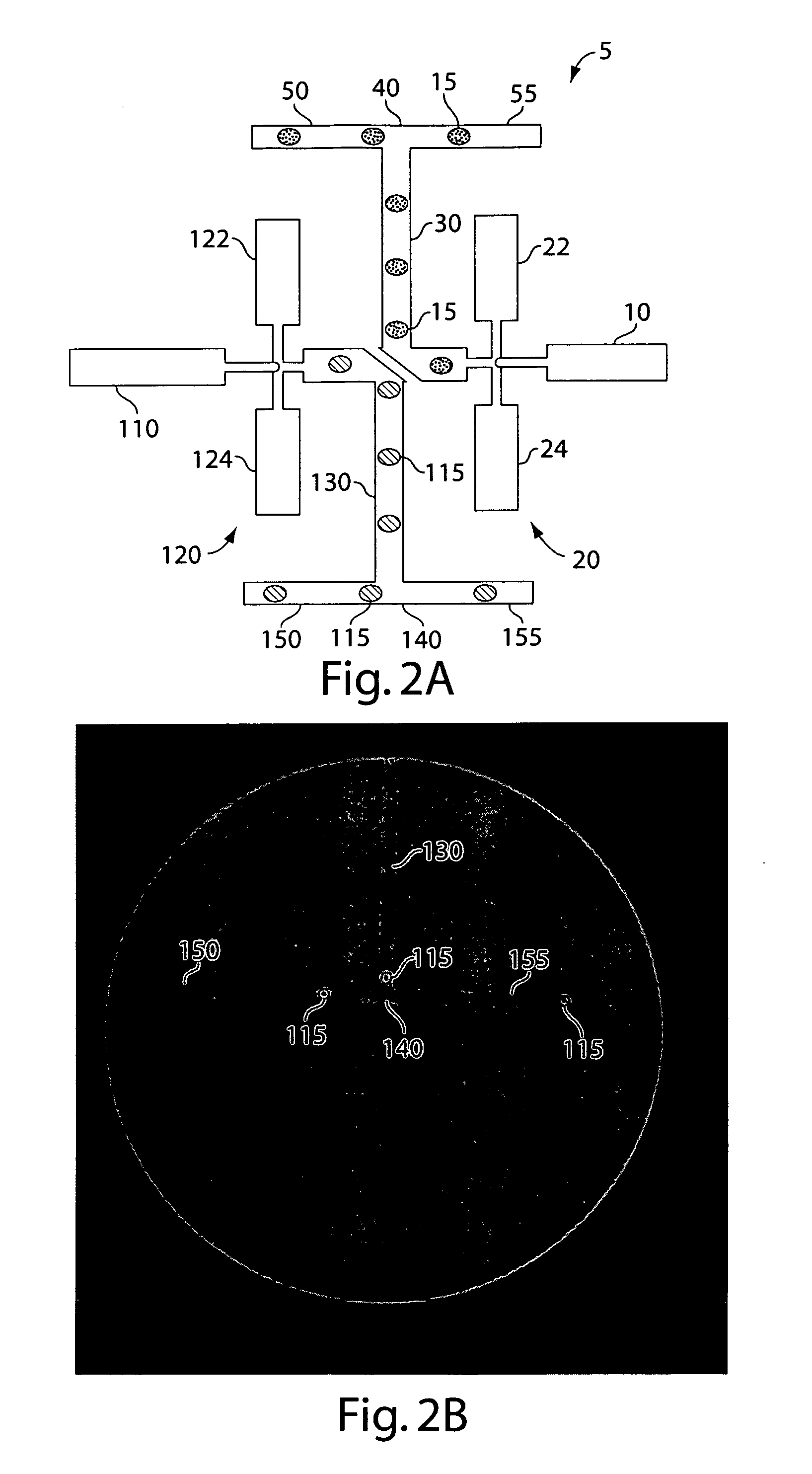
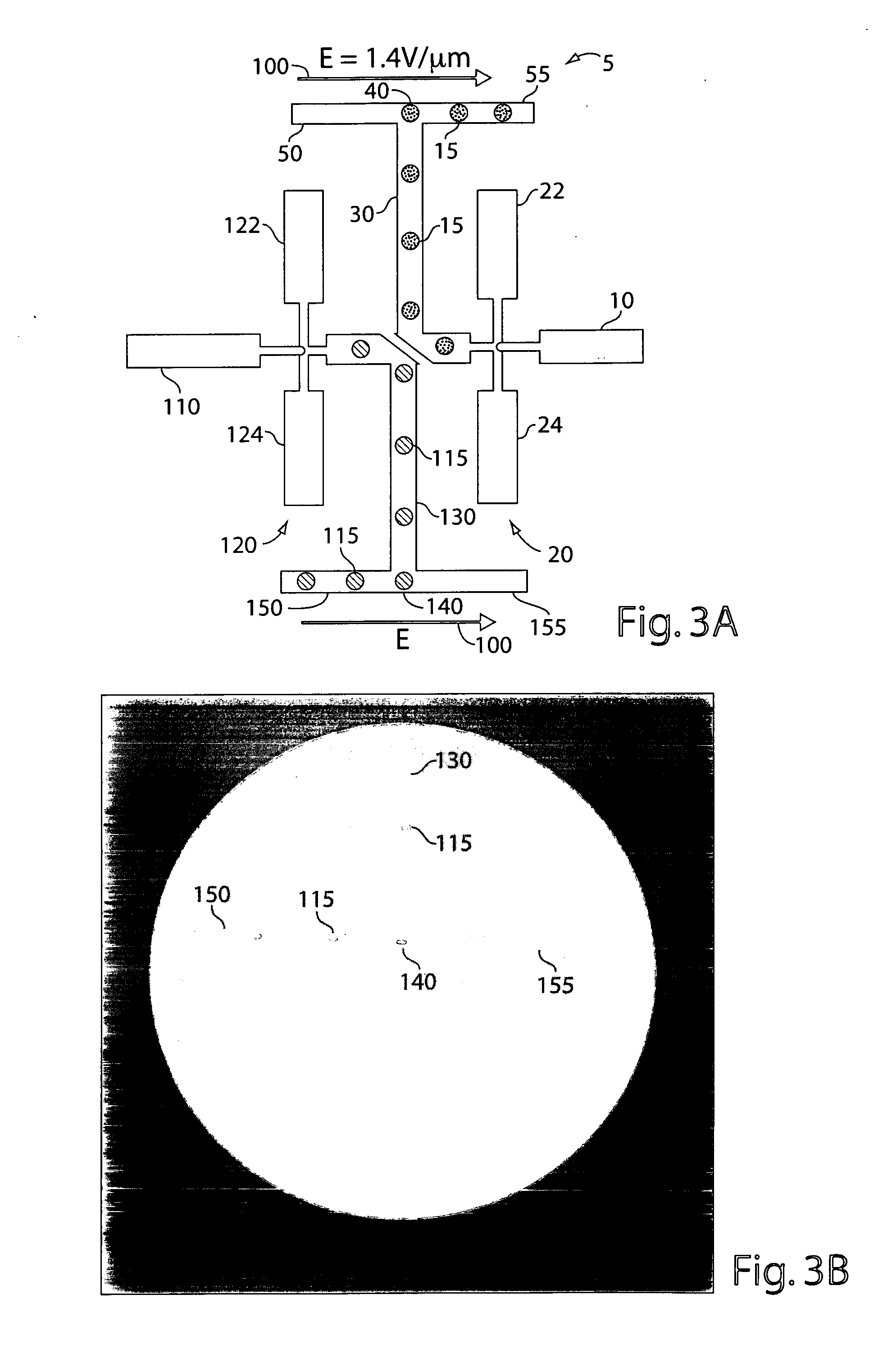
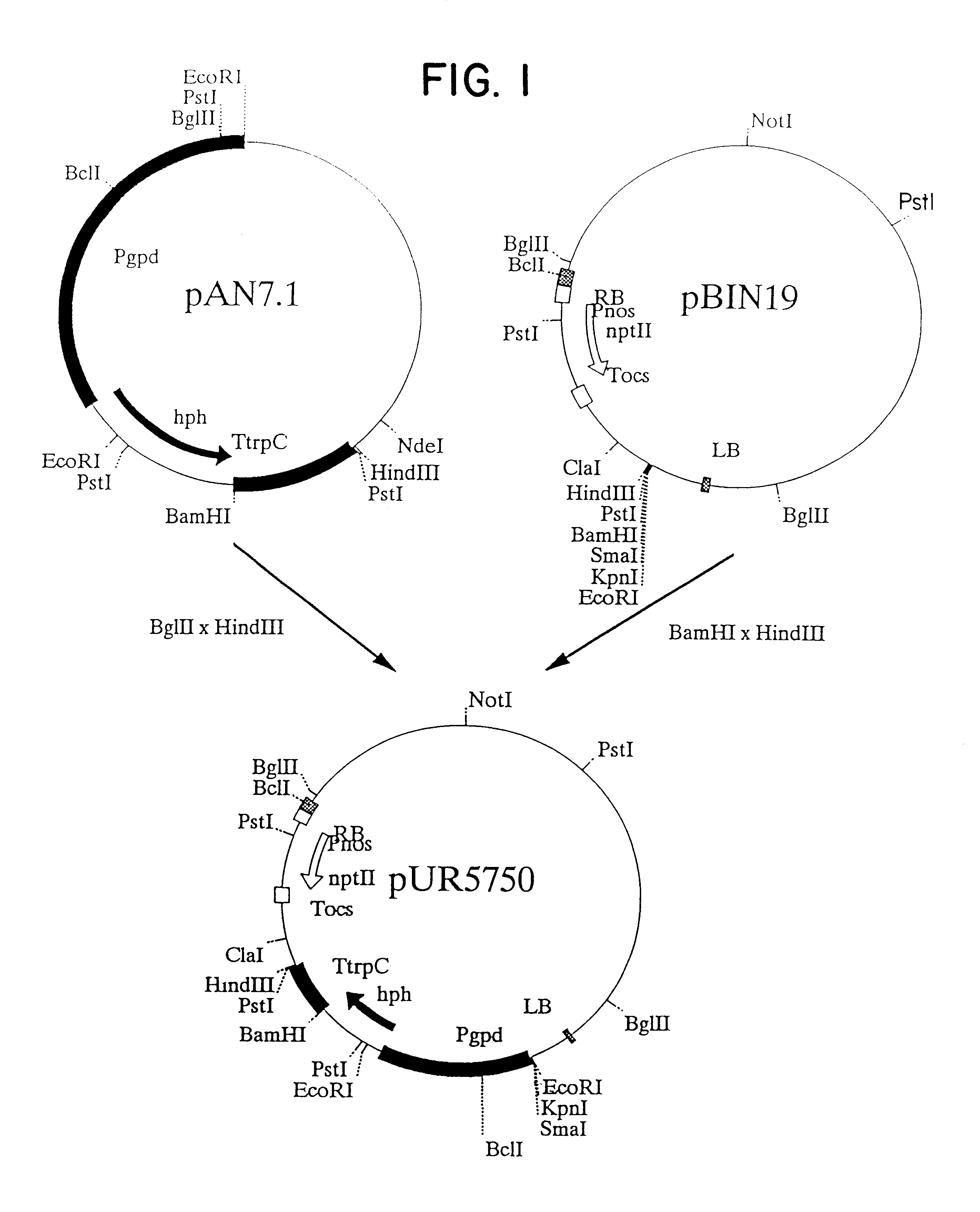
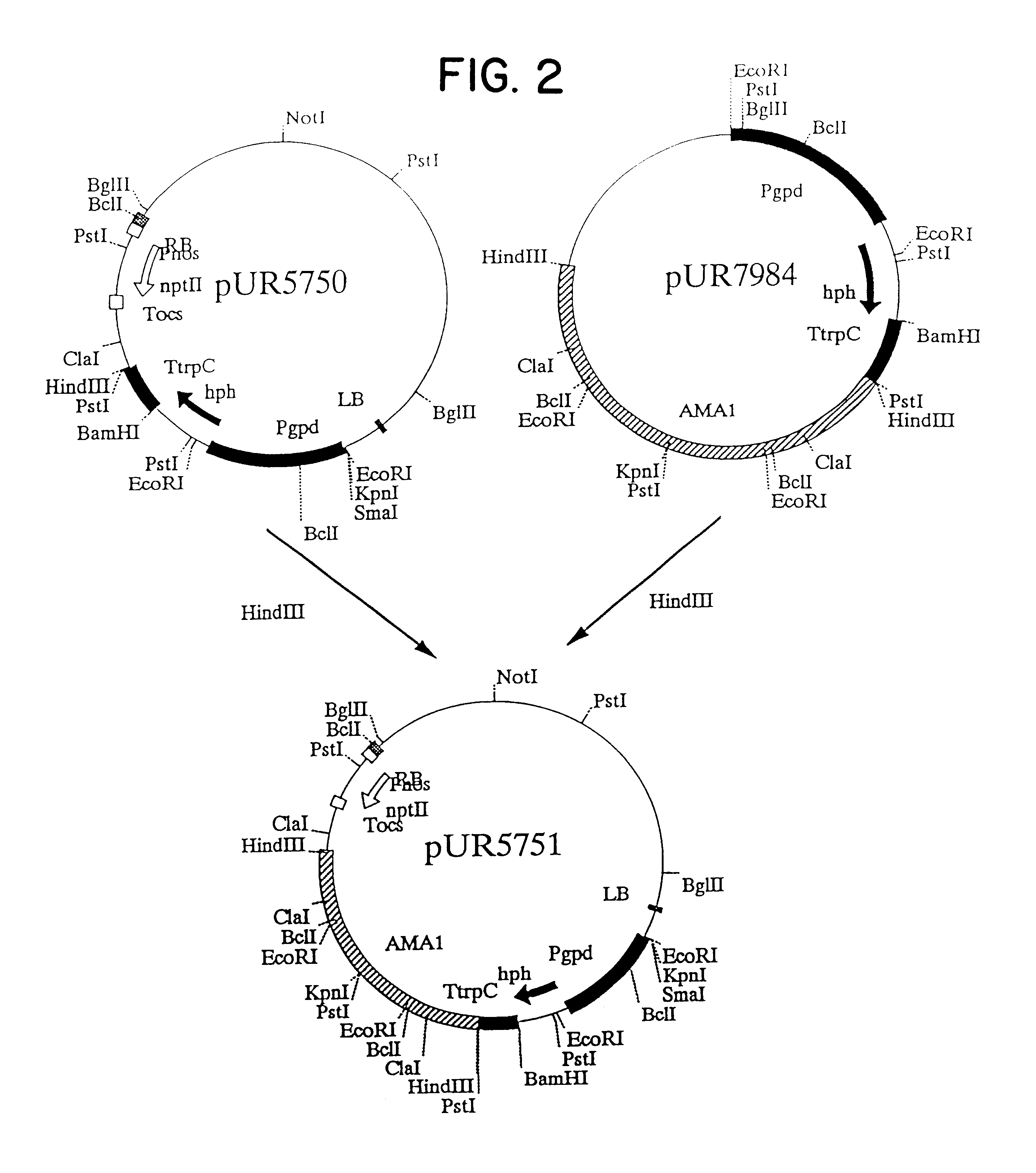
Patents
Literature
561 results about "Multiple copy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Copy and paste multiple items using the Office Clipboard Open the file that you want to copy items from. Select the first item that you want to copy, and press CTRL+C. Continue copying items from the same or other files until you have collected all of the items that you want. Click where you want the items to be pasted.
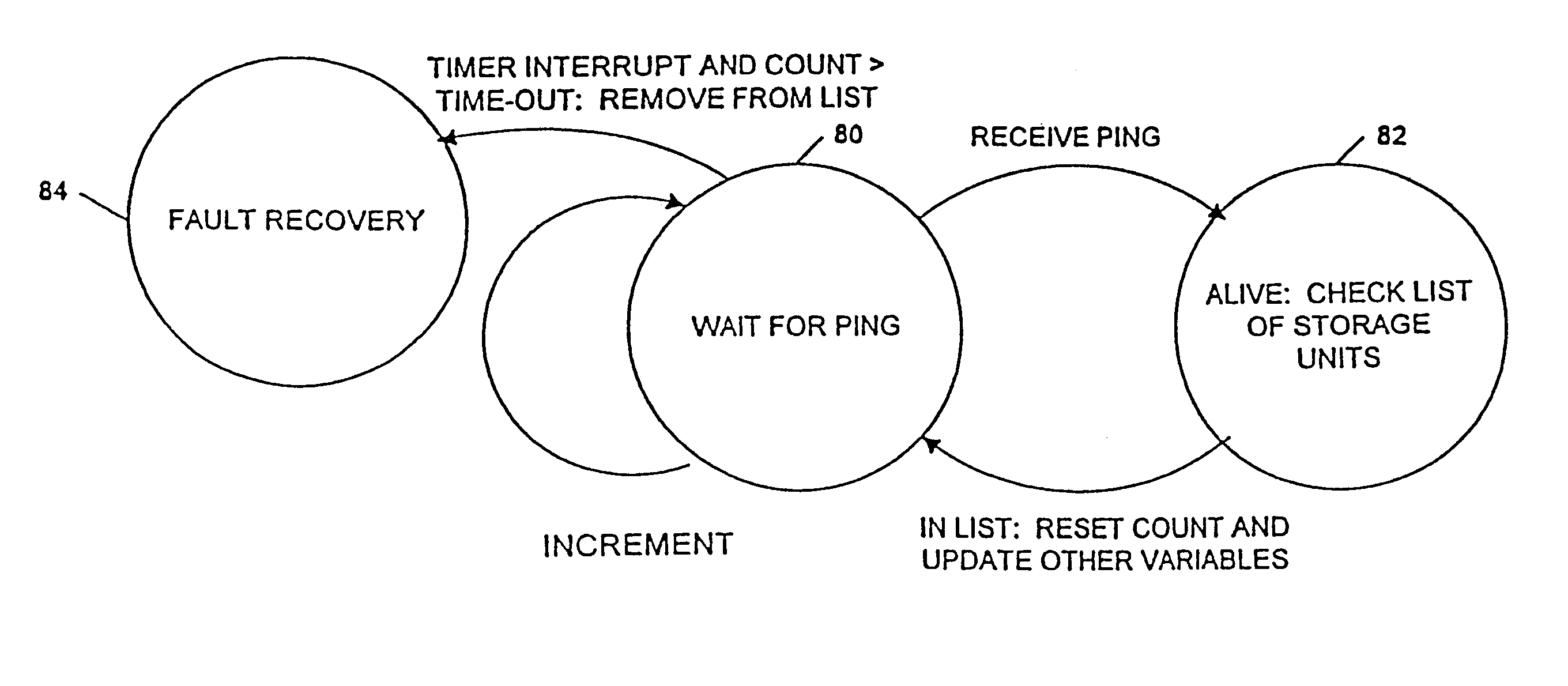
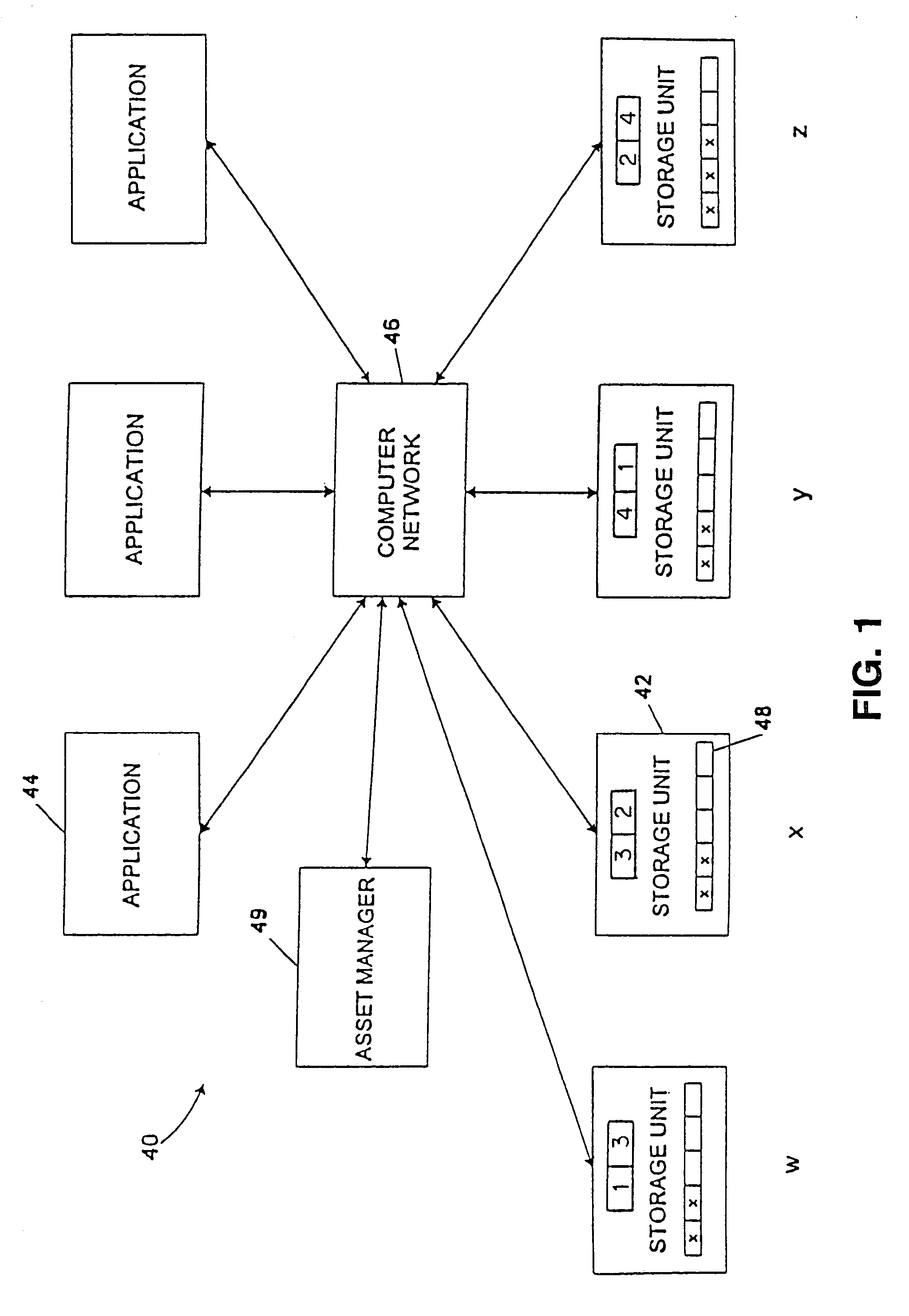
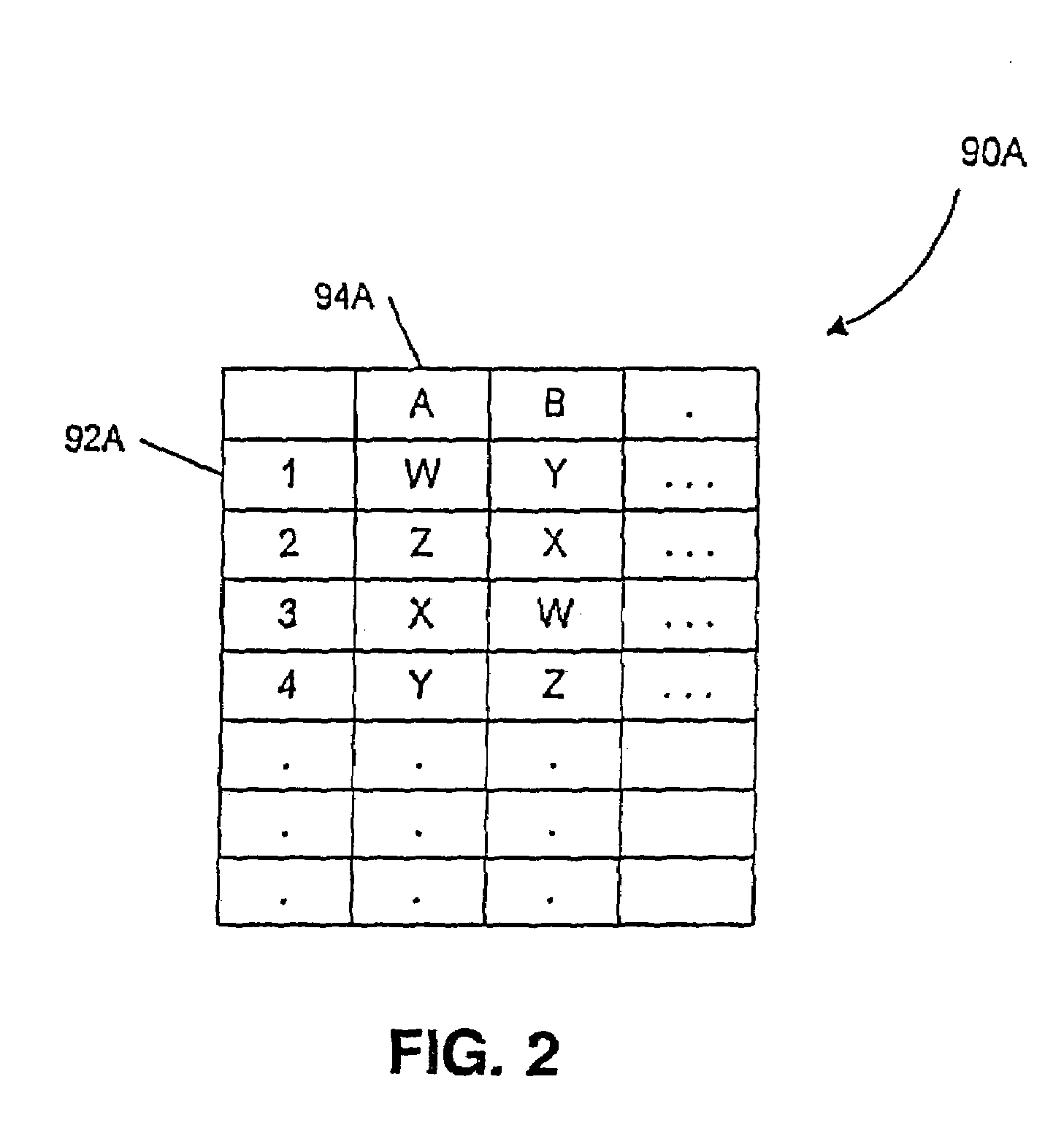
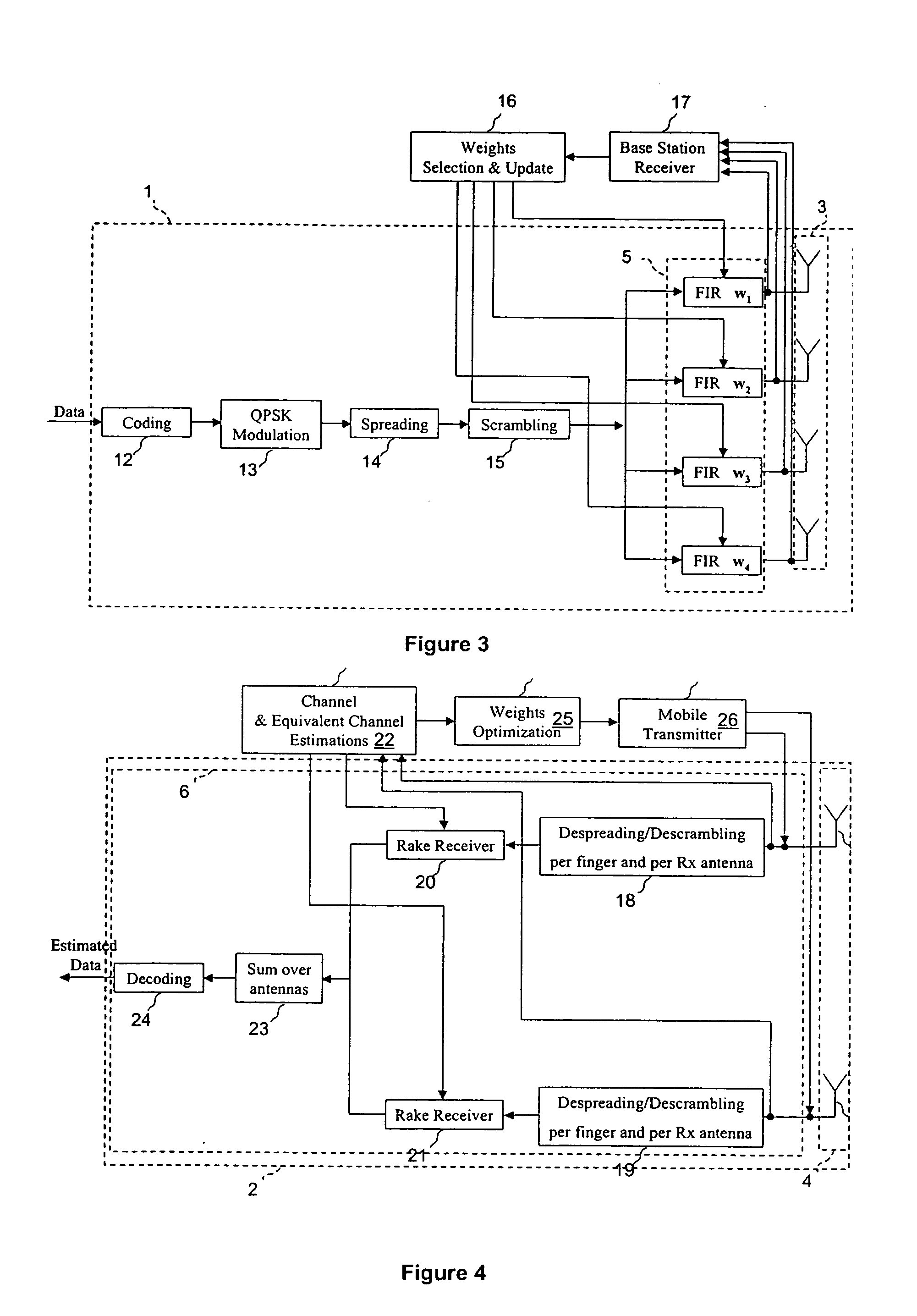
Computer system and process for transferring multiple high bandwidth streams of data between multiple storage units and multiple applications in a scalable and reliable manner
InactiveUS7111115B2Improve reliabilityImprove scalabilityInput/output to record carriersData processing applicationsHigh bandwidthData segment
Multiple applications request data from multiple storage units over a computer network. The data is divided into segments and each segment is distributed randomly on one of several storage units, independent of the storage units on which other segments of the media data are stored. At least one additional copy of each segment also is distributed randomly over the storage units, such that each segment is stored on at least two storage units. This random distribution of multiple copies of segments of data improves both scalability and reliability. When an application requests a selected segment of data, the request is processed by the storage unit with the shortest queue of requests. Random fluctuations in the load applied by multiple applications on multiple storage units are balanced nearly equally over all of the storage units. This combination of techniques results in a system which can transfer multiple, independent high-bandwidth streams of data in a scalable manner in both directions between multiple applications and multiple storage units.
Owner:AVID TECHNOLOGY
Compartmentalised screening by microfluidic control
InactiveUS20050221339A1Rapid and high-throughput screeningLow costCompound screeningSequential/parallel process reactionsCompound (substance)Drug development
The invention describes a method for the identification of compounds which bind to a target component of a biochemical system or modulate the activity of the target, comprising the steps of: a) compartmentalising the compounds into microcapsules together with the target, such that only a subset of the repertoire is represented in multiple copies in any one microcapsule; and b) identifying the compound which binds to or modulates the activity of the target; wherein at least one step is performed under microfluidic control. The invention enables the screening of large repertoires of molecules which can serve as leads for drug development.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE +1
Microfabricated integrated DNA analysis system
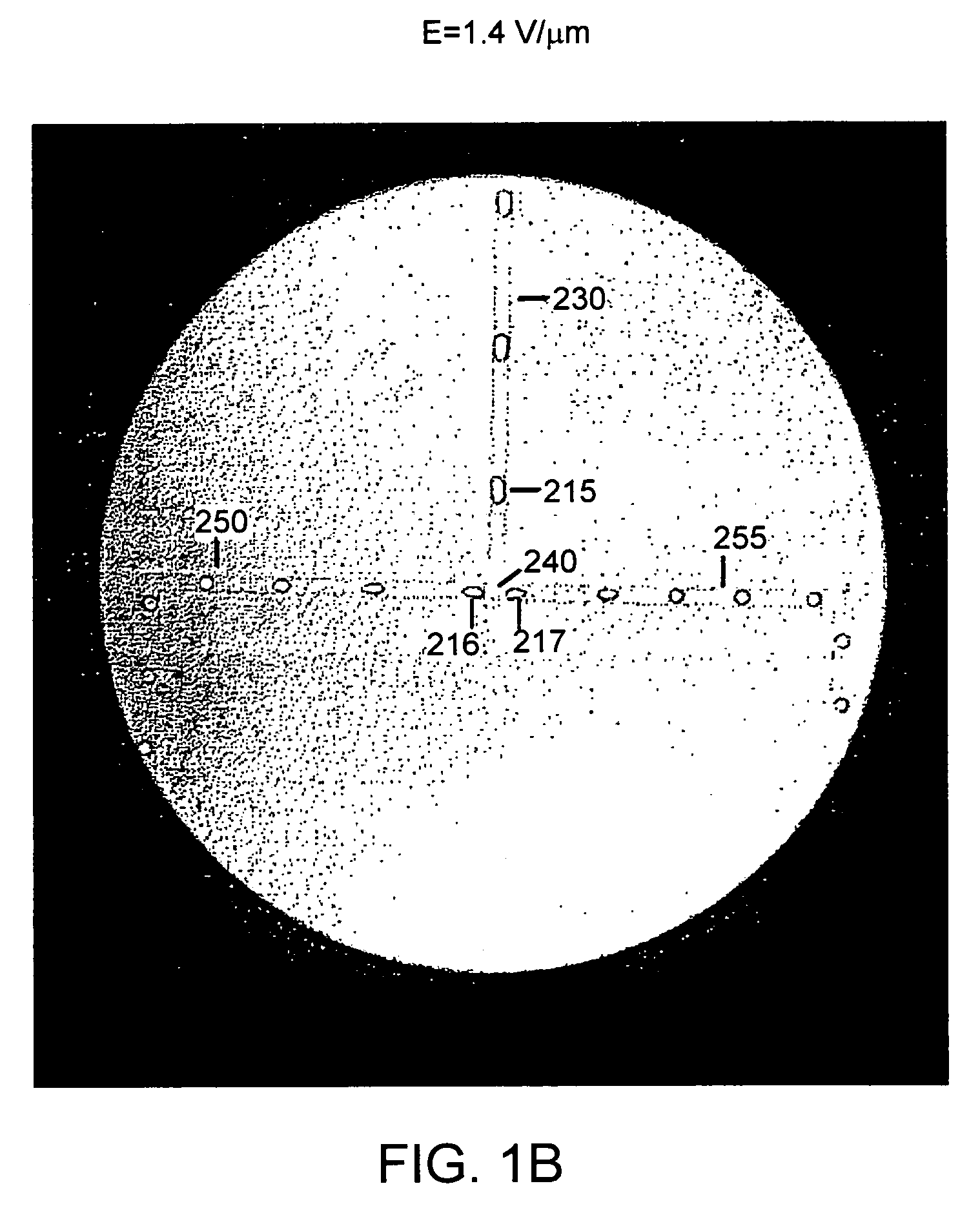
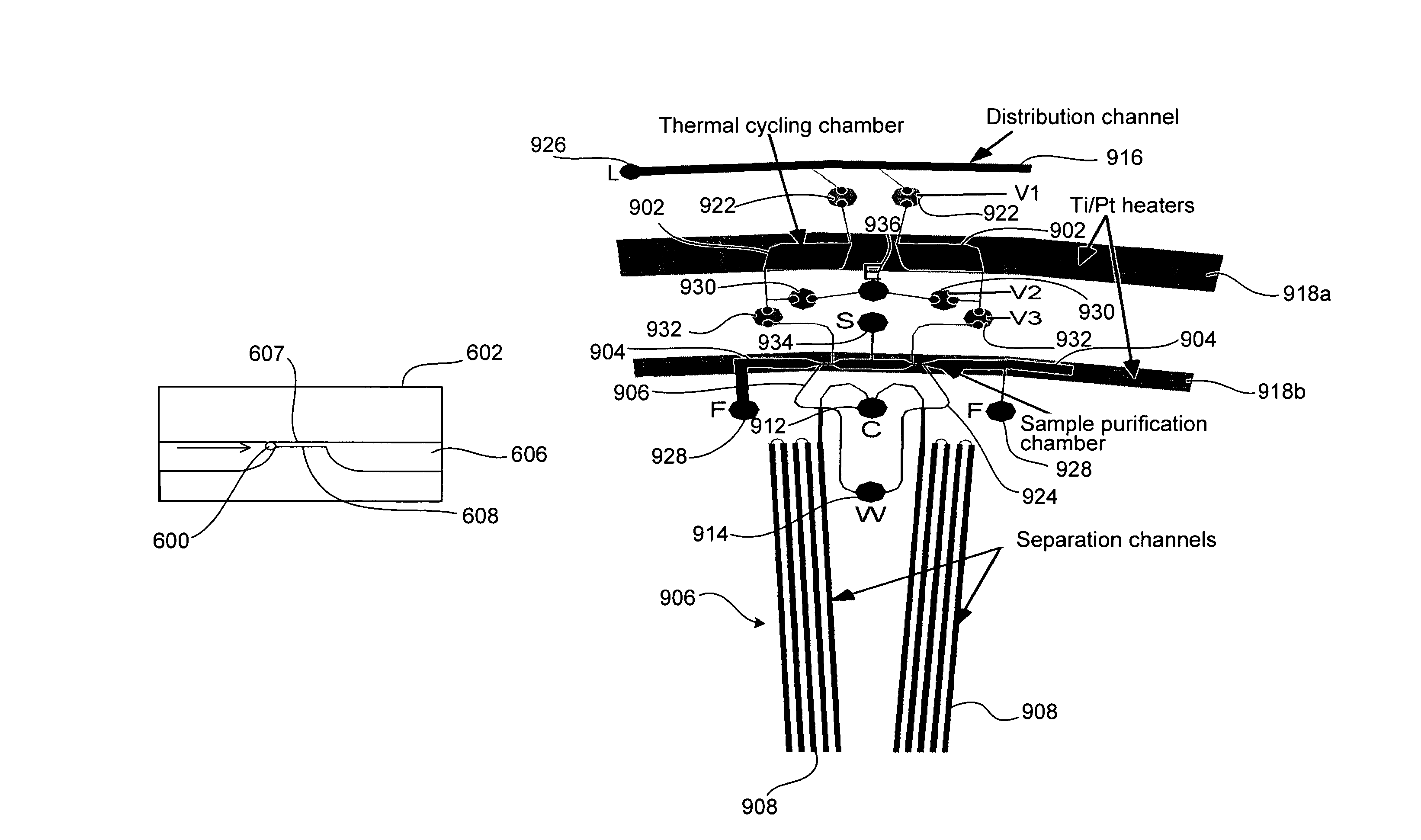
ActiveUS20050287572A1Improve automationBig spaceBioreactor/fermenter combinationsElectrolysis componentsMicroreactorMicrosphere
Methods and apparatus for genome analysis are provided. A microfabricated structure including a microfluidic distribution channel is configured to distribute microreactor elements having copies of a sequencing template into a plurality of microfabricated thermal cycling chambers. A microreactor element may include a microcarrier element carrying the multiple copies of the sequencing template. The microcarrier element may comprise a microsphere. An autovalve at an exit port of a thermal cycling chamber, an optical scanner, or a timing arrangement may be used to ensure that only one microsphere will flow into one thermal cycling chamber wherein thermal cycling extension fragments are produced. The extension products are captured, purified, and concentrated in an integrated oligonucleotide gel capture chamber. A microfabricated component separation apparatus is used to analyze the purified extension fragments. The microfabricated structure may be used in a process for performing sequencing and other genetic analysis of DNA or RNA.
Owner:RGT UNIV OF CALIFORNIA
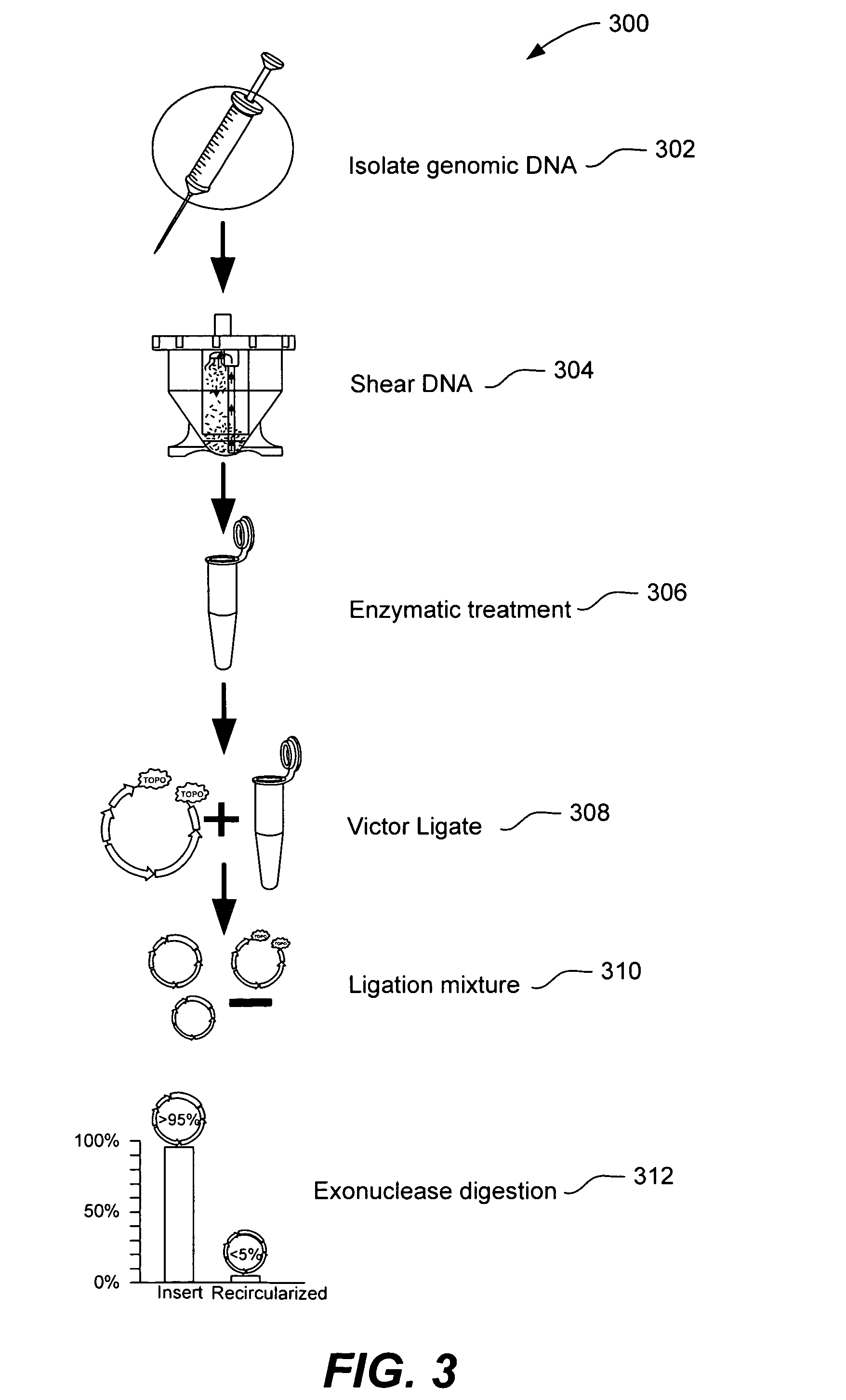
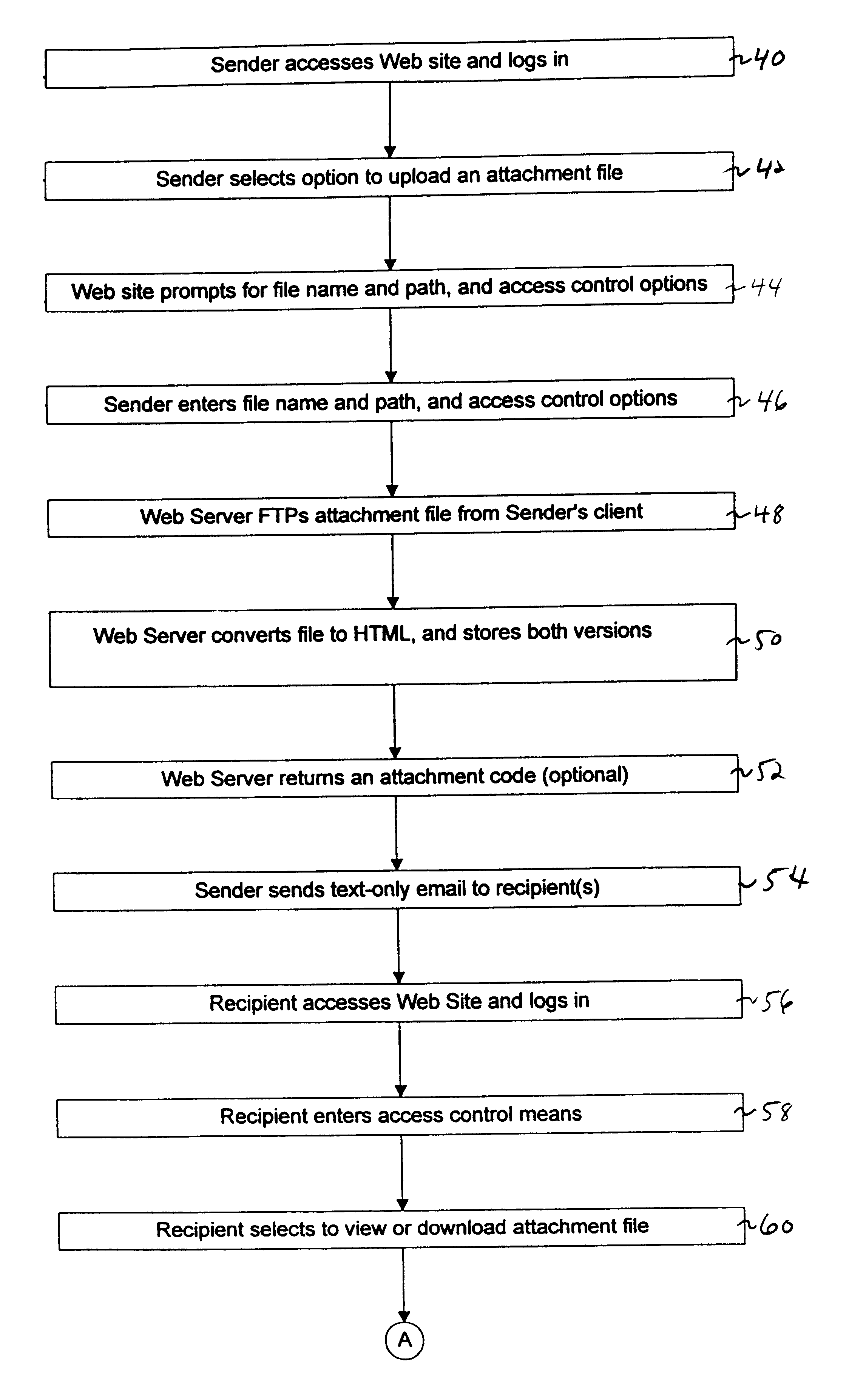
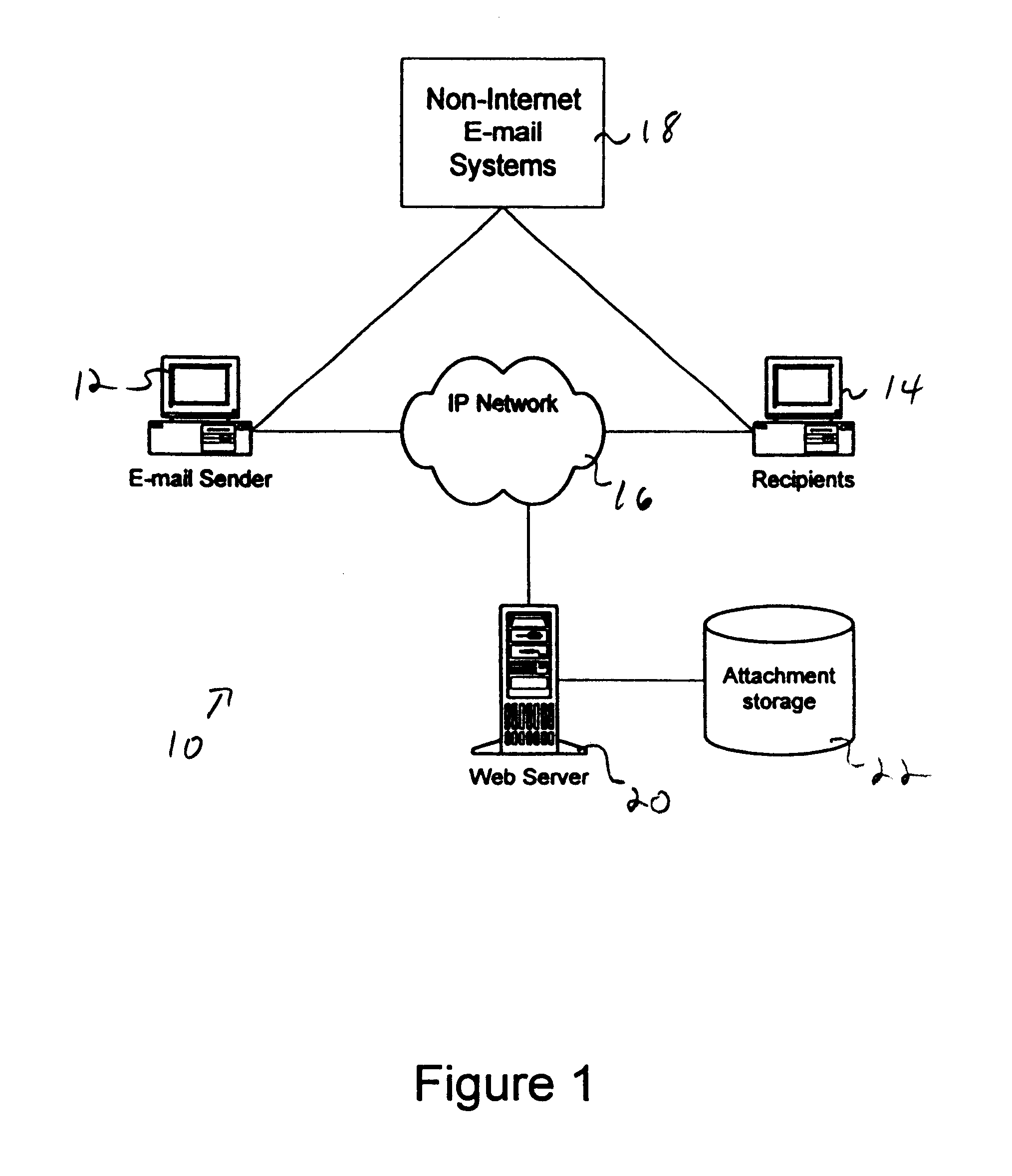
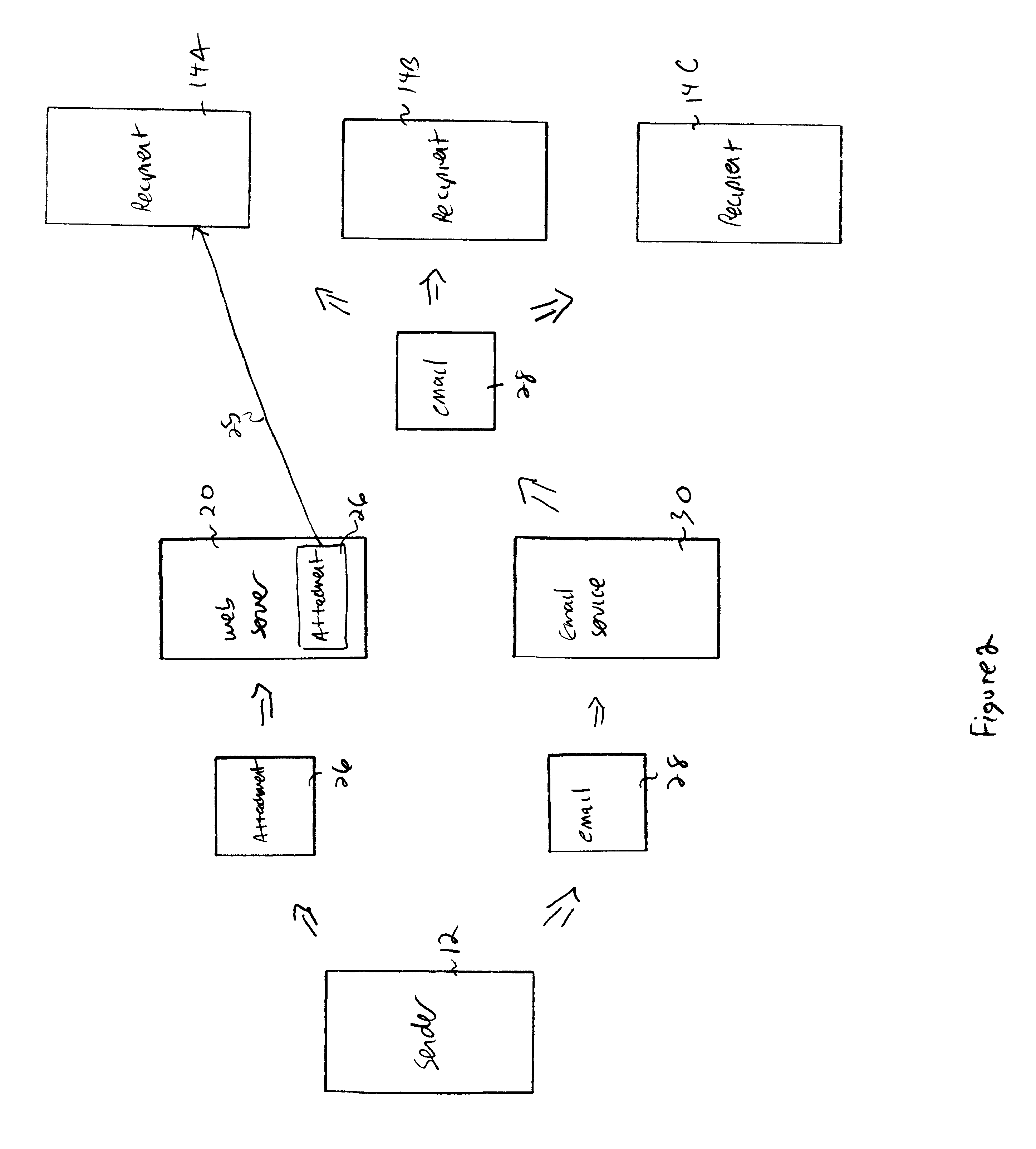
Facility for distributing and providing access to electronic mail message attachments
InactiveUS6839741B1Unauthorized memory use protectionMultiple digital computer combinationsEmail attachmentElectronic mail
A facility stores attachments for electronic mail messages so that the messages may be transmitted to the intended recipients without the attachments. The recipients may then review and / or download the attachments by contacting the facility. This facility is especially useful in instances wherein the attachments are large. The facility eliminates the need to store multiple copies of the attachment throughout a system; thus consuming a great deal of memory space. In addition, the facility prevents the recipient from extensive delays that are often associated with downloading email messages that contain large attachments via a dial-up connection with a low transmission rate. The facility may be realized as a server and may be a web server so as to provide access to the attachments via an IP network.
Owner:VERIZON PATENT & LICENSING INC
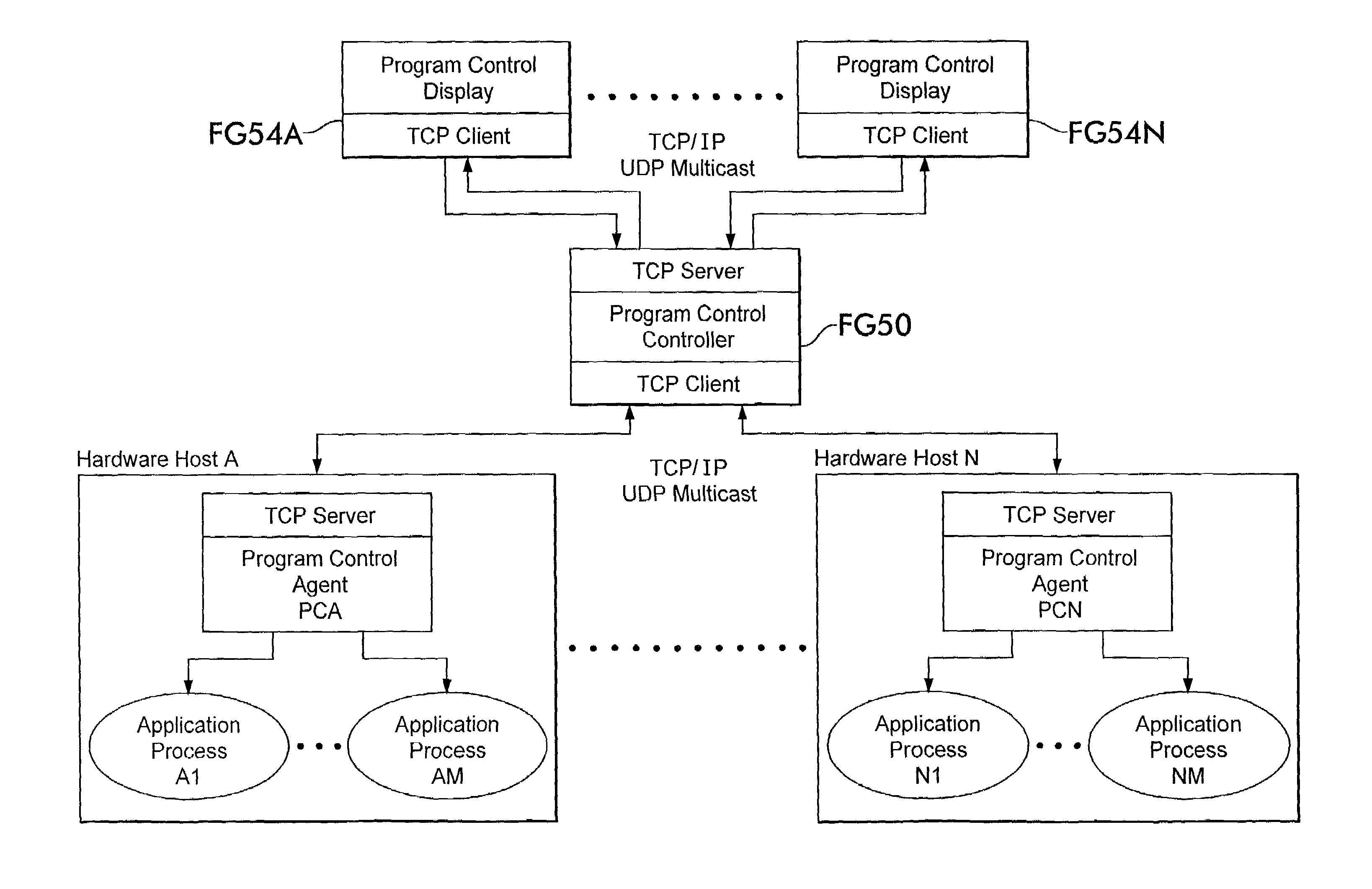
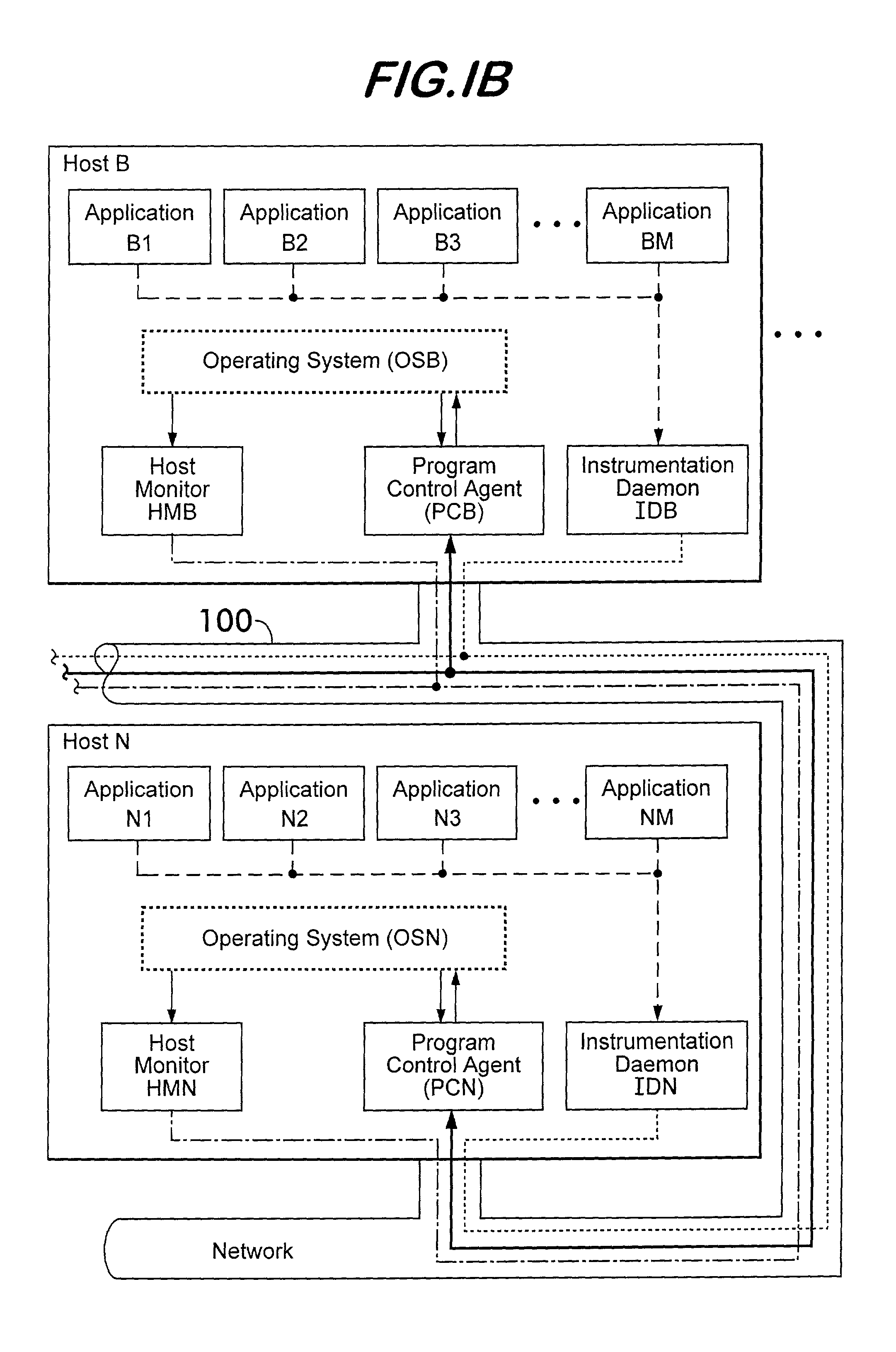
System for monitoring and reporting performance of hosts and applications and selectively configuring applications in a resource managed system
ActiveUS7051098B2Program initiation/switchingResource allocationResource Management SystemMonitoring system
A monitoring system for a distributed environment including a plurality of hosts capable of executing multiple copies of a scalable application includes a first device for generating first data corresponding to performance of all copies of the scalable application; a second device for generating second data corresponding to performance of all host in the distributed environment; and a third device for generating performance metrics based on the first and second data.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Compartmentalised screening by microfluidic control
InactiveUS20070092914A1Rapid and high-throughput screeningLow costCompound screeningSequential/parallel process reactionsCompound (substance)Drug development
The invention describes a method for the identification of compounds which bind to a target component of a biochemical system or modulate the activity of the target, comprising the steps of: a) compartmentalising the compounds into microcapsules together with the target, such that only a subset of the repertoire is represented in multiple copies in any one microcapsule; and b) identifying the compound which binds to or modulates the activity of the target; wherein at least one step is performed under microfluidic control. The invention enables the screening of large repertoires of molecules which can serve as leads for drug development.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE +1
Agrobacterium mediated transformation of moulds, in particular those belonging to the genus Aspergillus
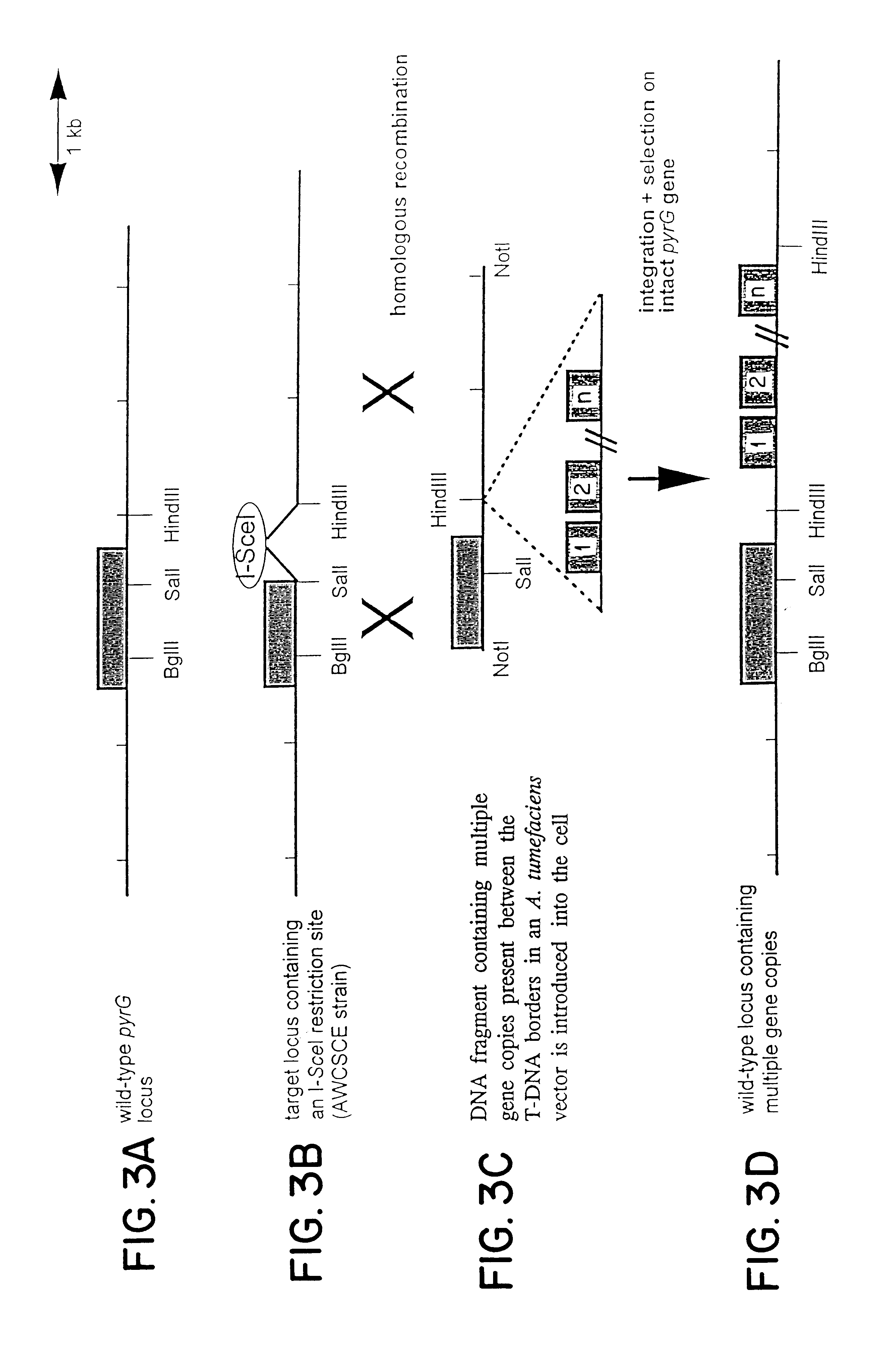
The invention relates to Agrobacterium mediated transformation of moulds comprising species of the fungal sub-divisions Ascomycotina, Basidiomycotina, Deuteromycotina, Mastigomycotina, and Zygomycotina.Examples demonstrate the transformation of Aspergillus awamori (both protoplasts and conidia), Aspergillus nidulans, Aspergillus niger, Colletotrichum gloeosporioides, Fusarium solani pisi, Neurospora crassa, Trichoderma reesei, Pleurotus ostreatus and Agaricus bisporus (all conidia), and Fusarium graminearum (both conidia and rehydrated freeze dried ATCC material).Especially for Aspergillus awamori the transformation frequency is much higher than with conventional mould transformation techniques.It has further been found that not only one expressable gene can be introduced into these moulds, but even multiple copies of such gene, which, moreover, can be targeted e.g. in the chromosomal pyrG locus, as exemplified for A. awamori. These multiple copies can be of a gene encoding a desired, homologous or heterologous, protein.
Owner:UNILEVER PATENT HLDG BV
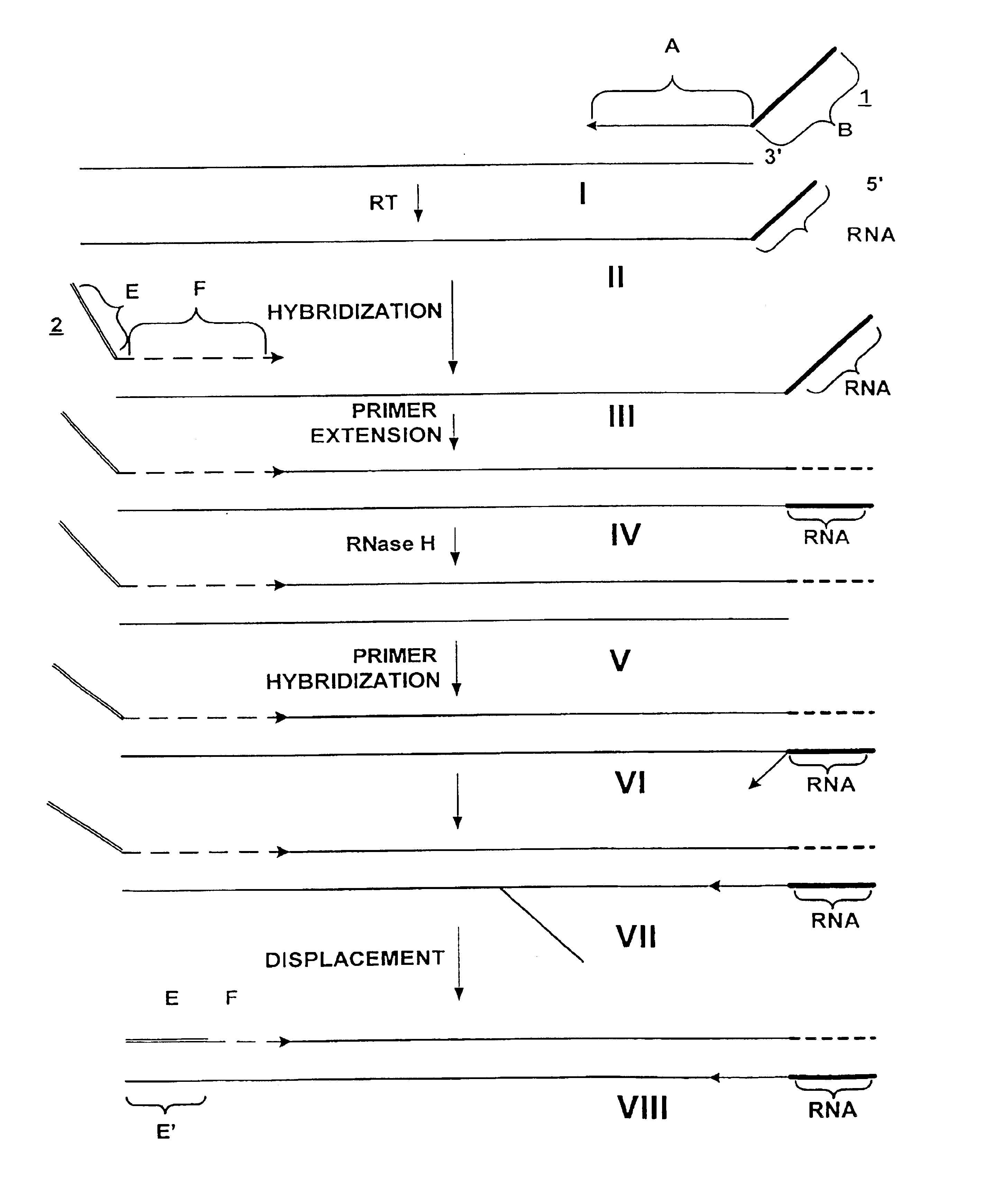
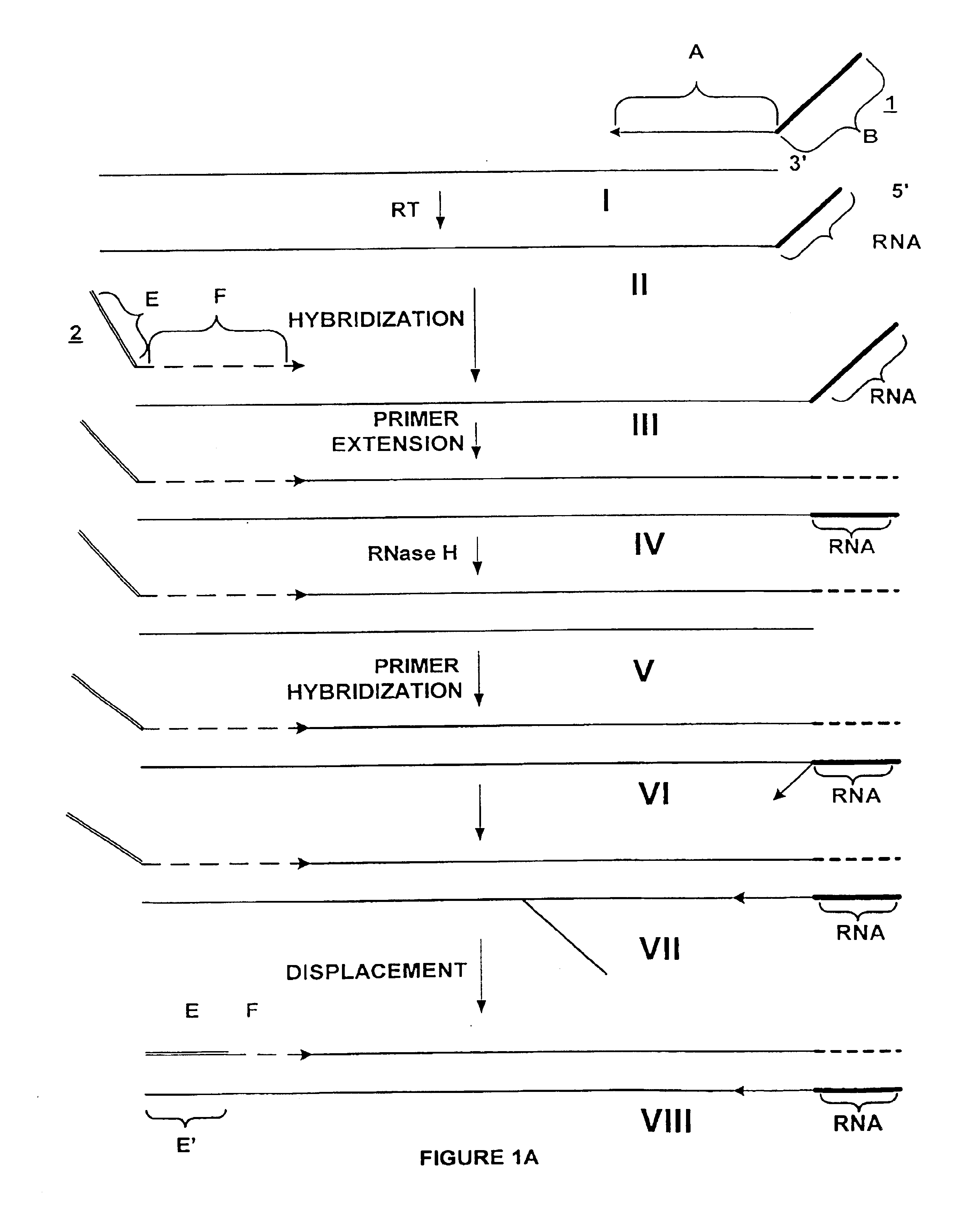
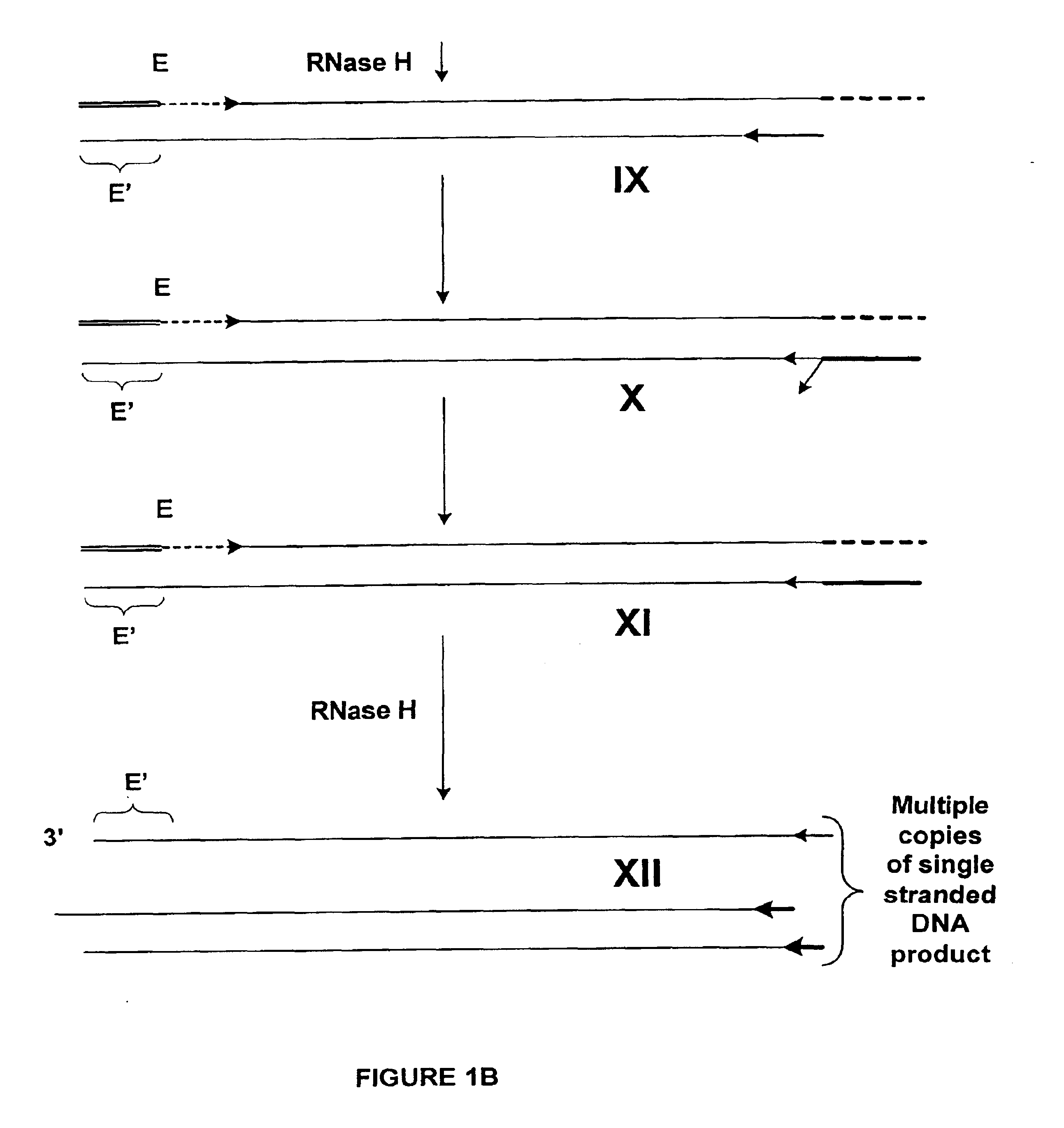
Methods and compositions for amplification of RNA sequences using RNA-DNA composite primers
InactiveUS6946251B2Improve automationHigh through-put proceduresSugar derivativesMicrobiological testing/measurementRNA SequenceDNA
Owner:NUGEN TECH
Selection by compartmentalised screening
ActiveUS20060153924A1Rapid and high-throughput screeningLow costMicroorganism librariesGranular deliveryDrug developmentBiochemistry
The invention describes a method for the identification of compounds which bind to a target component of a biochemical system or modulate the activity of the target, by compartmentalizing the compounds into microcapsules together with the target, such that only a subset of the repertoire is represented in multiple copies in any one microcapsules; and identifying the compound which binds to or modulates the activity of the target. The invention enables the screening of large repertoires of molecules which can serve as leads for drug development.
Owner:UK RES & INNOVATION LTD
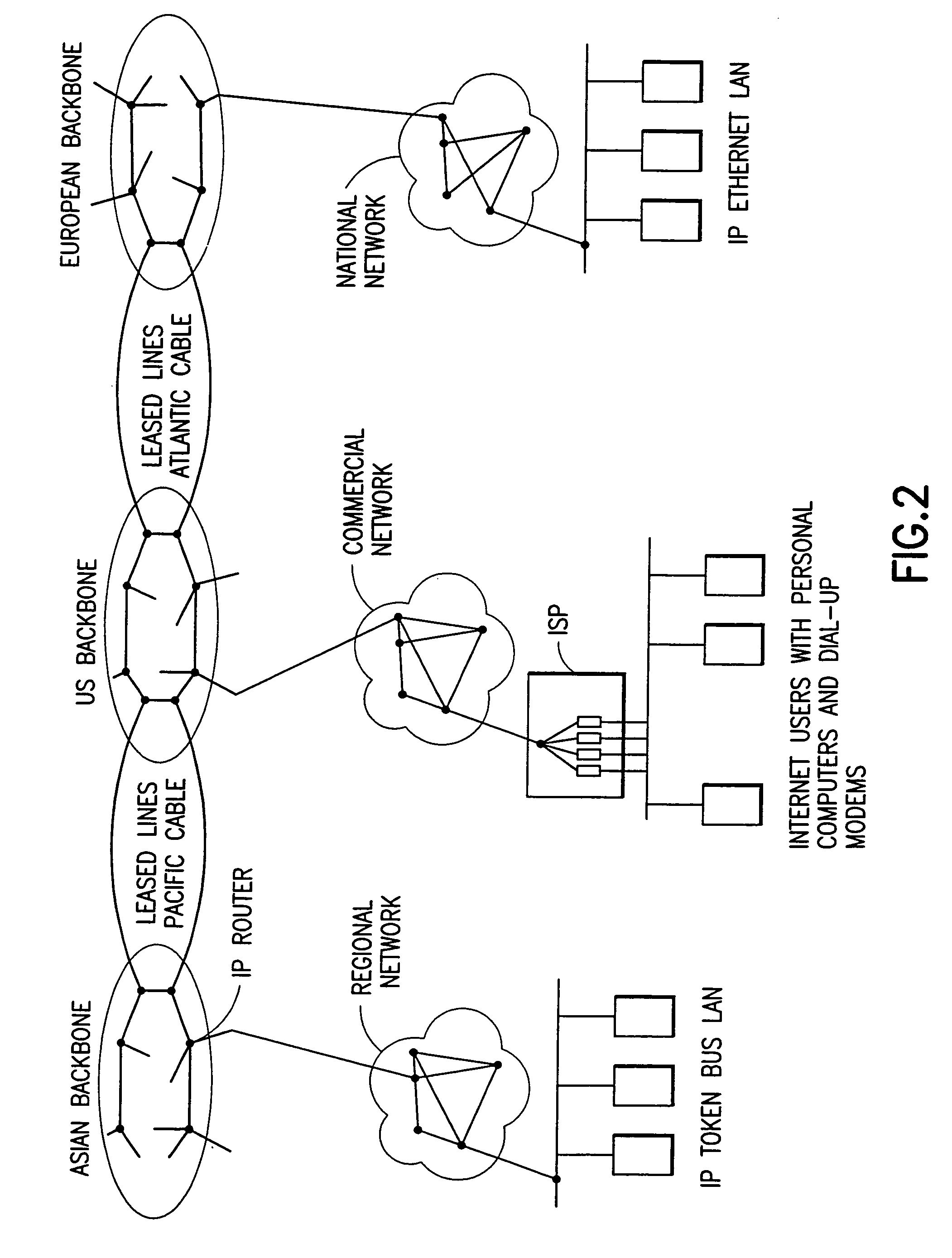
ISP system using non-geosynchronous orbit satellites
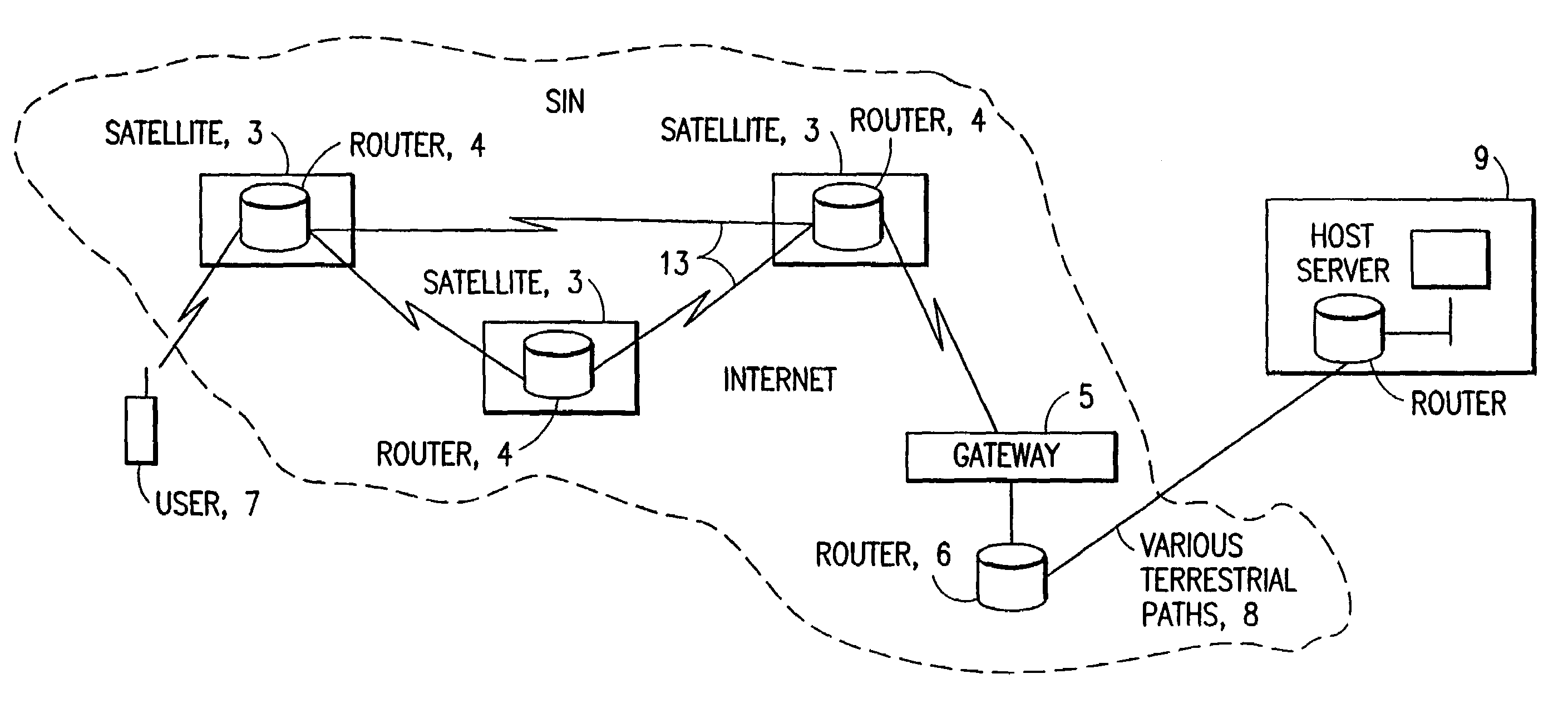
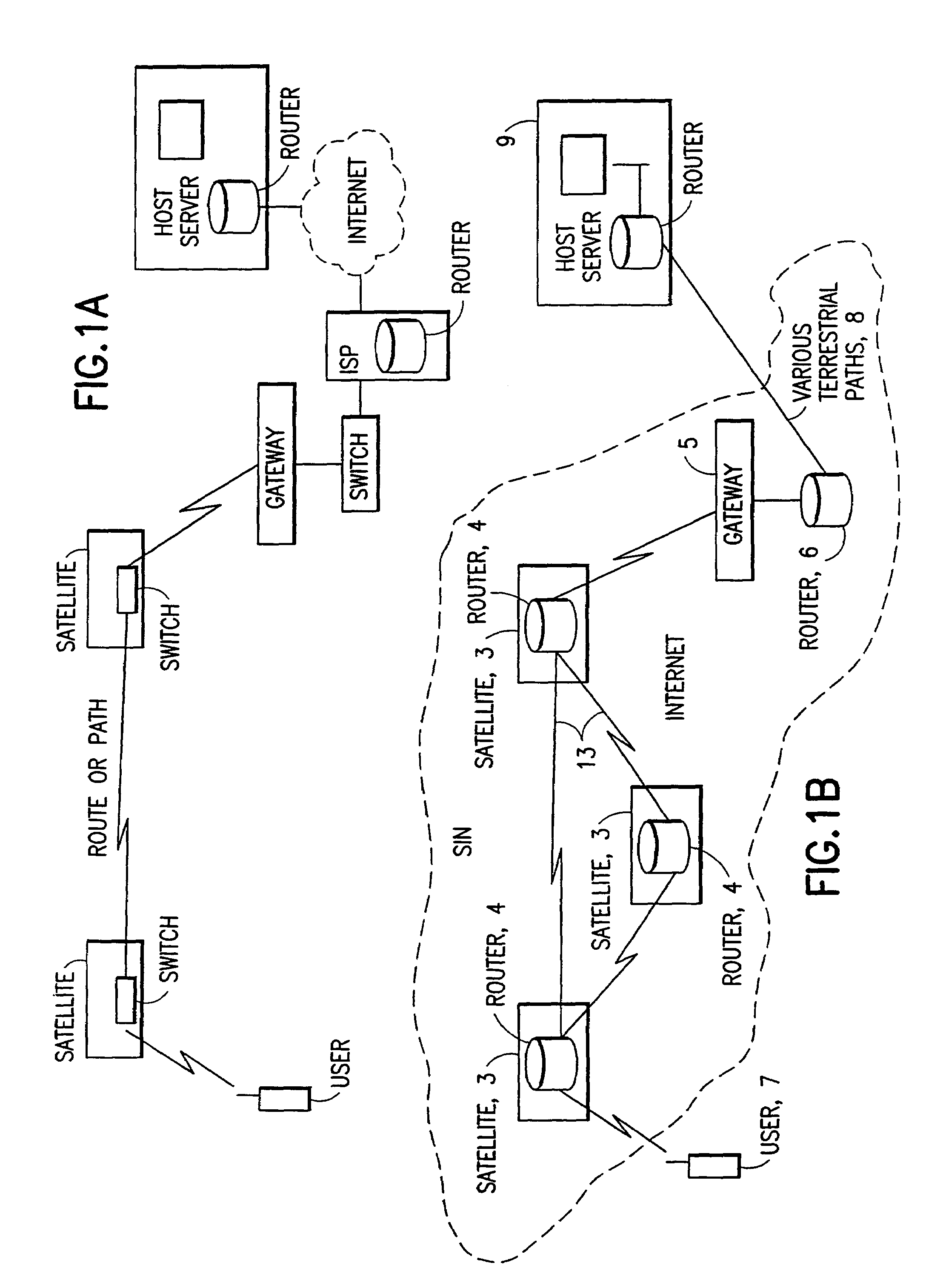
A satellite communication system includes a plurality of satellites, such as low earth orbit satellites, and a plurality of gateways. The satellite communication system is bidirectionally coupled to a terrestrial communication system through at least the plurality of gateways. The satellite communication system and the terrestrial communications system together form a data communication network having a plurality of nodes including source nodes, destination nodes and intermediate nodes. Multiple copies of a packet can coexist within the data communication network, and the packet and its one or more copies are routed, using at least in part satellite-resident routers and gateway-resident routers, over a plurality of different paths between a particular source node and a particular destination node. At least one duplicate copy of a given packet is simply not used during the execution of a packet reordering procedure in the destination node, or at an intermediate node. Certain of the paths are carried over satellite-to-satellite cross-links, while certain other ones of the paths are carried over satellite-to-gateway uplinks and downlinks, and at least one path exists between a user terminal and at least one satellite. In a preferred embodiment the packets are TCP / IP (or equivalent protocol) packets containing information for enabling the selective destruction of a duplicate packet to occur.
Owner:GLOBALSTAR INC
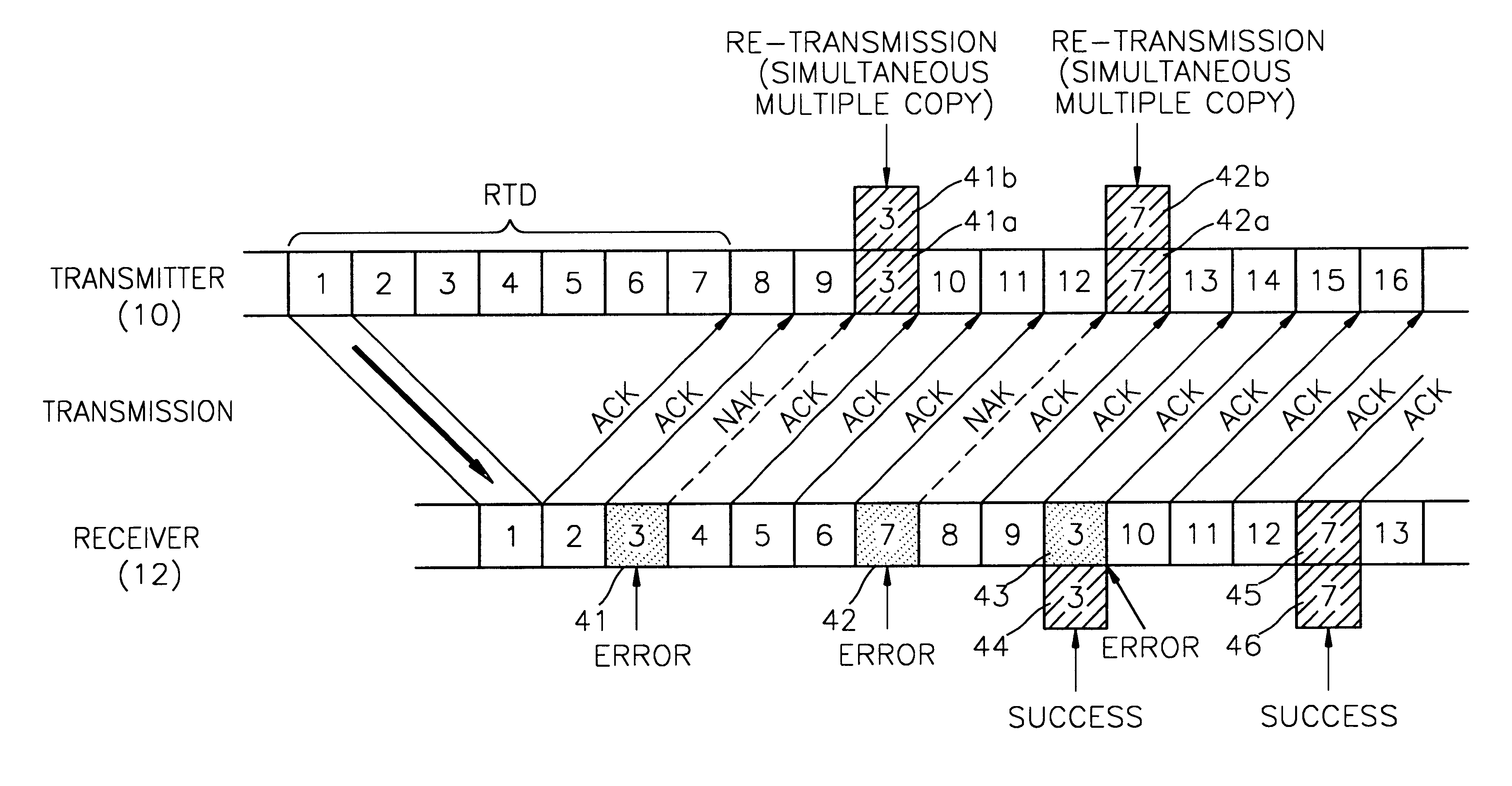
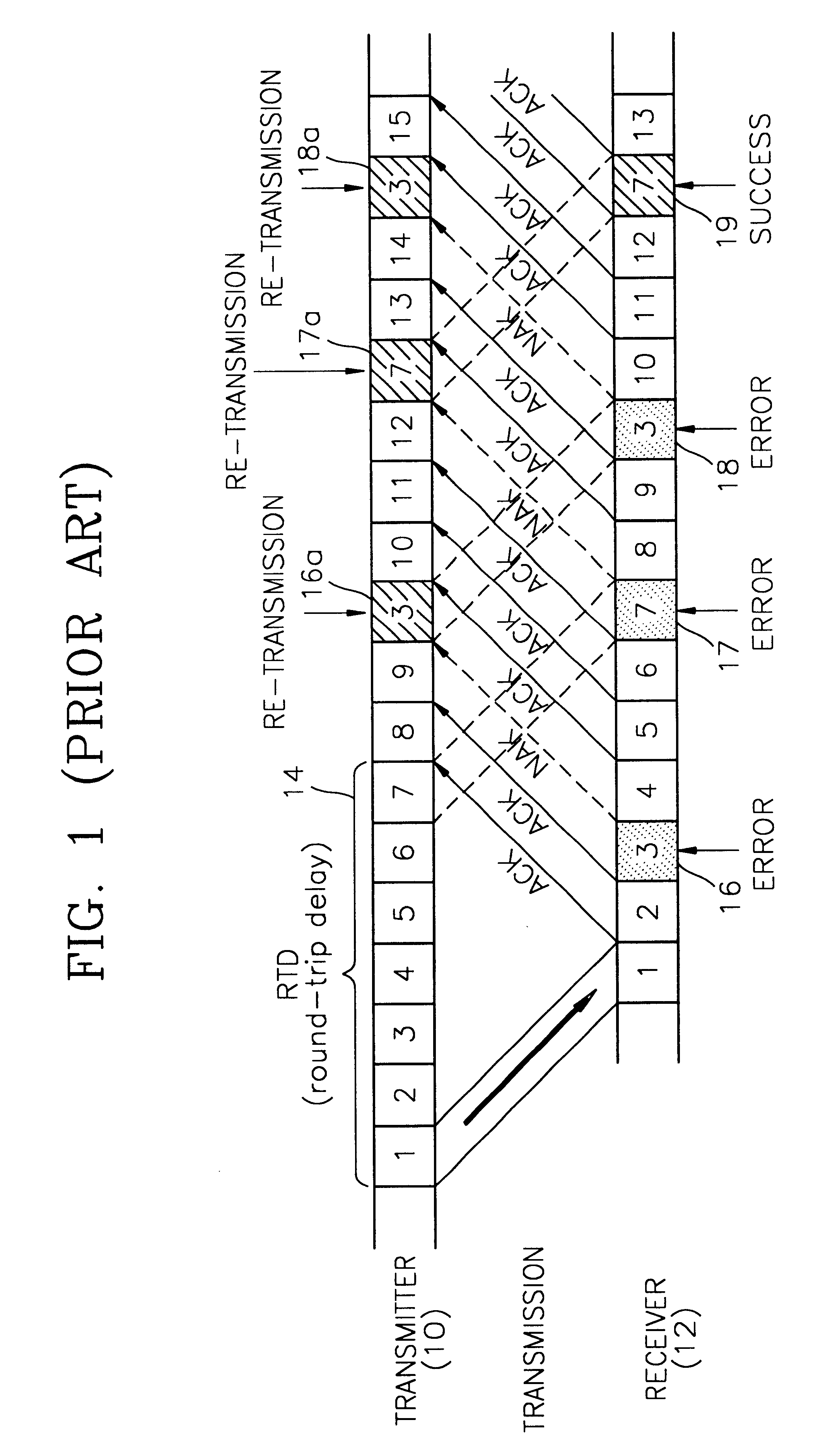
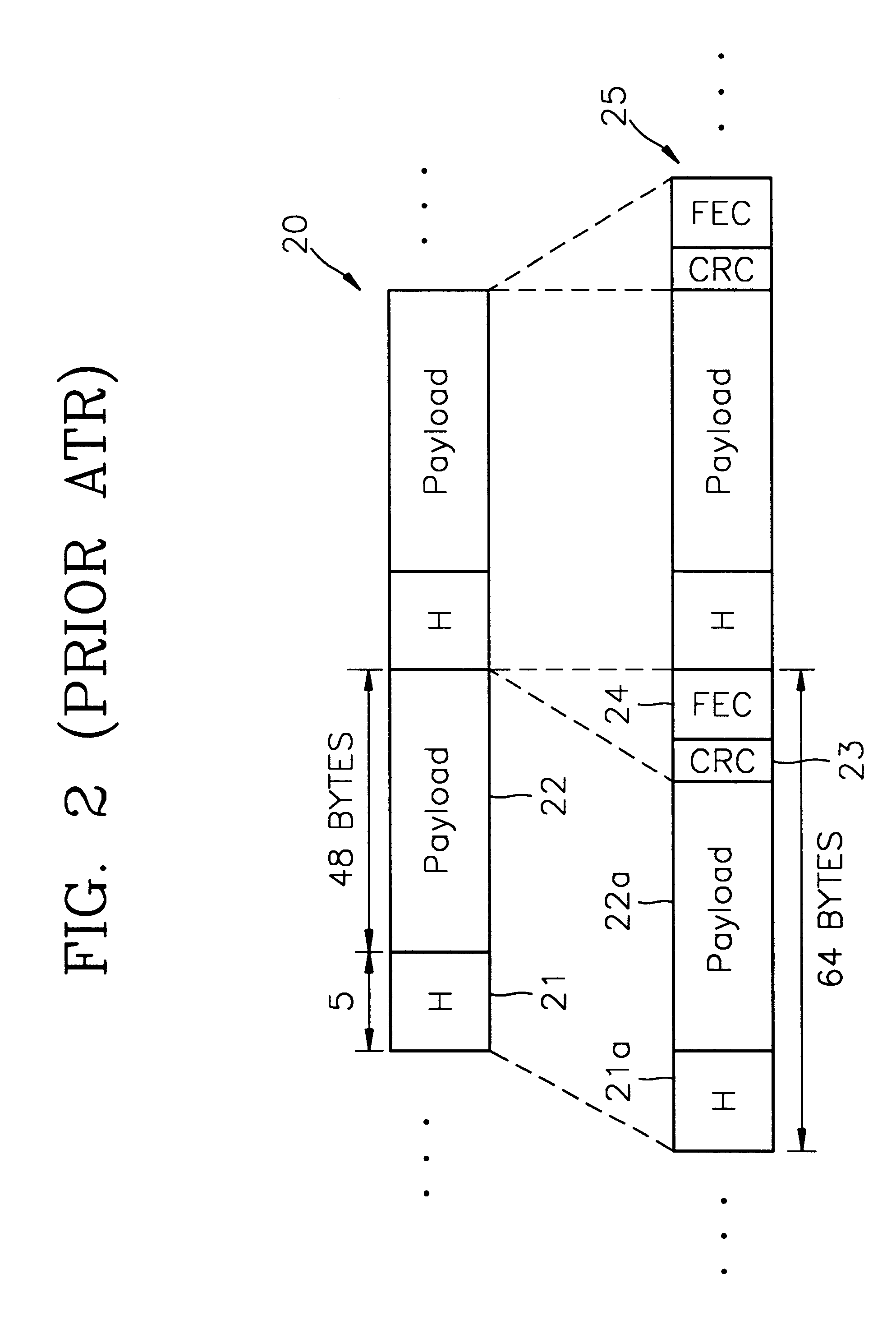
Method for controlling errors in link layer in wideband wireless communication and computer readable media therefor
InactiveUS6615382B1Error prevention/detection by using return channelTransmission systemsDelayed timeData link layer
A method for controlling errors in a wireless link layer using a simultaneous multiple copy scheme and an adaptive forward error correction (FEC) scheme in a wideband wireless communication is provided. The method for controlling errors in a link layer in wideband wireless communication using an automatic repeat request (ARQ) scheme, in which a wideband wireless channel is used for communication between a first node and a second node, includes the steps of (a) estimating the error ratio of a forward (a direction in which a cell is transmitted from the first node to the second node) channel using the state of a backward (a direction in which a cell is transmitted from the second node to the first node) channel, and transmitting a cell, in which a forward error correction (FEC) code having an encoding ratio that varies depending on the estimated error ratio is included in a protocol data unit (PDU) of a wireless link layer, through the forward channel and (b) re-transmitting the copy of a cell transmitted in the step (a), when feedback information that indicates that an error exists in the cell transmitted in the step (a) is received through the backward channel. It is possible to reduce the number of times of re-transmission by improving the probability of correcting forward errors using more error controlling bits as the state of the channel is worse and to minimize the waste of resources using less error controlling bits as the state of the channel is better, to thus obtain the optimal performance and guarantee the minimum delay time.
Owner:SAMSUNG ELECTRONICS CO LTD
Microfabricated integrated DNA analysis system
ActiveUS7799553B2Improve automationBig spaceBioreactor/fermenter combinationsElectrolysis componentsMicroreactorMicrosphere
Methods and apparatus for genome analysis are provided. A microfabricated structure including a microfluidic distribution channel is configured to distribute microreactor elements having copies of a sequencing template into a plurality of microfabricated thermal cycling chambers. A microreactor element may include a microcarrier element carrying the multiple copies of the sequencing template. The microcarrier element may comprise a microsphere. An autovalve at an exit port of a thermal cycling chamber, an optical scanner, or a timing arrangement may be used to ensure that only one microsphere will flow into one thermal cycling chamber wherein thermal cycling extension fragments are produced. The extension products are captured, purified, and concentrated in an integrated oligonucleotide gel capture chamber. A microfabricated component separation apparatus is used to analyze the purified extension fragments. The microfabricated structure may be used in a process for performing sequencing and other genetic analysis of DNA or RNA.
Owner:RGT UNIV OF CALIFORNIA
Selection by compartmentalised screening
InactiveUS20120010098A1Rapid and high-throughput screeningLow costLibrary screeningFluorescence/phosphorescenceDrug developmentBiochemistry
Owner:MEDICAL RESEARCH COUNCIL
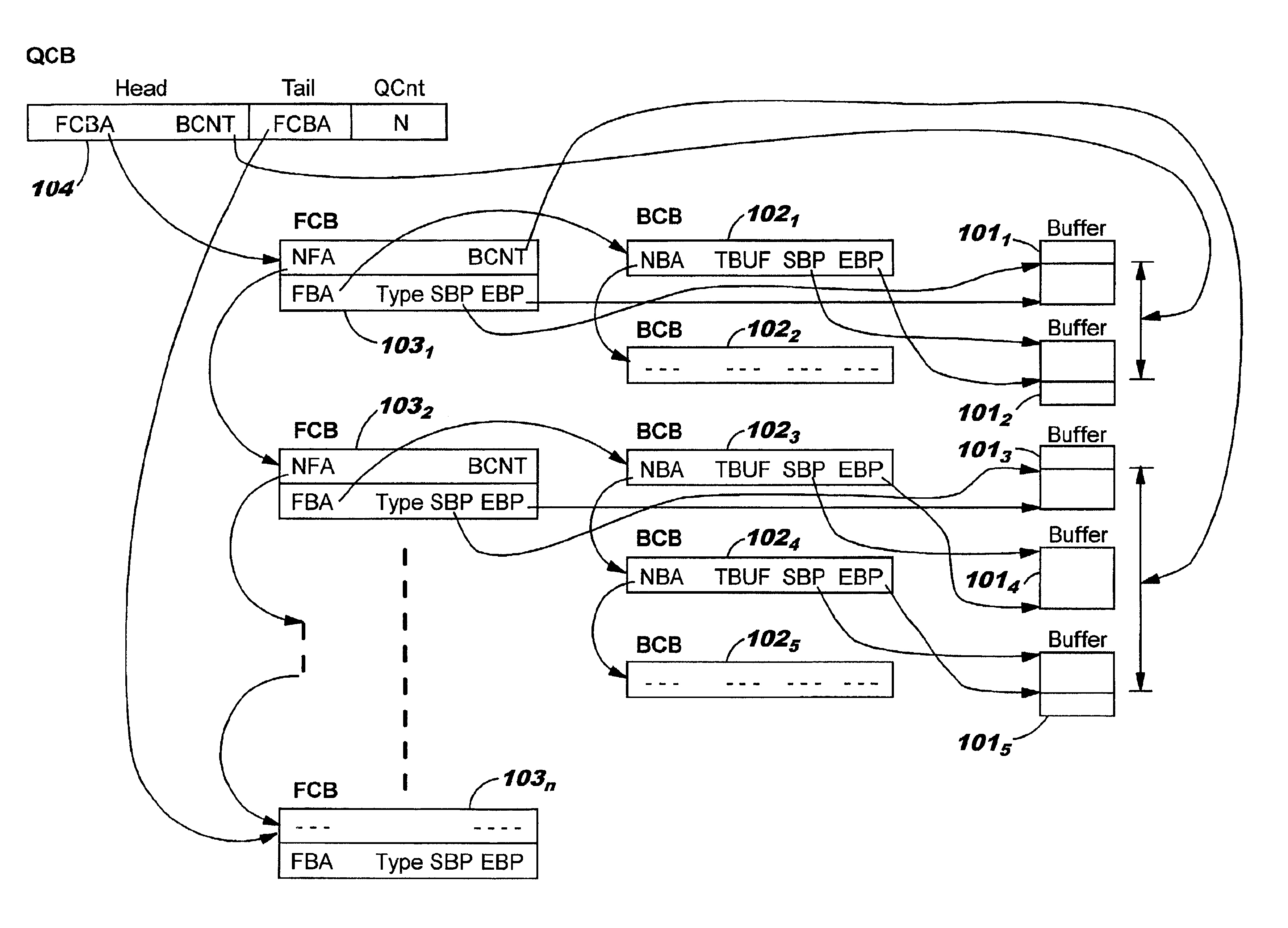
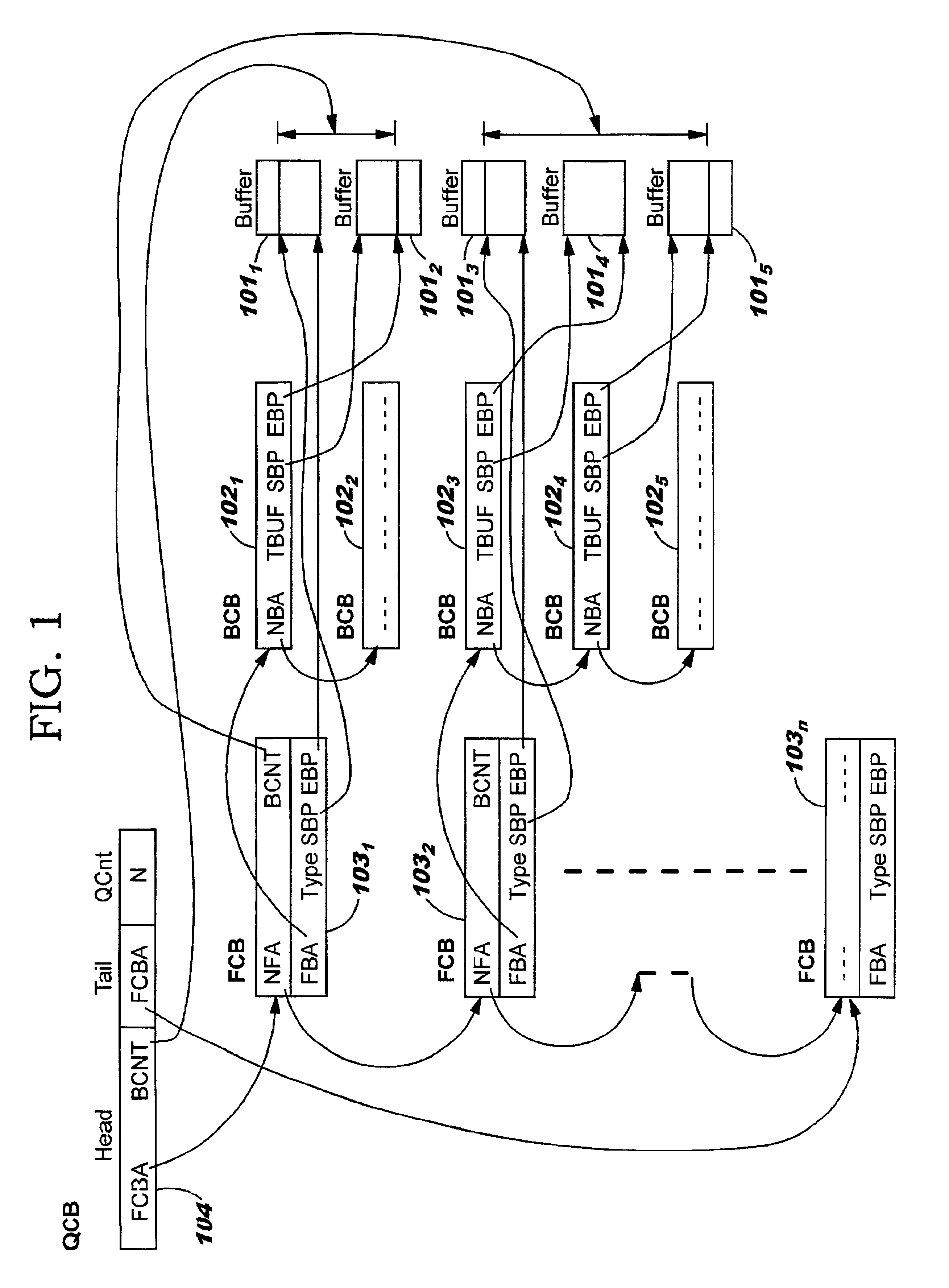
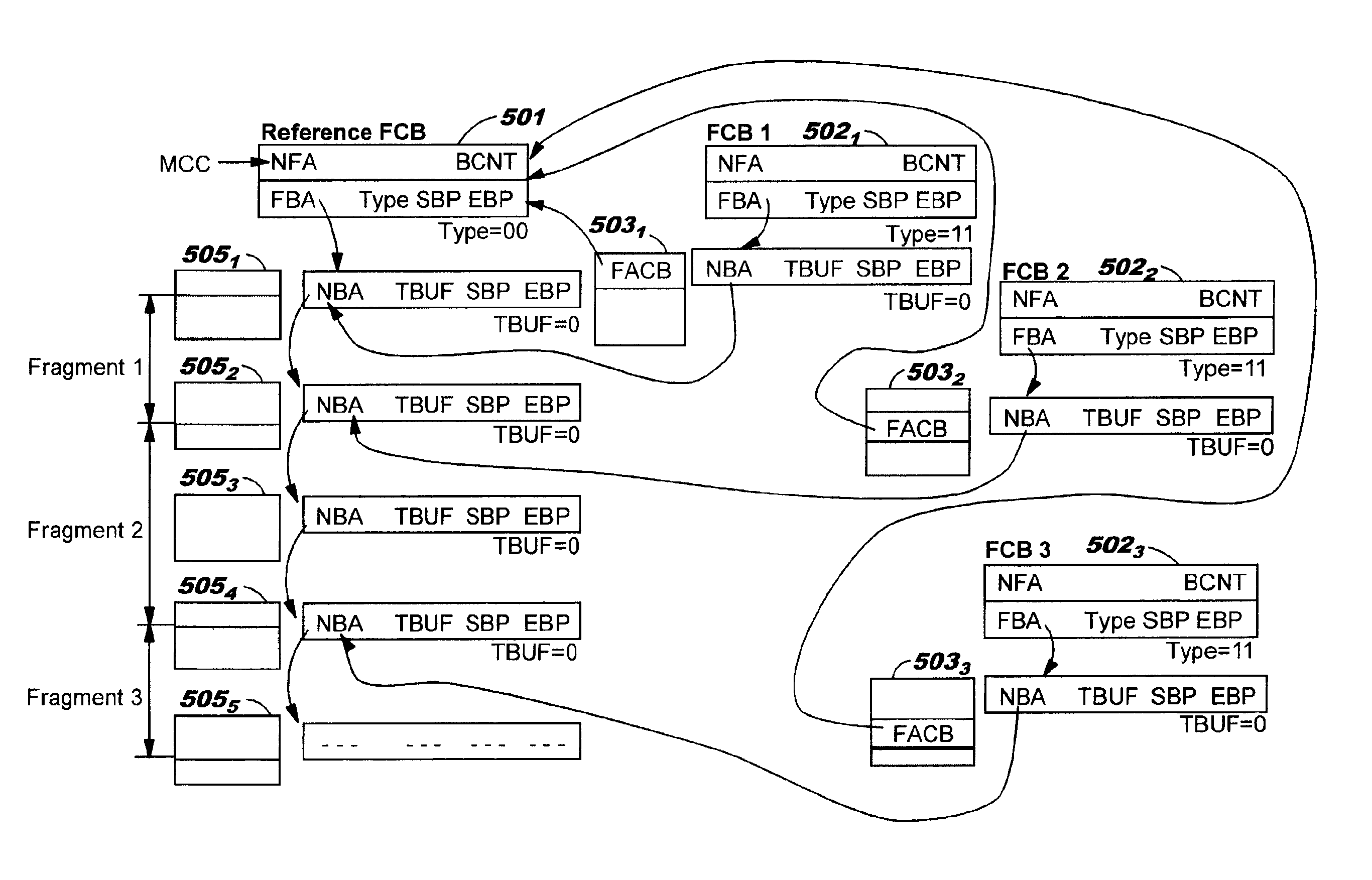
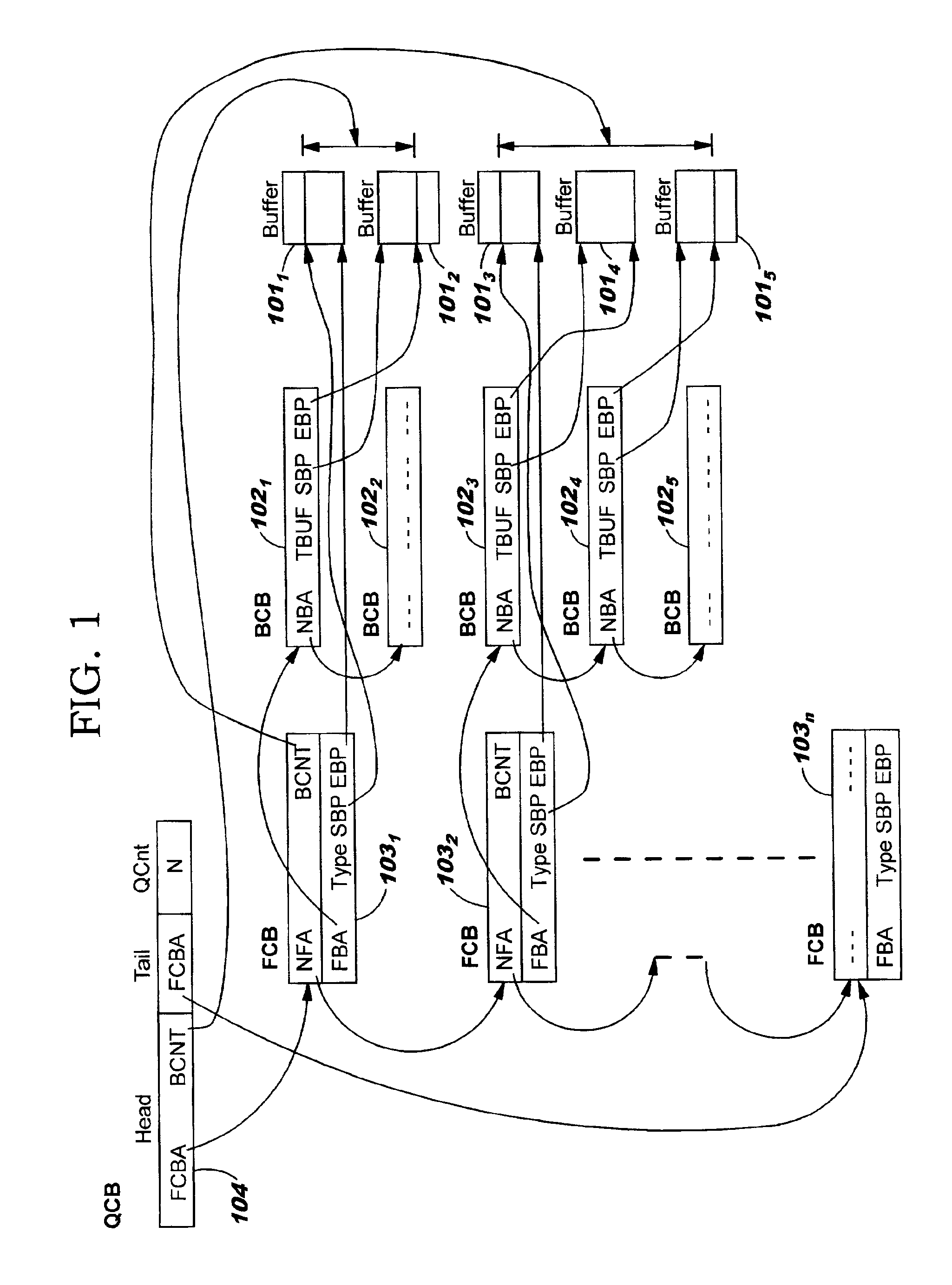
Data structures for efficient processing of multicast transmissions
InactiveUS6836480B2Reduce memory requirementsEliminate needSpecial service provision for substationTime-division multiplexArray data structureTransport system
Data structures, a method, and an associated transmission system for multicast transmission on network processors in order both to minimize multicast transmission memory requirements and to account for port performance discrepancies. Frame data for multicast transmission on a network processor is read into buffers to which are associated various control structures and a reference frame. The reference frame and the associated control structures permit multicast targets to be serviced without creating multiple copies of the frame. Furthermore this same reference frame and control structures allow buffers allocated for each multicast target to be returned to the free buffer queue without waiting until all multicast transmissions are complete.
Owner:ACTIVISION PUBLISHING
Selection by compartmentalised screening
ActiveUS20120010107A1Rapid and high-throughput screeningLow costNucleotide librariesFluorescence/phosphorescenceDrug developmentBiochemistry
The invention describes a method for the identification of compounds which bind to a target component of a biochemical system or modulate the activity of the target, by compartmentalizing the compounds into microcapsules together with the target, such that only a subset of the repertoire is represented in multiple copies in any one microcapsules; and identifying the compound which binds to or modulates the activity of the target. The invention enables the screening of large repertoires of molecules which can serve as leads for drug development.
Owner:UK RES & INNOVATION LTD
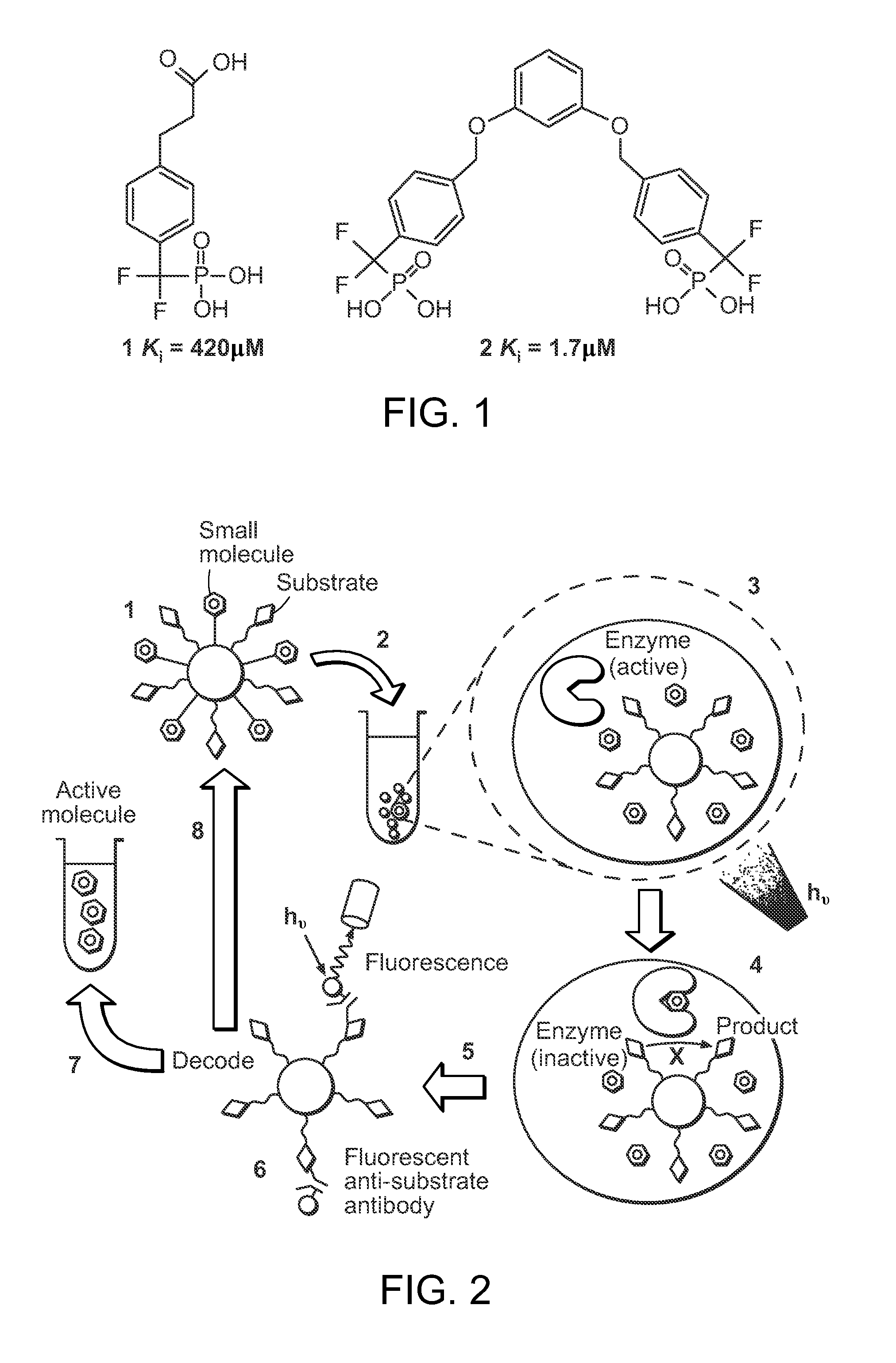
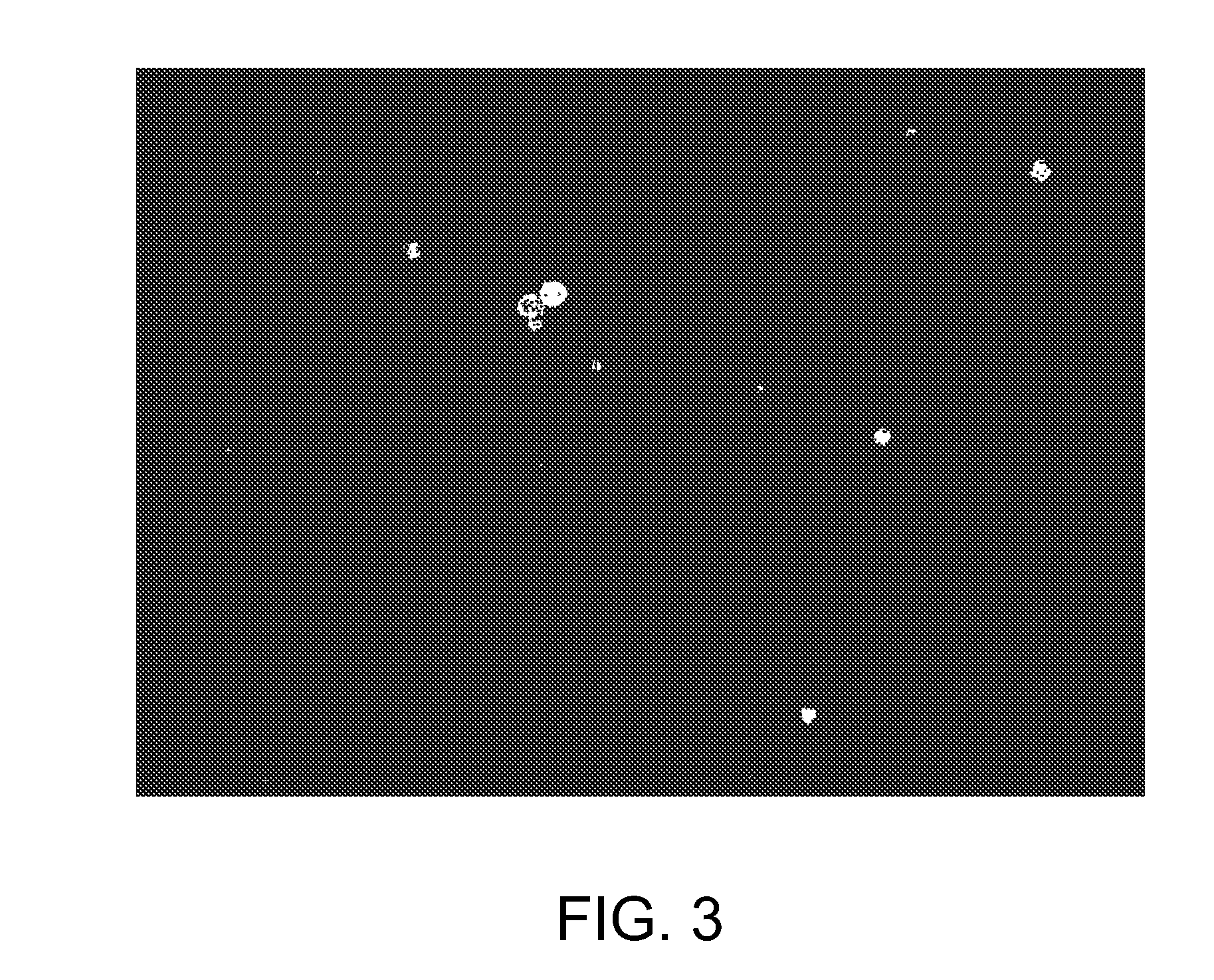
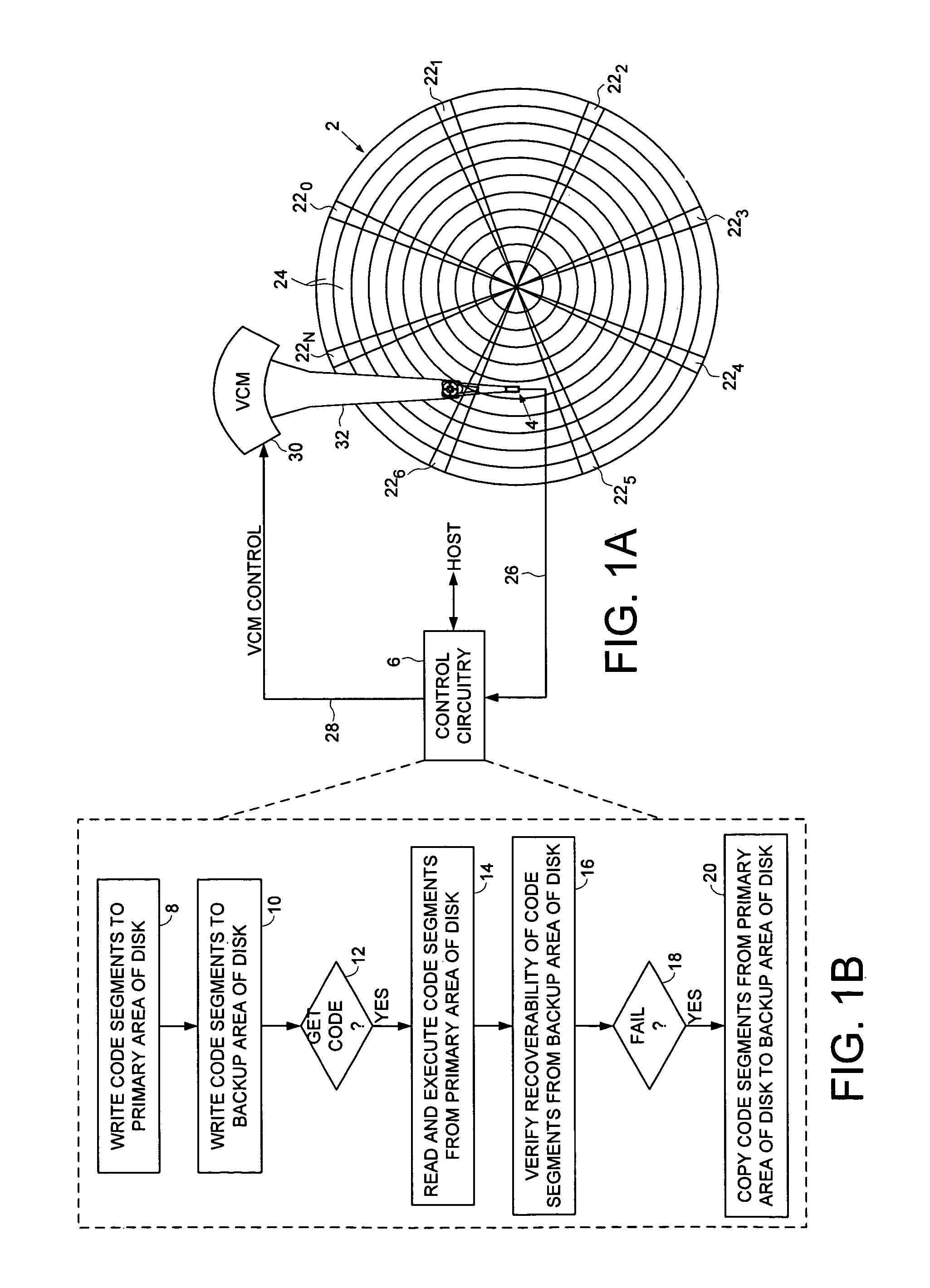
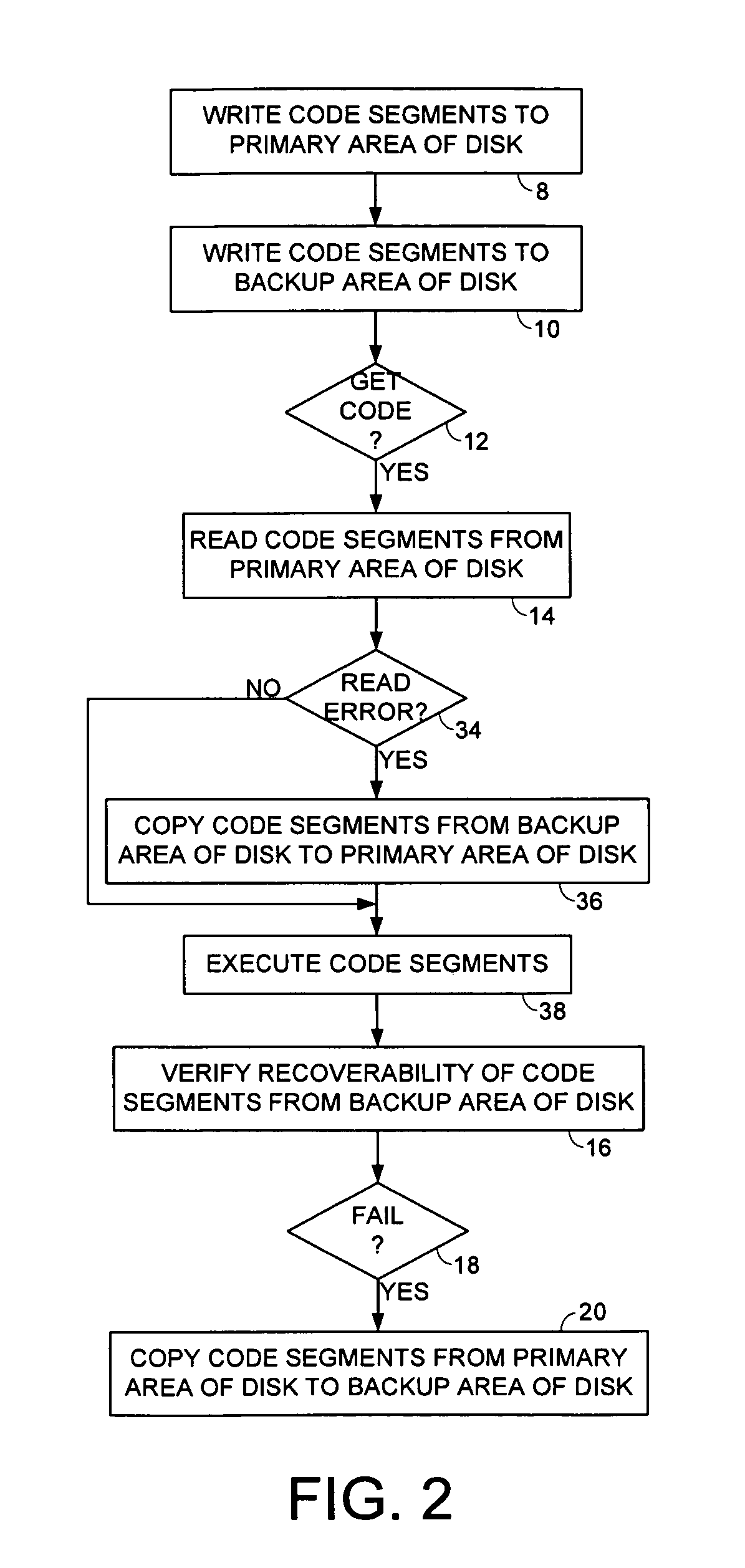
Disk drive maintaining multiple copies of code segments
InactiveUS8190575B1Digital data processing detailsRecord information storageControl circuitCode segment
Owner:WESTERN DIGITAL TECH INC
Storage system with multiple copy targeting
InactiveUS7386695B2Input/output to record carriersMemory loss protectionControl storeComputer science
A storage controller, cooperable with host computer apparatus, and a plurality of controlled storage apparatus, comprises a host write component operable to write a data object to a source data image at one of the plurality of controlled storage apparatus; a first copy component responsive to a first metadata state and operable to control copying of the data object to a first target data image at one of the plurality of controlled storage apparatus; a second copy component responsive to a second metadata state and operable to perform one of: controlling copying of the data object to a second target data image at one of the plurality of controlled storage apparatus; and causing the first copy component to perform copying of the second target data image to the first target data image.
Owner:IBM CORP
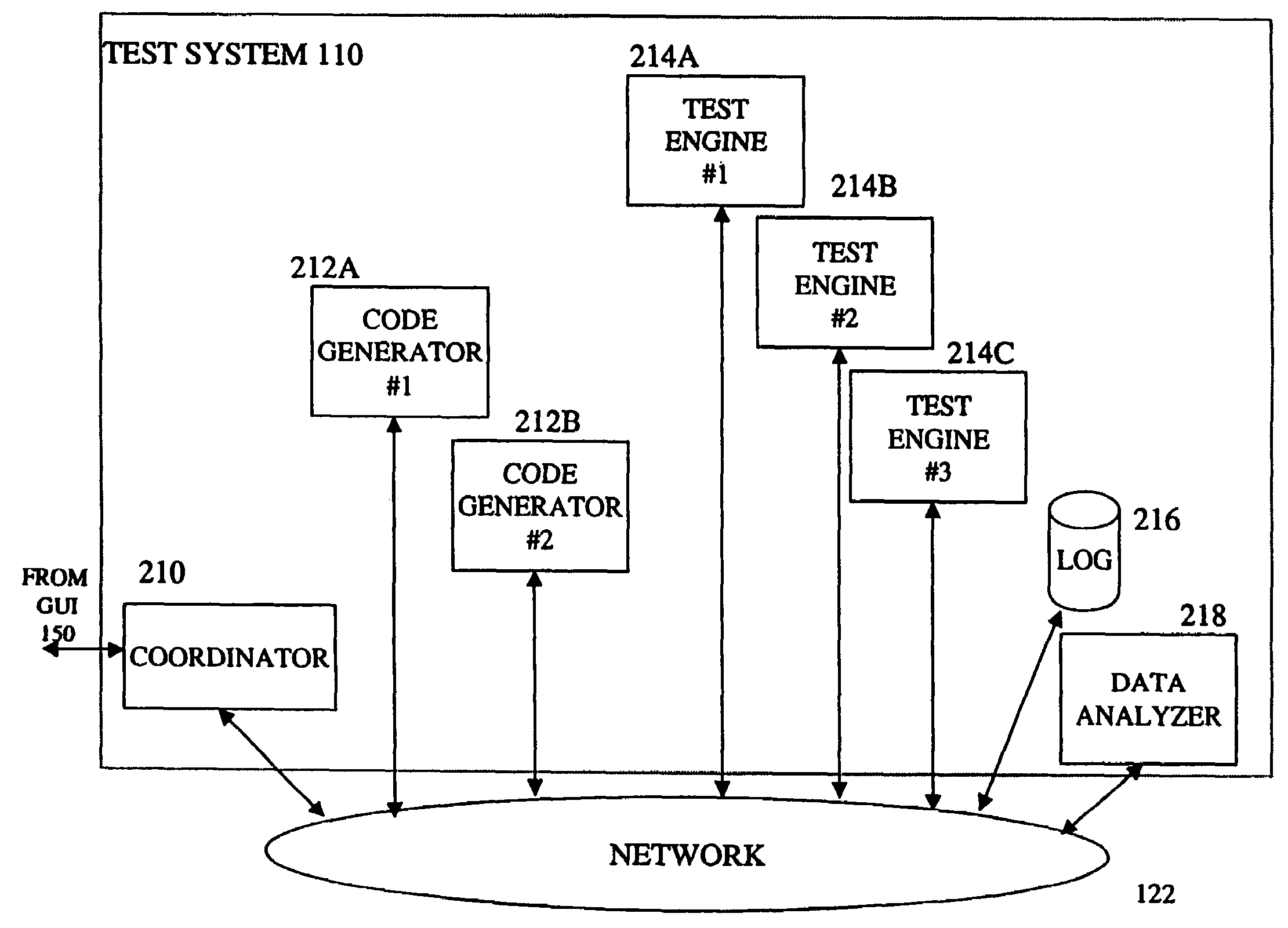
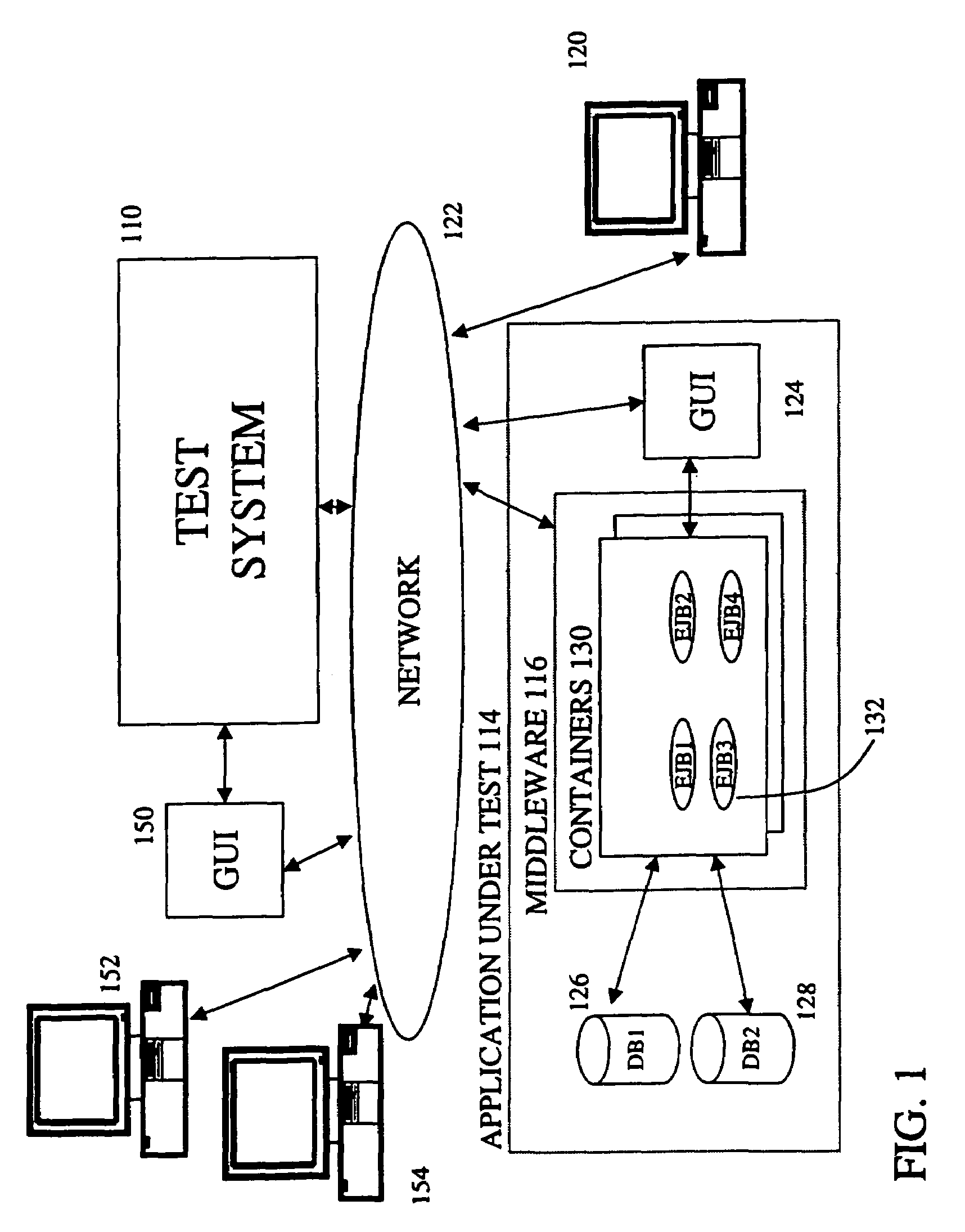
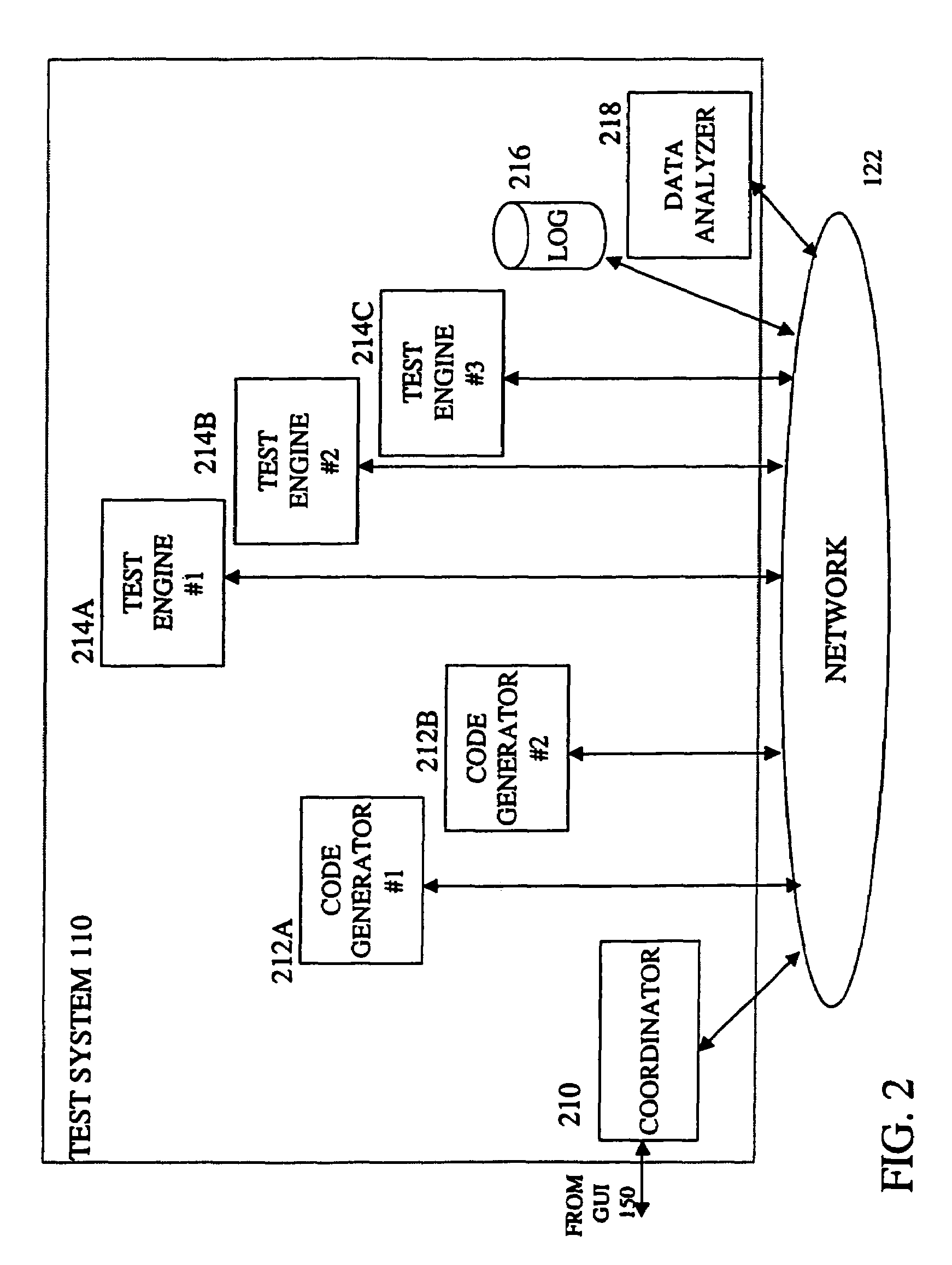
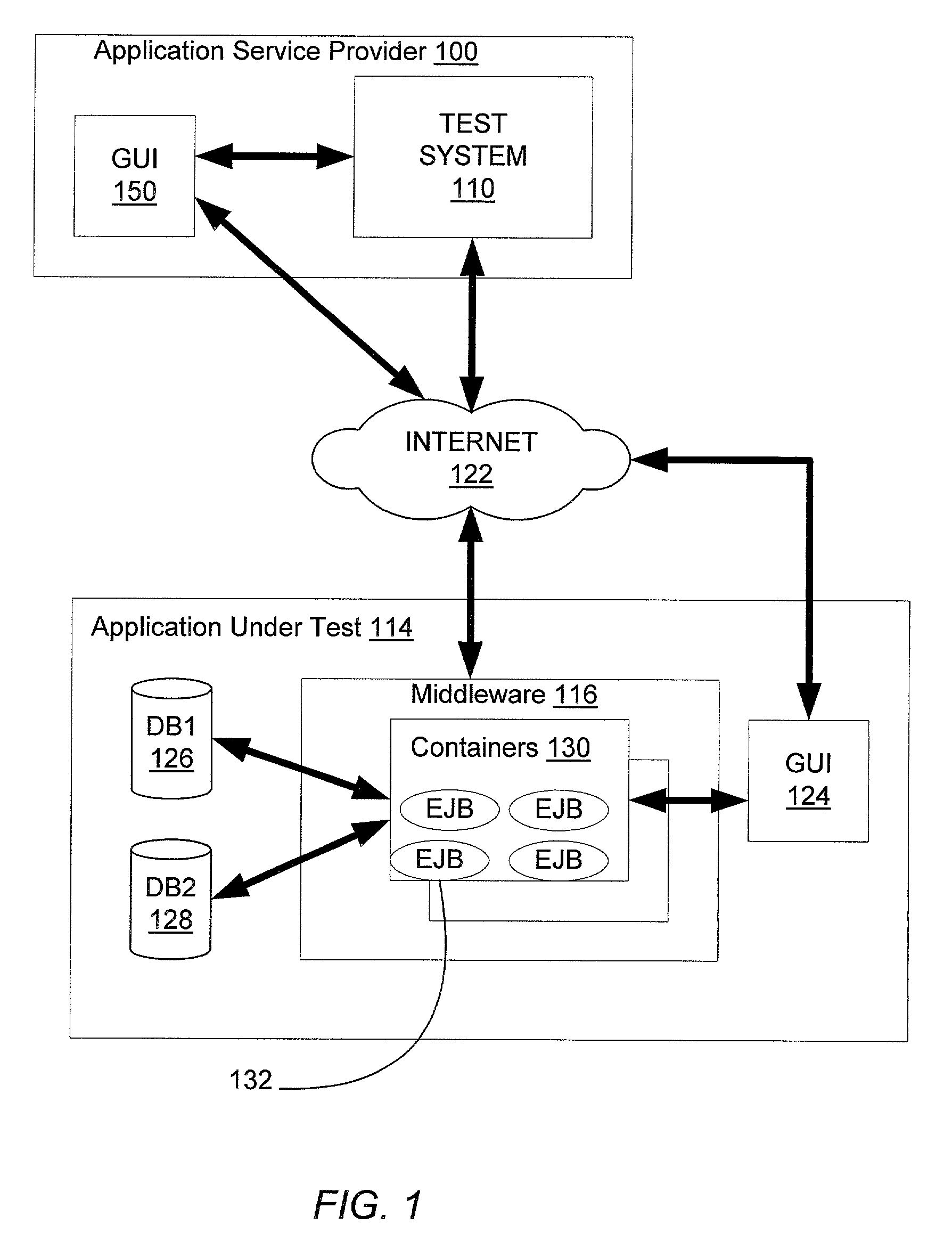
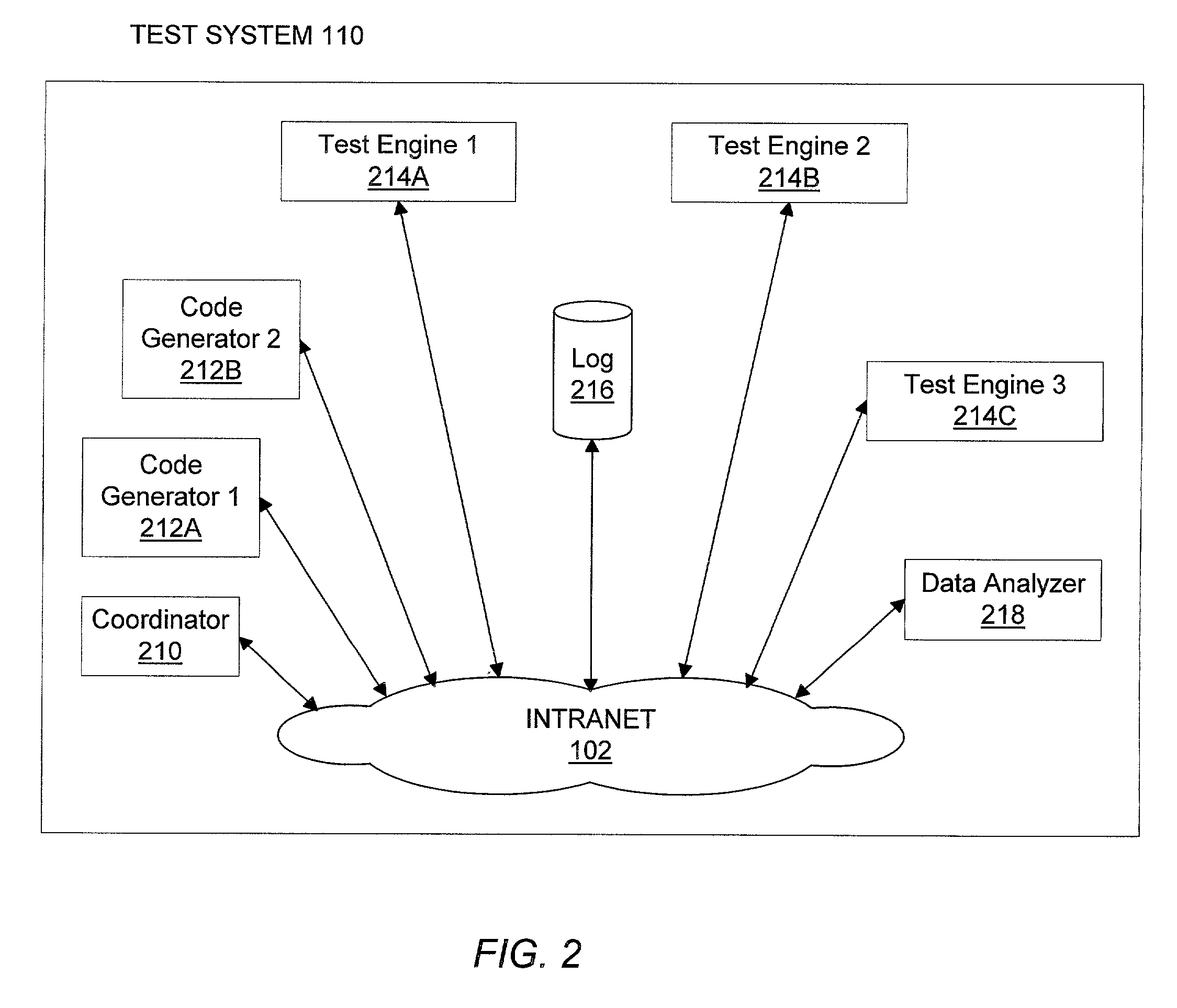
Test code generator, engine and analyzer for testing middleware applications
InactiveUS7000224B1Facilitate load based testing of N-tieredReduce physical laborElectronic circuit testingError detection/correctionProgramming languageData profiling
A system for testing middleware of applications in the N-tiered model. The test system contains test code generators, test engines to execute multiple copies of the test code and a data analyzer to analyze and present the results to a human user. The system is able to automatically generate test code to exercise components of the middleware using information about these components that would otherwise be available to the application under test. Multiple copies of the test code are executed in a synchronized fashion. Execution times of multiple events are recorded and then presented in one of several formats. With the system, an application developer can identify components that represent performance bottlenecks or can gather information on deployment properties of individual components that can be used to enhance the performance of the application under test.
Owner:ORACLE INT CORP
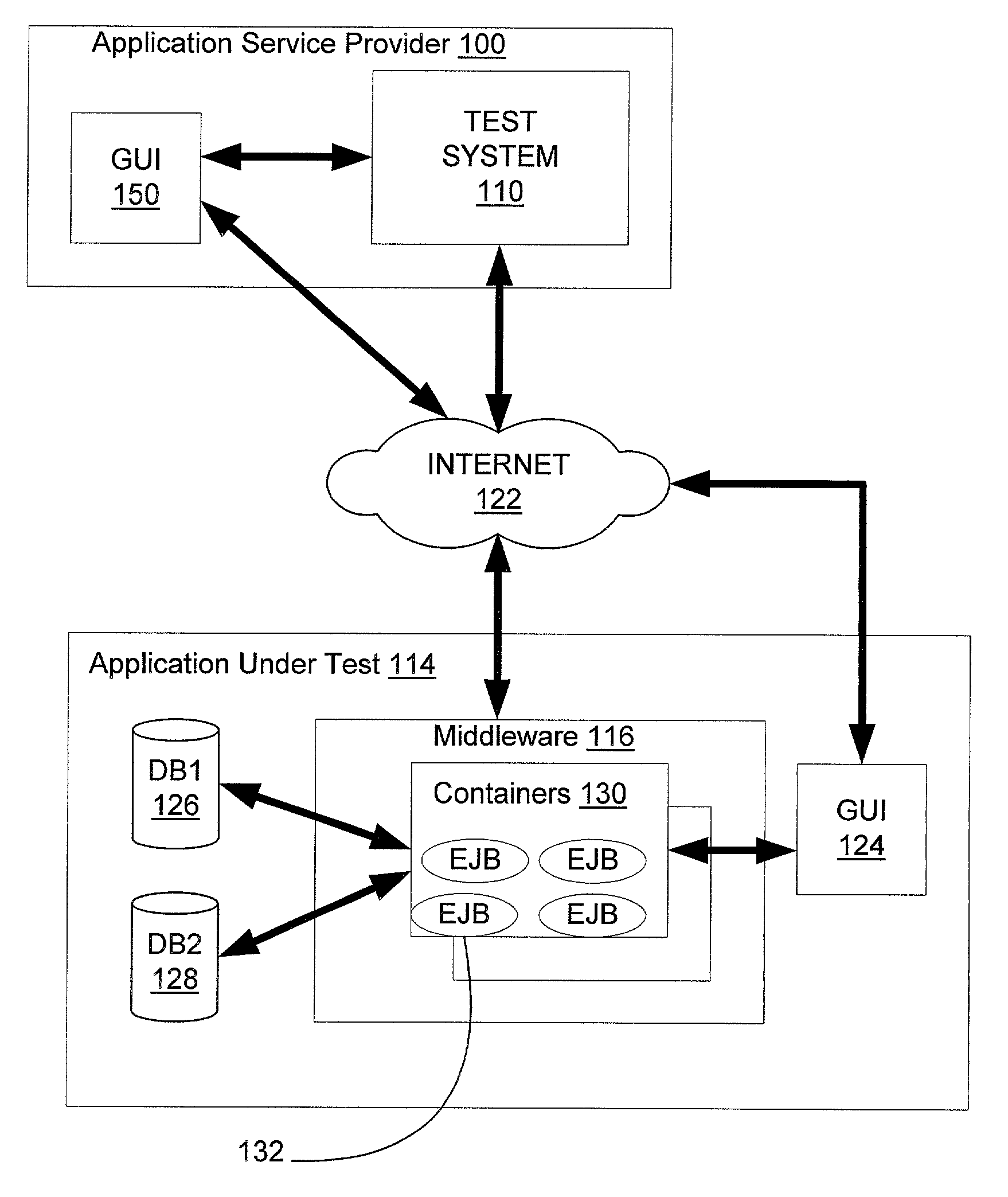
Method and system for web based software object testing
ActiveUS6993747B1Easy to testConvenient verificationSoftware testing/debuggingSpecific program execution arrangementsMultiple copyTest code
A system for remotely testing middleware of applications in the N-tiered model across a network. The test system contains test code generators, test engines to execute multiple copies of the test code and a data analyzer to analyze and present the results to a human user. The system is able to automatically generate test code to exercise remotely located components of the middleware using information about these components that would otherwise be available to the application under test. Multiple copies of the test code are executed in a synchronized fashion. Execution times of multiple events are recorded and then presented in one of several formats. By use of the system, an application developer can receive test results about components that represent performance bottlenecks or can be made aware of information on deployment properties of individual components that can be used to enhance the performance of the application under test.
Owner:ORACLE INT CORP
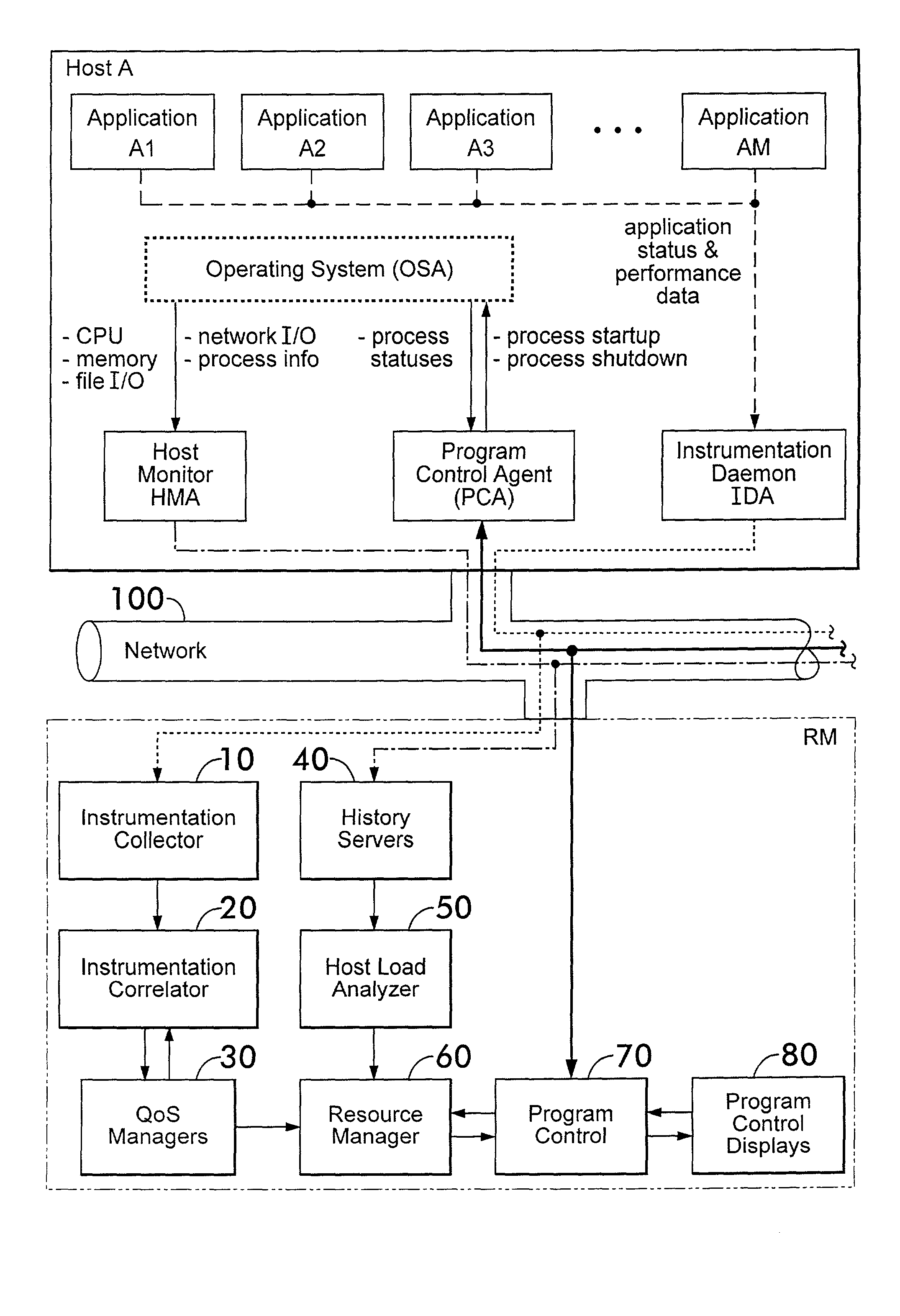
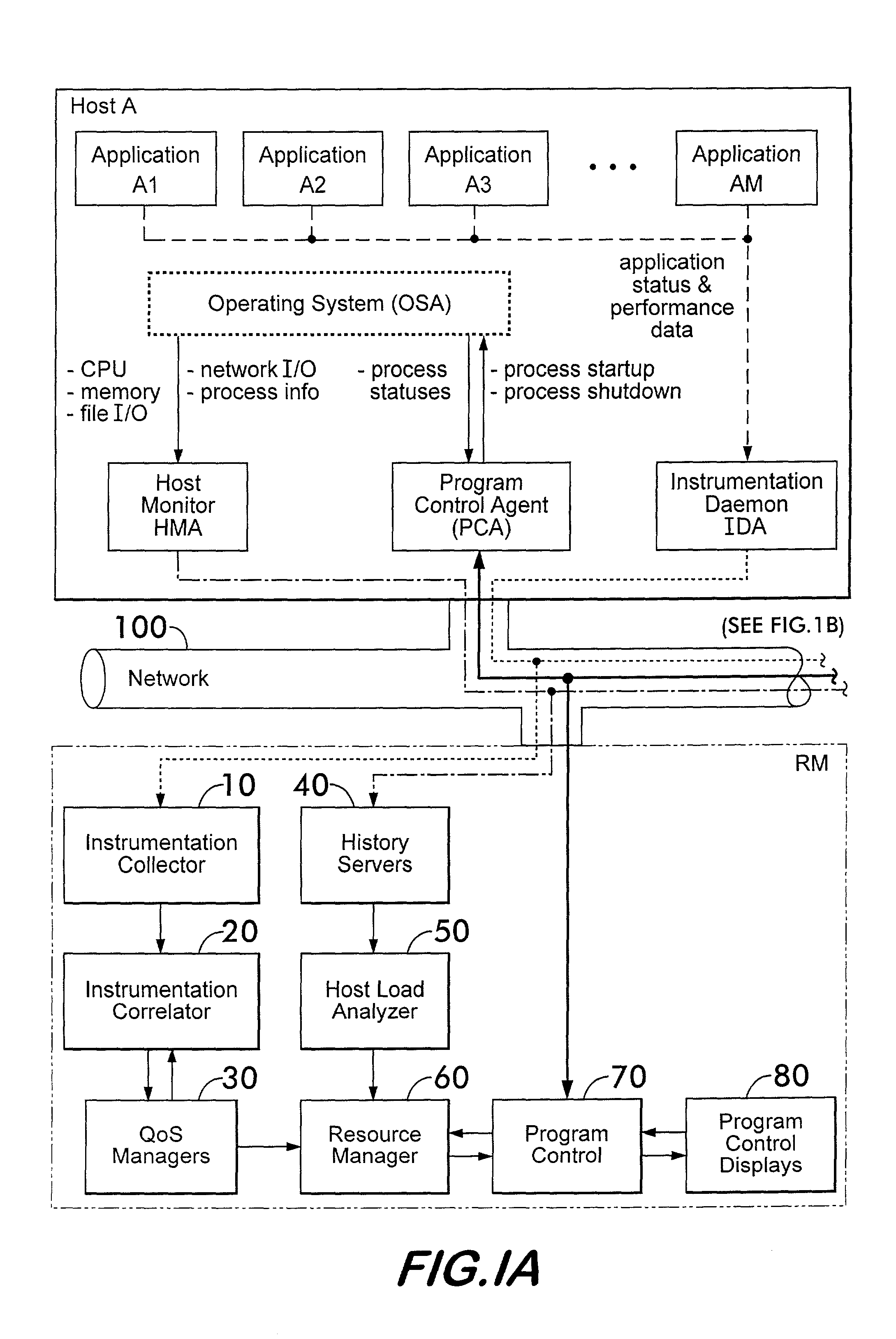
Instrumentation for resource management architecture and corresponding programs therefor
ActiveUS20050055322A1Program initiation/switchingResource allocationMonitoring systemResource management
A monitoring system for a distributed environment including a plurality of hosts capable of executing multiple copies of a scalable application includes a first device for generating first data corresponding to performance of all copies of the scalable application; a second device for generating second data corresponding to performance of all host in the distributed environment; and a third device for generating performance metrics based on the first and second data.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
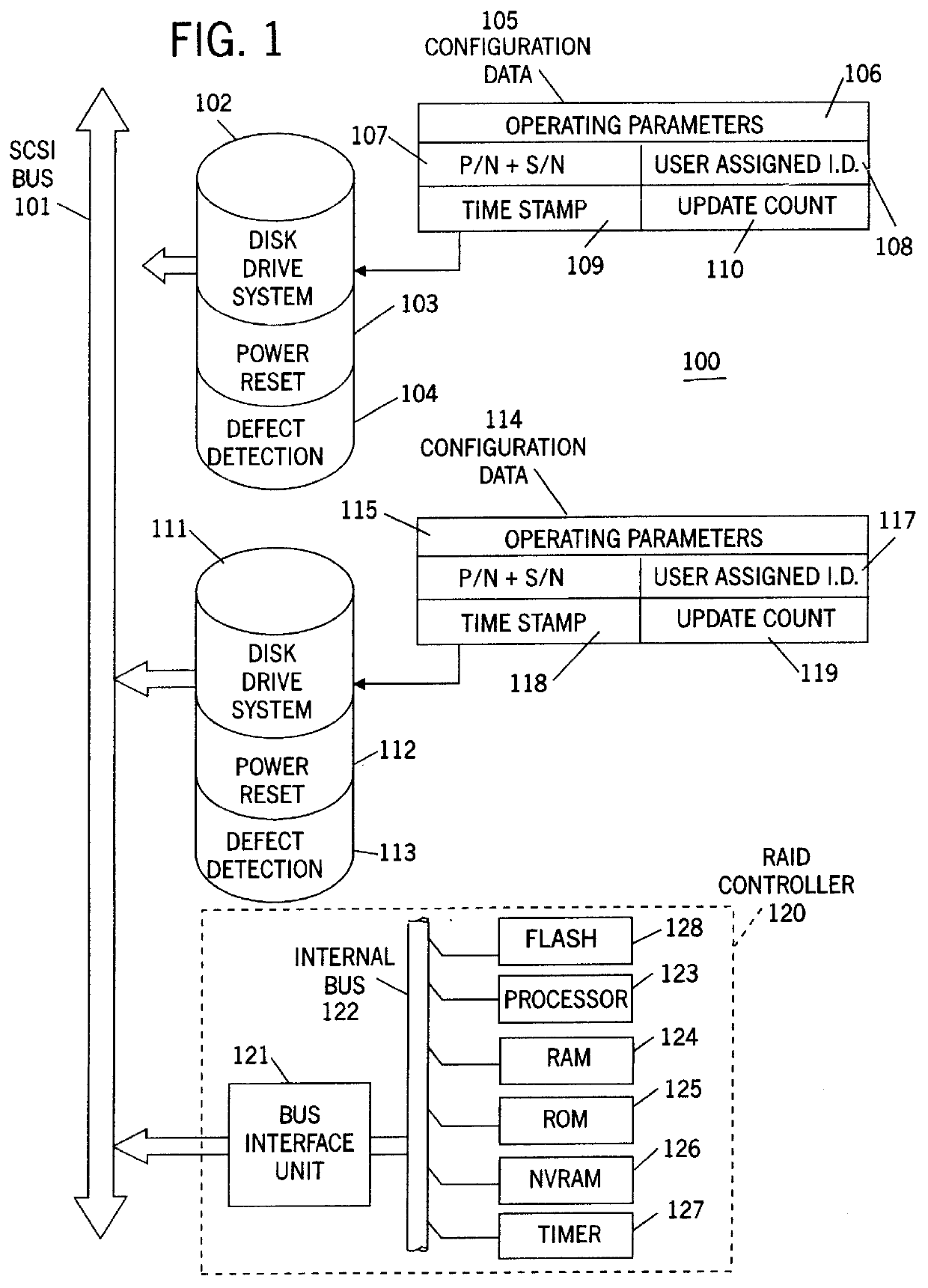
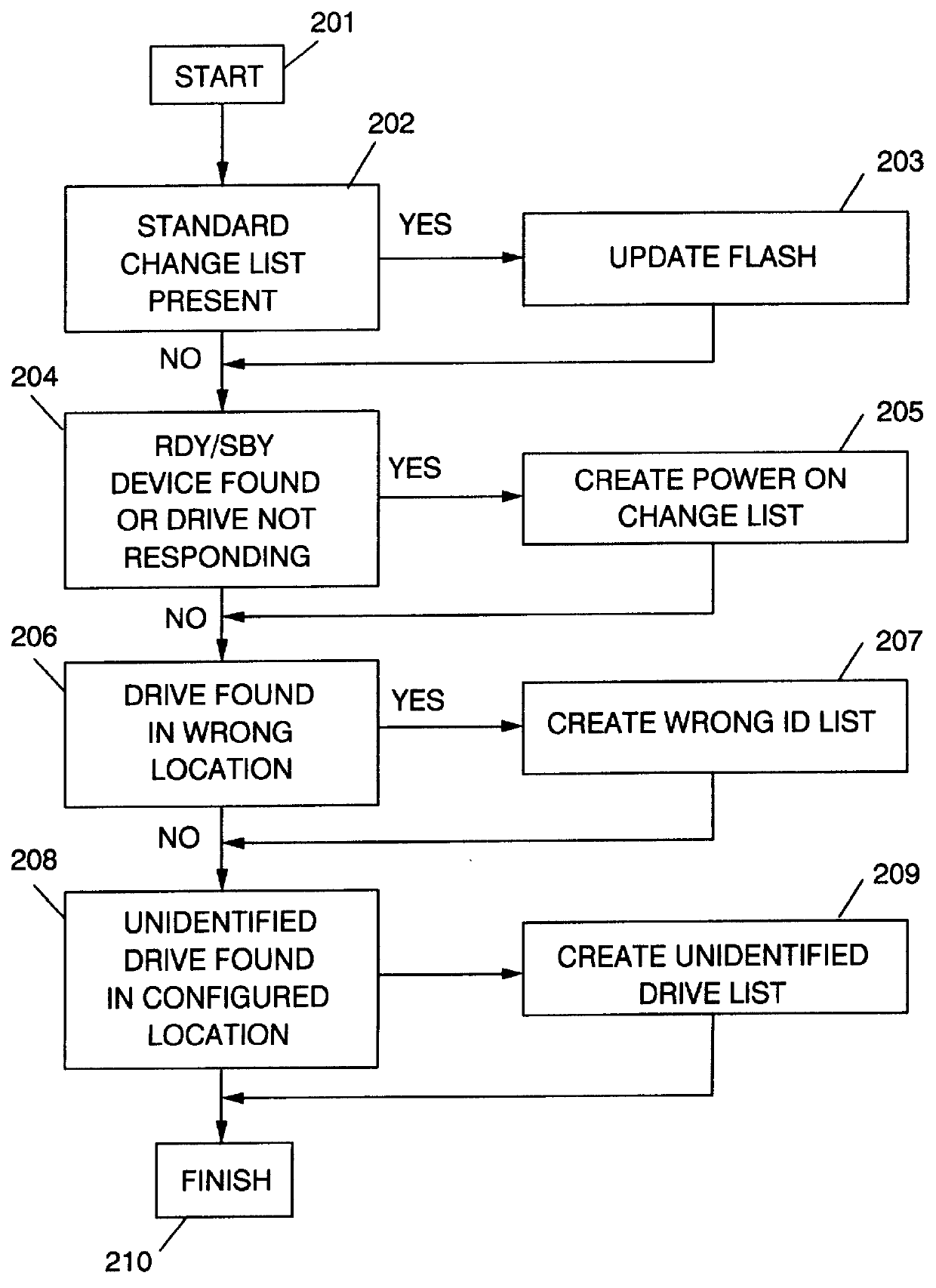
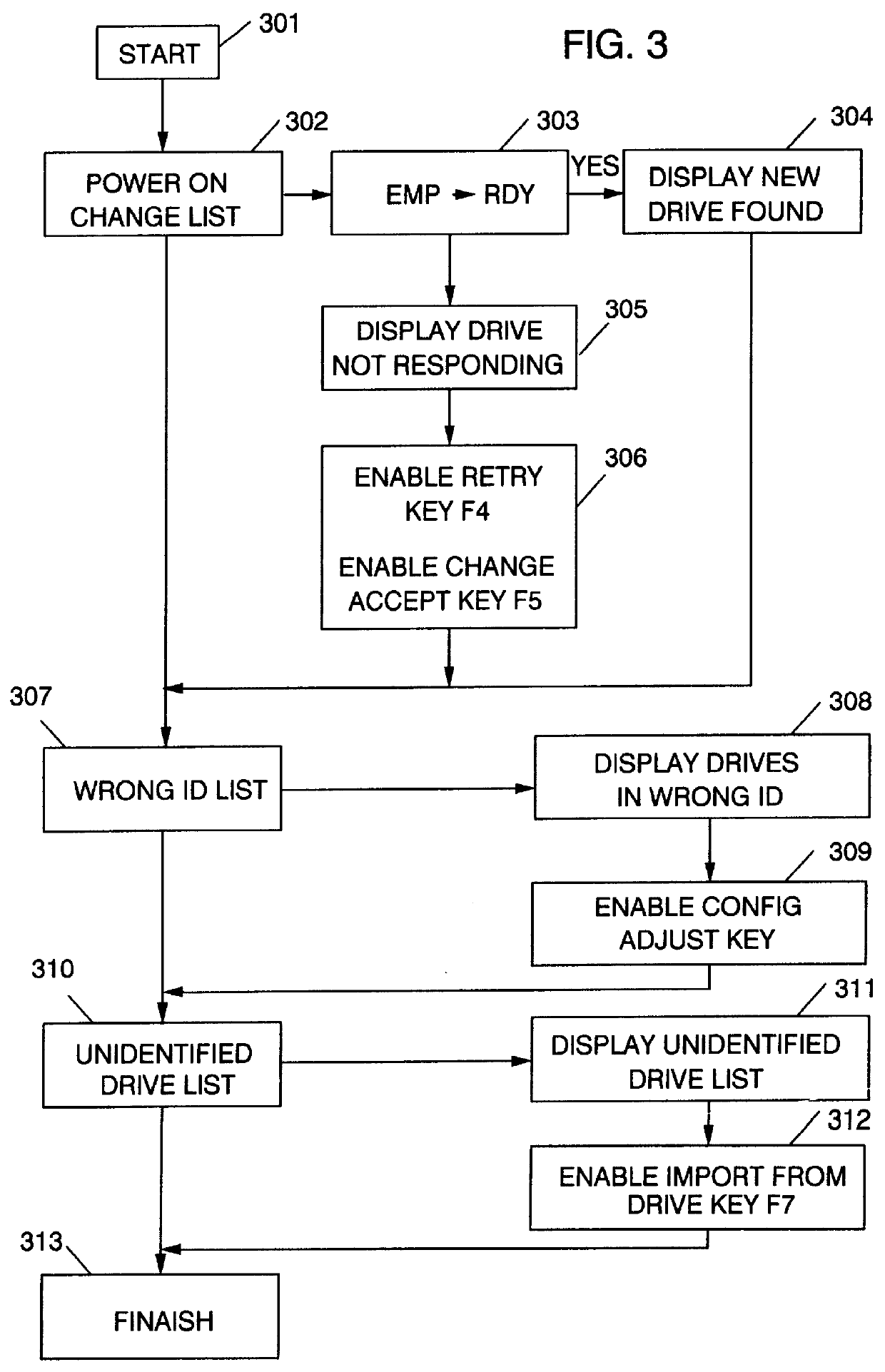
RAID system having a selectable unattended mode of operation with conditional and hierarchical automatic re-configuration
InactiveUS6058455AInput/output to record carriersDetecting faulty hardware by configuration testRAIDOperation mode
Because correct configuration data is essential to the operation of any RAID system, and because multiple copies of the configuration data are kept, not only in the RAID controller itself, but also in each disk drive unit in the configuration, it is imperative that the various copies of the configuration data do not become "out of synchronization", which means that one or more copies of the configuration data are different from one or more other copies of the configuration data. To maintain synchronization of all copies of the configuration data, the current invention compares the configuration data stored in the RAID controllers' NVRAM to that of the current system, and records any new, non-responding, repositioned or unidentified storage devices in a change list. The identities and the attachment points of any storage devices in the change list are then displayed to the user, and various options for correcting the lack of synchronization are provided by enabling one or more function keys that may be selected by the user. One such function key, an "accept change" key, causes the configuration data to be modified by changing the current operational state of any non-responding storage device. A "configuration adjustment" key, when selected by the user, causes the configuration data to be modified to reflect any changes in the attachments points of any repositioned storage deices. An "import configuration" key causes the configuration data to be changed to correspond to that of an unidentified storage device. And a "retry" key gives the user an opportunity to rearrange the system and then re-compares the configuration data in the controller to the current system configuration. When the system is operating in un-attended mode, means are disclosed to automatically perform the "accept change", "configuration adjustment" and "import configuration" functions in priority order so long as the "retry" key has not been enabled. The retry key implies attended operation.
Owner:IBM CORP
Paralleling processing method, system and program
ActiveUS20100138810A1Digital computer detailsConcurrent instruction executionSingle clusterParallel processing
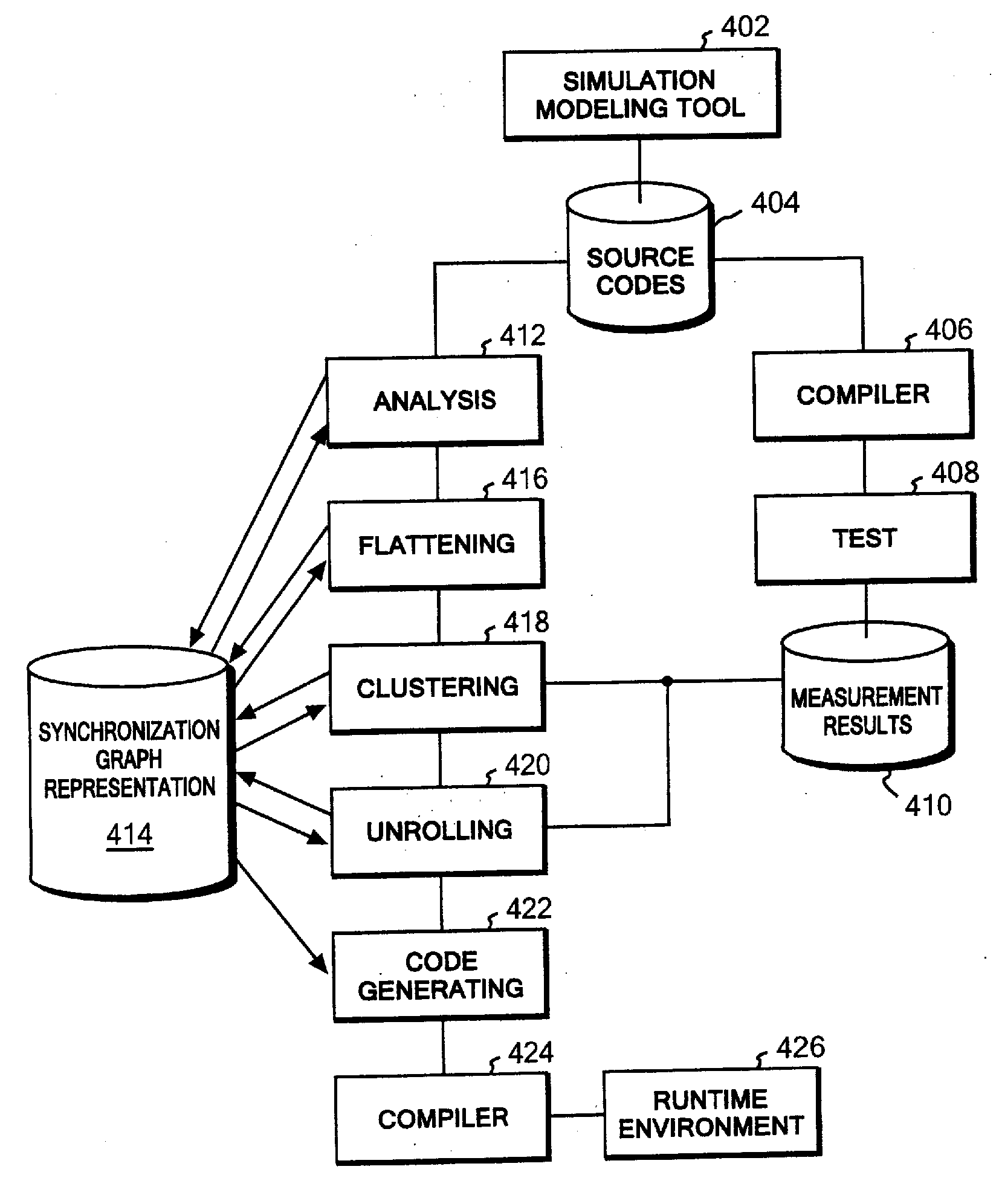
Paralleling processing system and method. When clusters are formed based on strongly connected components, a single cluster (fat cluster) having at least a predetermined number of blocks, or an expected processing time exceeding a predetermined threshold, is formed. The fat cluster is subjected to an unrolling process to make multiple copies of the processing of the fat cluster and to assign the copies to individual processors. Processing of the fat cluster is executed by the multiple processor devices in a pipelined manner. If a fat cluster to be iteratively executed cannot be executed in the pipelined manner because a processing result of an nth iteration of the fat cluster depends on a processing result of a preceding iteration of the fat cluster an input value needed for execution of the fat cluster is generated based on a certain prediction, and the fat cluster is speculatively executed.
Owner:IBM CORP
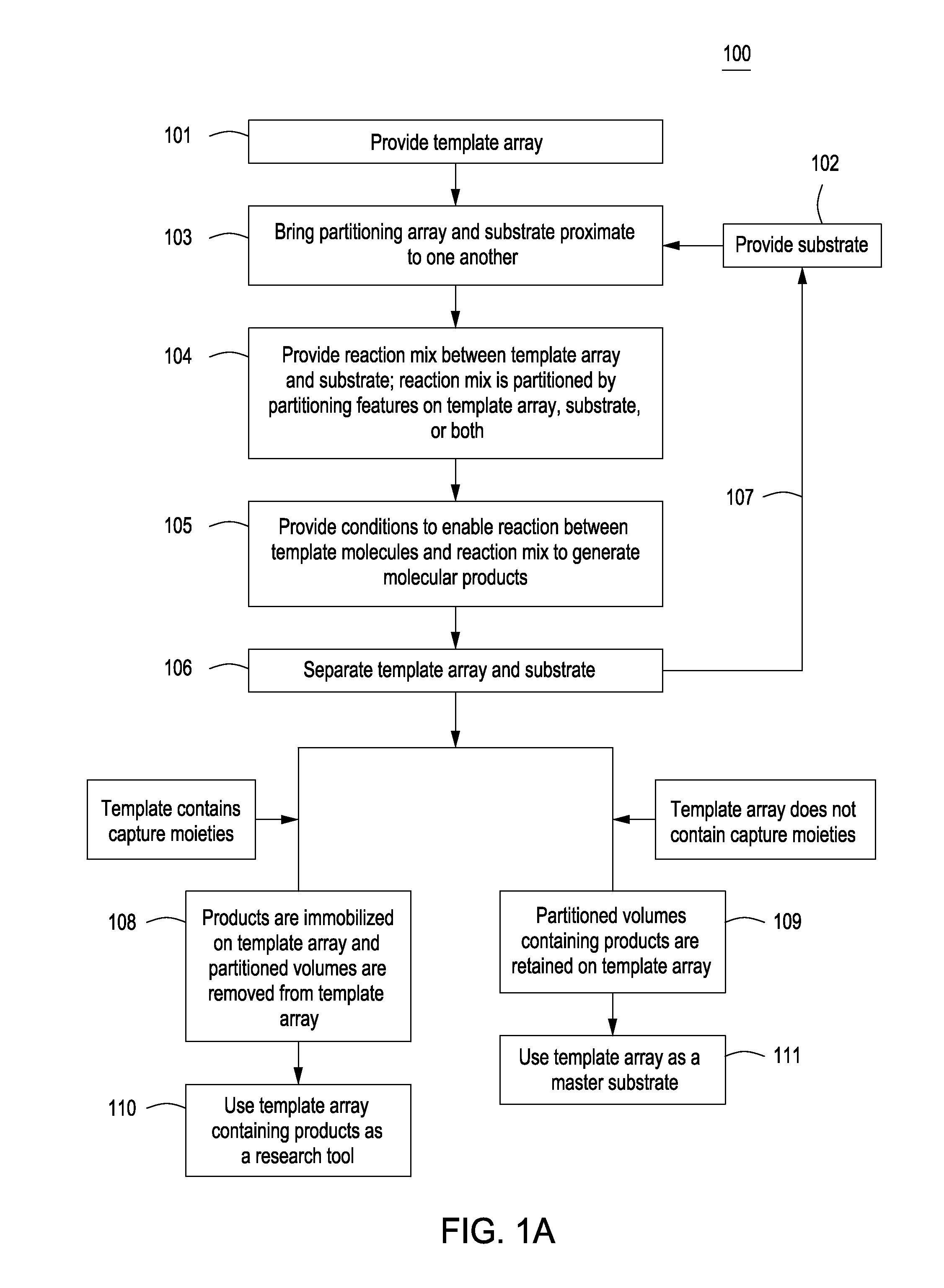
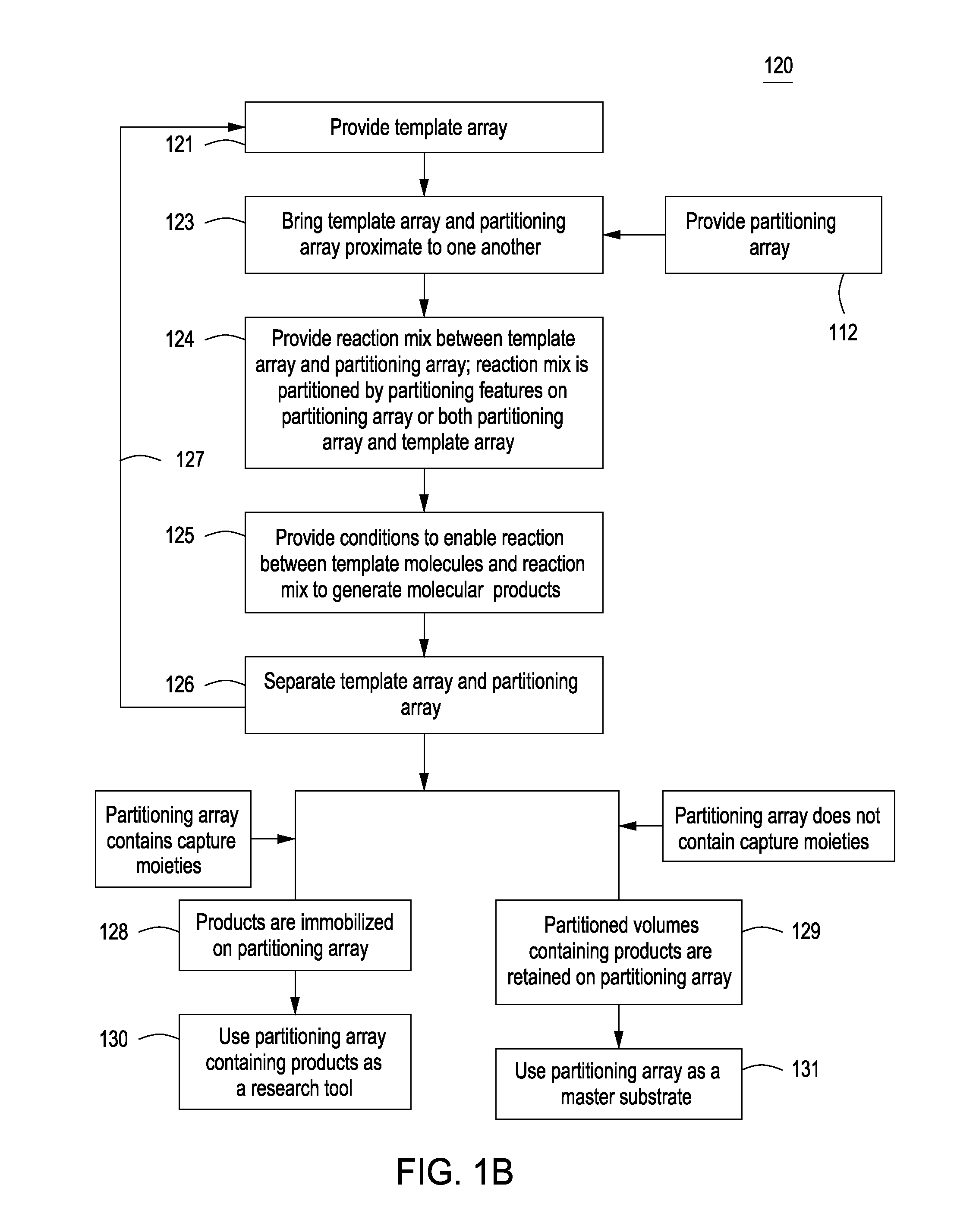
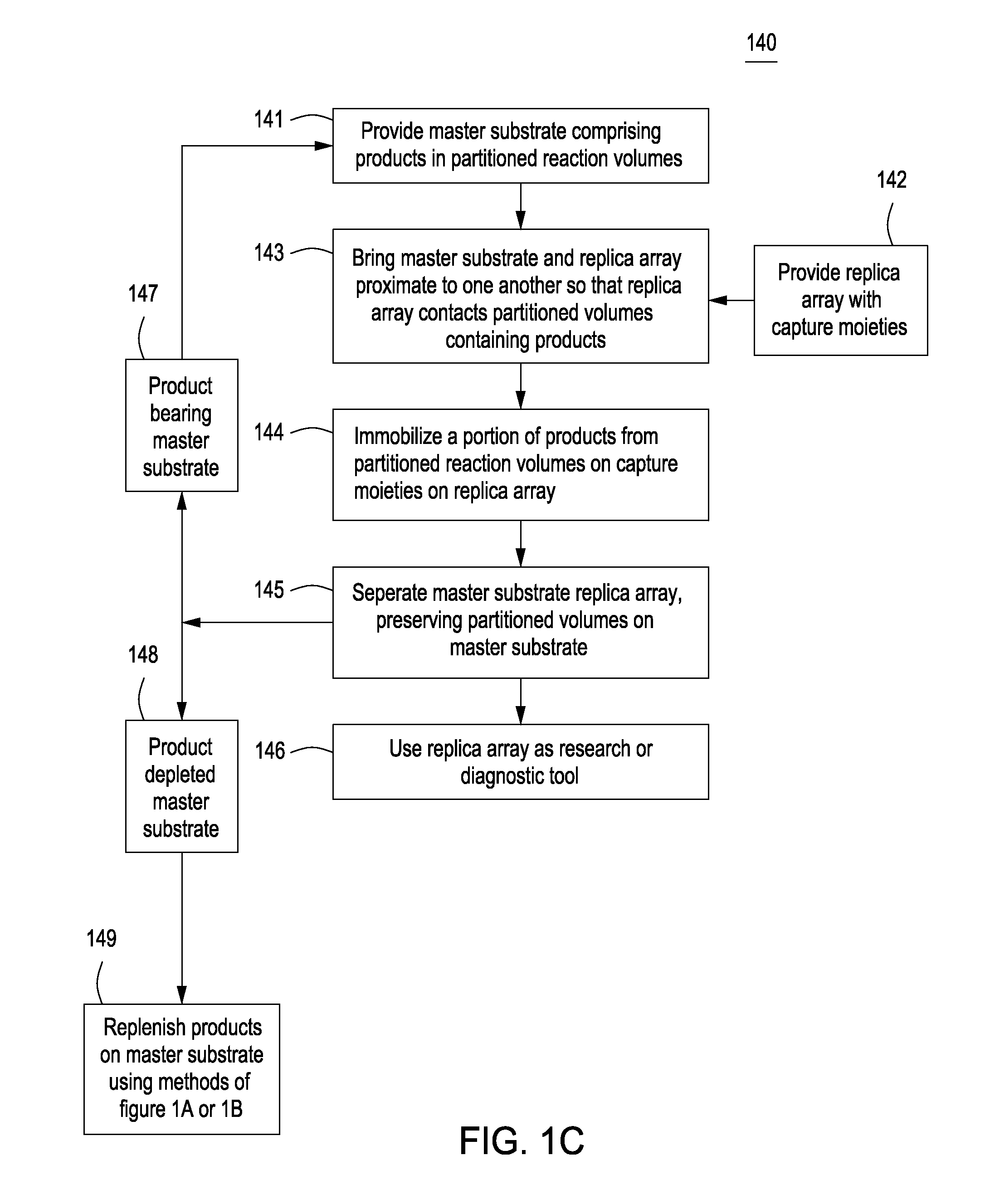
Methods for manufacturing molecular arrays
The methods of the present invention provide methods for manufacturing a master substrate and methods for manufacturing replica arrays from the master substrate. The methods may be used, for example, directly to manufacture or “print” peptide arrays from a DNA array; however, the methods are applicable to a wide range of manufacturing applications for use any time multiple copies of an array needs to be printed.
Owner:PROGNOSYS BIOSCI
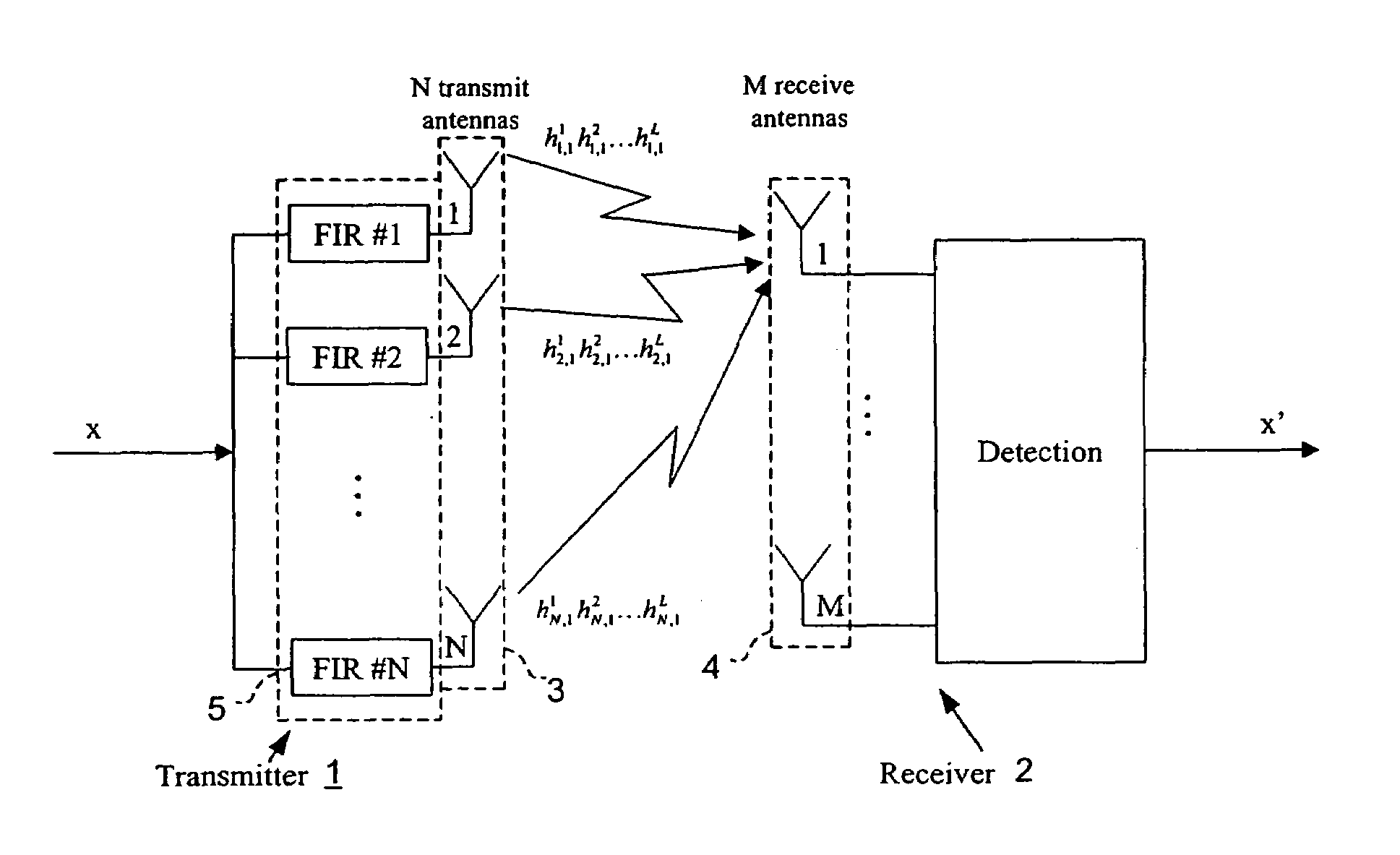
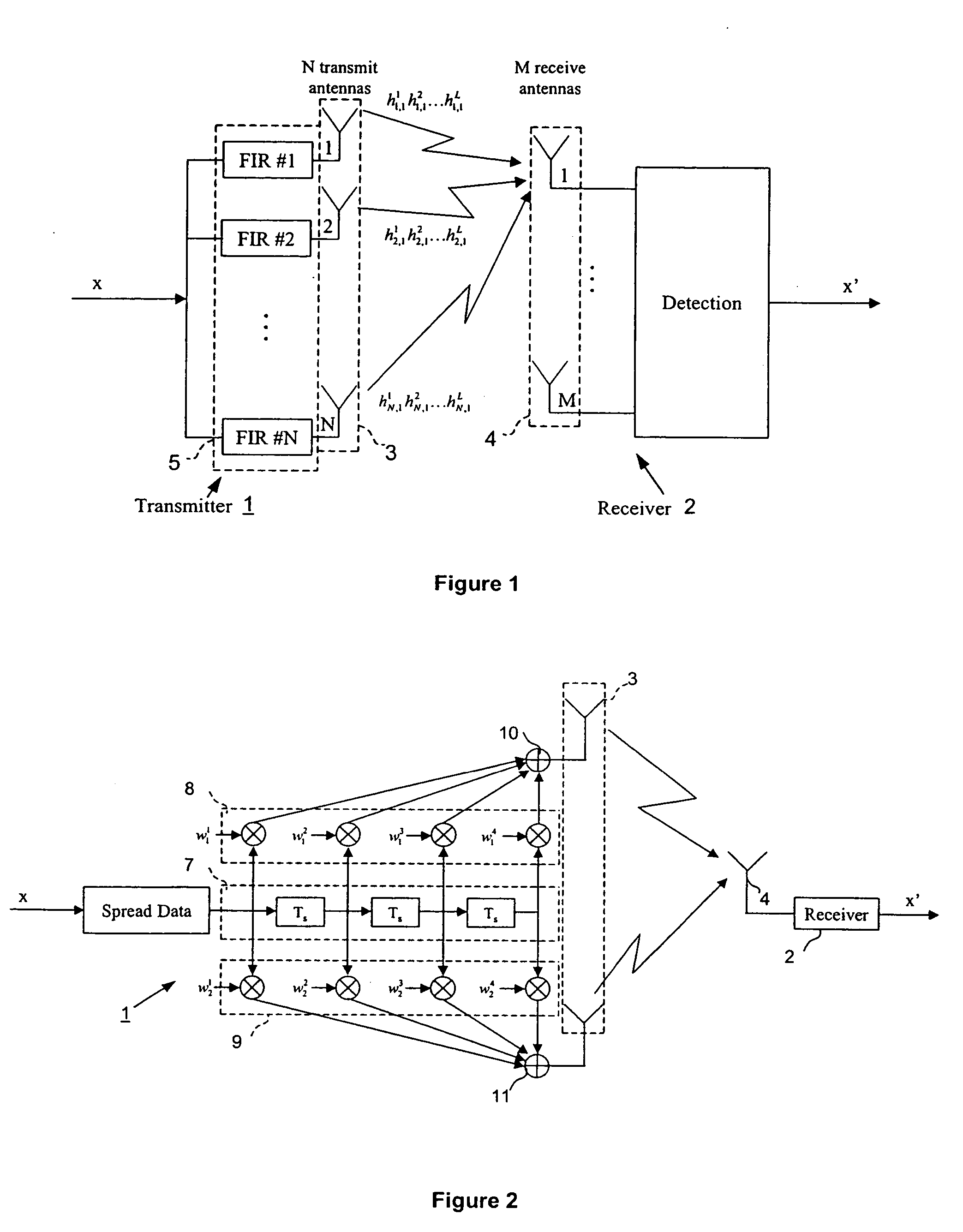
Wireless transmission using an adaptive transmit antenna array
ActiveUS7248645B2Spatial transmit diversityModulated-carrier systemsWireless transmissionClosed loop
Closed loop wireless communication of signals using an adaptive transmit antenna array, in which multiple copies of signals to be transmitted by the transmit antenna array are produced with delays and weights that are functions of the multi-path transmission channel characteristics from the transmit antenna array to a receive antenna array of a receiver and are combined before transmission by the transmit antenna array. The delays and weights of the transmit copies for each transmit antenna element are functions of the respective multi-path transmission channel characteristics from that transmit antenna element to the receive antenna array such that the multi-path signal components propagated to each receiver element are received with distinguishable delays according to the propagation path. The receiver combines the received signal components from each receive antenna element with delays and weights that are respective functions of the multi-path transmission channels.
Owner:GOOGLE TECHNOLOGY HOLDINGS LLC
System and Method for Achieving Different Levels of Data Consistency
InactiveUS20080256299A1Digital data information retrievalData processing applicationsMultiple copyData consistency
A system and method for maintaining consistency in a system where multiple copies of an object may exist is provided for maintaining consistent copies. Consistency is maintained using a plurality of consistency policies in which at least one consistency policy results in different performance than a second consistency policy. A consistency policy is selected from the plurality consistency policies for each object to improve system performance.
Owner:DROPBOX
Managing copies of data
ActiveUS7882093B2Digital data information retrievalData processing applicationsComputerized systemData management
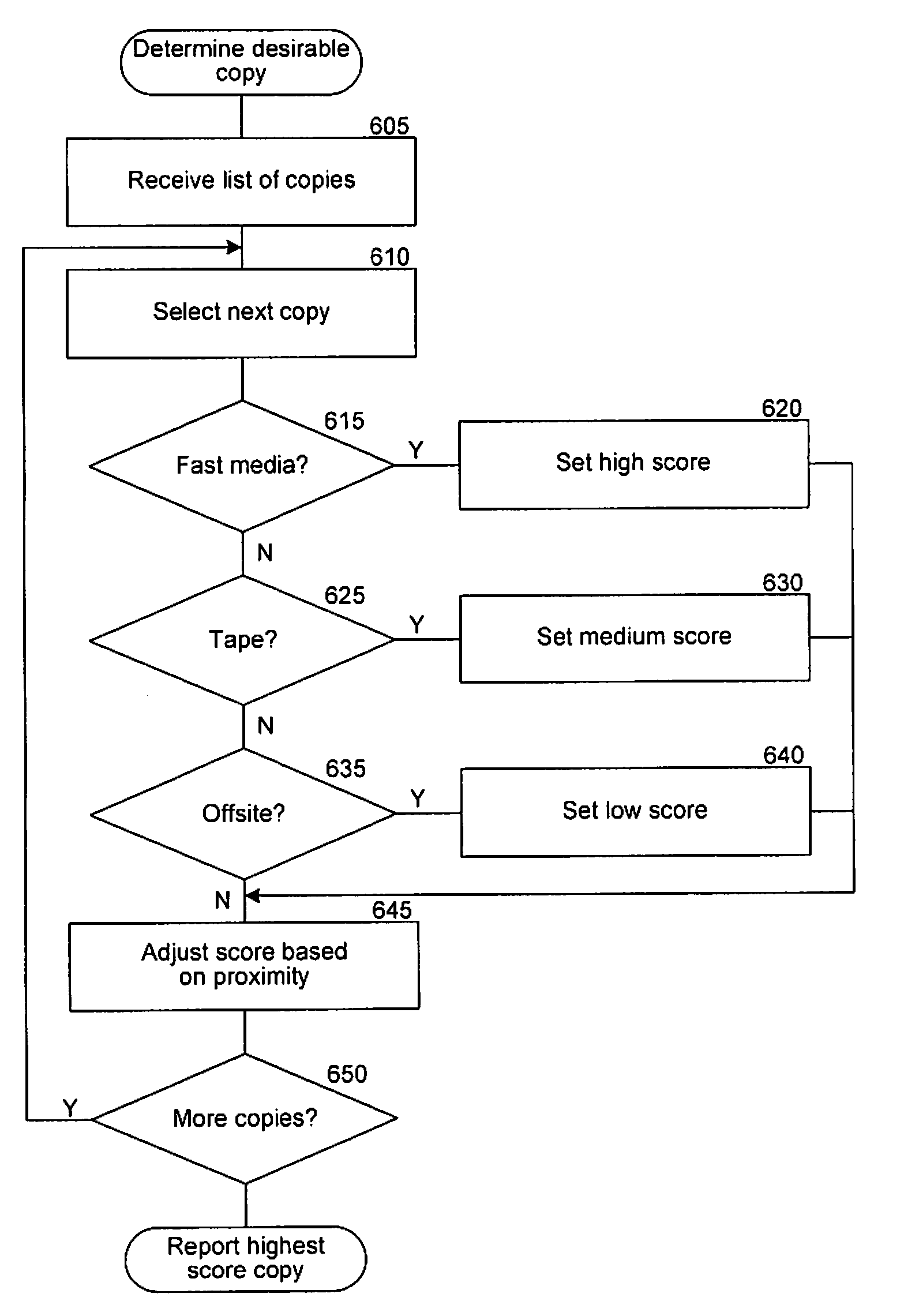
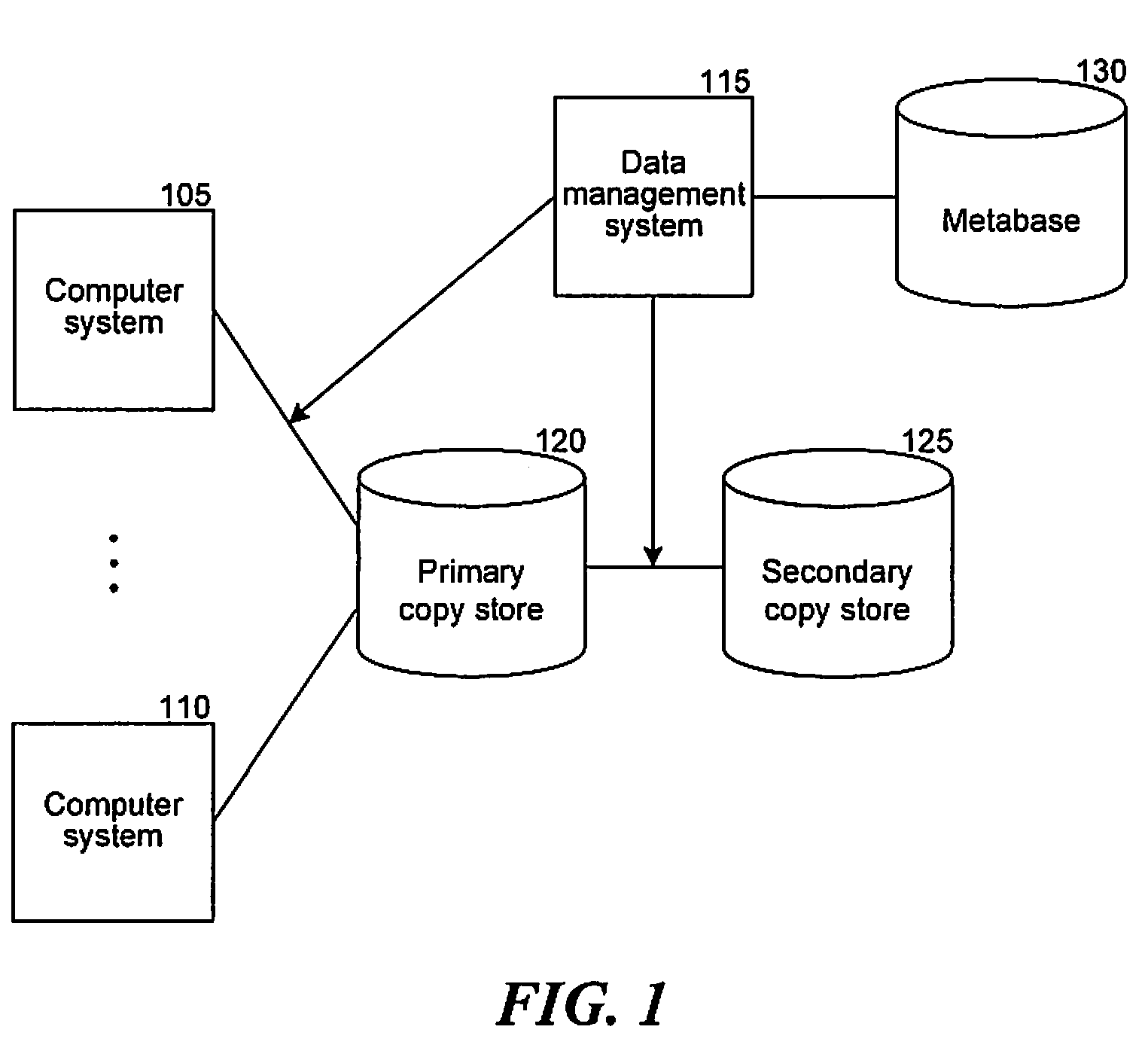
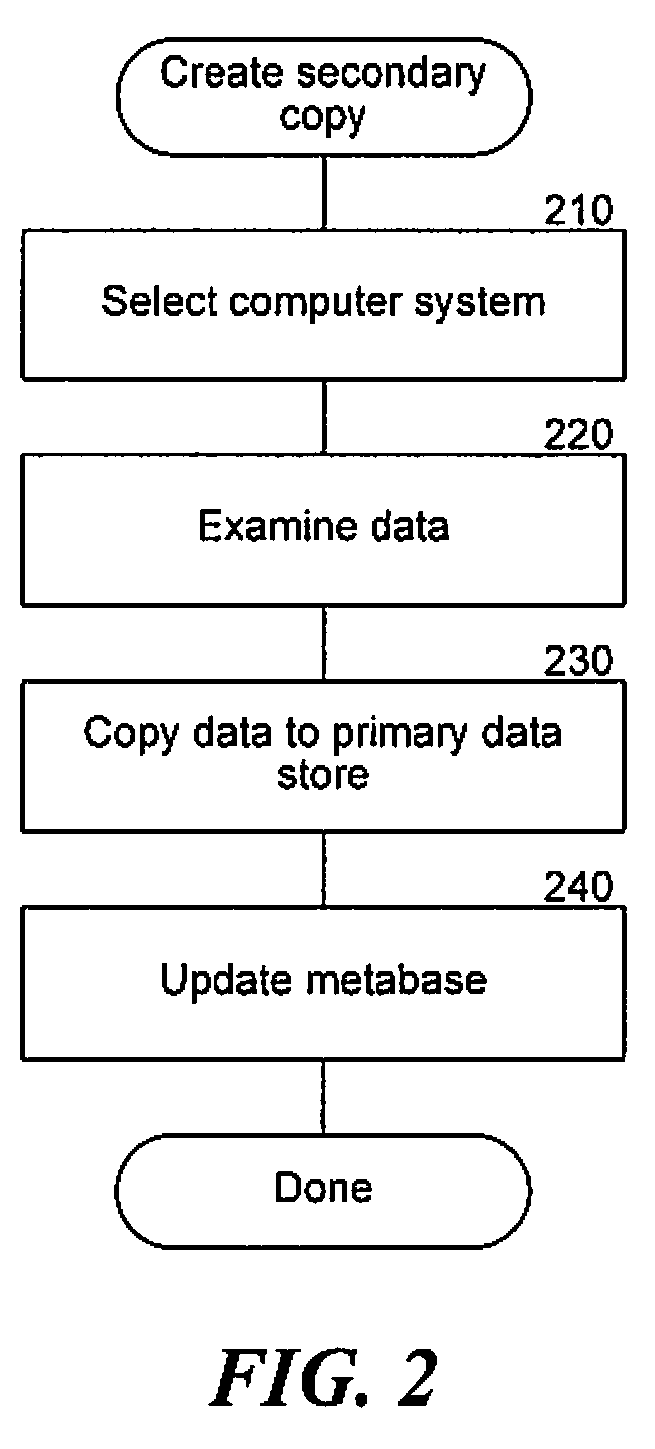
A method in a computer system for retrieving data from one of multiple copies of the data is provided, referred to as the data management system. The data management system receives a request identifying at least one data object to be accessed. Then, the data management system queries a metabase to locate data copies that contain the identified at least one data object, wherein the data copies are created from similar source data, and wherein for each data copy the metabase contains an indication of the availability of the copy relative to other copies. Next, the data management system determines one of the located data copies to use to access the identified at least one data object, wherein the determination is made based on the indicated availability contained in the metabase for each of the located data copies. Then, the data management system accesses the identified at least one data object using the determined one of the located data copies.
Owner:COMMVAULT SYST INC
High-throughput screening assays by encapsulation
InactiveUS20030027221A1Compound screeningApoptosis detectionHigh-Throughput Screening AssaysBiological cell
Candidates for biological activity are screened in capsules, each capsule containing a candidate, a target (which may be a molecular species or a biological cell or multiple copies of such a species or cell), and an intelligent substance. The target is one with which a successful candidate will interact to evoke a particular response in the target, and the intelligent substance is one that undergoes a transformation as a result of the response, the transformation being detectable by observation of the capsule itself. The candidate and the target are isolated from each other in the capsule until a designated point in time thereby enabling the operator to control the time interval between exposure of the target to the candidate and the observation of the capsule to determine whether or not a successful interaction has occurred and the transformation has taken place.
Owner:SMITHKLINE BECKMAN CORP
Method and system for automating the recovery of a credential store
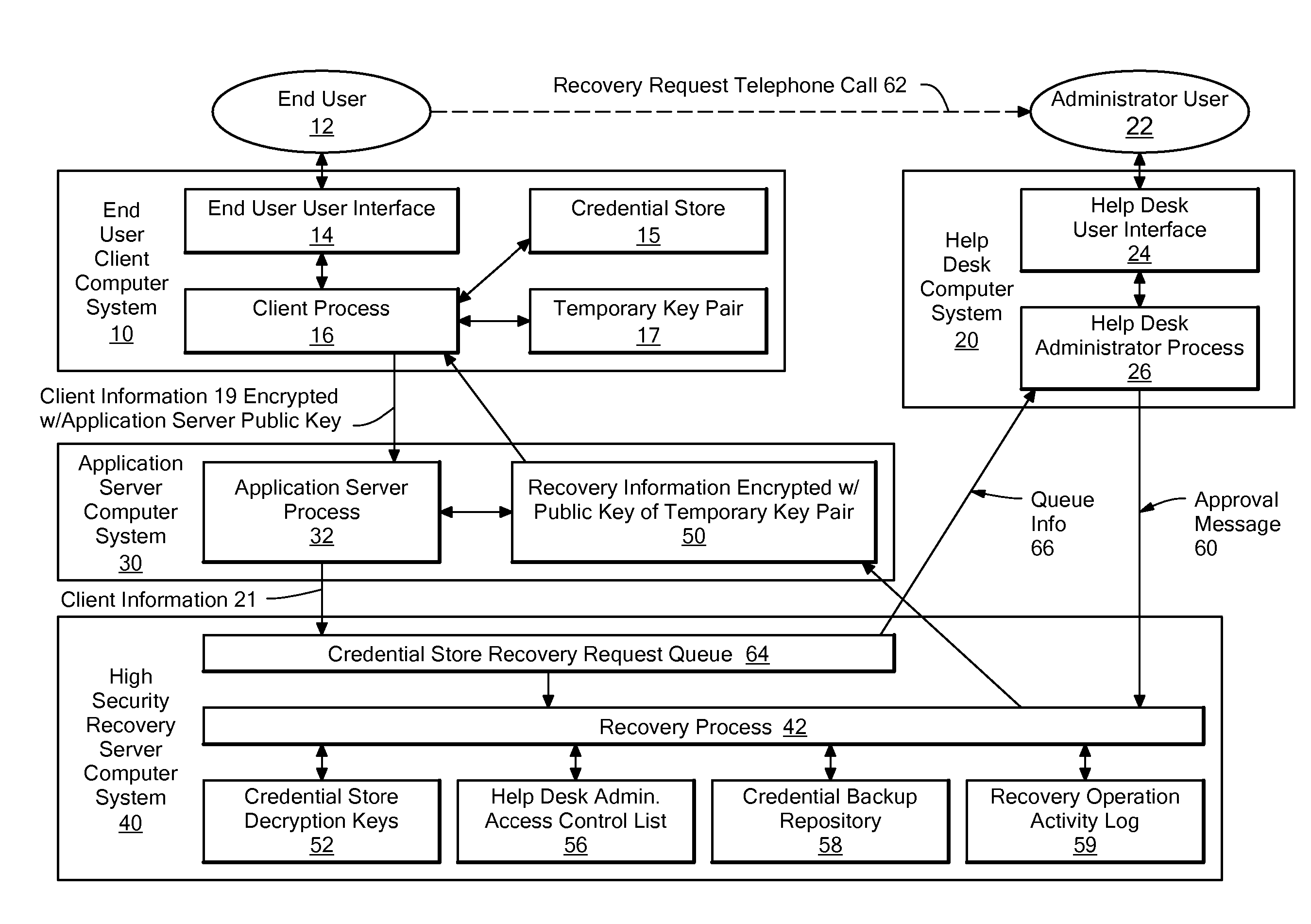
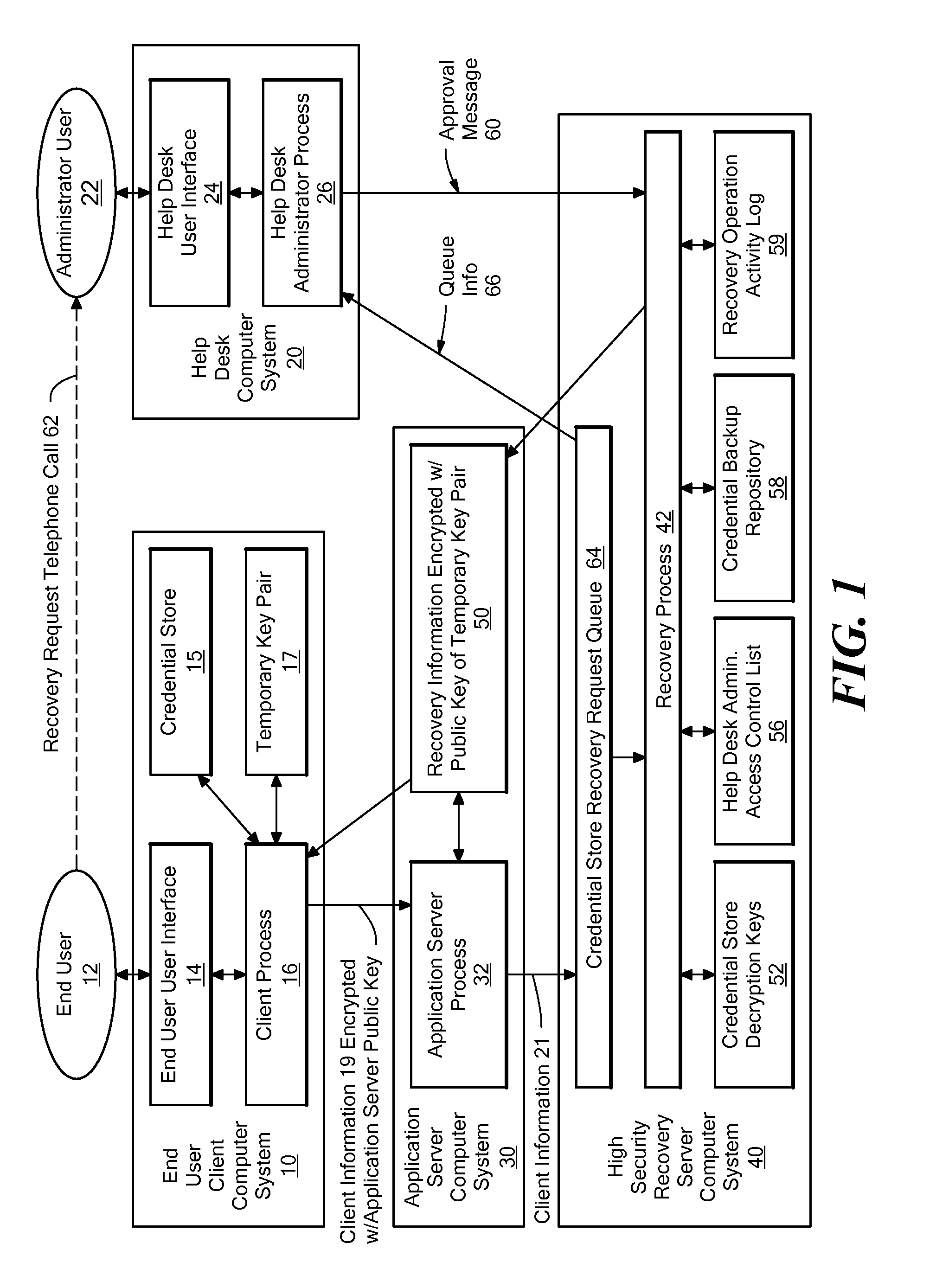
A system for automating the recovery of a credential store, in which client software generates a temporary key pair based on a new password, and sends client information including the user's name, the public half of the temporary key pair, and the host name of the client computer system to a server system, from which the client information is passed to a recovery process. The client software process displays a prompt indicating that the user should call a help desk. A help desk administrator verifies the user's identity and approves the user's request by causing an approval message to be sent to the recovery process. The recovery process obtains recovery information consisting of either the decryption key(s) for the credential store, or a decrypted copy of the credential store, and encrypts the recovery information using the temporary public key. The client process downloads the recovery information from the server, and decrypts it using private key of the temporary key pair. The credential store can then be decrypted using the recovery information if necessary, then re-encrypted based on the new password. The encrypted recovery information is stored on the server and re-used for a certain period of time, after which it is deleted, thus allowing multiple copies of the credential store to be conveniently recovered.
Owner:IBM CORP
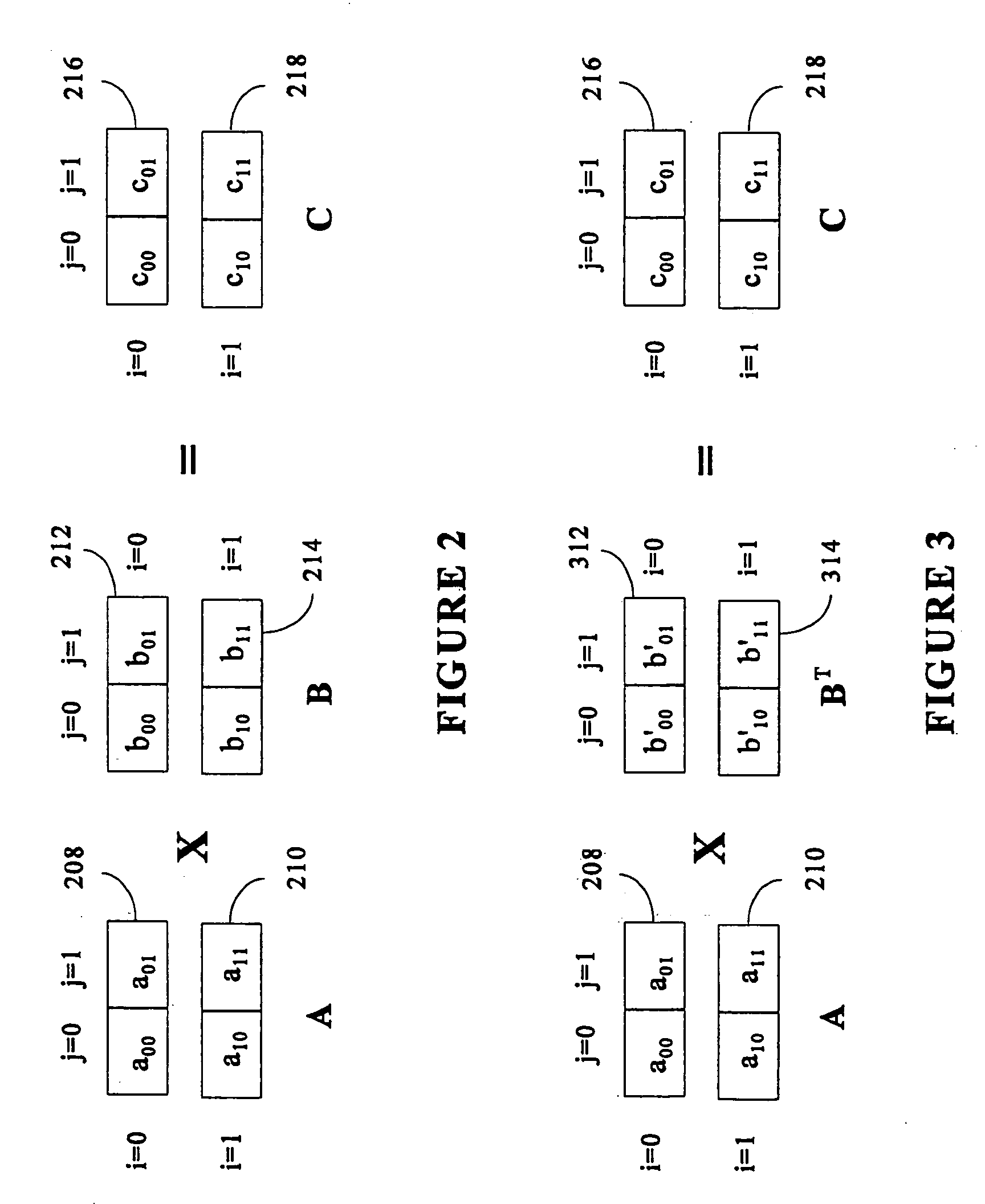
Matrix multiplication in a vector processing system
InactiveUS20050193050A1Efficient and rapid matrix multiplicationEfficient executionComputation using non-contact making devicesProgram controlAlgorithmProcessor register
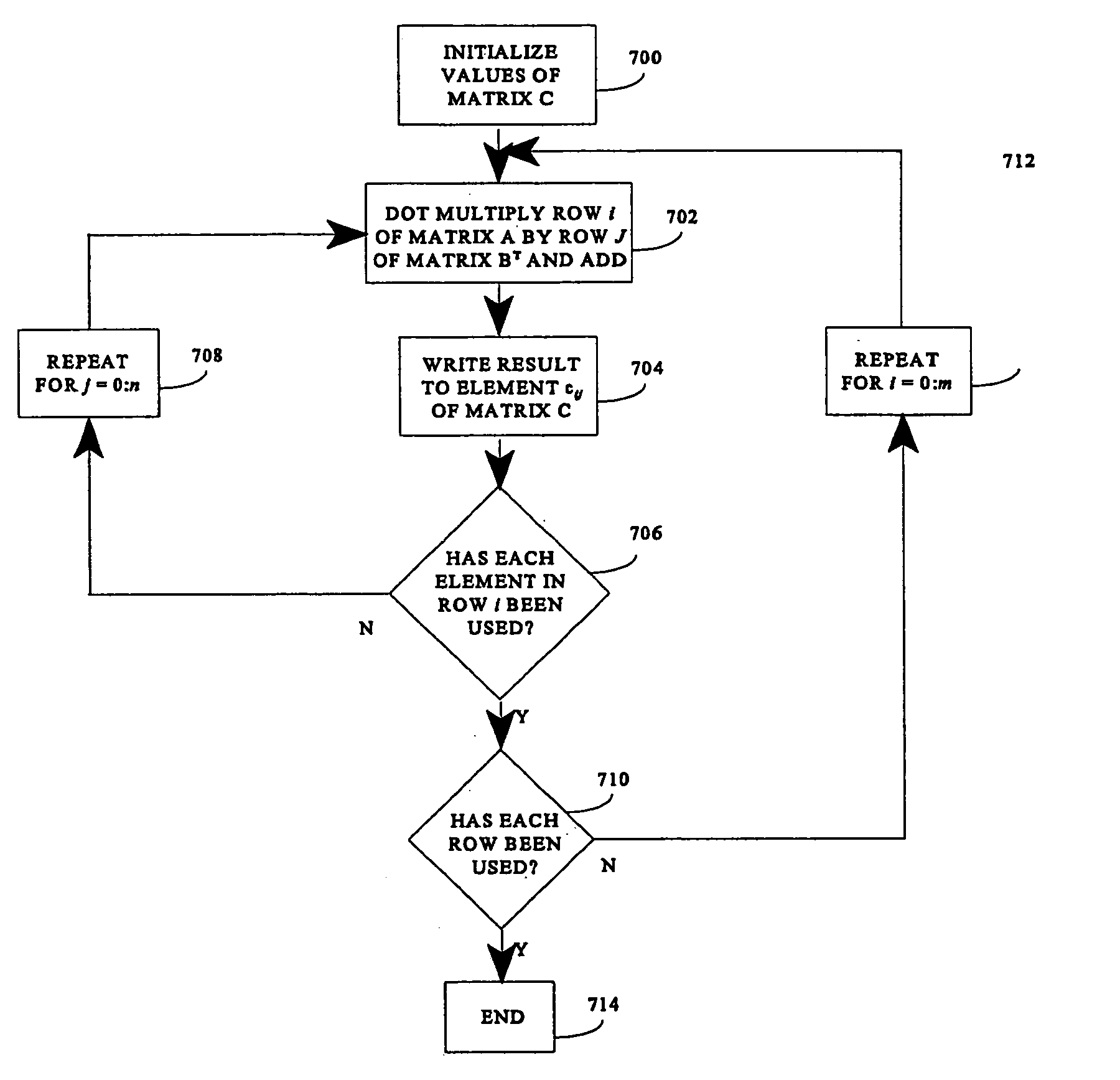
To perform multiplication of matrices in a vector processing system, partial products are obtained by dot multiplication of vector registers containing multiple copies of elements of a first matrix and vector registers containing values from rows of a second matrix. The dot products obtained from this dot multiplication are subsequently added to vector registers which form a product matrix. Each matrix can be divided into submatrices to facilitate the rapid and efficient multiplication of large matrices, which is done in parts by computing partial products of each submatrix. The matrix multiplication avoids rounding errors as it is bit-by-bit compatible with conventional matrix multiplication methods.
Owner:APPLE INC
Data structures for efficient processing of IP fragmentation and reassembly
InactiveUS6937606B2Requires minimizationReduce memory requirementsTime-division multiplexData switching by path configurationArray data structureIP fragmentation
Data structures, a method, and an associated transmission system for IP fragmentation and IP reassembly on network processors in order to minimize memory allocation requirements. Frame data for IP fragmentation or reassembly on a network processor is read into buffers to which are associated various control structures. The control structures permit IP fragmentation or reassembly to be accomplished without creating multiple copies of the frame or fragments.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com