Safety protection method and system, computer equipment and computer readable storage medium
A security protection and security kernel technology, applied in the field of computer-readable storage media, can solve system security issues and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
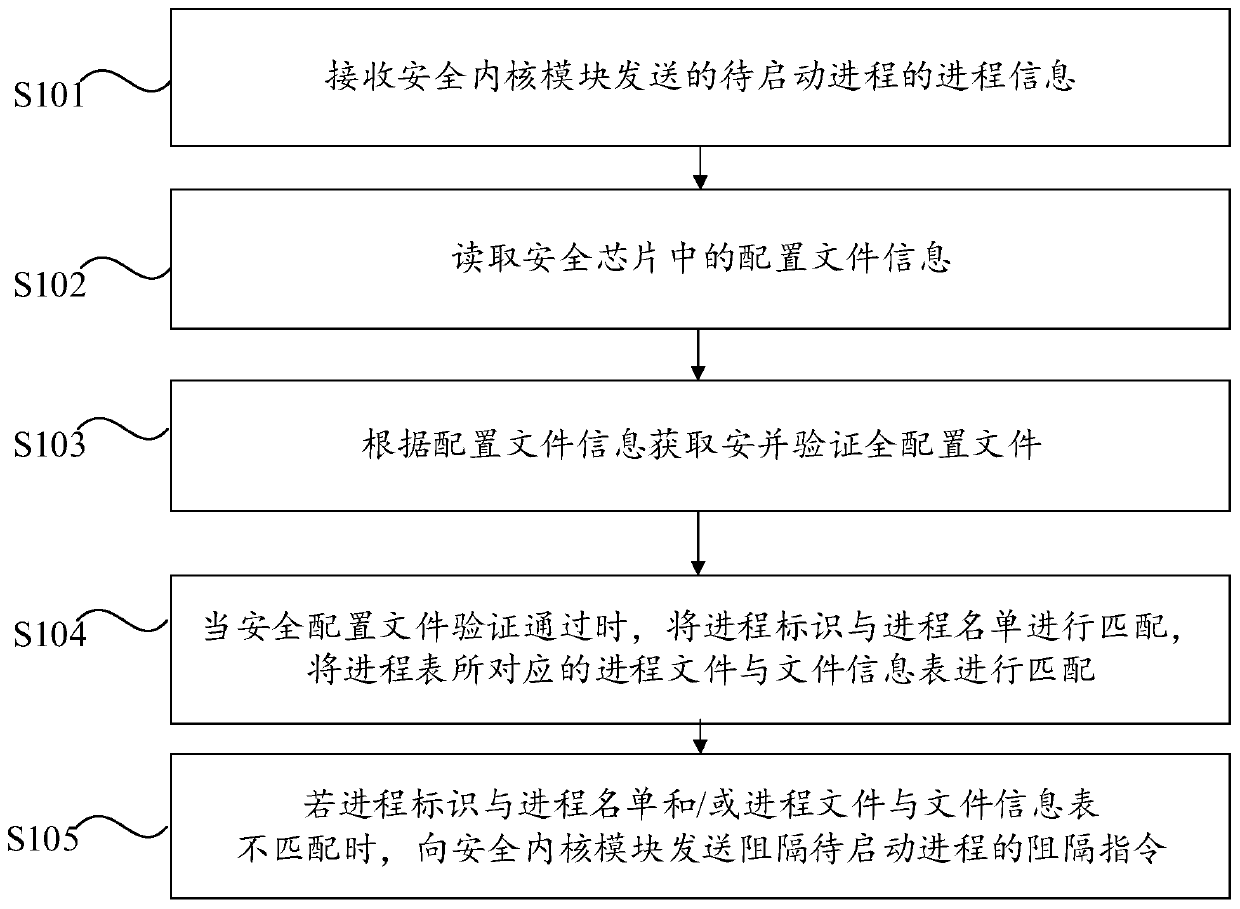
[0031] An embodiment of the present invention provides a security protection method, which is applied to a daemon process of a security protection system, wherein the security protection system includes the daemon process, and also includes a security kernel module and a security chip, wherein the daemon process and The security core modules are all software devices, and the security chip is a hardware structure, such as TPM (Trusted Platform Module, Trusted Platform Module) and the like. Through this method, the trusted root of the software in the security guard system is put into the security chip, and the security chip protects the root of the reliability verification of the security configuration file, and the daemon process and the security kernel module interact with the security chip separately to realize the Blocking of dangerous processes, specifically, the security protection method provided by this embodiment includes the following steps S101 to S109.
[0032] Step ...
Embodiment 2
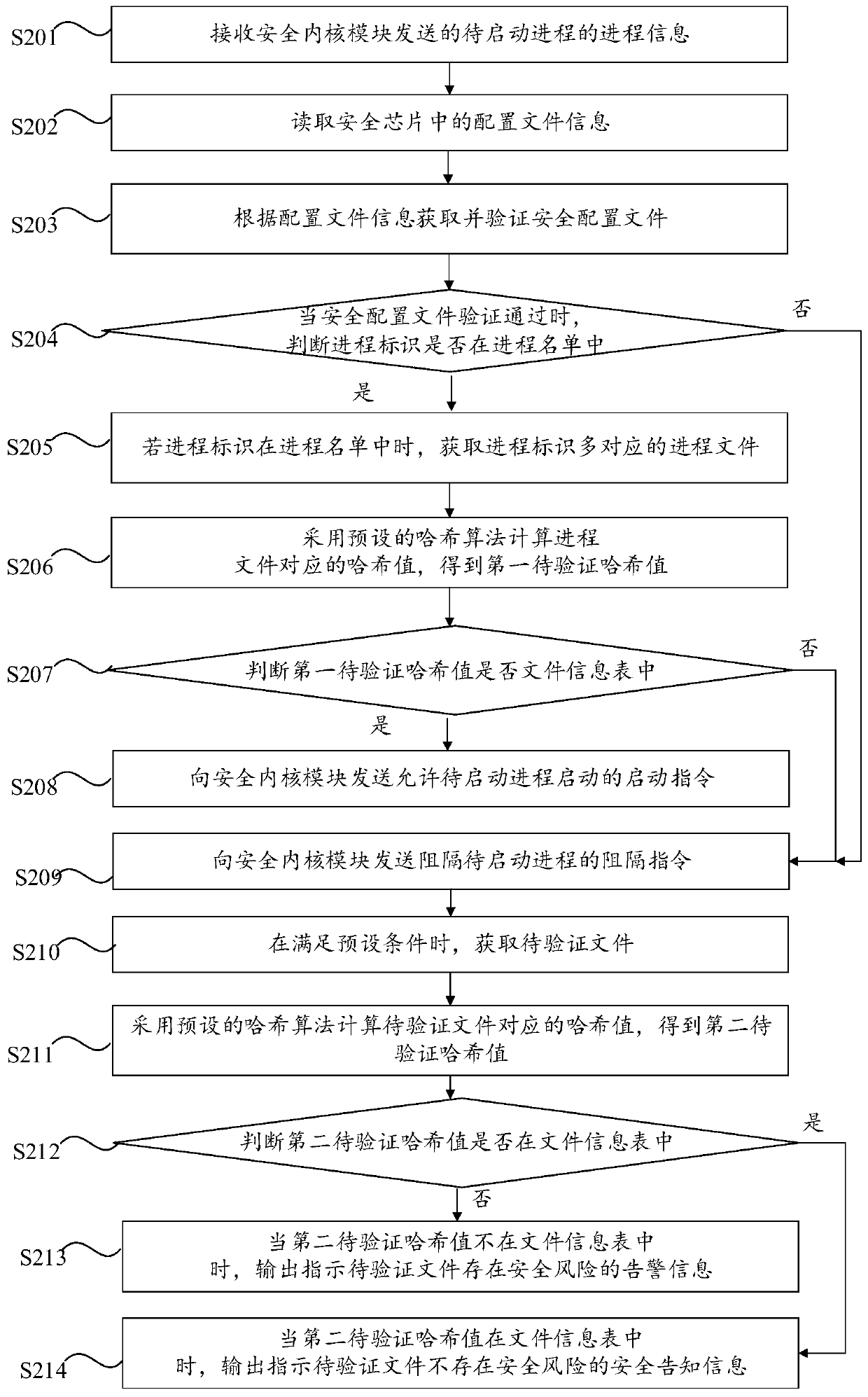
[0055] Embodiment 2 of the present invention provides a preferred security protection method, and some technical features are the same as those in Embodiment 1 above. For specific descriptions and corresponding technical effects, reference may be made to Embodiment 1 above. Further, in the second embodiment, when the process identifier matches the process list, the matching between the process file and the file information table is judged, which simplifies the judgment logic. In addition, the security protection method provided by this embodiment can also protect the integrity of the files in the server. Judgment on sex and effectiveness. specifically, figure 2 A flow chart of the security protection method provided in Embodiment 2 of the present invention, such as figure 2 As shown, the security protection method provided in the second embodiment includes the following steps S201 to S214.
[0056] Step S201: Receive the process information of the process to be started sen...
Embodiment 3
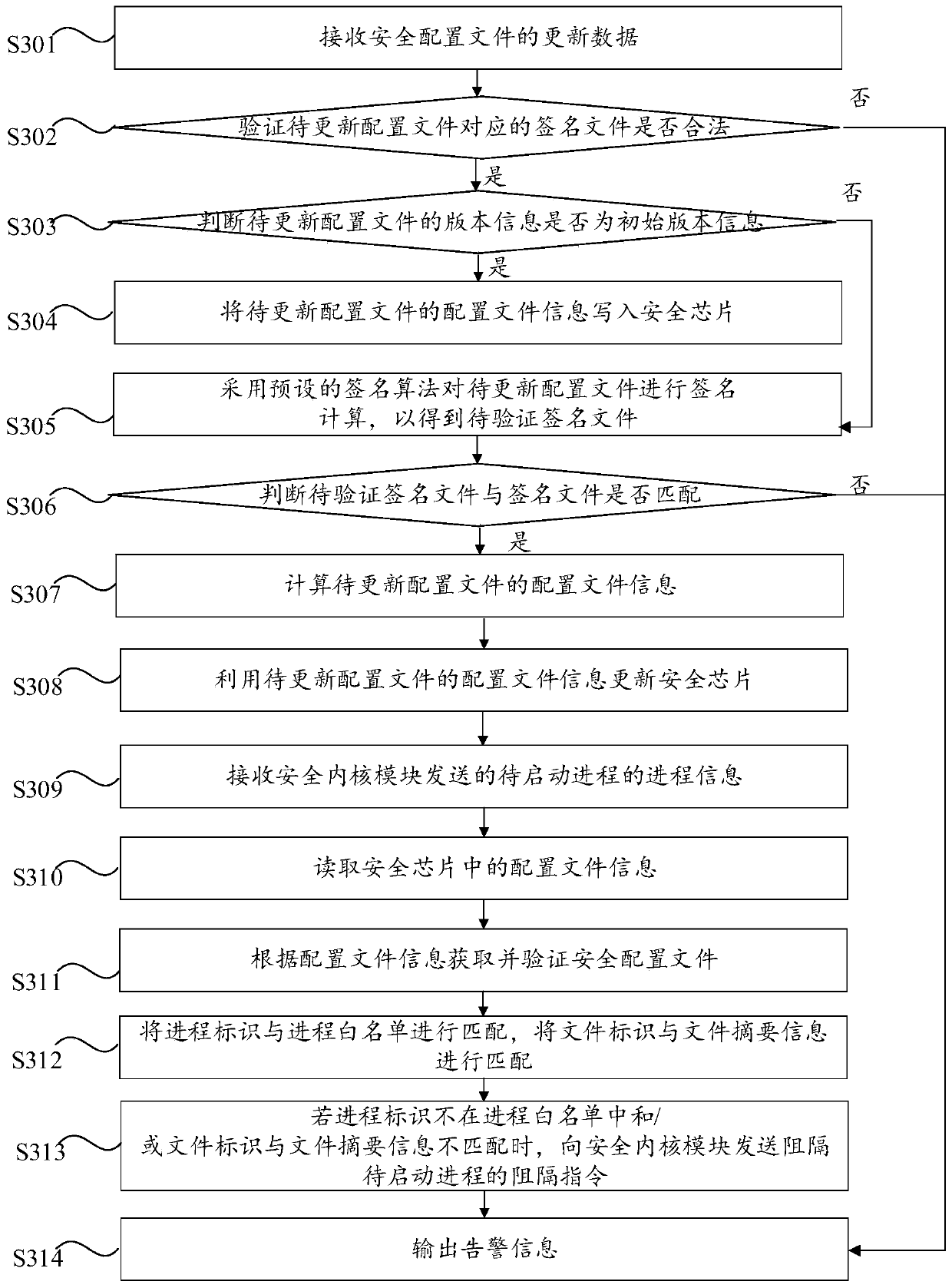
[0079] Embodiment 3 of the present invention provides a preferred security protection method, and some technical features are the same as those in Embodiment 1 above. For specific descriptions and corresponding technical effects, please refer to Embodiment 1 above. Further, the third embodiment can update the configuration file information in the security chip, and provides a safe update method. specifically, image 3 The flow chart of the security protection method provided by Embodiment 3 of the present invention, such as image 3 As shown, the security protection method provided by the third embodiment includes the following steps S301 to S314.
[0080] Step S301: Receive update data of the security configuration file.
[0081] Wherein, the update data includes the configuration file to be updated, the signature file corresponding to the configuration file to be updated, and the version information of the configuration file to be updated.
[0082] When the security confi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com