Service request processing method, Web server, equipment and medium
A business request and server technology, applied in the computer field, can solve problems such as being vulnerable to attacks, and achieve the effects of protecting safe operation, reducing the risk of attacks, and ensuring safe and reliable performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
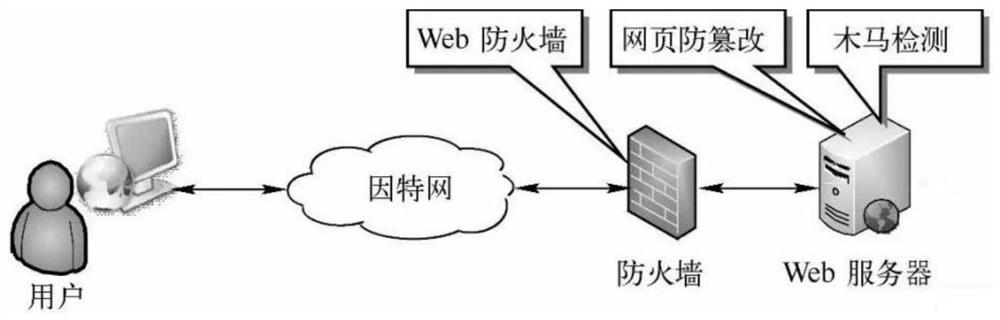
[0052] see figure 1 , in the related technology, the user visits the Web server again through the firewall through the Internet, and the protection of the server is usually through a hardware firewall ( figure 1 firewall in the ) and the web application server ( figure 1 The built-in functions such as webpage anti-tampering and Trojan horse detection are realized. This is because the IP address and Port port of the web application server are directly exposed on the Internet and are vulnerable to attacks; the conventional ID+Password method is used to verify user identity, which is easy to forge. Therefore, there are still certain risks in the above method.
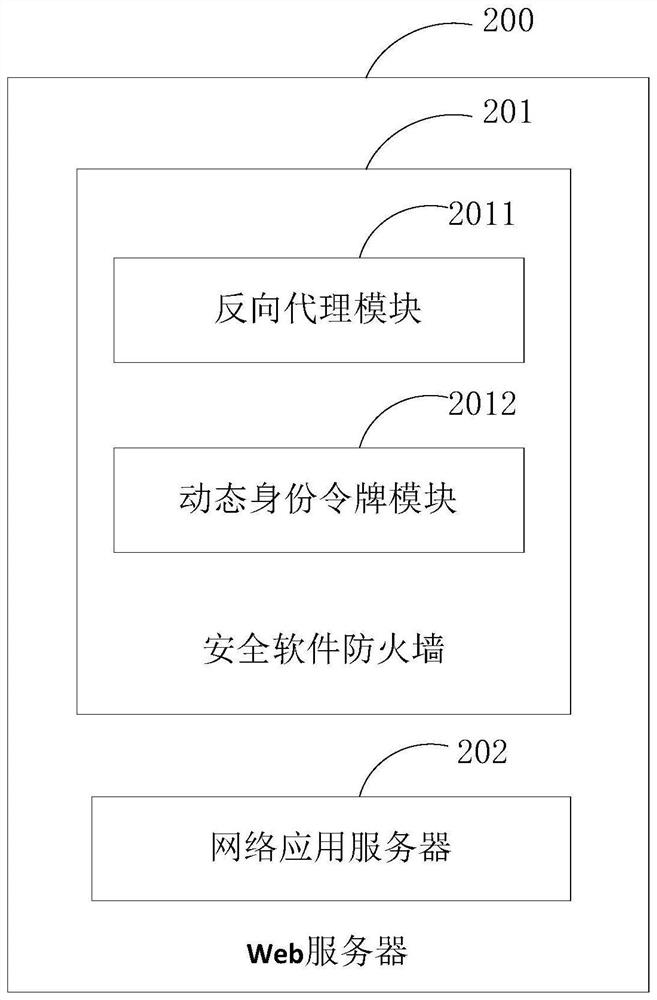
[0053] To solve the above problems, such as figure 2 As shown, the present embodiment provides a Web server 200, the Web server 200 includes a security software firewall 201 and a network application server 202, the security software firewall 201 includes a reverse proxy module 2011, and the reverse proxy module 2011 i...
Embodiment 2
[0106] see Figure 6 , this embodiment provides a service request processing method, the method comprising:
[0107] Step S101: setting a security software firewall in the server.
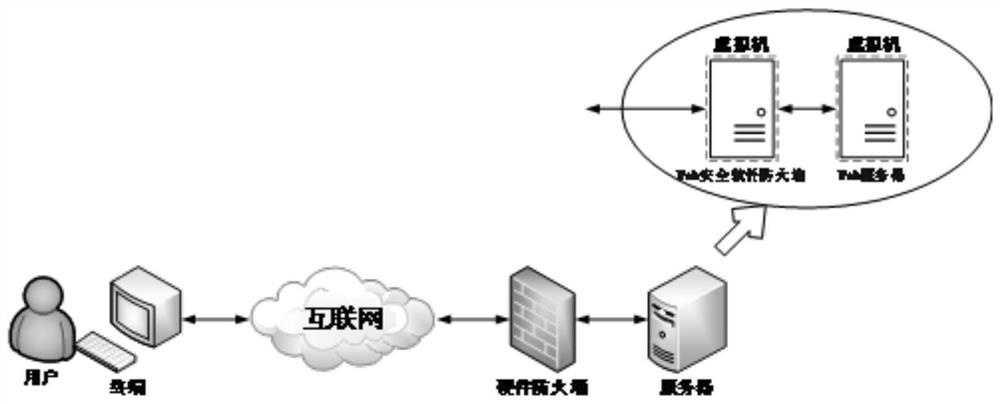
[0108] Among them, it can be realized by dividing the existing web server into two logically independent virtual machines, one of which is used as a security software firewall to provide software-level security protection for the back-end network application server, which is similar to the hardware firewall. connection; another virtual machine acts as a web application server, provides original web application services, and connects with the previous virtual machine.
[0109] Wherein, the security software firewall exposes the proxy address and proxy port to the Internet, and the proxy address and proxy port are different from the network address and network port of the back-end web application server. In this way, the user (service request sender) can access the proxy address and proxy port The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com