Patents
Literature
96results about How to "Change habits" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
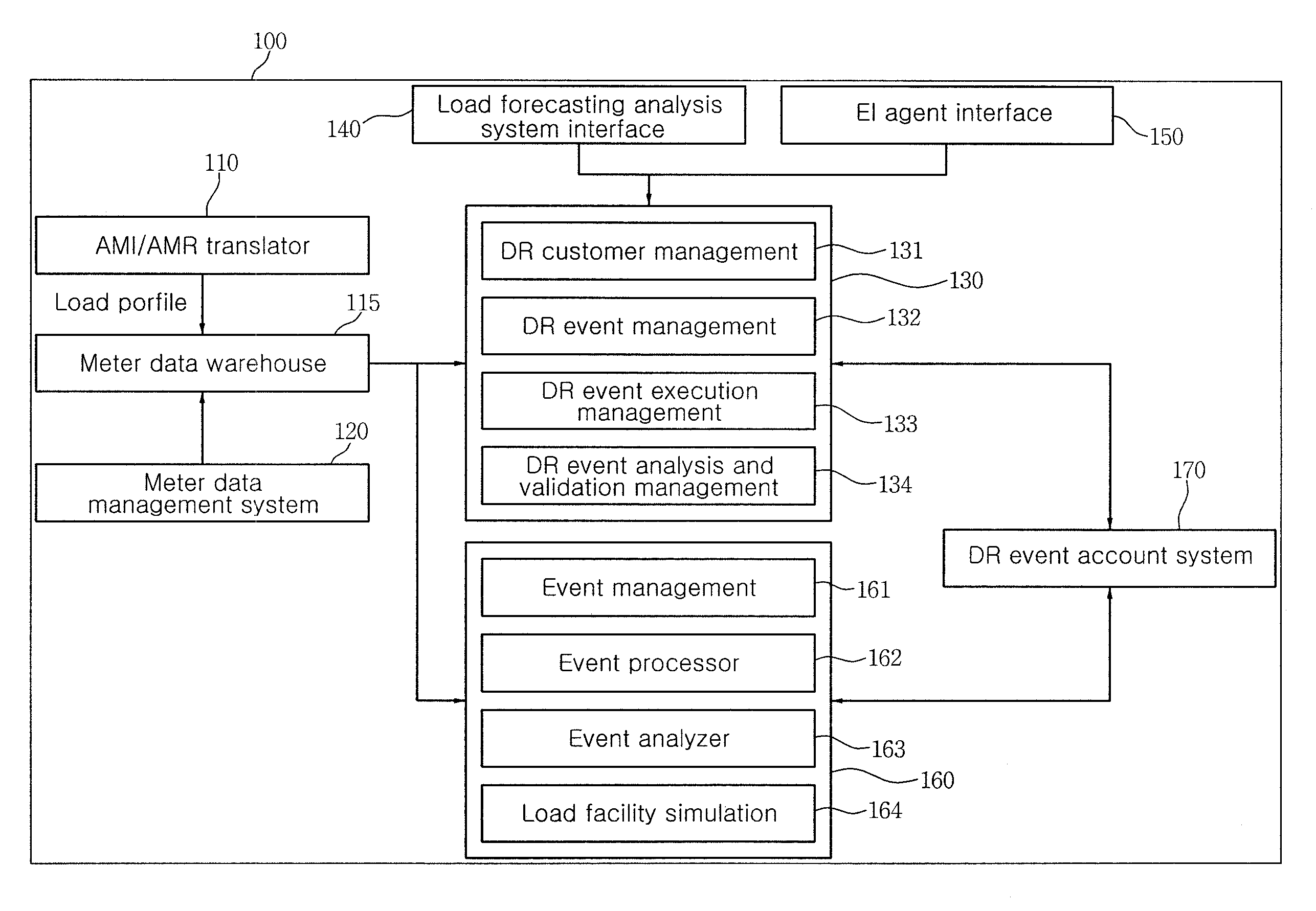
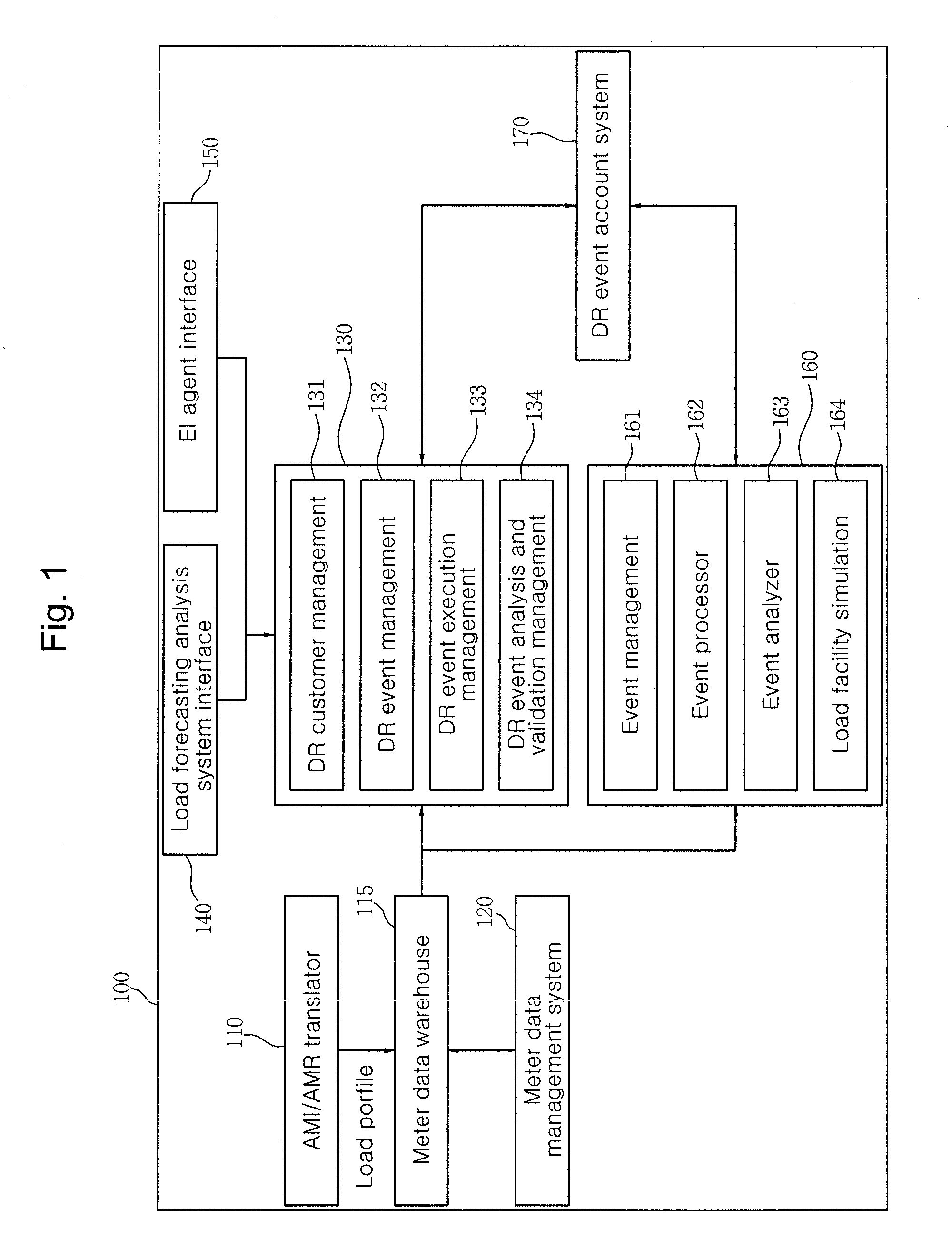
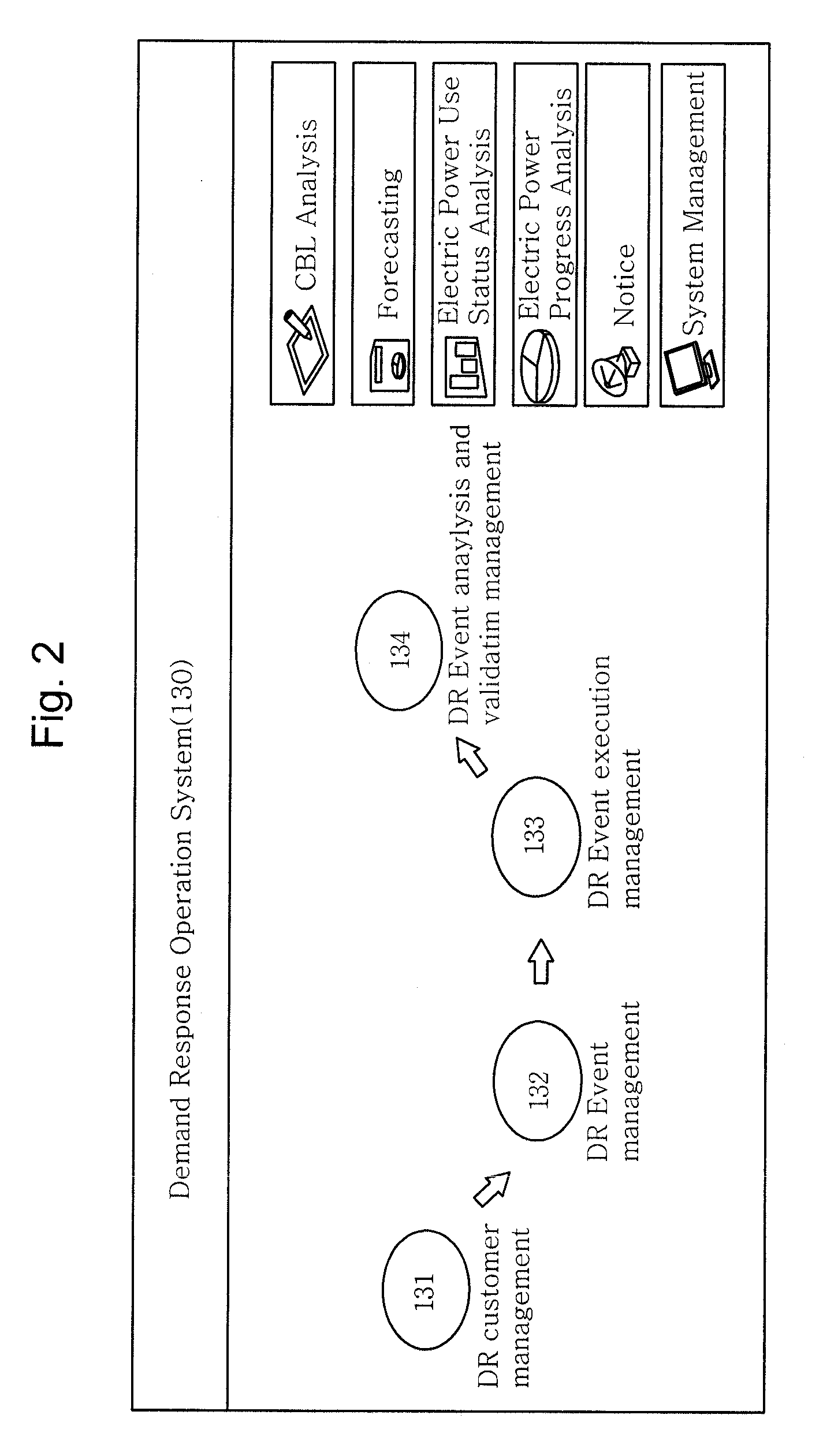
Day-ahead load reduction system based on customer baseline load
InactiveUS20100106342A1Efficient energy consumptionAddress rising pricesLevel controlLoad forecast in ac networkOperational systemData warehouse
Provided is a day-ahead load reduction system based on a customer baseline load for inducing a user to efficiently manage energy consumption by applying an incentive (user compensation according to load reduction) to achieve load reduction and load decentralization. The day-ahead load reduction system based on a customer baseline load operates in connection with a provider terminal and a user terminal through a network to induce a reduction in the load of a user and includes an AMI / AMR translator collecting load profile data of the user in real time, converting the load profile data and storing the load profile data in a meter data warehouse; a meter data management system monitoring and analyzing the load profile data stored in the meter data warehouse in real time; a demand response operation system managing the demand of the user by using the load profile data and performing overall management, analysis and verification of a day-ahead load reduction event; a customer energy management system operating in connection with the demand response operation system and providing information on the load to the user through the user terminal in real time to allow the user to control the load; and an account system operating in connection with the demand response operation system and the customer energy management system, calculating an incentive for the day-ahead load reduction event and notifying a provider and the user of the incentive through the provider terminal and the user terminal.
Owner:KOREA ELECTRIC POWER CORP
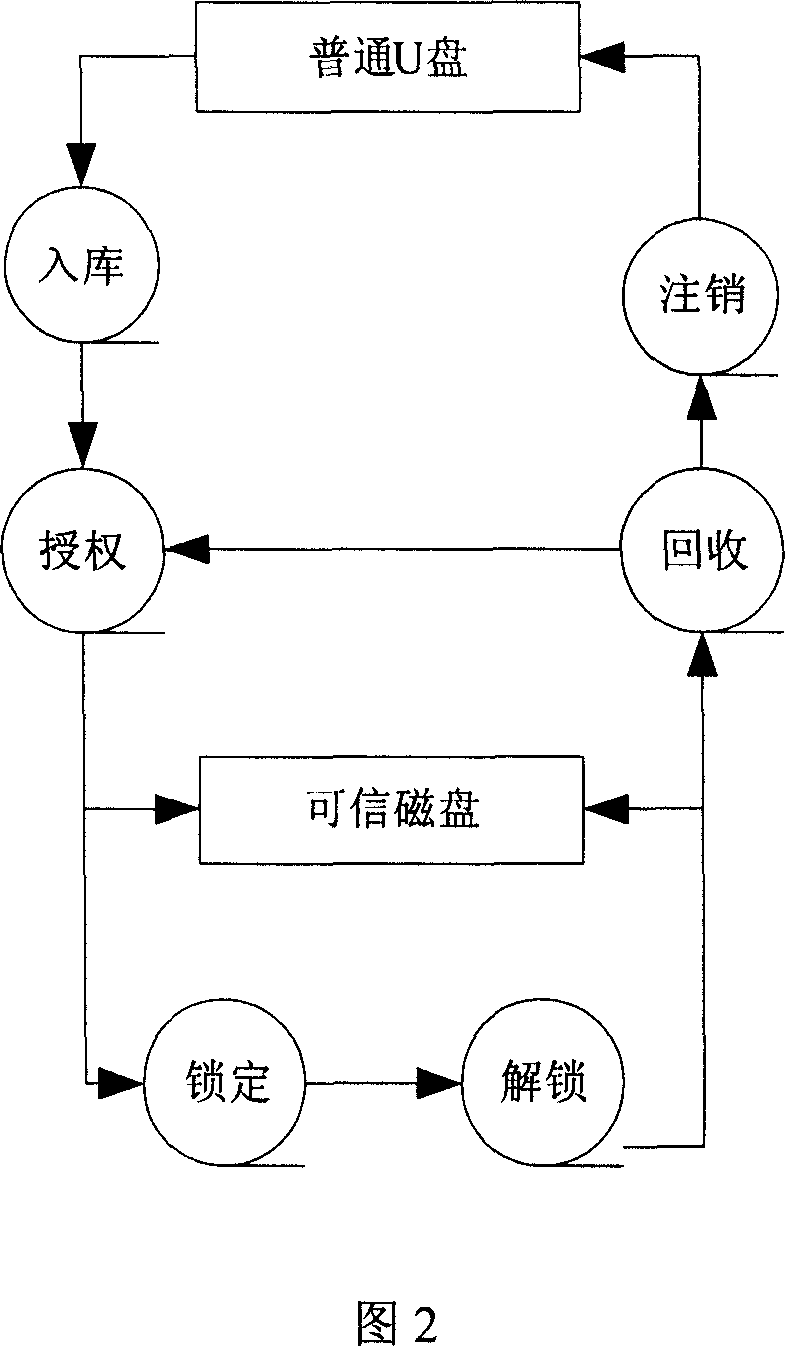
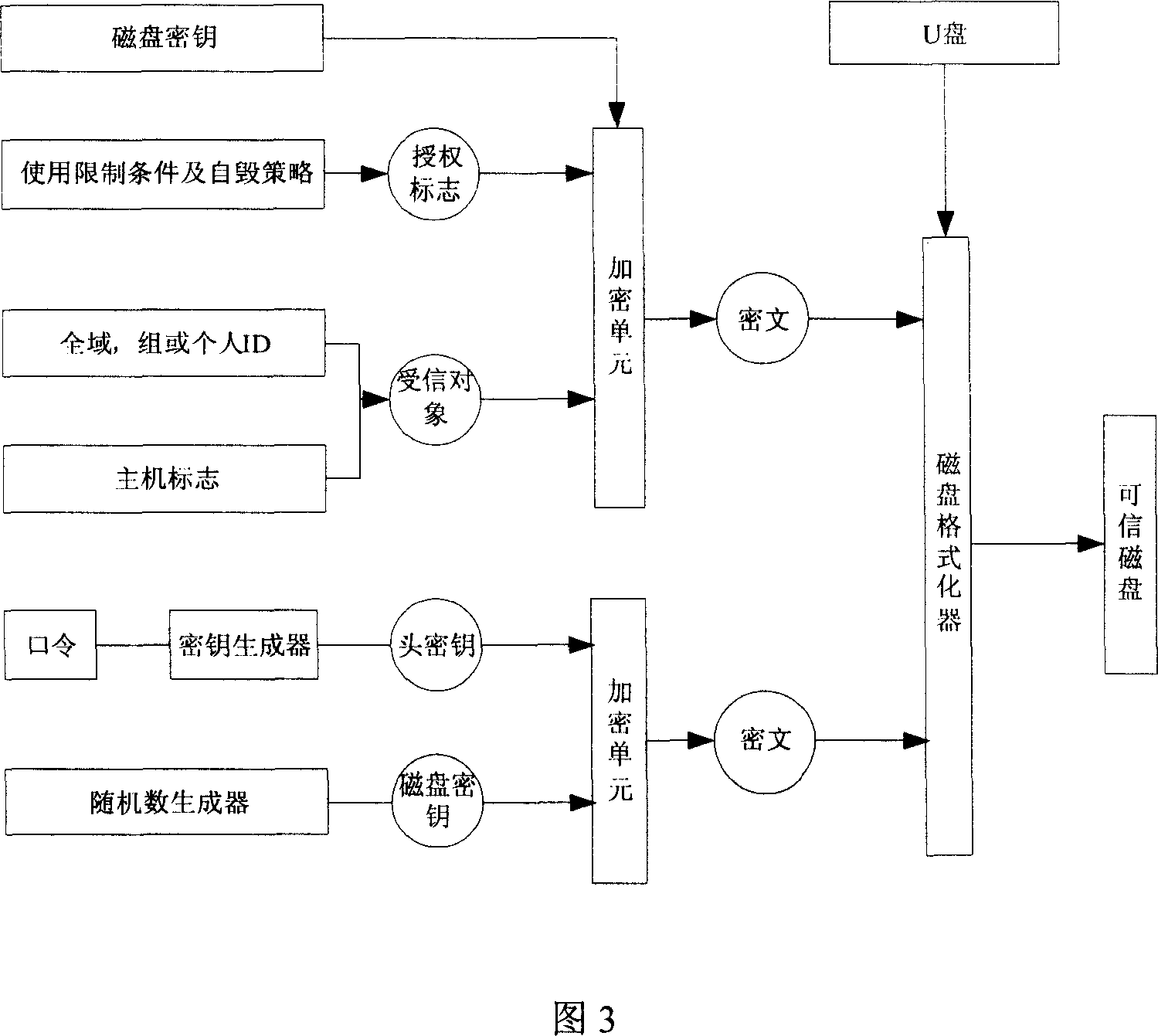
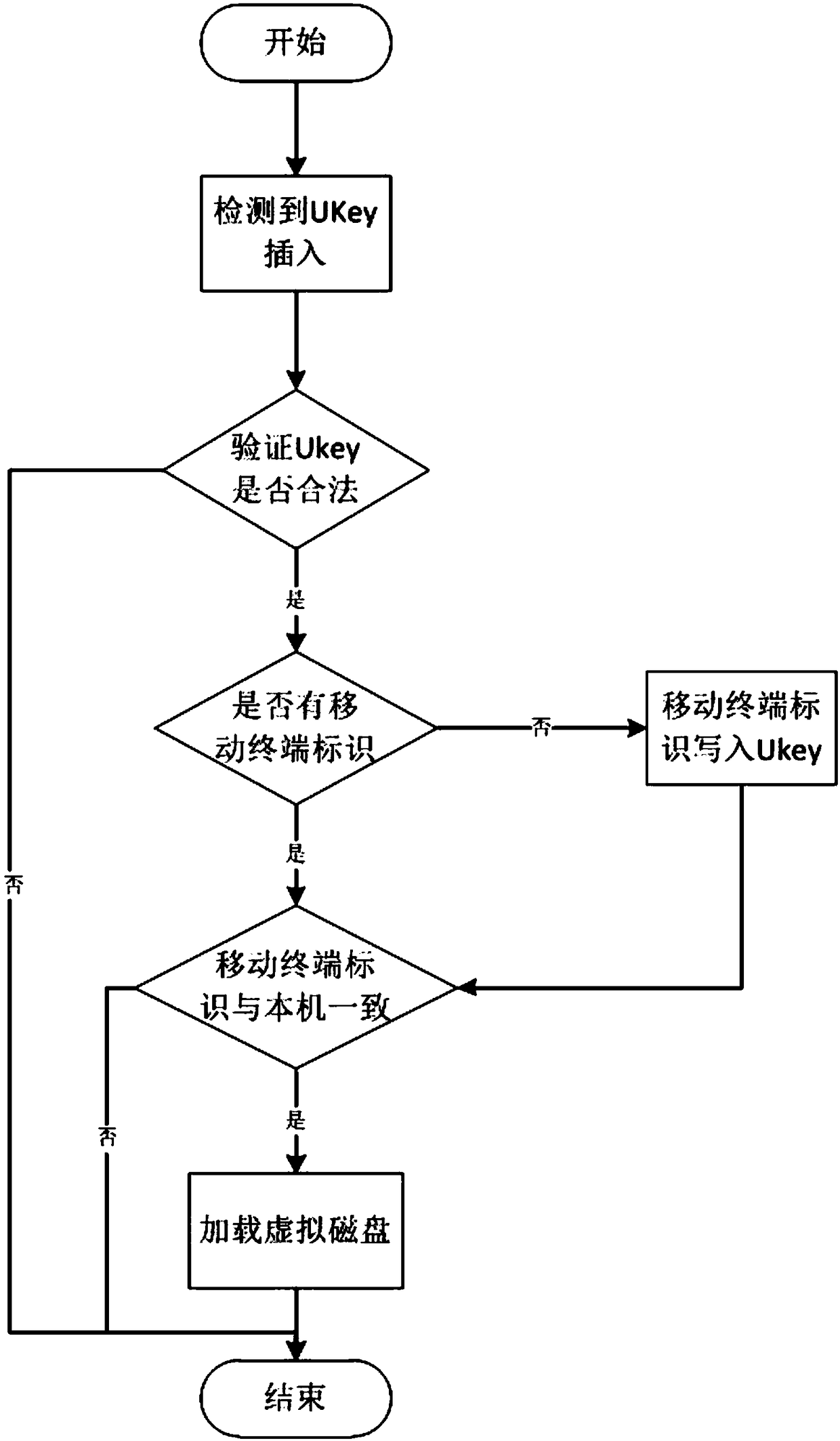
Mobile memory divulgence protection method and system
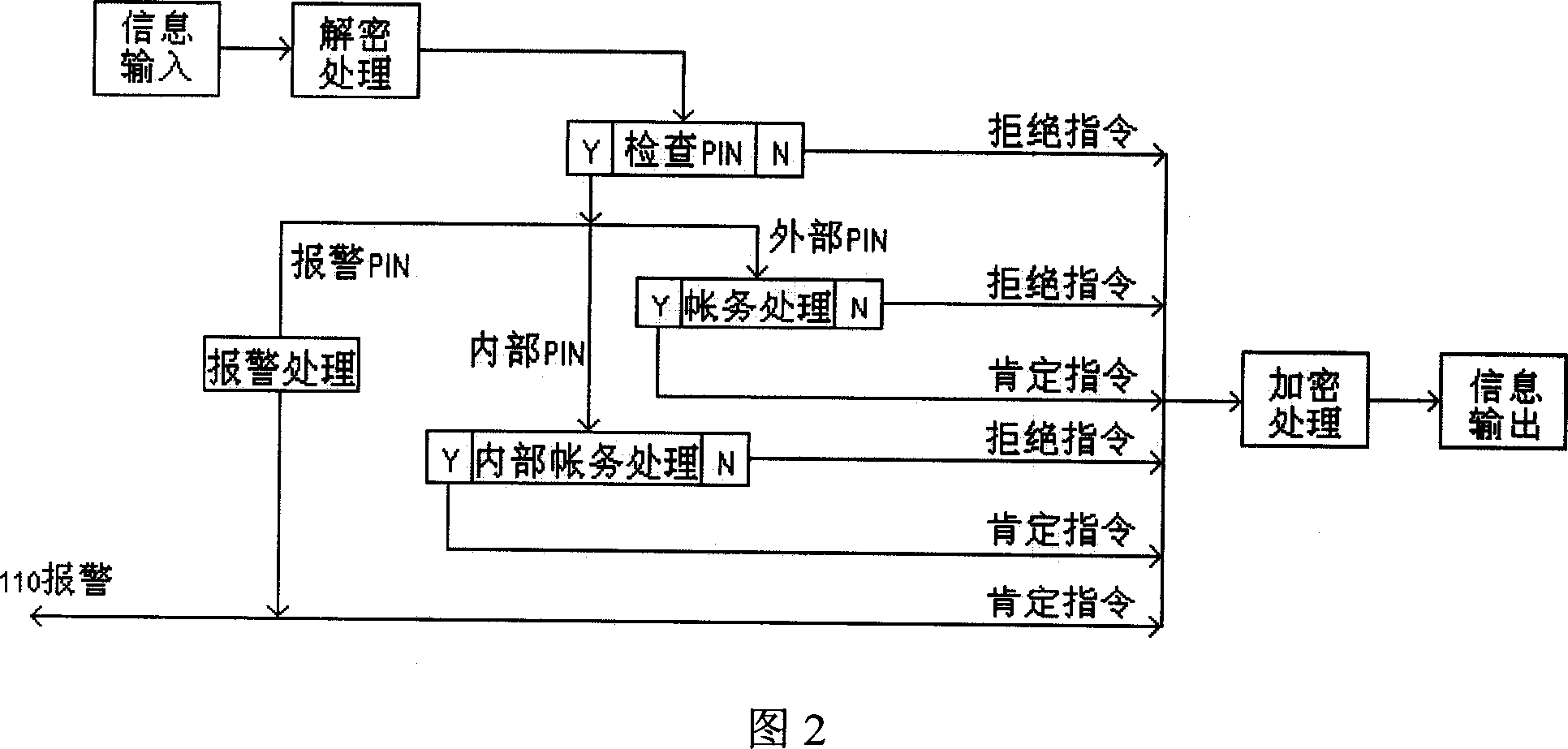
InactiveCN101079008AEasy to manageReach protectionUnauthorized memory use protectionInternal/peripheral component protectionCiphertextFloppy disk
The invention discloses a method of shifting memory leaking secret protection and system to realize the method, which is characterized by the following: utilizing virtual disk technique; adopting disk grade bridging method; proceeding encryption for the data in the common memory through the virtual disk with special pattern; storing the data on the shifting memory with cryptogram style; loading the virtual disk before reading or writing data; proceeding order checkout and user identification proved; non-loading without right order or special form; assuring the safety of the data in the shifting memory; setting the system as three module of server, warranting center and custom terminal. This invention can be used to various memories such as flash memory, shifting hard disk, soft disk and so on.
Owner:CHINA NAT SOFTWARE & SERVICE
Safe bubble-free infusion set
Owner:JIANGXI HONGDA MEDICAL EQUIP GROUP
Technical method for intelligently recommending data
InactiveCN104036002AChange habitsWeb data indexingSpecial data processing applicationsEngineeringData model
The invention mainly provides a solving method, and discloses a technical method for intelligently recommending data. The technical method includes firstly, acquiring a large quantity of information by the aid of crawlers, and then creating massive information sources by the aid of a keyword extracting algorithm and a theme algorithm; secondly, creating data models of users, acquiring behavioral data of browsing information and clicking information of the users, basic conditions and usage behavior of intelligent equipment, tracks of position change and the like according to the data models; thirdly, continuously improving feature images of the users by the aid of a model algorithm. The technical method has the advantages that by the aid of the solving method, the terminal users can quickly acquire information, and the problem of inconvenience due to the fact that users in the prior art need to search a large quantity of information to find favorable or required information in internet application procedures can be solved; modes in which the users passively acquire the information and spend time in searching the information can be changed by the solving method with a technology, and accordingly living habits of human can be truly changed by the internet; a server can judge information required by one of the users at the moment according to the feature images of the user when the user uses the intelligent equipment again, and the required information can be recommended to the user.
Owner:SHENZHEN INVENO TECH
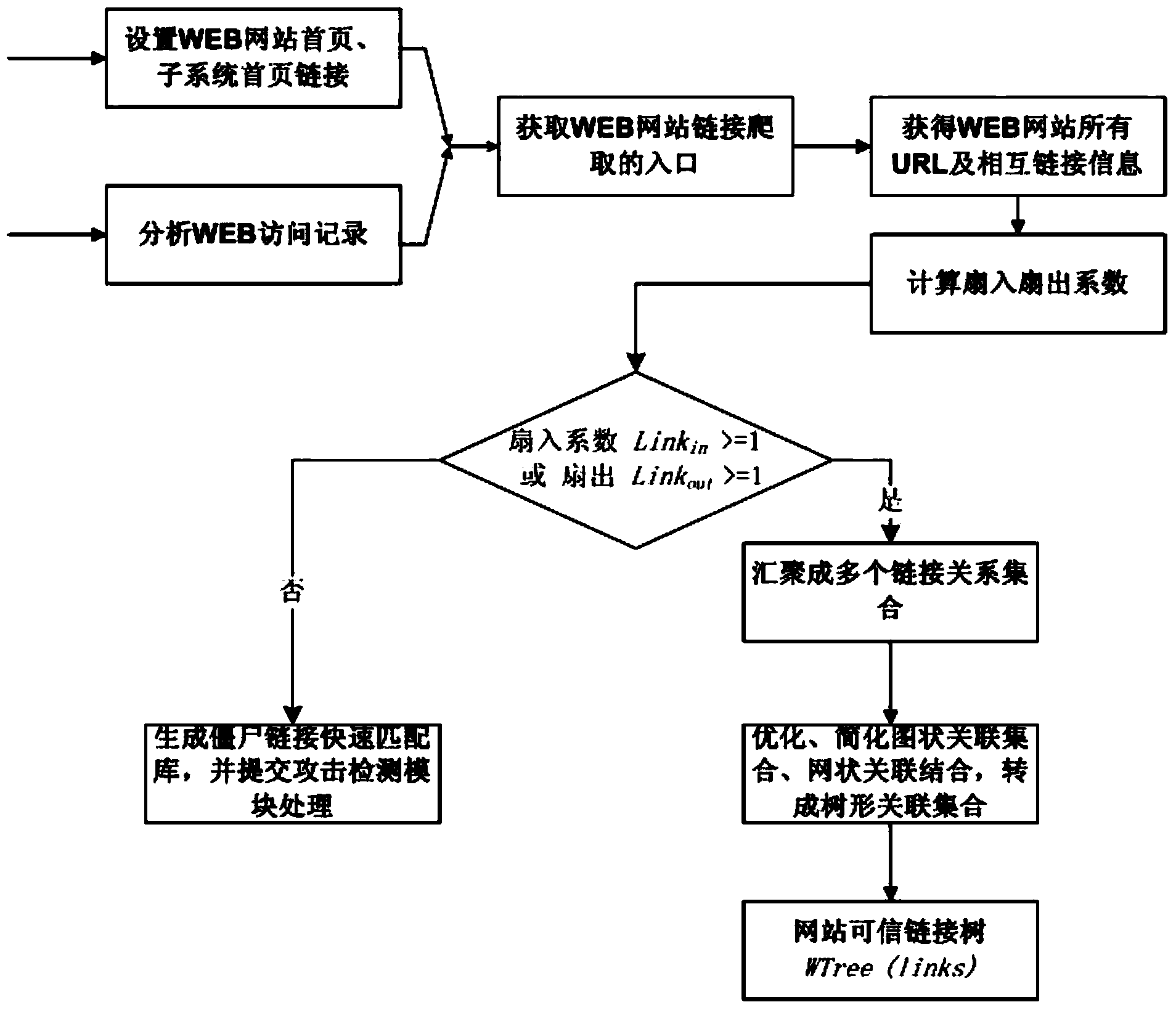
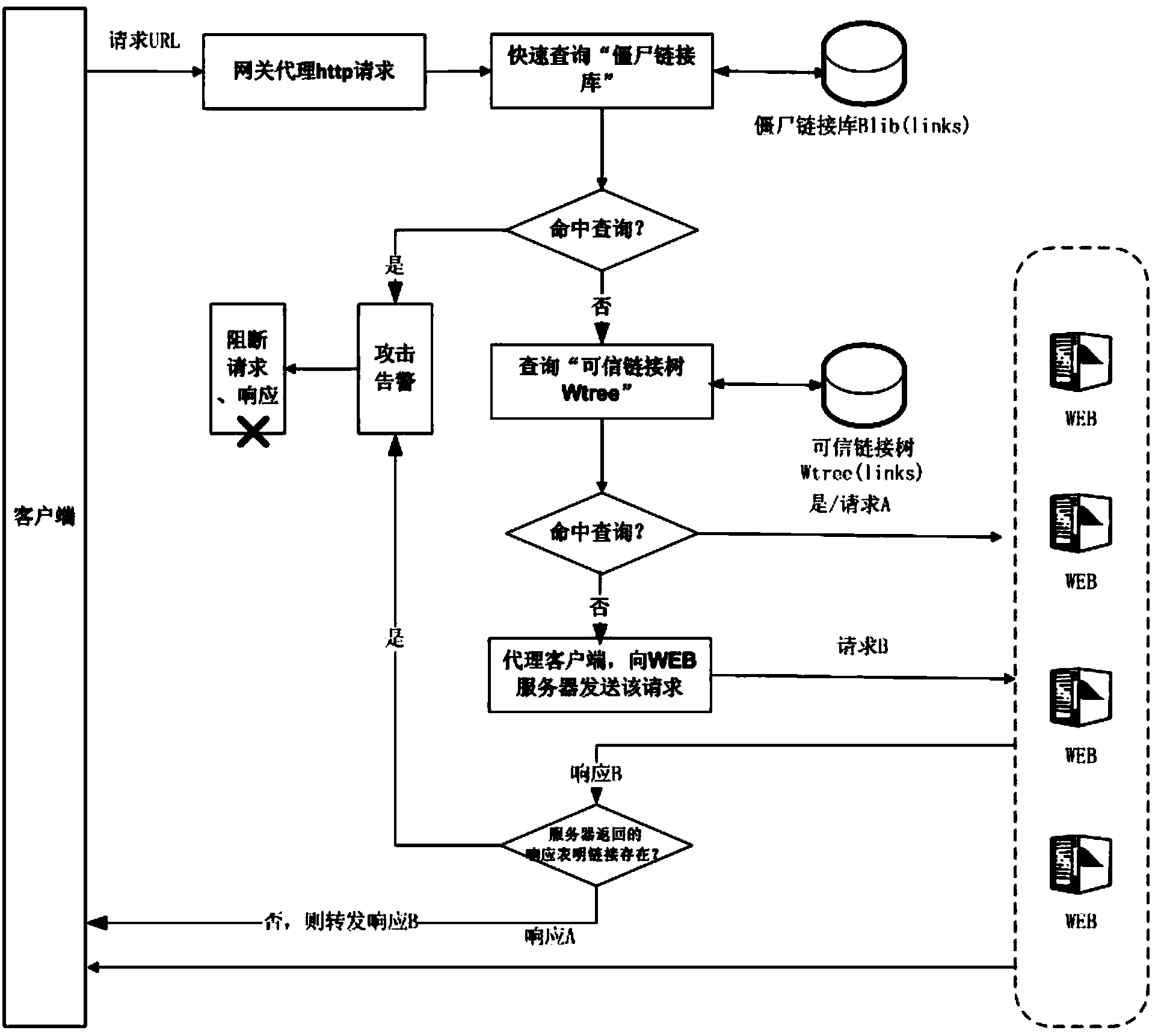
WEB backdoor detection method and system based on relevance tree
ActiveCN103561012AImprove relationshipSimplified link relationship tree associationTransmissionSpecial data processing applicationsWeb siteWeb application
The invention relates to a WEB backdoor detection method and system based on a relevance tree. The WEB backdoor detection system comprises a link relevance tree generation module and an attack real-time detection module. The detection system does not depend on antivirus software or file feature detection software, instead, initiative crawling and access record collecting are conducted on WEB links first, a link set of all URLs of a WEB is established through analysis and process, and the link and skip relation of the URLs is marked in a computerized algorithm in a tree mode, so that a link relevance tree is formed. If a backdoor URL request does not exist in the link relevance tree, a security monitoring module of the system gives an alarm, and the attack request is stopped. By means of the detection method, the safety of WEB application is improved, the problem of WEB backdoor attack which can not be detected and prevented by security products such as the antivirus software and a firewall is solved, the university is good, there is no need to mount software programs on a WEB server, and the type of the WEB server, WEB programming languages, customer usage and the like are all made to be transparent.
Owner:INST OF INFORMATION ENG CAS
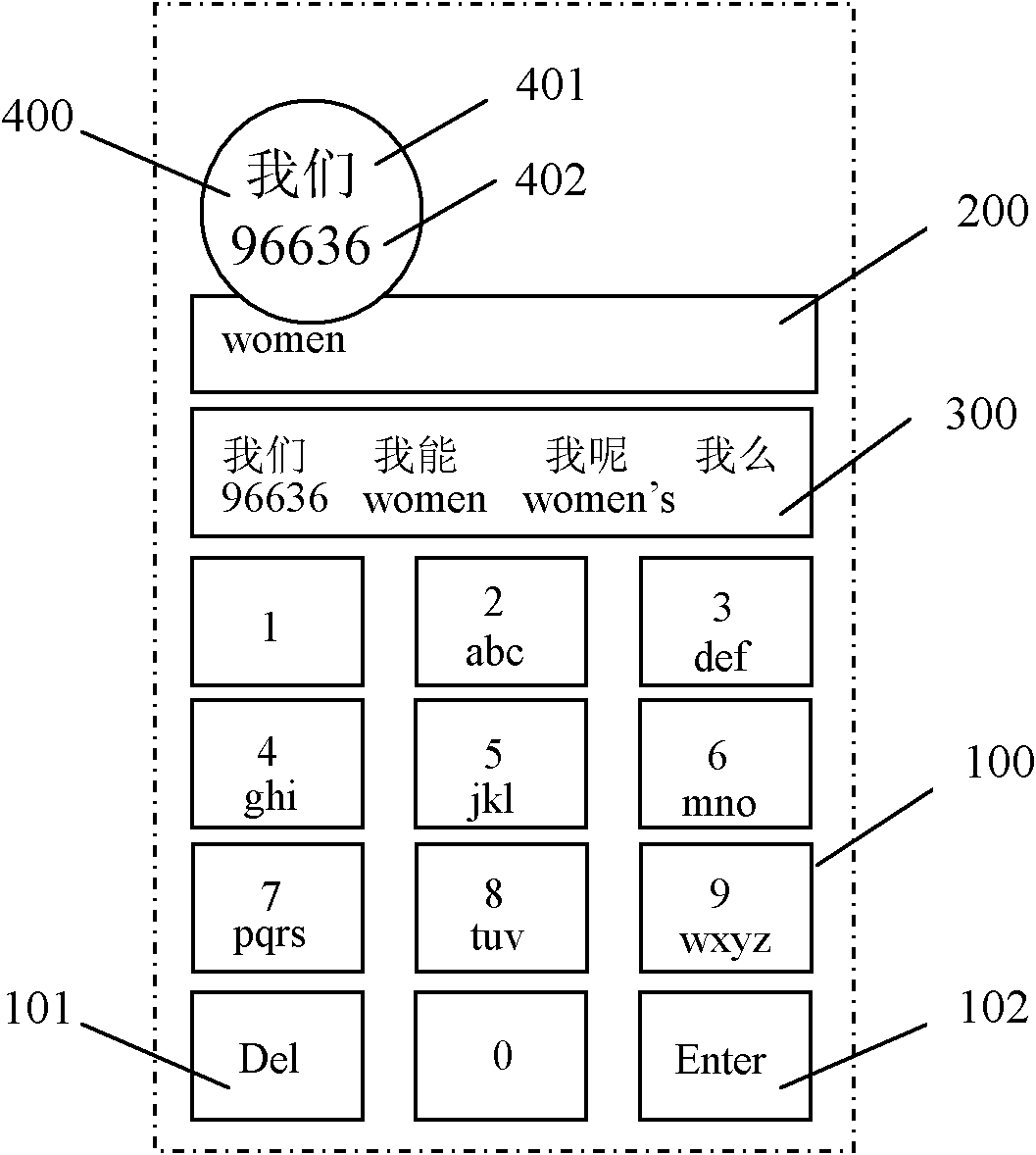
Multi-language hybrid input method used on embedded touch screen virtual keyboard
InactiveCN101976173AChange habitsImprove search abilityInput/output processes for data processingMulti languageComputer compatibility
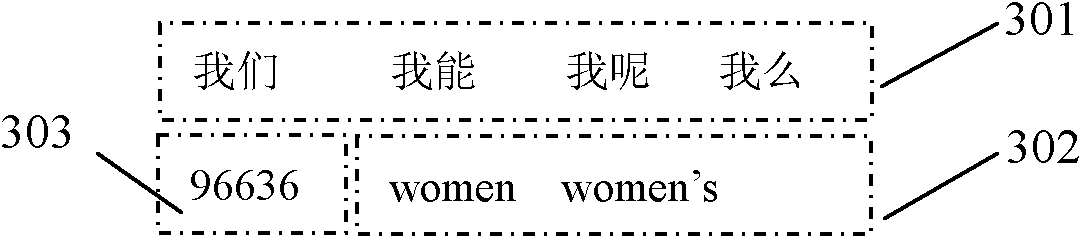
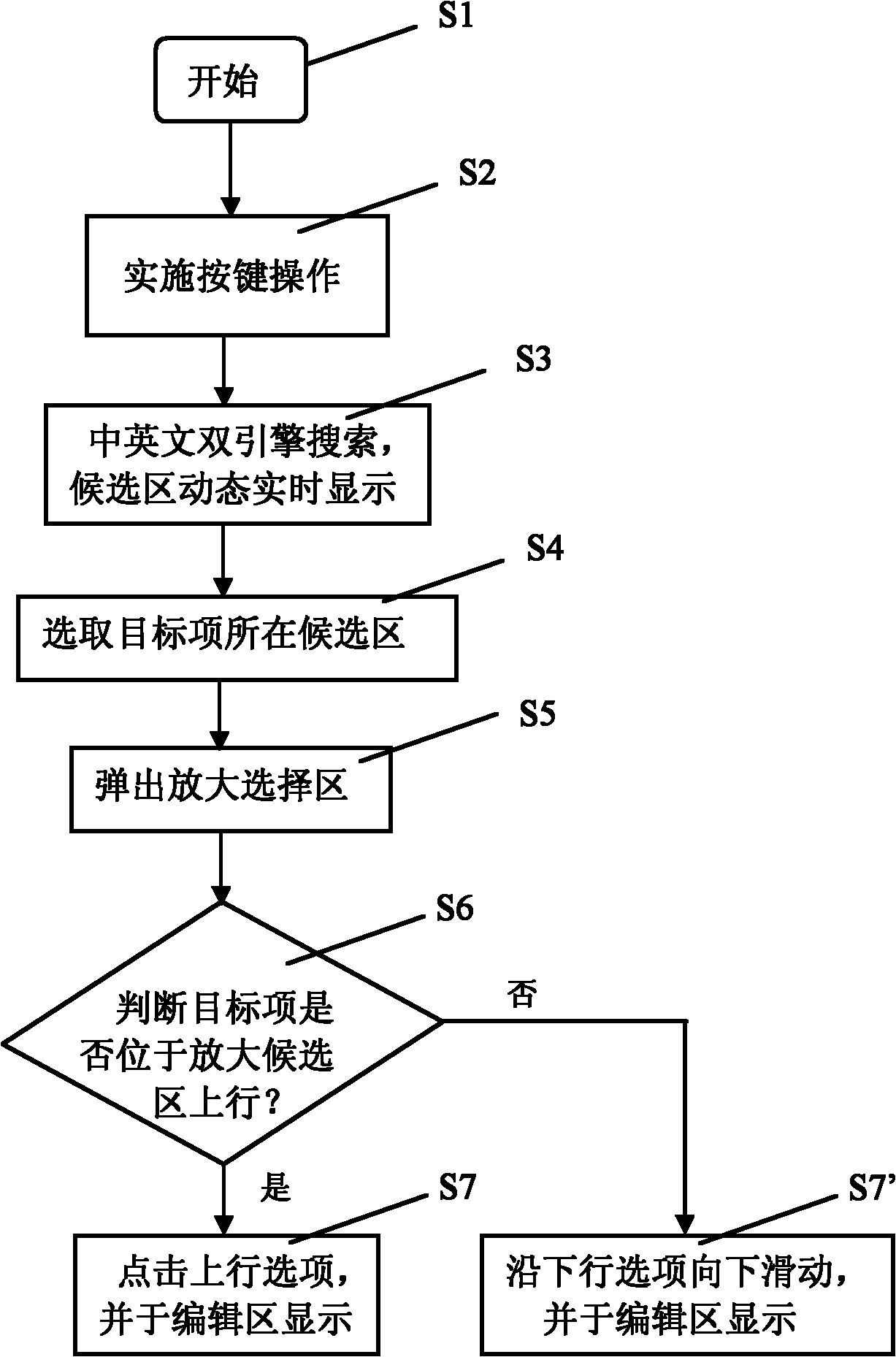
The invention discloses a multi-language hybrid input method used on an embedded touch screen virtual keyboard. Each key on the virtual keyboard maps three to four characters respectively; a display region of a touch screen is provided with a virtual keyboard region, an editing region and a candidate region; the touch screen also comprises a pop-up amplifying and selecting region; the method particularly comprises the following steps of: performing keystroke operation; dynamically displaying Chinese information, numerical information and foreign information related to the key at the candidate region; selecting the candidate region where a target item is positioned, popping up the amplifying and selecting region, and amplifying the row in which the target item is positioned in the candidate region by the amplifying and selecting region; and clicking or downwardly sliding the target item and selecting and displaying input Chinese information, numerical information or foreign information at the editing region in real time to finish the input. By the method, rapid hybrid input of Chinese, number, English and other foreign languages is realized, the efficiency of inputting written information is greatly improved, and the operation is intuitive and the compatibility of the method is good.
Owner:GUANGZHOU JIUBANG DIGITAL TECH
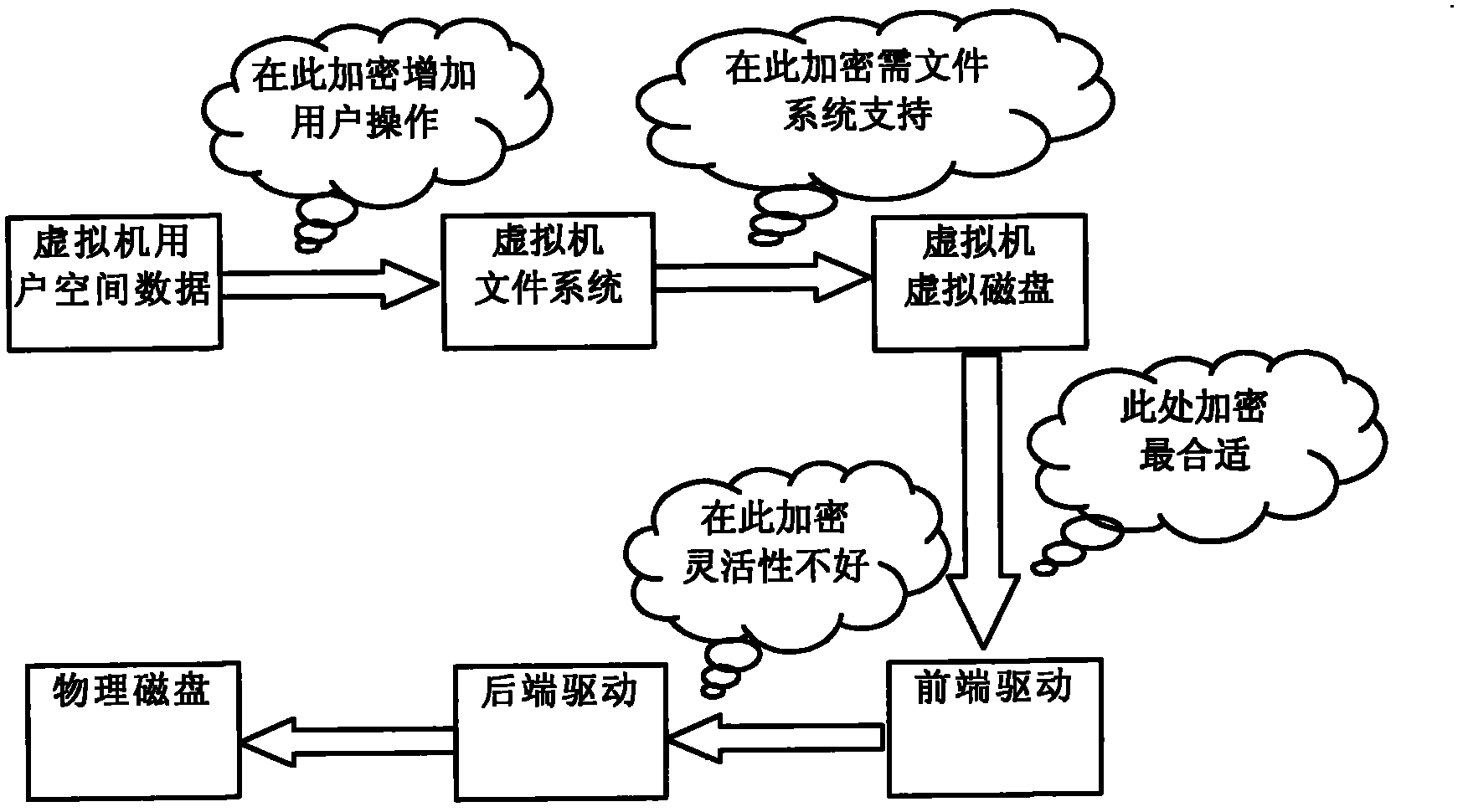
Data underlay encryption method based on disk drive in cloud computing environment
ActiveCN102034046AChange habitsGuaranteed privacyInternal/peripheral component protectionData storingCloud storage
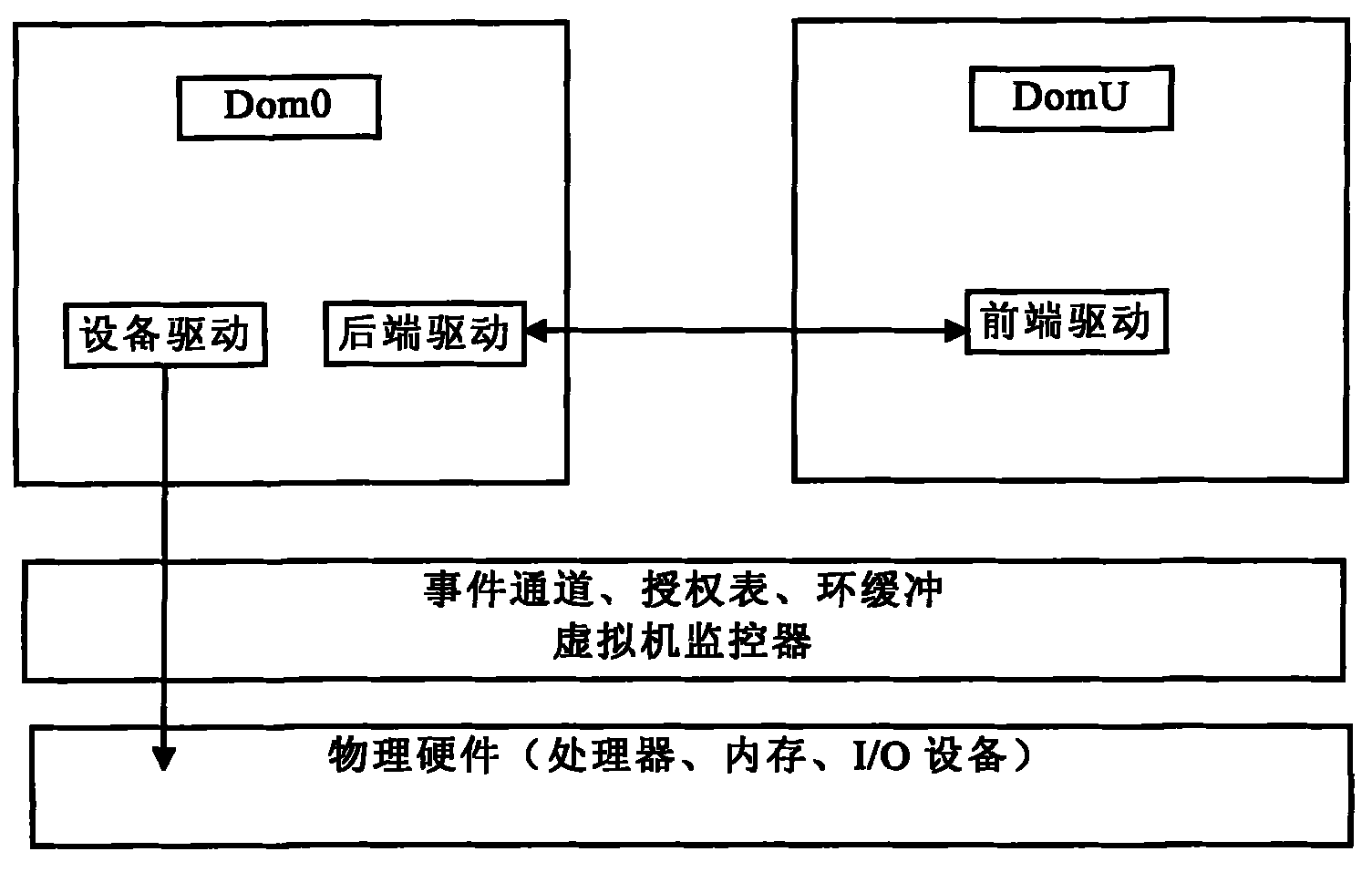
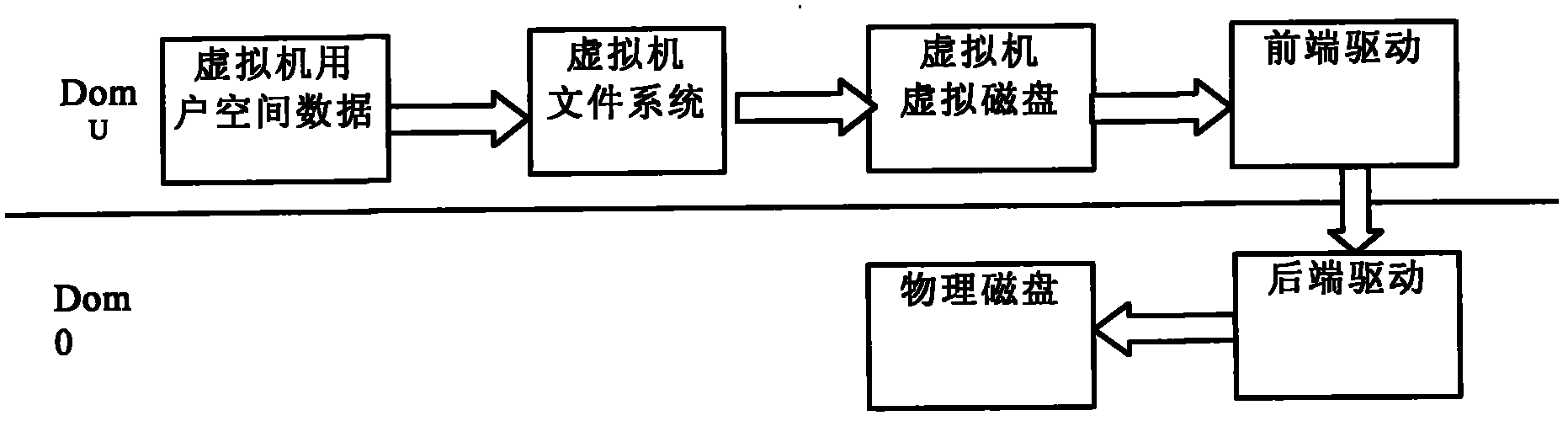
The invention discloses a data encryption underlay encryption method based on disk drive in the cloud computing environment, comprising the following steps of: (1) granting a page allocated by a memory space to an equipment virtual machine on which a rear-end drive is positioned through a front-end drive by using a grant table; (2) encrypting data in a buffer area by a front end; (3) placing a writing request of a disk into an annular buffer area shared with the rear-end drive and informing the writing request of the rear-end drive through an event channel; (4) after the rear-end drive is awaken, reading a writing disk request in the shared buffer area and mapping the granted page corresponding to the grant table to the own memory space to generate a real disk access request; and (5) after the disk request is finished, releasing the map by the rear-end drive, placing a response in the shared buffer area and simultaneously awaking the front-end drive through the event channel. The invention can ensure that important data stored by the user in a cloud memory are cipher texts and can still provide safety guarantee for private data of the user even if a storage cell is completely exposed.
Owner:BEIJING 21VIANET DATA CENT
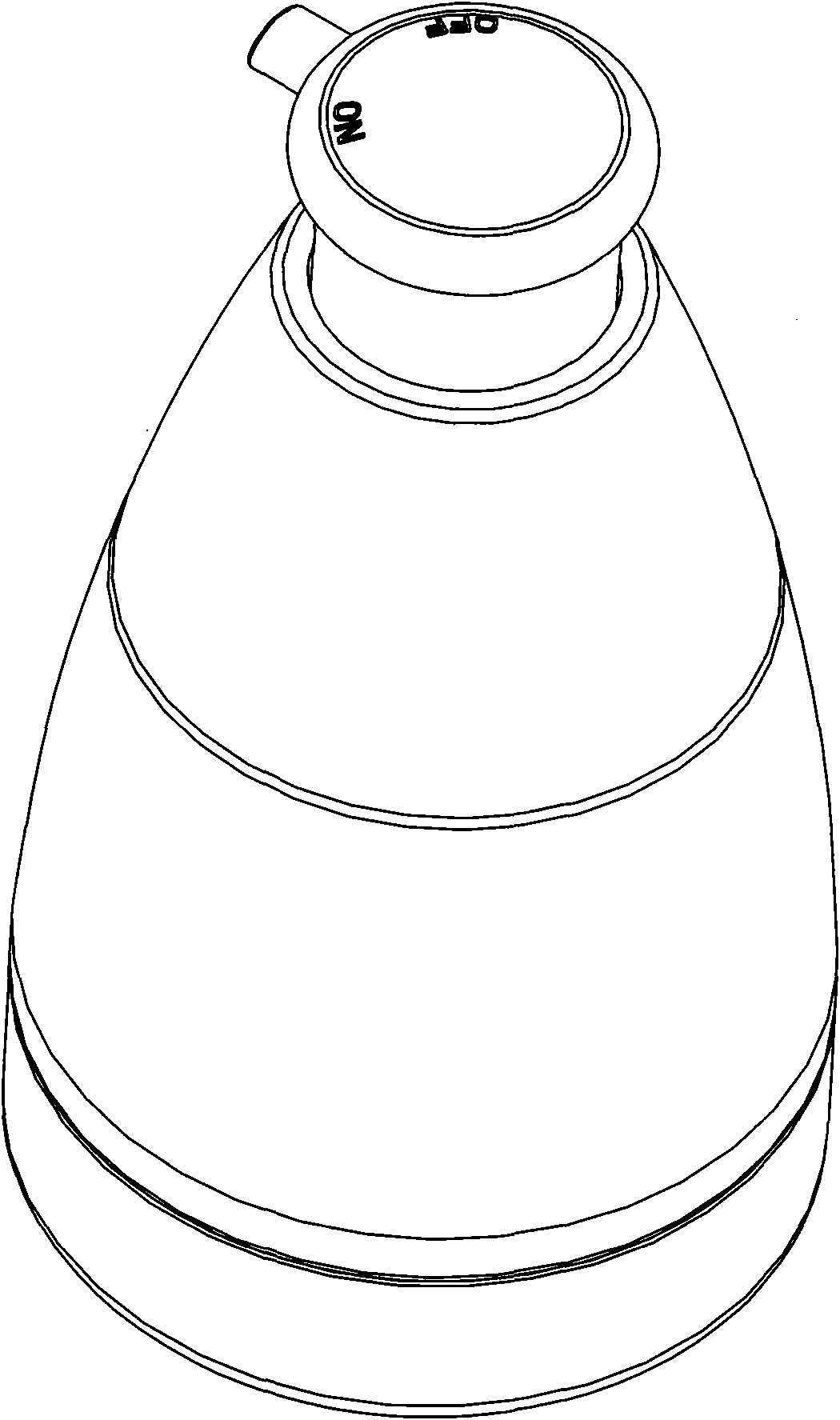
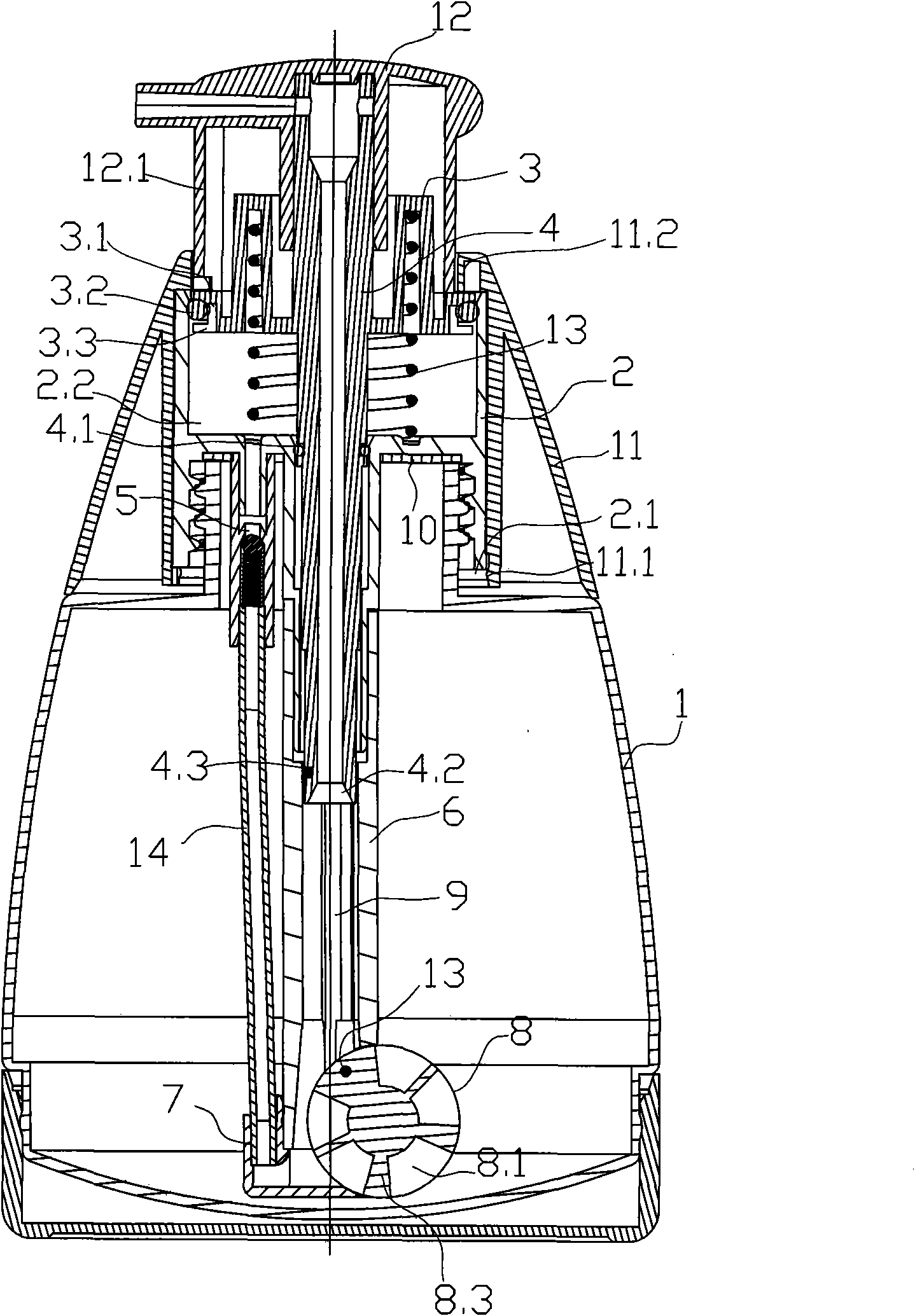
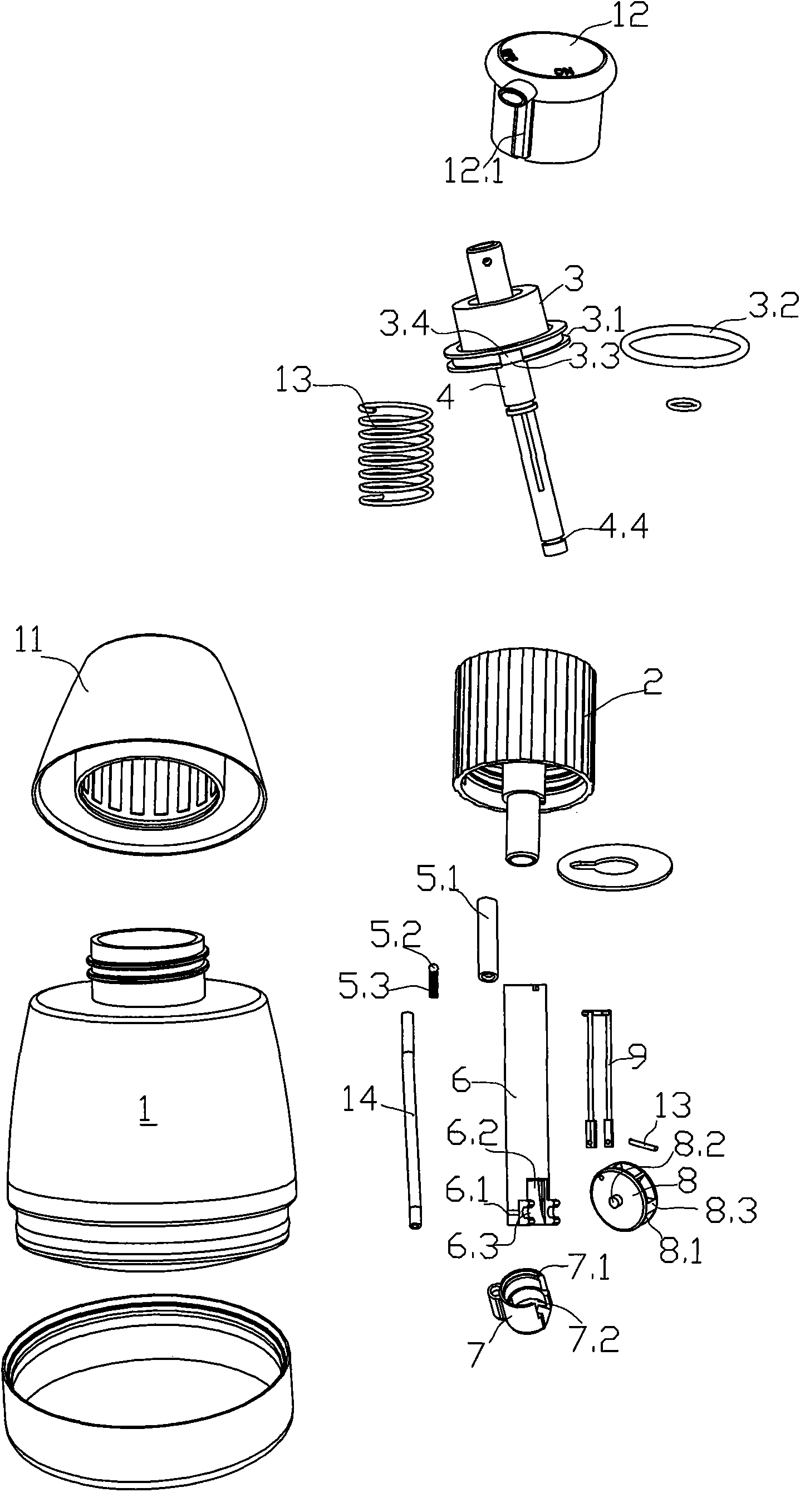
Dry powder pump
ActiveCN101879966AAvoid contactBig contactPowdered material dispensingDischarging meansProduct gasEngineering
The invention relates to a dry powder pump comprising a bottle body, a cap, a piston and an elastic element, wherein an inner cavity of the bottle body is used for containing powder; the cap is connected to a mouth of the bottle body to form a piston cavity; the piston is driven to slide up and down by a head cap and then is limited and installed in the piston cavity to form an air compressing mechanism; and the elastic element makes the piston have a resetting trend. The dry powder pump is characterized in that a one-way valve is arranged in the mouth of the bottle body, an air inlet and the one-way valve is communicated with the piston cavity, and an air outlet of the one-way valve is communicated with the inner cavity of the bottle body; and the upper end of a hollow pipeline is communicated with a nozzle on the head cap, and the lower end of the hollow pipeline passes through the mouth of the bottle body to extend nearby the bottom of the bottle body and is directly or indirectly communicated with the inner cavity of the bottle body. The dry powder pump has the advantages of reasonable and practical structure, favorable sealing performance, convenient operation and use, light weight and convenient carrying and is easy to spray mixed powder and air.
Owner:ZHEJIANG JM IND
Method for acquiring specific reference Gaussian plane rectangular coordinate based on continuous operational reference system (CORS) in real time
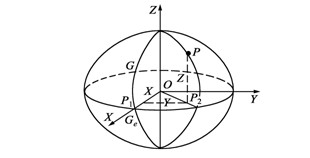
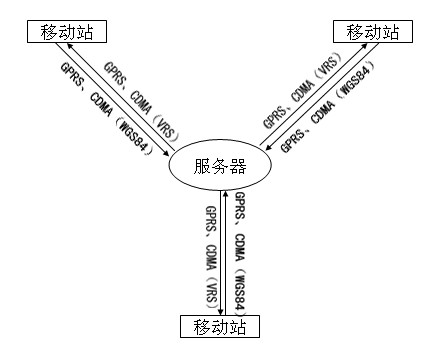
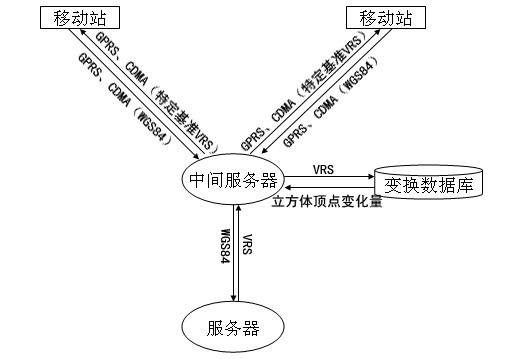
ActiveCN102223709AReduce use costChange habitsWireless communicationGeneral Packet Radio ServiceRectangular coordinates
The invention provides a method for acquiring coordinates based on a continuous operational reference system (CORS) in real time, and relates to a method for acquiring a specific reference Gaussian plane rectangular coordinate based on the CORS by using general packet radio service (GPRS) (or code division multiple access (CDMA)) communication technologies in real time. According to the invention, a middle server is arranged between a mobile station and a server for bi-directionally communicating with the mobile station and the server respectively, decoding virtual reference station (VRS) difference information which is generated by the server, and appropriately changing the coordinates (X, Y, Z) so that a user of the mobile station cannot acquire the real world geodetic system (WGS) 84 coordinate; corresponding false parameters are set on a holding book of the mobile station so as to acquire the specific reference Gaussian plane rectangular coordinate and avoid real parameters issuing. By the system, software, hardware and use habit of the user are not changed; the specific reference Gaussian plane rectangular coordinate is acquired; and elevation of the measured position is directly acquired by using ground level precise models, so that the working efficiency of the user is greatly improved; and the method is widely applied in fields such as surveying and mapping controlling, precise navigating and the like.
Owner:CHONGQING GEOMATICS & REMOTE SENSING CENT
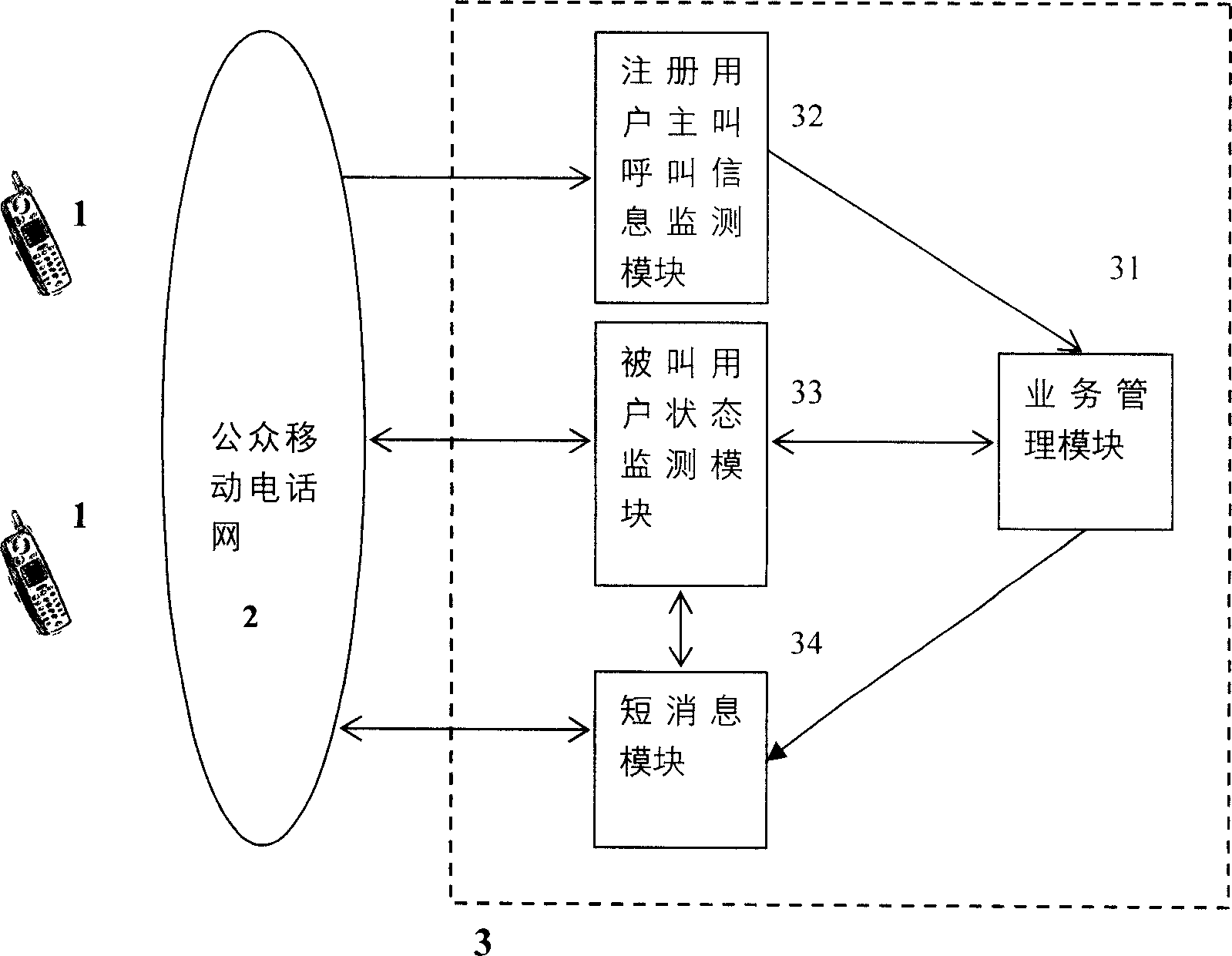
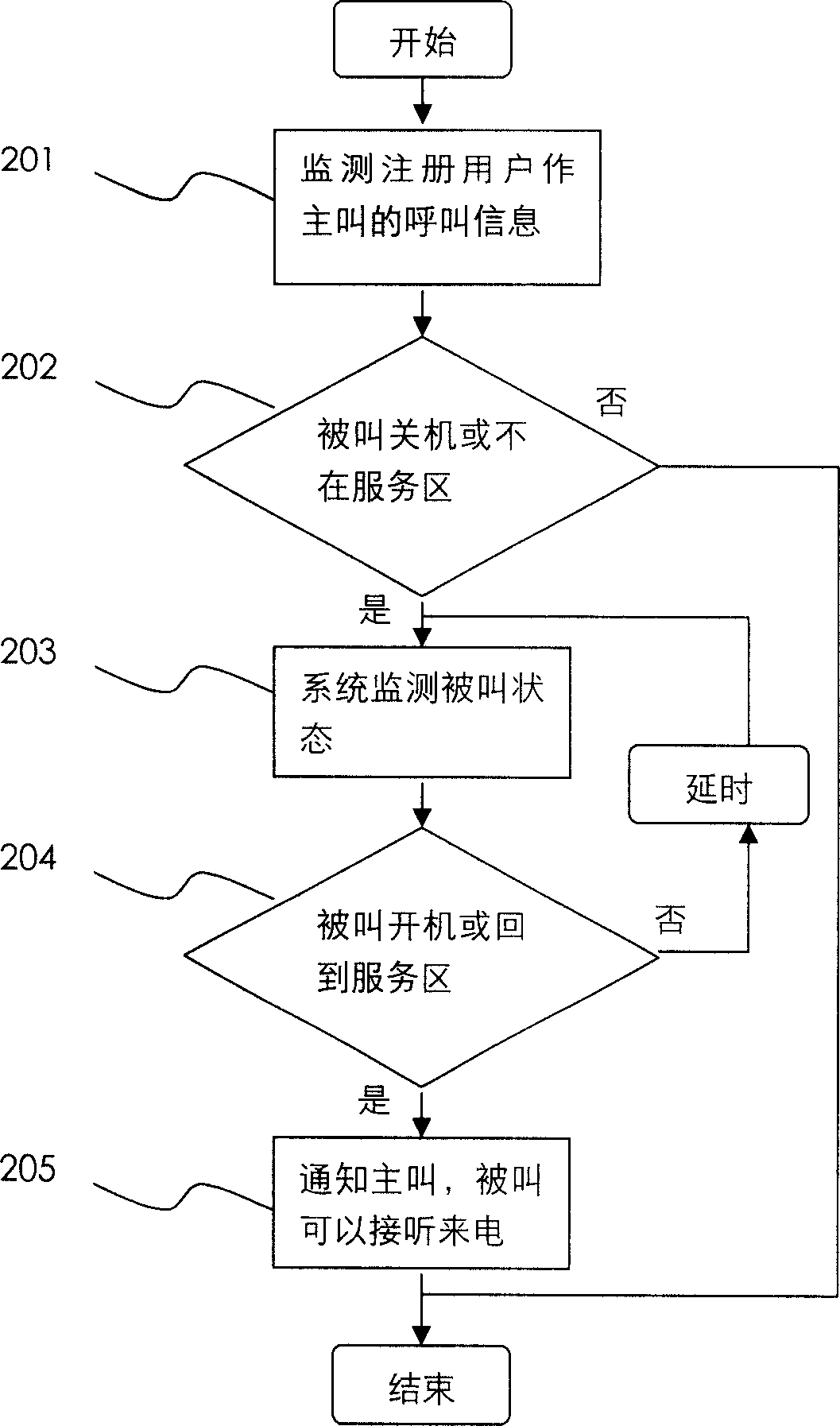
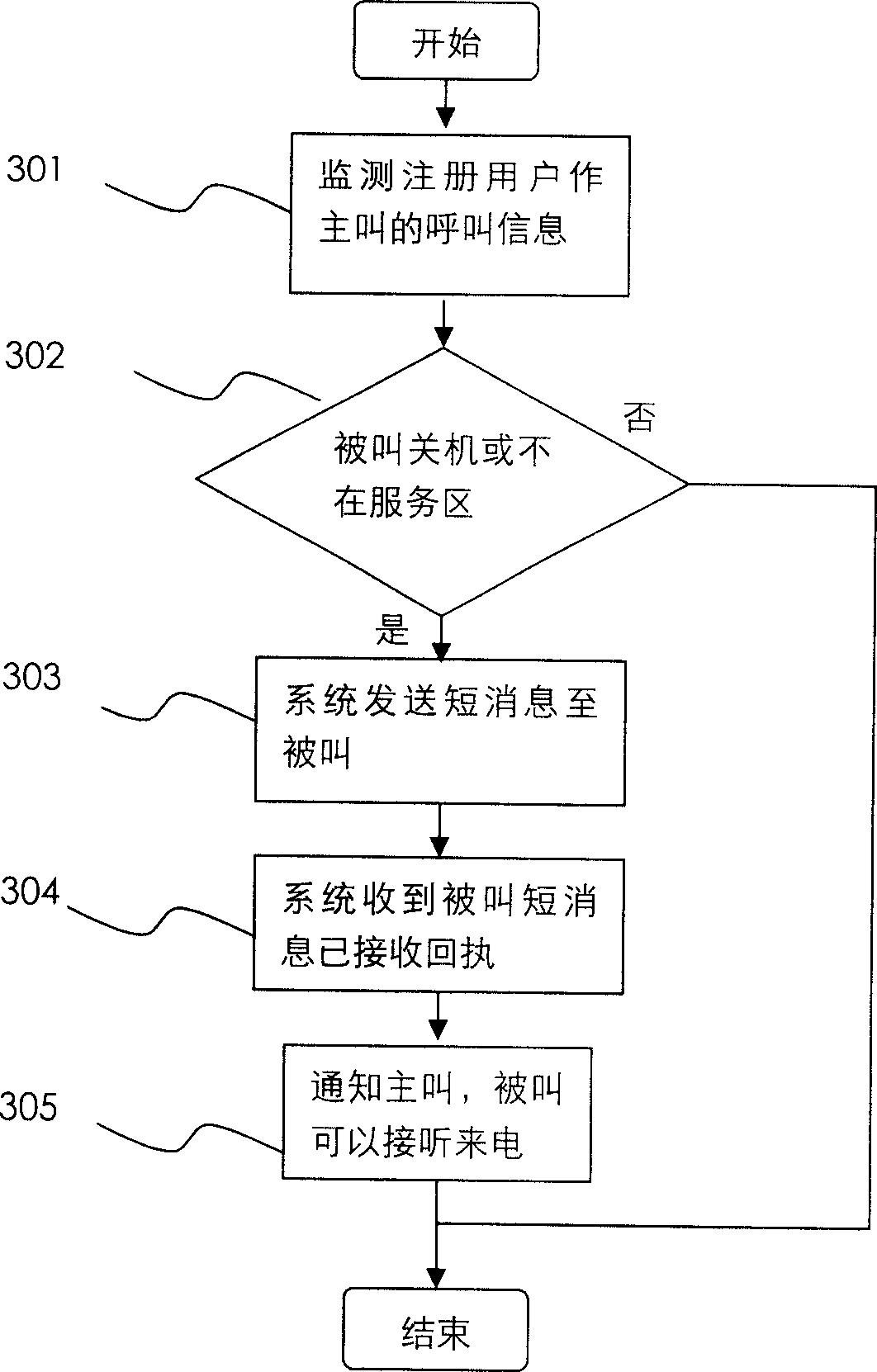
System and method for automatic prompting called party to turn on device or to be reachable from calling party
The method comprises: in case of not changing the using habits of user, by monitoring the call information from the registered user at calling party; when the call information is monitored to have the contents such as the called party shuts down or is not in service area, the system can actively make detection to find the information indicating the called part powers on or returns to service area, and actively prompts the calling party to initiate a call.
Owner:北京博为远景信息技术有限公司
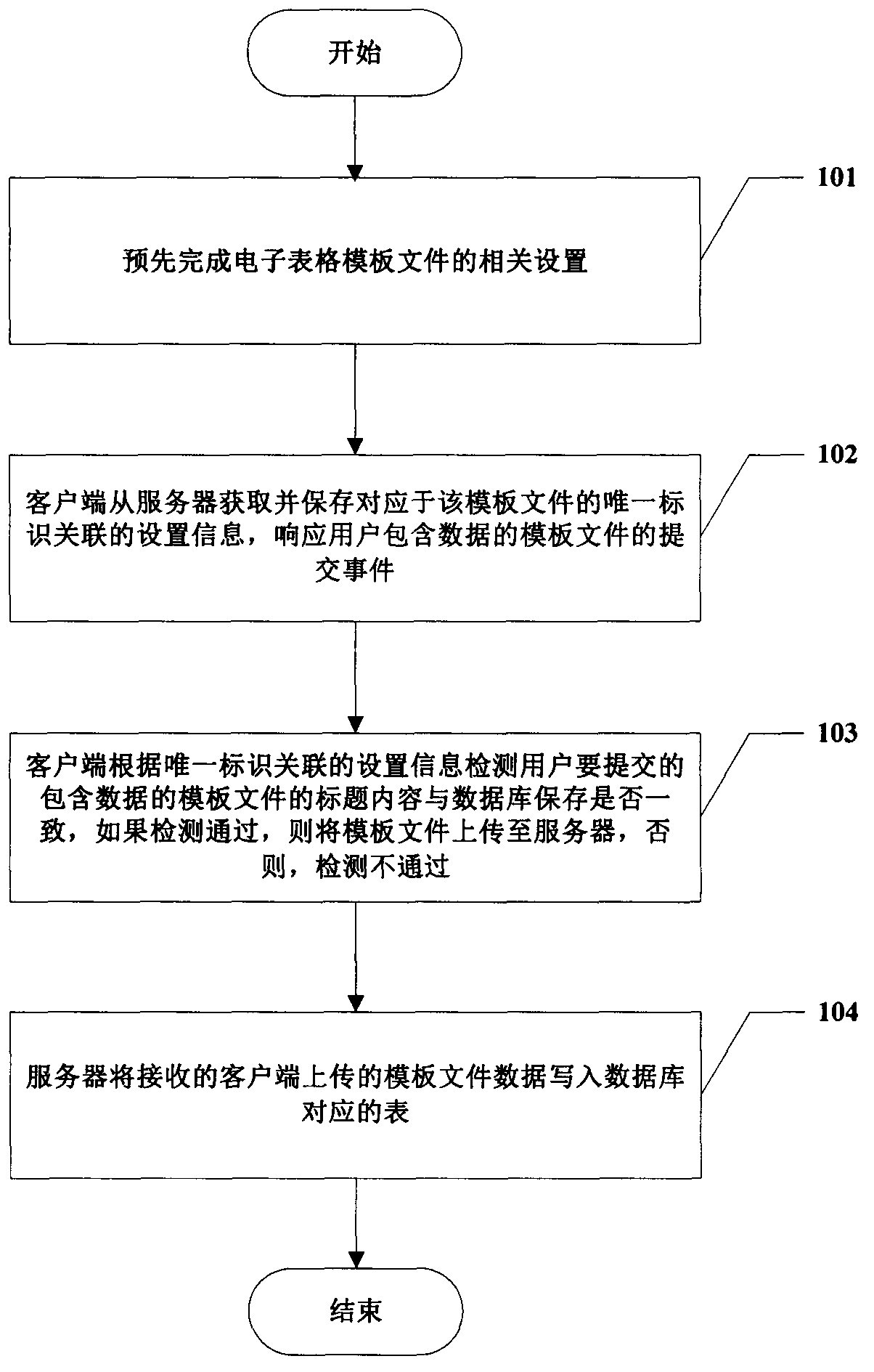
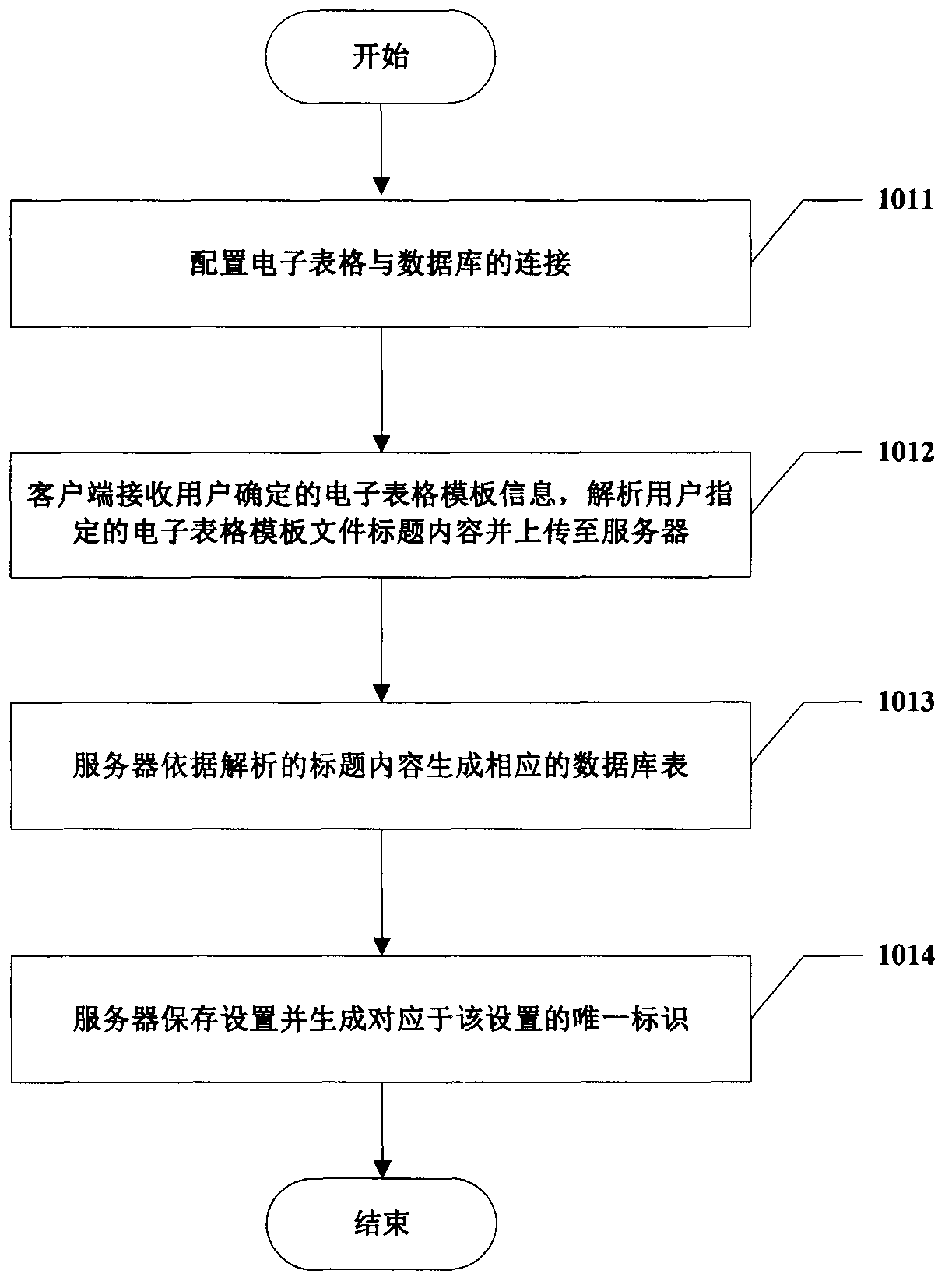
Spreadsheet data management method based on C/S mode
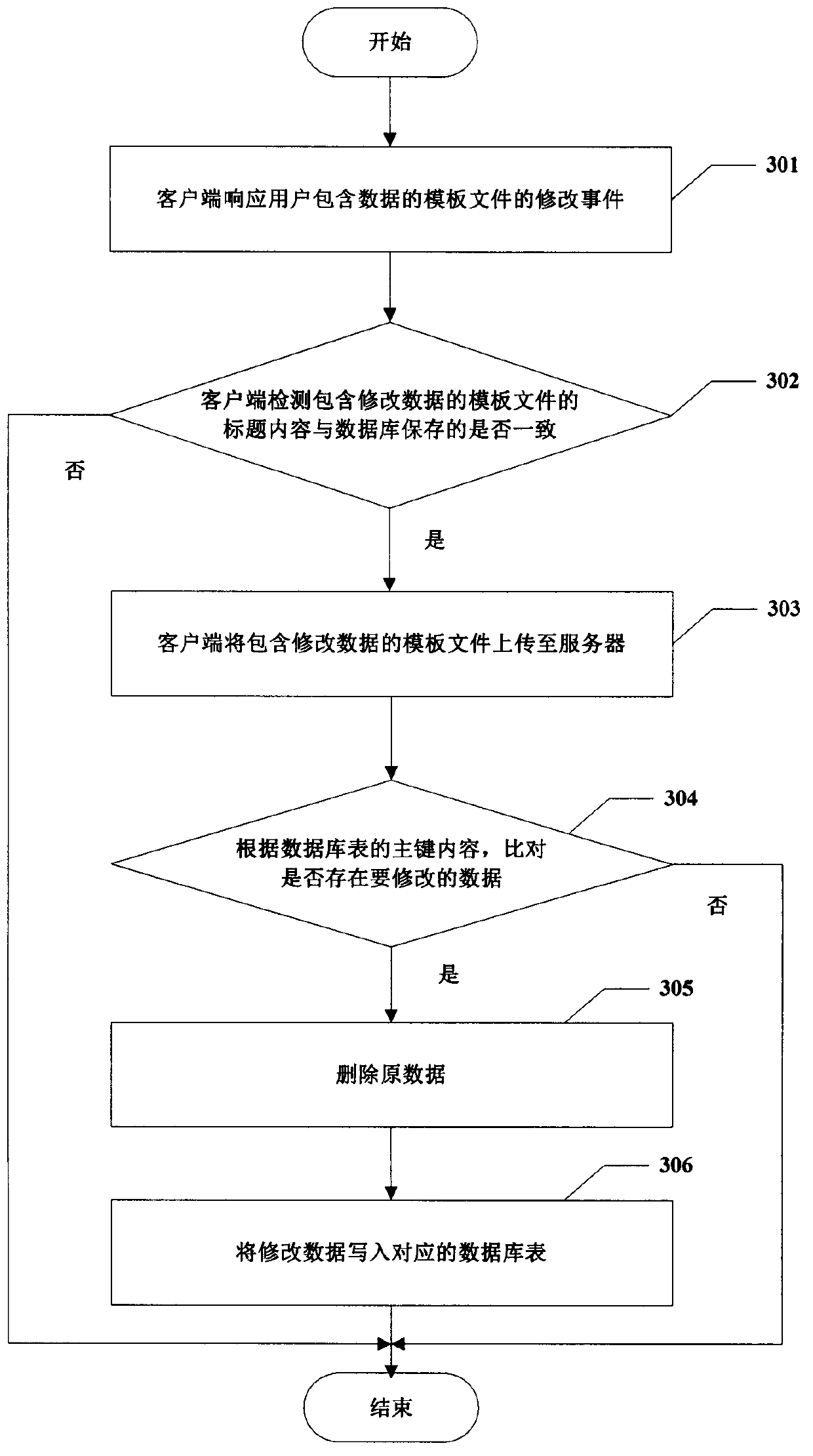
InactiveCN104239366ASolve the defects of scattered and difficult managementReduce the problem of slow loadingWeb data indexingFile/folder operationsData fileData management
The invention provides a spreadsheet data management method based on a C / S mode. The method includes the steps of S1, completing the related settings of a spreadsheet template file in advance; S2, by a client, acquiring the setting information associated with the unique identification corresponding to the template file from a sever, and saving the setting information; S3, by the client, detecting whether the title content of the template file which is about to be submitted by a user and contains data is consistent with the title content saved by a database or not according to the setting information associated with the unique identification; S4, by the server, writing the received template file data uploaded by the client into the corresponding table of the database. The method has the advantages that the spreadsheet template file data passing detection is managed through the database, and the defect that data is scattered and hard to manage when only the spreadsheet is used is overcome; data file data amount limitation of collected data is avoided; spreadsheet using habits of the user are unchanged, and friendly user interaction is achieved.
Owner:SUZHOU JINGYIHUI INFORMATION TECH
Intelligent sweeper
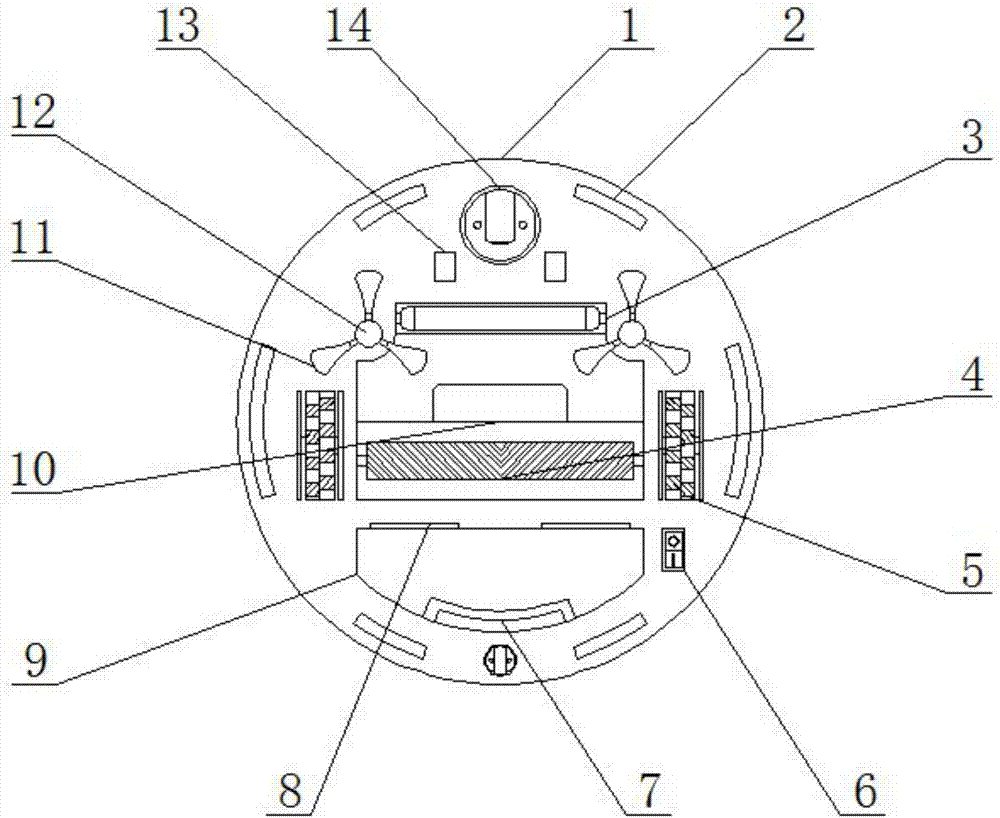
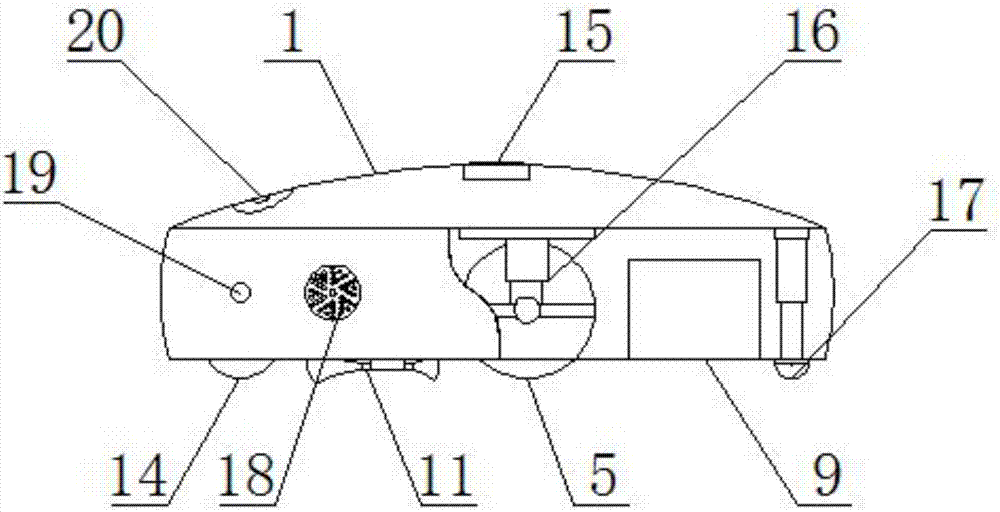
InactiveCN107361693AScientific and reasonable structureSafe to useSuction nozzlesElectric equipment installationEngineeringGround level
The invention discloses an intelligent sweeper which comprises a sweeper shell and a prompting lamp. A universal wheel is arranged in the middle of the top end of the inside of the sweeper shell, a fall-preventive sensor is arranged above the right side of the universal wheel, an automatic charging pole piece is arranged below the left side of the universal wheel, an ultraviolet sterilizing lamp is arranged below the automatic charging pole piece, and a dust lifting brush is arranged below the left side of the ultraviolet sterilizing lamp. The intelligent sweeper can enter low and small space in sofas or tea tables for sweeping; when coming across a step, an extensible rod extends, the front end of the intelligent sweeper goes up onto the step first, then the extensible rod contracts, a rear wheel also goes up onto the step, in this way, the intelligent sweeper can go up onto the ground higher for working; a camera on the sweeper can capture people's garbage throwing action, and if garbage is directly thrown onto the ground, a robot makes voice and turns on the prompting lamp to remind related personnel to pick up the garbage, so that people's habits can be changed, and the ground can be maintained clean.
Owner:合肥立腾信息科技有限责任公司
Paper calendar electronic generation method and device and electronic calendar generation method
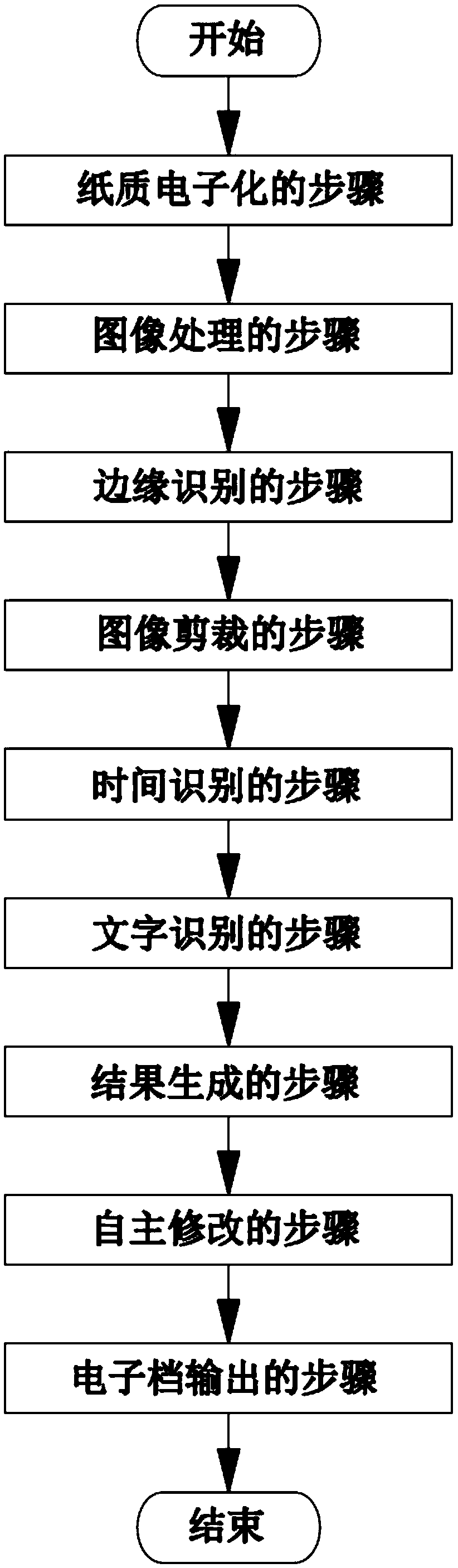
InactiveCN108805519ALow costImprove recognition rateCharacter and pattern recognitionSubstation equipmentElectronic documentText recognition
The invention discloses a paper calendar electronization method and device. The method comprises a paper electronization step, a binarization processing step, an edge recognition step, an image clipping step, a time recognition step, a text recognition step, a result generation step and an electronic document output step. According to the method, an APP in a smartphone and a special calendar are utilized, and analytical processing is performed on a collected image; by aid of an existing OCR (Optical Character Recognition) technology, the problem of low recognition rate is effectively solved; and through one piece of software, cost is lowered, and the purpose of efficient recognition is achieved. The device has the advantages of being high in recognition degree, low in cost, convenient to carry and good in user experience.
Owner:赵崇标
Charging detection circuit, charging box, communication device of earphone, and earphone
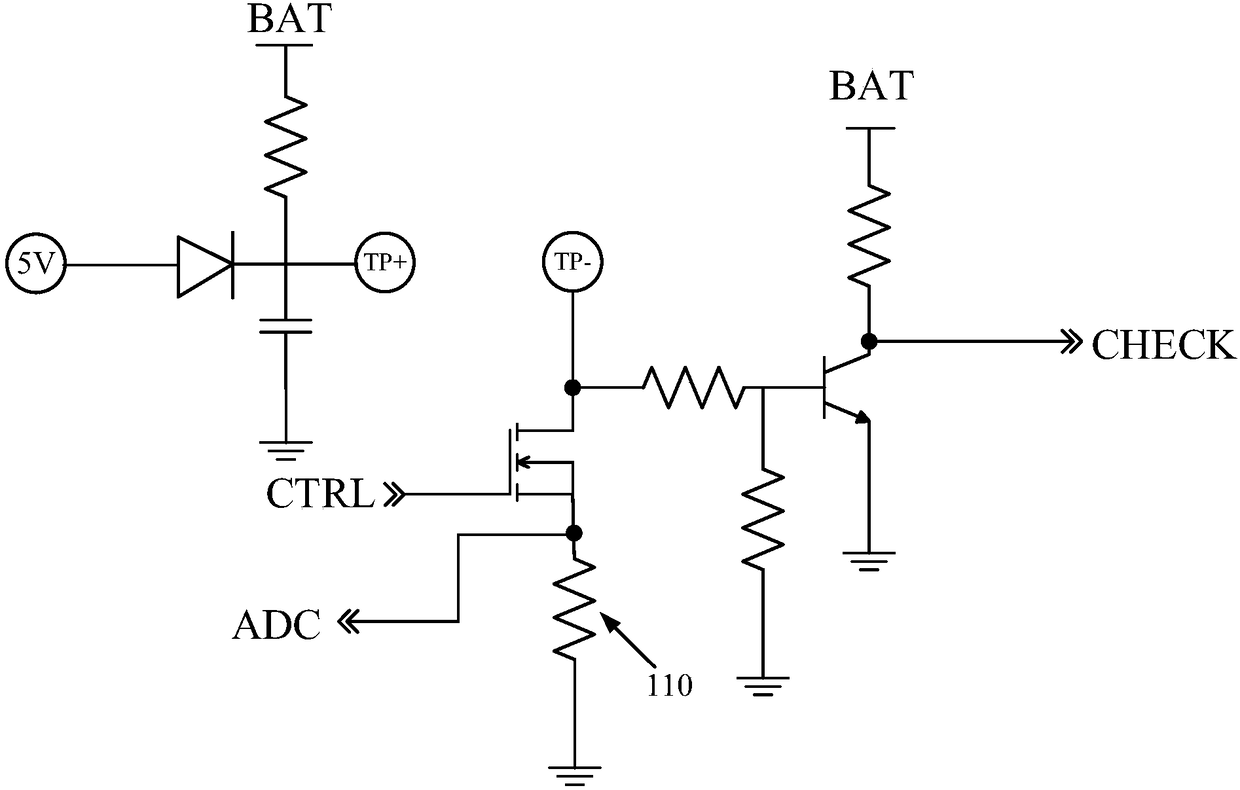
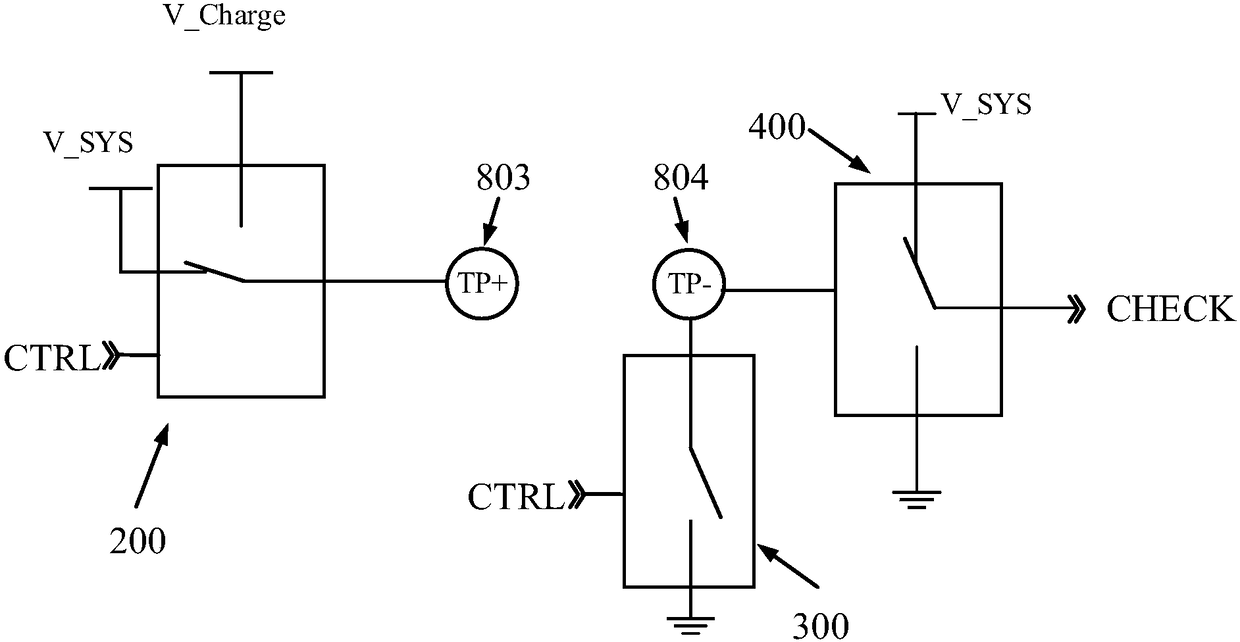
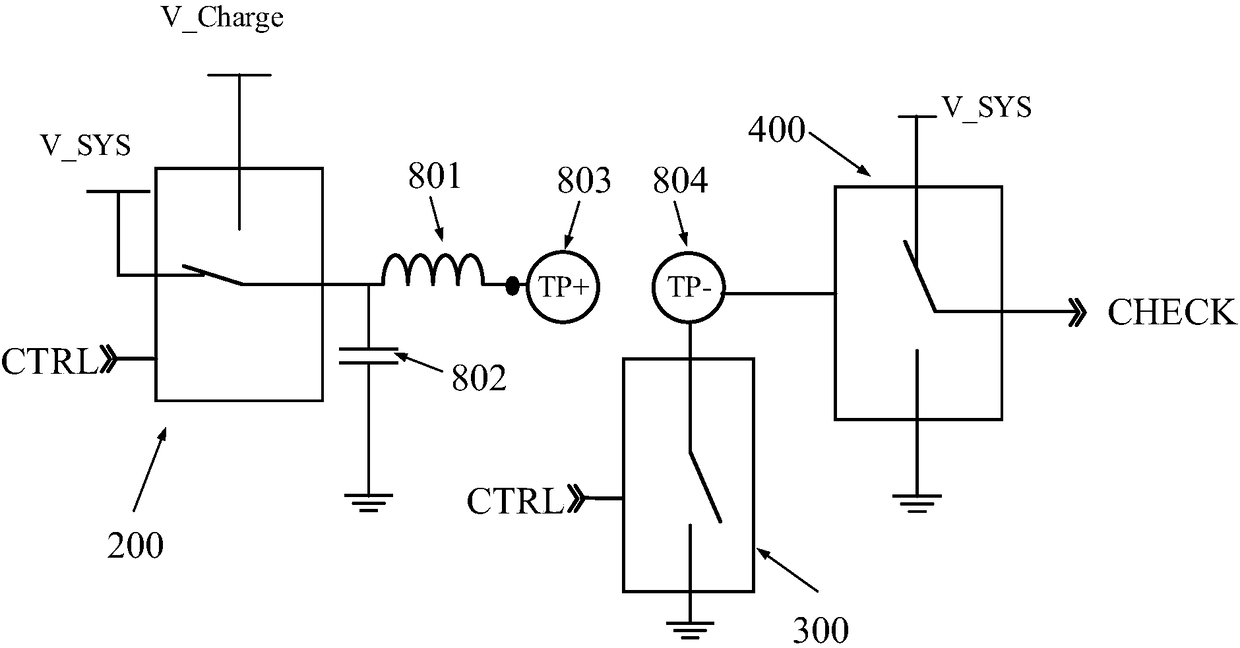
ActiveCN108352718AAccurately grasp the power statusChange habitsCircuit monitoring/indicationPower distribution line transmissionElectricityControl signal
Provided are a charging detection circuit, a charging box, a communication device of an earphone, and an earphone. The charging detection circuit comprises a first contact, a second contact, a switching circuit, a charging circuit, a detection circuit, and a first communication circuit. The switching circuit is connected with the first contact. The charging circuit is connected with the detectioncircuit through the second contact. The first communication circuit is connected with the first contact and / or the second contact. Supply voltage of the first contact is system voltage. When the firstcontact and the second contact contacts with a first device, the detection circuit triggers the first communication circuit to obtain electric quantity states of the first device. When the electric quantity state is in under-voltage stage, the control signal controls the switching circuit to connect the first contact with the charging voltage, to make the charging circuit charge the first device.In the embodiment, through information interaction between the first communication circuit and the first device, electric quantity states of the first device can be accurately known.
Owner:SHENZHEN WEITONGBO TECH CO LTD
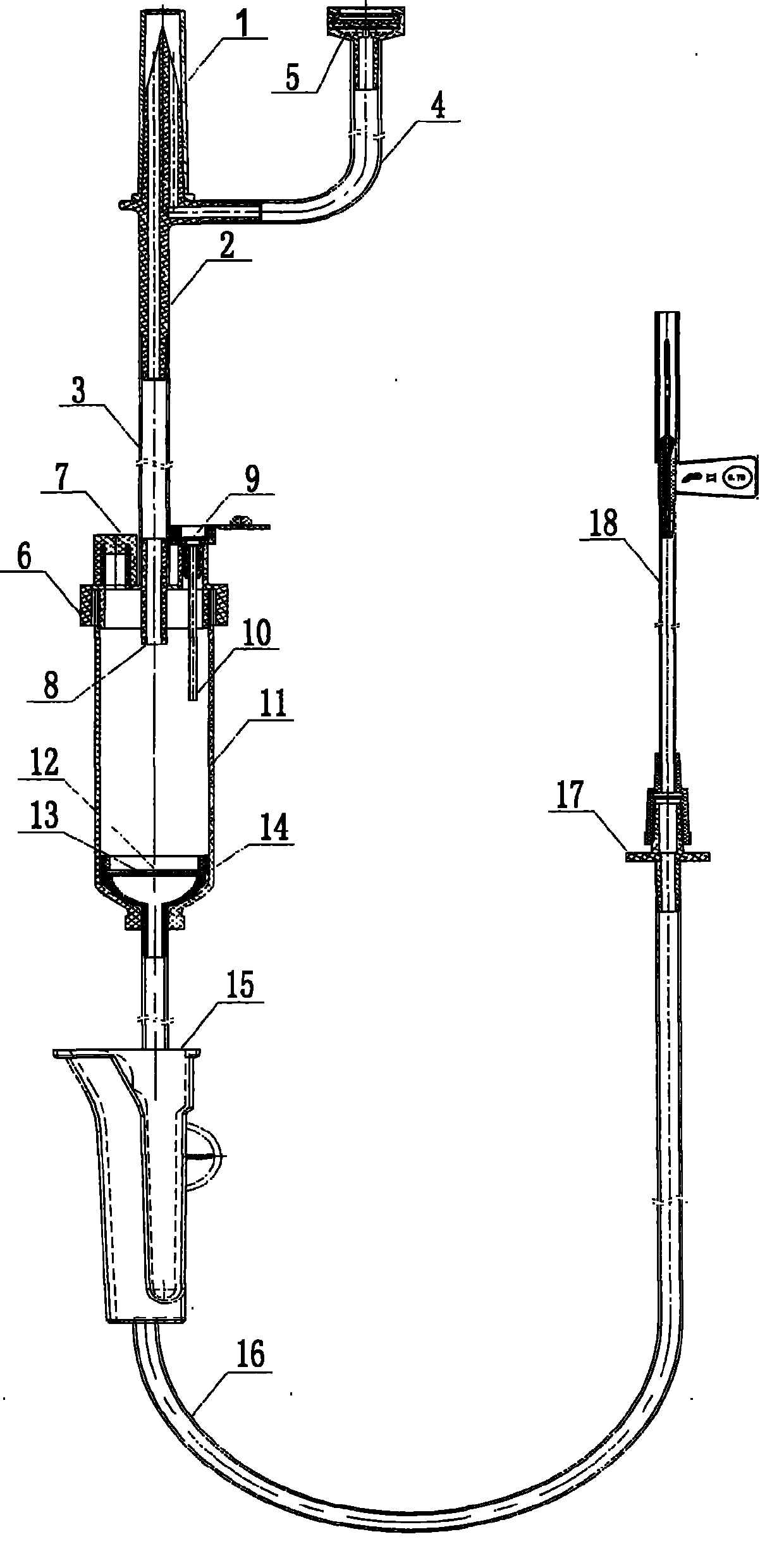
Liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus
The invention discloses a liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus. A dropping funnel cover (2a), an exhaust hole (2b), an exhaust filtering hole (2c) and an air filtering hole (2d) are in injection molding on a bottle stopper puncture device (2), an air filtering membrane (4) is installed inside the air filtering hole (2d) and sealed by an air filtering cap (3), an automatic exhaust device (5) is installed on the dropping funnel cover (2a), a dropping funnel (6) is connected at the bottom of the dropping funnel cover (2a), an automatic liquid-stopping device (7) is installed on the bottom face (6a) inside the dropping funnel, a liquid dropping opening (6b) is formed in the bottom of the dropping funnel (6) in an injection molding mode, one end of a long infusion catheter (9) is connected with the liquid dropping opening (6b), the other end of the long infusion catheter (9) penetrates through a flow regulator (10) to be connected with a medicine liquid injection part (11), a flareless fitting (12) and a vein needle (13), and the safe infusion apparatus is integrally formed. According to the liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus, automatic exhaust is achieved, liquid medicine automatically stops flowing, the exhaust operation steps are simplified, working intensity is relieved, the structure is simple, and the liquid-stopping tank-type automatic exhaust liquid-stopping infusion apparatus is safe and reliable.
Owner:HUAIAN CITY HENGCHUN MEDICAL PROD
Intuitive timer
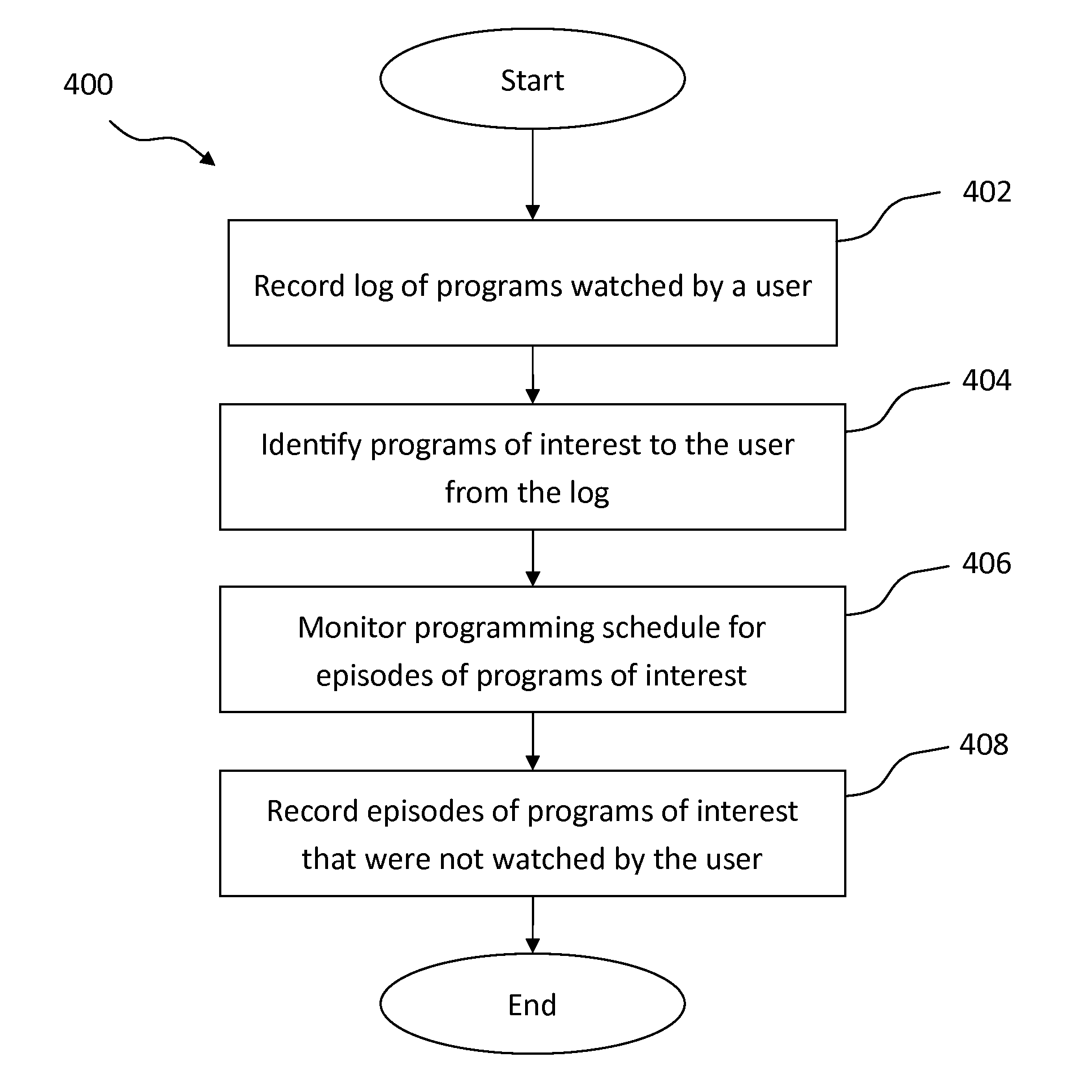
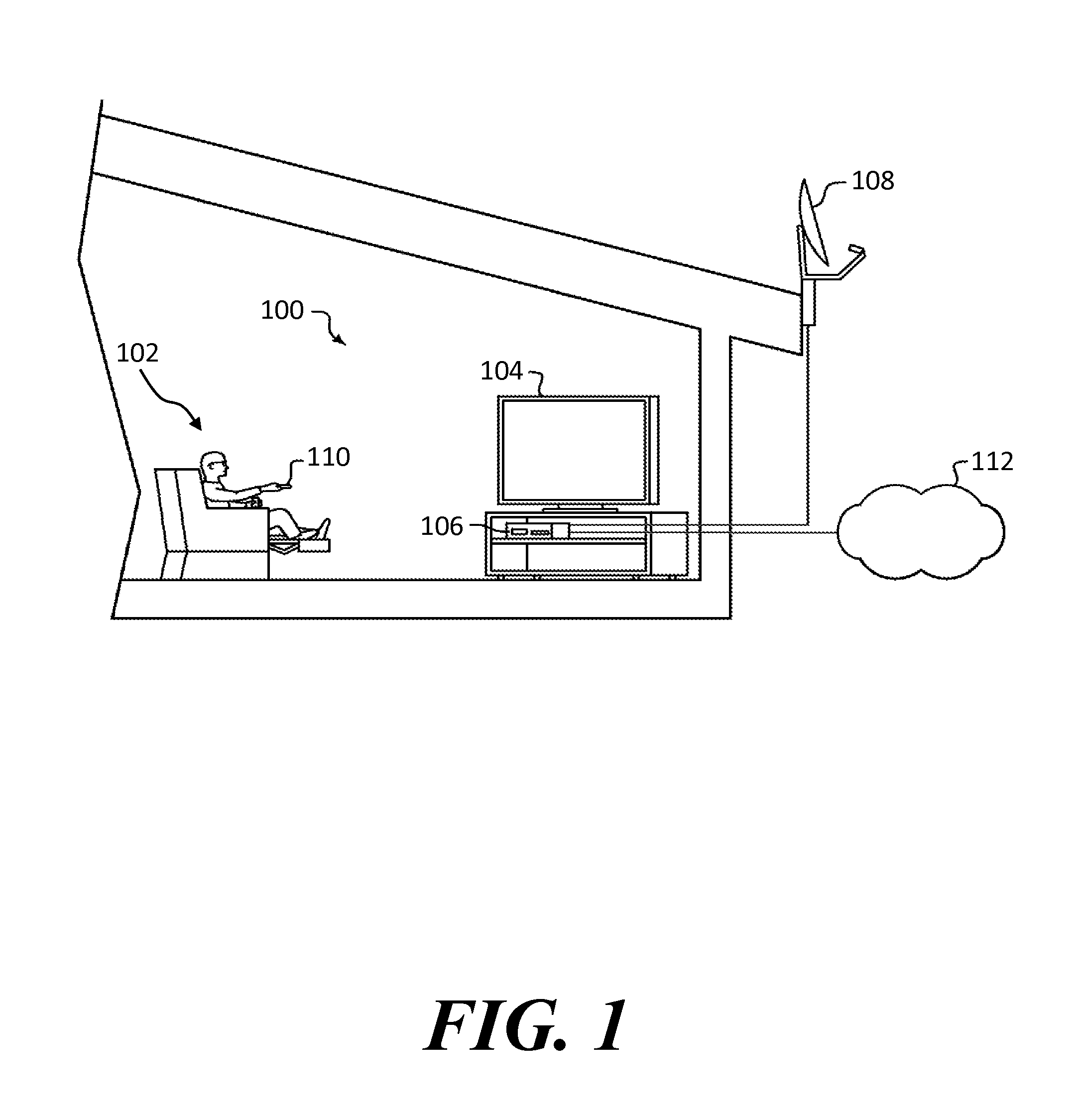
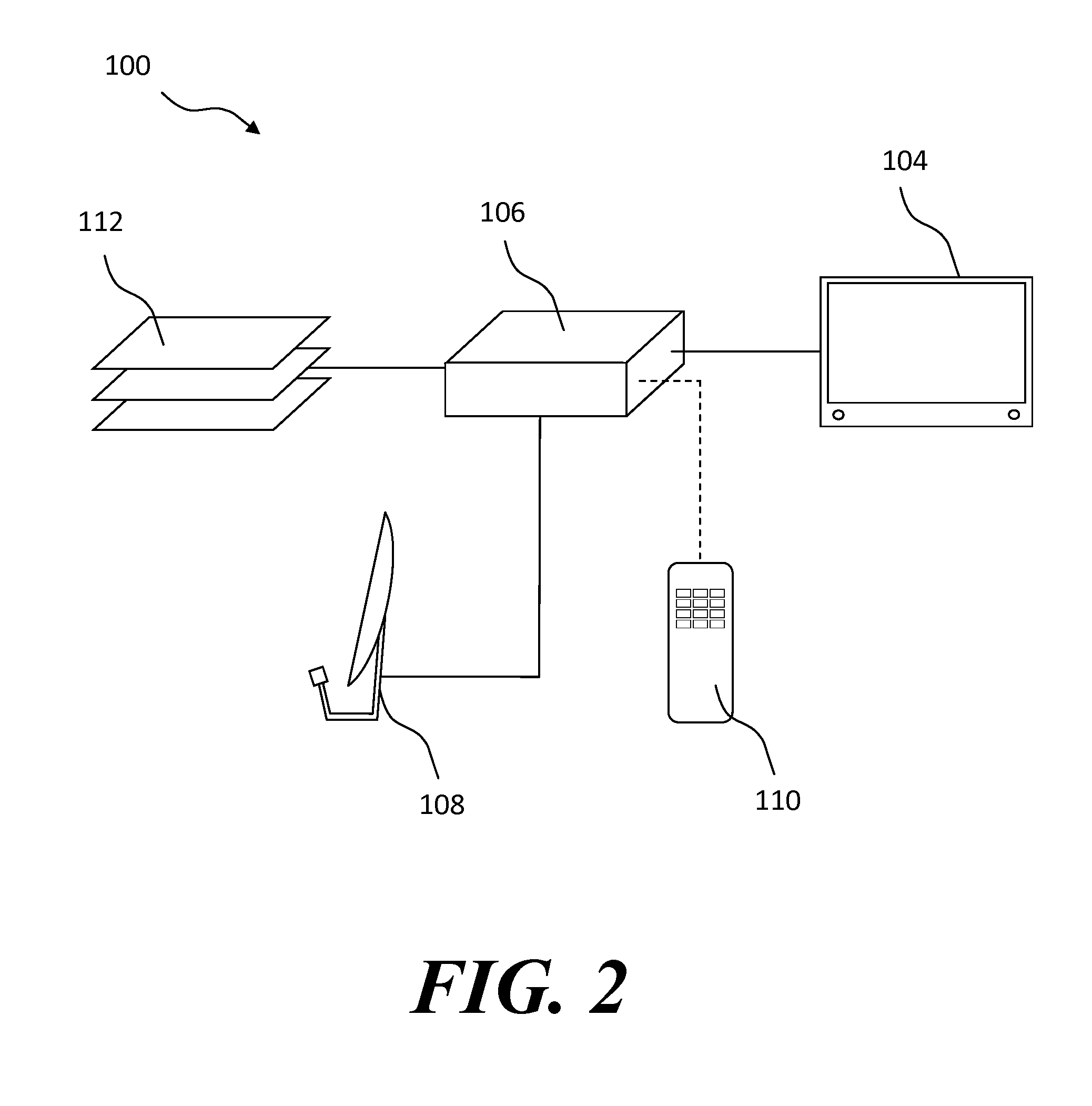
ActiveUS20160142761A1High interest levelChange habitsTelevision system detailsColor television detailsUser inputHabit
A method for determining a program of interest to a user and setting a timer to automatically record the program of interest. The method can interpret user inputs and watching habits, such as whether or not a user is present, to determine if a program being displayed for a user is a program of interest to the user. Once a program of interest is identified, a timer is set to record the next scheduled broadcast of the program of interest for the user. The user can then be notified, either before or after the timer is activated, that the automatic timer was set to record the program, and the user given the option of whether or not to keep the timer or recording.
Owner:DISH TECH L L C
Service switching method and system
ActiveCN101166300ARealize switching functionChange habitsNetwork traffic/resource managementRadio/inductive link selection arrangementsSwitching signalMobile station
The method for switching services includes steps: step S102, in procedure of voice call, when receiving signal tone for switching services from equipment at called user, the mobile station at the called party carries out service negotiation and hard switching through the base station controller at the called party to establish connection to network intercommunication function unit (NIFU) at the called party; step S106, through receiving in-band message, the base station controller at calling party starts switching services, establishes connection between the calling party and NIFU at the calling party so as to complete switching services. The invention also discloses the system for switching services. The invention also discloses another method and system for switching services. Without changing habit user uses, the invention implements function for switching IWF services between voice service and facsimile service so as to be convenient for user to do operations.
Owner:HUAWEI TECH CO LTD
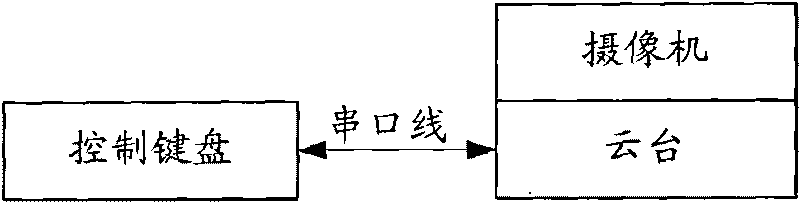
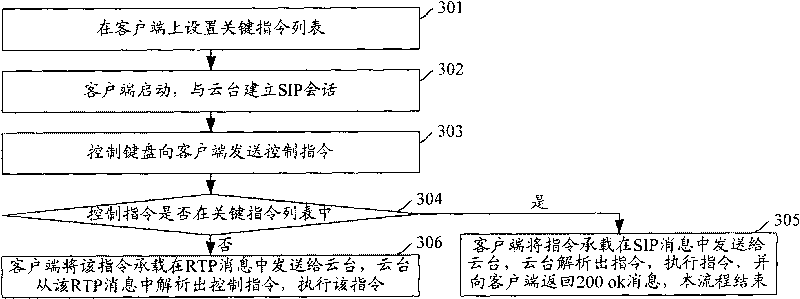
Holder controlling method, system and client
ActiveCN101729564AGuaranteed real-timeGuaranteed reliabilityTelevision system detailsColor television detailsComputer hardwareClient-side
The invention discloses a holder controlling method, system and client. The interface between the client and holder supports SIP and RTP, key instruction is set on the client, and the method includes: the client and holder establish SIP session; a control keyboard transmits a control instruction to the client, the client receives the control instruction, if the instruction is found to be the key instruction, the control instruction is contained in an SIP message to be transmitted to the holder, otherwise, the control instruction is contained in an RTP message to be transmitted to the holder; and the holder executes the control instruction. The invention ensures the real time and reliability of holder control.
Owner:GUANGDONG VIMICRO
Apparatus and method for a telematics service
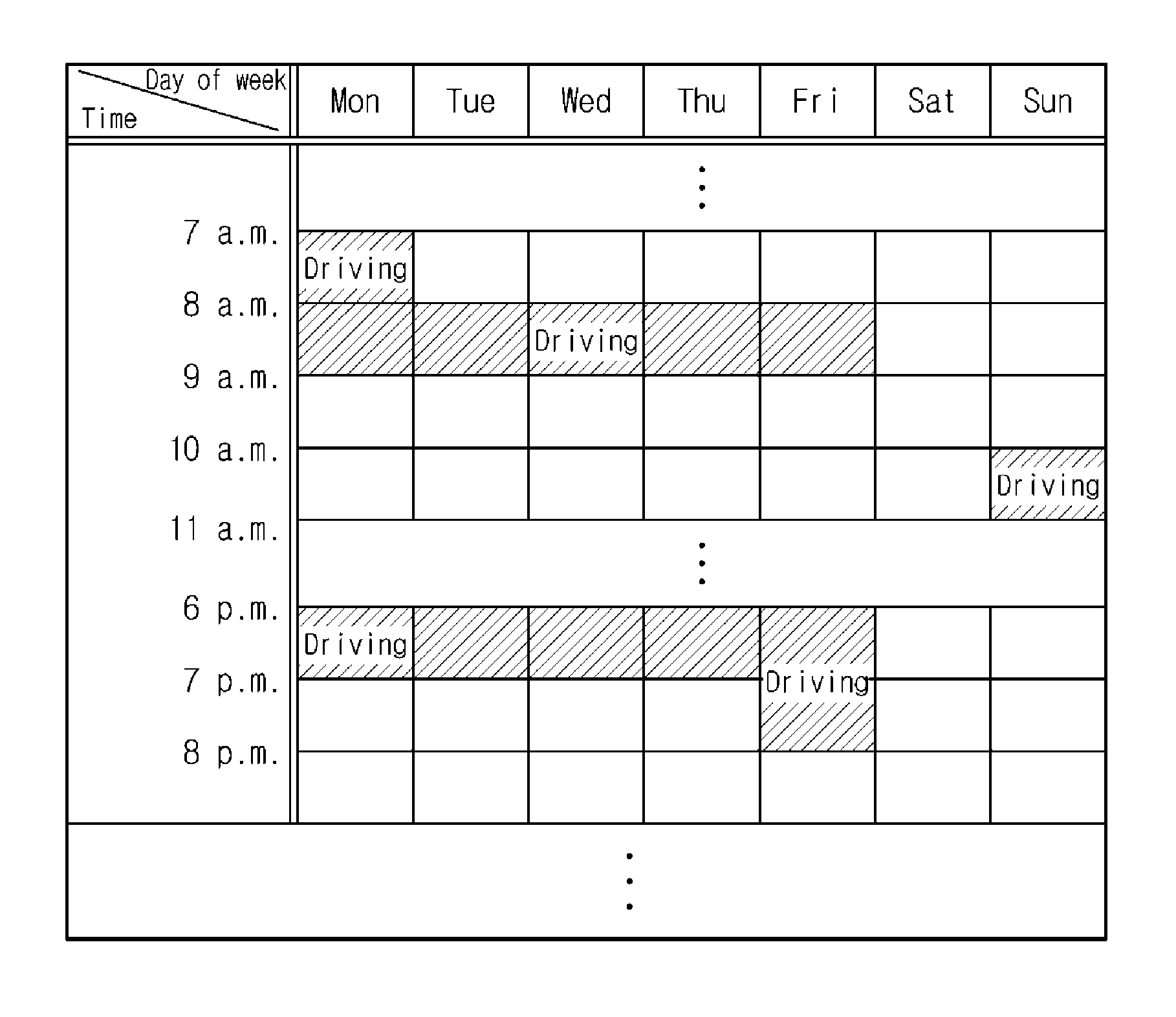
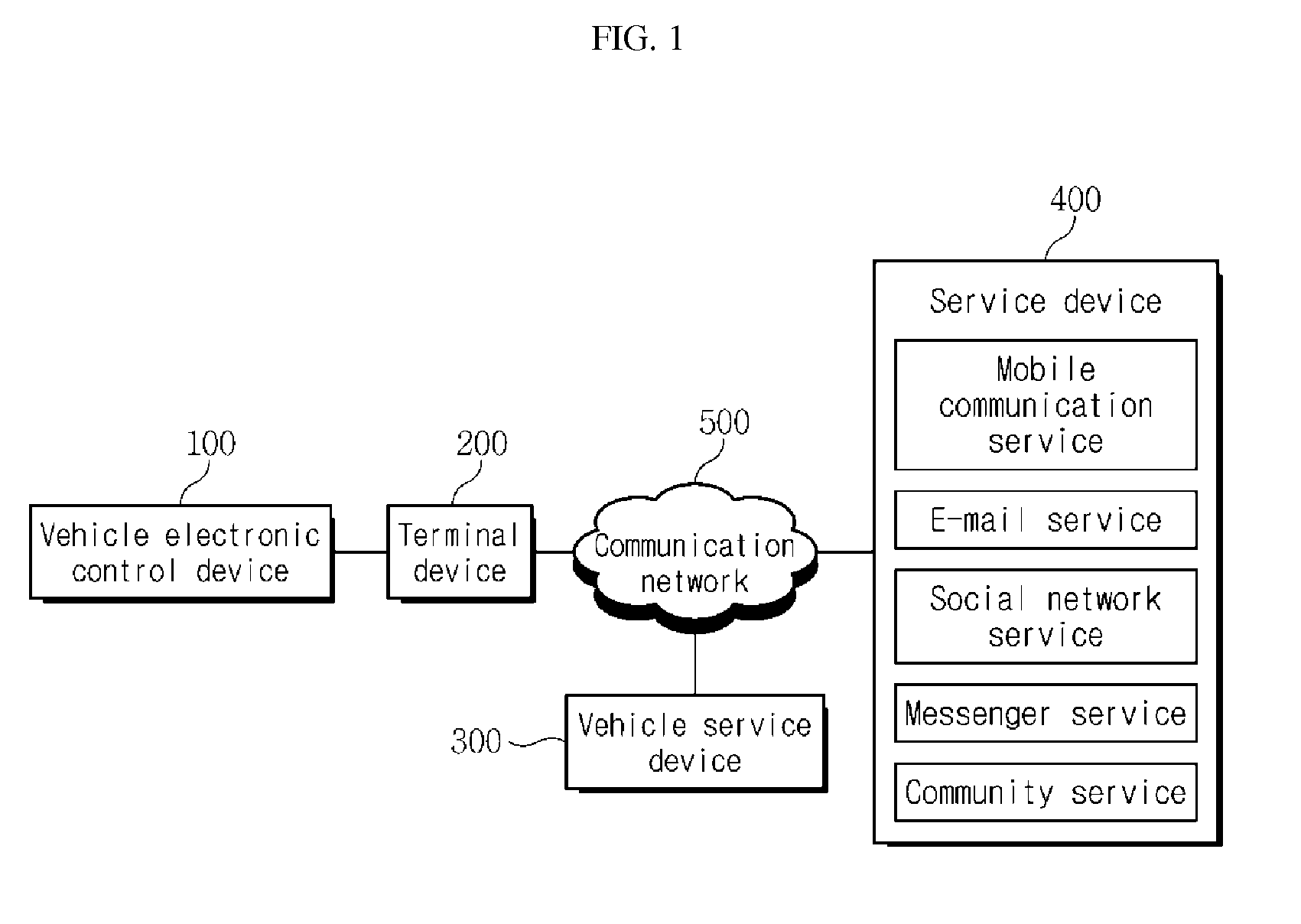
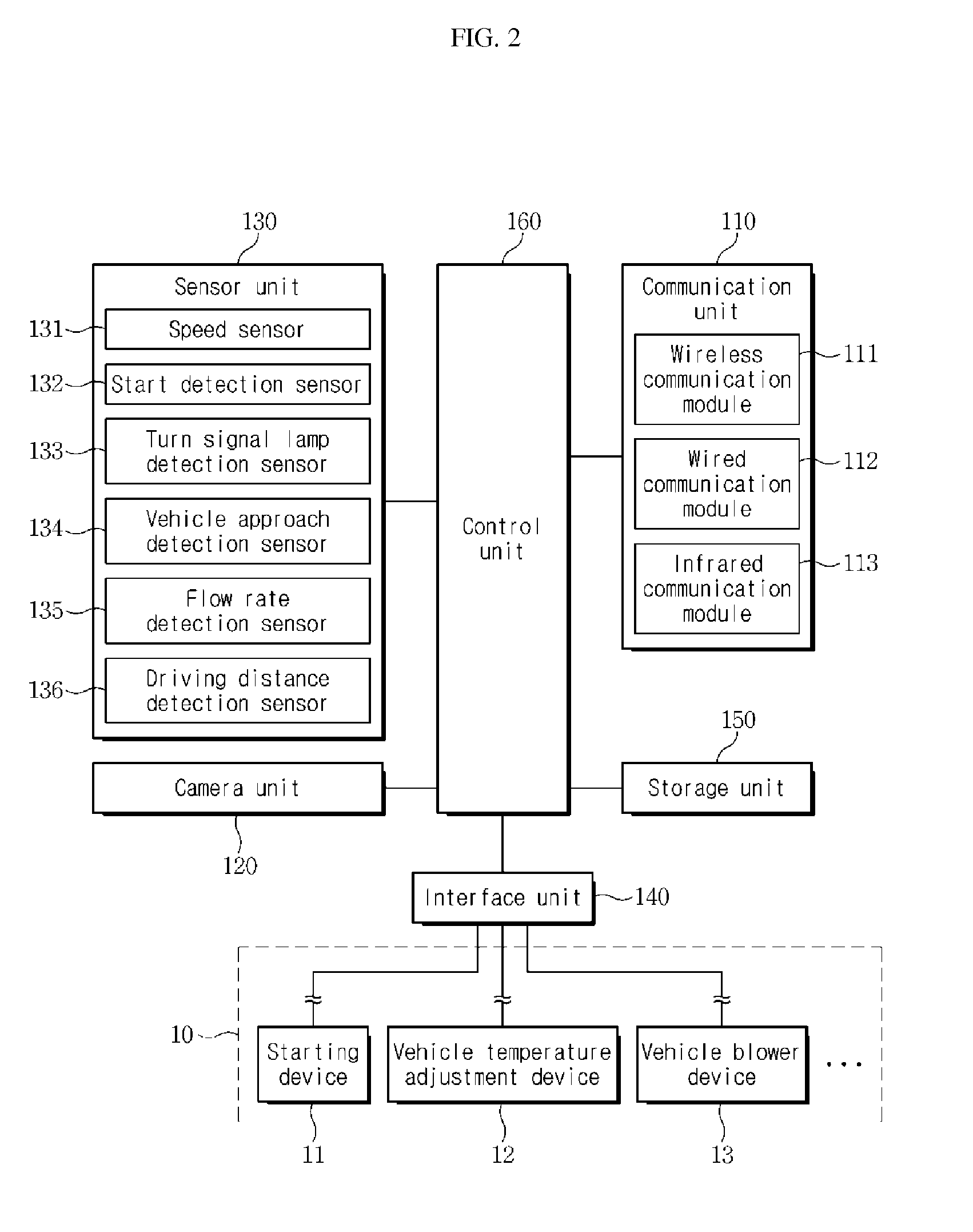
ActiveUS9073405B2Low costEasily check and createAir-treating devicesOperating modesTemperature controlStart time
A telematics service system and a terminal predict a driving start time of a vehicle based on a driving pattern of a user, compare status information of the vehicle and a set temperature before the predicted driving start time of the vehicle, and generate a temperature control signal so that an interior temperature of the vehicle reaches the set temperature. The terminal is fixed inside the vehicle. A vehicle electronic control device attached to the vehicle collects the status information of the vehicle, provides the collected information to the terminal device, and controls a temperature adjustment device of the vehicle in accordance with the temperature control signal of the terminal device to adjust the interior temperature of the vehicle to reach the set temperature.
Owner:T MAP MOBILITY CO LTD
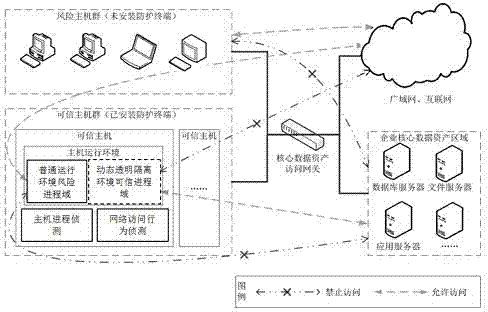
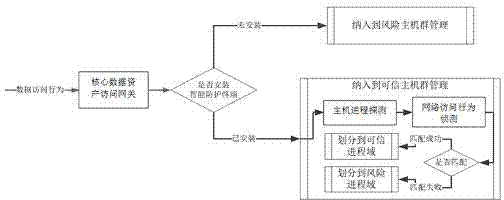
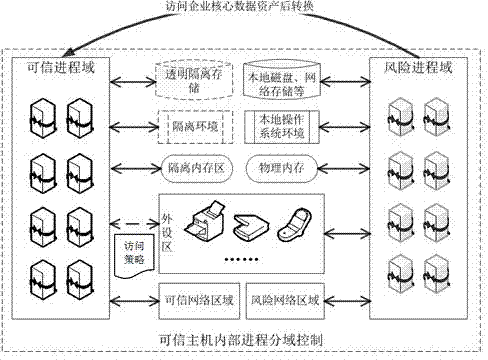
Dynamic transparent isolation protection based enterprise data asset protection method
ActiveCN104753924AReduce dependenceChange habitsResourcesTransmissionSecurity managementManagement strategy
The invention discloses a dynamic transparent isolation protection based enterprise data asset protection method. The dynamic transparent isolation protection based enterprise data asset protection method comprises the steps that user mainframe groups are into a risk mainframe group and a trusted mainframe group, wherein the trusted mainframe group is provided with a safety protection terminal, and enterprise core data asset can be accessed; the risk mainframe group cannot be accessed; progresses of mainframes of the trusted mainframe group are divided into risk progress domains and trusted progress domains, and the risk progress domains are converted into trusted progresses when sensitive data asset is accessed on purpose; transparent isolation protection processing is conducted on storage resources depended by the progresses to run, local OS environments and the like in the trusted processes, meanwhile a network and external access are under the control of a safety management strategy, and the risk progresses cannot access any data of a transparent isolation protection environment. By means of the dynamic transparent isolation protection based enterprise data asset protection method, the trusted processes and the risk progresses coexist, data leakage is avoided, local computing resources are applied to the maximum extent, and dependency on the network is reduced. The dynamic transparent isolation protection based enterprise data asset protection method has good adaptability and robustness.
Owner:南京盛泰惠智能科技有限公司
Lighter with simple safety device
The invention relates to a lighter with safety device, which comprises a frame, a wind-baffle cover, a outlet valve, a air compression plate, a fuel storage chamber, a piezoelectric device (electric) 2 for generating electric spark; a press key 1, a support flexible element 3 under the piezoelectric device, and a movable switch 23 opposite to the piezoelectric device to avoid the motion of piezoelectric device. When the movable switch is free, via the retraction of support flexible element 3, the piezoelectric device 2 can not generate electric spark; when the movable switch is pressed, the part of piezoelectric device that near the support flexible element is clamped, then pressing the press key to generate electric spark via the piezoelectric device.
Owner:黄家军
Fixing structure for vehicle seats
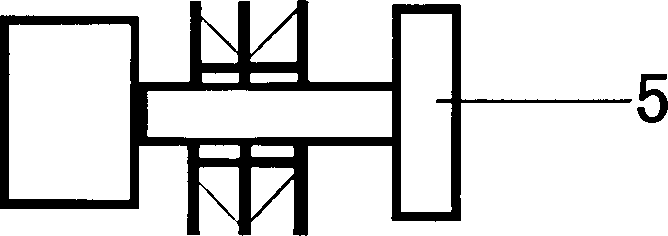
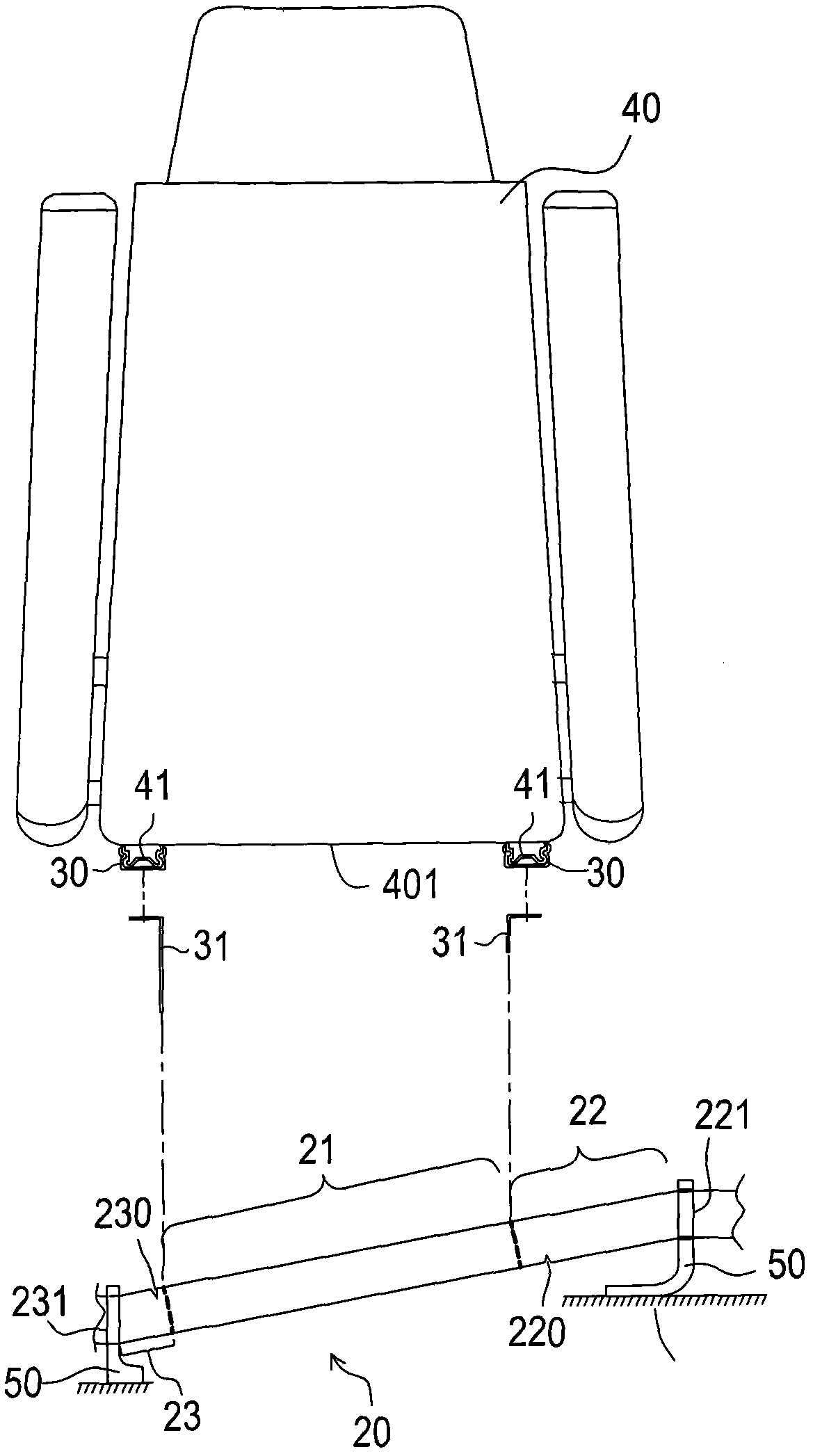
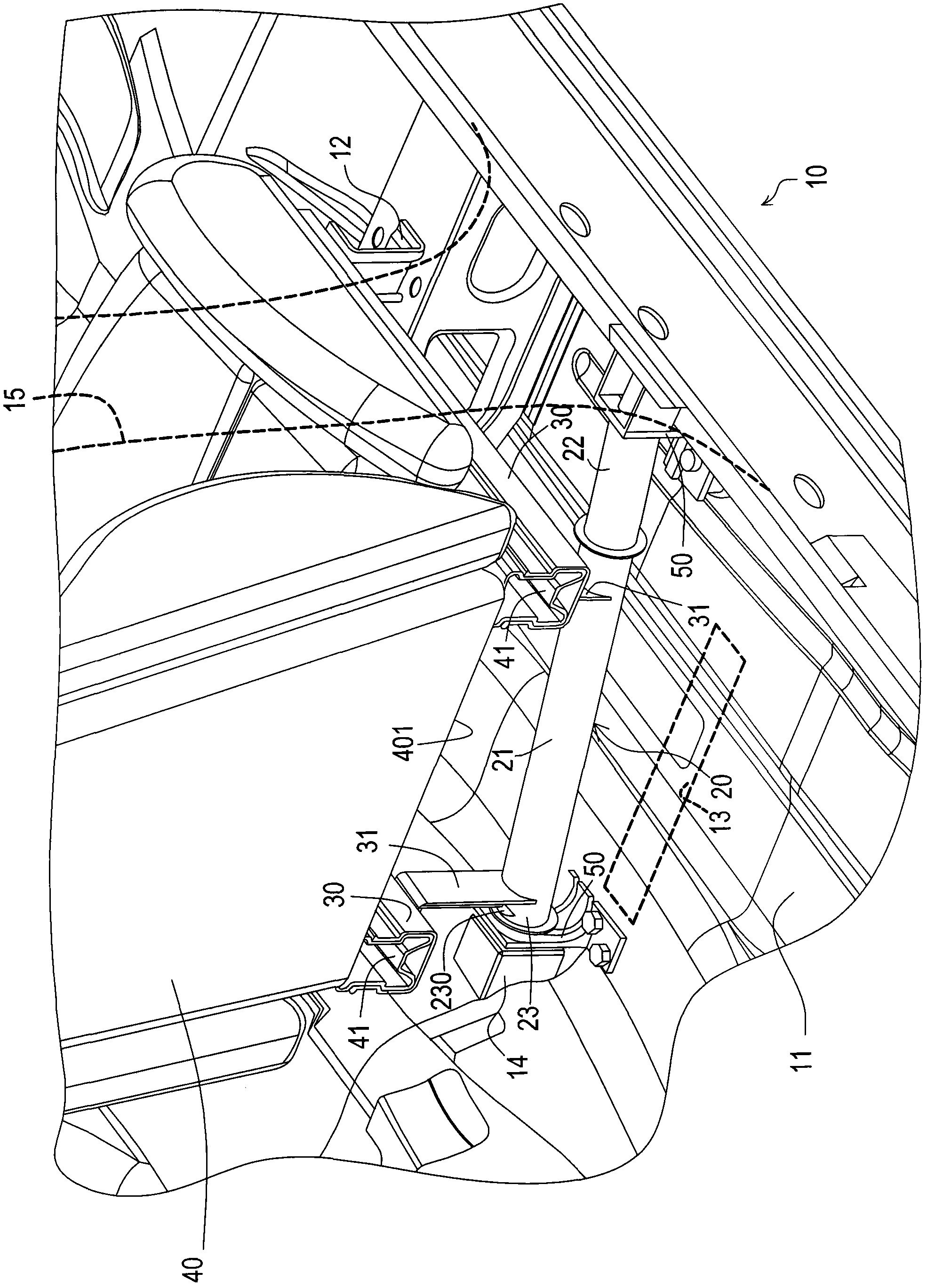
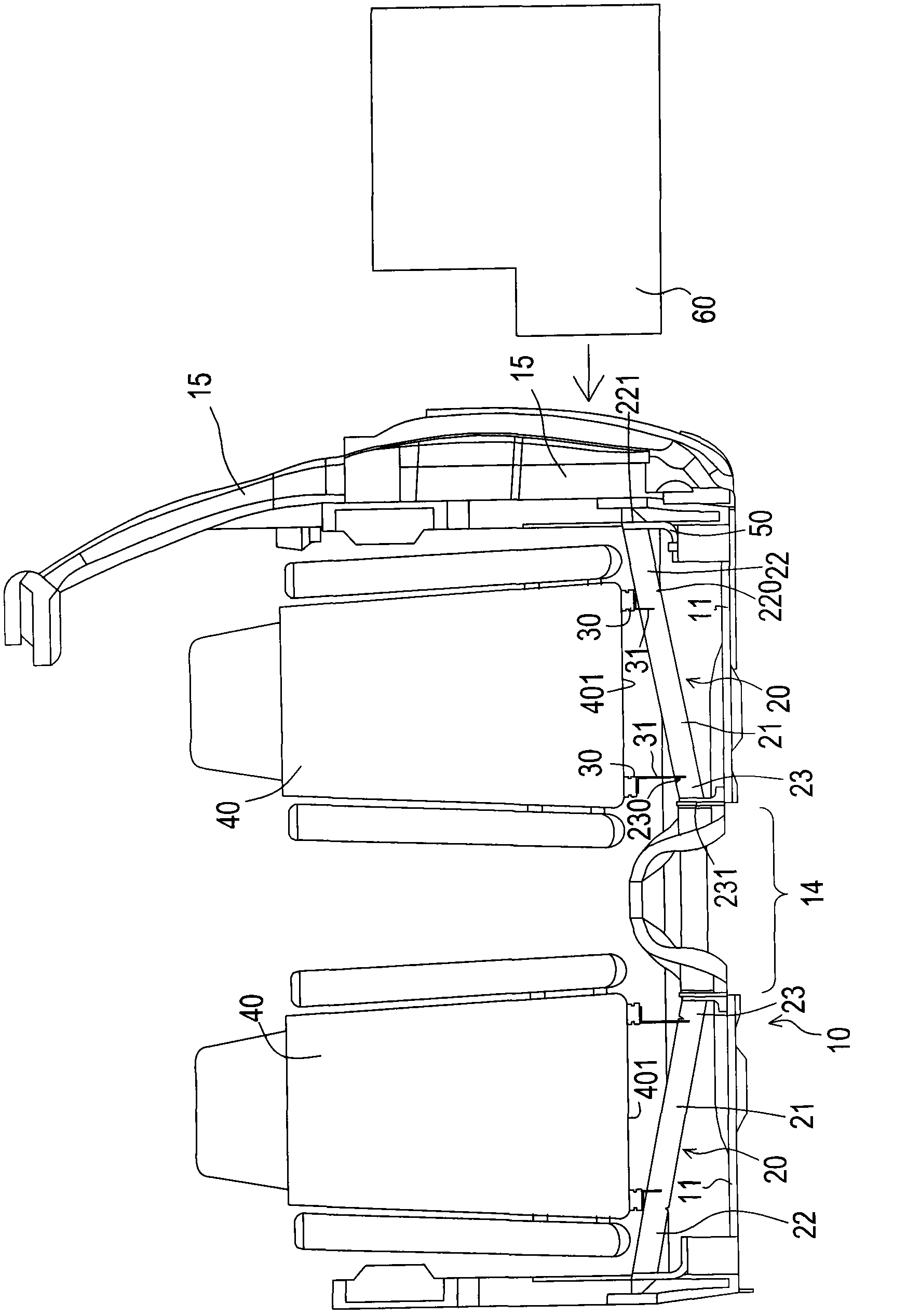
A fixing structure for a vehicle seat comprises a force transmission rack, seat slide tracks and a seat, wherein the force transmission rack is obliquely spanned above a rear looking area of the seat and is provided with a middle section, a first outer side section and a second outer side section, wherein the first outer side section is provided with a first end part at the tail end, and the second outer side section is provided with a second end part at the tail end; the first end part is connected with an upright post; the second end part is connected with a central passage; the horizontal height of the first end part is higher than that of the second end part; the seat slide tracks, which are parallel to each other, are horizontally fixed at the middle section and the front fixing points of the seat on the side corresponding to the seat slide tracks; a pair of sliding blocks is arranged at the bottom of the seat and are correspondingly sleeved on the seat slide tracks, so that the seat can move forwards and backwards along the seat slide tracks through adjusting the positions of the seat locked on the seat slide tracks.
Owner:METAL INDS RES & DEV CENT
Intelligent seal management system
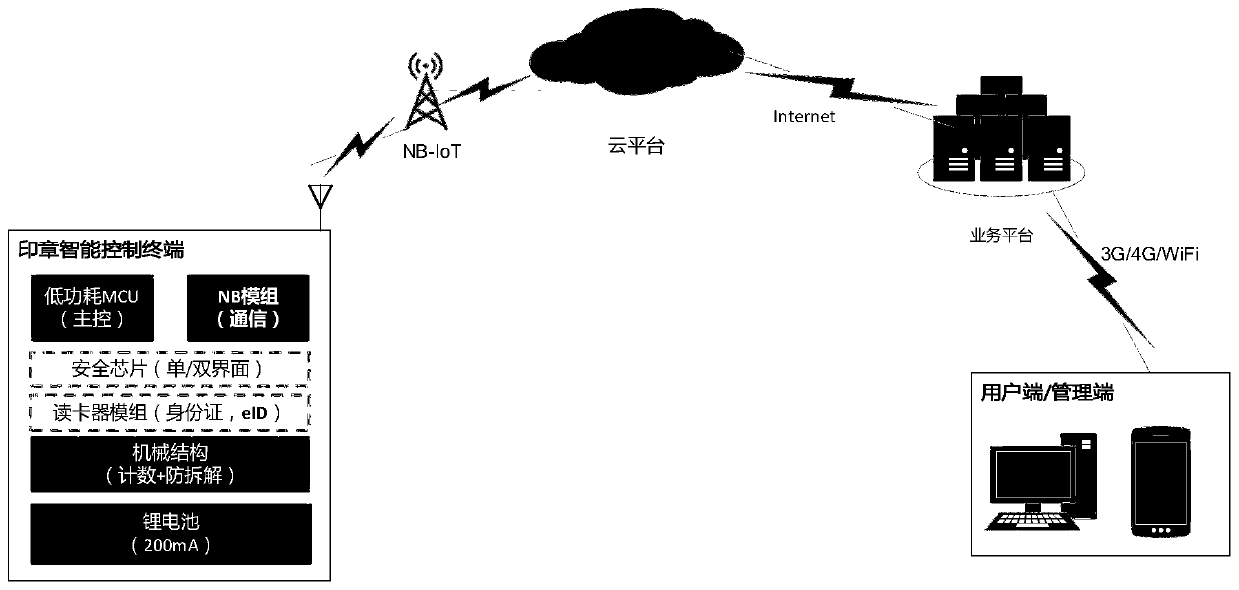
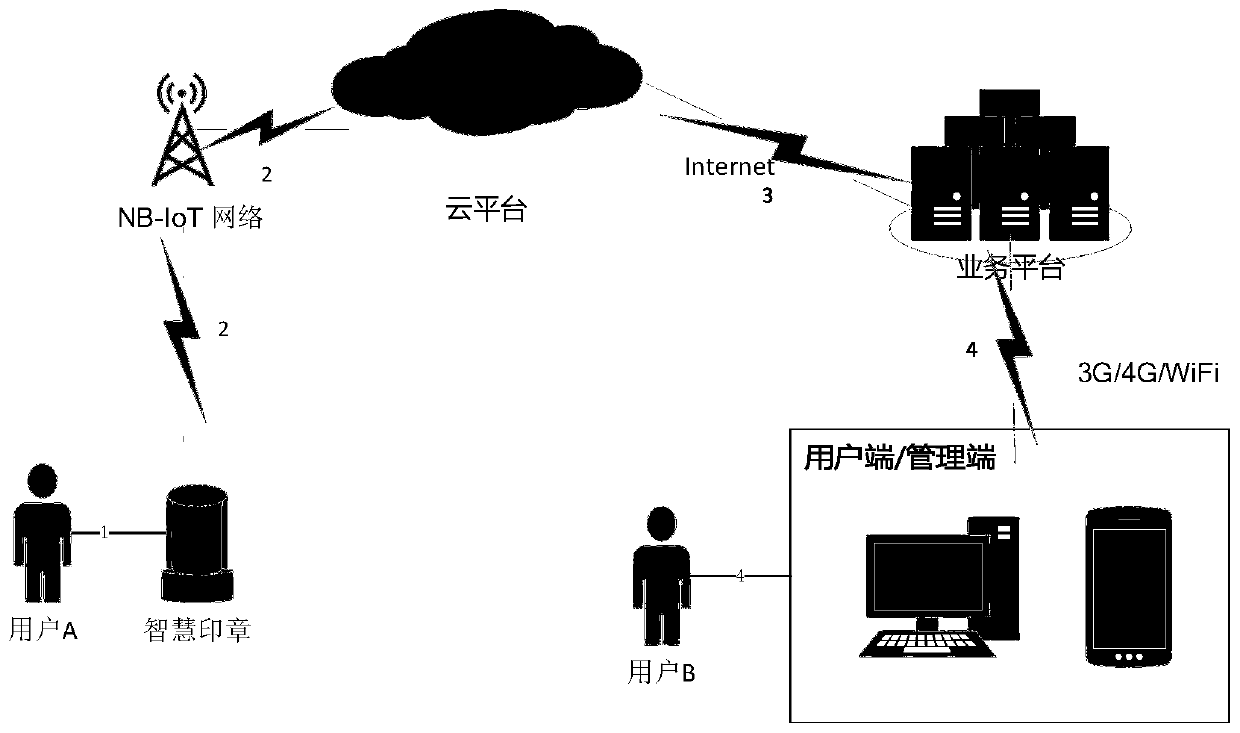
The invention provides an intelligent seal management system which comprises an intelligent seal control terminal, a cloud platform and a user terminal. The intelligent seal control terminal is used for receiving the seal use information and ensuring that the seal use information is automatically and regularly reported to the cloud platform in real time; Wherein the intelligent seal control terminal communicates with the cloud platform through the NB-IoT network to complete automatic recording of seal use information and cloud automatic backup; a cloud platform which is used for storing, processing and inquiring various data of the seal, providing value-added data service and deploying a cloud application; wherein the cloud platform updates the use information of the seal to the user database through the business platform; and a user terminal which is used for providing an information query and seal management interface; the cloud is logged in through the user terminal to inquire the information record of the seal. By adopting the Internet of Things technology, the cloud computing technology, the big data technology and the mobile terminal technology, a client can monitor the usingcondition of the seal, and value-added service is provided for the client through big data analysis.
Owner:张鹏
Barreled liquefied petroleum gas distribution system and barreled liquefied petroleum gas distribution method
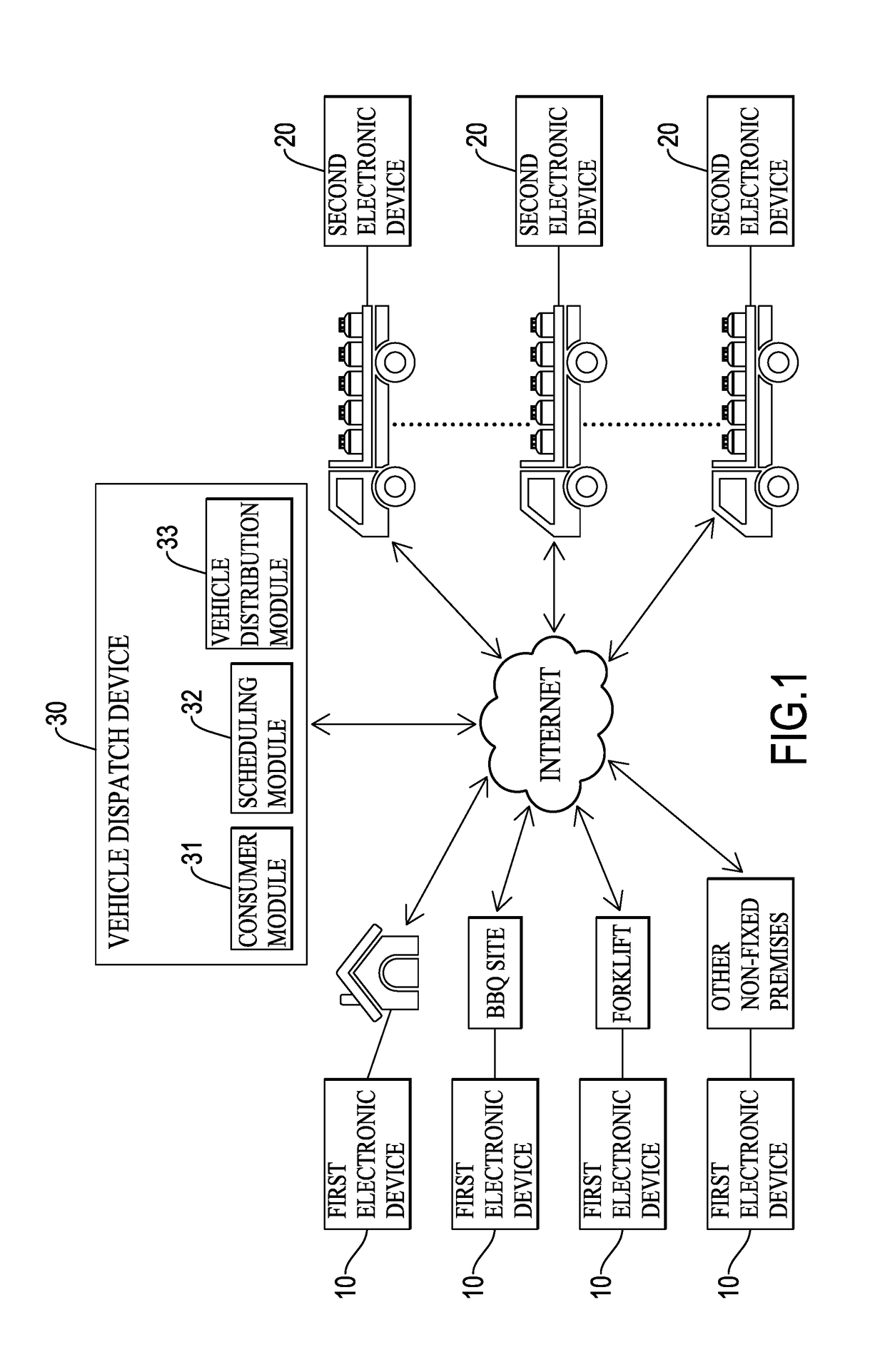
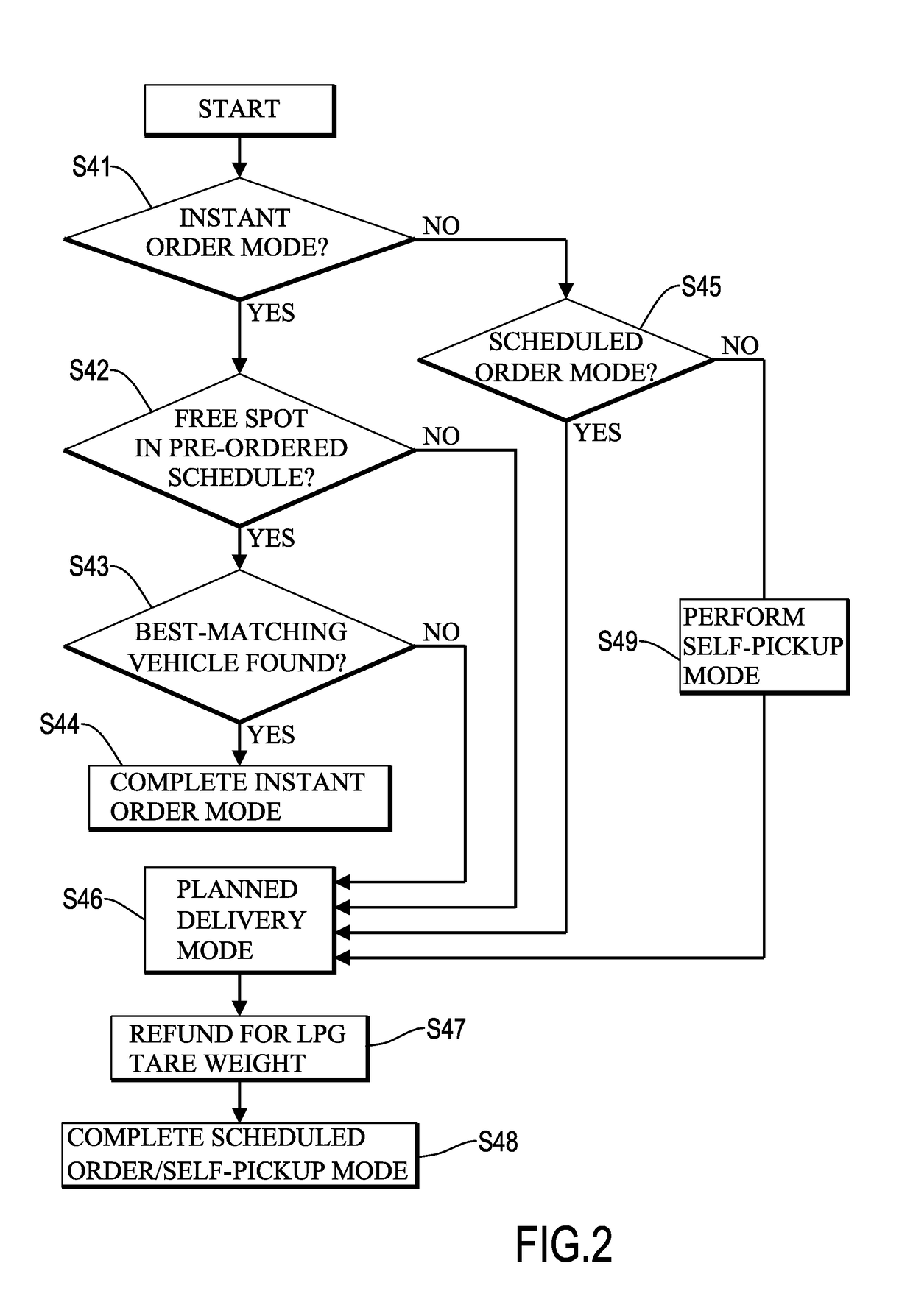
InactiveUS20180121863A1Improve distribution efficiencyConvenient ArrangementDiscounts/incentivesGaseous fuelsDistribution methodDistribution system
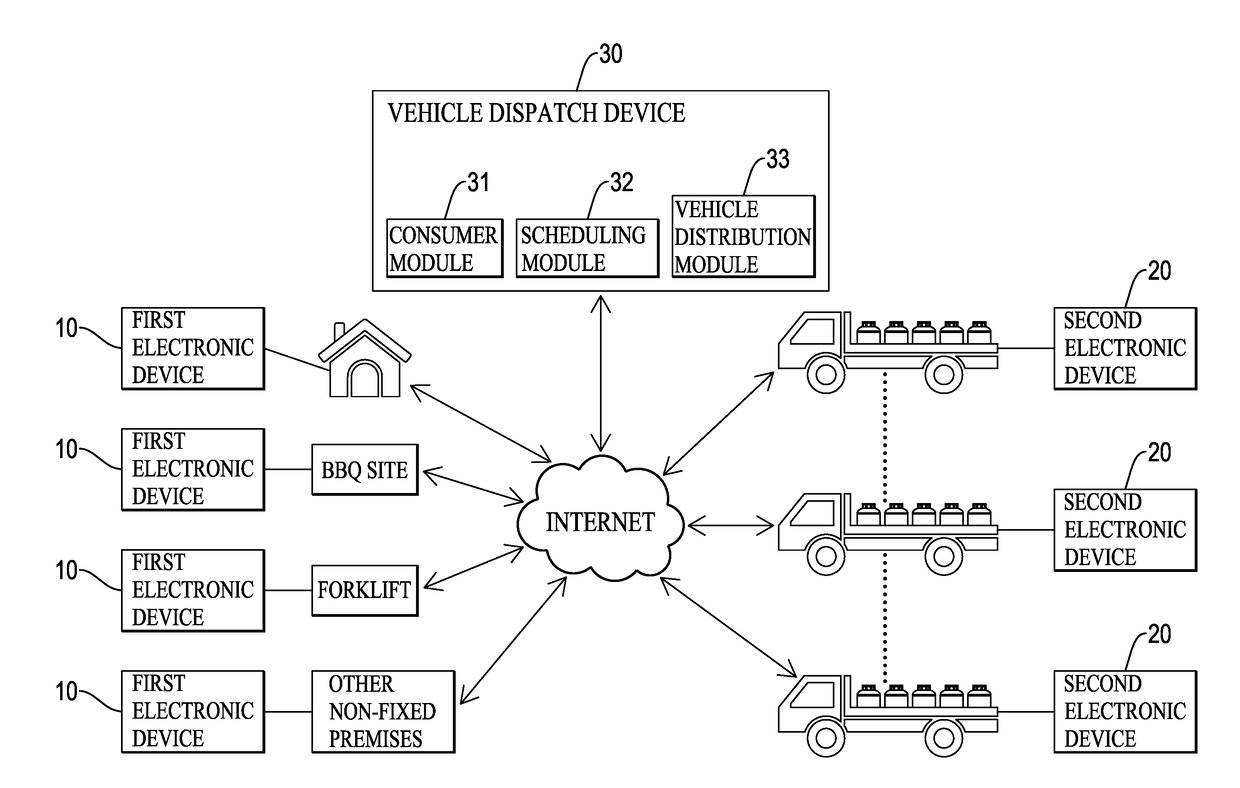
A barreled liquefied petroleum gas (LPG) distribution system has a system infrastructure with a vehicle dispatch device communicatively connected to multiple consumer ends and multiple vehicle ends. The consumer ends and the vehicle ends transceive signals by using multiple first and second electronic devices. When one of the consumer ends orders barreled LPG, a corresponding first electronic device is used to transmit an order message. The vehicle dispatch device performs a scheduled order mode, an instant order mode or a self-pickup order mode according to the order message. By the self-pickup order mode, barreled LPG can be personally delivered to consumers at non-fixed premises. Different discounts are given to consumers for choosing the scheduled order mode or the self-pickup order mode. Meanwhile, free spots within a delivery schedule can be utilized to support the instant order mode. Accordingly, distribution efficiency and consumer interaction can be enhanced.
Owner:Q GAS CO LTD
One-card-multiple-accounts bank card
InactiveCN1924939AReduce capital riskEnsure personal safetyCoded identity card or credit card actuationComputer hardwarePayment card number
This invention discloses one bank card with only one card number with multiple account number, which is located with magnetic bar to store one outer number, one inner number and bank card outside fund and inner funds information and stores one outer number, one inner number and one alarm numbers and outer funds information and inner funds information on the magnetic bar. This invention is through multiple account number and once the card is lost, the codes are stolen with only limit funds lost.
Owner:ZHEJIANG UNIV
Reclaimed water reuse water-saving device
InactiveCN101603320AConserve waterLong-term cleaningFlushing devicesDomestic plumbingWater savingFiltration
The invention discloses a reclaimed water reuse water-saving device and belongs to the field of daily products. The invention aims to provide a reclaimed water reuse water-saving device which reutilizes reclaimed water used once in life further to achieve a water-saving function. A concrete structure of the device is that: a coarse filter is arranged at a water outlet of a sewer pipe at the lower end of a lavabo, and is positioned into a filtration tank; and the inside of the filtration tank is provided with a fine filter; an outlet of the filtration tank is arranged in a reclaimed water storage tank; the inside of the reclaimed water storage tank is provided with a water feeding ring pipe connected with a tap water pipe; the water feeding ring pipe is provided with a water inlet floating valve, a float and a hole; the lower end of an overflow pipe in the reclaimed water storage tank is communicated with a sewer outlet of the reclaimed water storage tank; and a water pump in the reclaimed water storage tank is communicated with a toilet water tank through a reclaimed water feeding pipe. The device changes the conventional medium of clear water for flushing toilets, changes the clear water into the reclaimed water, and saves water.
Owner:刘庆和 +1
3D imaging device for surgical microscopes
The invention relates to a 3D imaging device for surgical microscopes, comprising a shell. The shell is provided with a lens body connecting part connected with a main lens body, and a lens cone connecting part connected with a binocular lens cone. A beam splitter group, a variable diaphragm, left and right imaging lens groups, and left and right photosensitive elements are arranged in the microscope body. After a double beam is split by the beam splitter group, one channel of double beam is imaged on the left and right photosensitive elements after passing through the variable diaphragm and the left and right imaging lens groups, and the other channel of double beam is observed directly through the binocular lens cone. The 3D imaging device of the invention is arranged separately, and can be directly connected with a surgical microscope as an accessory of the surgical microscope. The 3D imaging device has a simple structure, and is convenient to use. Users can observe through the binocular lens cone, without changing the using habit of the traditional surgical microscope.
Owner:ZUMAX MEDICAL
Fluorogenic quantitative PCR detection system for gallbladder carcinoma gene screening and application thereof
InactiveCN107988364AOptimize your lifestyleAvoid triggersHealth-index calculationMicrobiological testing/measurementRisk levelCrowds
The invention relates to the technical field of biological detection, and in particular relates to a fluorogenic quantitative PCR detection kit and further discloses an application of the kit for detecting gallbladder carcinoma. The fluorogenic quantitative PCR detection system comprises a detection kit for genes at special loci, calculates the score of risk of gallbladder carcinoma according to the risk value of each locus on the risk of gallbladder carcinoma, grades crowds according to an existing database, and obtains the individual gallbladder carcinoma risk level through individual score,so as to estimate the risk of illness of a subject and guide people with high-risk to improve the living style and avoid inducing factors and increase physical examination frequency. At the same time, a Chinese crowd database is established for the two selected gene polymorphic sites, thereby laying a foundation for estimating gallbladder carcinoma special for Chinese crowds.
Owner:SHENZHEN MEIGENE MEDICAL LAB
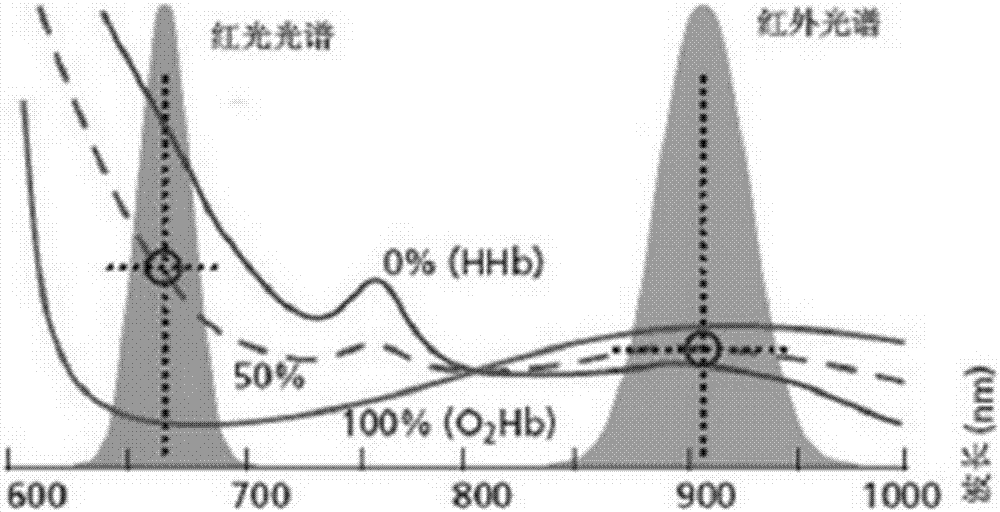
Off-line blood oxygen measurement device
ActiveCN106859667ARealize the effect of wireless vital sign monitoringChange habitsSensorsTelemetric patient monitoringEngineeringOxygen Measurement
The embodiment of the invention provides an off-line blood oxygen measurement device. The off-line blood oxygen measurement device comprises a front end blood oxygen collection module and a rear end current output module, the front end blood oxygen collection module is used for collecting a photoelectric signal related to blood oxygen of a patient, then conducting digital processing on the photoelectric signal and conducting transmission through a wireless communication channel; the rear end current output module is used for receiving the digitalized photoelectric signal through the wireless communication channel, and converting the digitalized photoelectric signal into a simulation electric signal capable of being received by a monitor.
Owner:铂元智能科技(北京)有限公司
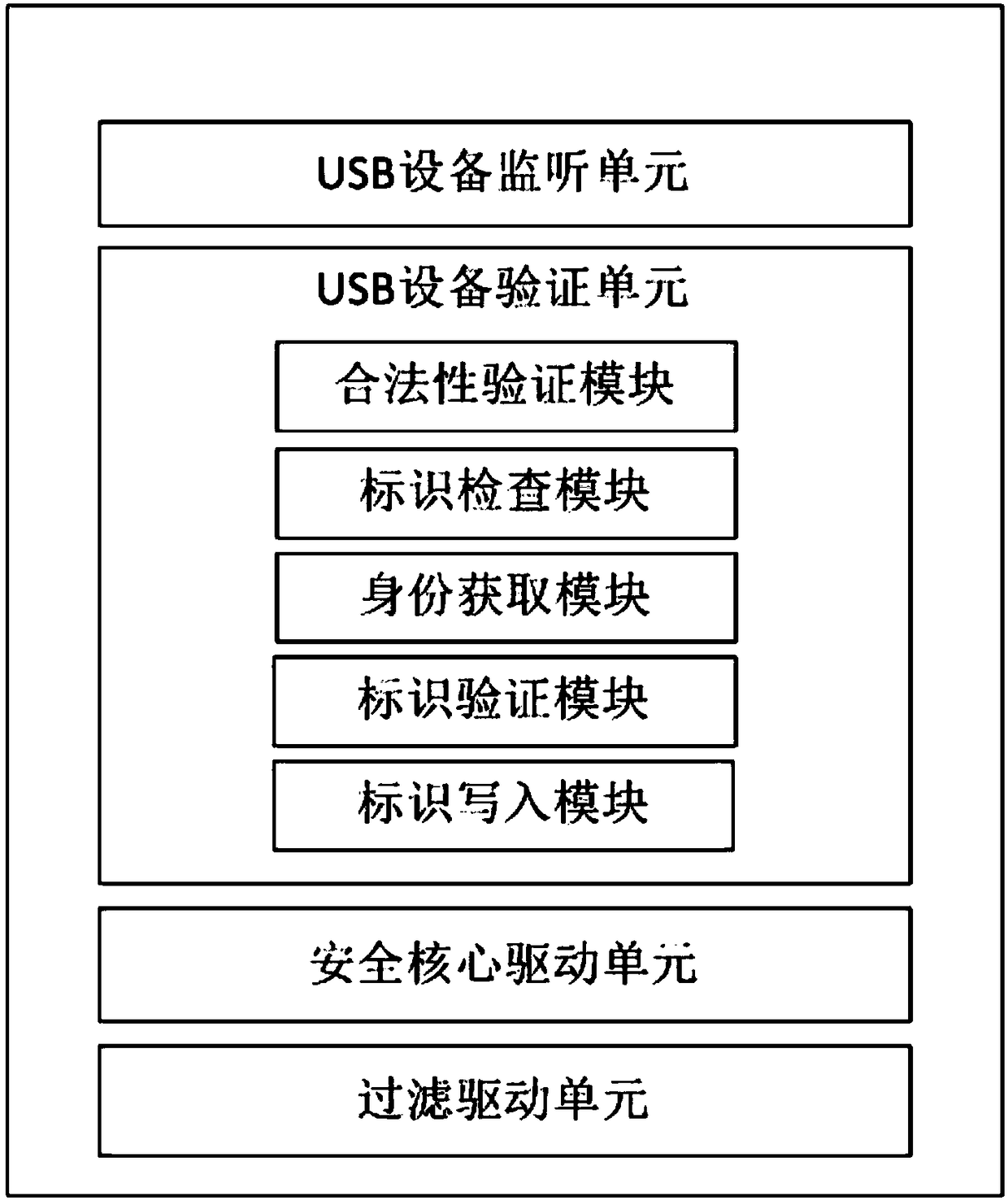
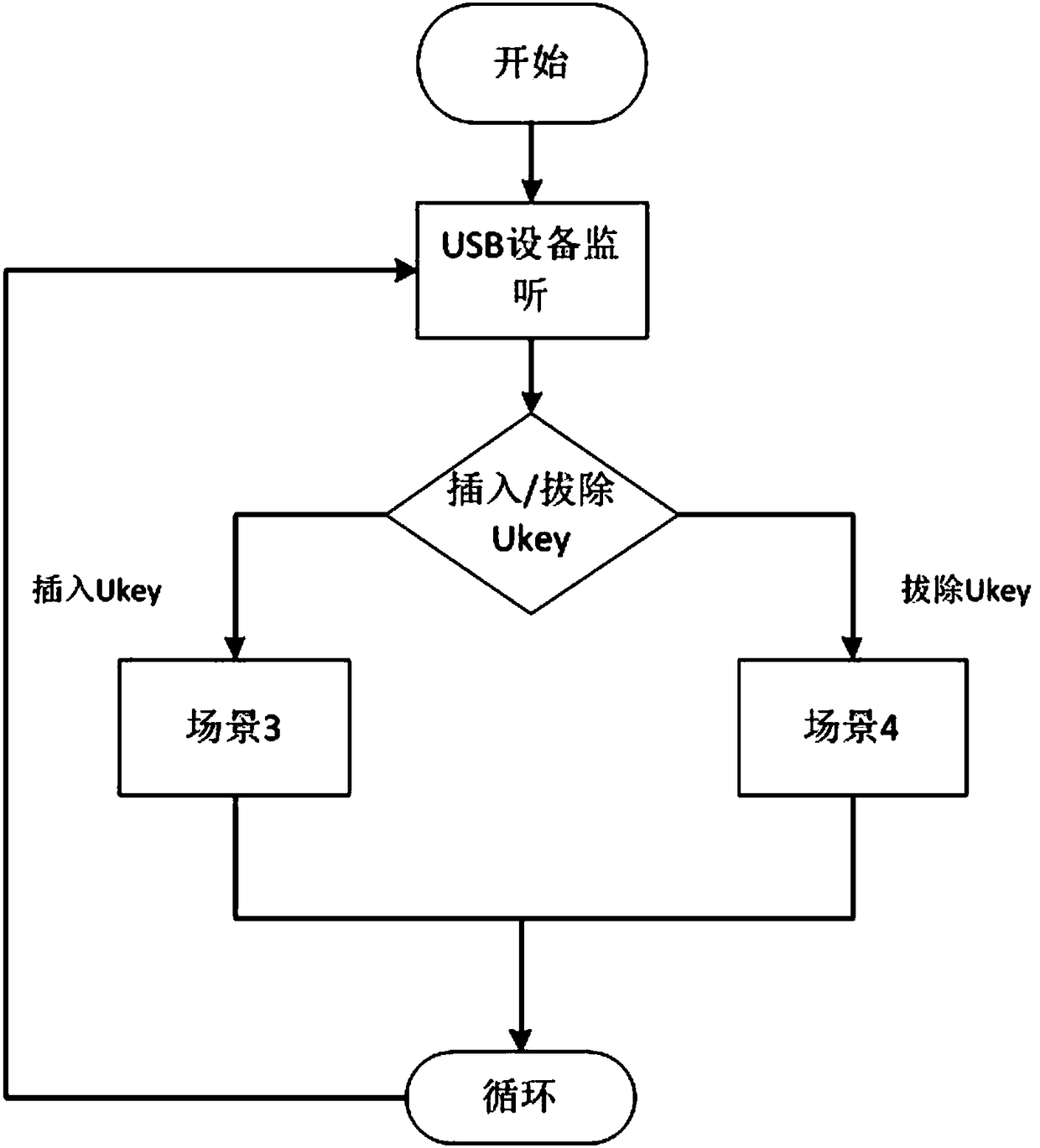
Security management system and method used for mobile terminal file
ActiveCN108287988AChange habitsImprove securityInternal/peripheral component protectionDigital data authenticationData operationsSafety management systems
The invention relates to the field of mobile terminal data security protection, and provides a security management system used for a mobile terminal file. The security management system comprises a USB equipment monitoring unit, a USB equipment verifying unit, a security kernel driving unit and a filtering driving unit. The invention further provides a security management method used for the mobile terminal file. The method includes the following steps that S1, a PC end is started, a client side program is run, and all the units are initialized; S2, the USB equipment monitoring units is adopted for detecting whether USB equipment is connected into the PC end; S3, the USB equipment verifying unit verifies whether the identity of the USB equipment is matched with the mobile terminal or not;S4, the security kernel driving unit is adopted for selecting to load the security kernel function of a virtual disk for the equipment, wherein the identity of the equipment is verified by the USB equipment verifying unit; S5, the filtering driving unit is adopted for scanning and filtering data operation in the virtual disk, and selecting to encrypt or decrypt the data in the virtual disk. The security management system and method are high in security and convenient and rapid to implement, and will not change the using habit of a user.
Owner:武汉华工安鼎信息技术有限责任公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com