Data underlay encryption method based on disk drive in cloud computing environment
A cloud computing environment and disk drive technology, applied in computing, electrical digital data processing, computer security devices, etc., can solve problems such as user inconvenience, restriction of user freedom of use, and burdensomeness, and achieve the effect of guaranteeing privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
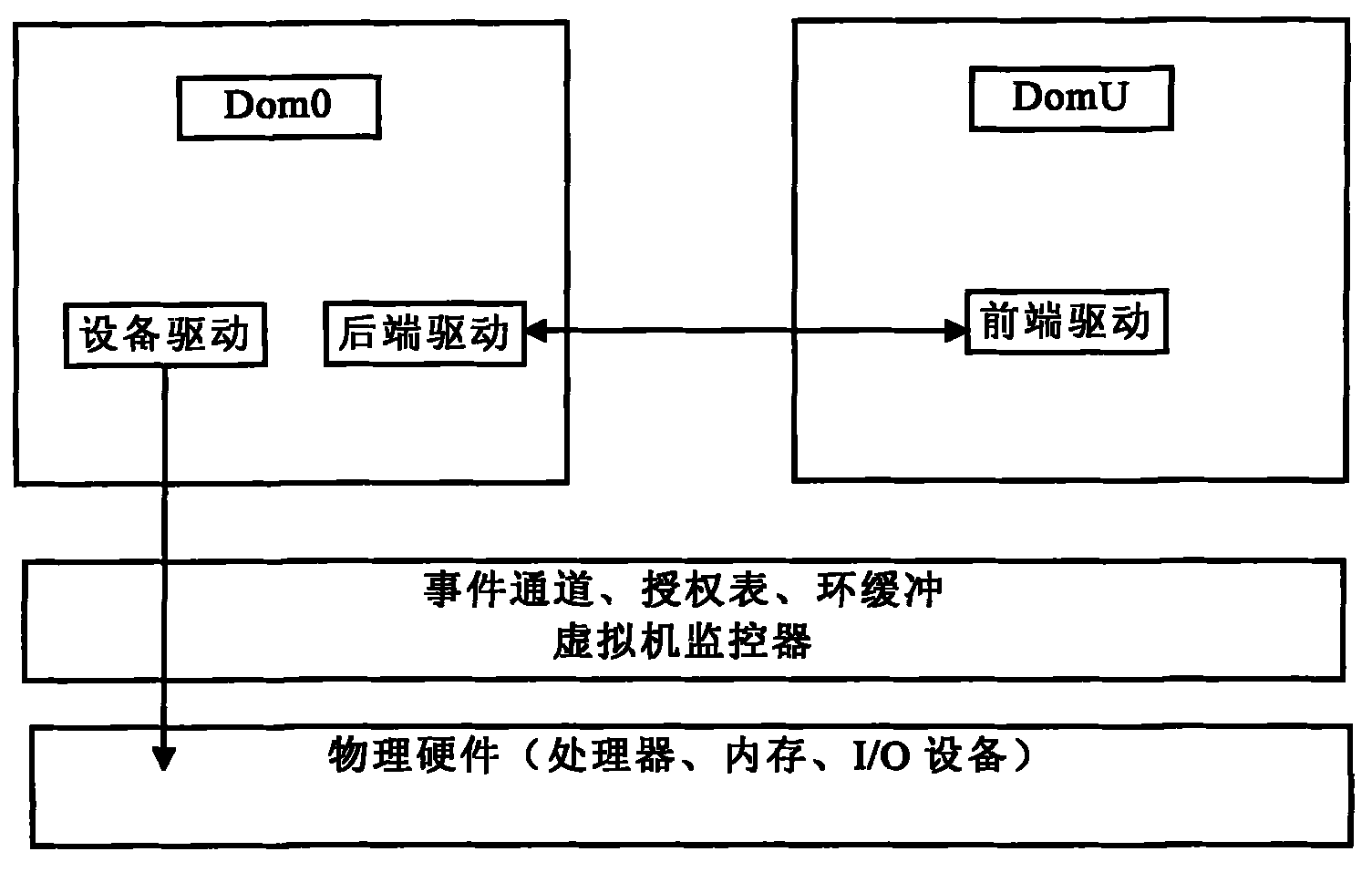
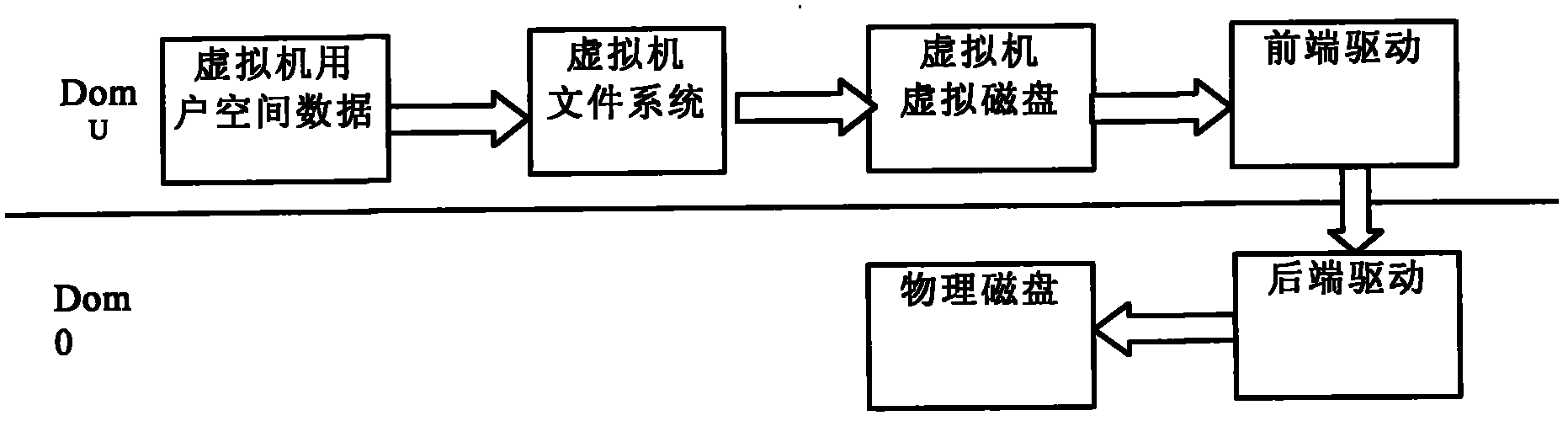
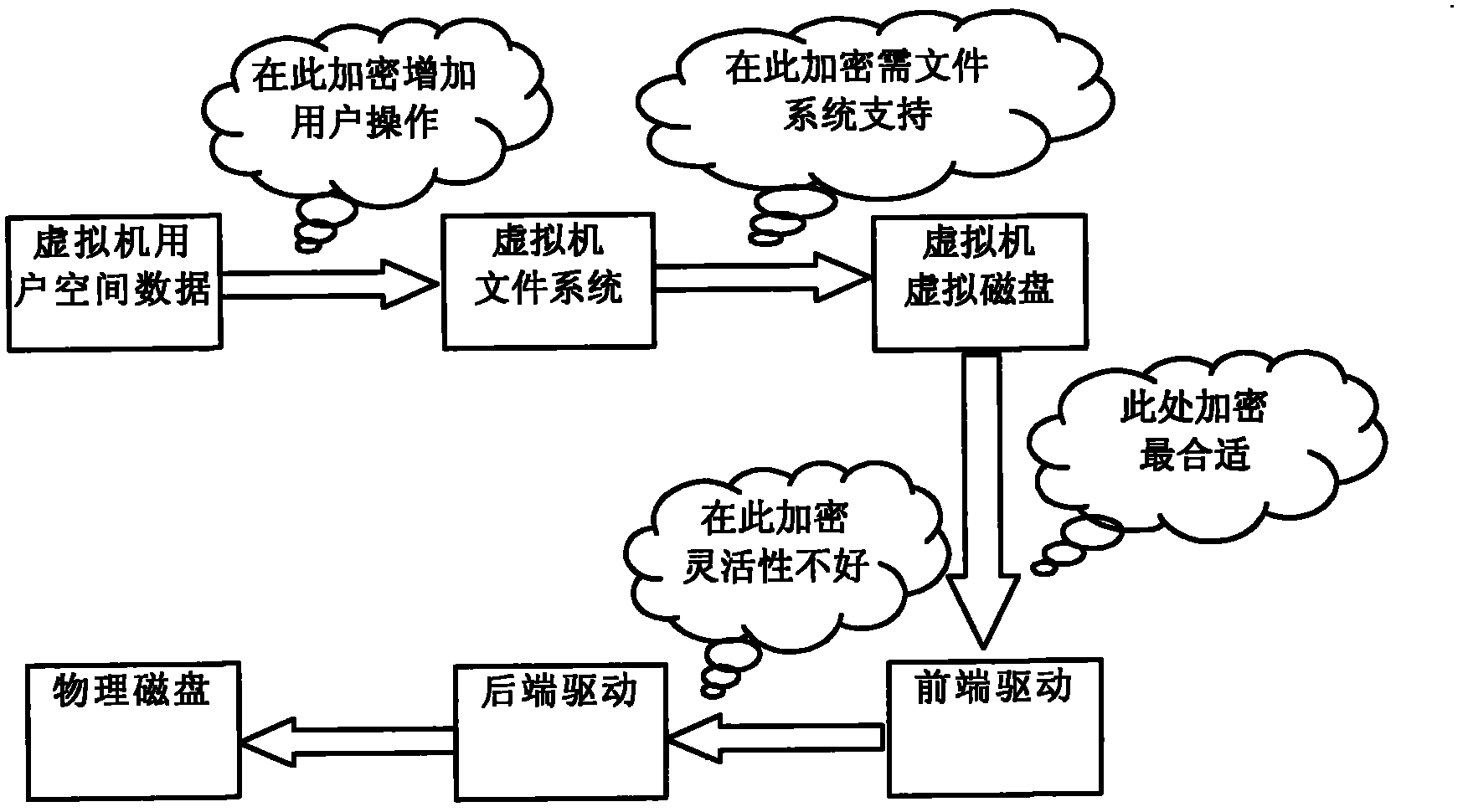
[0021] The invention relates to a disk drive-based data bottom encryption method in a cloud computing environment, which is data encryption based on the disk I / O level. Therefore, here we first elaborate on the disk device driver model of xen. Xen is an open source virtualization product. Xen uses a software layer called a hypervisor to regulate access to real hardware, enabling multiple sub-operating systems (that is, multiple virtual machines) to run on a single computer. Xen virtualization technology is divided into full virtualization and paravirtualization. Correspondingly, the I / O subsystem can be divided into front-end and back-end drive modes, emulation devices and direct distribution devices. Xen refers to the client as a virtual domain (Domain), wherein virtual domain 0 provides system management services for the service domain as an extension of the monitoring program. The monitoring program owns some hardware IO resources such as timer devices, interrupt devices P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com