Client program monitoring method, device and client
A technology of client programs and monitoring devices, which is applied in hardware monitoring, computer security devices, instruments, etc., can solve the problems of client user losses, increase usage costs, etc., and achieve the effects of avoiding malicious uploads, protecting security and user interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
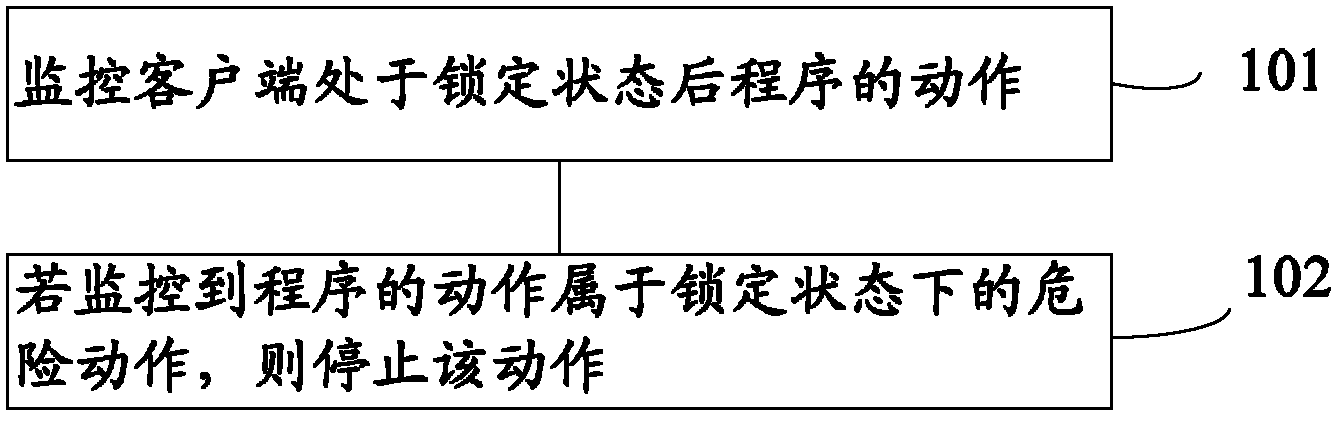
[0062] refer to figure 1 , showing Embodiment 1 of the client program monitoring method of the present invention, including the following steps:
[0063] Step 101, monitor the program action after the client is in the locked state.
[0064] The client here refers to mobile terminals or PCs, such as mobile phones, notebook computers, desktop computers and other devices with application programs.
[0065] The locked state here refers to client idle states such as standby, screen locked, computer locked, input device locked, etc.
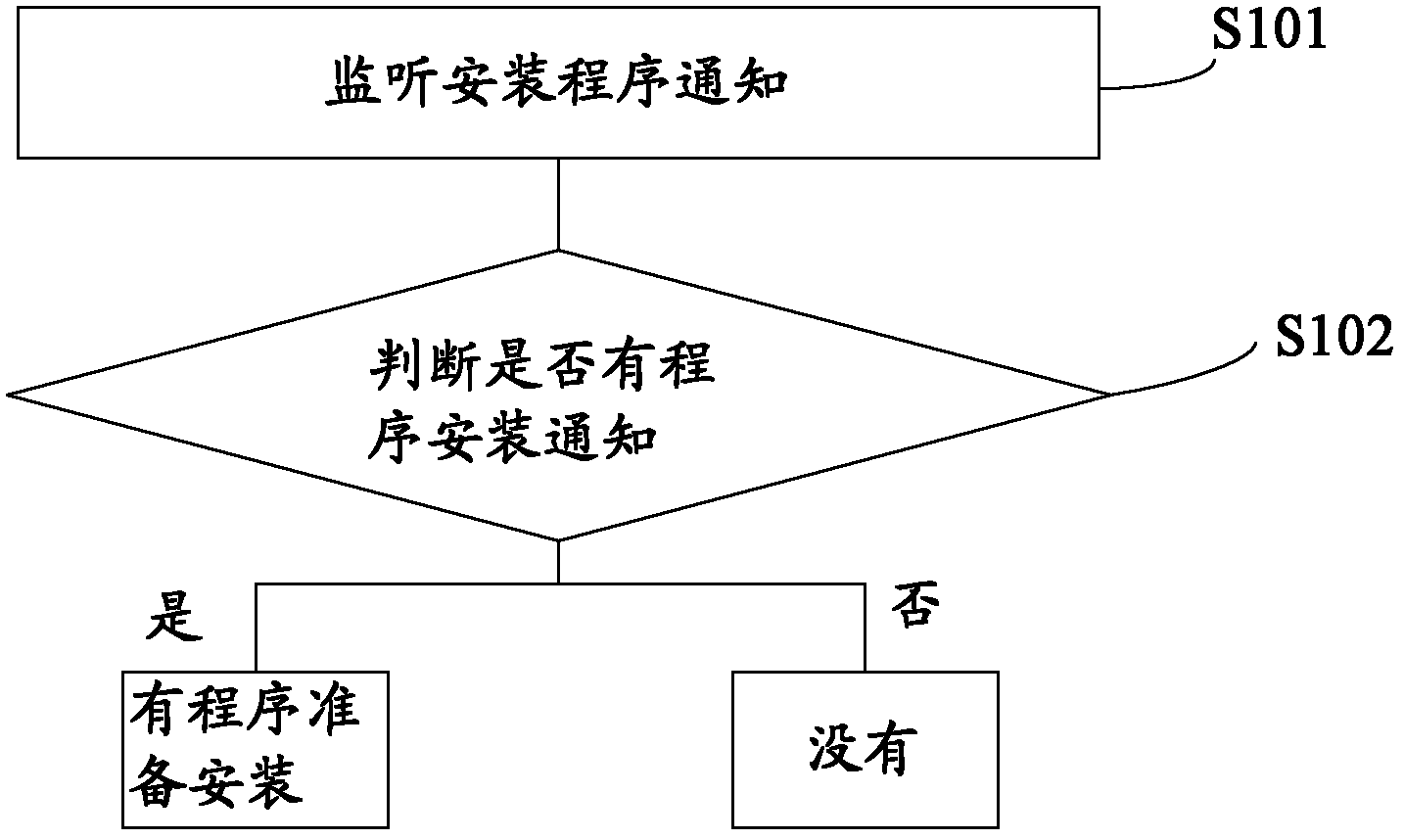
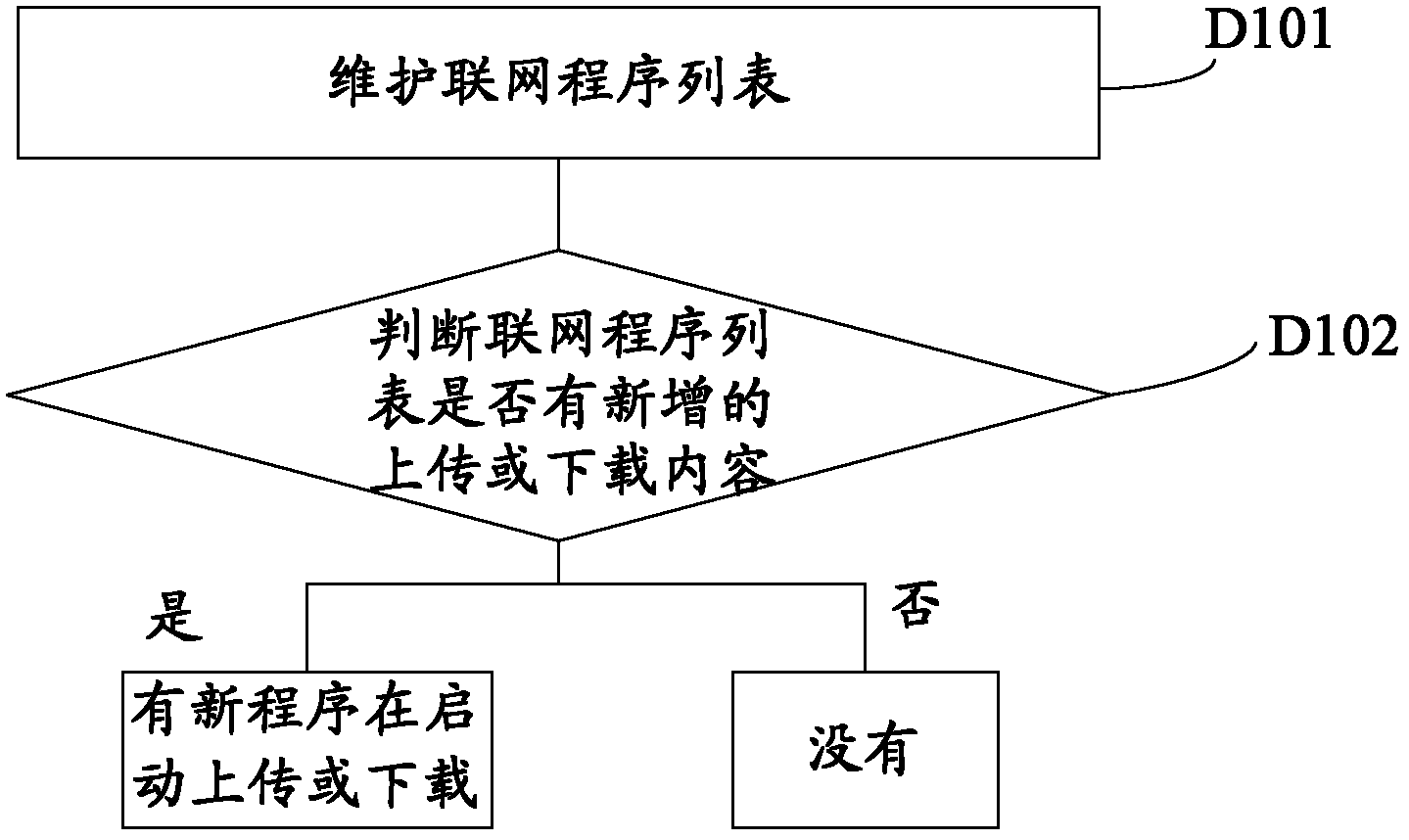
[0066] The actions of the program after the client is in the locked state include new dynamics of the program, for example, scanning at the start of the program, installation at the start of the program, uploading or downloading data at the start of the program, networking at the start of the program, deleting data or uninstalling software, closing anti-virus software or firewall, modifying the registration table information, etc.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com