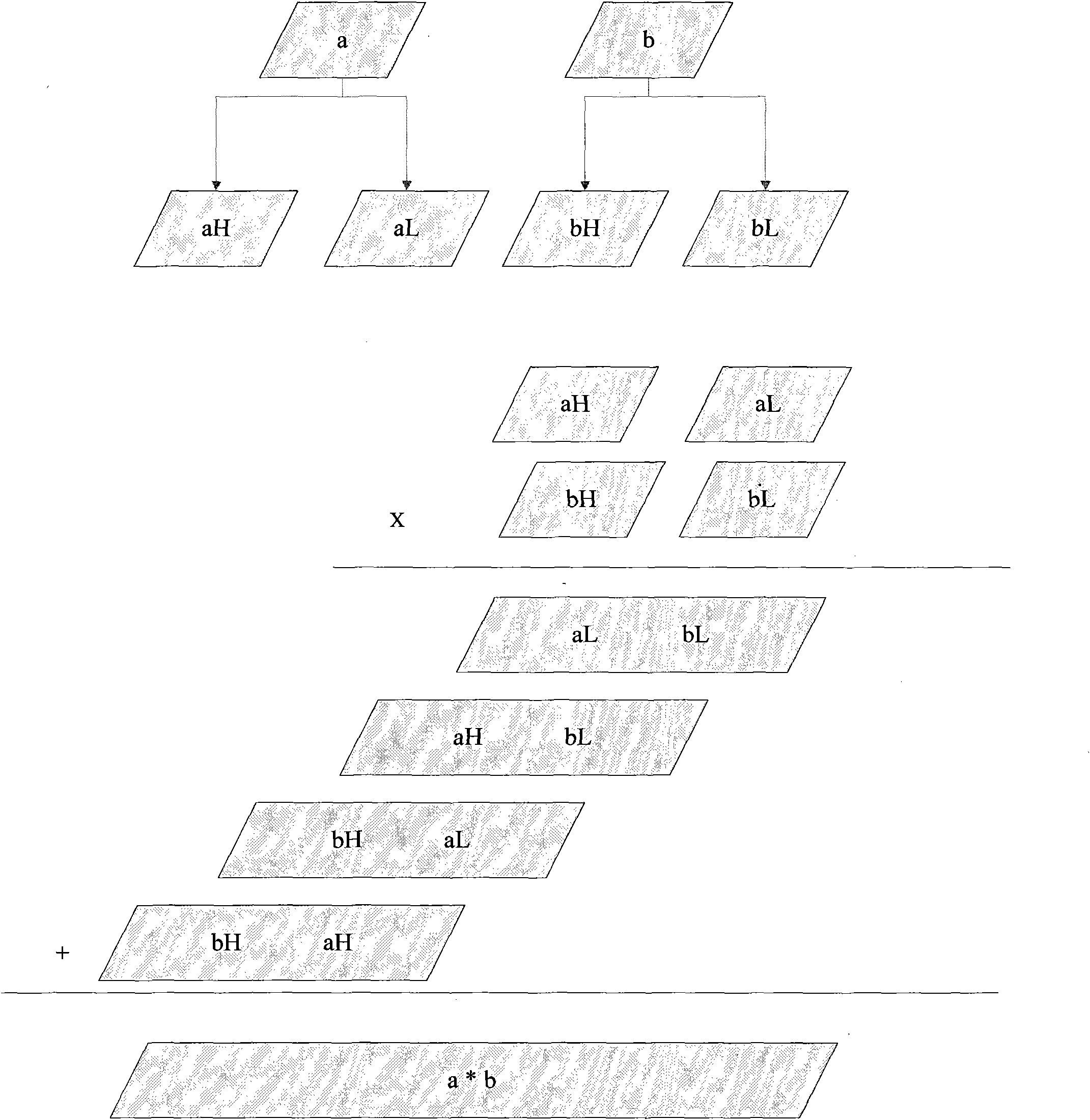RSA (Ron Rivest, Adi Shamir and Leonard Adleman) algorithm digital signature method
A technology of RSA algorithm and digital signature, applied in key distribution, can solve the problem of low calculation efficiency of software modulo function, and achieve the effect of quick time to market and lower chip cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The invention can make the L / 2-bit long modular multiplier calculate the L-bit long RSA private key operation, so as to reduce the chip cost, or use limited resources to meet market changes, and help the rapid development and listing of products. This algorithm can be used when it is necessary to use a small bit length modular multiplier to realize a large bit length RSA private key operation. Specific steps are as follows:
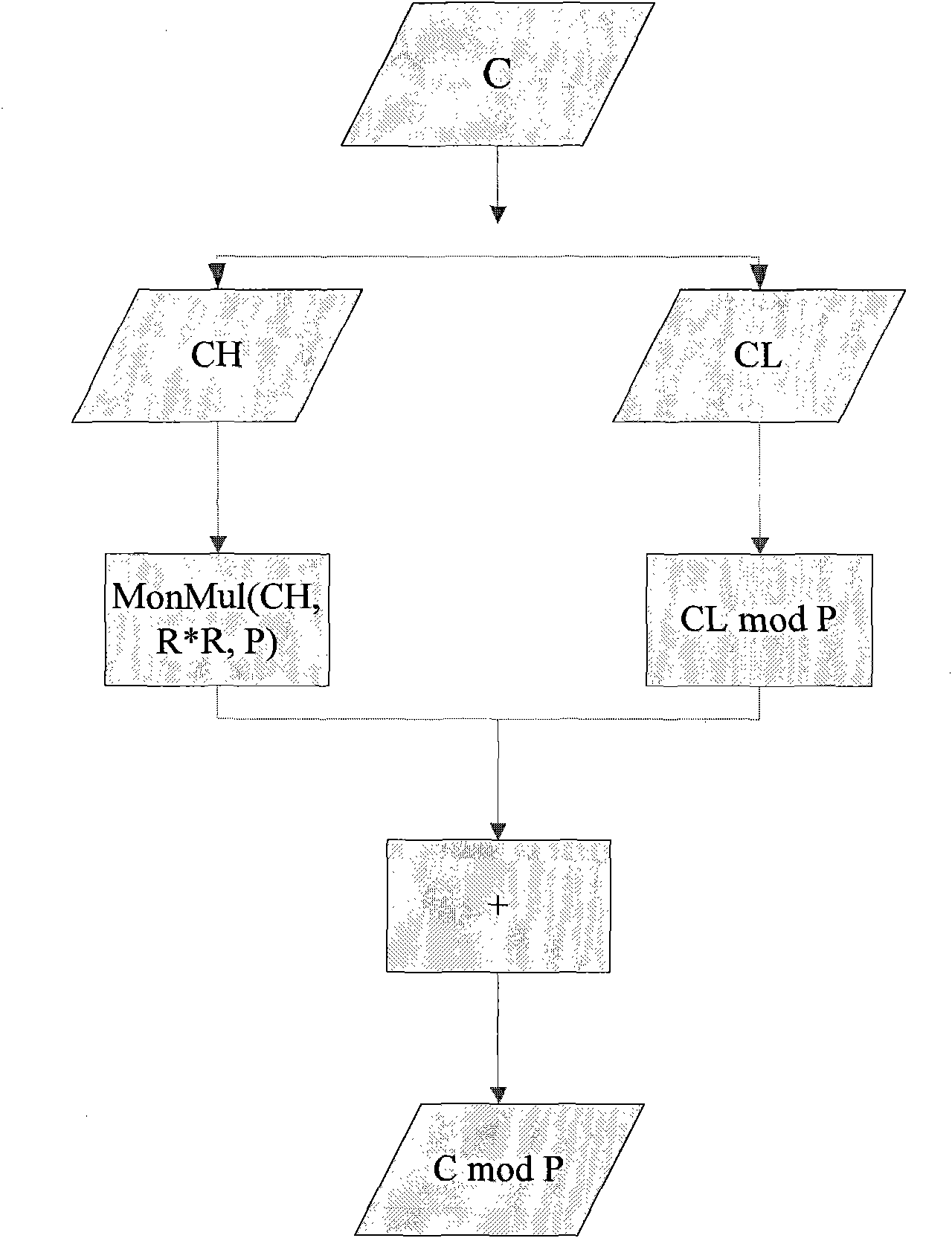
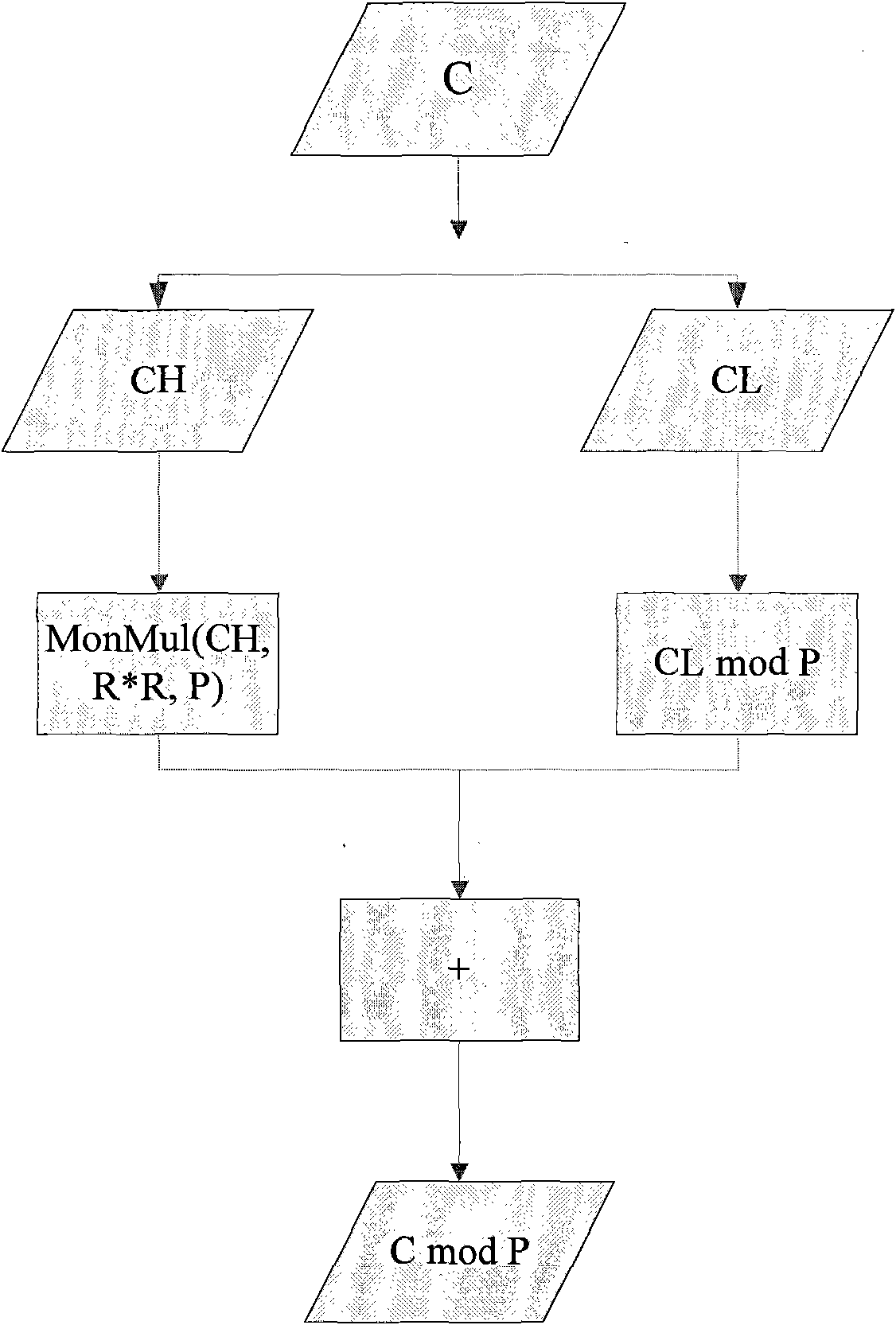
[0028] The following method is used when calculating C mod P:
[0029] 1. Divide C into two parts of equal length, record CH as the high L / 2 part, and CL as the low L / 2 part, so that the L-length C is split into two L / 2-length data, and C=CH<<L / 2+CL, where "<<" is a leftward translation operation.
[0030] 2. Further analysis of CH<
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com