A malicious site access interception method and detection system based on flow analysis
A traffic analysis and malicious technology, which is applied in the field of network information security, can solve the problems of unpublished real-time online detection methods of malicious sites, and achieve the effects of easy promotion, real-time monitoring, and improvement of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with examples.
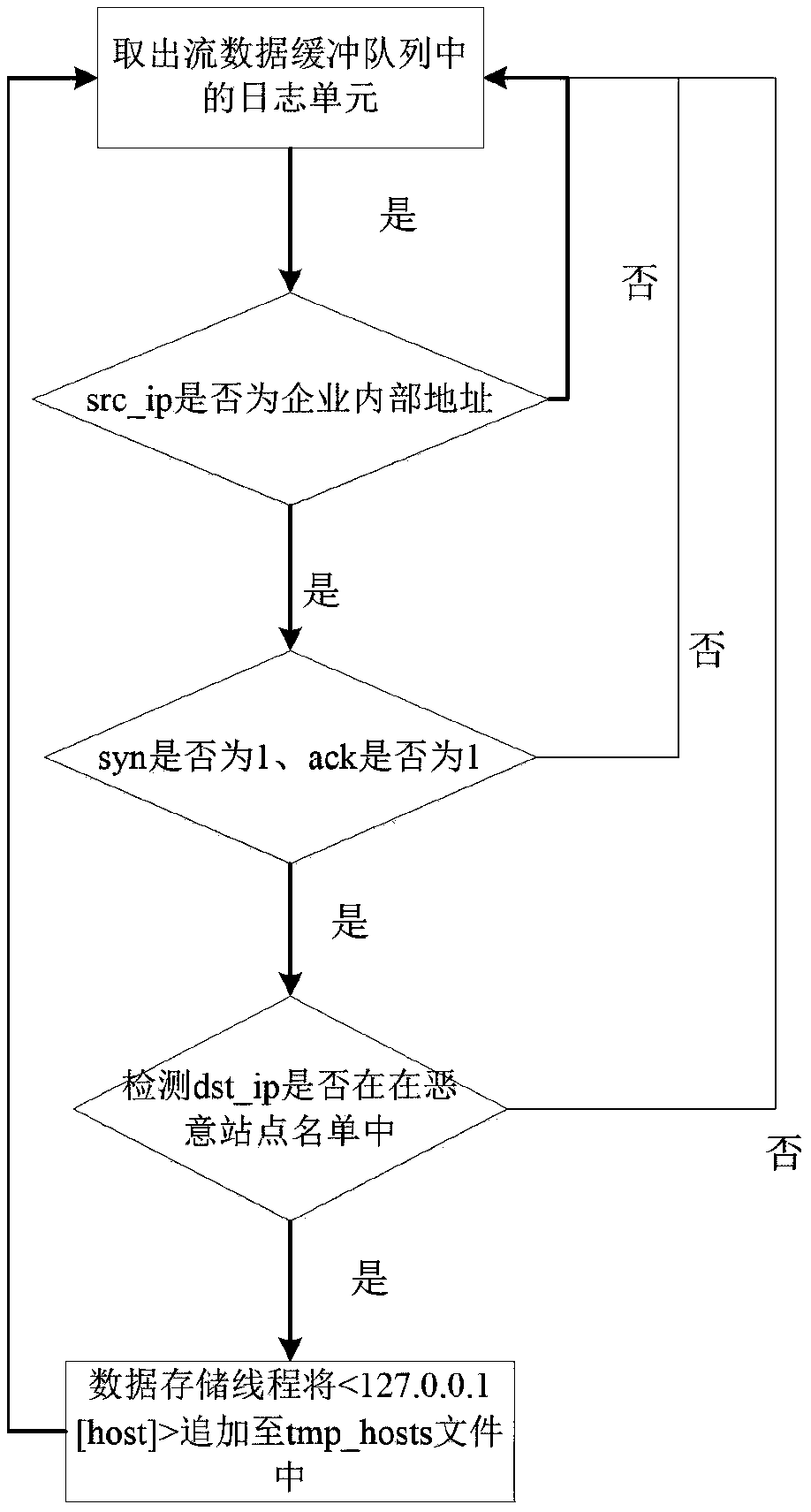
[0027] The present invention detects malicious site visits based on flow analysis, and specifically uses the log feature information of "source IP address, syn value of TCP protocol, ack value of TCP protocol, and destination IP address" in the flow data to identify whether the current visit is is a visit to a malicious site. After the present invention collects the traffic packet, it will extract characteristic information therefrom to generate a log data unit, as shown in Figure 1, which is the format of the log data unit:
[0028] Table 1
[0029] Attributes
attribute name
src_ip
source ip address
dst_ip
destination ip address
host
Main site domain name
syn
The syn value of the TCP protocol
message
Raw log information
[0030] In order to realize the monitoring of malicious site visits, the present invention ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com