Dynamic transparent isolation protection based enterprise data asset protection method
An asset and transparent technology, applied in the field of enterprise data asset protection based on dynamic transparent isolation and protection, can solve problems such as changing operating habits, high network performance requirements, and large impact areas, and achieves enhanced adaptability and robustness, network dependence Low sexiness, guaranteed consistent effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
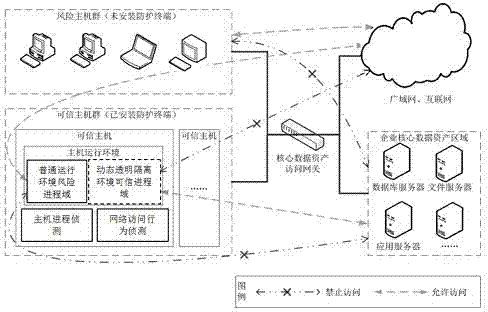
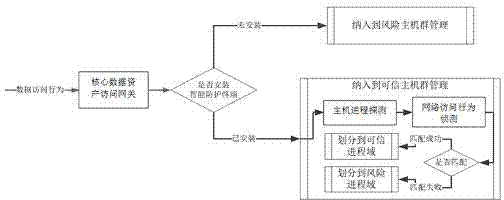
[0021] In the embodiment of the present invention, in the example of the present invention, a method for protecting enterprise data assets based on dynamic transparent isolation protection, the steps are as follows:
[0022] (1) Divide the user host group into a risk host group and a trusted host group. The trusted host group is equipped with a security protection terminal, which can penetrate the core data assets to access the gateway, and then access the enterprise's core data assets; and the risk host group It is difficult to penetrate and can only access other network resources.
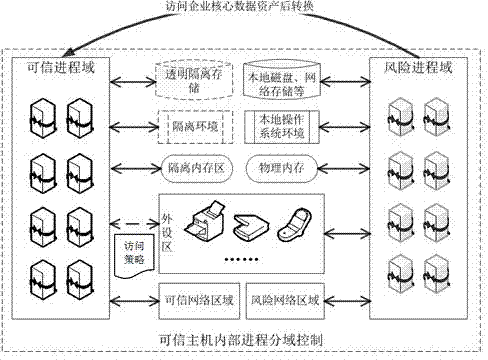
[0023] (2) In the hosts located in the trusted host group, the processes running in the system are divided into risk process domain and trusted process domain. Under the initial conditions, all processes are located in the risk process domain, and the process behavior is not controlled, but any behavior that accesses the core data assets of the enterprise will be detected, and then automatically ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com