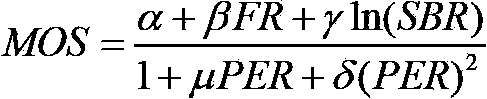Patents
Literature
219 results about "Traversal algorithms" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data Structure & Algorithms - Tree Traversal. Traversal is a process to visit all the nodes of a tree and may print their values too. Because, all nodes are connected via edges (links) we always start from the root (head) node. That is, we cannot randomly access a node in a tree.
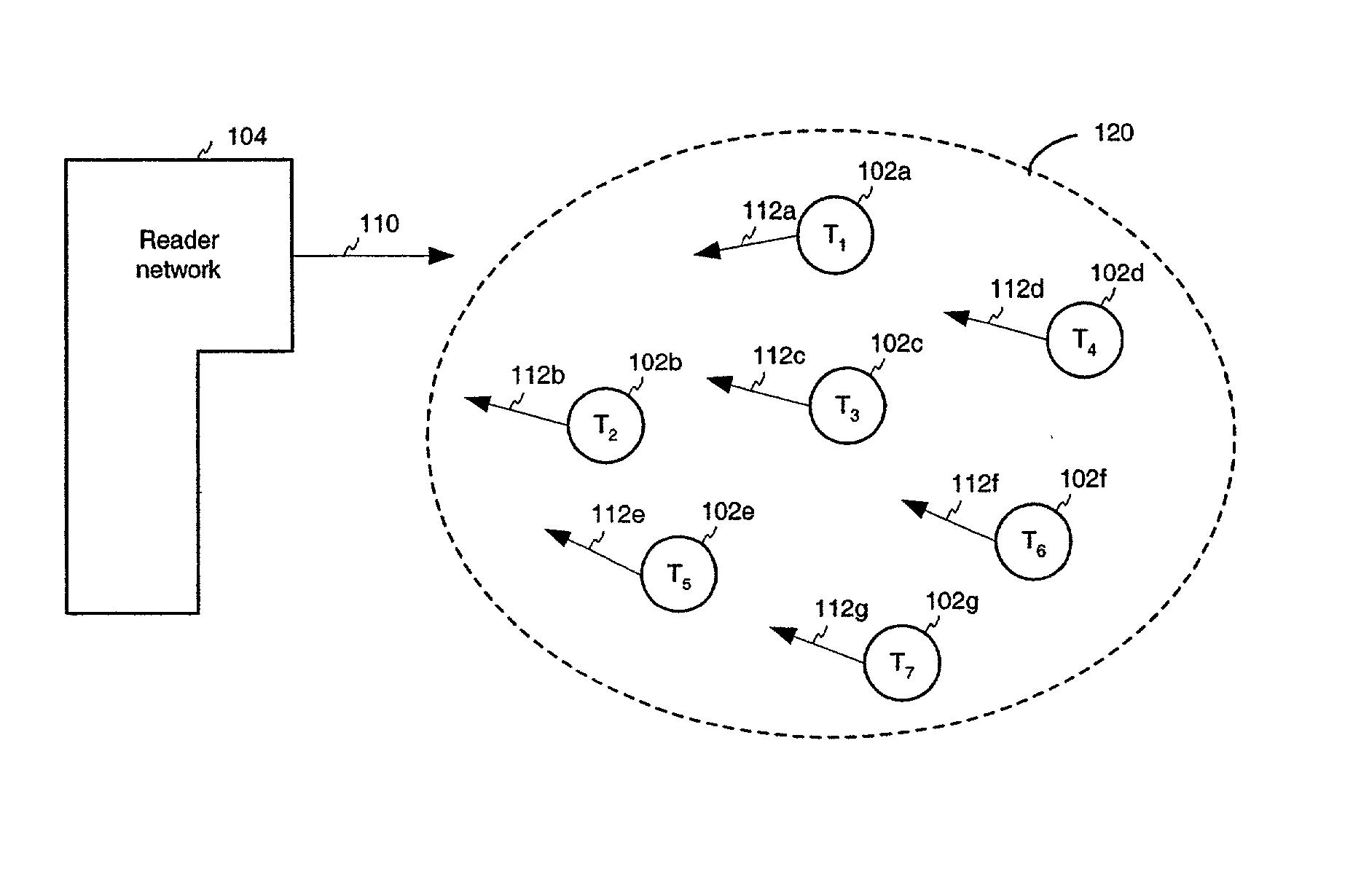
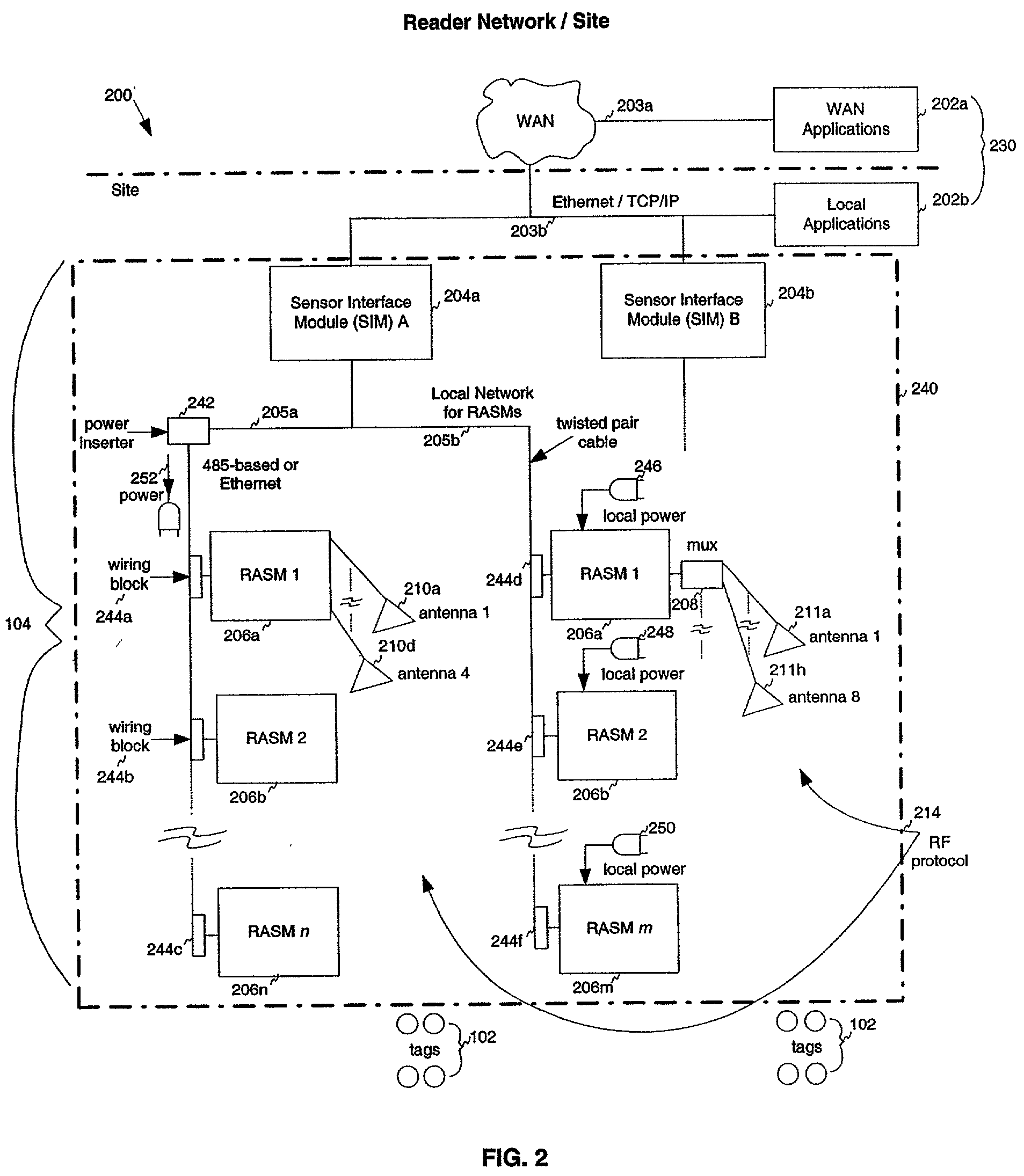
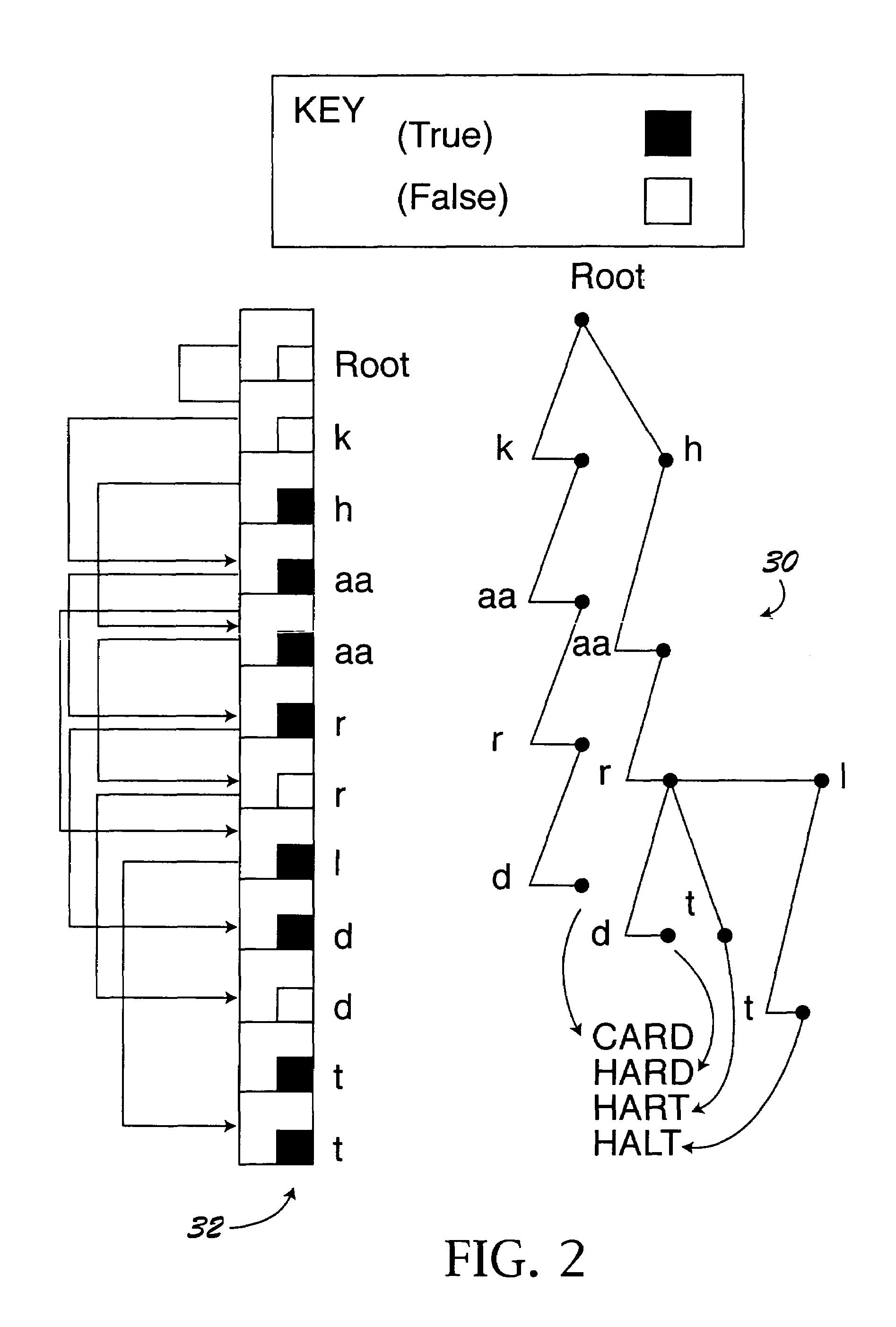
Method, system, and apparatus for binary traversal of a tag population
ActiveUS20020149481A1Processing intensiveHigh data rateMemory record carrier reading problemsCo-operative working arrangementsComputer hardwareRadio frequency
A method, system, and apparatus for interrogating a radio frequency identification (RFID) tag population are described. Tags are interrogated by a reader. The reader and tags engage in communication according to binary traversal algorithms, where single bit data symbols are exchanged between the reader and tags. Furthermore, a reader implicitly controls the operating state of every tag in the tag population by transmitting a single data symbol. Bit patterns may be collected from the tags by the reader, using a variety of interrogation techniques. In a general interrogation, the reader exchanges symbols with the tag population to interrogate the entire tag population. In a specific interrogation, a reader exchanges symbols with the tag population to target a particular tag identification number. Tags may also be placed in a superposition state by the reader, where they respond whenever a received data symbol matches the next bit of their identification number.
Owner:SYMBOL TECH LLC
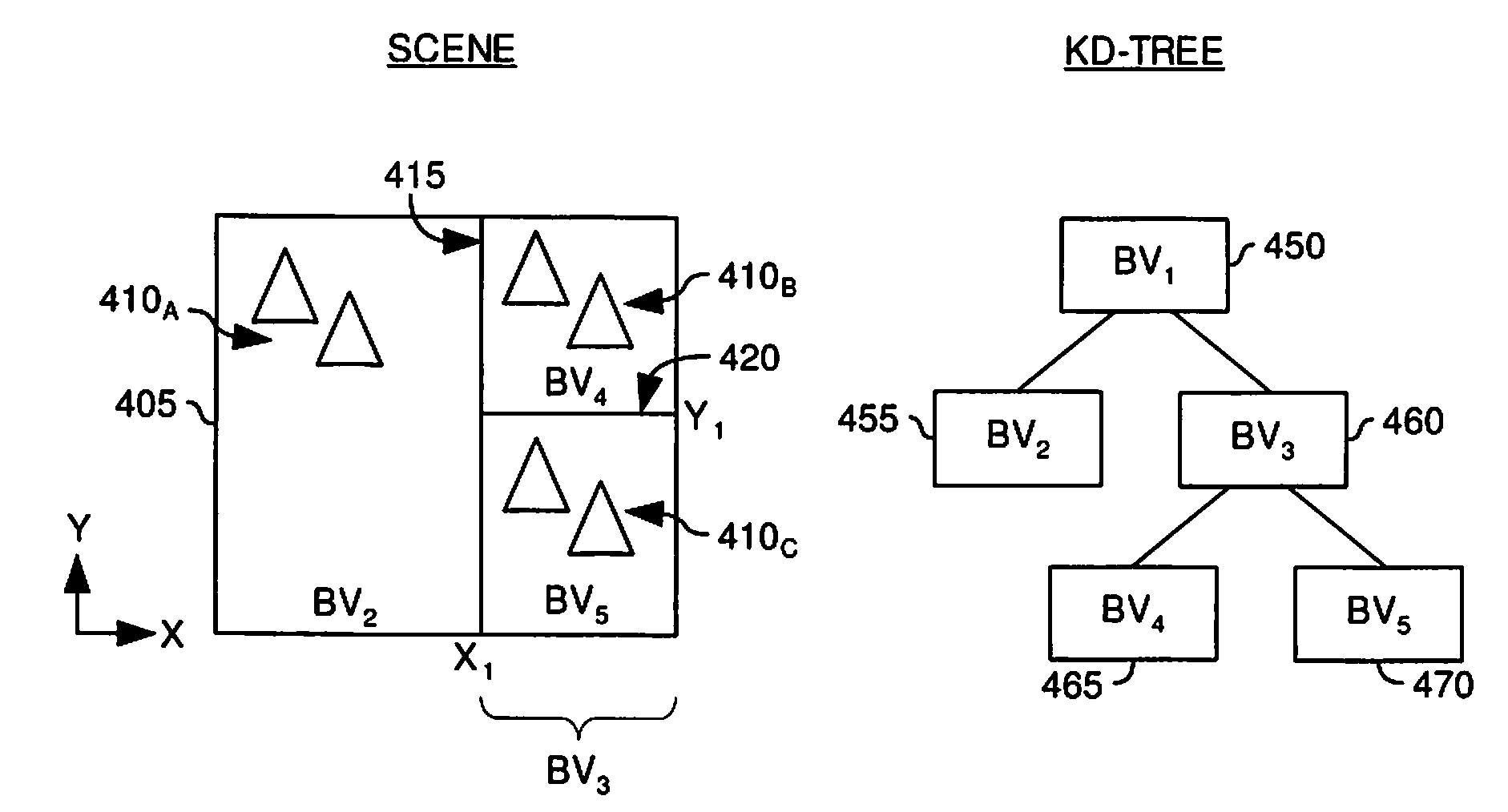
Cache Utilization Optimized Ray Traversal Algorithm with Minimized Memory Bandwidth Requirements
Embodiments of the invention provide methods and apparatus for recording the traversal history of a ray through a spatial index structure and utilizing the recorded traversal history. An image processing system may initially determine which nodes a ray intersects as it traverses through a spatial index. Results of the node intersection determinations may be recorded as the ray traverses the spatial index, and the recorded determinations may be associated with the ray. Furthermore, the image processing system may decide upon a traversal path based upon some probability of striking primitives corresponding to the nodes which make up the spatial index. This traversal path may also be recorded and associated with the ray. If the image processing system needs to re-traverse the spatial index at a later time, the recorded traversal history may be used to eliminate the need to recalculate ray-node intersections, and eliminate incorrect traversal path determinations.
Owner:IBM CORP
Recognition system using lexical trees
InactiveUS7035802B1Limited processing powerRecognition speed is fastDigital data information retrievalSpeech recognitionLexical itemTheoretical computer science
The dynamic programming technique employs a lexical tree that is encoded in computer memory as a flat representation in which the nodes of each generation occupy contiguous memory locations. The traversal algorithm employs a set of traversal rules whereby nodes of a given generation are processed before the parent nodes of that generation. The deepest child generation is processed first and traversal among nodes of each generation proceeds in the same topological direction.
Owner:PANASONIC CORP
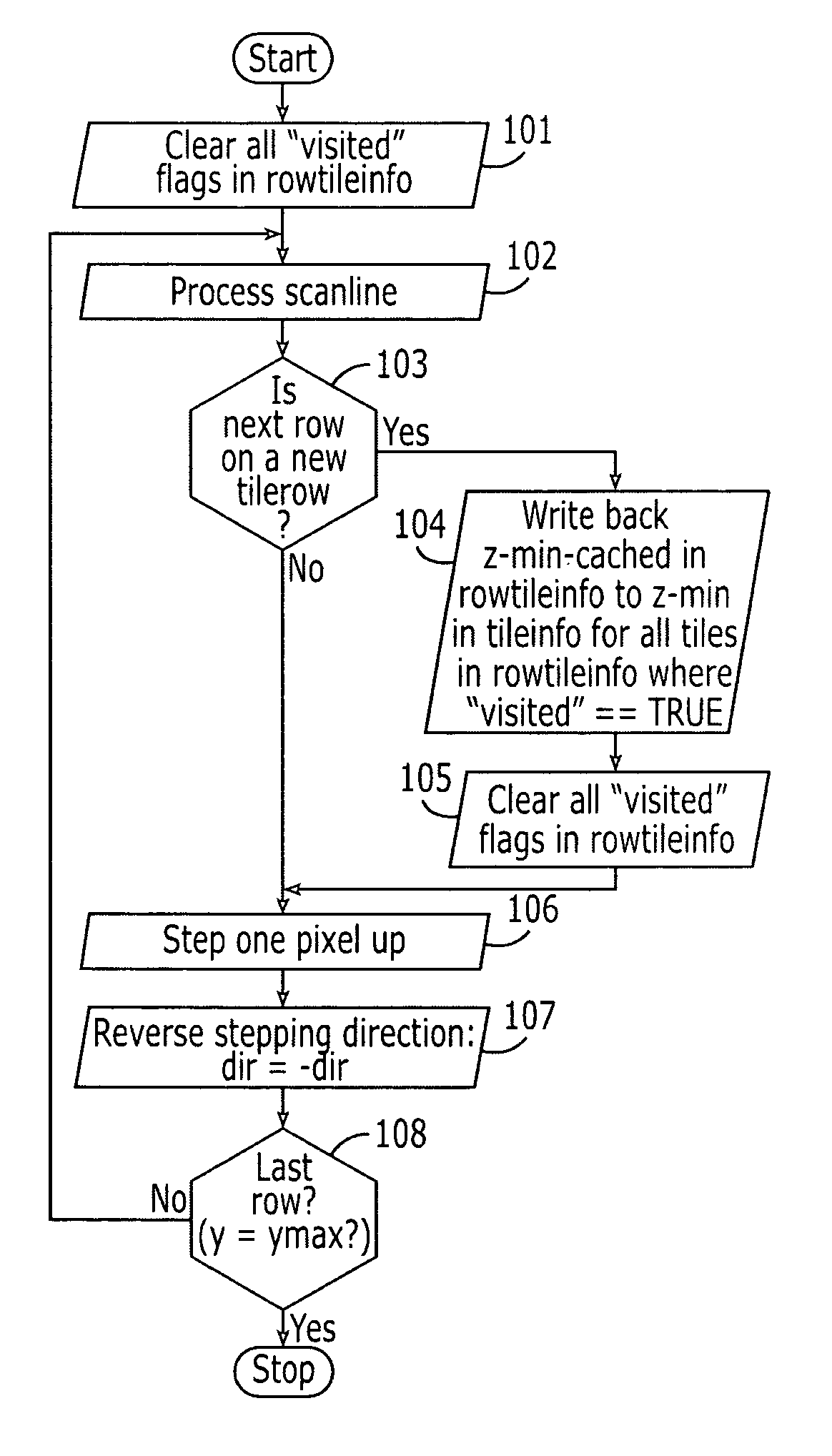
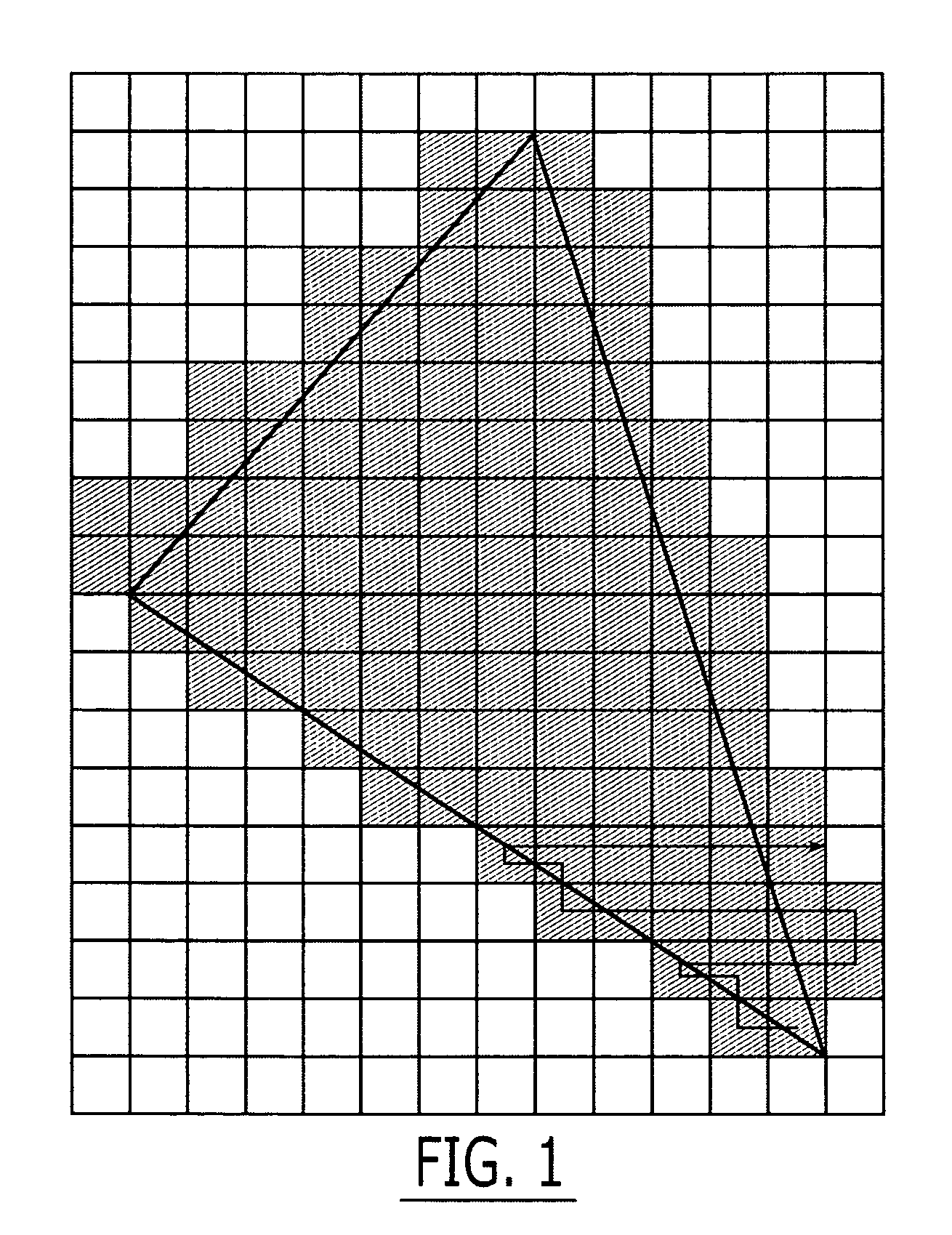
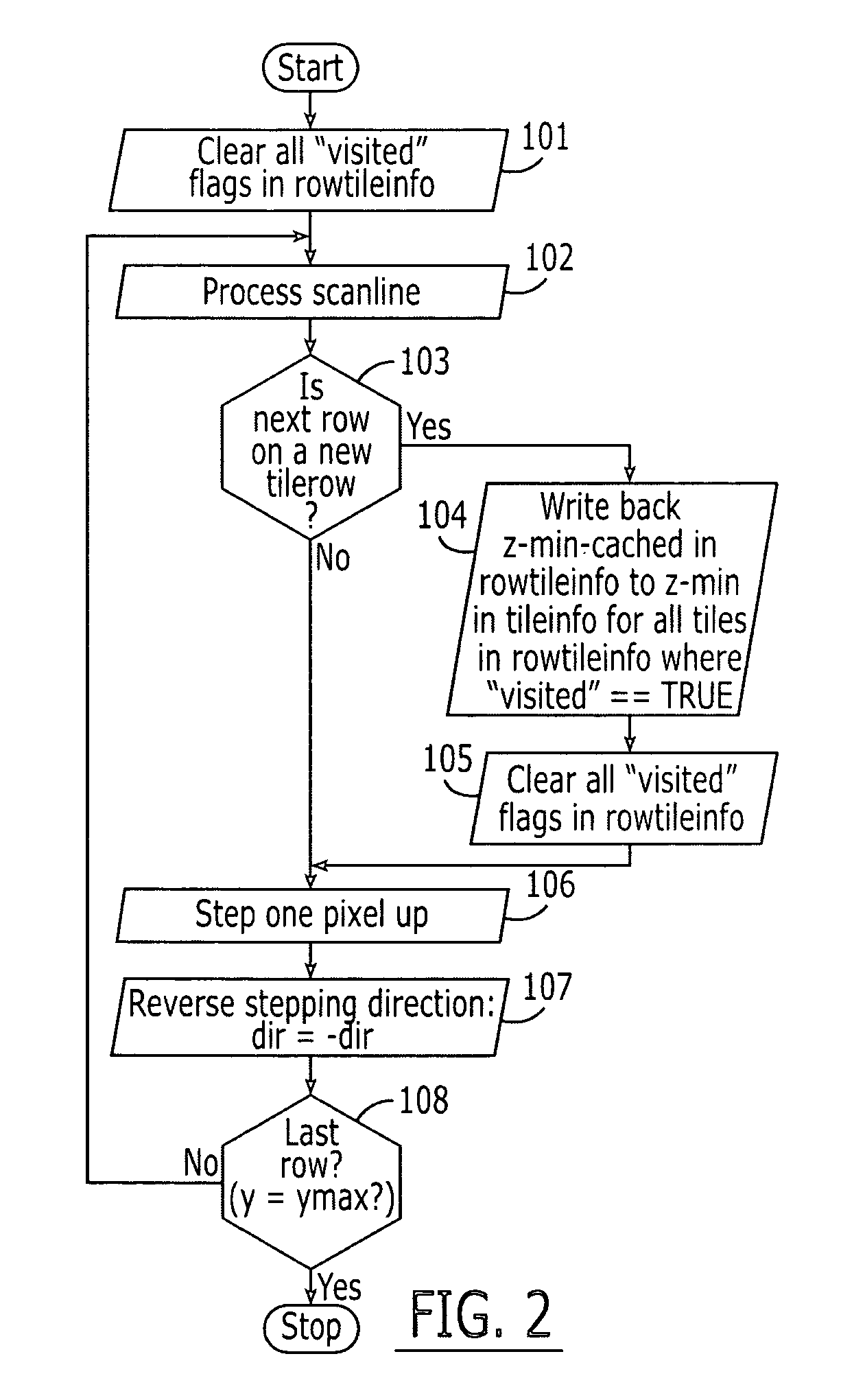
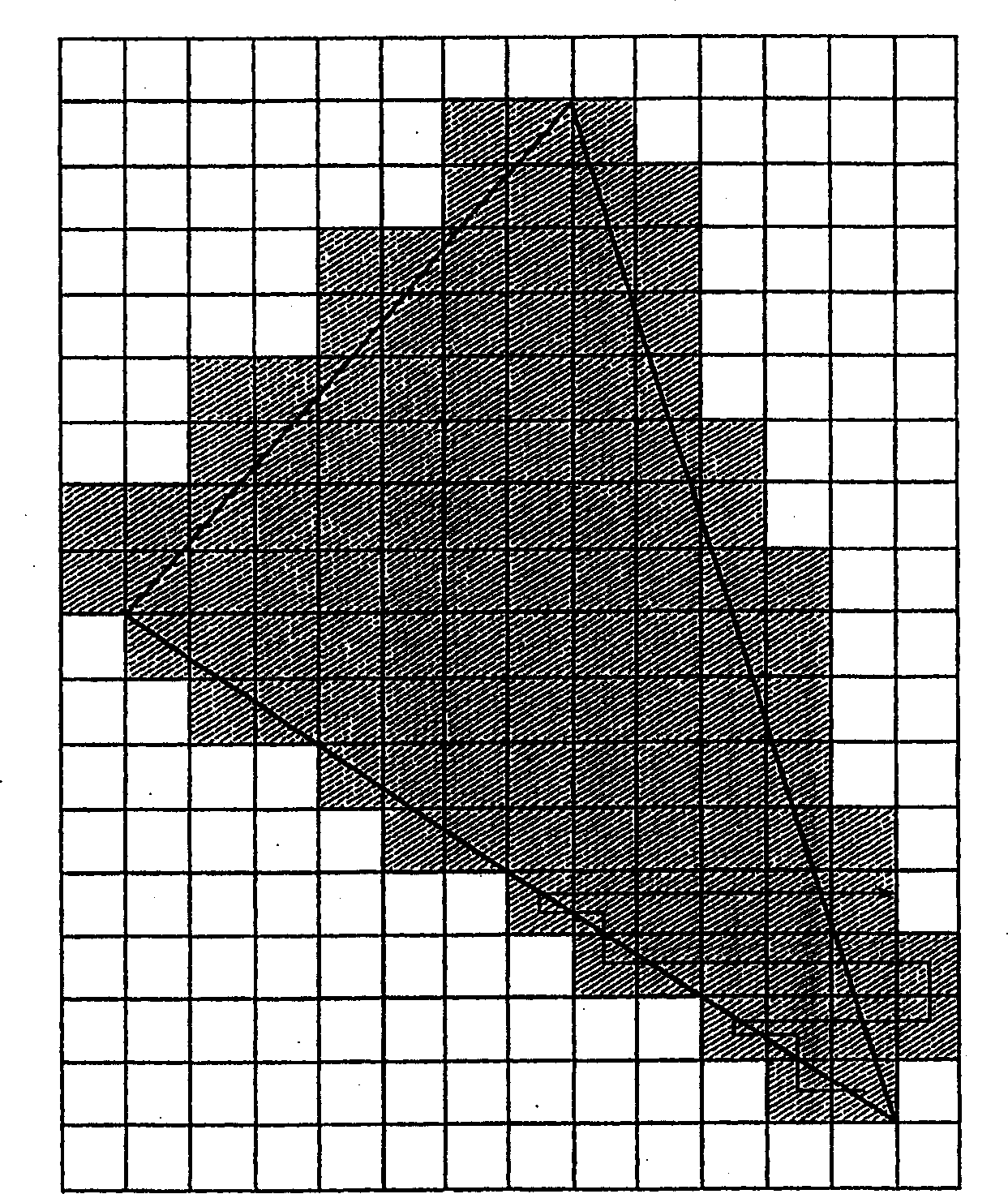
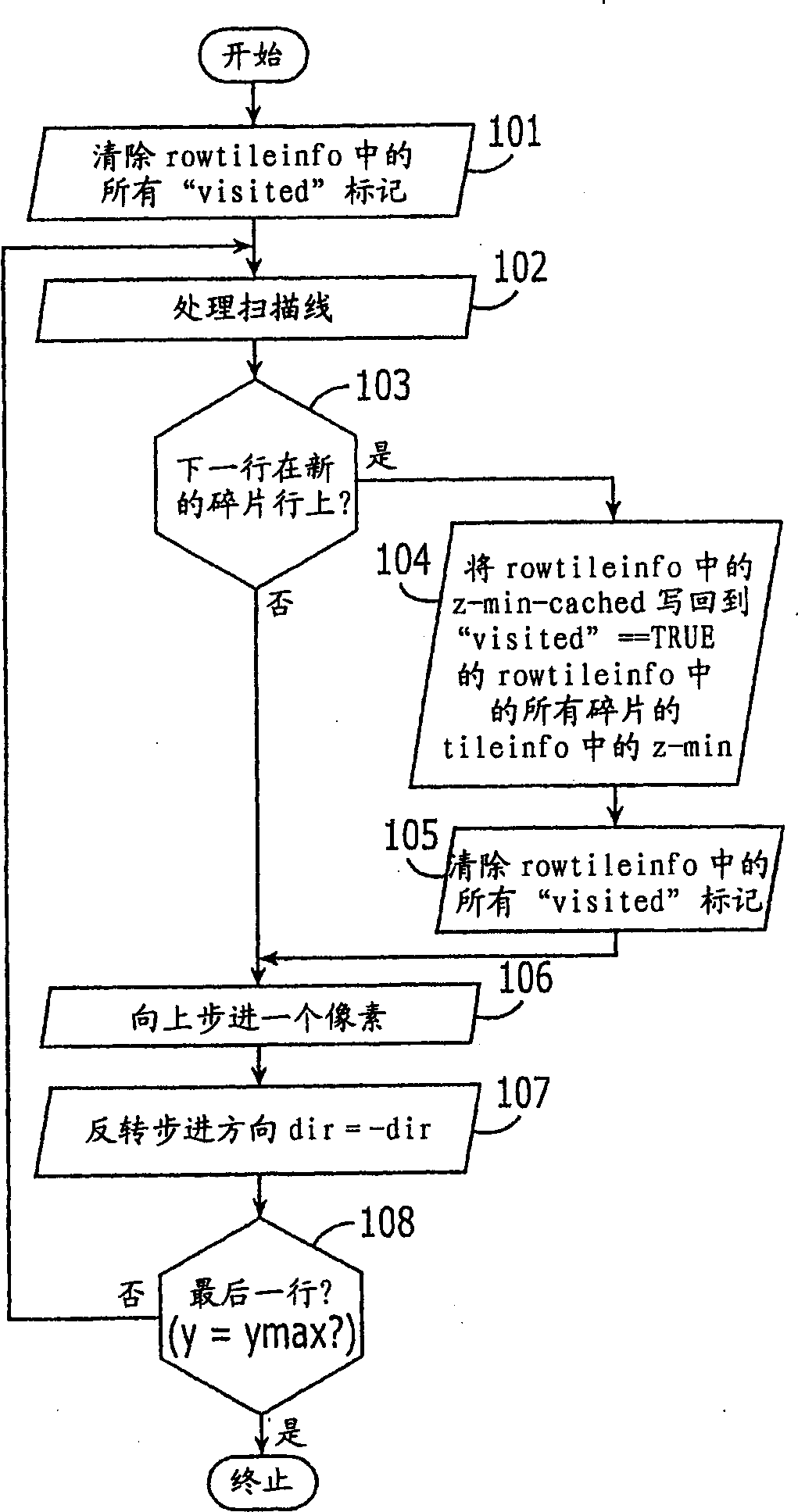
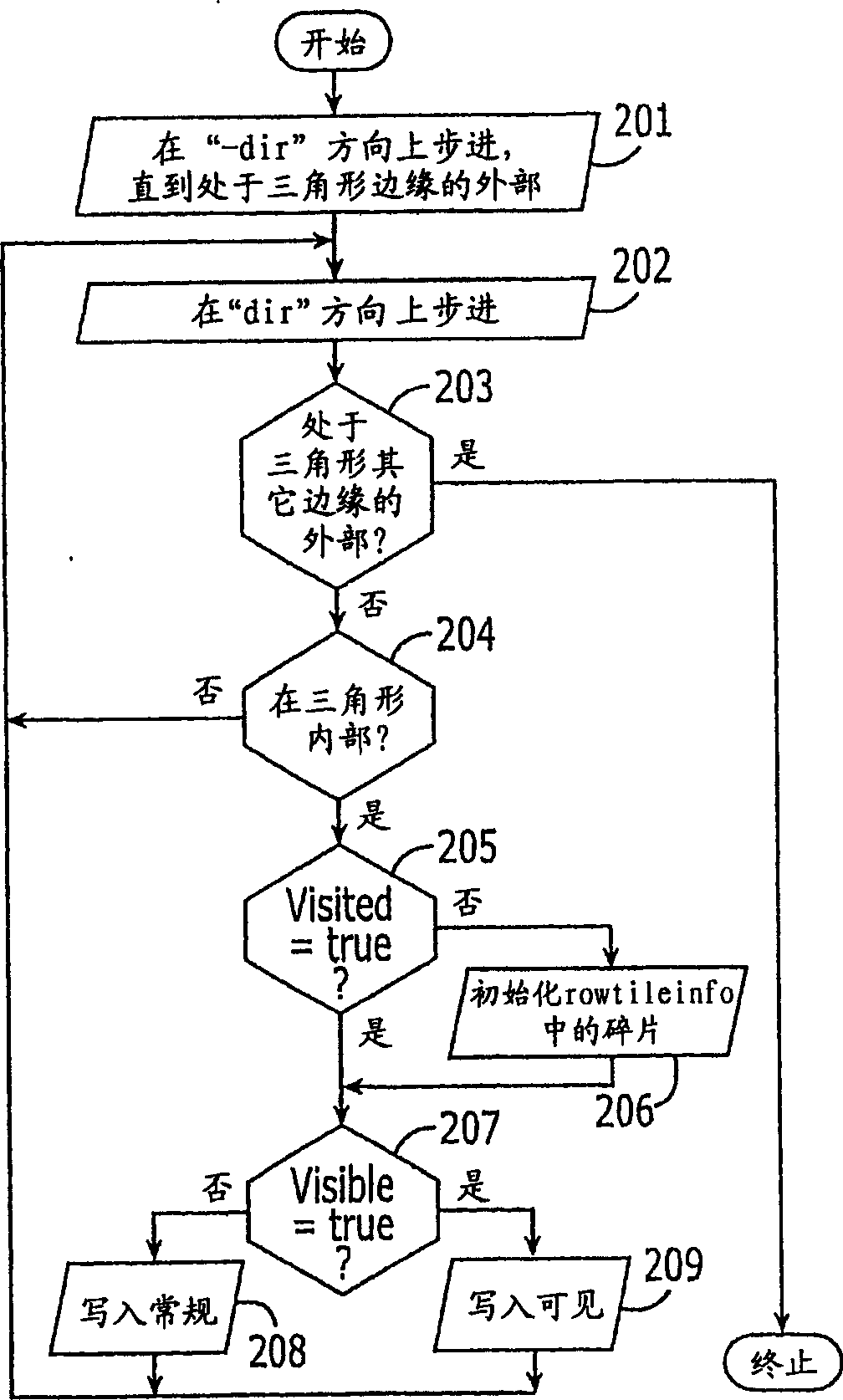
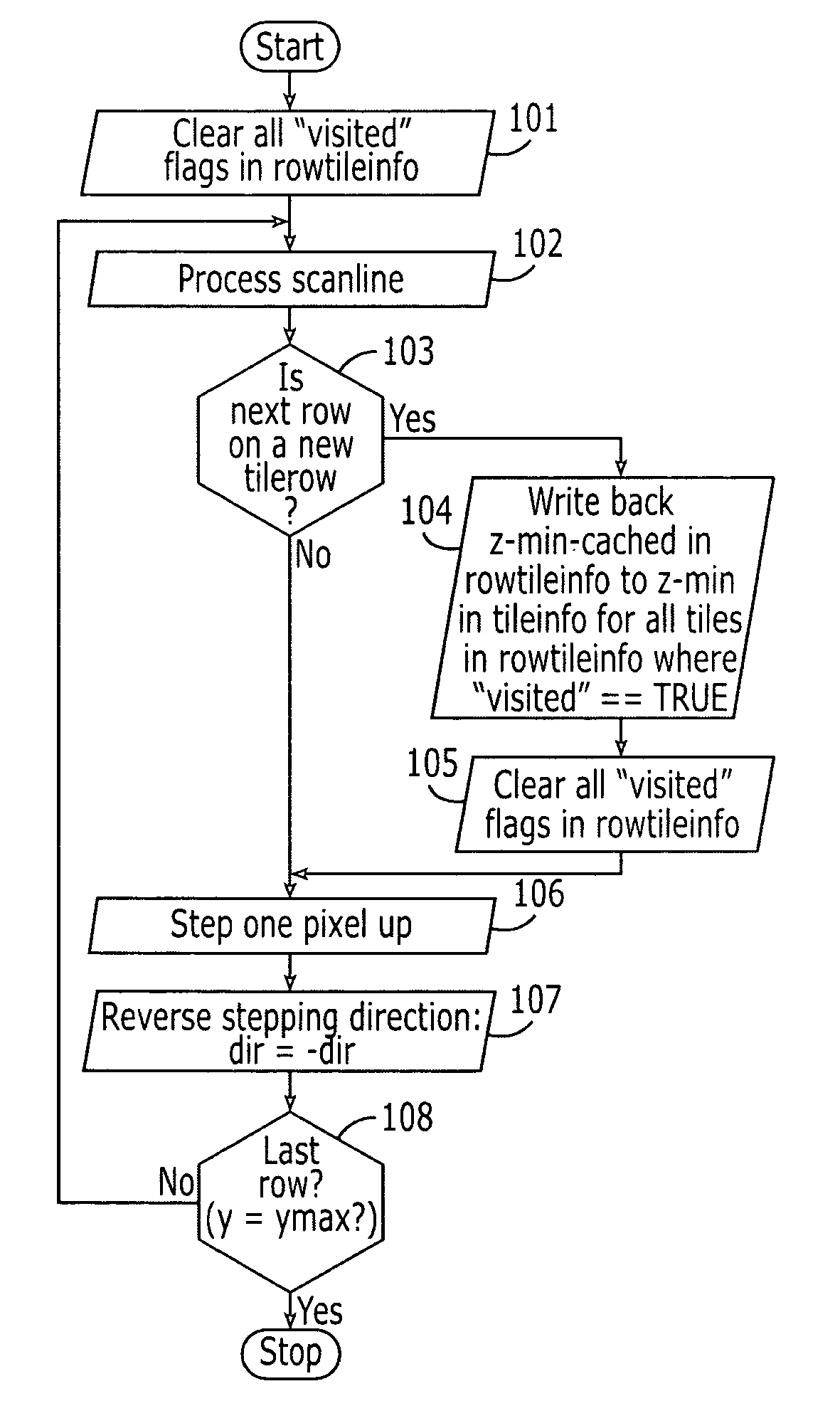
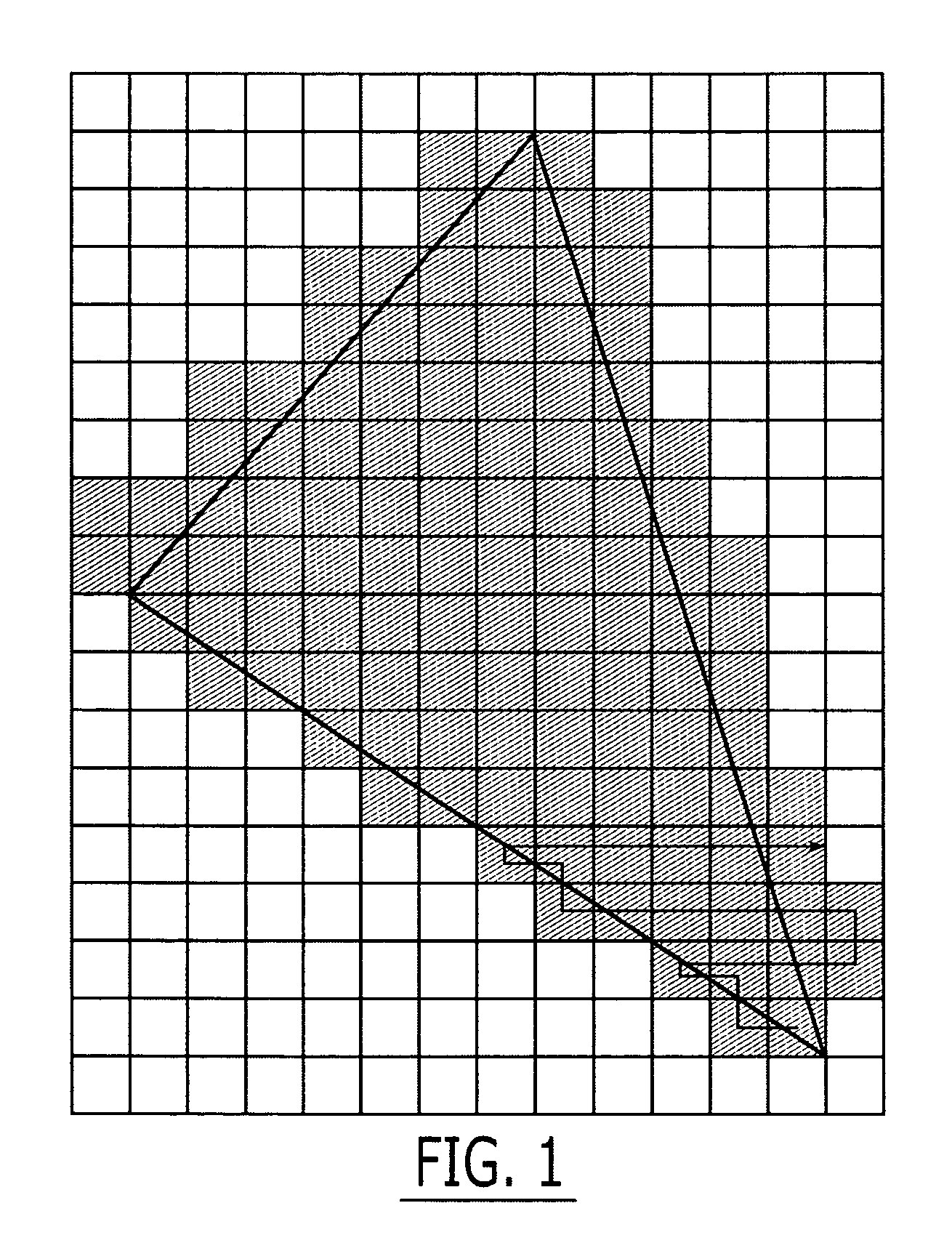
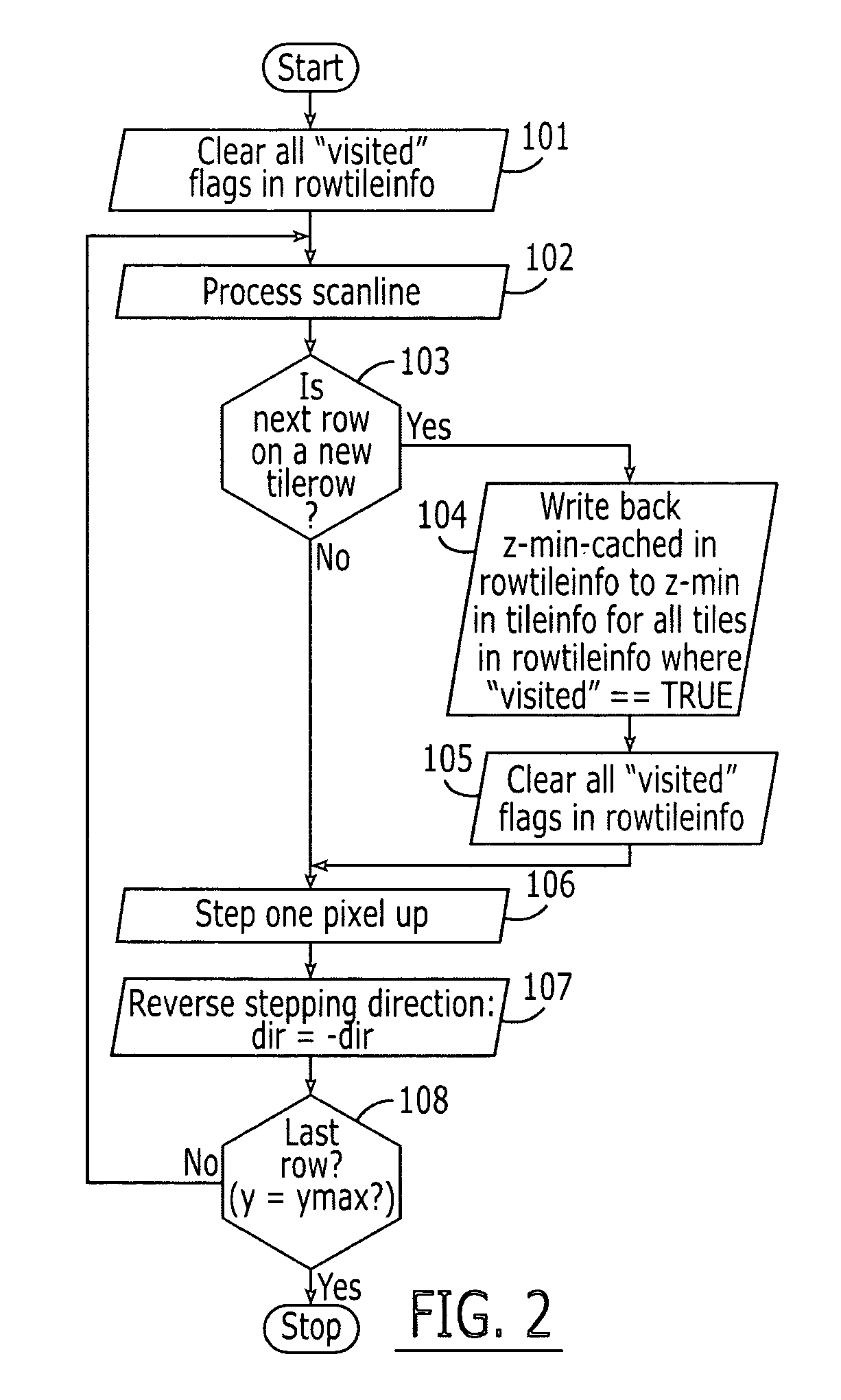
Graphics processing apparatus, methods and computer program products using minimum-depth occlusion culling and zig-zag traversal
A plurality of rows of tiles is defined in a graphics display field comprising a plurality of rows of pixels, each tile including pixels from at least two rows of pixels. Occlusion flags for respective tiles of a row of tiles for a graphics primitive are set based on whether respective representative depth values for the tiles of the row of tiles meet an occlusion criterion. Pixels in rows of pixels corresponding to the row of tiles are processed for the graphics primitive in a row-by-row manner responsive to the occlusion flags. The processing may include processing rows of pixels in the row of tiles using a zig-zag traversal algorithm.
Owner:TELEFON AB LM ERICSSON (PUBL)
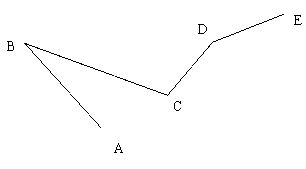
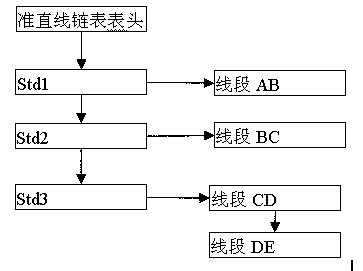
Method for planning velocity of S-shaped acceleration and deceleration control for control system of numerical control equipment
The invention discloses a method for planning the velocity of S-shaped acceleration and deceleration control for a control system of numerical control equipment. A 'collimation line' concept is introduced in the method and the method comprises the following steps: setting the parameters of a vectorial line segment are set; calculating the allowed velocity Vc of a collimation line according to theinput vectorial line segment; judging whether the collimation line conditions are reached or not, if so, producing one collimation line, and adding the produced collimation line into a collimation line linked list in sequence; after the collimation line linked list is fixed, respectively calculating the maximum velocity of each collimation line according to a traversal algorithm; and completing the collimation line interpolation task through a field programmable gate array (FPGA) program, distributing the pulses of the collimation lines to all the practical movement axes of an electronic gear, and converting digital information into electrical information for controlling the movement of a motor. The method has the beneficial effects that the method is applied to S-shaped acceleration deceleration control, so that shacking and collision which are generated because a machine is very heavy can be well avoided, the operation stability of the machine is improved, and the processing efficiency is increased. The solution idea of the collimation line is introduced. The data processing amount is effectively reduced, and the data processing capability is improved.
Owner:成都乐创自动化技术股份有限公司
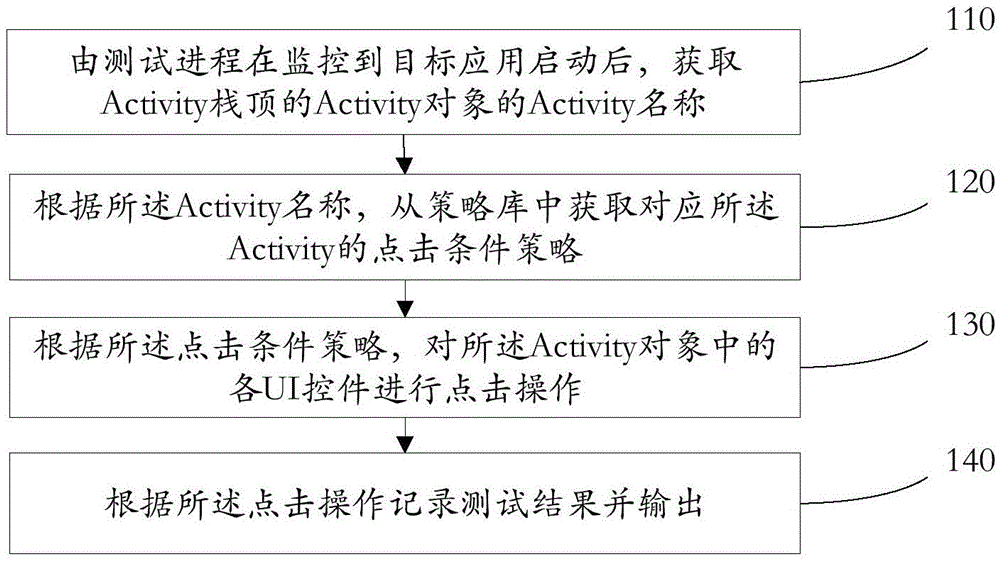
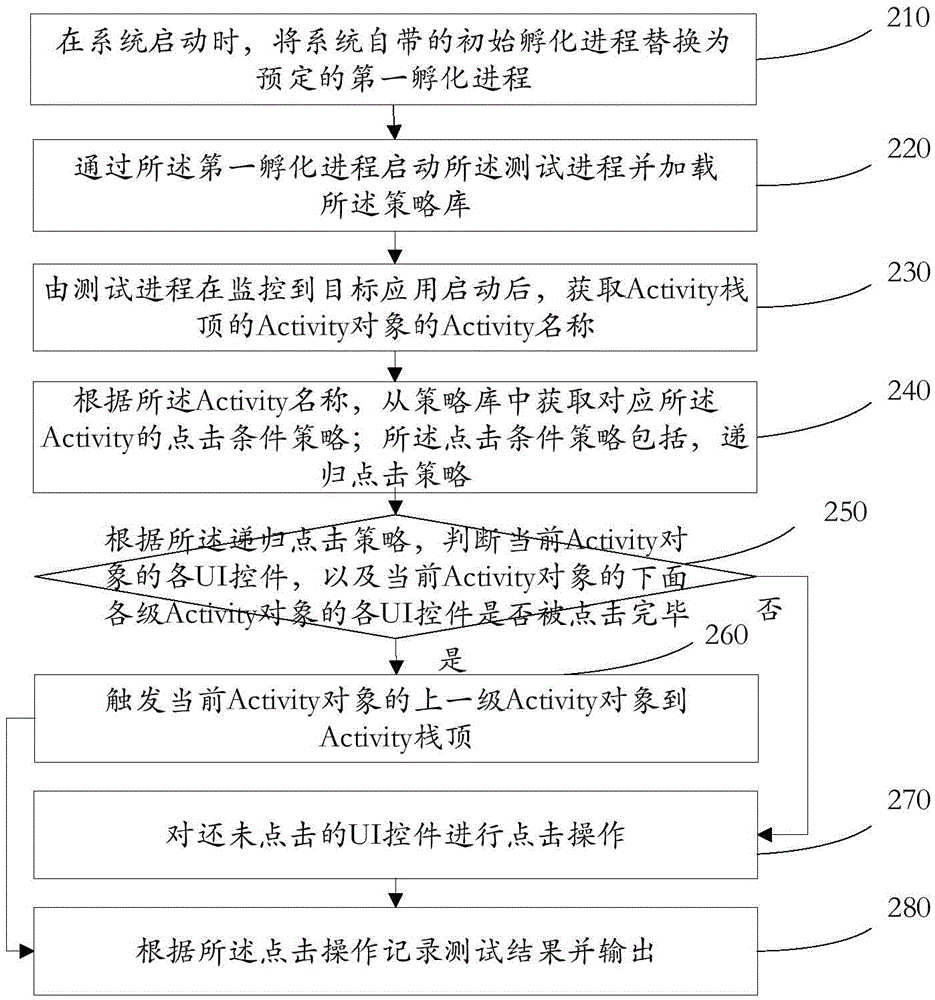
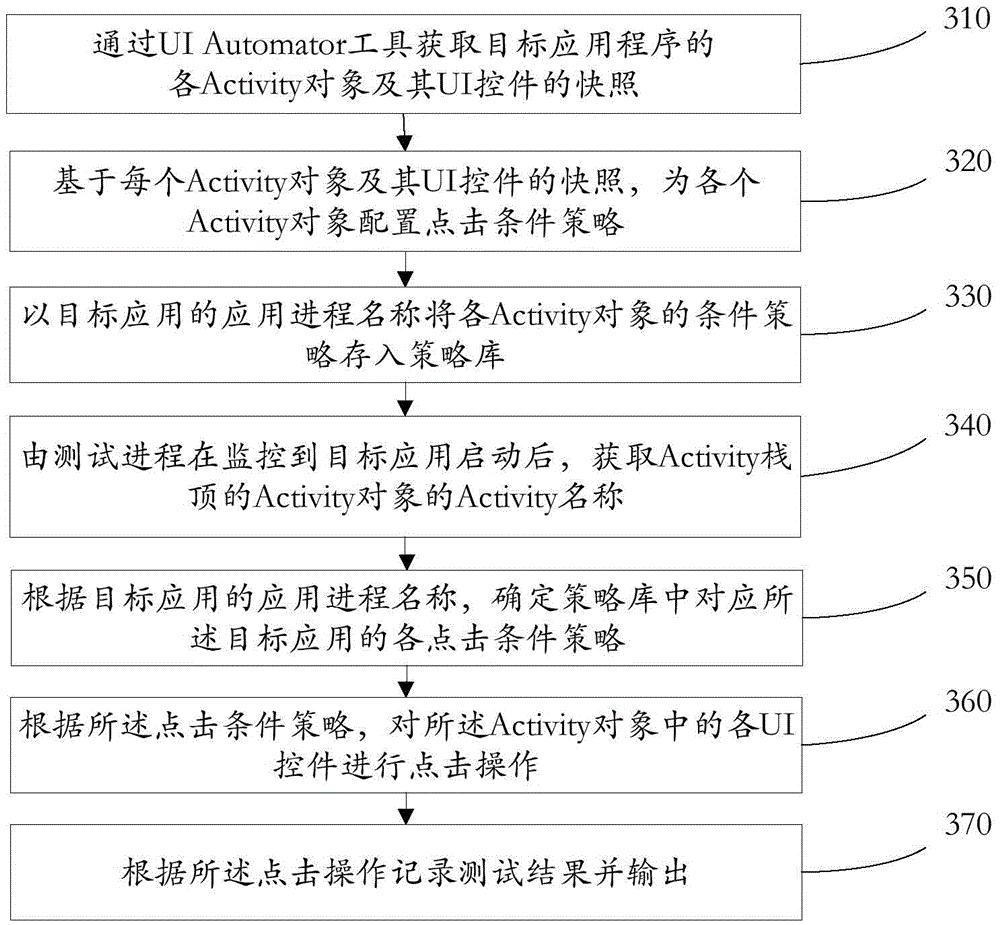
Accurate traversal method and apparatus for UI controls of android application
ActiveCN105468529AImprove applicabilityEasy to detectSoftware testing/debuggingTraversal algorithmsOperating system
An embodiment of the invention provides an accurate traversal method and apparatus for UI controls of an android application, and relates to the technical field of computers. The method comprises: after it is monitored that a target application is started by a test process, obtaining an Activity name of an Activity object of an Activity stack top; according to the Activity name, obtaining a click condition policy corresponding to an Activity from a policy library; according to the click condition policy, performing click operation on each UI control in the Activity object; and according to the click operation, recording and outputting a test result. According to the accurate traversal method and apparatus, the problem of relatively low active intervention degree of a user caused by low applicability, random disordered UI clicking, relatively poor functional detection capability and no test policy setting of a conventional traversal algorithm is solved, and the beneficial effects of improving the applicability due to capability of performing traversal operation on all applications in an Android system and improving manual intervention level and functional detection capability due to capability of manually presetting a UI clicking scheme are achieved.
Owner:BEIJING QIHOO TECH CO LTD
Computer-implemented system and method for designing a fire protection system
A computer-implemented system for designing a fire protection and / or piping system comprising a personal computer for loading programs into dynamic memory and storing data on a static memory device, means for providing user input, and program files comprising a process algorithm, traversing algorithm, and tagging algorithm. The process algorithm performs data validation, error checking and error resolution, saves data to a start point inserted by a user, pulls layer details into programming variables, applies processing logic to the system, and comprises a main pipes algorithm and a branch resizing algorithm. The traversing algorithm travels the system and presents objects to the process, main pipes and branch resizing algorithms in a logical order. The tagging algorithm attaches to each pipe in the system a tag with property set data pulled into and displayed in the tag. A method of using the foregoing system to design a fire protection and / or piping system.
Owner:RAEL AUTOMATIC SPRINKLER COMPANY
Graphics processing apparatus, methods and computer program products using minimum-depth occlusion culling and zig-zag traversal
A plurality of rows of tiles is defined in a graphics display field comprising a plurality of rows of pixels, each tile including pixels from at least two rows of pixels. Occlusion flags for respective tiles of a row of tiles for a graphics primitive are set based on whether respective representative depth values for the tiles of the row of tiles meet an occlusion criterion. Pixels in rows of pixels corresponding to the row of tiles are processed for the graphics primitive in a row-by-row manner responsive to the occlusion flags. The processing may include processing rows of pixels in the row of tiles using a zig-zag traversal algorithm.
Owner:TELEFON AB LM ERICSSON (PUBL)
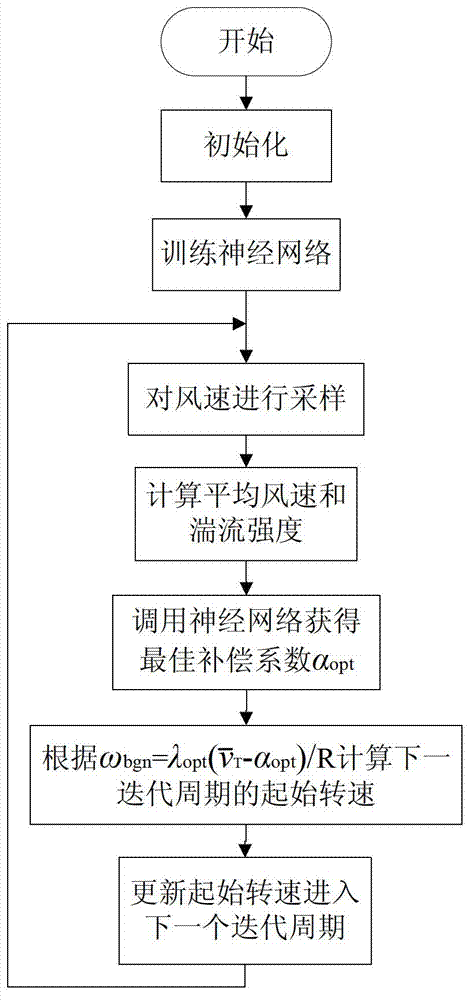
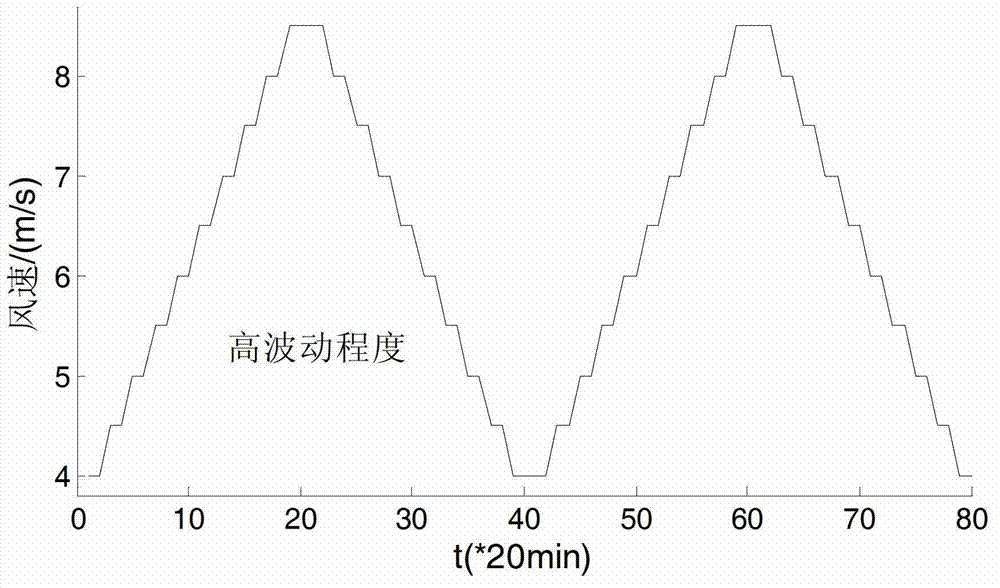
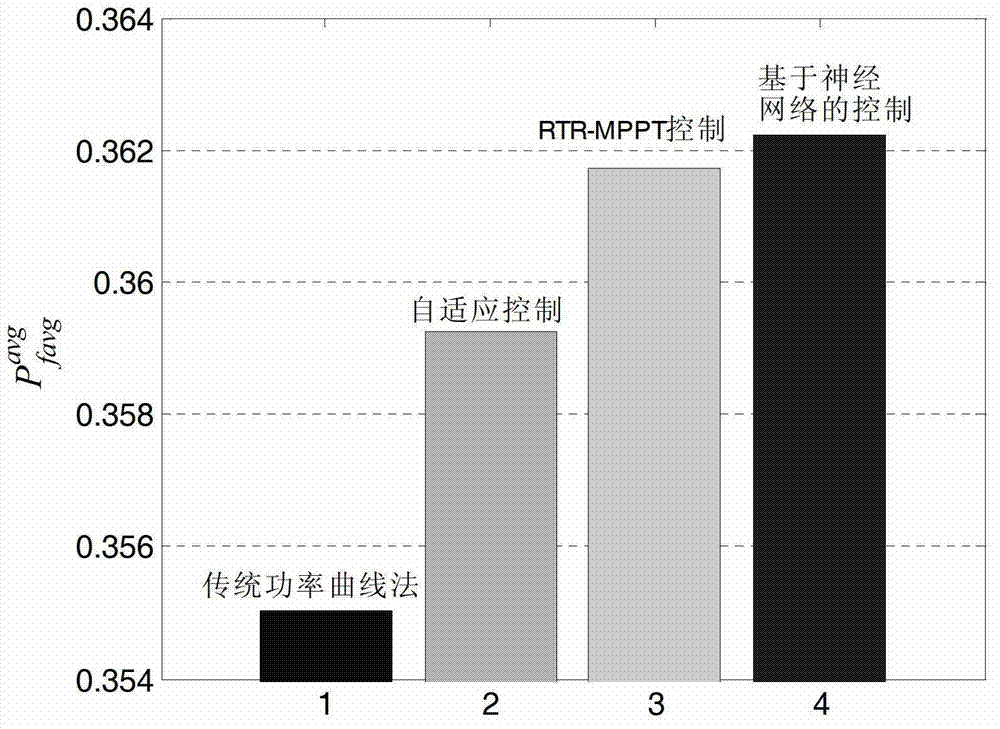
Maximum power point tracing control method based on neural network optimization starting rotating speed
ActiveCN103835878AImprove capture efficiencyEasy to trackWind motor controlMachines/enginesSimulationControl theory
The invention provides a maximum power point tracing control method based on the neural network optimization starting rotating speed. According to the method, on the basis of an existing MPPT control method, a neural network is adopted to obtain the best starting generator rotating speed according to wind speed condition dynamic optimization compensation factors, and then wind energy capture efficiency is further improved. The adopted neural network takes the average wind speed and turbulence intensity as input, and takes the best compensation factor as output. Mass draining data obtained through the traversal algorithm are used for training the neural network, the trained neural network is adopted for obtaining the corresponding best compensation factor through calculation according to the changed wind speed conditions, and then the best compensation factor is used for optimizing the starting generator rotating sped, so that the best MPPT tracking interval is obtained, and the wind energy capture efficiency is further improved. Compared with various traditional MPPT control methods, the effectiveness and superiority of the algorithm are verified.
Owner:NANJING UNIV OF SCI & TECH
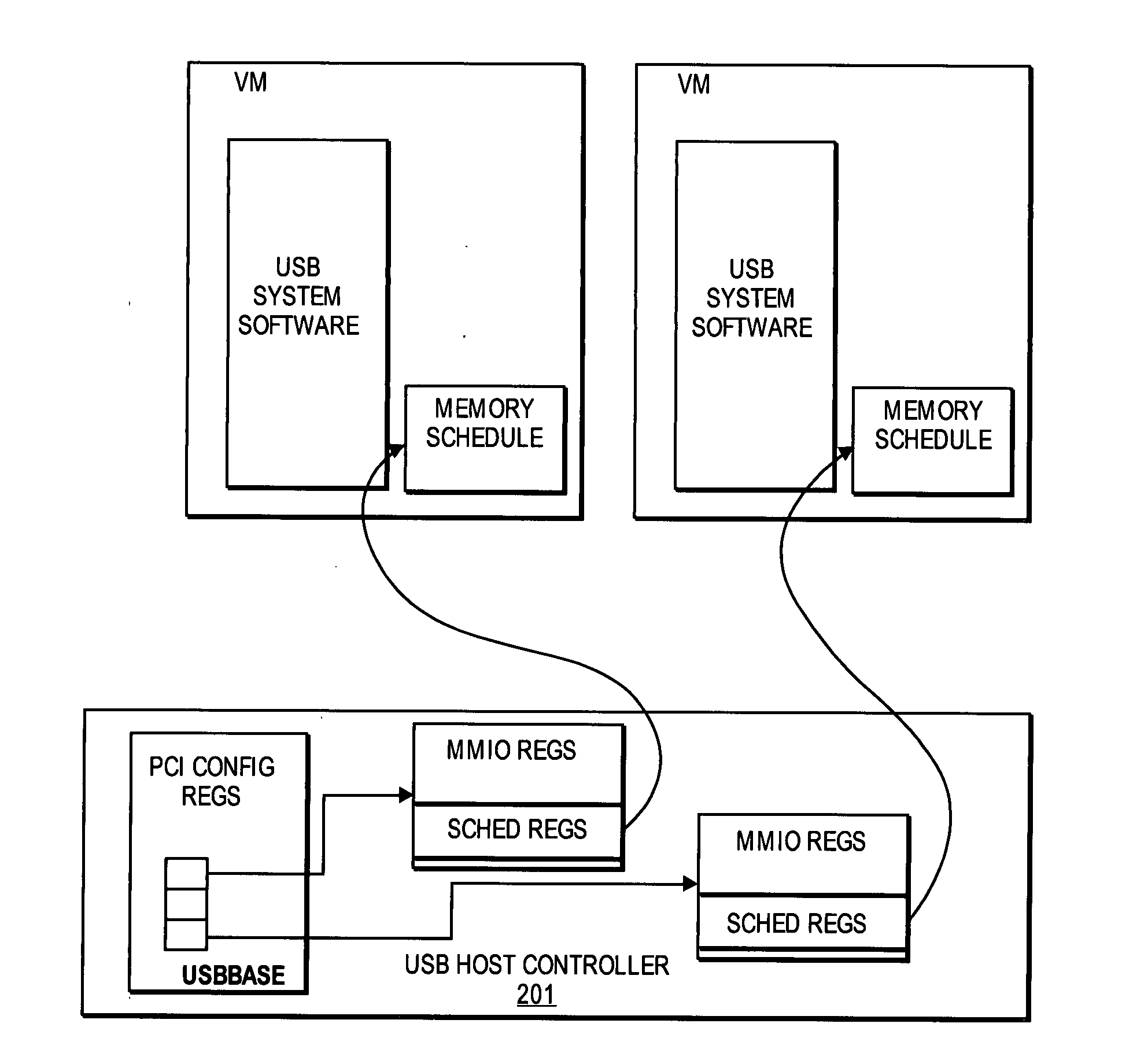
Method and system for replicating schedules for virtualization
ActiveUS20070044100A1Multiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationProgram planning
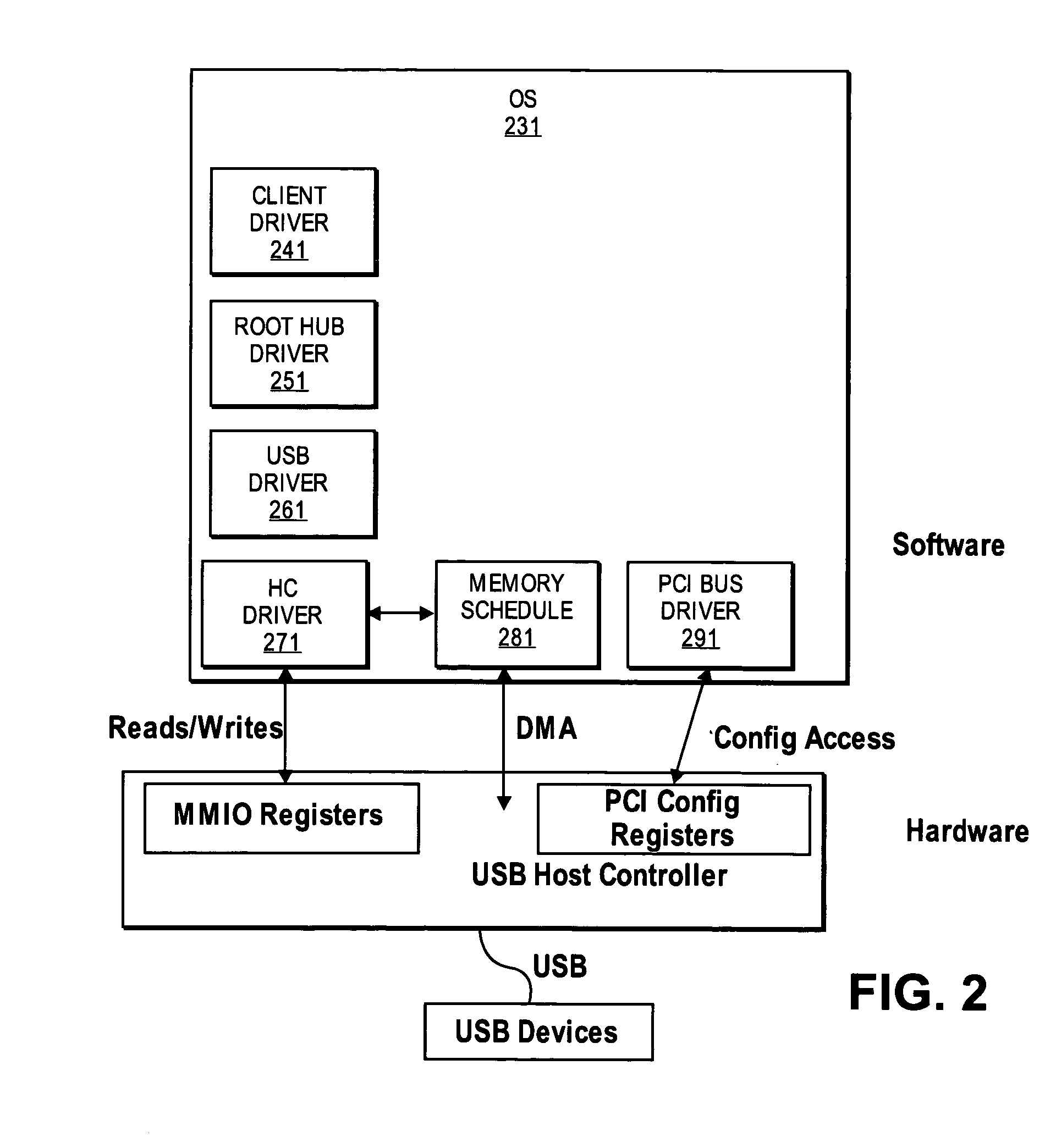
A discussion for improving USB device virtualization by giving virtual machines (VMs) direct access to USB devices with a combined hardware and software solution, including providing a set of PCI configuration registers and operational registers for each VM, providing an interrupt request line for each VM, and using a new schedule traversal algorithm for multiple schedules, including a fairness algorithm that prevents starvation of any VM's bulk traffic.
Owner:INTEL CORP
Embedded software testing method based on AADL (Architecture Analysis and Design Language) mode transformation relationship
InactiveCN102053910ASolve the "Oracle problemGuaranteed reliabilitySoftware testing/debuggingSoftware designMetamorphic testing
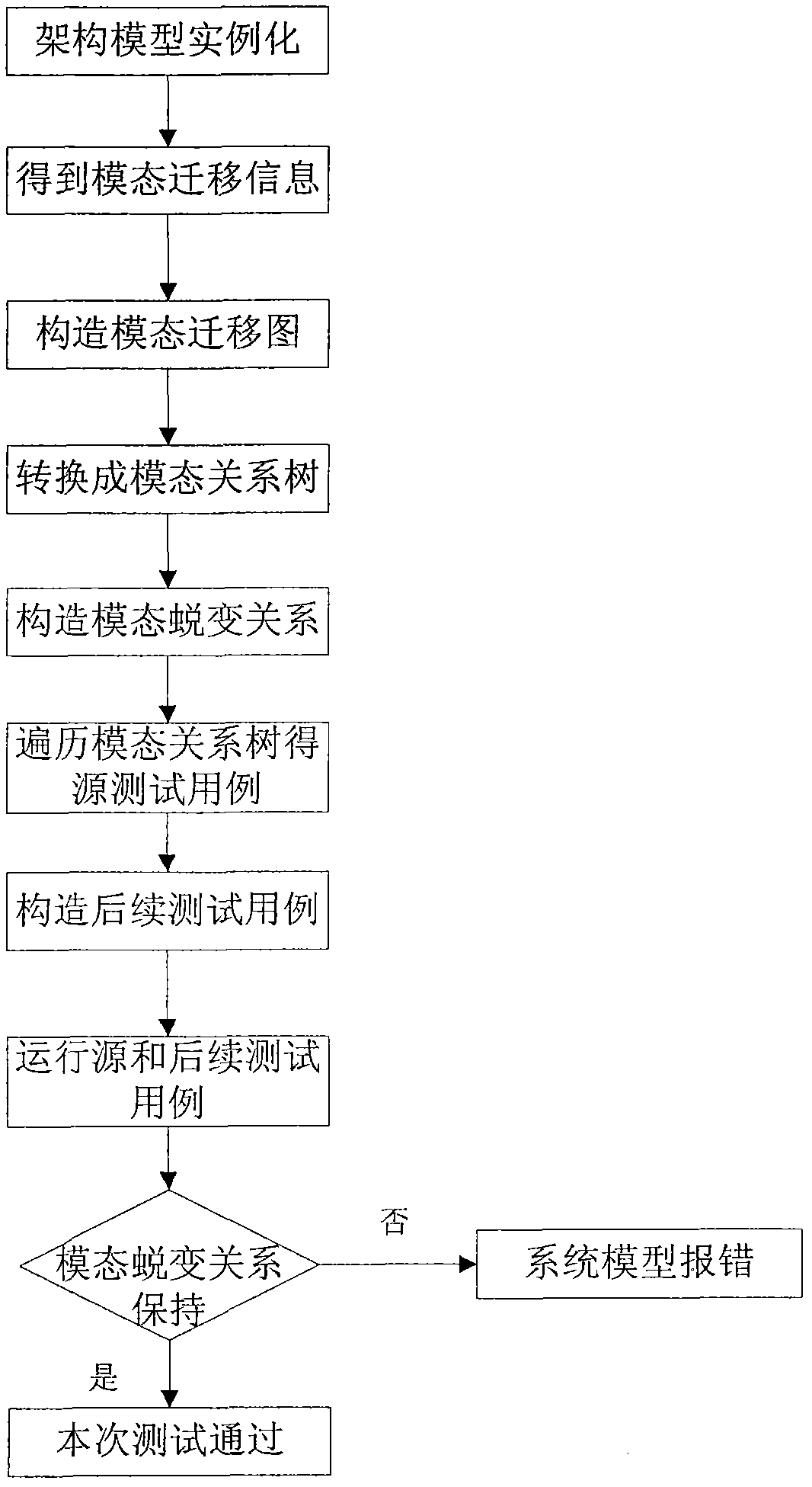
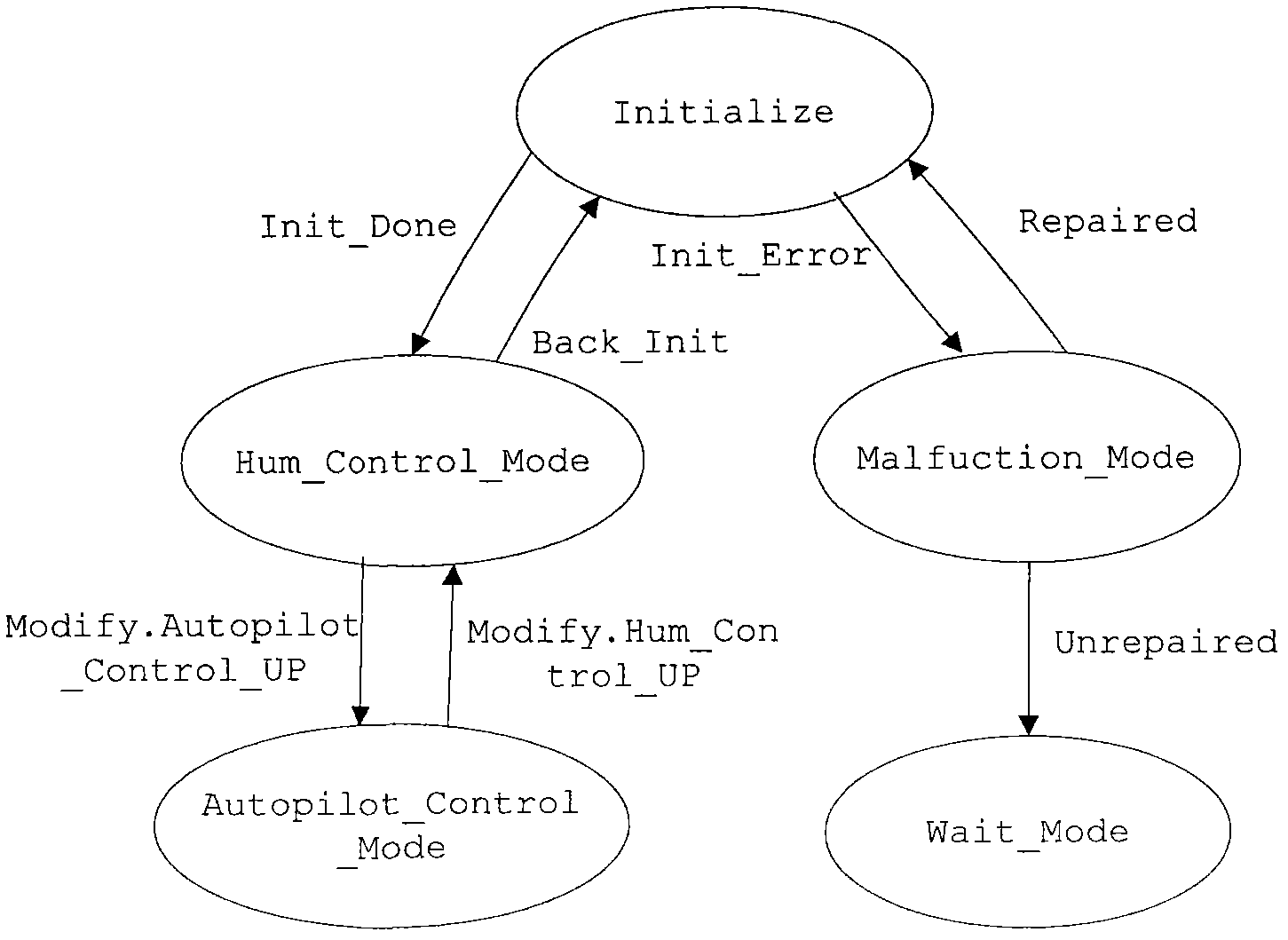
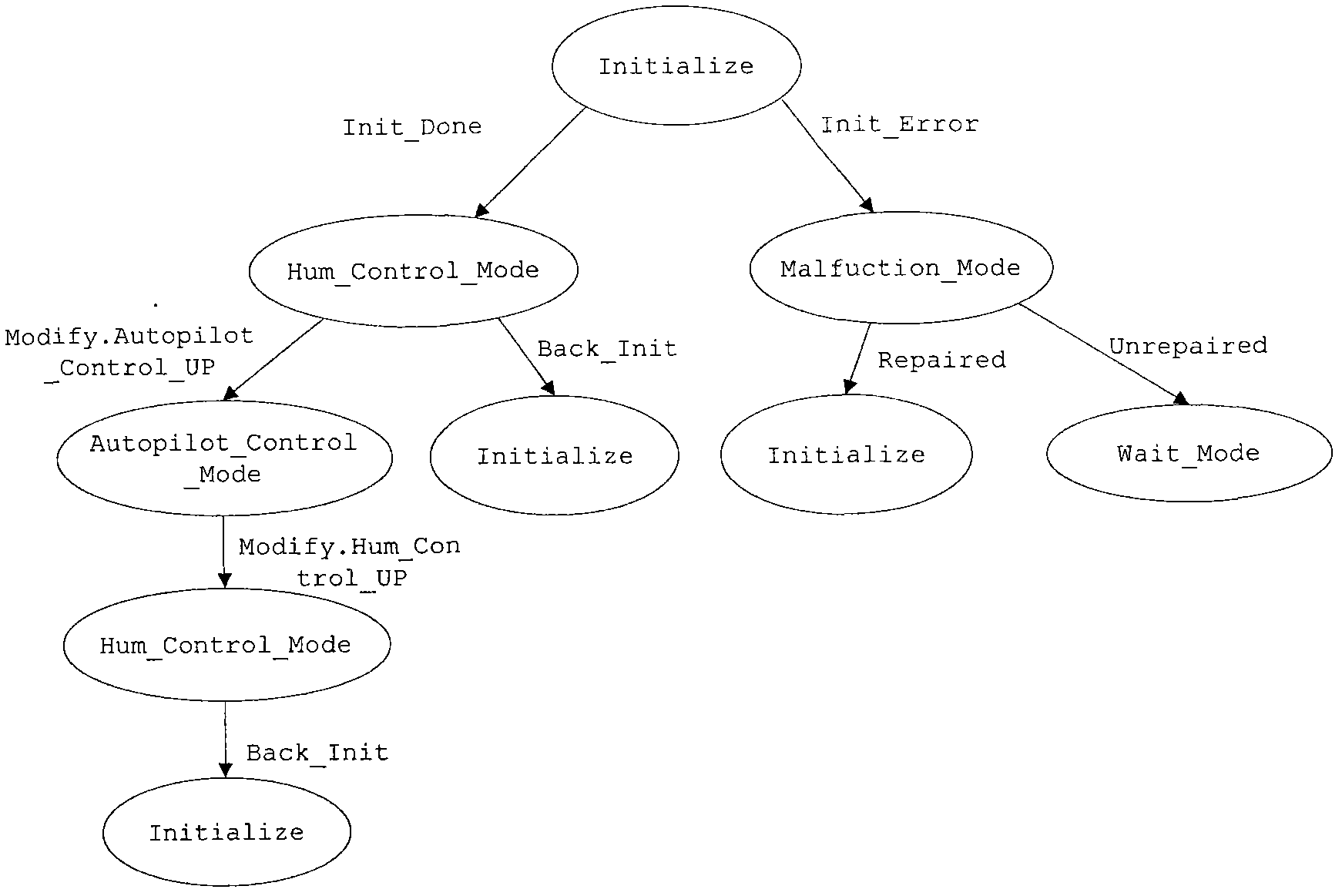
The invention relates to an embedded software testing method based on AADL (Architecture Analysis and Design Language) mode transformation relationship, which has the following steps of: constructing a mode transition diagram on the basis of mode information in an AADL model, and converting the diagram into a mode relationship tree required by a transformation test according to the improved depth-first traversing algorithm; constructing a source test case in the mode transformation relationship by traversing the mode relationship tree, generating a subsequent test case by means of the mode transformation relationship in the AADL model, and verifying the mode transformation relationship to obtain the conclusion of the transformation test. The embedded software testing method based on AADL mode transformation relationship solves the 'Oracle' problem existing in the embedded software test, is convenient for a user to test the embedded software at an early stage of software design and ensures the reliability of software at a system architecture level. If the model architecture can not meet corresponding requirements, the architecture of the software can be modified at an early stage of development, thus the development cost is saved, and meanwhile, the development cycle can also be shortened.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Key transmission section identification-based cascading failure analysis method for alternating current/direct current power network
The invention provides a key transmission section identification-based cascading failure analysis method for an alternating current / direct current power network. The method comprises the following steps: (A) searching all transmission sections between a direct current transmitting end and a direct current receiving end by a graph theory-based transmission section traversal algorithm, forming a node set S0={vS} from a node vS of the direct current transmitting end, searching all cut sets of branches between S0 and the adjacent point thereof, and finishing traversal searching in a manner of expanding the node set S0 outwards step by step; (B) further identifying key transmission sections which can cause a relatively large cascading failure risk by indexes of a power flow transfer coefficient and section maximum overload rate; and (C) giving cascading failure sets with relatively large risks and key branches which should be mainly monitored in the key transmission sections through transient stability calculation. By the method provided by the invention, the key transmission sections and the key braches, which are prone to cascading failures after a direct current monopole is locked can be effectively determined.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
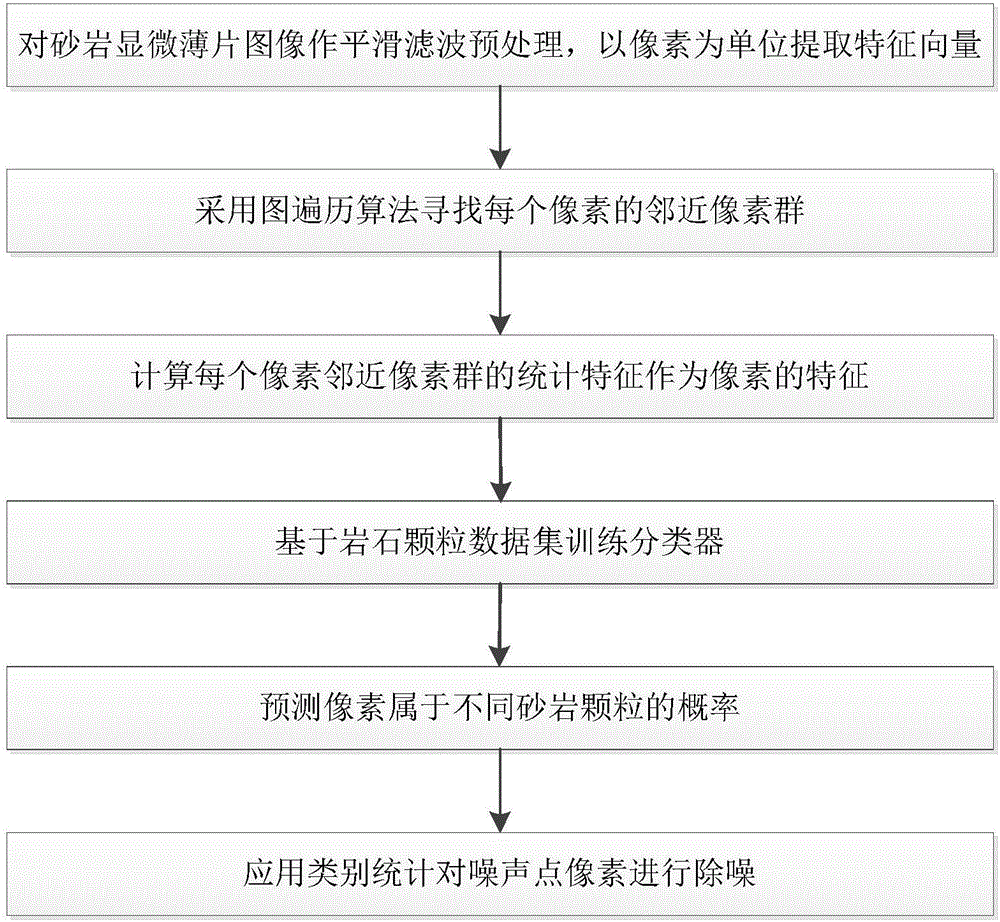
Automatic recognition method for rock particles in sandstone microsection
ActiveCN106485223ARealize automatic identificationShorten the timeCharacter and pattern recognitionForeign matterData set
The invention discloses an automatic recognition method for rock particles in a sandstone microsection, and the method comprises the steps: 1), carrying out the smoothing filtering preprocessing of the inputted sandstone microsection, extracting the pixel color and texture features, and forming a characteristic vector of pixel similarity measure; 2), searching an adjacent pixel group of each pixel through an image traversal algorithm and a similarity measurement method; 3), calculating the statistical characteristics of the adjacent pixel group, and enabling the statistical characteristics to serve as the characteristic vector of the pixels; 4), training a logic regression classifier based on a rock particle sample data set; 5), predicting the probability that each pixel belongs to quartz, feldspar or rock debris, and determining a noise point; 6), carrying out the processing of the noise point, and determining the dividing and classification of the rock particles. The method employs the image processing technology and a machine learning method, automatically recognizes the rock particles in the sandstone microsection, can solve the positioning of the boundary of a rock particle region and the recognition of foreign matters in the rock particles, is higher in accuracy, and reduces the recognition time and cost of rock particles. The method has application values for mineral discrimination and oil-gas exploration.
Owner:NANJING UNIV
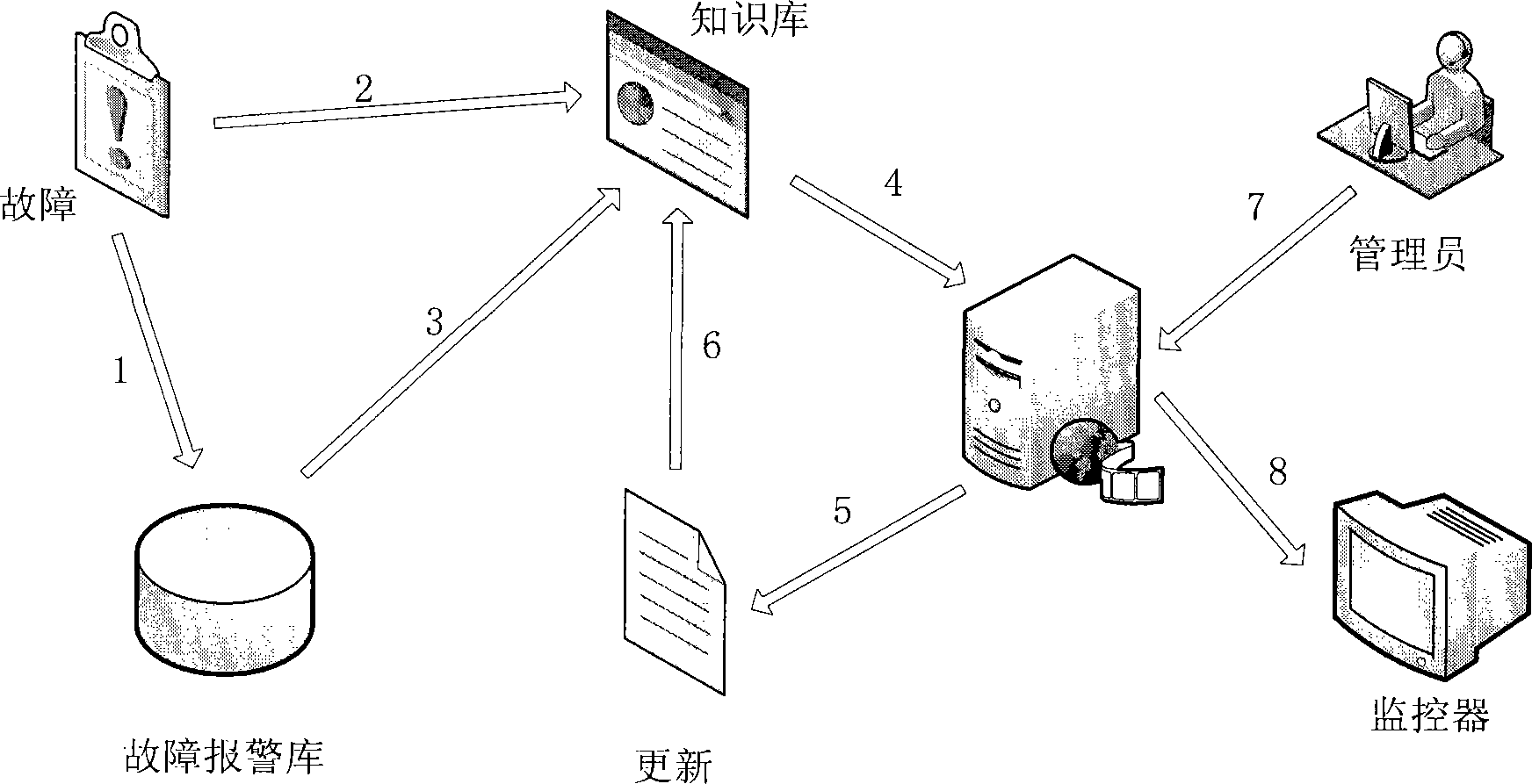
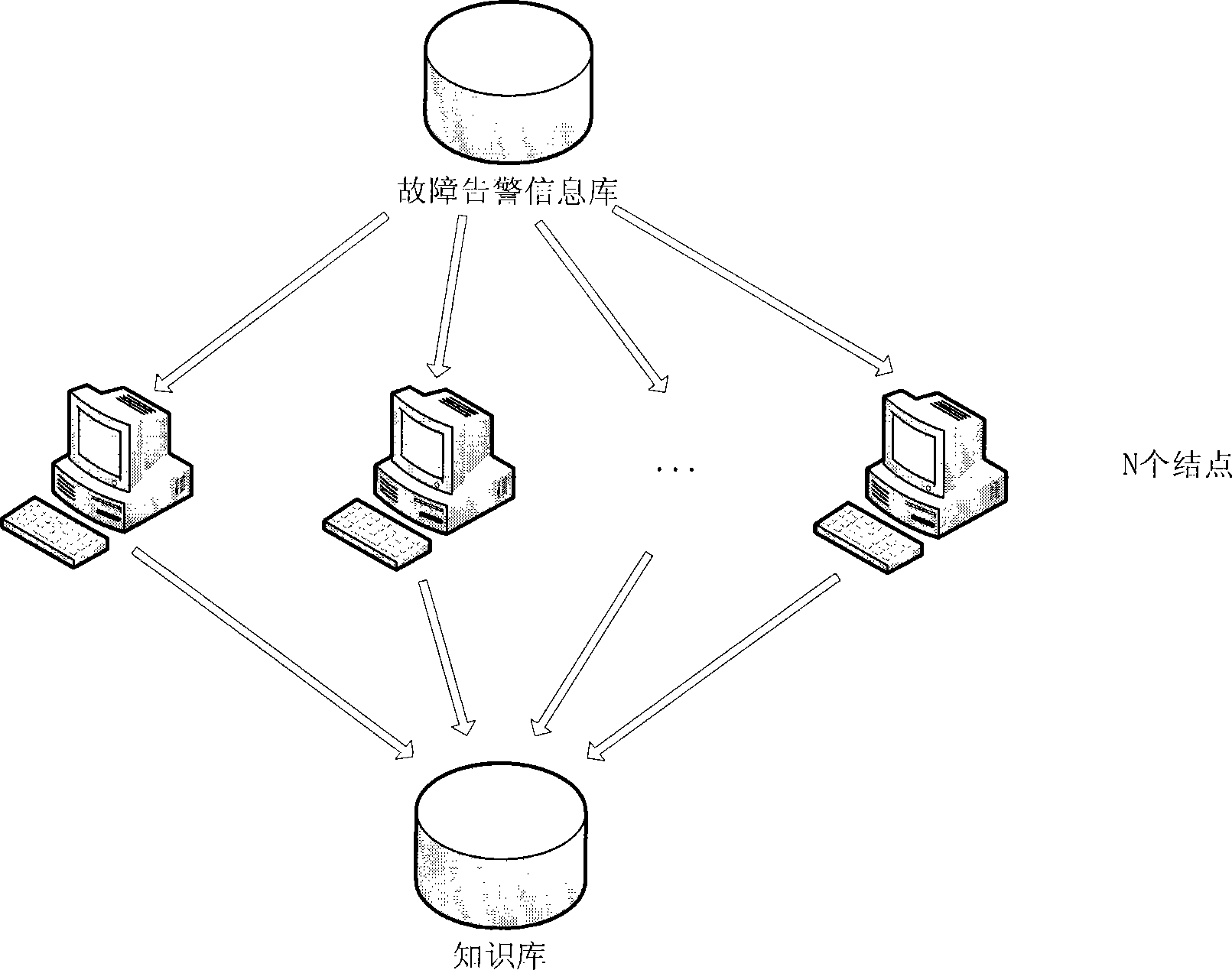
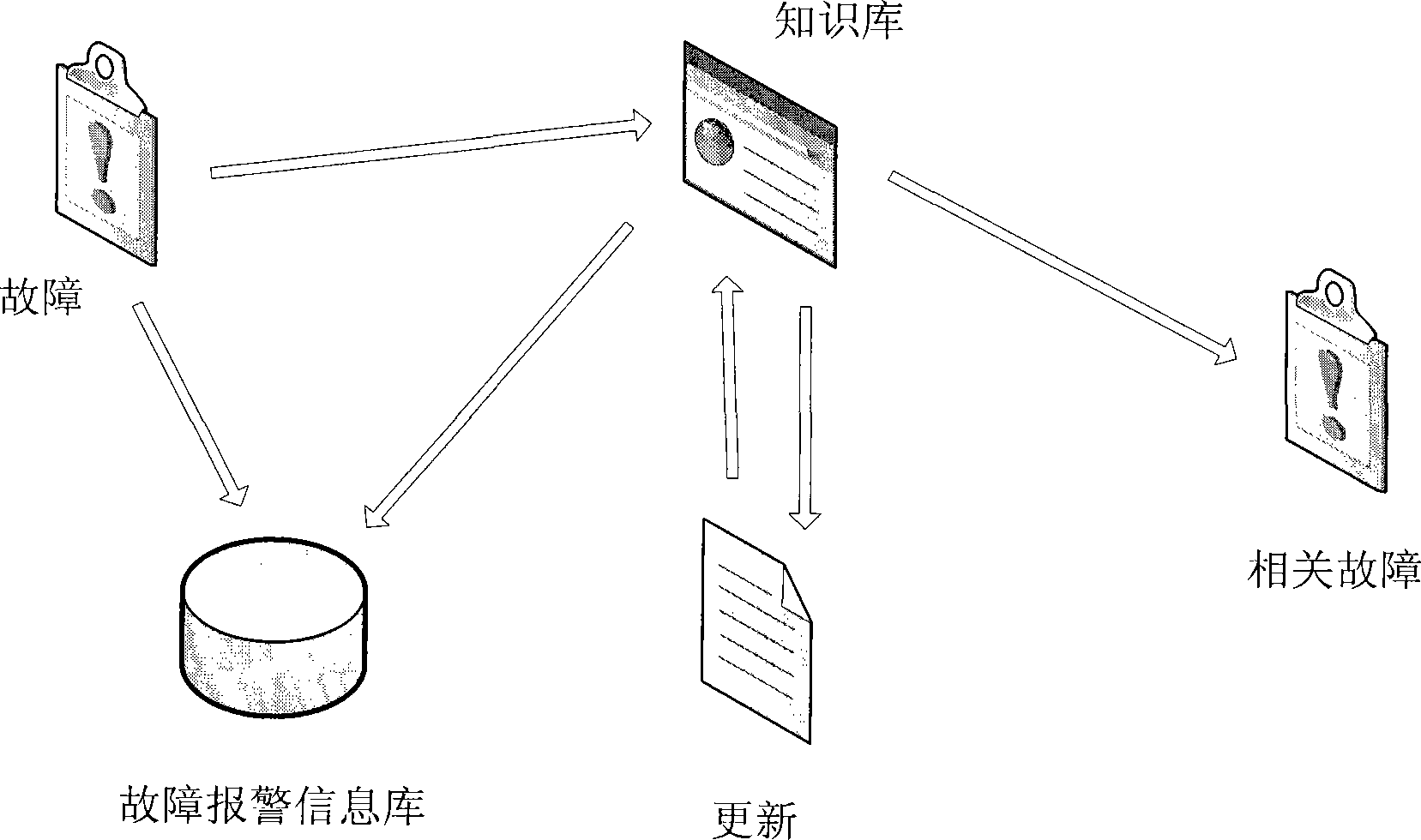
Equipment fault alarm, prediction and processing mechanism based on data mining
InactiveCN103414581AFault real-time monitoringTroubleshootingData switching networksParallel algorithmTime cost
The invention discloses an equipment fault, alarm, prediction and processing mechanism based on data mining. The equipment fault, alarm, prediction and processing mechanism based on data mining comprises a fault relevance description and fault prediction and processing mechanism obtained based on data mining. Because the amount of fault alarm information is huge nowadays and is continuously updated every day, time cost will be increased in a geometric mode through an ordinary traversal algorithm, data relevance mining efficiency is greatly reduced, real-time requirements can not be met in reality, and accordingly fault information association rules are mined from a fault alarm information database according to a clustering distribution type parallel algorithm to form a knowledge base. When a kind of fault alarm information is generated, the probability of happening of relevant faults is quickly predicted in real time by the fault predicting and processing mechanism according to the association rules in the knowledge rules to guide fault processing.
Owner:PCI TECH GRP CO LTD
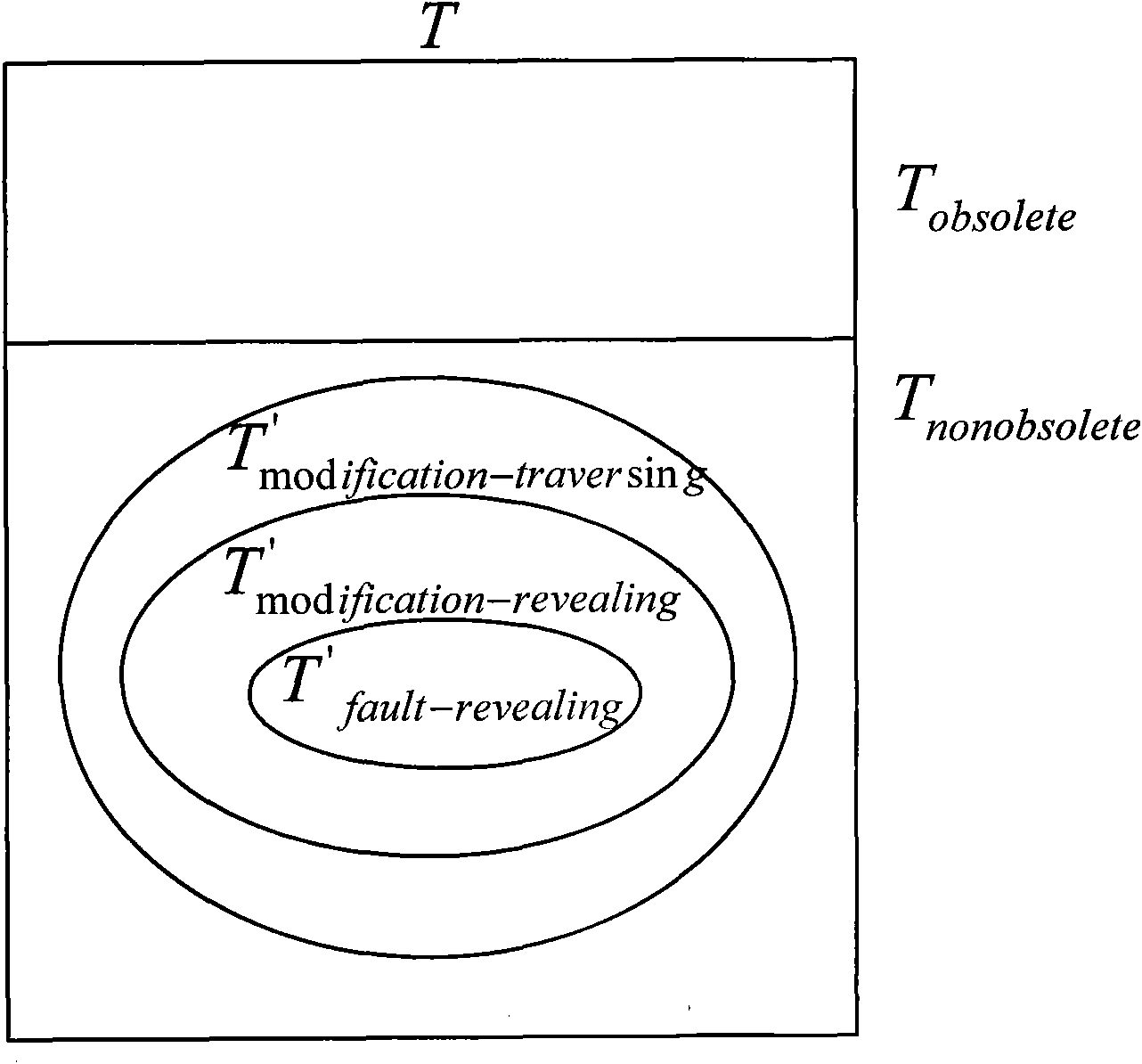
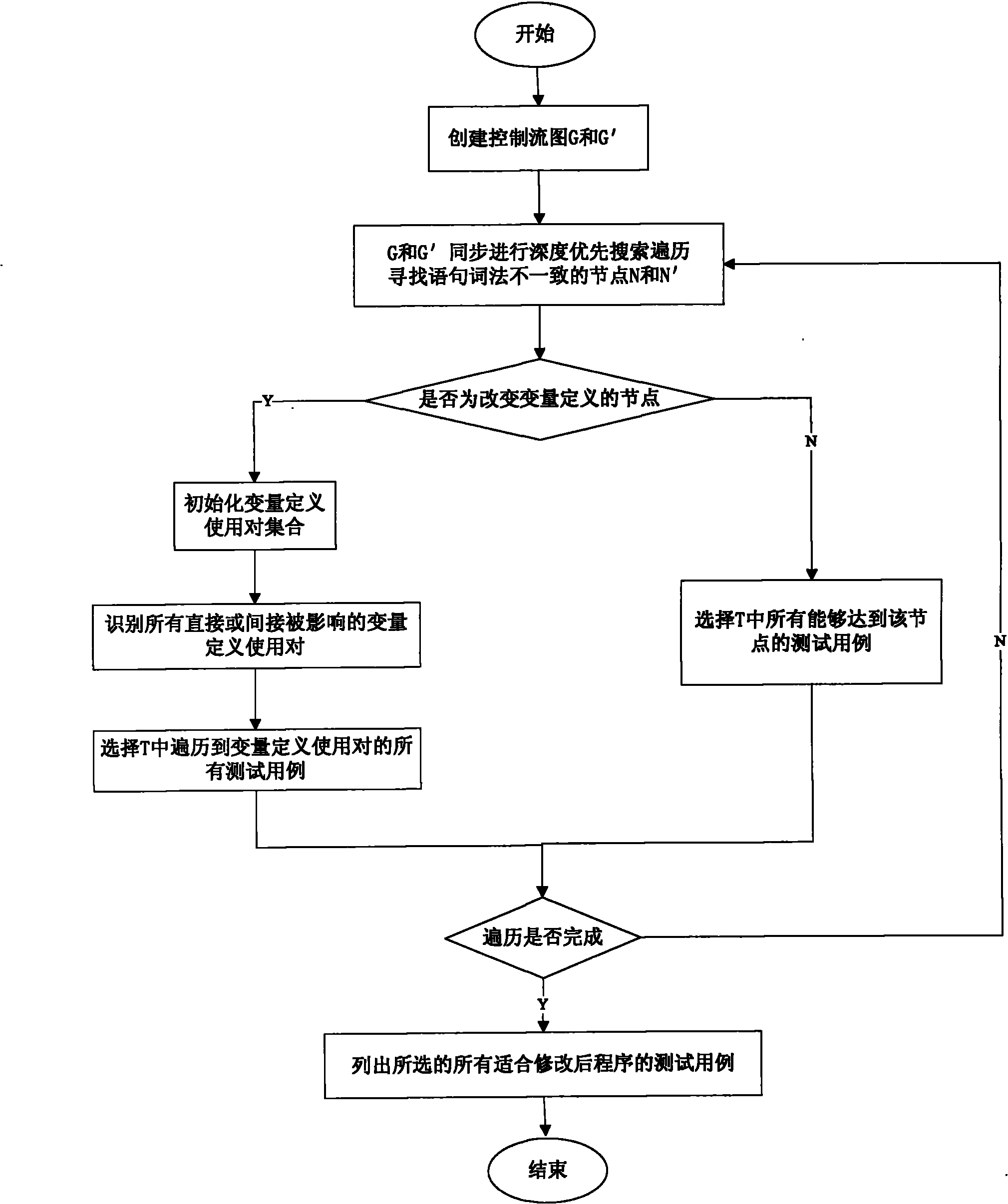
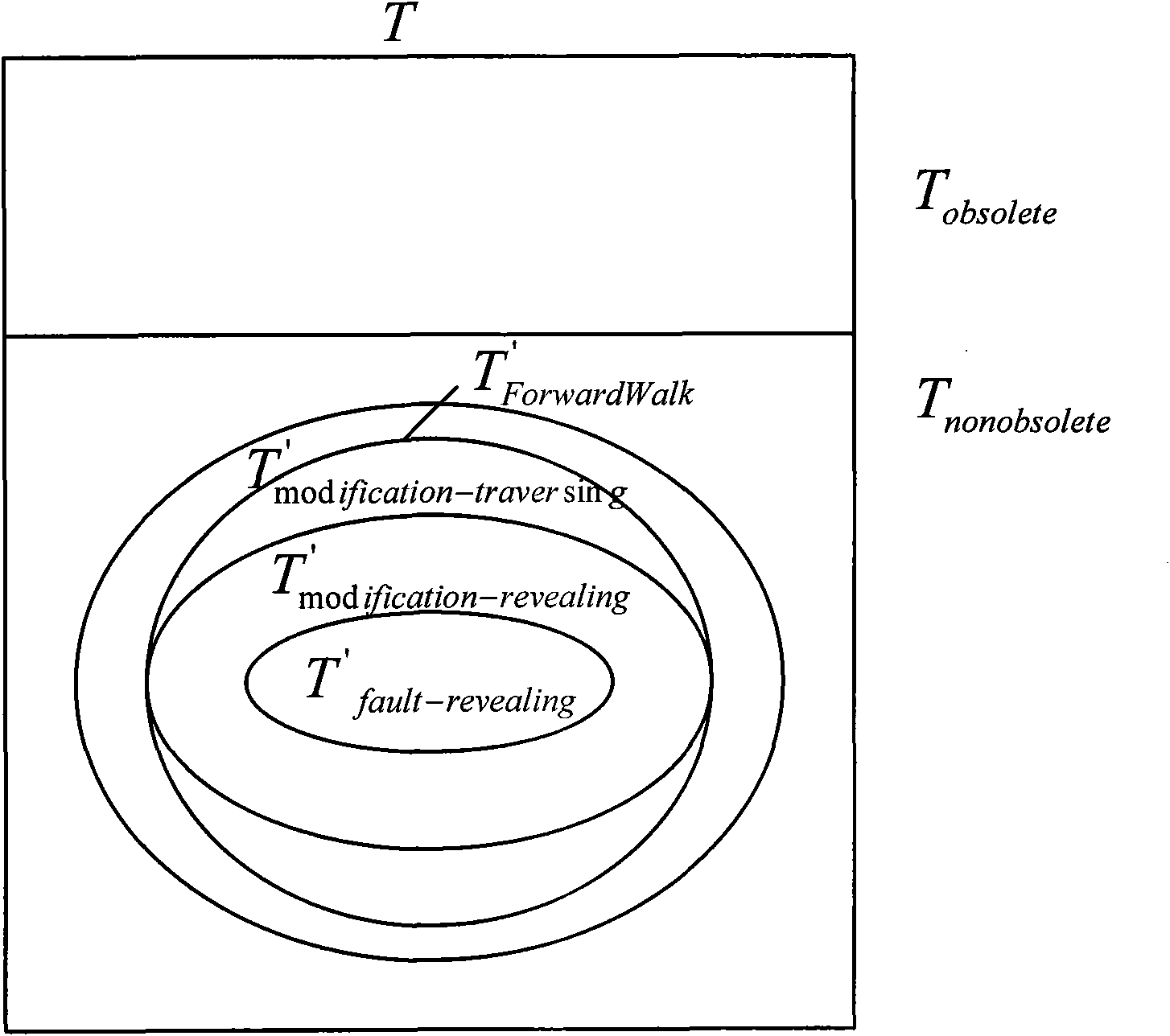
Software testing method based on combination of control flow graph traversal and slice forward traversal
The invention provides a software testing method based on the combination of control flow graph traversal and slice forward traversal. The method improves the traversal strategy of the selective regression testing method based on control flow graph traversal, changes the definitions of variables in codes and introduces the slice forward traversal algorithm; and in the method, all the definition-use pairs vdefine-vuse which are affected directly or indirectly is identified, only the test case of the variable definition-use pairs are selected to traverse, thus avoiding the consumption of test time and effect caused by selecting all the test cases through one node. As the improvement of strategy and the introduction of algorithm only aim at the modification of variable definition and the deletion of code is not considered, the method disclosed by the invention can not influence the safety and increase the selection accuracy of test cases in a certain scope.
Owner:哈尔滨哈船导航技术有限公司
System, program product and method of rendering a three dimensional image on a display
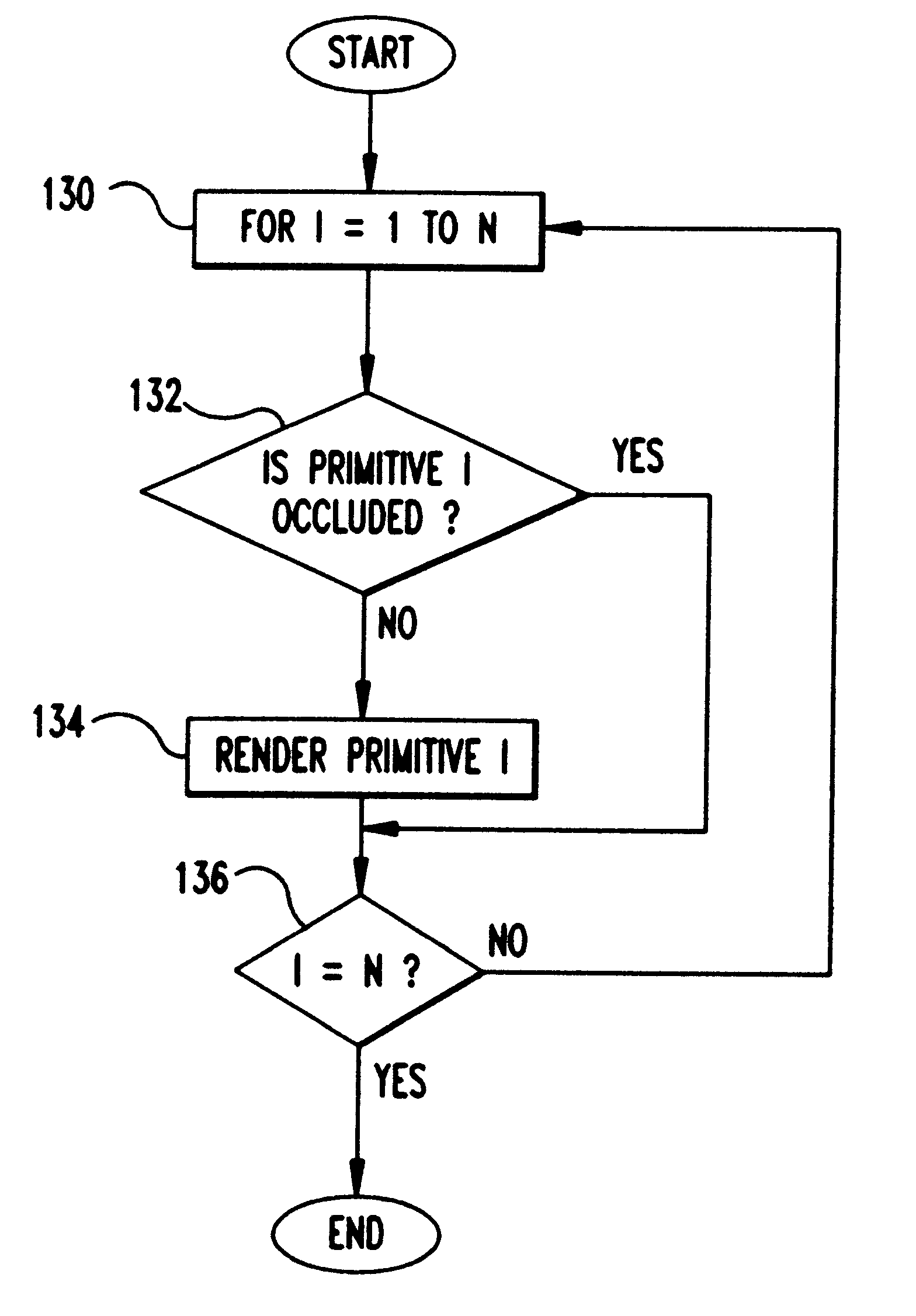
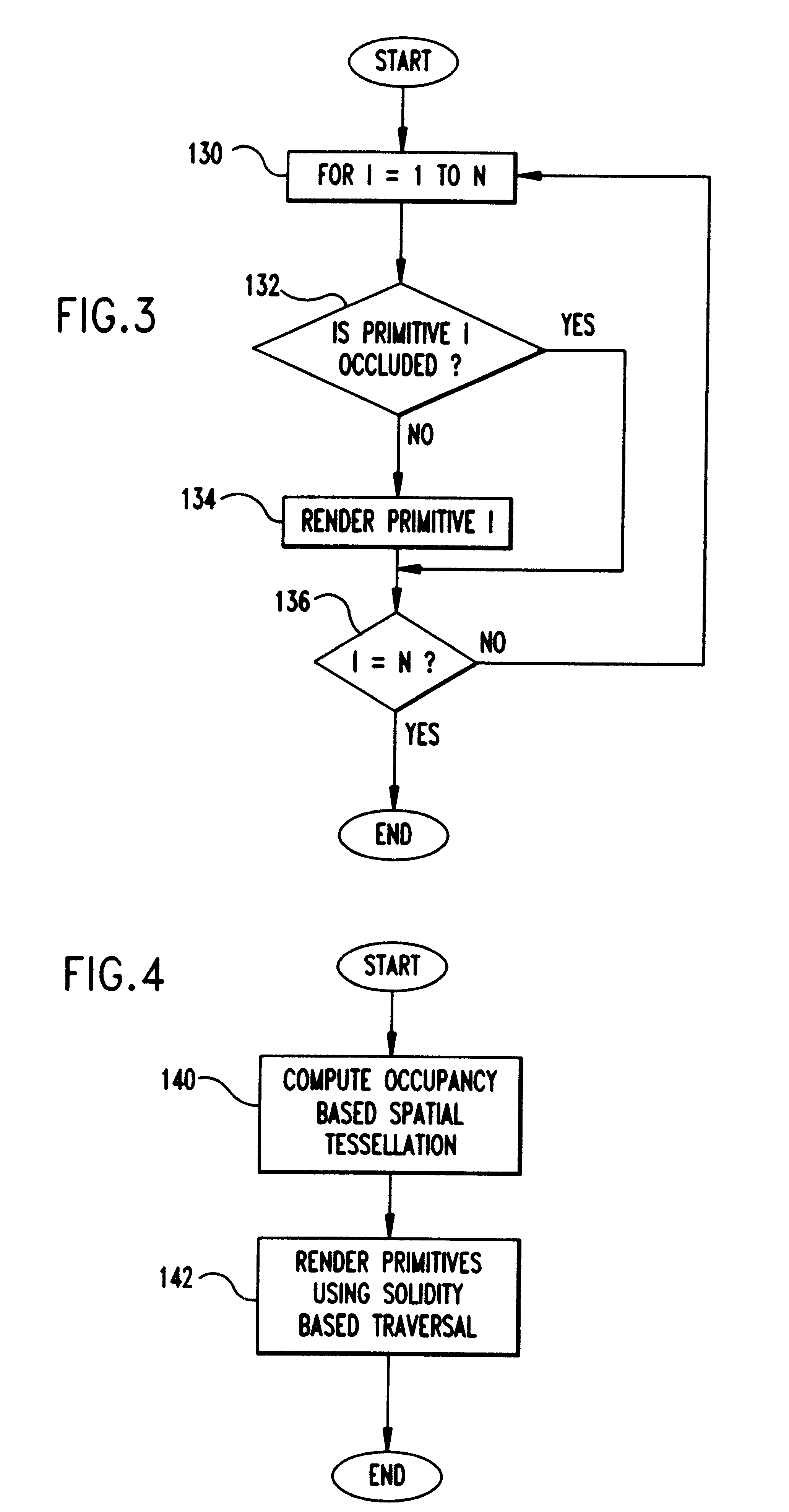
A Prioritized-Layered Projection (PLP) method and system for optimizing the rendering high-depth complexity scenes. Objects in each frame are prioritized with an estimation of the visible set within the rendered frame. A priority order for only the primitives in visible sets within the frame are computed "on demand" to maximize the likelihood of rendering visible primitives before rendering occluded ones. For a fixed budget, such as, time or number of triangles, rendering is constrained to a geometry budgeted priority. The method includes two main steps: an occupancy-based tessellation of space; and a solidity-based traversal algorithm. By first computing an occupancy-based tessellation of space, more cells result where there are more geometric primitives. In this spatial tessellation, each cell is assigned a "solidity" value directly proportional to its likelihood of occluding other cells. In its simplest form, a cell's solidity value is directly proportional to the number of primitives contained within the cell. Cells are marked for projection, and the geometric primitives contained within the marked cells are rendered. Cell solidity, and other view-dependent information determines the order cells are rendered.
Owner:IBM CORP
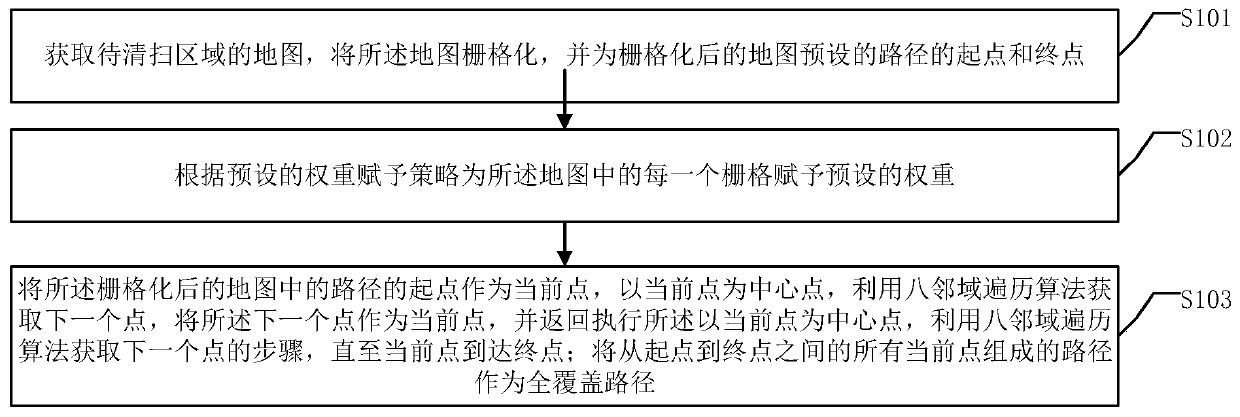
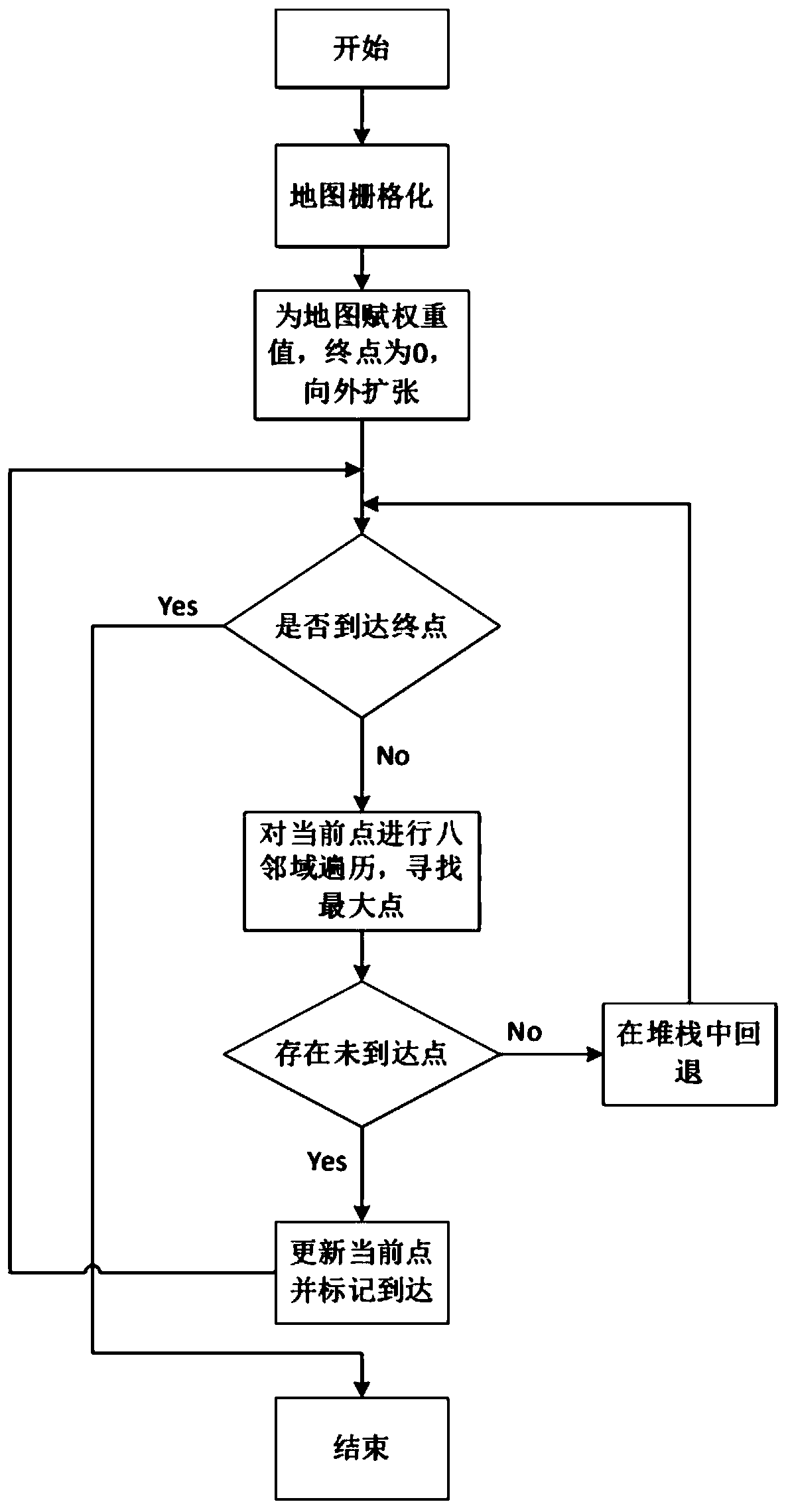
Method and device for planning full-coverage path of cleaning robot
ActiveCN111012251ASimplify the planning processImprove planning efficiencyCarpet cleanersFloor cleanersPathPingSimulation
The embodiment of the invention provides a method and device for planning a full-coverage path of a cleaning robot, and the method comprises the following steps: obtaining a map of a to-be-cleaned region, rasterizing the map, and presetting a starting point and an ending point of a path for the rasterized map; endowing each grid in the map with a preset weight according to a preset weight endowingstrategy; taking a starting point of a path in the rasterized map as a current point, taking the current point as a central point, obtaining a next point by utilizing an eight-neighborhood traversalalgorithm, taking the next point as the current point, and returning to execute the step of obtaining the next point by taking the current point as the central point and utilizing the eight-neighborhood traversal algorithm until the current point reaches the ending point; and taking a path formed by all the current points from the starting point to the ending point as a full-coverage path. By applying the embodiment of the invention, the path planning process can be simplified, and the path planning efficiency is improved.
Owner:合肥哈工澳汀智能科技有限公司
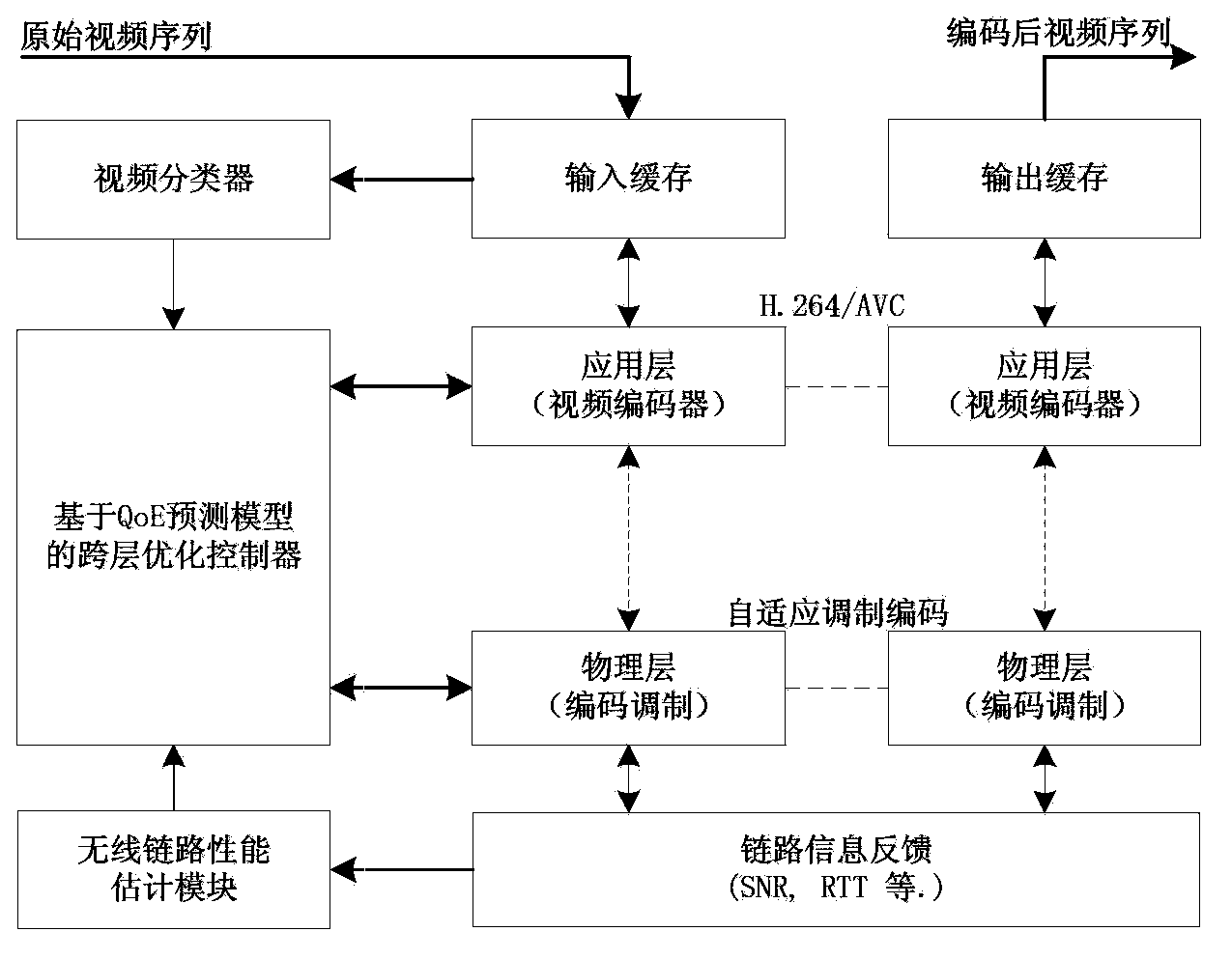
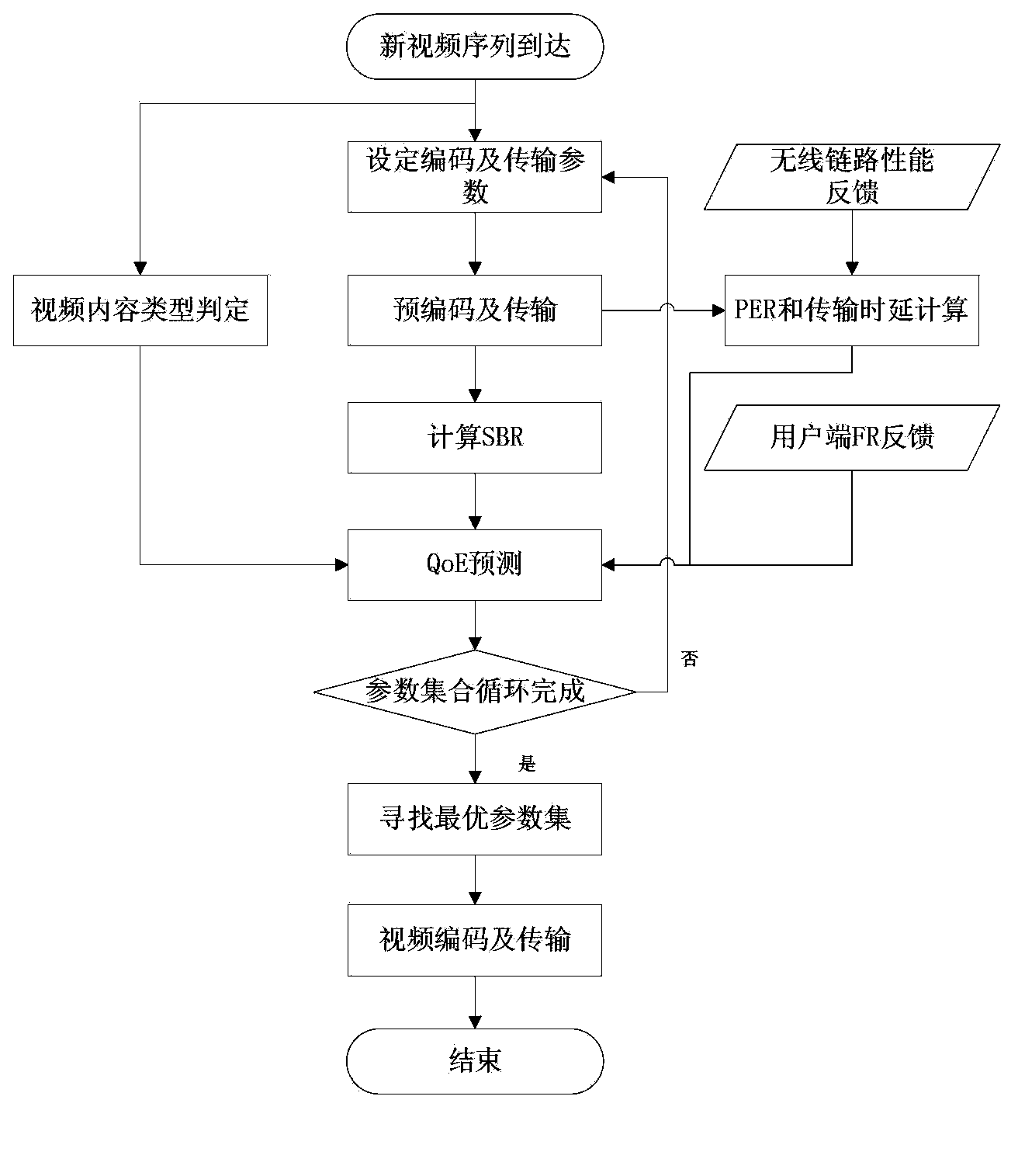
QoE-based cross-layer optimal video transmission method and system under MIMO-OFDM (Multi-Input Multi-Output-Orthogonal Frequency Division Multiplexing) system
InactiveCN103686218AReduce complexityAccurate predictionPulse modulation television signal transmissionSelective content distributionMulti inputPacket loss
The invention discloses cross-layer optimal video transmission method and system under an MIMO-OFDM (Multi-Input Multi-Output-Orthogonal Frequency Division Multiplexing) system. The method adopts a strategy of predicting a terminal QoE as an optimization target. The method comprises the following steps: 101) structuring a user experience quality prediction model of obtaining a user expect mean opinion value according to the video content type, frame rate, video transmission bit rate and packet loss probability; 102) obtaining each concrete parameter value in the user experience quality prediction model and obtaining the maximal value of a video packet transmission delay; 103) obtaining a parameter value corresponding to the maximal value of the user expect mean opinion score under the maximal transmission delay condition as an optimal parameter value by adopting a traversal algorithm, wherein the optimal parameter value comprises a video encoding parameter value and a modulation encoding mode parameter value, and finally, respectively encoding and transmitting the video correspondingly to the video encoding parameter of an application layer and the modulation encoding mode of a physical layer.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
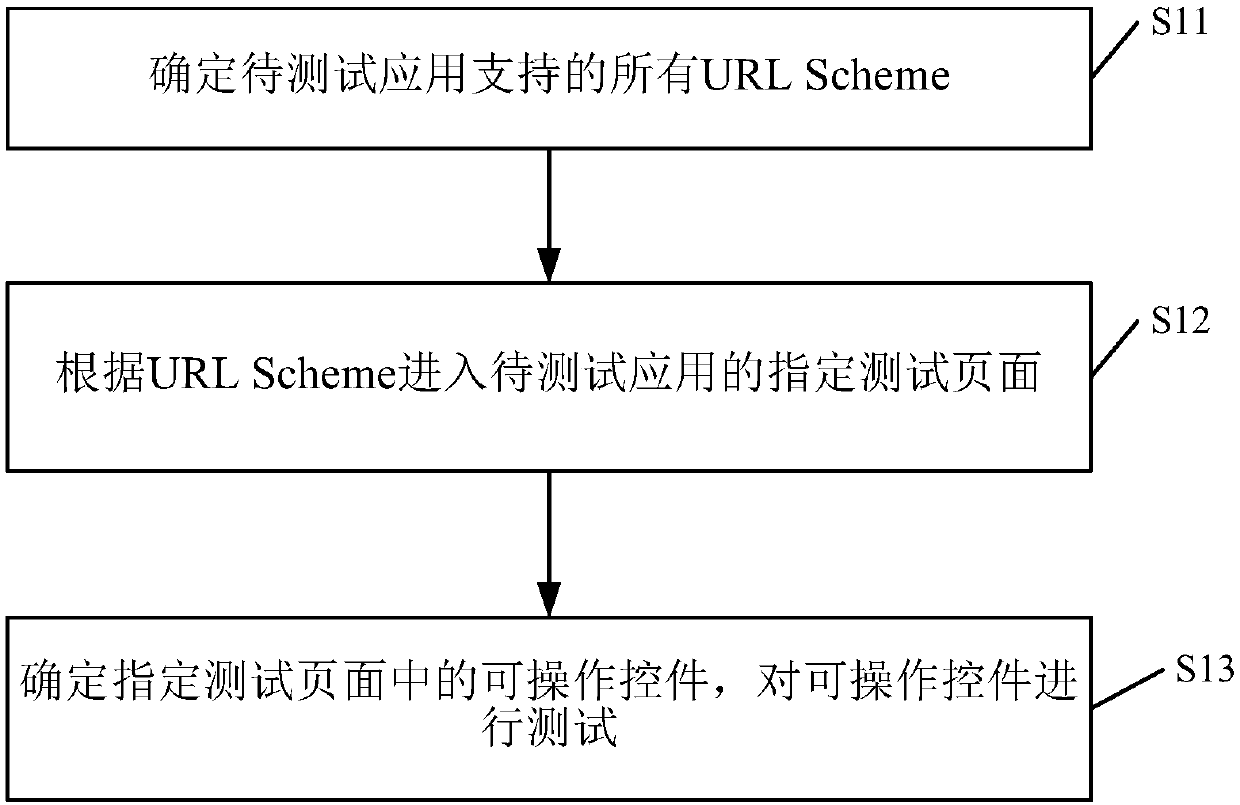
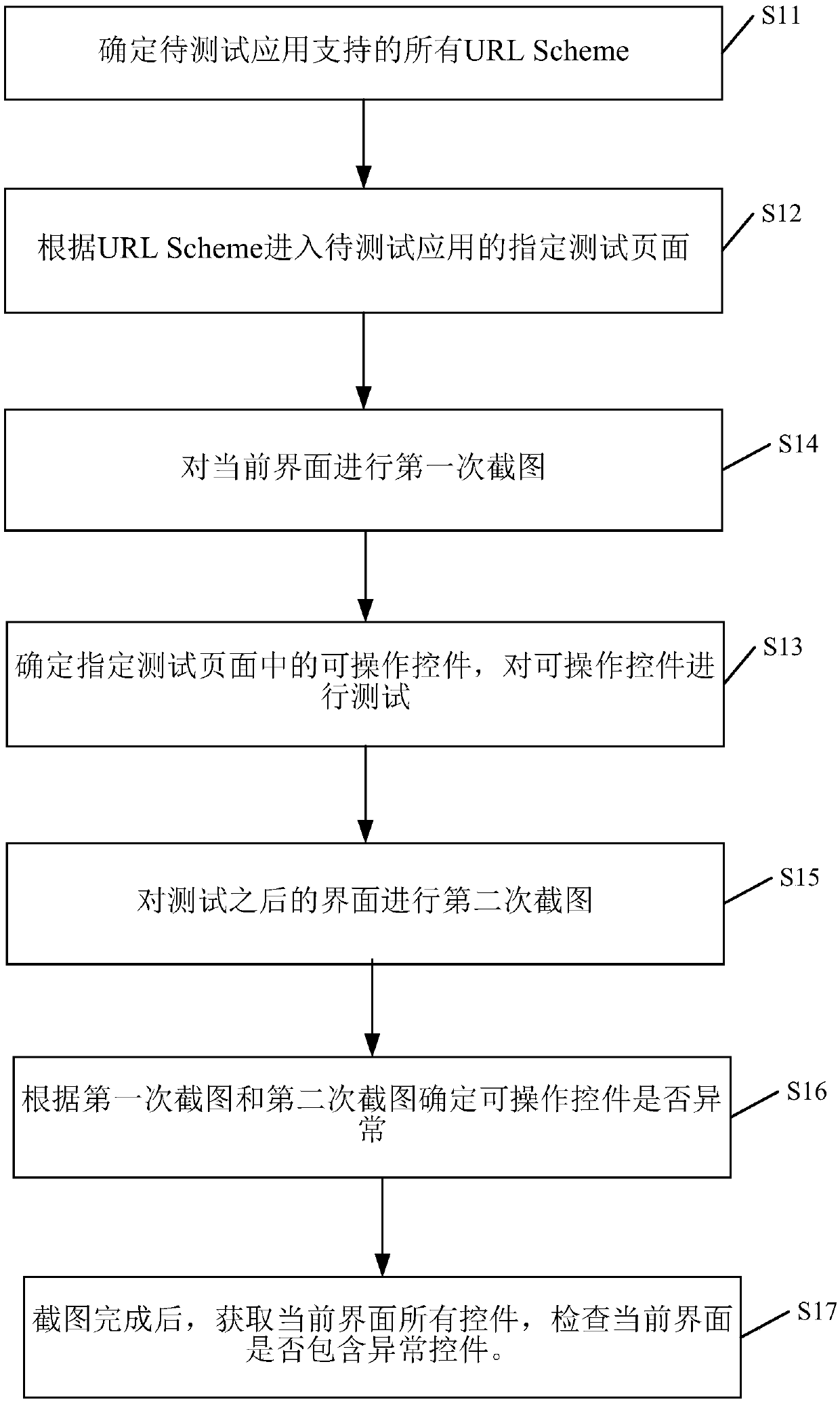
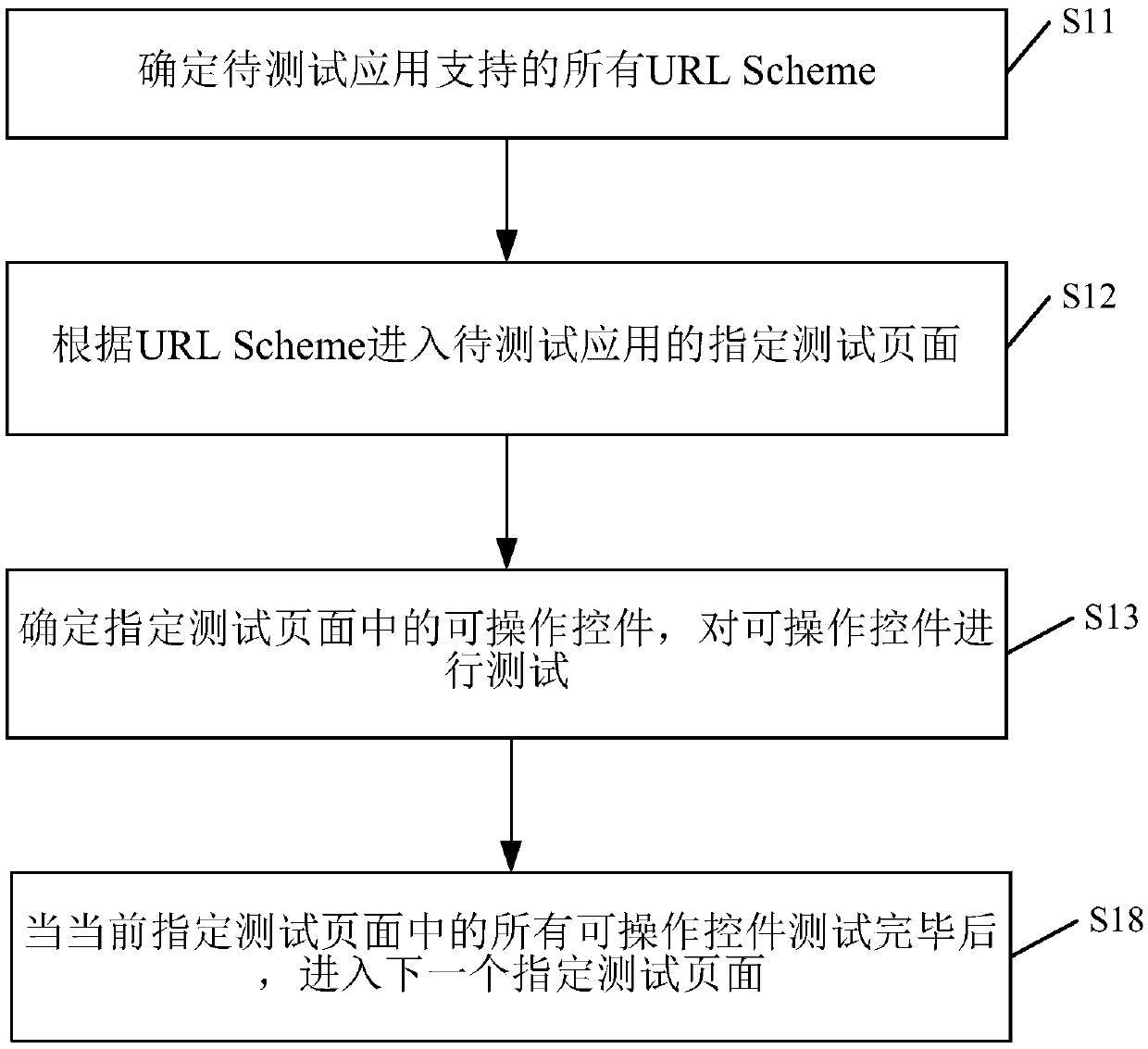
Page testing method and apparatus
InactiveCN107622016AReduce developmentFix stability issuesSoftware testing/debuggingSoftware engineeringTraversal algorithms
The present invention discloses a page testing method and apparatus. The method comprises: determining all URLschemes supported by a to-be-tested application, entering a specified test page of the to-be-tested application according to the URLSchemes, determining an operable control in the specified test page, and testing the operable control. According to the technical scheme of the present invention, the development of the UI automated testing business code can be effectively reduced, the UI automated testing return is more targeted, and bugs in the UI presentation layer can be initiatively discovered; and compared with other traversal algorithms, the technical scheme of the present invention solves the problems that the Monkey, depth-first traversal, and other methods are instable, traversal efficiency is low, initiative detection of UI bugs is lacked, the test page cannot be customized, and scripts are instable.
Owner:无线生活(杭州)信息科技有限公司
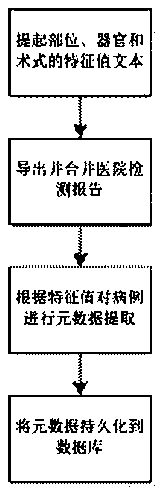
A method for converting a medical record text into structured metadata from a natural language
ActiveCN109710670AConvenient statisticsEasy to analyzeDatabase management systemsPatient-specific dataMedical recordData set
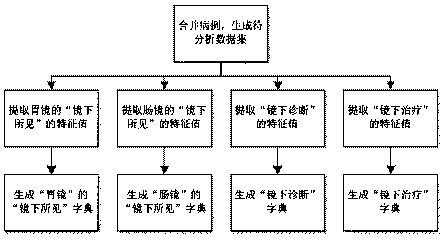
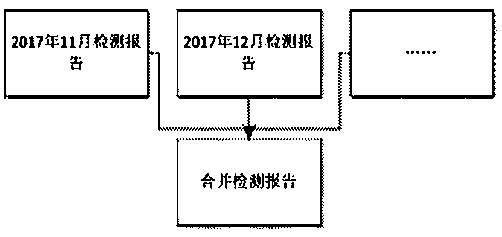
The invention relates to a method for converting a medical record text into structured metadata from a natural language, which comprises the following steps of: 1, extracting characteristic value texts of specific organs, parts and surgical expressions in a text format from a historical case report, and carrying out characteristic value analysis on the characteristic value texts to obtain a characteristic dictionary; 2, exporting historical detection reports needing to be analyzed from a hospital, and merging the historical detection reports into a to-be-processed data set; Step 3, traversingthe patient cases in the data set, segmenting words according to the characteristic value dictionary, and intercepting the description of the organ, the part or the surgical expression; and step 4, persisting the data content intercepted by the part into a structured database. According to the method, historical cases are utilized, a traversal algorithm is used, the use cost is reduced, the generation step of a training set is omitted, lesions of different organs and parts can be conveniently counted, analyzed and searched for through the converted structured cases, and doctors can conveniently carry out medical research, paper writing and teaching.
Owner:萱闱(河南)生命科学研究院有限公司
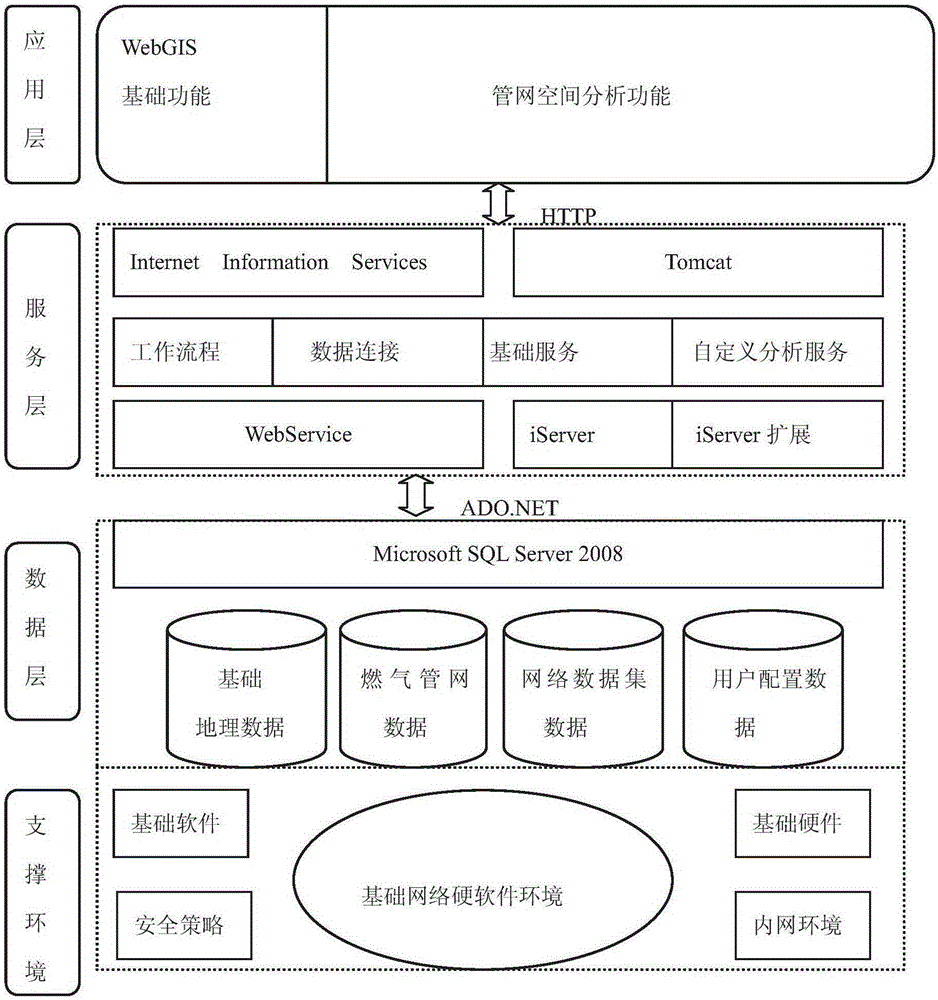
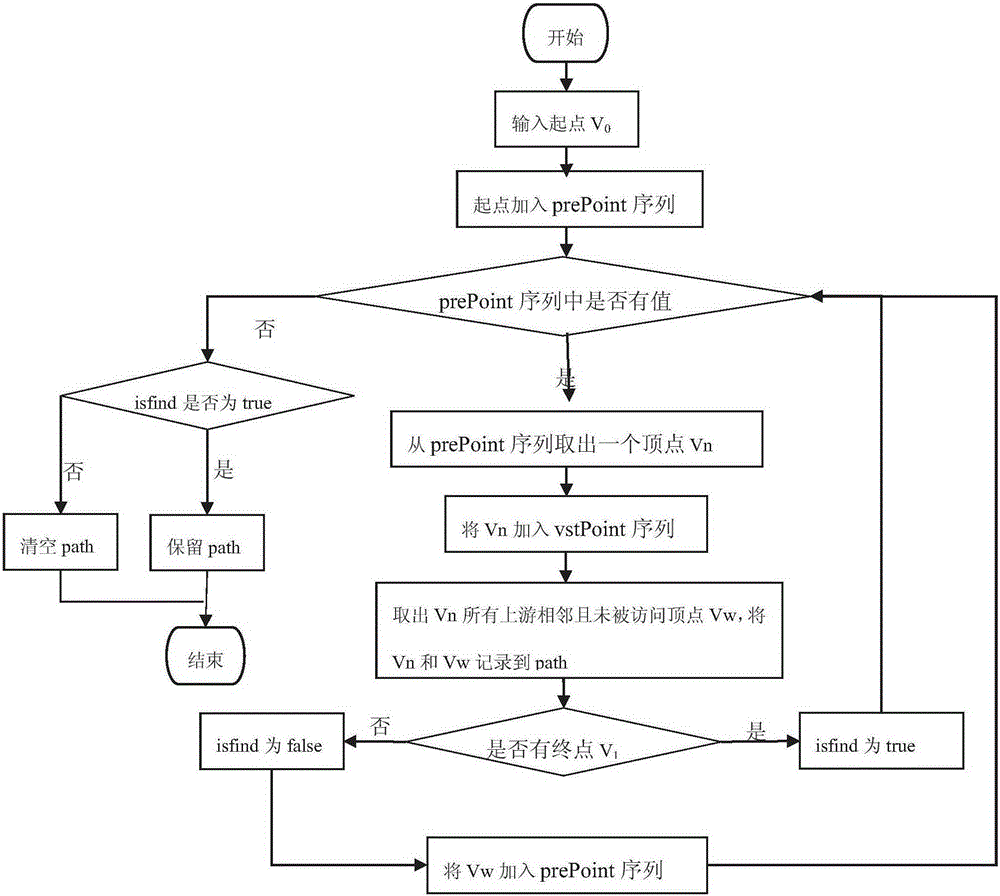
Pipeline network spatial analysis method based on breadth-first search algorithm
InactiveCN105225187AEasy to implementEasy to updateData processing applicationsSpecial data processing applicationsSpatial analysisCommunity management
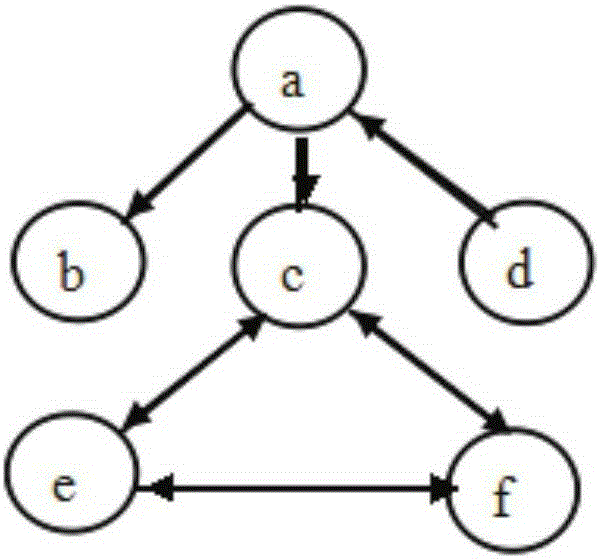
The present invention discloses a pipeline network spatial analysis method based on a breadth-first search algorithm. The method comprises: performing outward extension from a source point V0, wherein a distance from the source point V0 to a firstly accessed vertex is K and non-accessed adjacent vertices are V1, V2 and V3 until Vn; then, by taking the vertices as centers, accessing other non-accessed vertices with distances of K+1 to the source point V0 until all the vertices are accessed, wherein n is an integer greater than 1; and therefore, achieving connectivity analysis, pipe-broken analysis, shortest path analysis and profile analysis of a pipeline network. The method provided by the present invention uses a breadth-first search algorithm as a unified method for pipeline network traversal, explores calculation of the pipeline network by a breadth-first traversal algorithm of a digraph, facilitates implementation and update of the algorithm, facilitates derivation of other algorithms, and perfects a community management service system, an innovative community management mode and service functions.
Owner:SUZHOU SHENGJING INFORMATION TECH CO LTD
Graphics processing apparatus, methods and computer program products using minimum-depth occlusion culling and zig-zag traversal
ActiveUS7301537B2Reduce frequencyImage enhancementImage data processing detailsComputational scienceGraphics
A plurality of rows of tiles is defined in a graphics display field comprising a plurality of rows of pixels, each tile including pixels from at least two rows of pixels. Occlusion flags for respective tiles of a row of tiles for a graphics primitive are set based on whether respective representative depth values for the tiles of the row of tiles meet an occlusion criterion. Pixels in rows of pixels corresponding to the row of tiles are processed for the graphics primitive in a row-by-row manner responsive to the occlusion flags. The processing may include processing rows of pixels in the row of tiles using a zig-zag traversal algorithm.
Owner:TELEFON AB LM ERICSSON (PUBL)
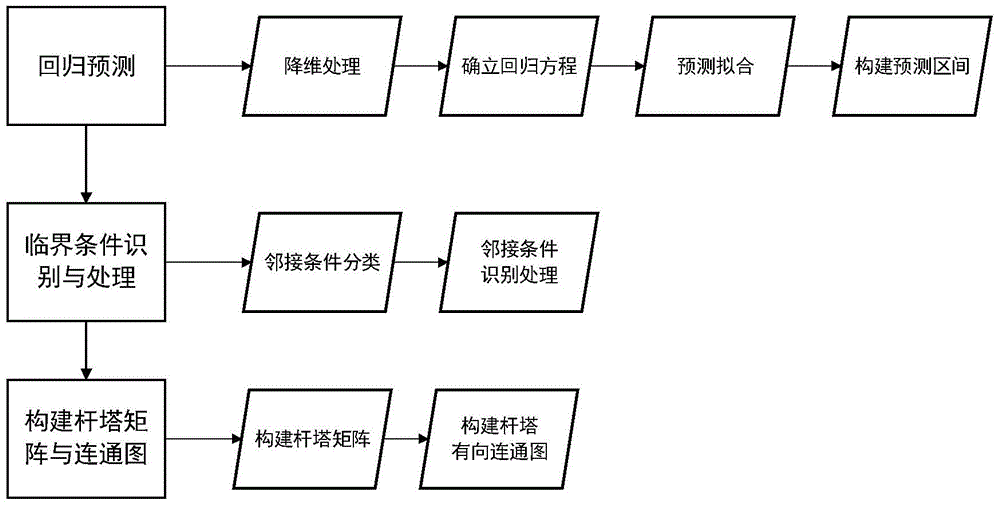
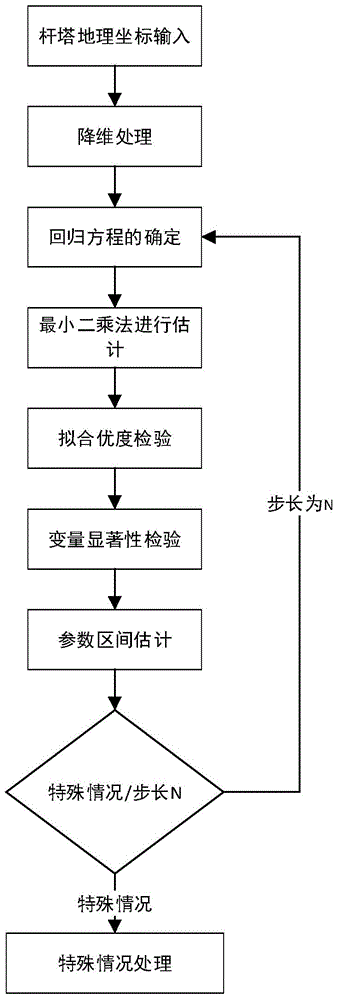
Intelligent tower connected graph construction method for planning inspection route of unmanned aerial vehicle (UAV)
ActiveCN105045274AImprove planning efficiencyImprove line inspection efficiencyPosition/course control in three dimensionsCritical conditionSingle element
The present invention provides an intelligent tower connected graph construction method for planning the inspection route of an unmanned aerial vehicle (UAV). The method comprises the steps of A, predicting the distribution of transmission line towers according to the single-element nonlinear regression prediction method to generate a plurality of tower lines, wherein each tower line is composed of a plurality of towers; B, based on the critical conditions of tower distribution, connecting the plurality of tower lines to form a line connection graph, wherein the critical conditions are composed of crossed crossing condition, parallel distribution situation of multiple tower lines at a relatively near distance relative to one another, tower steering condition and tower branch condition; C, constructing a storage structure of the line connection graph. According to the technical scheme of the invention, power transmission lines are intelligently planned based on the above algorithm, so that the planning efficiency is improved. Meanwhile, an entire patrol scheme is provided. In this way, not only the patrol can be conducted on going and returning paths, but also the line inspection is conducted on going and returning paths. Therefore, the line inspection efficiency is greatly improved. Based on the intelligent traversal algorithm, an optimal inspection route for a line network can be planned. In this way, all towers can be traversed within a region at a shortest inspection distance.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
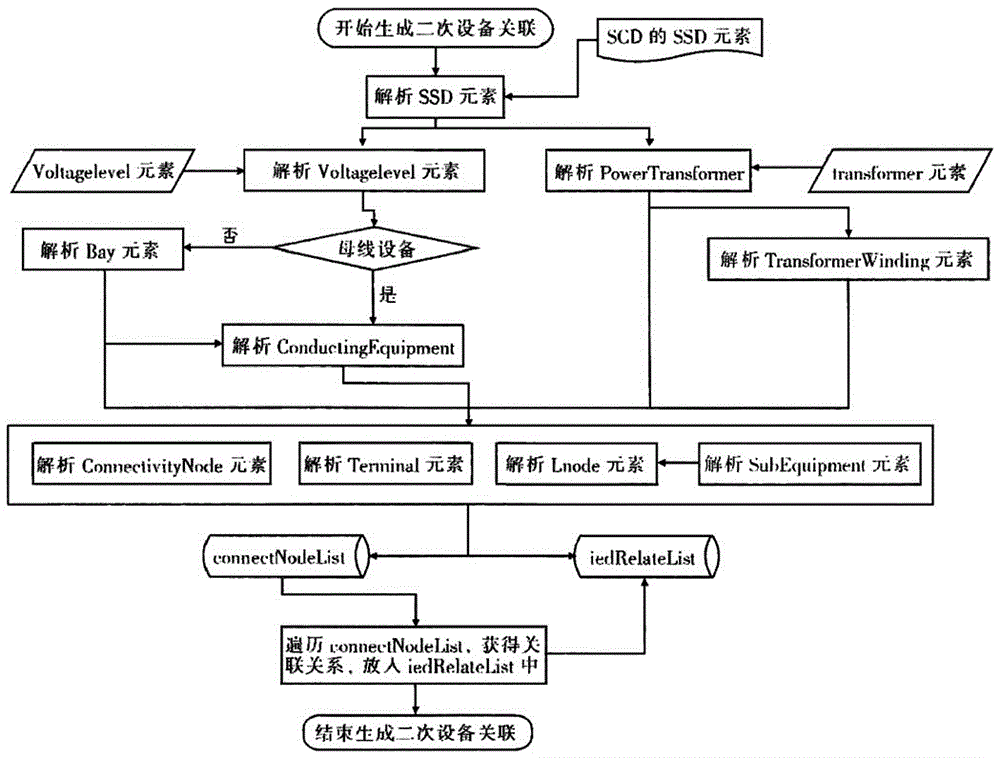
Method for automatically generating secondary equipment associating configuration based on system description
InactiveCN106528961AReduce workloadGeometric CADSpecial data processing applicationsSmart substationTransformer
The invention provides a method for automatically generating secondary equipment associating configuration based on system description. The method is characterized in that on the premise that the description of a transformer substation description file on the configuration of a primary system of a transformer substation and related key logic contacts is complete and accurate, a secondary equipment standard information and knowledge library is constructed according to relative standard of relay protection standard design, and the key information is gained from the system description file through the traversal algorithm, and thus the secondary equipment associating configuration of a smart transformer substation can be obtained based on the key information and the standard information and knowledge library. According to the method a standard IEC 61850 model and the system description are utilized to determine the relation of physical devices; the advantages of the standard model are fully utilized, so that the workload of system configuration can be decreased; the communication connection configuration of secondary equipment can be automatically created; a traditional secondary equipment associating manner using one-to-one corresponded positive terminals is completely changed.
Owner:STATE GRID CORP OF CHINA +2
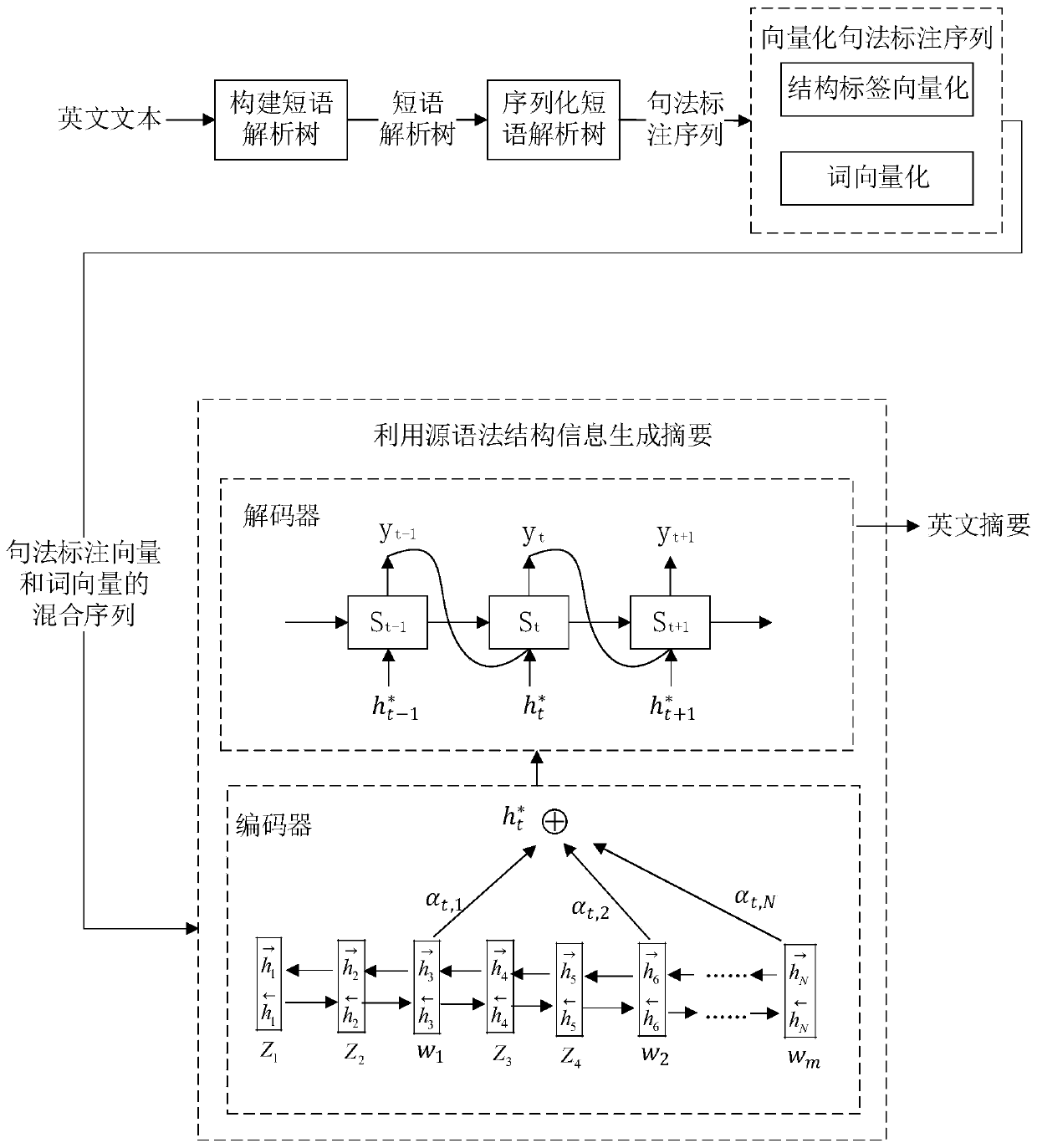
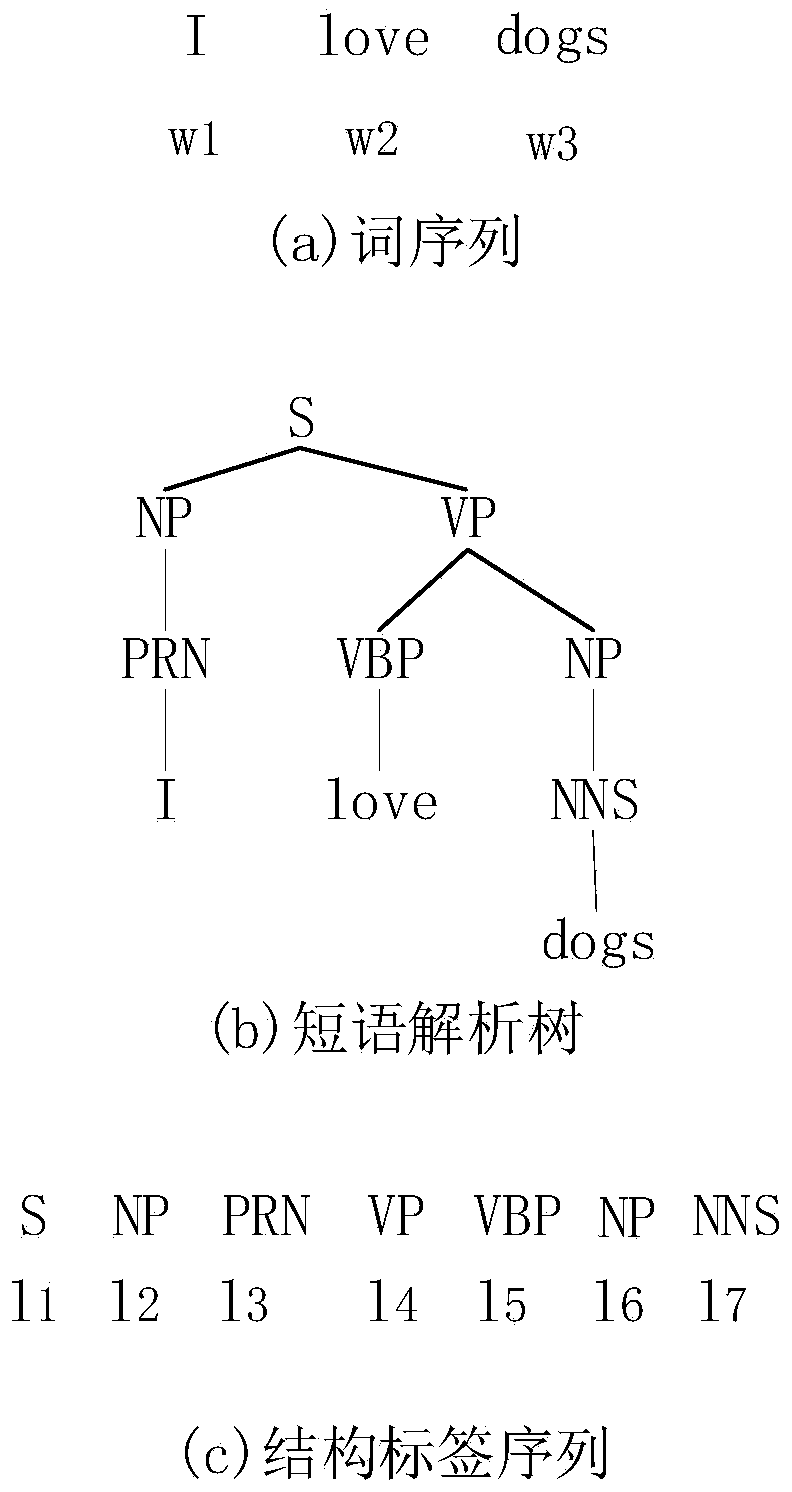
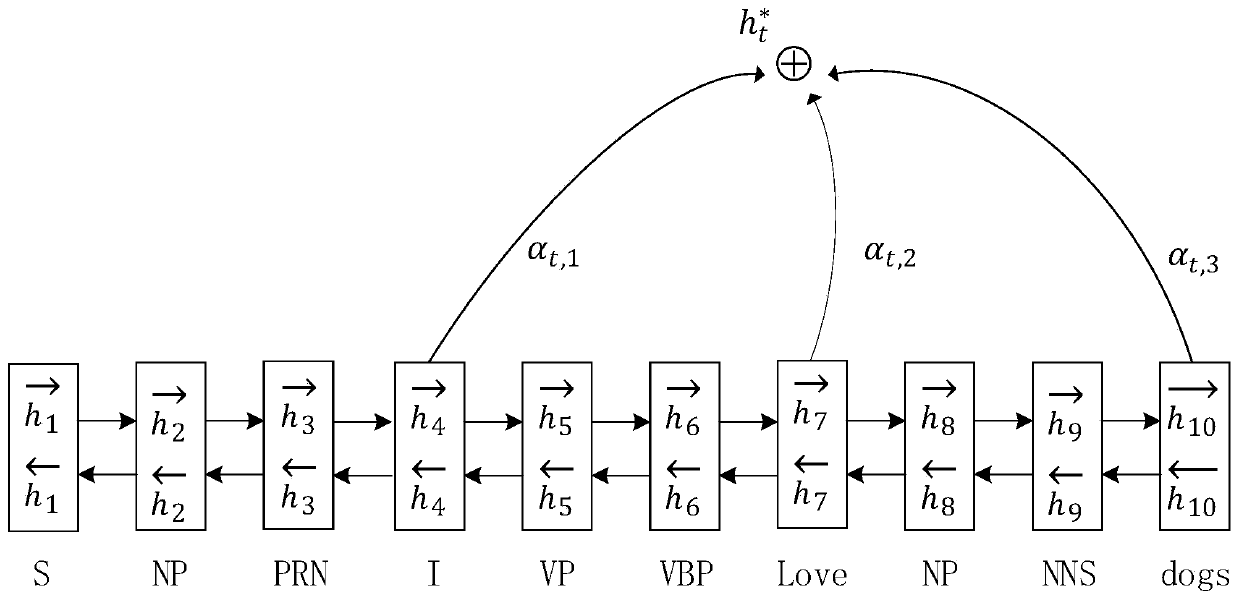
A generation type text abstract method fusing a sequence grammar annotation framework
The invention relates to a sequence grammar annotation framework fused generation type text abstract method, and belongs to the field of natural language processing. The method mainly aims to solve the problem that an existing model does not consider a grammar structure when generating an abstract, so that the generated abstract does not meet grammar rules. The method comprises the following steps: firstly, carrying out component syntactic analysis on sentences by utilizing an open source syntactic analyzer Berkley Parser to generate a phrase analysis tree; secondly, linearizing the phrase analysis tree into a structure label sequence through a depth-first traversal algorithm; vectorizing the grammar annotation sequence by using a word2vec tool; and finally, inputting the source syntax structure information into an encoder, encoding and decoding through an abstract generation module, and finally generating an abstract. The experiment is carried out on a CNN / Day Mail data set, and the result shows that the problems of super-outline words, repeated phrases, non-significant themes and the like are solved, the generated abstract basically meets grammar rules, the readability is higher,the abstract is more consistent with source text grammar, and the ROUGE score is improved to a certain extent compared with an advanced algorithm.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
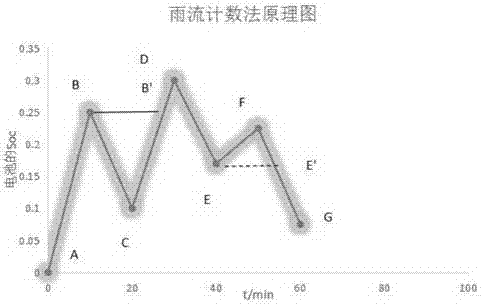
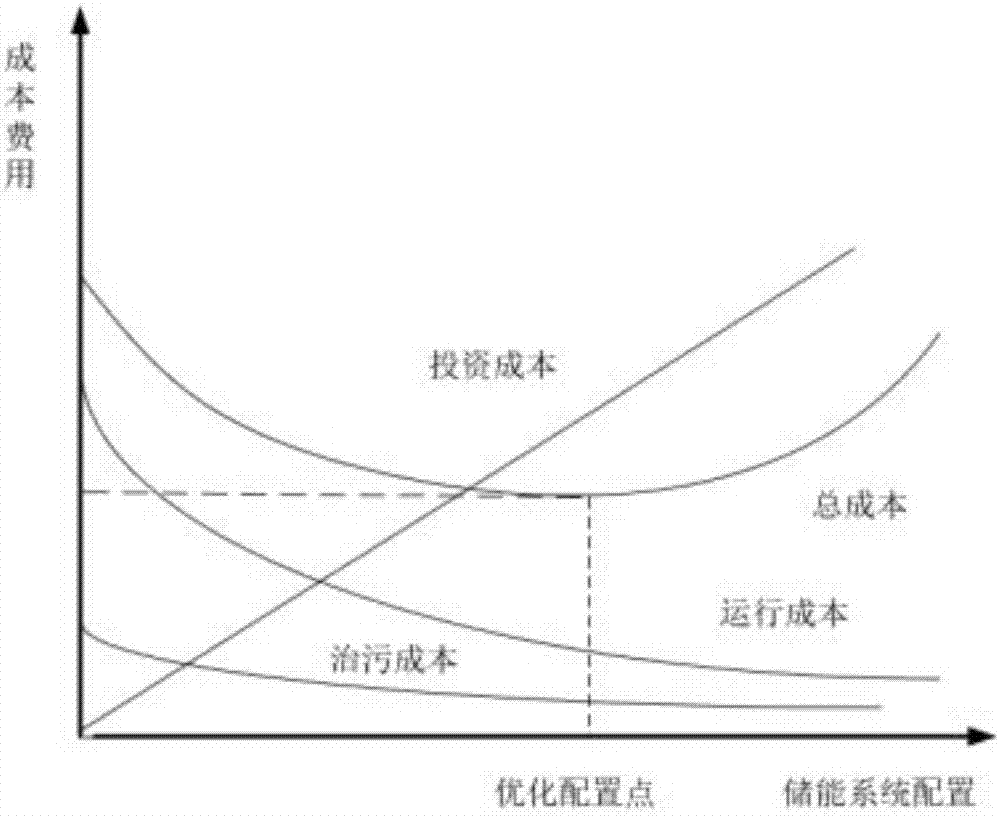
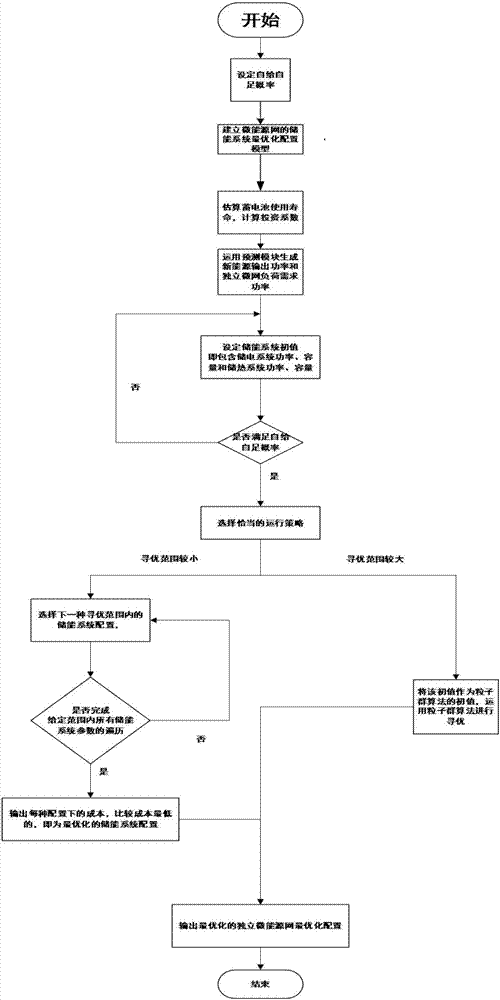
Optimal configuration closing method for energy storage system of independent type micro power grid
ActiveCN107134810ASatisfy economyGuaranteed stabilityFlicker reduction in ac networkLoad forecast in ac networkTraversal algorithmsParticle swarm algorithm
The invention discloses an optimal configuration closing method for an energy storage system of an independent type micro power grid. The method comprises the steps that a self-sufficiency probability requirement of the micro power grid is determined; an optimal configuration module of the energy storage system of the micro power grid is established; aimed at the optimal configuration module of the energy storage system, a rain-flow counting method is used to estimate the service life of a storage battery, and an investment coefficient is obtained; and load data and wind power data of one year are predicted, a proper operation strategy is adapted in the simulated operation process, and according to the optimization searching range, a traversal algorithm or particle swarm optimization is used to search configuration of the energy storage system. The method satisfies economical performance, provides the self-sufficiency probability requirement, and pursuits the system stability; the system stability is kept when the economical performance is optimal; and a balance is made among investment, operation and pollution treatment cost.
Owner:YANSHAN UNIV
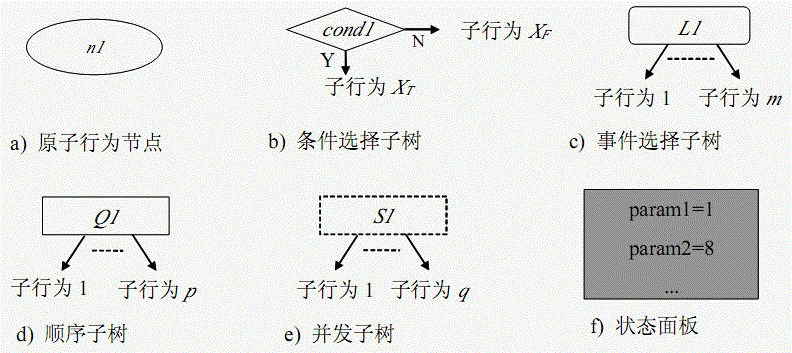
Method for achieving distributed system behavior simulated analysis tool based on behavior tree
ActiveCN106021816AStrong descriptive abilityDesign optimisation/simulationSpecial data processing applicationsJavaLogisim
The invention discloses a method for achieving a distributed system behavior simulated analysis tool based on a behavior tree. The method comprises the steps that a graphic symbol of a pel corresponding to a typical behavior tree factor is established, a simulation function on a behavior tree model expressed by an XML document is designed and achieved, a traversal algorithm of the behavior tree model based on XML is designed and achieved, an input interface through which a user defines whether a behavior is reachably verified or not within time cost is given, a variable for recording traversal time cost is designed, an external java programmatic interface defined by the behavior in the model is achieved, and therefore a simulation tool can call a function defined by the user. By means of the method, the graphic simulated analysis tool based on the behavior tree can be achieved, the tool achieved through the method can achieve system modeling, a method is provided for interactive logic reasonability, timeliness and reliability analysis of a distributed system, and the advantages of being simple in model, high in description capacity, accurate and comprehensive are achieved.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
A data mining method for shield tunneling parameters of TBM
ActiveCN109213810AUnderstand the construction levelUnderstanding the Comparison GapData miningDatabase modelsRegion analysisShield tunneling
A data mining method for shield TBM tunneling parameters mainly includes two parts: a 16-dimensional combined modeling method for distribution dynamic segmentation statistical analysis and a dynamic core empirical region analysis method for tunneling parameters. While receiving a large number of shield tunneling parameters of TBM on construction lines, accumulated frequency histogram data are periodically aggregated according to the prescribed rolling time window, the histogram core region is calculated according to a certain range, and the core region is judged by a fast reciprocating traversal algorithm, so that the optimal range of tunneling parameters is obtained through the accumulation of large data.
Owner:STATE KEY LAB OF SHIELD & TUNNELING TECH +1
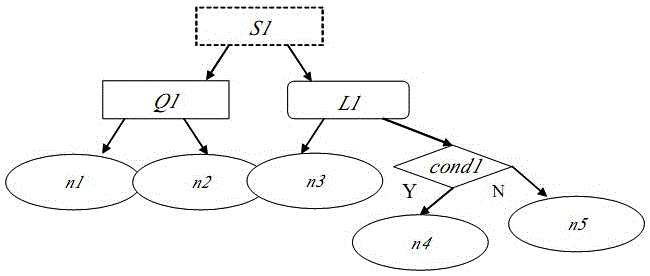
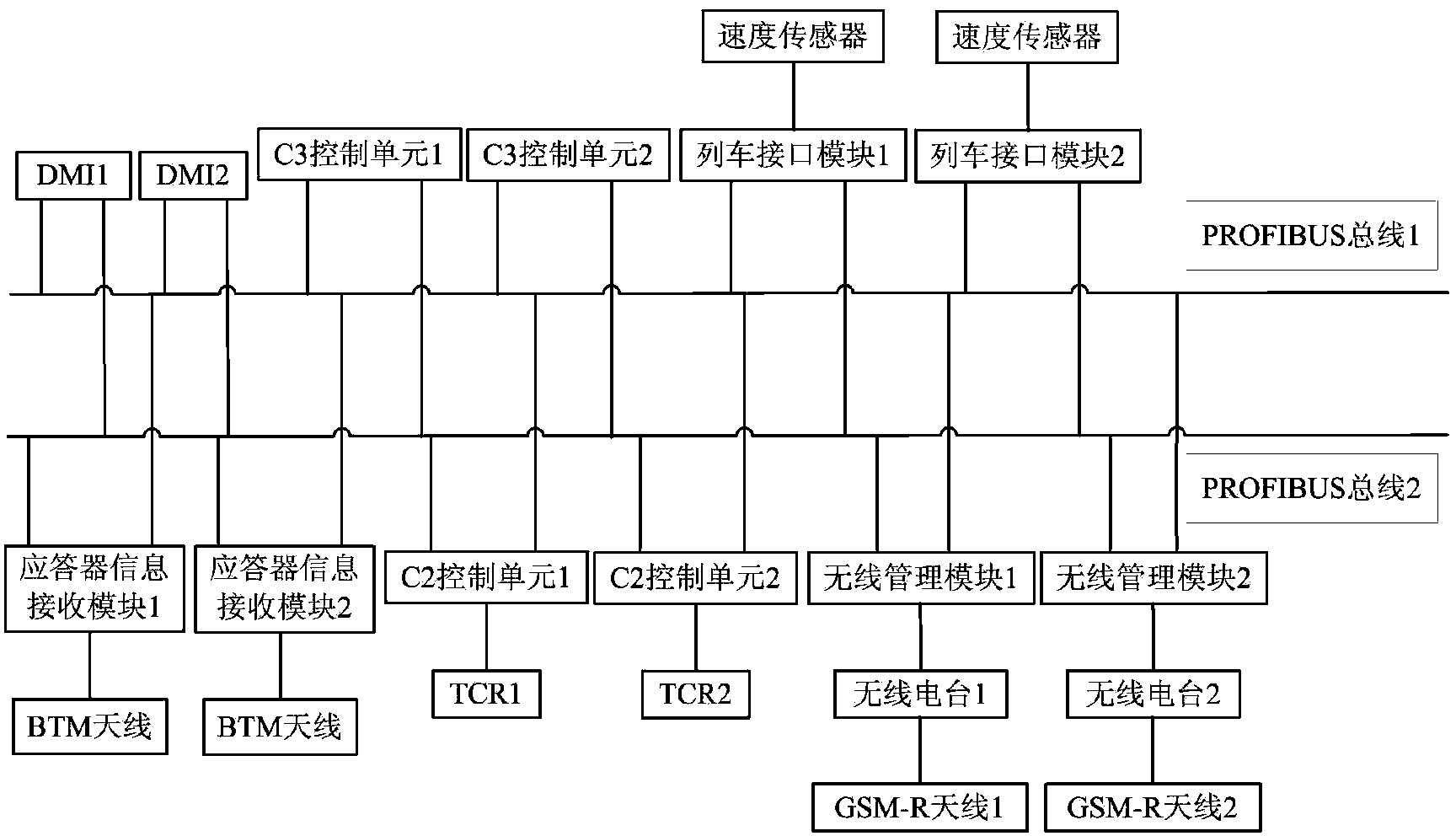
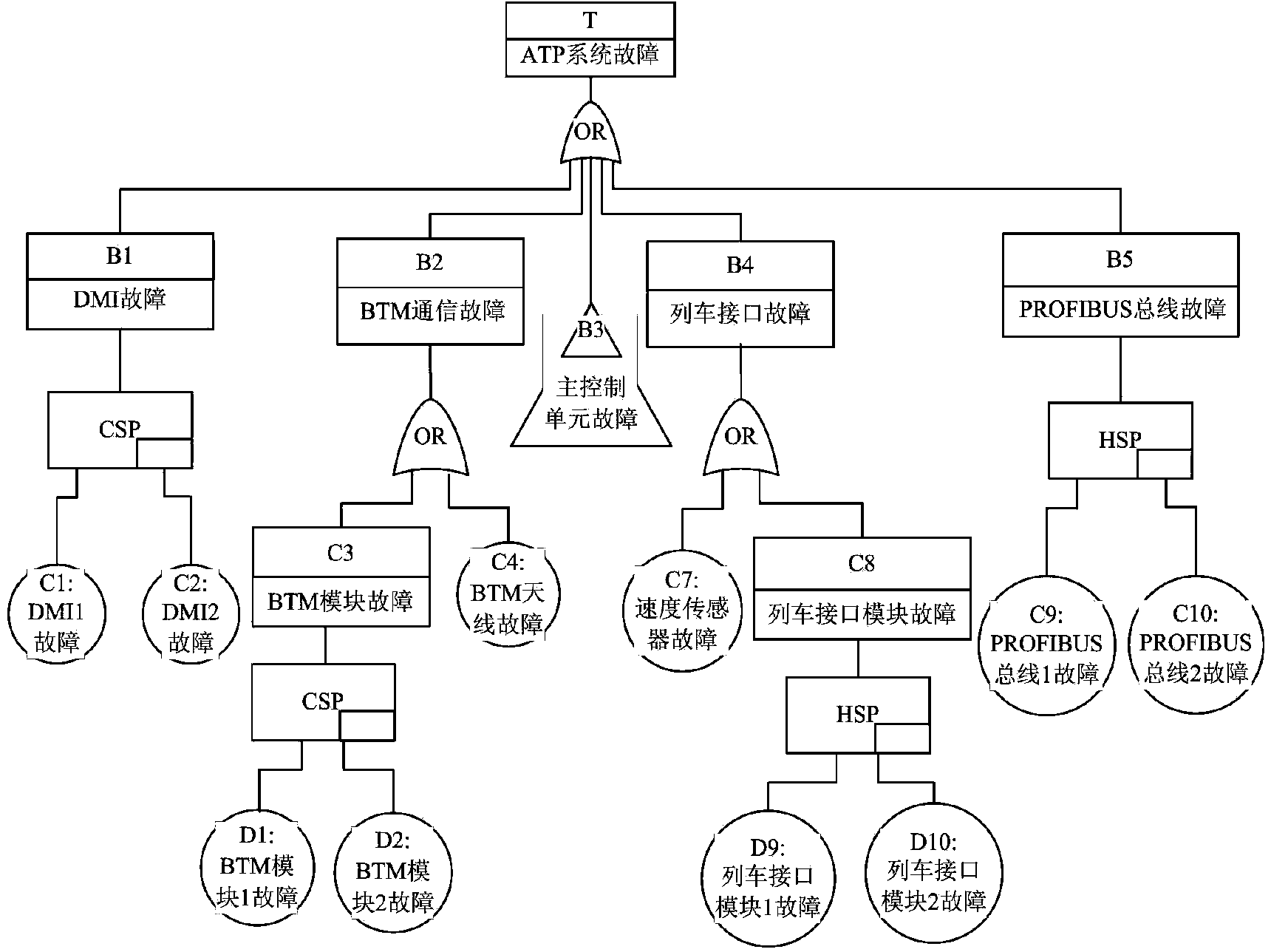
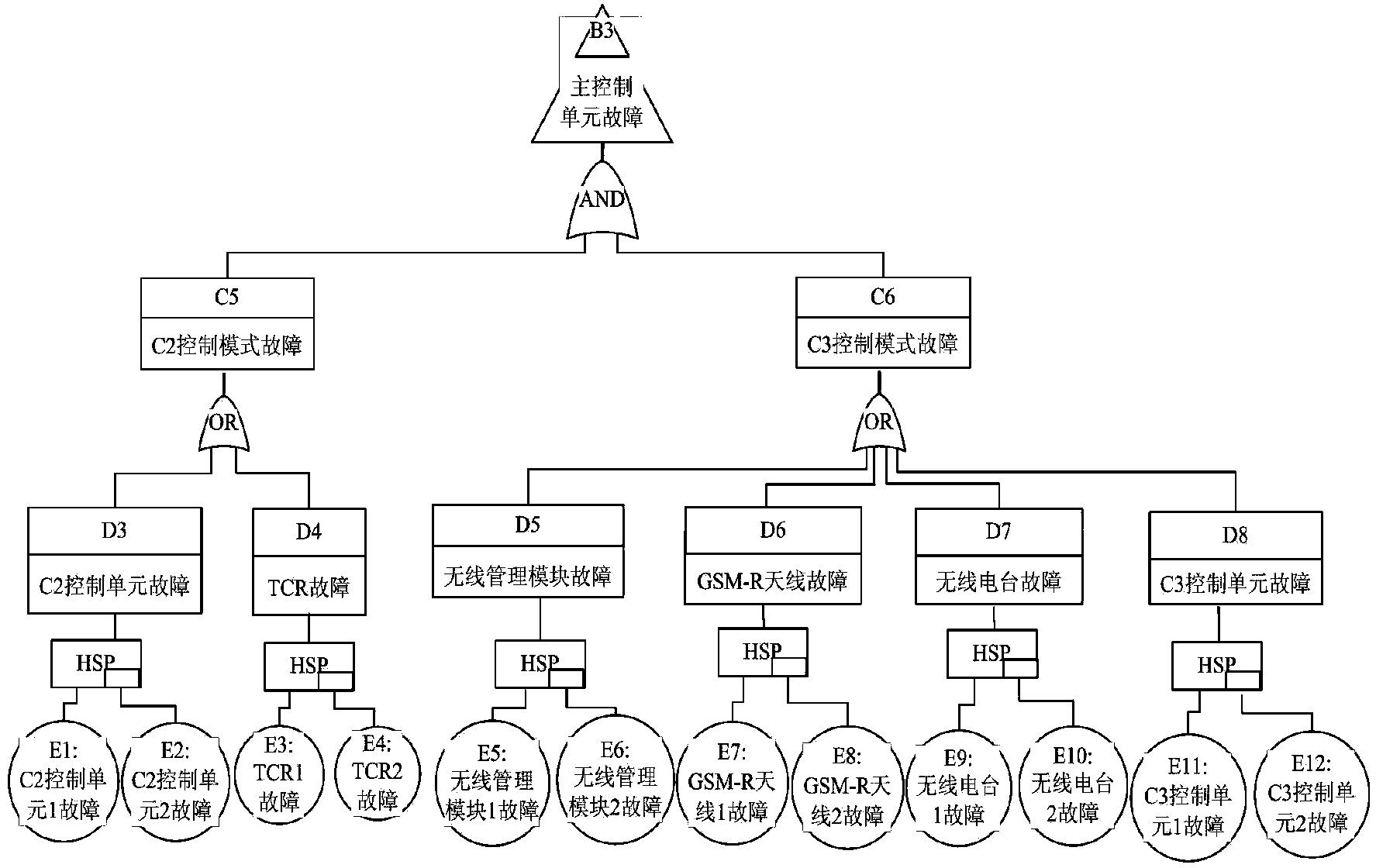
Method for estimating reliability of ATP (Automatic Train Protection) system of CTCS-3 (Chinese Train Control System of Level 3) based on dynamic fault tree
InactiveCN103955616AHigh expressionEasy assessment processSpecial data processing applicationsAutomatic train protectionRepairable systems
The invention discloses a method for estimating the reliability of an ATP (Automatic Train Protection) system of CTCS-3 (Chinese Train Control System of Level 3) based on a dynamic fault tree. The adopted technical schemes comprises the following steps: building a dynamic fault tree model that the ATP system of the CTCS-3 fails and a dynamic fault tree model that a master control unit fails according to the ATP system of the CTCS-3; judging the independence of each sub-tree module by adopting a depth-first leftmost traversing algorithm search model; solving a sub-tree by adopting a markov model of a repairable system, and obtaining a reliability index of the sub-tree; synthesizing solving results of the sub-tree module by combining a layered iteration method so as to obtain the reliability index of the system; estimating the system by adopting the system reliability index. The dynamic fault tree-based method has the benefits that the characteristics of the system can be described better by adopting the dynamic tree fault method which can express the dynamic failure process of the system; the estimating process is simple; the accuracy rate is high.
Owner:LANZHOU JIAOTONG UNIV
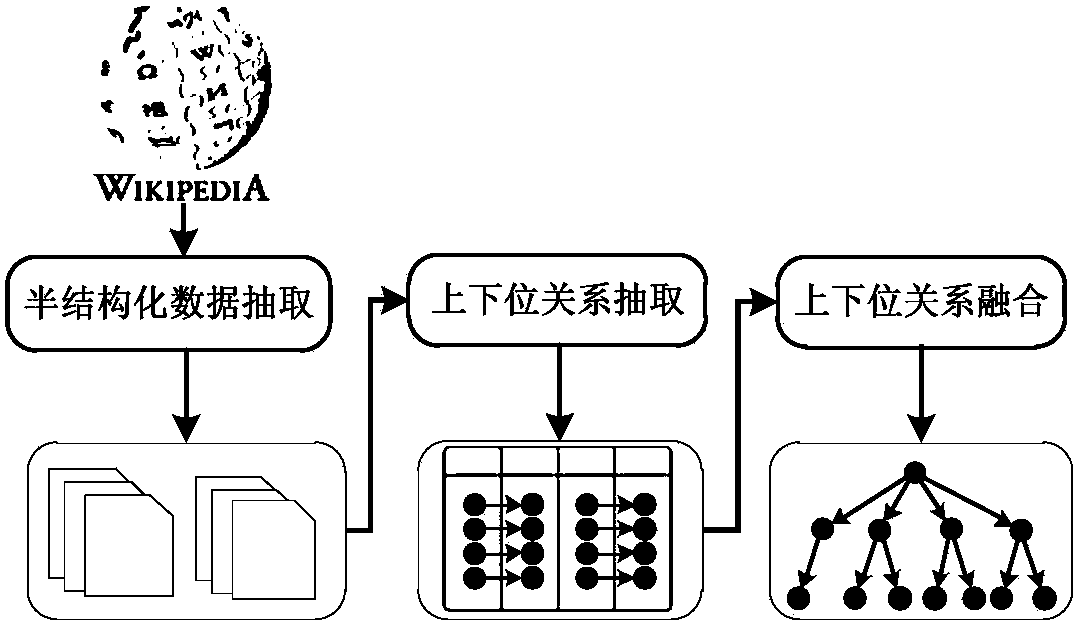
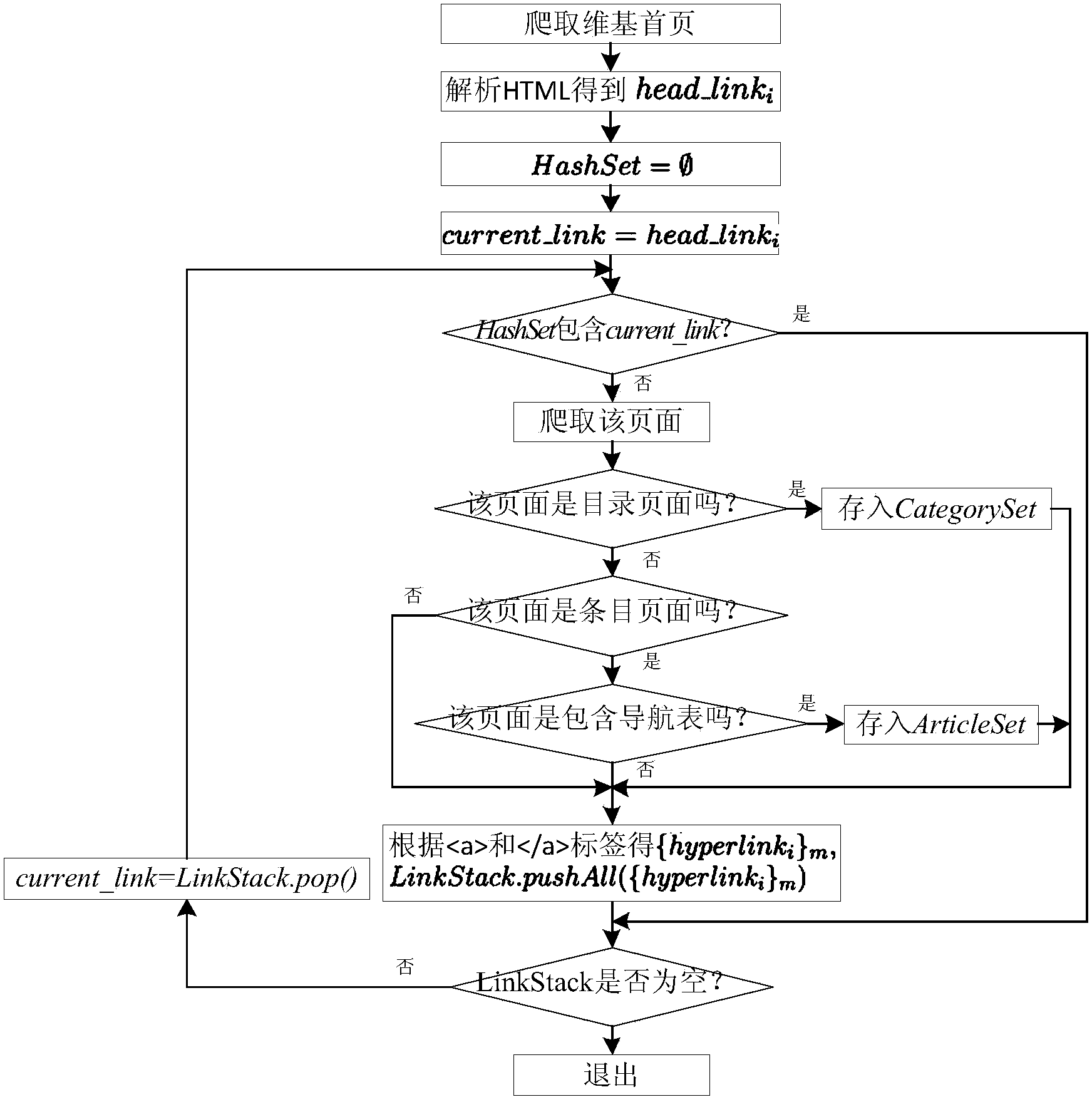
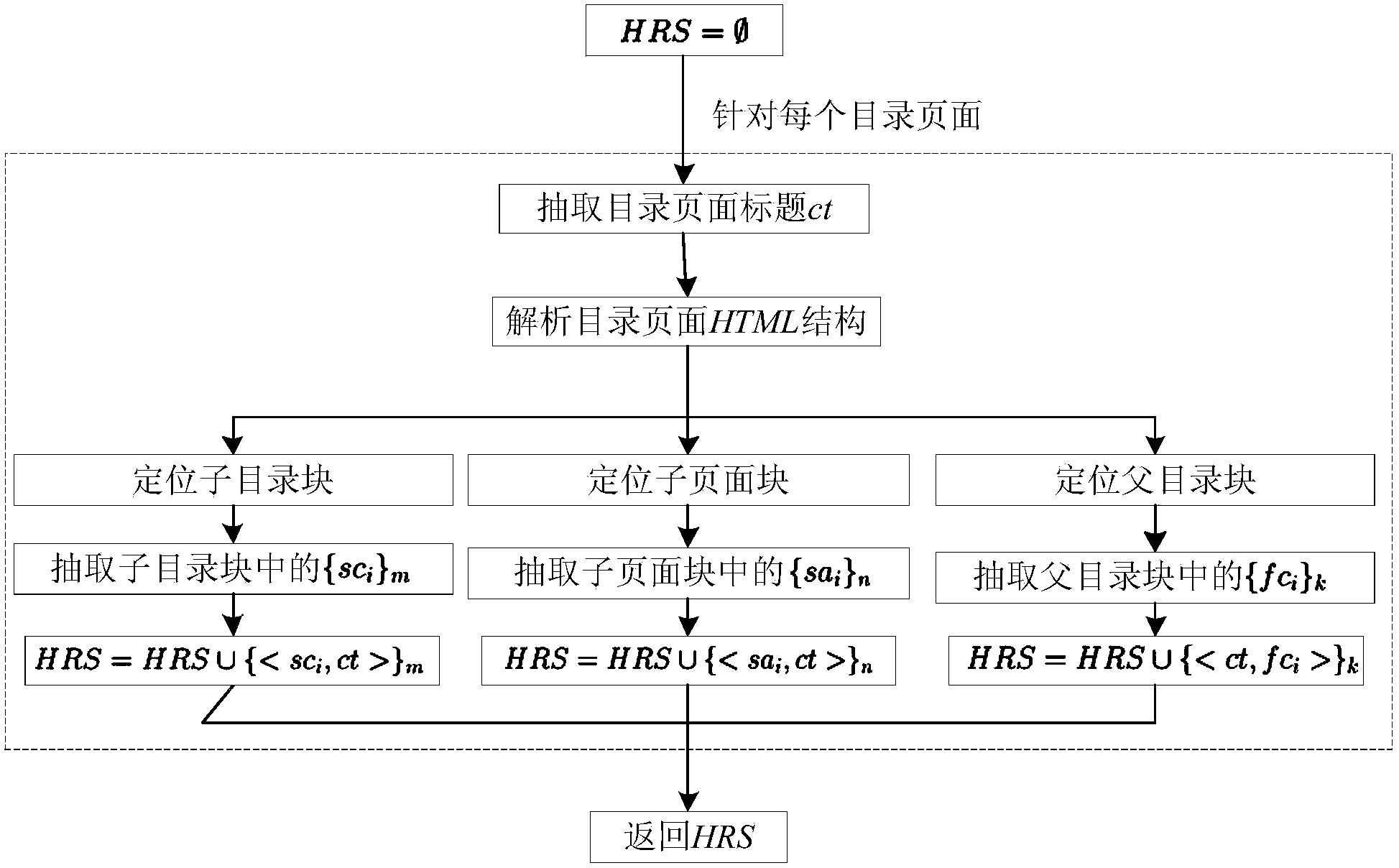
Method for automatically building classification tree from semi-structured data of Wikipedia
InactiveCN103778238ASimple technologyAuthoritativeSpecial data processing applicationsSemi-structured dataData mining
The invention discloses a method for automatically building a classification tree from the semi-structured data of Wikipedia. The method comprises the steps: (1) extracting the semi-structured data, to be specific, acquiring the HTML of a page by analysis, and identifying the page containing the semi-structured data; (2) extracting a hyponymy relationship among the semi-structured data, to be specific, acquiring the hyponymy relationship contained in a Wikipedia catalog page according to the layout characteristics of the Wikipedia catalog page, analyzing an HTML element, and acquiring the hyponymy relationship contained in a navigation table according to the structure of the navigation table; (3) integrating the hyponymy relationships from different semi-structured data, to be specific, building a simple directed and unweighted graph according to the extracted hyponymy relationship set, and then generating a classification tree based on the depth-first traversal algorithm of the simple directed and unweighted graph. The method can automatically extract the hyponymy relationship in Wikipedia pages, and build the classification tree, thereby reducing the building cost by experts in the domain, and fully reusing the hyponymy relationship manually built by volunteers.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com