Security repository-based security requirement acquisition method
A technology of security knowledge and acquisition method, applied in the field of security requirements acquisition, can solve the problems of no unified security requirements analysis and acquisition method, no security requirements method, time and energy consumption, etc., to reduce costs, improve development efficiency, The effect of reducing repair costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
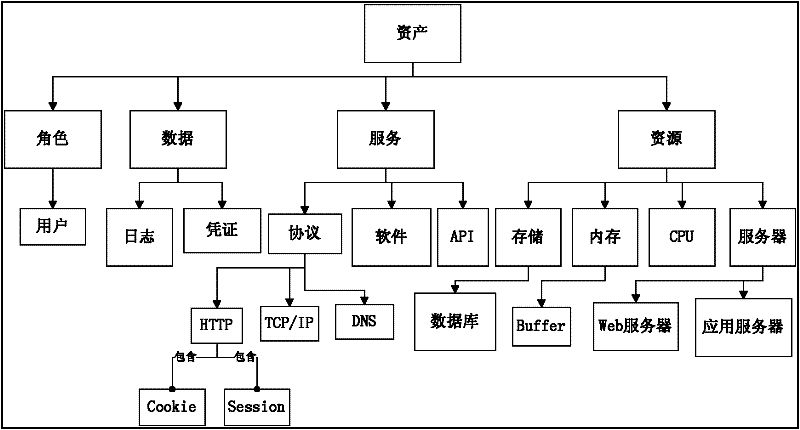
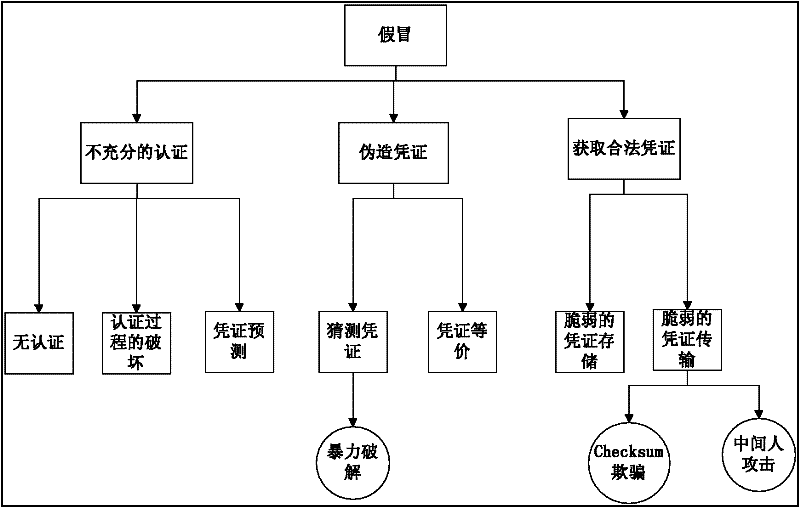
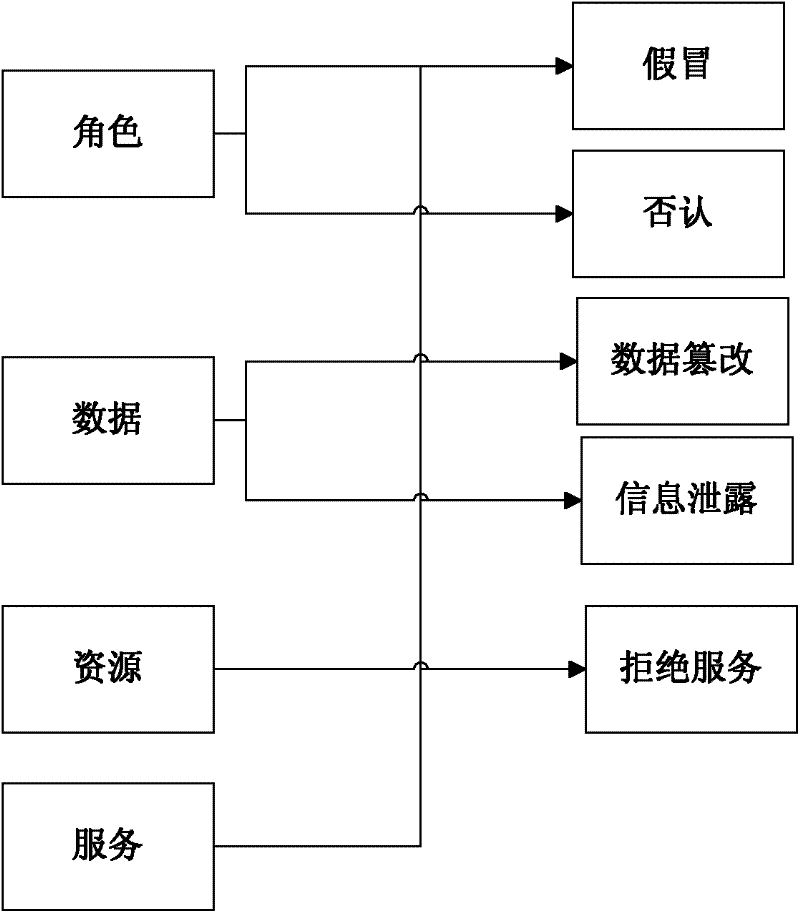
[0027] The present invention proposes a method for obtaining security requirements based on CC, which conducts semi-automatic analysis and detection for the possible security threats of assets in the software system during the software requirements stage. On the one hand, the security of the software system is improved, and on the other hand, security holes are reduced. mitigation costs. The method first establishes an asset threat knowledge base by abstracting and classifying common assets and threats of application systems. Then analyze the system use case diagram to obtain the key assets, and then match the key system assets with the asset threat knowledge base, and automatically analyze the threats and CC security function components to further obtain security requirements. The introduction is as follows:
[0028] 3) Build asset threat knowledge base
[0029] The construction of the knowledge base includes three parts: assets, threats and security function components. H...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com