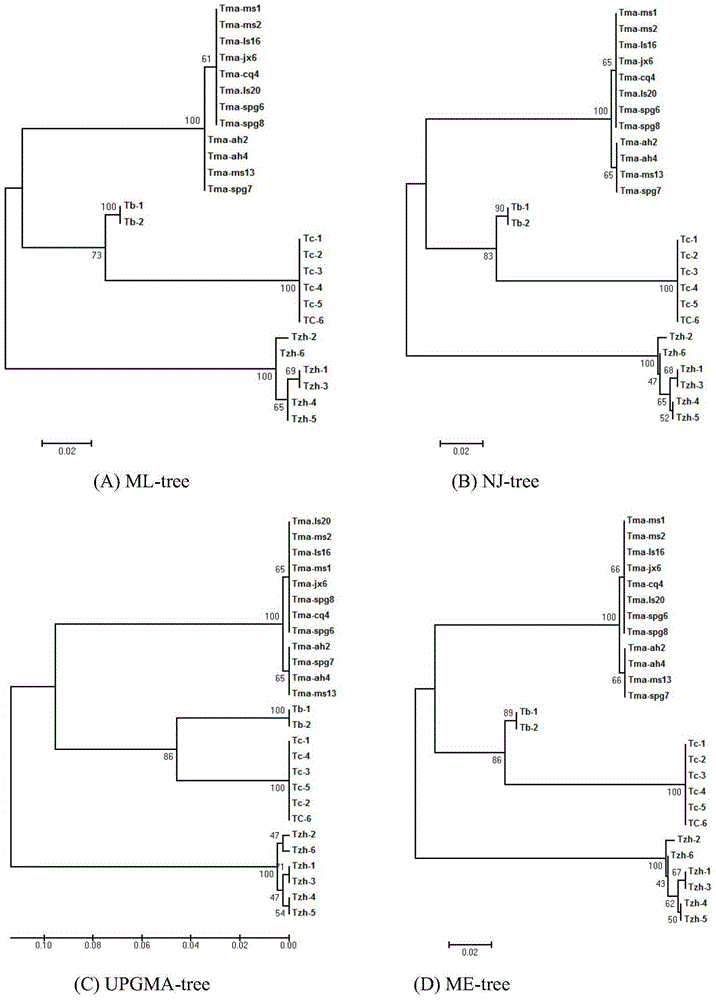
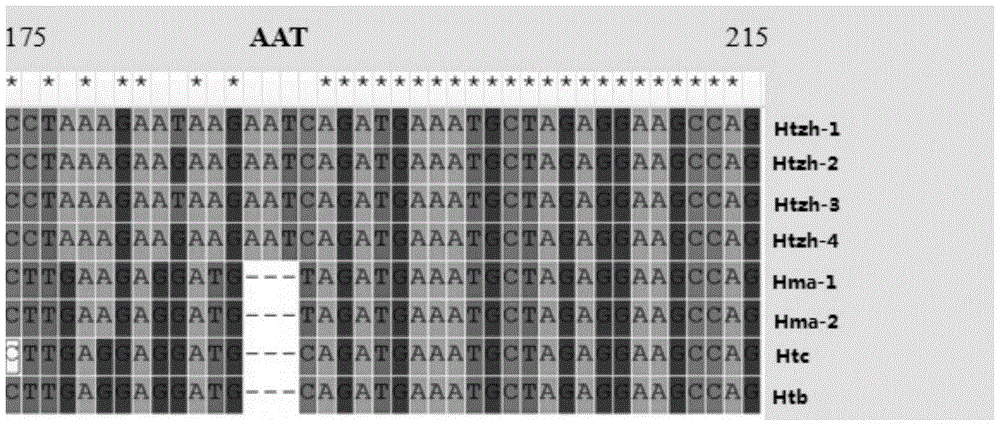
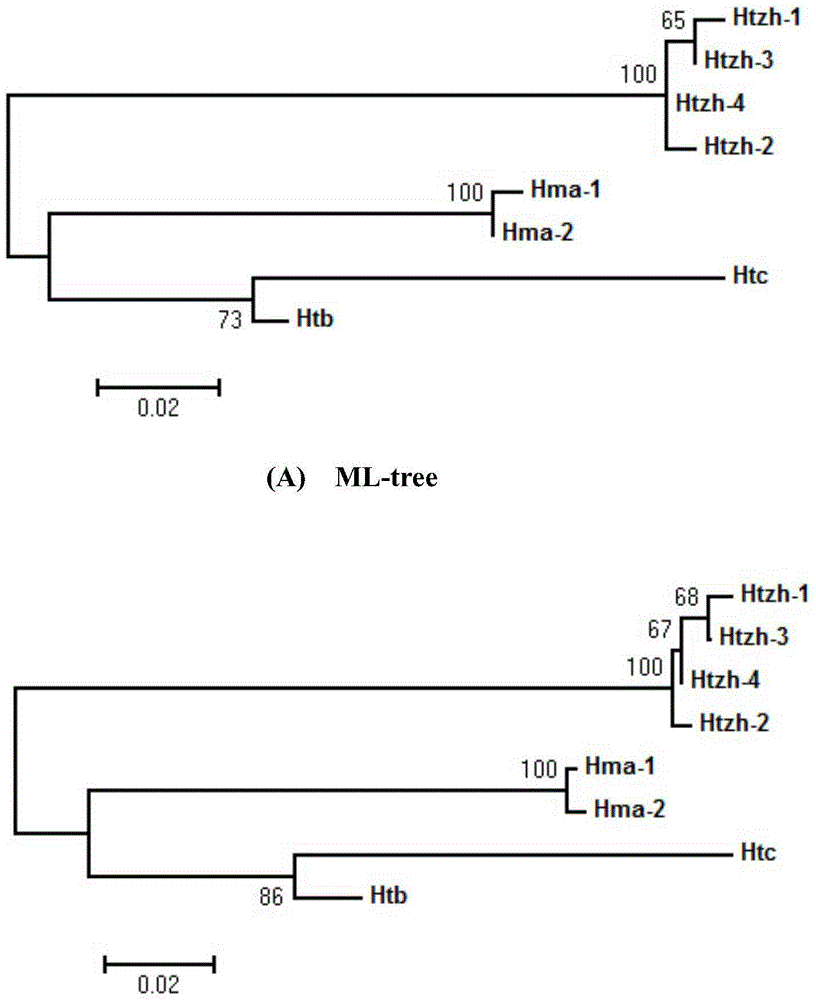
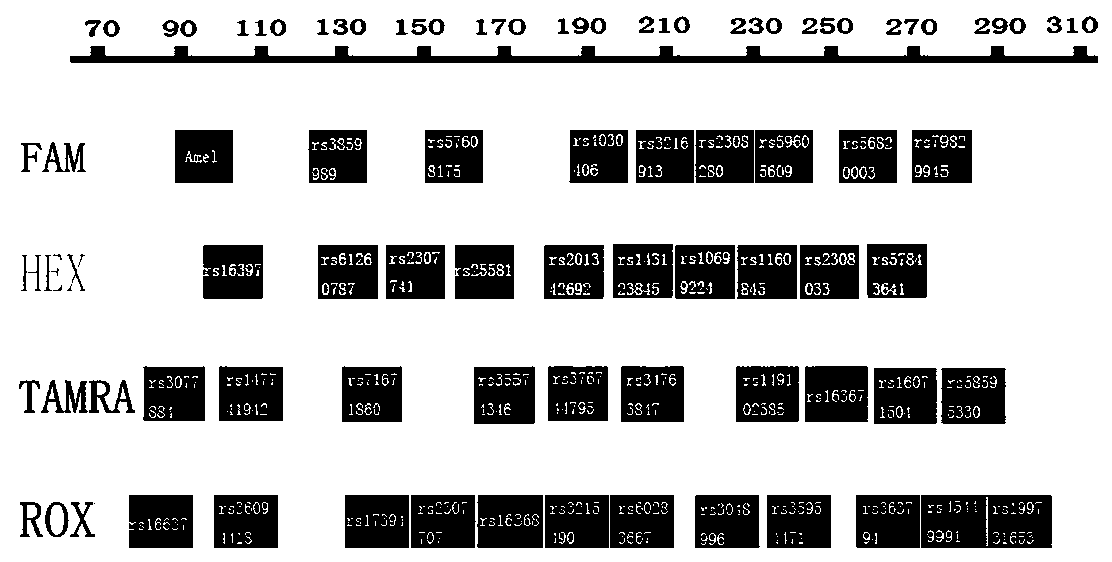
Patents
Literature
59results about How to "Strong identification ability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
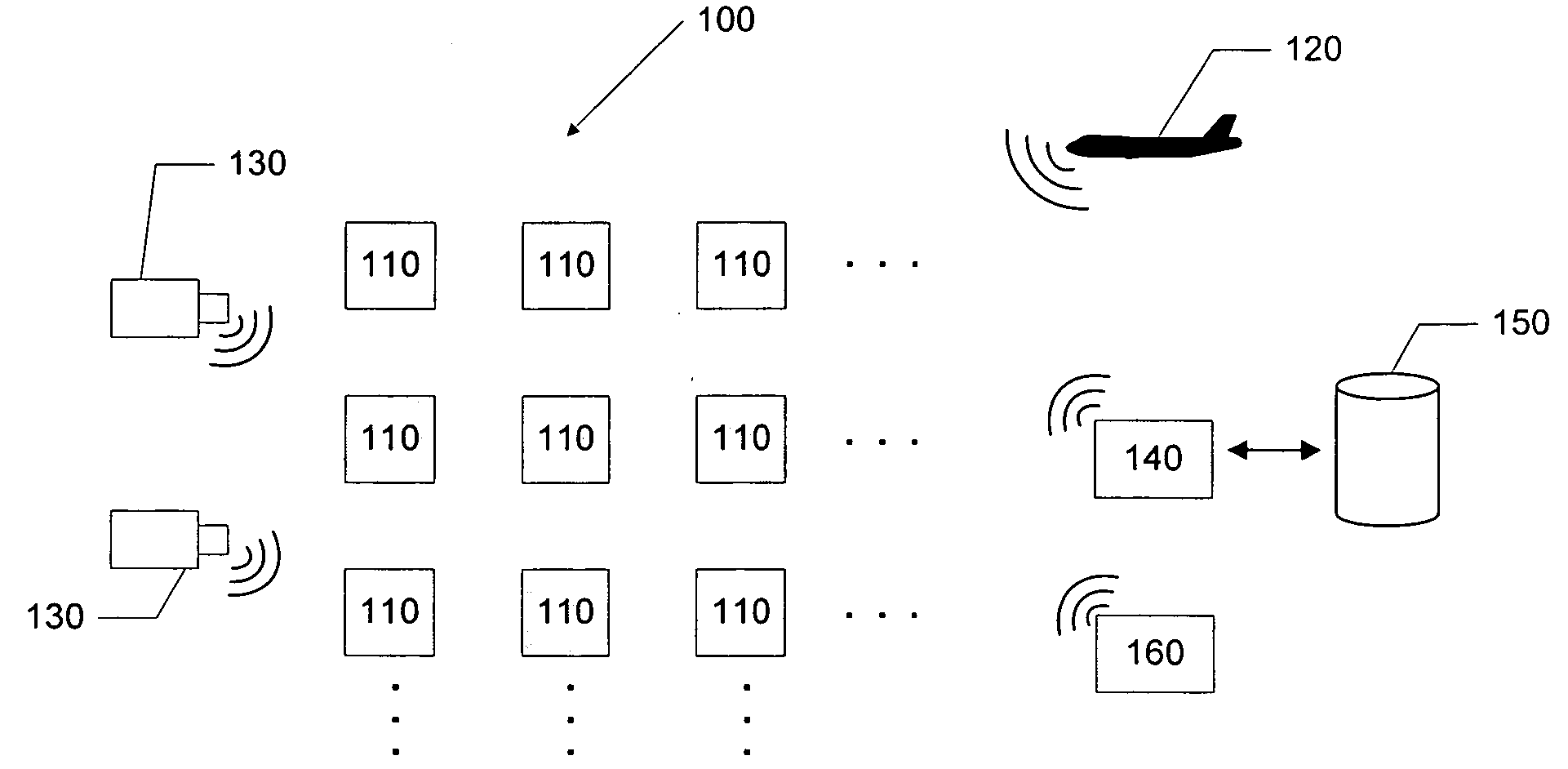
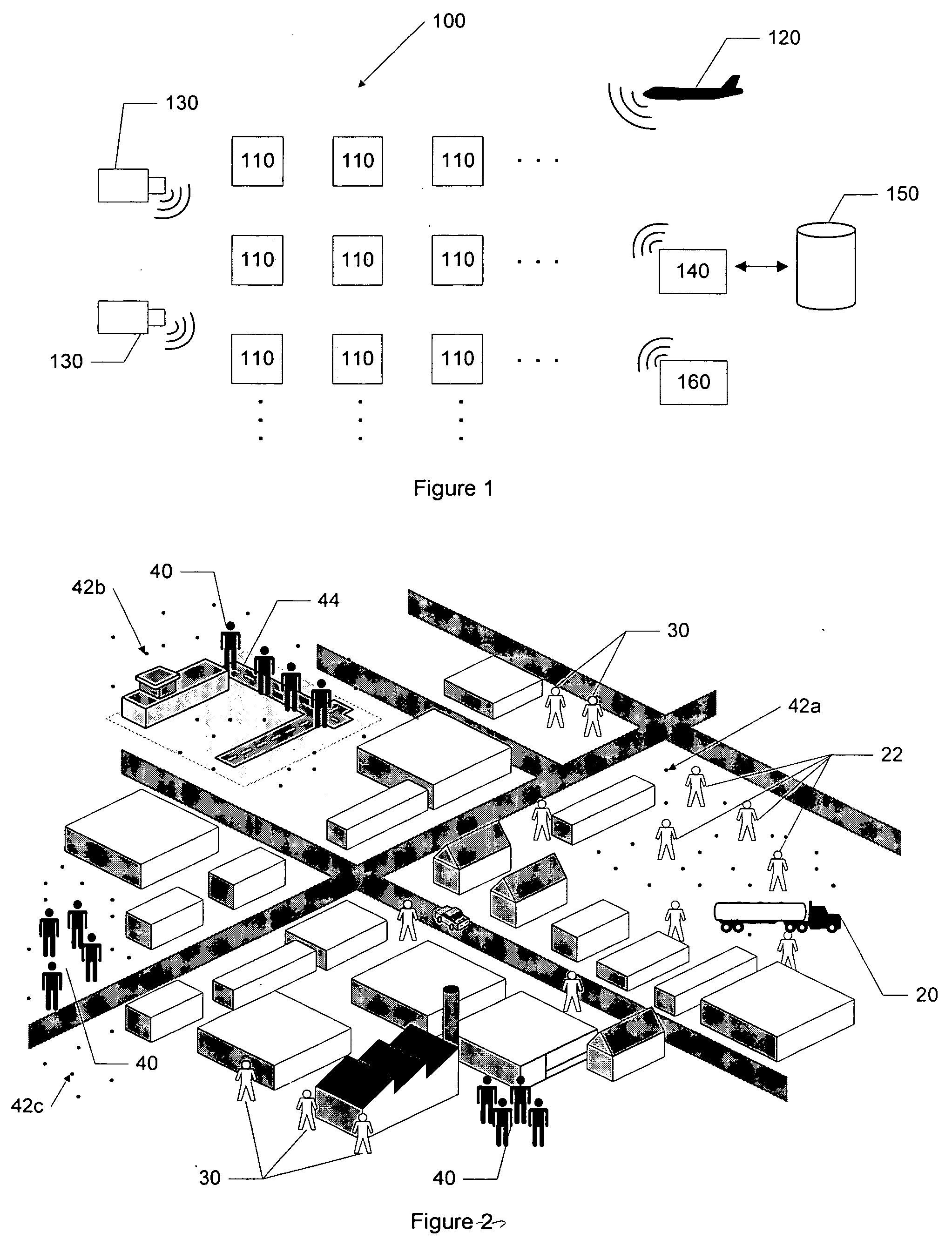
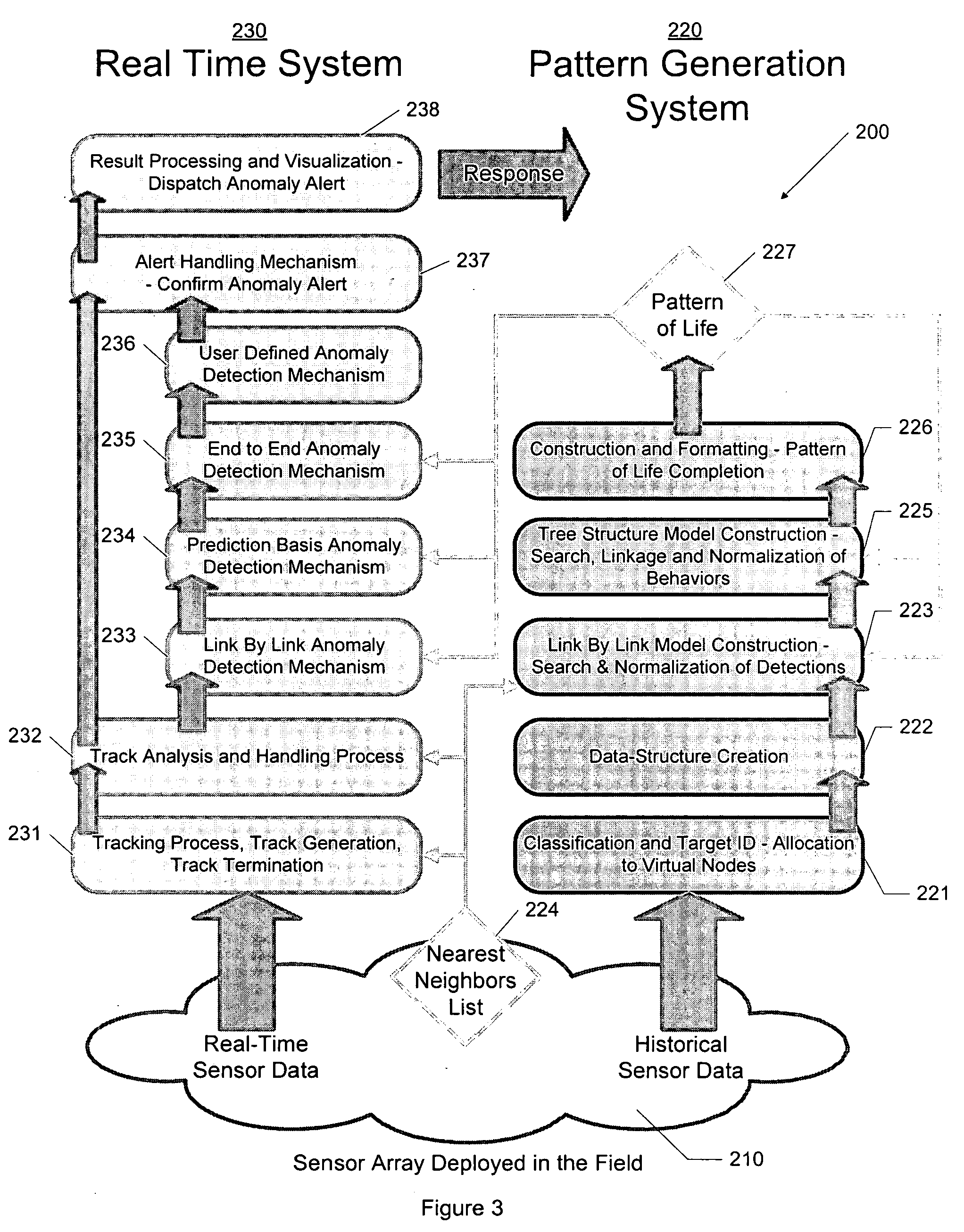
Apparatus and method for surveillance system using sensor arrays
InactiveUS20090195401A1Easy to processGreat communication rangeCharacter and pattern recognitionAlarmsSensor arrayMonitoring system
Embodiments of the invention may include a sensor system and a method used to track the behaviors of targets in an area under surveillance. The invention may include a sensor array located in the area that is capable of sending messages to a user when behavior of a tracked target is determined to be anomalous. In making the determination of anomalous behavior, the sensor system and method may generate and continuously refine a pattern of life model that may examine, for example, the paths a target may take within the sensor array and the end points of the paths taken. The sensor system and method may also incorporate any user defined conditions for anomalous behavior.
Owner:GENERAL DYNAMICS UK
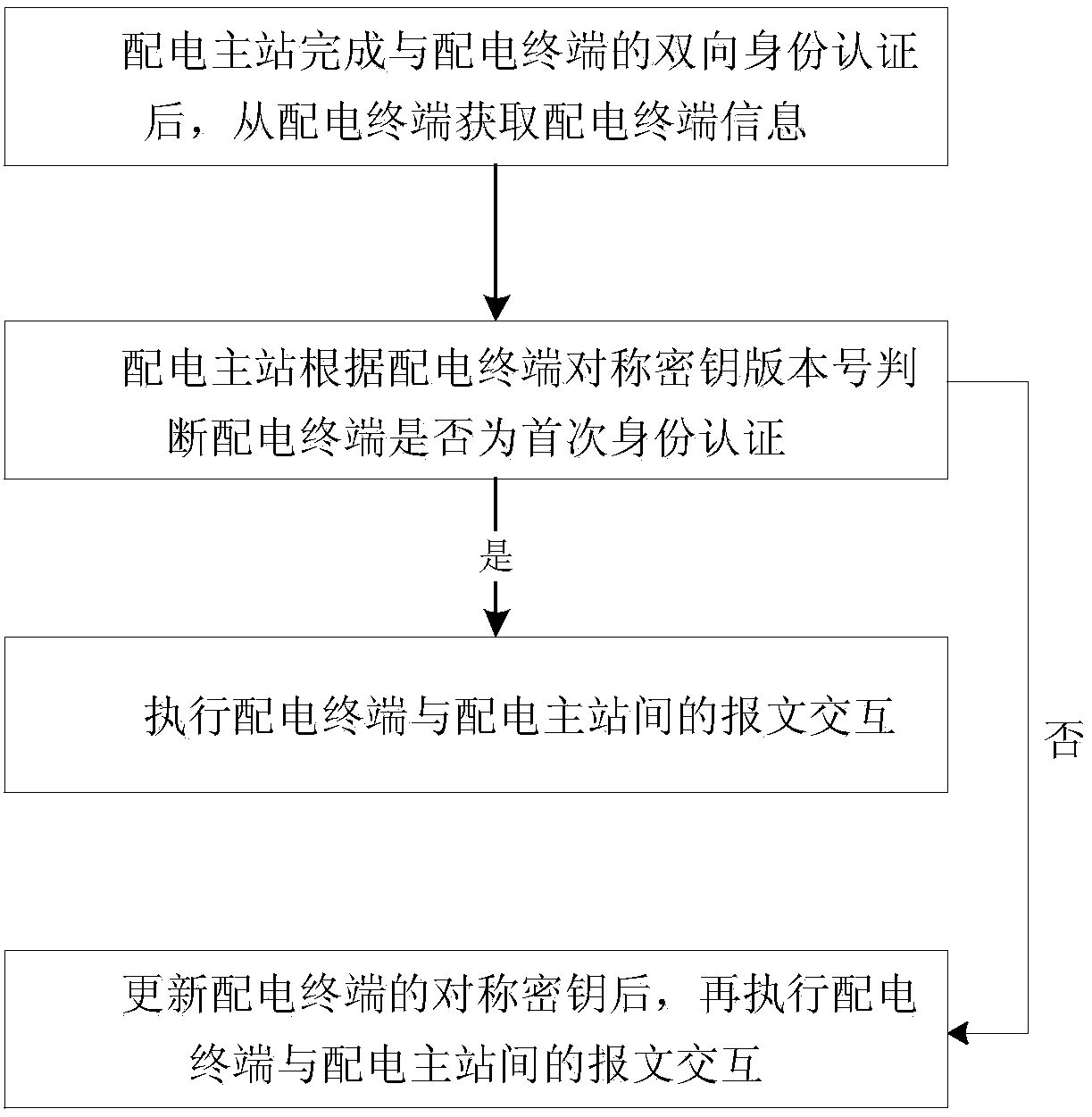
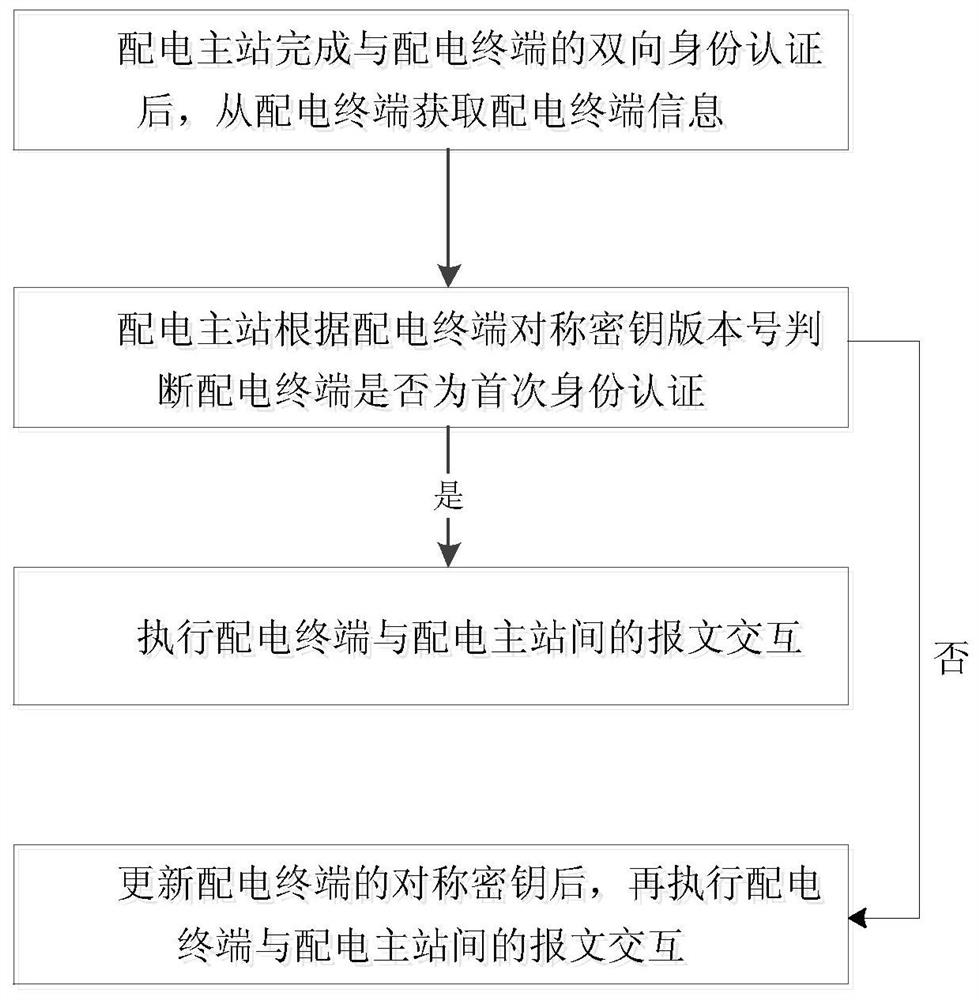
Communication message security interaction method and device of distribution automation system
ActiveCN109257327AImprove the level of security protectionAvoid safety hazardsKey distribution for secure communicationCircuit arrangementsRemote controlConfidentiality
The invention provides a communication message security interaction method and a device of a distribution automation system. After completing two-way identity authentication between a distribution master station and a distribution terminal, a main distribution station obtains distribution terminal information from the distribution terminal. The main distribution station judges whether that distribution terminal is the first identity authentication according to the version number of the symmetrical key of the distribution terminal, if not, the message exchange between the distribution terminaland the main distribution station is carried out; otherwise, after the symmetric key of the distribution terminal is updated, message exchange between the distribution terminal and the distribution master station is performed. The scheme makes up for the shortcomings that the distribution master station can not identify the distribution terminal in the distribution automation system security protection system, and the confidentiality and integrity of the communication message can not be guaranteed, and improves the security protection level of the vertical communication between the distribution master station and the distribution terminal in the distribution automation system. At that same time, the problem that the remote control / parameter set message has the hidden trouble of the replayattack and the like are sol.
Owner:CHINA ELECTRIC POWER RES INST +1
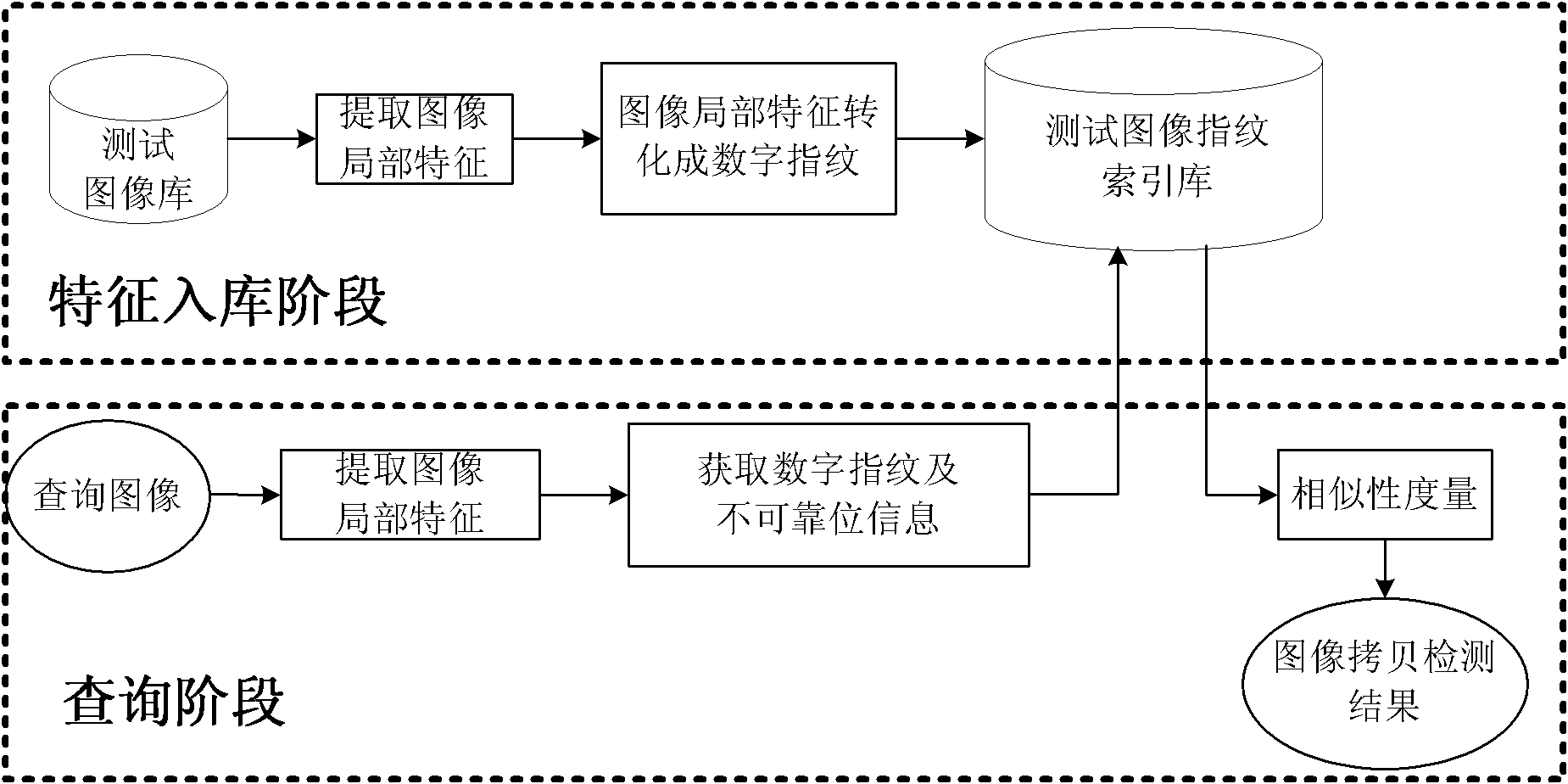
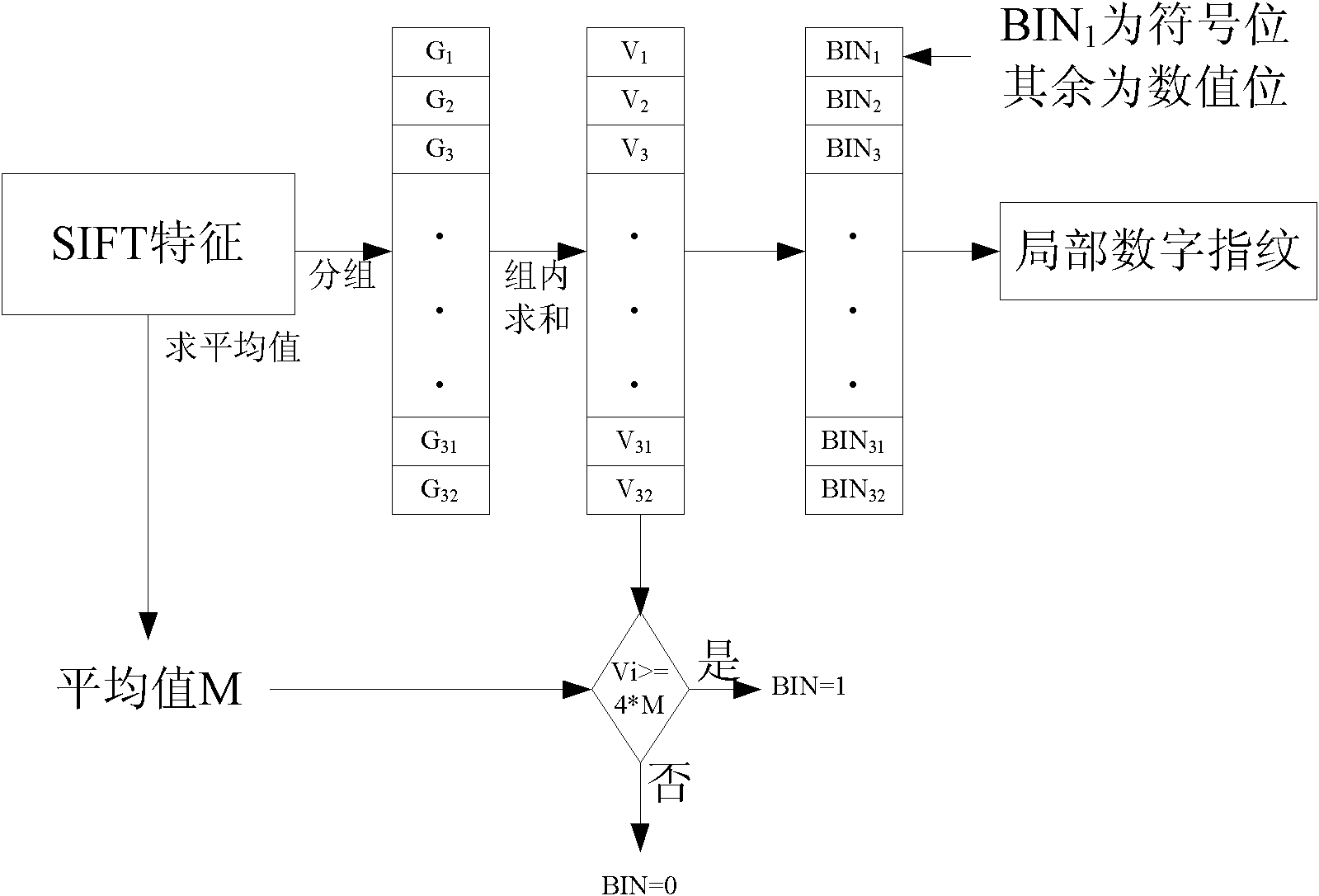
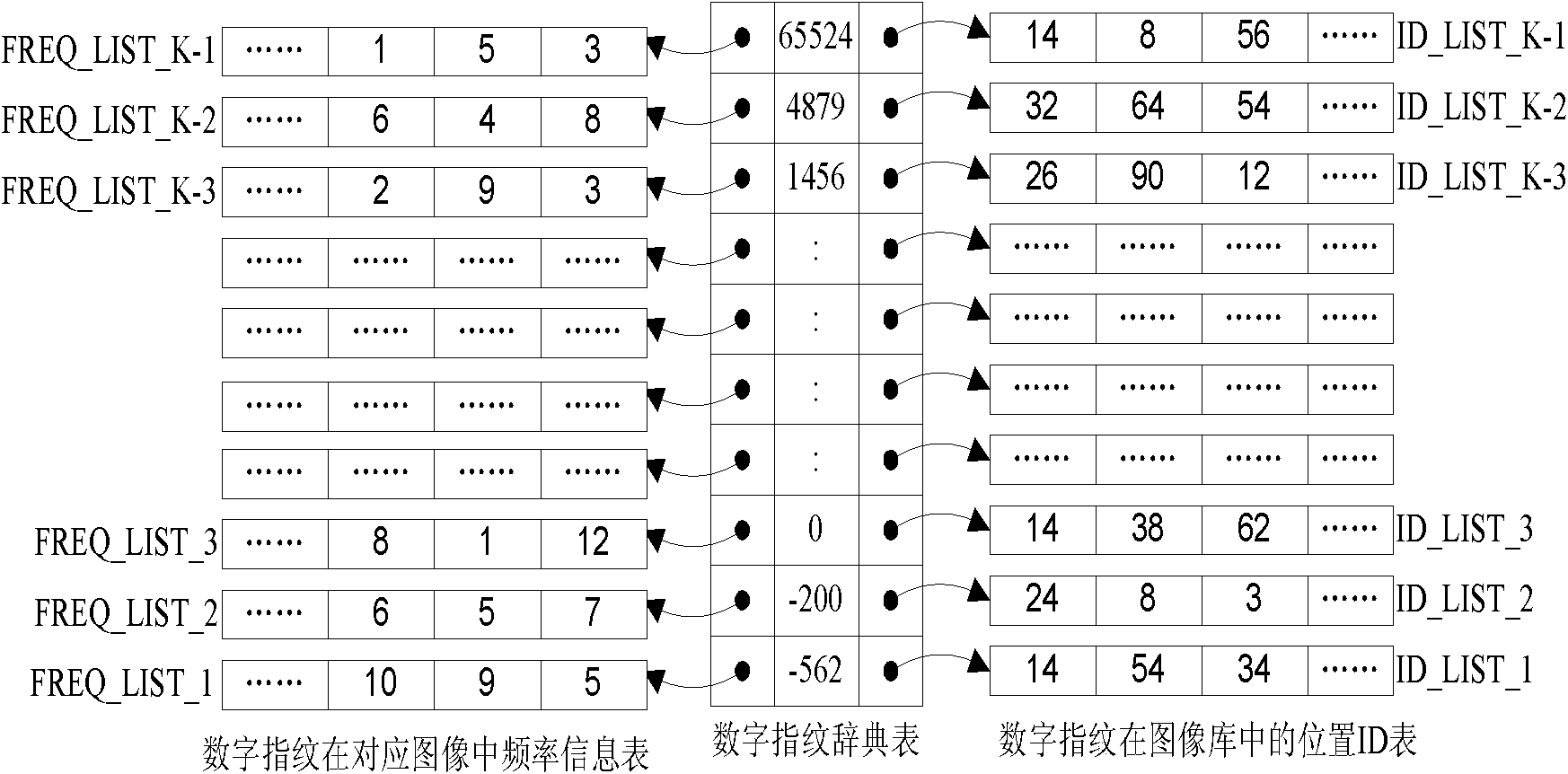
Image copying detection method based on local digital fingerprint
InactiveCN101853486AImprove robustnessStrong identification abilityImage data processing detailsSpecial data processing applicationsImage extractionFeature vector
The invention discloses an image copying detection method based on local digital fingerprint, which comprises the following steps that: local SIFI features are extracted from each image in a tested image library, local digital fingerprint conversion is carried out to the high-dimensional SIFT feature vector and the frequency of the fingerprint in each image is calculated so as to establish a digital fingerprint database; and when the image is inquired, the SIFT features are first extracted from the inquired image and then converted into the digital fingerprint and the information of unreliable positions during the conversion process, then inquiry is carried out in an inverted index structure in a tested fingerprint library by integrating the unreliable information so as to quickly obtain and inquire a tested image set associated with the local digital fingerprint of the inquired image, measure the similarity of the inquired image and the associated tested image and judge whether is image is copied. In the detection of the copying performance, the method has very good recall rate and precision; and in detecting the copying efficiency, the method can also detect the copying of the inquired image.
Owner:HUAZHONG UNIV OF SCI & TECH
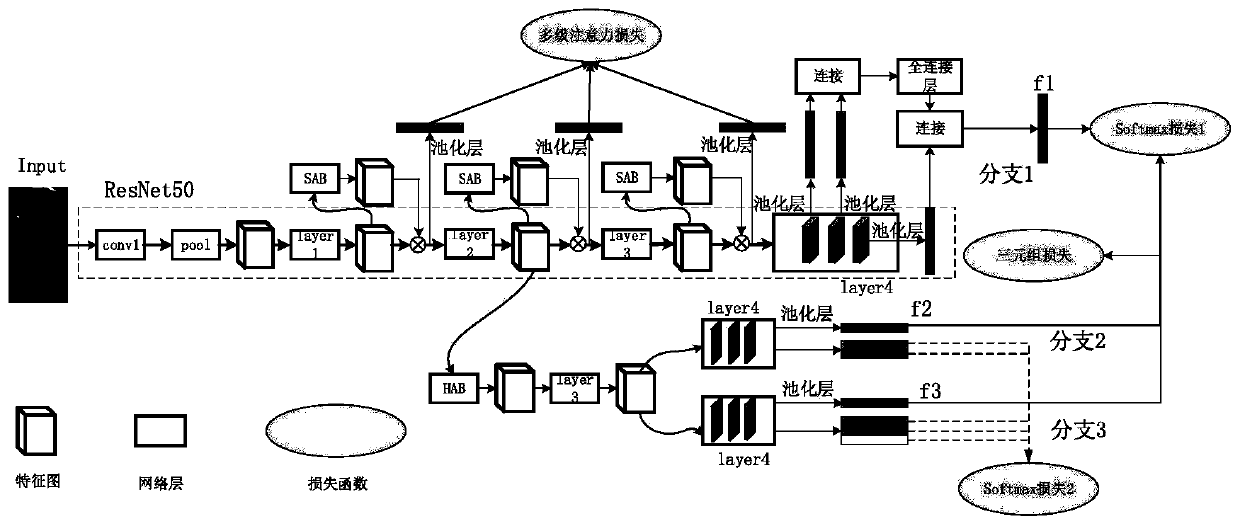
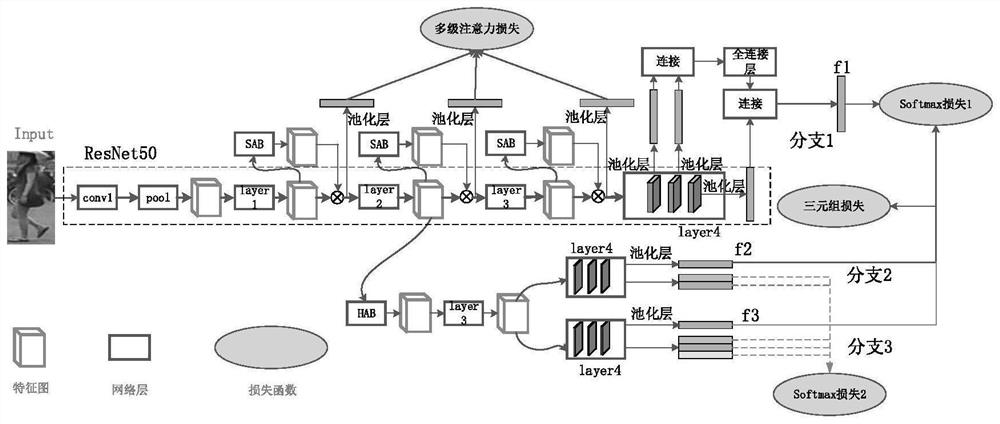
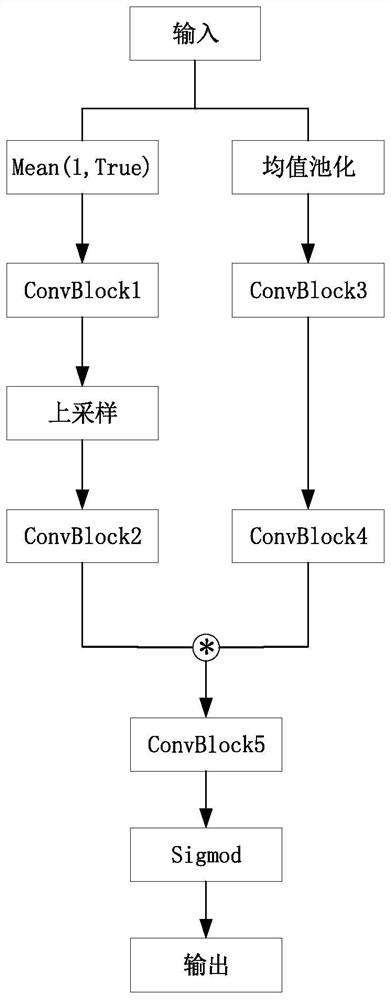
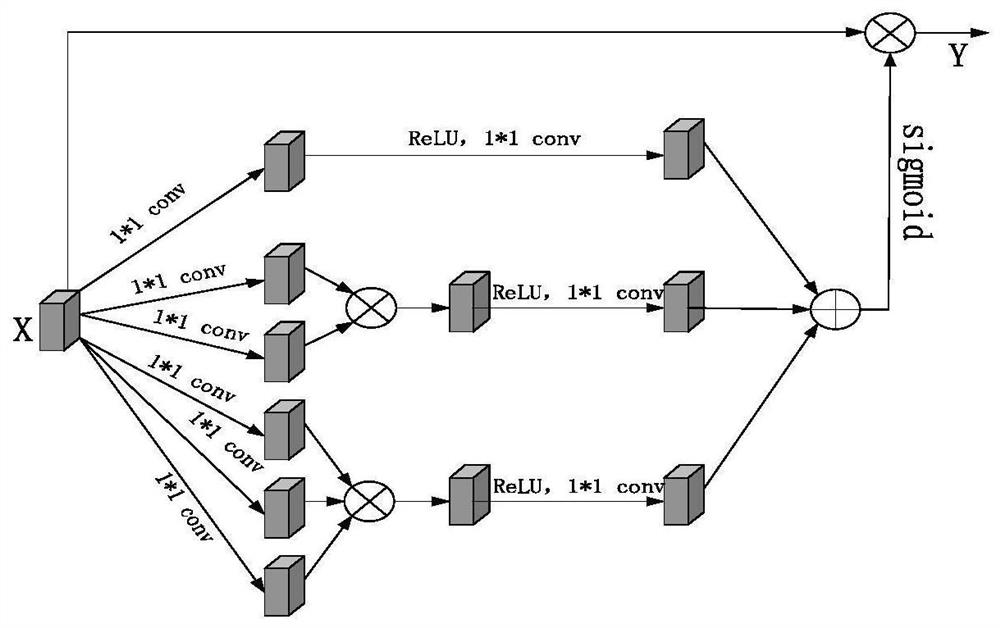
Image pedestrian re-identification method and system based on multi-attention joint learning
ActiveCN111539370AImprove learning effectStrong identification abilityCharacter and pattern recognitionNeural architecturesImaging processingFeature extraction
The invention discloses an image pedestrian re-identification method and system based on multi-attention joint learning, and belongs to the technical field of image processing. Soft attention and high-order attention are introduced into a ResNet50 feature extraction network; by utilizing the complementary effect of two different types of attention on feature extraction, the learning ability of thefeature extraction network on pedestrian features is improved, so that the feature extraction network pays attention to more discriminative features in pedestrian images. In order to obtain more accurate attention features, a multistage attention loss function is provided, the loss function is utilized to guide training and learning of the feature extraction network, and the learning ability of the feature extraction network for pedestrian features is further improved. When pedestrian global features are learned, intermediate features in the feature extraction network are fused, learning of pedestrian local features is enhanced, the ability of the network to learn subtle differences between pedestrian features is improved, and the performance of the network in image pedestrian re-identification is improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Two-dimensional code compiling method
InactiveCN103177281AImprove aestheticsAvoid influenceRecord carriers used with machinesData compressionTerra firma
The invention discloses a two-dimensional code compiling method. The two-dimensional code compiling method comprises the following steps of: on the basis of a self-adaptive code compiling extended black and white code compiling technology and a code compiling scheme applicable to different multimedia, introducing an interweaving technology into an error-correcting code compiling technology by using a data compression technology with an open structure during compression code compiling; and adopting an advanced morphologic image pre-processing technology based on multi-scale structural analysis. The two-dimensional code compiling method has the advantages that a two-dimensional code is superior to the conventional two-dimensional code standard in terms of information bearing capacity, robustness, safety, reliability and adaptability; and coding and decoding bottom-layer supporting software provides technical support for various types of application of the two-dimensional code to the field of the internet of things in an open interface mode, the market monopoly position of the conventional foreign two-dimensional code standard can be broken, the chaotic situation of the conventional domestic two-dimensional code application is changed, and a firm foundation is laid for the development of the internet-of-things industry.
Owner:江苏圆坤二维码研究院有限公司
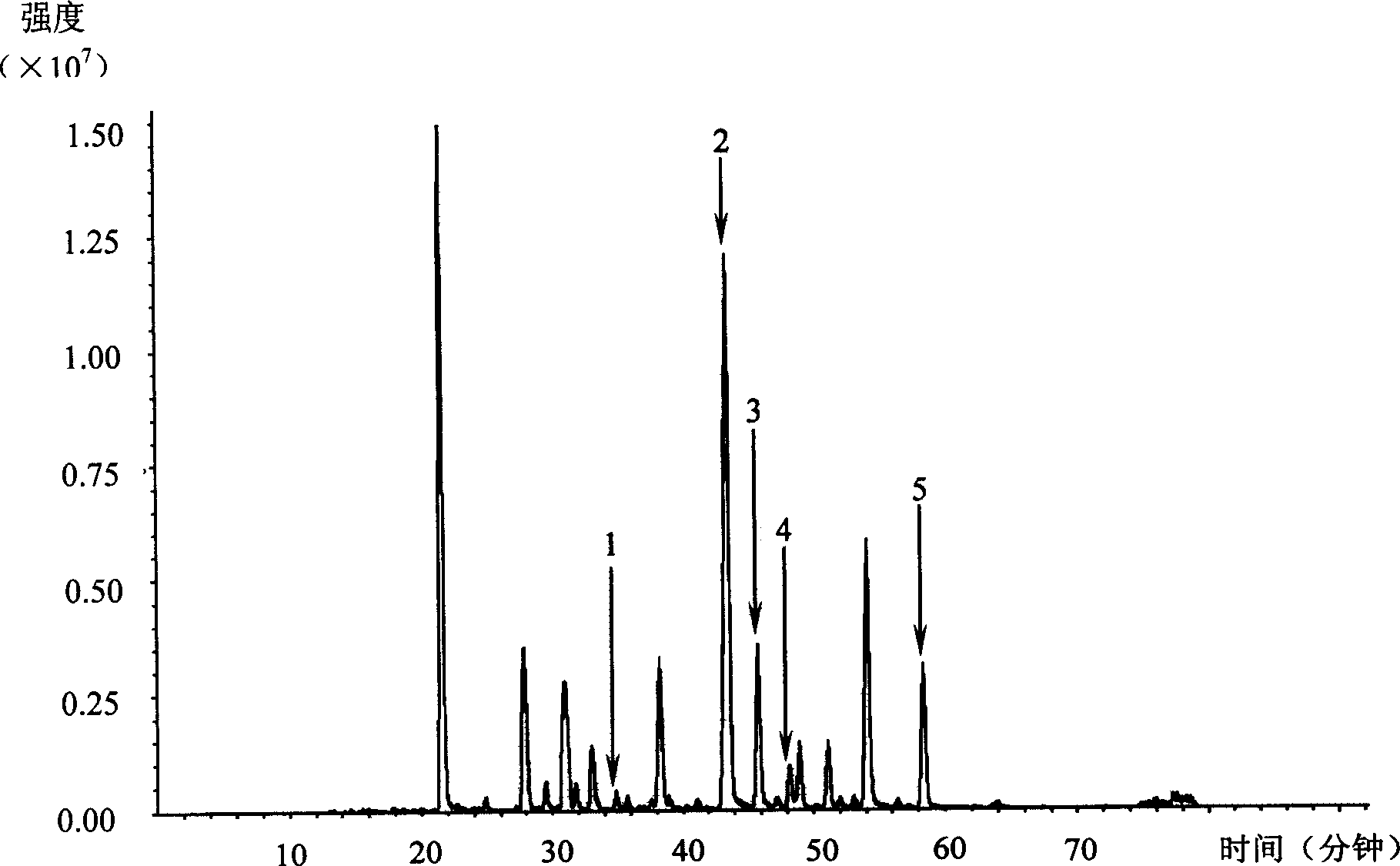
Method for identifying medicinal materials using characteristic atlas
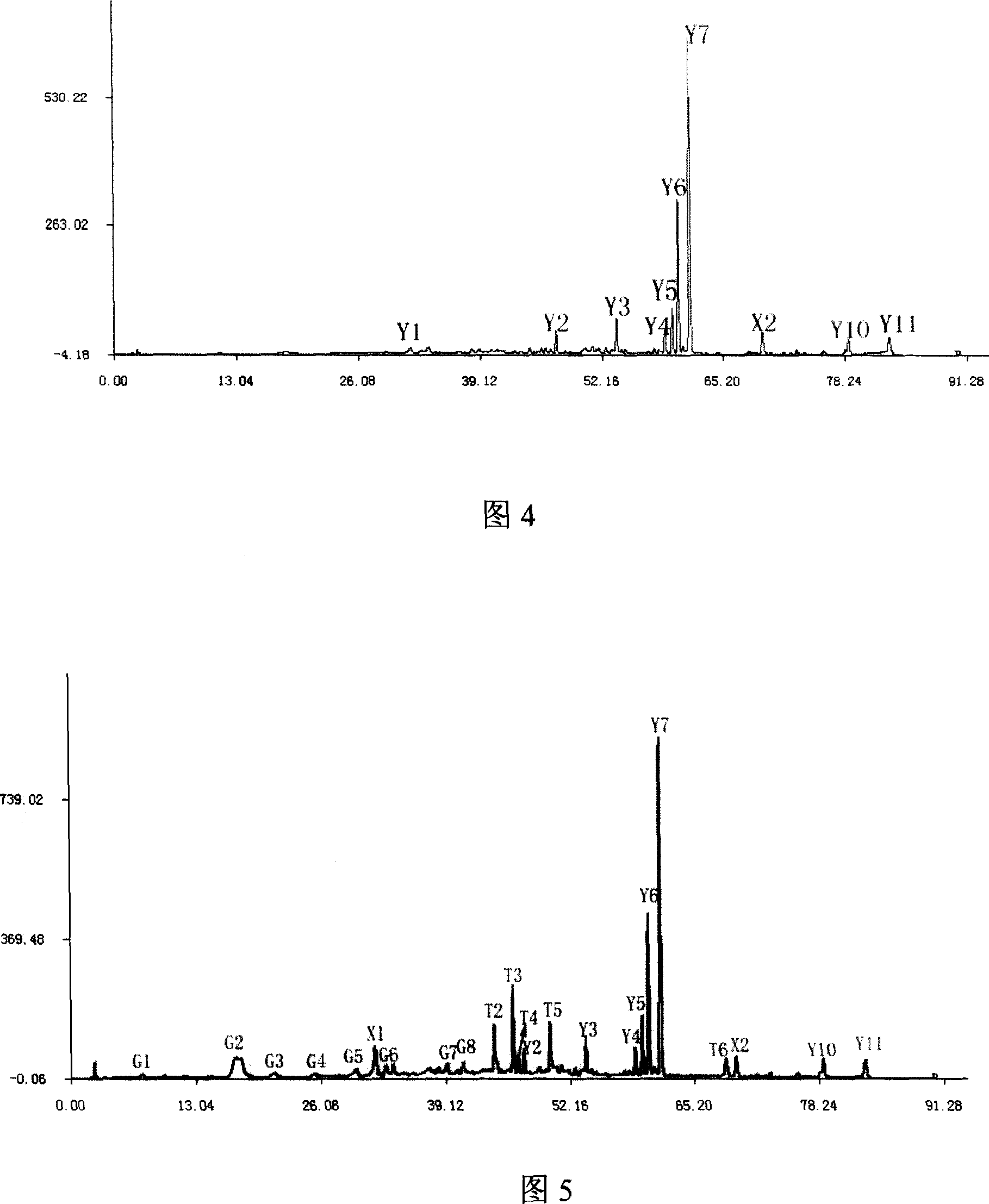
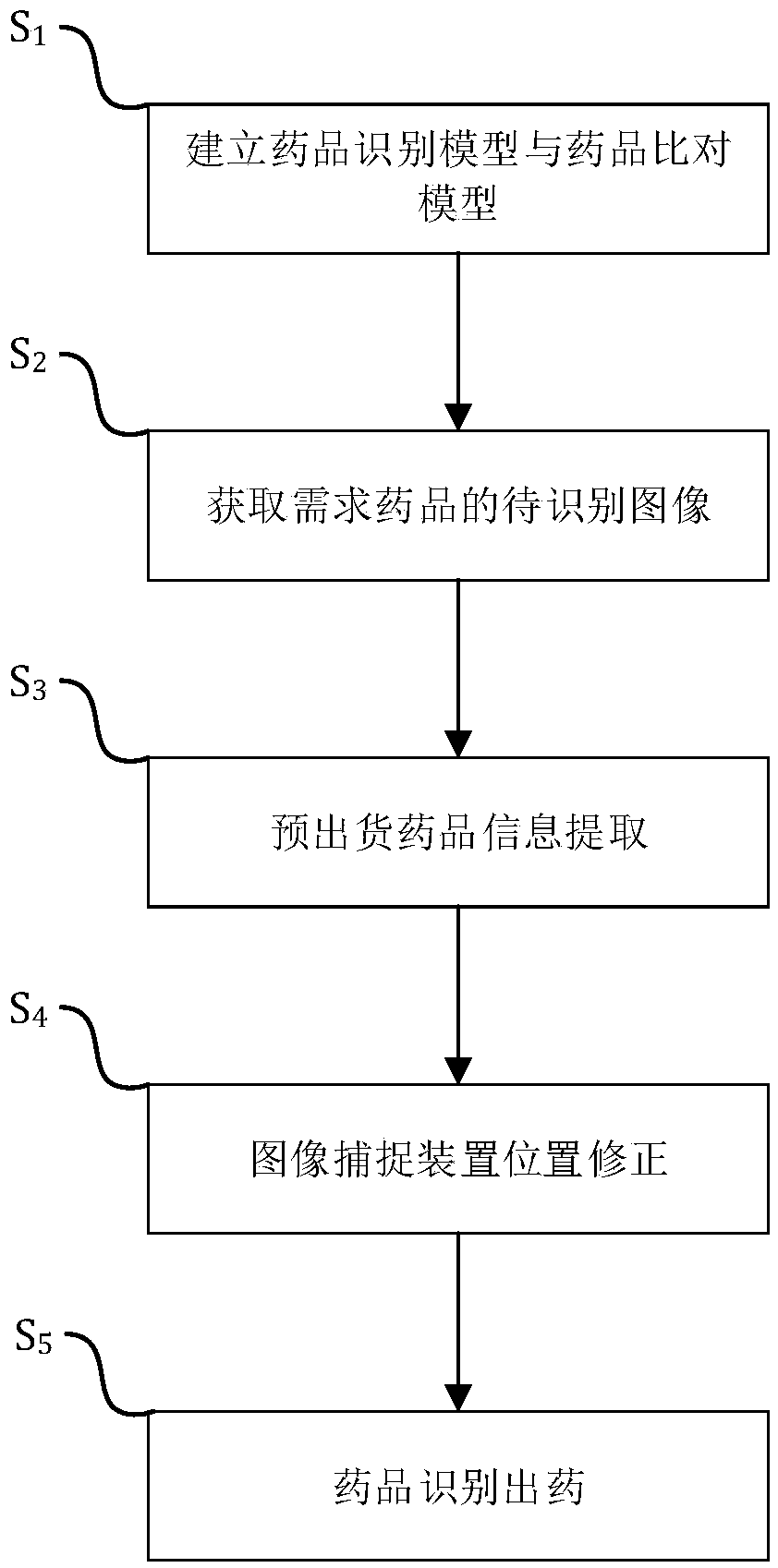
InactiveCN1588050AImprove stabilityImprove featuresComponent separationPattern recognitionData acquisition
The invention relates to a identification method for drugs with characteristic graphoes. The method acquire the characteristic graphoes with liquid phase chromaspectrum-mass spectrum combining technology and identify medicine with the characteristic graphoes. The identification method provided by the invention is based on the characteristic graphoes,the steps includes data acquirement, chromatography matching, the data normalization processing,the characteristic selection and the characteristic graphoes establishment. The invention has the following advantages and remarkable effect compared to the current method of adopting the original fingerprint map to identify drugs: 1)the specification of the data acquisition system is low,the characteristic graphoes has good stability, specificity and objectivity; 2)the characteristic graphoes causes the increas of the difference of the sample in the same category and between the different categories, getting better category charateristics, its identifying ability is better than the original fingerprint graphoes; 3)the identification result of the drugs is accurate, available and reliable.
Owner:TSINGHUA UNIV
Primer probe set, kit and detection method for detecting SARS-CoV (Severe Acute Respiratory Syndrome Coronavirus) and MERS-CoV (Middle East Respiratory Syndrome Coronavirus)
InactiveCN108060266AQuick judgmentShort timeMicrobiological testing/measurementAgainst vector-borne diseasesMiddle East respiratory syndrome coronavirusRecombinase Polymerase Amplification
The invention discloses a primer probe set, kit and detection method for detecting SARS-CoV and MERS-CoV based on Recombinase Polymerase Amplification (RPA) detection. The primer probe set for detecting SARS-CoV and MERS-CoV based on the RPA detection comprises primers for nucleotide sequences as shown in SEQ ID NO.1-4 and probes for nucleotide sequences as shown in SEQ ID NO. 5-6. The invention further provides the kit for detecting SARS-CoV and MERS-CoV based on the RPA detection, wherein the kit comprises the primer probe set. By adopting the technical scheme, the sensitivity, specificity and simplicity for detecting SARS-CoV and MERS-CoV are obviously improved.
Owner:北京卓诚惠生生物科技股份有限公司
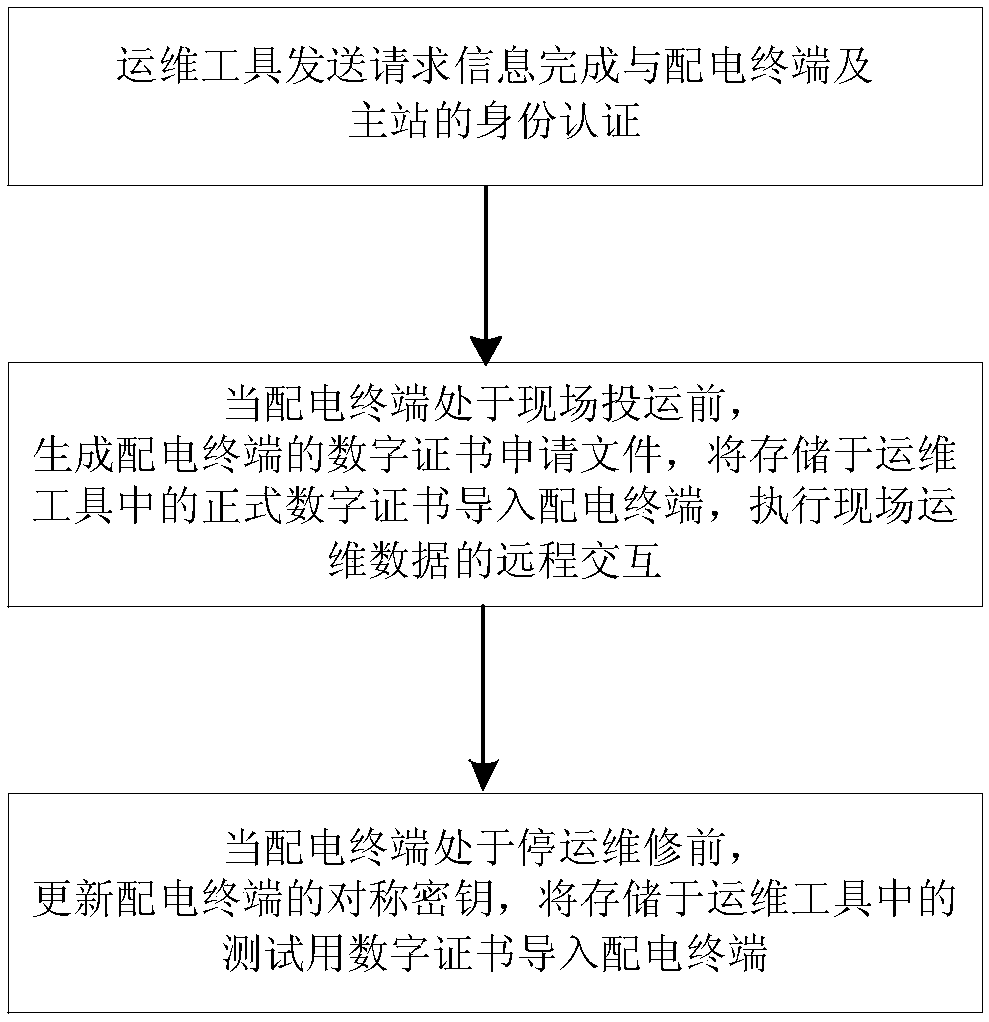
Method and a device for safely interacting on-site operation and maintenance data
ActiveCN109257328APrevent imitationAvoid destructionKey distribution for secure communicationCircuit arrangementsMaster stationComputer terminal
The invention relates to a method and a device for safely interacting on-site operation and maintenance data, comprising the following steps: an operation and maintenance tool sends request information to complete identity authentication with a power distribution terminal and a master station; generating a digital certificate application file of the distribution terminal before the distribution terminal is put into operation on site, importing a formal digital certificate stored in an operation and maintenance tool into the distribution terminal, and performing remote interaction of the fieldoperation and maintenance data; when the distribution terminal is out of service, the symmetric key of the distribution terminal is updated, and the test digital certificate stored in the operation and maintenance tool is imported into the distribution terminal. This scheme improves the management flow of digital certificate and symmetric key, and makes up for the security loopholes in the operation and maintenance process of distribution terminals, so as to improve the security protection level of field application and operation and maintenance of distribution terminals.
Owner:CHINA ELECTRIC POWER RES INST +1
Method for overall monitoring kidney-tonifying body-strengthening tablet quality
InactiveCN101011480AStrong identification abilityComprehensive monitoringComponent separationDigestive systemProcess qualityMedicine
The invention relates to a method for detecting the quality of kidney tonifying tablet, which comprises that first, building the standard fingerprint diagram of barren wort, doddor, woodwardic, middle extract and final tablet; second, checking the fingerprints of tested barren wort, doddor, woodwardic, middle extract and final tablet; third, comparing the fingerprints with standard ones. The groups with met similarity can be used as material to be used in production, and the qualified middle extract is used in next process, and the final tablet is used as final product. The invention can realize full-process quality detection.
Owner:MASSON GROUP
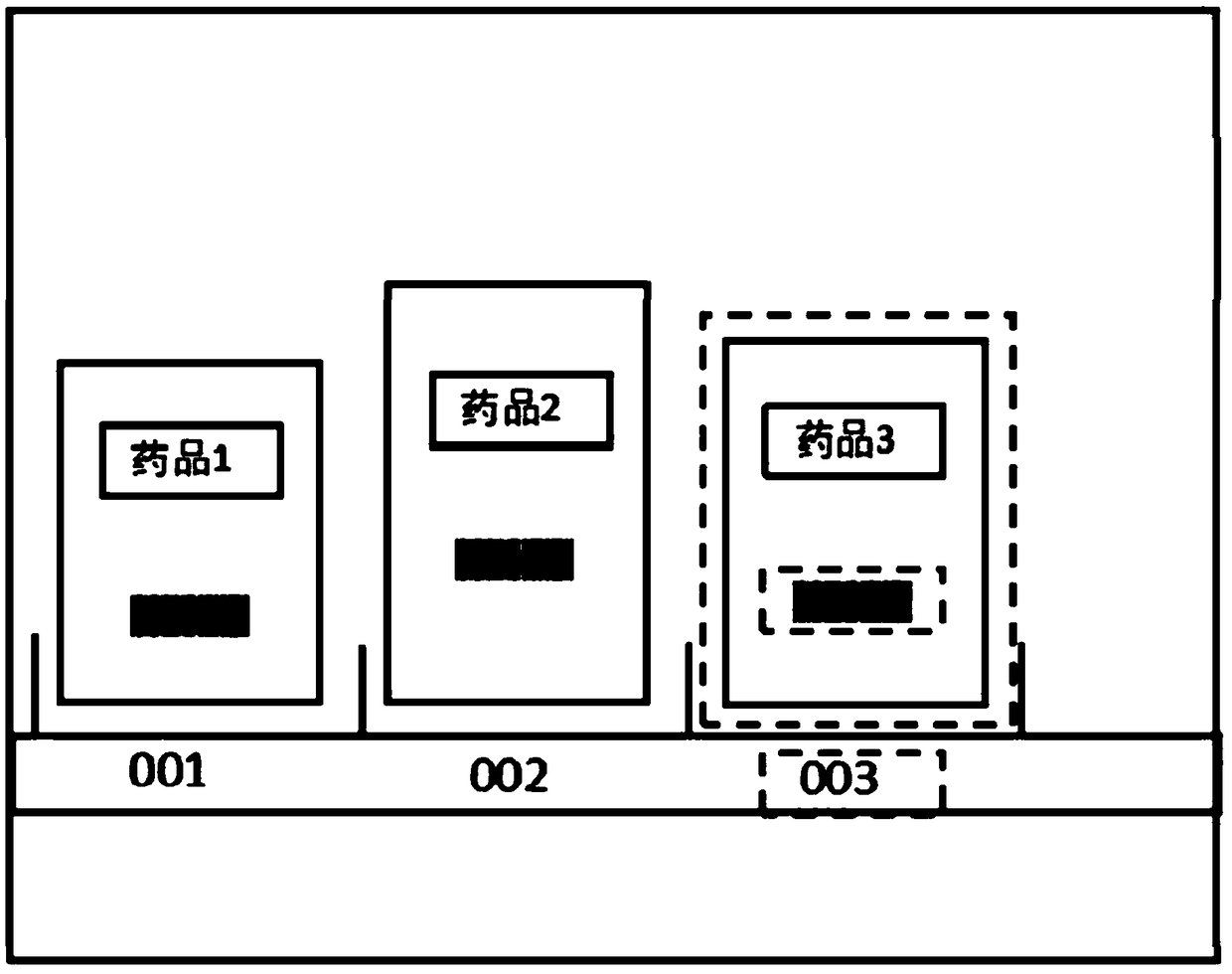
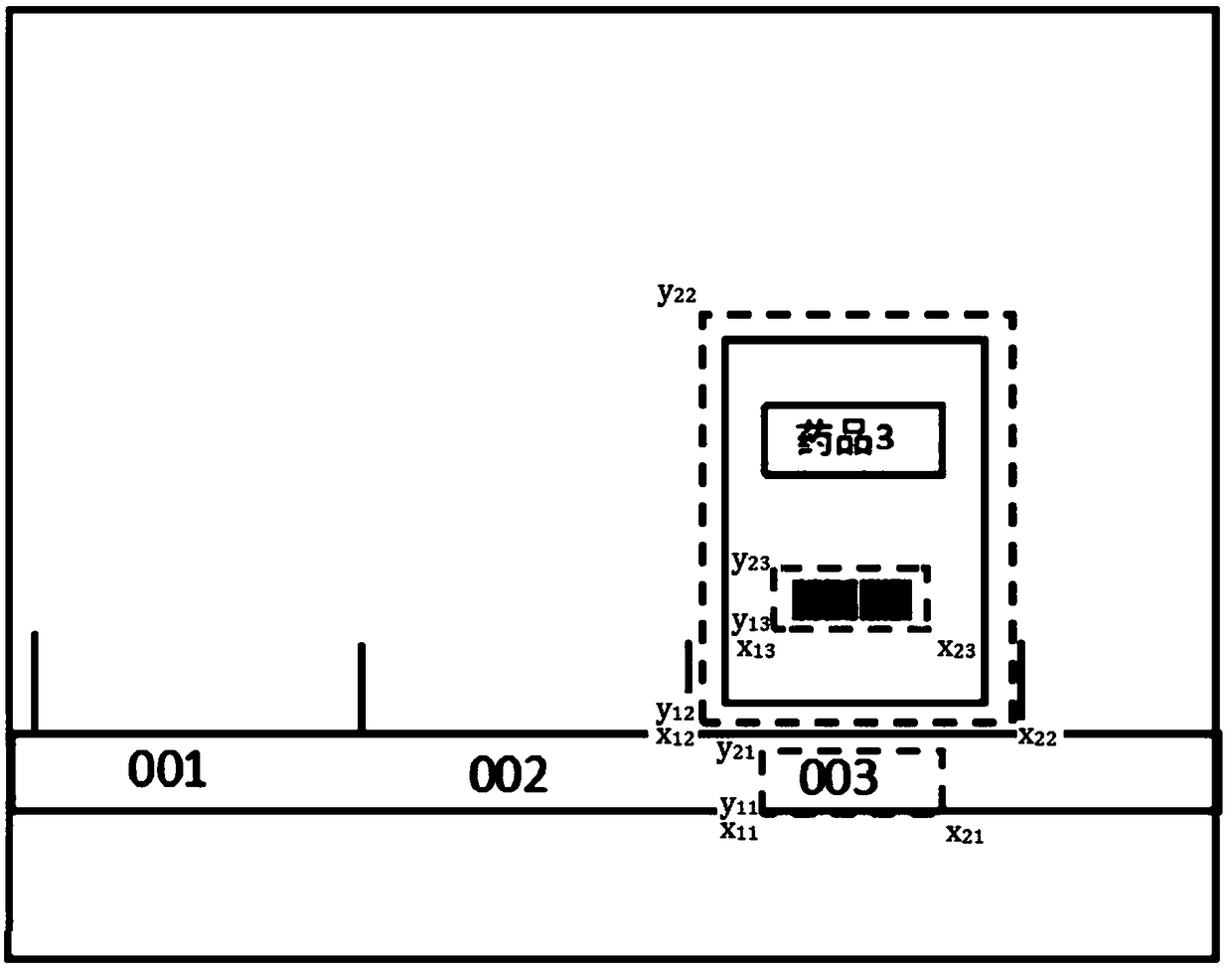
Drug cabinet intelligent positioning management method and system
ActiveCN109472297APrevent missellingImprove management efficiencyImage enhancementGeometric image transformationImage detectionManagement efficiency
The invention relates to a medicine cabinet intelligent positioning management method and a medicine cabinet intelligent positioning management system in the technical field of medicine retail, comprising the following steps: S1, establishing a medicine identification model and a medicine comparison model; S2, obtaining an image to be identified of the medicine in demand; 3, extract that pre-shipment drug information; 4, position correction of that image capture device; S5. Drug identification. The invention uses the image detection technology to match the expected medicine of the customer with the medicine to be shipped to prevent the wrong sale of the medicine and improve the safety of the medicine. At that same time, the medicine information in the medicine cabinet can be update in realtime, the medicine management efficiency in the medicine cabinet can be improved, and the management cost can be reduce.
Owner:陕西鑫泉通道网络科技有限公司
DNA bar code primer pair, kit and method for identifying Taxus chinensis species
InactiveCN105177151AEfficient identificationRich genetic variationMicrobiological testing/measurementDNA/RNA fragmentationDNA barcodingA-DNA
The invention discloses a DNA bar code primer pair, kit and method for identifying Taxus chinensis species. The kit comprises the following DNA bar code primer pair including an upstream primer Taxus Indel-F(SEQ ID NO.1) and a downstream primer Taxus Indel-R(SEQ ID NO.2). DNA bar codes include the Taxus chinensis DNA bar code, the Taxus chinensis var.mairei DNA bar code, the Taxus cuspidata DNA bar code, and the Taxus baccata DNA bar code, wherein the sequence of the Taxus chinensis DNA bar code is shown as SEQ ID NO.3 to SEQ ID NO.6, the sequence of the Taxus chinensis var.mairei DNA bar code is shown as SEQ ID NO.7 to SEQ ID NO.8, the sequence of the Taxus cuspidata DNA bar code is shown as SEQ ID NO.9, and the sequence of the Taxus baccata DNA bar code is shown as SEQ ID NO.10. The kit and the identifying method are simple, easy to implement and capable of being effectively used for Taxus species identification, protection and related research, and results are accurate and reliable.
Owner:CENTRAL SOUTH UNIVERSITY OF FORESTRY AND TECHNOLOGY
Compound amplification detection kit containing forty InDel genetic polymorphic sites of human X chromosome
ActiveCN110578009ALow mutation rateHigh sensitivityMicrobiological testing/measurementInsertion deletionX chromosome
The invention discloses a compound amplification detection kit containing forty InDel genetic polymorphic sites of human X chromosome. The forty InDel sites of the X chromosome and an individual identification location point are amplified simultaneously by a primer group. Compared with a traditional STR genetic marker, an insertion deletion genetic marker used in the compound amplification detection kit has the advantages of low mutation rate and high sensitivity; and the polymorphism detection sites involved in the compound amplification detection kit combine the advantages of an InDel genetic marker and the special genetic characteristics of the X chromosome, and effective supplementary means can be provided for identification of difficult or special cases.
Owner:GUANGDONG HUAMEI ZHONGYUAN BIOLOGICAL SCI & TECH +2
Comprehensive passenger transport hub pedestrian colorful guide sign setting method
InactiveCN101968897AEnhance spatial cognitionImprove transfer efficiencyMaps/plans/charts3D modellingRouting decisionGraphics
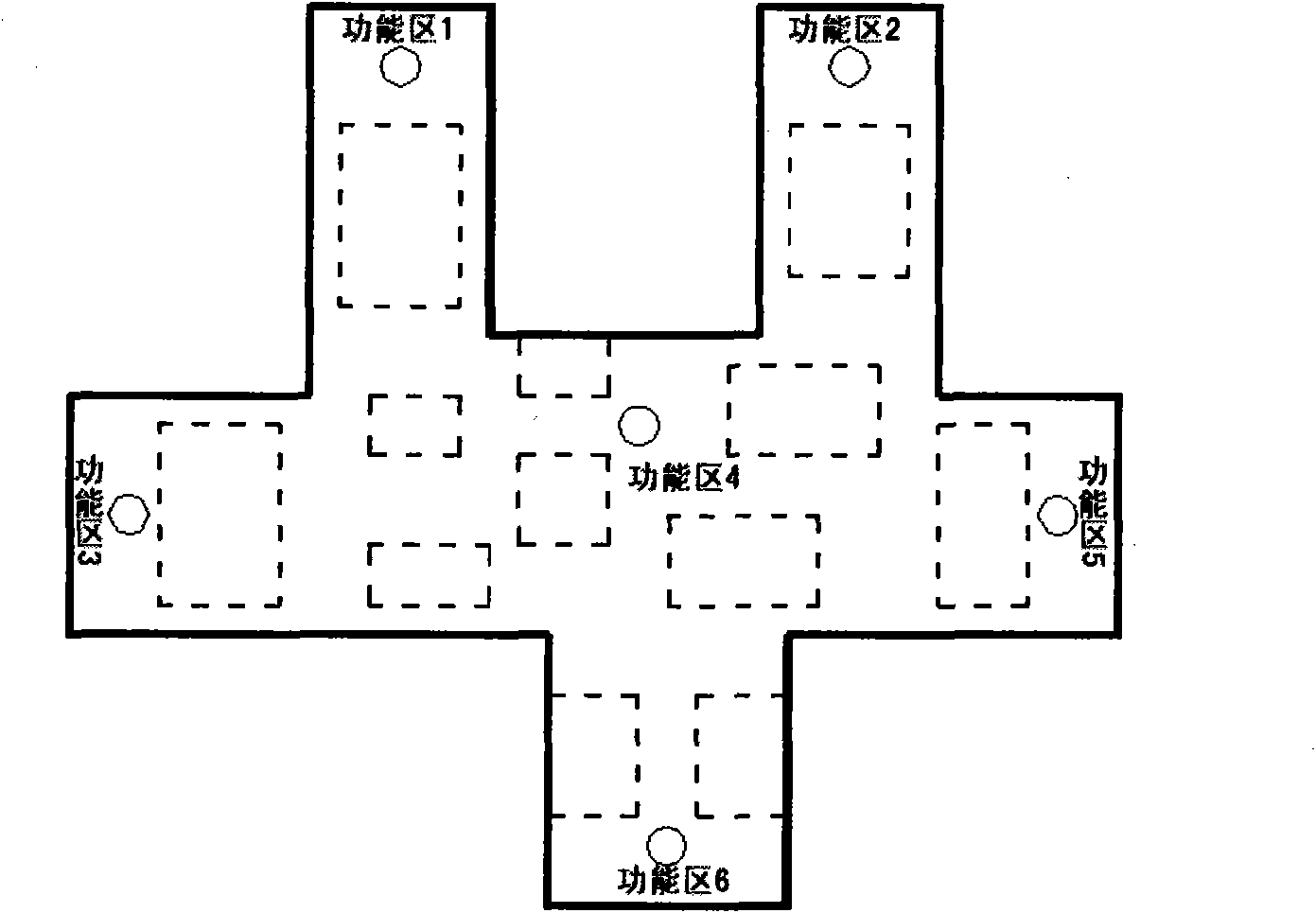
The invention provides a comprehensive passenger transport hub pedestrian colorful guide sign setting method. Comprehensive passenger transport hub pedestrian colorful guide signs comprise comprehensive passenger transport hub spacial colorful graphic signs and direction inducing colorful arrow signs. The comprehensive passenger transport hub spacial colorful graphic sign setting method comprises the steps of: drawing three-dimensional layout charts of a comprehensive passenger transport hub by layers; finding out geometric center positions of main functional zones and route decision points of the layers; and marking names of the functional zones. The direction inducing colorful arrow sign setting method comprises the steps of: drawing a planar layout chart of the comprehensive passenger transport hub; and drawing a planar layout vectorgram of the comprehensive passenger transport hub. The method is used for guiding passengers to select advancing routes in the hub, and has strong identifiability. A computing method for set positions of the direction inducing colorful arrow signs adopts a simple principle of mathematics, is easy to implement through a computer, and has low resource consumption and high computing efficiency.
Owner:HARBIN INST OF TECH
Method for extracting stable spectrum characteristics of solid matter
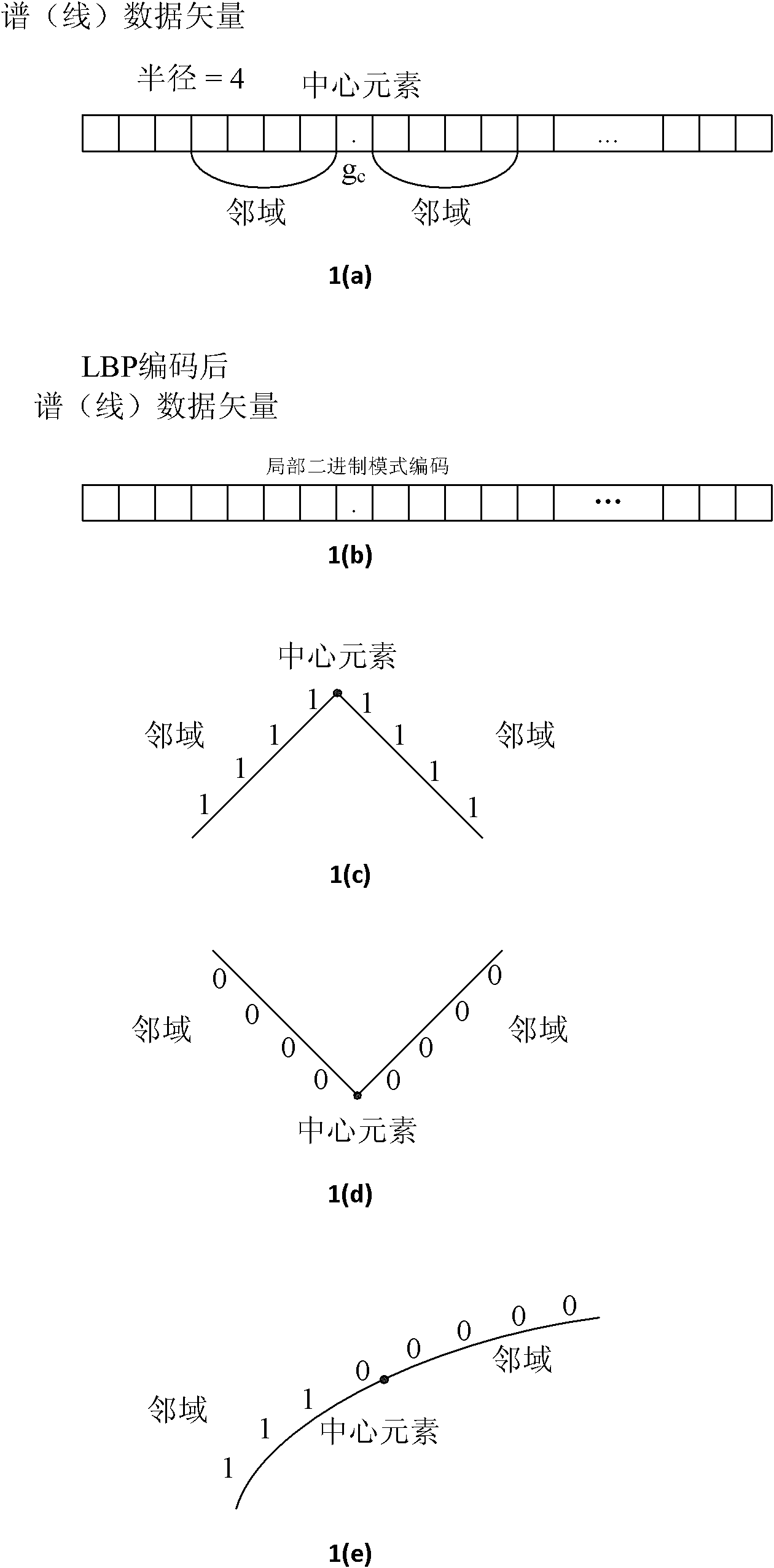
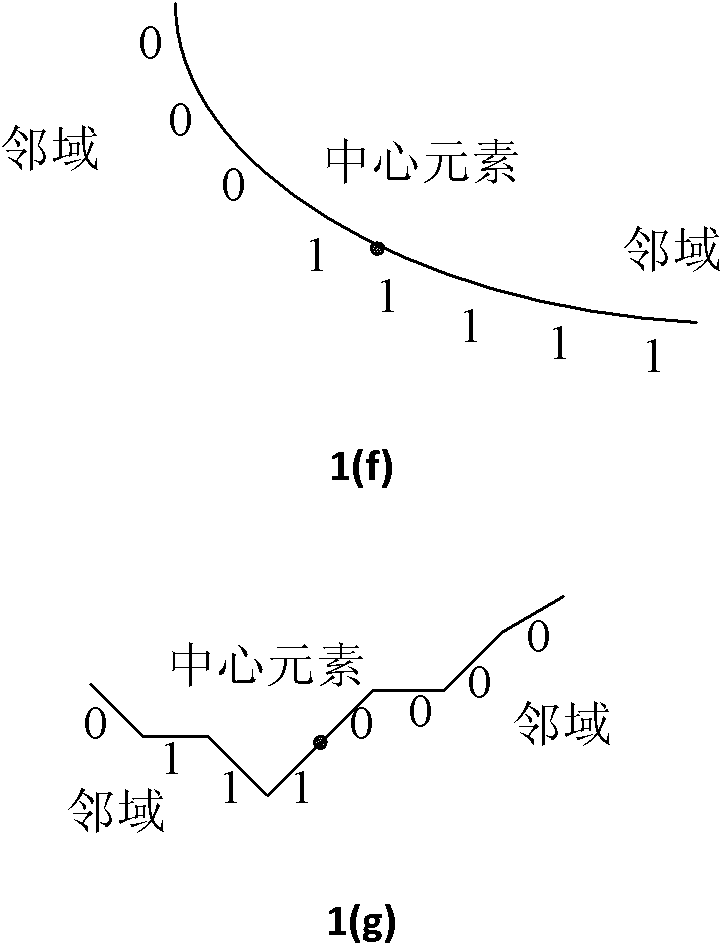
ActiveCN101976337AEfficiently obtain invariant featuresGet invariant featuresCharacter and pattern recognitionMultiscale decompositionFeature extraction
The invention provides a method for extracting stable spectrum characteristics of a solid matter, comprising the steps of: firstly, carrying out multiscale decomposition on spectrum data, then carrying out regional division on the topography under all the scales respectively, carrying out local binary coding on each region so as to complete the expression on shape trends for the spectrum data, then generating a regional characteristic histogram according to the binary coding of each region, sequentially connecting all the regional characteristic histograms of all the regions under the same scale so as to form a spatial enhanced histogram, and finally carrying out weighting and calculating on the obtained spatial enhanced histograms of different scales to obtain a spectrum characteristic vector. The invention is used for extracting the stable intrinsic spectrum characteristics of solid materials under different conditions, has robustness resistant to condition changes and excellent separating capacity, and provides support for spectrum based target identification under complex conditions.
Owner:HUAZHONG UNIV OF SCI & TECH
Interference identification method based on radio spectrum pattern identification
ActiveCN105223552AStrong identification abilityNot easy to simulateWave based measurement systemsFrequency spectrumTime domain waveforms
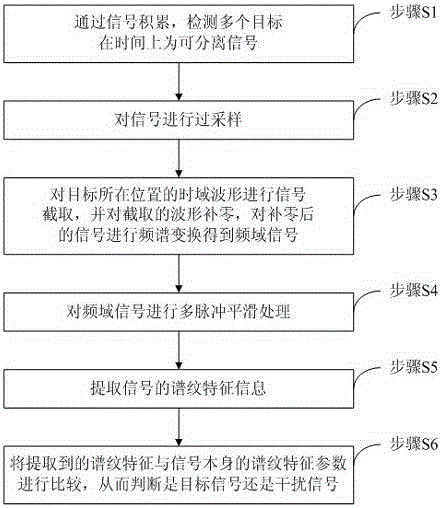
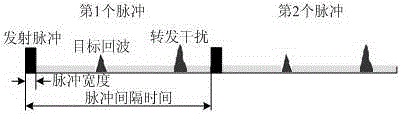
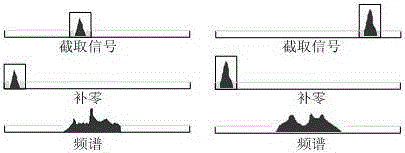
An interference identification method based on radio spectrum pattern identification is disclosed. The method is characterized in that through signal accumulation, detecting a plurality of objects which can be separable signals on an aspect of time; then, carrying out oversampling on the signals; and then carrying out signal interception on a time domain waveform of a position where the objects are located, carrying out zero fill on the intercepted waveform, carrying out frequency spectrum transformation on the signals after zero fill so as to acquire a frequency domain signal; carrying out multiple pulse smoothing processing on the frequency domain signal; extracting spectrum line characteristic information of the signal; finally, comparing the extracted spectrum line characteristic to a signal parameter so as to determine whether the signal is an object signal or an interference signal. By using the method of the invention, an identification capability to the interference signal is high, and good robustness and realizability are possessed.
Owner:SHANGHAI RADIO EQUIP RES INST
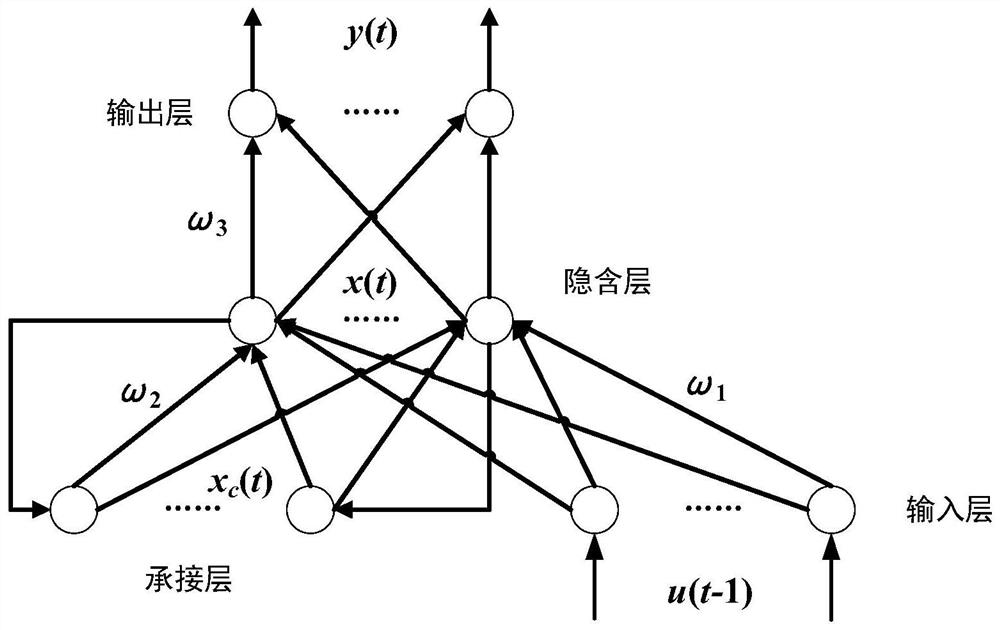
SCR denitration system bad data identification method based on Elman neural network
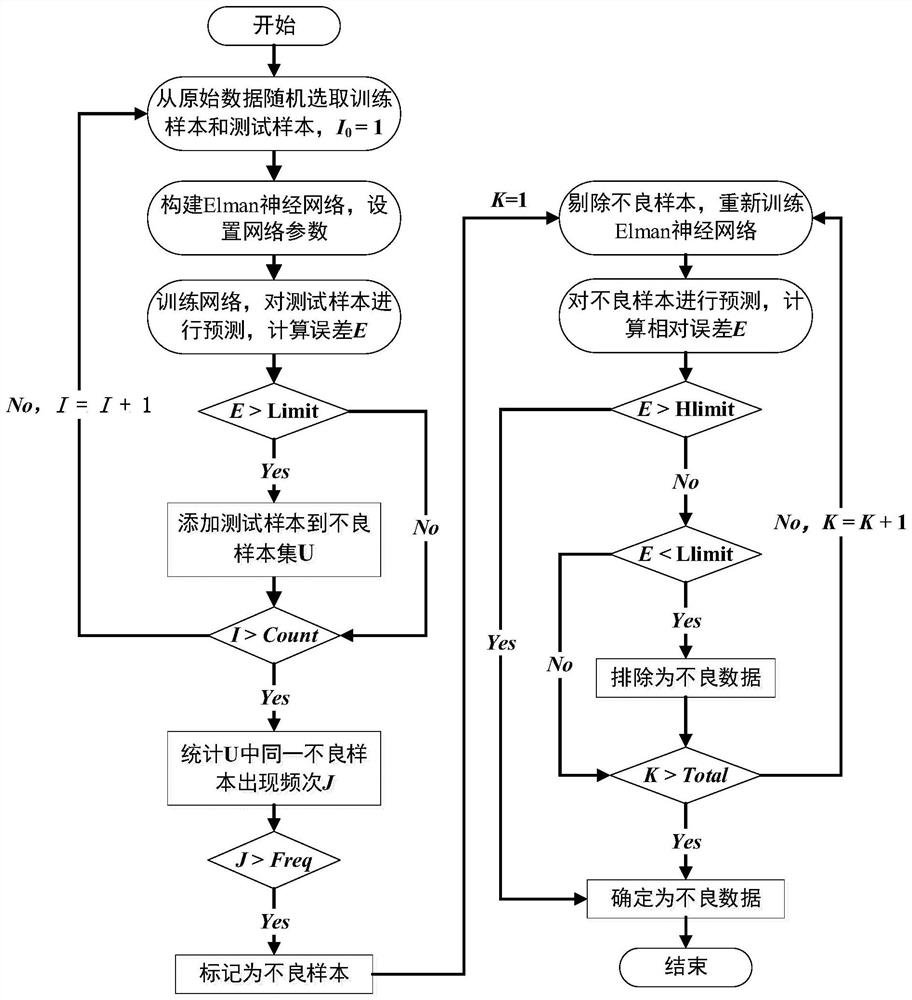
PendingCN112016248AStrong predictive and discerning abilityAvoid misjudgmentDesign optimisation/simulationNeural architecturesMachine learningEngineering
The invention provides a method for predicting, estimating and identifying bad data of a denitration system based on an Elman neural network. The method mainly comprises the following steps: acquiringoriginal data, constructing an Elman neural network, learning the neural network, screening, marking bad samples, removing the bad samples, then reconstructing and training the Elman neural network,and finally inspecting and correcting the bad samples by using the trained neural network. According to the invention, the bad data of the denitration system is predicted, estimated and identified based on the Elman neural network; the influence of bad samples on the network prediction precision is reduced by constructing and training the Elman neural network for many times; the subjectivity of manual selection is avoided by randomly testing an original sample; by optimizing sample construction and training the Elman neural network, the identified bad samples are inspected and corrected, misjudgment of the bad samples is avoided, and the method has the advantages of being suitable for large fluctuation and time-varying characteristics of denitration system data parameters, high in identification precision and accuracy and capable of being widely applied to identification of bad data in the field of flue gas denitration.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Speaker recognition method and system based on multi-source attention network
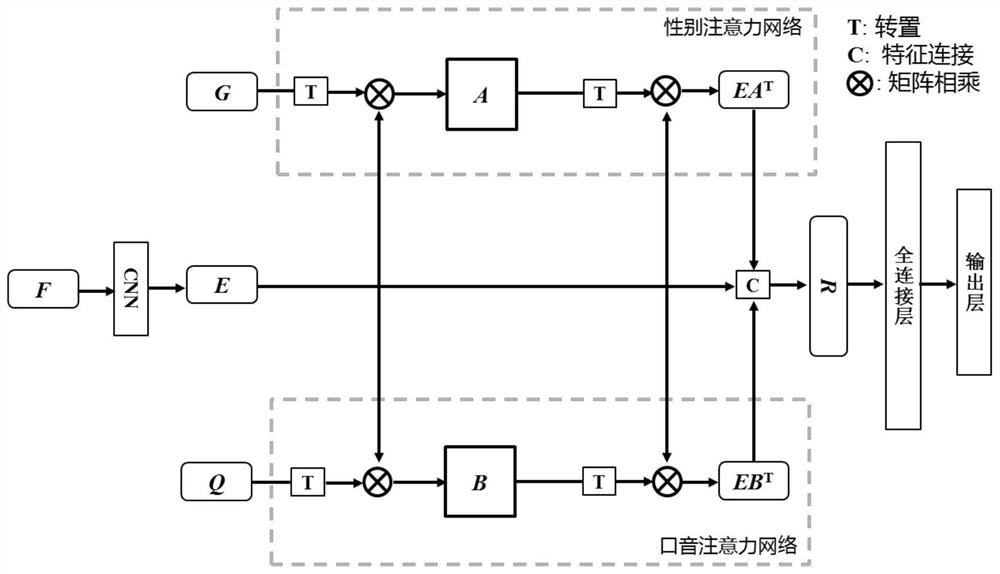
ActiveCN113077797AEasy to distinguishEasy to identifySpeech analysisNeural architecturesConfusionSpeech sound
The invention discloses a speaker recognition method and system based on a multi-source attention network. The method comprises the steps of extracting gender features of a speech segment to be recognized; extracting accent features of the speech segment to be recognized; based on a CNN network of the trained multi-source attention network, extracting tone features of the speech segment to be recognized; on the basis of a gender attention network of the trained multi-source attention network, constructing gender auxiliary features by using the gender features and tone features; based on an accent attention network of the trained multi-source attention network, constructing accent auxiliary features by utilizing the accent features and tone features to ; and combining the timbre feature, the gender auxiliary feature and the accent auxiliary feature to identify the speaker. The speaker recognition method is designed by simulating the thinking mode of human for speaker recognition, so that the recognition effect is better, and particularly for speakers which are extremely easy to cause confusion, the speaker recognition method can better distinguish the speakers.
Owner:SHANDONG NORMAL UNIV
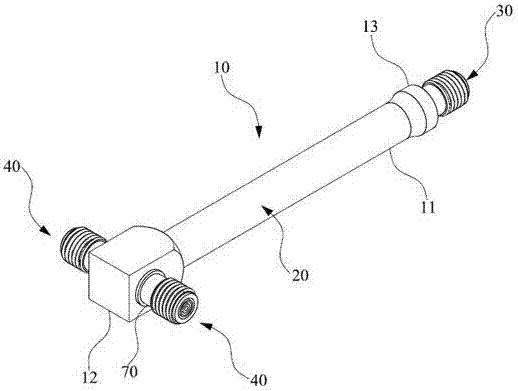
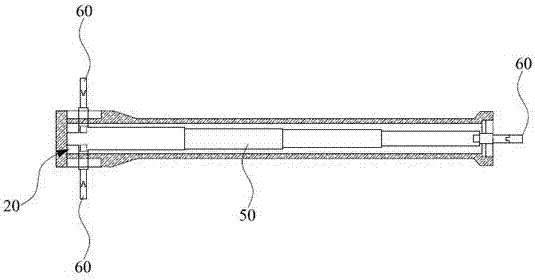
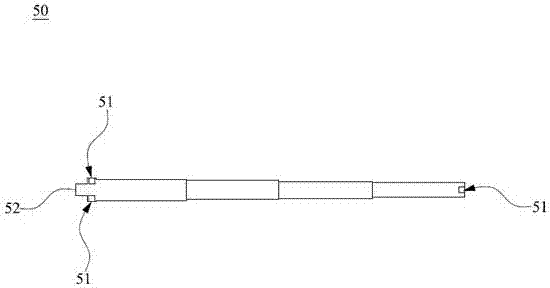
Power divider
Owner:江苏凡为通信科技有限公司
Device and method for detecting inside of small-diameter high-pressure water filling pipeline
InactiveCN111550682AGuaranteed smooth passageReduce tensionMaterial analysis by optical meansPipeline systemsFeature extractionControl signal
The invention relates to a device and method for detecting the inside of a small-diameter high-pressure water filling pipeline. The device comprises an aircraft, a cable and a controller; a bow part of the aircraft is of a hemispherical expansion structure, a middle part of the aircraft is of a pressure-resistant cabin, and a tail part of the aircraft is of an ellipsoidal structure; a vertical propeller, horizontal propellers, cameras, lighting lamps, a main control panel and a cable connector are arranged in the aircraft; a signal output end of each camera is correspondingly connected with asignal input end of the main control panel; a signal output end of the main control panel is respectively connected with control signal input ends of the vertical propeller, the horizontal propellers,the cameras and the lighting lamps; the signal input end and the signal output end of the main control panel are connected with the cable connector; and the two ends of the cable are respectively connected with the cable connector and the controller. The method comprises the steps of initializing, acquiring real-time images, carrying out fault diagnosis and image capture, processing the images, carrying out feature extraction, deciding fault categories, storing and displaying results. The device and method for detecting the inside of the small-diameter high-pressure water filling pipeline have the advantages of compact structure, flexible motion, easy control and high identification.
Owner:湖北迈得科技有限公司
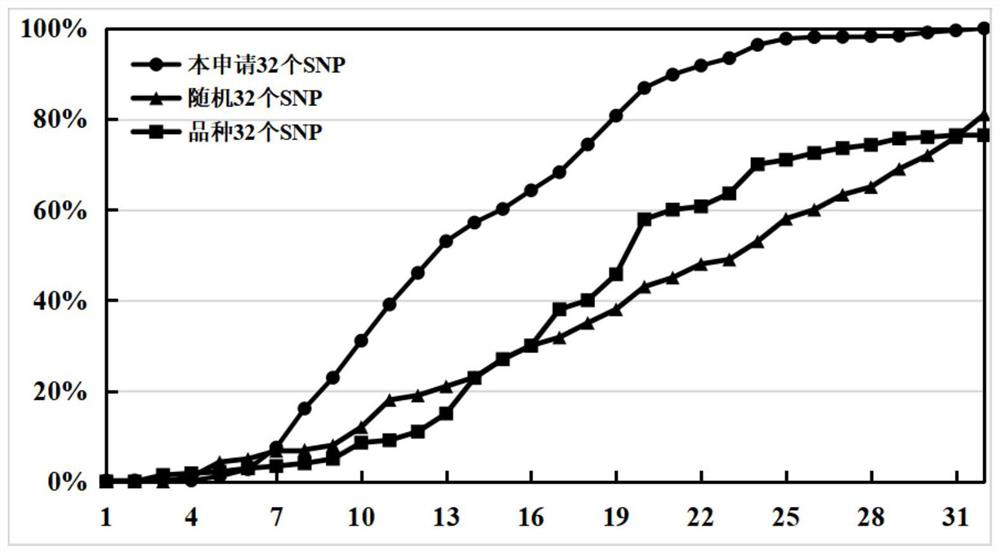
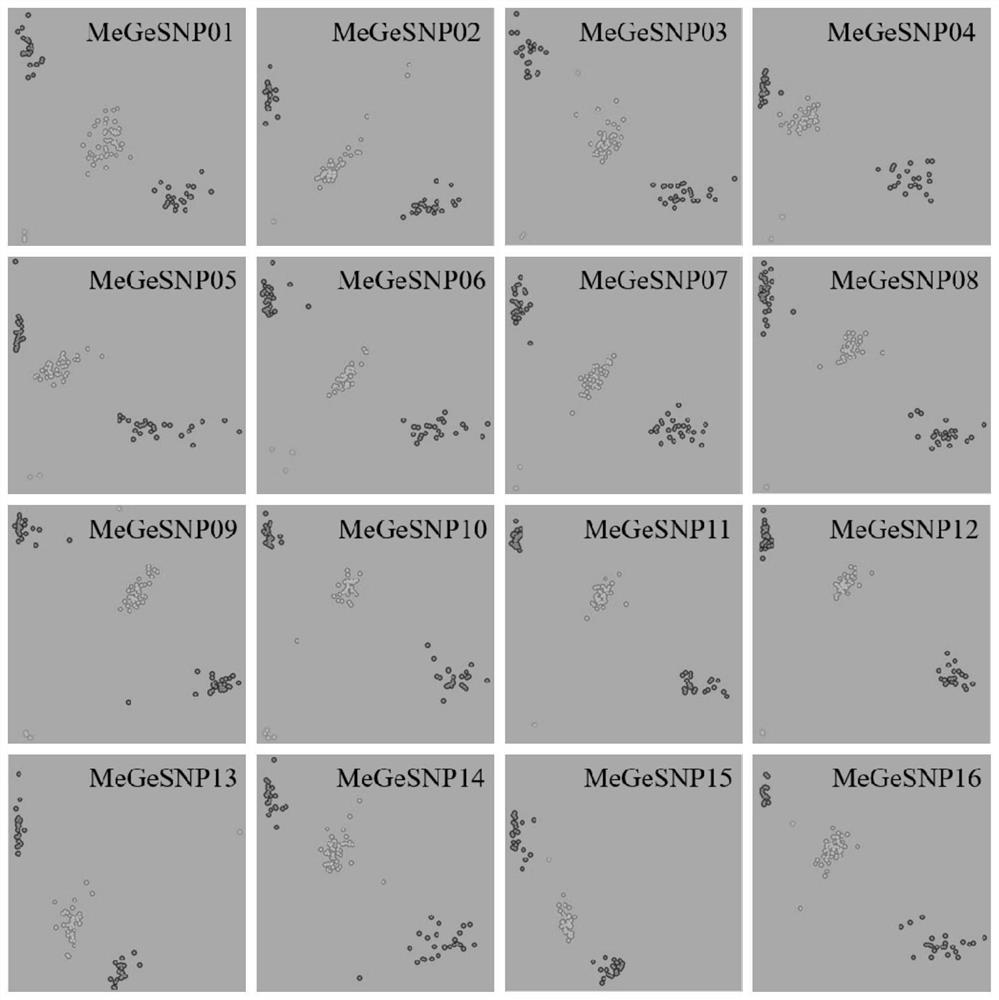
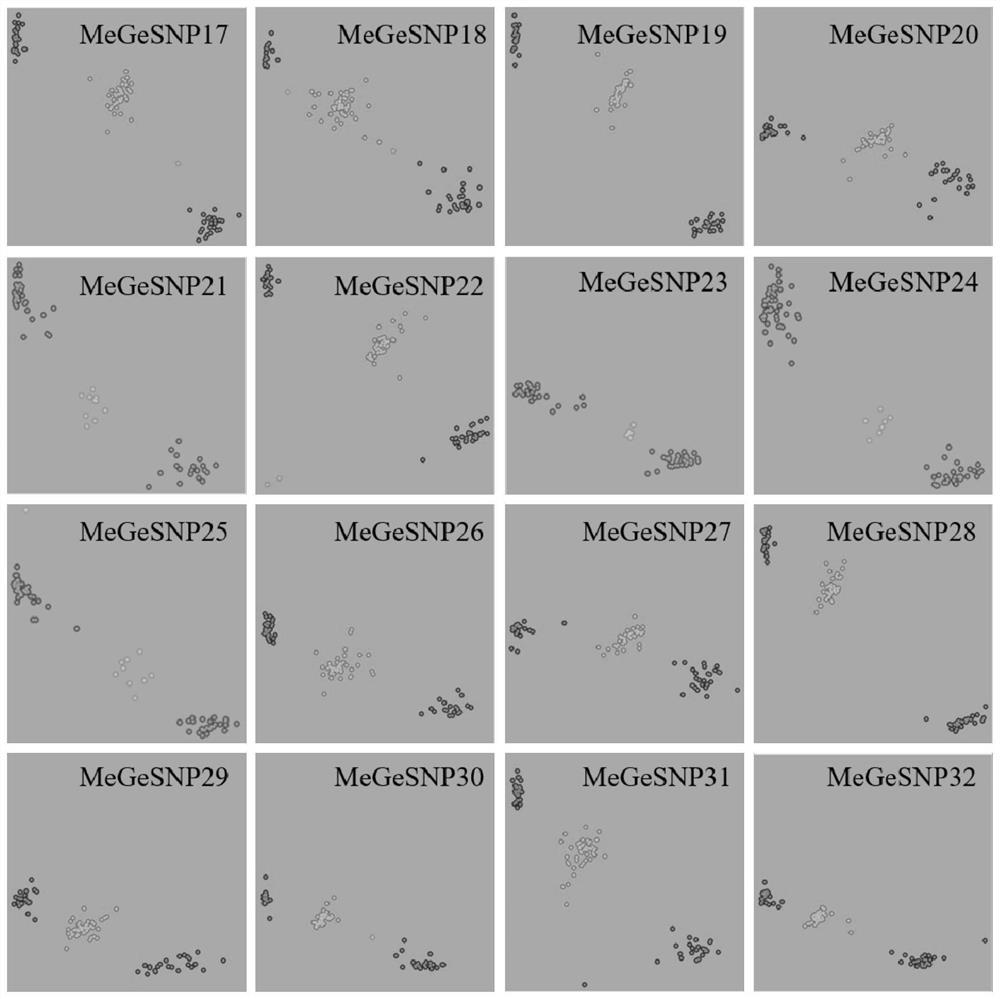
SNP locus and primer combination for identifying germplasm authenticity of cucumis melo, and application
ActiveCN112029890AProtection of rights and interestsImprove throughputMicrobiological testing/measurementAngiosperms/flowering plantsHigh fluxGermplasm
The invention belongs to the field of molecular markers and detection thereof, and particularly relates to a core SNP locus and primer combination for identifying the germplasm resource authenticity of cucumis melo, an SNP locus-based DNA fingerprint database and database construction method, and an SNP locus-based cucumis melo germplasm resource authenticity identification method and application,wherein SNP loci are selected from any one to 32 of the first SNP locus to the thirty-two SNP locus. A DNA fingerprint database for identifying the germplasm resource authenticity of the cucumis melobased on high-throughput sequencing is established in the invention. The method provided by the invention not only can be used for identifying unknown cucumis melo germplasm resources, but also can be used for identifying the authenticity of known cucumis melo germplasm resources. The method provided by the invention has the advantages of high flux, accuracy, low cost, simplicity in operation, manpower and material resource saving and the like, and has a very wide application prospect.
Owner:BEIJING ACADEMY OF AGRICULTURE & FORESTRY SCIENCES
Method for detecting nitrofuran antibiotics or quinolone antibiotics in drinking water
ActiveCN109596593AHigh sensitivityGood choiceFluorescence/phosphorescenceChemistryExcitation wavelength
The invention discloses a method for detecting nitrofuran antibiotics or quinolone antibiotics in drinking water, and relates to methods for detecting the antibiotics in the drinking water. An existing lanthanide series metal-organic framework has instability of dependence on excitation wavelength; and an existing antibiotic measuring method has the problems that a professional instrument is needed, the pretreatment is tedious, and the operation cost is high. The detection method comprises the following steps of 1, preparing Tb-dcpcpt crystals; 2, preparing an RhB@Tb-dcpcpt composite material;3, preparing an RhB@Tb-dcpcpt dispersion liquid; and 4, carrying out fluorescence detection. The method is used for detecting the nitrofuran antibiotics or the quinolone antibiotics in the drinking water.
Owner:HEILONGJIANG UNIV
Active sonar identity reorganization method based on watermark
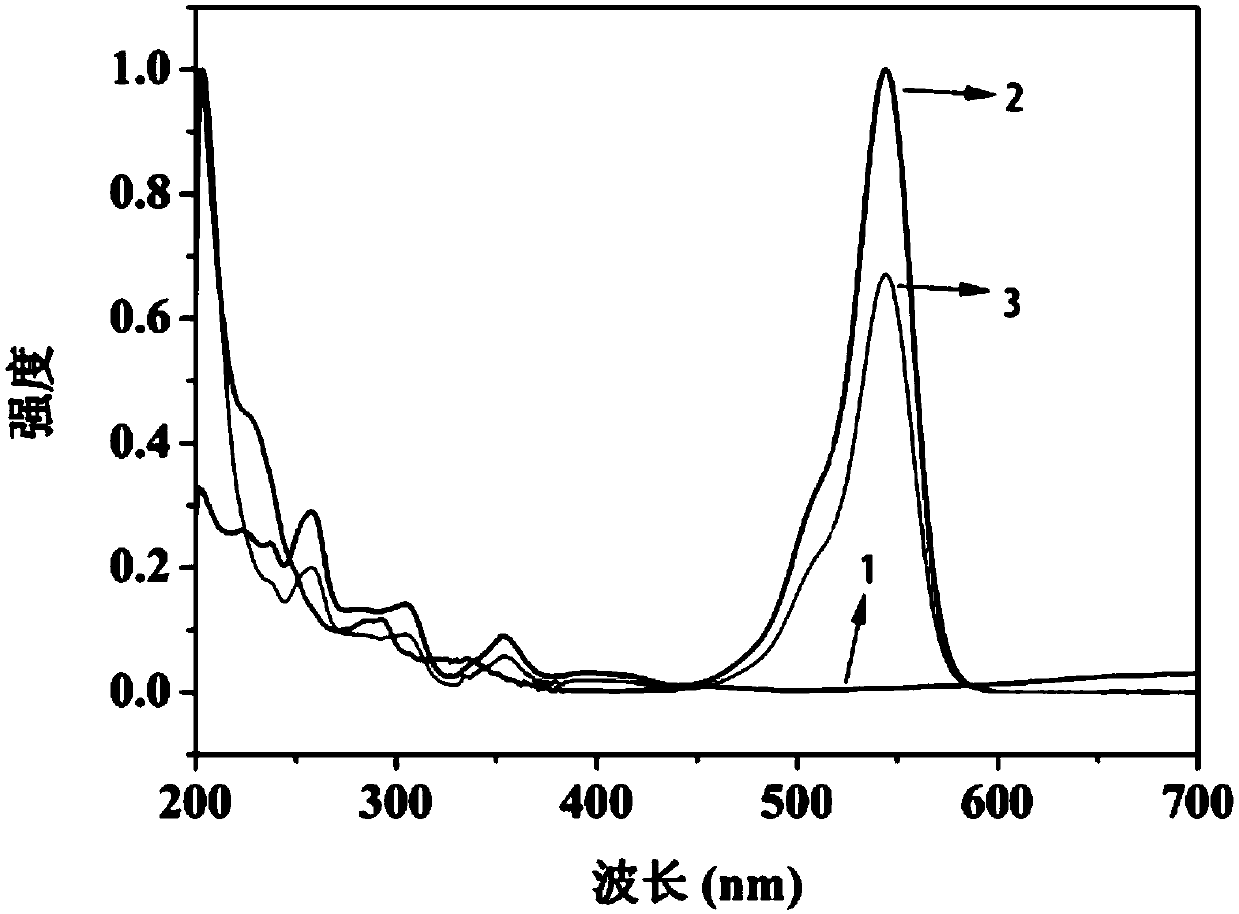
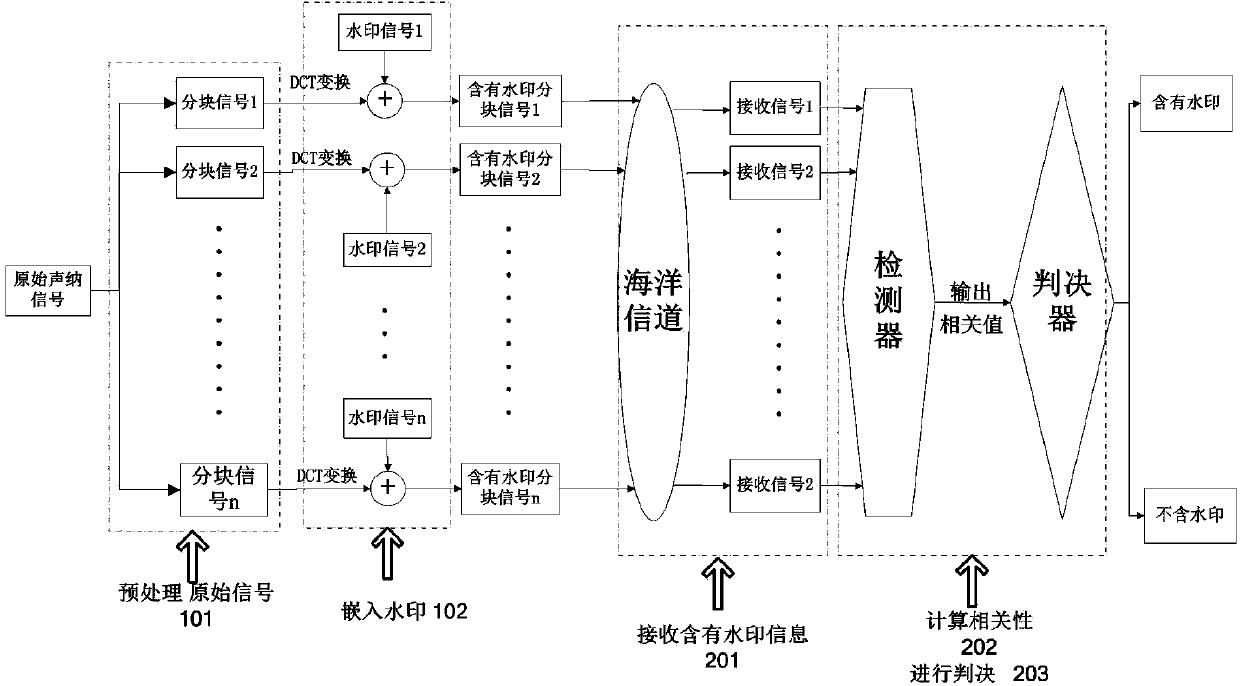
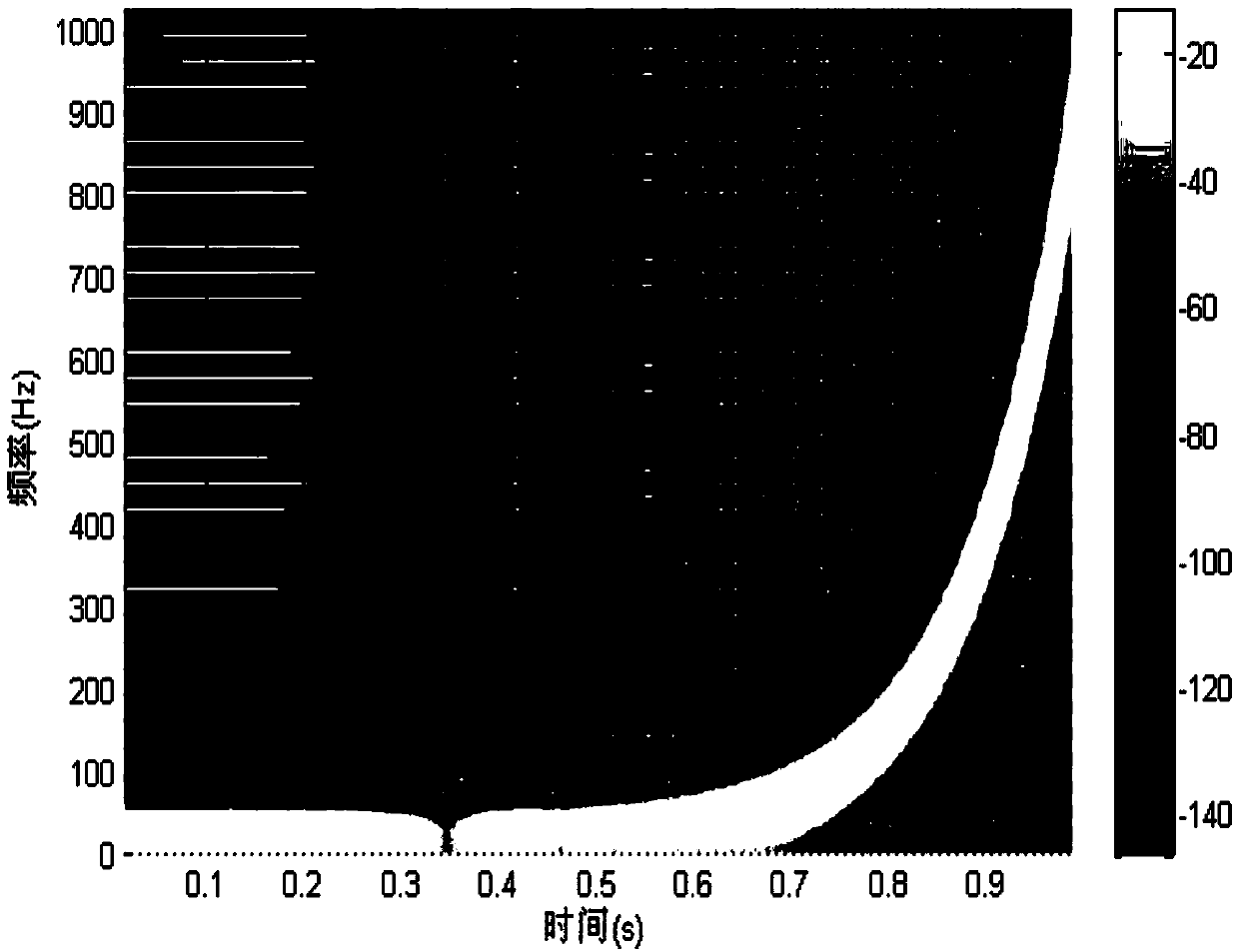
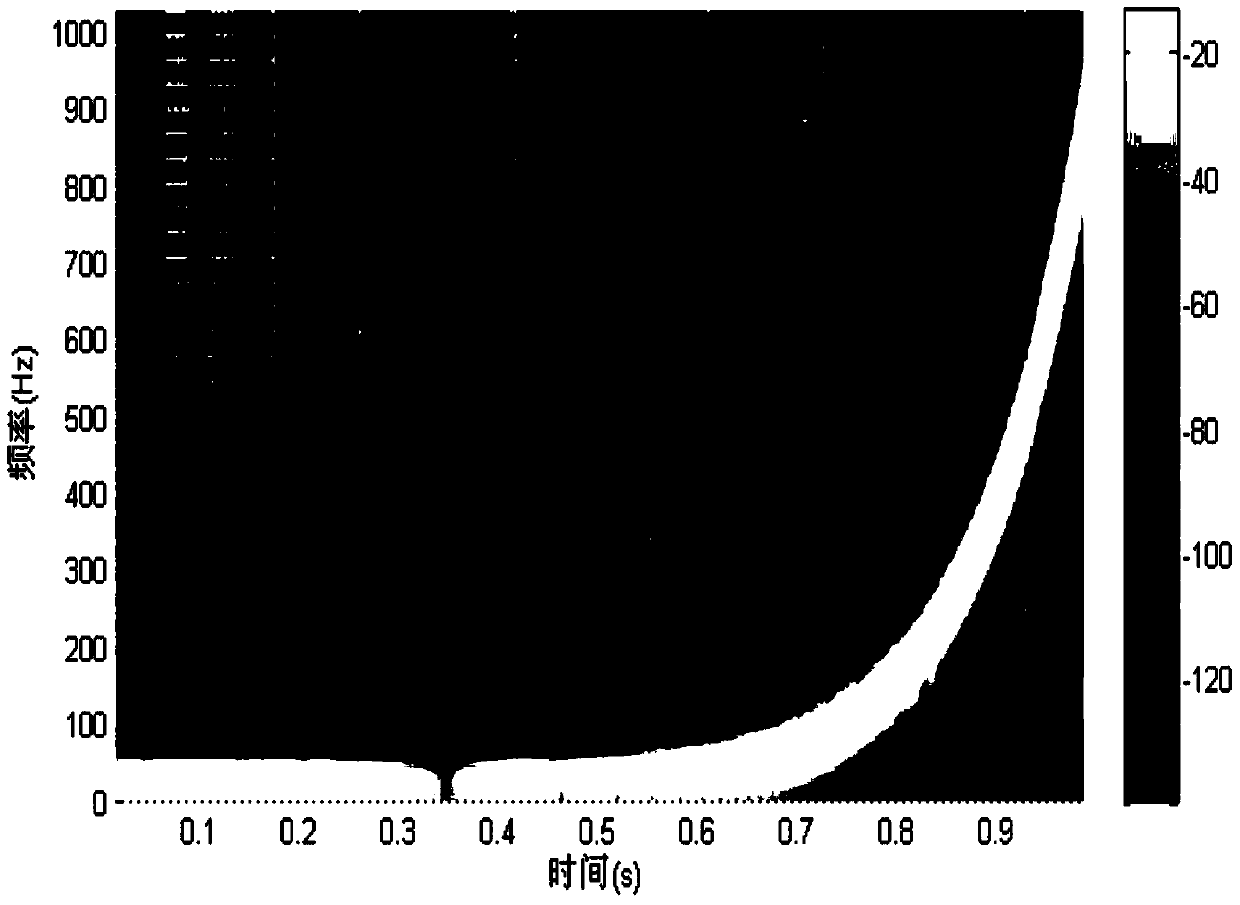
InactiveCN103794217AThe form is variable and optionalStrong identification abilitySpeech analysisSonarControllability
The invention discloses an active sonar identity reorganization method based on a watermark. The active sonar identity reorganization method based on the watermark is different from existing active sonar identity reorganization methods which are achieved through the inherent features of active sonar detection signals. According to the active sonar identity reorganization method based on the watermark, the digital watermark is embedded into a detection signal sent by active sonar by a sender, and a receiver recognizes the identity of the signal by detecting whether the received signal contains watermark information; specifically, part of DCT coefficients in an original signal are modified by generating a watermark sequence at the sending end, whether the watermark is contained is determined at the receiving end by calculating the relevance between a watermark template and the received signal, and thus the identity of the sonar signal is recognized. Compared with existing methods, the active sonar identity reorganization method based on the watermark has the advantages of being more flexible, higher in controllability and better in reorganization effect.
Owner:JIANGSU UNIV OF SCI & TECH
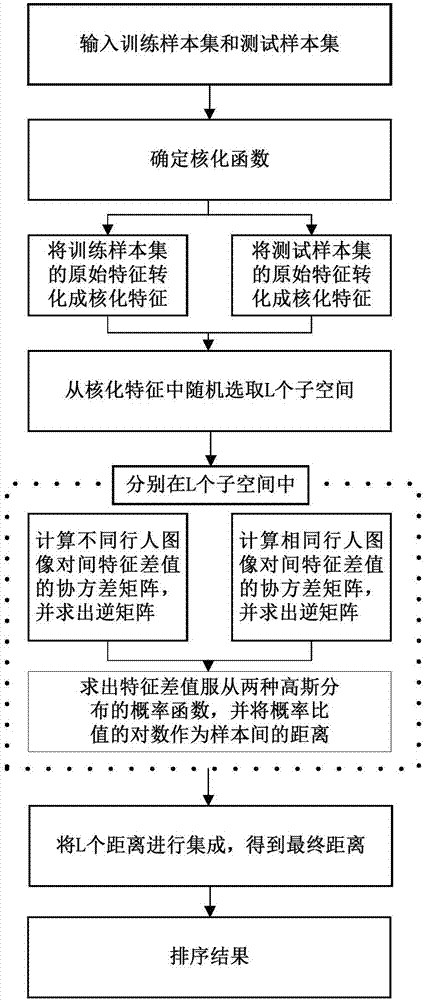
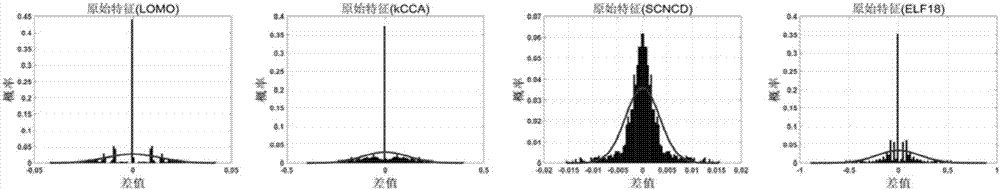
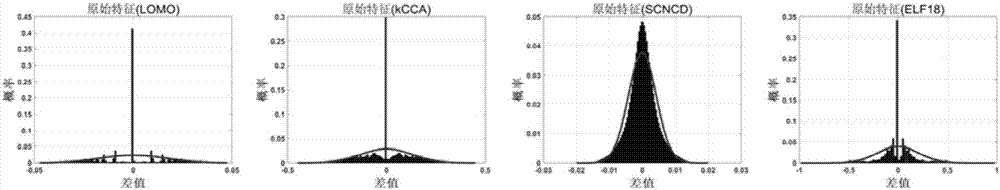
Pedestrian re-identification method based on kernelization features and random subspace integration
ActiveCN107122795AImprove performanceOptimizing the process of distance calculationCharacter and pattern recognitionTest sampleCharacteristic space
The invention relates to a pedestrian re-identification method based on kernelization features and random subspace integration. The method comprises the following steps that: S1, the training sample set and test sample set of pedestrian images are obtained, and the kernelization function between of the two sample sets is determined; S2, the original features of the two sample sets are transformed into kernelization features; S3, a plurality of subspaces are randomly selected from the kernelization feature space of the training sample set, the covariance matrixes and the inverse matrixes thereof of the kernelization feature difference values of different pedestrian image pairs and identical pedestrian image pairs are calculated, the distribution function of the kernelization feature difference values of the image pairs is obtained; S4, the probability of a sample pair being the same pedestrian and the probability of a sample pair being different pedestrians under each subspace are calculated, the ratio of the two probabilities is adopted as the distance between the samples; and S5, the distances are integrated, so that final distances between each sample pair are obtained. Compared with the prior art, the method of the invention has the advantages of excellent pedestrian re-identification ability, suitability for a variety of different features and high robustness.
Owner:TONGJI UNIV
Quantum encryption information transmission system
PendingCN114091055APrevent imitationAvoid destructionQuantum computersDigital data protectionInformation transmissionDatabase server
The invention relates to a quantum encryption information transmission system, and the system comprises a first authentication module which is used for a communication server to send request information and authenticate the identity of a CA server; a second authentication module which is used for sending request information and identity authentication of the base station by the communication server; a remote interaction module which is used for generating a digital certificate application file of the CA server before the CA server is in a working state, importing a formal digital certificate stored in the database server into the CA server and executing remote transmission of quantum encryption information; and an updating module which is used for updating the symmetric key of the CA server before the CA server stops information transmission, and importing the test digital certificate stored in the communication server into the CA server. According to the scheme, the management process of the terminal digital certificate and the symmetric key is improved, the security protection loophole of the CA server in the quantum encryption information transmission process is made up, and therefore the security protection level of CA server field application and transmission is improved.
Owner:深圳天通信息科技有限公司
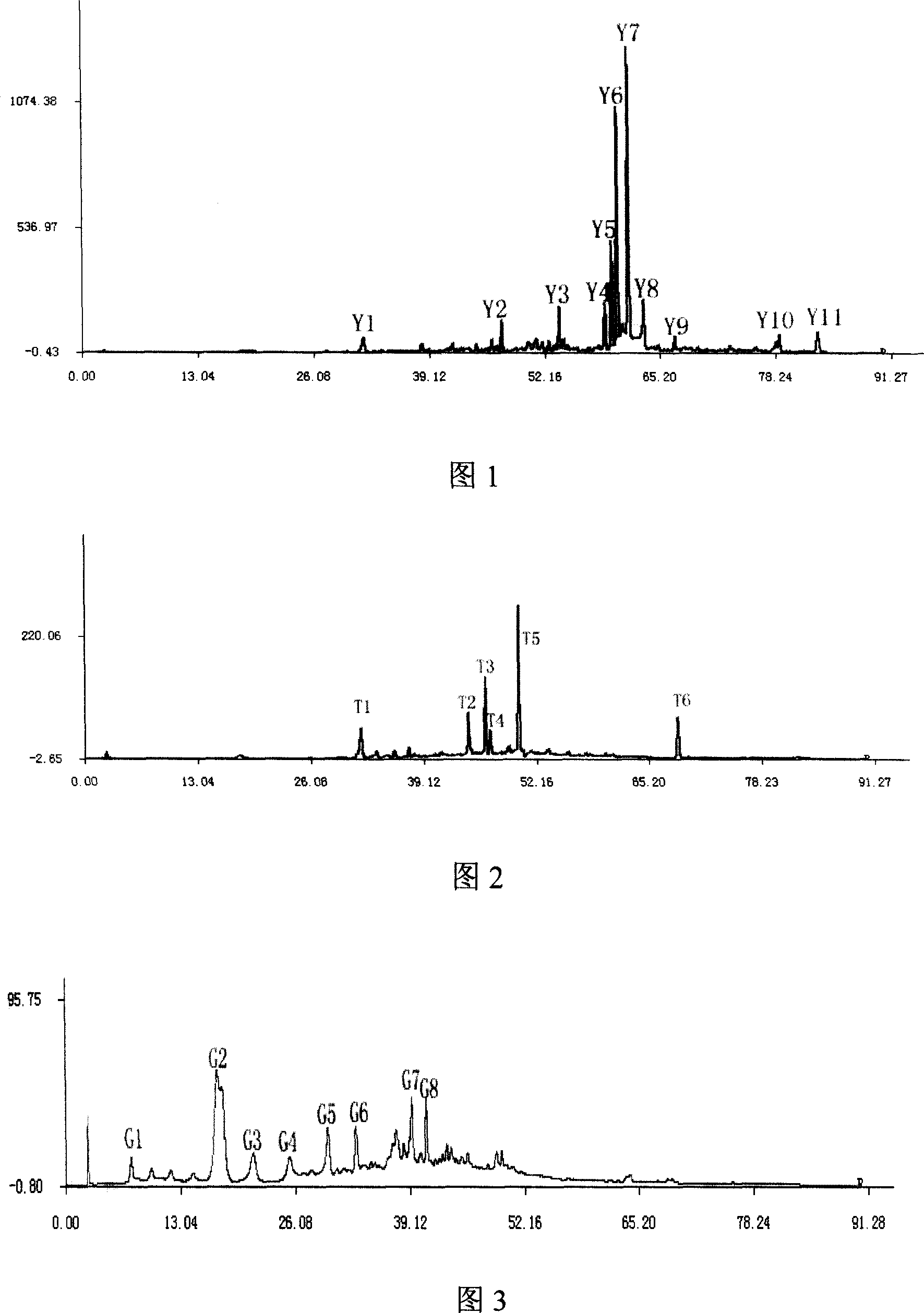
Method for detecting and identifying volatile substances in Maotai-flavor base liquor
ActiveCN113917061AAddress subjectivityIncrease credibilityComponent separationManufacturing computing systemsBiotechnologySensory analysis
The invention discloses a method for detecting and identifying volatile substances in Maotai-flavor base liquor. The method comprises the following steps: determining volatile flavor substances; detecting volatile substances of the Maotai-flavor base liquor; constructing a Maotai-flavor base liquor identification model; verifying the Maotai-flavor base liquor identification model; and determining different substances of the Maotai-flavor base liquor. The invention provides a method for rapidly identifying Maotai-flavor type breakstone base liquor and broken sand base liquor by combining a gas chromatographic method with chemometrics analysis, and key difference substances causing difference are screened from the Maotai-flavor type breakstone base liquor and the broken sand base liquor. According to the method, the identification model of the Maotai-flavor Baijiu and the broken Baijiu is constructed for the first time, the identification ability is good, the subjectivity problem of sensory evaluation identification is solved, the identification model and sensory analysis can be combined to be used for identification of Maotai-flavor Baijiu of different processes, the identification method is more efficient and accurate, and the credibility of the identification result is improved.
Owner:GUIZHOU UNIV
Method for whole monitoring of radix bupleuri oral liquid quality
InactiveCN103529158AStrong identification abilityComprehensive monitoringComponent separationMedicineRadix bupleuri
The invention relates to a method for whole monitoring of radix bupleuri oral liquid quality. The method comprises the steps of firstly, constructing a fingerprint spectrum of a radix bupleuri medicinal material, intermediate extract and a finished radix bupleuri oral liquid product; secondly, detecting the fingerprint spectrum of the radix bupleuri medicinal material, the intermediate extract and the finished radix bupleuri oral liquid product; and thirdly, comparing the fingerprint spectrum of the radix bupleuri medicinal material, the intermediate extract and the finished radix bupleuri oral liquid product to a standard fingerprint spectrum; producing by taking the radix bupleuri medicinal material with integral similarity consistent with requirement as a raw material, turning to a next process when integral similarity of the fingerprint spectrum of the intermediate extract and the standard fingerprint spectrum is consistent with requirement, and delivering the finished radix bupleuri oral liquid product where integral similarity of the fingerprint spectrum therein and the standard fingerprint spectrum is consistent with requirement out of factory. The method can monitor quality from the medicinal material to the intermediate extract and to the finished product, so that the production process is easier to control, and more scientific and reasonable to regulate; and quality of the finished product is stable and consistent.
Owner:LUOYANG SHUNSHI PHARMA
A method and system for image person re-identification based on multi-attention joint learning
ActiveCN111539370BImprove learning effectStrong identification abilityBiometric pattern recognitionNeural architecturesImaging processingFeature extraction
The invention discloses an image pedestrian re-identification method and system based on multi-attention joint learning, belonging to the technical field of image processing. The present invention introduces Soft attention and high-order attention into the ResNet50 feature extraction network, uses the complementary effects of two different types of attention on feature extraction, improves the feature extraction network's ability to learn pedestrian features, and makes the feature extraction network Focus on more discriminative features in pedestrian images. In order to obtain more accurate attention features, a multi-level attention loss function is proposed. This loss function is used to guide the training and learning of the feature extraction network, and further improve the learning ability of the feature extraction network for pedestrian features. While learning the global features of pedestrians, the intermediate features in the feature extraction network are fused and the learning of local features of pedestrians is strengthened, which improves the ability of the network to learn the subtle differences between pedestrian features, and improves the performance of the network in image pedestrian re-identification.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for overall monitoring for kidney-tonifying body-strengthening tablet quality
InactiveCN101011480BStrong identification abilityComprehensive monitoringComponent separationDigestive systemProcess qualityAdditive ingredient
The present invention relates to a method for detecting the quality of kidney tonifying tablet using fingerprints, which comprises the following steps: first, building the standard fingerprint diagram of barren wort, doddor, woodwardic, middle extractum and final tablet; second, checking the fingerprints of tested barren wort, doddor, woodwardic, middle extract and final tablet; third, comparing the fingerprints of the three ingredients to be tested with each standard fingerprint. The groups with met similarity can be used as material to be used in production, and the qualified middle extract is used in next process, and the final tablet is used as final product. The method for detecting the quality of kidney tonifying tablet using fingerprints of the present invention can realize full-process quality monitoring including crude medicine and midbody extractum so that the whole productive technology is more easy to be controlled and the adjustment is more scientific and reasonable, thus eventually obtaining stable and consistant product quality.
Owner:MASSON GROUP
Communication message security interaction method and device for distribution automation system
ActiveCN109257327BImprove the level of security protectionAvoid safety hazardsKey distribution for secure communicationCircuit arrangementsStationConfidentiality
The invention provides a communication message security interaction method and a device of a distribution automation system. After completing two-way identity authentication between a distribution master station and a distribution terminal, a main distribution station obtains distribution terminal information from the distribution terminal. The main distribution station judges whether that distribution terminal is the first identity authentication according to the version number of the symmetrical key of the distribution terminal, if not, the message exchange between the distribution terminaland the main distribution station is carried out; otherwise, after the symmetric key of the distribution terminal is updated, message exchange between the distribution terminal and the distribution master station is performed. The scheme makes up for the shortcomings that the distribution master station can not identify the distribution terminal in the distribution automation system security protection system, and the confidentiality and integrity of the communication message can not be guaranteed, and improves the security protection level of the vertical communication between the distribution master station and the distribution terminal in the distribution automation system. At that same time, the problem that the remote control / parameter set message has the hidden trouble of the replayattack and the like are sol.
Owner:CHINA ELECTRIC POWER RES INST +1
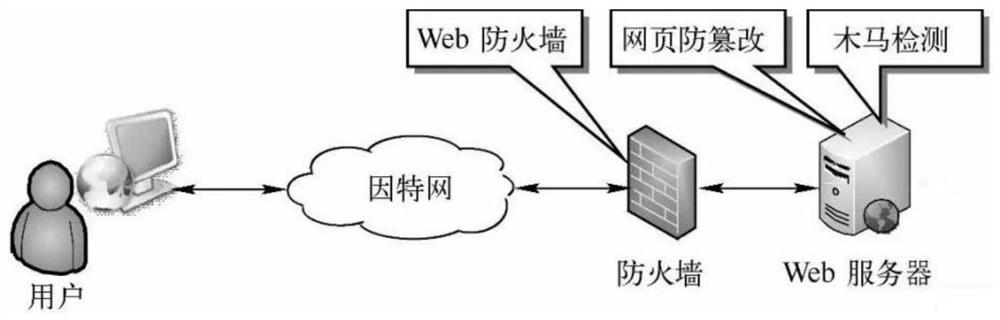
Service request processing method, Web server, equipment and medium
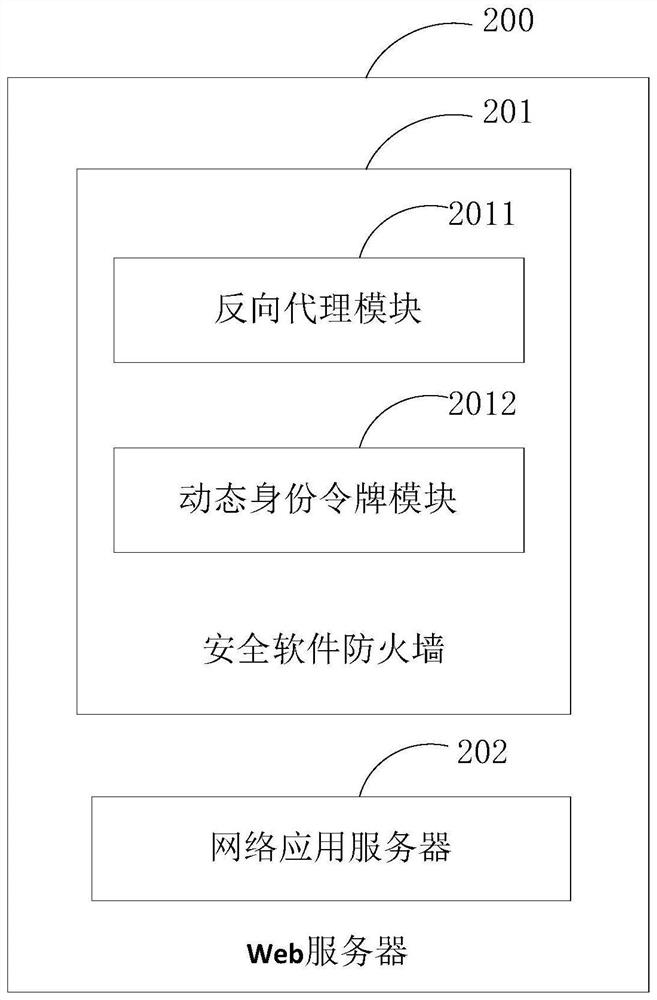
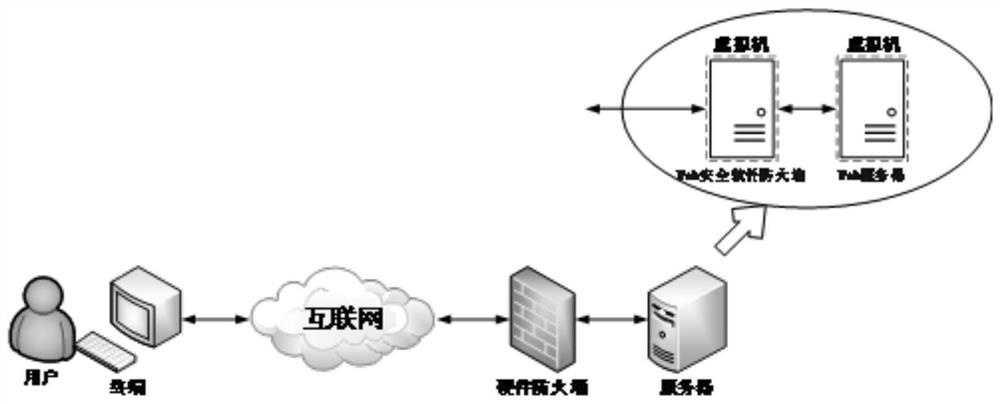
PendingCN114172698AProtect safe operationGuarantee safe and reliable performanceSecuring communicationReverse proxyIdentity recognition
The invention provides a service request processing method, a Web server, a device and a medium, the server comprises a security software firewall and a network application server, the security software firewall comprises a reverse proxy module, and the reverse proxy module is used for exposing a proxy address and a proxy port of the reverse proxy module to the Internet. The security software firewall obtains a service request and sends the service request to a network application server according to a preset routing information table, and the security software firewall further comprises a dynamic identity recognition module which generates a message secret key during first identity authentication, performs identity authentication of a demand side by using the secret key in subsequent message interaction with the service demand side, and sends the service request to the network application server. According to the method, no entity server is added, the security software firewall is implanted into the existing server to form a three-level network system architecture of the application server, the firewall and the service demand side, so that the security operation of the website server is further protected, the attack risk of the website server is reduced, the identity authentication capability of a communication object is improved, and the security and reliability of the application server are jointly guaranteed.
Owner:CHONGQING CHUANYI AUTOMATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com