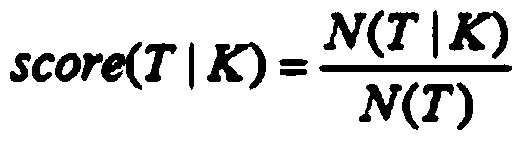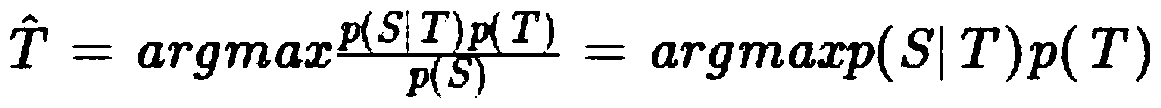Patents
Literature
79results about How to "Authoritative" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
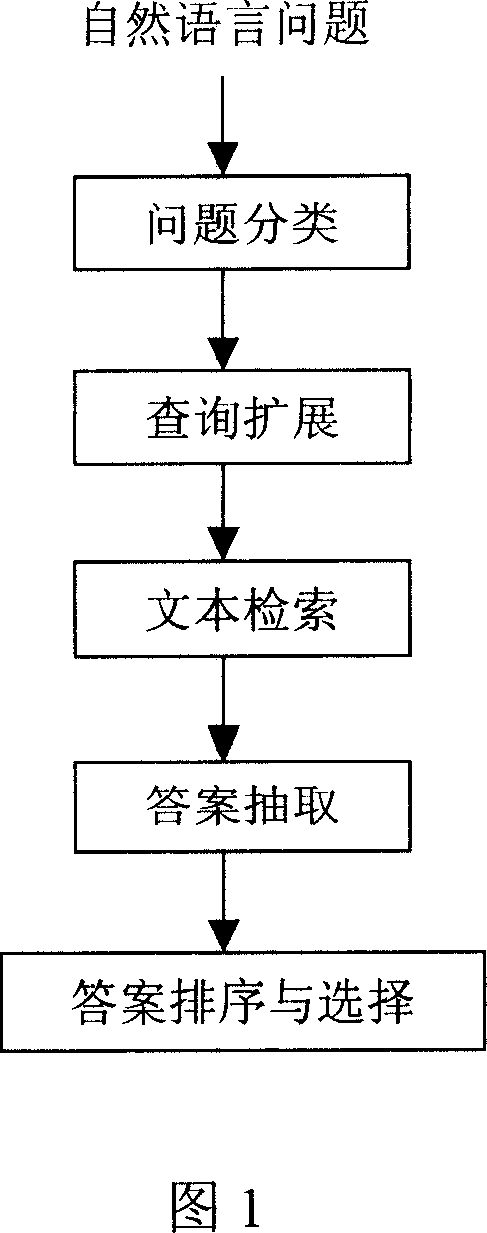
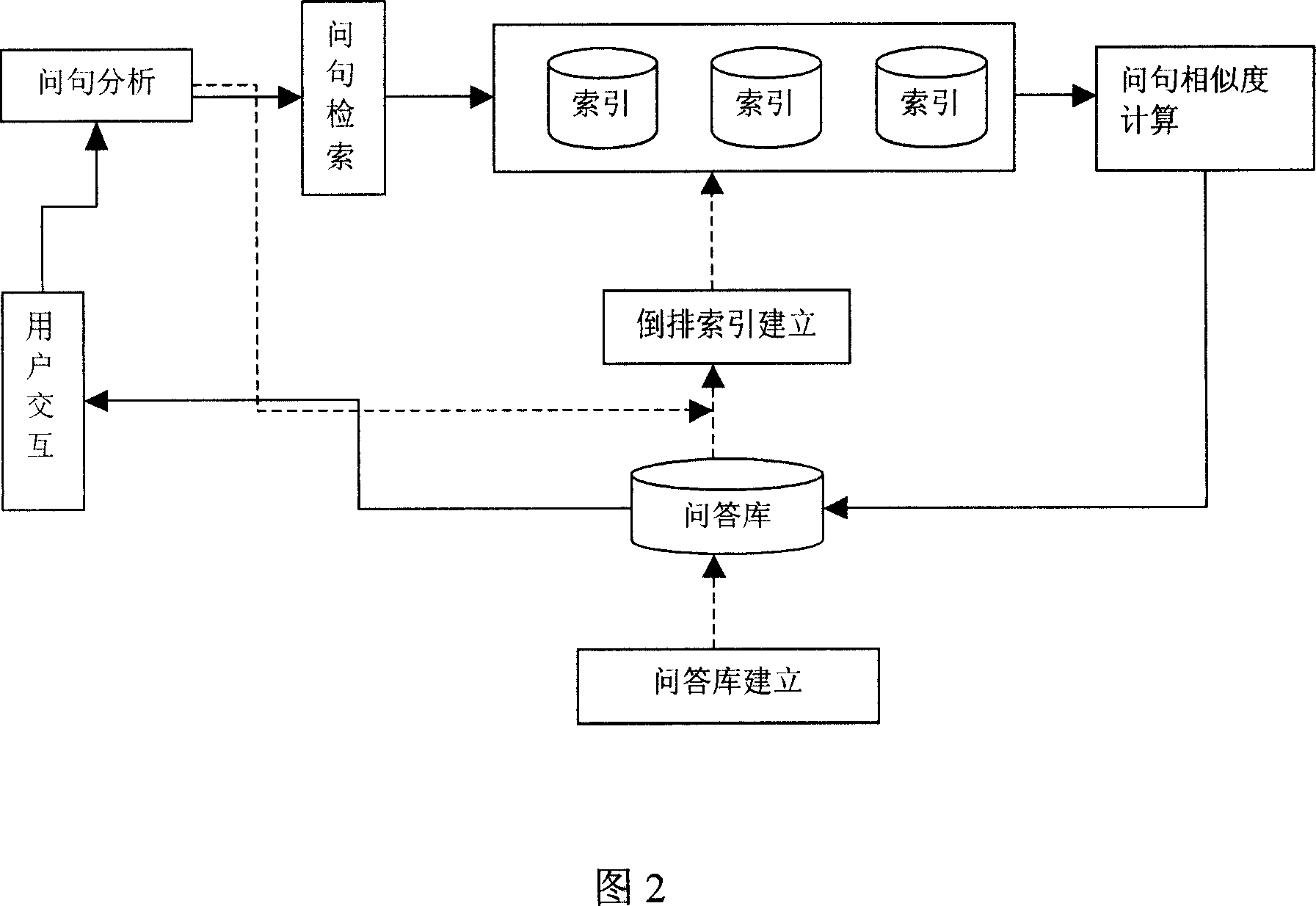
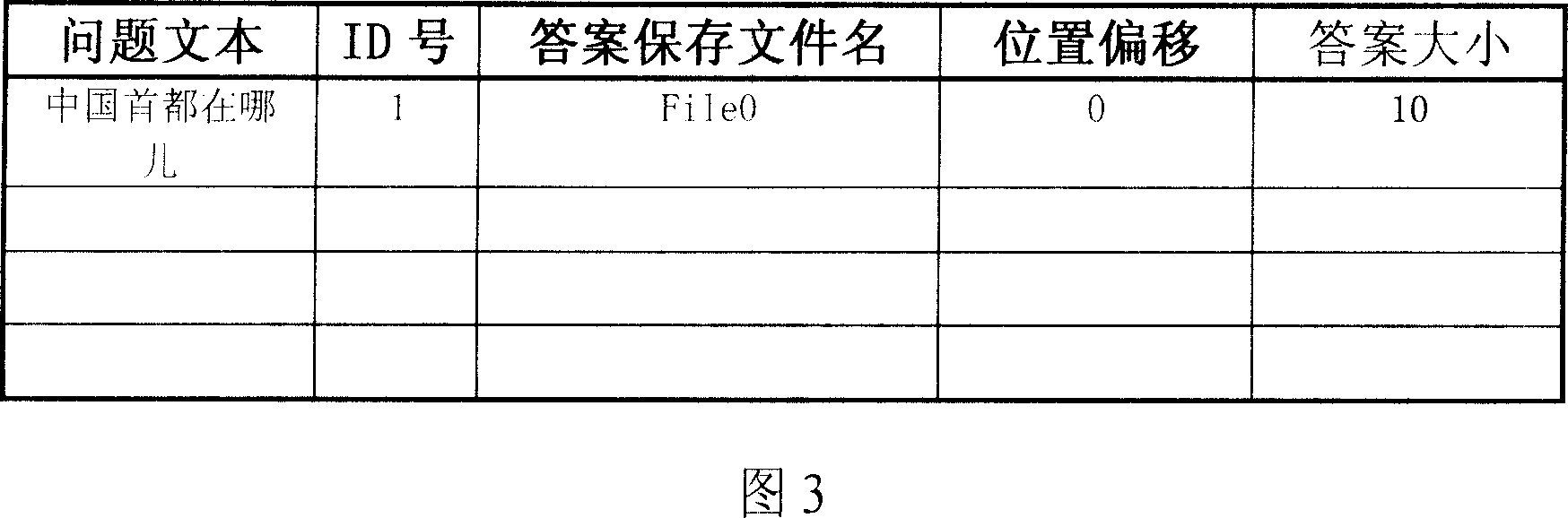
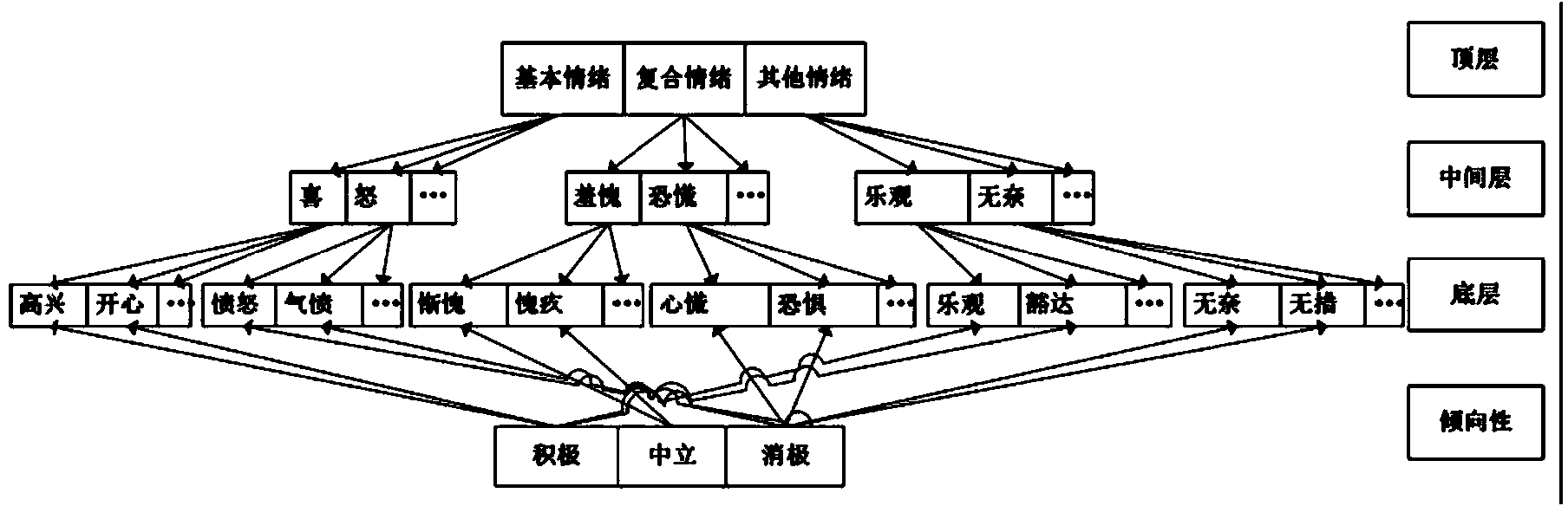
FAQ based Chinese natural language ask and answer method
InactiveCN1928864ARegular formatAuthoritativeSpecial data processing applicationsOpen communityWeb structure
The disclosed database-based Chinese natural language question-answering method comprises mainly analyzing Web structure to extract internet FAQ and question-answering from opening community to build database. Unlike to prior art, this invention can accept natural language query and return the answer directly without user screening, and overcomes defects in a certain extent.
Owner:ZHEJIANG UNIV
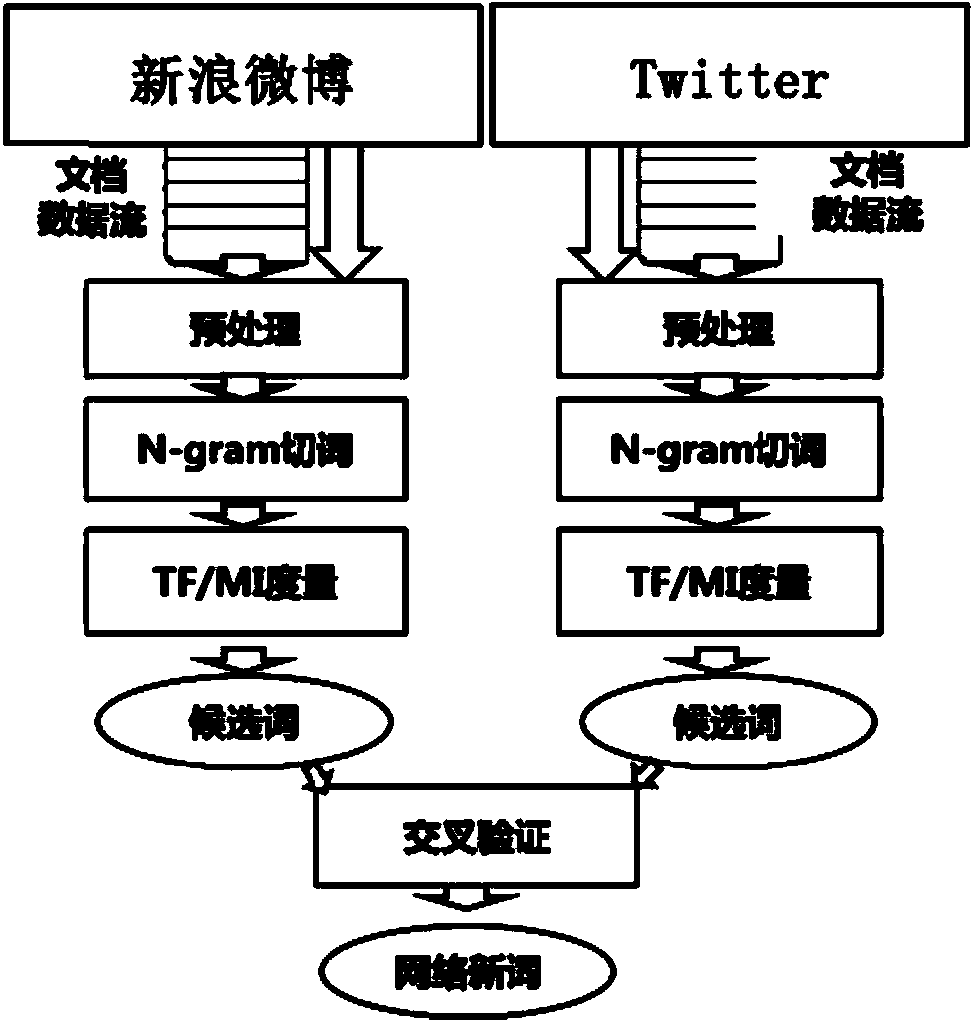
Extraction method for network new words in microblogs and microblog emotion analysis method and system
InactiveCN103559233AEnsure comprehensivenessAvoid sparsitySemantic analysisSpecial data processing applicationsEmotion detectionText corpus
The invention discloses an emotion analysis method which aims at network microblogs. The emotion analysis method which aims at the problem that in the traditional emotion analysis, expression of diversification emotion of emergencies is not enough is based on a multi-dimensional vector representation model. The emotion analysis method comprises extracting emotional words in combination with a clinical psychological emotion detection table and initializing emotion analysis vectors; automatically finding the network new words in the microblogs through a method which is based on large-scale corpuses and statistics, automatically absorbing the network new words and emotional identifiers which can express emotion, continuously expanding the emotion vectors and setting a gradational structure of the emotion vectors; performing multi-dimensional emotion analysis and timing sequence analysis on the microblogs based on an existing vector model.
Owner:NAT UNIV OF DEFENSE TECH
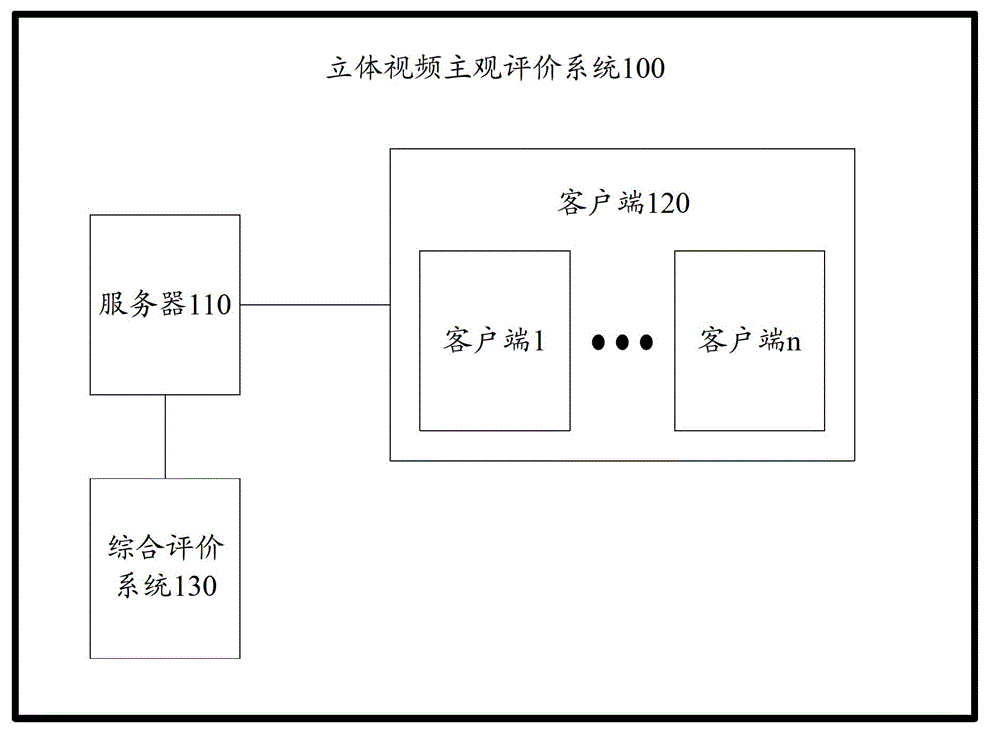
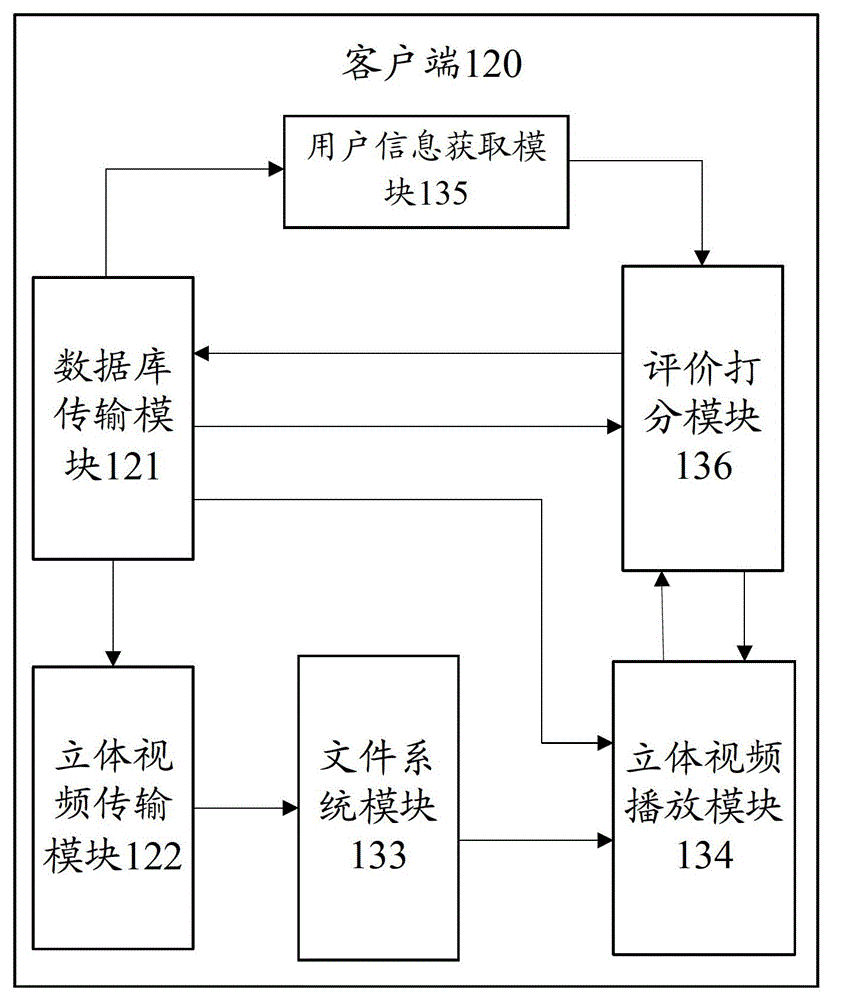
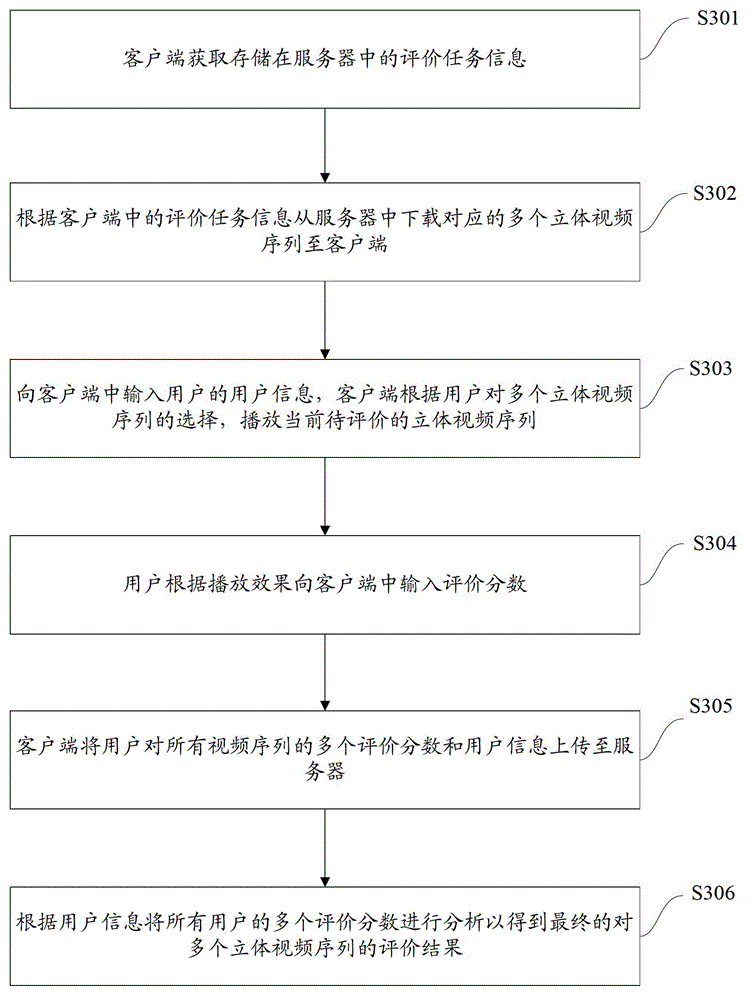
System and method for subjective assessment of stereoscopic videos
InactiveCN102724544AImprove objectivityAuthoritativeTelevision systemsSteroscopic systemsStereoscopic videoVideo sequence
The invention provides a system and a method for subjective assessment of stereoscopic videos. The system comprises a server, a client side and a comprehensive assessment system, wherein the server is used for storing assessment task information and video sequences; the client side is used for acquiring the assessment task information in the server, acquiring a plurality of corresponding video sequences from the server according to the assessment task information, recording user information and playing current to-be-assessed video sequences according to user's choices so as to store assessment scores after the user completes assessment of the current to-be-assessed video sequences, and uploading the user's assessment score of each video sequence of the video sequences and the user information to the server; and the comprehensive assessment system connected with the server is used for making statistics on user number according to the user information and analyzing all the assessment scores according to the user number so as to obtain final assessment results. According to the embodiment, mutual interference among assessment staff is lowered, and assessment objectivity is guaranteed so that the assessment results are more authoritative and persuasive.
Owner:TSINGHUA UNIV +1
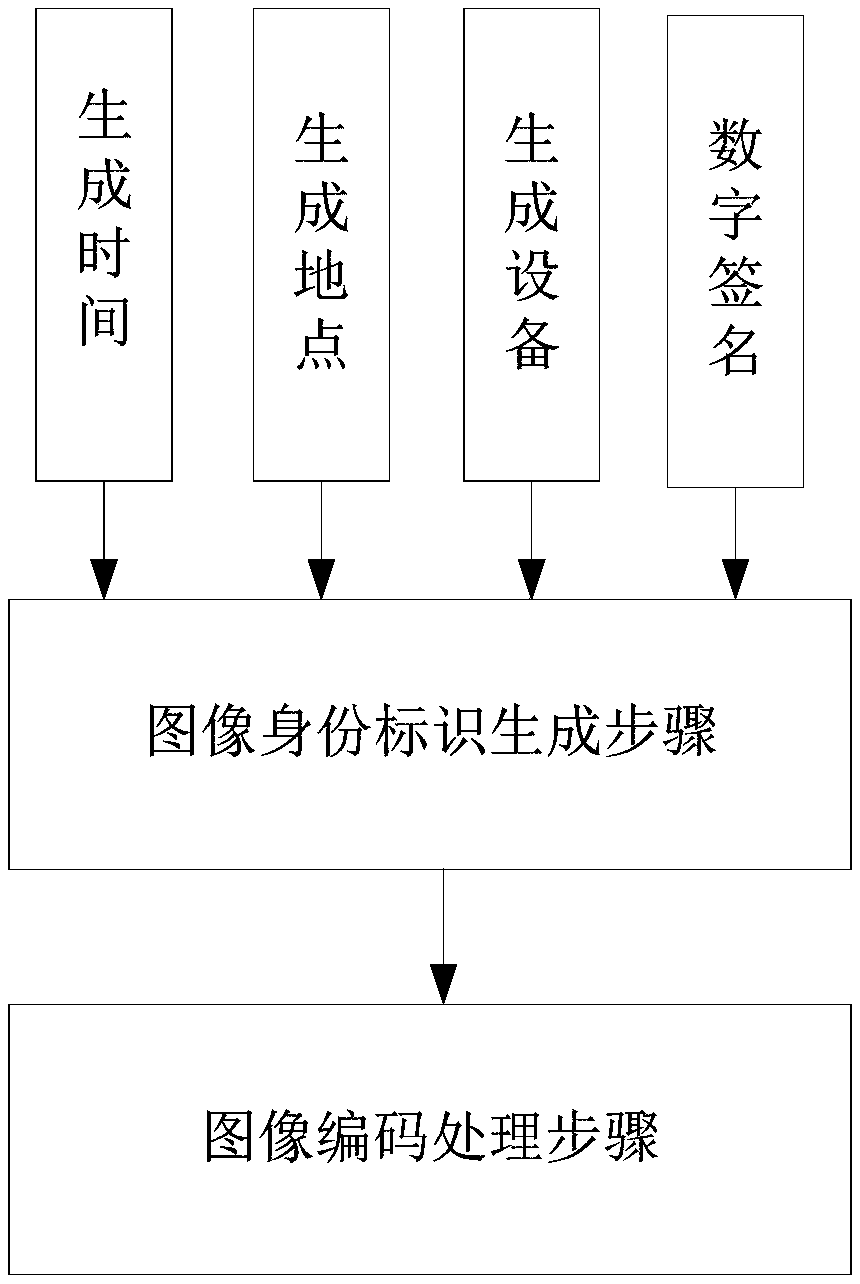
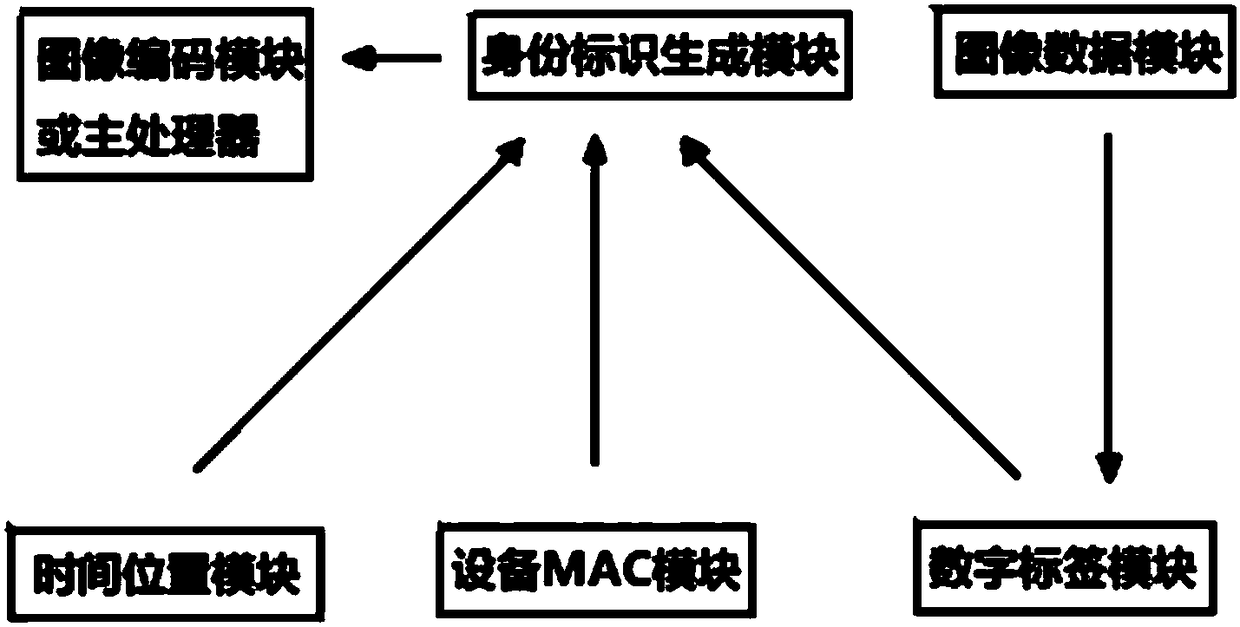
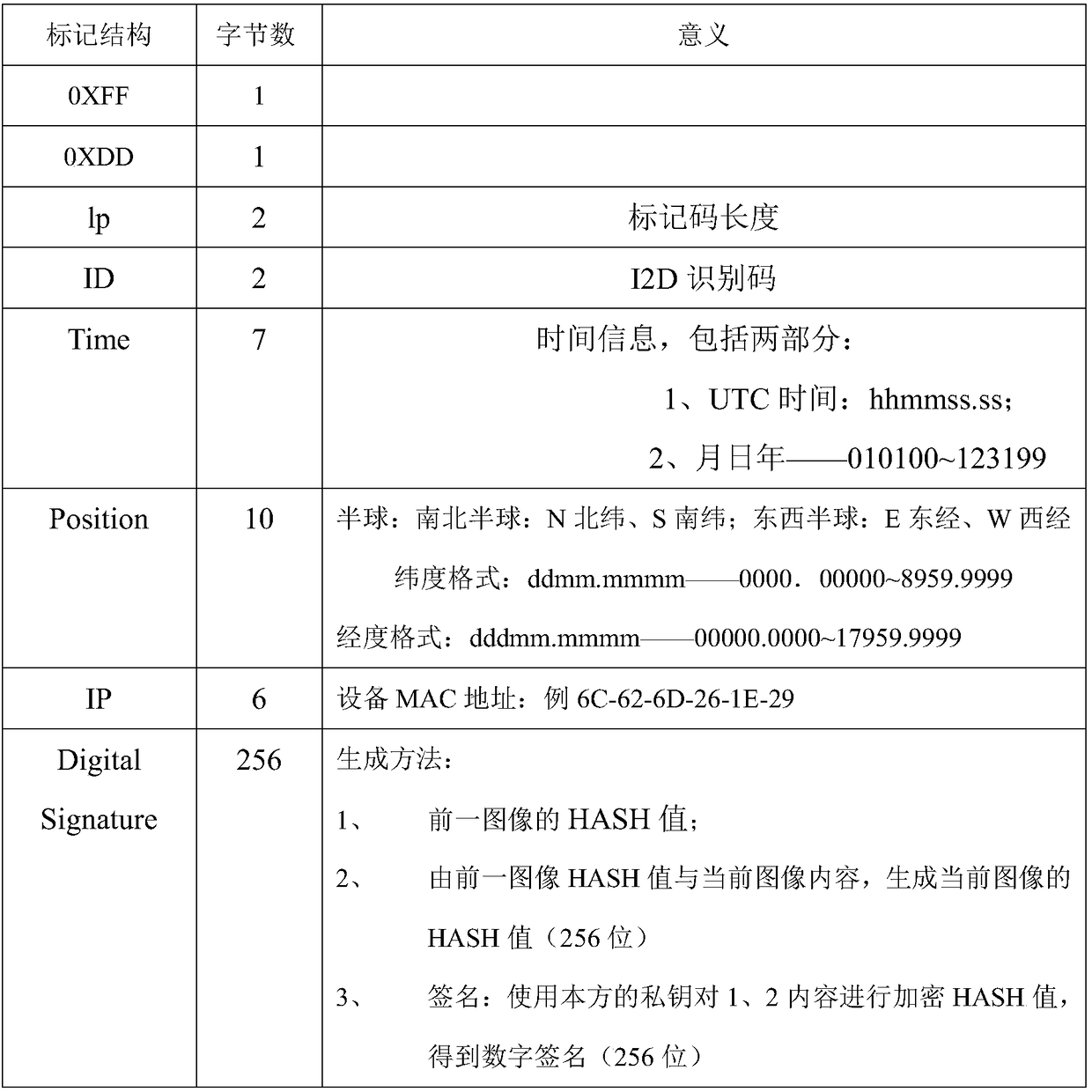
Identity identification method and system for image and video data
InactiveCN108551582AUniqueness guaranteedAuthoritativeUser identity/authority verificationDigital video signal modificationPattern recognitionDigital signature
The invention discloses an identity identification method and an identity identification system for image and video data. The identity identification method comprises the steps of: during acquisitionof each image, forming identity identification information of the image by reading local information, wherein the identity identification information at least comprises an image generation time, an image generation location, image generation equipment and a digital signature of the image; performing image coding on the identity identification information to enable coded image data to comprise theidentity identification information of the image, so as to obtain the unique identity identification of the image, i.e., an image ID. For video data, a video ID describing video sequence information is formed by image identity identification information of key frames. Through adoption of the identity identification method of the invention, the unique ID is designed for the image and video data, thereby providing meta-information with uniqueness, authority, safety, universality and privacy for processing such as coding, channel transmission and decoding reestablishment, space-time synchronization fused analysis, tracing and tamper resistant of the image.
Owner:SHANGHAI JIAO TONG UNIV
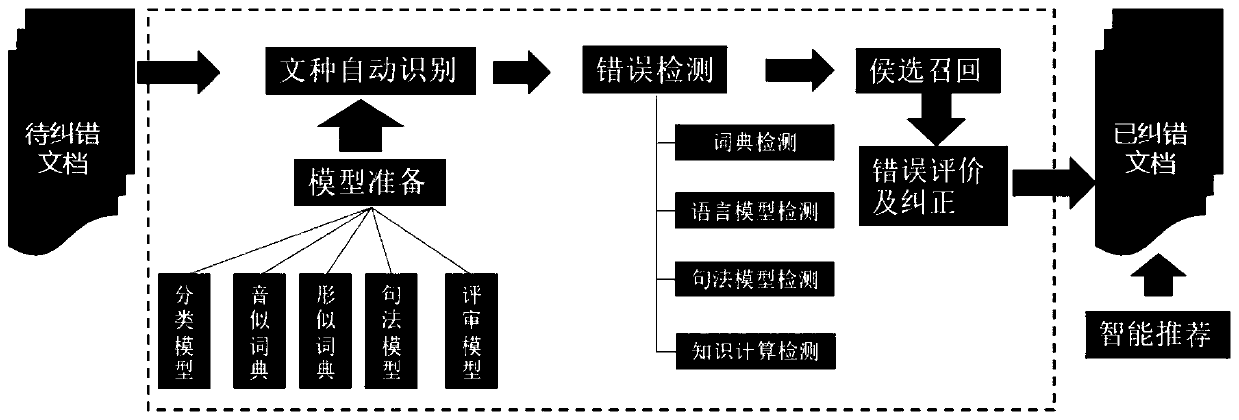
Official document error correction method
InactiveCN111090986AImprove error correction performanceAuthoritativeSemantic analysisCharacter and pattern recognitionText recognitionText detection
The invention discloses an official document error correction method, which comprises the following steps of: a text detection step: carrying out text recognition model training by utilizing machine learning, and classifying document texts into notification, report, approval, notification, letter, conference summary and ask-for-leave types; an error detection step: making word segmentation througha Chinese word segmentation device, detecting errors from the aspects of word granularity and word granularity, integrating suspected error results of the two types of granularity detection, to forma suspected error position candidate set; using a bidirectional character-level N-gram LM deep learning model for scoring characters in sentences, regarding the position with the low score as a position to be corrected, conducting dictionary word checking on the position to be corrected and context combinations, and when all the combinations cannot be found in a dictionary, regarding the combinations as wrong characters and added into a wrong position candidate set. According to the scheme, auditing requirements such as row text specifications, incomplete contents, unknown questions, grammar error correction, smoothness detection, context association and the like are combined, the characteristics are used for innovating, reconstructing and combining the existing technical scheme, and the error correction effect of the enterprise electronic official document can be effectively improved through tests.
Owner:FUJIAN YIRONG INFORMATION TECH +2
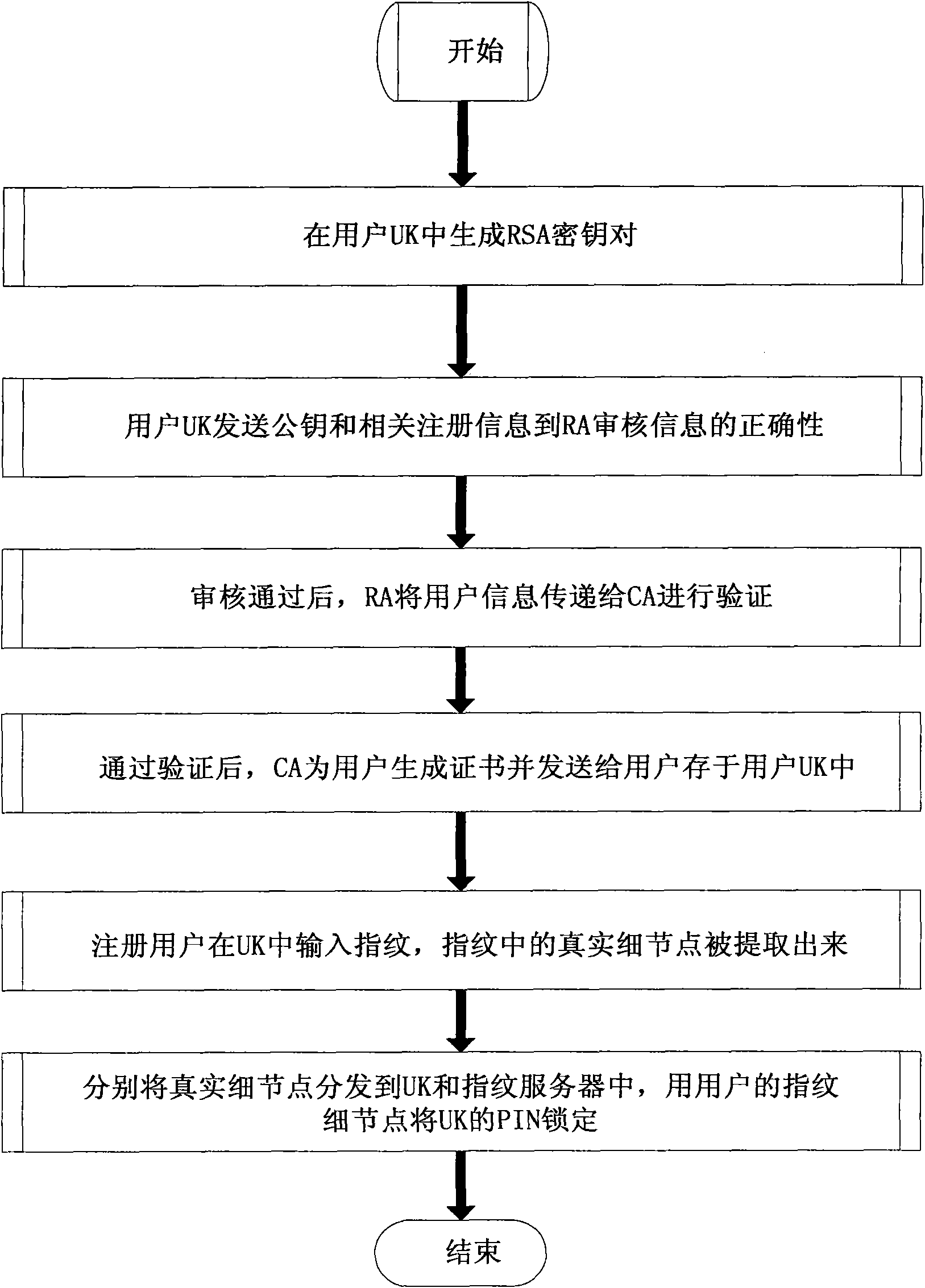
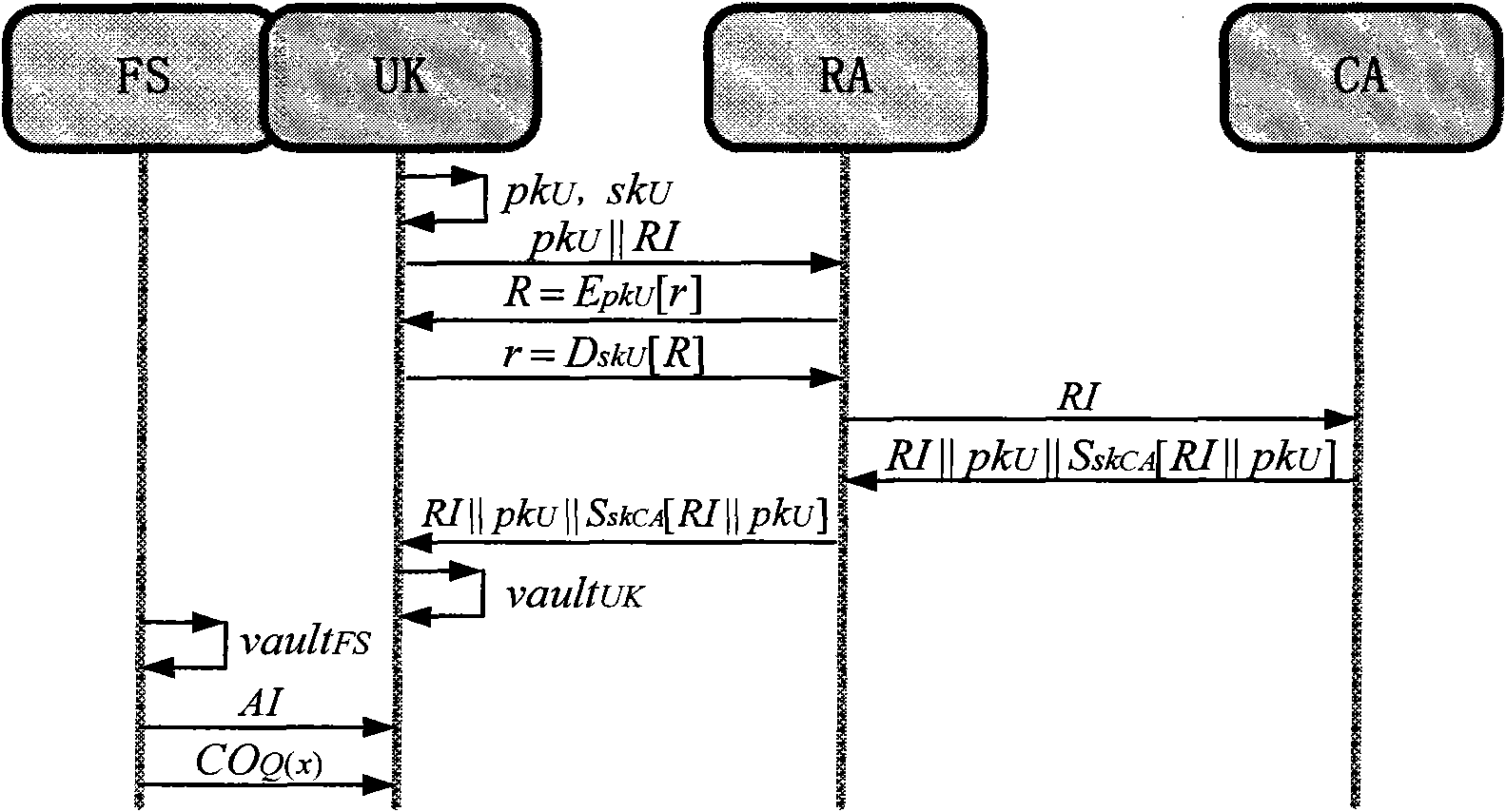
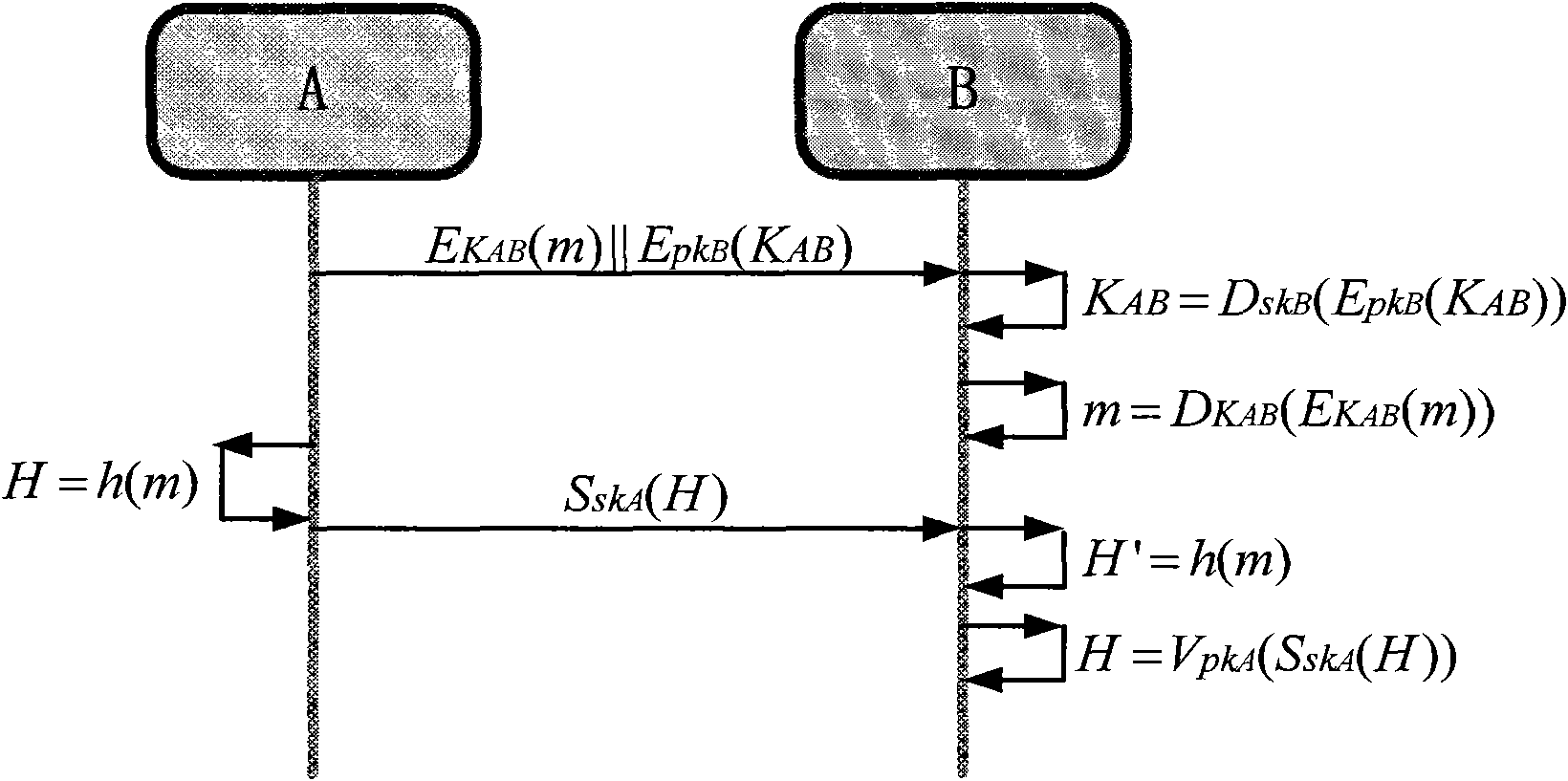
Identity authentication method based on fuzzy vault and digital certificate
InactiveCN101945114AImprove security and trustAvoiding the problem of forward secrecyUser identity/authority verificationUser informationRegistered user
The invention relates to an identity authentication method based on a fuzzy vault and a digital certificate, wherein the digital certificate and fingerprint identification are combined in a smart card, so that the digital identity and the physical identity of a user correspond to realize the identity authentication with high safety. The method comprises the following steps of: firstly generating an RSA key pair in a user UK, and sending a public key and relevant registration information to an RA for auditing by the user UK; when the auditing is passed, transferring user information to a CA for verification by the RA; after the verification is successful, generating the digital certificate for the user and sending to the user to be stored in the UK by the CA; and inputting a fingerprint in the UK by the registered user, extracting the true detail points in the fingerprint, dispensing the true detail points into the UK and a fingerprint server, and locking the PIN of the UK by the true detail points of the user, so that the digital certificate stored in the UK and a corresponding private key can be safely protected. In order to reduce the calculation amount of the smart card, a secret sharing method is introduced, so that only when the information in both the smart card and the server can be obtained, the PIN of the smart card can be recovered to release the digital certificate containing the private key.
Owner:XIDIAN UNIV +1
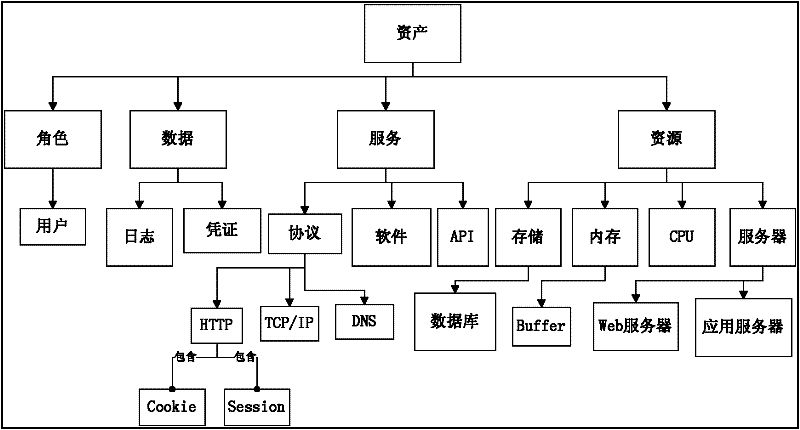
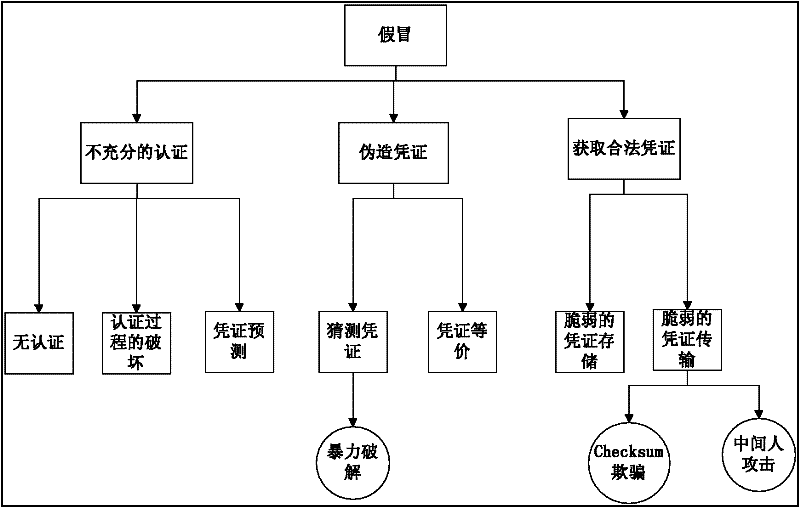
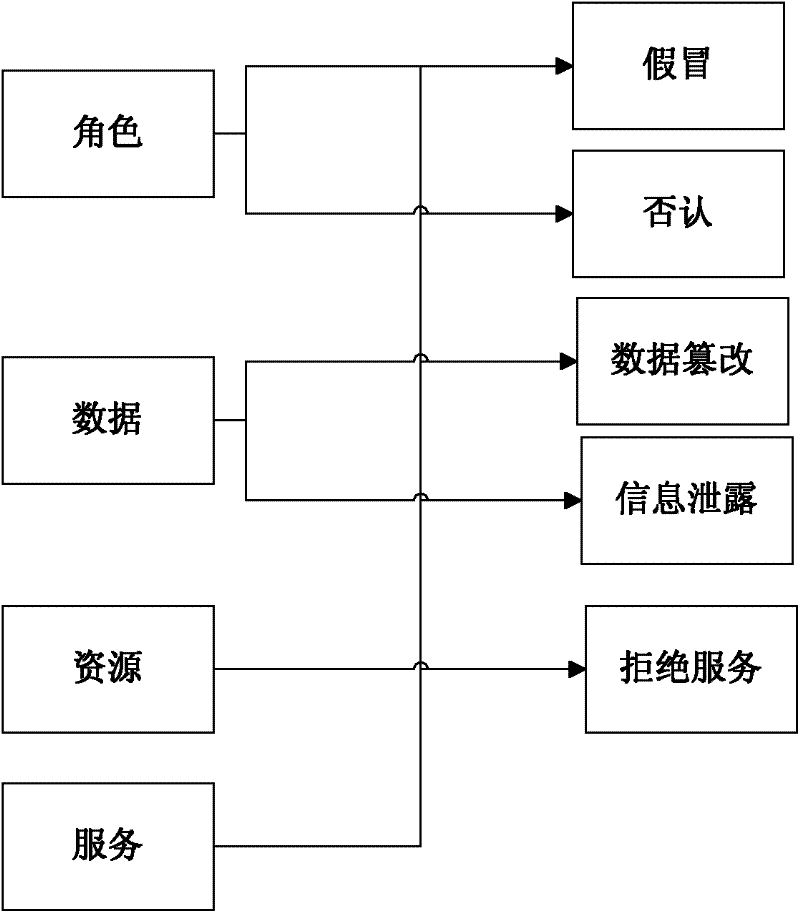
Security repository-based security requirement acquisition method
InactiveCN102236758AReduce repair costsImprove securityComputer security arrangementsSecurity functionSoftware development
The invention belongs to the field of dependable computing, and relates to a security repository-based security requirement acquisition method. The method comprises two parts: 1, classifying assets and threats respectively, establishing correspondence, and constructing an asset-threat repository comprising the assets, the threats and a security functional component; and 2, performing a specific security requirement acquisition process which comprises the steps of analyzing a case, determining the asset, analyzing the threat, detailing the security requirement and iterating the security requirement. The method is mainly used for security requirement analysis and information acquisition of software at a requirement analysis stage by using CC (Common Criteria) standard, so that the security flaw at the early stage of software development is reduced.
Owner:TIANJIN UNIV
Method for building an ISSR (inter-simple sequence repeat) fingerprint applicable to distinguishing and identification of Ulmus varieties
InactiveCN102605061ARapid identificationAccurate identificationMicrobiological testing/measurementElectrophoresisA-DNA
A method for building an ISSR (inter-simple sequence repeat) fingerprint applicable to distinguishing and identification of Ulmus varieties relates to a method for building an ISSR fingerprint, and includes: firstly, extracting DNA; secondly, performing ISSR-PCR (ISSR-polymerase chain reaction) amplification and electrophoresis; thirdly, building a DNA fingerprint; and fourthly, using the built DNA fingerprint to identify Ulmus varieties. The method is convenient for quick and accurate identification of Ulmus varieties. Compared with conventional planting test and biochemical test, the method is insusceptible to crop growth environment and season, and accordingly the results are more stable and reliable, and time and labor are economized. DNA fingerprint building and the identification technology lay a solid basis for wide application of ISSR molecule marker technology to plant variety identification, relationship analysis, plant genetic source innovation and molecular marker assisted selection. The method has the advantages of simplicity in operation, visuality, practicality and the like.
Owner:DAQING BRANCH OF HEILONGJIANG ACAD OF SCI
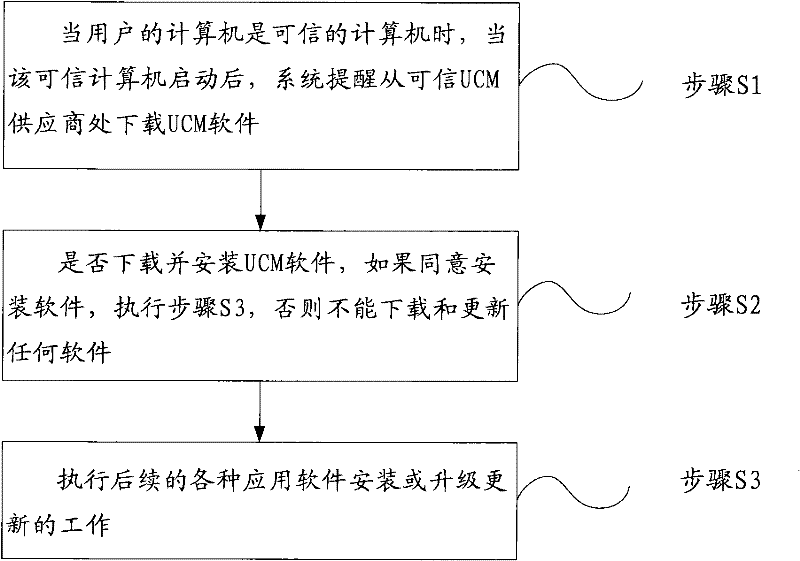
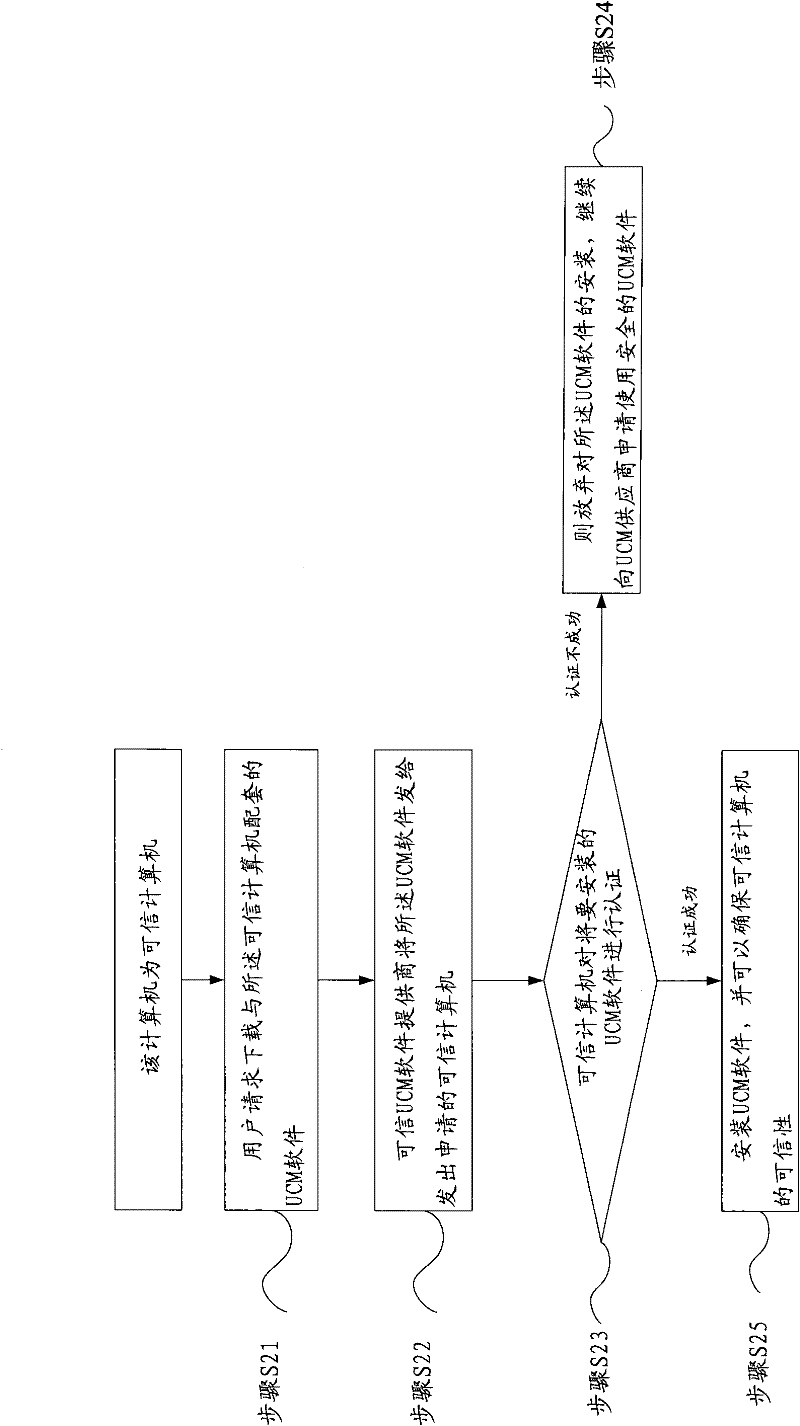
Trustiness measuring method for installing and upgrading software
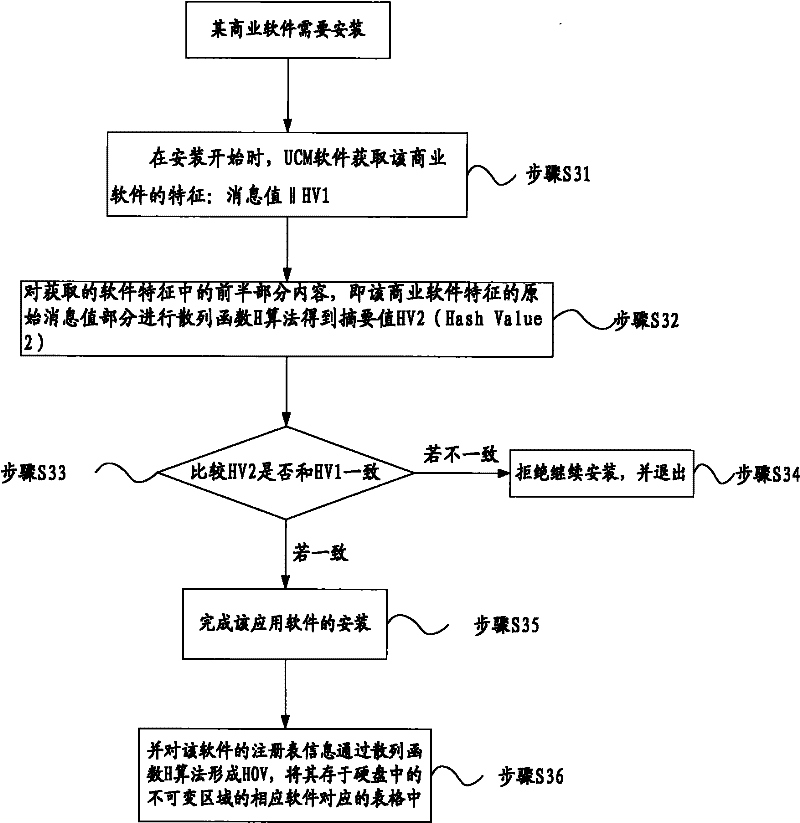
ActiveCN102236752AAuthoritativeQuick and easy measurementComputer security arrangementsProgram loading/initiatingChange managementTrusted Computing
The invention provides a trustiness measuring method for installing and upgrading software. The method comprises the following steps of: 1, in the case that a computer of a user is a trusted computer, prompting to download UCM (Unified Change Management) software from a trusted UCM provider by a system after the trusted computer is started; 2, determining whether to download and install the UCM software, if agreeing to install the UCM software, executing a step 3, otherwise, failing in downloading and updating of any software; and 3, executing subsequent various application software to finish installing or upgrading work. According to the method, the installed or upgraded software can be effectively measured, so that the installed or upgraded software is safe and trusted.
Owner:AEROSPACE INFORMATION
Linear model method used for simplified-Chinese readability measurement
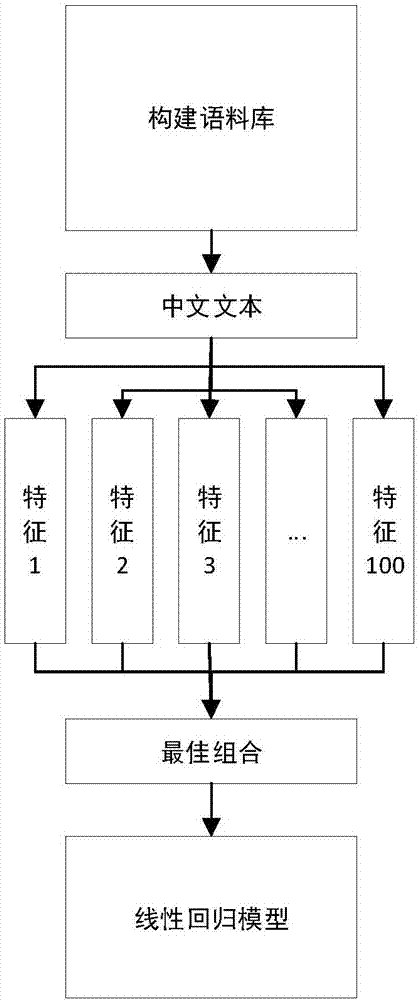
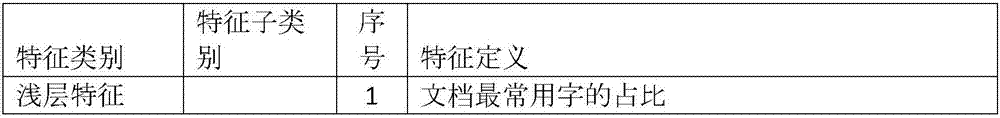
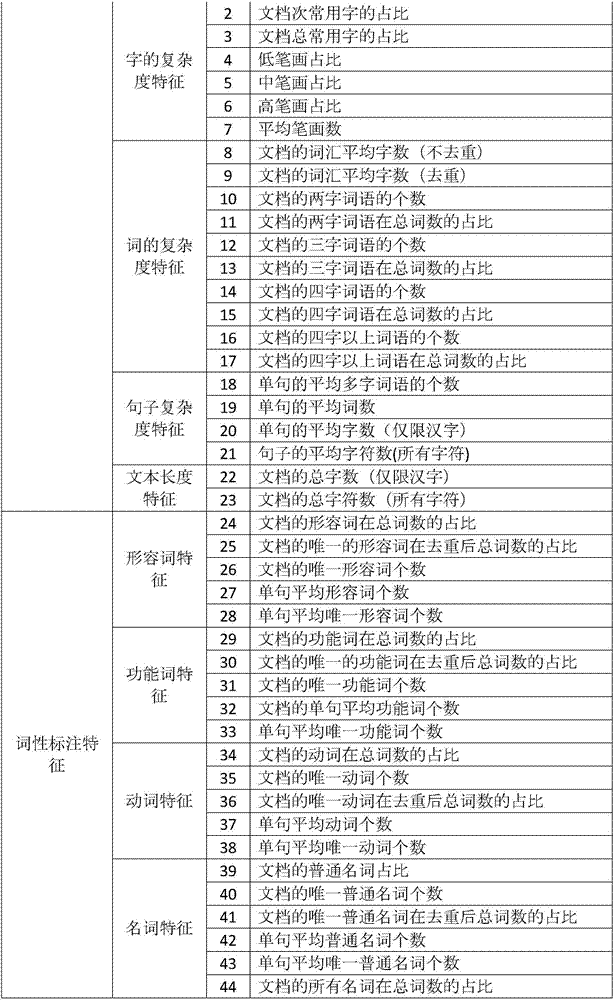
InactiveCN107977449AWide coverageAuthoritativeNatural language data processingSpecial data processing applicationsPart of speechSentence segmentation
The invention discloses a linear model method used for simplified-Chinese readability measurement. The method includes the steps of: constructing simplified-Chinese text and a readability level corpusthereof; preprocessing the text, wherein word segmentation, sentence segmentation, part-of-speech labeling, named-entity recognition, component syntax analysis, dependency syntax analysis, clause labeling and stroke counting are included; extracting and calculating text language features; constructing a best feature combination according to the language features and a regression algorithm; and constructing a linear regression model of readability measurement. The text language features adopted by the model cover four aspects of shallow-layer features, part-of-speech label features (also called semantic or lexical features), grammatical features, textual features and the like, a readability level of simplified-Chinese text for learners of which native languages are Chinese can be automatically predicted, and a gap of readability prediction models based on the simplified-Chinese text is filled. The model of the invention is high in a fitting degree, is high in interpretability, and hasextensibility and an important reference value for evaluating readability of application text.
Owner:GUANGDONG UNIVERSITY OF FOREIGN STUDIES
Method for automatically building classification tree from semi-structured data of Wikipedia
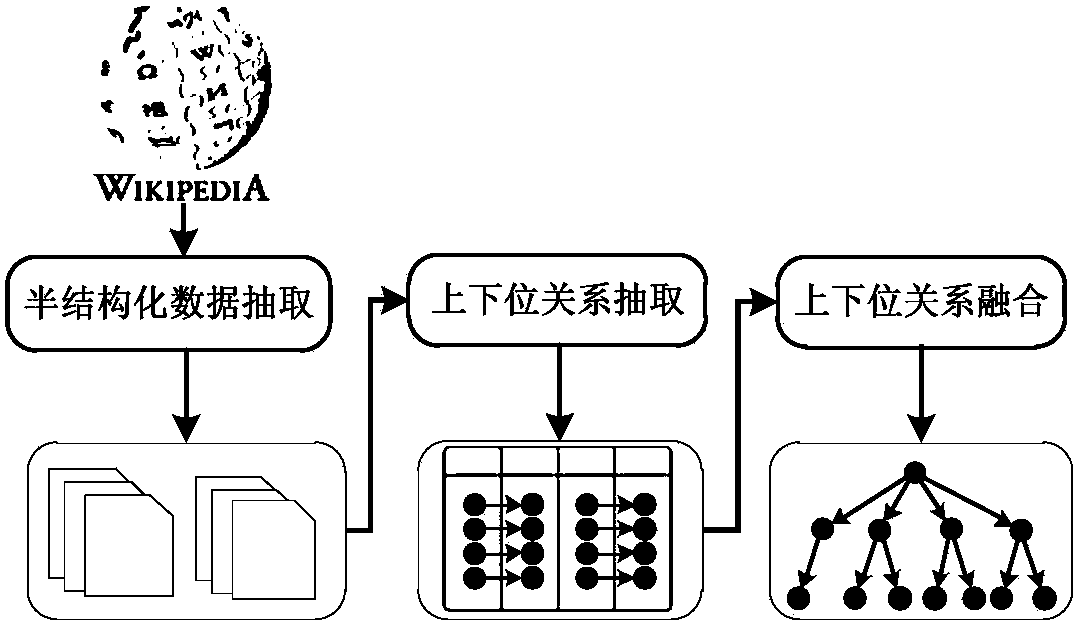
InactiveCN103778238ASimple technologyAuthoritativeSpecial data processing applicationsSemi-structured dataData mining
The invention discloses a method for automatically building a classification tree from the semi-structured data of Wikipedia. The method comprises the steps: (1) extracting the semi-structured data, to be specific, acquiring the HTML of a page by analysis, and identifying the page containing the semi-structured data; (2) extracting a hyponymy relationship among the semi-structured data, to be specific, acquiring the hyponymy relationship contained in a Wikipedia catalog page according to the layout characteristics of the Wikipedia catalog page, analyzing an HTML element, and acquiring the hyponymy relationship contained in a navigation table according to the structure of the navigation table; (3) integrating the hyponymy relationships from different semi-structured data, to be specific, building a simple directed and unweighted graph according to the extracted hyponymy relationship set, and then generating a classification tree based on the depth-first traversal algorithm of the simple directed and unweighted graph. The method can automatically extract the hyponymy relationship in Wikipedia pages, and build the classification tree, thereby reducing the building cost by experts in the domain, and fully reusing the hyponymy relationship manually built by volunteers.
Owner:XI AN JIAOTONG UNIV
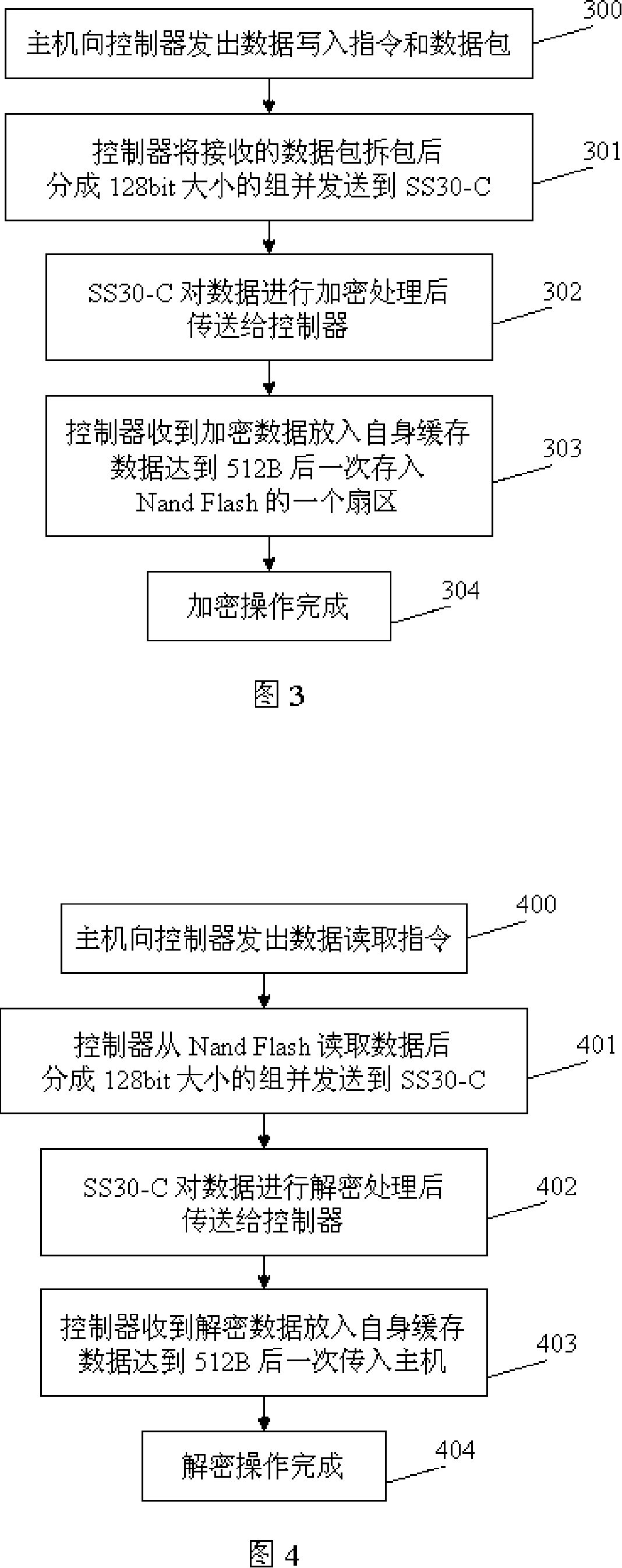
Enciphered mobile storage apparatus and its data access method
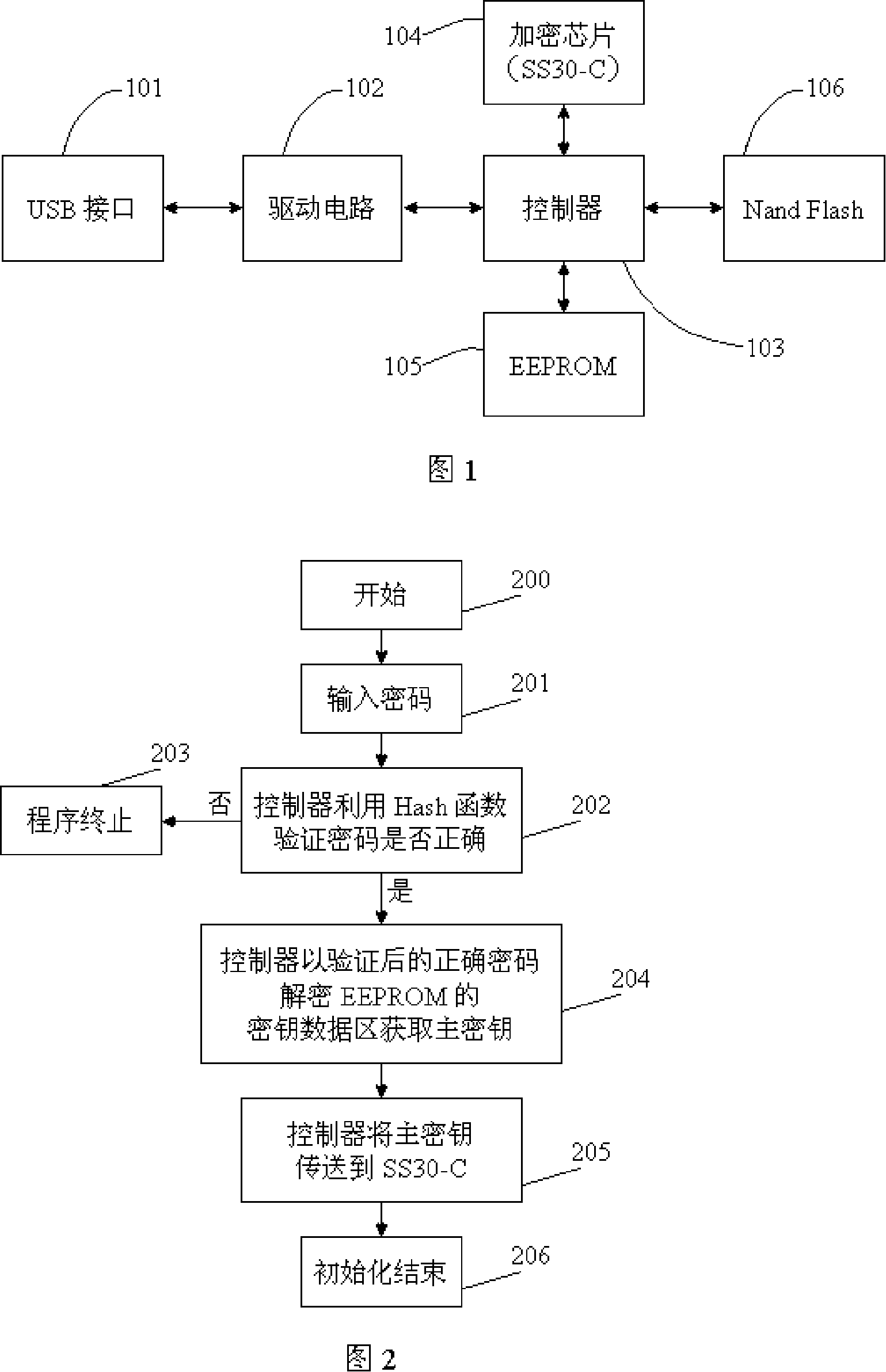
InactiveCN101127013AAuthoritativeReliableUnauthorized memory use protectionInternal/peripheral component protectionAccess methodData access
The utility model relates to data encryption technology, in particular to an encrypted mobile memory device and the data access method. The utility model discloses a mobile memory device that adopts hardware encryption and the data access method to strengthen the security of storing data of mobile memory devices. The technical proposal of the utility model is that: the encrypted mobile memory device comprises a USB interface, a drive circuit, a controller, a memory and an encryption chip; the USB interface, the drive circuit, the controller and the memory are connected sequentially; the encryption chip is connected with the controller; the encryption chip is used for the encryption of stored data and the decryption of read data. The utility model also discloses the data access method of the device. The utility model has the advantages that: special chip hardware encryption is adopted; the encryption algorithm is authentic and reliable; the encryption intensity is high and the secrecy is strong. Decryption data cannot be gotten even the mobile memory device is taken apart and the memory is taken out if the device is not decrypted by the encryption chip.
Owner:CHENGDU SANTAI ELECTRONICS INDUSTRY CO LTD
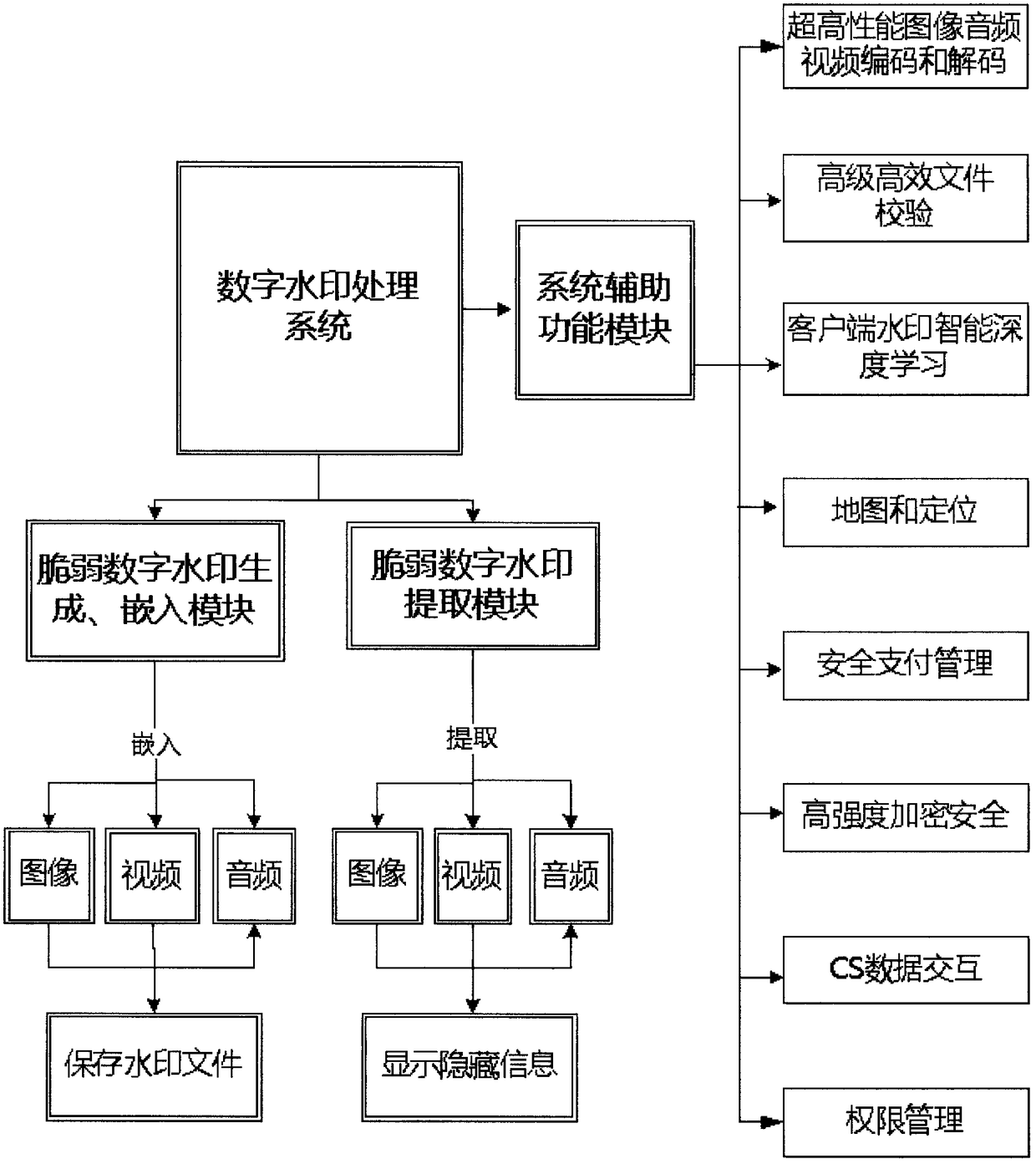
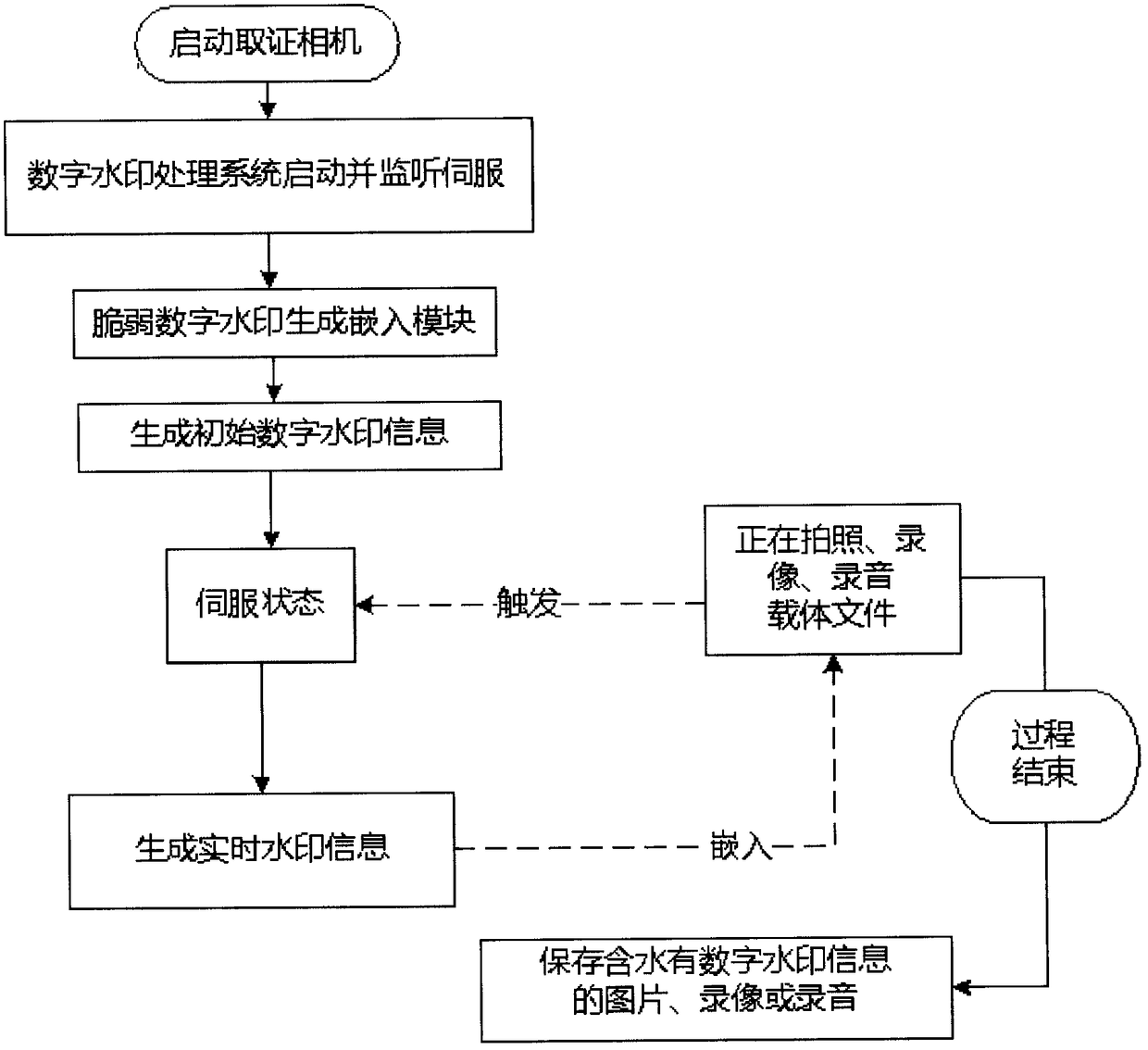
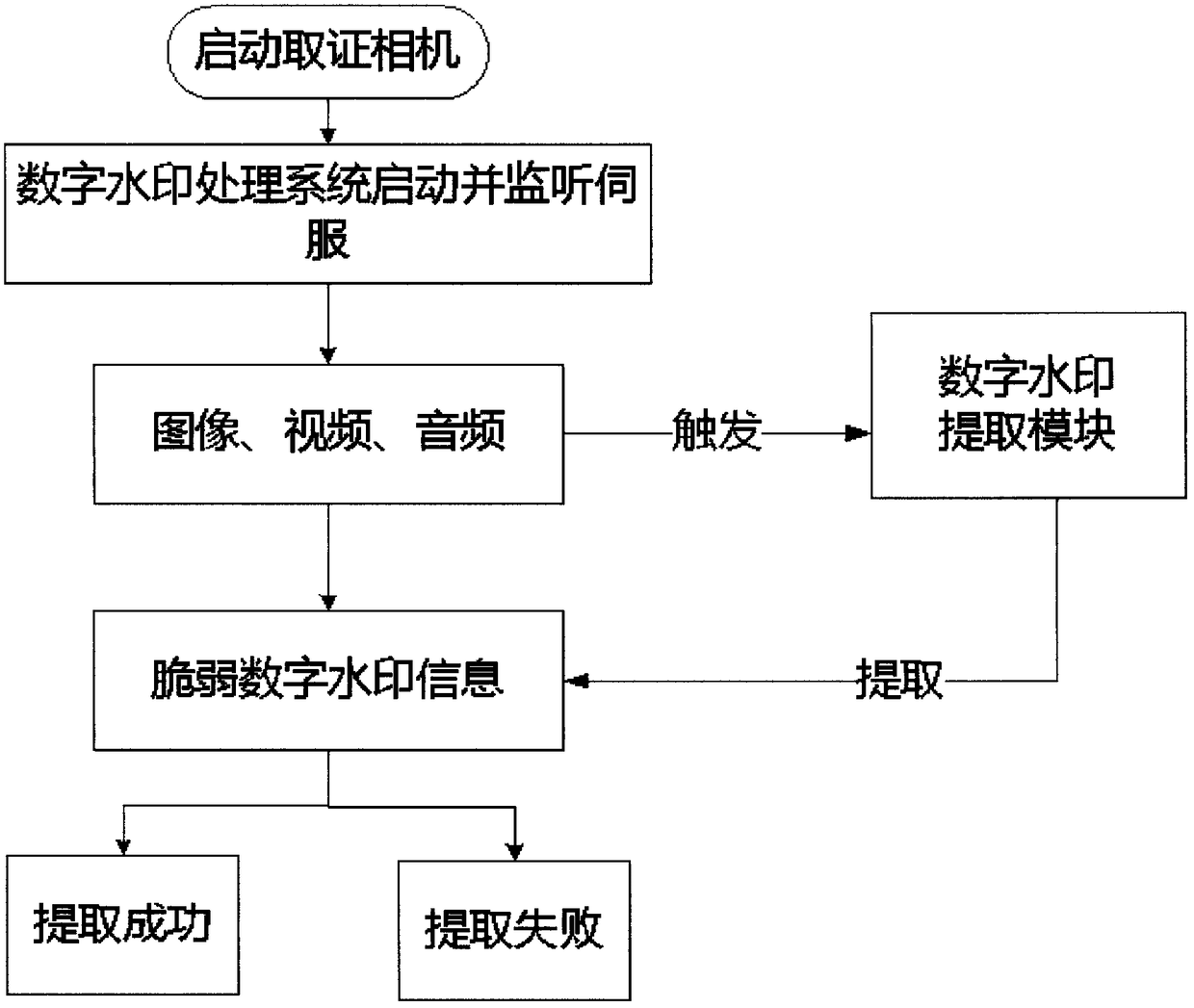
Multimedia digital watermark evidence taking mobile phone
ActiveCN109151157AGain credibilityHave completeSubstation equipmentDigital video signal modificationFragilityDigital evidence
The invention discloses a multimedia digital watermark evidence taking mobile phone. The multimedia digital watermark evidence taking mobile phone is an intelligent evidence taking mobile phone whichuses the unique stability, concealment, security and fragility of a fragile digital watermark to ensure the integrity, the authenticity, the stability, the reliability and the authority of photographed and recorded multimedia data based on an image, audio and video fragile digital watermark embedding and extraction technology. When a user uses the mobile phone, imperceptible and unmodifiable fragile digital watermark information with unique identity confirmation is embedded in real time in a photographed image, audio and video. The image or the audio or the video with the fragile watermark canbe normally used and distributed but can not be modified manually. The authenticity of a file can be identified according to whether the photographed digital file contains the digital watermark information. The evidence taking process is quick, efficient, accurate, safe and convenient. The evidence taking content has the uniqueness of a digital evidence and the legal authority of evidence use, and the multimedia digital watermark evidence taking mobile phone disclosed in the invention can be used for evidence taking and recording in fields such as judicature, law enforcement and claim.
Owner:CHENGDU YUFEI INFORMATION ENG
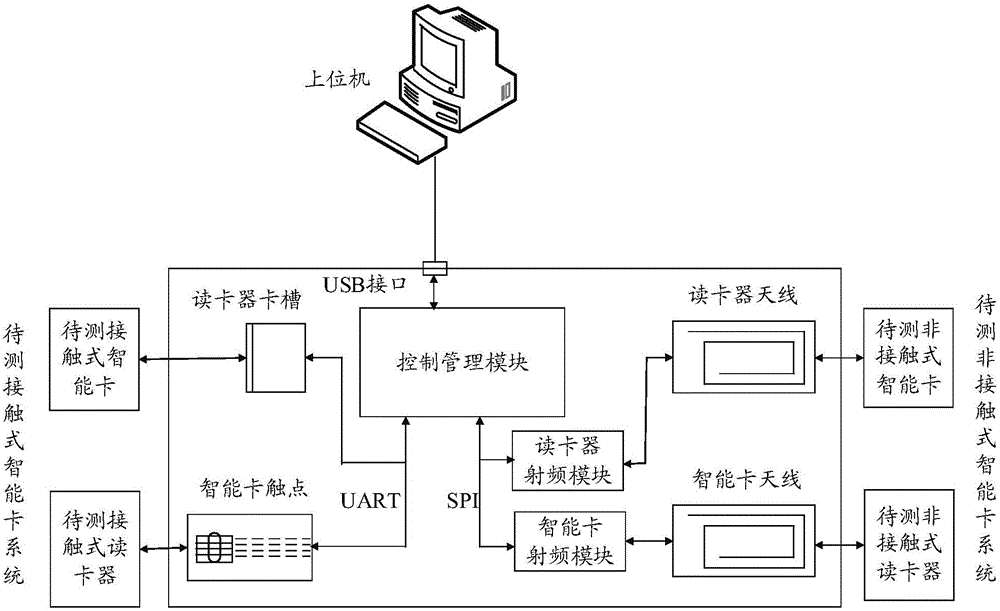
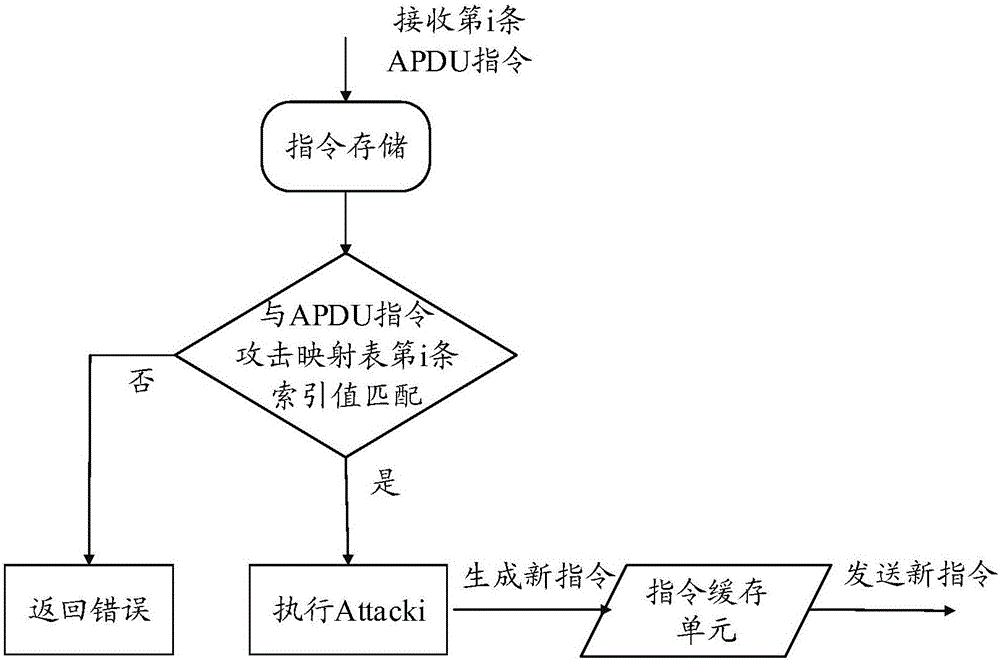
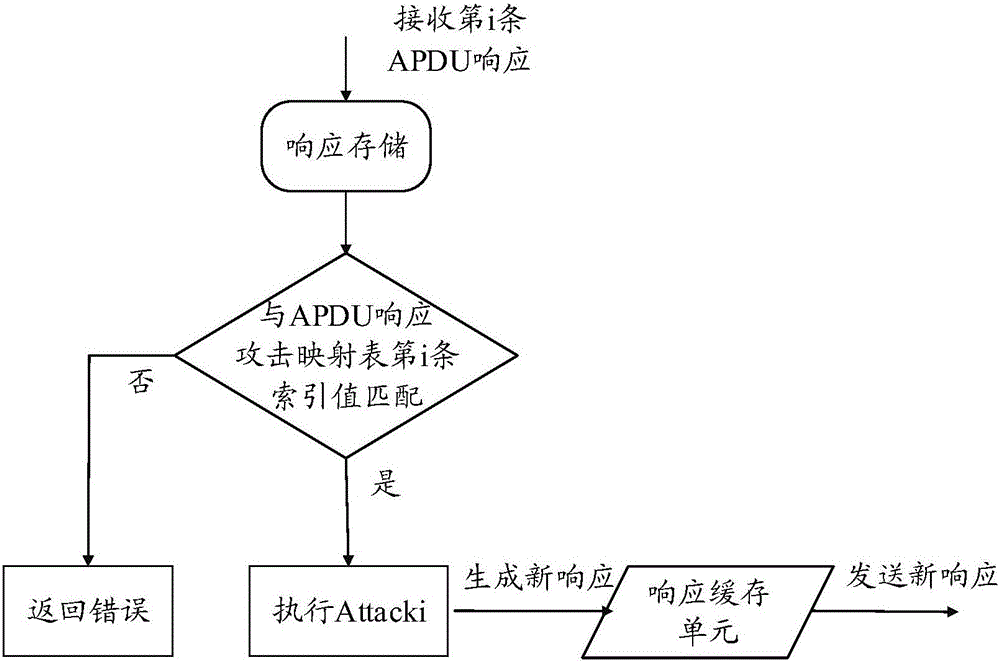
Intelligent card system man-in-the-middle attack verification platform and test method
ActiveCN106021117AGuarantee authenticityGuaranteed validitySoftware testing/debuggingPlatform integrity maintainanceMan-in-the-middle attackProcessing Instruction
The invention relates to an intelligent card system man-in-the-middle attack verification platform and a test method. One end of the verification platform conducts communication with an intelligent card, and the other end of the verification platform conducts communication with a card reader. A control management module is arranged in the verification platform and used for loading an attack test program and storing and processing instructions and responses sent by the card reader and the intelligent card. By the adoption of the intelligent card system man-in-the-middle attack verification platform of the structure and the test method, the uniformity of an intelligent card system design scheme and the practical running process can be verified, and authenticity and effectiveness of a security evaluation result is guaranteed; the evaluation result has higher persuasion and authority; due to the fact that a middle attack needs to be executed actually, cost of the man-in-the-middle attack can be quantified effectively and accurately, the ability of an intelligent card system in resisting the man-in-the-middle attack can be evaluated accurately, and thus the security level of the intelligent card system to be tested is confirmed.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
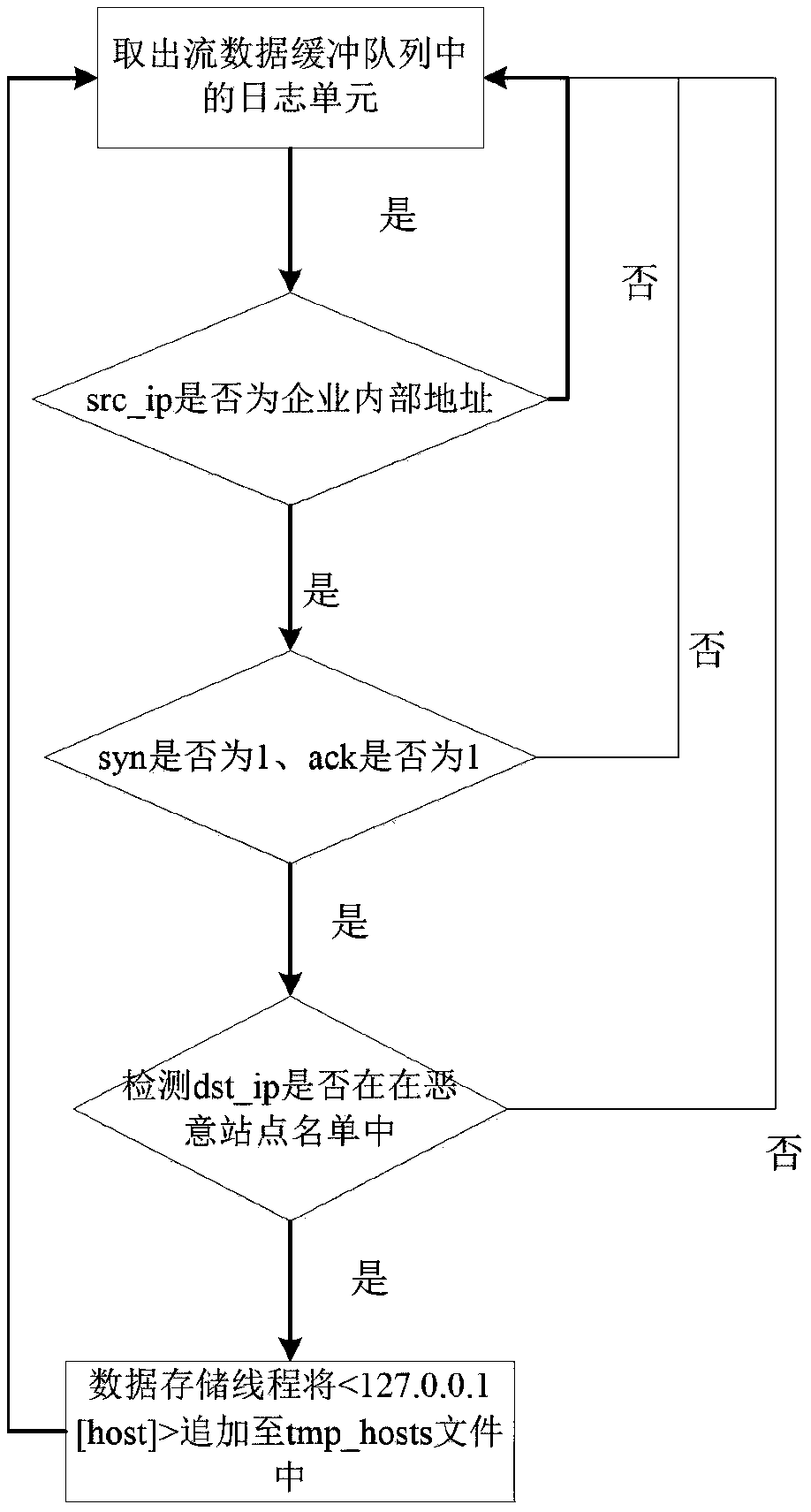
A malicious site access interception method and detection system based on flow analysis
InactiveCN109271790ARealize real-time monitoringImprove securityPlatform integrity maintainanceDomain nameTraffic capacity
The invention discloses a malicious site access interception method and detection system based on flow analysis. The method comprises the following steps: S1, constructing a malicious site detection model based on log characteristic information detection in flow data; wherein, the malicious site model performs access interception according to detected malicious site access; S2, collecting the flowmirror data packet at the network outlet in real time, extracting the log characteristic information in the flow mirror data packet to generate a log data unit, and sending the log data unit to the log buffer queue; S3: The malicious site detection model constructed based on S1 analyzes and detects the log data unit in S2, and updates the detected IP address-domain name mapping temporary file tothe IP address-domain name mapping file of the DNS server. The invention realizes the real-time on-line detection of the malicious site and the real-time interception of the detected visit of the malicious site, thereby improving the security of the network system.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
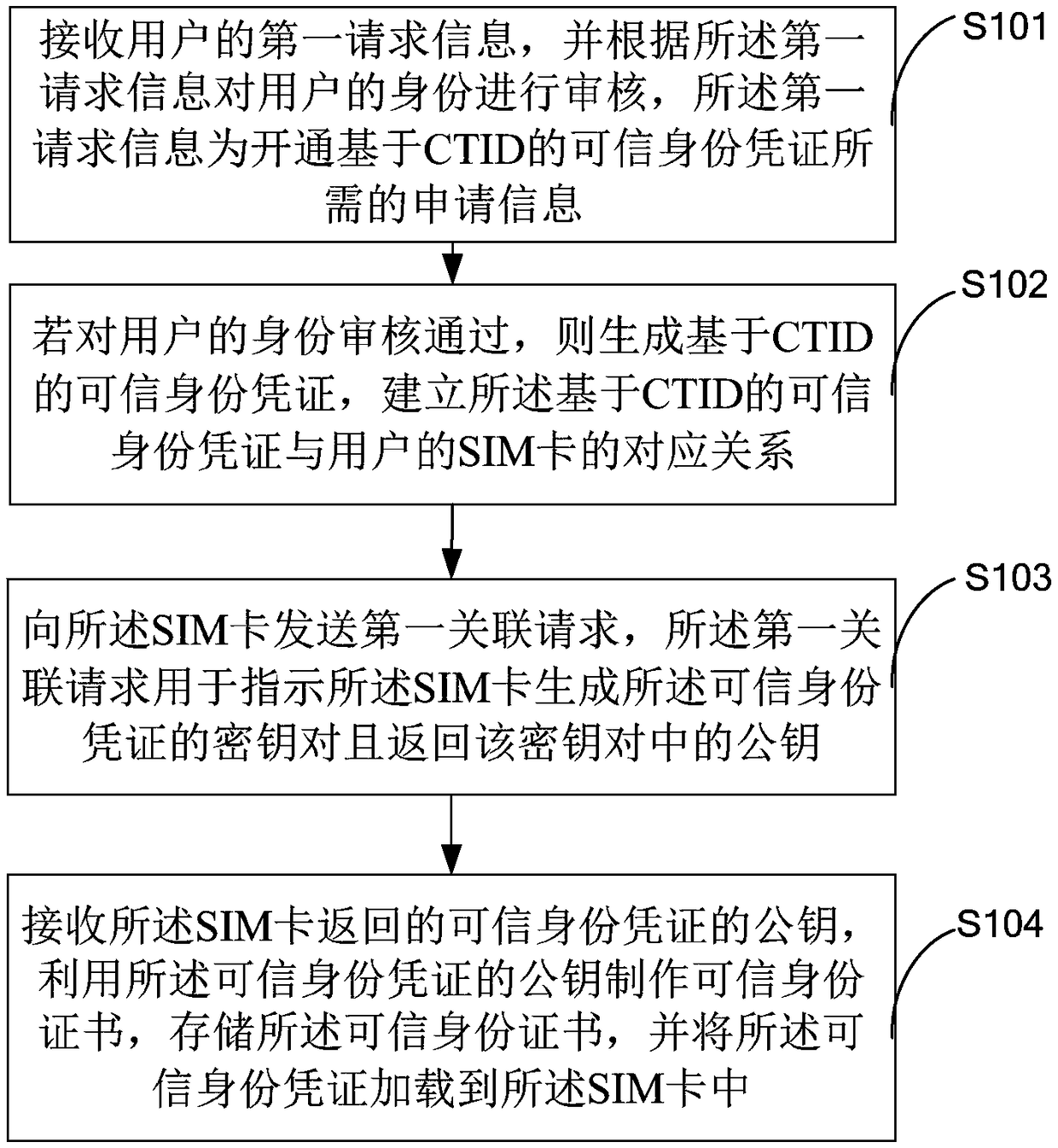
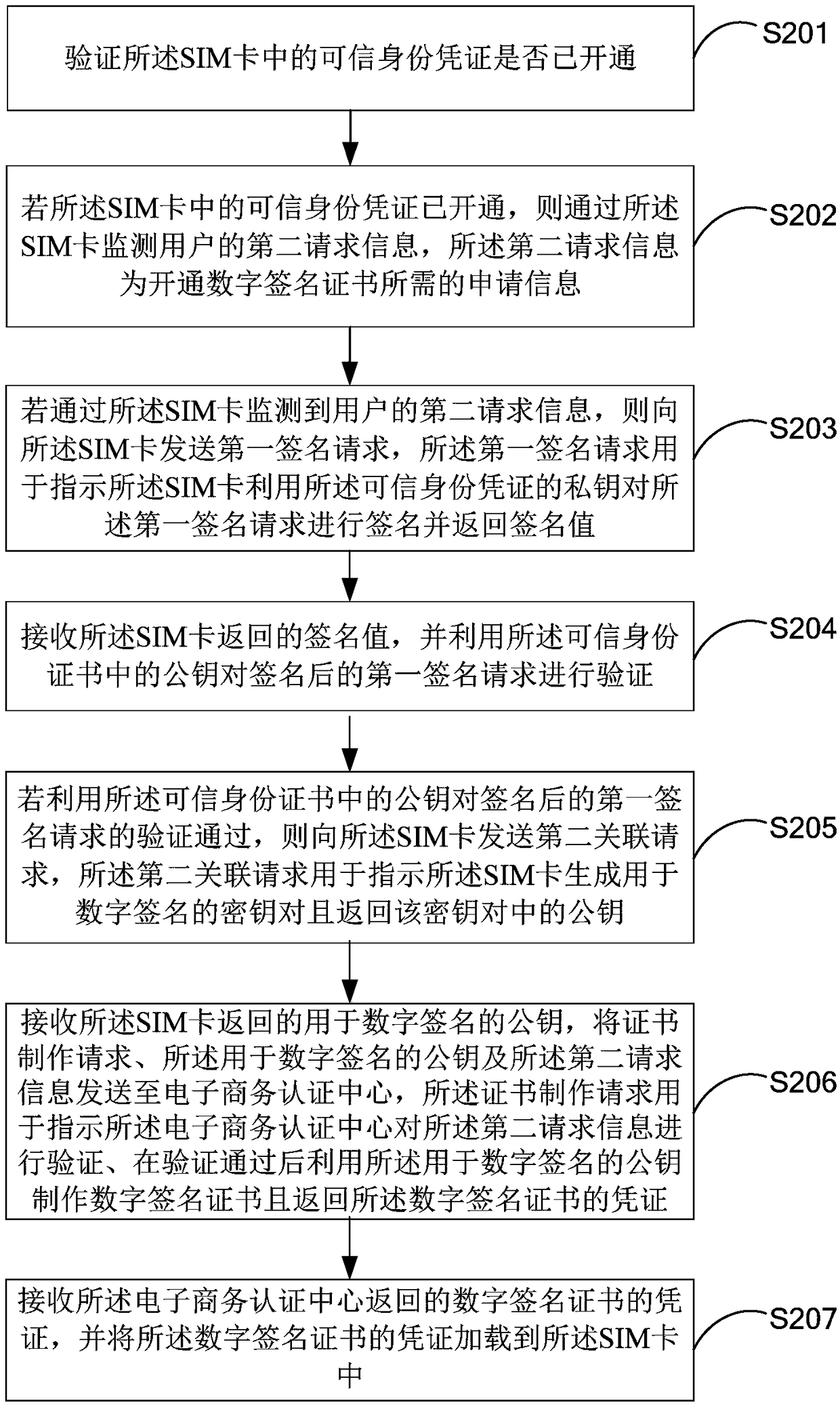
Method for implementing trusted identity authentication by loading PKI based on SIM card
ActiveCN109361697AAvoid the problem of multiple vectorsAuthoritativeUser identity/authority verificationSecurity arrangementElectronic authentication
The invention is applicable to the technical field of communication, and provides a method for implementing trusted identity authentication by loading PKI based on an SIM card. The method comprises the following steps: receiving first request information of a user, and auditing the identity of the user according to the first request information; if the identity of the user is approved, generatinga CTID-based trusted identity certificate, establishing a corresponding relationship between the CTID-based trusted identity certificate and the SIM card of the user; sending a first association request to the SIM card; receiving a public key of the trusted identity certificate returned by the SIM card, creating a trusted identity certificate by using the public key of the trusted identity certificate, storing the trusted identity certificate, and loading the trusted identity certificate in the SIM card. By adoption of the method, the problem that electronic authentication terminal carriers are numerous, resulting in carrying inconvenience and use inconvenience of the user in the prior art is solved effectively.
Owner:SHENZHEN ANXIN CERTIFICATION SYST CO LTD
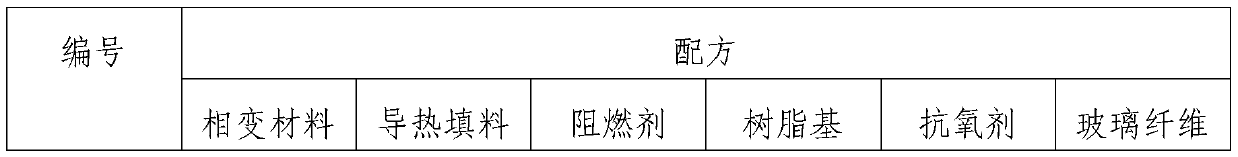
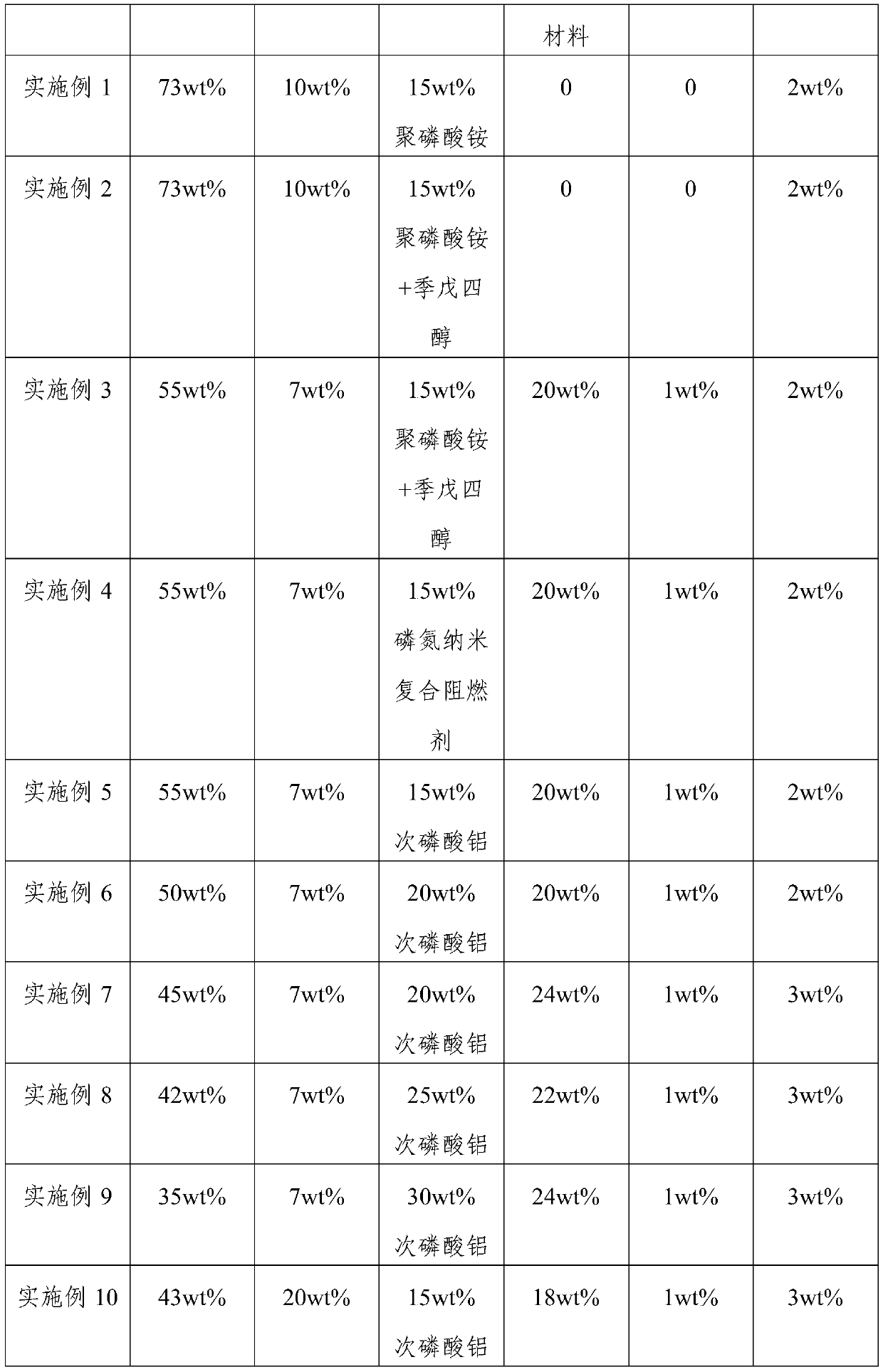
Composition, high-efficiency flame-retardant phase change thermal management composite material which is prepared from composition and preparation method of composition and high-efficiency flame-retardant phase change thermal management composite material
InactiveCN110423474ASensitiveEfficientHeat-exchange elementsWorking temperatureOperating temperature range
The invention relates to a composition, a high-efficiency flame-retardant phase change thermal management composite material which is prepared from the composition and a preparation method of the composition and high-efficiency flame-retardant phase change thermal management composite material. The composition comprises, by weight, 25-90% of an alkane phase change material with a phase transitiontemperature of 20-60 DEG C, 5-15% of thermally conductive filler, 5-25% of one or more of the following flame retardants including aluminum hypophosphite, an ammonium polyphosphate-pentaerythritol composite and a phosphorus-nitrogen nanocomposite flame retardant, 0-30% of a resin-based material, 0-2% of an antioxidant and 0-3% of glass fiber. The composite material has excellent mechanical properties, high thermal conductivity, a high encapsulation rate for phase change materials and no leakage after phase change is performed, the temperature of a battery pack can be regulated effectively, andthe temperature of the battery pack can be controlled within an optimal working temperature range, so that the service life and reliability of the battery pack are improved; and a highest level of V-0 in the UL 94 standard is achieved, excellent flame retardant performance is achieved, and the safety of the battery pack is improved.
Owner:AEROSPACE INST OF ADVANCED MATERIALS & PROCESSING TECH
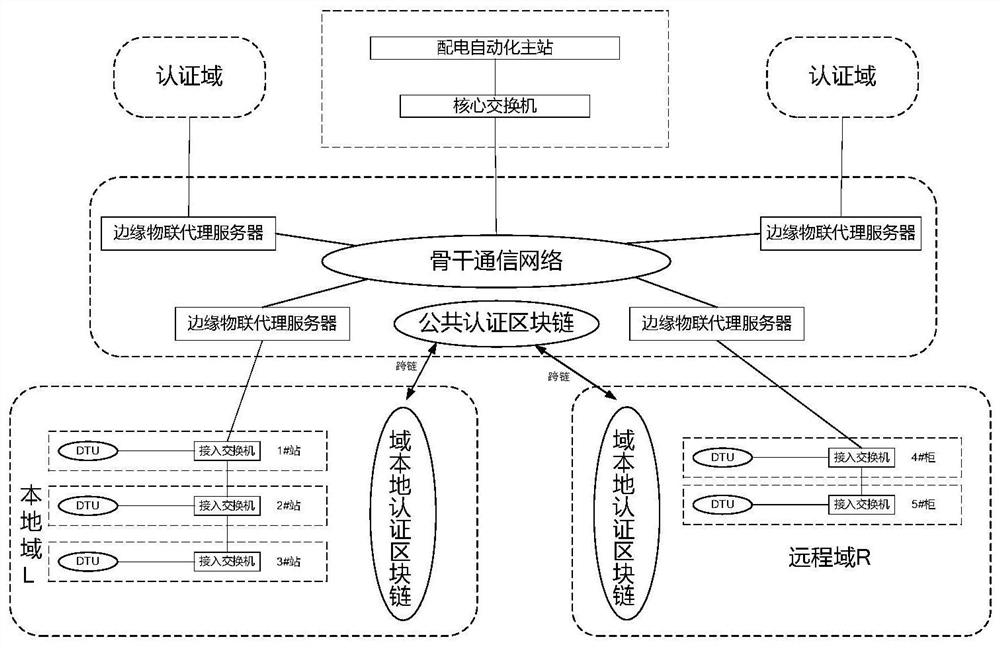
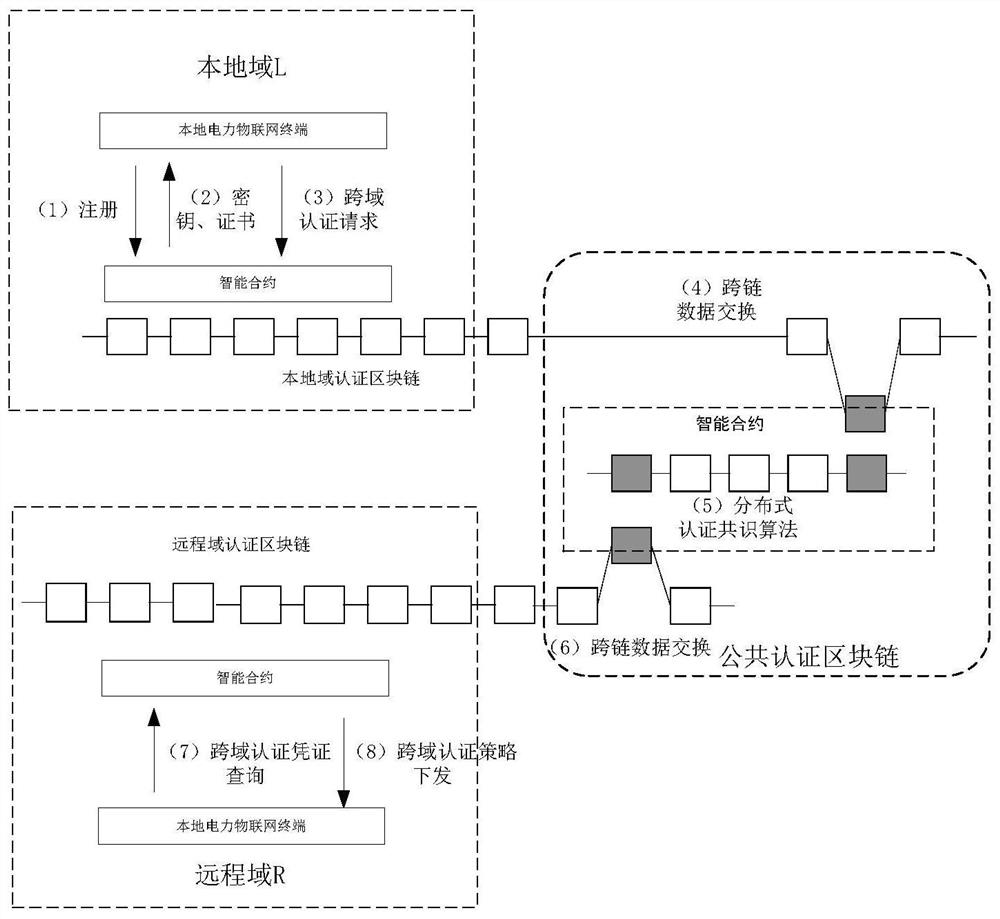
Electric power Internet of Things cross-domain authentication method based on cross-chain technology
ActiveCN112019349AEasy to findAuthoritativeUser identity/authority verificationInstrumentsEngineeringAuthentication server
The invention discloses an electric power Internet of Things cross-domain authentication method based on a cross-chain technology. Each power Internet of Things terminal belongs to an authentication domain where the power Internet of Things terminal is located. Each authentication domain maintains an authentication block chain; an electric power Internet of Things system deployed in an edge Internet of Things proxy server maintains a public authentication block chain. Cross-domain authentication between the authentication domain and the public authentication block chain comprises three processes of registration, cross-domain authentication and cross-domain access. According to the method, the characteristic that the block chain cannot be tampered is utilized, so that safe and credible cross-domain transmission of the authentication data is guaranteed, the authentication server is deployed on the edge side, cross-chain transaction is performed through the edge Internet of Things agent,and the system operation efficiency and safety are guaranteed.
Owner:NANJING INST OF TECH
Method for dynamic omnidistance score tracking and processing of the entire personnel based on exam place
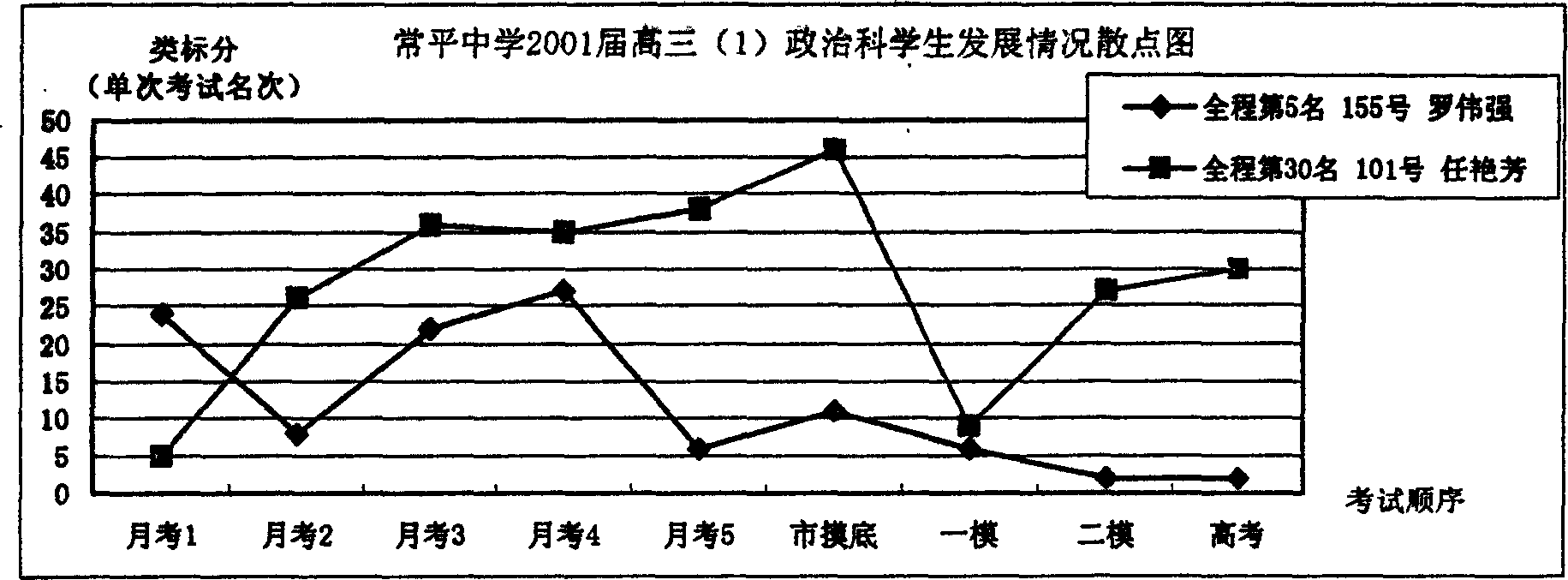
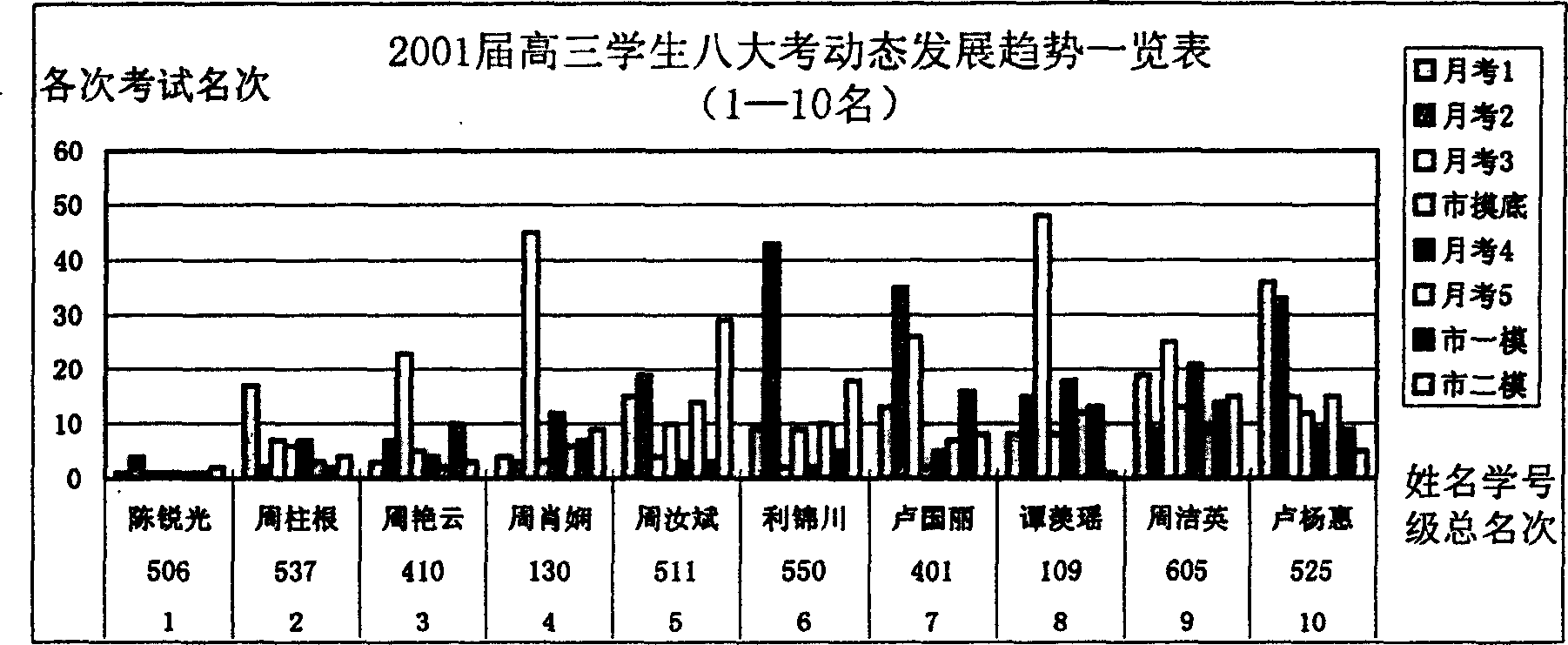
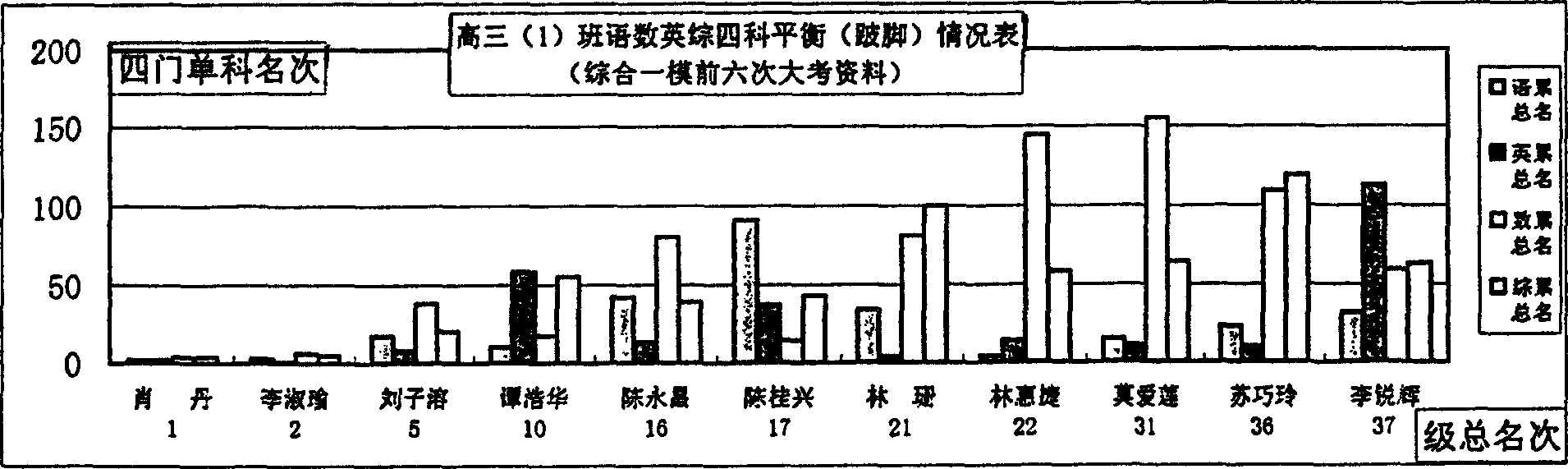
InactiveCN1547129ASave human resourcesImprove management efficiencySpecial data processing applicationsPass rateOperability
The invention provides a method for dynamic tracing and processing scores in a round trip based on test places. The character lies in: the invention can process the comparison evaluation of test scores in the same or different test of the same course or different courses, the historical tracing evaluation developing state of the single course or the multi-course, the description and supervising evaluation of balance developing state of each course, the dynamic tracing evaluation of the passing rate of one course in a class and the evaluation of college entrance examination quickly and high efficiently through the integration to the passing rate from top downward according to the human proportion by the computer software and campus network. The invention has comparability and intuition, the efficiency is high. It overcomes the deficiency of traditional score managing mode of original scores.
Owner:王功学 +2
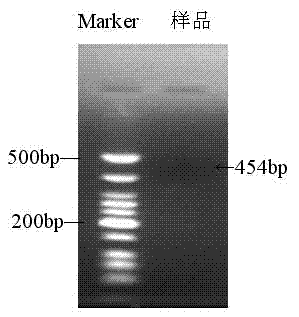
Nest polymerase chain reaction (PCR) detecting method of transgenic crop cauliflower mosaic virus
InactiveCN102534046ASolve detection technical problemsEfficient detection methodMicrobiological testing/measurementMicroorganism based processesAgricultural scienceConserved sequence
A nest polymerase chain reaction (PCR) detecting method of a transgenic crop cauliflower mosaic virus relates to the field of molecular biology. The method designs two specificity outer primers and adopts a CaMV35S promoter published by an announcement NO. 953-6-2007 of a ministry of agriculture to detect a primer serving as an inner primer according to a conserved sequence of a cauliflower mosaic virus CaMV35S promoter, and the group of primers can detect the cauliflower mosaic virus CaMV35S promoter in different transgenic crops and has the characteristic of a broad spectrum. The detecting method has the advantages of being efficient, sensitive, accurate and the like, can avoid a 'false negative' result, and can effectively solve the technical problem of detecting transgenic crops. The nest PCR detecting method can provide technical support for agricultural transgenic organism safety management directly, can conduct effective monitoring on research, production and sales of transgenic crop products, and has important meaning on guaranteeing health of people, environment safety and biodiversity.
Owner:SHENYANG INSTITUTE OF CHEMICAL TECHNOLOGY
Method for refreshing BIOS (Basic Input Output System) by using FPT (Flash Programming Tool) on basis of Intel platform
InactiveCN105589716AAchieve diversificationAuthoritativeVersion controlProgram loading/initiatingSoftware engineeringBIOS
The invention provides a method for refreshing a BIOS (Basic Input Output System) by using an FPT (Flash Programming Tool) on the basis of an Intel platform. The method adopts the FPT of Intel to refresh the BIOS. The method comprises the following steps of: 1, copying a BIOS file to be refreshed to a USB (Universal Serial Bus) Flash, and then copying the FPT to the USB Flash; 2, booting a machine to be refreshed to a U disk; 3, after booting the machine into the U disk, inputting fpt-f XXX.rom on a command line so as to automatically start to refresh the BIOS; and 4, after completing refreshment, powering off the machine, then restarting the machine, and viewing whether a version and a Release Date of the BIOS are updated. The method gets rid of a single and limited BIOS refreshing method, achieves diversification, and is more comprehensive in refreshing region.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
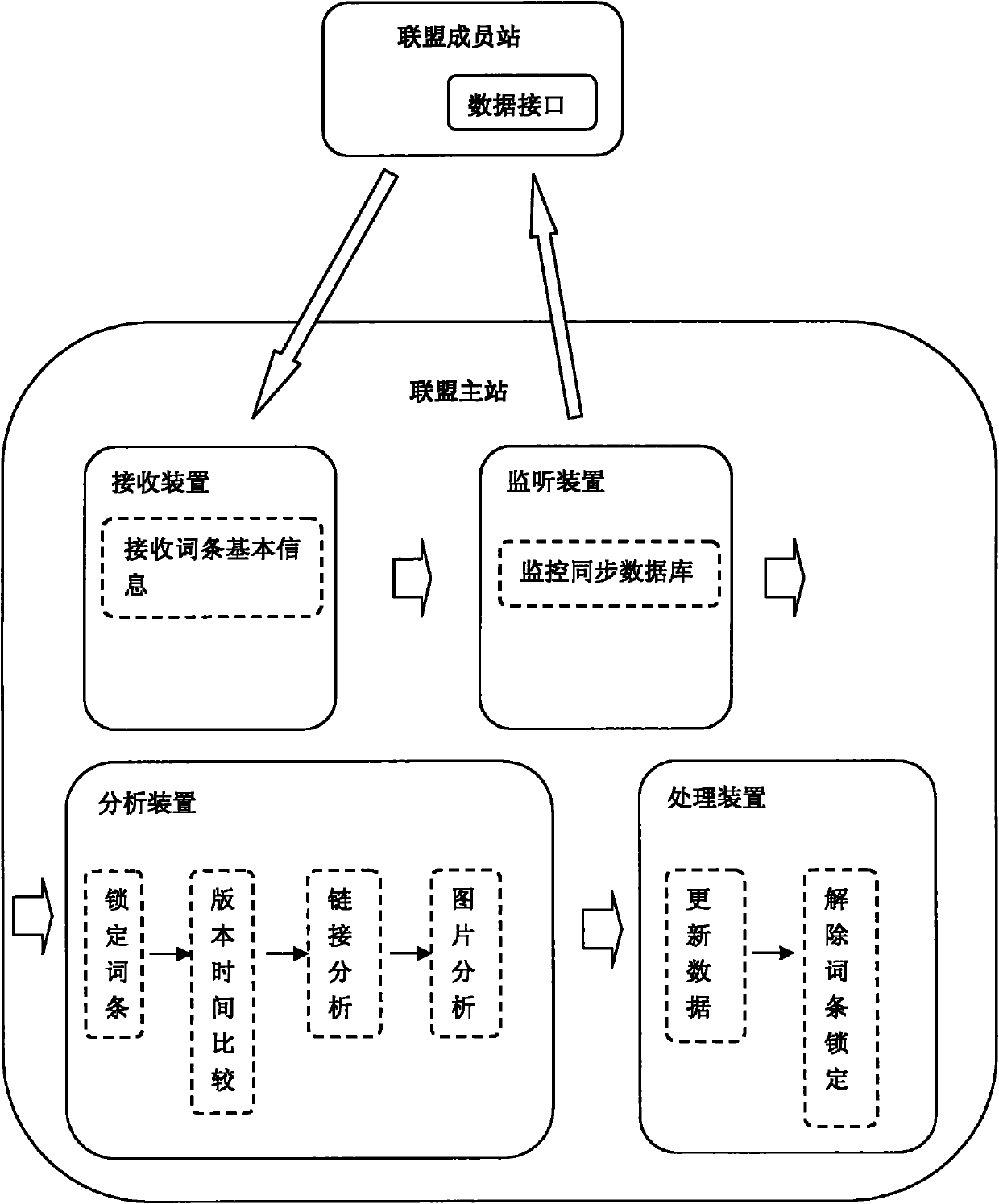
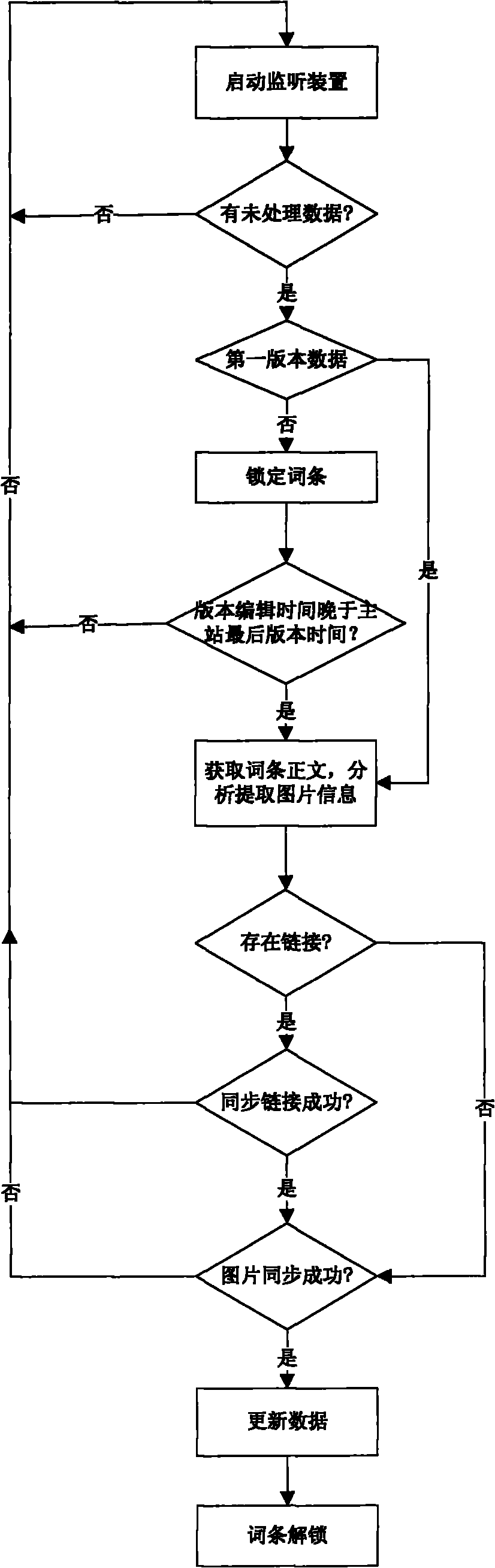
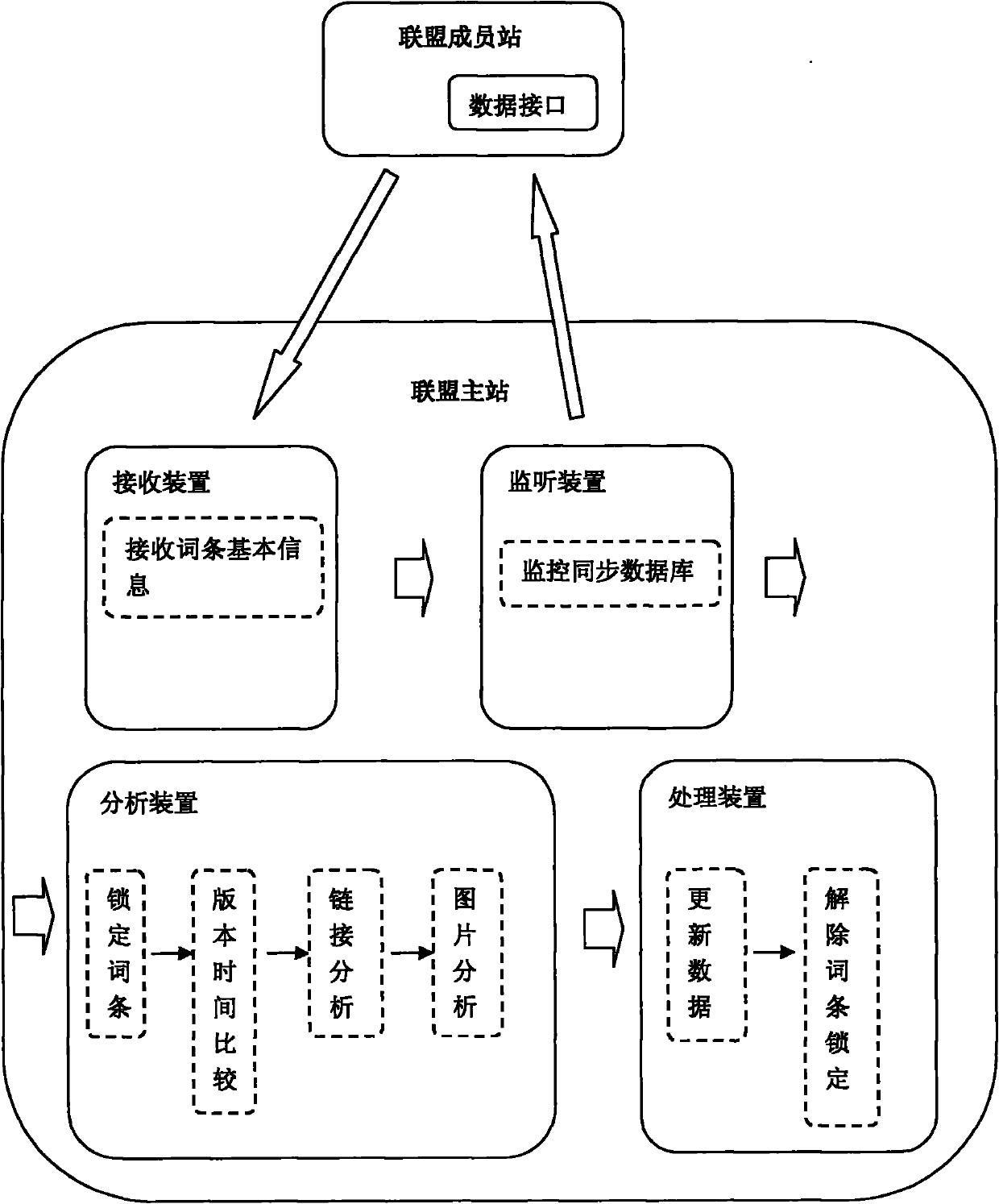
Method and device for synchronizing entries
InactiveCN101908061ABig amount of dataRich contentTransmissionSpecial data processing applicationsPrimary stationData sharing
The invention relates to a method and a device for synchronizing entries. The device is positioned in a union main station and comprises a receiving device, a monitoring device, an analyzing device and a processing device. The method for synchronizing entries comprises the following steps of: forming a union relation by using the union main station as a center and rounding a plurality of union member stations, wherein entry data can be shared in the union, and basic data of all the union member stations are shared from the union main station; and supplementing and editing the basic data by all the union member stations to generate new contents. In the invention, the entries of the union main station in the center are continuously updated and enriched through the entry synchronizing method of the union, meanwhile, the member stations are also helped in the data sharing mechanism of the union.
Owner:北京互动百科网络技术有限公司
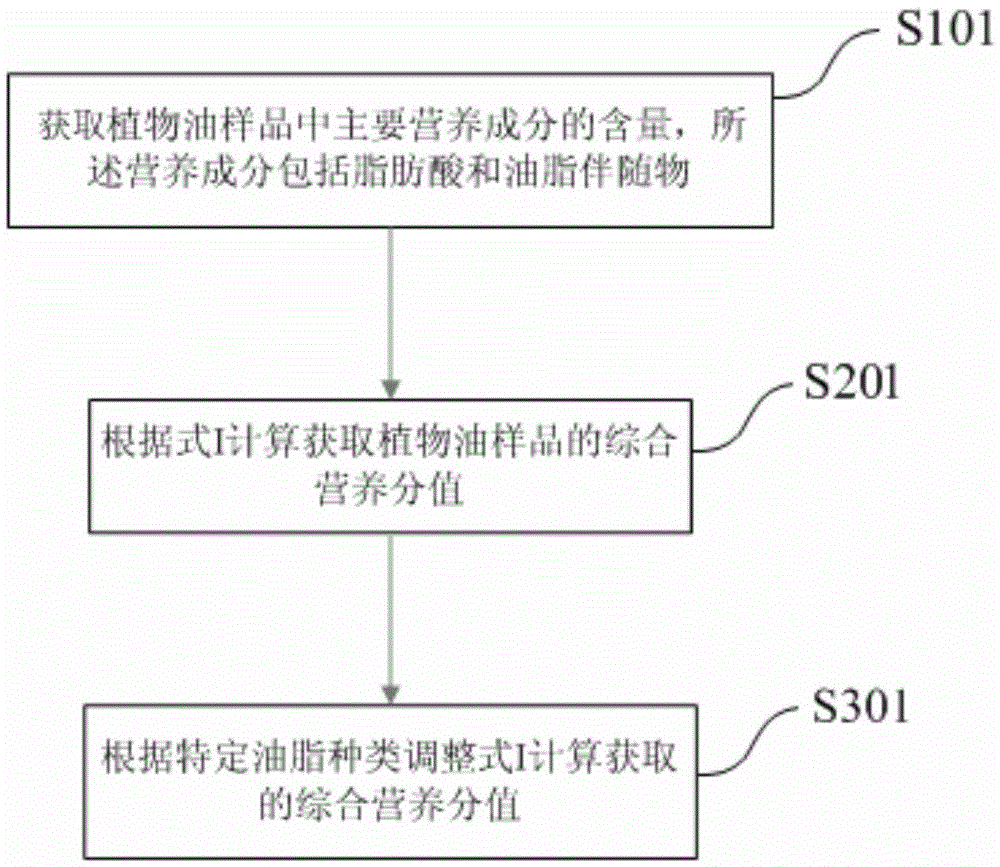
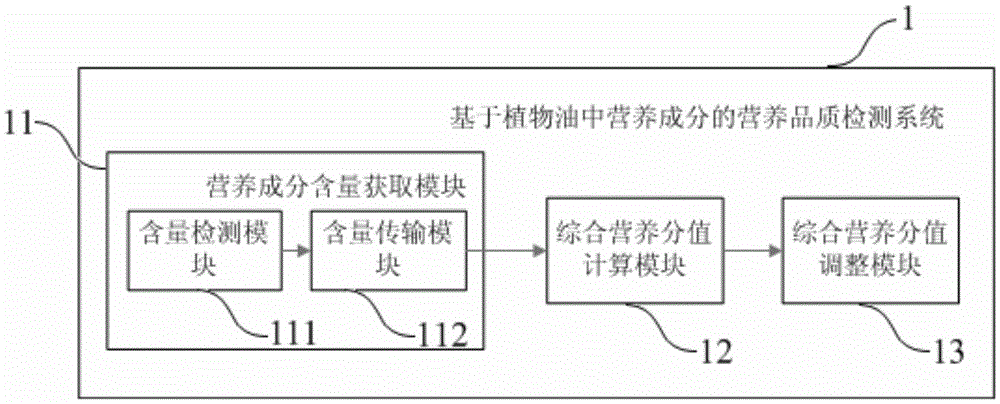
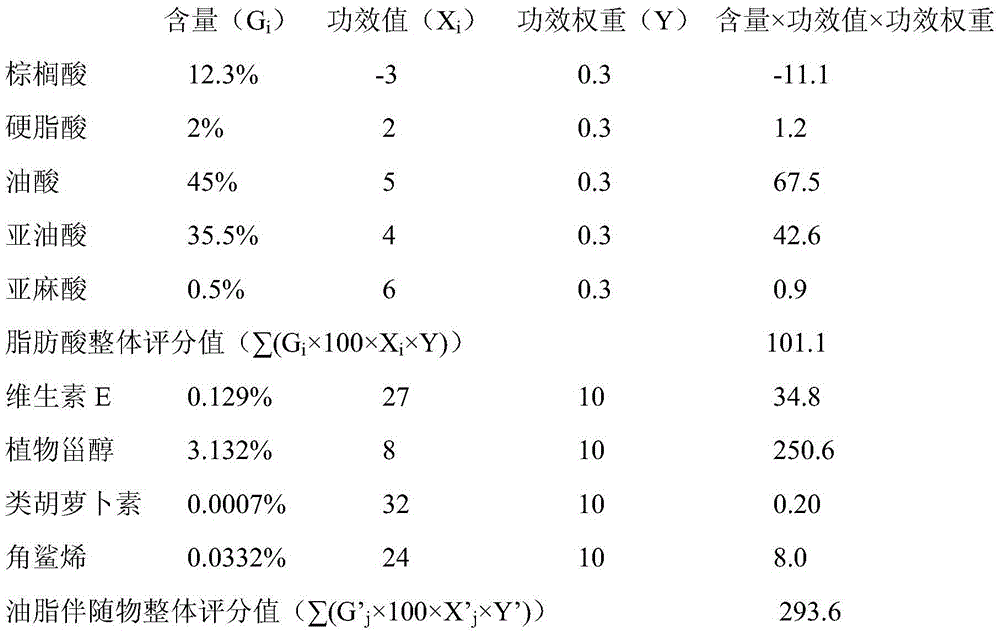
Detection method and detection system for nutritional quality based on nutritional ingredients in vegetable oil
The invention relates to the field of detection (nutritional value evaluation) of edible fat and oil, in particular to a detection method and a detection system for nutritional quality based on nutritional ingredients in vegetable oil. The invention provides the detection method for the nutritional quality based on the nutritional ingredients in the vegetable oil. The detection method comprises the following steps of firstly, acquiring the contents of main nutritional ingredients in a vegetable oil sample; secondly, calculating a comprehensive nutrition score of the acquired vegetable oil sample according to a formula I. The detection method and the detection system for the nutritional quality based on the nutritional ingredients in the vegetable oil, provided by the invention, aim to solve the problem that an existing edible fat and oil value evaluation system focuses on discussion or evaluation emphasizing qualitative and specified fat and oil and specified ingredients is solved, and the current situation that academia and industry are short of scientific and comprehensive universal indictors and quantitative comparison for nutritional values of different fats and oils is changed.
Owner:李容若
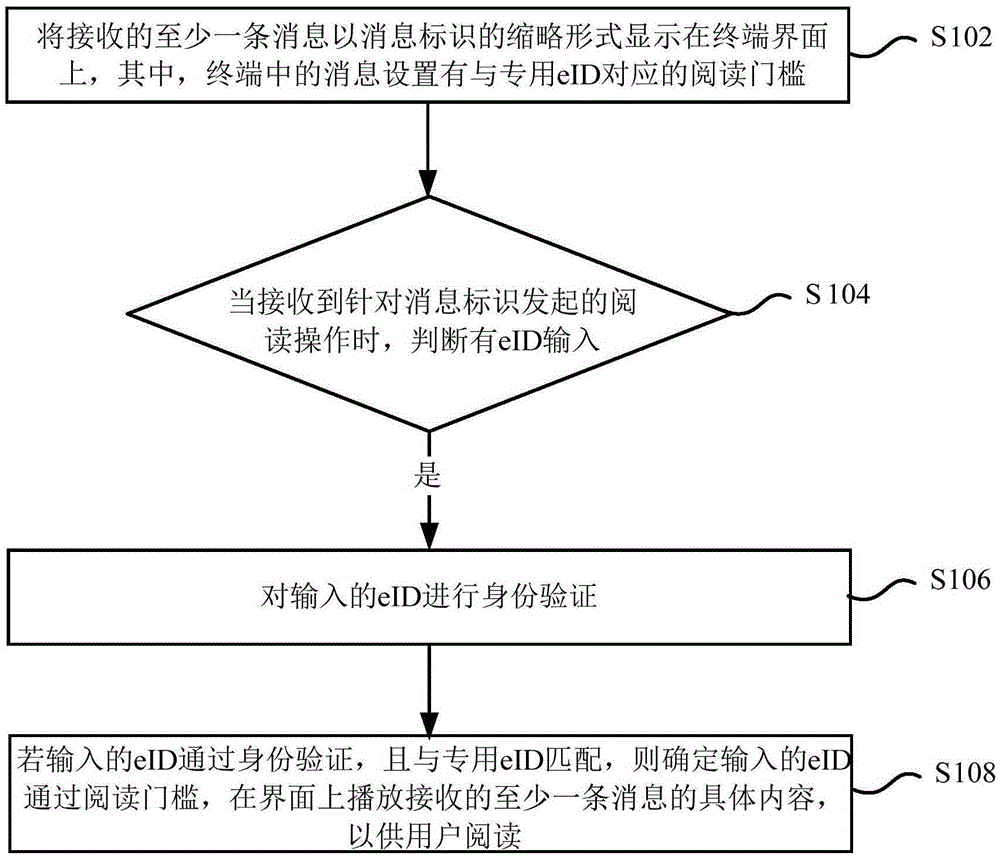
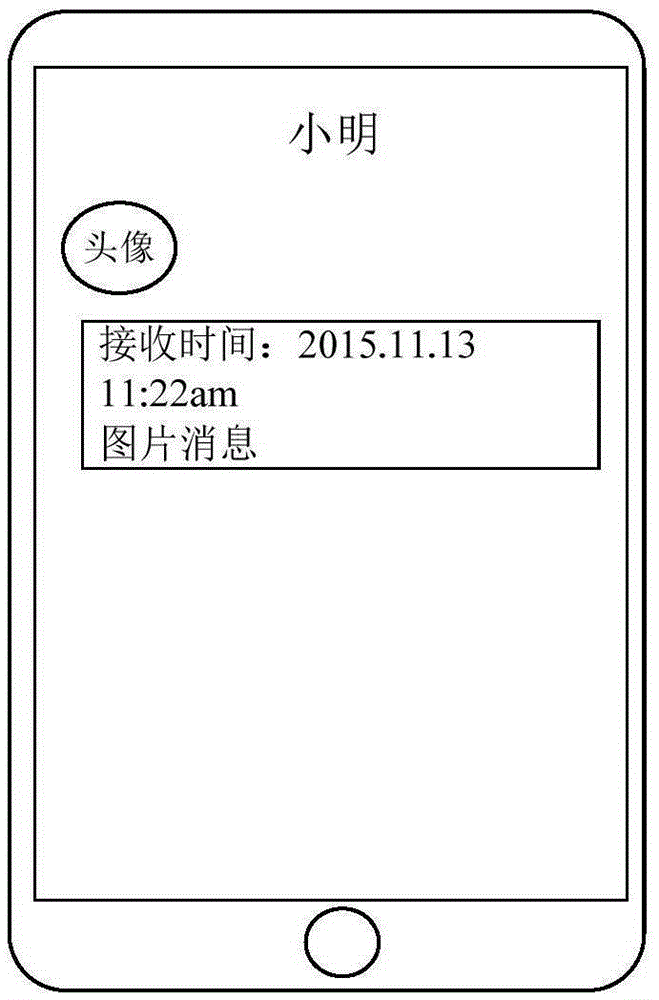
Message reading method and apparatus thereof
InactiveCN106790961AAvoid gettingNot easy to getUser identity/authority verificationSubstation equipmentComputer hardwareAuthentication
The invention provides a message reading method and an apparatus thereof. The method comprises the following steps of displaying at least one received message on a terminal interface as a contracted form of a message identification, wherein the message in a terminal is provided with a reading threshold corresponding to a special-purpose eID; when a reading operation initiated aiming at the message identification is received, determining whether there is eID input; if there is the eID input, carrying out identity verification on the input eID; and if the input eID passes the identity verification and matches with the special-purpose eID, determining that the input eID passes the reading threshold, playing a specific content of the at least one received message on the interface so that a user can read. By using the method of the invention, the message received by the terminal is protected and a condition that a received message content is easily acquired by other users and even malicious users is avoided, and high safety is possessed.
Owner:BEIJING QIHOO TECH CO LTD +1
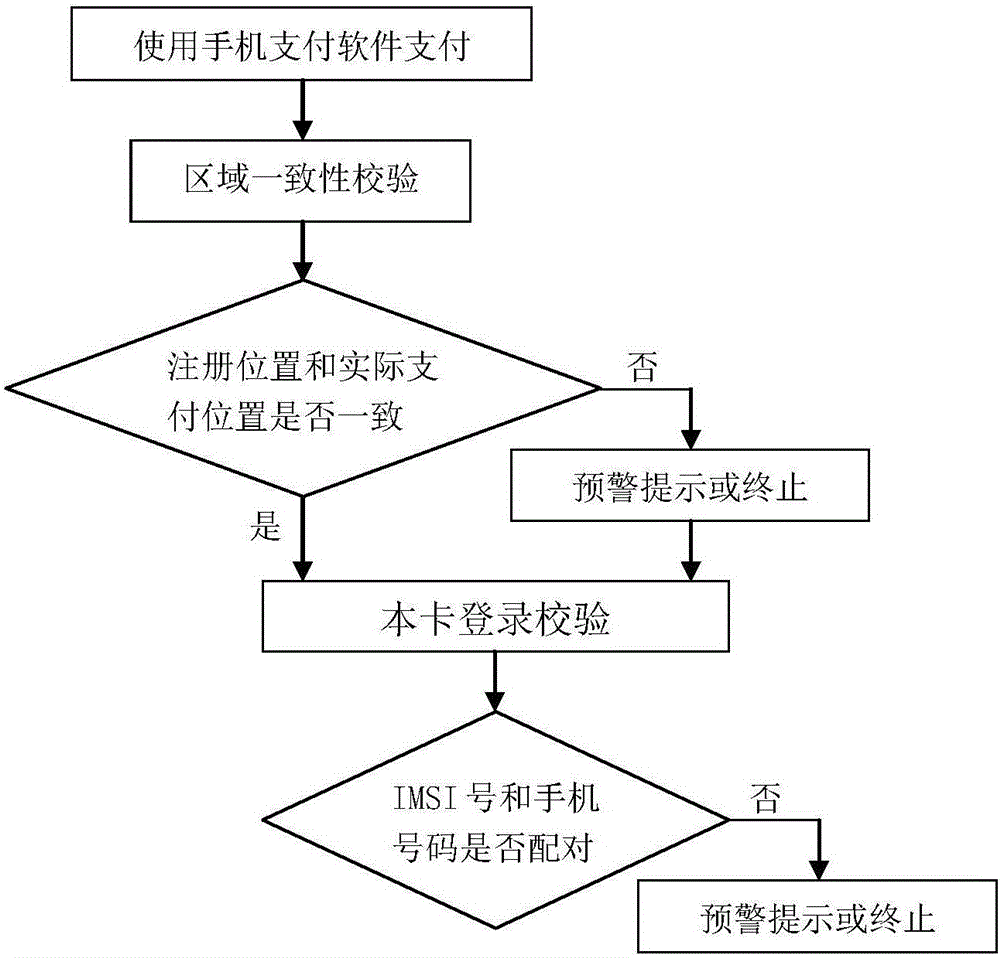
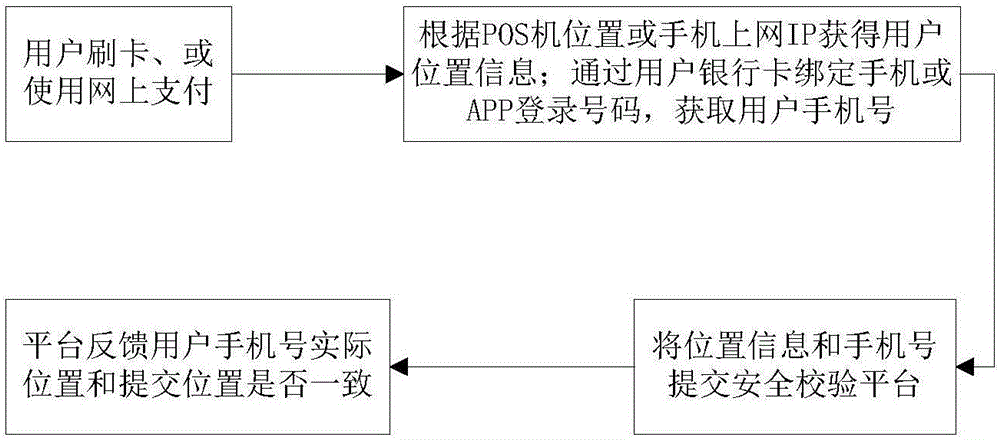
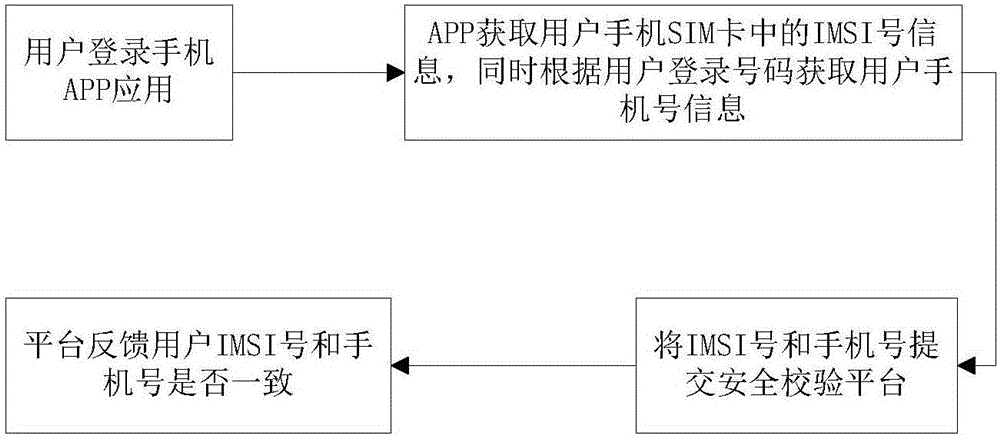
Mobile phone security verification method based on intelligent network
The invention provides a mobile phone security verification method based on an intelligent network. The security of a payment account of a user is not protected just depending on the consistency verification of the account password of the user, data are obtained from the network ability of an operator, the payment security risks are identified by the combination of regional consistency verification and login verification of the present card, the verification is realized by the network of the operator without being affected by the Trojan virus of the mobile phone, thereby being unlikely to break, higher in security, and authoritative, and the flow of the present platform cannot be duplicated by technical means at the outside.
Owner:江苏号百科技有限公司
Method for implementing computer driving service security network system
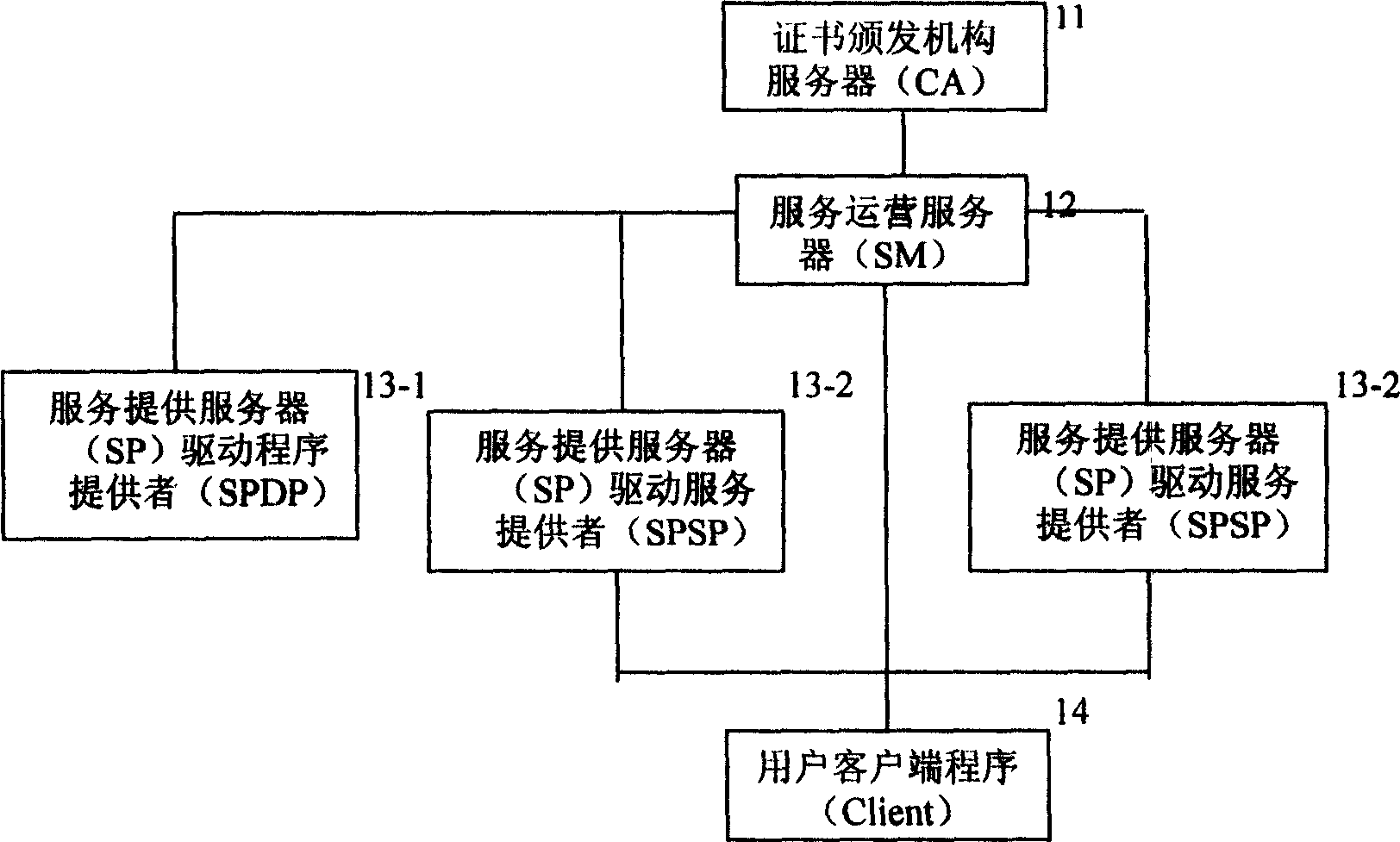
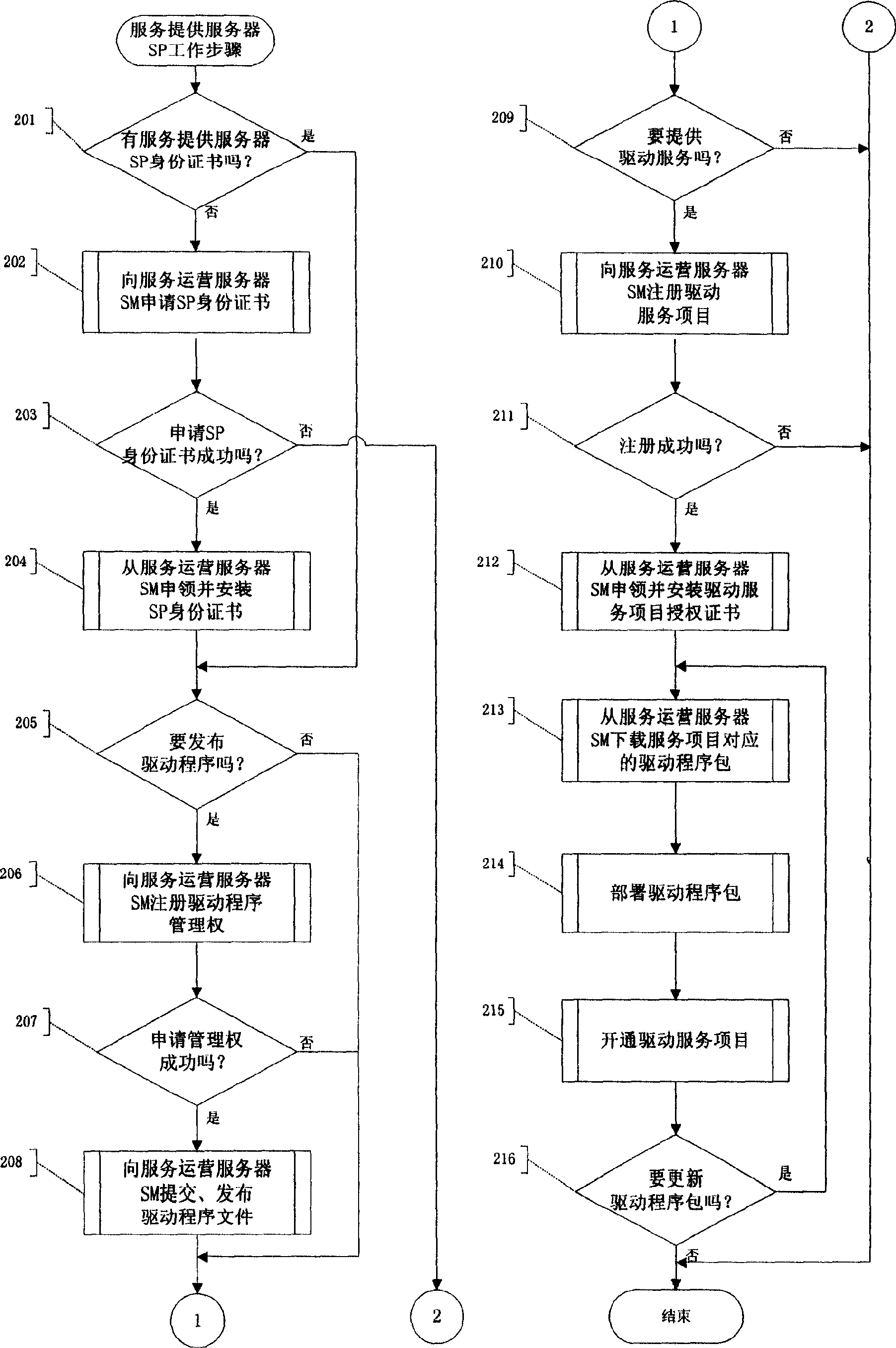
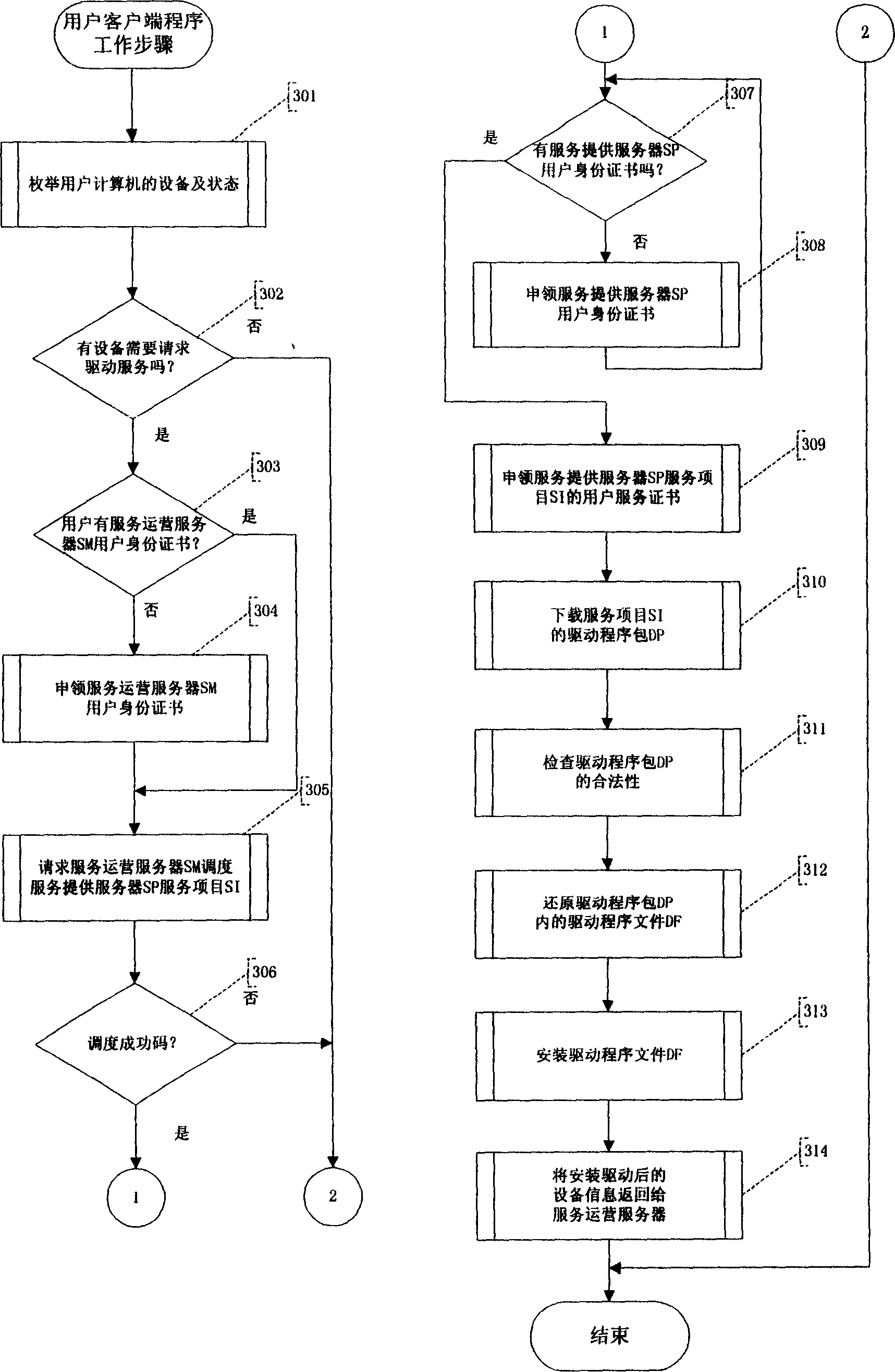
InactiveCN1606270AAvoid complexityAvoid hidden dangersUser identity/authority verificationProgram loading/initiatingService provisionClient-side
This invention provides a realization method for a computer driving service safety network including: A driving service provider (SP) applies for a service providing identity certification (SPC) to an operation server(SM), the SP for providing driving programs (SPDP) provides the driving program (DF) to SM and examined by SM, the DF is issued by the service items SI. The SPSP registers a service of SI to SM. The user customer end program client gets the service of SI to ensure the true and legal driving program source.
Owner:耿健
Learning resource management method, system, block chain system and storage medium
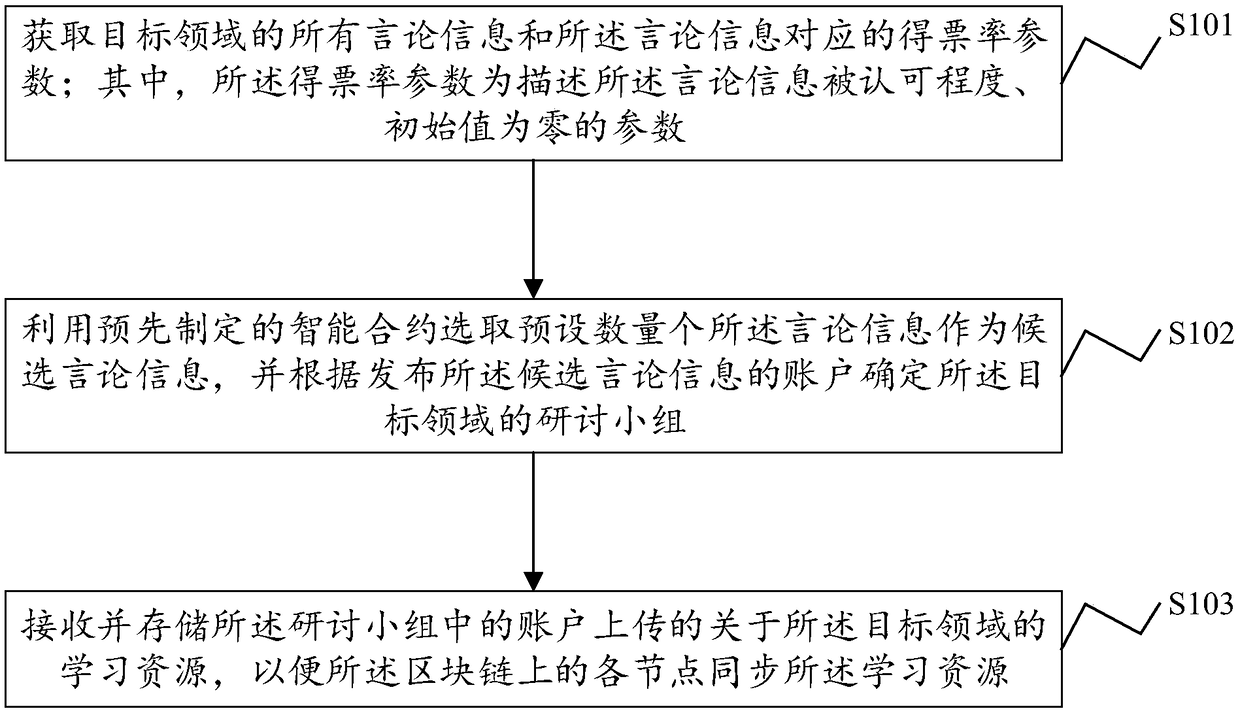
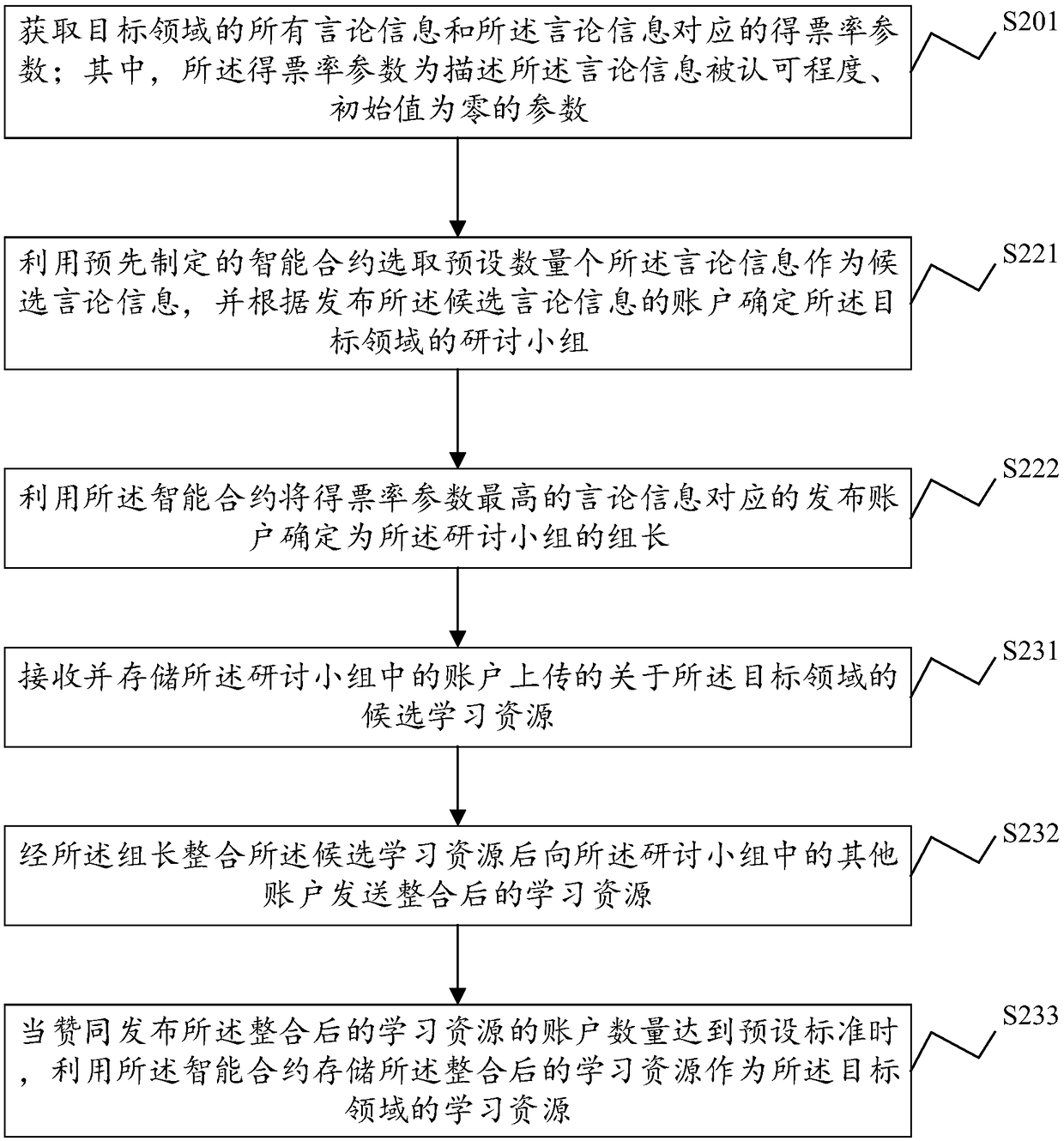
ActiveCN109214200AEnsure safetyAuthoritativeData processing applicationsDigital data protectionRate parameterResource management
The invention discloses a learning resource management method, a system, a block chain system and a computer-readable storage medium. The method comprises the following steps: obtaining all speech information of a target field and a voting rate parameter corresponding to the speech information; among them, the voting rate parameter is a parameter describing the degree of approval of speech information, and the initial value is zero; selecting a preset number of the speech information as candidate speech information by using a preset intelligent contract, and determining a discussion group of the target field according to an account for publishing the candidate speech information; learning resources on the target domain uploaded from an account in the seminar group are received and stored so that nodes on the block chain synchronize the learning resources. The learning resource management method provided by the present application ensures the security of the learning resource stored onthe learning resource by utilizing the decentralized and non-tamperable characteristics of the block chain technology.
Owner:LAUNCH TECH CO LTD
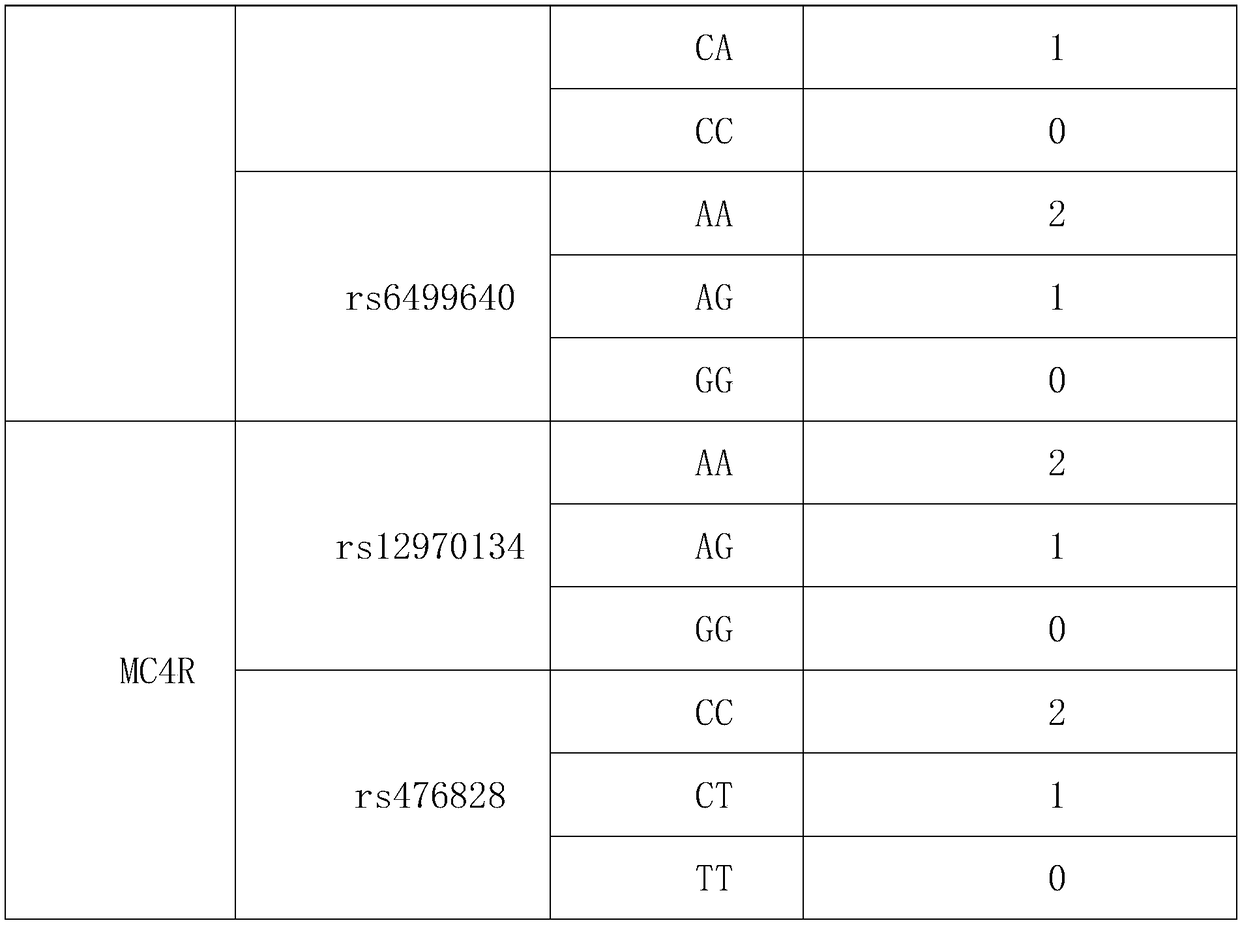
Genetic evaluation method for appetite ability
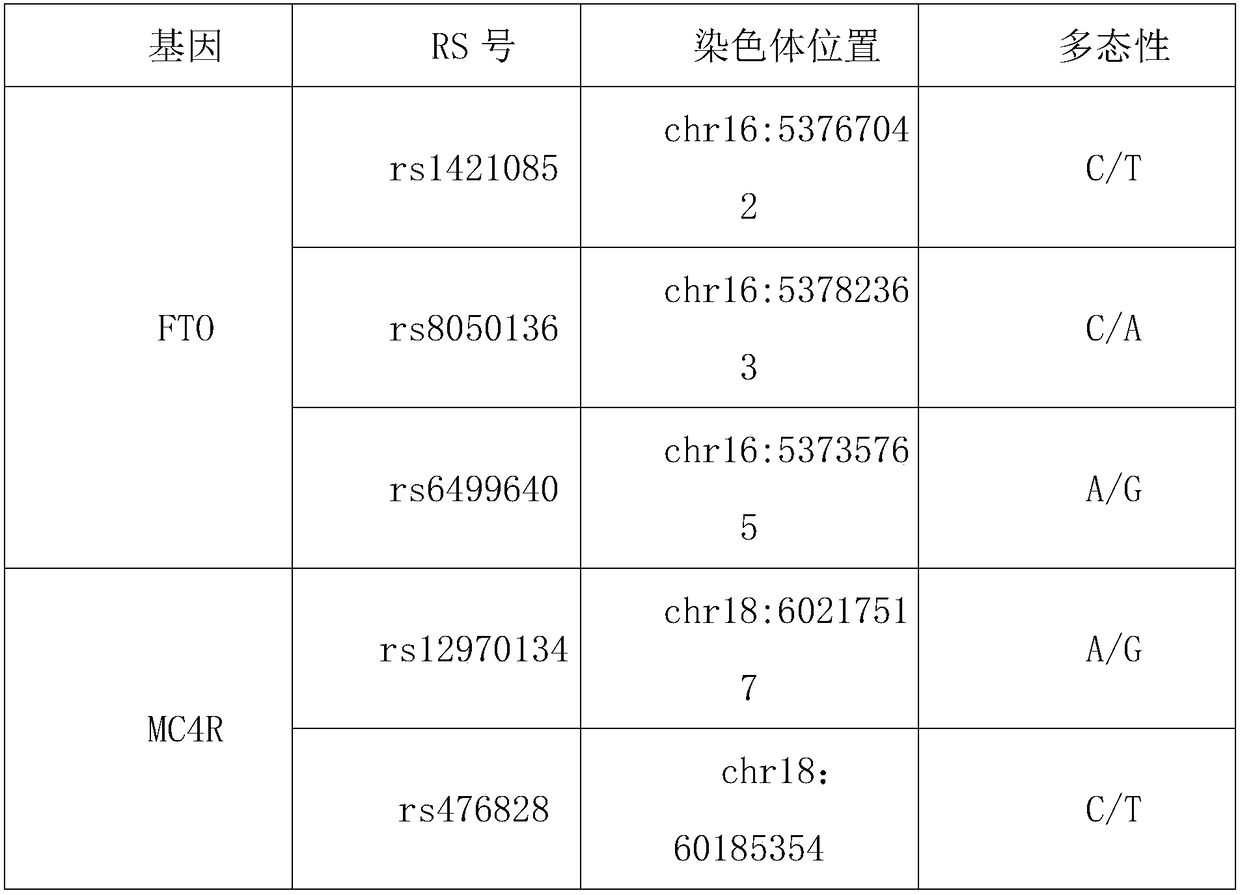
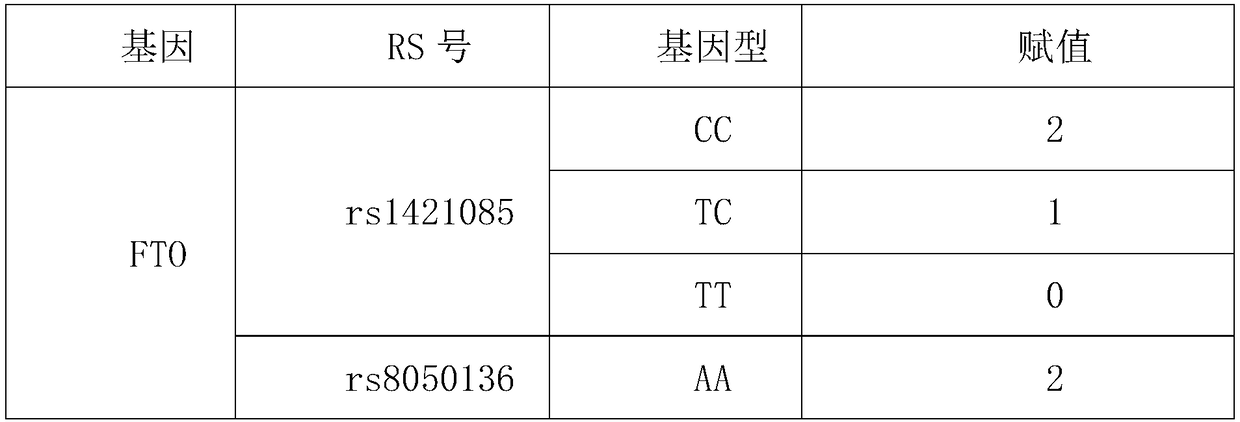
InactiveCN108998542AAvoid disunityAuthoritativeMicrobiological testing/measurementAssessment methodsBiology
The invention provides a genetic evaluation method for appetite ability, wherein the genetic evaluation method includes the following steps: step (1), genes and loci related to obesity are determined;step (2), all loci determining the genes and loci related to the obesity are assigned; step (3), according to the detection result, appetite ability genes are evaluated, an algorithm comprises that detected genotypes of five loci of two genes are used for obtaining a synthesized score by a summation method, wherein the addition values are the assignments in the step (2) corresponding to the detected genotypes; and step (4), the judging criteria for the obtained synthesized score of the five loci of the two genes of a detected person comprises that if the synthesized score is greater than or equal to 2, the appetite is relatively large, and if the synthesized score is less than or equal to 1, the appetite is normal. With combination of the clear and definite gene detection evaluation method and standard, the inconsistency of evaluation results caused by different people's evaluation is avoided, and the product is replicable and operable.
Owner:上海佰臻生物科技有限公司
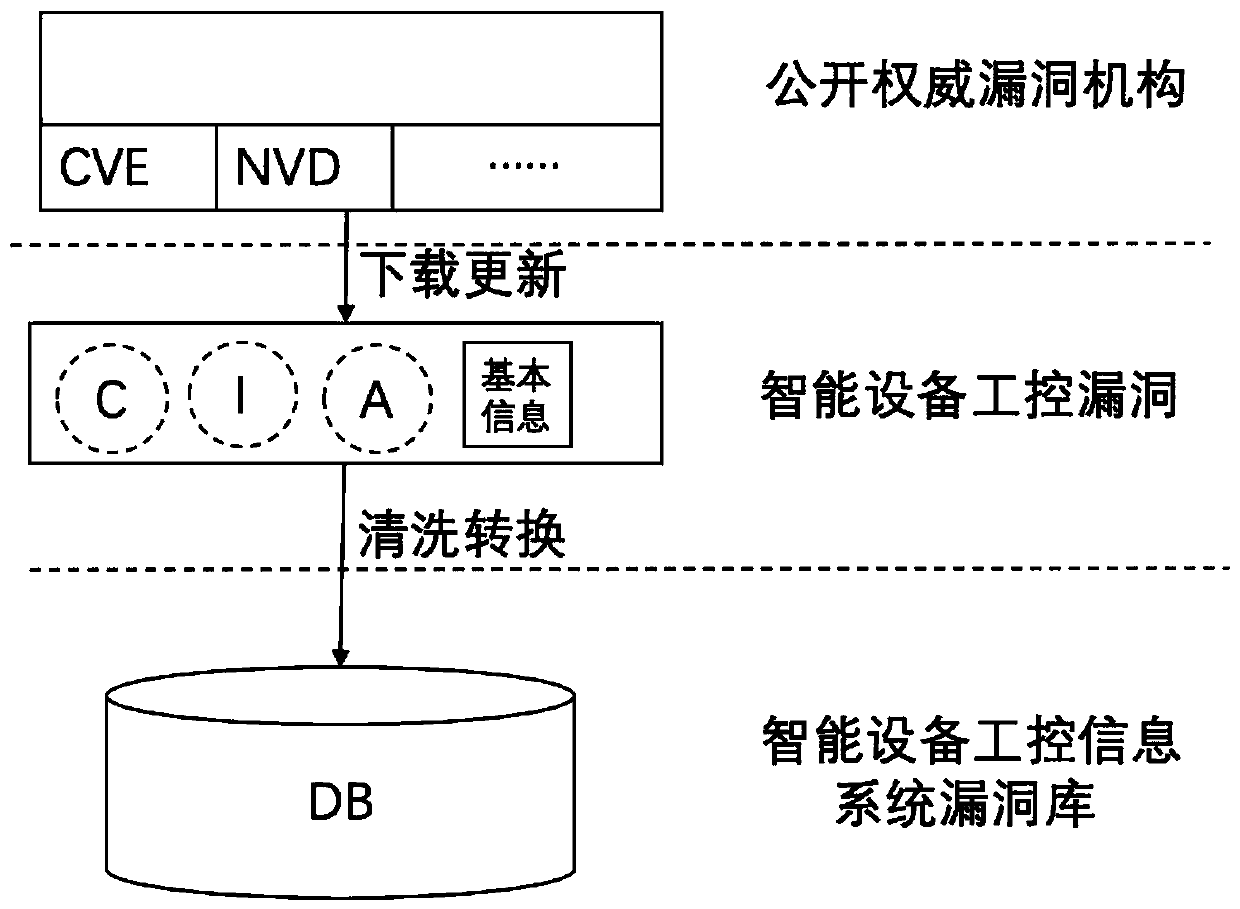
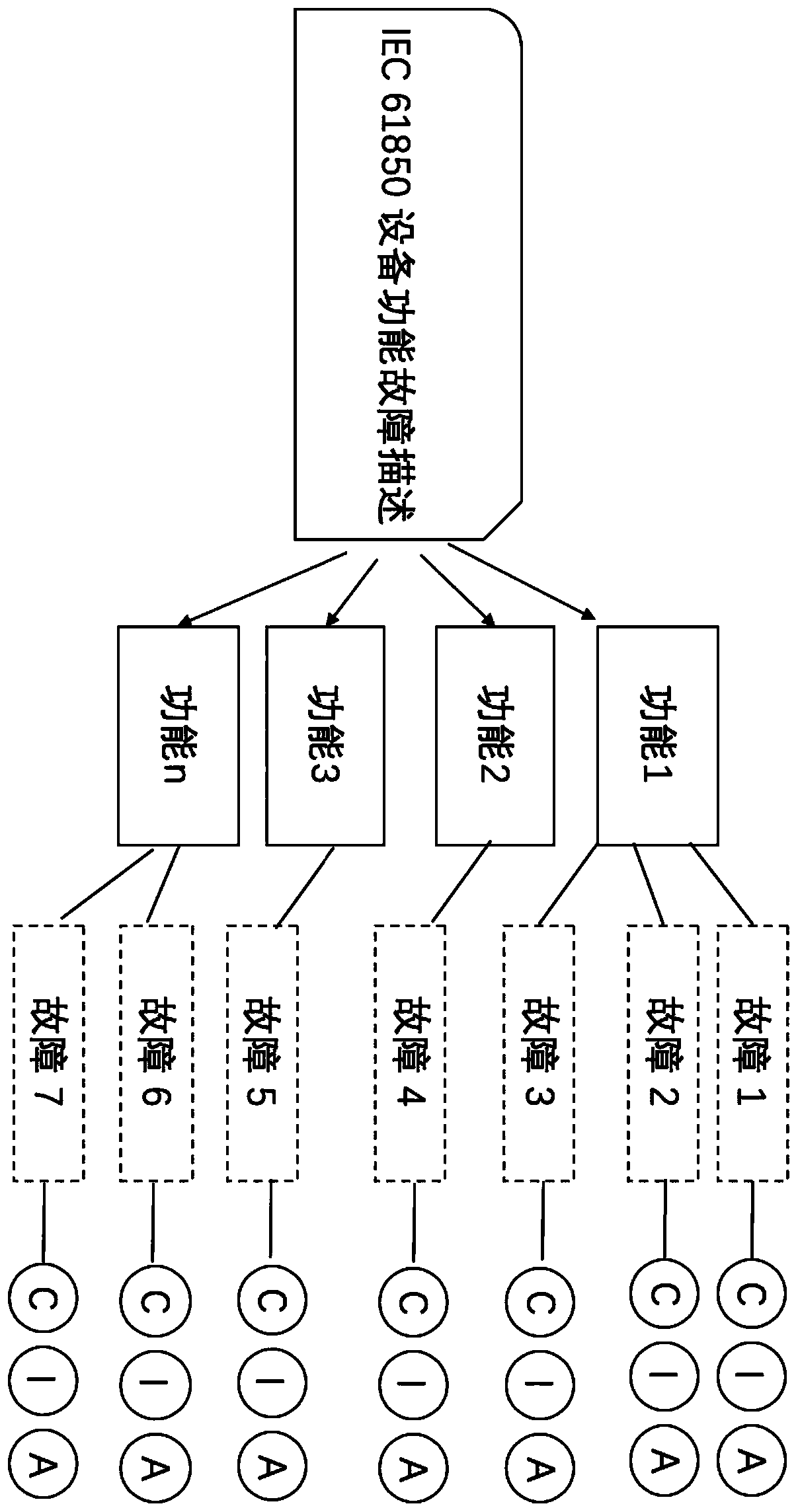
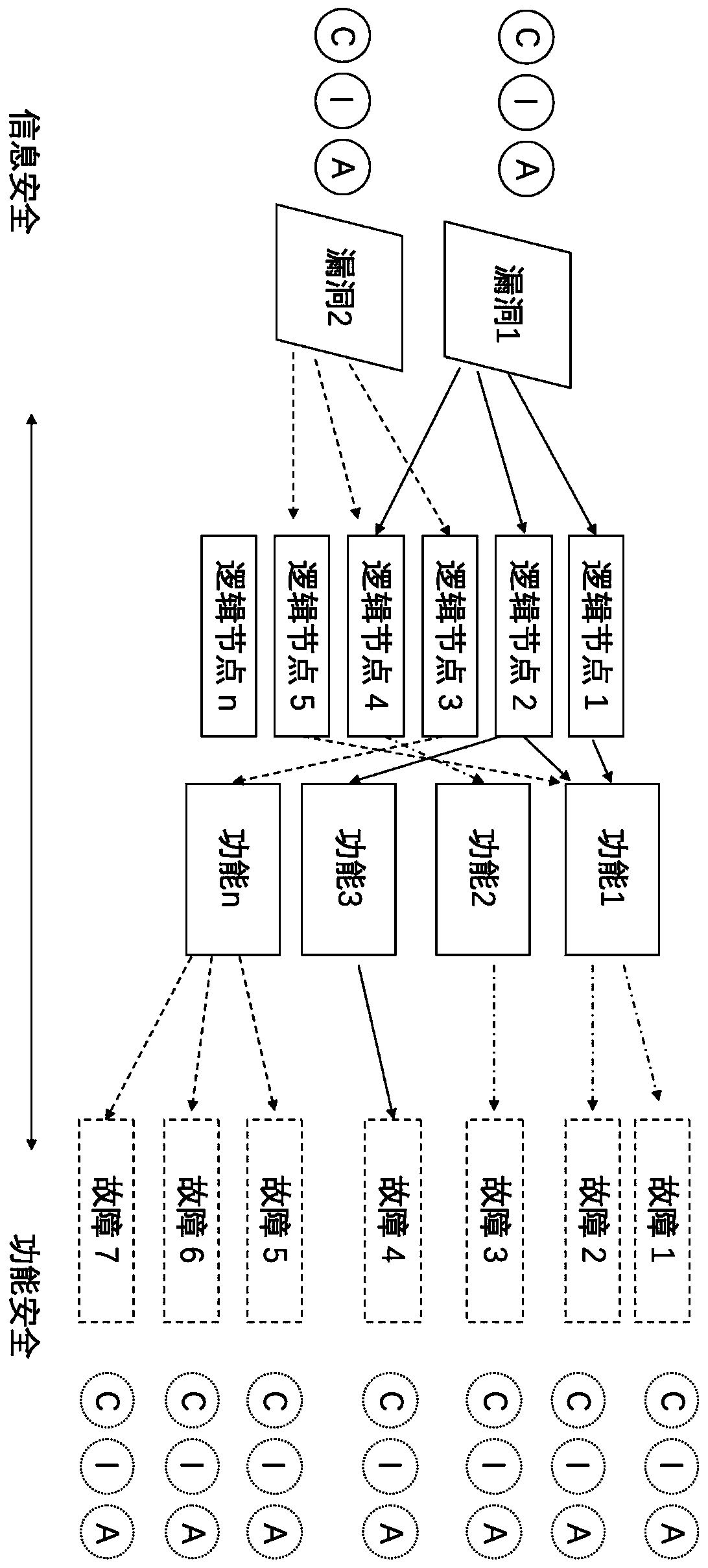
Information security and function security association analysis method
ActiveCN111125720AImprove general performanceAuthoritativeFunctional testingPlatform integrity maintainanceInformation repositoryConfidentiality
The invention relates to an information security and function security association analysis method, and belongs to the field of information security. The method comprises the following steps that: anintelligent equipment information system security risk assessment model, an intelligent equipment function fault security analysis model and an information security and function fault matching model are included, and the intelligent equipment information system security risk assessment model is mainly used for collecting authoritative known industrial control information system security vulnerability information and establishing a CIA information base for the vulnerability information. The equipment function fault safety analysis model is used for calculating a confidentiality threat value, anintegrity threat value and an availability threat value of a logic node function according to description of the logic node function fault of the intelligent equipment involved in the IEC 61850 standard; and a logic node function fault CIA threat library is established. The information security and function fault matching model is used for establishing a corresponding relation calculation methodof information system security CIA and intelligent equipment security CIA threat values.
Owner:STATE GRID SICHUAN ELECTRIC POWER CORP ELECTRIC POWER RES INST +1
Test bench of vacuum toilet stool system
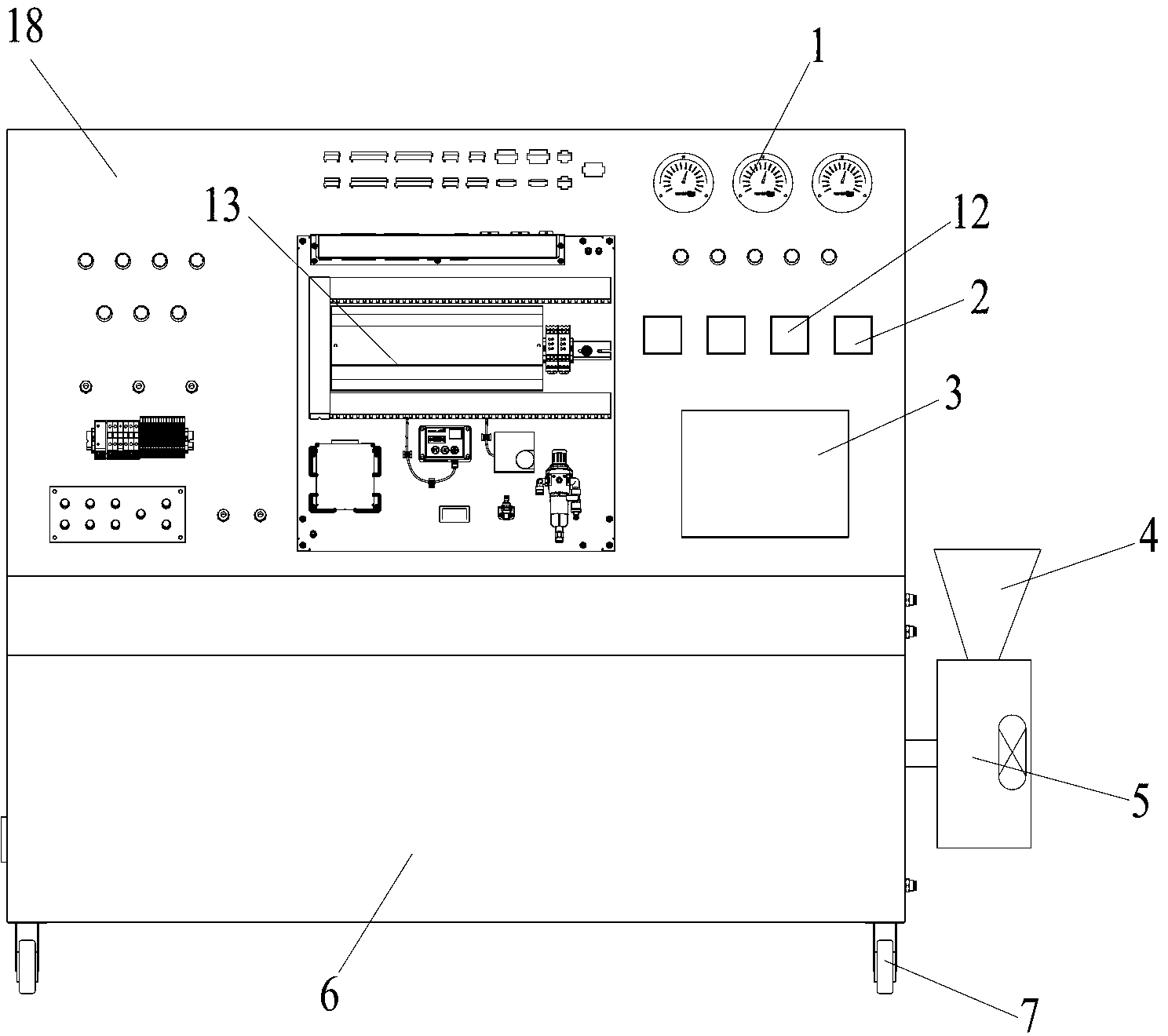
ActiveCN103226069AEasy to operateIntuitive display interfaceStructural/machines measurementInput controlVoltmeter
The invention relates to a test bench of a vacuum toilet stool system, which comprises a test bench housing, wherein the test bench housing comprises a bench top part and a mounting test part; a pressure gauge for displaying pressure, a voltmeter for displaying measured voltage, an ammeter for displaying measured current and a touch screen for input control and display are arranged on the mounting test part of the test bench housing; the touch screen, the pressure gauge, the voltmeter and the ammeter are electrically connected with a controller in the test bench housing; the test bench housing is internally provided with a pressure tank for providing high pressure water for flushing a toilet stool, and a dirt box for collecting discharged sewage of the toilet stool; a water pump is arranged on the dirt box; the water pump can convey treating water in the dirt box to an intermediate box; the intermediate box is communicated with the pressure tank; and the pressure tank, the water pump and the intermediate box are electrically connected with the controller. The test bench is simple and compact in structure, convenient to operate, high in detecting precision, wide in application scope, safe and reliable, detects conveniently, and improves the detecting efficiency.
Owner:WUXI WANLI IND DEV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com