Trustiness measuring method for installing and upgrading software
A software installation and software upgrade technology, applied in the computer field, can solve problems such as judgment without considering the credibility of the application, loss of trust value, and large loss of trust.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The above and other technical features and advantages of the present invention will be described in more detail below in conjunction with the accompanying drawings.
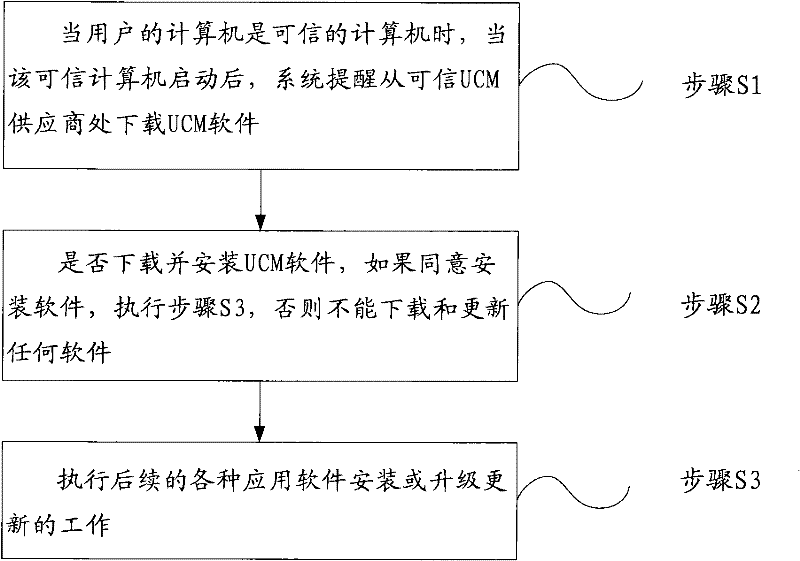
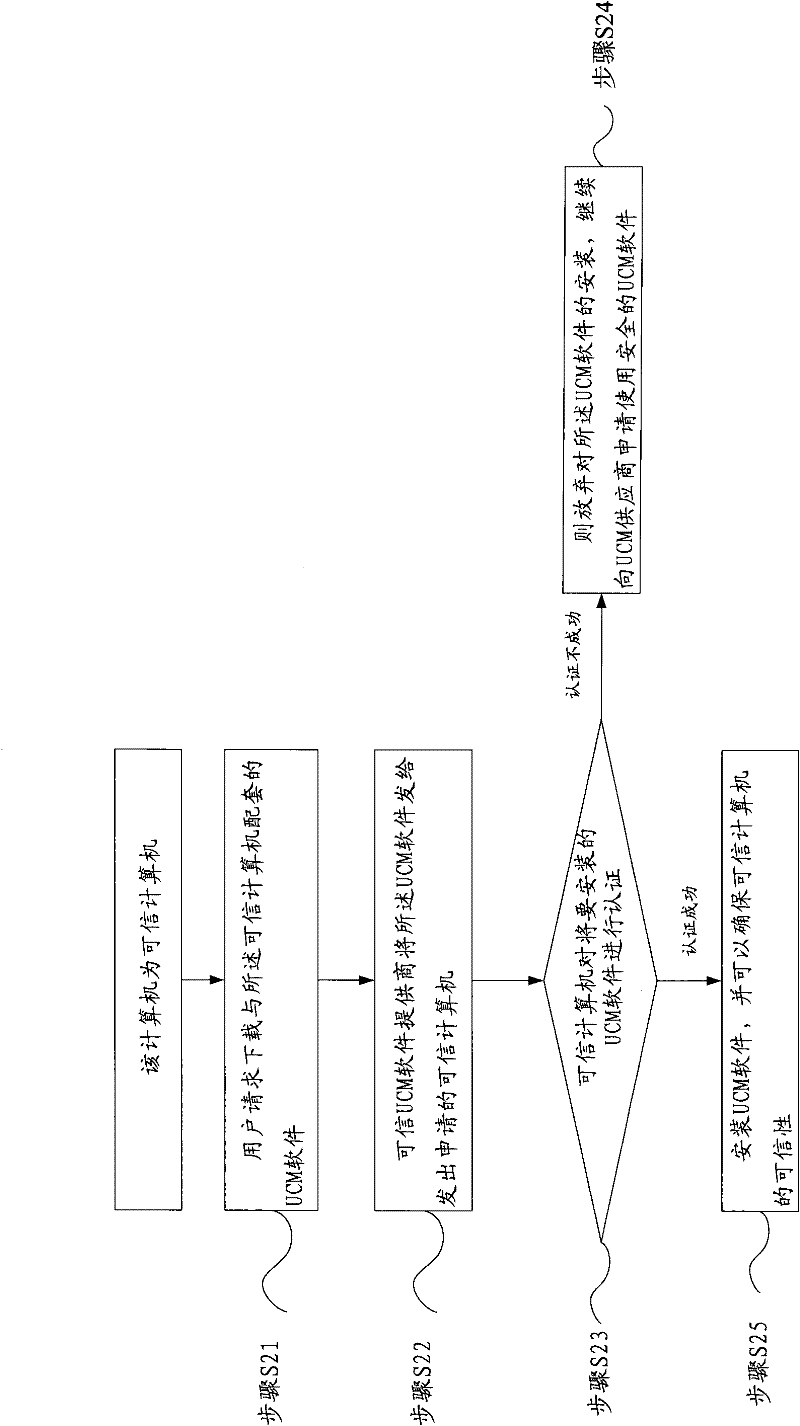
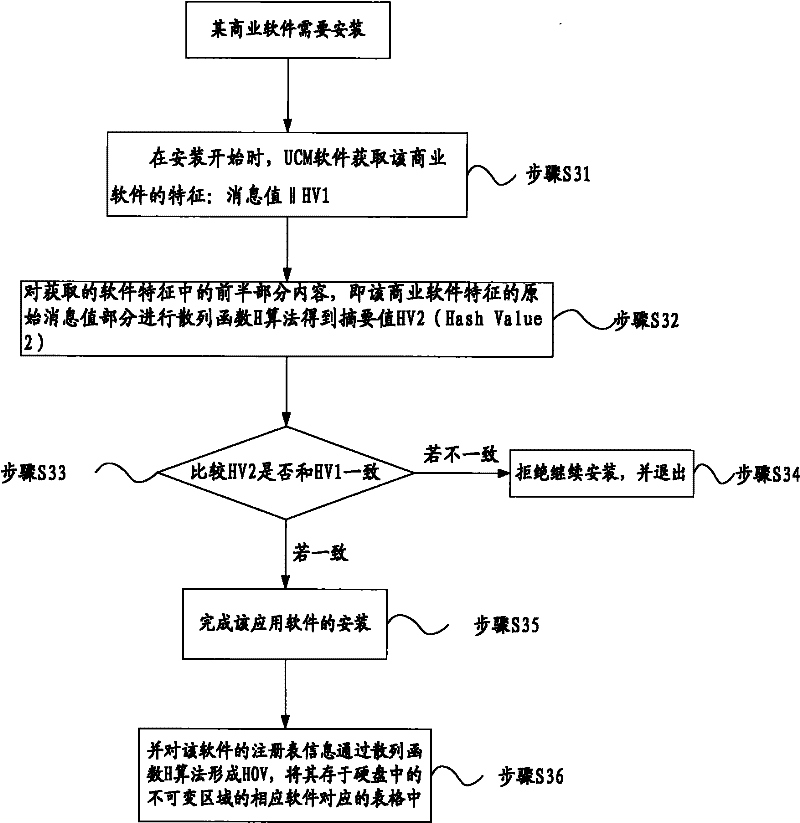
[0060] Such as figure 1 As shown, the present invention provides a trusted measurement method for software installation and upgrade. The present invention first introduces an upgrade control module (Updata Control Module). If the computer used by the user is a trusted computer, that is, a TCM (Trust Cryptography Module) computer (There is a trusted UCM software supplier associated with the issuing TCM computer, which provides absolutely safe UCM software matched with TCM to complete the precise measurement of software installation and upgrade parts), then if you want to install the application , you must pass the verification of the UCM software to obtain the right to install. When the software needs to be upgraded, the UCM software also needs to control it to guide the installation and perform security a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com