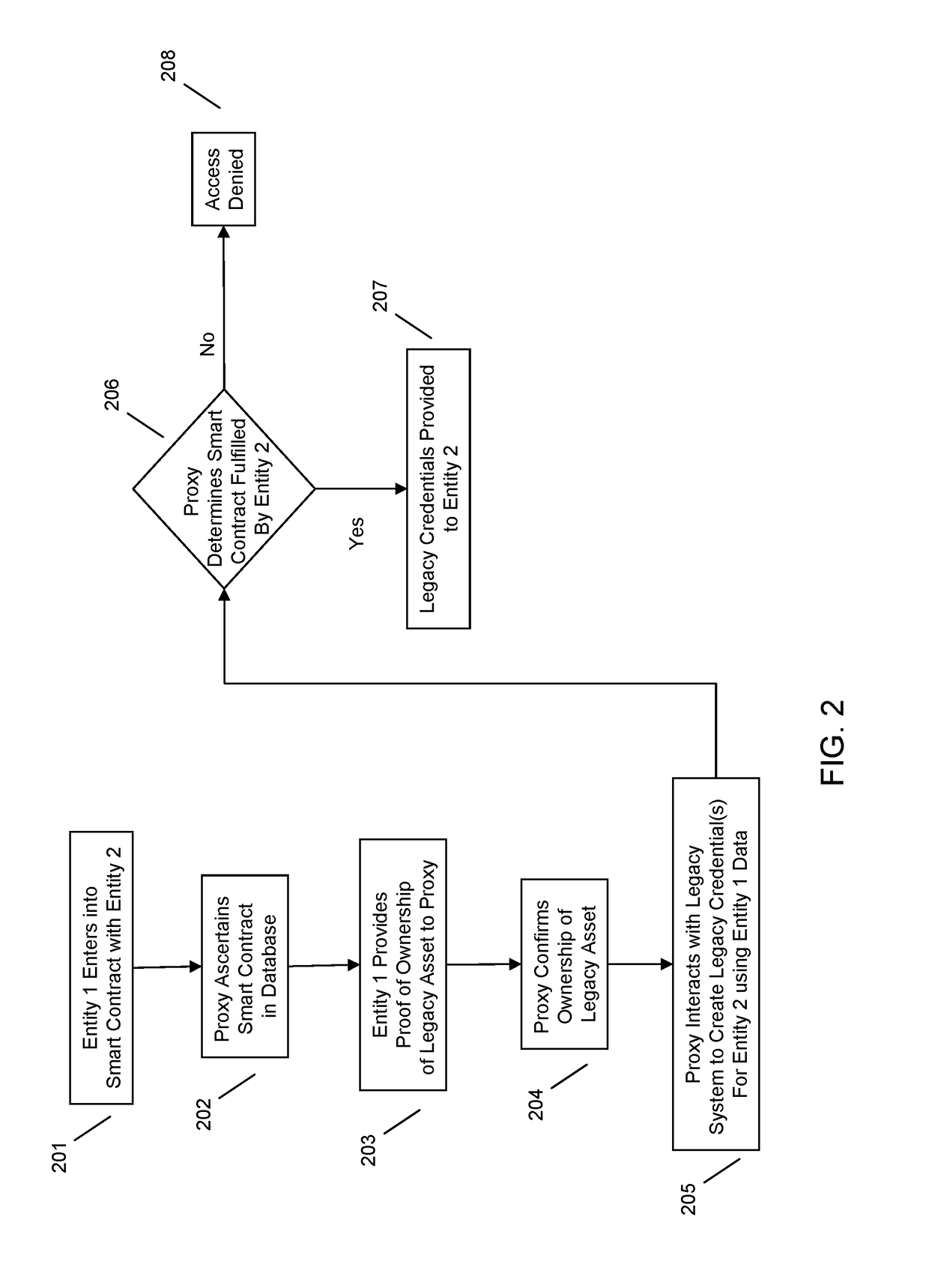
Proxy system mediated legacy transactions using multi-tenant transaction database
One embodiment provides a method for proxy system mediated legacy transactions using multi-tenant transaction database, including: utilizing at least one processor to execute computer code that performs the steps of: ascertaining, using a processor associated with a proxy system, that a first transacting entity and a second transacting entity have placed a transaction on a multi-tenant transaction database, the transaction including transfer of a legacy asset; decrypting, using a processor associated with the proxy system, a legacy system account access credential of the second transacting entity included in the transaction, the decrypting comprising recovery of a function of a public key corresponding to a private key associated with the second transacting entity; confirming, using a processor associated with the proxy system, that the legacy system account credential authorizes the second transacting entity to transfer the legacy asset; and transferring, using a processor associated with the proxy system, the legacy asset from the second transacting entity to the first transacting entity. Other aspects are described and claimed.
Owner:IBM CORP
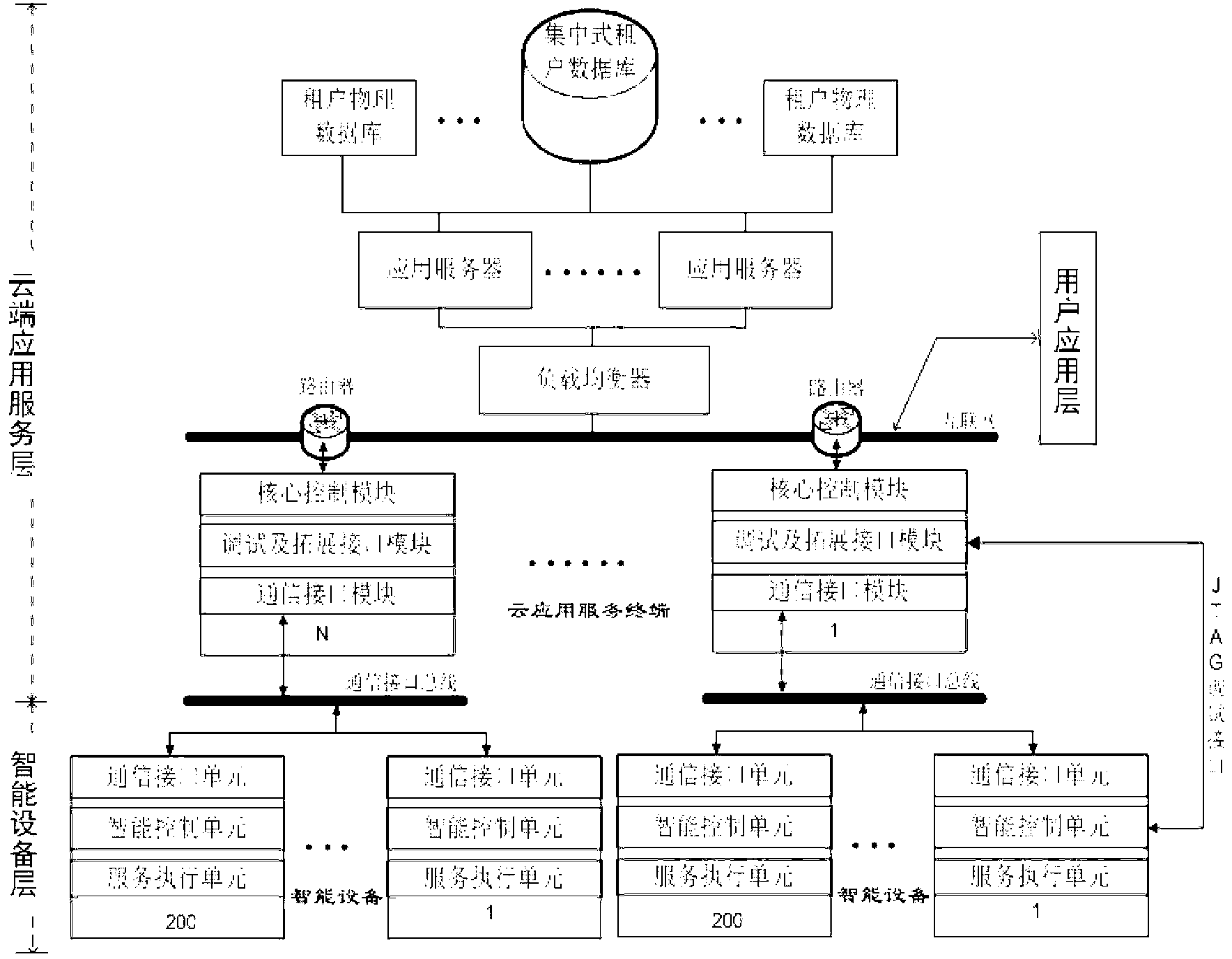
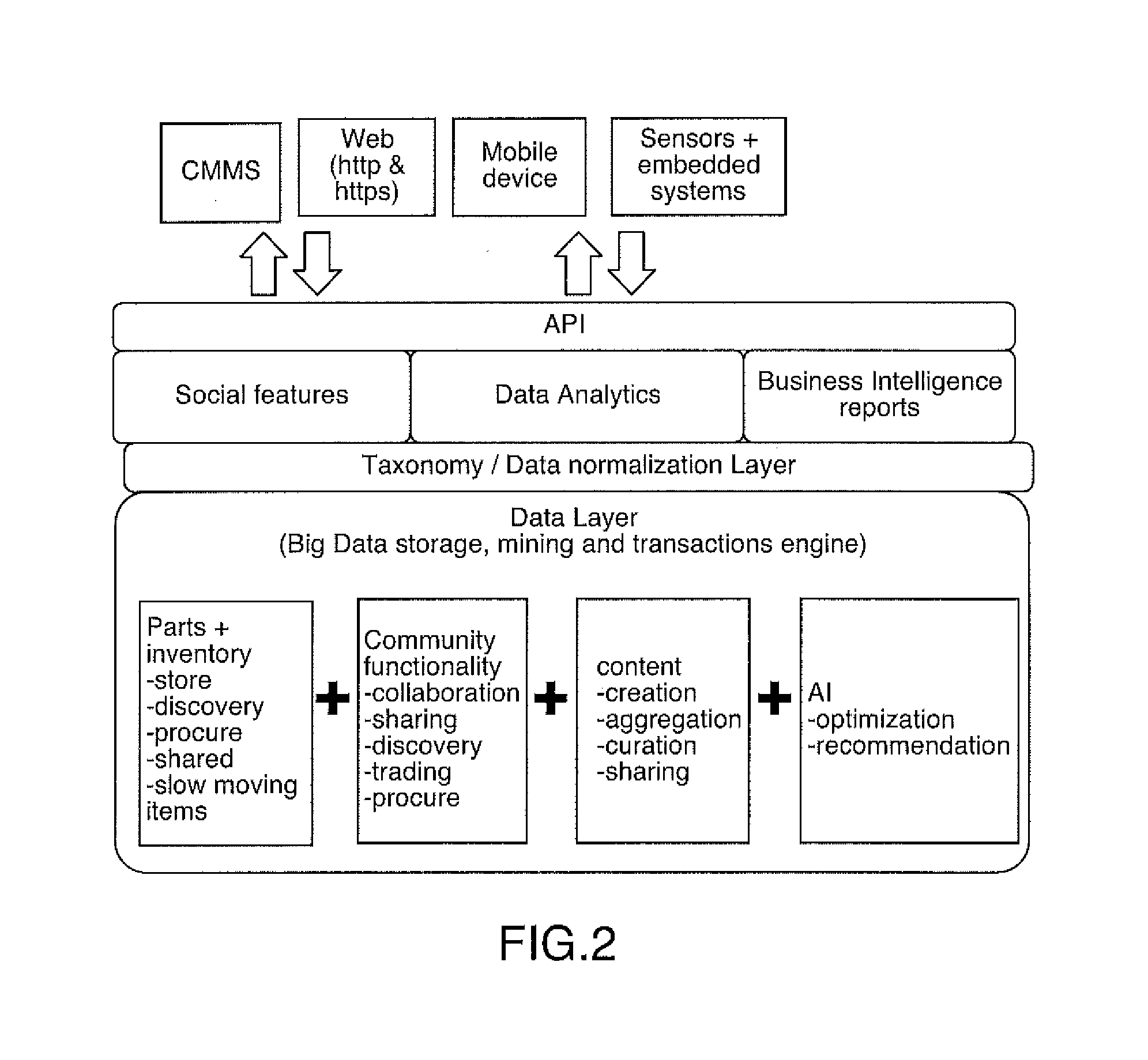
Intelligent device monitoring and managing system based on software as a service (SaaS)
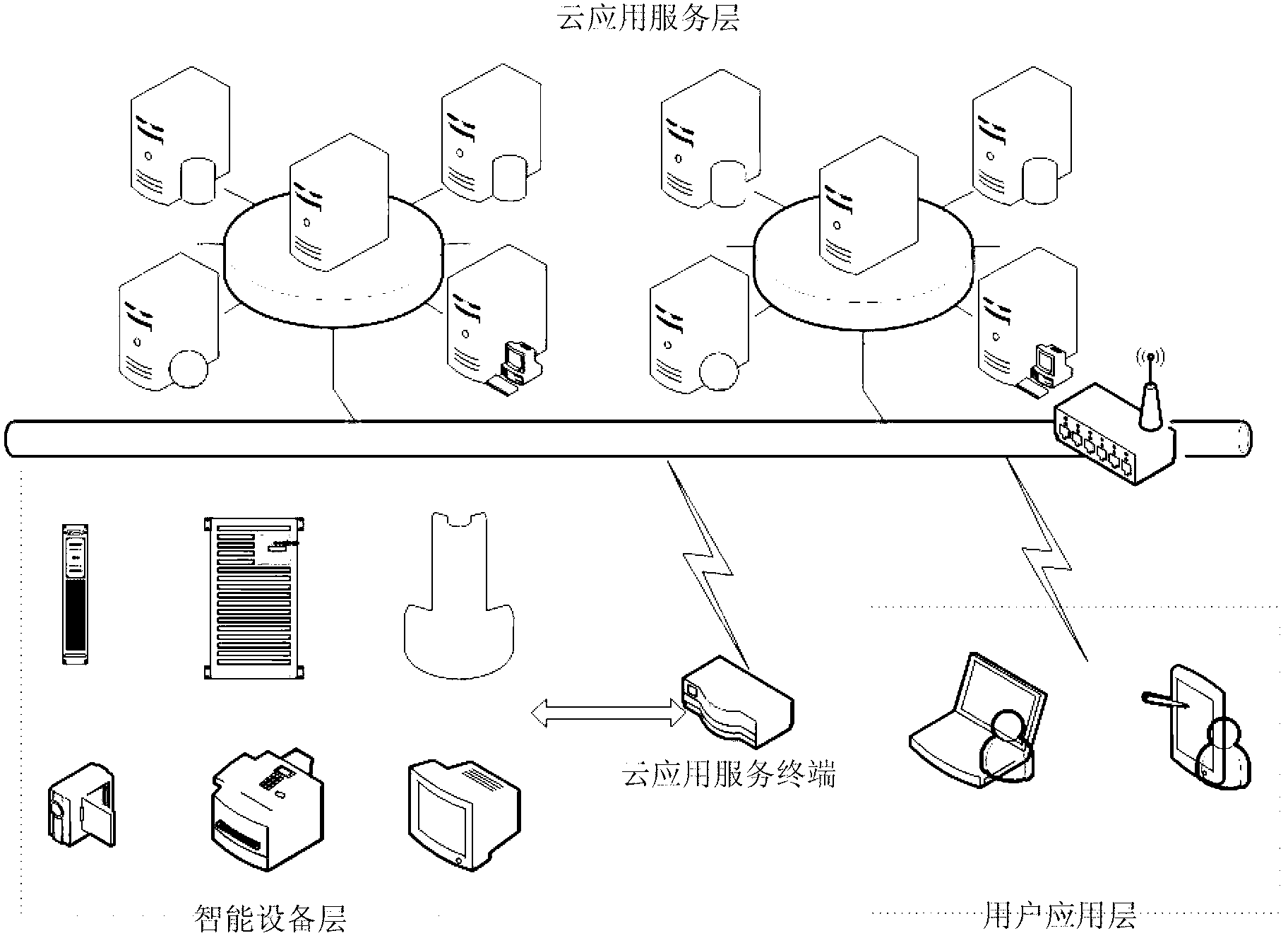
ActiveCN102981440ASolve the problems caused by scaleTake advantage ofProgramme controlComputer controlNetwork serviceInformation integration
The invention relates to an intelligent device monitoring and managing system based on software as a service (SaaS). The system comprises an intelligent device layer, a cloud application and service layer and a user application layer, wherein the intelligent device layer is assemble of monitoring and managing objects of the same category, the cloud application and service layer is a group of network server cluster, and the user application layer comprises any devices and users capable of accessing the internet and carrying a web browser. A user can use the web browser as a monitor terminal to request monitoring service, managing service or other services of intelligent devices to the cloud application and service layer. The cloud application and service layer adopts an Saas multi-tenant and distributed application procedural framework, processes data in a distributed cache according to a monitoring service strategy customized by the user, and logs the data in a data base at regular time. The cloud application and service layer drives a cloud application and service terminal and controls the intelligent devices to execute responding service motions. According to the intelligent device monitoring and managing system based on SaaS, application services such as remote control, management and information integration of the intelligent devices based on a SaaS platform are achieved, problems caused by large-scale monitoring objects are effectively solved, servers and information bearing capacity can be arranged dynamically according to the quantity of users, hardware resources of the servers can be utilized completely, and therefore operating cost is reduced.
Owner:WUHAN UNIV OF TECH
Sharing with performance isolation between tenants in a software-as-a service system
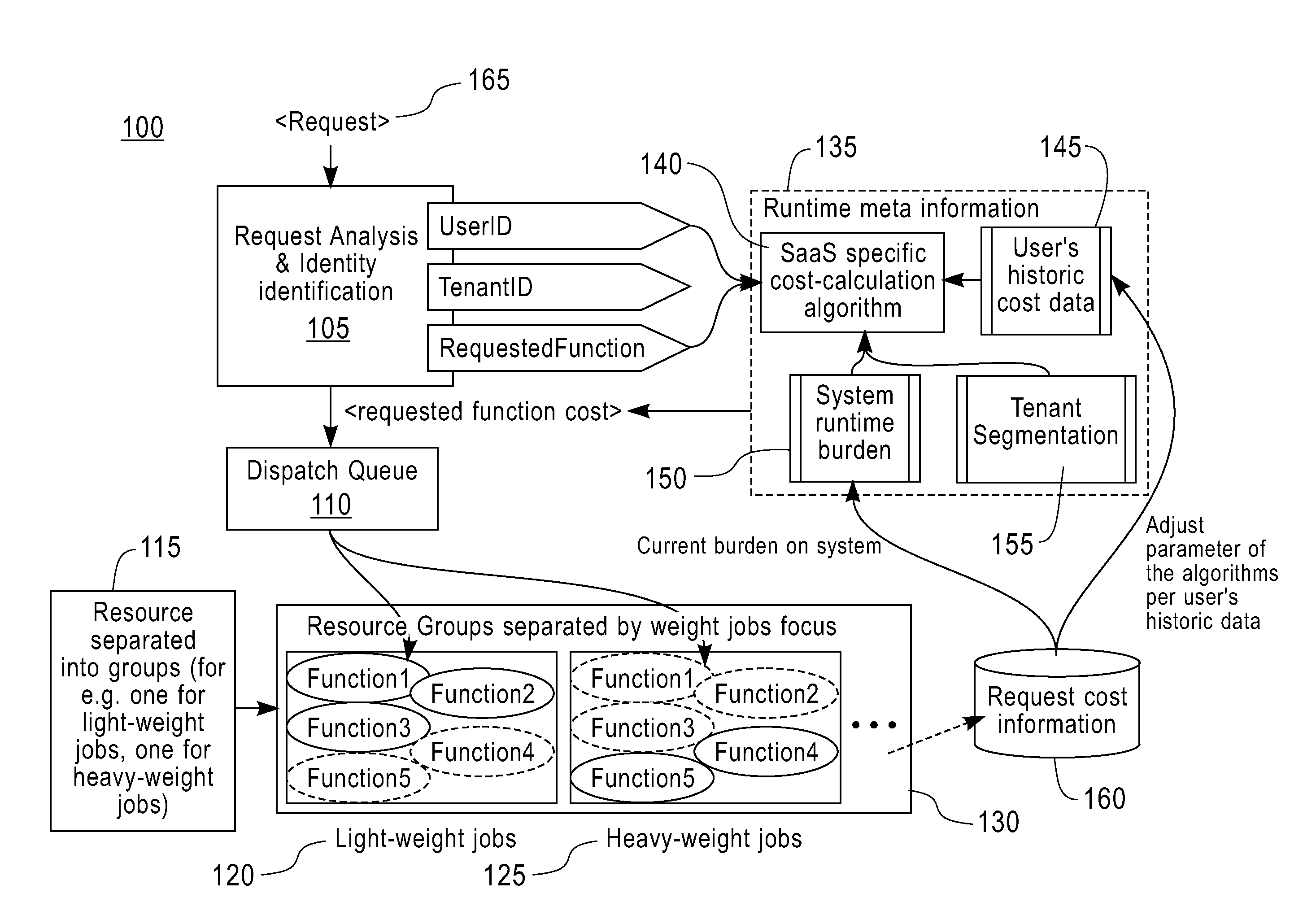
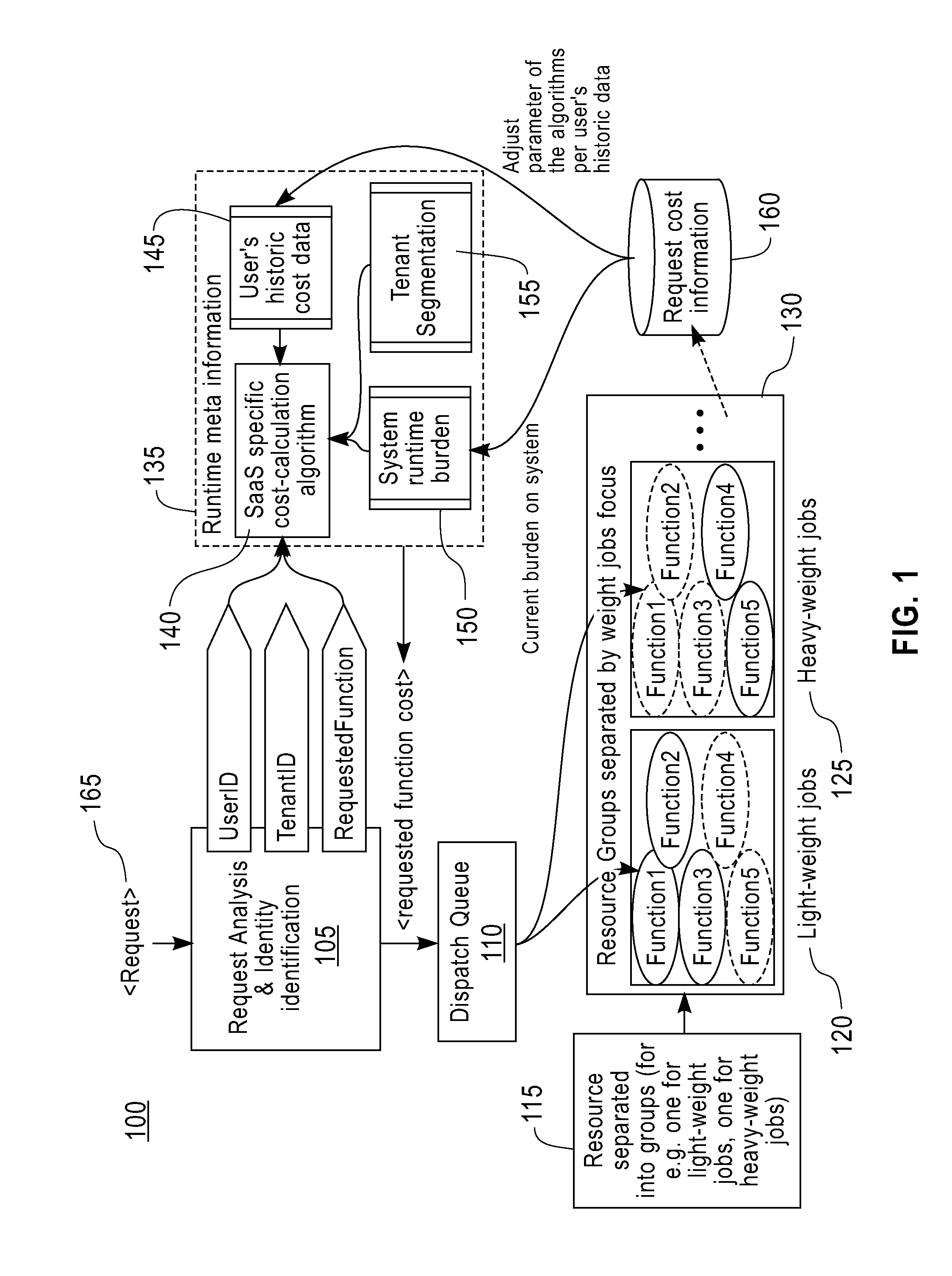
InactiveUS20120011518A1Maximizing capabilityMultiprogramming arrangementsMemory systemsSoftware as a serviceShared resource
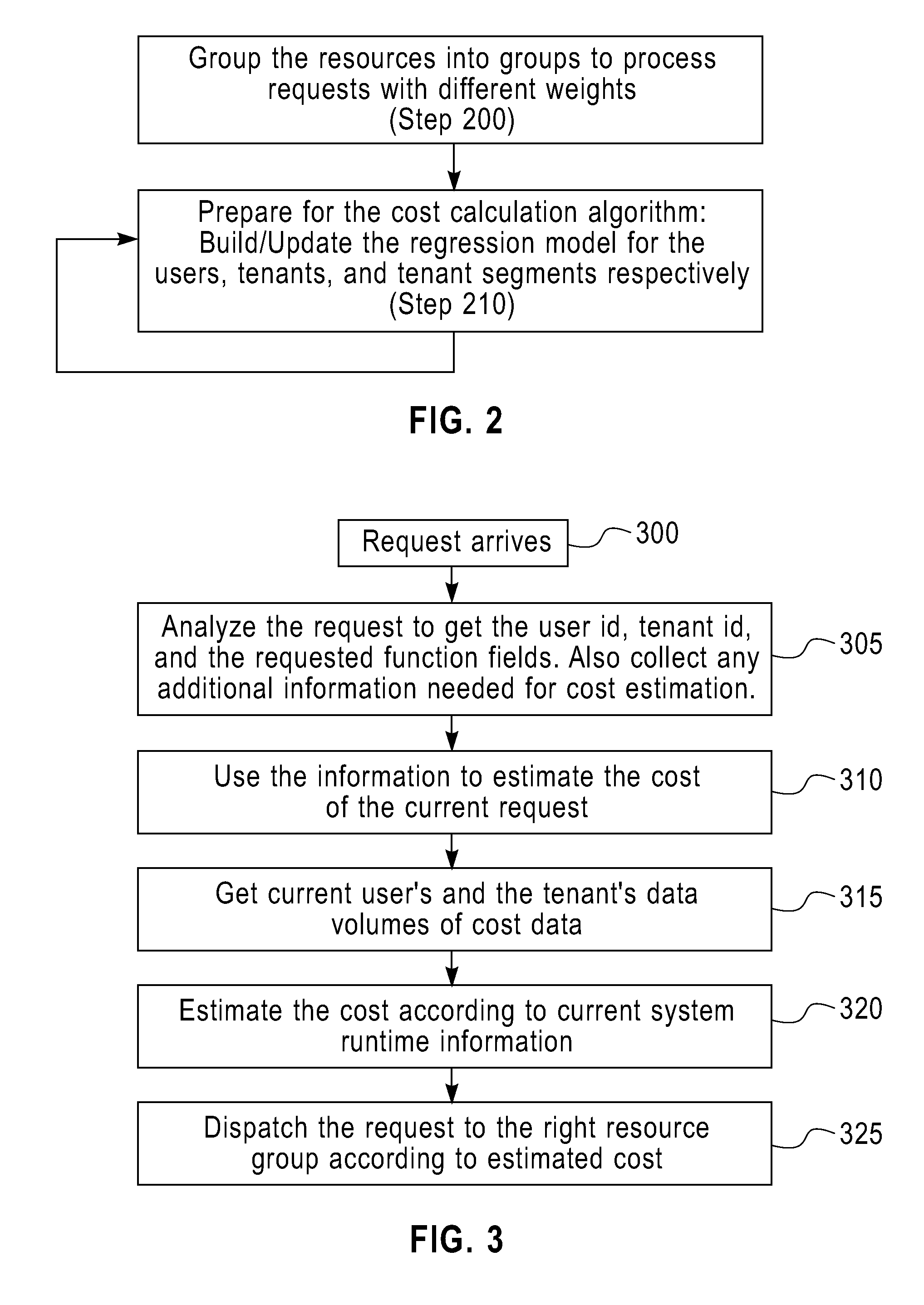
An apparatus hosting a multi-tenant software-as-a-service (SaaS) system maximizes resource sharing capability of the SaaS system. The apparatus receives service requests from multiple users belonging to different tenants of the multi-tenant SaaS system. The apparatus partitions the resources in the SaaS system into different resource groups. Each resource group handles a category of the service requests. The apparatus estimates costs of the service requests of the users. The apparatus dispatches service requests to resource groups according to the estimated costs, whereby the resources are shared, among the users, without impacting each other.
Owner:IBM CORP
Role based delegated administration model
ActiveUS20100306775A1Well formedSpecific access rightsMemory systemsDelegated administrationDatabase
Owner:MICROSOFT TECH LICENSING LLC
Computer system and method for maintenance management including collaboration across clients
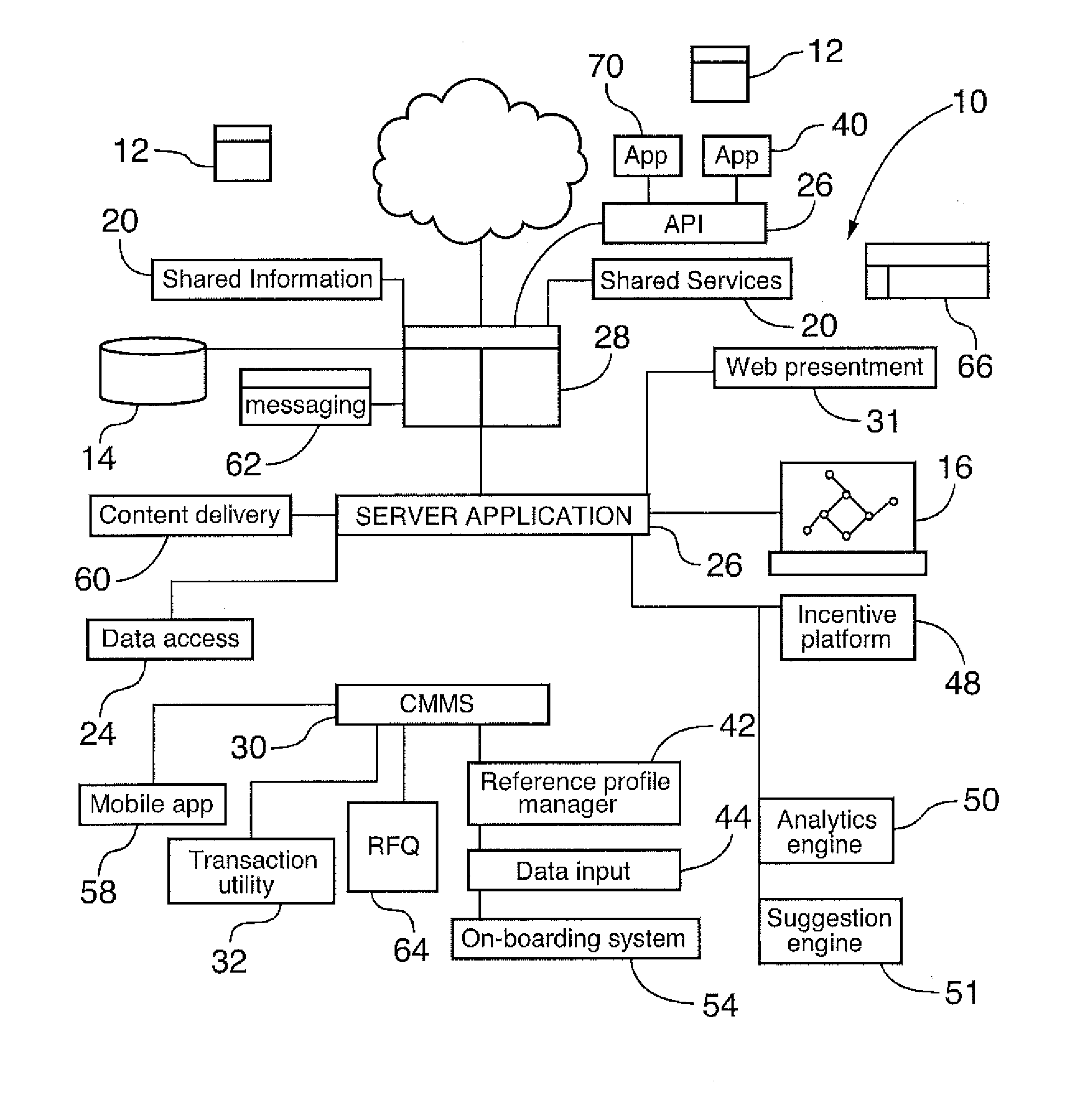
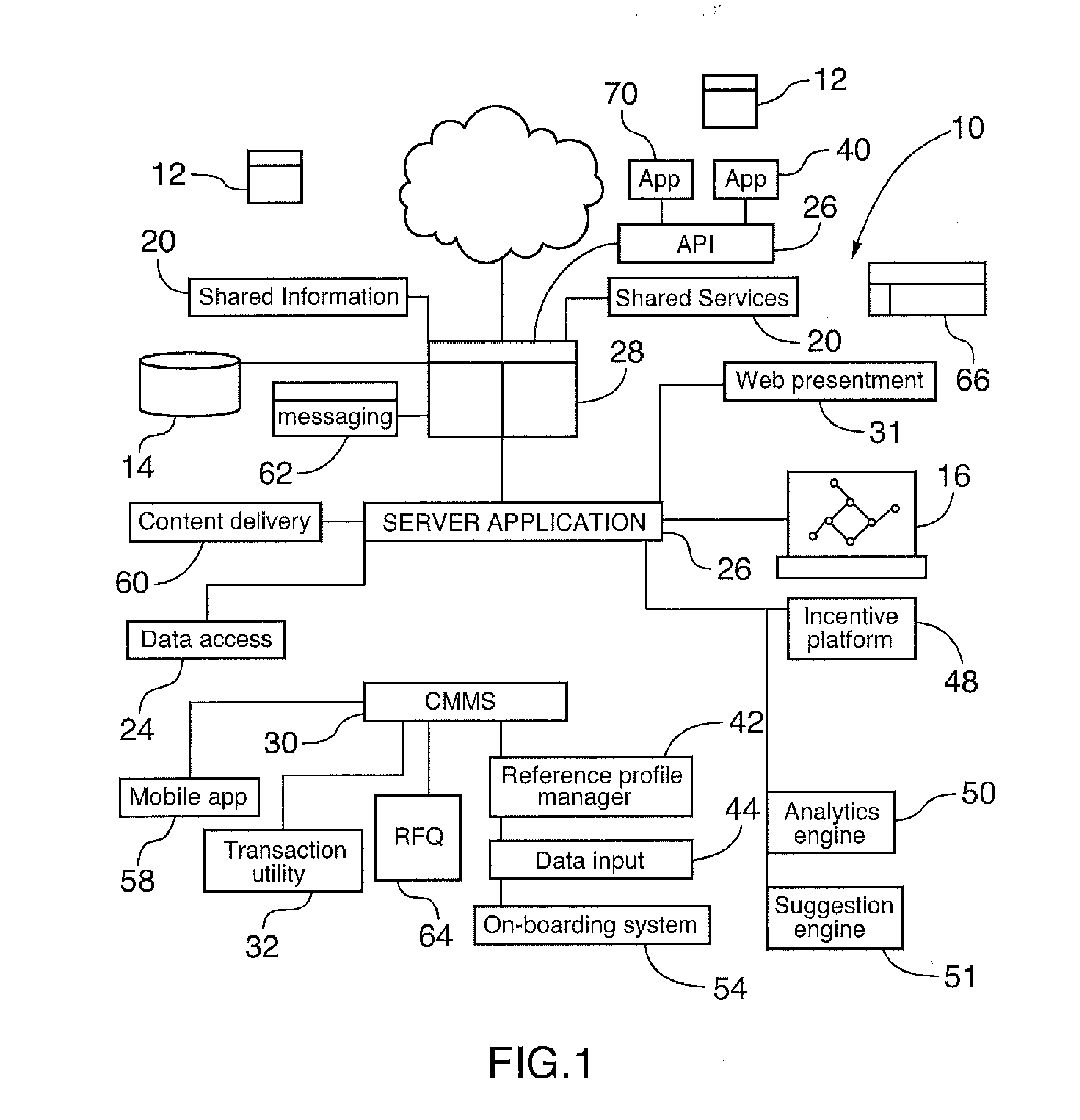
A computer system is provided that is connected to the Internet and enables a plurality of network connected devices to access a novel and innovative resource management platform. The computer system includes an Internet enabled computer platform that implements a multi-tenant architecture that enables multiple platform clients to populate the platform with various information regarding their resource management requirements. The computer system includes one or more tools that (i) track activities of users in connection with the management of resources, (ii) extracts insights from such activities, and / or (iii) enables users to upload information or documents related to resource management to the computer system, such tools enabling the automated suggestion of maintenance actions and / or product or service requirements of platform clients. A range of different intelligent features are provided. The computer system may include a CMMS with intelligent features. A number of related computer implemented methods for managing resources in an intelligent way, and based on collective information and knowledge is also provided.
Owner:ROCKWELL AUTOMATION CANADA LTD
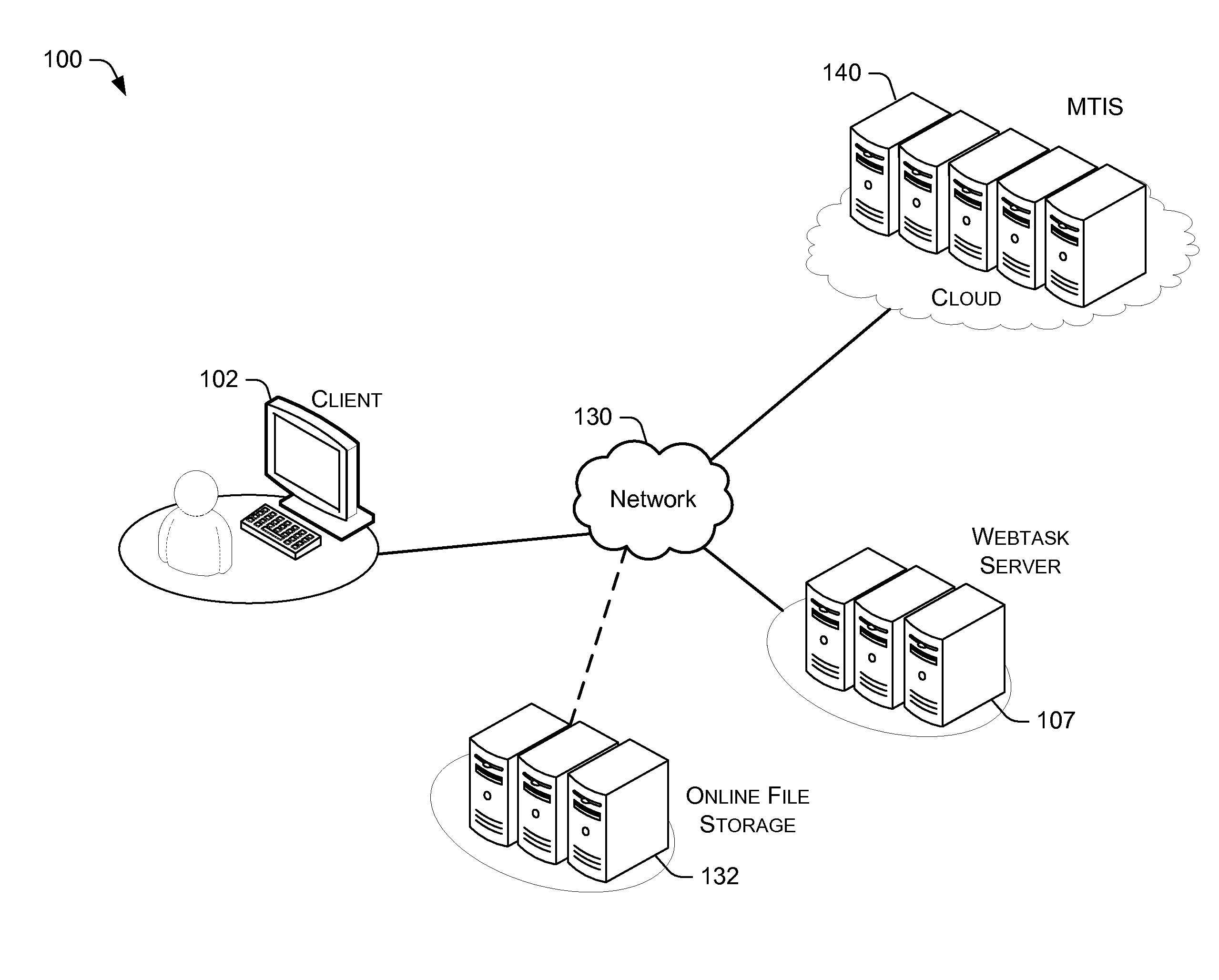
Multi-tenancy via code encapsulated in server requests
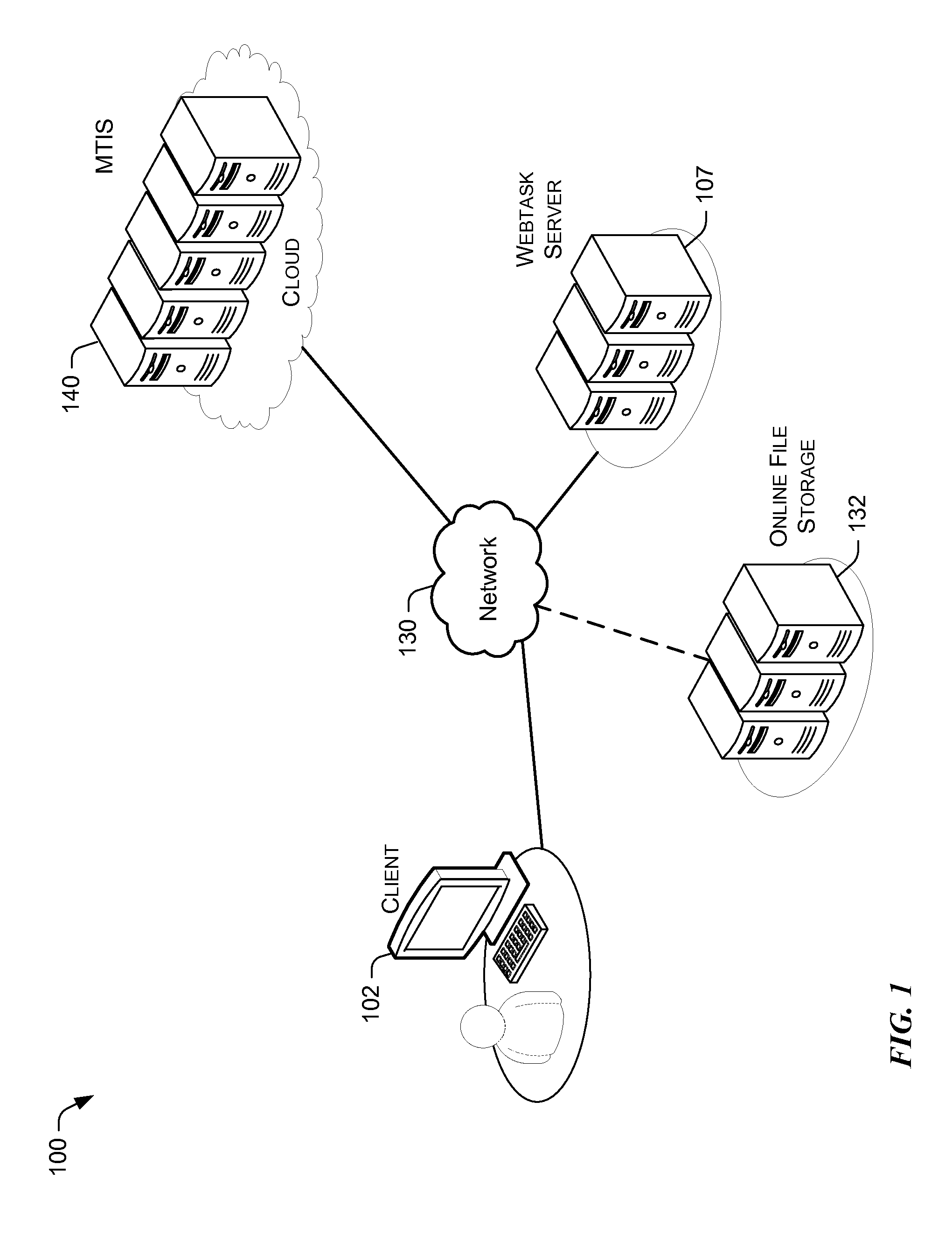
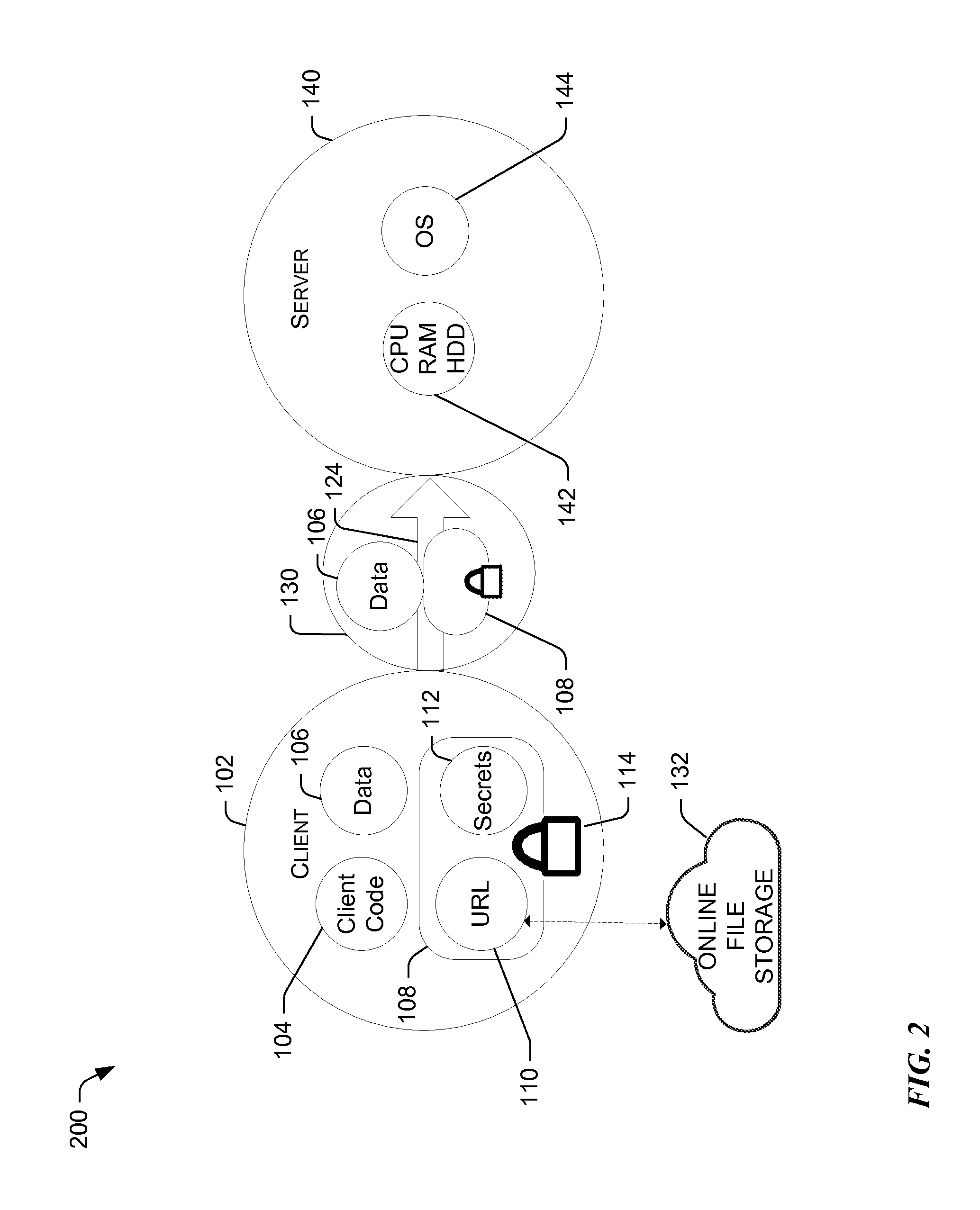
ActiveUS20160150053A1Software engineeringMultiple digital computer combinationsSoftware engineeringMultitenancy
A multitenant infrastructure server (MTIS) is configured to provide an environment to execute a computer routine of an arbitrary application. The MTIS receives a request from a webtask server to execute the computer routine in a webtask container. The computer routine is executed in the webtask container at the MTIS. Upon successful execution of the computer routine, a result set is returned to the webtask server. If the execution of the computer routine is unsuccessful, an error notification is returned to the webtask server. The resources consumed during the execution of the computer routine are determined. The webtask container is destroyed to prevent persistent storage of the computer routine on the MTIS.
Owner:AUTH0
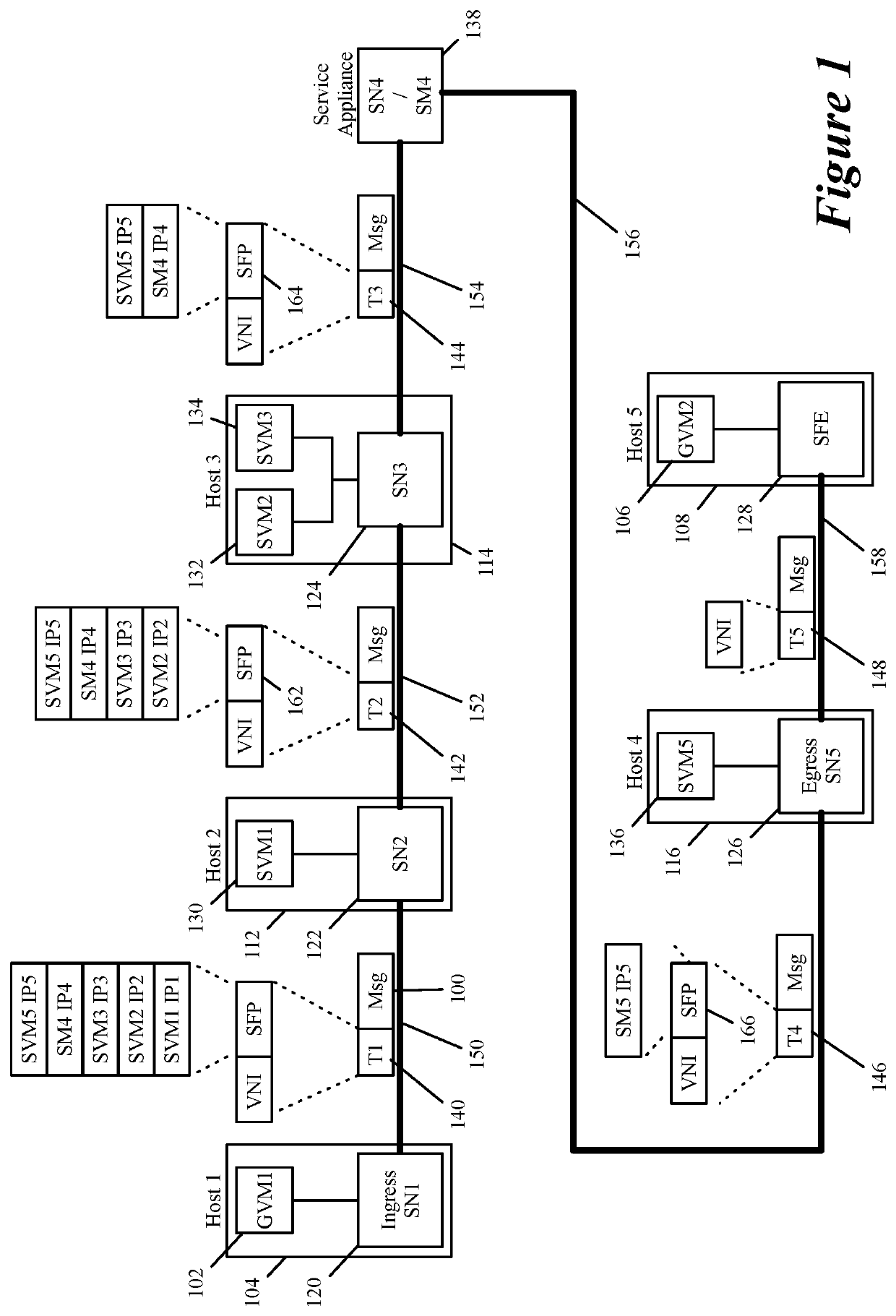
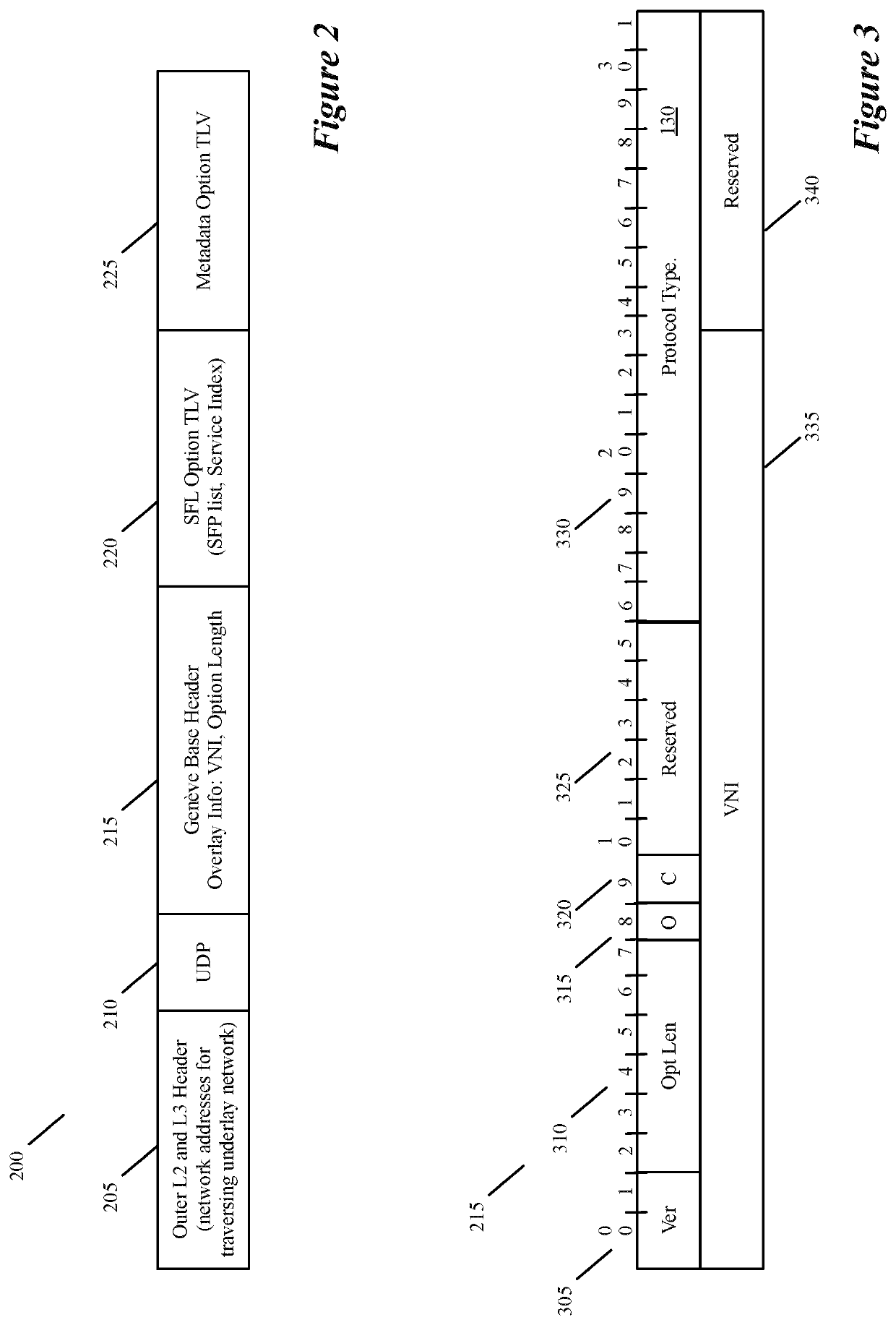
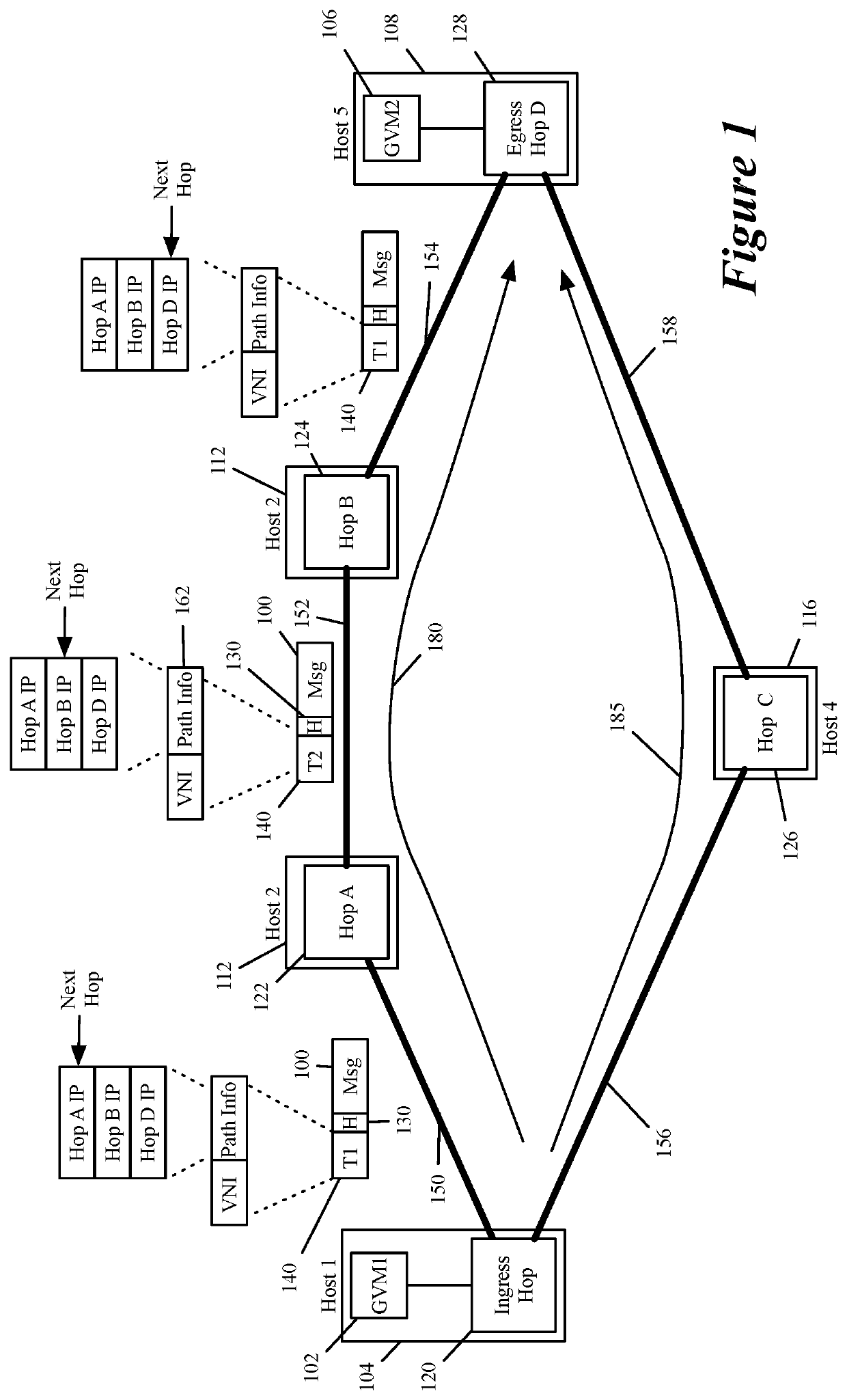
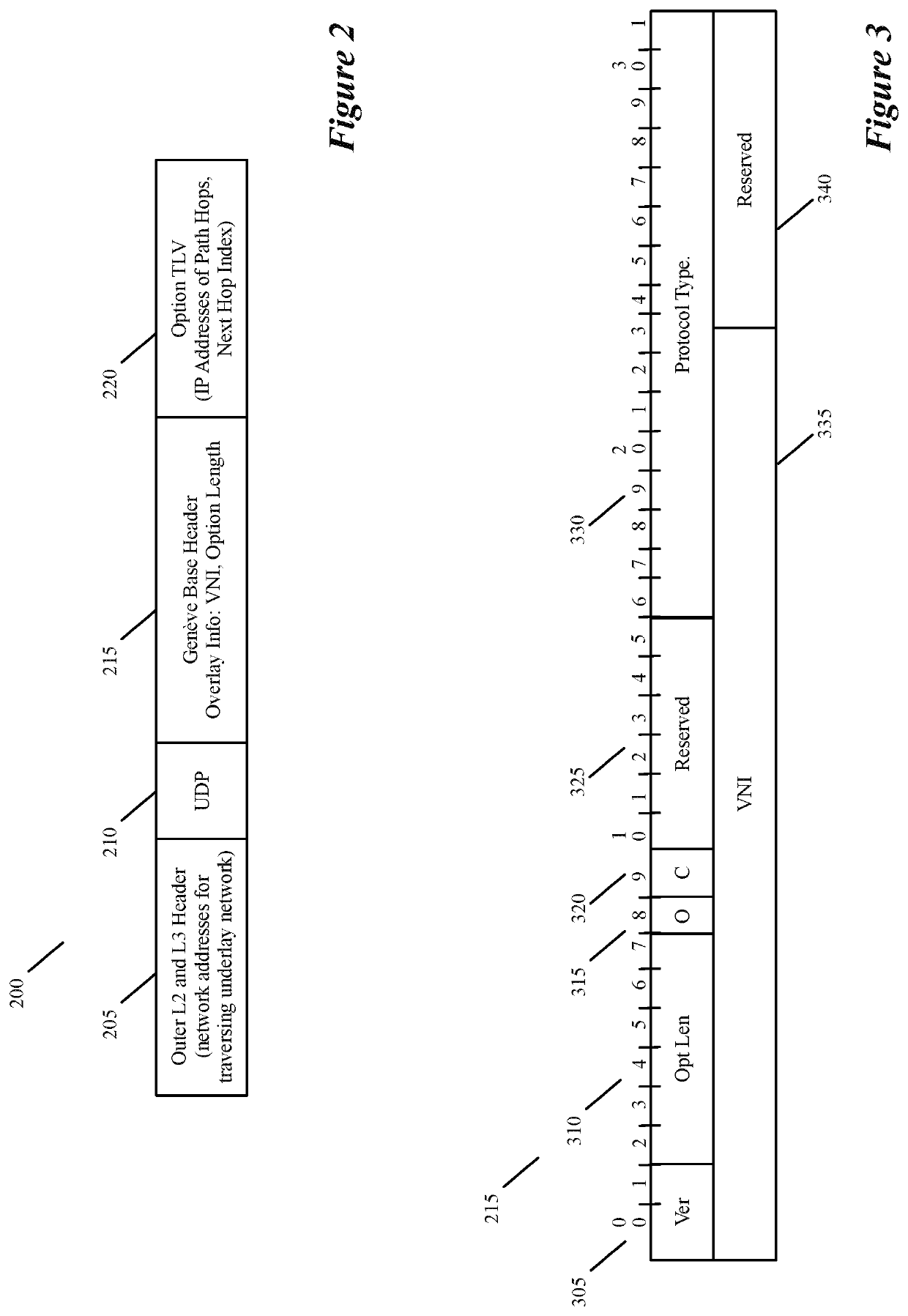
Specifying and utilizing paths through a network
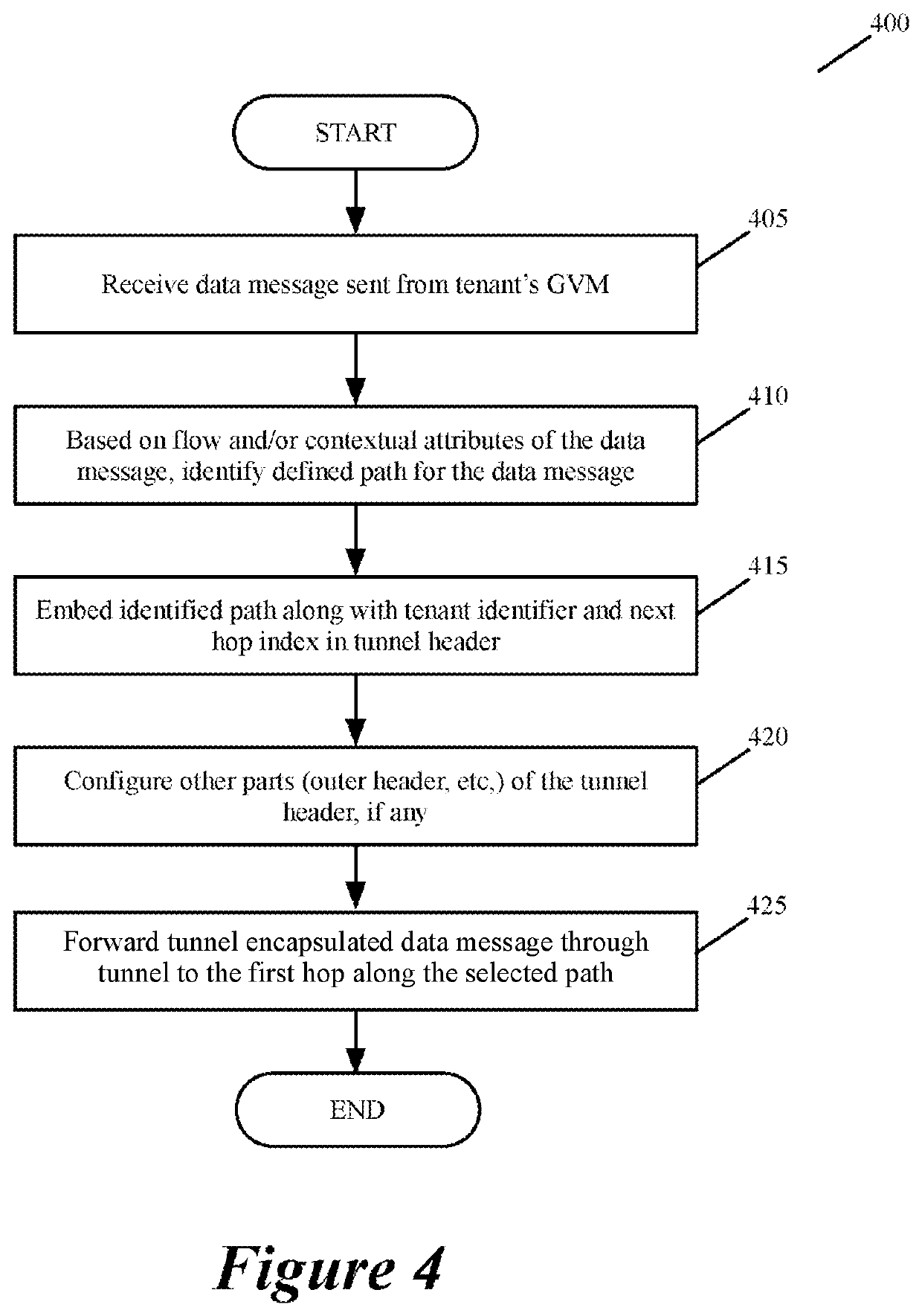
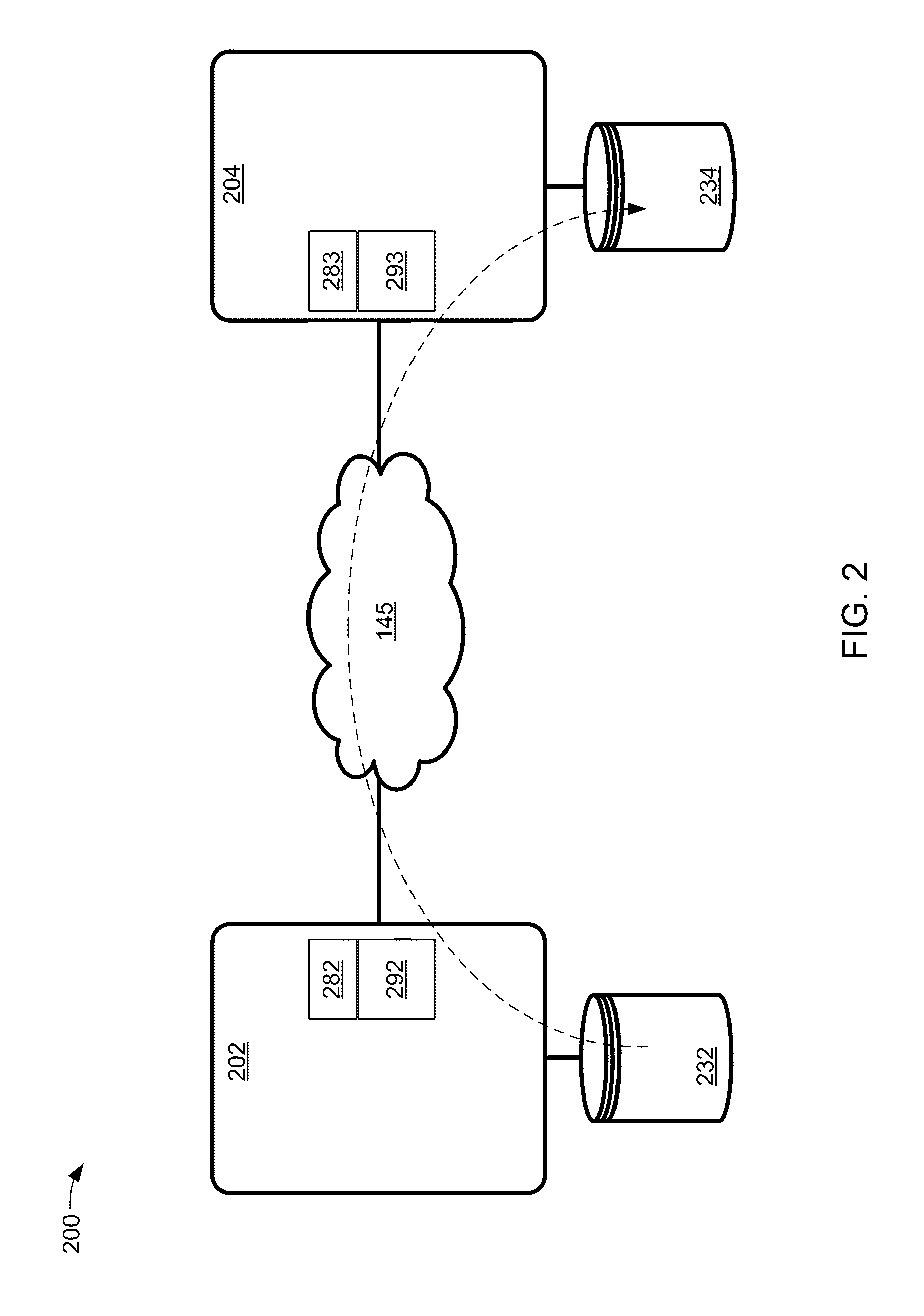
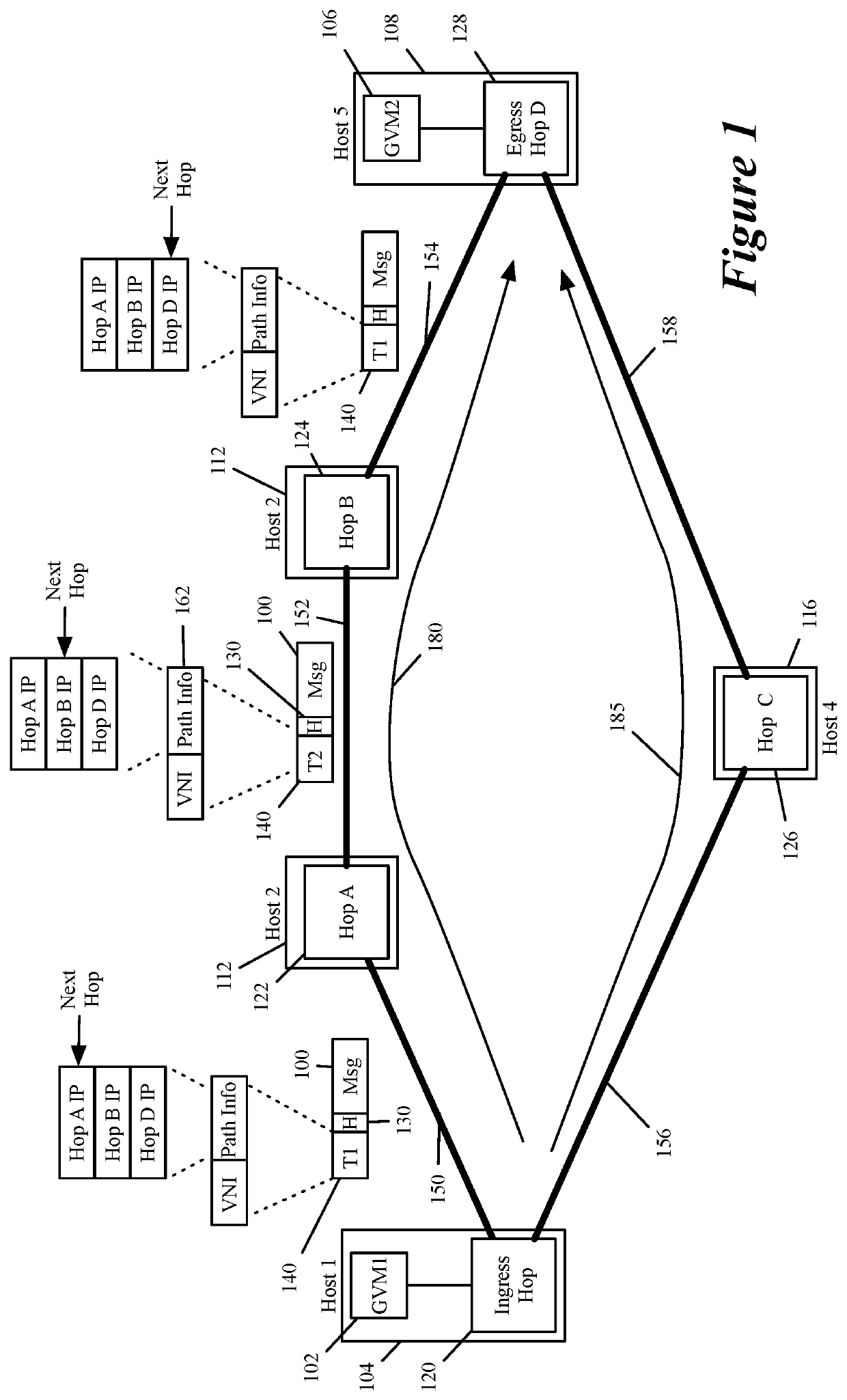
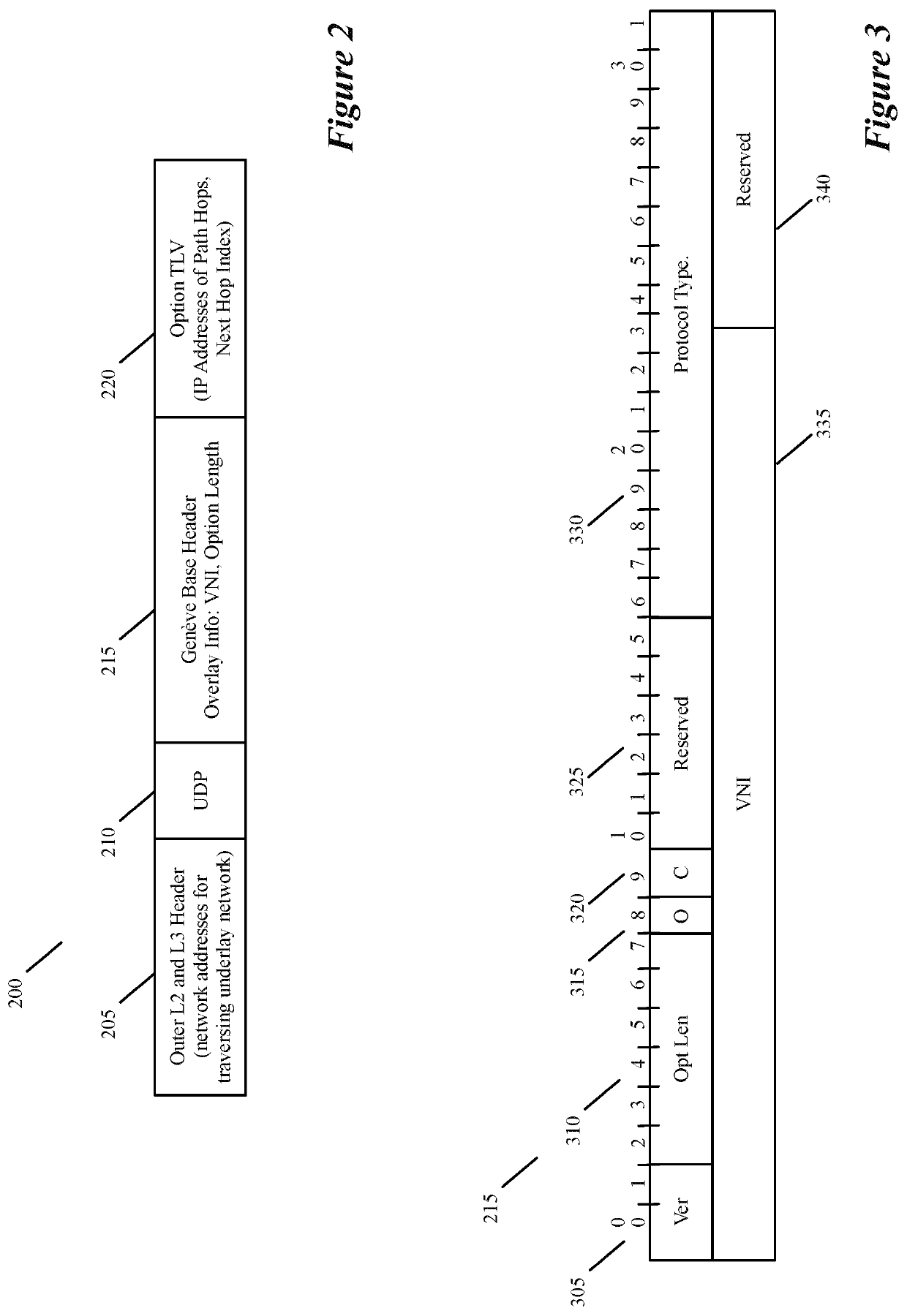
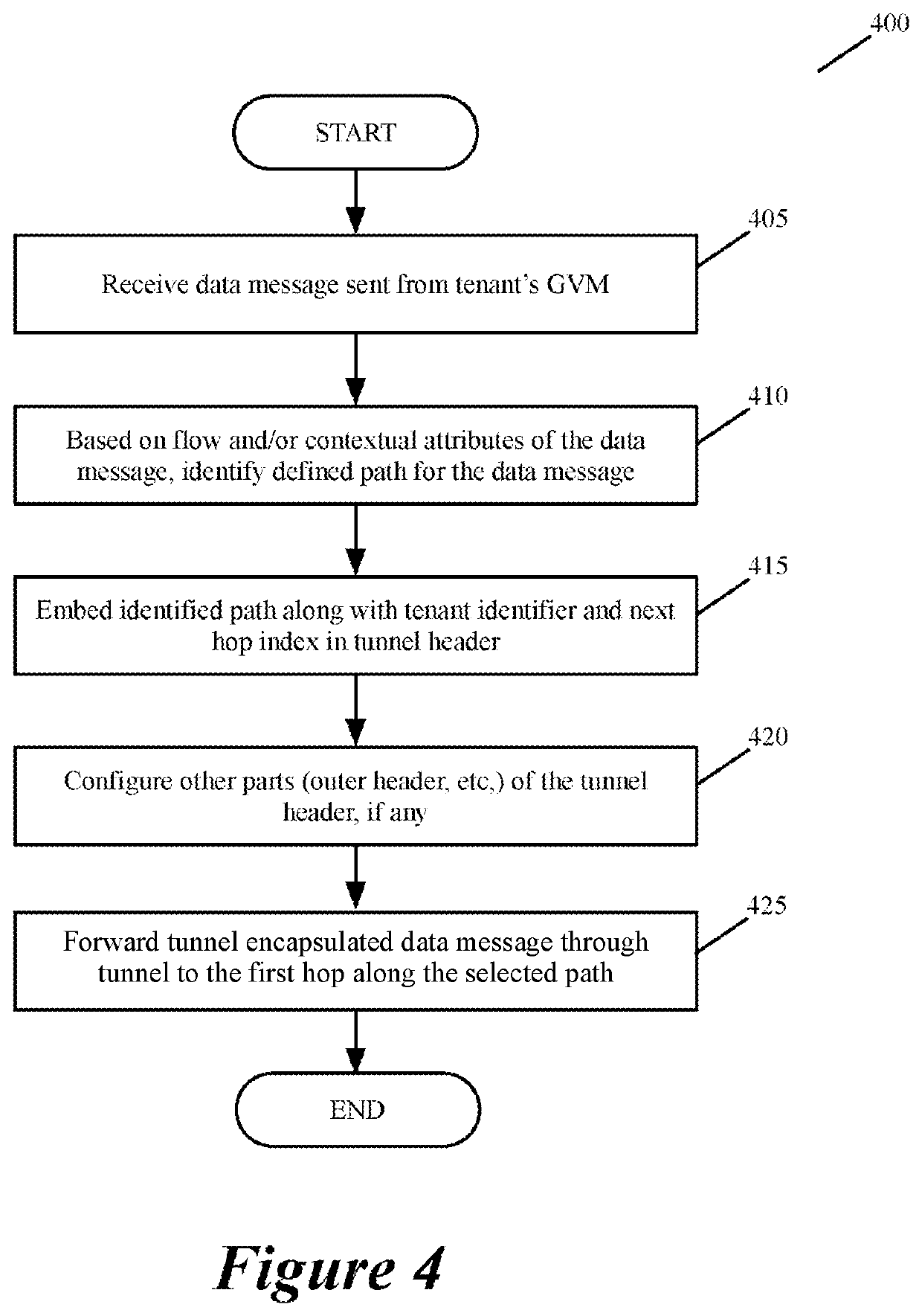
For a multi-tenant environment, some embodiments of the invention provide a novel method for (1) embedding a specific path for a tenant's data message flow through a network in tunnel headers encapsulating the data message flow, and then (2) using the embedded path information to direct the data message flow through the network. In some embodiments, the method selects the specific path from two or more viable such paths through the network for the data message flow.
Owner:NICIRA
Mechanism and apparatus for transparently enables multi-tenant file access operation
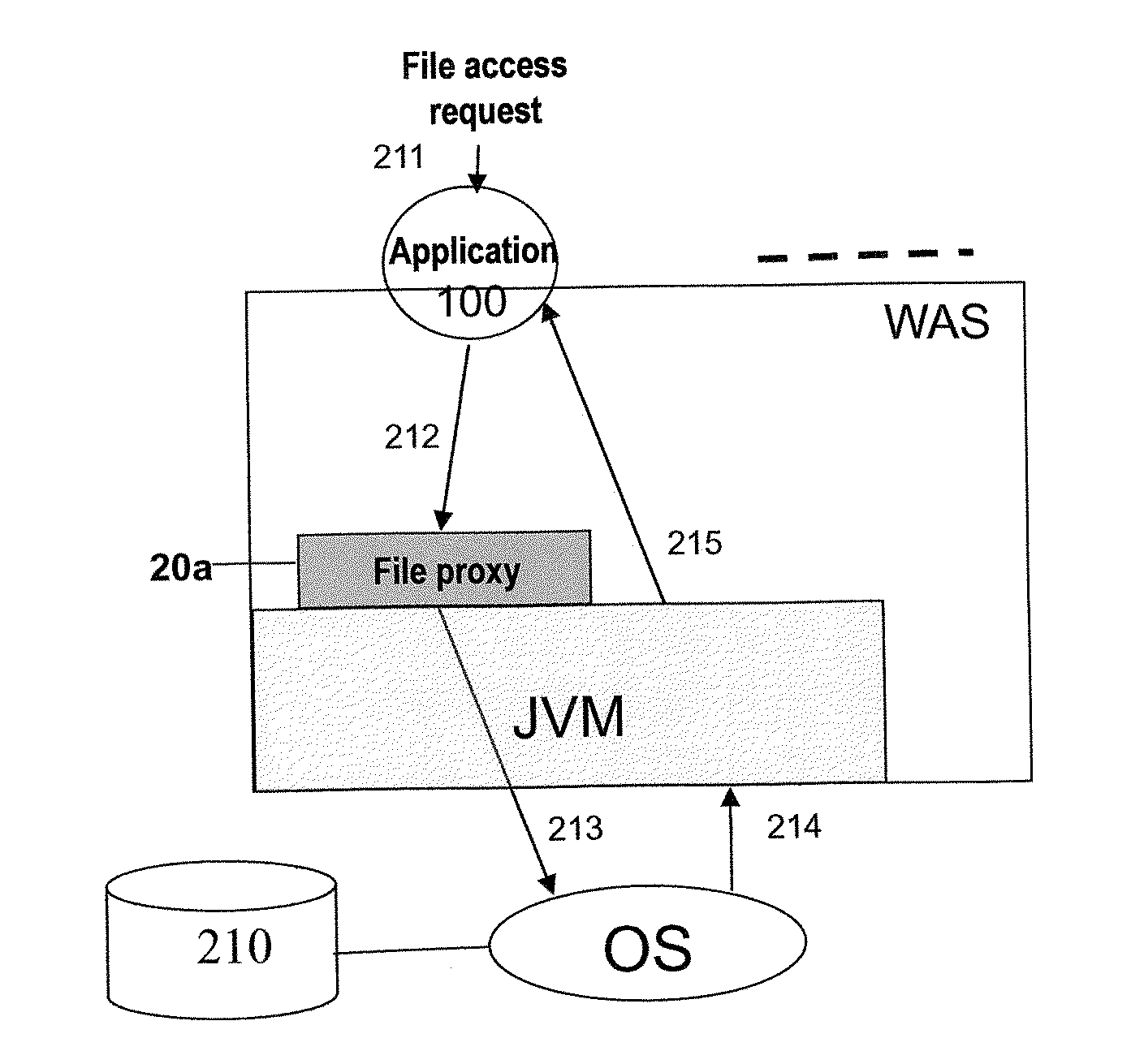
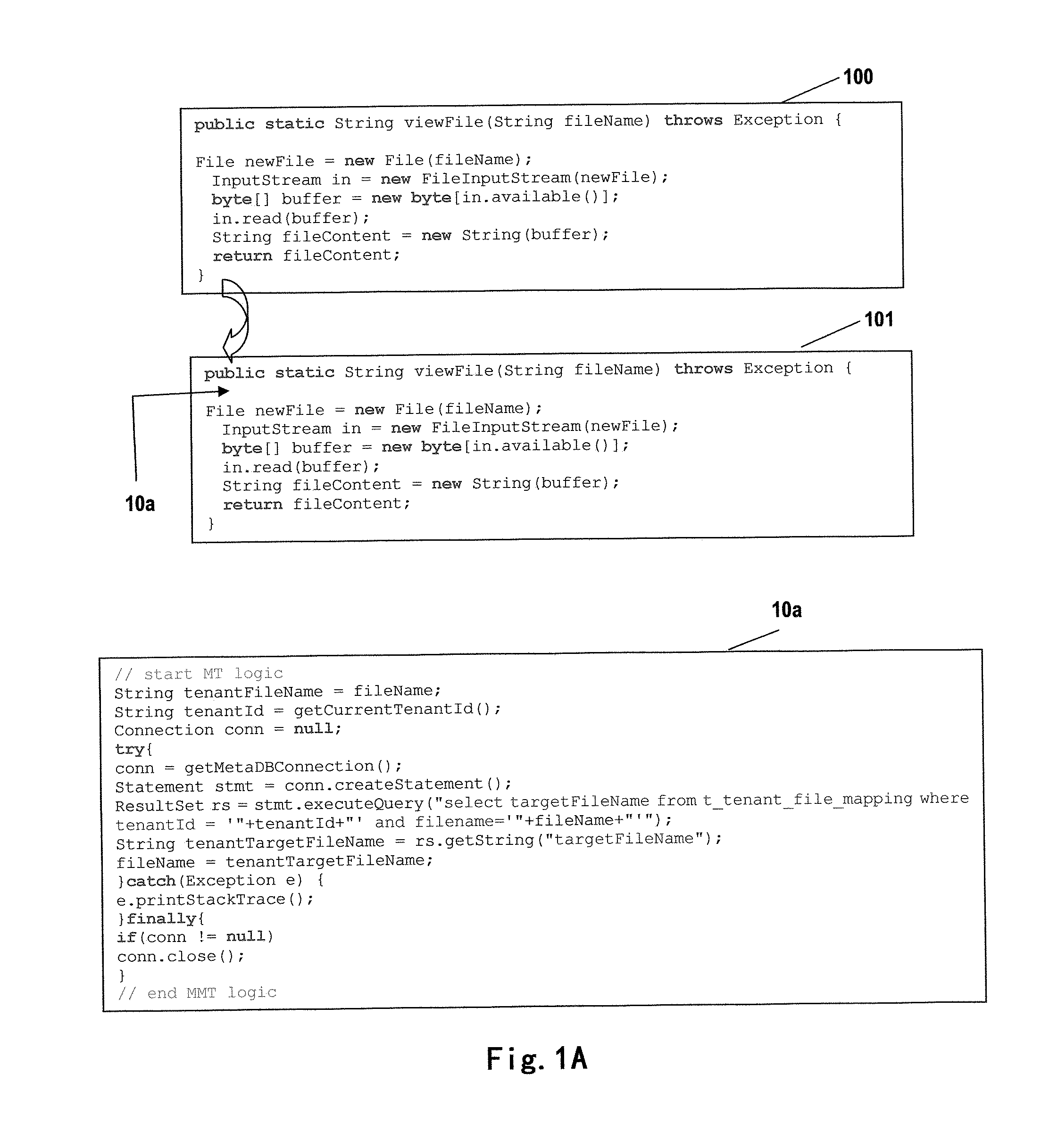
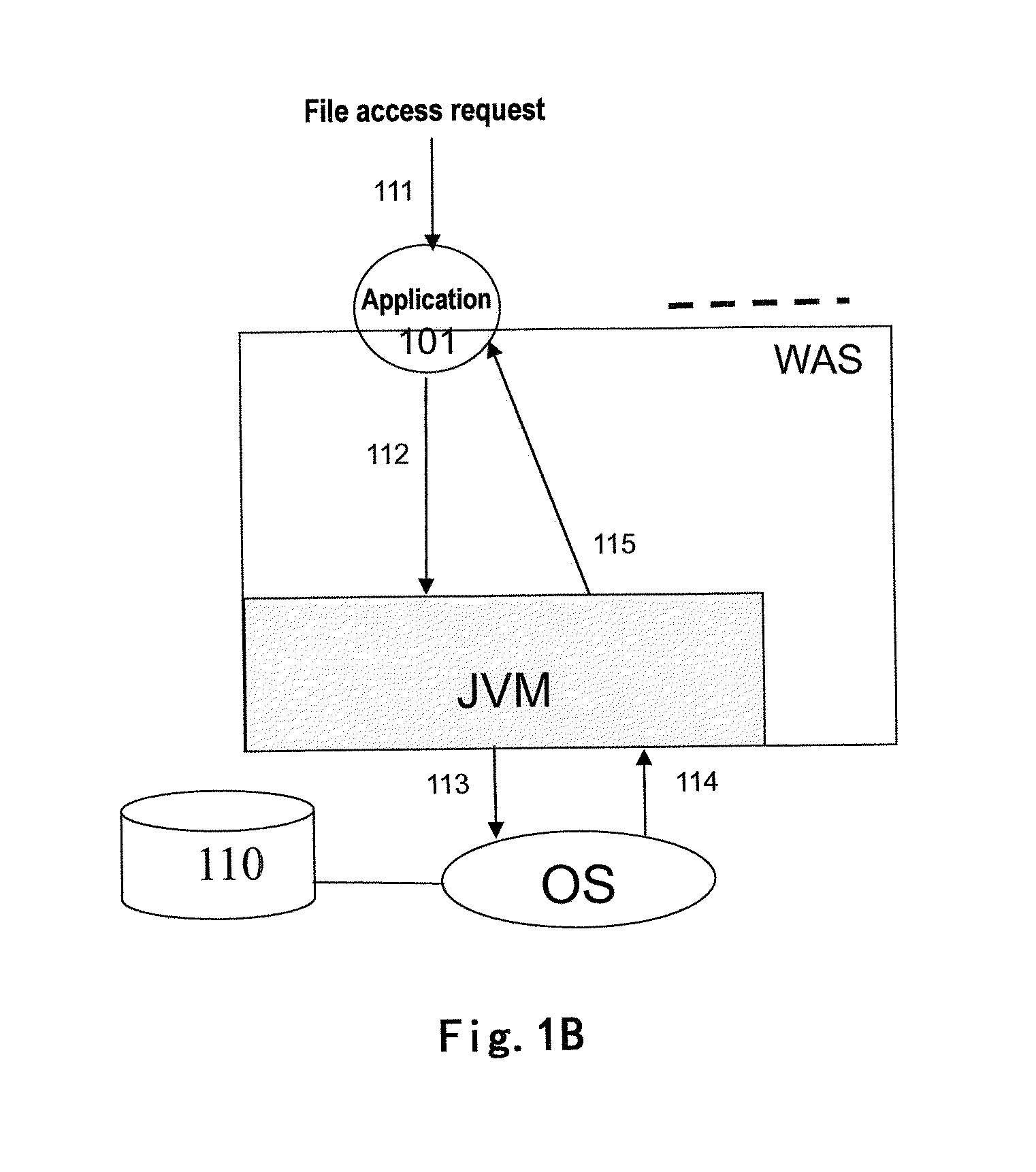
InactiveUS20110270886A1Enhanced middlewareDigital data processing detailsComputer security arrangementsOperational systemFile system
The present invention relates to a multi-tenant technology. The disclosure provides a method for processing a file access request to a multi-tenant application by using a file proxy and a corresponding file proxy apparatus, the method comprising: intercepting a file access request; converting the file access request based on a predetermined file isolation model; and transmitting the converted file access request to an operating system. By using this invention, the necessity of modifying a source code of an application so as to enabling a single-tenant application to support an operation in the multi-tenant model may be reduced. The present invention further provides a multi-tenant file system adapted for a multi-tenant application. In cooperation with the multi-tenant system, the method and file proxy apparatus according to the present invention may provide transparent support to fulfill security isolation and access control of tenant files with different SLAs.
Owner:IBM CORP
Method, equipment and system for managing shared objects of a plurality of lessees based on cloud computation
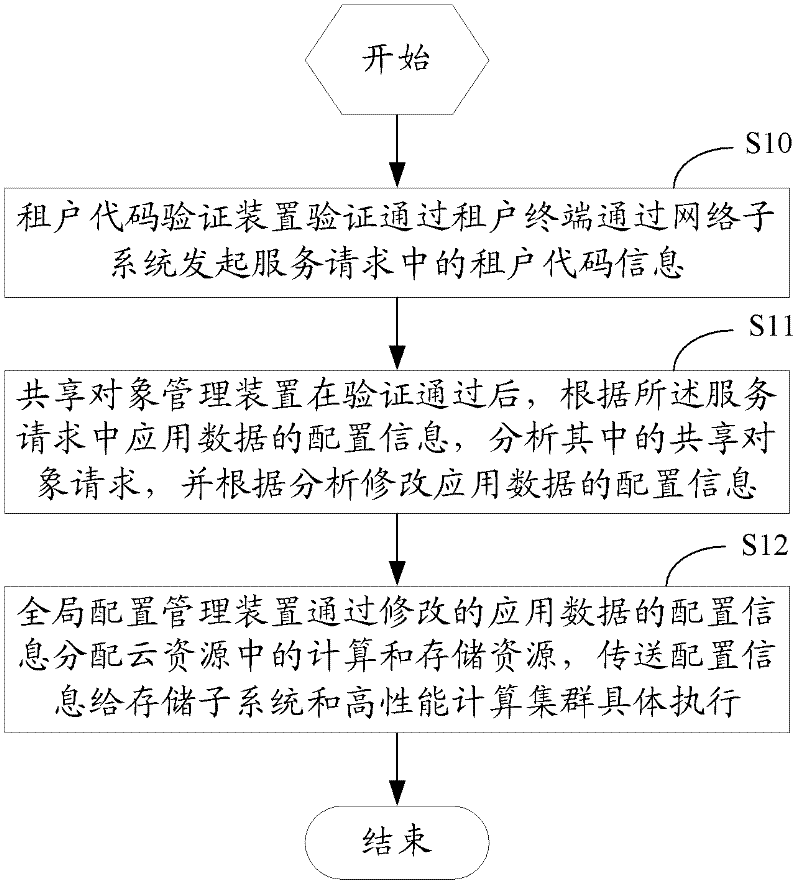
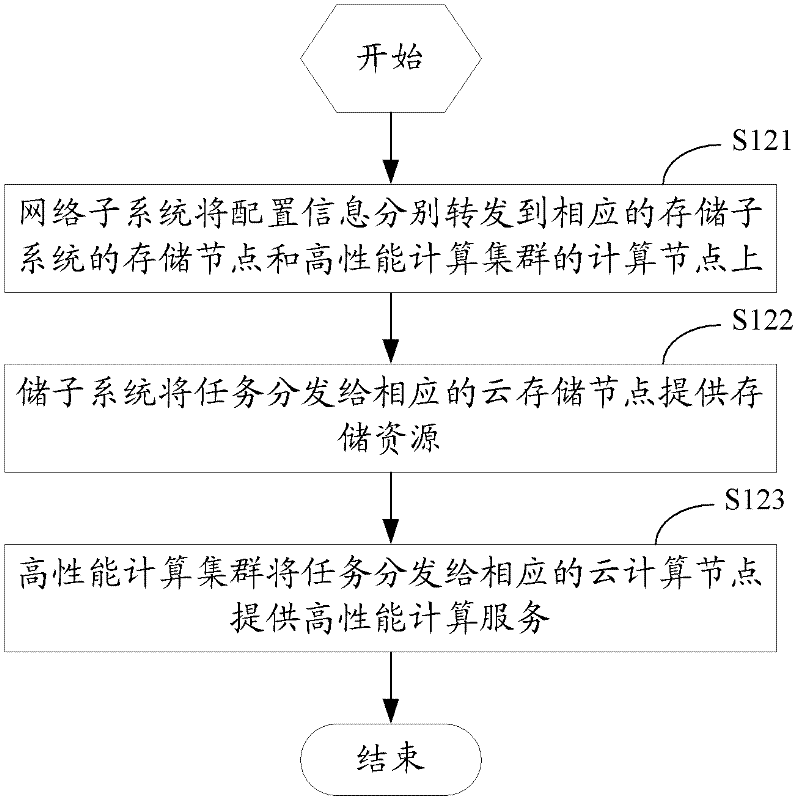
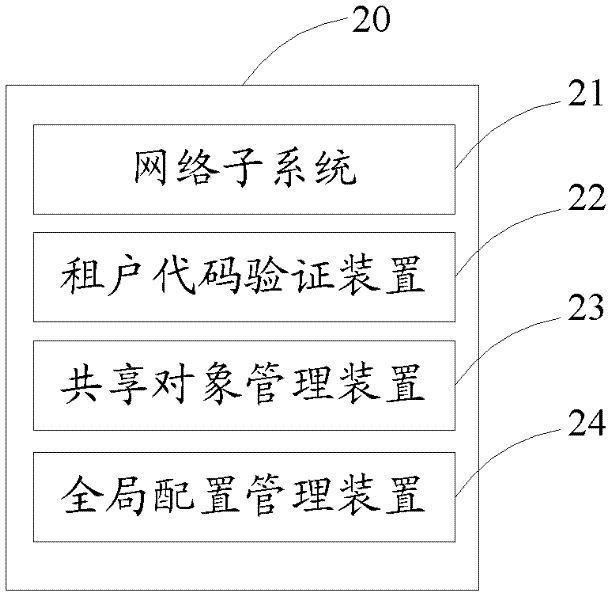
The invention discloses a method, equipment and a system for managing the shared objects of a plurality of lessees based on cloud computation. The system can comprise a lessee code authentication device, an overall configuration management device, a network subsystem, a storage subsystem, a high-performance computation cluster and a shared object management device; according to the method, the equipment and the system for managing the shared objects of the lessees based on the cloud computation, the problem of how to reasonably utilize resources and share information in lessees which are exclusively mapped can be solved by lessee codes under a structure of a plurality of lessees in cloud computation; by managing the shared objects of a plurality of lessees, a feasible solution for interconnecting and intercommunicating information resources is provided; the method, the equipment and the system for managing the shared objects of the lessees based on the cloud computation are beneficial to integrating existing information resources; and the resources of computation, storage, bandwidth and the like of the system are reasonably utilized.
Owner:国家超级计算深圳中心(深圳云计算中心)
Service operation chaining
ActiveUS10797966B2Networks interconnectionSoftware simulation/interpretation/emulationMessage flowIp address
For a multi-tenant environment, some embodiments of the invention provide a novel method for forwarding tenant traffic through a set of service machines to perform a set of service operations on the tenant traffic. In some embodiments, the method performs a classification operation on a data message flow of a tenant, in order to identify a set of service operations to perform on the data message flow. For some data message flows, the classification operation selects the identified set of service operations from several candidate sets of service operations that are viable service operation sets for similar data message flows of the tenant. In some embodiments, the classification operation is based on a set of attributes associated with the data message flow (e.g., five tuple identifier, i.e., protocol and source and destination ports and IP addresses).
Owner:NICIRA
Methods and apparatus for web-based migration of data in a multi-tenant database system
InactiveUS20110302277A1Database distribution/replicationMultiple digital computer combinationsProtocol for Carrying Authentication for Network AccessData migration
A computer-implemented system and method includes migrating a database from one multi-tenant database to a second multi-tenant database over a network using a Web protocol such as secure hypertext transfer protocol (HTTPS). The transferred data records may be sent as serializable Java objects in response to a migration request produced by one of the multi-tenant databases.
Owner:SALESFORCE COM INC
Specifying and utilizing paths through a network
For a multi-tenant environment, some embodiments of the invention provide a novel method for (1) embedding a specific path for a tenant's data message flow through a network in tunnel headers encapsulating the data message flow, and then (2) using the embedded path information to direct the data message flow through the network. In some embodiments, the method selects the specific path from two or more viable such paths through the network for the data message flow.
Owner:NICIRA
Dynamically splitting multi-tenant databases
ActiveUS20120102067A1Well formedDigital data processing detailsDatabase distribution/replicationWeb serviceRetargeting
An online service includes managed databases that include one or more tenants (e.g. customers, users). A multi-tenant database may be split between two or more databases while the database being split continues processing requests. For example, web servers continue to request operations on the database while content is being moved. After moving the content, tenant traffic is automatically redirected to the database that contains the tenant's content.
Owner:MICROSOFT TECH LICENSING LLC
Multi-tenant system achievement based on software as a service (SAAS) application
The invention relates to multi-tenant system achievement, in particular to the multi-tenant system achievement based on software as a service (SAAS) application. The multi-tenant system achievement belongs to the field of network communication and is characterized in that tenant register and user register of each tenant of the SAAS application are completed through a register management module; a verifying process of tenant information and tenant data information is completed through a tenant verifying module; binding of functional modules customized by the tenants is completed through an example custom-tailor module; limit information set by the tenants is bound to a set user through a limit binding module; and record storage of various data of the tenants is completed through a data management module. The multi-tenant system achievement uses a multi-tenant register middleware sharing mode and meets requirements of achieving multi-tenant management of the SAAS application by creating different application examples in a single application program according to different tenant requirements.
Owner:ZHENJIANG JINRUAN COMP TECH
Multi-tenant over-the-top multicast
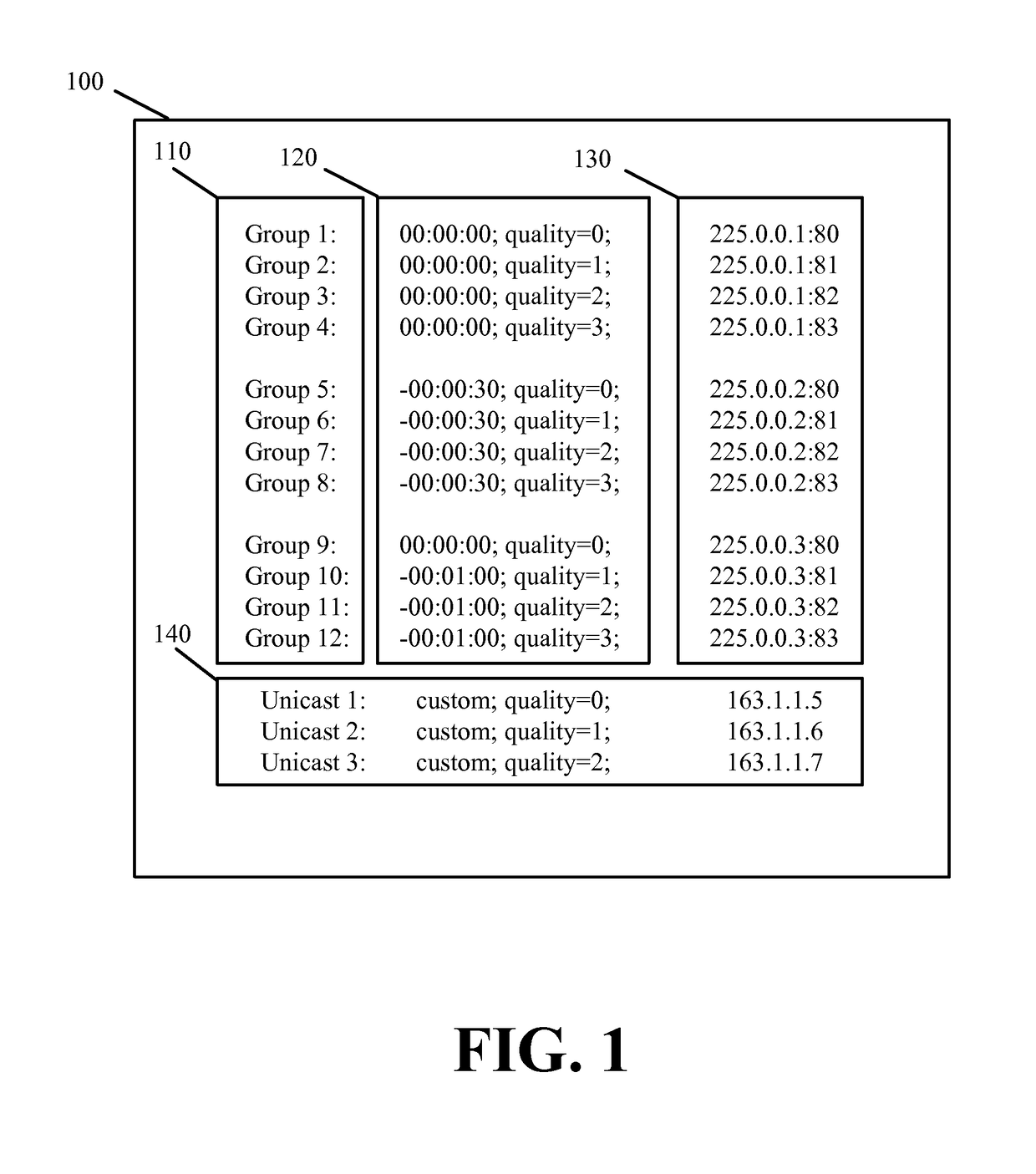
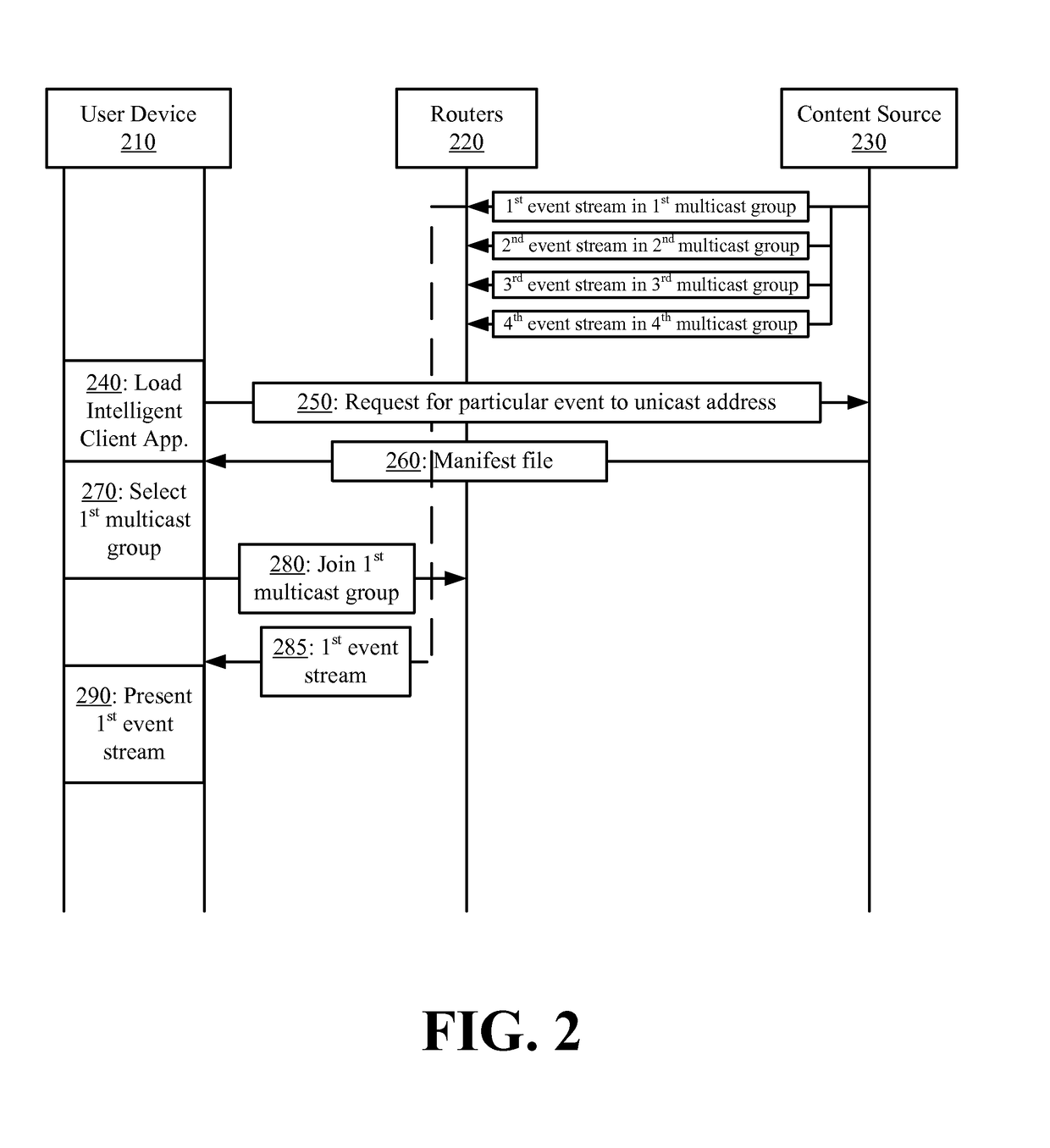
Some embodiments provide a multi-tenant over-the-top multicast solution that integrates the per user stream customizability of unicast with the large scale streaming efficiencies of multicast. The solution involves an application, different multicast groups streaming an event with different customizations, and a manifest file or metadata identifying the different groups and customizations. The solution leverages the different multicast groups in order to provide different time shifts in the event stream, different quality level encodings of the event stream, and different secondary content to be included with a primary content stream. The application configured with the manifest file or metadata dynamically switches between the groups in order to customize the experience for a user or user device on which the application executes. Switching from multicast to unicast is also supported to supplement available customizations and for failover.
Owner:EDGIO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com