Computer protecting method based on programm behaviour analysis
A behavior analysis, computer technology, applied in computing, program control devices, instruments, etc., can solve the problems of anti-virus software, complicated use of firewalls, and the inability of anti-virus software to protect against unknown viruses and Trojans.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
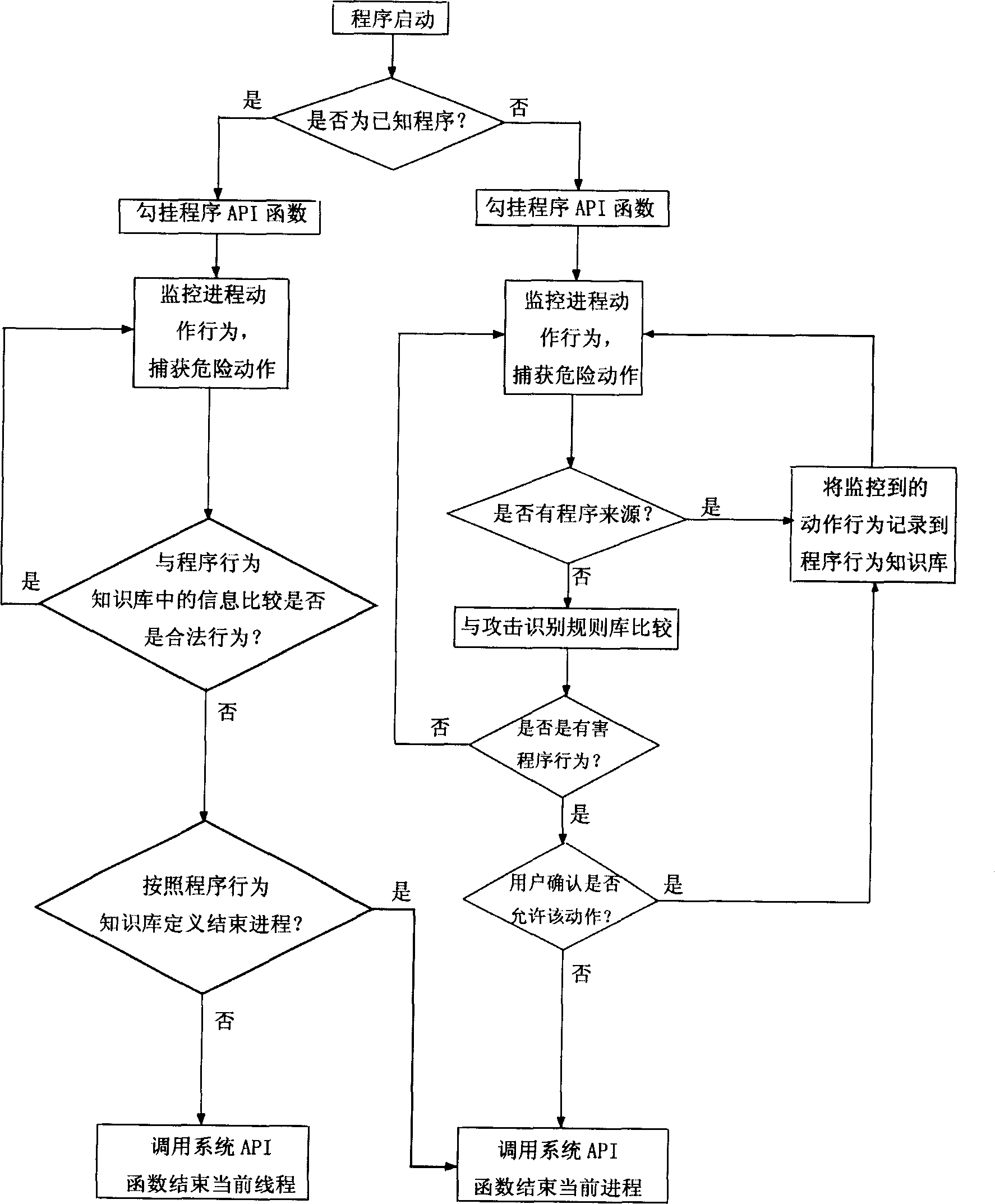
[0079] Referring to the accompanying drawings, and in conjunction with the most commonly used Microsoft Windows operating system, the computer protection method based on program behavior analysis of the present invention is applied to the Microsoft Windows operating system, and the embodiments of the present invention are described in detail.
[0080] Such as figure 1 Shown is a flow chart of the computer protection method based on program behavior analysis of the present invention.
[0081] The computer protection method based on program behavior analysis of the present invention is characterized in that:
[0082] For a known program, monitor its behavior and compare it with the legal behavior of the known program recorded in the program behavior knowledge base to determine whether the known program has been illegally attacked;
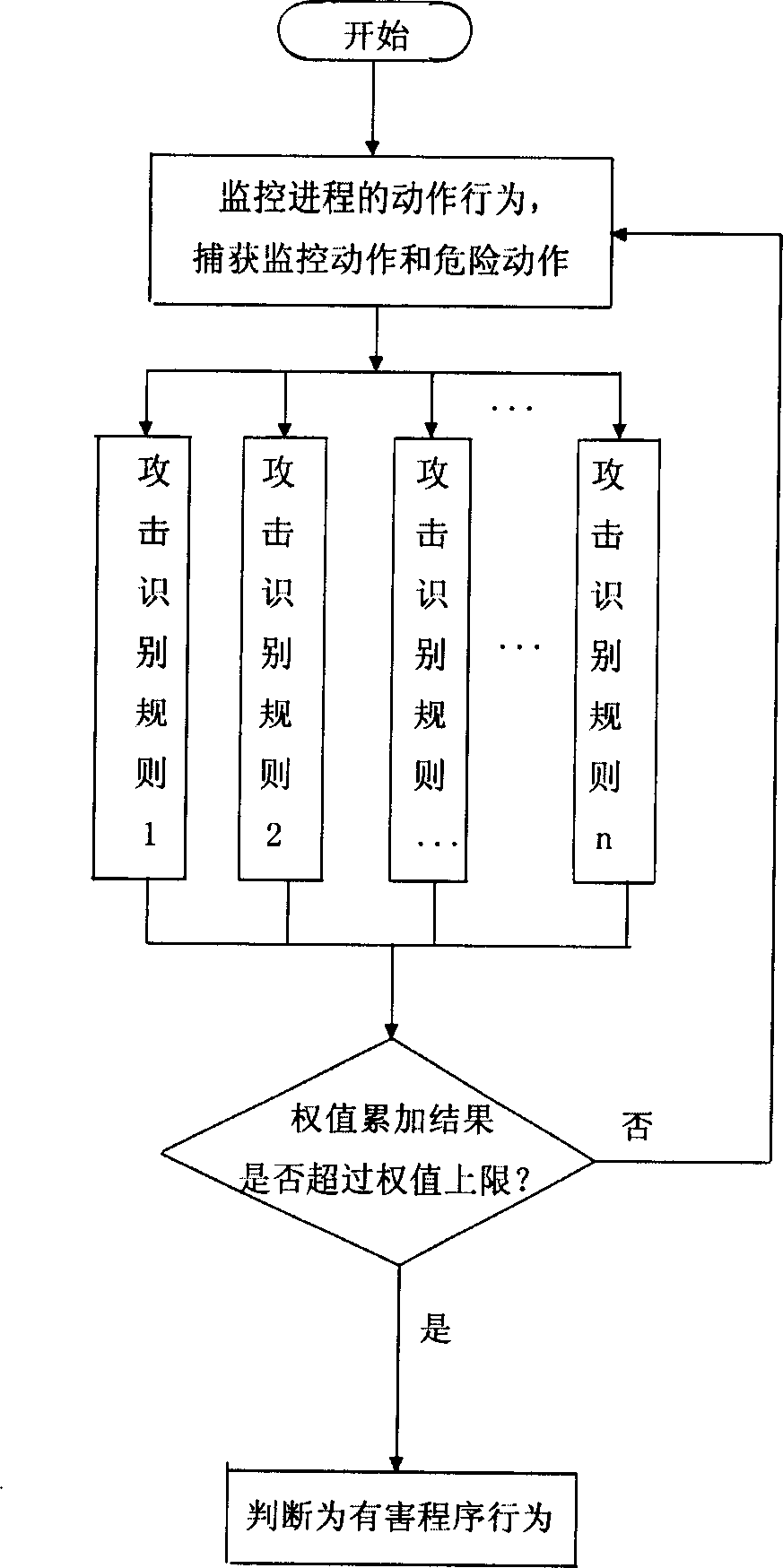
[0083] For unknown programs, monitor their actions and compare them with the attack identification rules recorded in the attack identification rule...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com