Patents
Literature
205 results about "Copy-on-write" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
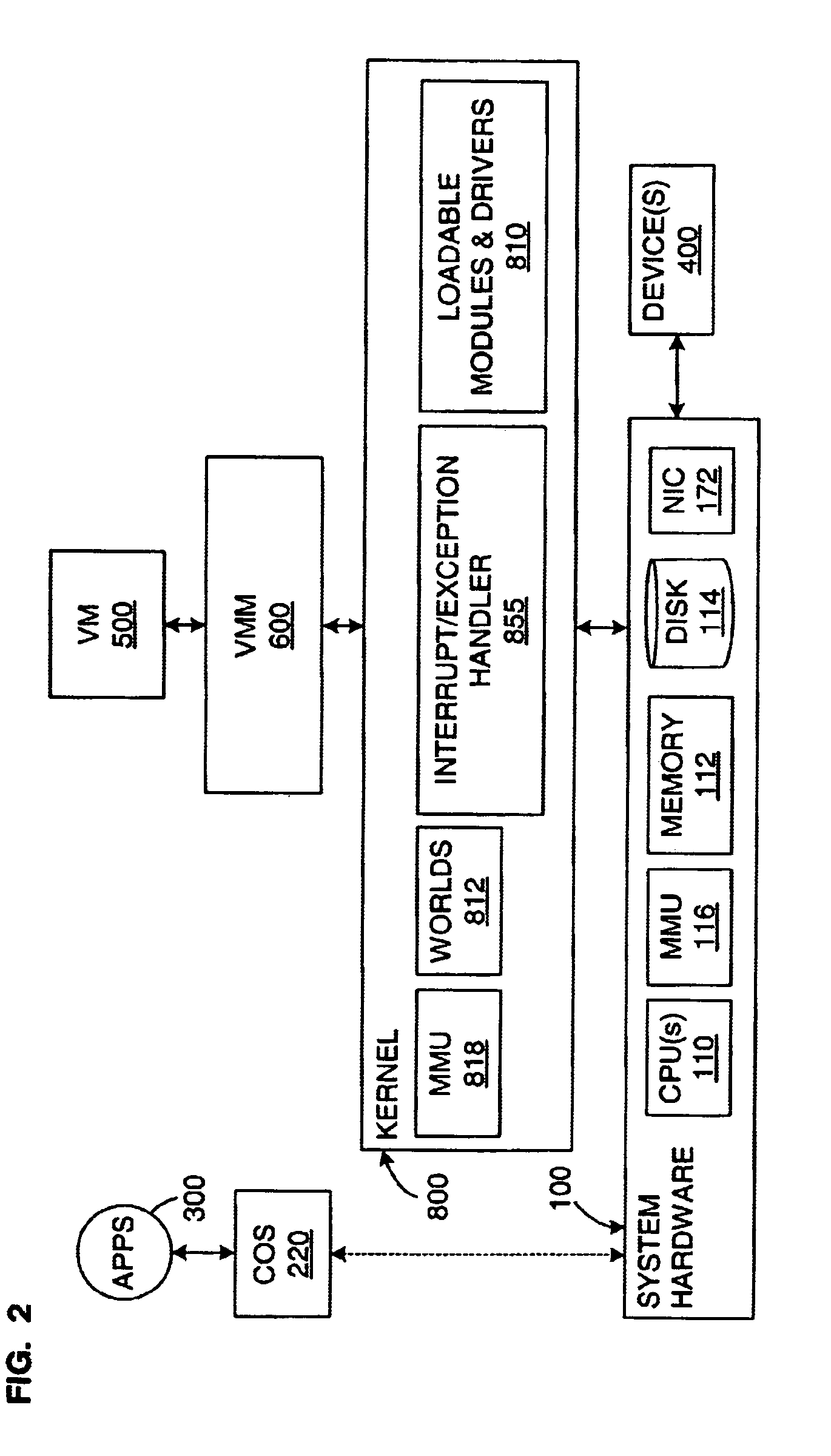
Copy-on-write (CoW or COW), sometimes referred to as implicit sharing or shadowing, is a resource-management technique used in computer programming to efficiently implement a "duplicate" or "copy" operation on modifiable resources. If a resource is duplicated but not modified, it is not necessary to create a new resource; the resource can be shared between the copy and the original. Modifications must still create a copy, hence the technique: the copy operation is deferred to the first write. By sharing resources in this way, it is possible to significantly reduce the resource consumption of unmodified copies, while adding a small overhead to resource-modifying operations.
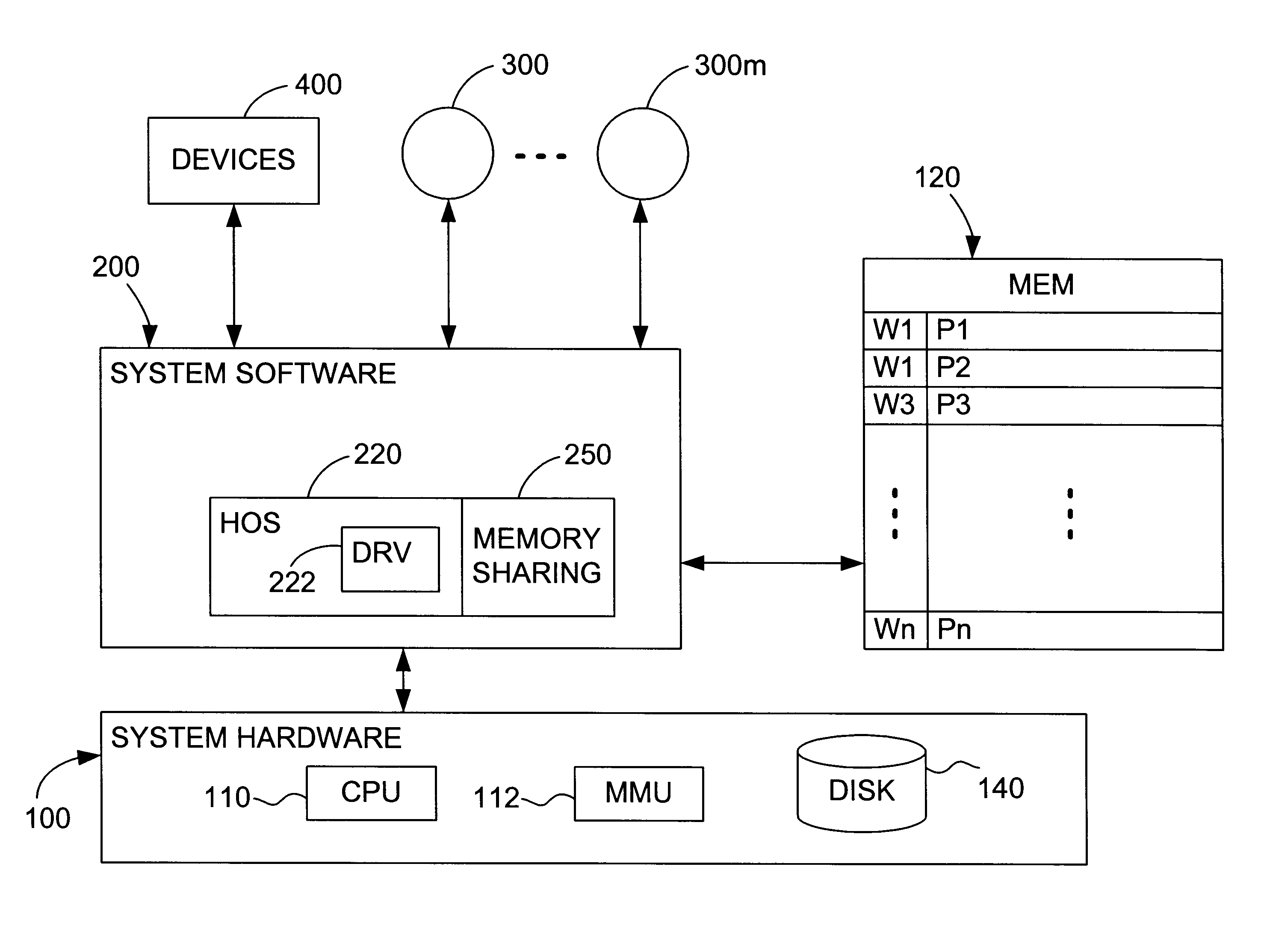
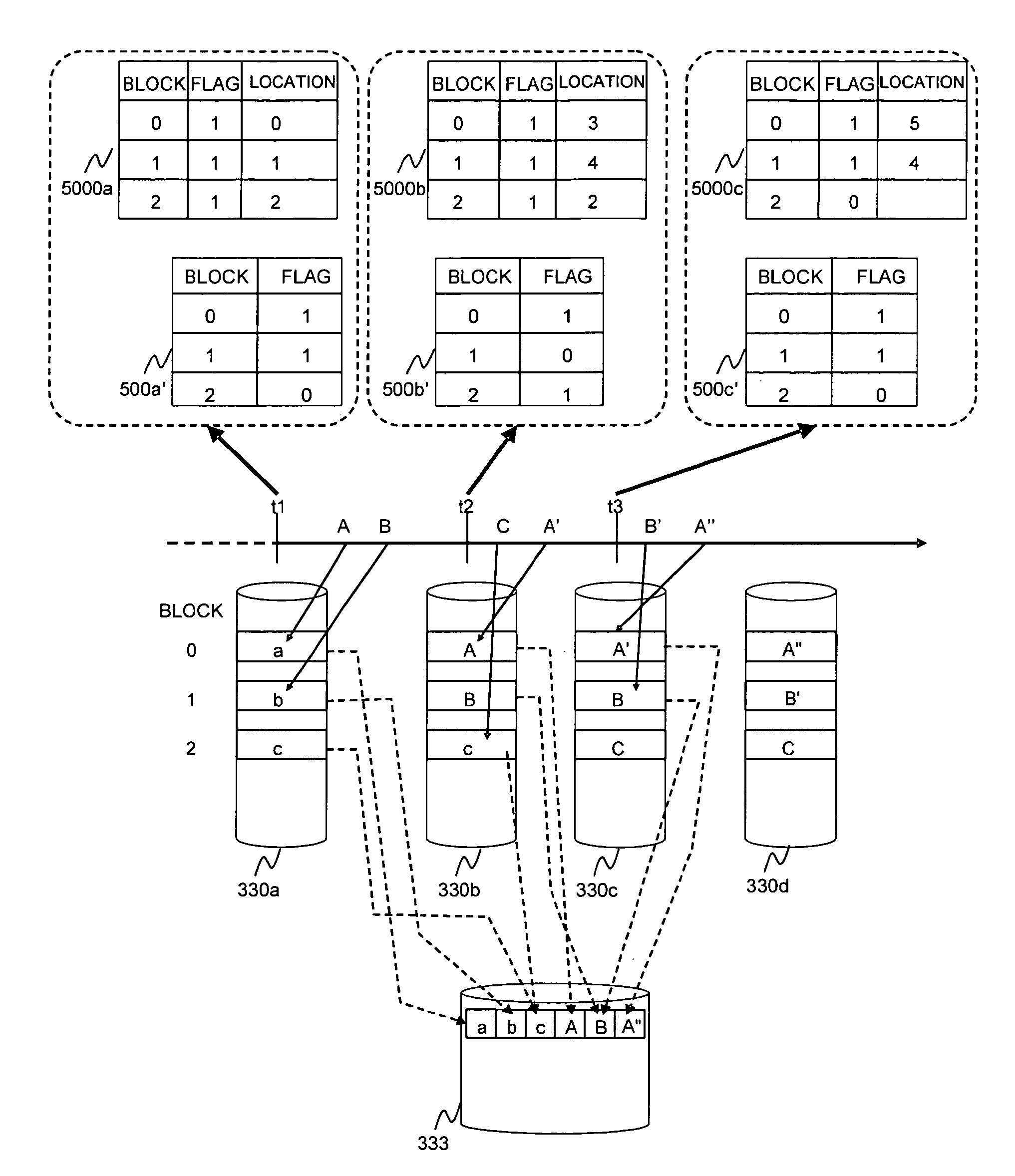
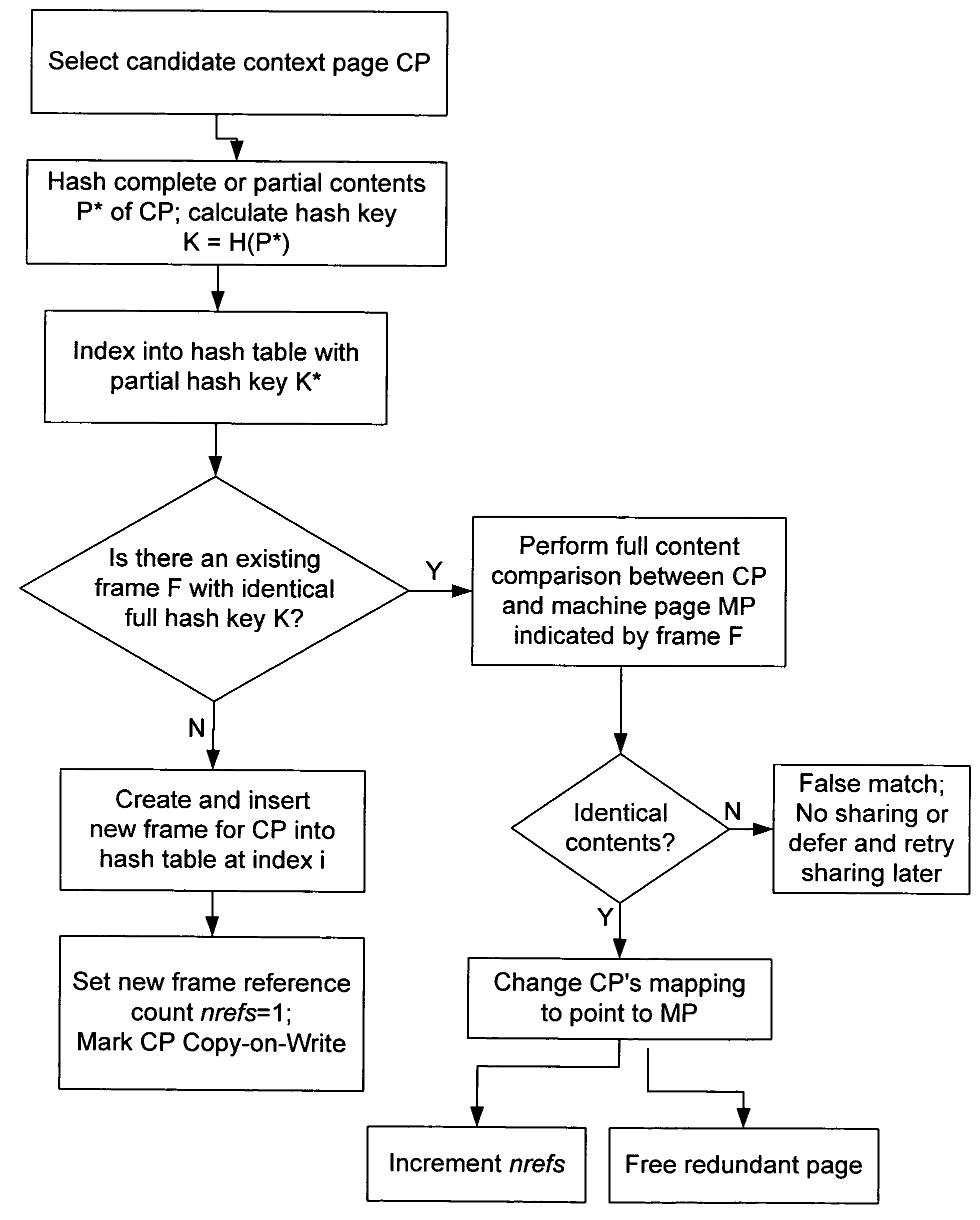
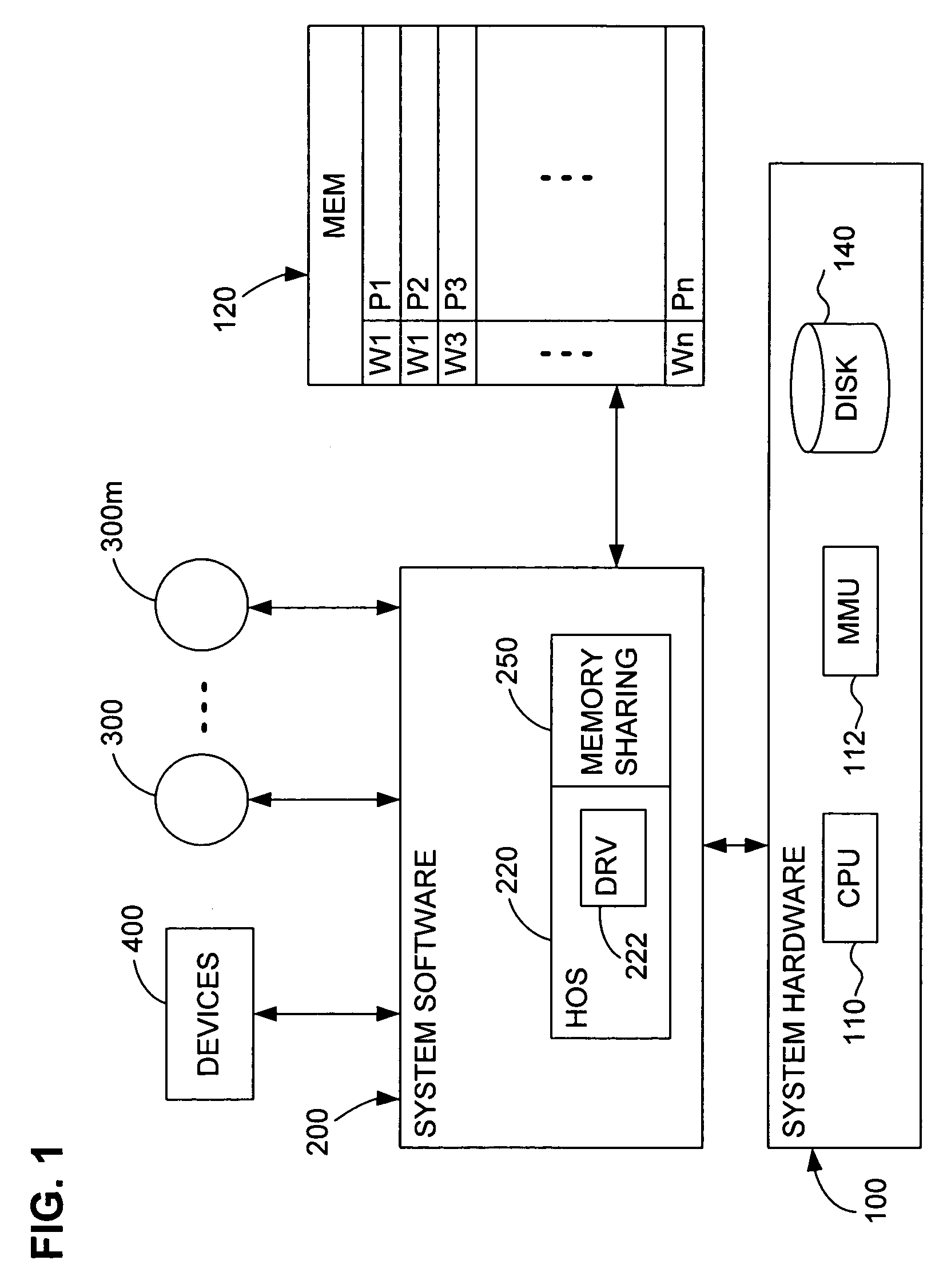
Content-based, transparent sharing of memory units
InactiveUS6789156B1Memory architecture accessing/allocationMemory adressing/allocation/relocationComputer hardwareMultiple context
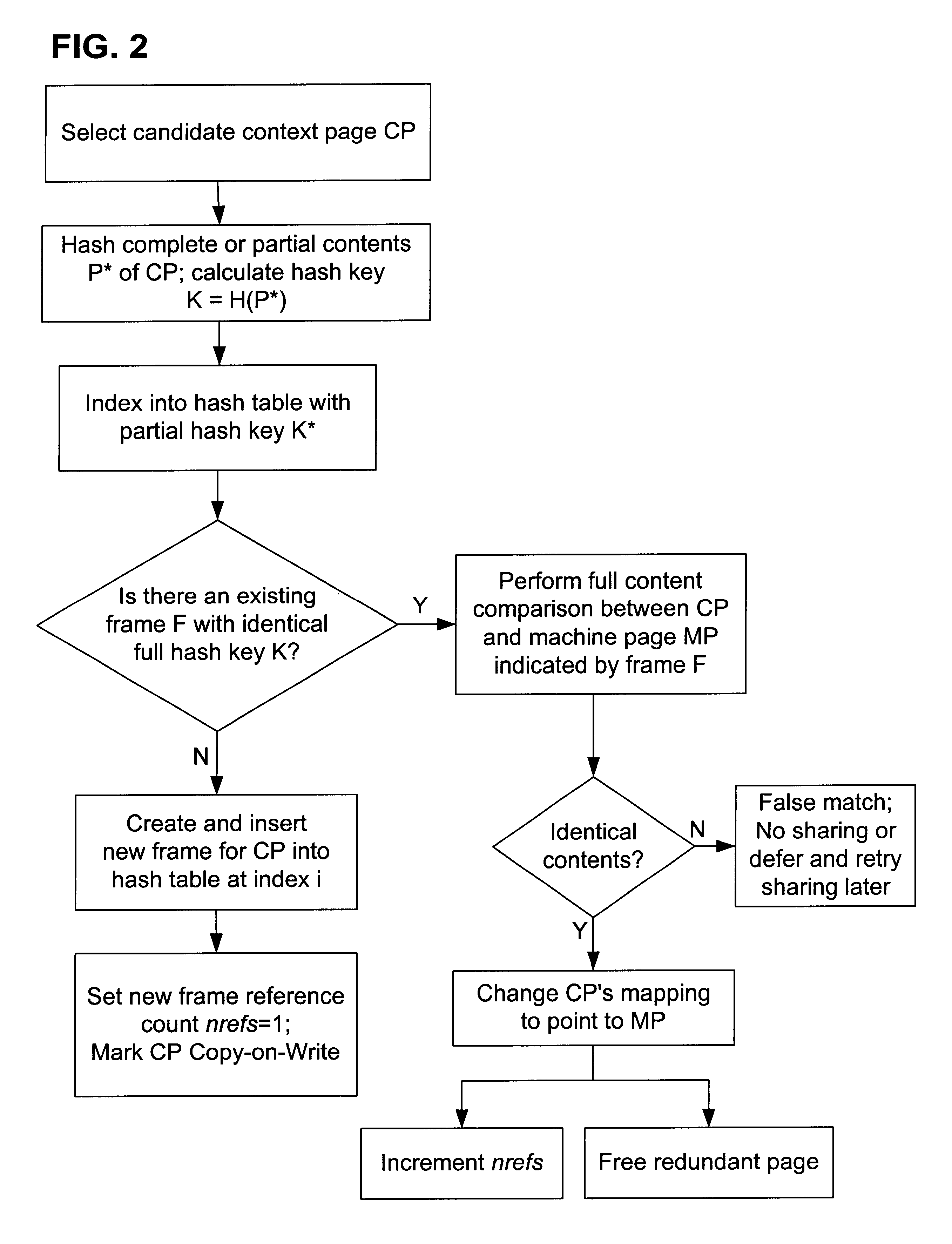
A computer system has one or more software context that share use of a memory that is divided into units such as pages. In the preferred embodiment of the invention, the context are, or include, virtual machines running on a common hardware platform. The context, as opposed to merely the addresses or page numbers, of virtual memory pages that accessible to one or more contexts are examined. If two or more context pages are identical, then their memory mappings are changed to point to a single, shared copy of the page in the hardware memory, thereby freeing the memory space taken up by the redundant copies. The shared copy is ten preferable marked copy-on-write. Sharing is preferably dynamic, whereby the presence of redundant copies of pages is preferably determined by hashing page contents and performing full content comparisons only when two or more pages hash to the same key.
Owner:VMWARE INC
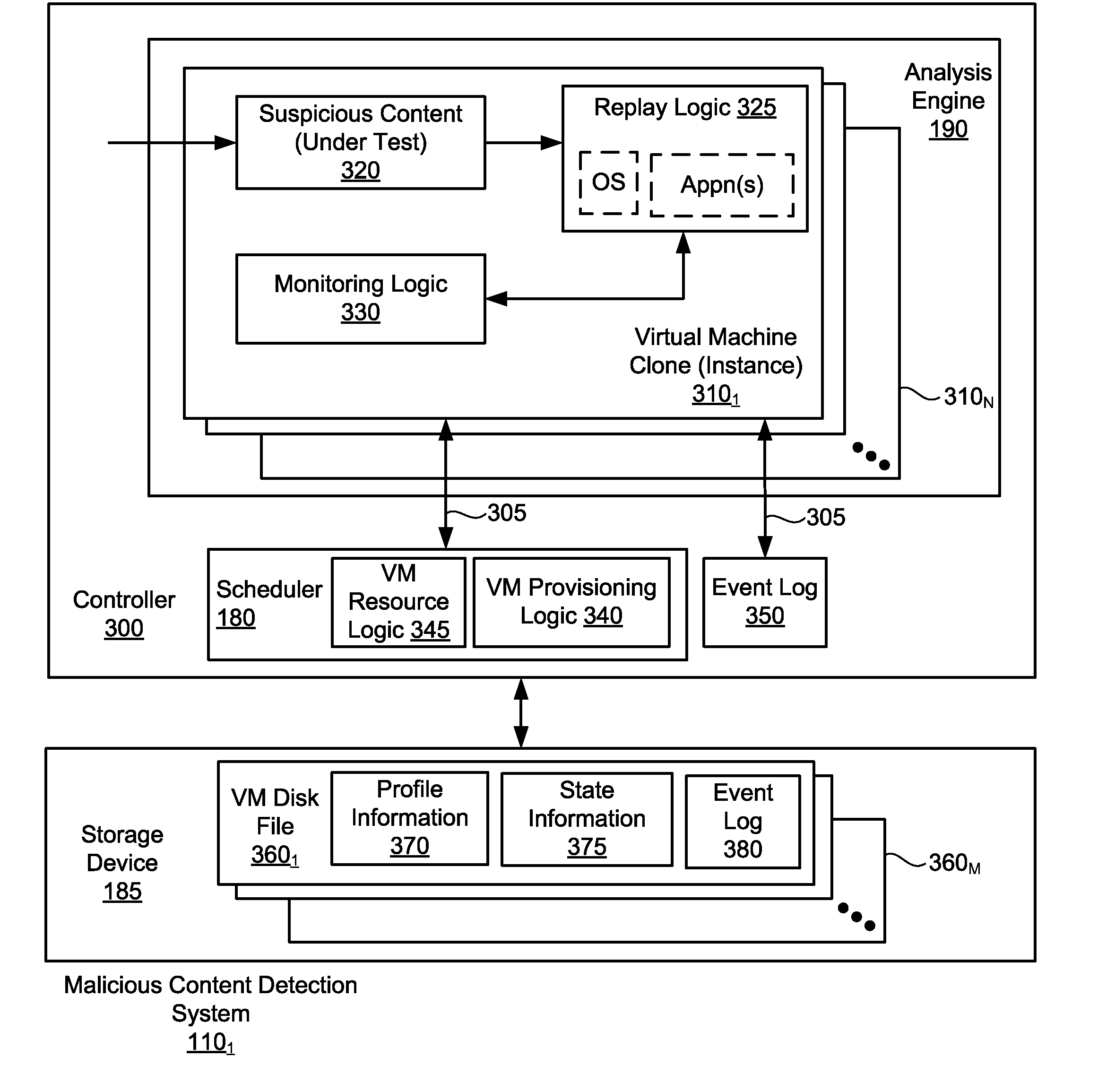
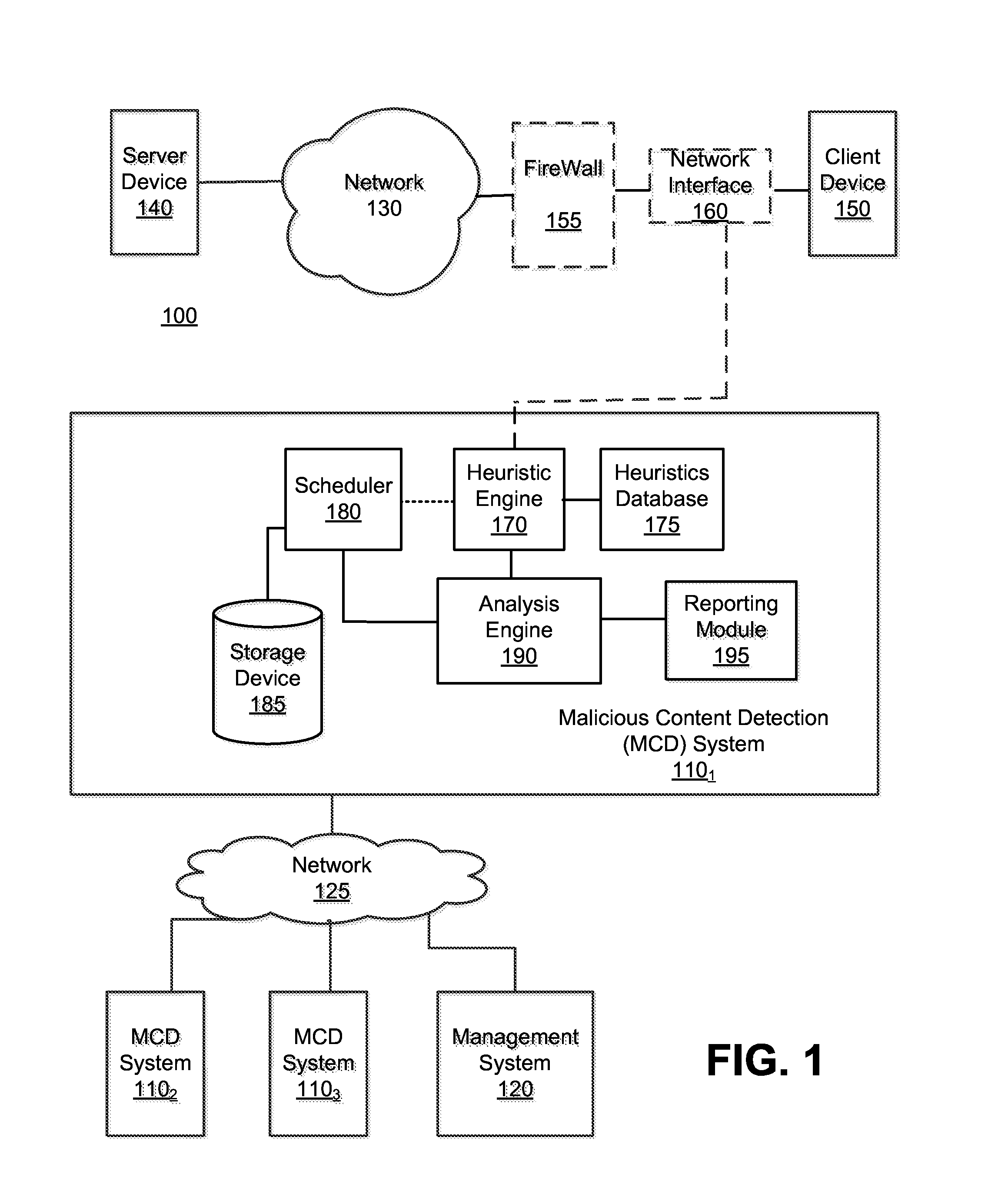
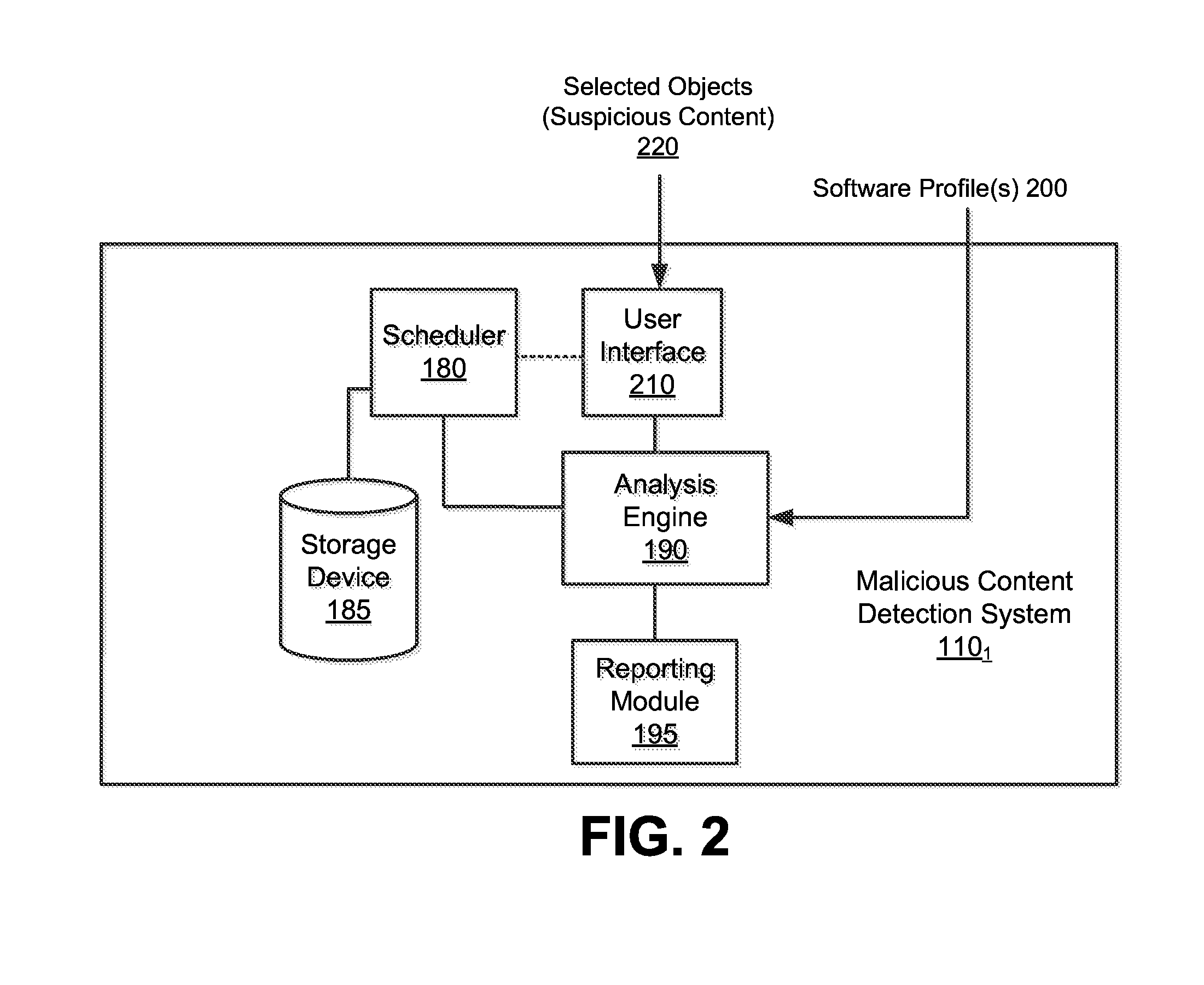
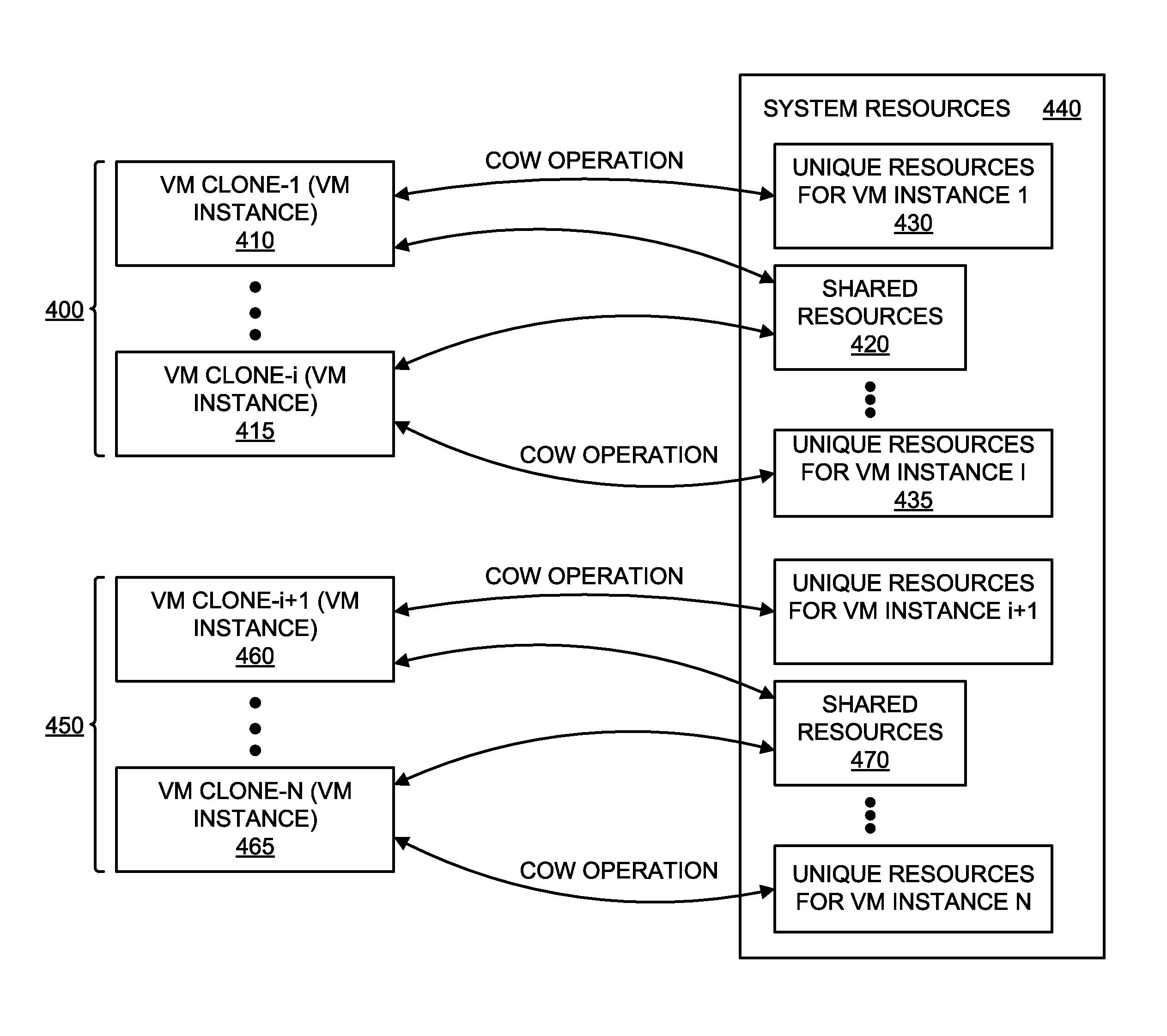
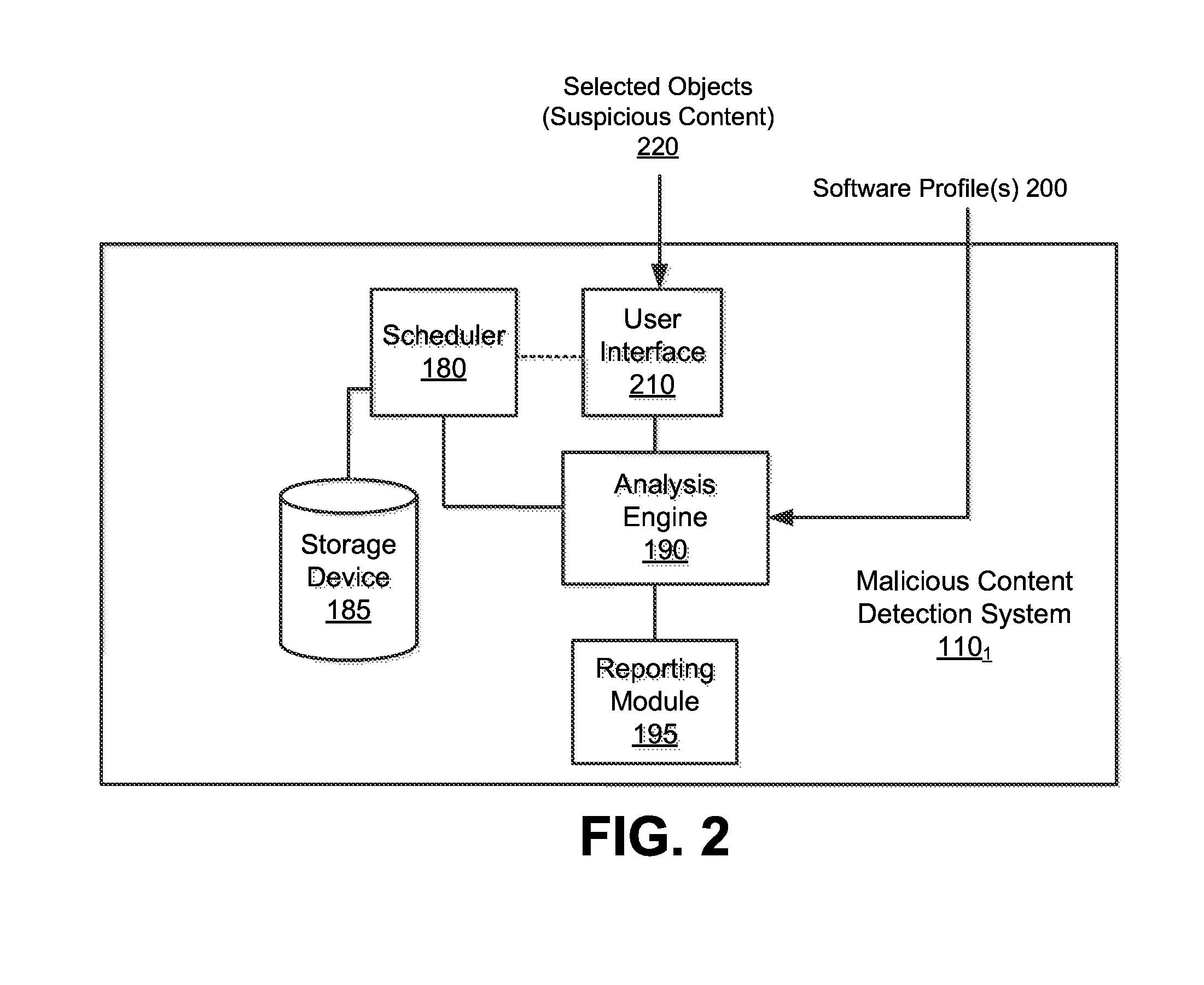
Optimized resource allocation for virtual machines within a malware content detection system
According to one embodiment, a computerized method comprises operations of instantiating a first virtual machine instance and a second virtual machine instance to run concurrently with the first virtual machine instance. The first virtual machine instance provides a first virtual operating environment while the second virtual machine instance is adapted to share the resources allocated to the first virtual machine instance. The second virtual machine instance is further adapted to allocate additional resources upon conducting a Copy-On Write operation.
Owner:FIREEYE SECURITY HLDG US LLC
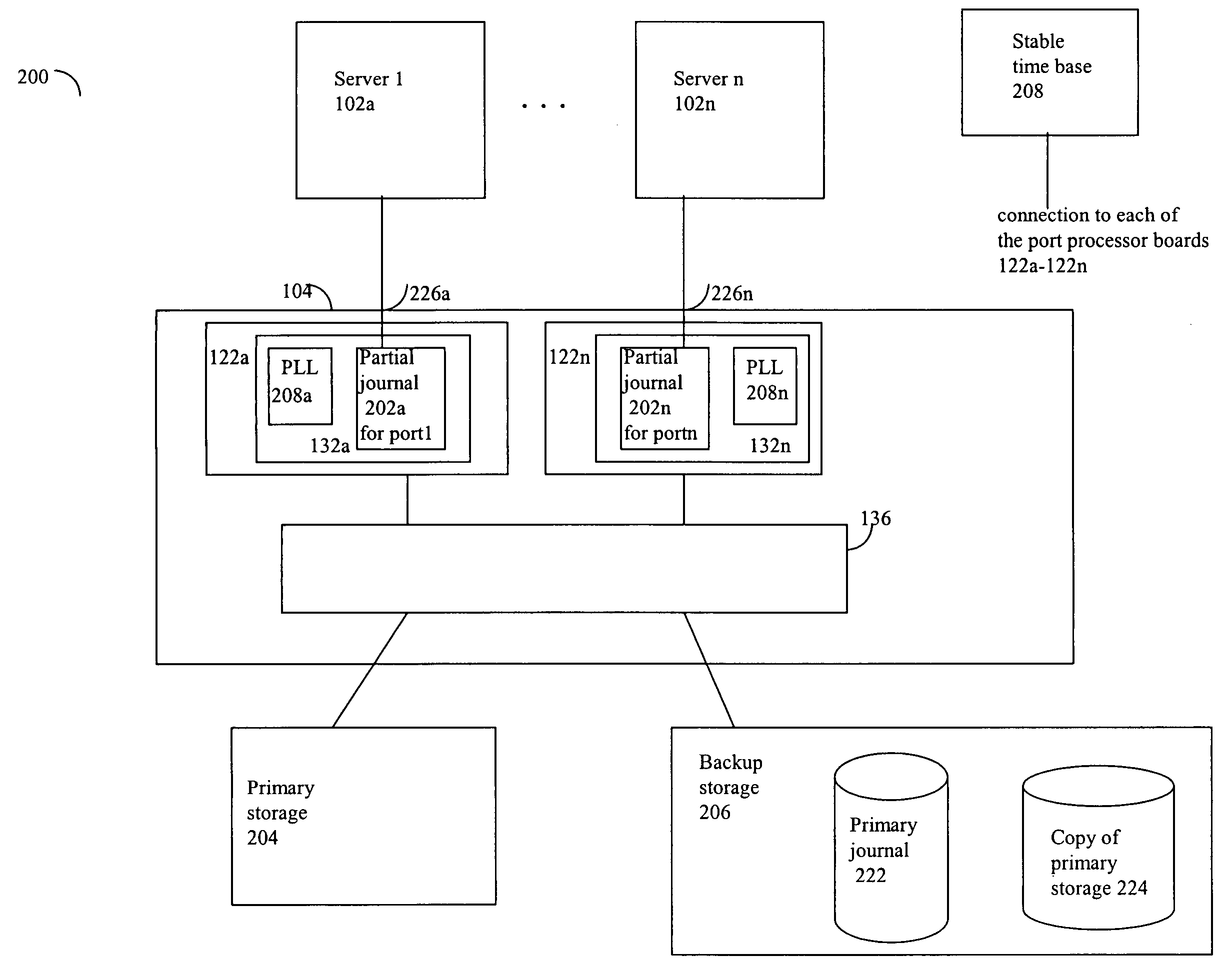
Continuous data backup using distributed journaling
Described are techniques used in connection with providing continuous data backups of primary storage. A first technique uses distributed partial journals and a copy of the primary storage. A distributed partial journal is used for each input port. The partial journals are periodically incorporated into a main journal in accordance with a time stamp for the data modification recorded in each partial journal entry. A second technique, a copy on write, uses the distributed partial journals without requiring a copy of the primary storage. For each write to an address, the current contents of the address is journaled before the address on primary storage is updated.
Owner:EMC IP HLDG CO LLC
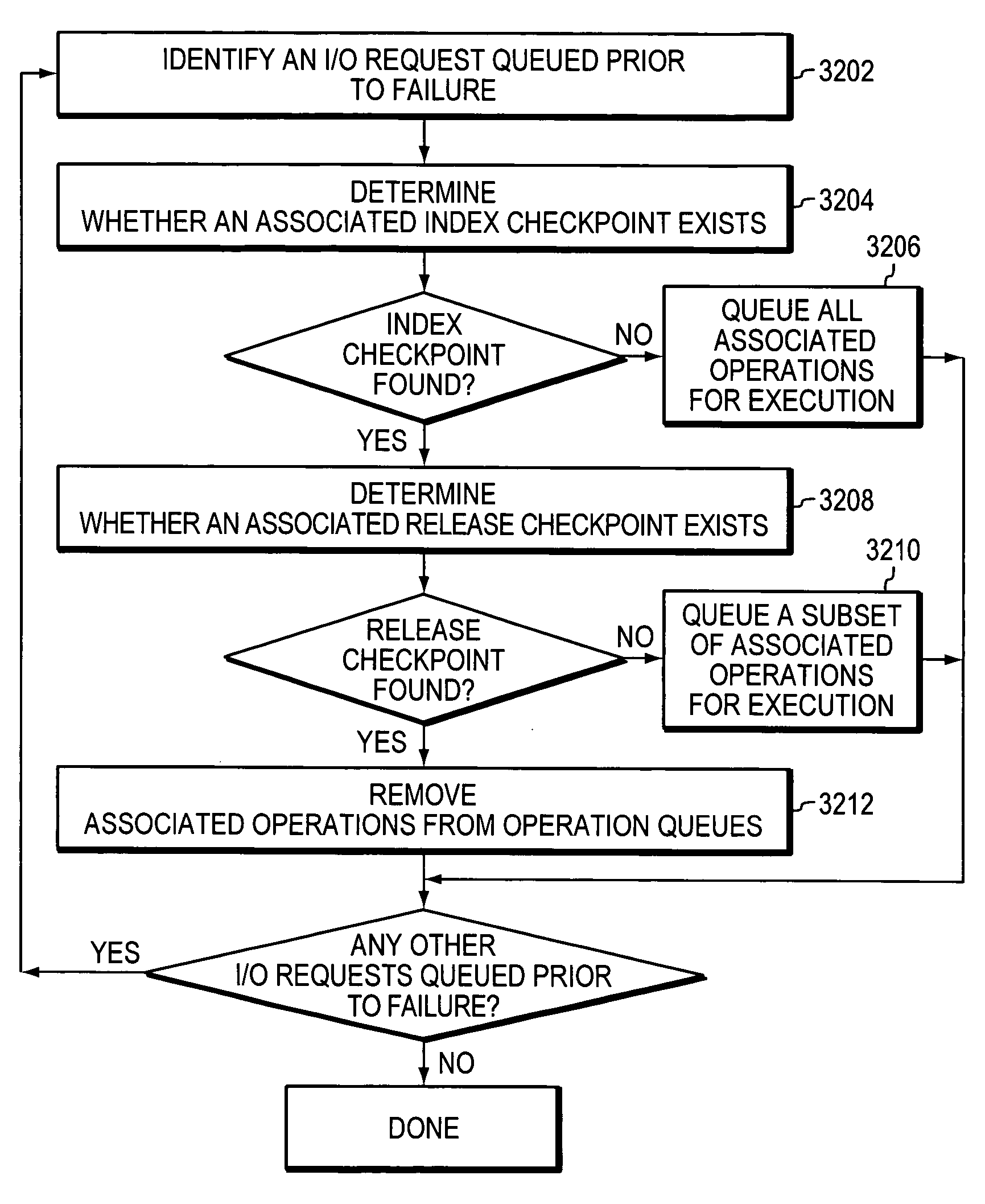
Recovering from storage transaction failures using checkpoints
ActiveUS20060047925A1Easy to useInformation can be usedMemory loss protectionError detection/correctionSuccessful completionOriginal data
The disclosed technology facilitates recovery from storage-related failures by checkpointing copy-on-write operation sequences. An operation sequence incorporating such checkpoints into a copy-on-write can include the following: receive a write request that identifies payload data to be written to a first data store, read original data associated with the first data store, copy the original data to a second data store, record transactional information associated with the write request, generate a first checkpoint to confirm the successful recordation of the transactional information and the successful copying of the original data to the second data store, write the payload data to the first data store, acknowledge a successful completion of the copy-on-write operation sequence, and generate a second checkpoint that confirms the successful completion of such operation sequence. The first and second checkpoints are used to form a pre-failure representation of one or more storage units (or parts thereof). The checkpoints can be stored with other transactional information, to facilitate recovery in the event of a failure, and can be used to facilitate the use of optimizations to process I / O operations.
Owner:SYMANTEC OPERATING CORP
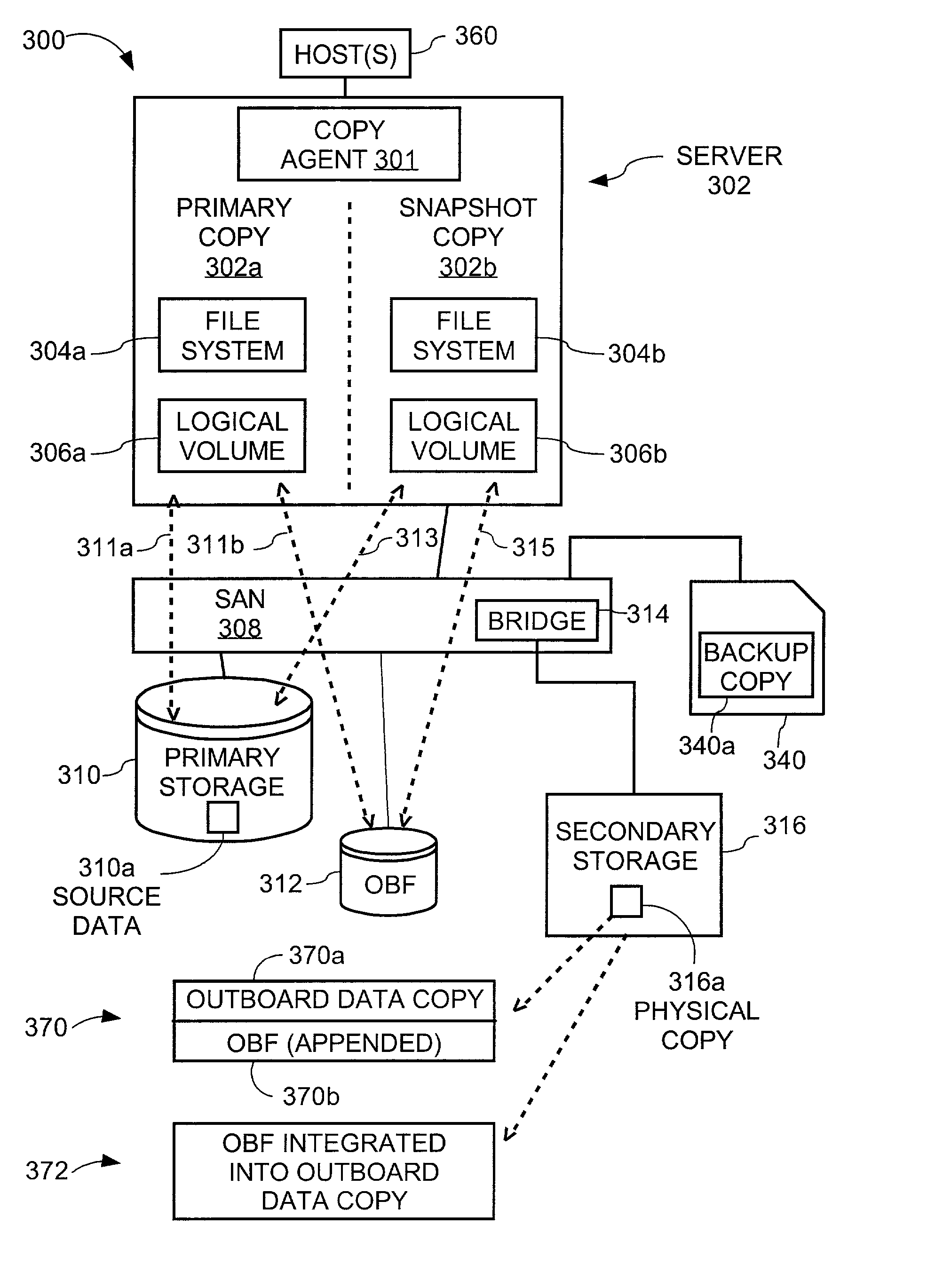
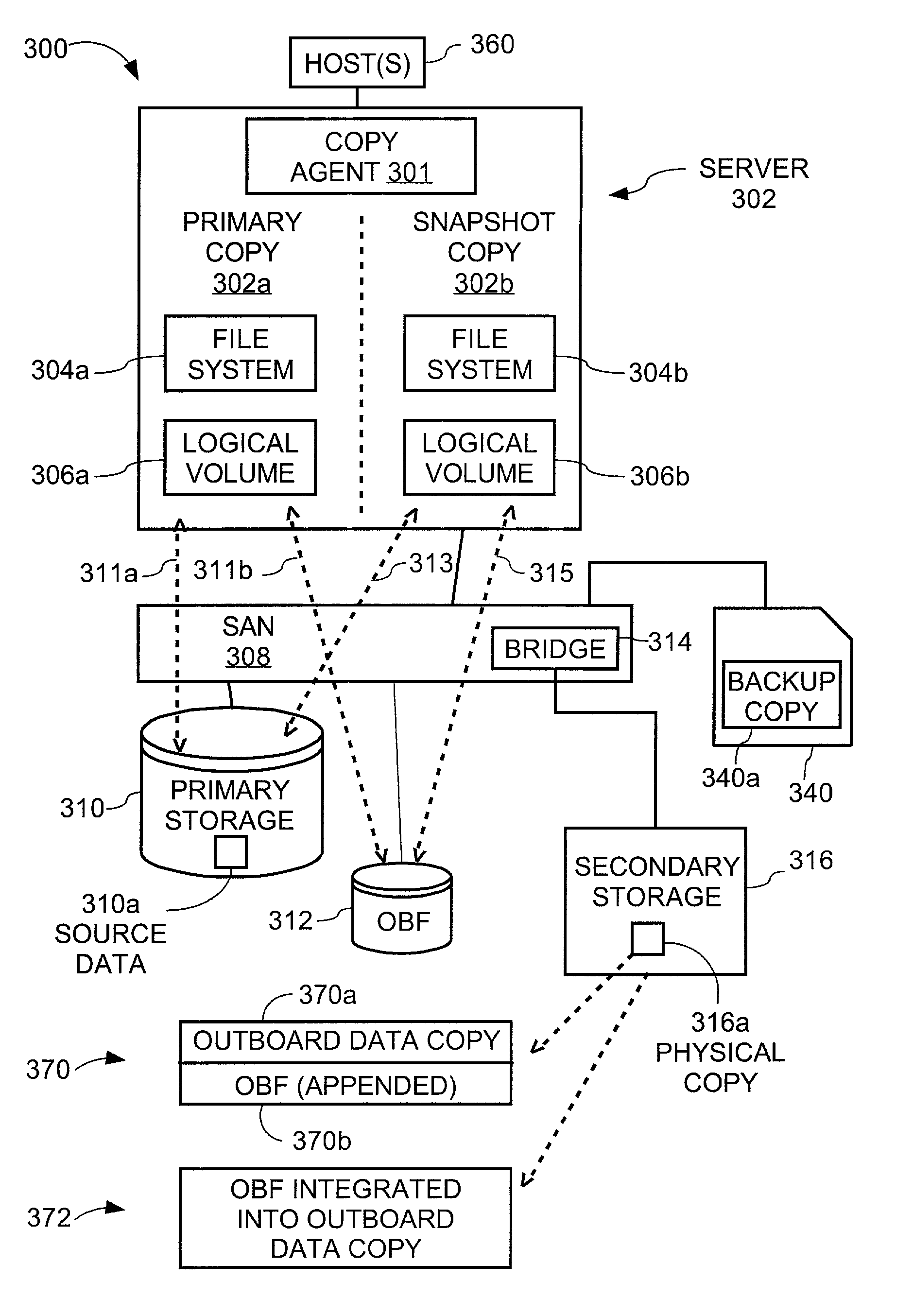
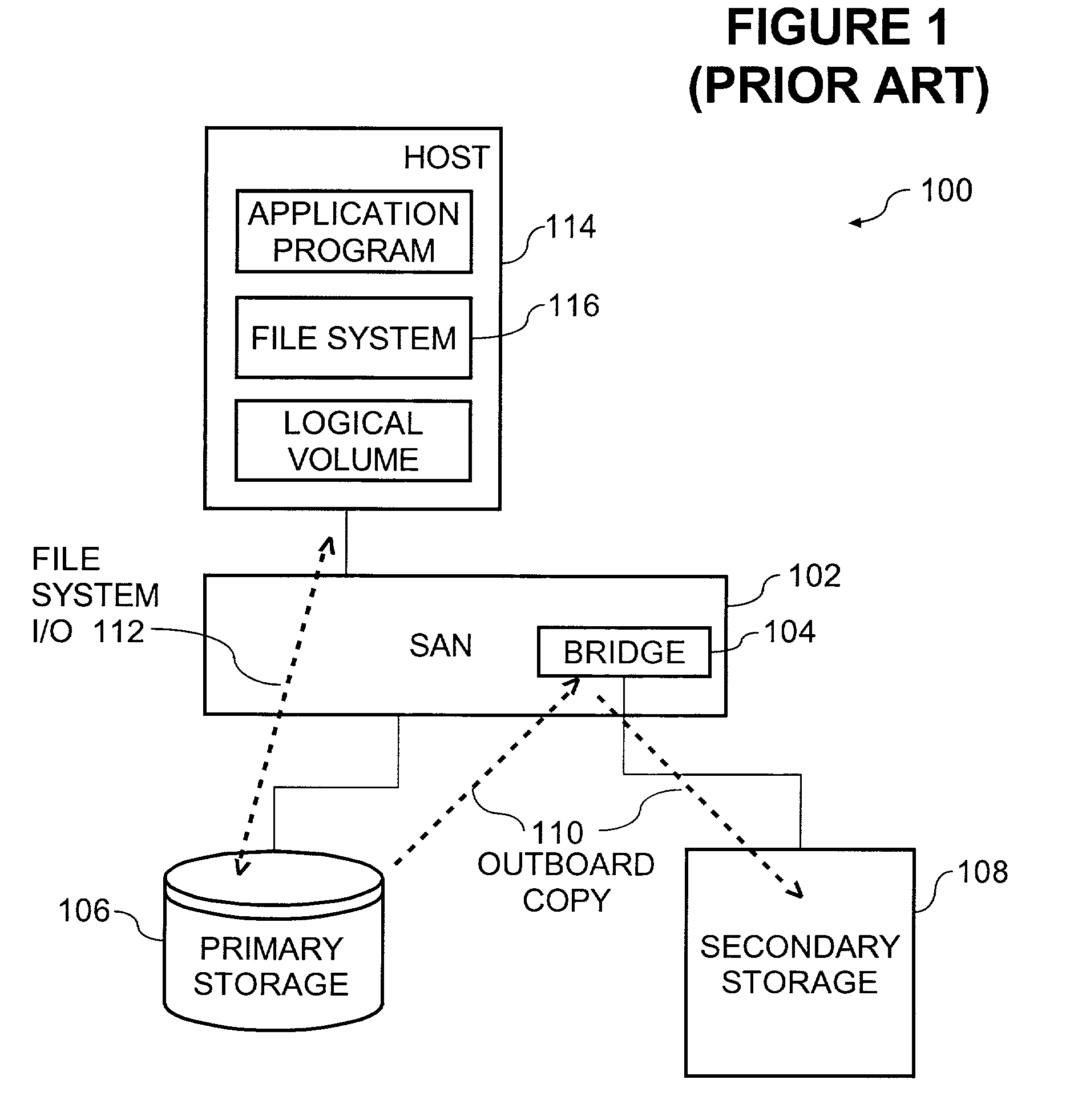
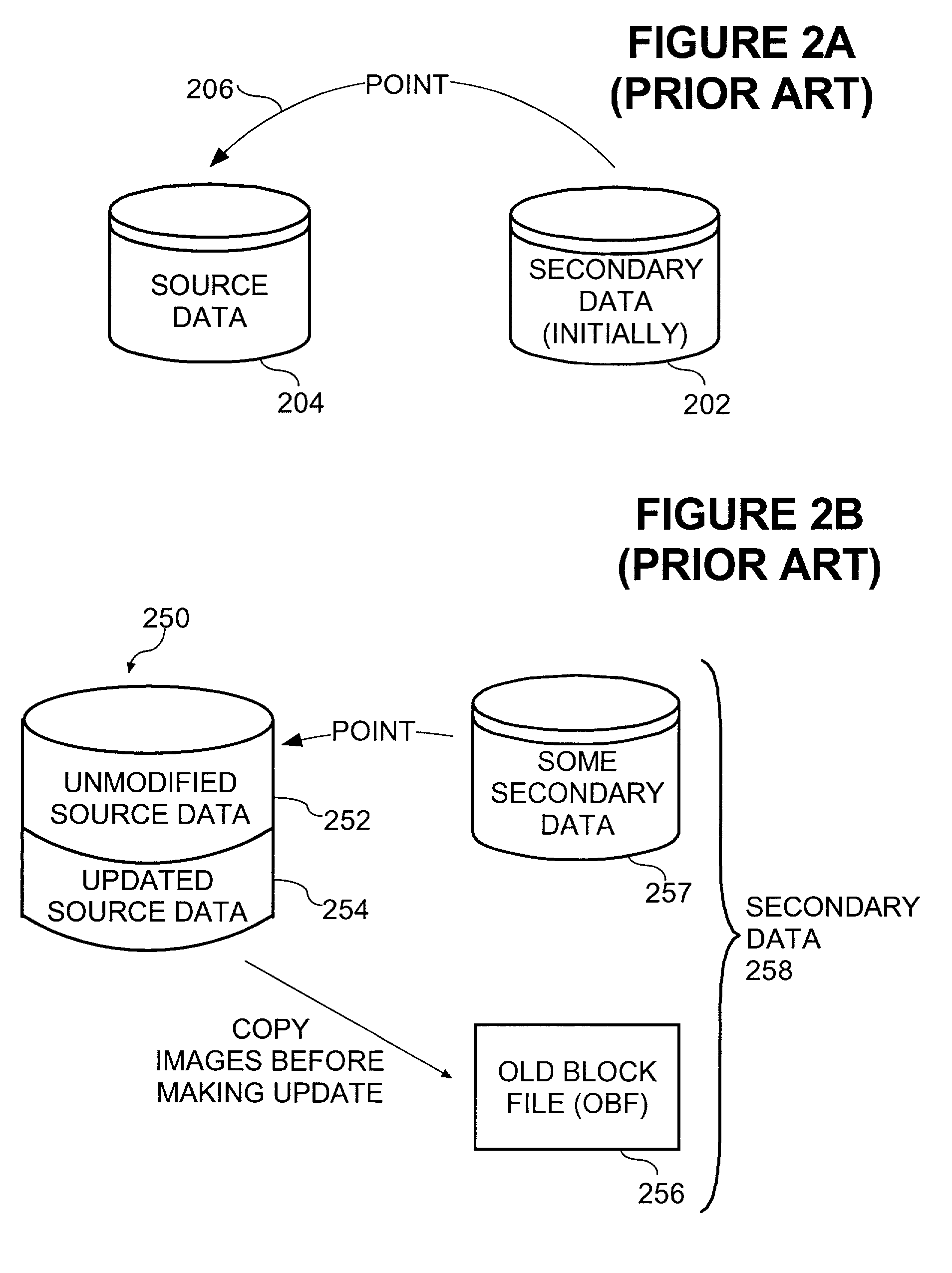
Copy method supplementing outboard data copy with previously instituted copy-on-write logical snapshot to create duplicate consistent with source data as of designated time
InactiveUS20030140070A1Data processing applicationsRedundant operation error correctionExternal applicationExternal data
A copy method creates a copy-on-write relationship between specified source data and an original image cache for updates from a designated host application. This copy-on-write relationship involves, responsive to at least a first update of each item of source data, writing an original image of said updated item of data and its associated address to the original image cache. An application outboard of the designated host application is utilized to copy all source data to secondary media without regard to whether the data has been updated since creating the copy-on-write relationship. A specified amount of data is copied from the original image cache to the secondary media. The secondary media therefore contains contents of the source data as of the moment of forming the copy-on-write relationship.
Owner:IBM CORP
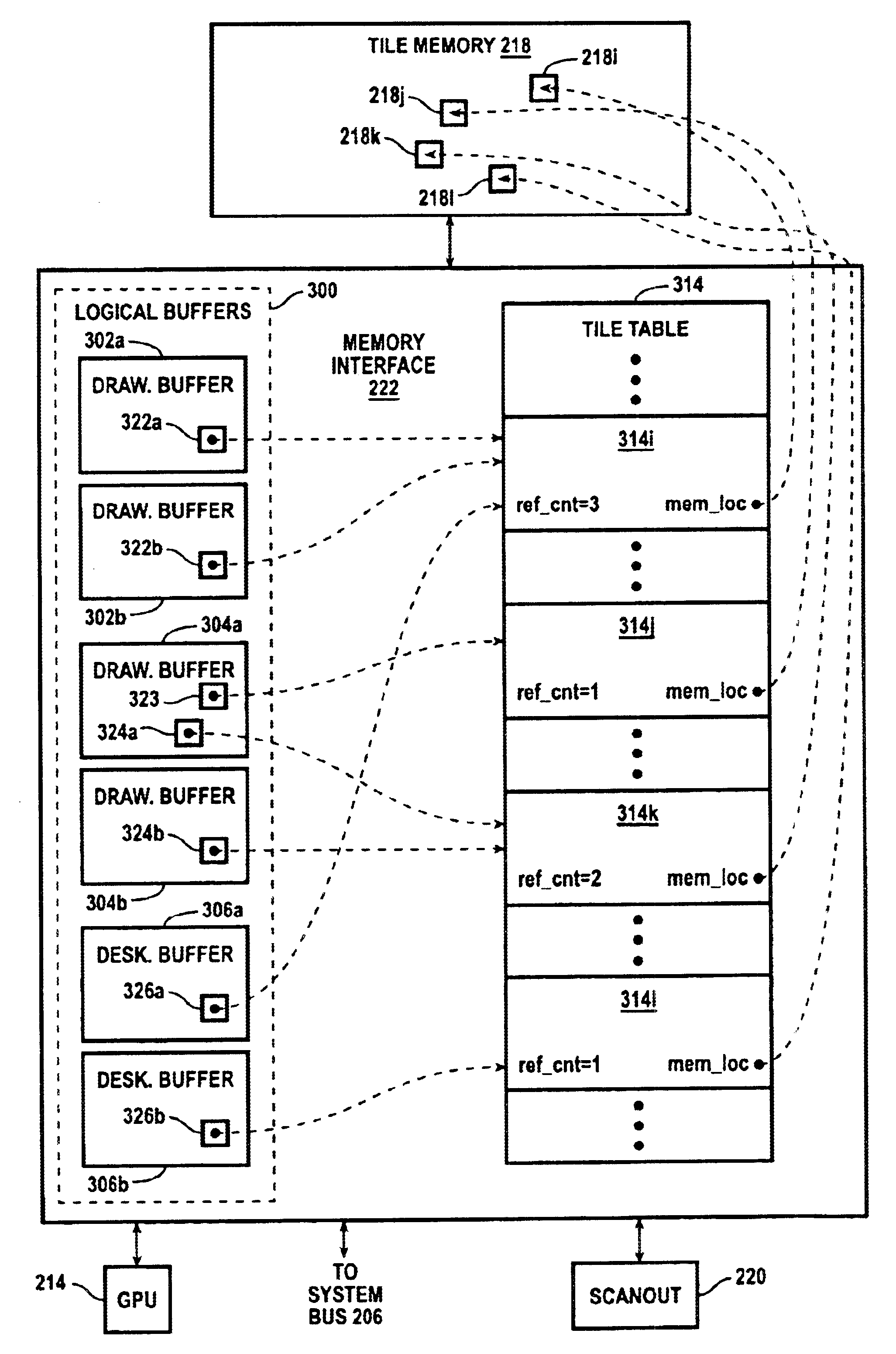
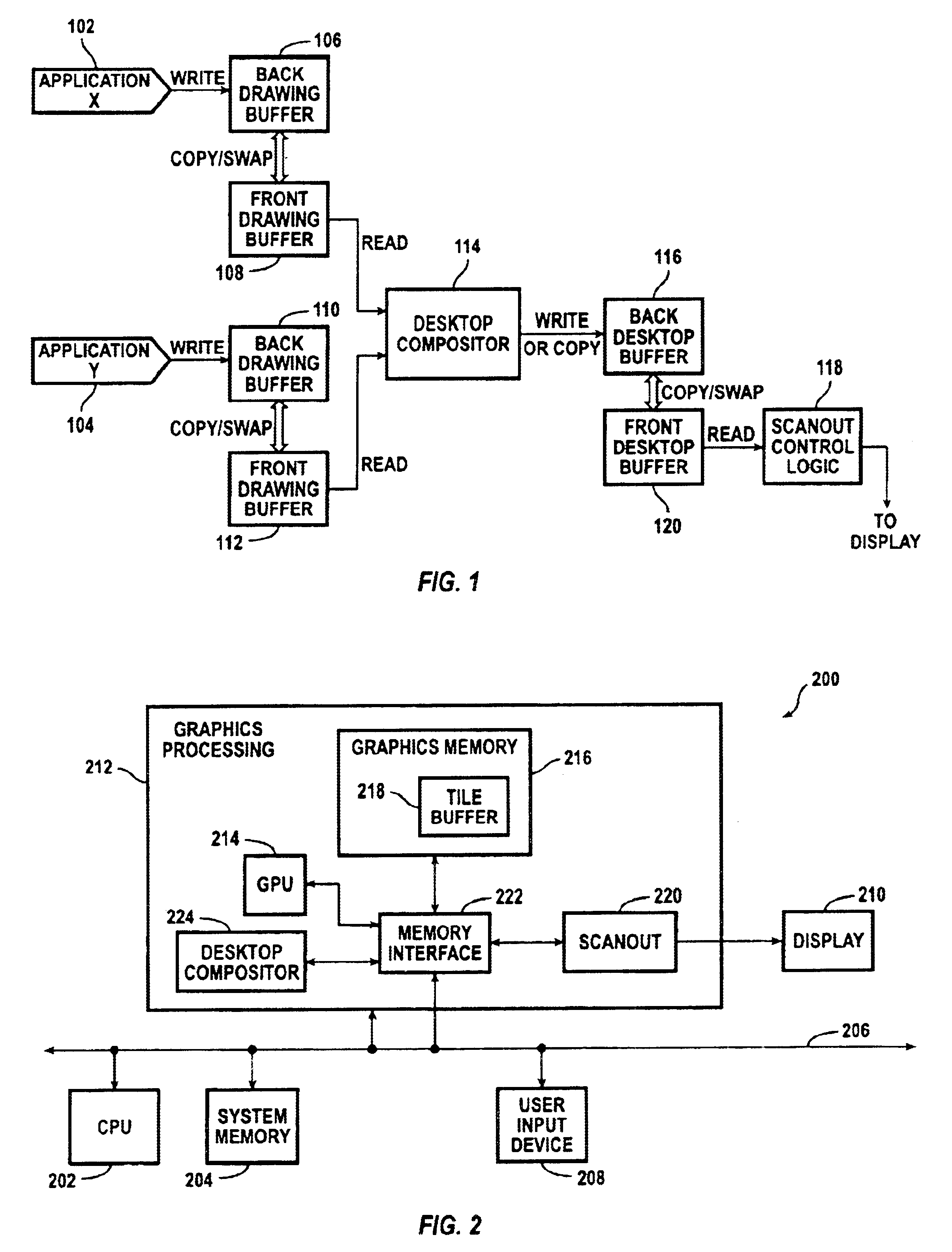
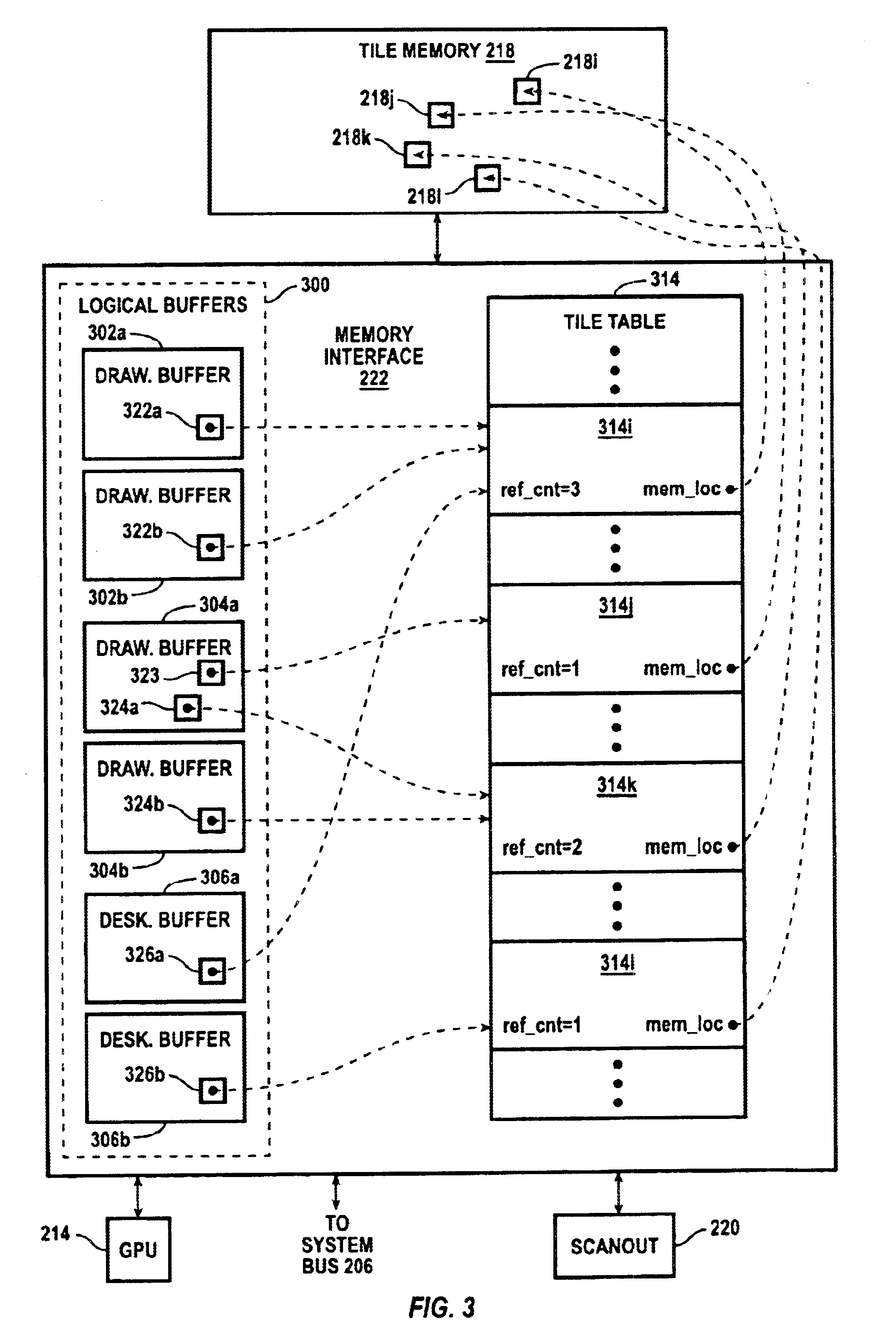
Desktop compositor using copy-on-write semantics
ActiveUS6911984B2Reduce memory bandwidthCathode-ray tube indicatorsMultiple digital computer combinationsParallel computingSemantics
Tile data for drawing and desktop buffers in a desktop compositor system is managed using “copy-on-write” semantics, in which tile data stored in a memory location is not transferred to another location until the tile data for one of the buffers is modified. For each tile in drawing buffers and desktop buffers, an association is maintained with a location in a tile memory, and the number of buffer tiles associated with each location is tracked. To copy a tile from one buffer to another, the tile association for the tile in the destination buffer is modified. New data for a tile of a buffer is written to the tile memory location associated with the buffer after ensuring that the tile memory location is not associated with any other tiles of any of the buffers. As a result, memory bandwidth can be considerably reduced.
Owner:NVIDIA CORP
Optimized resource allocation for virtual machines within a malware content detection system
According to one embodiment, a computerized method comprises operations of instantiating a first virtual machine instance and a second virtual machine instance to run concurrently with the first virtual machine instance. The first virtual machine instance provides a first virtual operating environment while the second virtual machine instance is adapted to share the resources allocated to the first virtual machine instance. The second virtual machine instance is further adapted to allocate additional resources upon conducting a Copy-On Write operation.
Owner:FIREEYE SECURITY HLDG US LLC
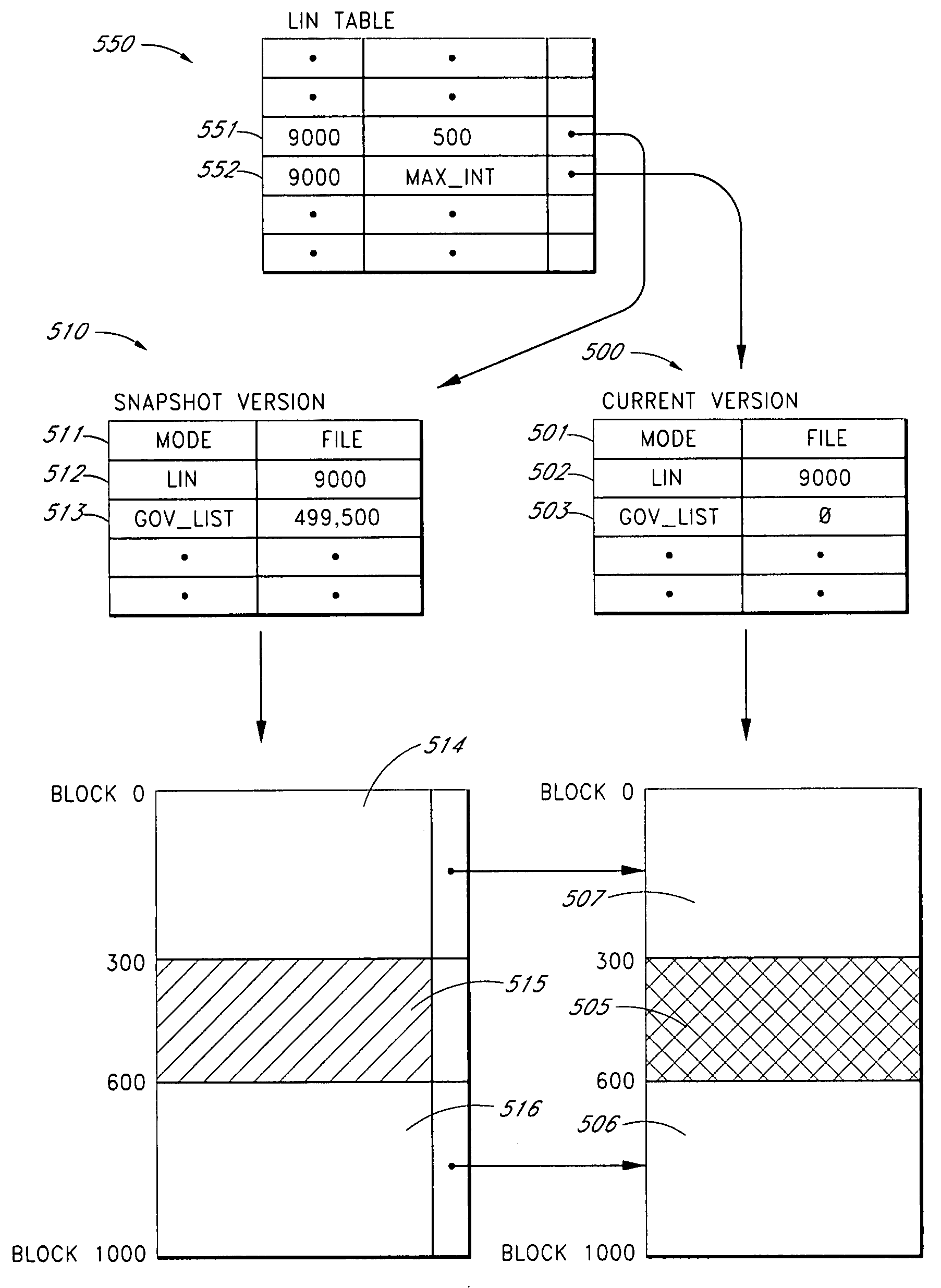
Systems and methods for adaptive copy on write
ActiveUS20090055607A1Digital data information retrievalMemory loss protectionDistributed File SystemFile system
In one embodiment, a user or client device communicates with a distributed file system comprised of one or more physical nodes. The data on each of the physical nodes store metadata about files and directories within the file system. Some of the embodiments permit a user to take a snapshot of data stored on the file system. The snapshot may include a single file, a single directory, a plurality of files within a directory, a plurality of directories, a path on the file system that includes nested files and subdirectories, or more than one path on the file system that each includes nested files and directories. In some embodiments, systems and methods intelligently choose whether to use copy-on-write or point-in-time copy when saving data in a snapshot version of a file whose current version is being overwritten. In some embodiments, systems and methods allow snapshot users to return from a snapshot directory to the immediate parent directory from which the user entered into the snapshot.
Owner:EMC IP HLDG CO LLC
System and method for asynchronous reads of old data blocks updated through a write-back cache
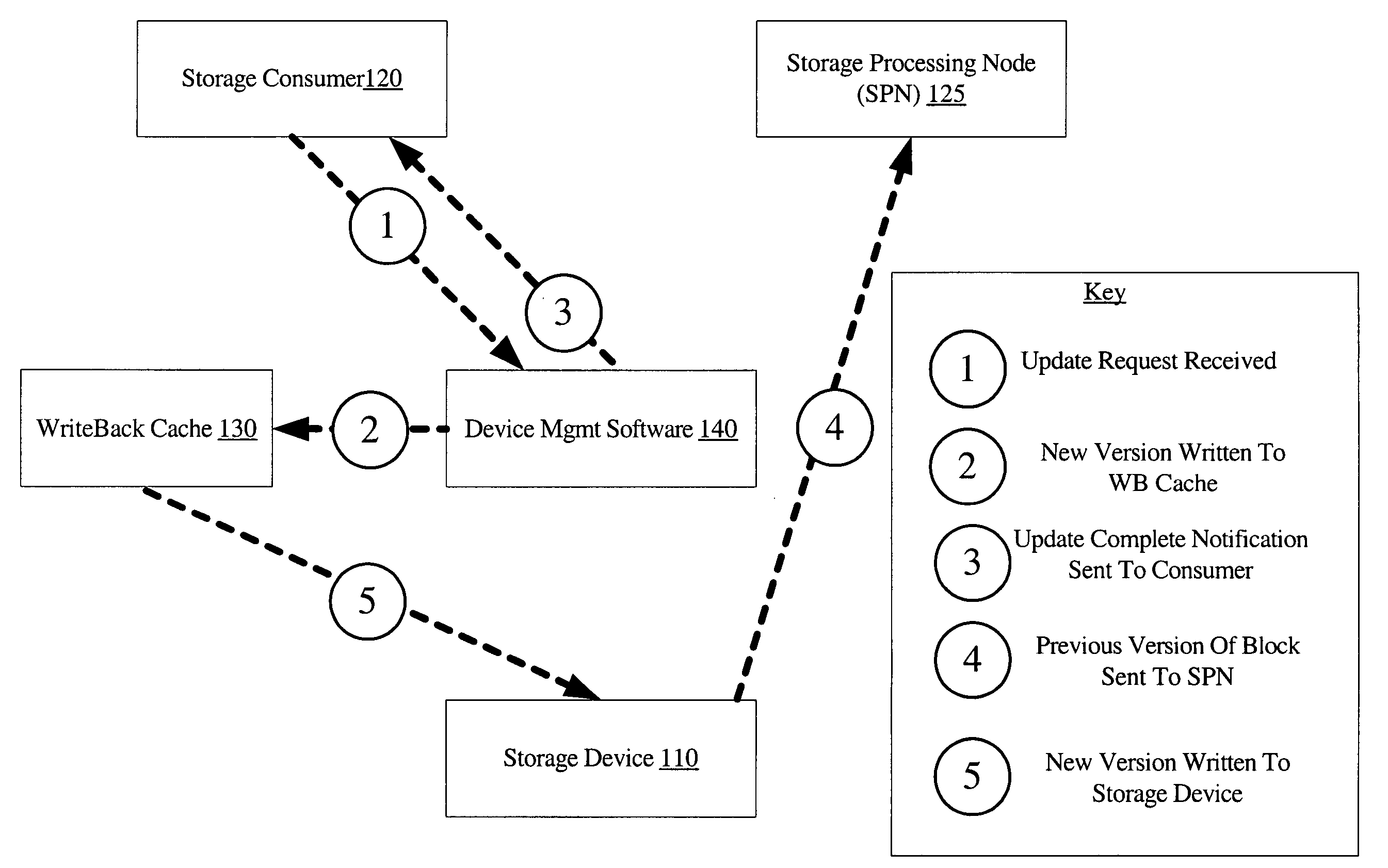
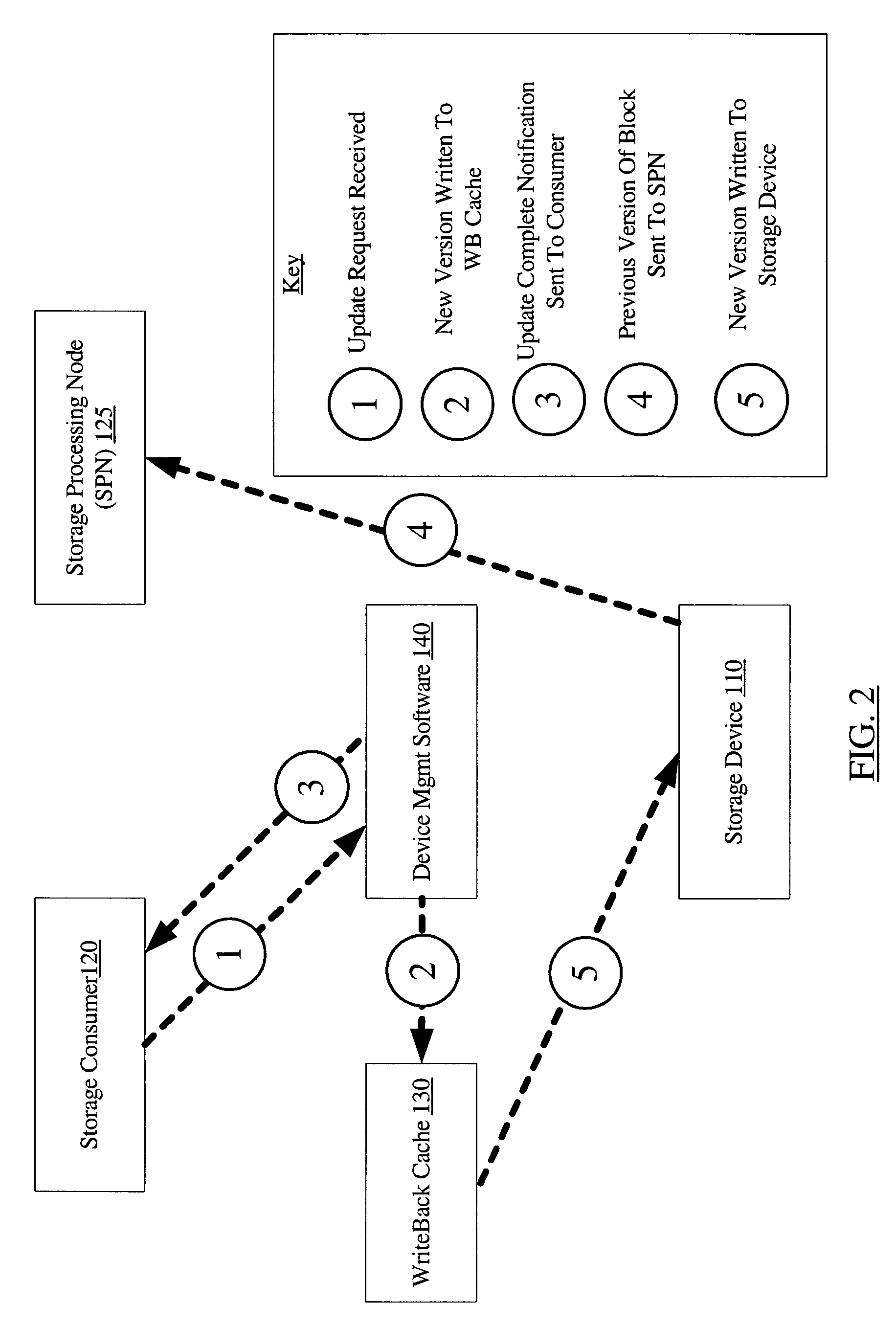
ActiveUS7636814B1Reduce update latencyMemory adressing/allocation/relocationInput/output processes for data processingSoftwareCopy-on-write
A system for asynchronous reads of old data blocks updated through a write-back cache includes a storage device, a write-back cache, a storage consumer, a storage processing node, and device management software. The device management software may be configured to store a new version of a data block in the write-back cache in response to an update request from the first storage consumer and to then send an update completion notification to the first storage consumer. Some time after the update completion notification has been sent, the device management software may be configured to send a previous version of the updated data block to the storage processing node, where it may be required to perform an operation such as a copy-on write operation or a snapshot update.
Owner:SYMANTEC OPERATING CORP
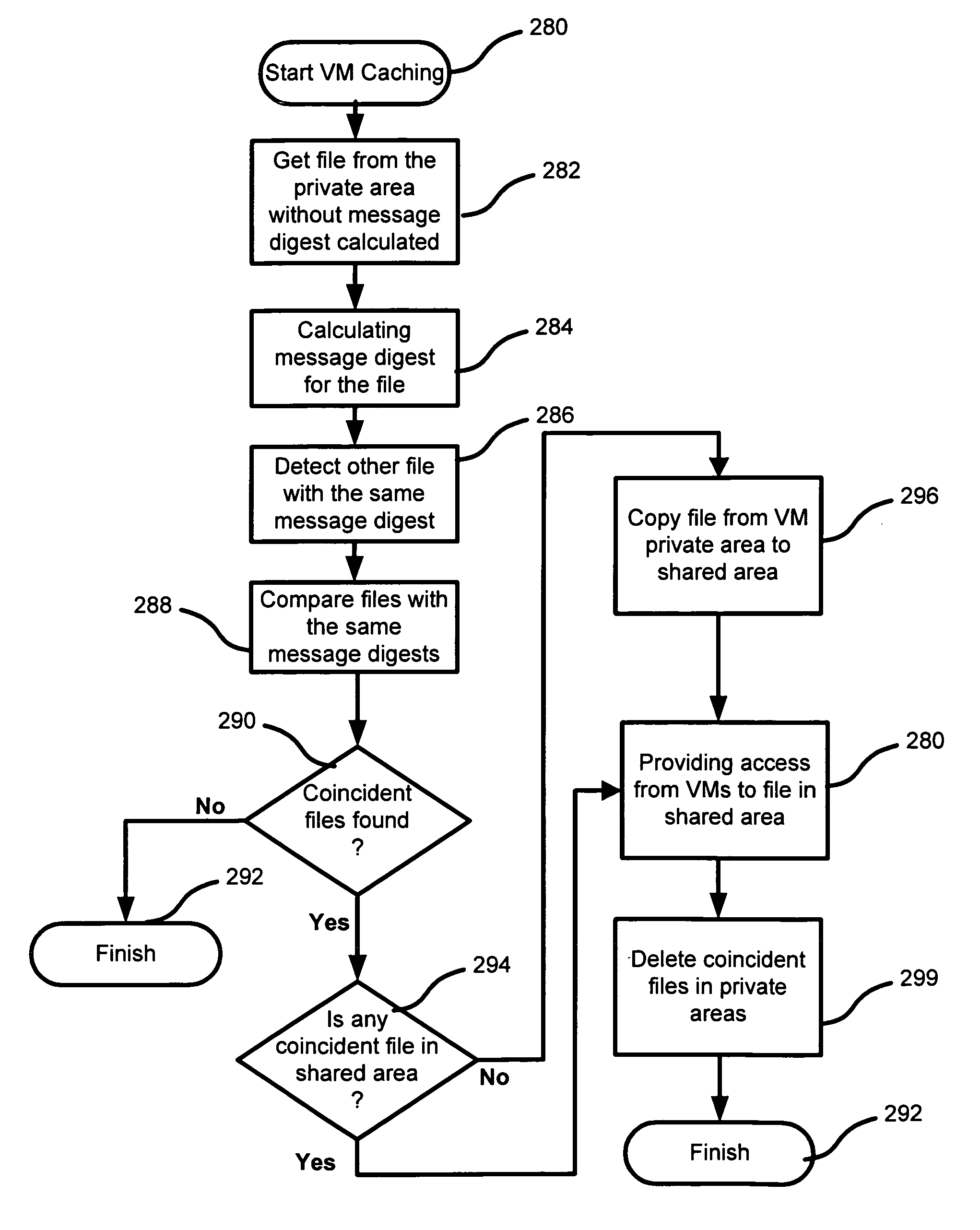
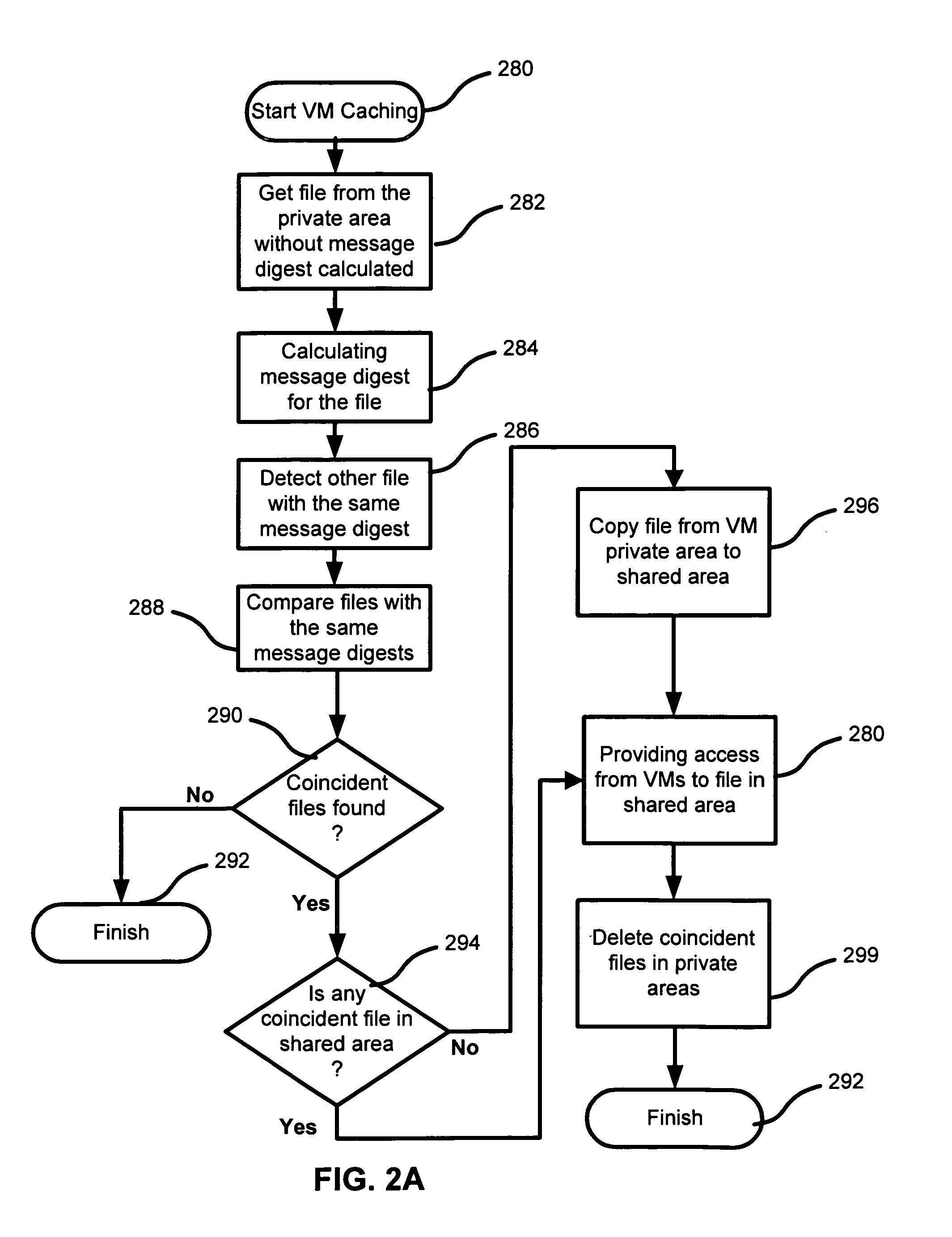
Method to share identical files in a common area for virtual machines having the same operating system version and using a copy on write to place a copy of the shared identical file in a private area of the corresponding virtual machine when a virtual machine attempts to modify the shared identical file
ActiveUS8656386B1Memory adressing/allocation/relocationMultiprogramming arrangementsOperational systemComputer program
A system, method and computer program product for managing files of Virtual Machines, including launching a plurality of Virtual Machines in a computing system having a host OS; using a content of at least one file of the host OS as a shared file; using a re-direct, providing access to the shared file when any Virtual Machine attempts to access its private file; using copy-on-write, making a copy of the shared file if the Virtual Machine attempts to modify the shared file, and placing a copy of the shared file in a private area of the corresponding Virtual Machine.
Owner:PARALLELS HLDG
Selective encryption system and method for I/O operations
InactiveUS7428636B1Unauthorized memory use protectionHardware monitoringComputer hardwareVirtual machine
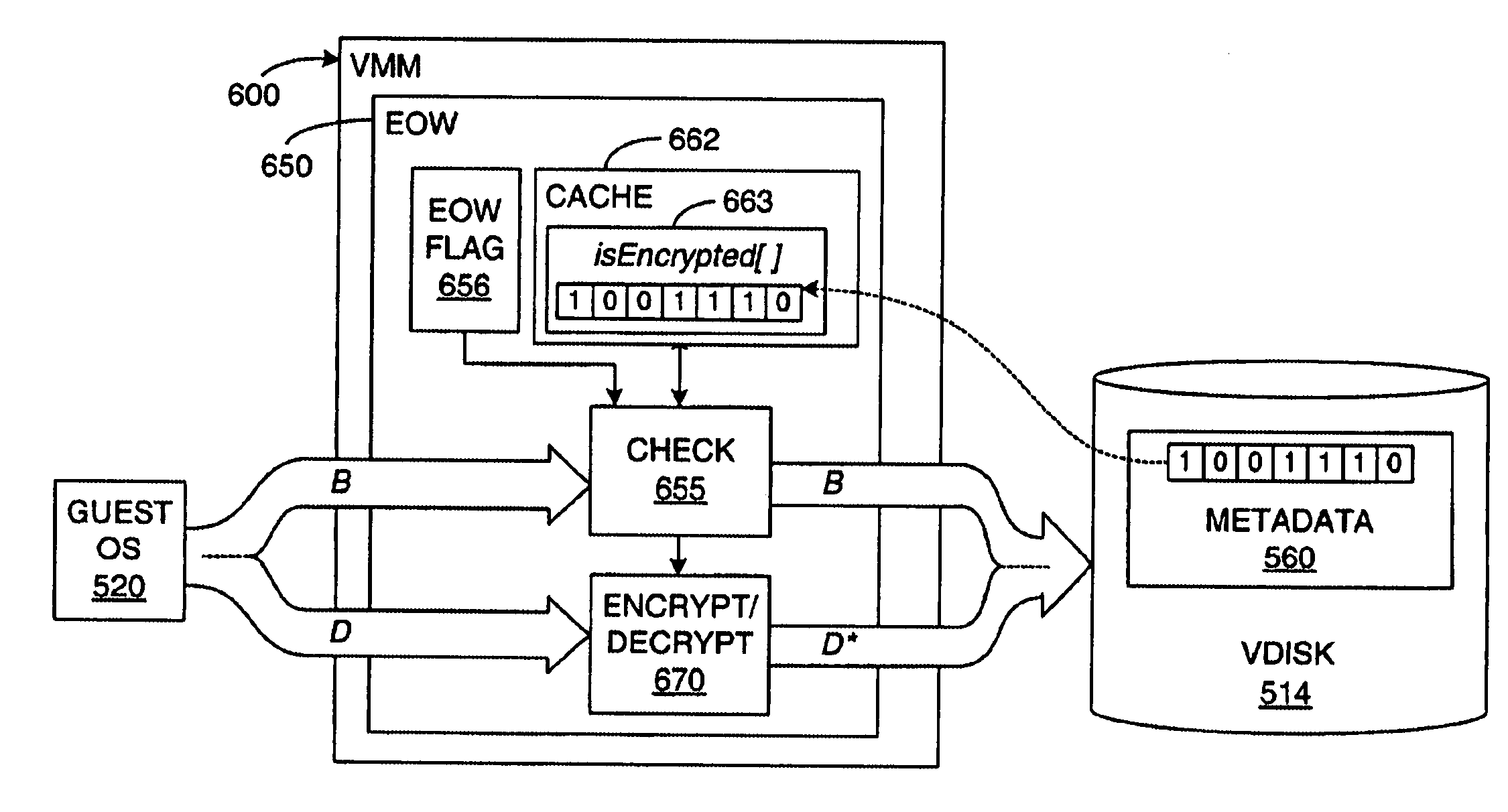
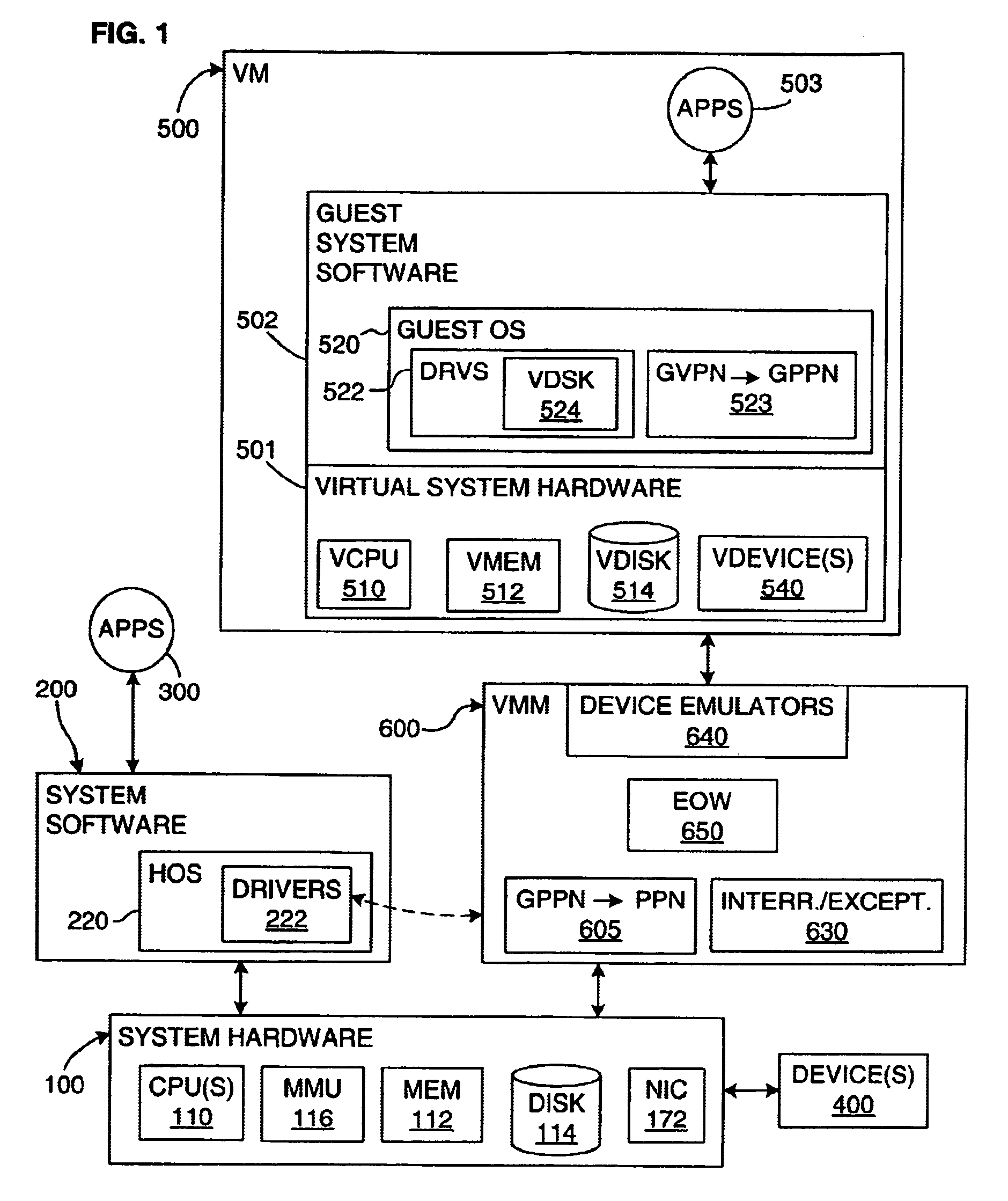
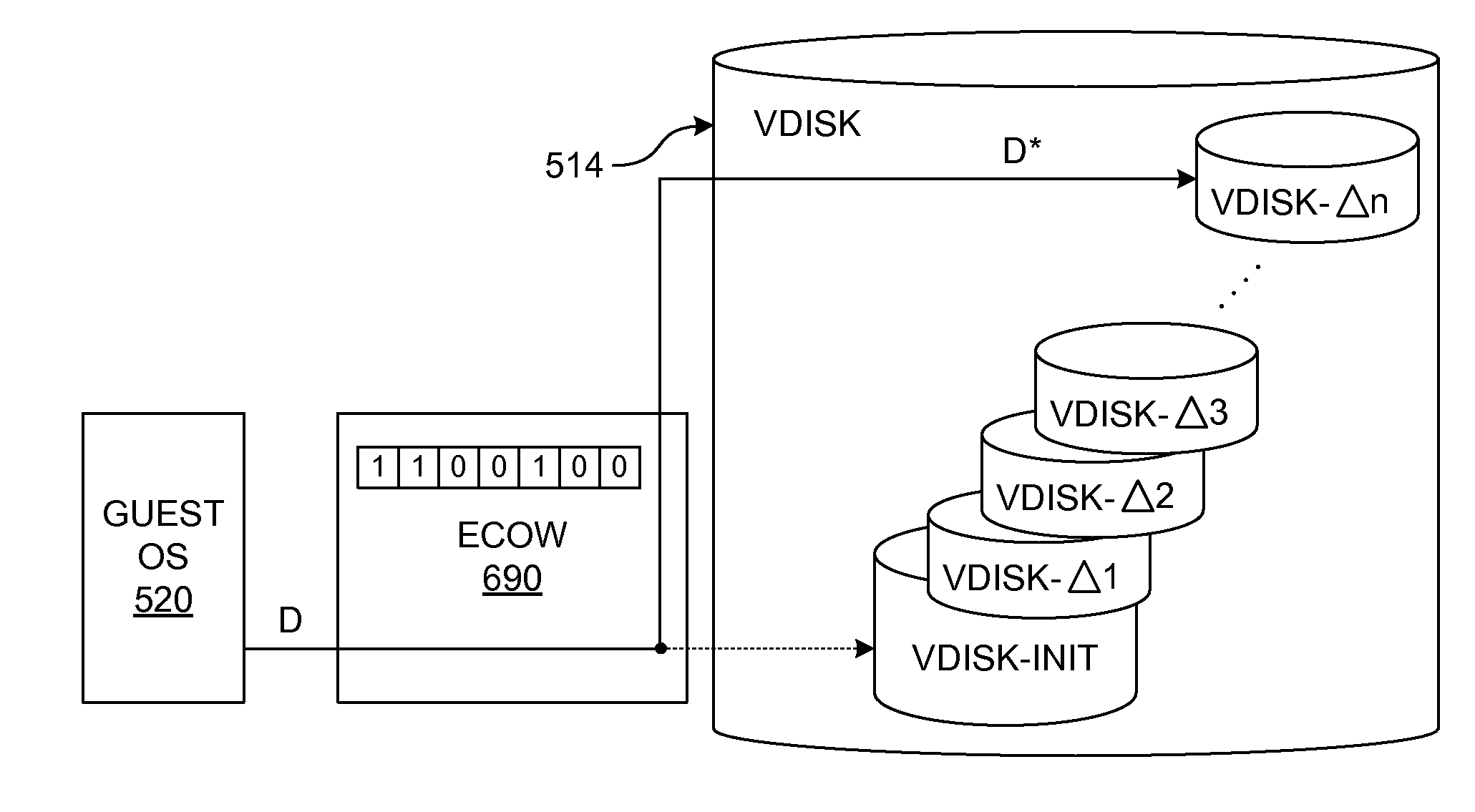
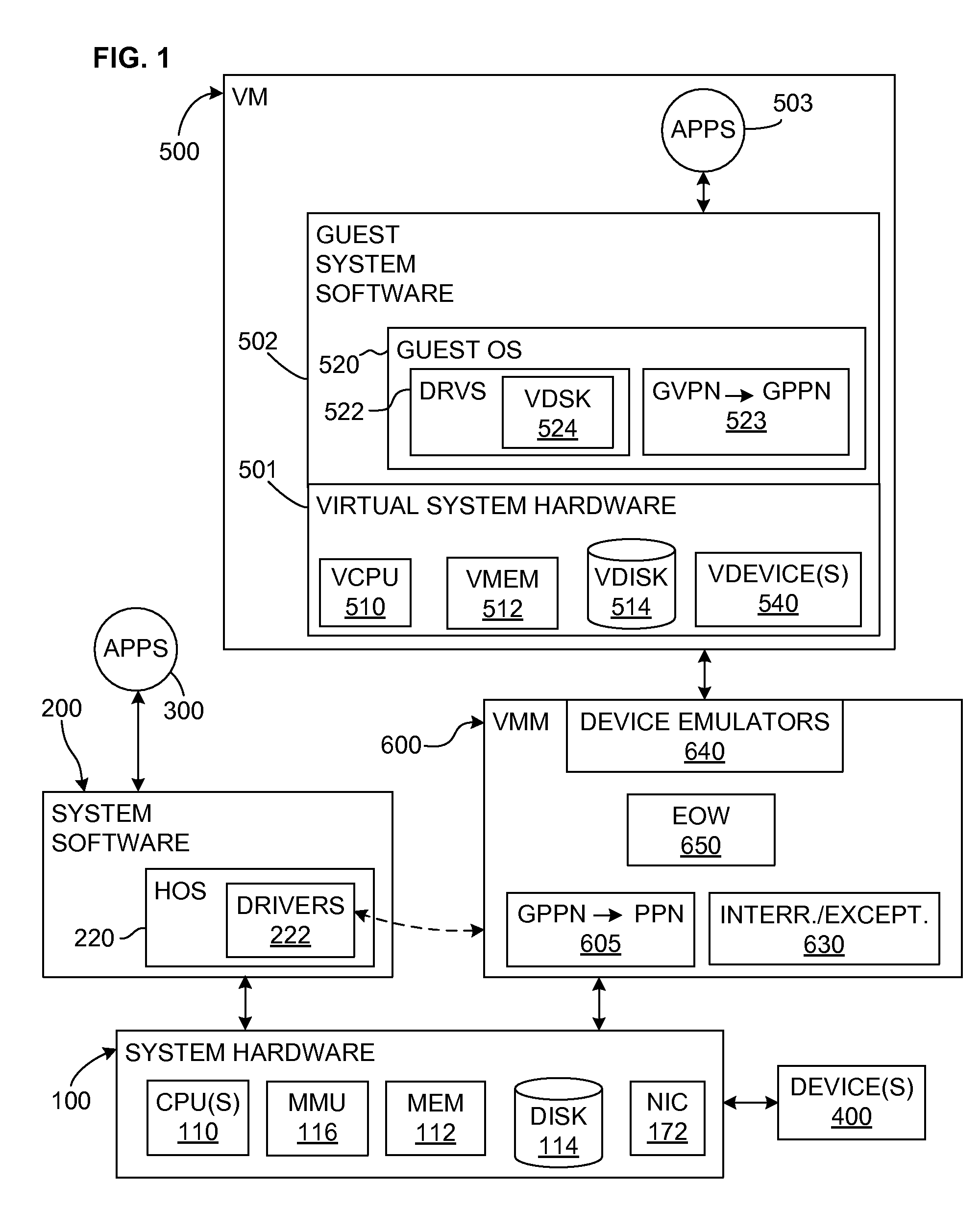
Upon occurrence of a trigger condition, writes of allocation units of data (including code) to a device, such as writes of blocks to a disk, are first encrypted. Each allocation unit is preferably a predetermined integral multiple number of minimum I / O units. A data structure is marked to indicate which units are encrypted. Upon reads from the device, only those allocation units marked as encrypted are decrypted. The disk protected by selective encryption is preferably the virtual disk of a virtual machine (VM). The trigger condition is preferably either that the virtual disk has been initialized or that the VM has been powered on. Mechanisms are also provided for selectively declassifying (storing in unencrypted form) already-encrypted, stored data, and for determining which data units represent public, general-use data units that do not need to be encrypted. The “encrypt-on-write” feature of the invention may be used in conjunction with a “copy-on-write” technique.
Owner:VMWARE INC
On demand virtual machine image streaming
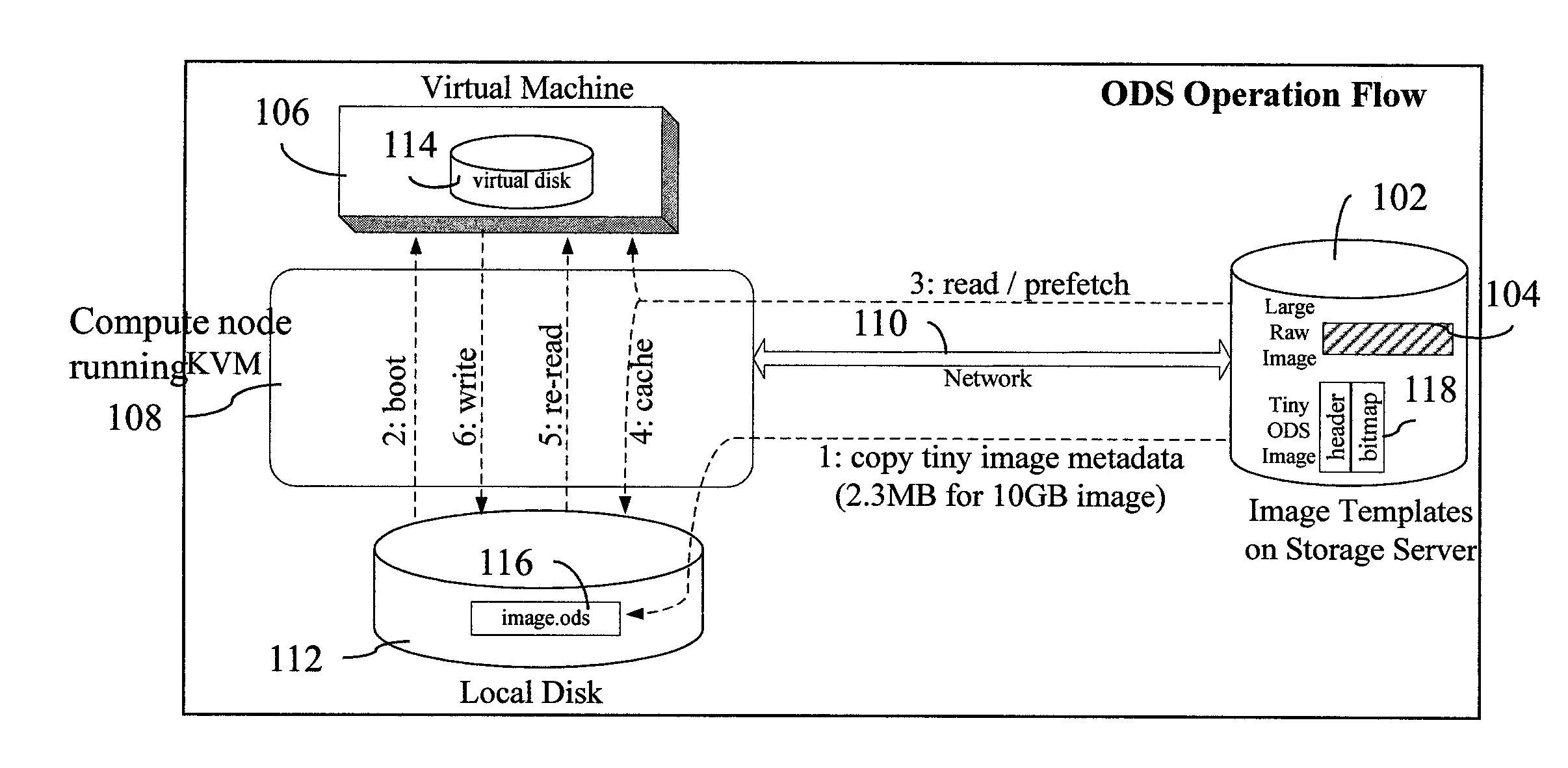
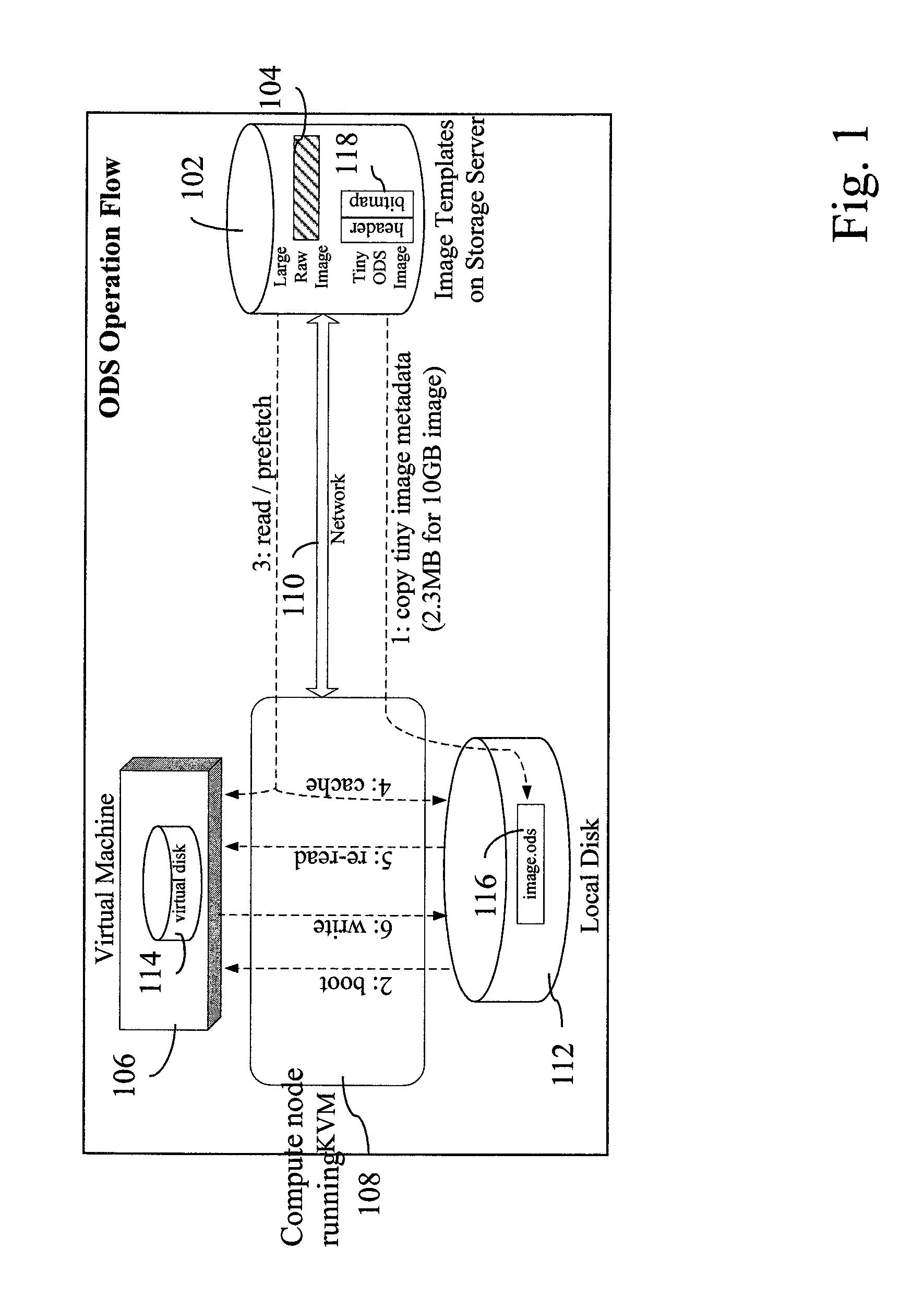
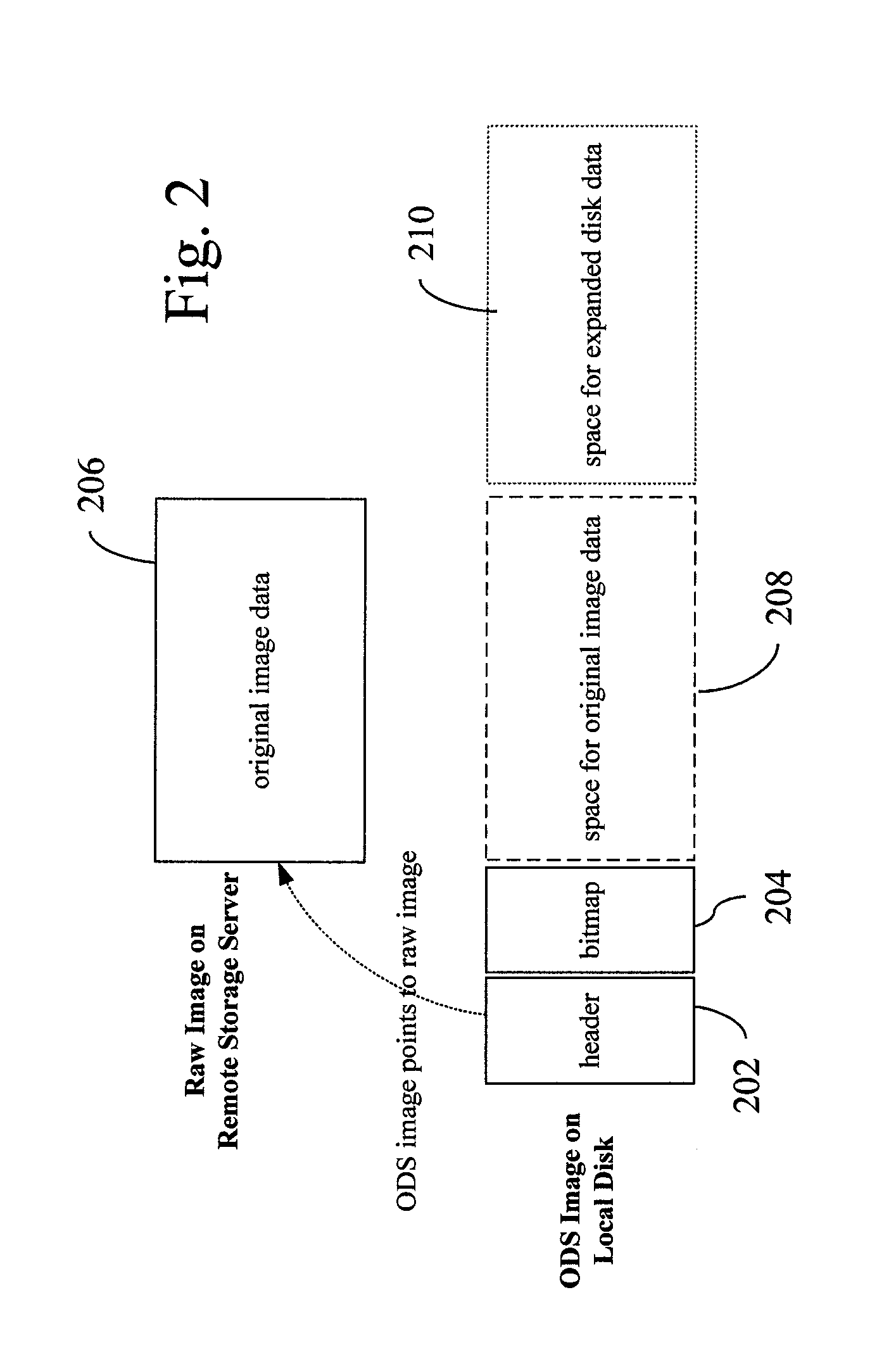
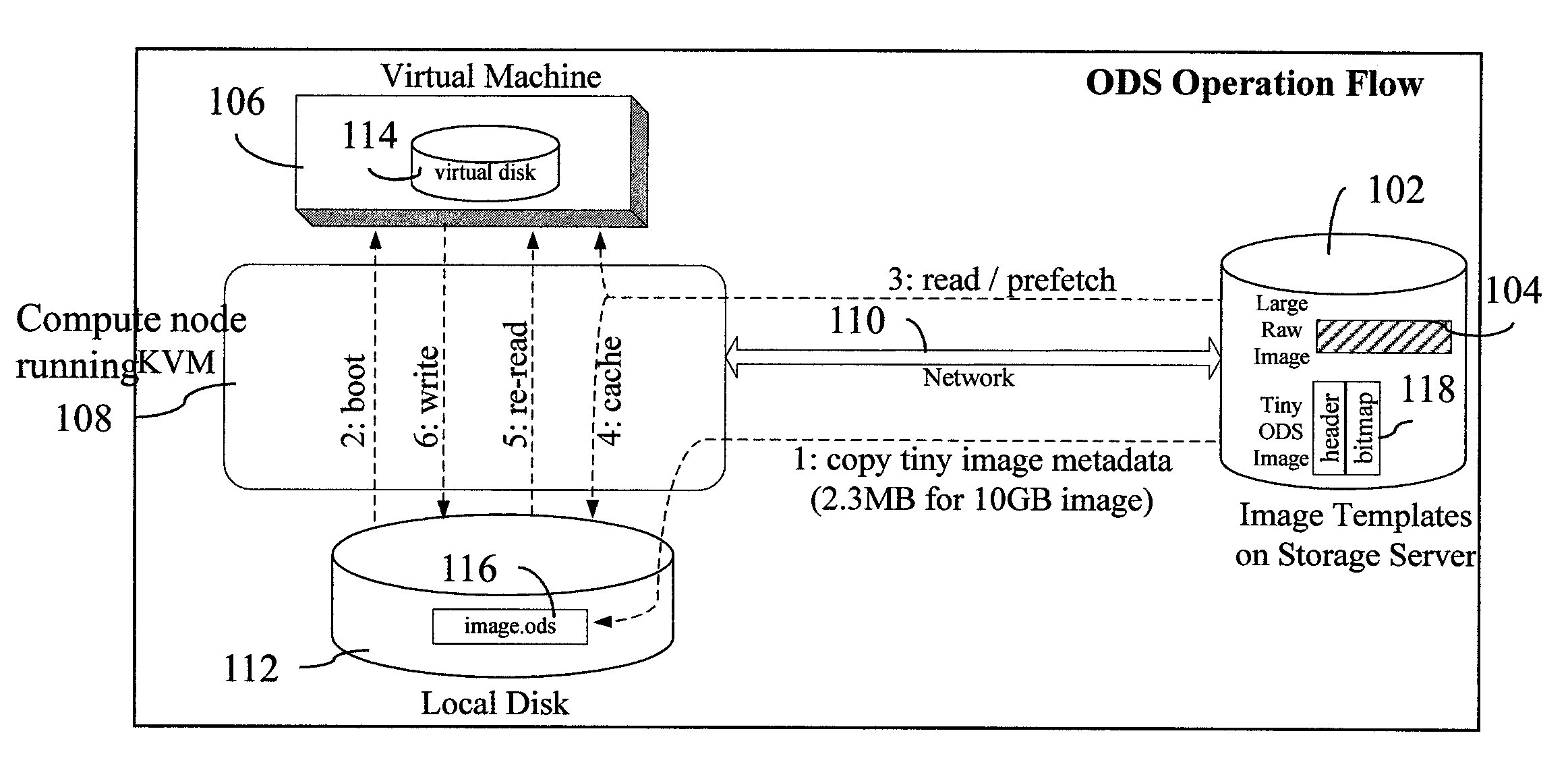
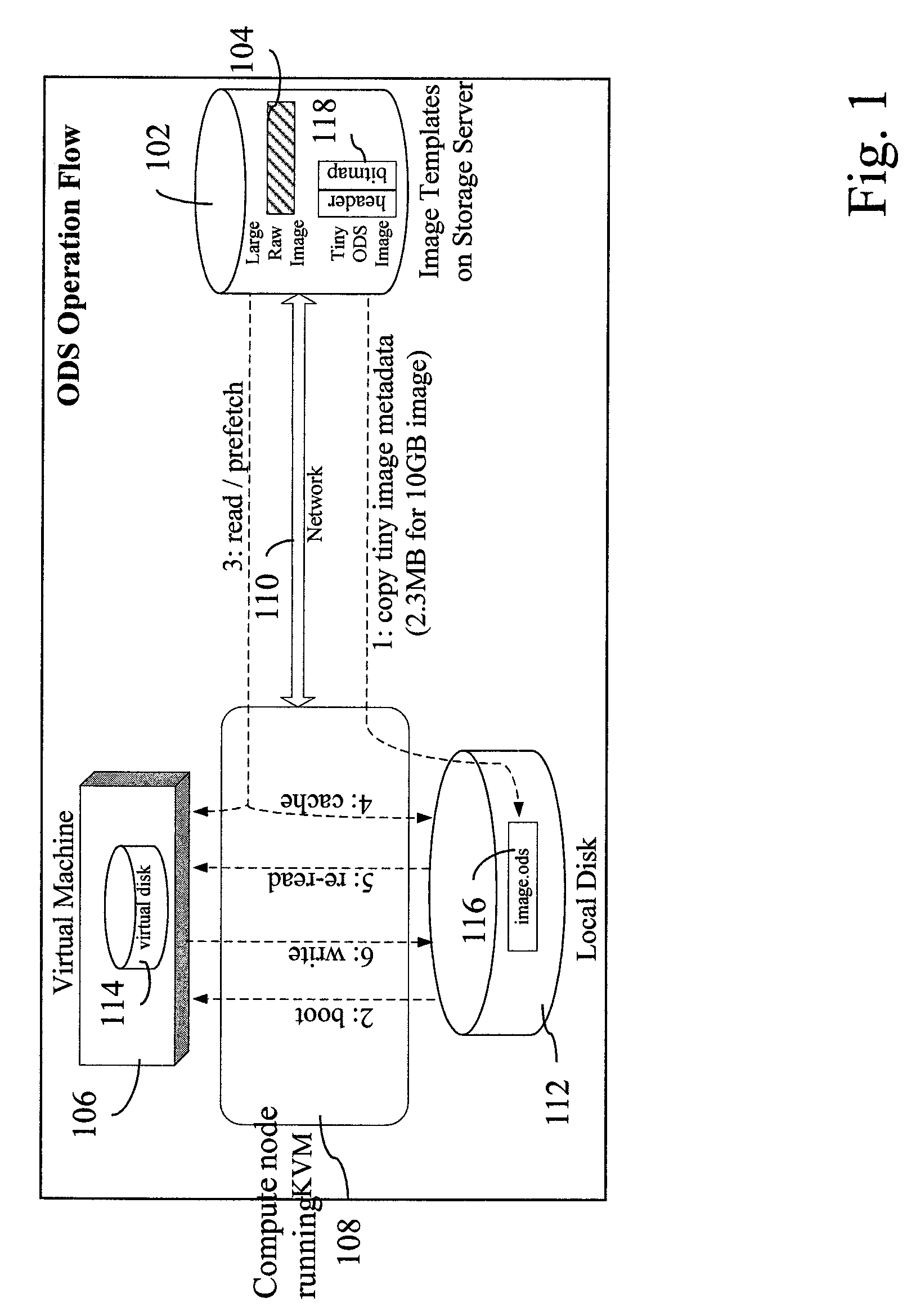
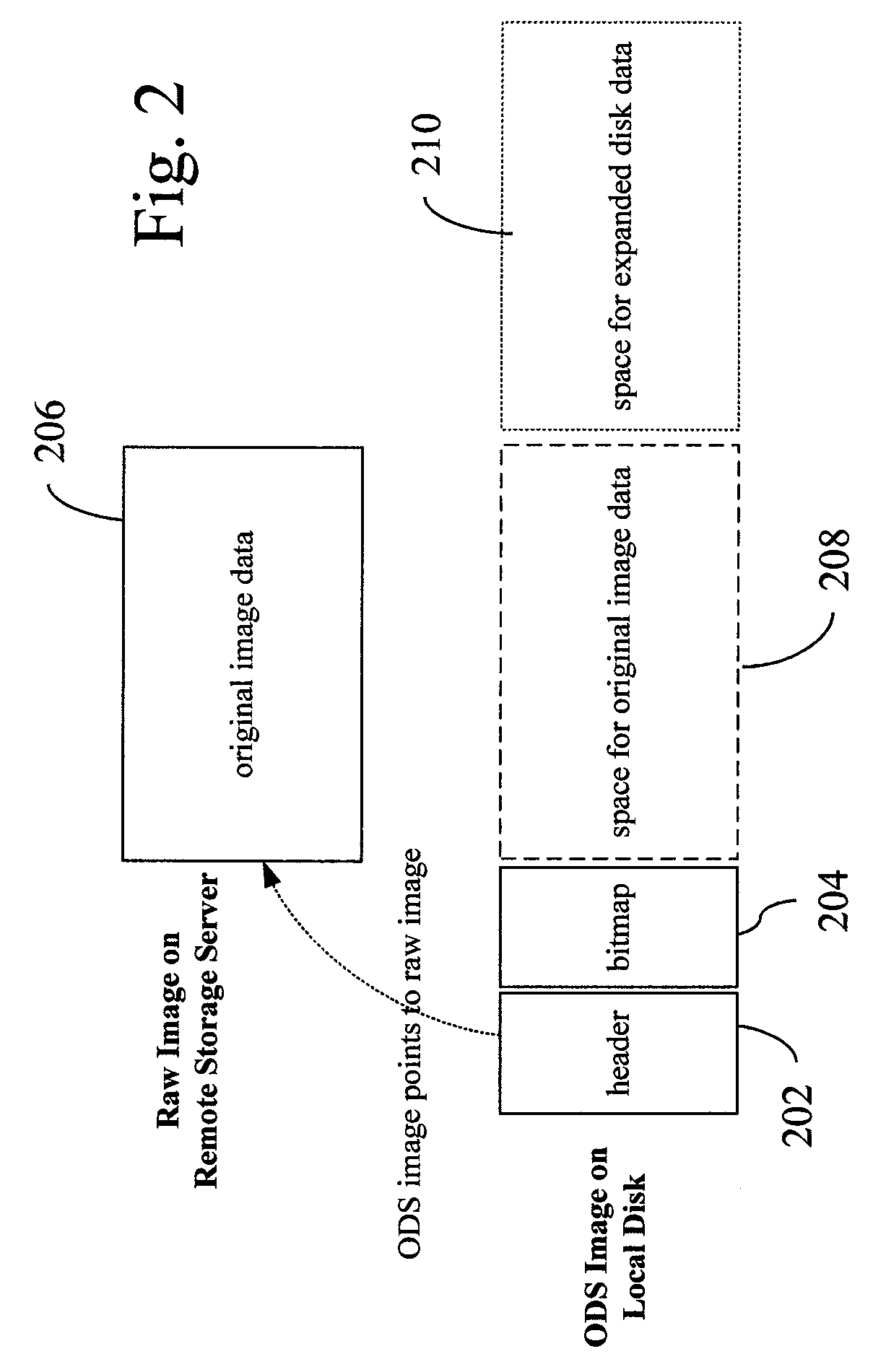
InactiveUS20120066677A1Multiple digital computer combinationsSoftware simulation/interpretation/emulationOn demandVirtual machine
On demand image streaming (ODS), in one aspect, may perform both copy-on-write and copy-on-read to gradually bring data on remote storage server to a host's local disk. Prefetching may be performed during the time the resources are otherwise idle to bring in data from the remote storage server to the host's local disk. A new image format and the corresponding block device driver for a hypervisor or the like may be also provided. ODS' image format may include a header and a bitmap that indicates whether the data sectors are on local disk or remote storage server, and an image content, for instance, stored in raw format.
Owner:IBM CORP
Optimizing defragmentation operations in a differential snapshotter
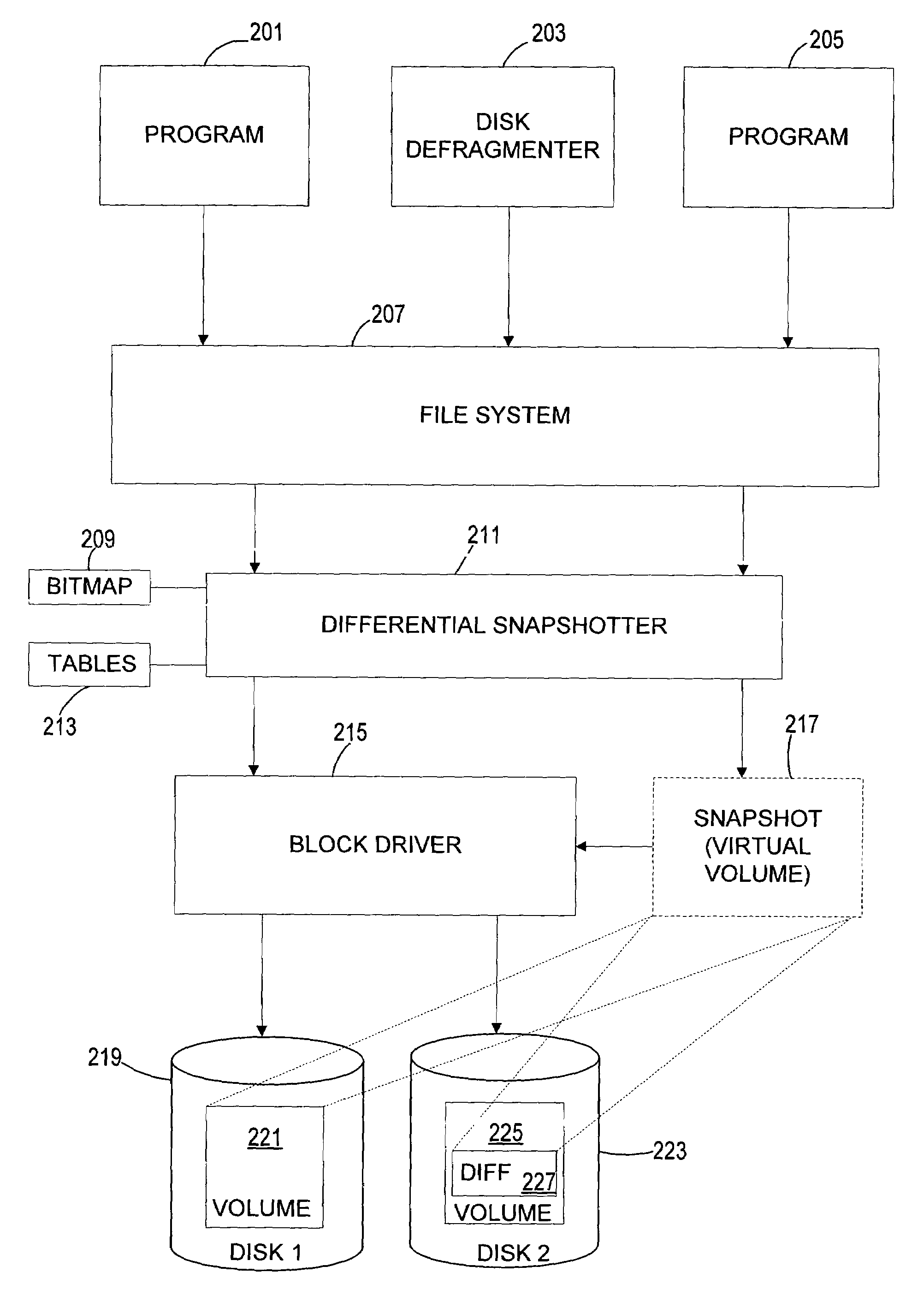
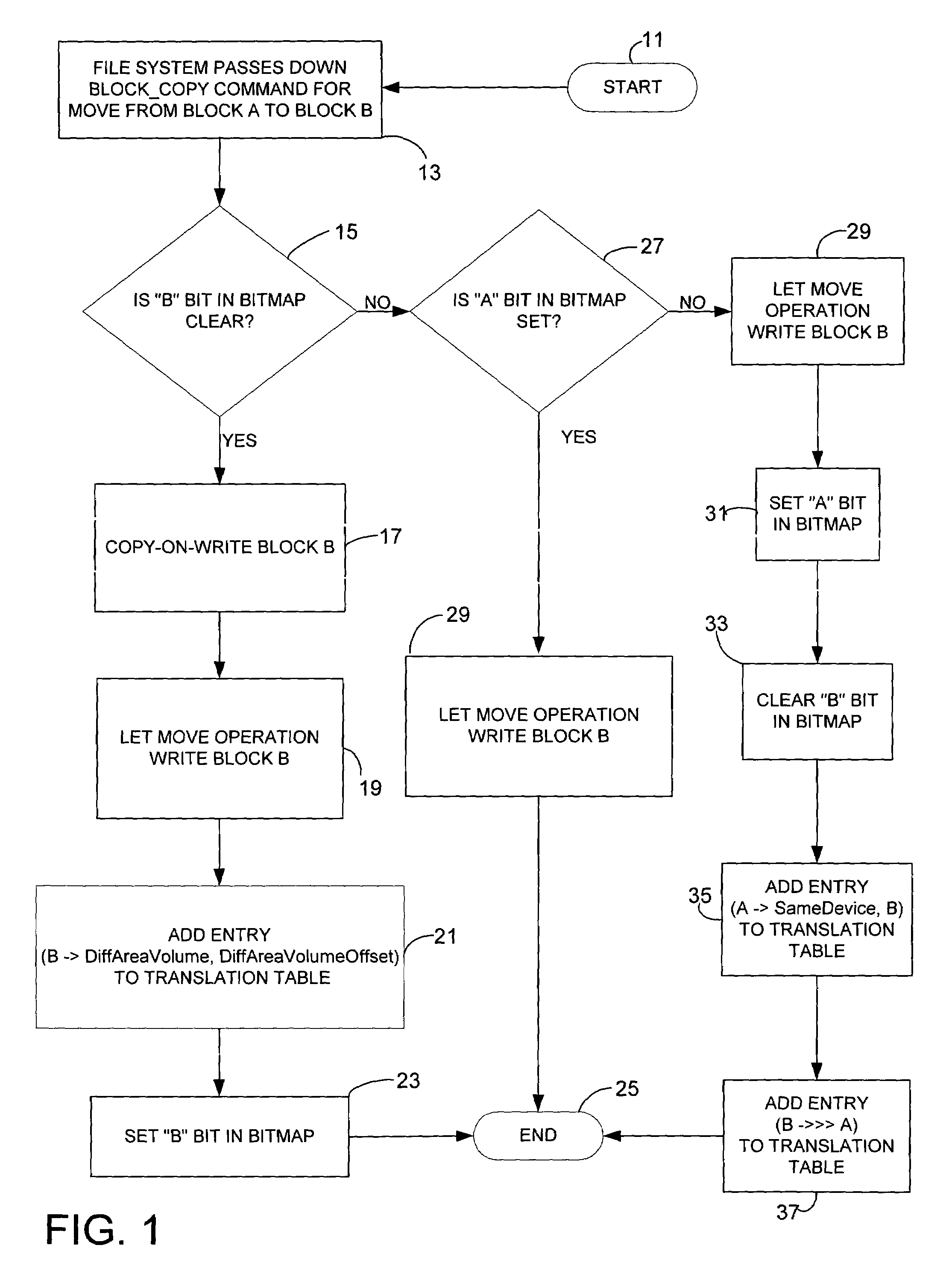
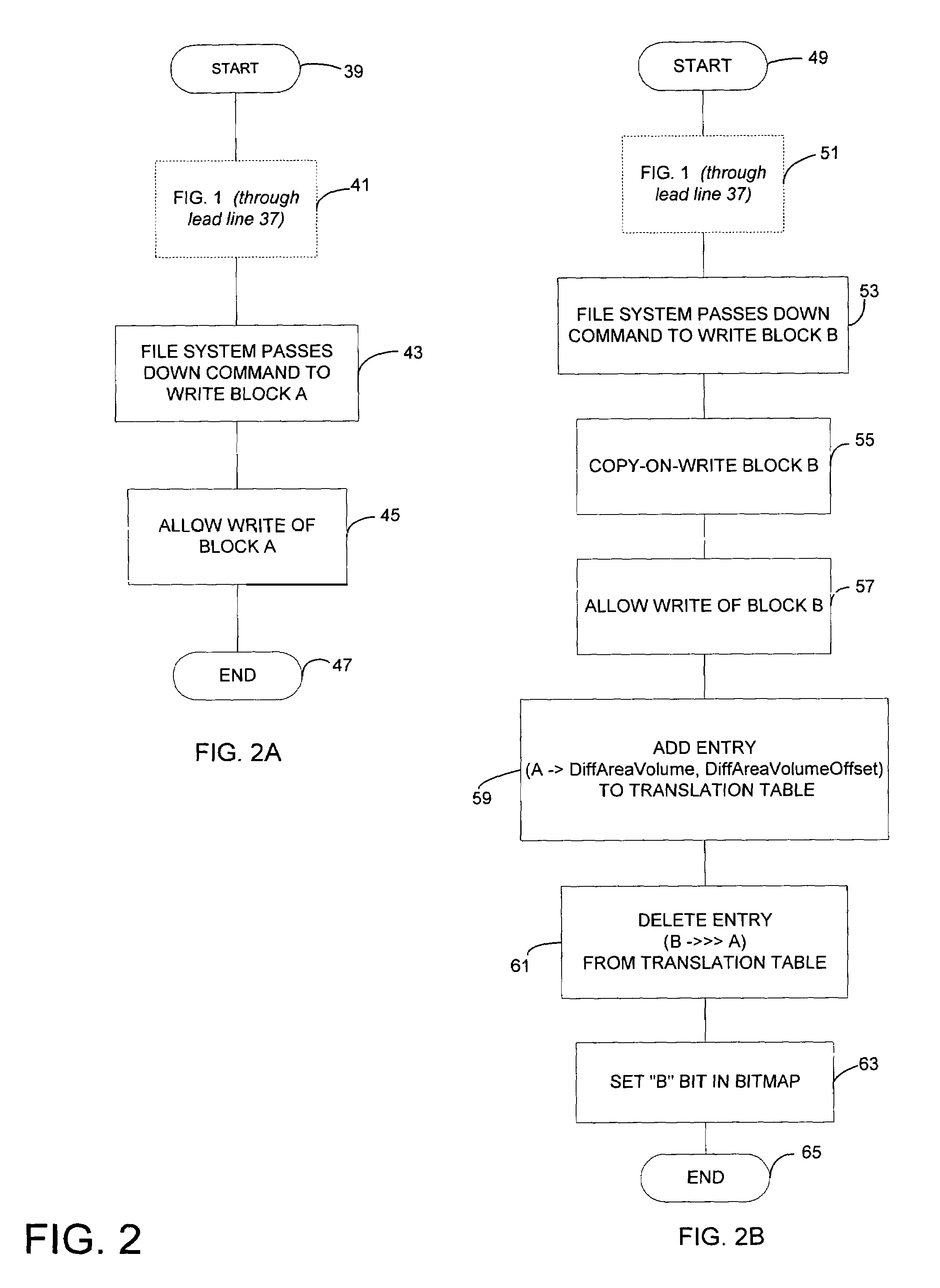
InactiveUS7664771B2Avoid unnecessary copy-on-write operationInput/output to record carriersDigital data processing detailsFile systemTranslation table
A differential snapshot is established and maintained for a set of files stored on a volume. Copy-on-write operations are avoided for logically insignificant moves of blocks, such as the block rearrangements characteristic of defragmentation utilities. A file system passes a block copy command to lower-level drivers that are to inform the snapshotter that a block move operation is not logically meaningful. When the logically insignificant move is of a block whose data forms part of the data captured in the snapshot virtual volume, and when the move is to a block location that is functioning as logical free space, the snapshotter can simply modify its block bitmap and update translation table entries without needing to perform a copy-on-write.
Owner:MICROSOFT TECH LICENSING LLC
On demand virtual machine image streaming
InactiveUS8490088B2Multiple digital computer combinationsSoftware simulation/interpretation/emulationOn demandVirtual machine
Owner:INT BUSINESS MASCH CORP
Coordinated distributed log-based snapshots in a multi-host environment
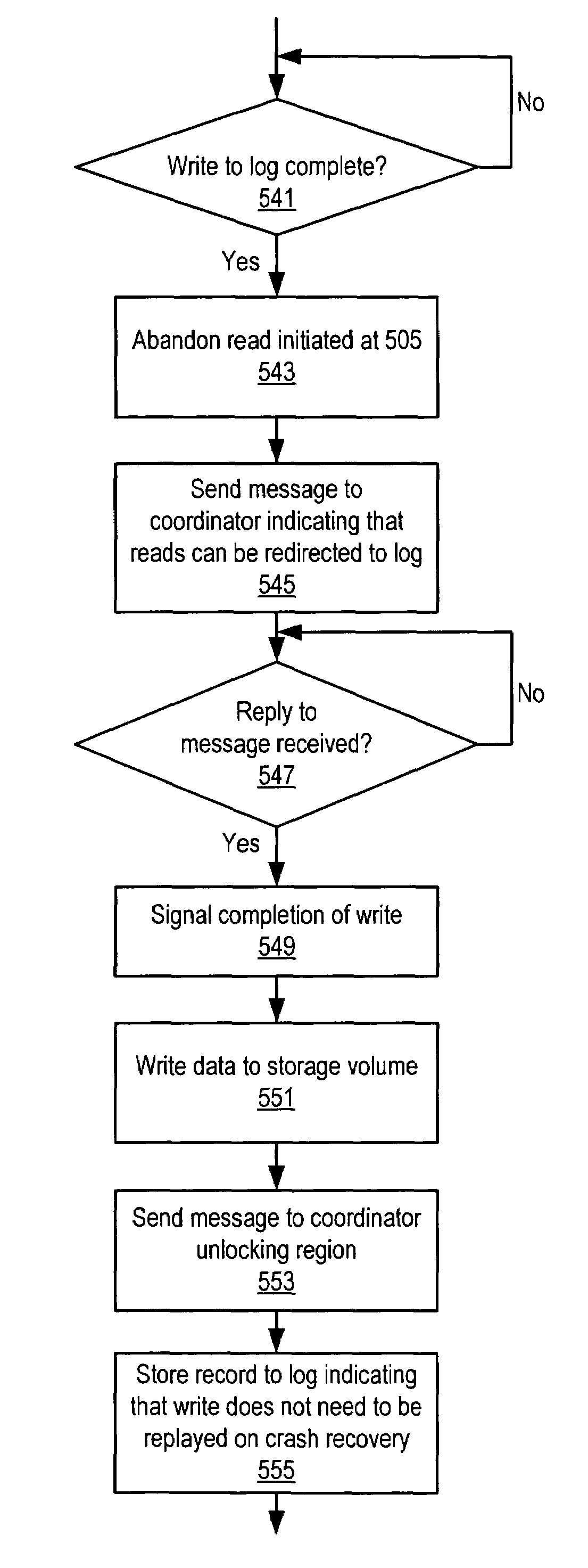
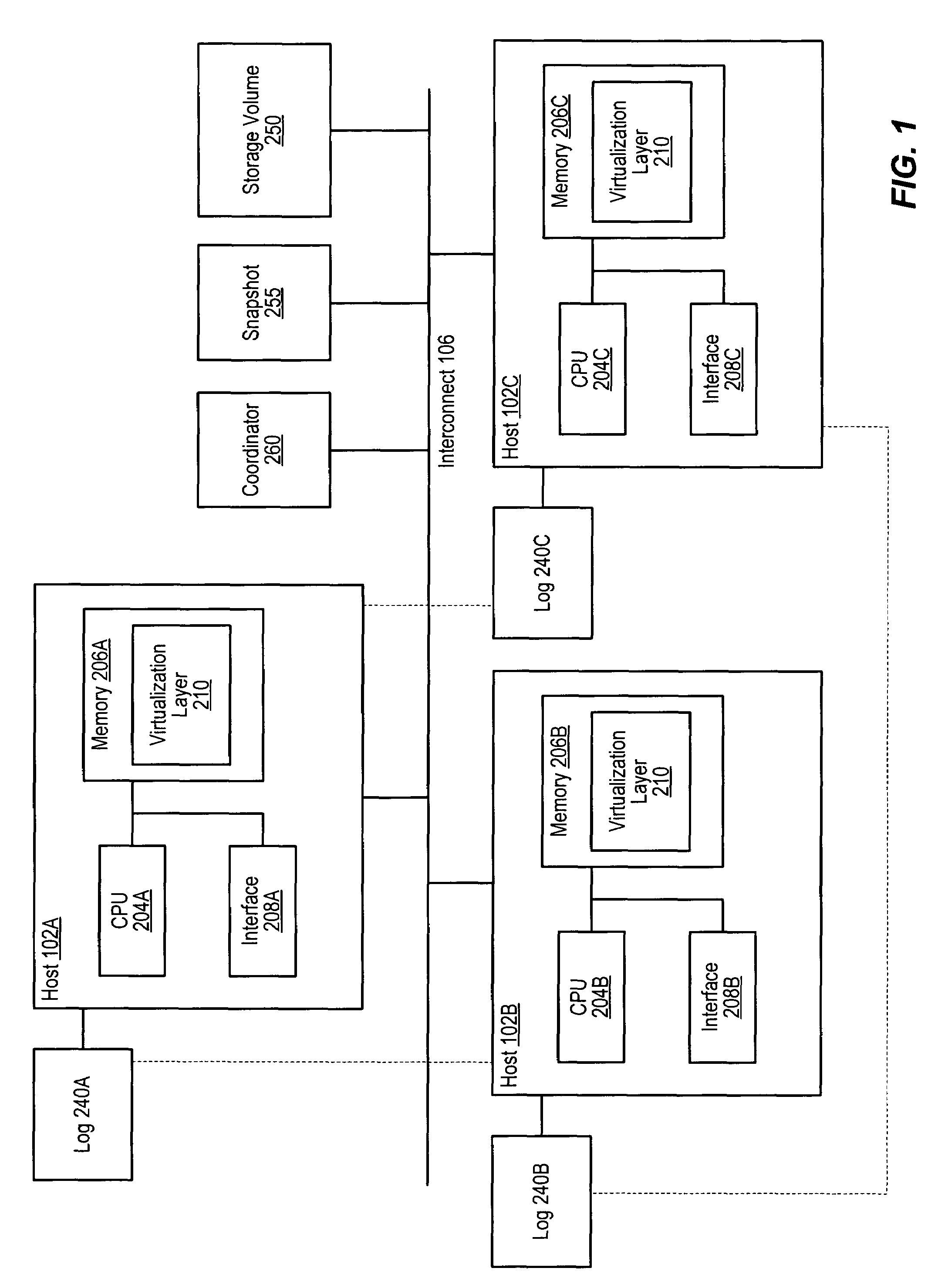
ActiveUS7328226B1Data processing applicationsDigital data processing detailsHosting environmentApplication software
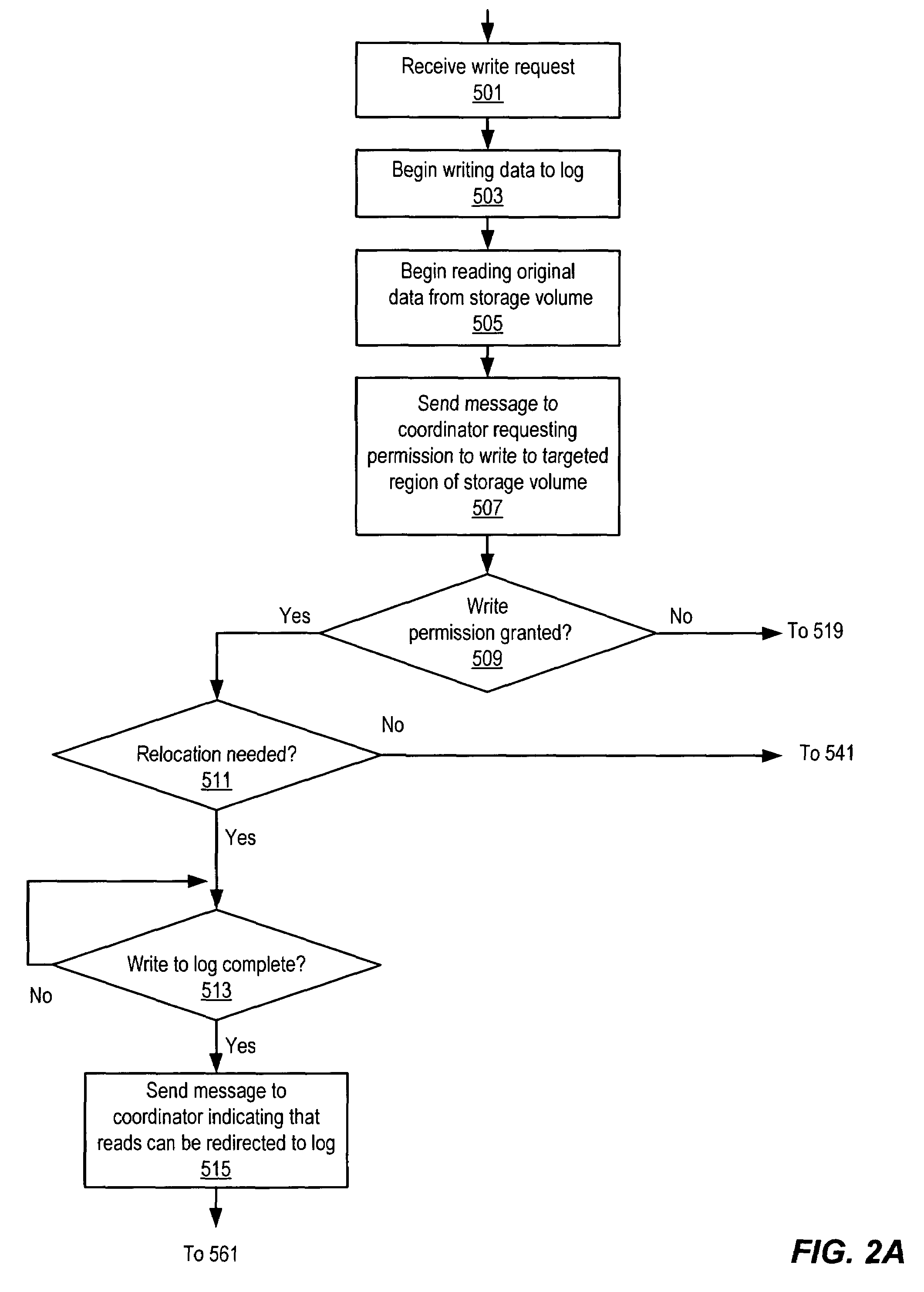
A method for coordinating access to a storage volume between several hosts, each of which has an associated log, may involve: one of the hosts requesting permission from a coordinator to perform a write to a region of the storage volume; the host storing write data for the write to an associated log; and the coordinator sending a response granting permission to perform the write to the host, where the response indicates whether an old version of data in the region of the storage volume should be relocated to a COW (Copy On Write) snapshot volume. The host may signal completion of the write to an application that initiated the write prior to performing the write to the region of the storage volume and subsequent to both storing the write data to the associated log and receiving the response from the coordinator.
Owner:SYMANTEC OPERATING CORP
Systems and methods for portals into snapshot data
ActiveUS20090055604A1Digital data information retrievalError detection/correctionDistributed File SystemFile system
In one embodiment, a user or client device communicates with a distributed file system comprised of one or more physical nodes. The data on each of the physical nodes store metadata about files and directories within the file system. Some of the embodiments permit a user to take a snapshot of data stored on the file system. The snapshot may include a single file, a single directory, a plurality of files within a directory, a plurality of directories, a path on the file system that includes nested files and subdirectories, or more than one path on the file system that each includes nested files and directories. In some embodiments, systems and methods intelligently choose whether to use copy-on-write or point-in-time copy when saving data in a snapshot version of a file whose current version is being overwritten. In some embodiments, systems and methods allow snapshot users to return from a snapshot directory to the immediate parent directory from which the user entered into the snapshot.
Owner:EMC IP HLDG CO LLC
Method and apparatus for monitoring the quantity of differential data in a storage system
Copy-on-write snapshot processing is performed on a storage system in order to produce snapshots of one or more logical volumes in the storage system. The write I / O operations made to the storage system are observed for a certain period of time. Based on the observations an estimate of the size of the storage space required to preserve the snapshot data can be computed. The information can be used to provide sufficient storage space for the snapshot process.
Owner:GOOGLE LLC
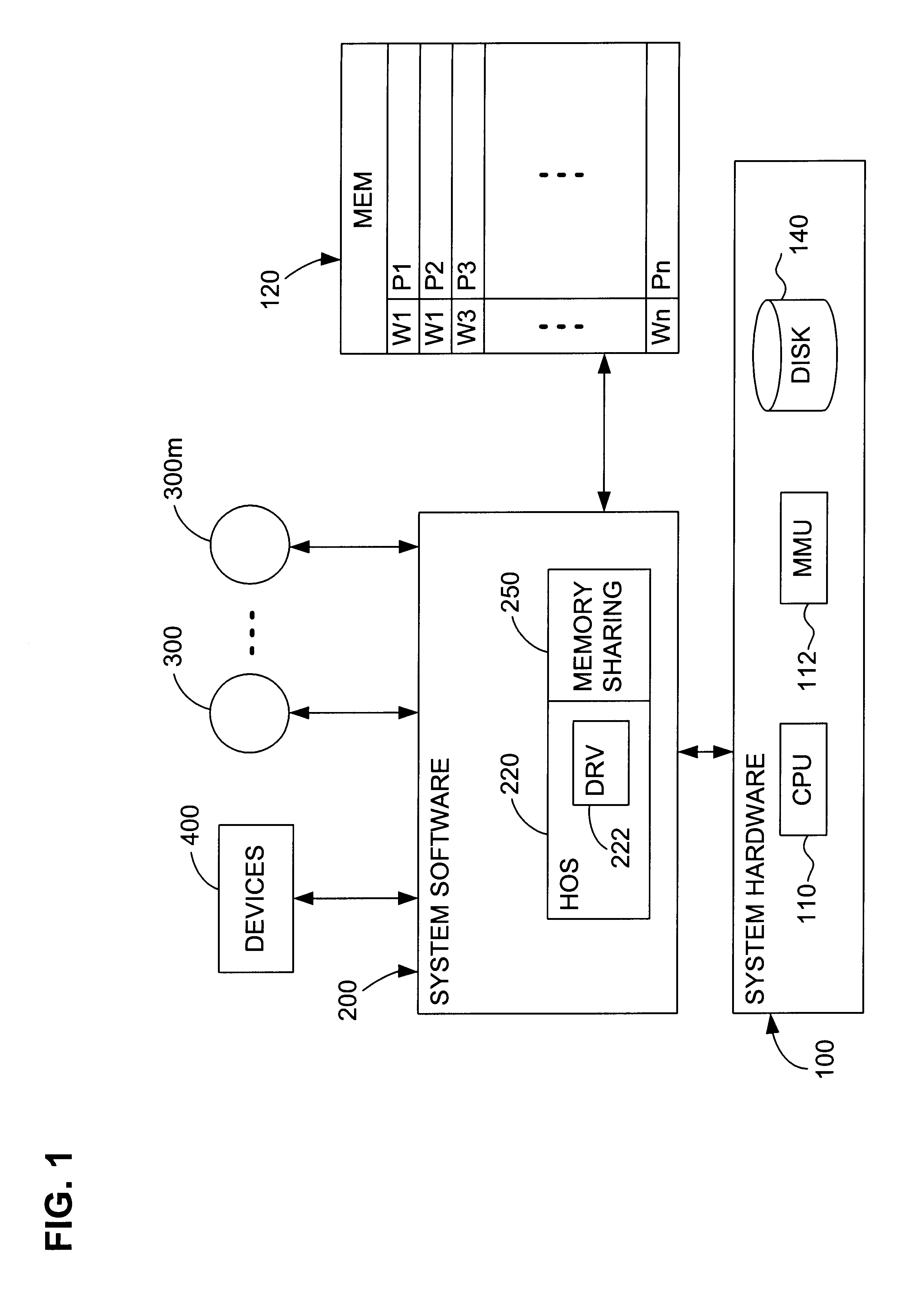
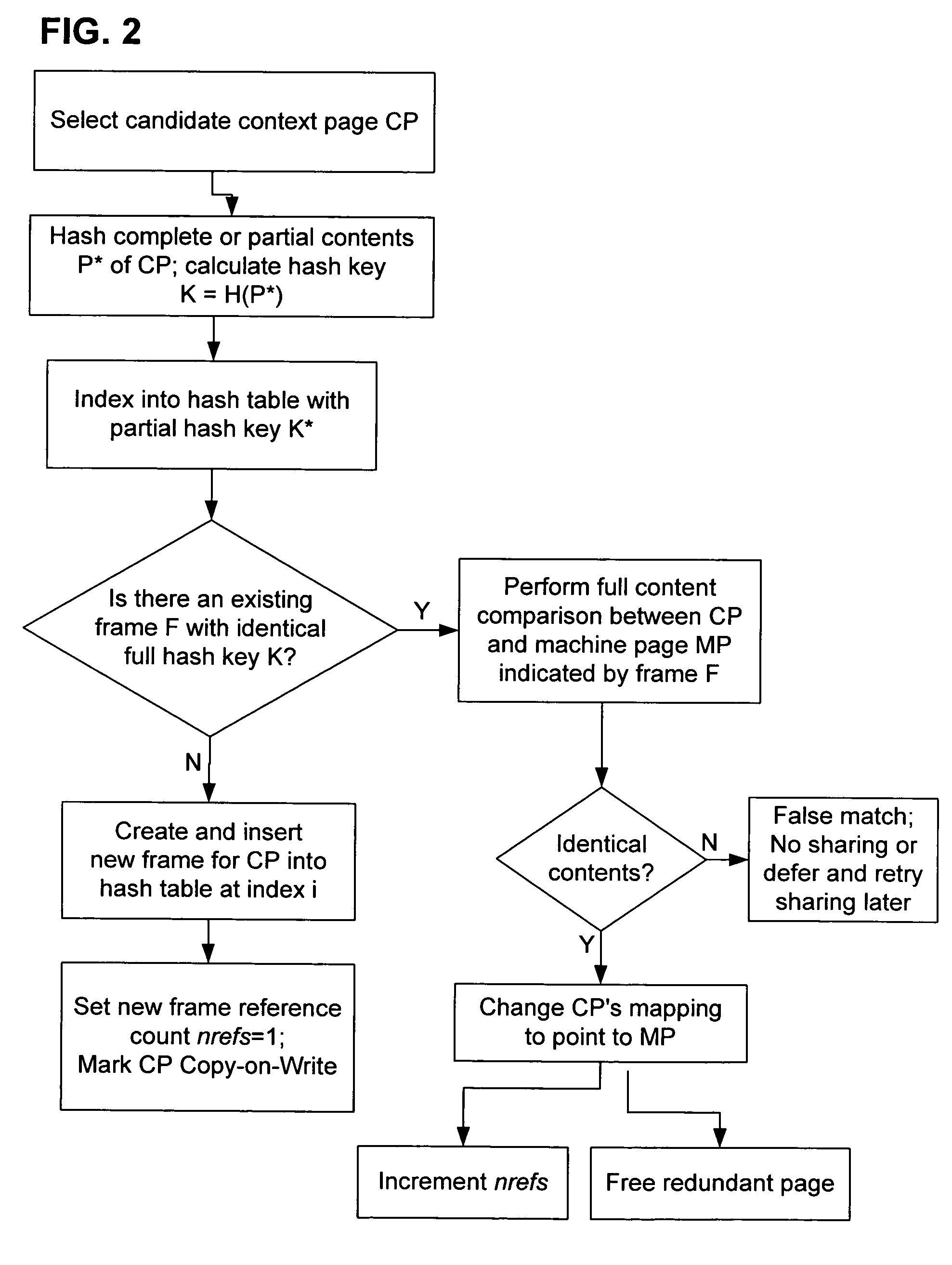
Transparent sharing of memory pages using content comparison
InactiveUS7620766B1Memory architecture accessing/allocationMemory adressing/allocation/relocationMultiple contextVirtual memory
A computer system has one or more software contexts that share use of a memory that is divided into units such as pages. In the preferred embodiment of the invention, the contexts are, or include, virtual machines running on a common hardware platform. The contents, as opposed to merely the addresses or page numbers, of virtual memory pages that are accessible to one or more contexts are examined. If two or more context pages are identical, then their memory mappings are changed to point to a single, shared copy of the page in the hardware memory, thereby freeing the memory space taken up by the redundant copies. The shared copy is then preferably marked copy-on-write. Sharing is preferably dynamic, whereby the presence of redundant copies of pages is preferably determined by hashing page contents and performing full content comparisons only when two or more pages hash to the same key.
Owner:VMWARE INC
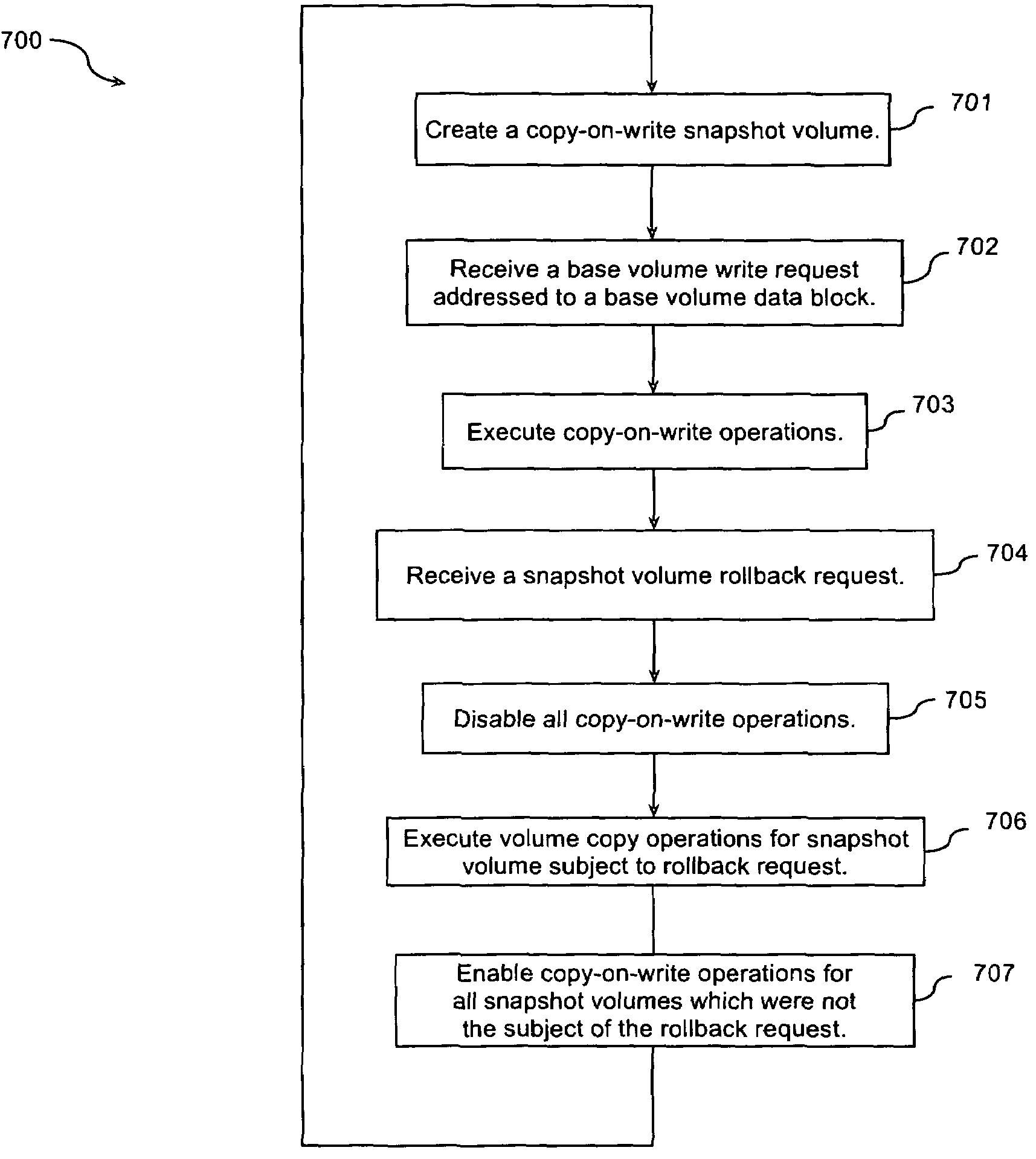
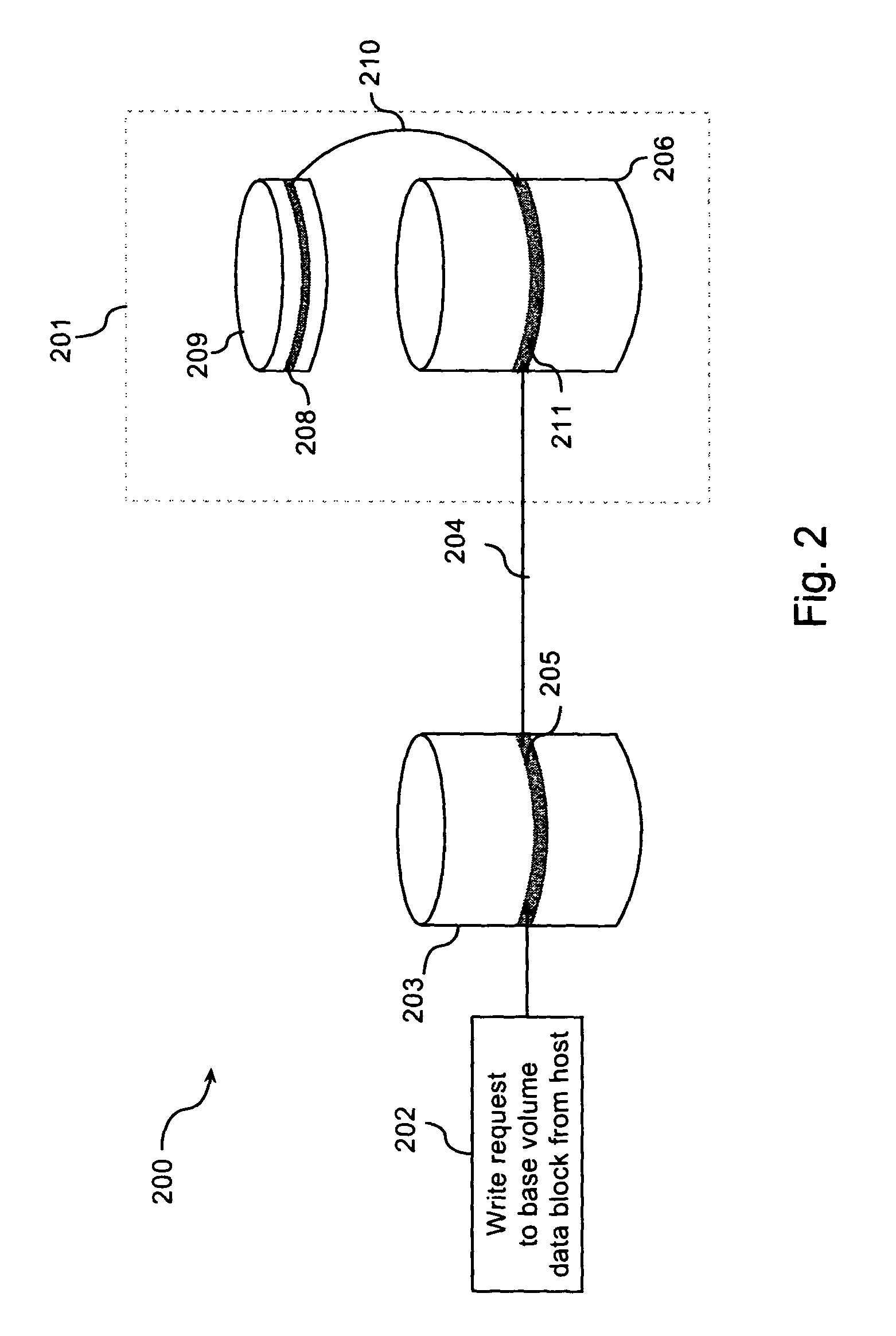
Optimized rollback of copy-on-write snapshot volumes
The present invention is an optimized method for the rollback of copy-on-write snapshot volumes. A method in accordance with the present invention may comprise the following steps: (a) creating a copy-on-write snapshot volume; (b) receiving a base volume write request addressed to a base volume data block; (c) executing copy-on-write operations; (d) receiving a snapshot volume rollback request; (e) disabling the copy-on-write operations; and (f) executing volume copy operations.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
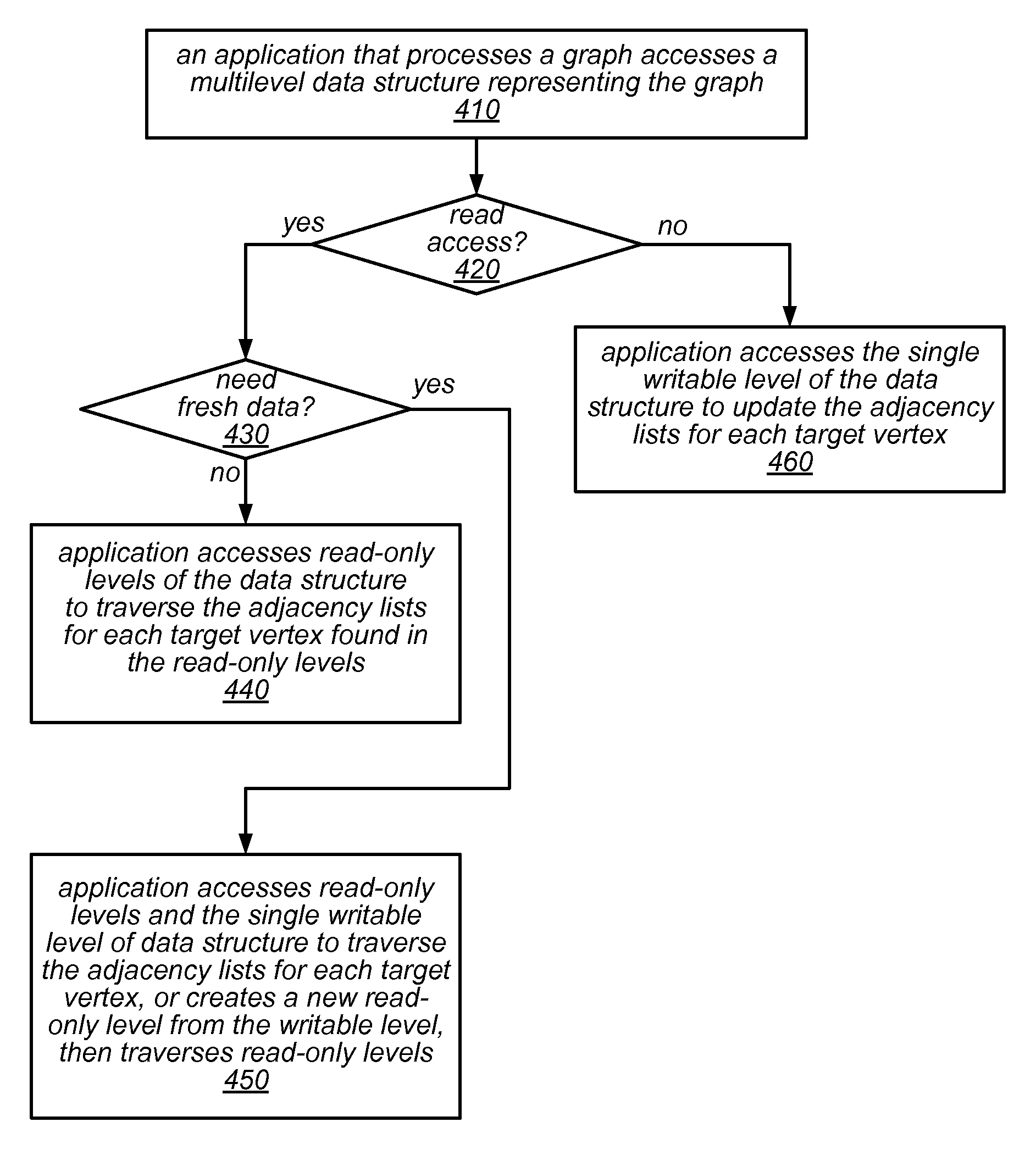
Graph Processing Using a Mutable Multilevel Graph Representation
ActiveUS20160071233A1Improve performanceIncrease spacingDrawing from basic elementsImage memory managementTheoretical computer scienceAdjacency list
A mutable multilevel data structure representing a graph structure may include multiple read-only levels and a single writable level. Each read-only level may include a vertex table (which includes references to edge tables on the same level or a different level containing elements of adjacency lists for some vertices) and an edge table (which includes elements of adjacency lists that changed since the previous read-only level). A hybrid variant may switch between a performance-optimized variant (whose edge tables include complete adjacency lists for vertices whose edge sets were modified) and a space-optimized variant (whose edge tables include only newly added adjacency list elements). The vertex tables and / or the writable level may be implemented using copy-on-write arrays, each including an indirection table and multiple fixed-sized data pages. Computations may be run on the read-only levels or on the writable level and read-only levels.
Owner:ORACLE INT CORP
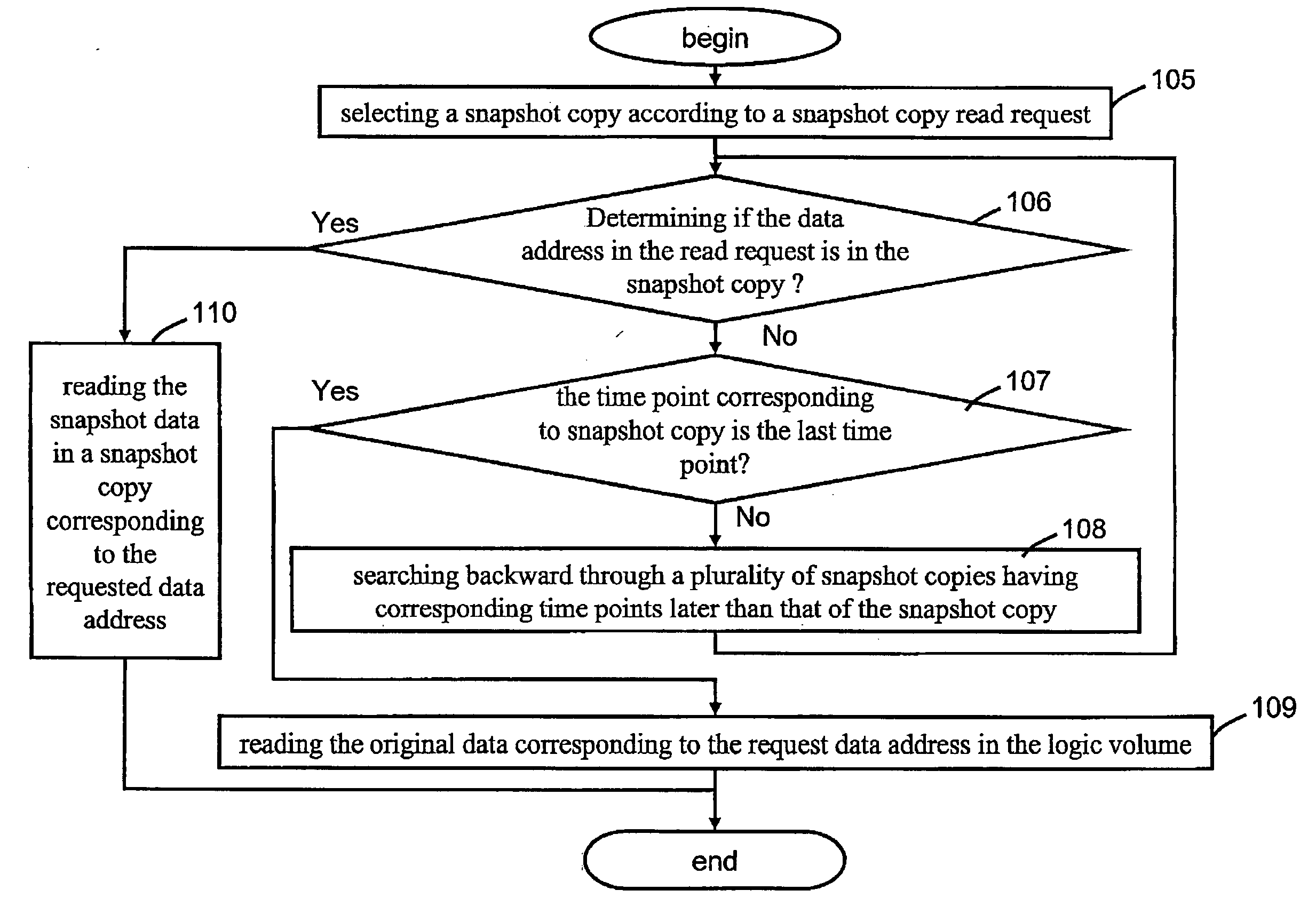
Snapshot copy management method used for logic volume manager
InactiveUS20070288711A1High speed copy functionSave storage spaceDigital data information retrievalMemory loss protectionOperating systemCopy-on-write
Owner:INVENTEC CORP
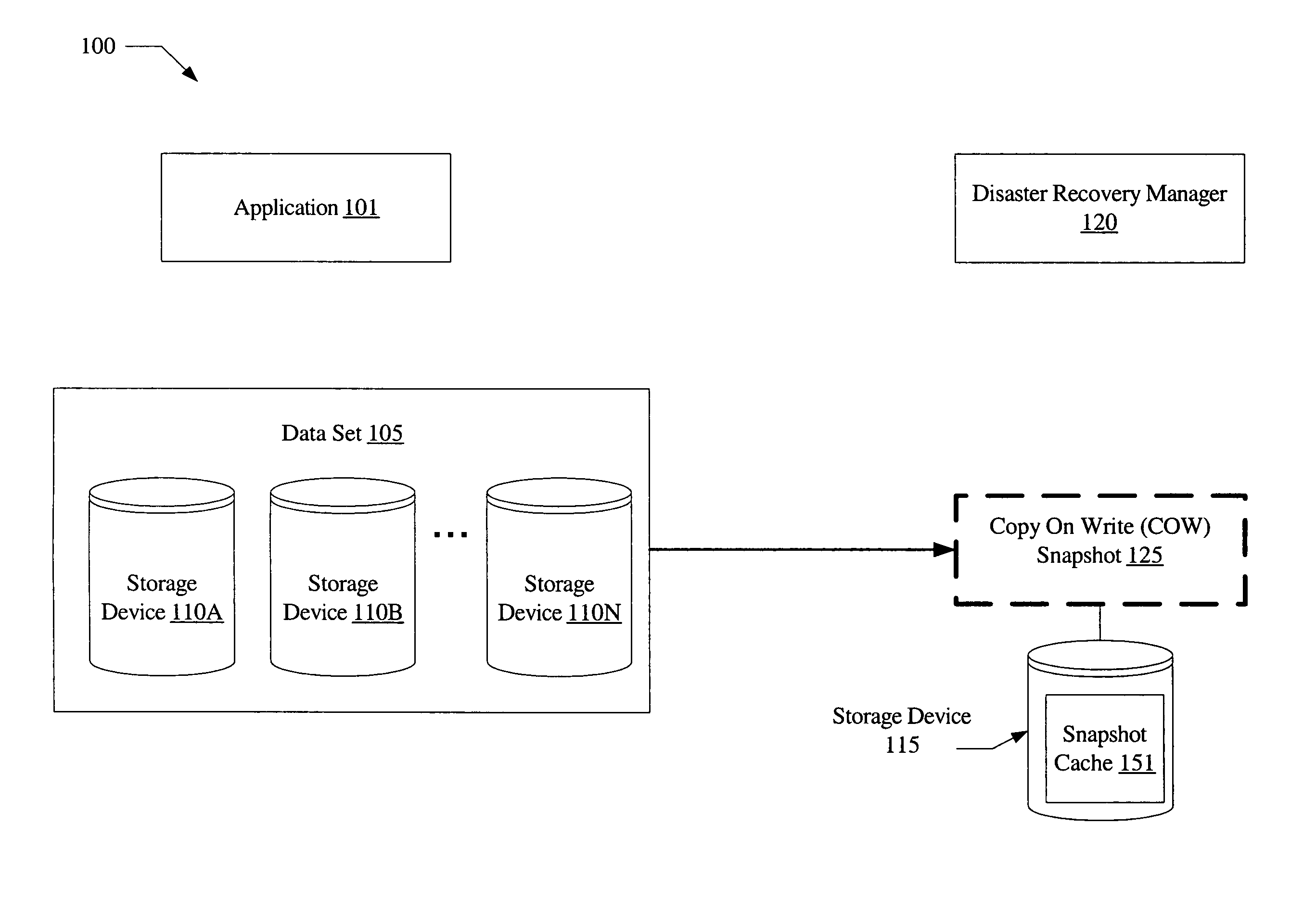
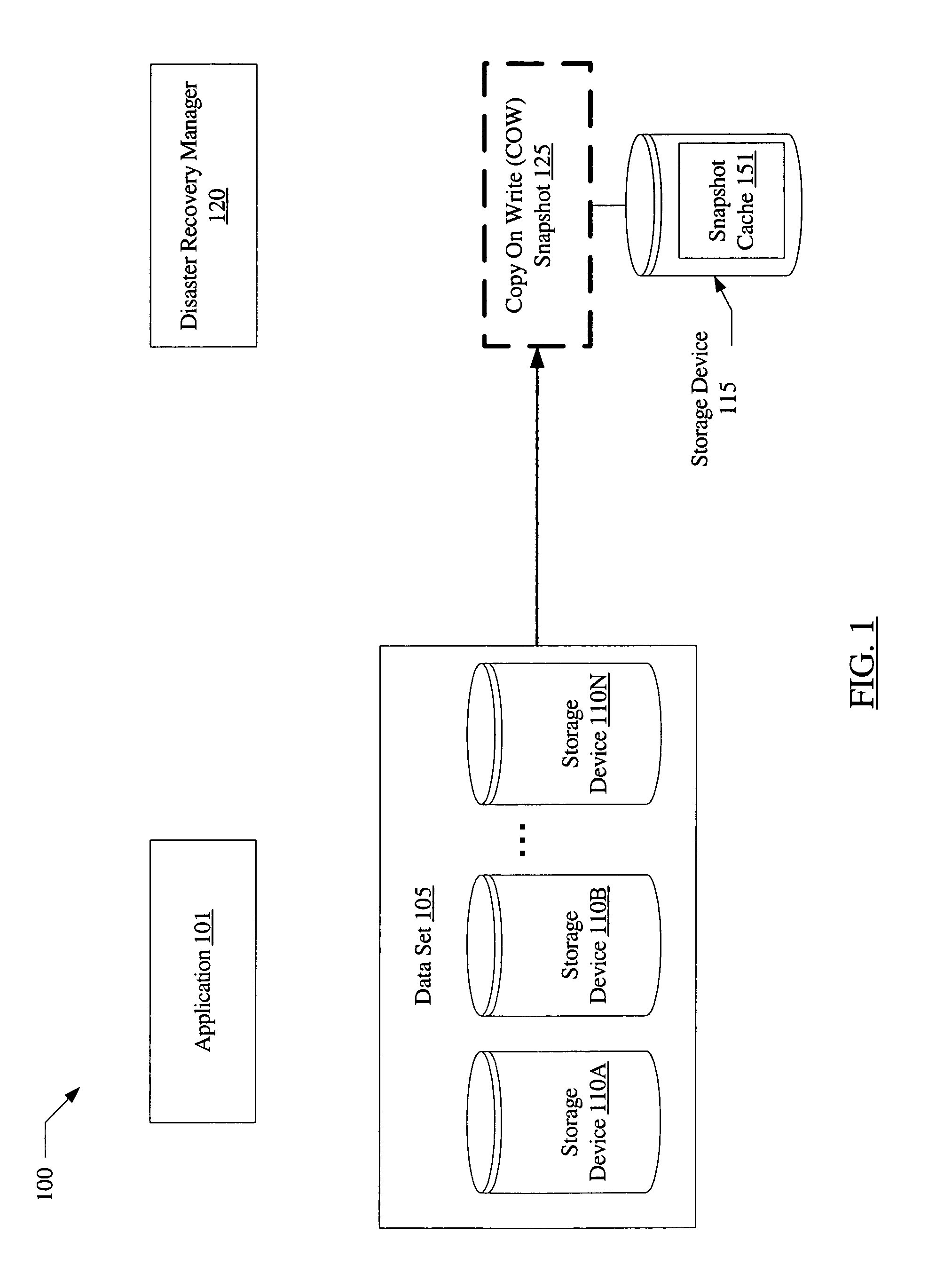
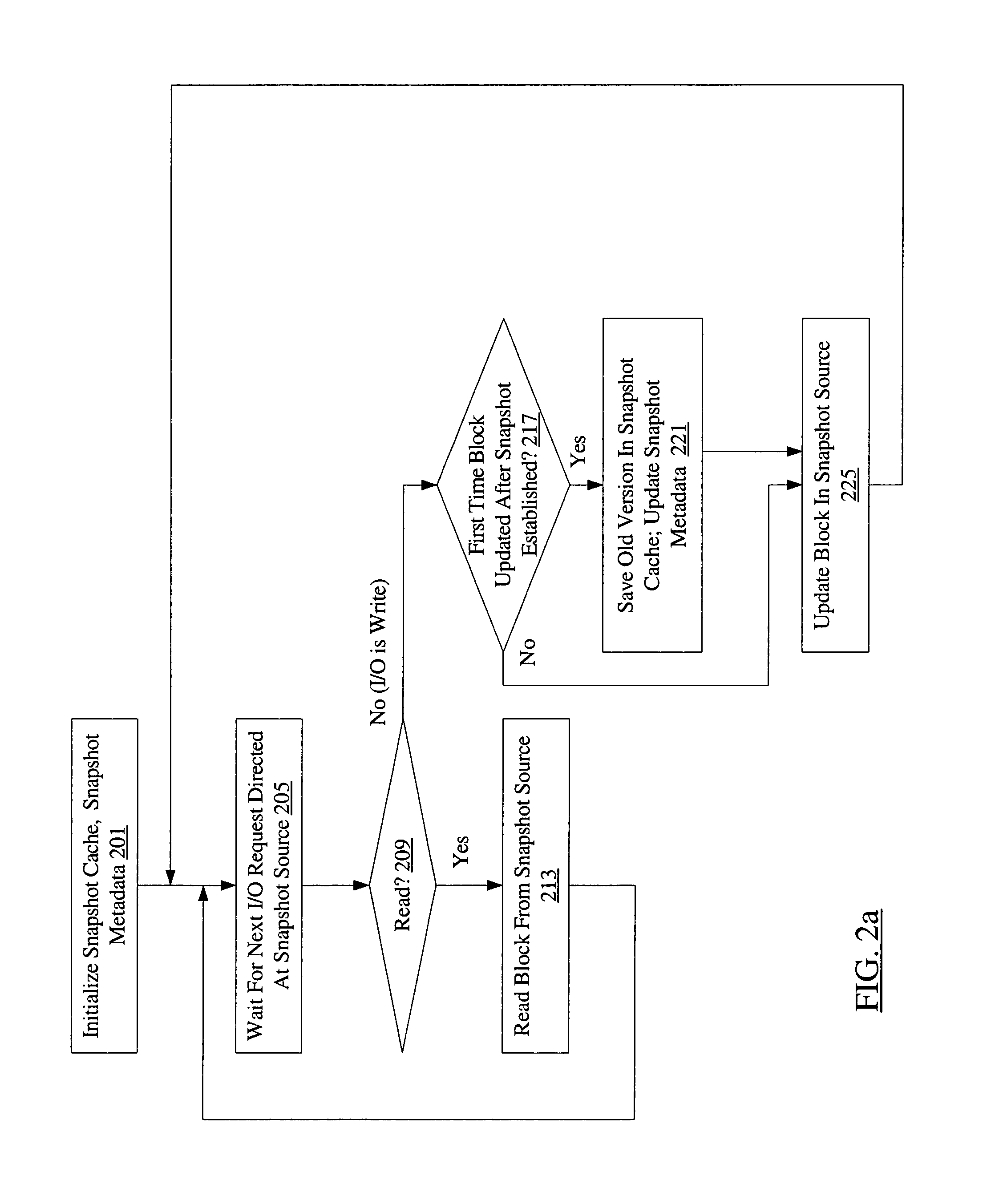
Disaster recovery rehearsal using copy on write
A system for disaster recovery rehearsals using copy-on-write may include a data set of an application and a disaster recovery manager. The disaster recovery manager may be configured to perform a disaster recovery rehearsal using a copy-on-write snapshot of the data set.
Owner:SYMANTEC OPERATING CORP
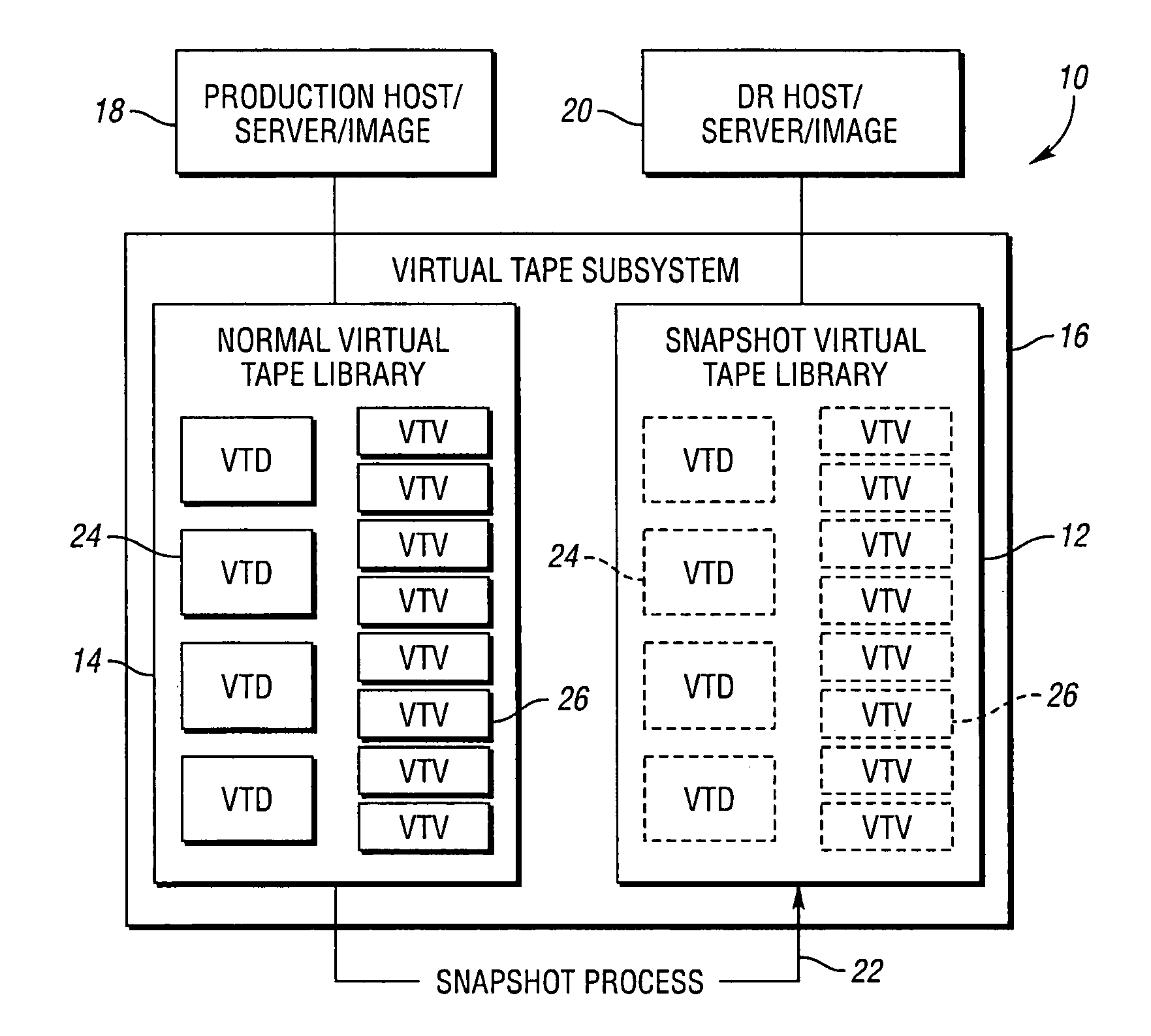
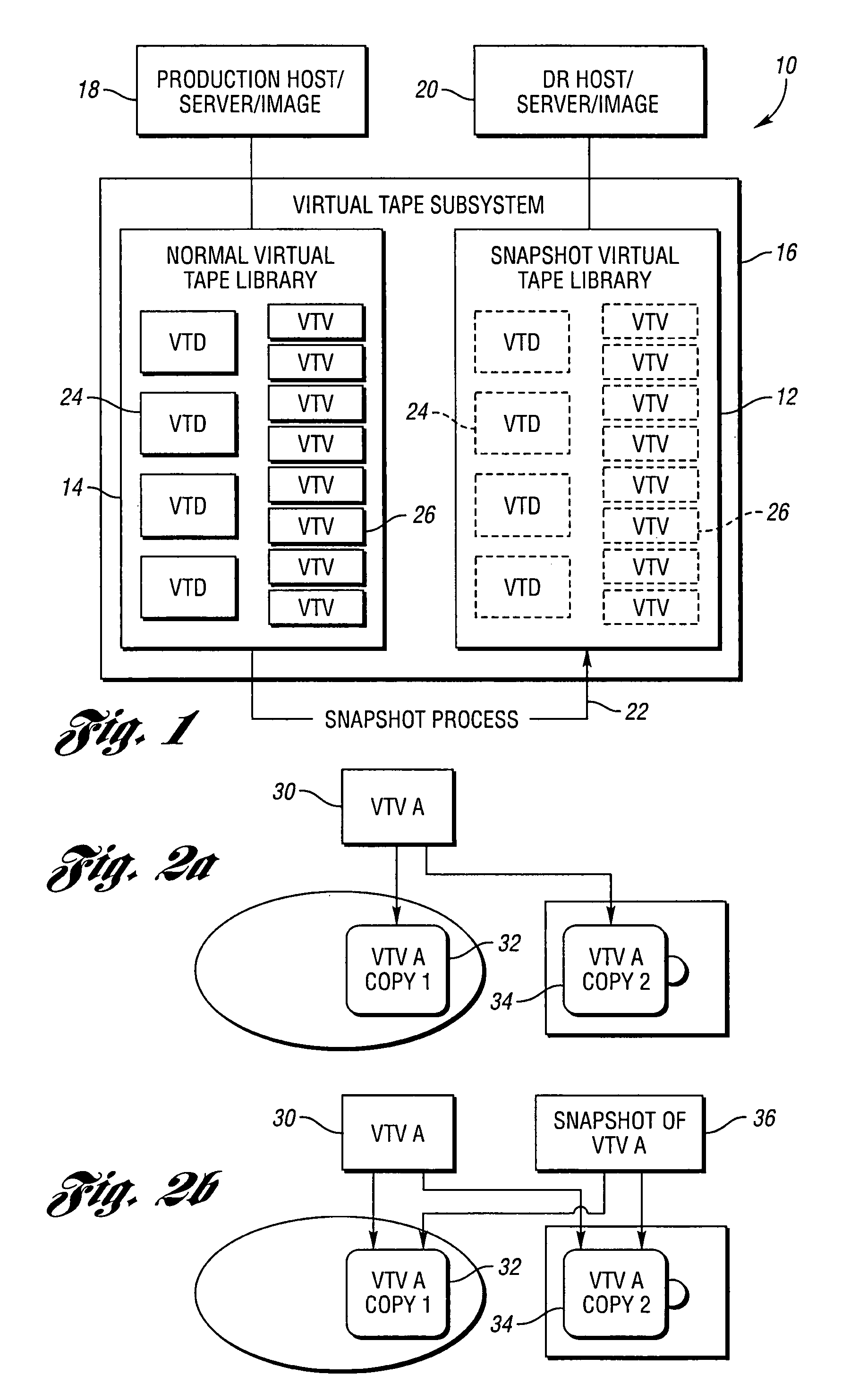
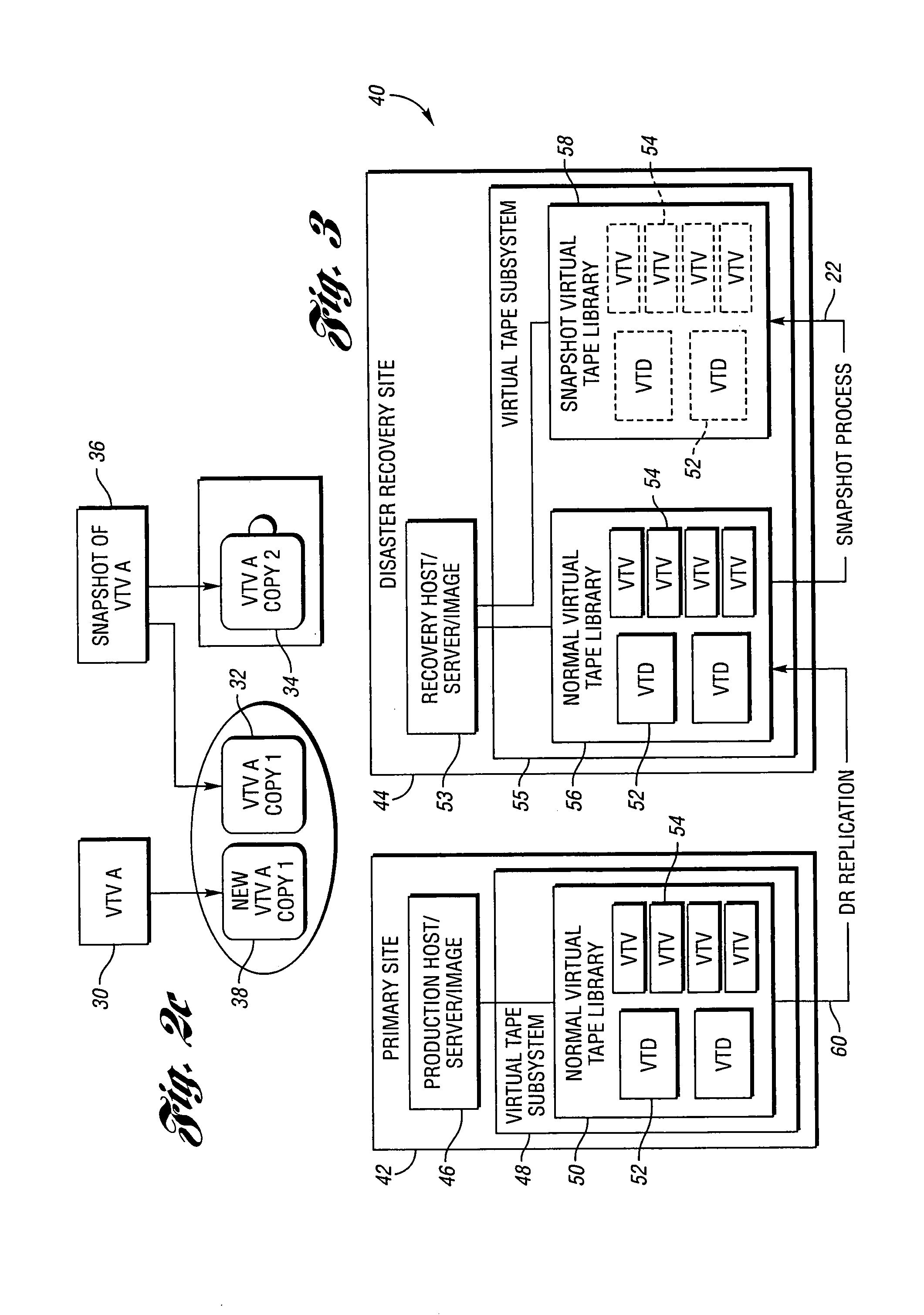
Virtual tape storage system having snapshot virtual tape library for disaster recovery testing
ActiveUS7302540B1Heavy write activityAmount of storage can be consumedError detection/correctionMemory systemsMagnetic tapeVirtual tape library
A virtual tape storage system includes an original virtual tape library for storing data and includes snapshot virtual tape library (SVTL). The SVTL includes a snapshot of the data stored in the original virtual tape library. A host is operable to receive the snapshot data from the SVTL to perform a disaster recovery test of the original virtual tape library. The SVTL is generated from the original virtual tape library using a copy-on-write snapshot process. In an embodiment, the original virtual tape library stores the stored data on a number of virtual tape volumes (VTVs), and the SVTL includes a snapshot of those VTDs and VTVs which are required for a disaster recovery test of the original virtual tape library. In this case, the host uses the SVTL to perform the disaster recovery test of the original virtual tape library.
Owner:ORACLE INT CORP
Selective Encryption System and Method for I/O Operations
InactiveUS20080320316A1Memory loss protectionEncryption apparatus with shift registers/memoriesComputer hardwareVirtual machine
Upon occurrence of a trigger condition, writes of allocation units of data (including code) to a device, such as writes of blocks to a disk, are first encrypted. Each allocation unit is preferably a predetermined integral multiple number of minimum I / O units. A data structure is marked to indicate which units are encrypted. Upon reads from the device, only those allocation units marked as encrypted are decrypted. The disk protected by selective encryption is preferably the virtual disk of a virtual machine (VM). The trigger condition is preferably either that the virtual disk has been initialized or that the VM has been powered on. Mechanisms are also provided for selectively declassifying (storing in unencrypted form) already-encrypted, stored data, and for determining which data units represent public, general-use data units that do not need to be encrypted. The “encrypt-on-write” feature of the invention may be used in conjunction with a “copy-on-write” technique.
Owner:VMWARE INC
Write allocation based on storage system map and snapshot
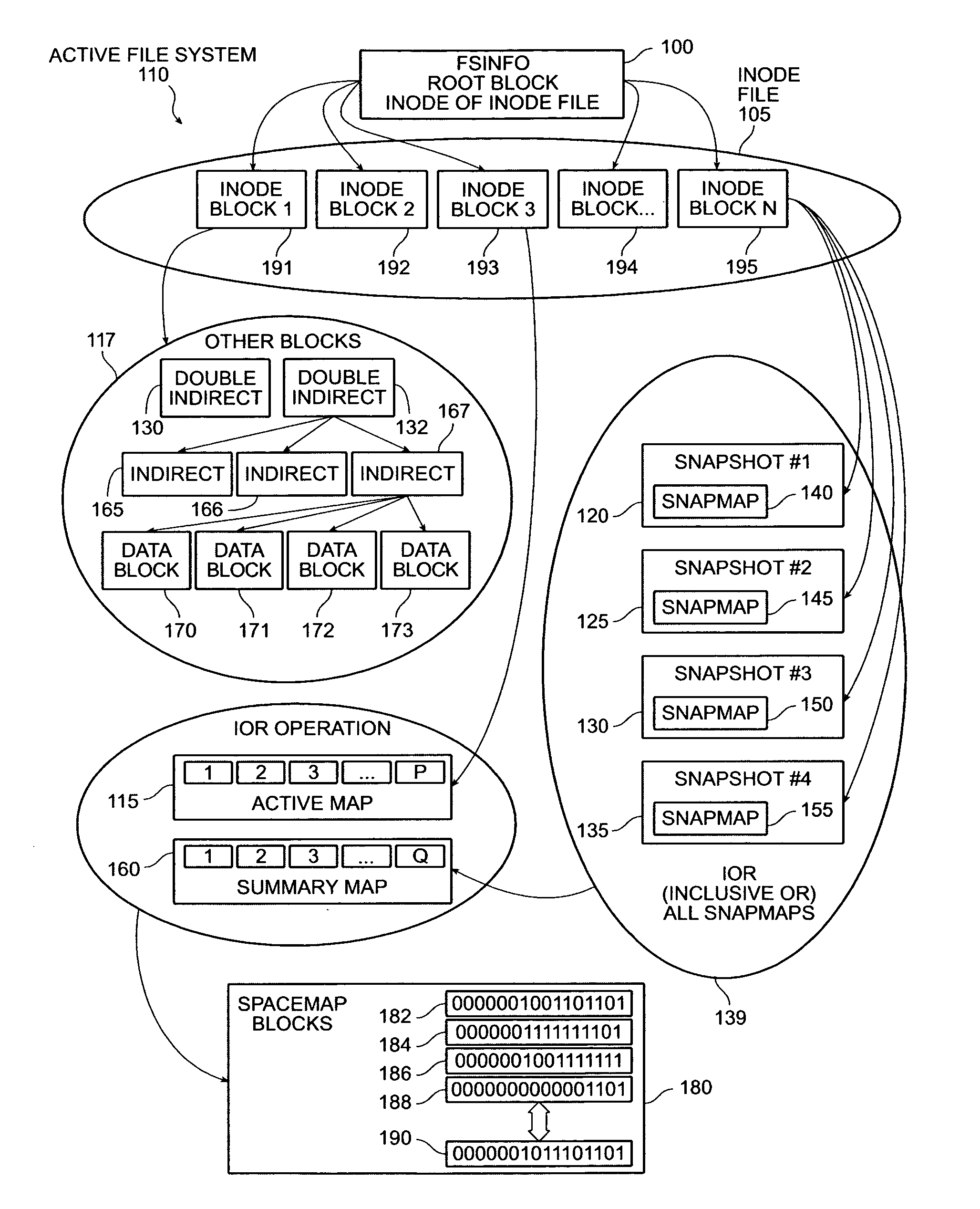
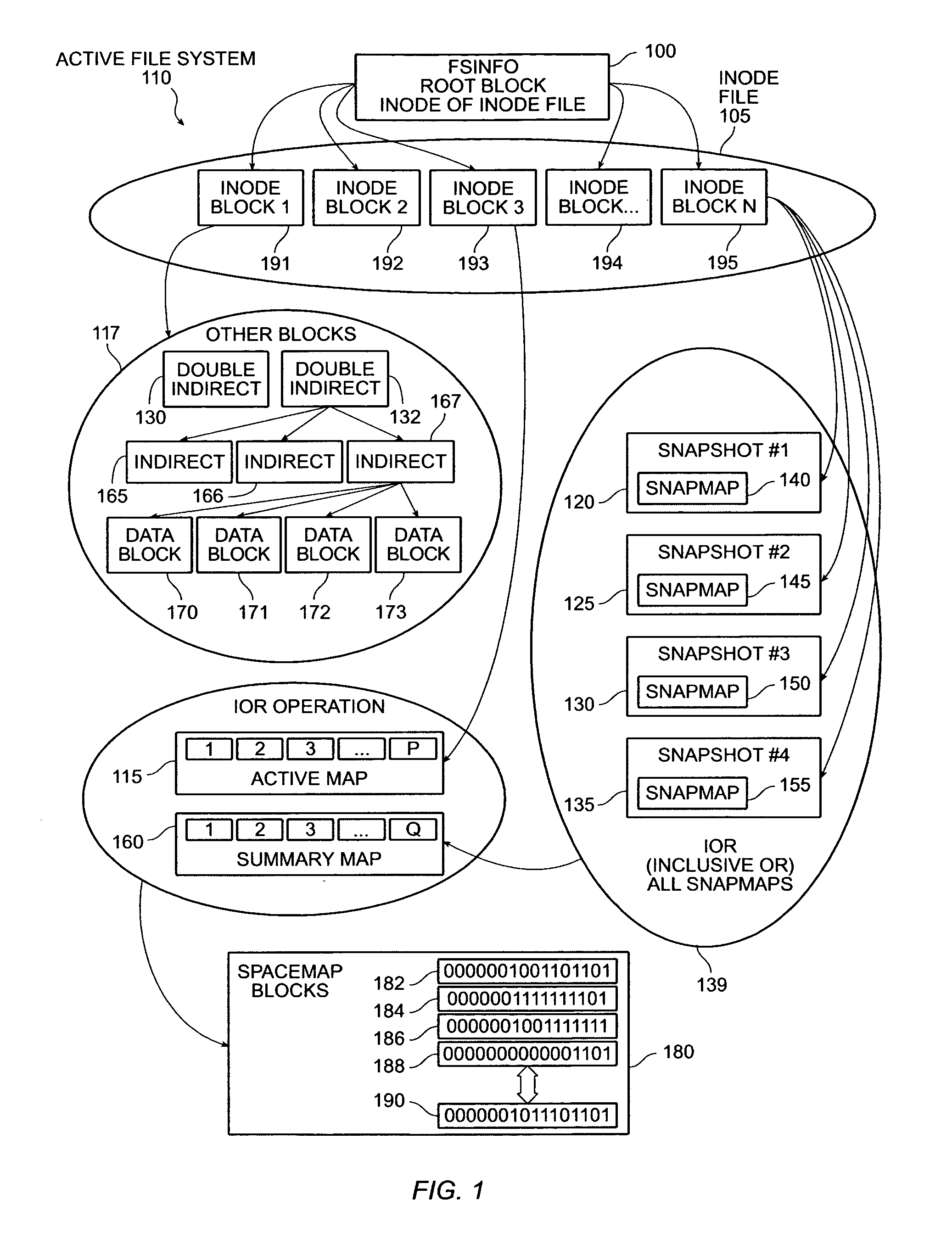
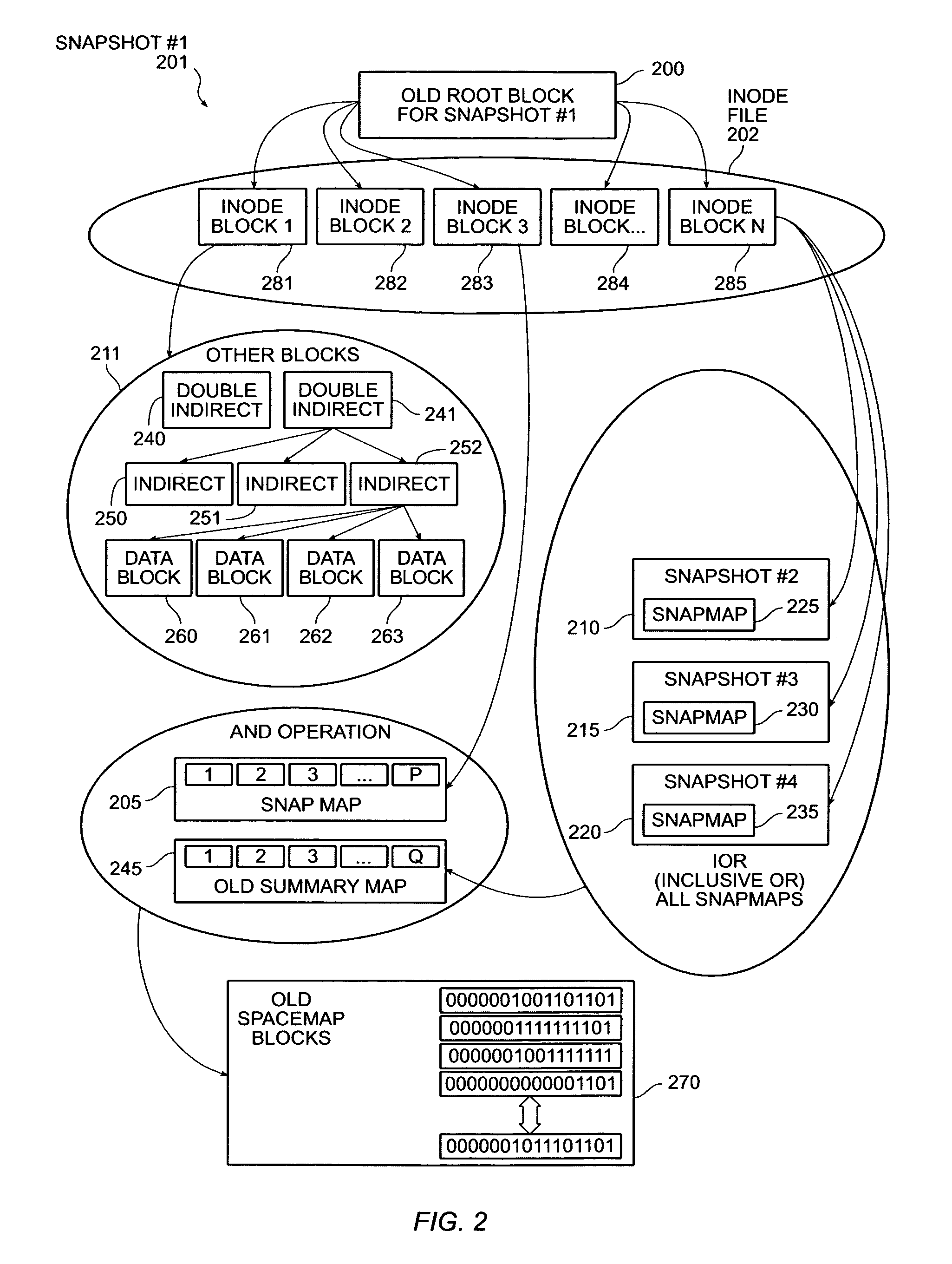
InactiveUS7454445B2Create and delete snapshots very quicklyData processing applicationsDigital data processing detailsInodeImproved method
The invention provides an improved method and apparatus for creating a snapshot of a file system. A “copy-on-write” mechanism is used. The snapshot uses the same blocks as the active file system until the active file system is modified. Whenever a modification occurs, the modified data is copied to a new block and the old data is saved. In this way, the snapshot only uses space where it differs from the active file system, and the amount of work required to create the snapshot is small. A record of which blocks are being used by the snapshot is included in the snapshot itself, allowing effectively instantaneous snapshot creation and deletion. A snapshot can also be deleted instantaneously simply by discarding its root inode.
Owner:NETWORK APPLIANCE INC
Copy method supplementing outboard data copy with previously instituted copy-on-write logical snapshot to create duplicate consistent with source data as of designated time
InactiveUS7072915B2Quantity minimizationData processing applicationsRedundant operation error correctionExternal applicationExternal data
A copy method is disclosed to provide a duplicate copy of source data where the duplicate copy is consistent with the source data as of a designated time. The method includes creating a copy-on-write relationship between specified source data and an original image cache, utilizing an application outboard of the designated host application to copy all items of source data and their associated locations to a secondary data object without regard to whether the items source data have been updated since creating the copy-on-write relationship, and copying a specified amount of contents of the original image cache to the secondary data object. The specified amount includes contents of the original image cache as of completion of the utilizing operation. In addition, the method includes permitting copy-on-write relationship to continue during the utilizing operation and during at least part of the copying operation.
Owner:IBM CORP
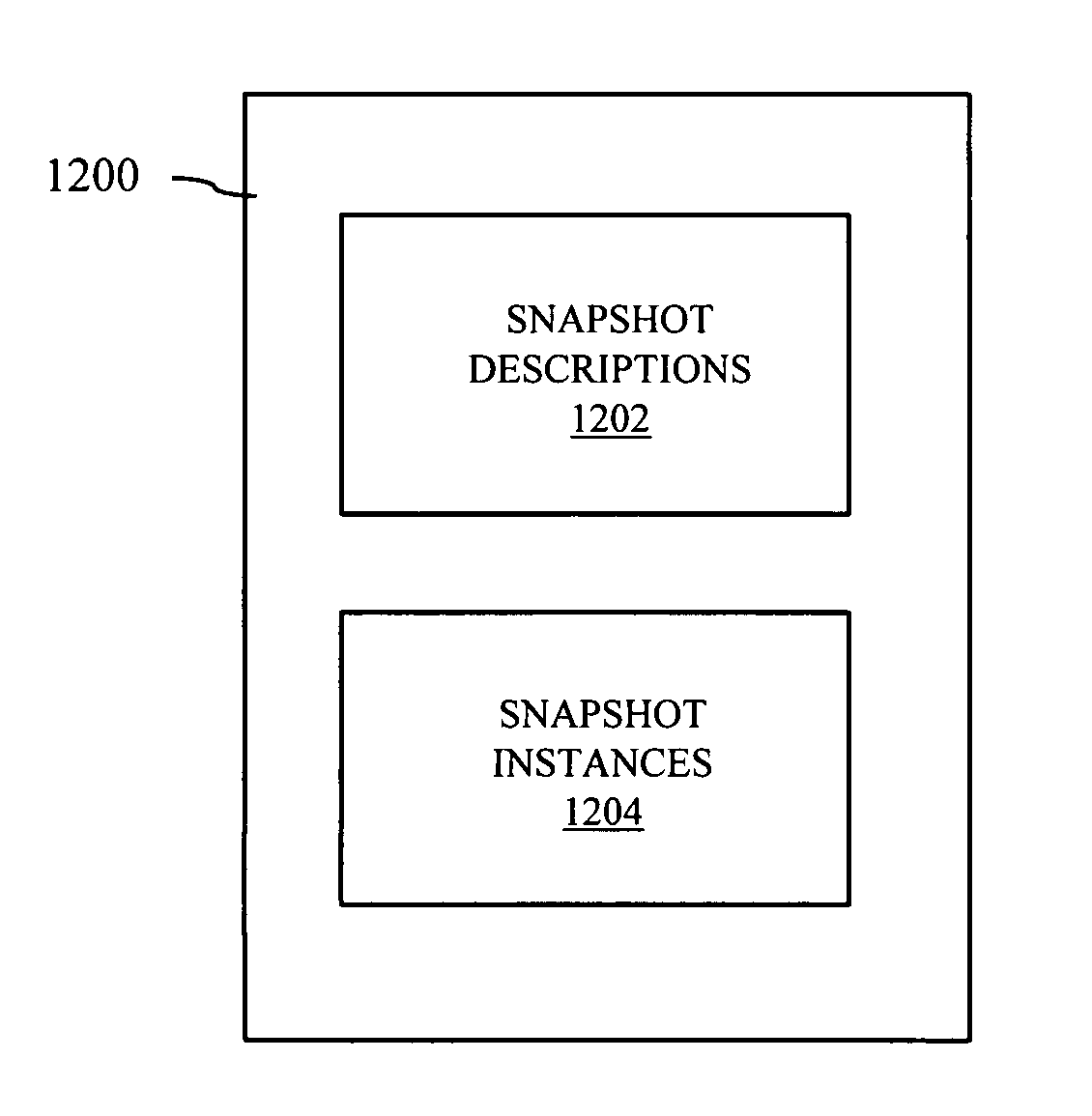
Fine-grain policy-based snapshots
ActiveUS8352431B1Maximum flexibilityImprove efficiencyDigital data information retrievalDigital data processing detailsObject basedTimestamp
Providing a snapshot copy of data includes selectively collecting a plurality of data objects based on evaluation of a predicate associated with each of the data objects and performing a snapshot operation in connection with modifying at least one of the plurality of data objects. The snapshot operation may be performed prior to modifying the at least one of the plurality of data objects. The snapshot operation may be a copy on write operation. Providing a snapshot copy of data may also include providing a data structure that maintains a plurality of snapshot instances. The data structure may be a table. Each of the snapshot instances may include at least one of: an object set description, a timestamp indicating when the snapshot was initiated, a snapshot name and a handling policy.
Owner:EMC IP HLDG CO LLC
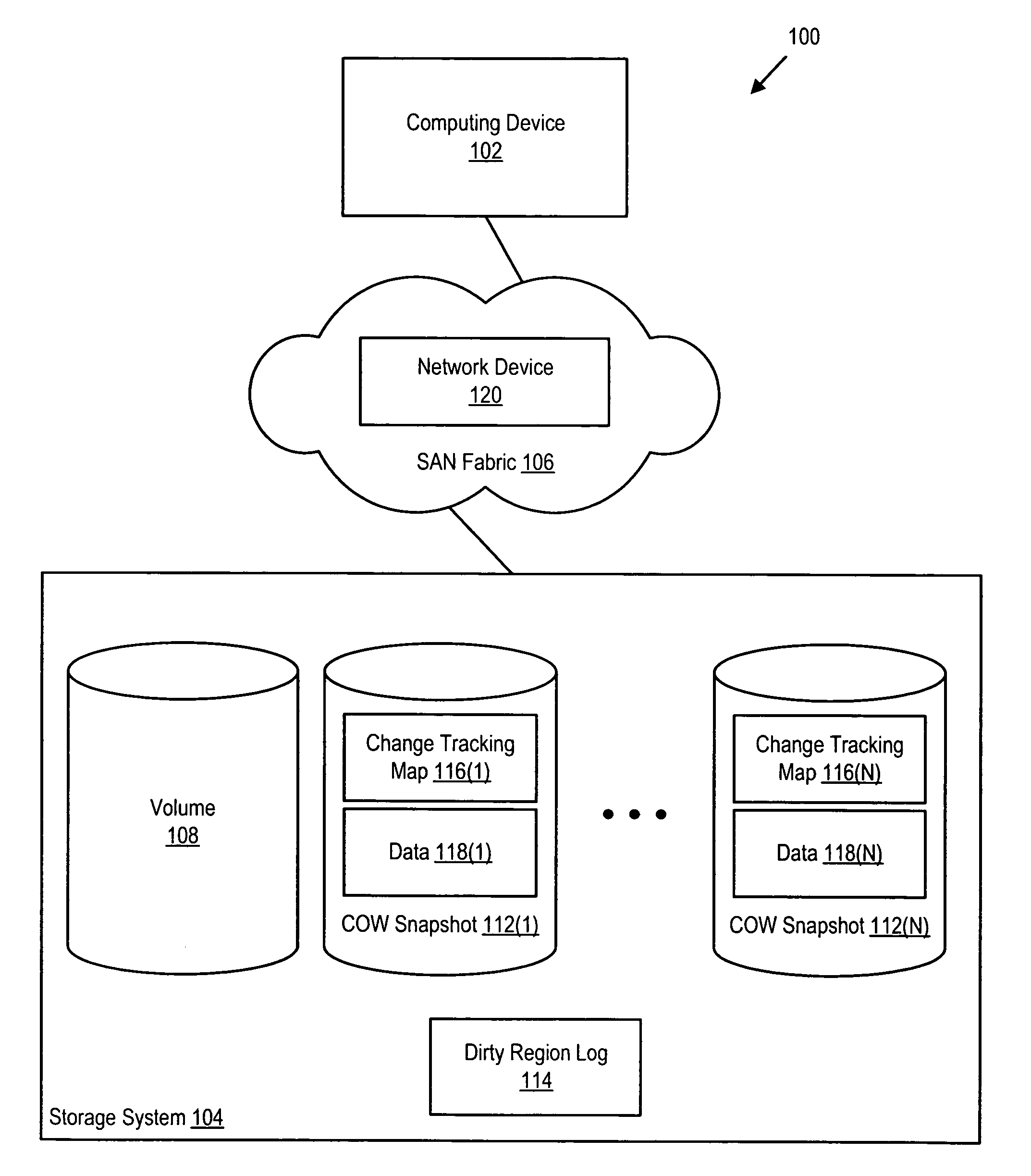
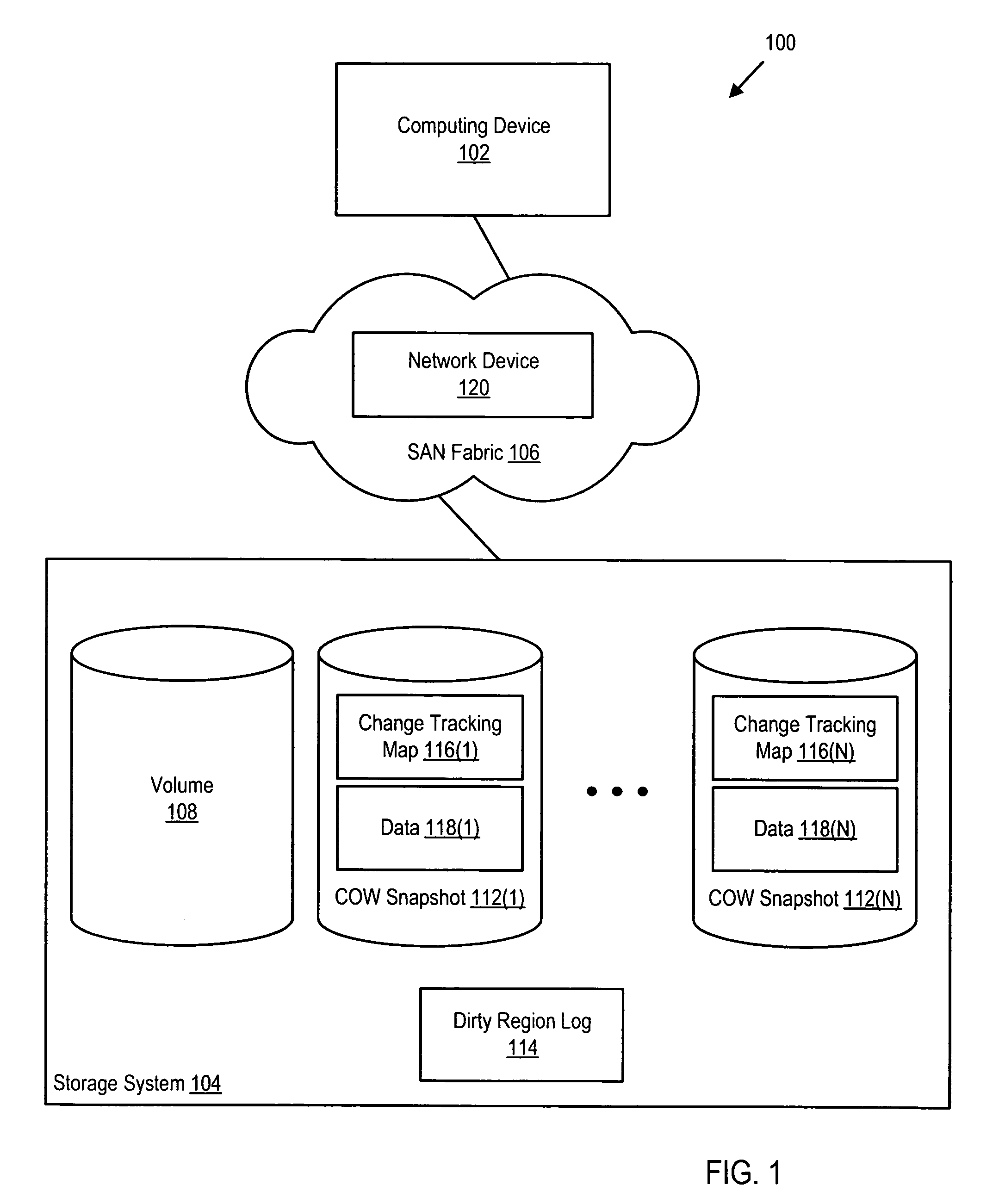
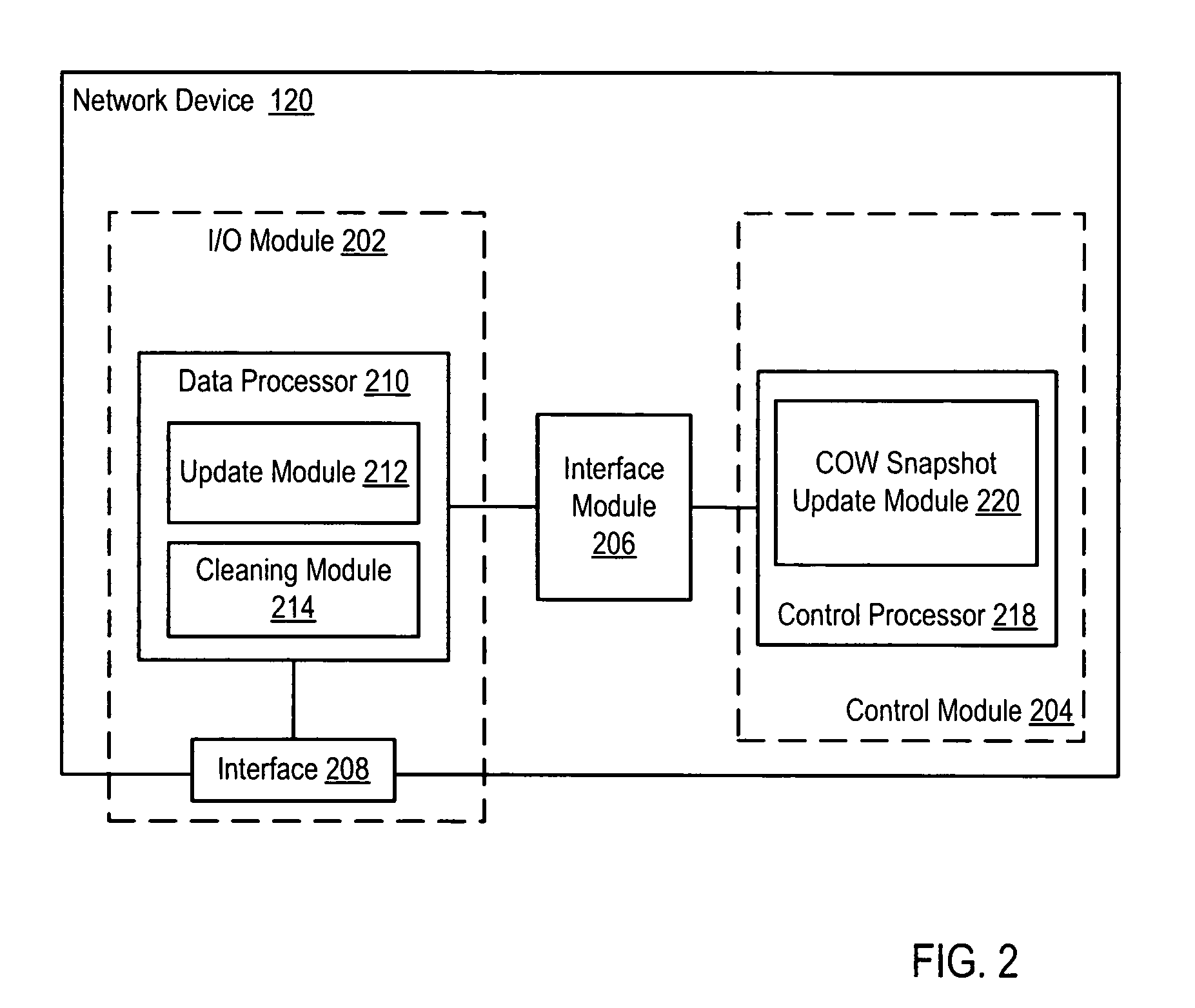
System and method for updating a copy-on-write snapshot based on a dirty region log
Various methods and systems for updating a copy-on-write snapshot based on a dirty region log are disclosed. For example, a method involves maintaining a dirty region log and updating a copy-on-write snapshot change tracking map, based on information in the dirty region log. In some embodiments, the copy-on-write snapshot change tracking map is updated in response to an indication of a dirty region log cleaning cycle. The dirty region log cleaning cycle is inhibited until after the copy-on-write snapshot change tracking map has been updated. The method can be used to update multiple copy-on-write snapshot change tracking maps, each of which is associated with a respective one of several copy-on-write snapshots, based on information in the dirty region log. Such a method can be performed by a virtualizing network device.
Owner:SYMANTEC OPERATING CORP
Method and device for processing metadata
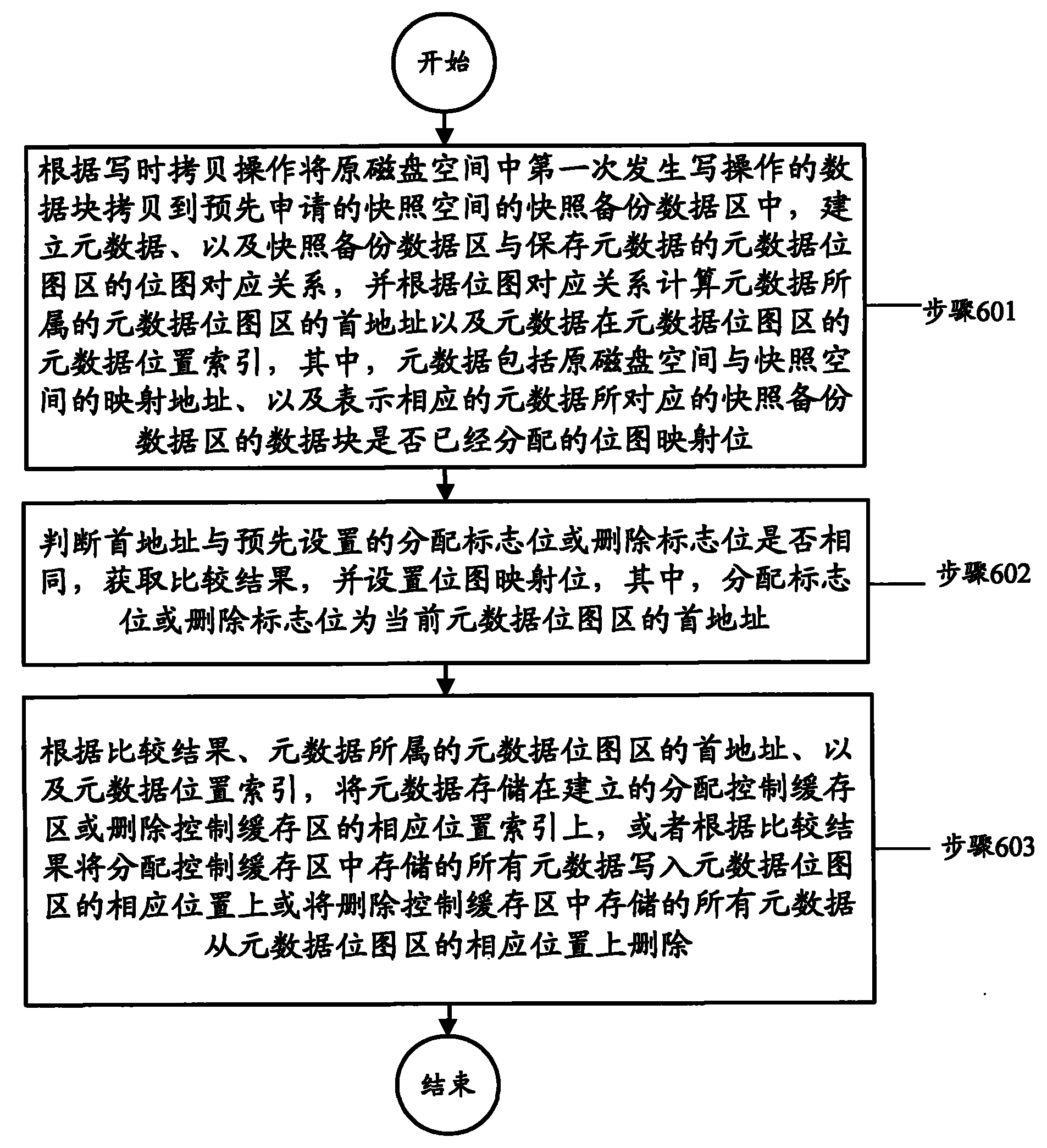
ActiveCN101814044AImprove processing efficiencyReduce the number of timesMemory adressing/allocation/relocationRedundant operation error correctionBitmapMetadata
The invention discloses a method and a device for processing metadata. The method comprises the following steps of: copying data written for the first time in an original disk space into a snapshot backup data area according to copy-on-write operation, establishing metadata and bitmap corresponding relationships and calculating a first address of a metadata bitmap area where the metadata belongs and metadata position indexes of the metadata in the metadata bitmap area according to the bitmap corresponding relationships; judging whether the first address is the same as a preset allocation marker bit or a deletion marker bit or not to obtain a comparison result and setting bitmap mapping bits; and according to the comparison result, the first address of the metadata bitmap area where the metadata belongs, and the metadata position indexes, storing the metadata into corresponding position indexes of an allocation control buffer area or a deletion control buffer area, or writing all the metadata in the allocation control buffer area into corresponding positions of the metadata bitmap area or deleting all the metadata in the deletion control buffer area from the corresponding positionsof the metadata bitmap area.
Owner:ZTE CORP
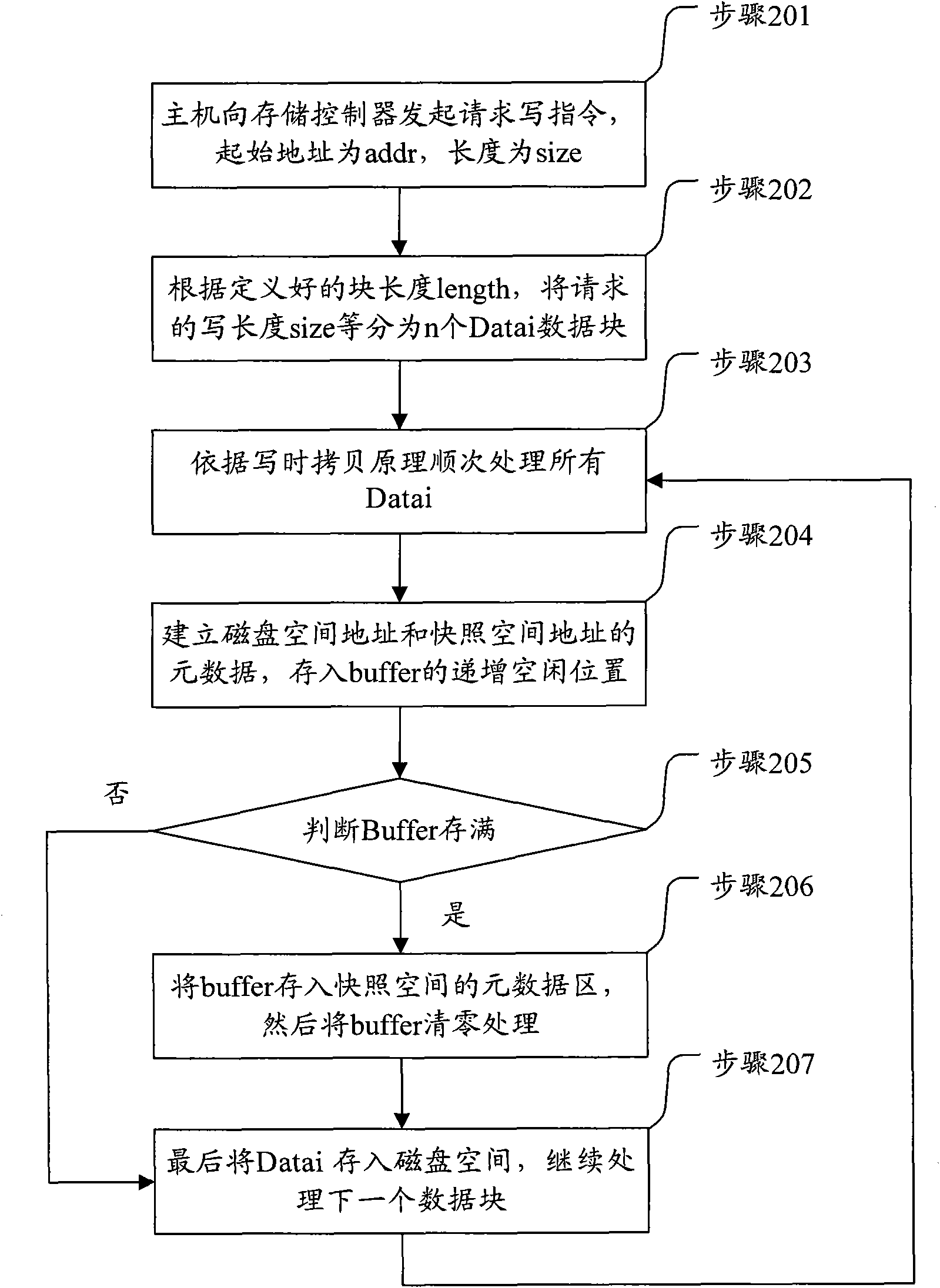
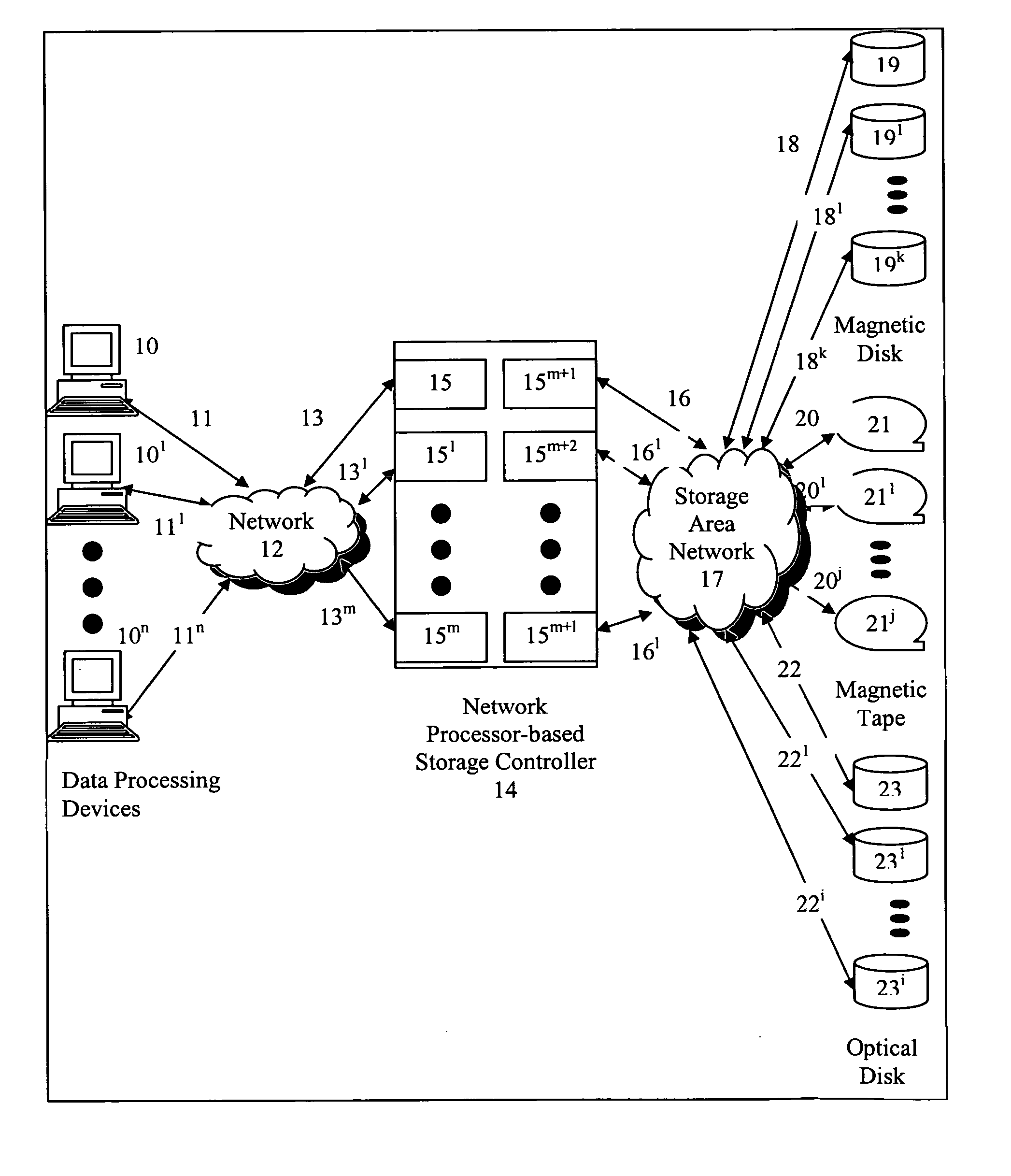
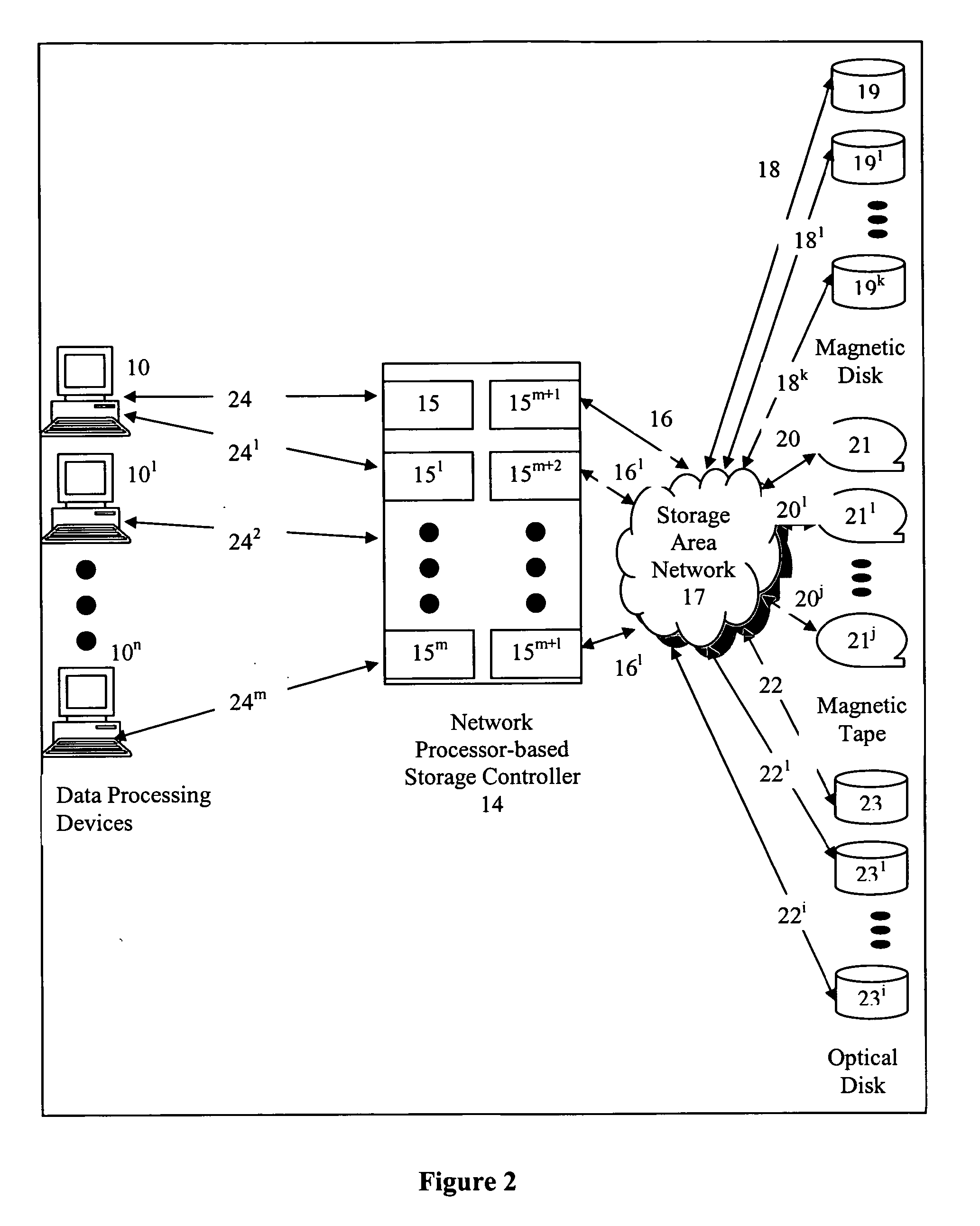
Network processor-based storage controller, compute element and method of using same
A data storage controller providing network attached storage and storage area network functionality comprising a network processor (37) and providing for volume management (preferably one or more of mirroring, RAID5, and copy on write backup), caching of data stored, protocol acceleration of low level protocols (preferably one or more of ATM, Ethernet, Fibre Channel, Infiniband, Serial SCSI, Serial ATA, and any other serializable protocol), and protocol acceleration of higher level protocols (preferably one or more of IP, ICMP, TCP, UDP, RDMA, RPC, security protocols, preferably one or both of IPSEC and SSL, SCSI, and file system services, preferably one or both of NFS and CIFS).
Owner:CORBIN JOHN R
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com