Patents
Literature
130 results about "Activity monitor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
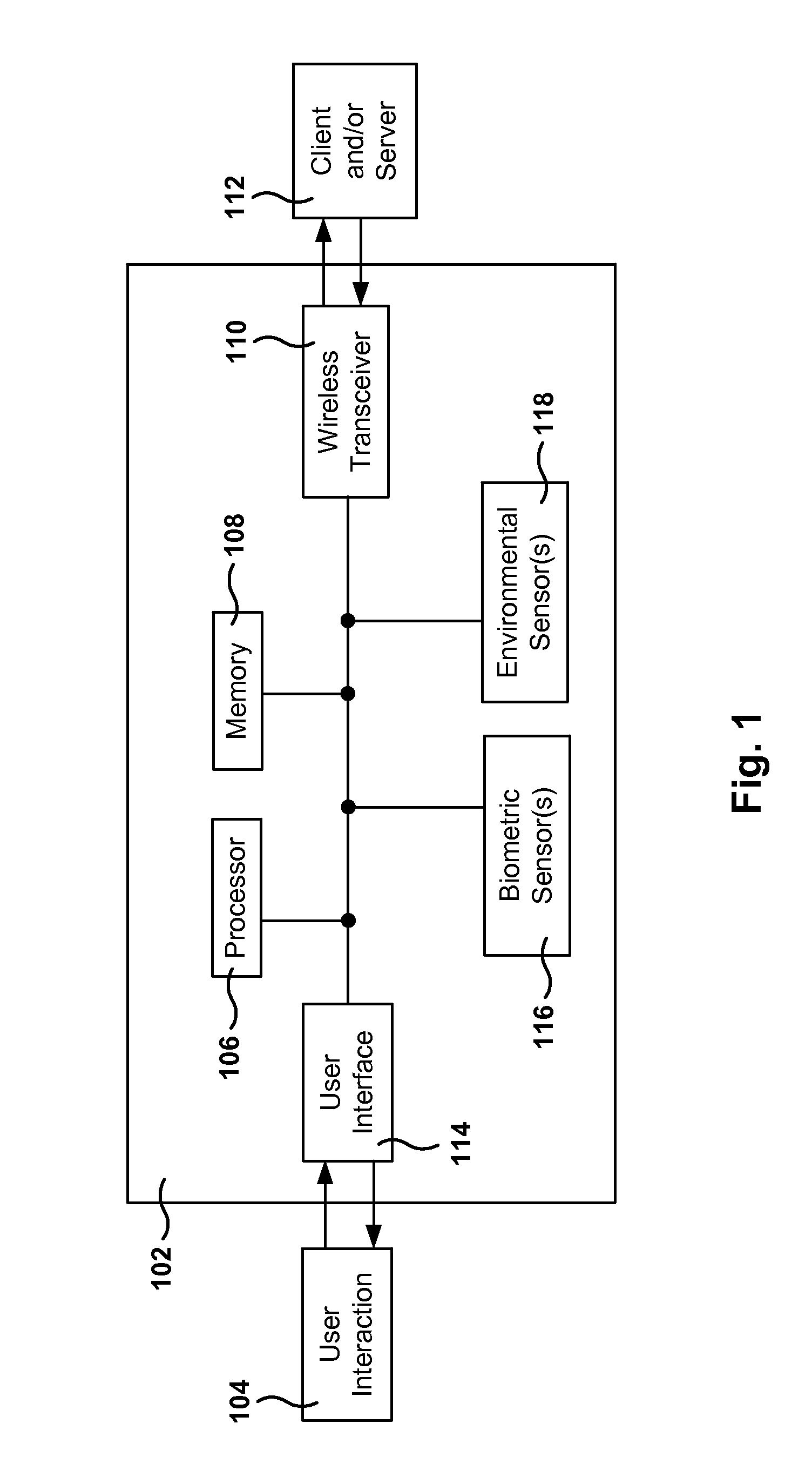
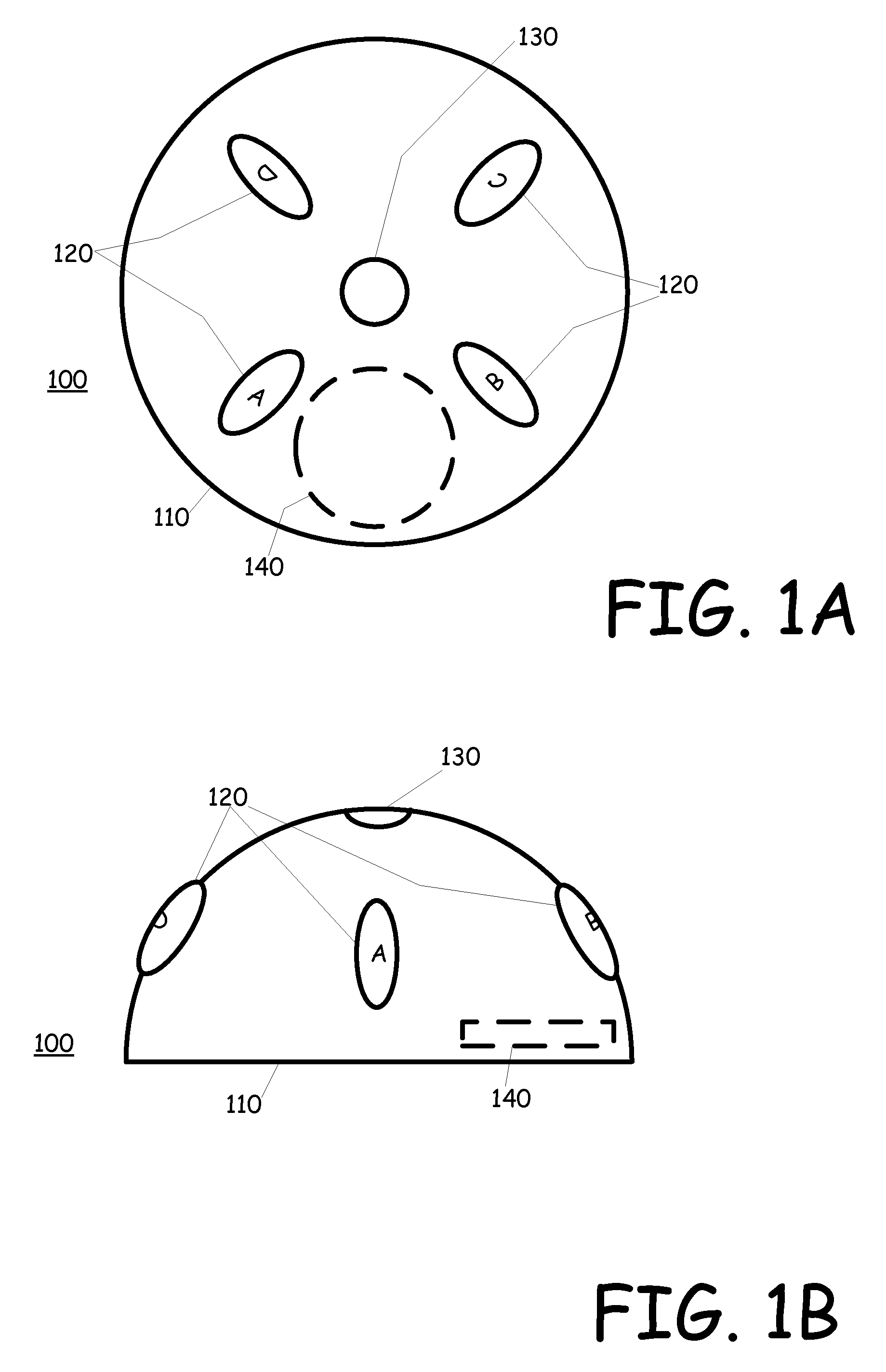
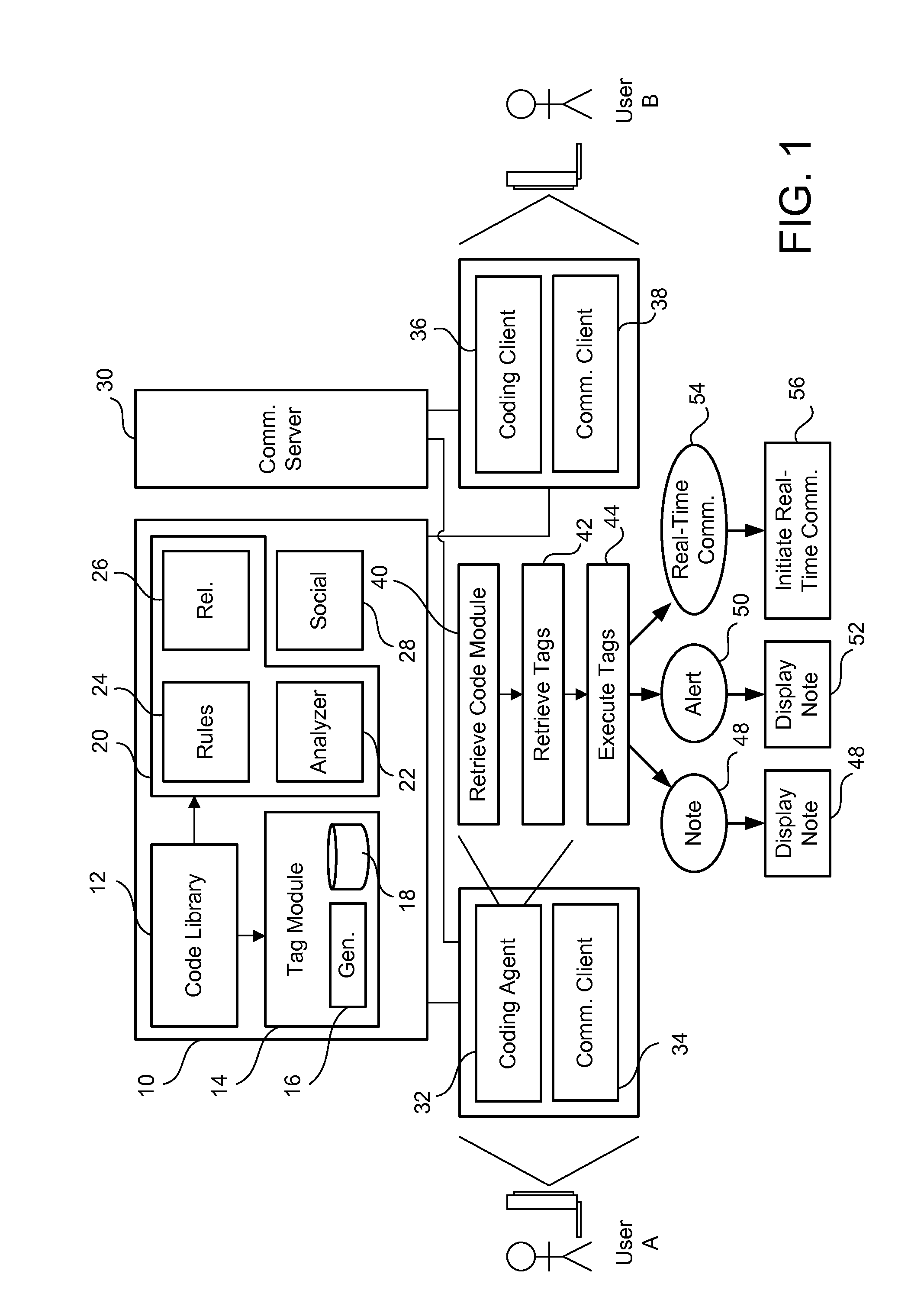
Real-time activity monitoring and reporting
InactiveUS20070039049A1Maintain transparencyNo delayMemory loss protectionError detection/correctionActivity monitorComputerized system
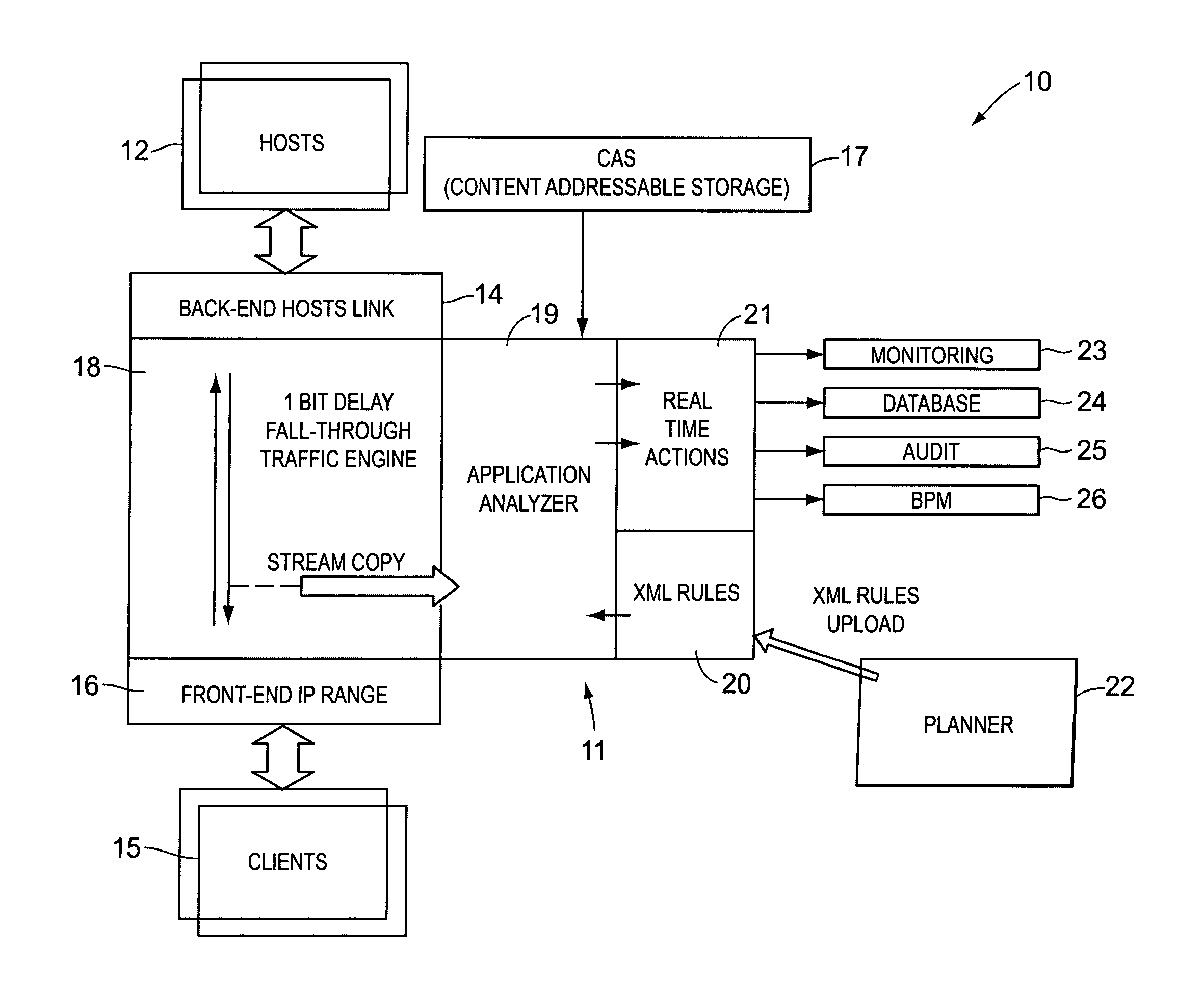
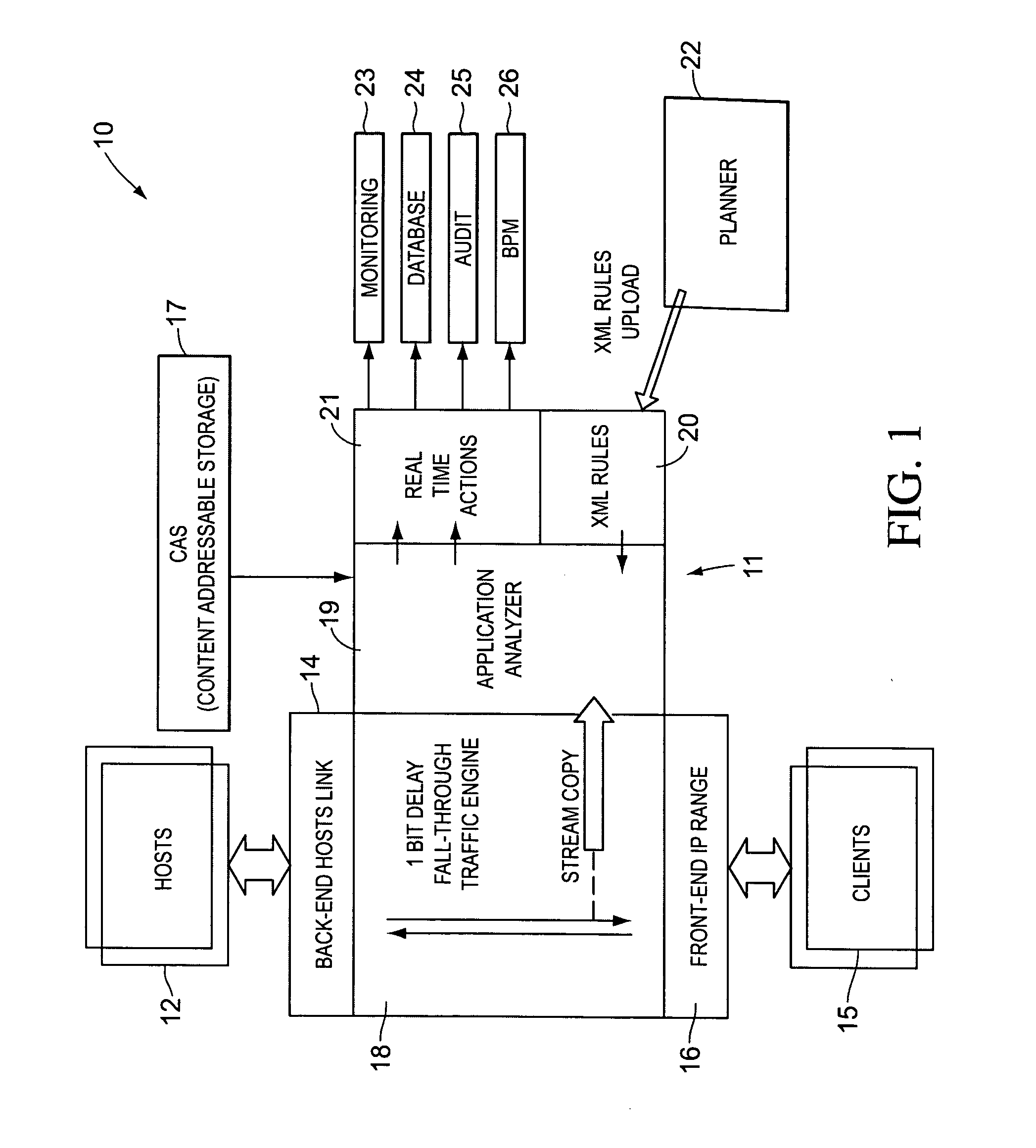
In order to track activities in a computerized system with client-server or other communications, a system configuration is needed which monitors, logs and reports traffic. This is somewhat akin to but not entirely similar a firewall. Thus, the invention contemplates a real-time, platform-independent, rule-based activity monitor for detecting a particular activity of interest as it occurs and for reporting such activity and the user substantially as fast.
Owner:MICRO FOCUS US
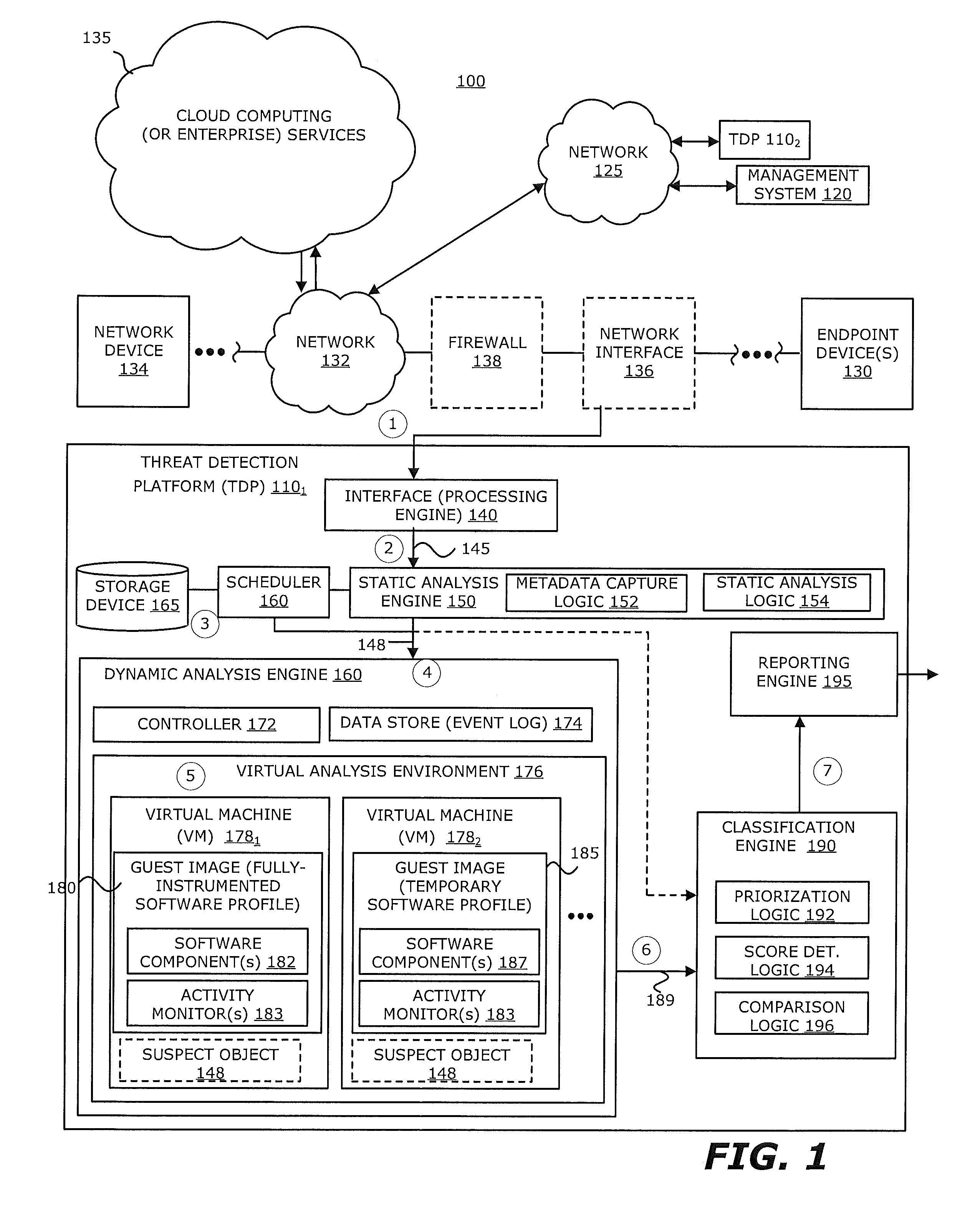
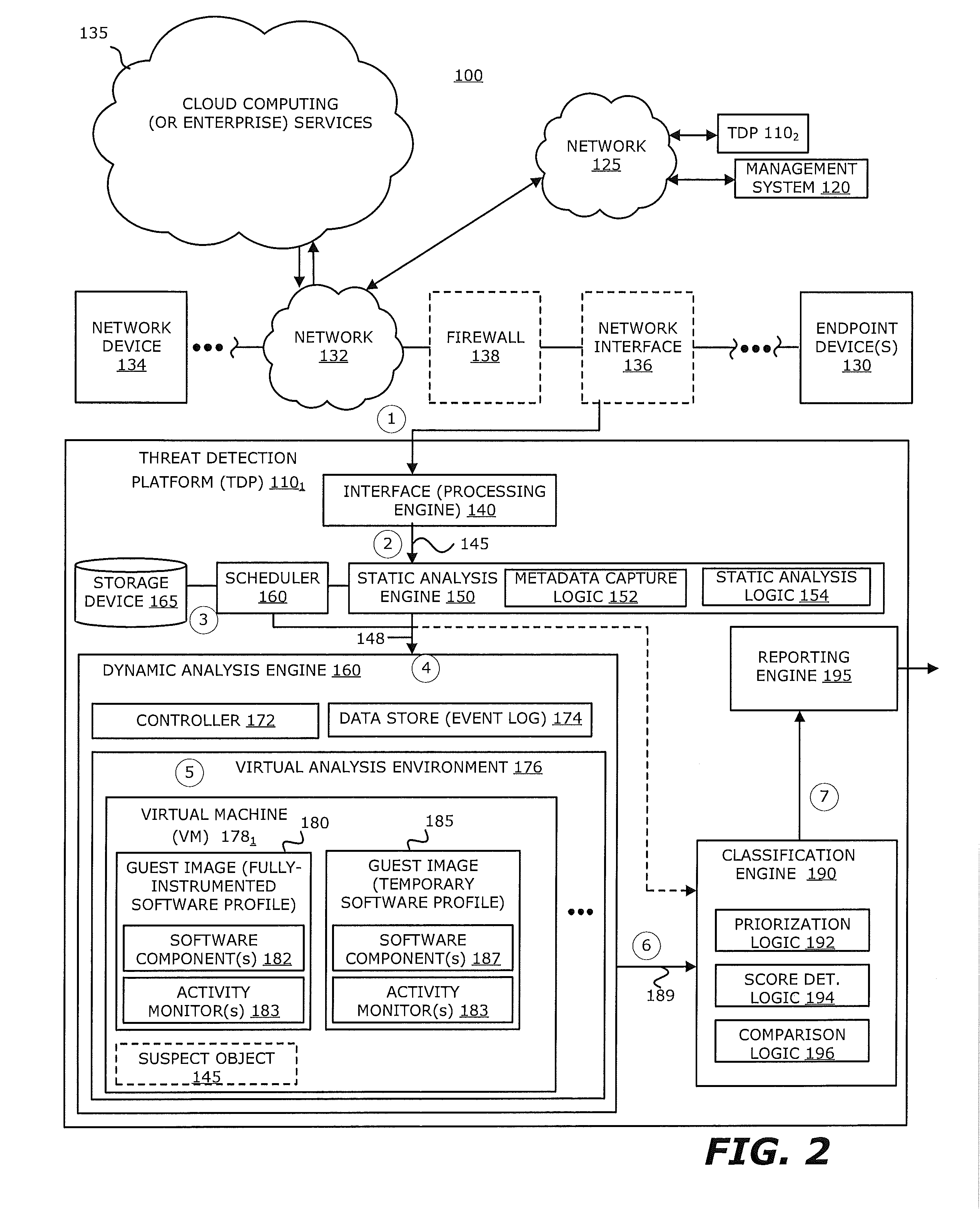
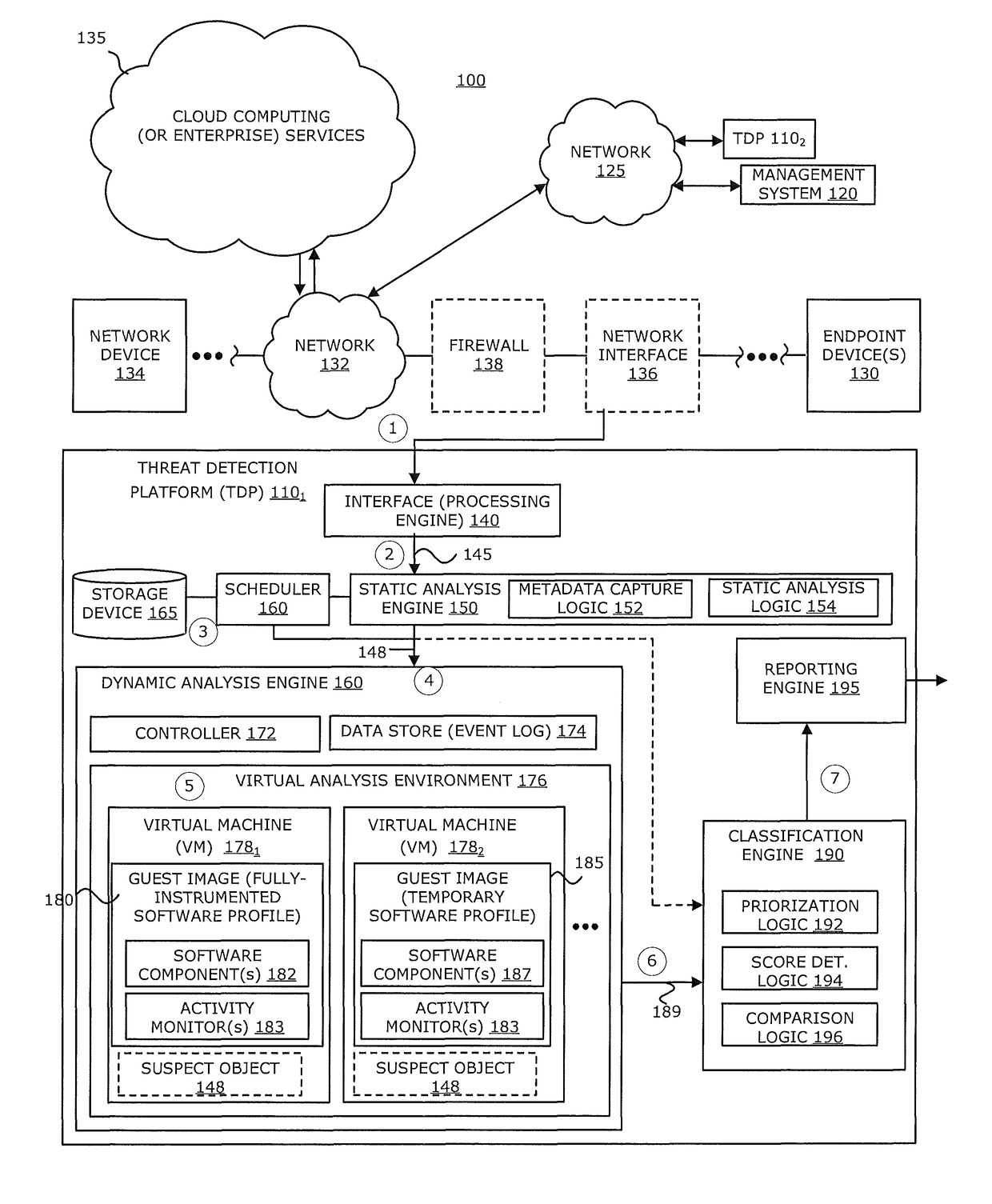
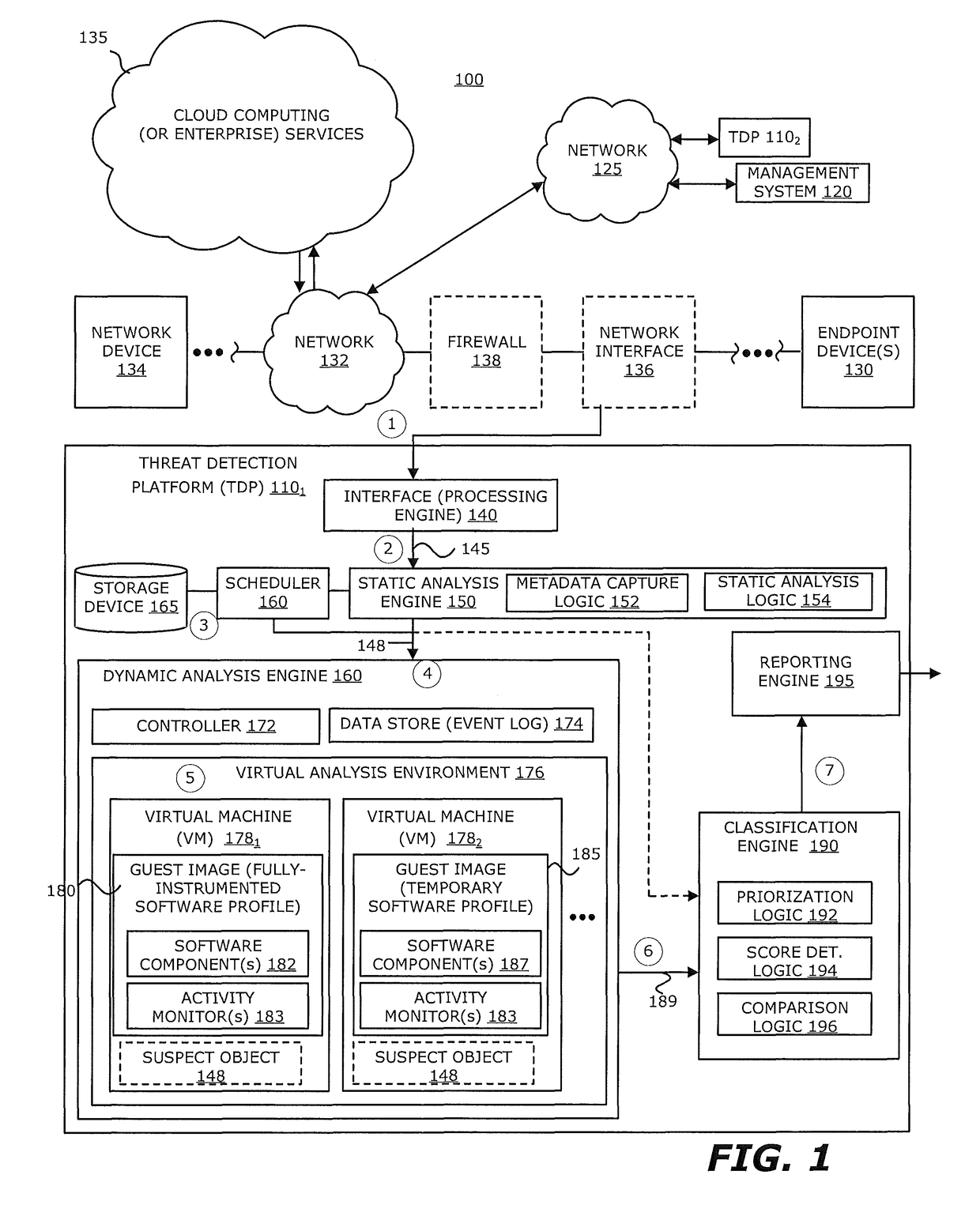
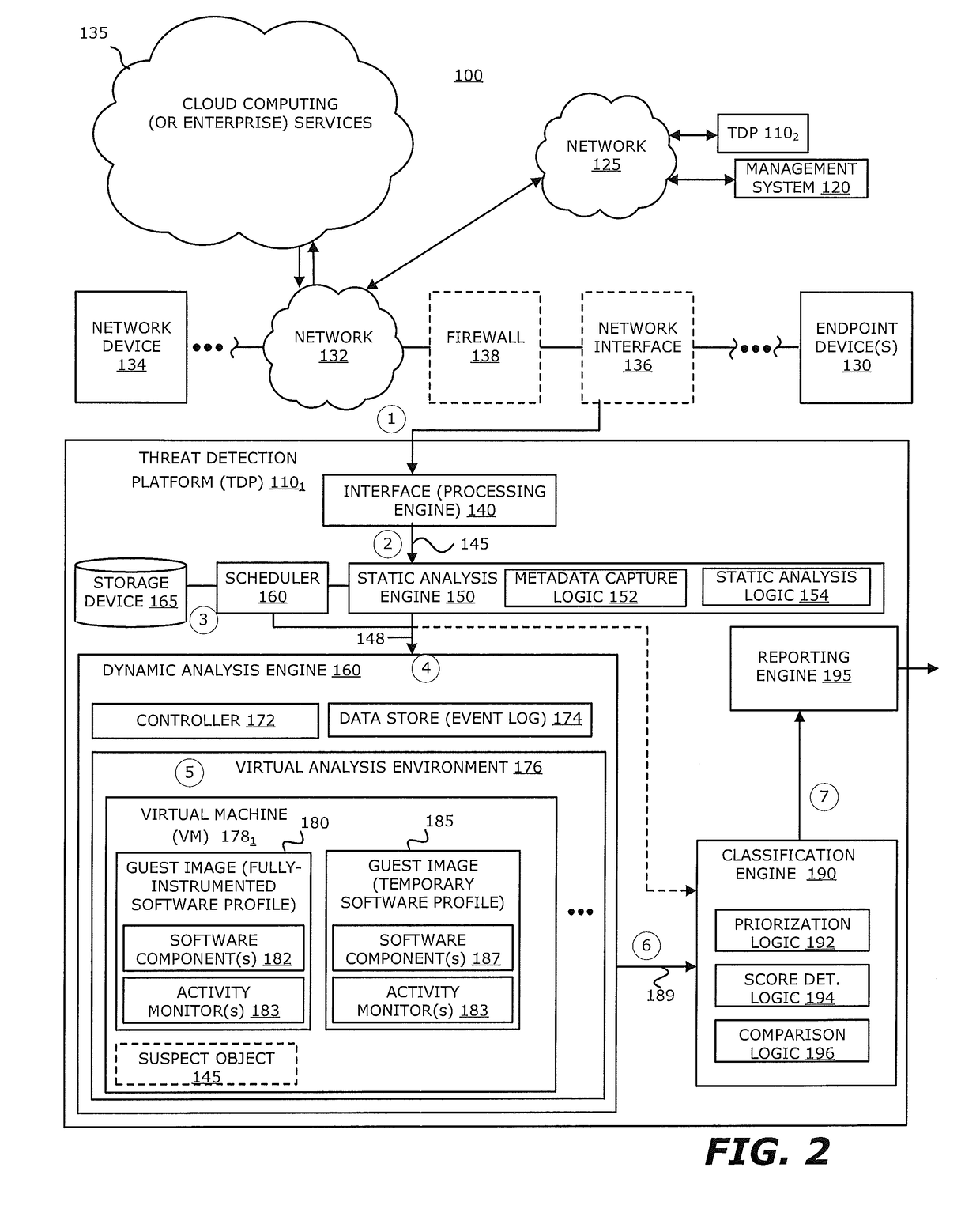
Zero-Day Rotating Guest Image Profile
ActiveUS20160191547A1Memory loss protectionError detection/correctionCommunication interfaceActivity monitor
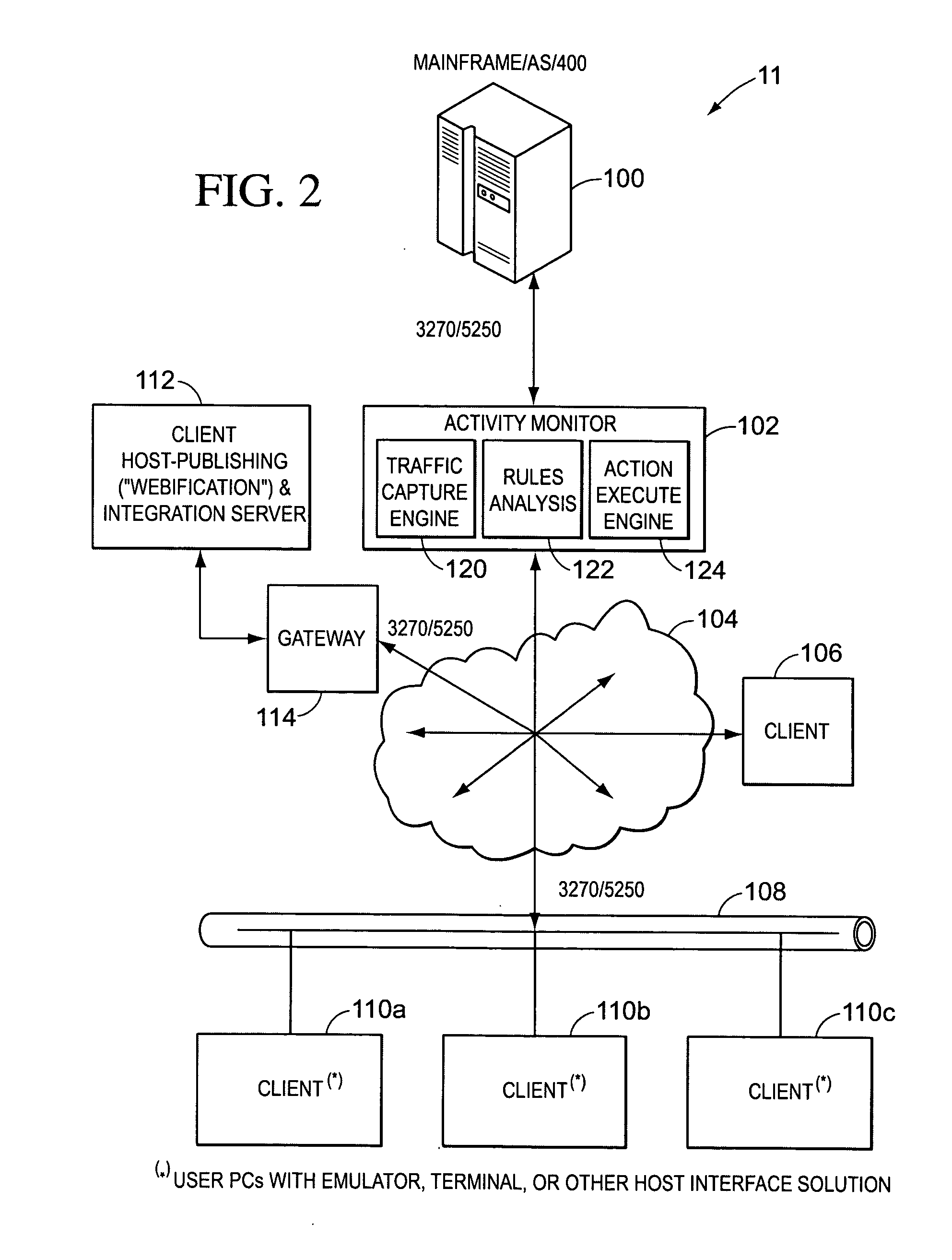
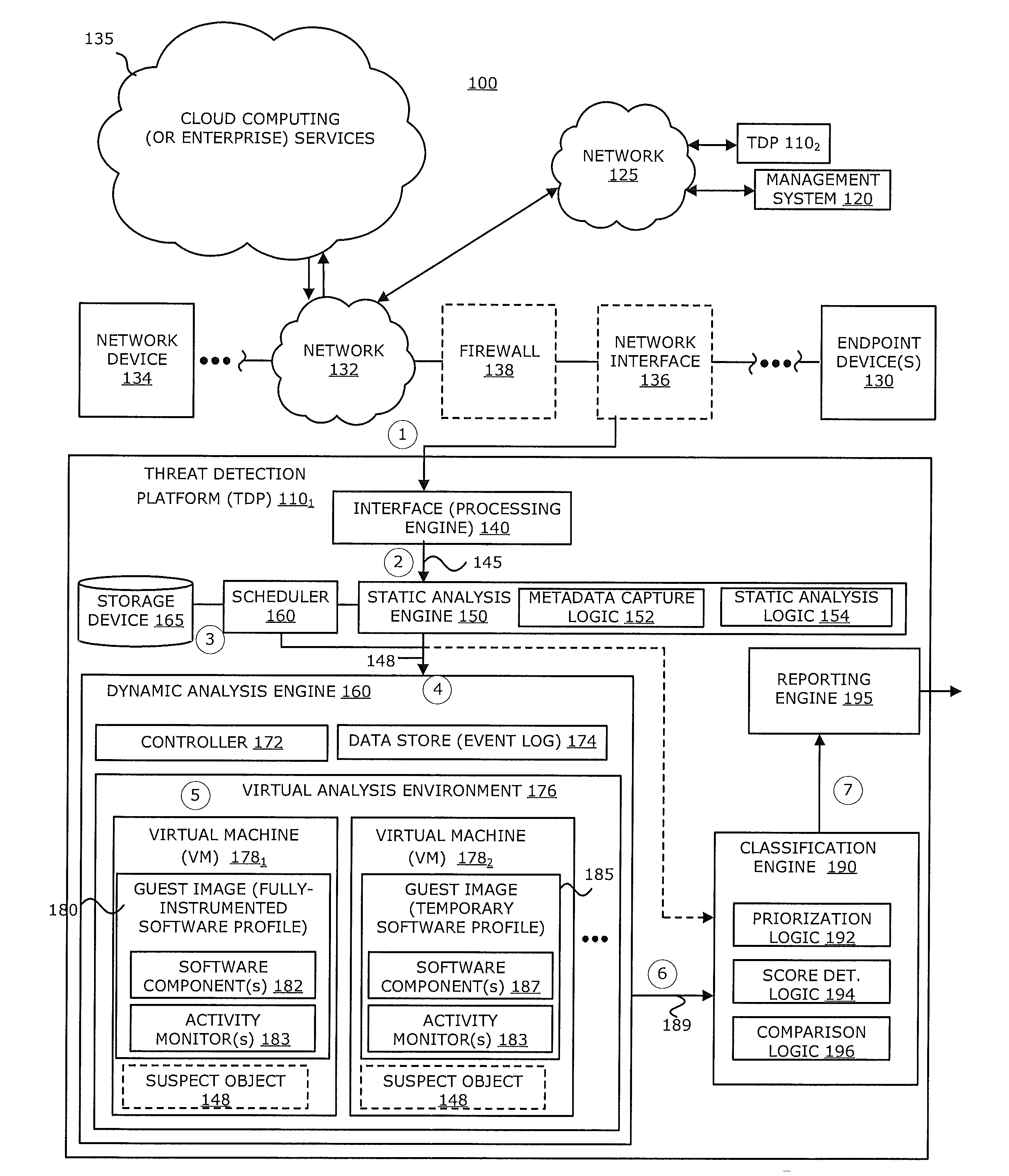
According to one embodiment, a threat detection platform features a housing, a communication interface, a processor coupled to the communication interface, and a data store. The data store includes (i) an event log, (ii) a first virtual machine, and (iii) a second virtual machine. The first virtual machine is provisioned with a first guest image that is based on an instrumented software profile that includes a first software component and activity monitors configured for the first software component. The second virtual machine is provisioned with a second guest image that is based on a temporary software profile that includes a second software component that is a more recent version of the first software component and the activity monitors configured for the first software component.
Owner:FIREEYE SECURITY HLDG US LLC
Zero-day rotating guest image profile
ActiveUS10075455B2Platform integrity maintainanceTransmissionCommunication interfaceActivity monitor
According to one embodiment, a threat detection platform features a housing, a communication interface, a processor coupled to the communication interface, and a data store. The data store includes (i) an event log, (ii) a first virtual machine, and (iii) a second virtual machine. The first virtual machine is provisioned with a first guest image that is based on an instrumented software profile that includes a first software component and activity monitors configured for the first software component. The second virtual machine is provisioned with a second guest image that is based on a temporary software profile that includes a second software component that is a more recent version of the first software component and the activity monitors configured for the first software component.
Owner:FIREEYE SECURITY HLDG US LLC
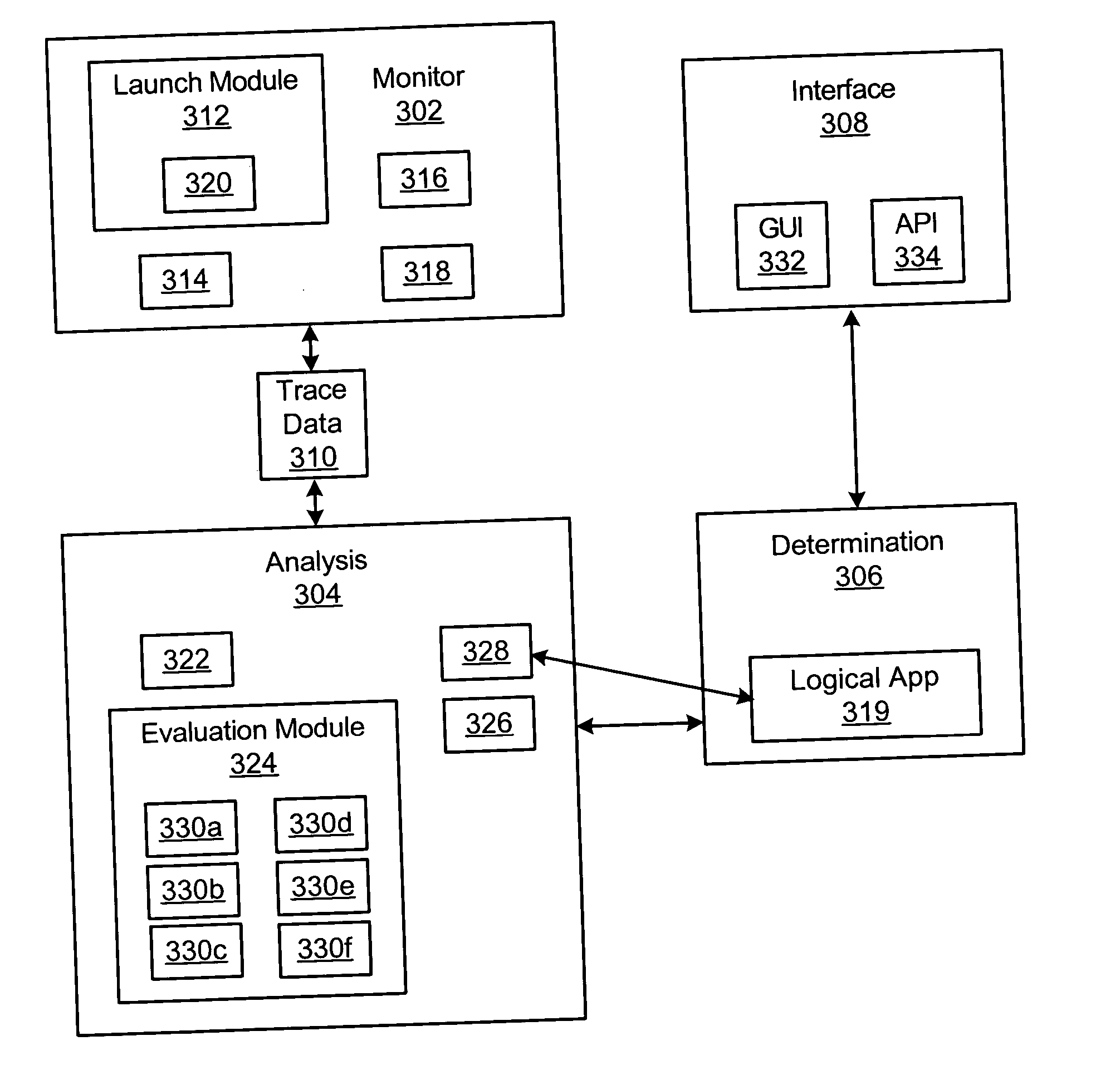
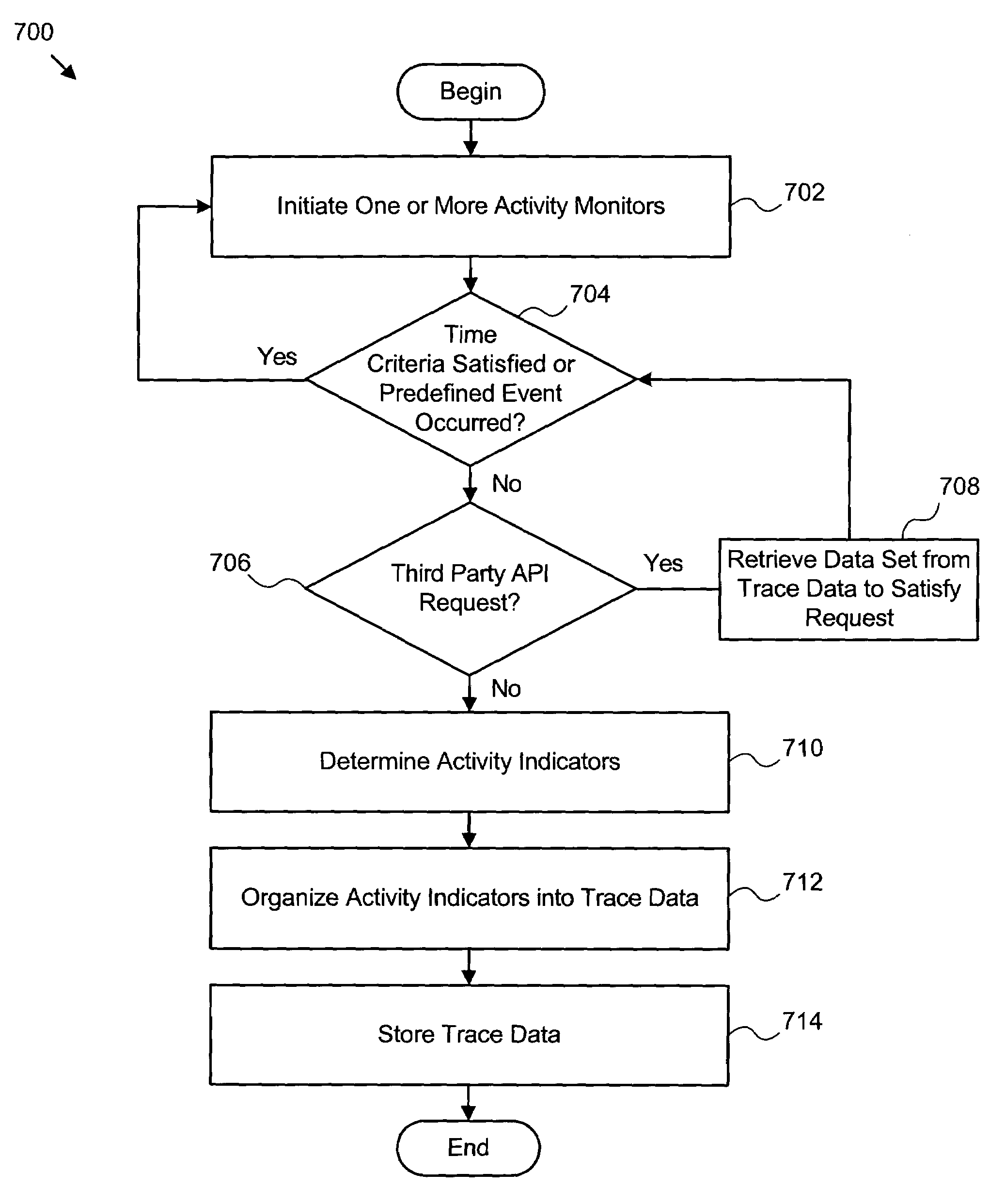
Apparatus, system, and method for gathering trace data indicative of resource activity
InactiveUS20060047805A1Memory loss protectionError detection/correctionActivity monitorReal-time computing
An apparatus, system, and method are provided for gathering trace data indicative of resource activity on a computer system. The present invention includes a monitoring module that initiates one or more activity monitors on a target computer system to detect different types of resource activity. A determination module determines activity indicators involving resources of the target computer system using the one or more activity monitors. The activity indicators may comprise a variety of information useful in identifying one or more separate resource activities. A collection module organizes the activity indicators into trace data representative of the resource activity. Preferably, the monitoring module, determination module, and collection module operate continuously on the target computer system. In this manner, the trace data includes an accurate set of both current activity indicators as well as historical activity indicators.
Owner:IBM CORP
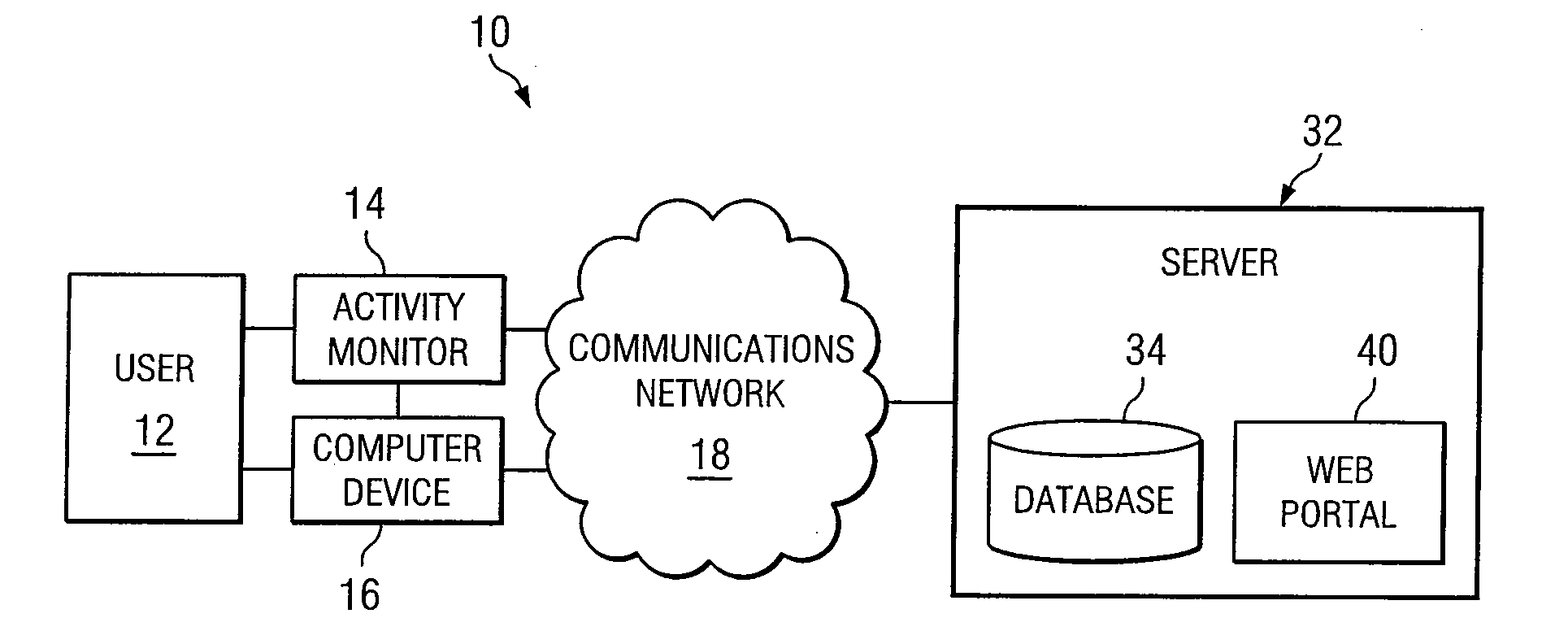
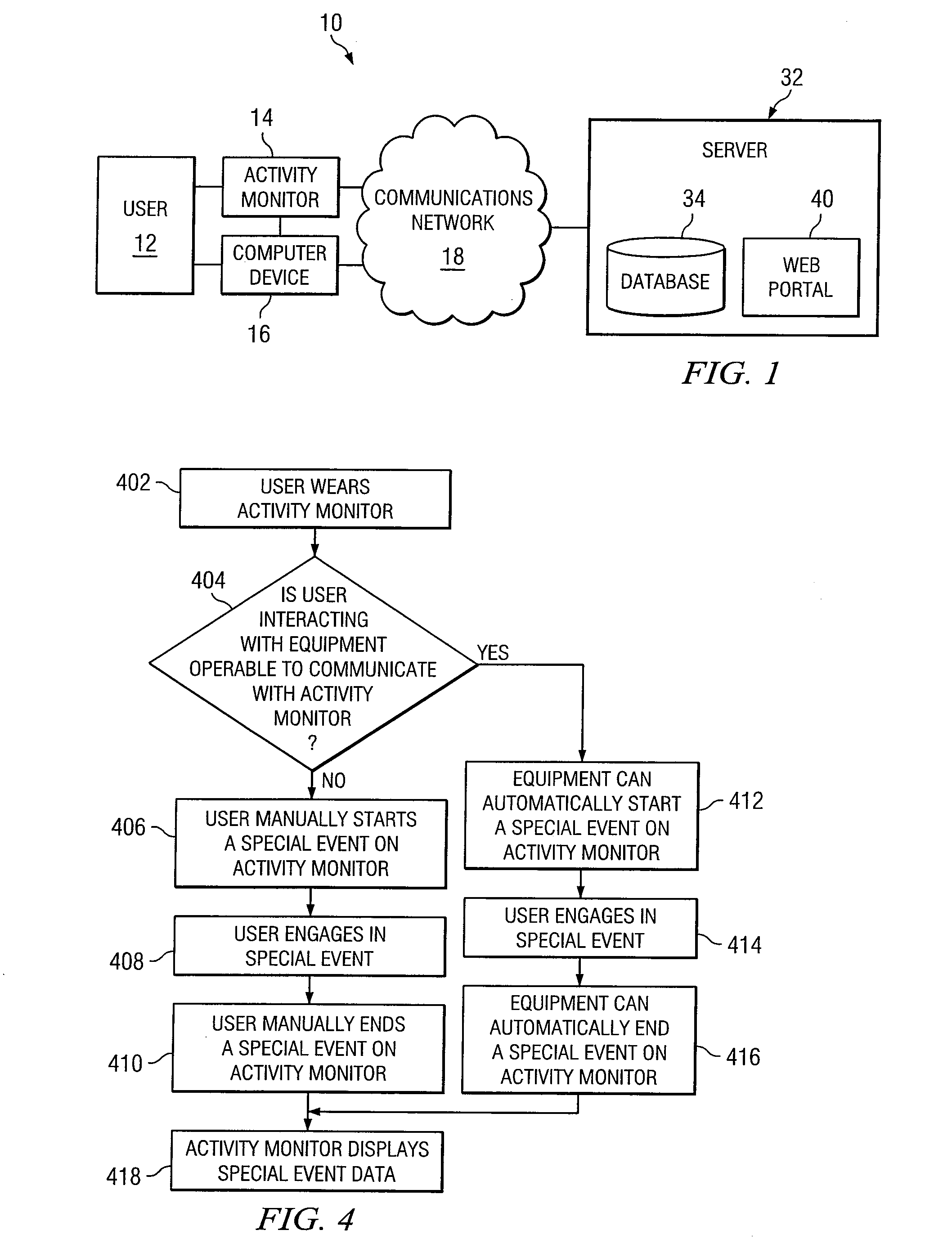
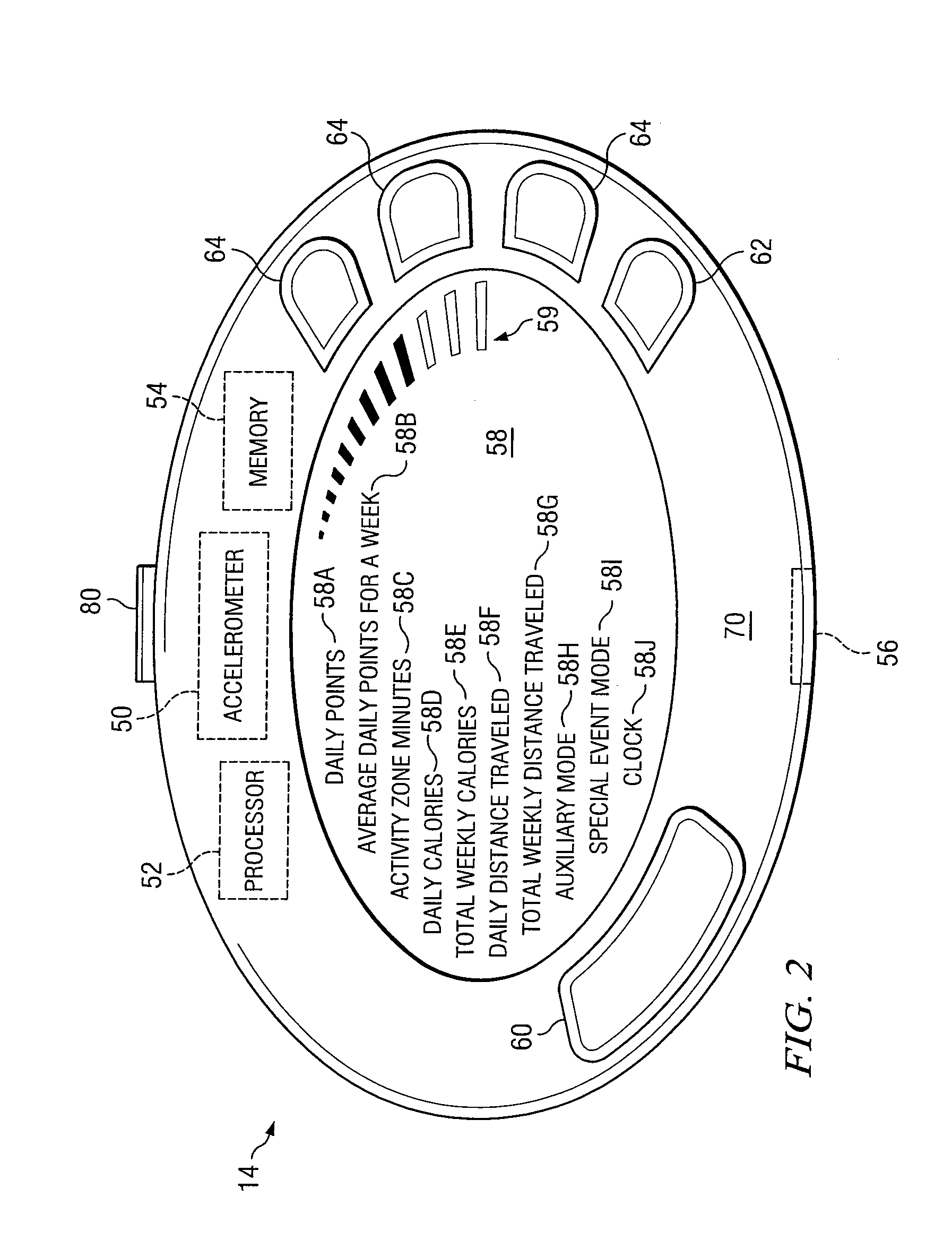
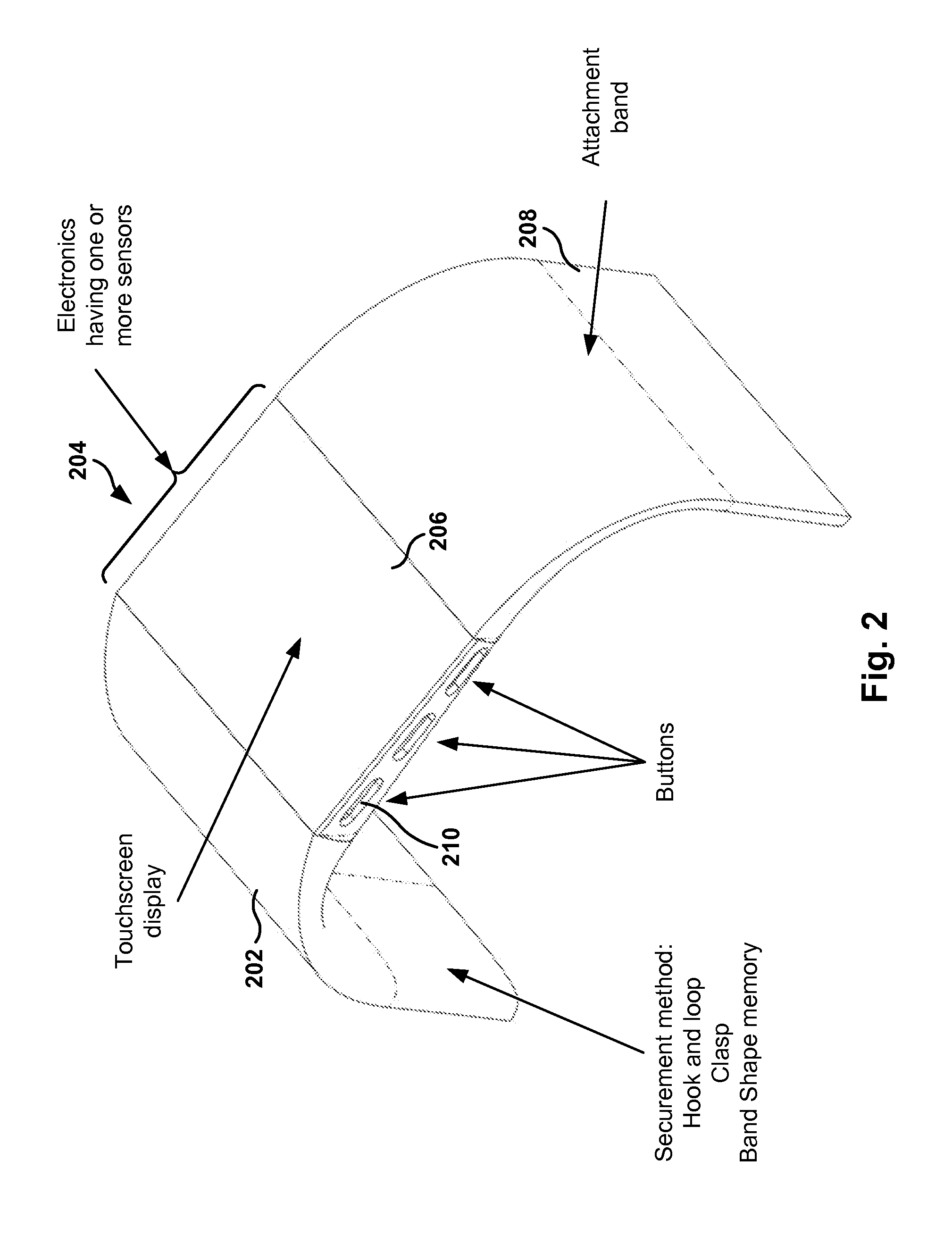
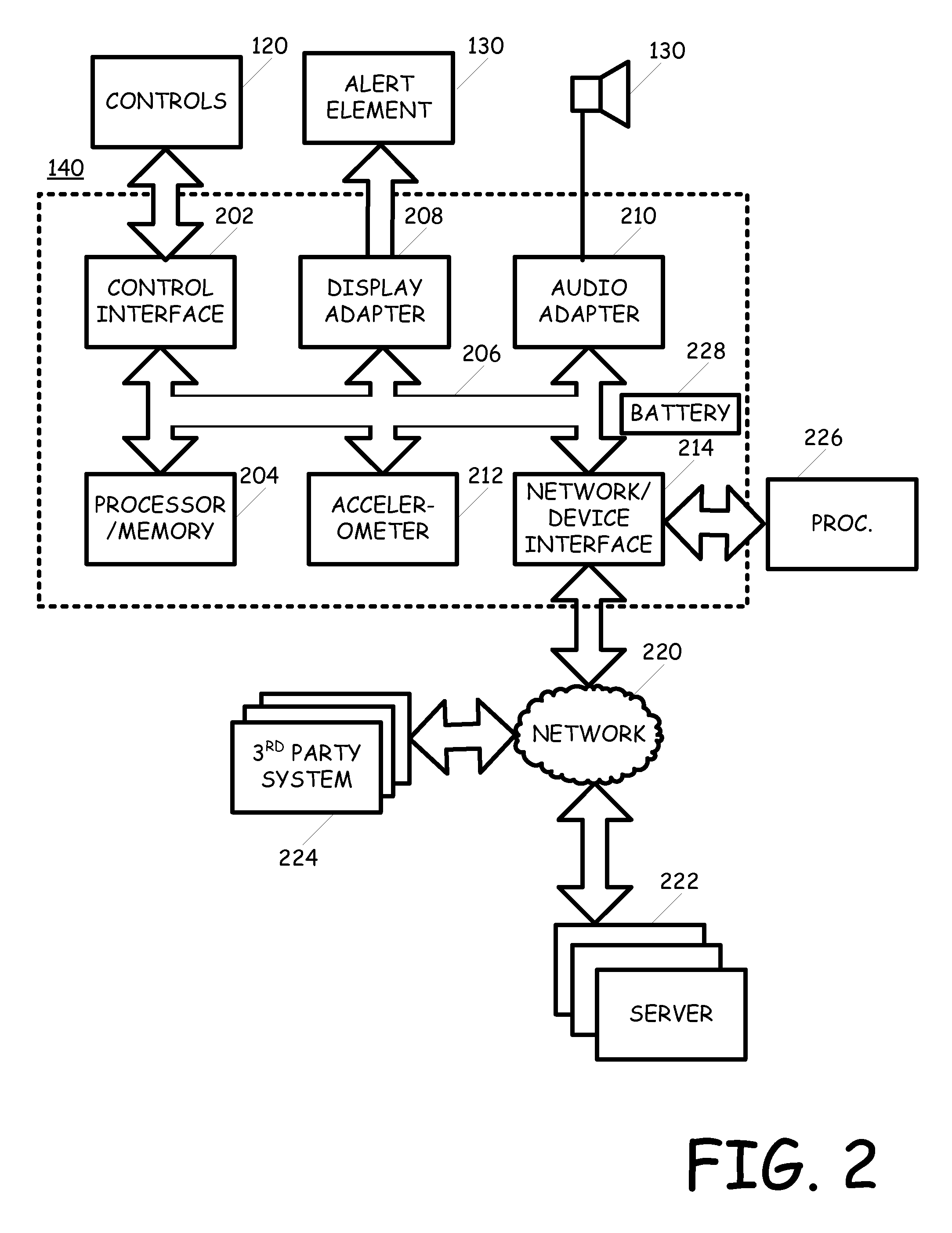
Activity Monitor for Collecting, Converting, Displaying, and Communicating Data
InactiveUS20080155077A1Eliminates and reduces disadvantageEliminates and reduces and problemPhysical therapies and activitiesLocal control/monitoringCommunications systemActivity monitor
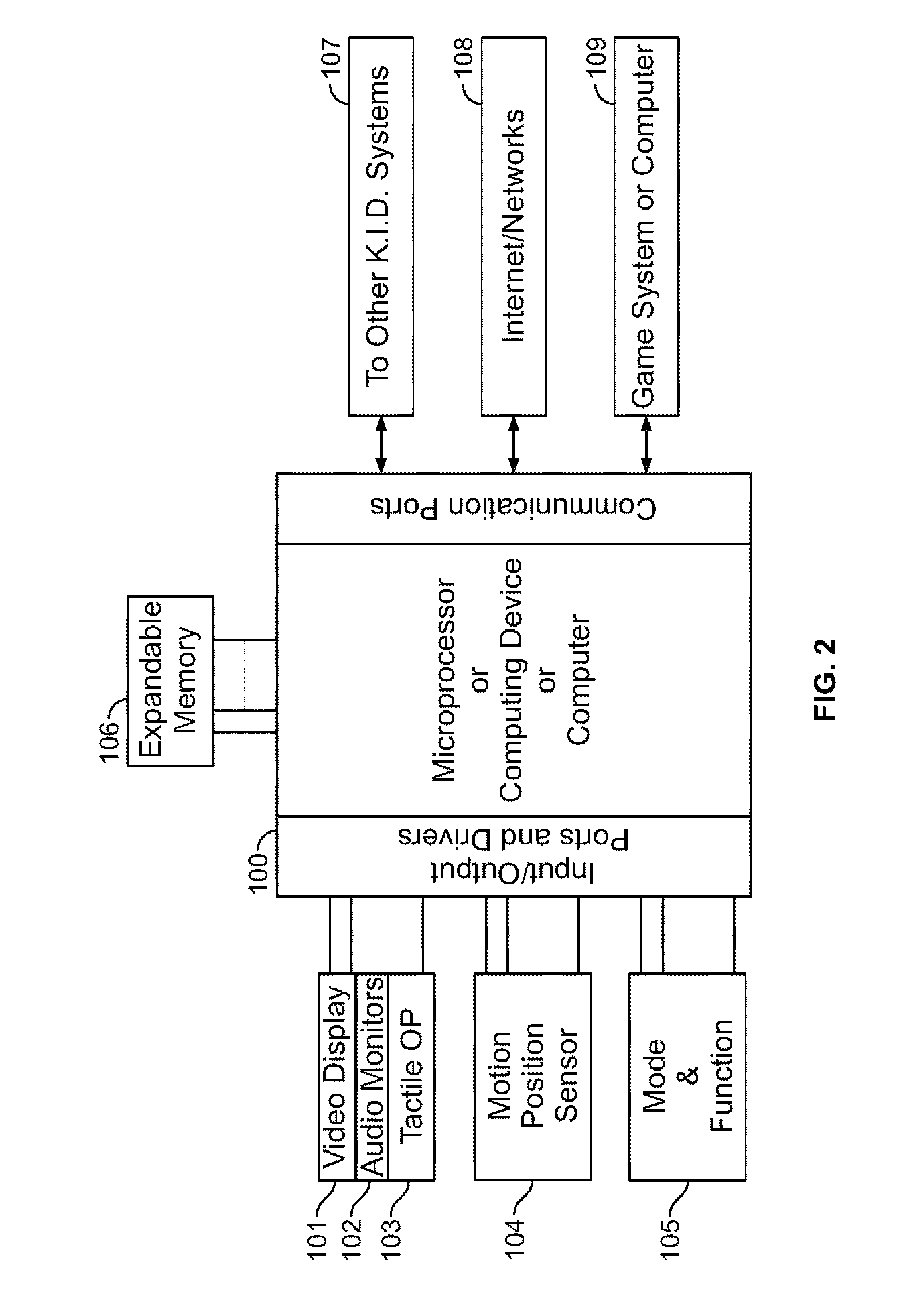
A communication system utilizes an activity monitor that is operable to collect data, convert data, display data, and communicate data. Web portal and activity monitor are operable to communicate data between one another. Web portal enables a user to monitor an individual or population's activity data. Activity monitor enables user to toggle through one or more activity modes to be displayed. Activity monitor constantly measures a user's activity. Auxiliary mode enables user to track data that can be unrelated to activity data. Special event mode on activity monitor enables a user or machine to begin and to end a special event, while the activity monitor measures activity data during the special event.
Owner:JAMES TERRY L
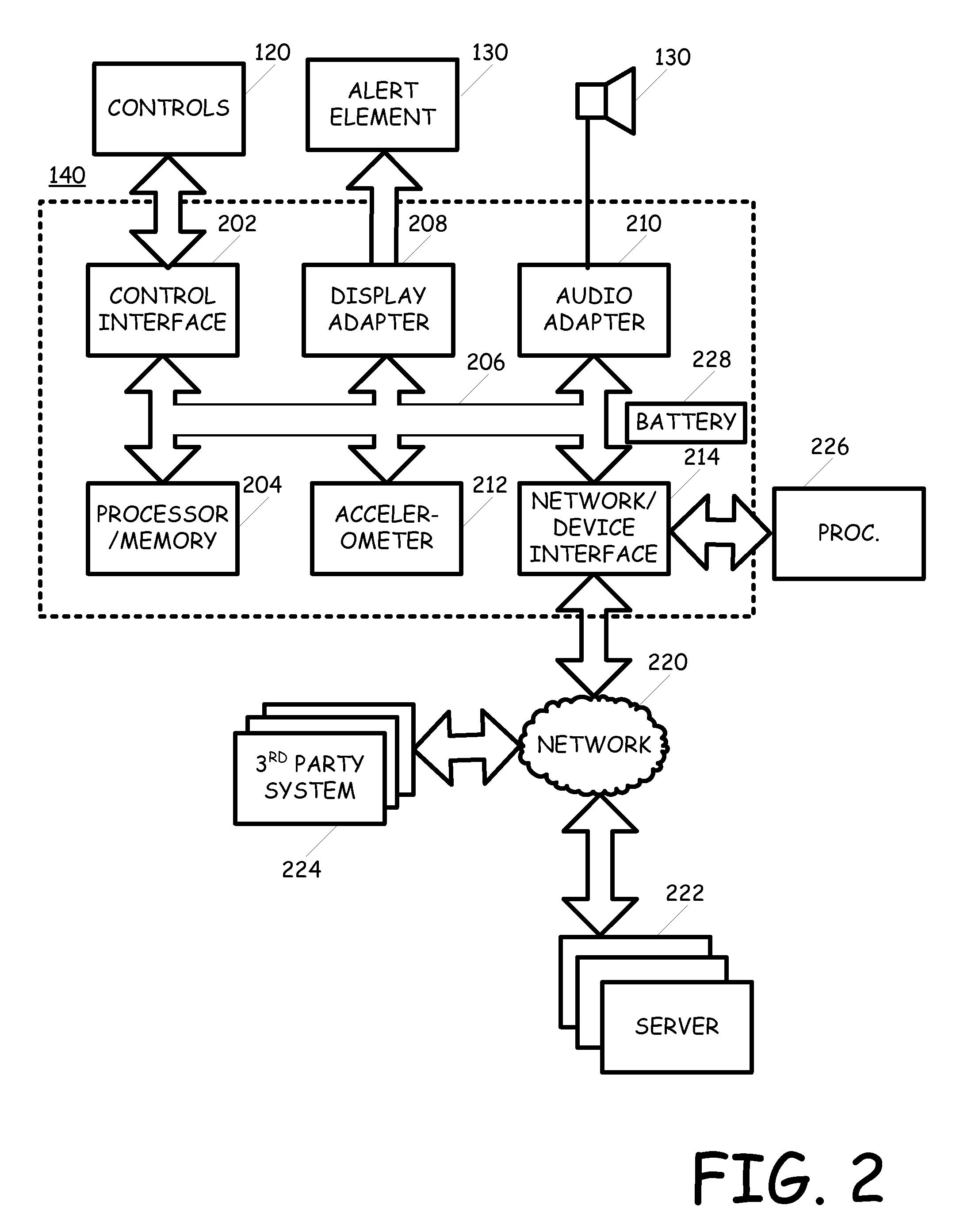
Selection of display power mode based on sensor data
Methods, devices, and computer programs are presented for managing power consumption in an activity monitoring device associated with a user. One method includes an operation for analyzing sensor data acquired by sensors of an activity monitoring device to be worn on a wrist of a user, the sensor data being associated with motion of the user. In addition, the method includes an operation for determining the motion profile of the activity monitoring device based on the sensor data. The method further includes an operation for identifying display settings for a display of the activity monitoring device based on the motion profile. The display settings are associated with a rate of power consumption by the display. The display settings are applied to the display of the activity monitoring device when the identified display settings are different than the current display settings.
Owner:FITBIT INC
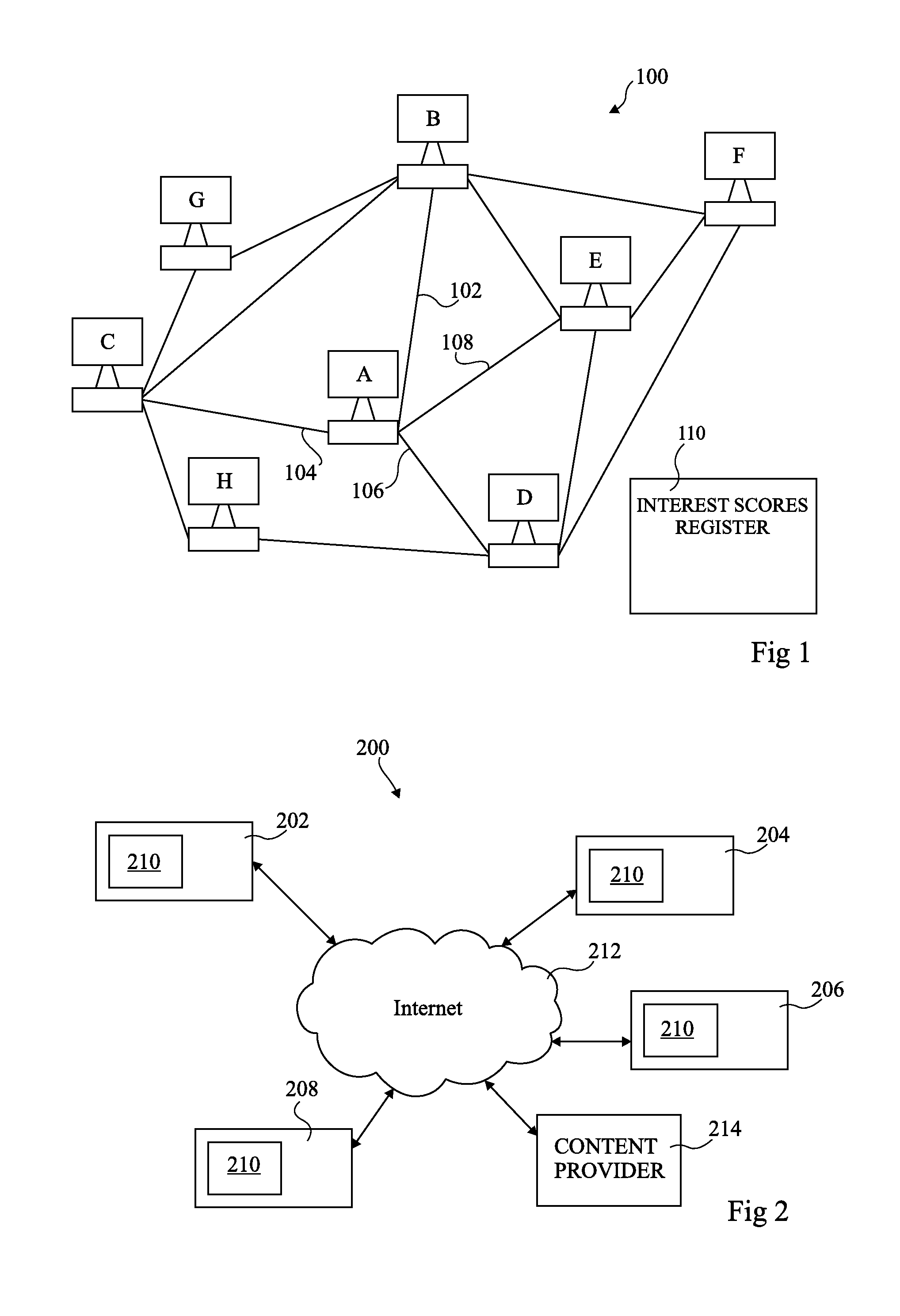
System for transmitting an electronic recommendation
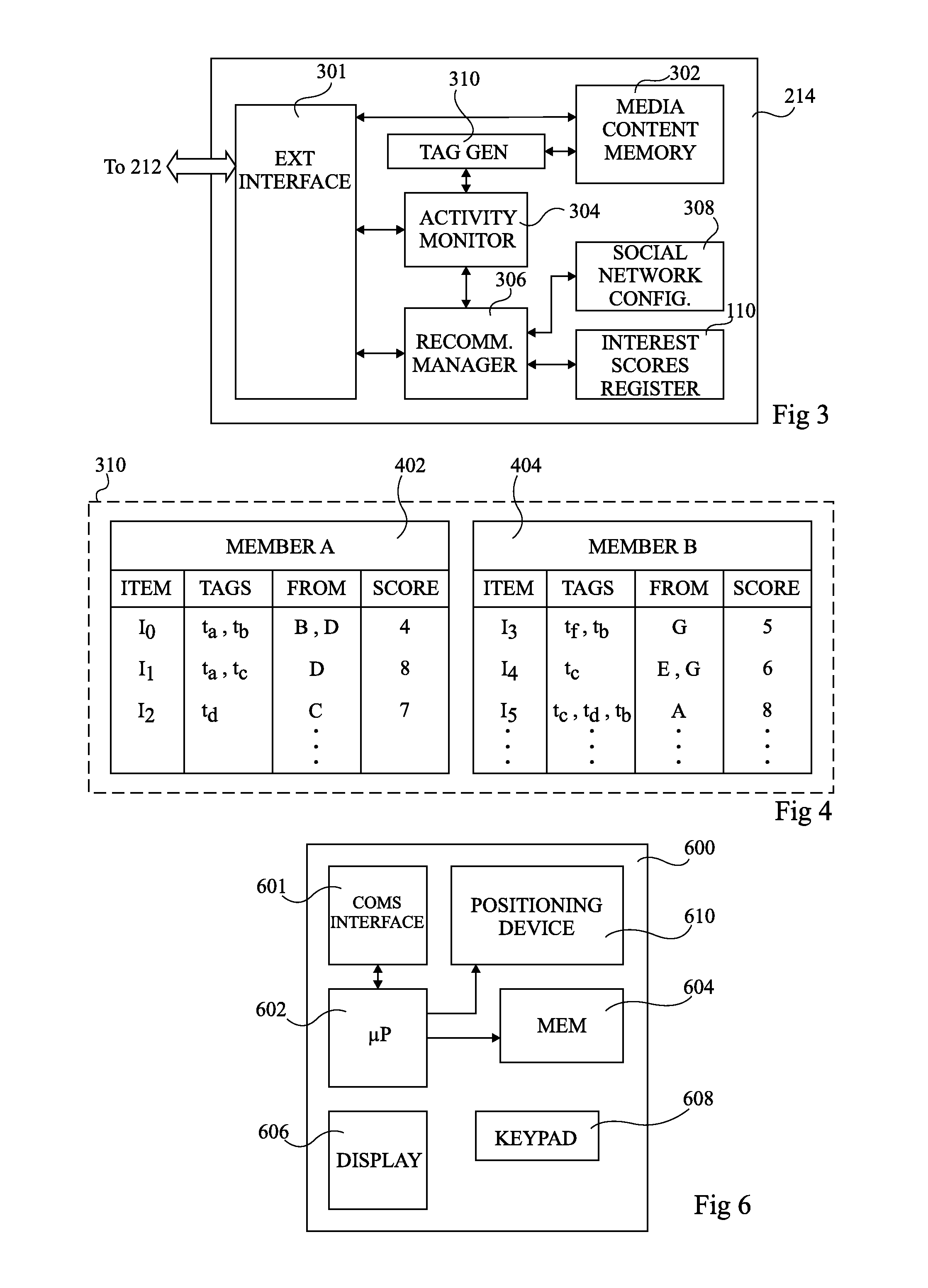
ActiveUS20100262658A1Need be addressMultiple digital computer combinationsOffice automationProcessor registerActivity monitor
The invention concerns a system for transmitting an electronic recommendation to members of a social network, the system having a user activity monitor (304) adapted to determine when a set of friends of a member in the social network accesses an item of media content or activity associated with at least one category and finds it of interest; a register arranged to store interest scores indicating an interest to the member of one or more items of media content or activities previously recommended to the member; and a recommendation manager (306) adapted to transmit an electronic recommendation relating to the item of media content or activity to the member based on the interest scores stored by the register relating to items of media content or activities of the at least one category previously recommended to the member by one or more of the set of friends.
Owner:ACCENTURE GLOBAL SERVICES LTD
System, apparatus and method for presenting and displaying content on a wide area network
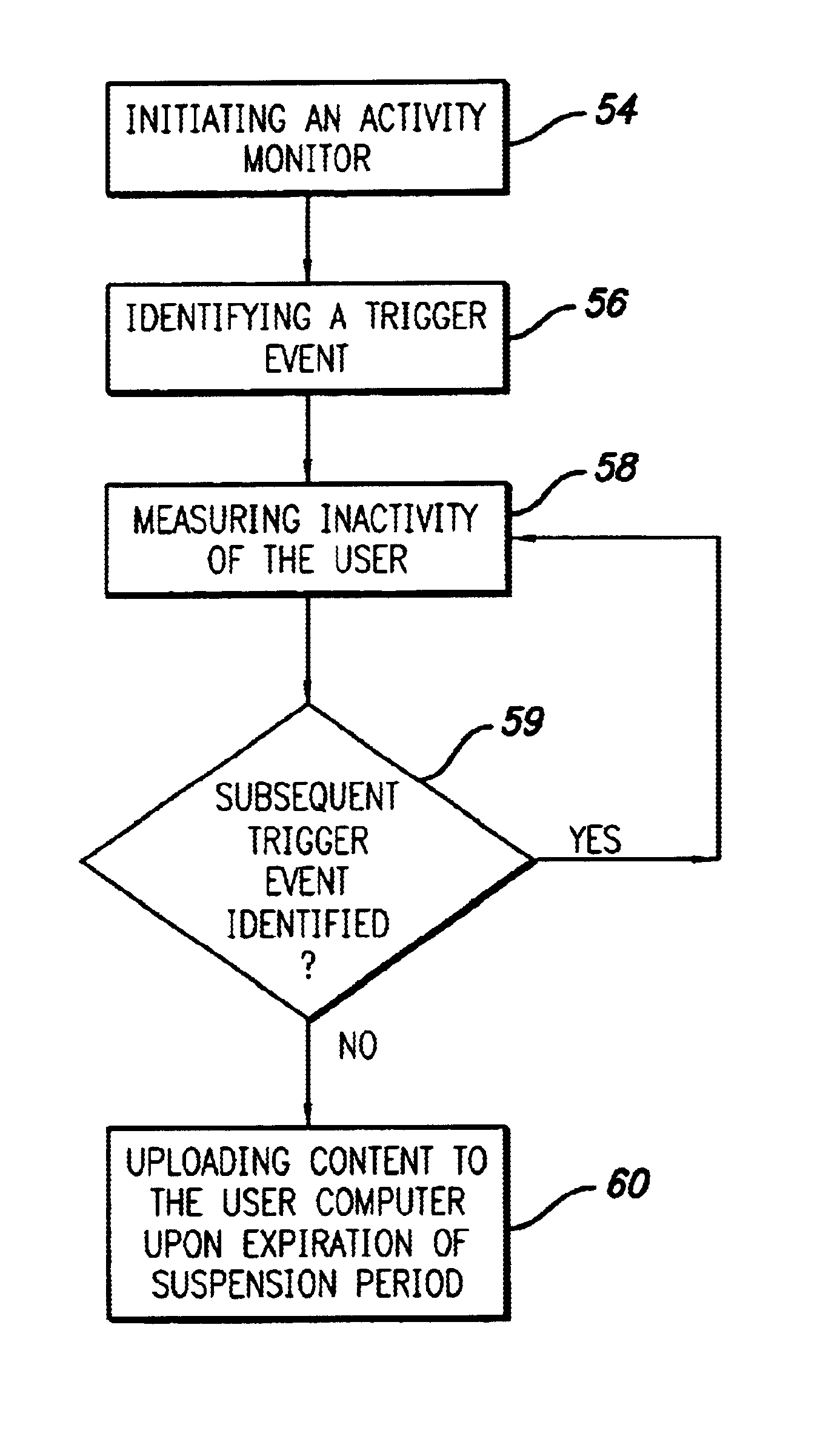
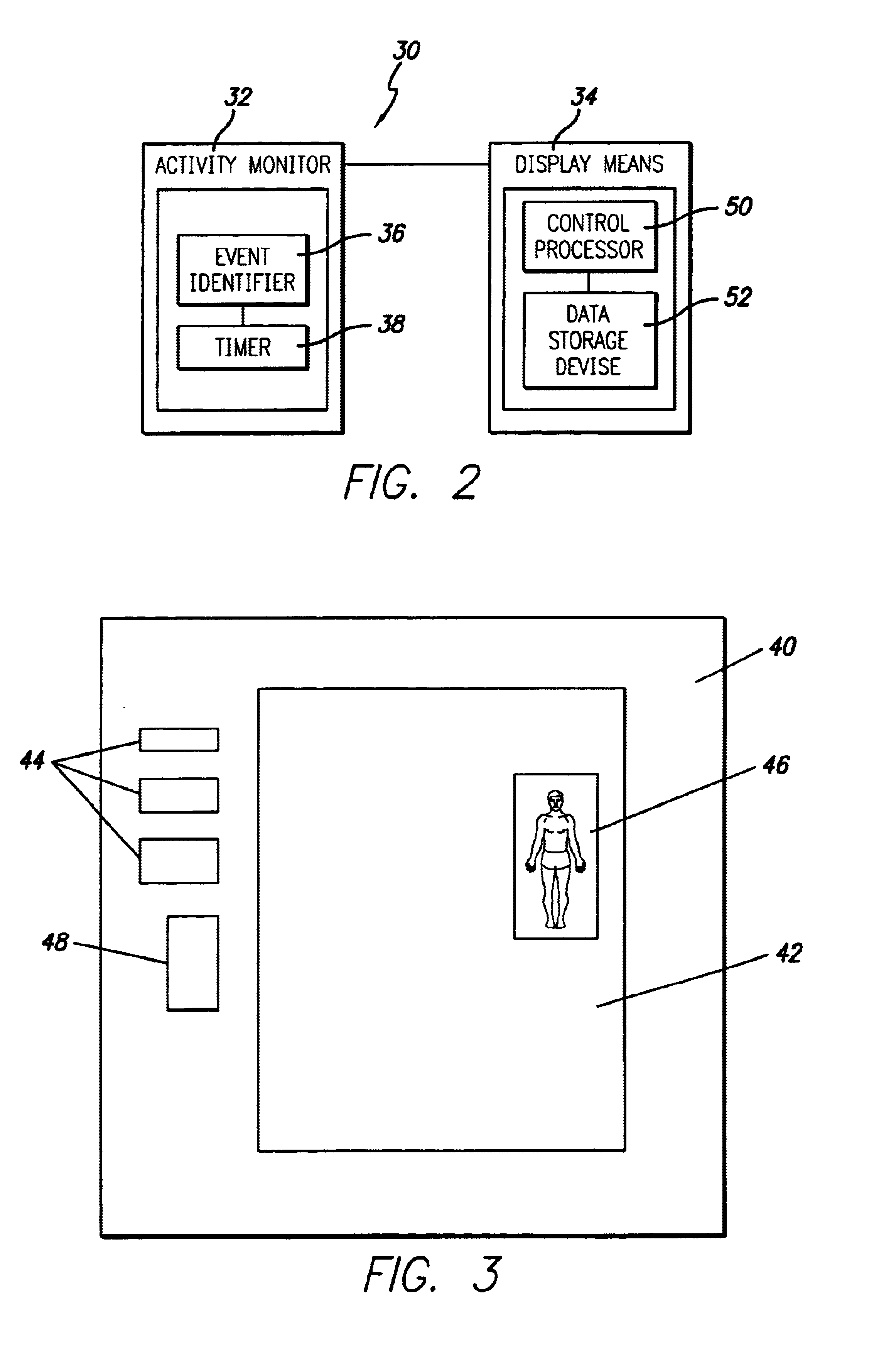
InactiveUS6763379B1Multiple digital computer combinationsBuying/selling/leasing transactionsMonitoring systemTimer
Embodiments of the instant invention are directed to a system, apparatus and method for monitoring a user's activities and displaying and presenting unsolicited content to users over a wide area network. Embodiments of the instant invention include a monitoring system comprising an activity monitor and a content transfer and display means, wherein the activity monitor comprises an event identifier and a timer. The monitoring system monitors user activities, identifies trigger events, measures the elapsed time of inactivity of the user and initiates the presentation of unsolicited data, or content, to the user computer. In general, the monitoring system identifies trigger events and measures the elapsed time between trigger events. If the elapsed time between the trigger events exceeds a predefined time period the monitoring system causes unsolicited data to be presented on the user computer.
Owner:INTELLECTUAL VENTURES I LLC
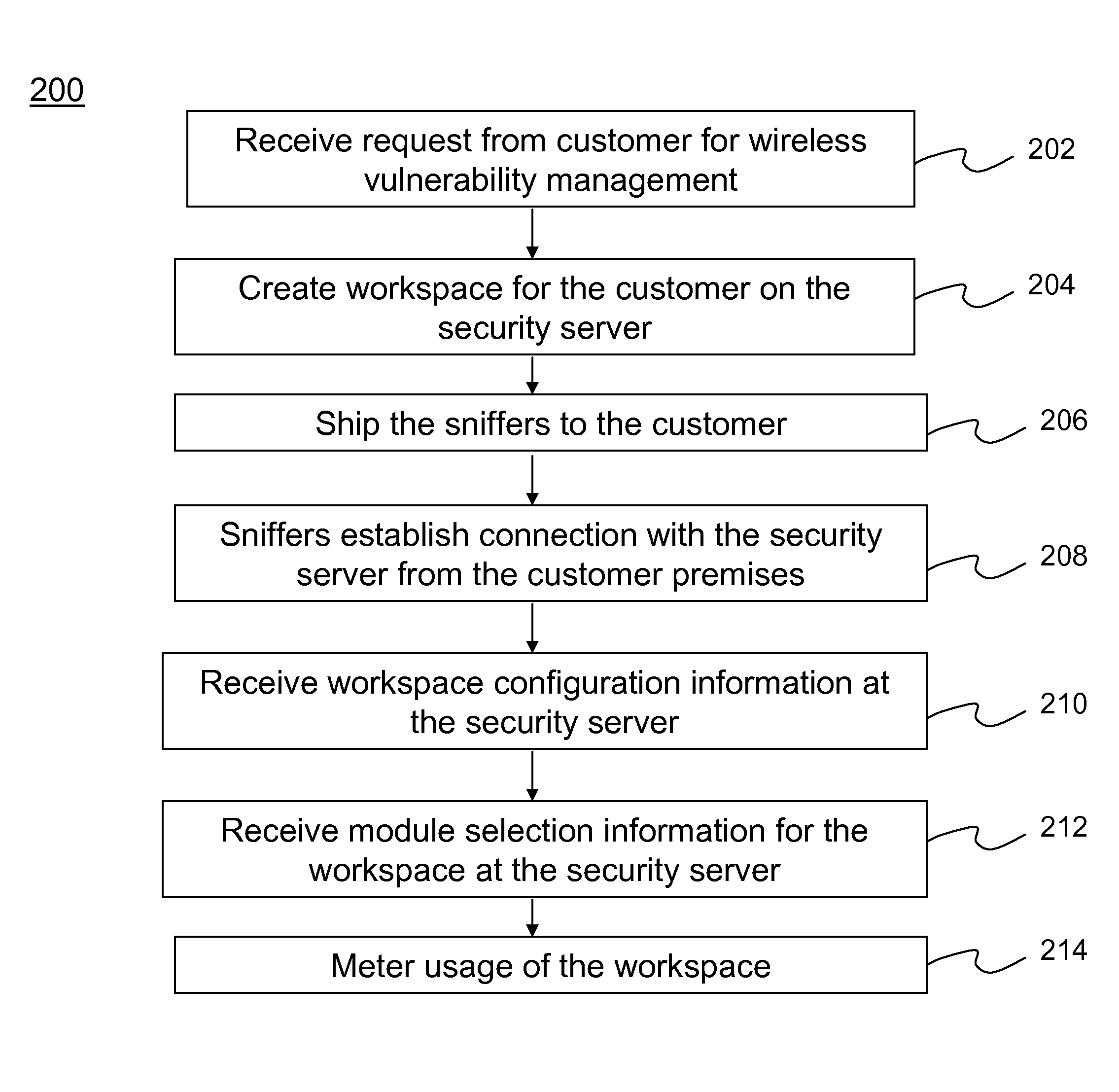
Method and system for providing wireless vulnerability management for local area computer networks
ActiveUS20090119776A1Reduce overheadEasy to customizeMemory loss protectionDigital computer detailsVulnerability managementComputer network
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:ARISTA NETWORKS
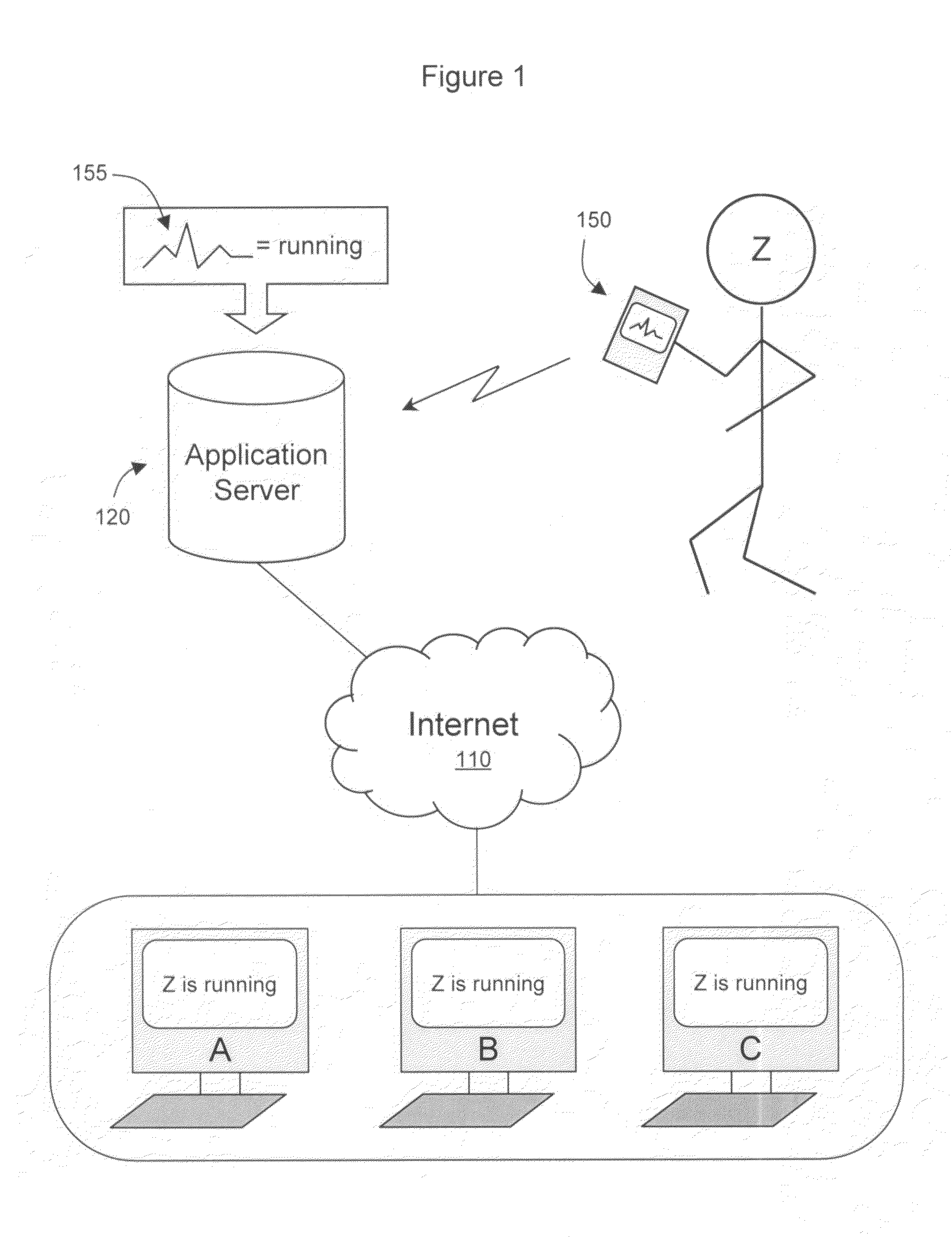
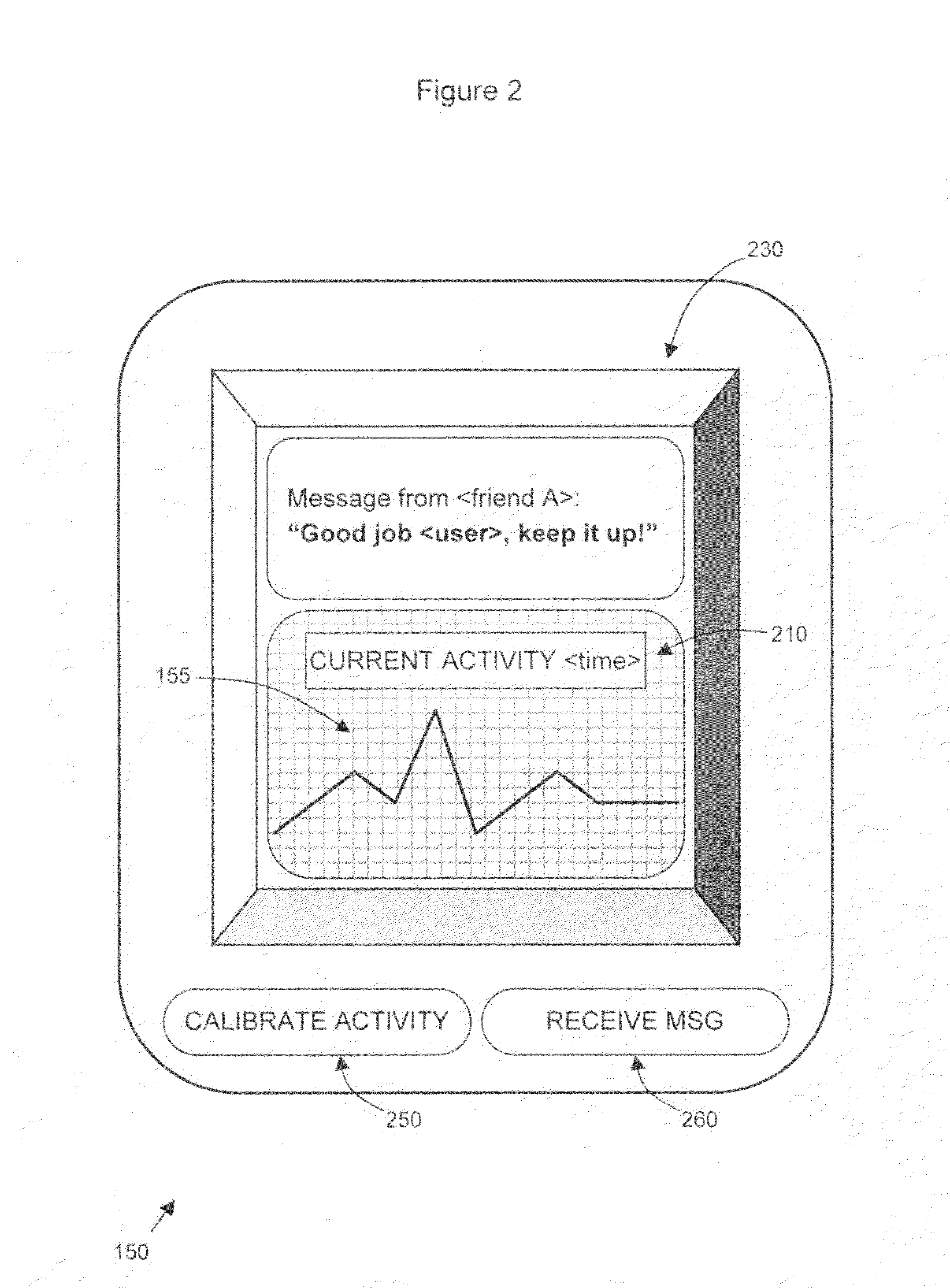
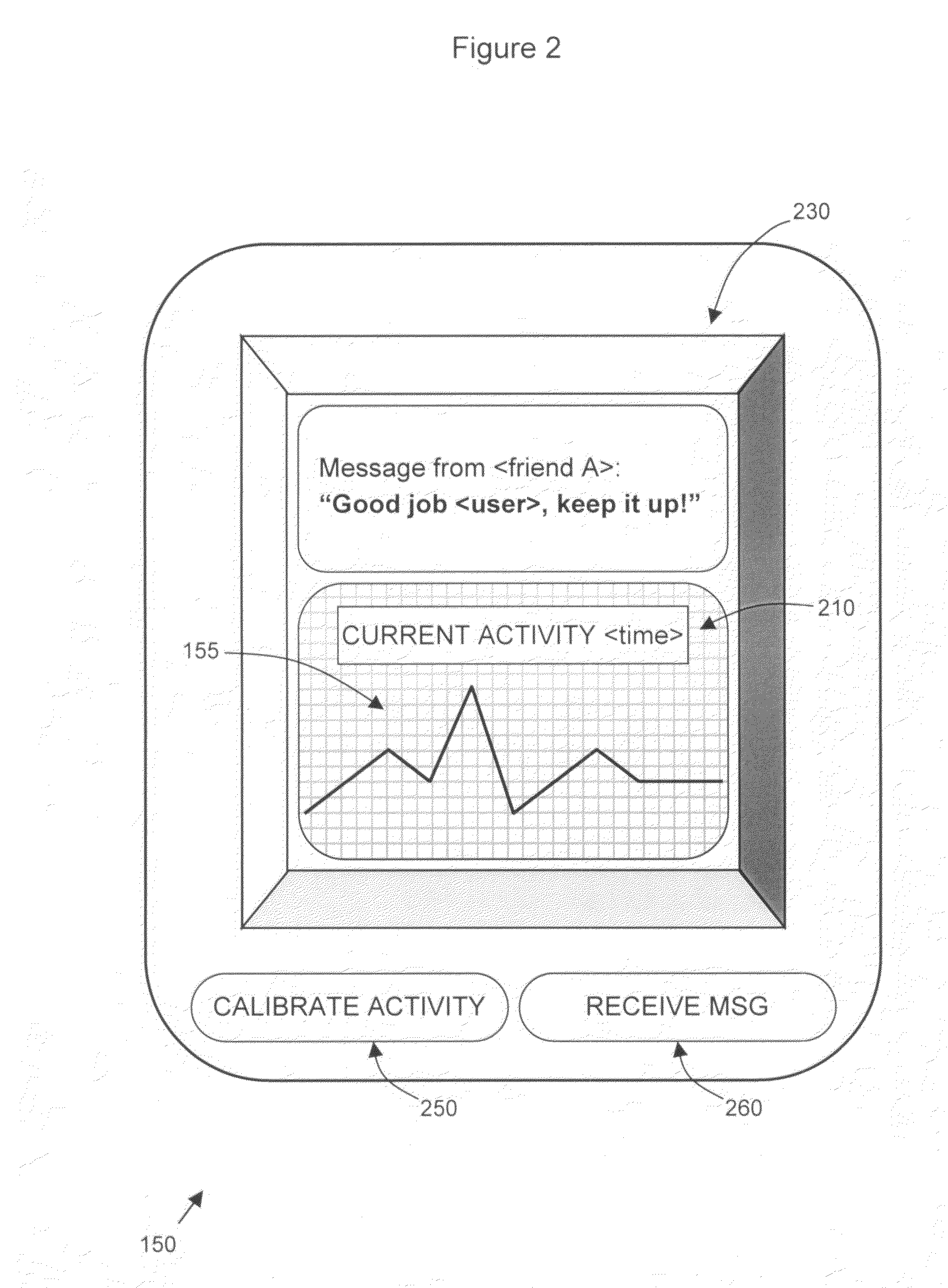
User-calibrated activity newsfeed on a social network
ActiveUS8533269B2Digital data information retrievalCathode-ray tube indicatorsPersonalizationWeb site
Calibration and publication of user activity on a computer implemented social network is provided. Activity signals of user activity is measured by an activity monitor and calibrated by the user. The calibration includes assigning an activity signal with a personalized identifier for the activity for comparison with future measured activity signals. Near real-time publication of the activity on the social network allow users of the network to timely view user behavior. The publication on a social networking website includes the identifier if the activity has been calibrated. By calibrating and publishing user activity, users can connect to others based on the activity. The publication can be on newsfeed on a user profile for friends of the user to view. A user and the user's friends can communicate with each other, which allows the user to receive motivation from the friends and be accountable to the friends.
Owner:INVENT LY LLC
Heartbeat apparatus via remote mirroring link on multi-site and method of using same
InactiveUS20050229034A1Robustness of serviceFast failoverDigital computer detailsTransmissionFailoverActivity monitor
The present invention is directed to a heartbeat apparatus via a remote mirroring link for a multi-site and a method for using the heartbeat apparatus. Information is registered in a configuration table, wherein the configuration table stores host ID information and volume ID information. The configuration table is configured, access requests from a host are verified, host activity is recorded, and additional records are created in the configuration table when a match is found between the access records and the registered information. In a multi-site having two, three or more sites in a multi-hoop configuration, a failover process with remote mirroring pairs is performed by configuring a correlation between a remote mirroring pair group, an activity monitor function and an alert function, wherein the alert function is performed by a host sending status information regarding activity monitoring in a storage system and retrieving the notification information via a plurality of data links, and creating a status manage table using the notification information.
Owner:HITACHI LTD
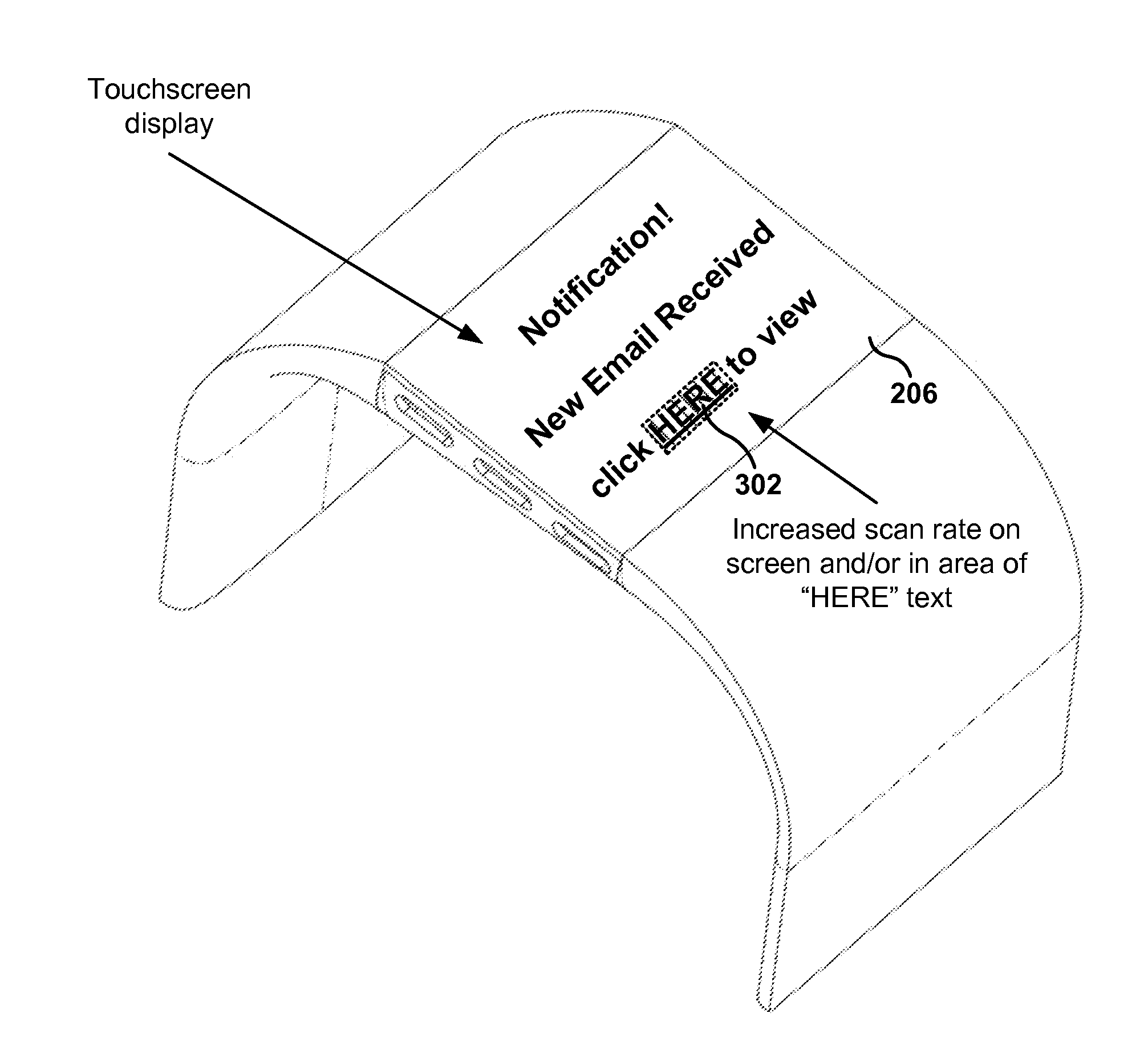
Power consumption management of display in portable device based on prediction of user input
ActiveUS20140125619A1Improve processingPhysical therapies and activitiesInertial sensorsUser inputActivity monitor
Methods, devices, and computer programs are presented for managing power consumption of a display. One method includes an operation for setting a first display setting for a touchscreen of an activity monitoring device associated with a user. The first display setting has having a first rate of power consumption by the display and a first touchscreen scan rate for detecting touch on the touchscreen. Further, the method includes operations for receiving data at the activity monitoring device, the data being indicative of an external event, and for applying a second display setting for the touchscreen based on a predefined expected user interaction. The second display setting has a second rate of power consumption and a second touchscreen scan rate.
Owner:FITBIT INC
User-calibrated activity newsfeed on a social network
ActiveUS20090144369A1Digital data information retrievalCathode-ray tube indicatorsPersonalizationWeb site
Calibration and publication of user activity on a computer implemented social network is provided. Activity signals of user activity is measured by an activity monitor and calibrated by the user. The calibration includes assigning an activity signal with a personalized identifier for the activity for comparison with future measured activity signals. Near real-time publication of the activity on the social network allow users of the network to timely view user behavior. The publication on a social networking website includes the identifier if the activity has been calibrated. By calibrating and publishing user activity, users can connect to others based on the activity. The publication can be on newsfeed on a user profile for friends of the user to view. A user and the user's friends can communicate with each other, which allows the user to receive motivation from the friends and be accountable to the friends.
Owner:INVENT LY LLC
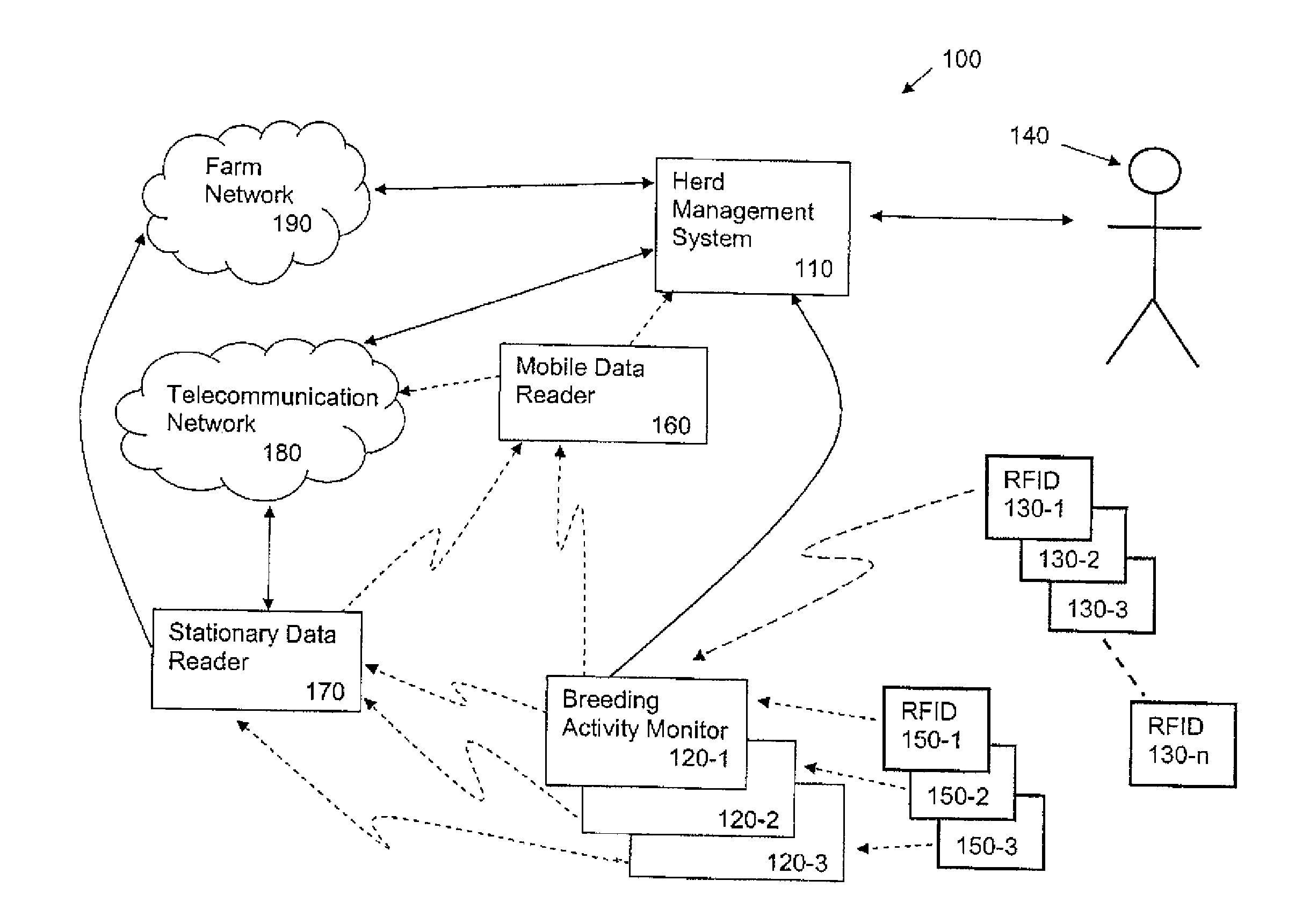
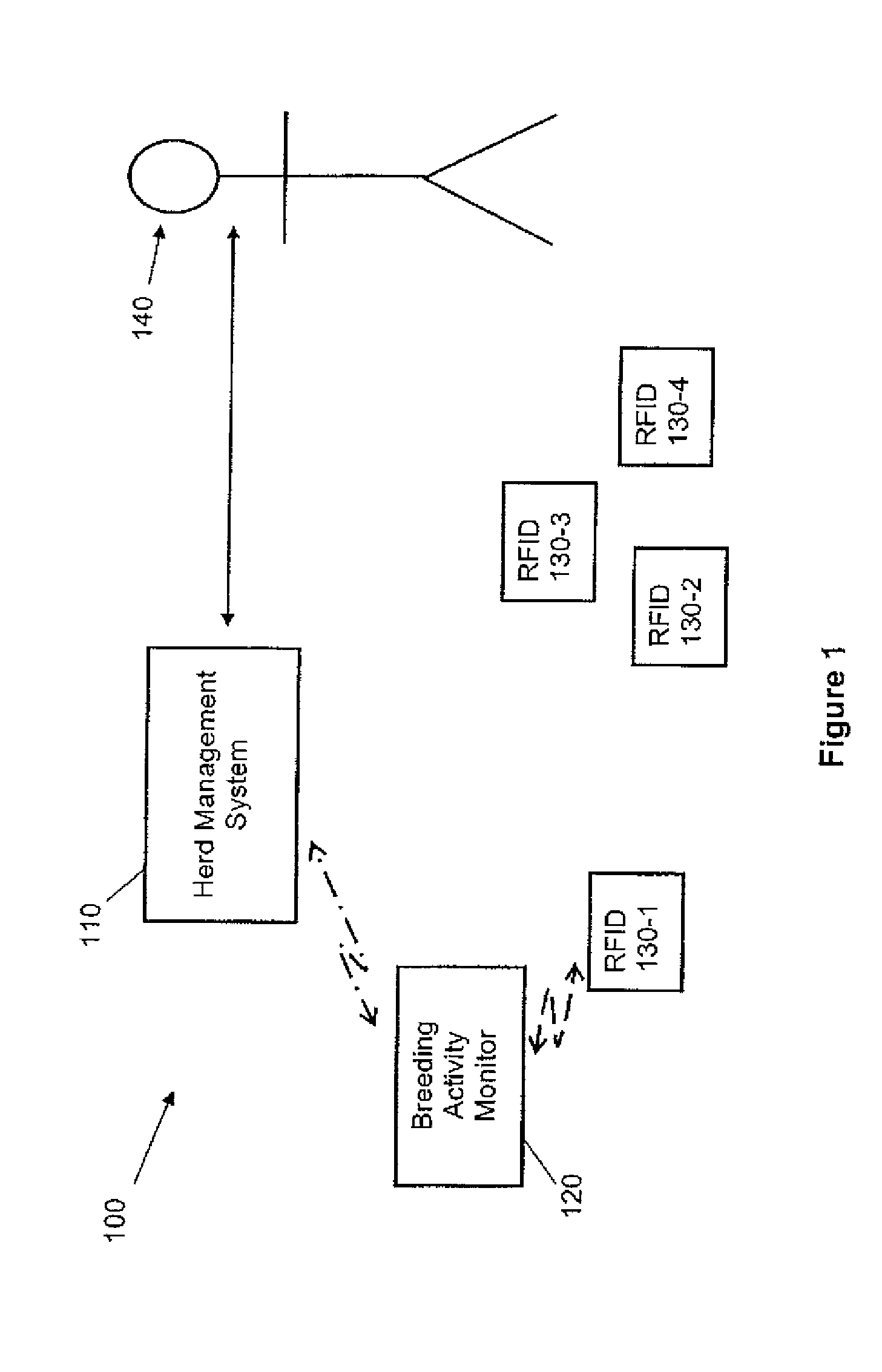
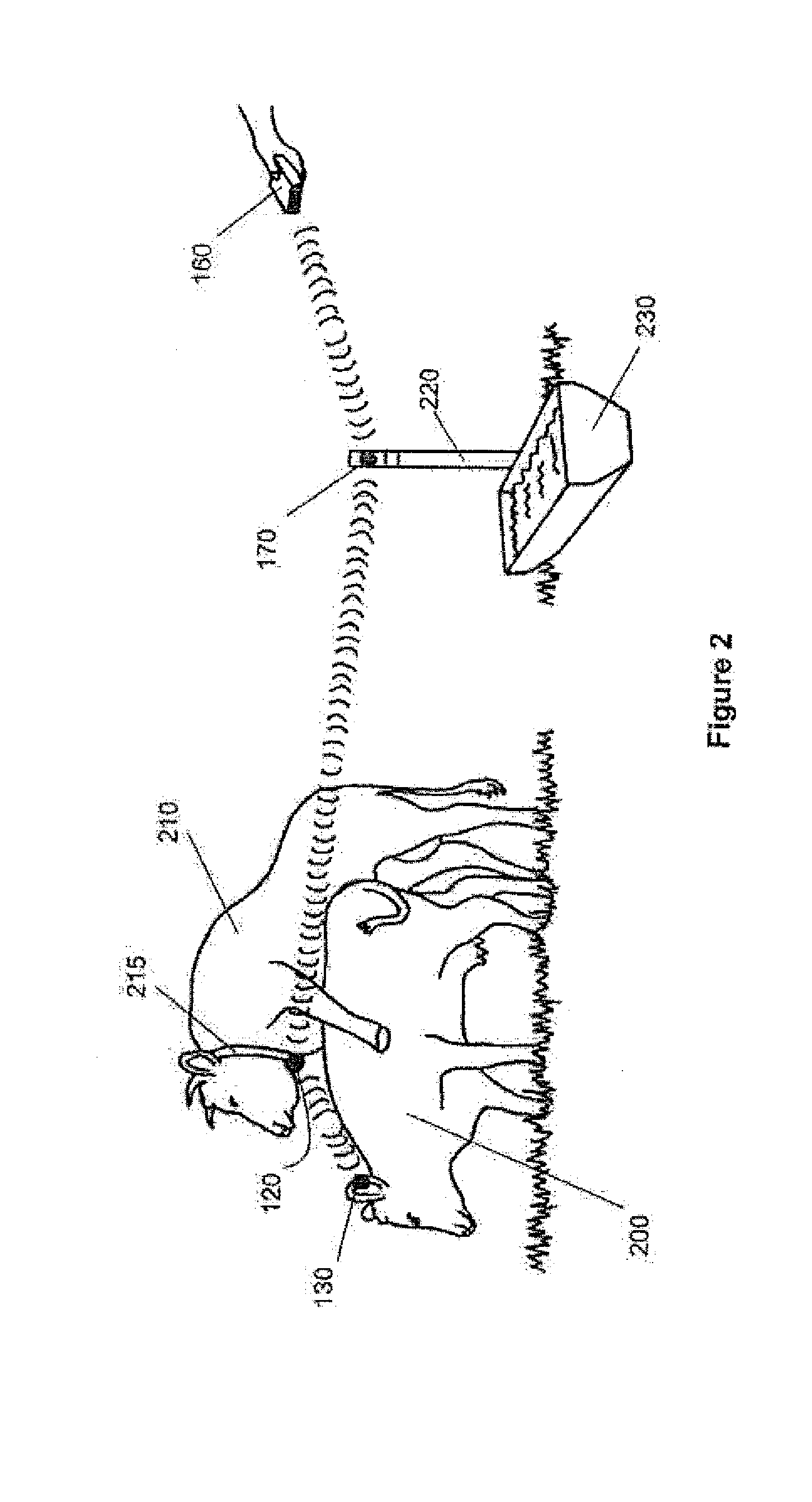
Livestock breeding and management system
A method and system for livestock breeding and management for use with a herd where each female animal carries a radio frequency identification (RFID) tag. The system comprises a herd management system and one or more breeding activity monitors to be carried by each male animal. Each breeding activity monitor is adapted to detect when the male animal is mounting a female animal based on the body position of the male animal, read identification data from the RFID tag carried by the mounted female animal, and generate breeding activity data including the identification data of the mounted female animal, mounting male animal and timing data for each mounting for output to the herd management system. The herd management system is adapted to process breeding activity data output from the breeding activity monitors to generate herd management data.
Owner:BREEDCARE
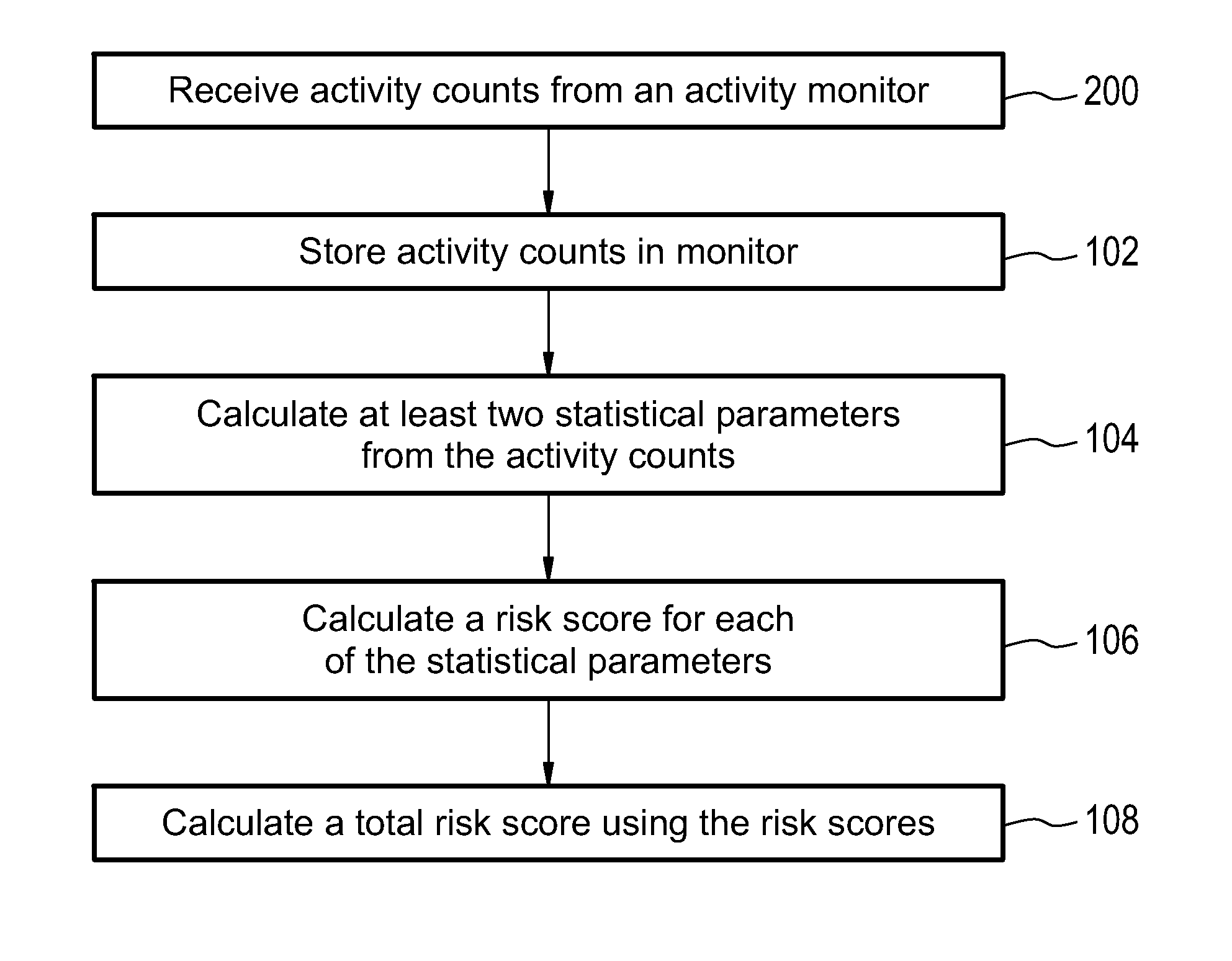
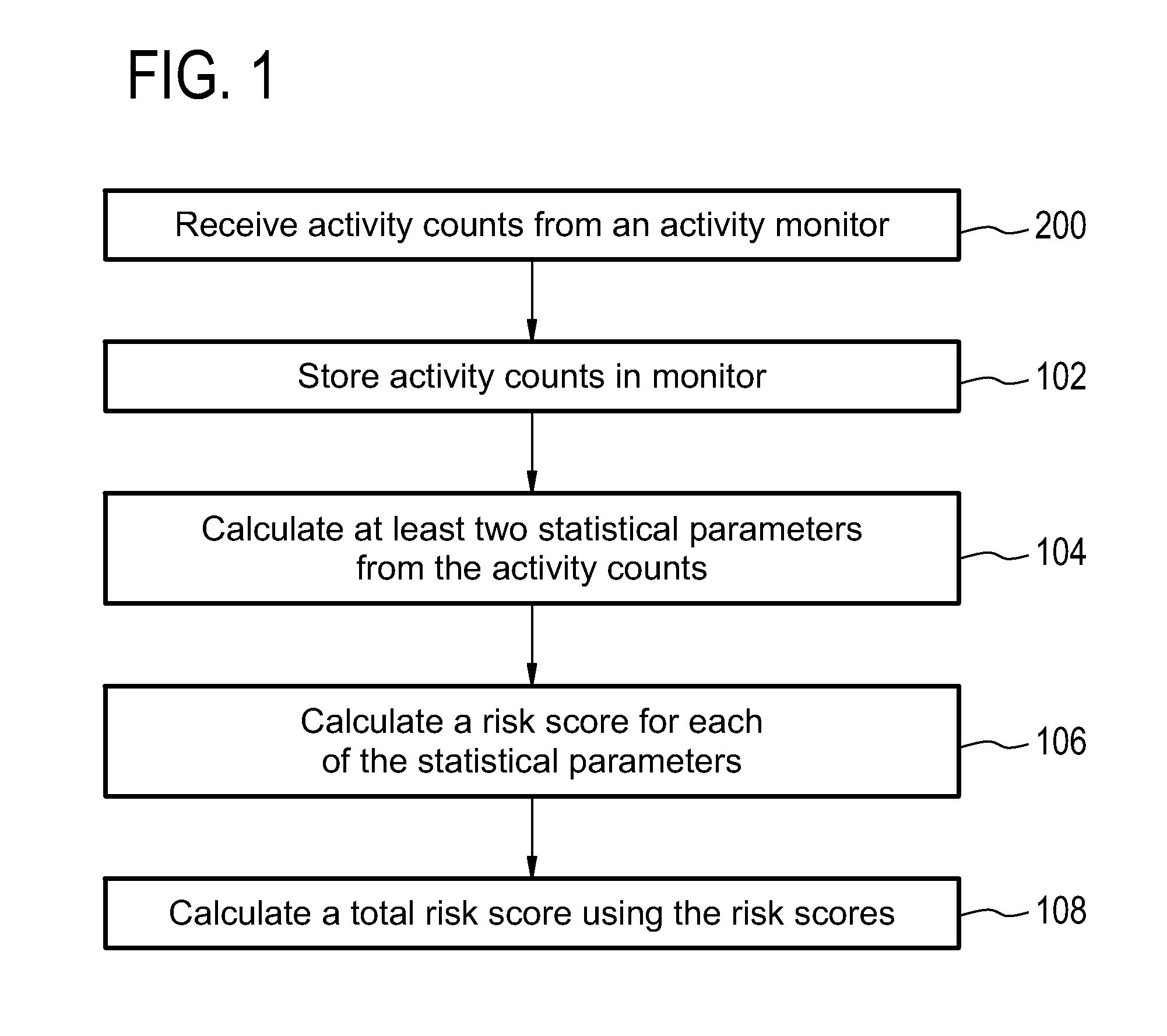
Health monitoring system for calculating a total risk score
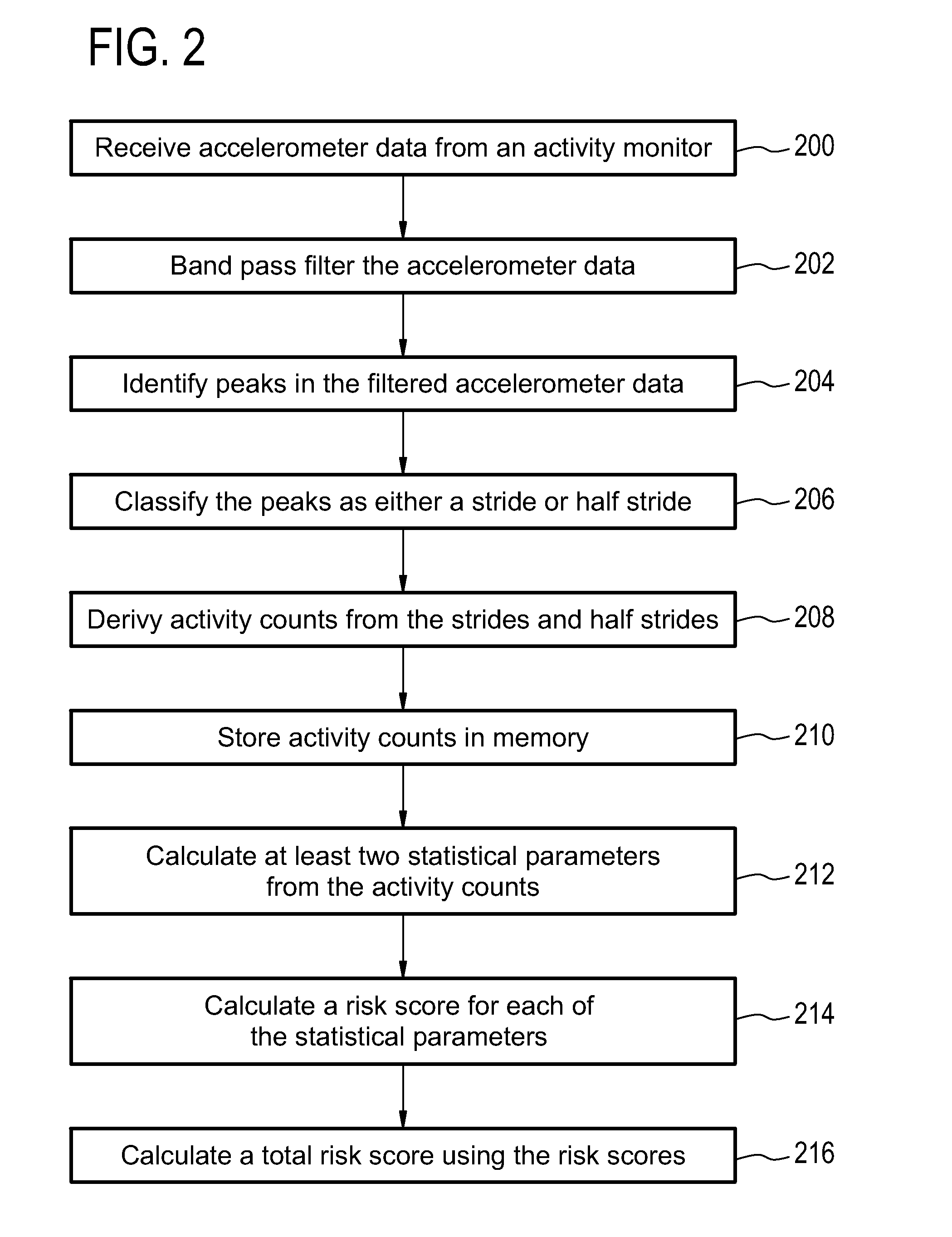
InactiveUS20150324541A1Avoid hospitalizationData processing applicationsHealth-index calculationTotal riskMonitoring system
Embodiments of the invention provide for a health monitoring system comprising an activity monitor. The health monitoring system further comprises a processor and a memory for storing machine readable instructions. The instructions cause the processor to derive activity counts from the activity data acquired by the activity monitor. The instructions further cause the processor to store the activity counts in the memory, and are associated with a time. The instructions further cause the processor to calculate at least two statistical parameters from the activity counts, wherein the at least two statistical parameters are descriptive of the activity counts as a function of time. The instructions further causes the processor to calculate a risk score for each of the at least two statistical parameters. The instructions further cause the processor to calculate a total risk score using the risk score for each of the at least two statistical parameters.
Owner:KONINKLJIJKE PHILIPS NV
System and method for estimating cardiovascular fitness of a person
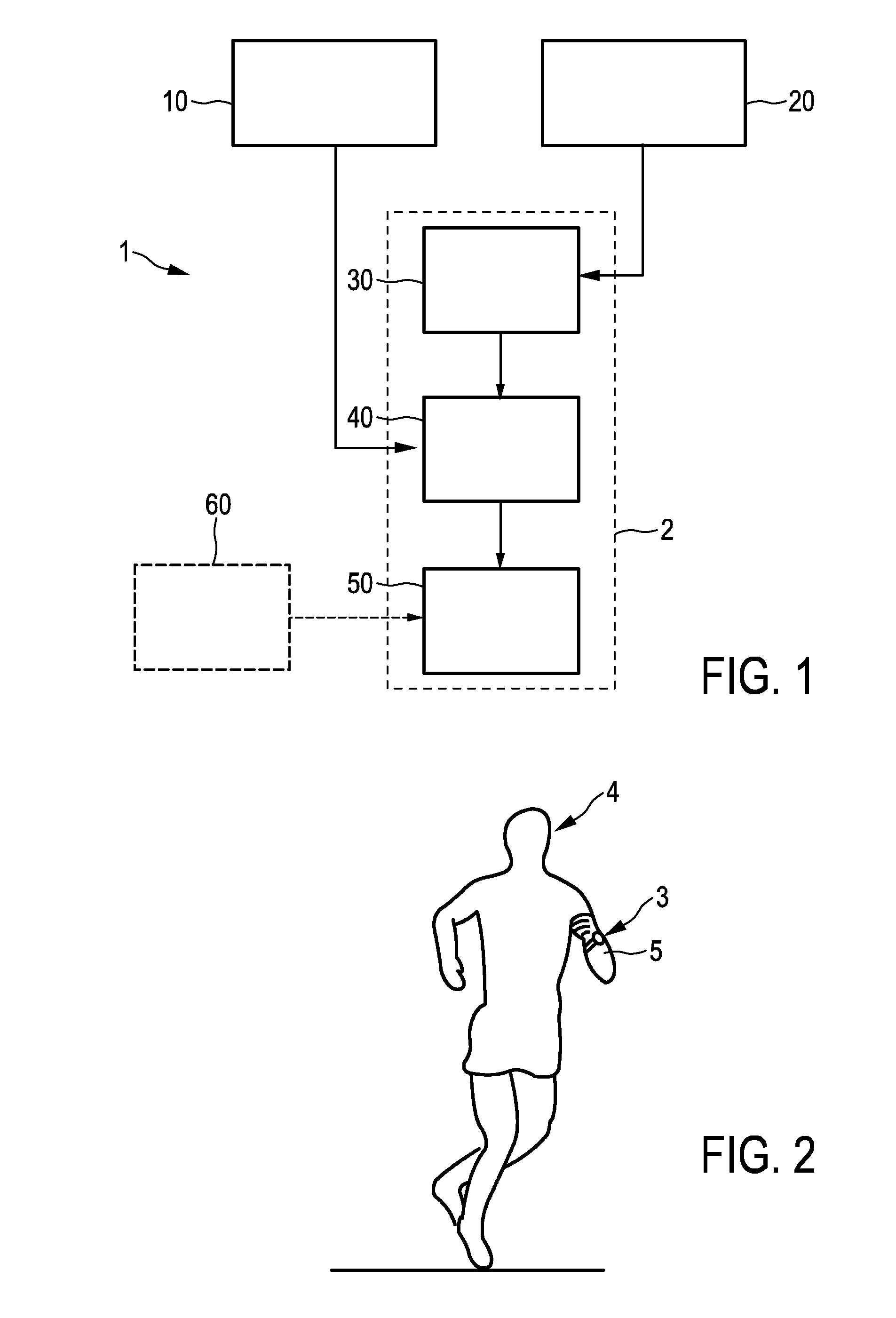
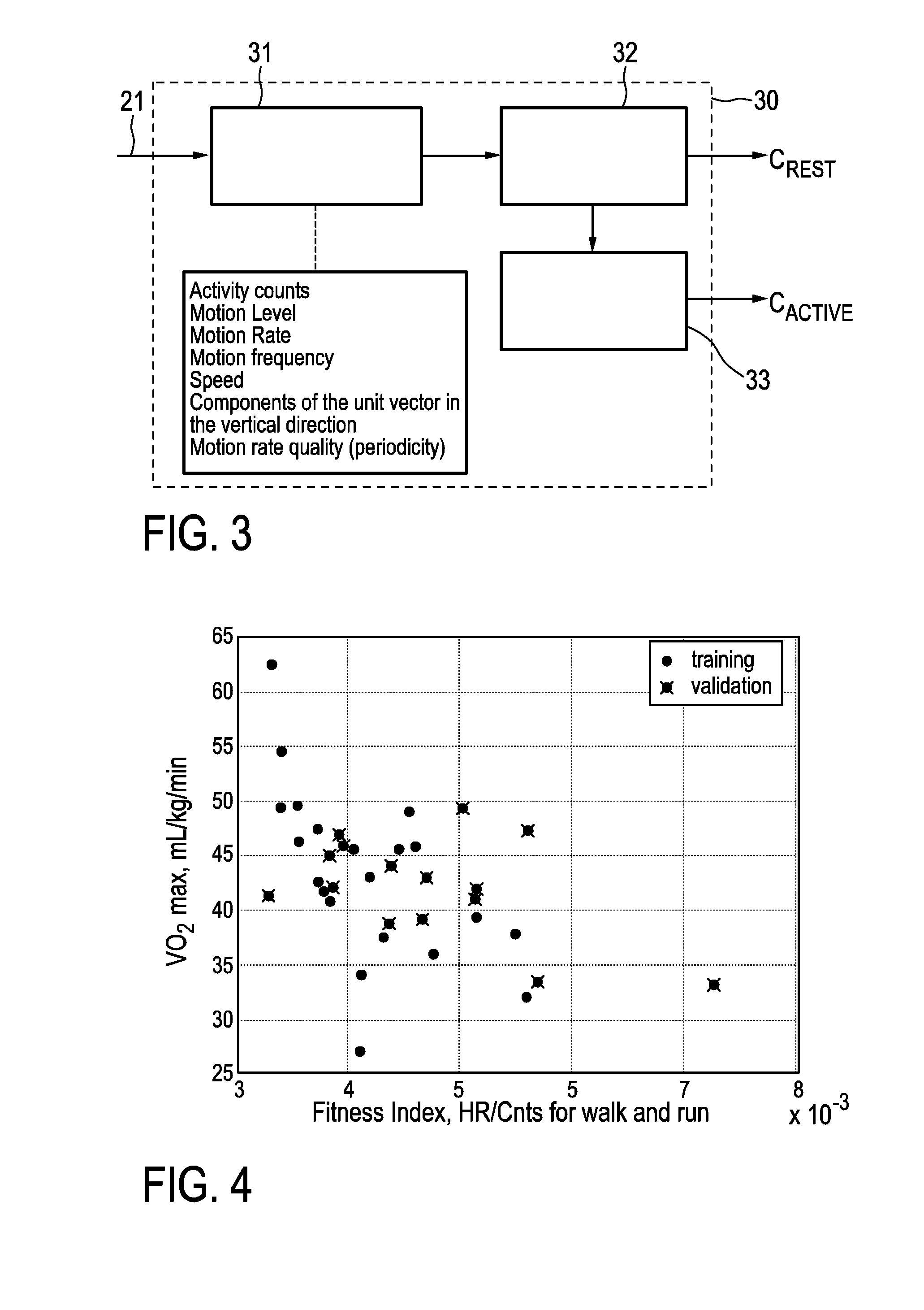
ActiveUS20160206248A1Reliably assess his cardiovascular fitnessAccurate estimateInertial sensorsMedical automated diagnosisActivity monitorPulse rate
The present invention relates to a system (1) for estimating cardiovascular fitness of a person, comprising a heart rate monitor (10) for acquiring a heart rate signal including information about the heart rate of the person, an activity monitor (20) for acquiring an activity signal indicative of physical activity of the person, a classifier (30) for classifying the activity of the person based on the acquired activity signal, a selector (40) for selecting one or more heart rate features obtained from the acquired heart rate signal based on the acquired heart rate signal and the classification of the activity for use in an estimation of the cardiovascular fitness of the person, and an estimator (50) for estimating the cardiovascular fitness of the person based on the one or more selected heart rate features.
Owner:KONINKLJIJKE PHILIPS NV
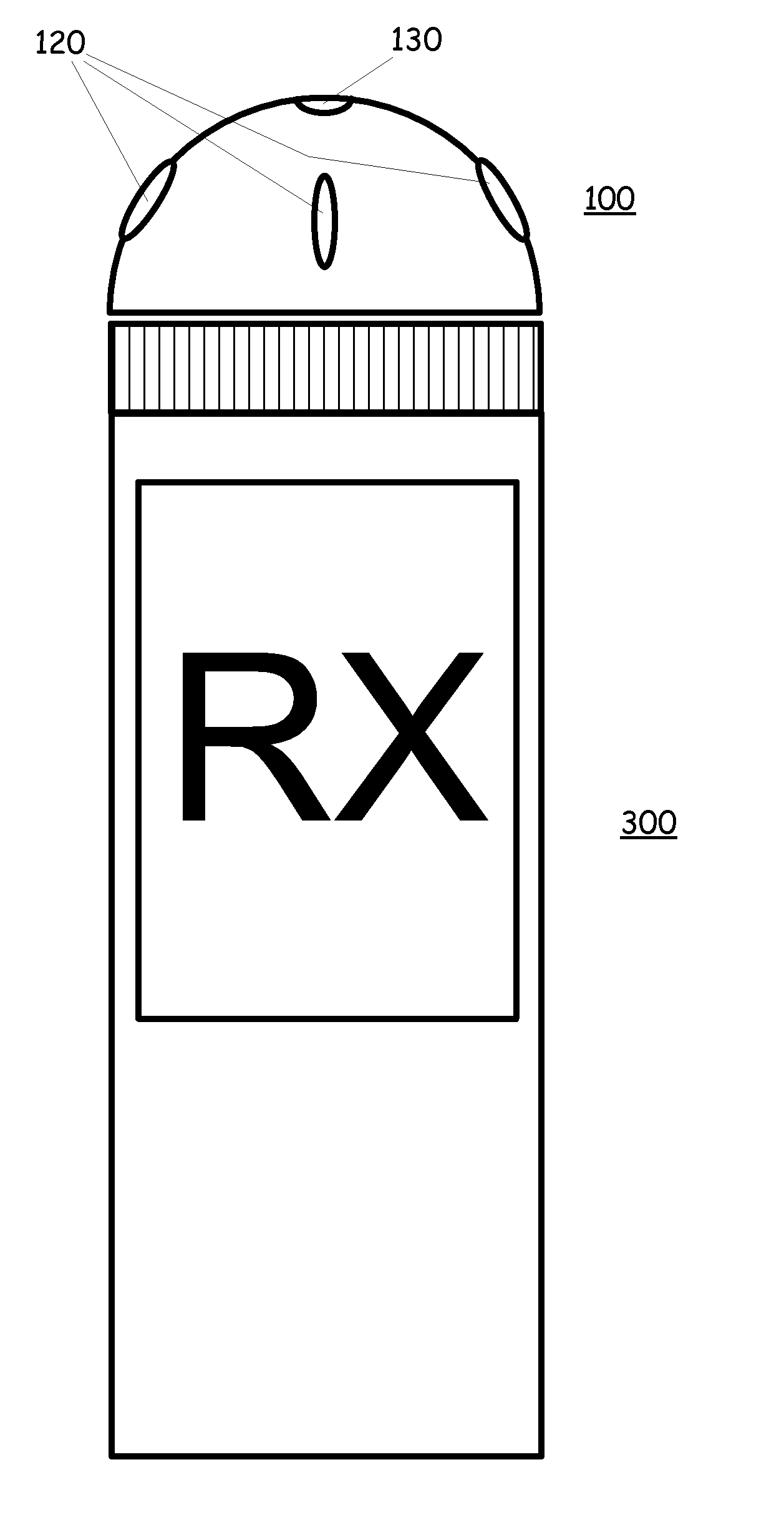
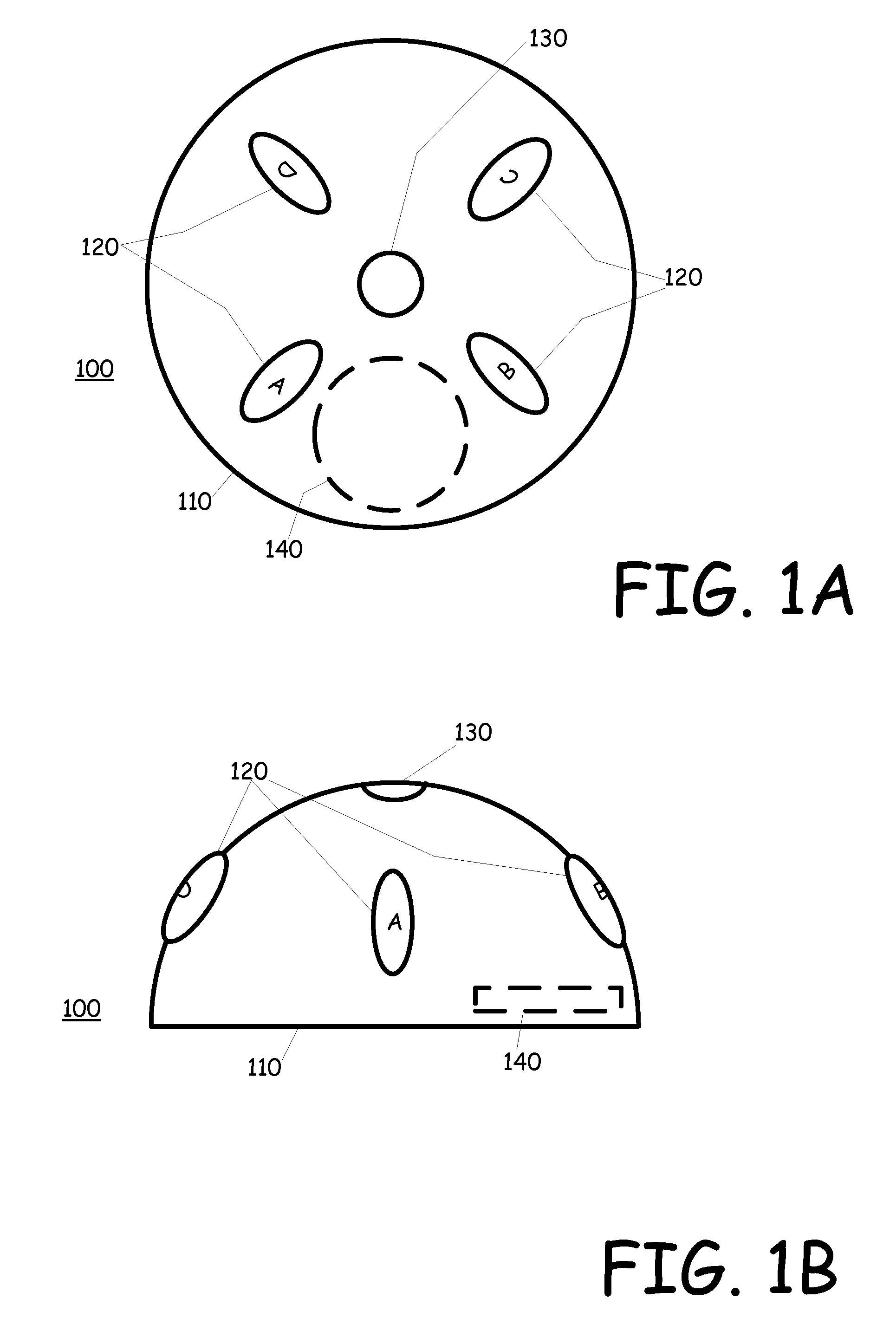
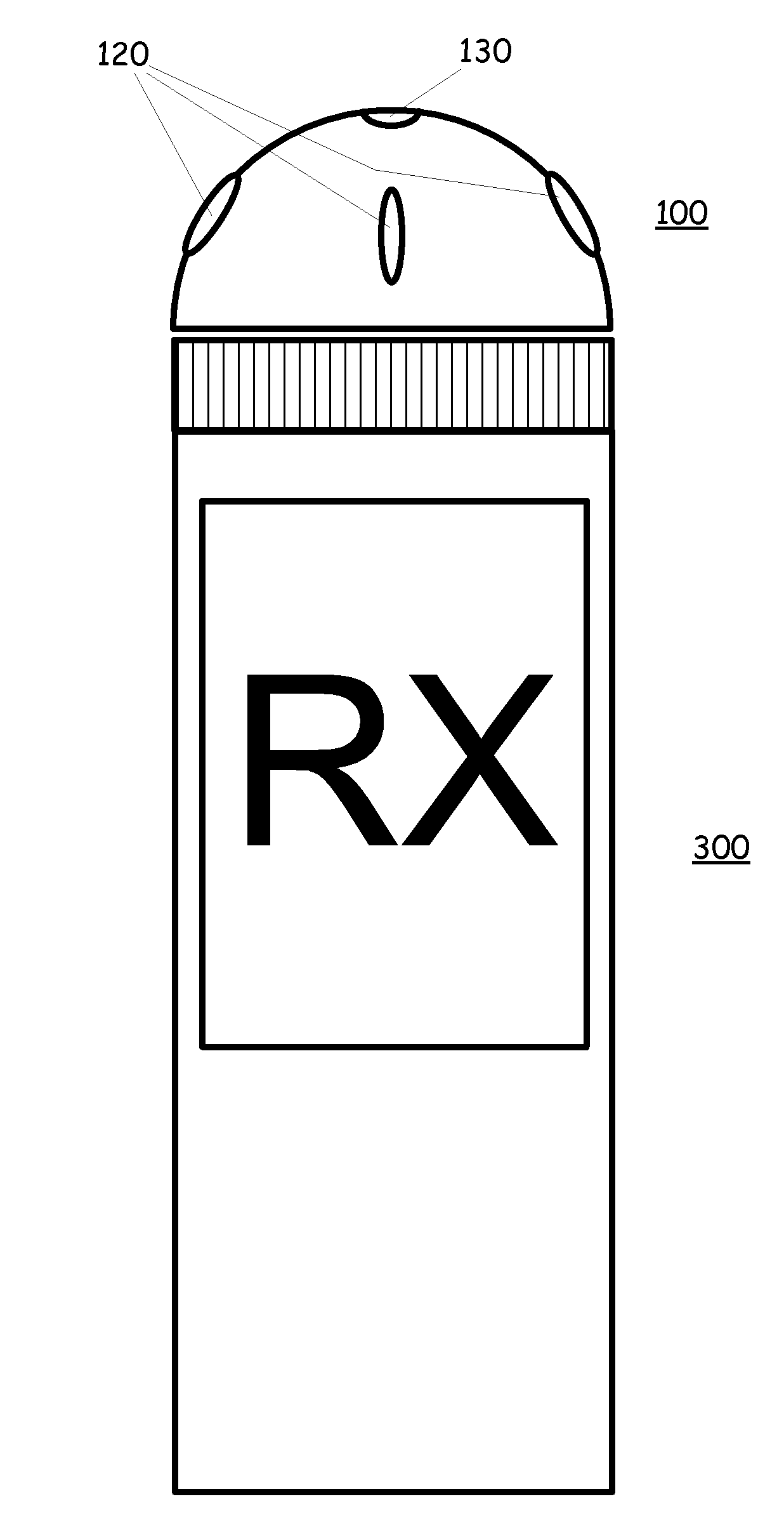
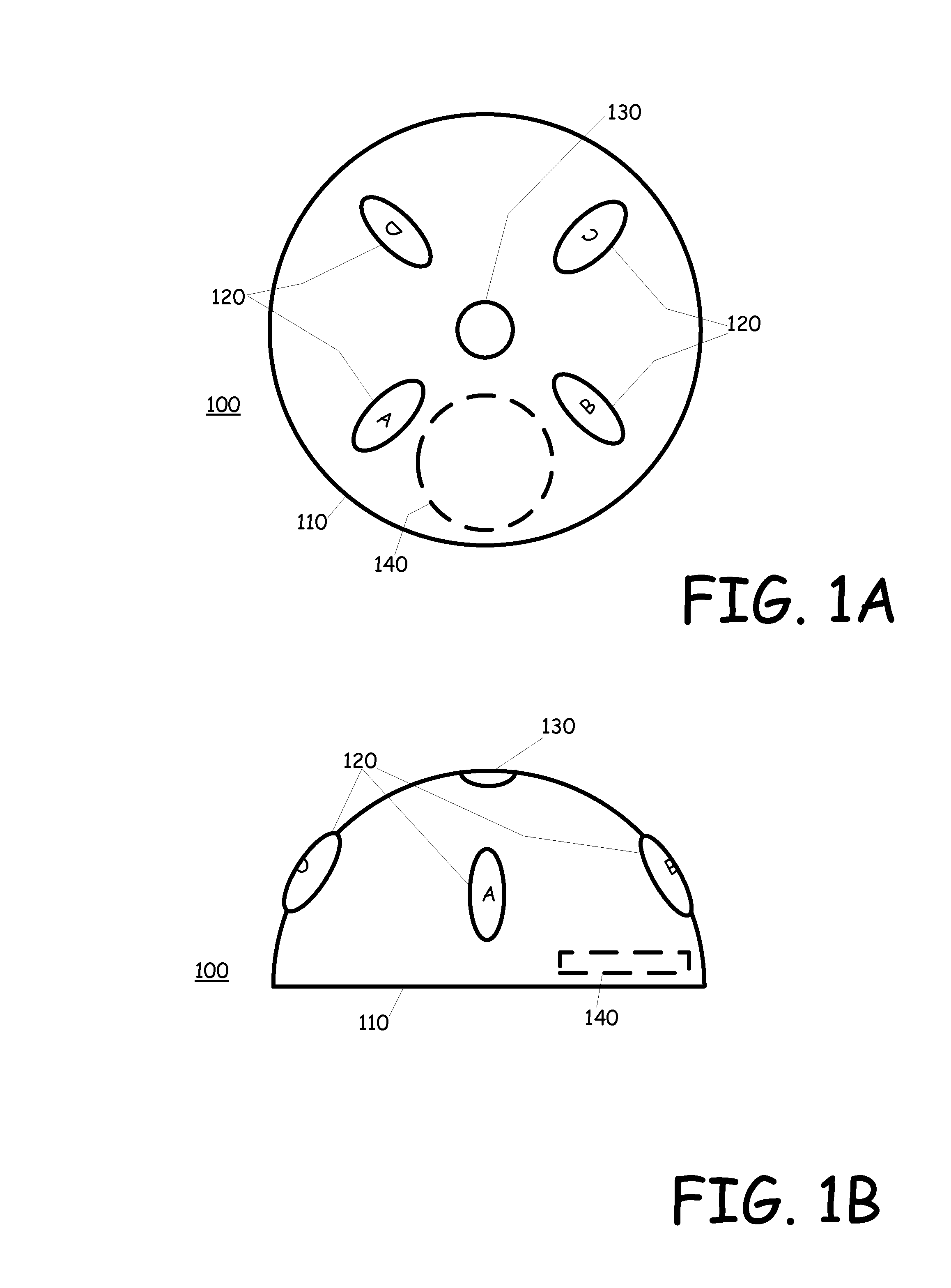
Activity monitor to alleviate controlled substance abuse
ActiveUS8284068B2Drug and medicationsDiagnostic recording/measuringSubstance abuserControl substances
An activity monitor which can be pre-programmed at the factory, the doctors office or the pharmacist, or that can be programmed by the user. The activity monitor is affixed to a medicine bottle or container and activity associated with the bottle or container, such as movement, opening, volume changes, etc. are monitored in view to the schedule. The activity monitor records and allows for the analysis of the recorded data to determine is there is a likelihood of substance abuse.
Owner:JOHNSON SAM
Method and system for providing wireless vulnerability management for local area computer networks
InactiveUS20120185390A1Customization processReduce overheadDigital data processing detailsUser identity/authority verificationVulnerability managementComputer network
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:AIRTIGHT NETWORKS
Motion or opening detector
An activity monitor which can be pre-programmed at the factory, the doctors office or the pharmacist, or that can be programmed by the user. The activity monitor is affixed to a medicine bottle or container and activity associated with the bottle or container, such as movement, opening, volume changes, etc. are monitored in view to the schedule. If the schedule indicates that a dose of medicine should be taken at a particular time, but the monitored activity does not determine that the medicine has been taken, an alert signal will be issued to alert the user that it is time to take the medicine. In addition, if the monitored activity indicates that the medicine bottle has been opened prior to a scheduled time, then a tamper alert can be triggered.
Owner:JOHNSON SAM
Method and system for providing wireless vulnerability management for local area computer networks
InactiveUS20090119741A1Reduce overheadEasy to customizeFinanceComputer security arrangementsVulnerability managementService provision
A Software-as-a-Service (SaaS) based method for providing wireless vulnerability management for local area computer networks. The method includes providing a security server being hosted by a service provider entity to provide analysis of data associated with wireless vulnerability management for a plurality of local area computer networks of a plurality of customer entities, respectively. The method includes creating a workspace for wireless vulnerability management for a customer entity on the security server and receiving configuration information associated with the workspace. The method also includes supplying one or more sniffers to the customer entity. The method includes receiving at the security server information associated with wireless activity monitored by the one or more sniffers at premises of the customer entity and processing the received information within the workspace for the customer entity using the security server. The method includes metering usage of the workspace for wireless vulnerability management for the customer entity.
Owner:AIRTIGHT NETWORKS
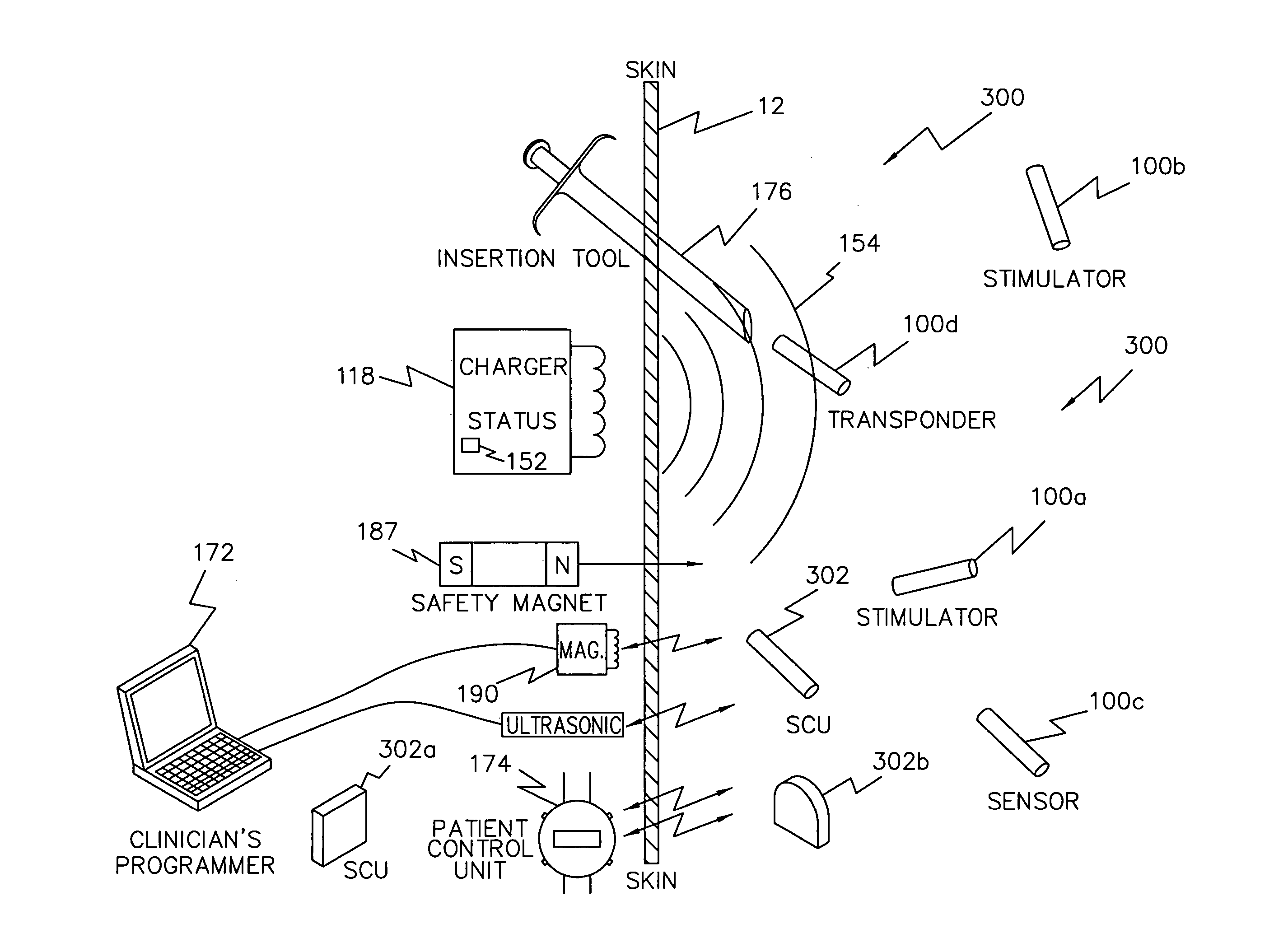
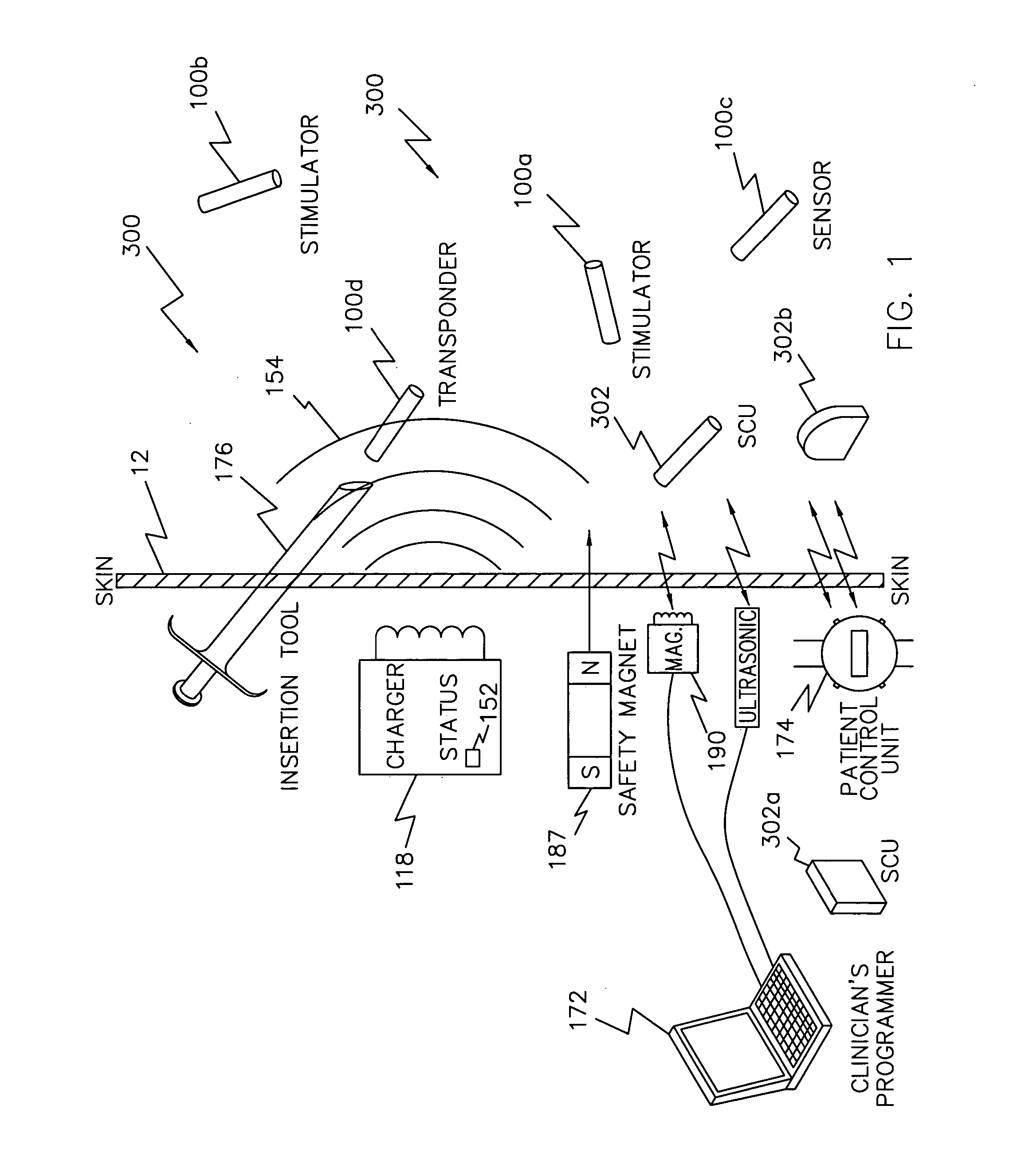
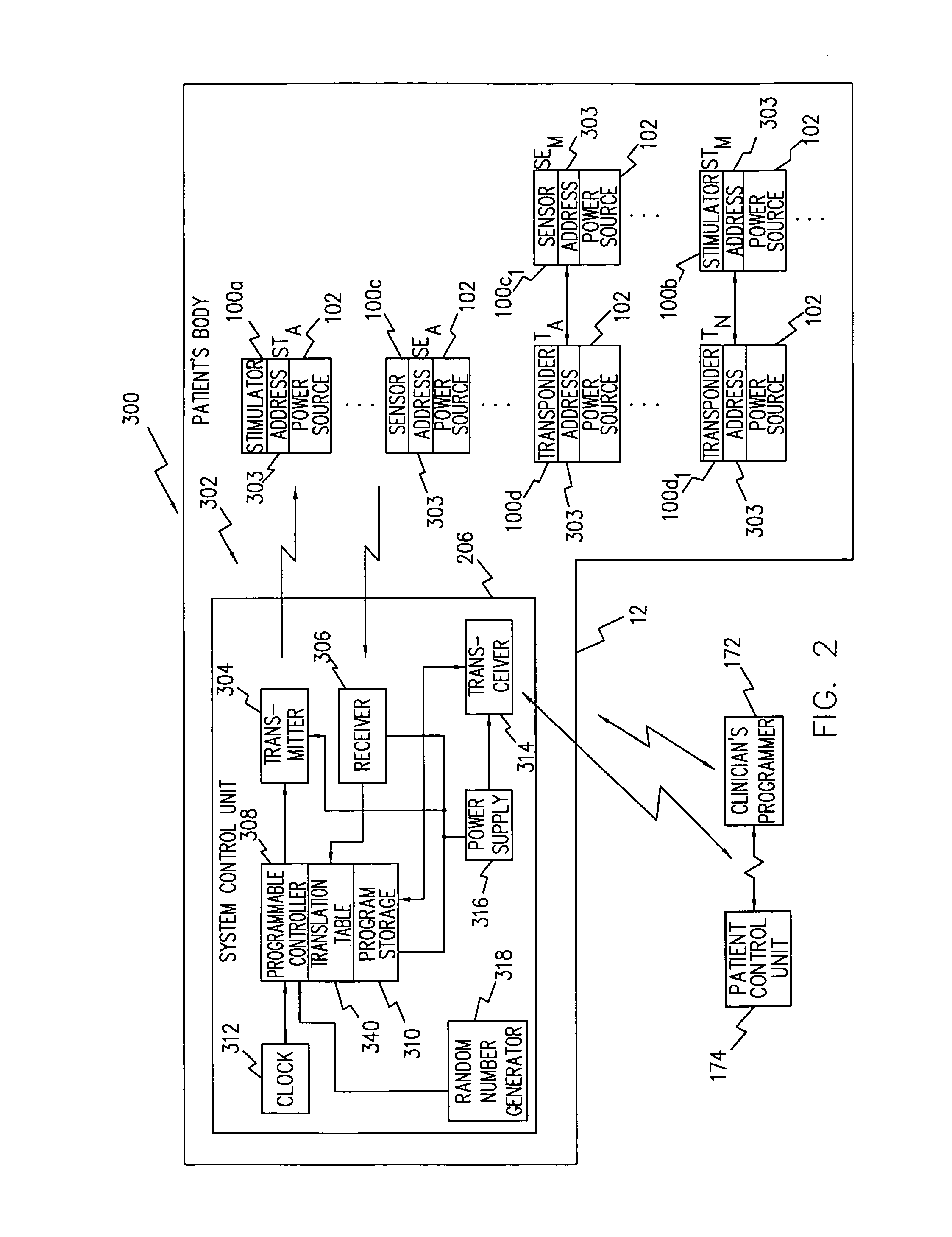
Neuromuscular stimulation to avoid pulmonary embolisms
ActiveUS20060122663A1Avoid it happening againPerson identificationImplantable neurostimulatorsAccelerometerMedicine
A system and method that provide a prophylactic treatment to a person, e.g., a patient, to avoid the occurrence of pulmonary embolisms by the system providing neuromuscular stimulation to a person's lower extremities, e.g., the person's legs, when the system senses that a person has been immobile for an extended period of time. An implantable neuromuscular pacer, such as that described in U.S. Pat. Nos. 5,193,539; 5,193,540; 6,164,284; 6,185,452; 6,208,894; 6,315,721; 6,564,807; and their progeny, may be used to provide to selectively provide such stimulation. Preferably, such a device may be battery powered so that it can operate independent of an external apparatus. In particular, systems and devices of the present invention preferably additionally include an activity monitor, e.g., an accelerometer or the like, that disables or limits stimulation to pronged time periods in which there is limited activity.
Owner:ALFRED E MANN FOUND FOR SCI RES
Active learning device and method
ActiveUS8123527B2Easy to learnPromote growthPhysical therapies and activitiesCosmonautic condition simulationsVirtual userActivity monitor
Owner:NEWGENT
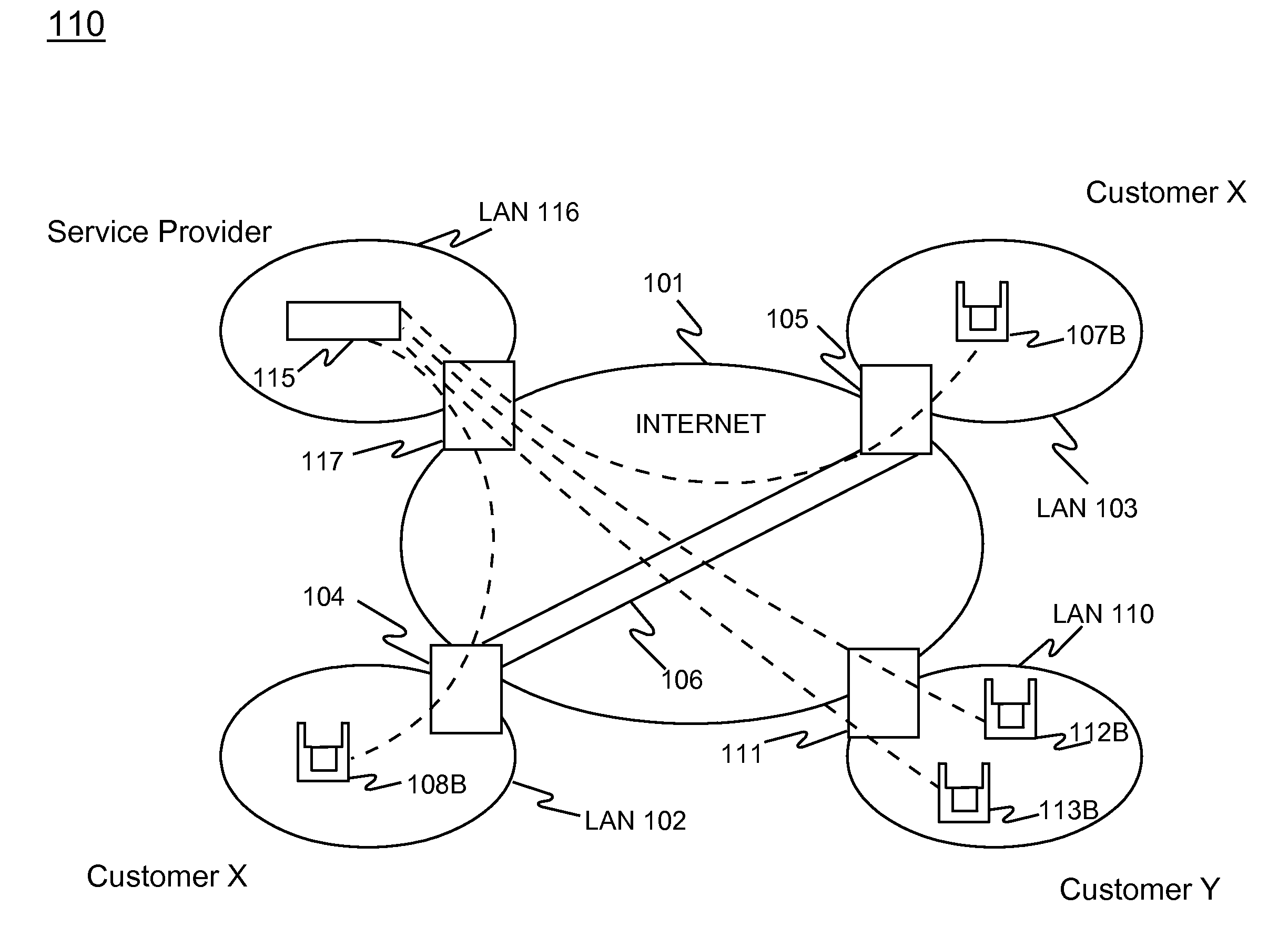
Supervised Access Computer Network Router
InactiveUS20100325259A1Good effectError detection/correctionMultiple digital computer combinationsComputer usageNetwork communication
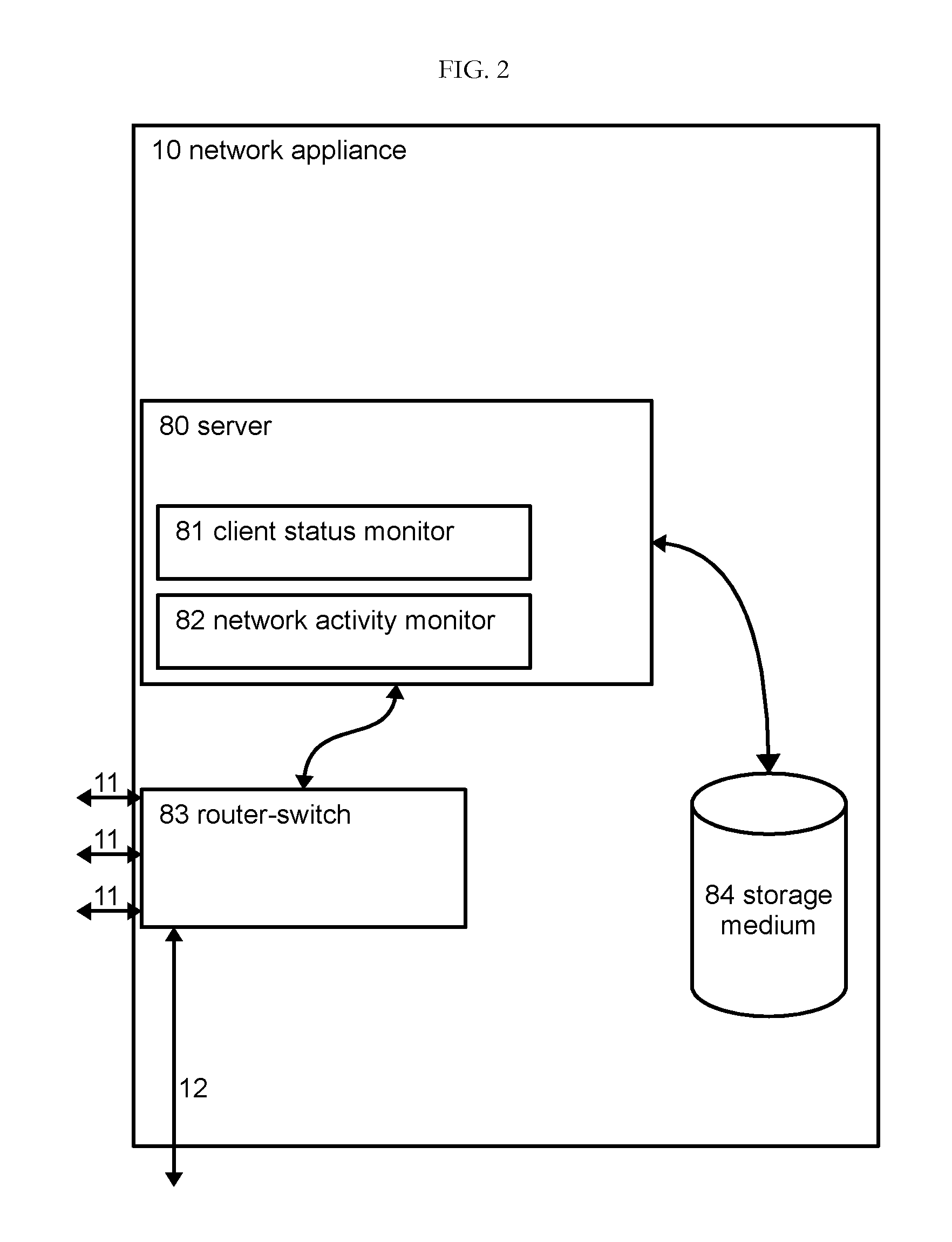
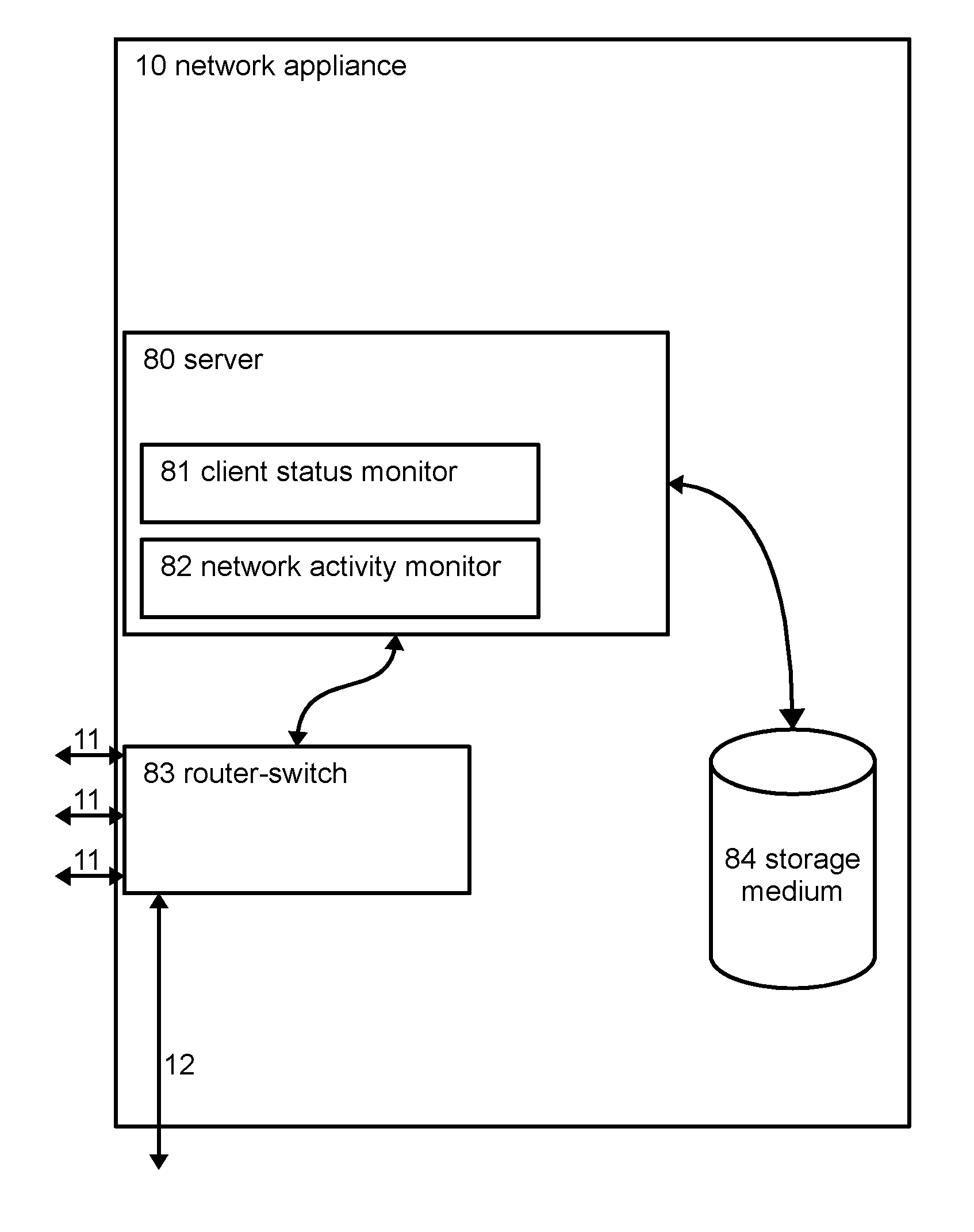
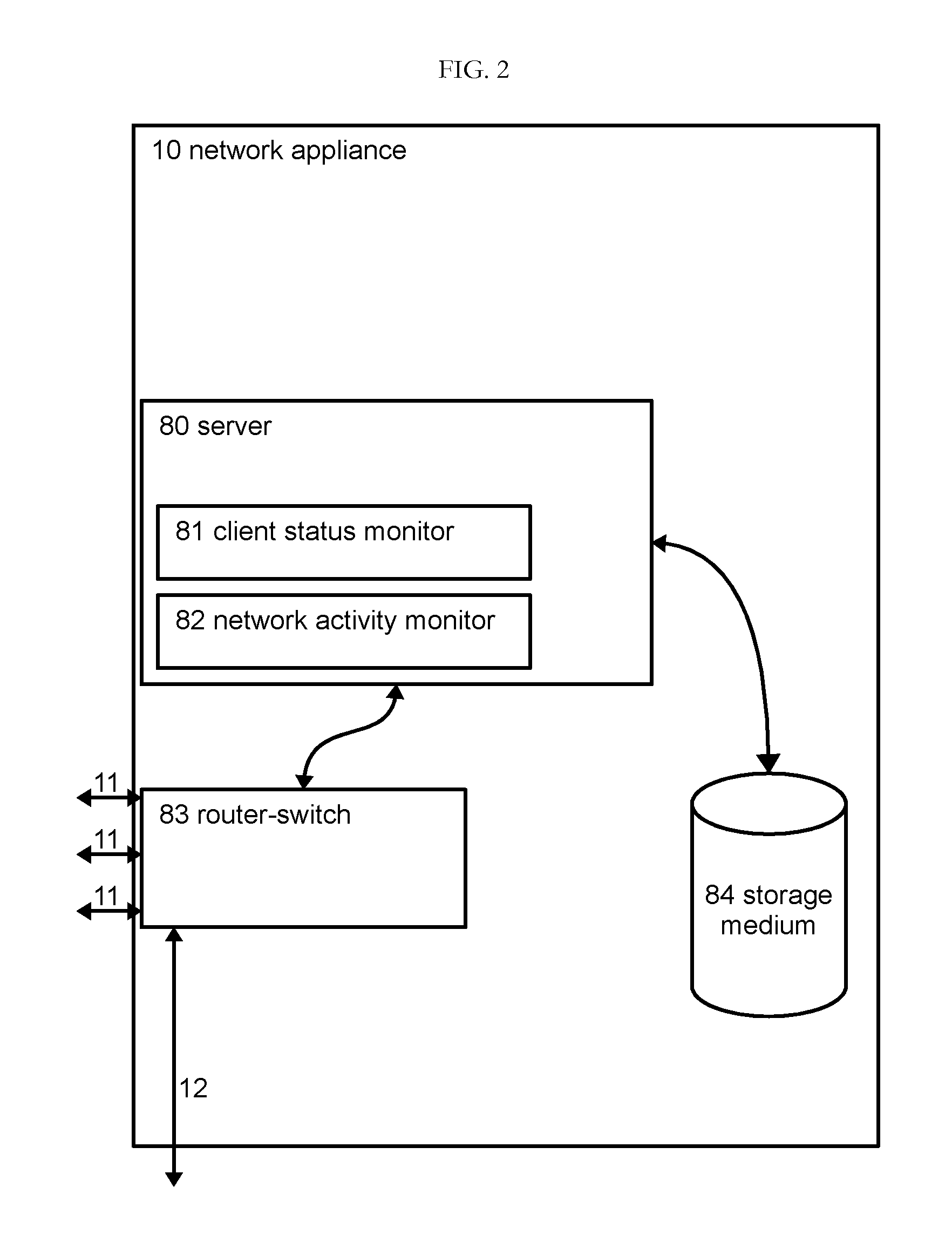
A system for monitoring and regulating computer usage on a local network is disclosed. Computers on a network are configured with a client activity monitoring module that collects activity information including screen captures, keyboard activity, and / or information relating to network communications and sends the collected activity information to a network activity monitor for storage and later retrieval. Each computer on the local network periodically verifies that its client activity monitor module is operable. If a computer fails to send such verification, the system restricts network access by that computer, thus enforcing compliance with the activity monitoring system. The system further provides means for automatically displaying the collected activity information, including through screen savers, automatically changing desktop background images, and pop-up or sidebar windows. The system thus enables review of computer activities for appropriateness by both supervisors or parents as well as by peer users without requiring the reviewer to take affirmative steps to retrieve the activity information.
Owner:VOLONICS CORP
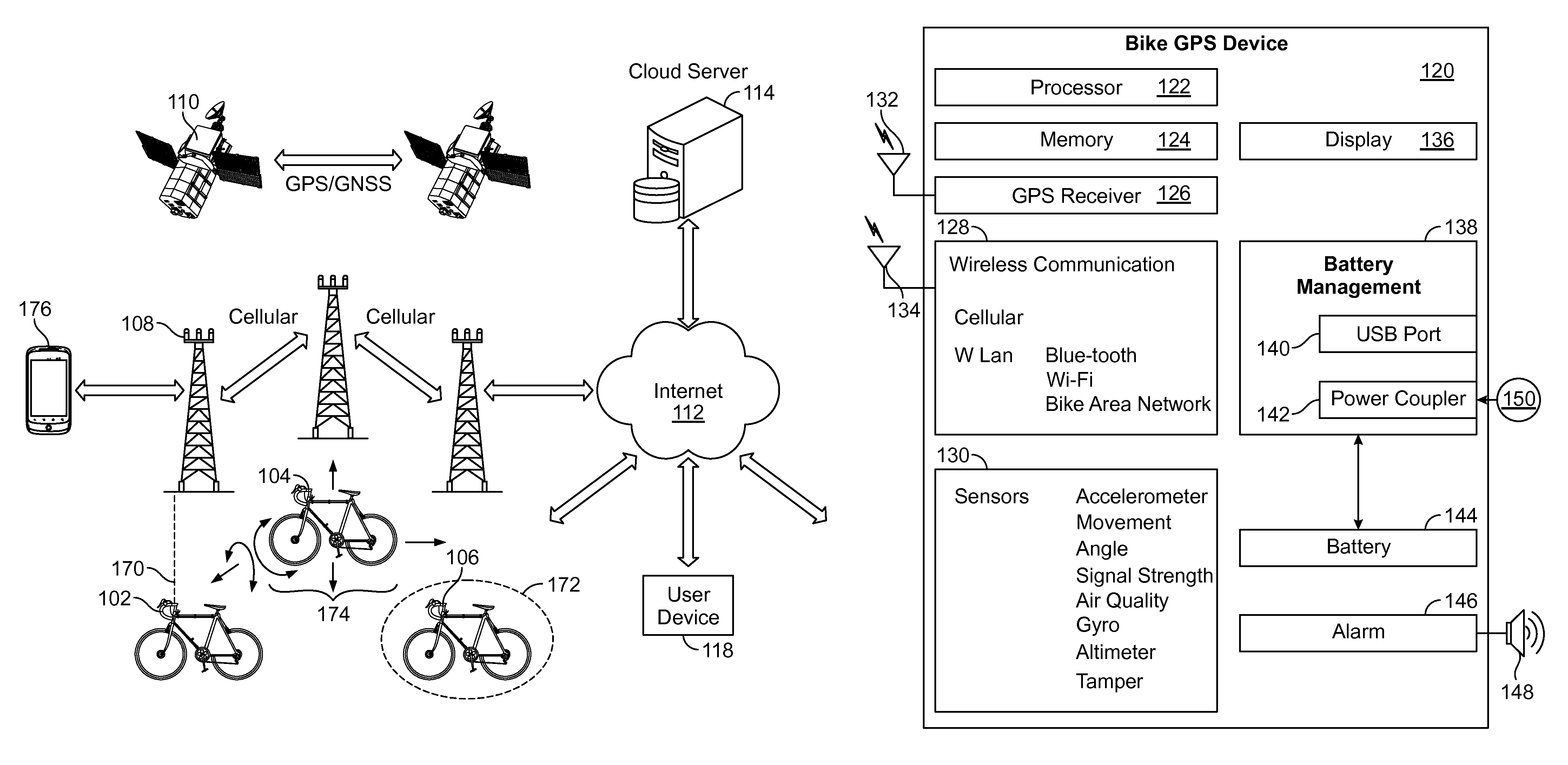
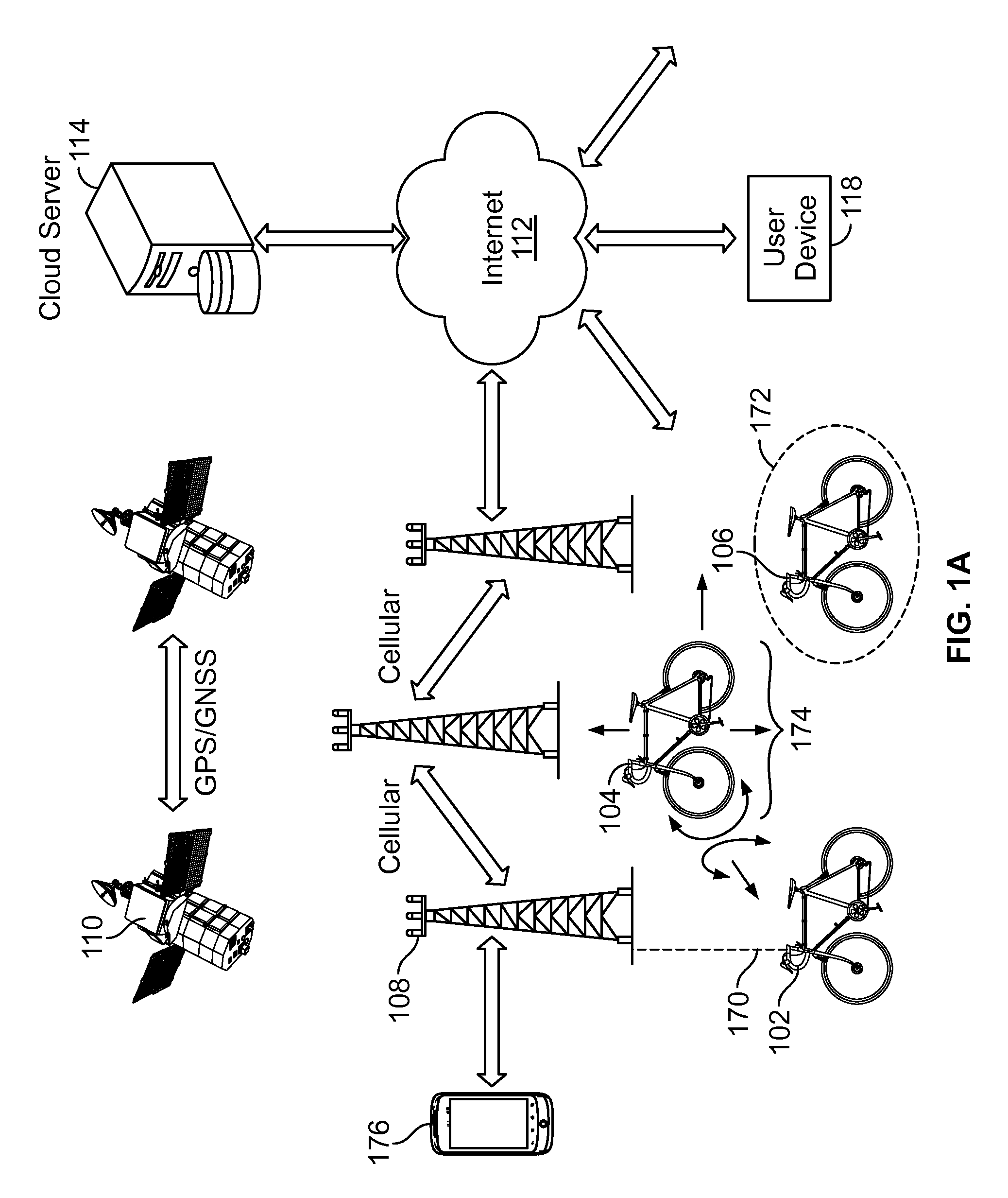
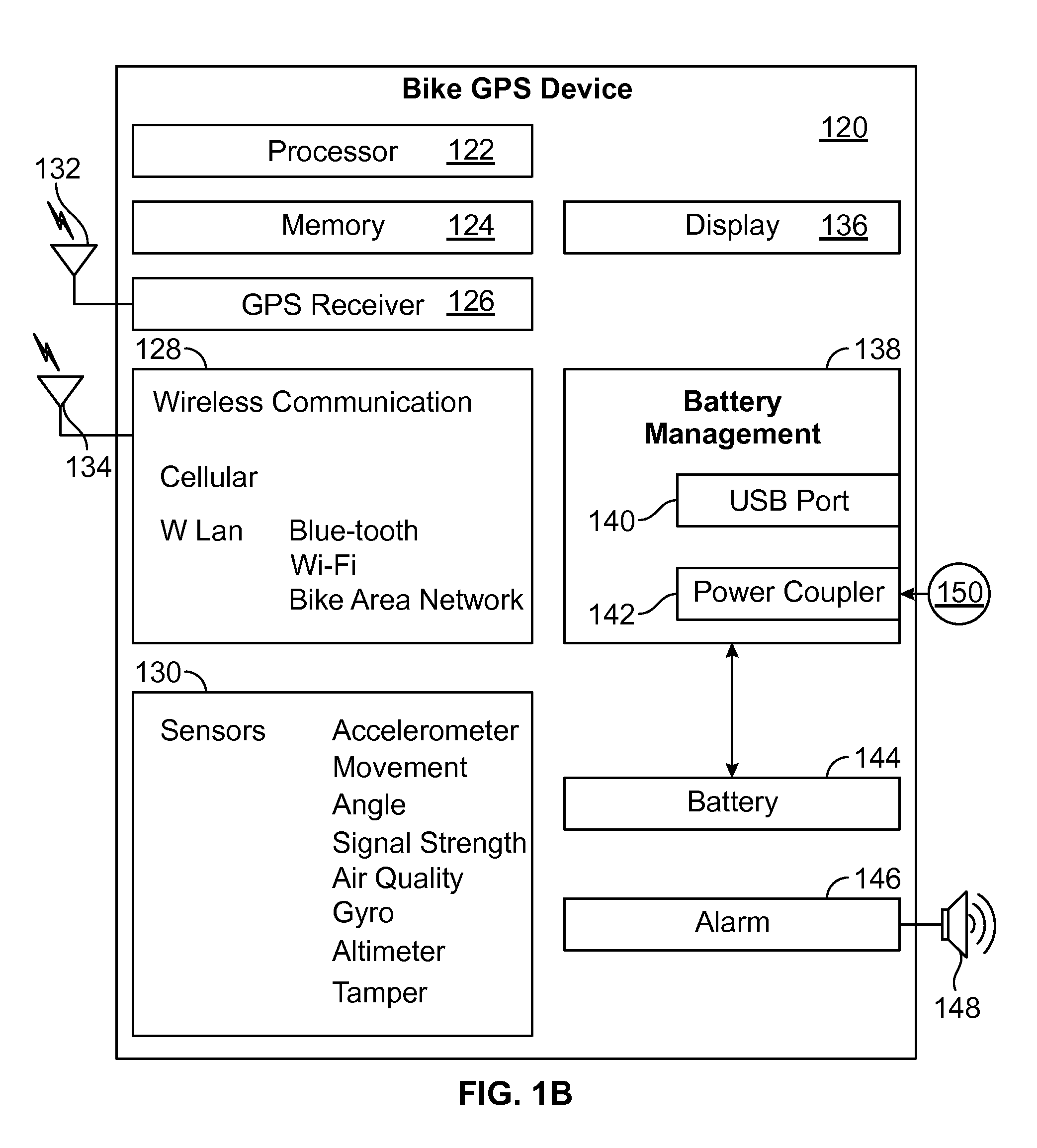
Cloud based activity monitor for bicycles and application
A method for obtaining data and communicating with a bicycle mounted cloud based activity monitor is provided. The method includes accepting into a server a plurality of sensor data and GPS location coordinates from a device attached to a bicycle, wherein the activity monitor communicates data to the cloud server via a wireless coupling. The method further includes writing information relating to sensor, GPS, and alarm functions from the cloud based server into the bike mounted activity tracker via a wireless link.
Owner:WI MM
Apparatus, system, and method for gathering trace data indicative of resource activity
InactiveUS7661135B2Memory loss protectionError detection/correctionComputerized systemReal-time computing
An apparatus, system, and method are provided for gathering trace data indicative of resource activity on a computer system. The present invention includes a monitoring module that initiates one or more activity monitors on a target computer system to detect different types of resource activity. A determination module determines activity indicators involving resources of the target computer system using the one or more activity monitors. The activity indicators may comprise a variety of information useful in identifying one or more separate resource activities. A collection module organizes the activity indicators into trace data representative of the resource activity. Preferably, the monitoring module, determination module, and collection module operate continuously on the target computer system. In this manner, the trace data includes an accurate set of both current activity indicators as well as historical activity indicators.
Owner:IBM CORP
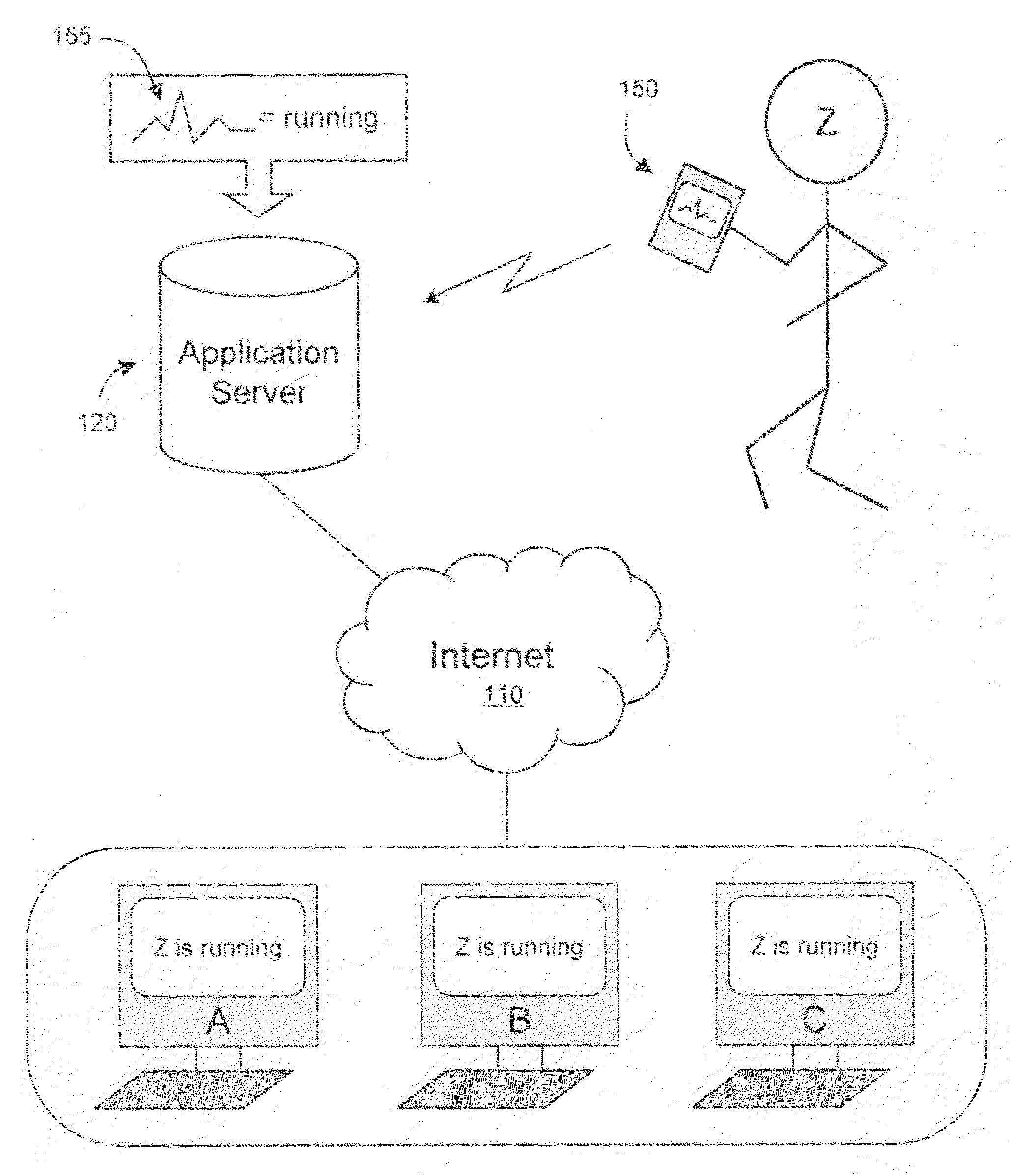
Motion or opening detector
ActiveUS20110012742A1Provide activityBurglar alarm by openingSignalling system detailsMedicineActivity monitor
An activity monitor which can be pre-programmed at the factory, the doctors office or the pharmacist, or that can be programmed by the user. The activity monitor is affixed to a medicine bottle or container and activity associated with the bottle or container, such as movement, opening, volume changes, etc. are monitored in view to the schedule. If the schedule indicates that a dose of medicine should be taken at a particular time, but the monitored activity does not determine that the medicine has been taken, an alert signal will be issued to alert the user that it is time to take the medicine. In addition, if the monitored activity indicates that the medicine bottle has been opened prior to a scheduled time, then a tamper alert can be triggered.
Owner:JOHNSON SAM
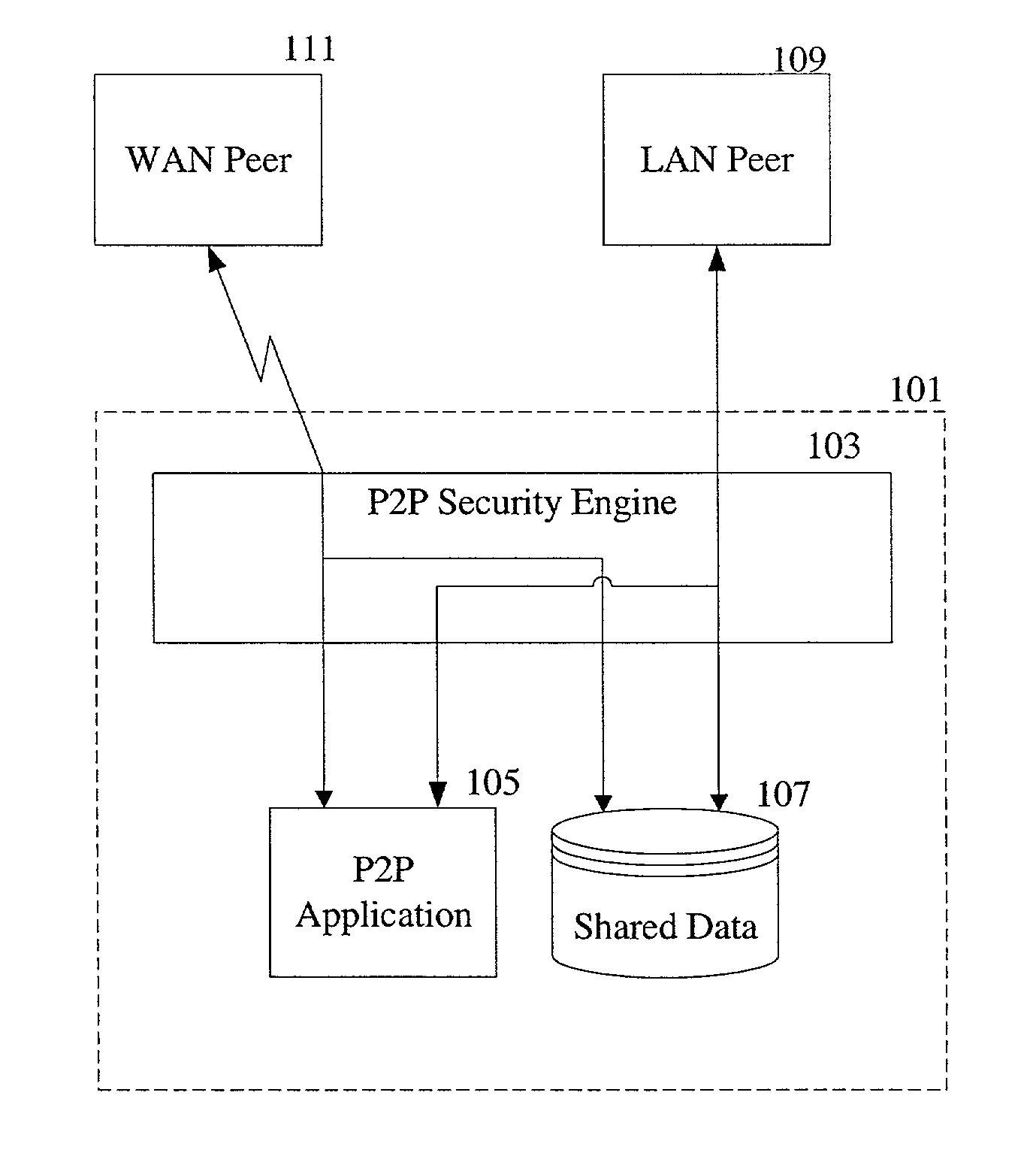
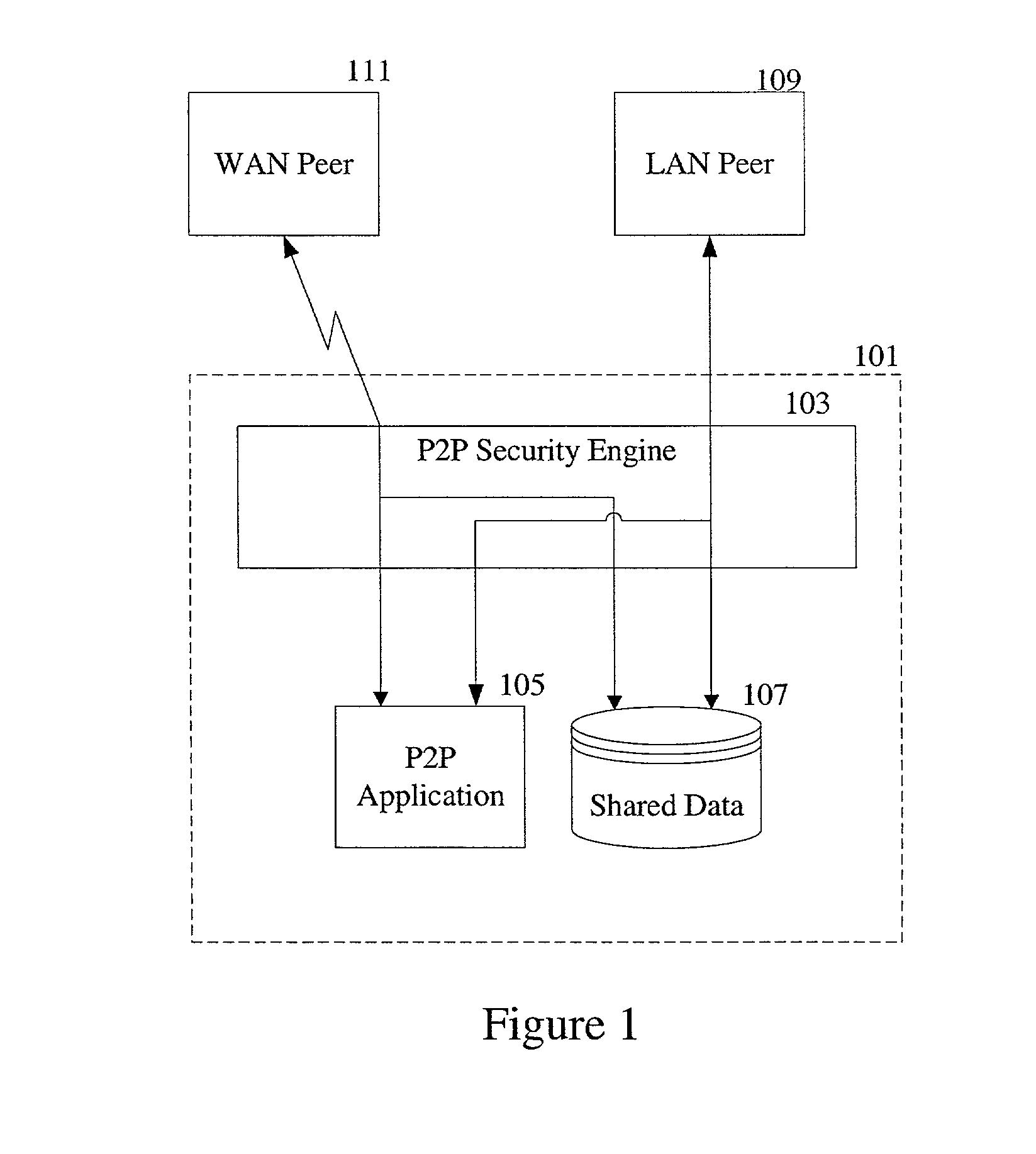
Desktop security in peer-to-peer networks
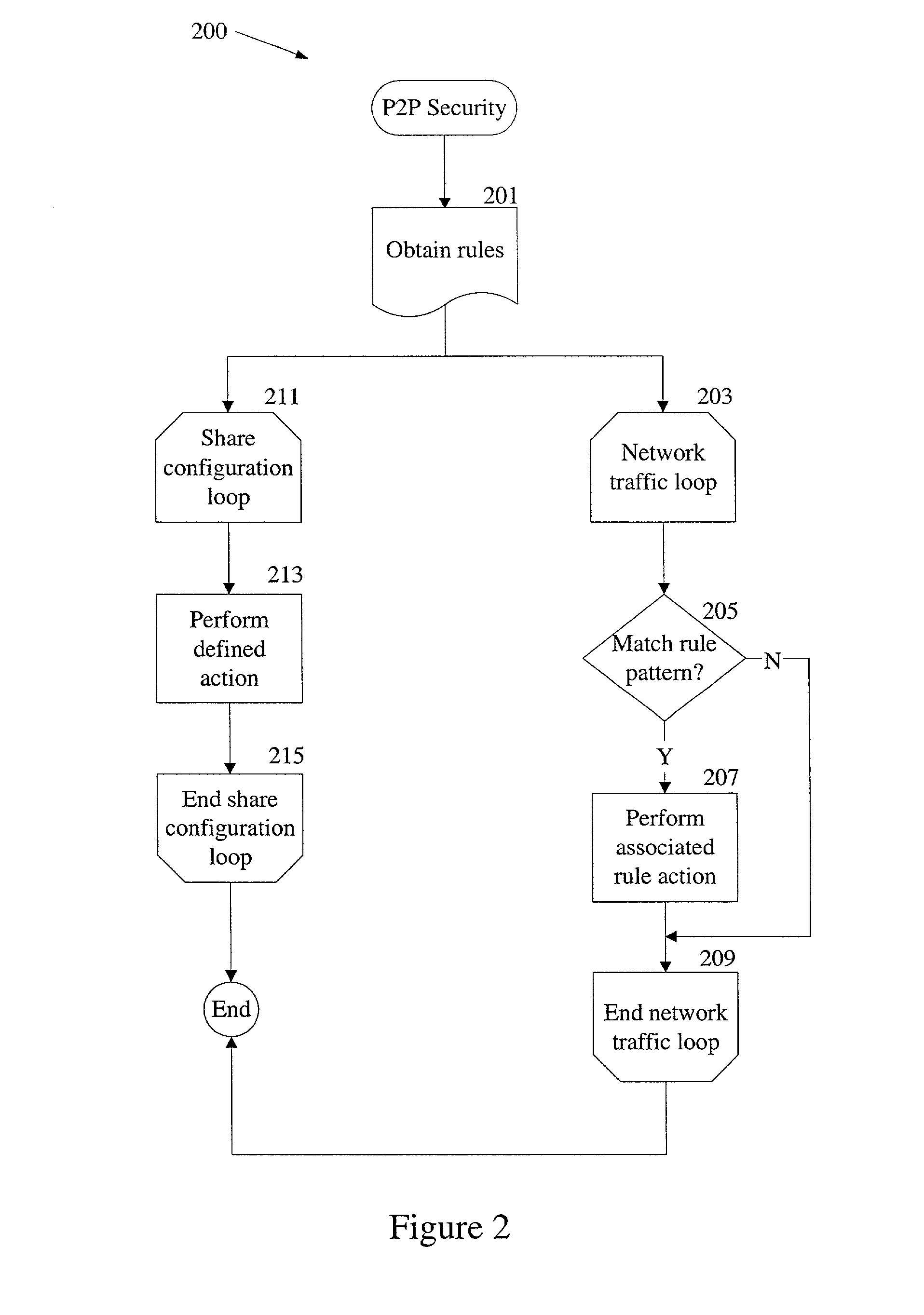
A peer-to-peer network is monitored for suspicious activity based on patterns of activity. When a particular pattern of suspicious activity is detected, an action associated with the particular pattern is taken. The activity monitored may include network traffic among peers and data sharing on a peer in the network. The action may be to log information about the suspicious activity and / or to send an alert about the suspicious activity.
Owner:MCAFEE LLC
Supervised access computer network router
InactiveUS8307068B2Good effectError detection/correctionMultiple digital computer combinationsNetwork activityComputer usage
A system for monitoring and regulating computer usage on a local network is disclosed. Computers on a network are configured with a client activity monitoring module that collects activity information including screen captures, keyboard activity, and / or information relating to network communications and sends the collected activity information to a network activity monitor for storage and later retrieval. Each computer on the local network periodically verifies that its client activity monitor module is operable. If a computer fails to send such verification, the system restricts network access by that computer, thus enforcing compliance with the activity monitoring system. The system further provides means for automatically displaying the collected activity information, including through screen savers, automatically changing desktop background images, and pop-up or sidebar windows. The system thus enables review of computer activities for appropriateness by both supervisors or parents as well as by peer users without requiring the reviewer to take affirmative steps to retrieve the activity information.
Owner:VOLONICS CORP
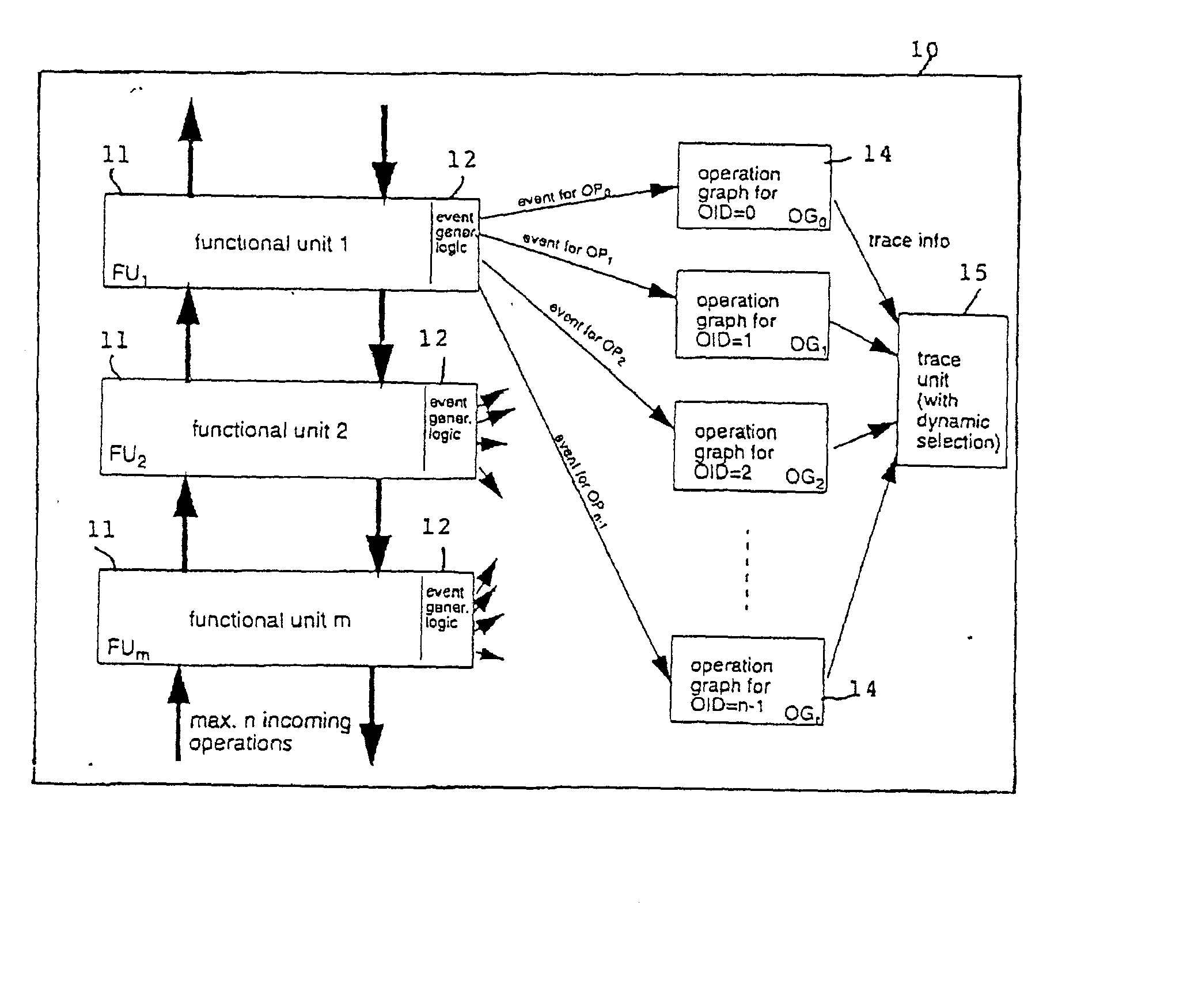
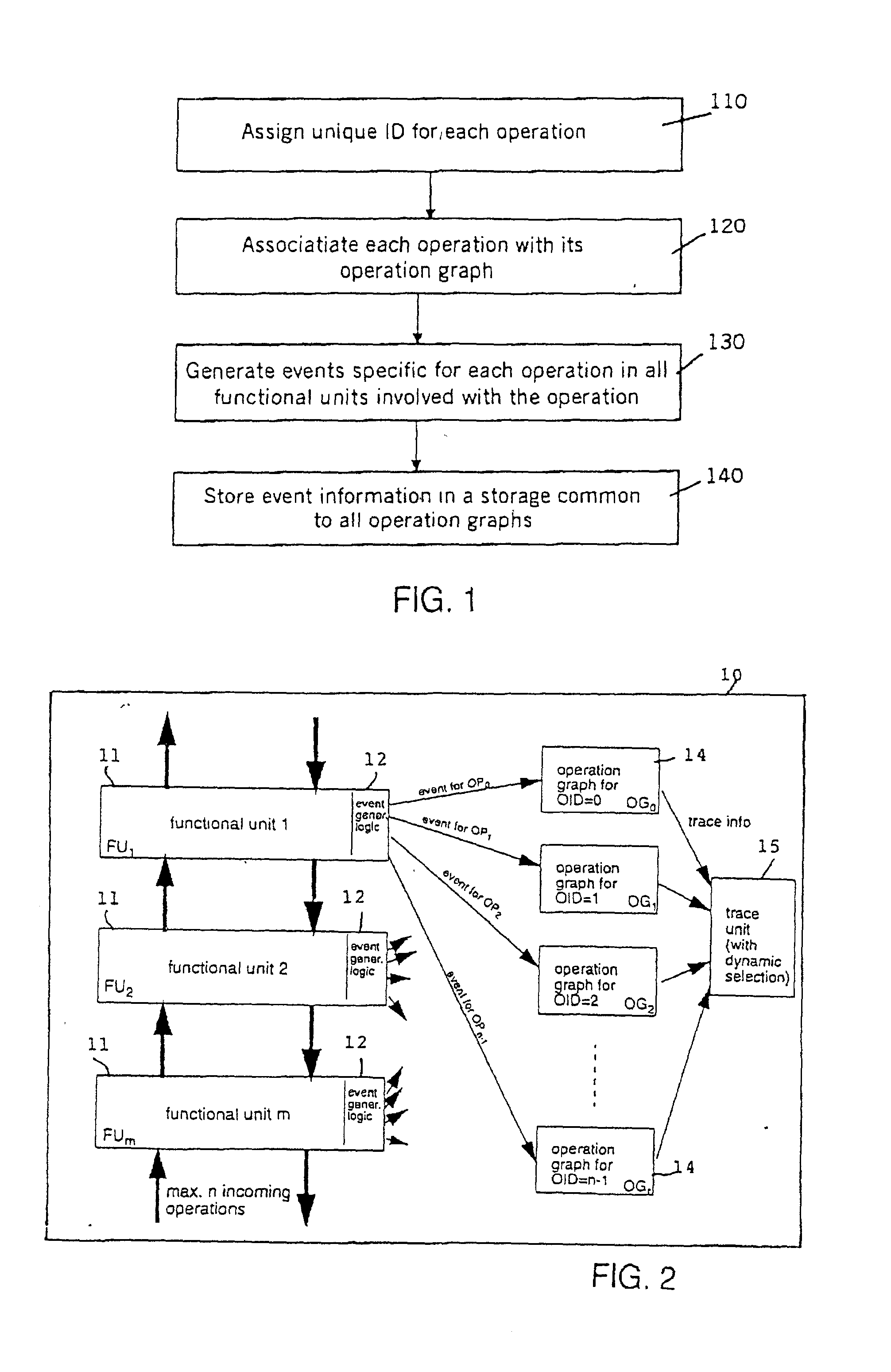
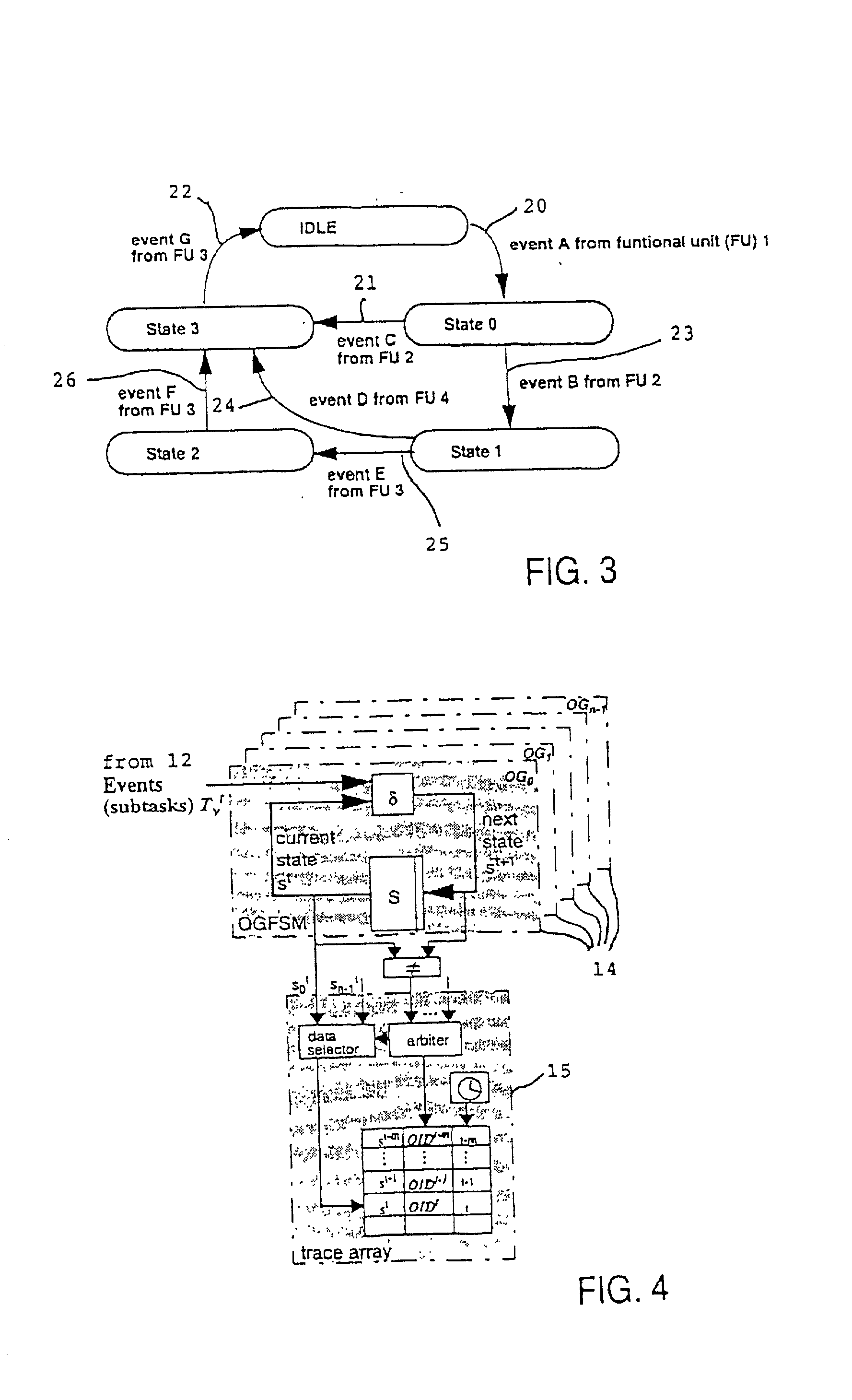
Operation graph based event monitoring system
InactiveUS20020100025A1Reduce in quantityPossible to monitorError detection/correctionSpecific program execution arrangementsConcurrent computingConcurrent computation
A non-obtrusive activity monitor is proposed for advantageously monitoring and tracing disjunct, concurrent computer system operations in heavily queued computer systems. For each traced and pending computer system operation, the monitor uses a hardware implementation of an event triggered operation graph to trace the path of the computer system operation through the computer system. For each followed path, a unique signature is generated that significantly reduces the amount of trace data to be stored. In a preferred embodiment, the trace information is stored together with a time stamp for debugging and measuring queuing effects and timing behavior in a computer system.
Owner:IBM CORP
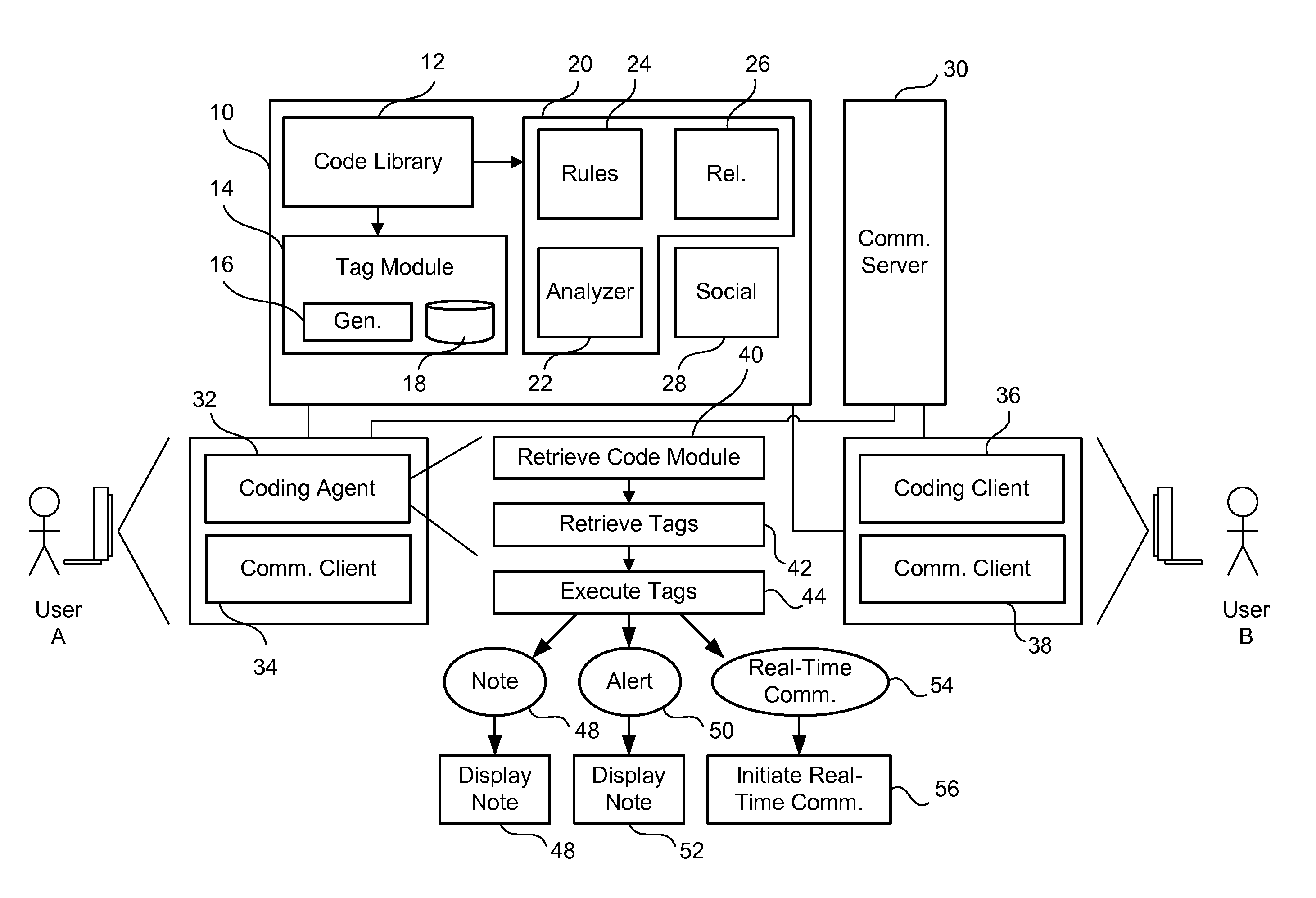
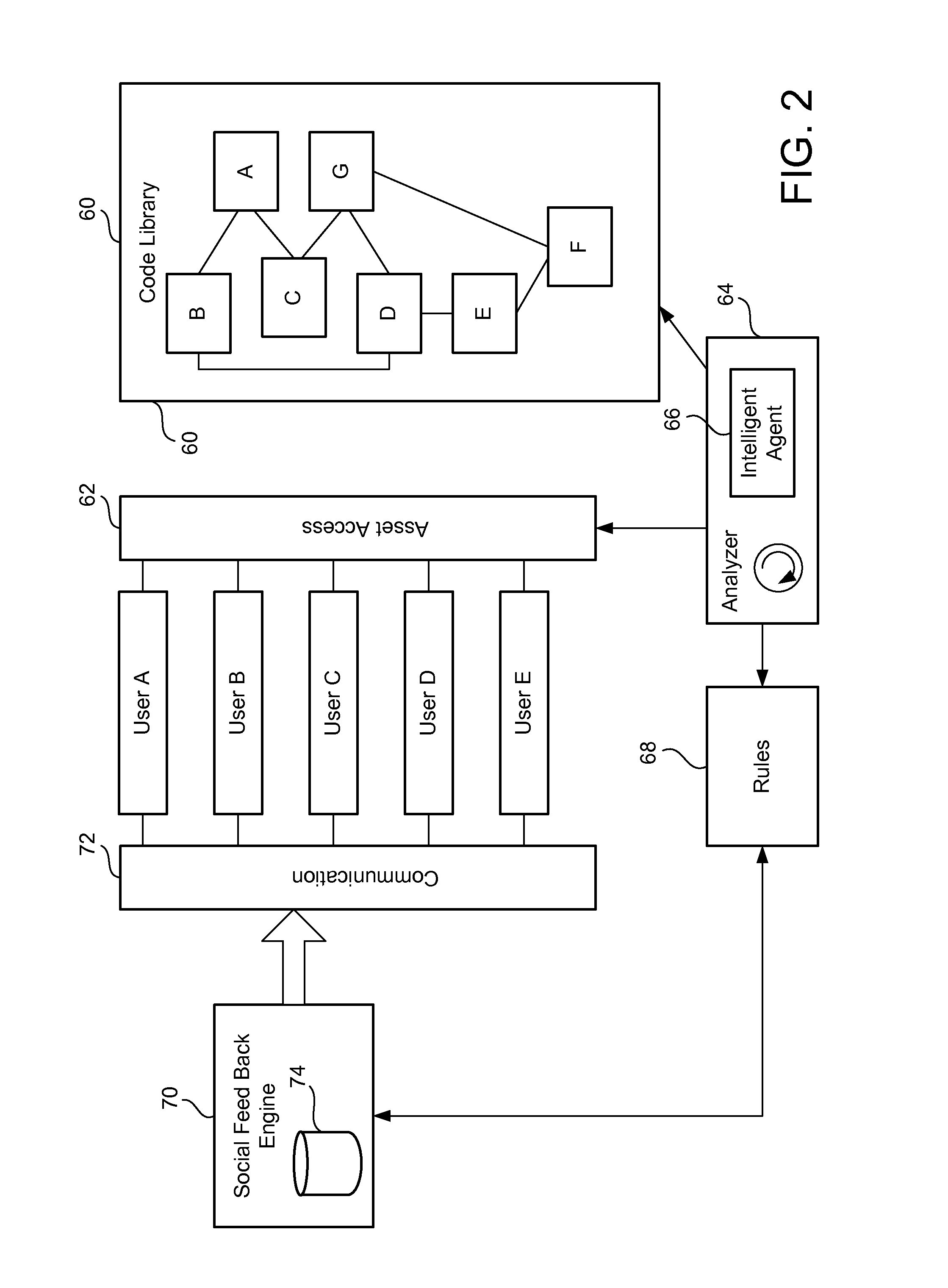
Social interactive code development
InactiveUS20120272207A1Version controlSpecific program execution arrangementsCode moduleActivity monitor
A system for social interactive code development of a plurality of code modules is provided. The system includes an activity monitor for monitoring access to one or more of the plurality of code modules. The system further includes a social feedback engine for initiating a communication based on triggering a predefined access threshold set for at least part of a specific one of the plurality of code modules.
Owner:SONY INTERACTIVE ENTERTAINMENT AMERICA LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com