Method for automatically updating identification private key and password system
A technology that identifies private keys and automatically updates them. It is applied in the field of information security and can solve problems such as inability to obtain identification private keys and unsatisfactory satisfaction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
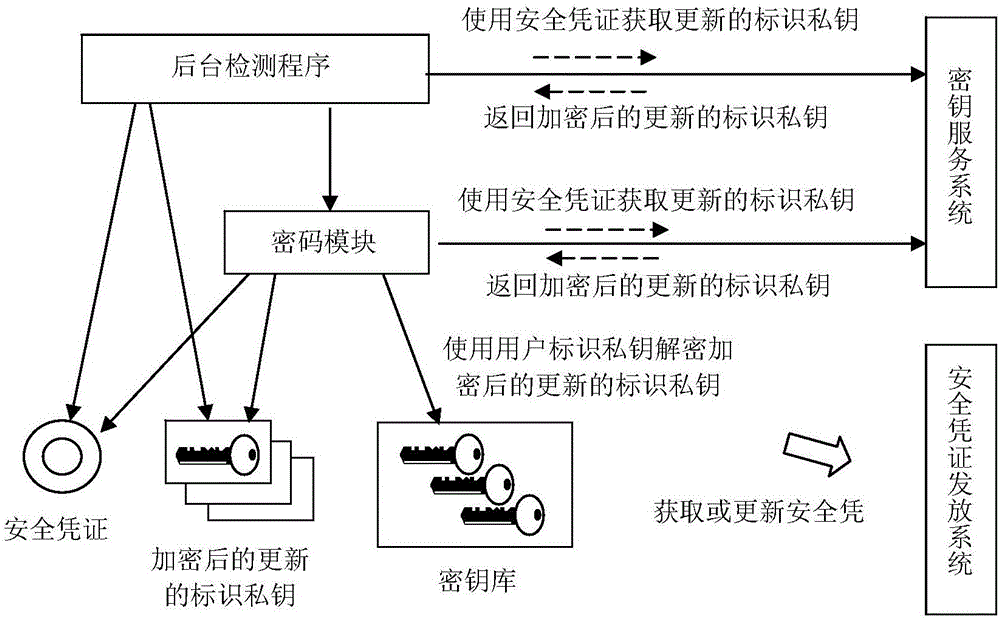
[0045] like figure 1 Described, in this embodiment, the cryptographic module of the user is a software cryptographic module (such as based on the CSP dynamic storehouse of WindowsCryptoSPI interface, based on the PKCS#11 dynamic storehouse of PKCS#11 interface), the identification private key of the user is stored in the user's computer local In a key store of a user, and stored in the key store, the identity private key (series) corresponding to an identity of a user is stored after being encrypted with a symmetric key (this symmetric key is called the identity private key encryption key) key), and this identification private key encryption key is also stored in the key store after being encrypted with the user's password or PIN code (the derived key). After the user enters the password or PIN code, the cryptographic module or the background detection program can obtain the encryption key of the identity private key through decryption, and then use this identity private key t...
Embodiment 2
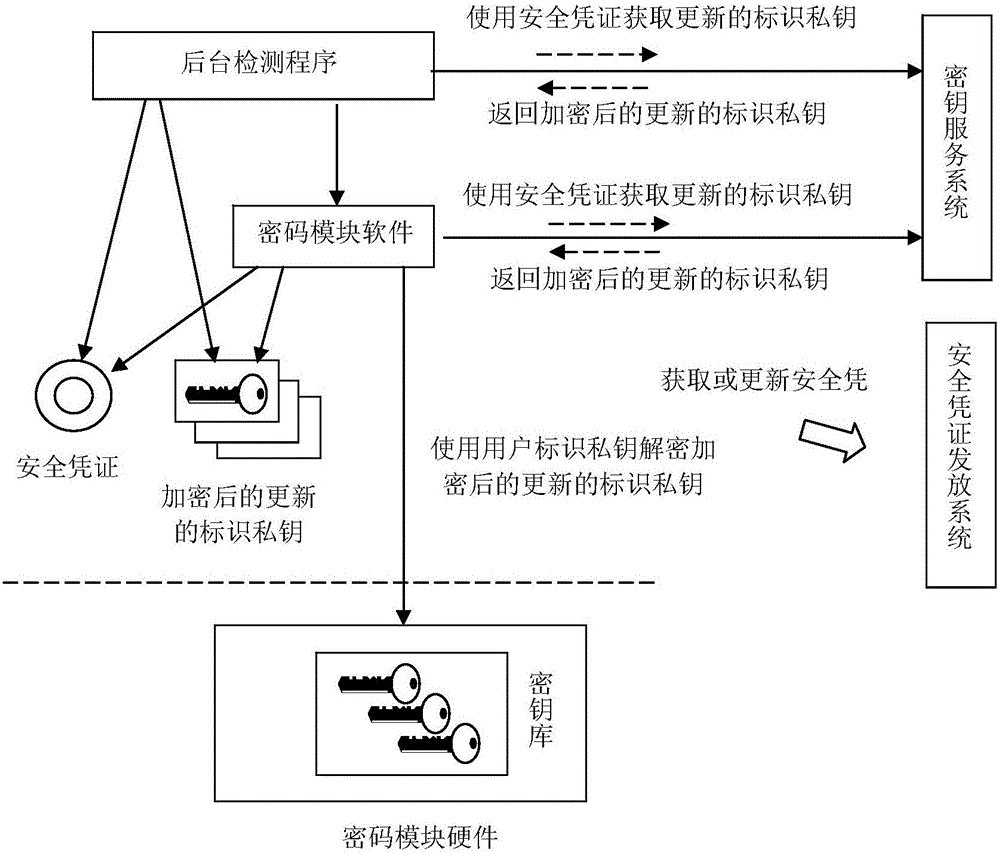
[0053] like figure 2As mentioned above, the difference between Embodiment 2 and Embodiment 1 is that the cryptographic module at this time is a combination of software and hardware, wherein the hardware part (such as USB Key) stores the user identification private key and uses the identification private key to perform cryptographic operations ( Such as data decryption, digital signature, etc.); only after the user inserts the cryptographic hardware into the computer and enters the cryptographic hardware or the protection password (PIN code) that identifies the private key, various programs can be called through the software part (cryptographic interface) of the cryptographic module, Use the identified private key in the cryptographic hardware to perform cryptographic operations. At this time, the software part of the cryptographic module provides the call interface (cryptographic interface) between the cryptographic hardware and the application program, and the cryptographic ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com