Methods and systems for the rapid detection of concealed objects
a technology of concealed objects and methods, applied in the direction of material analysis using wave/particle radiation, liquid/fluent solid measurement, instruments, etc., can solve the problems of compromising detection performance, difficult interpretation of radiographs, and inability to calculate the actual atomic number of dual-energy methods. , to achieve the effect of reducing the dependence on operator skill and performan
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
second embodiment
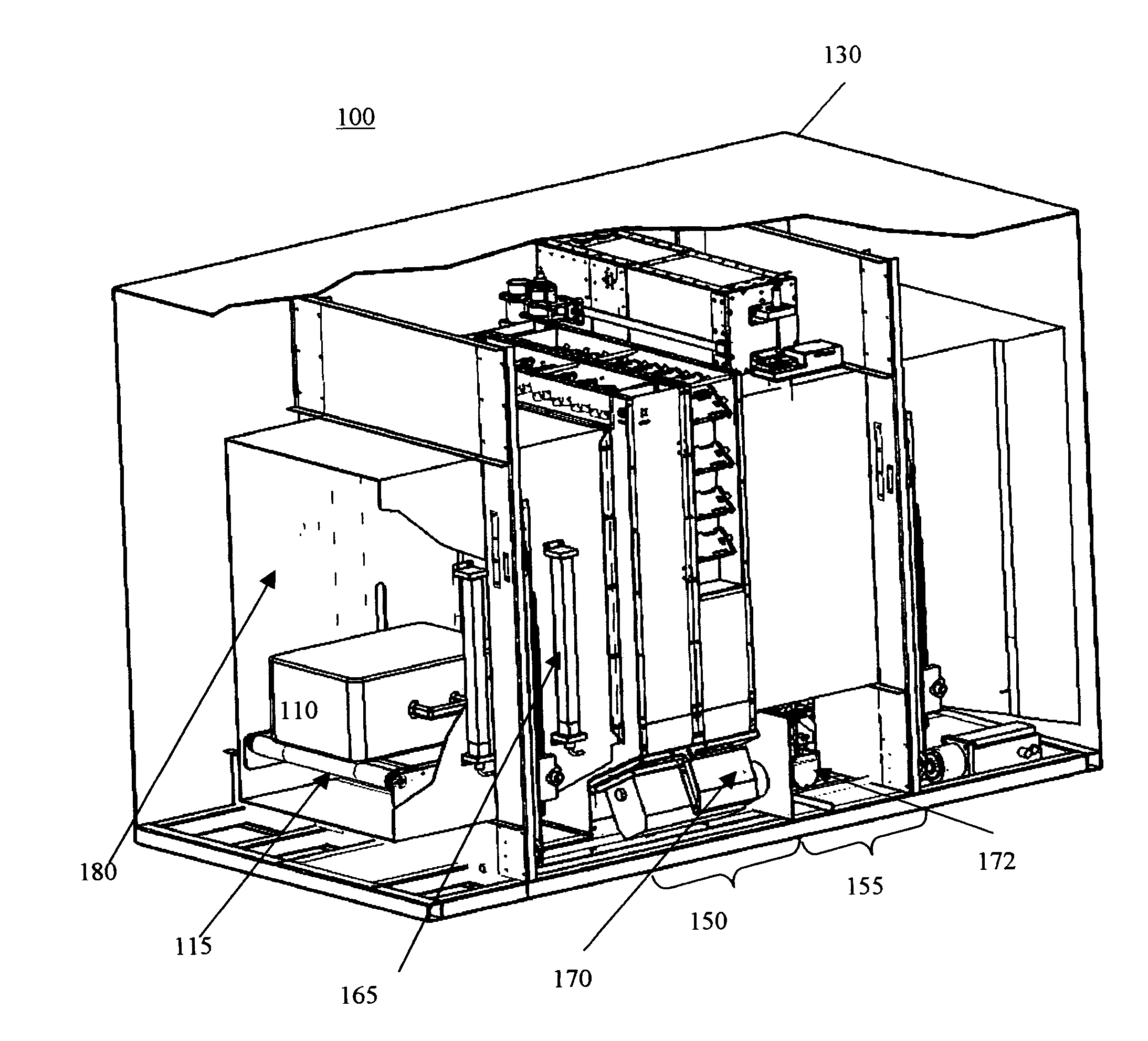
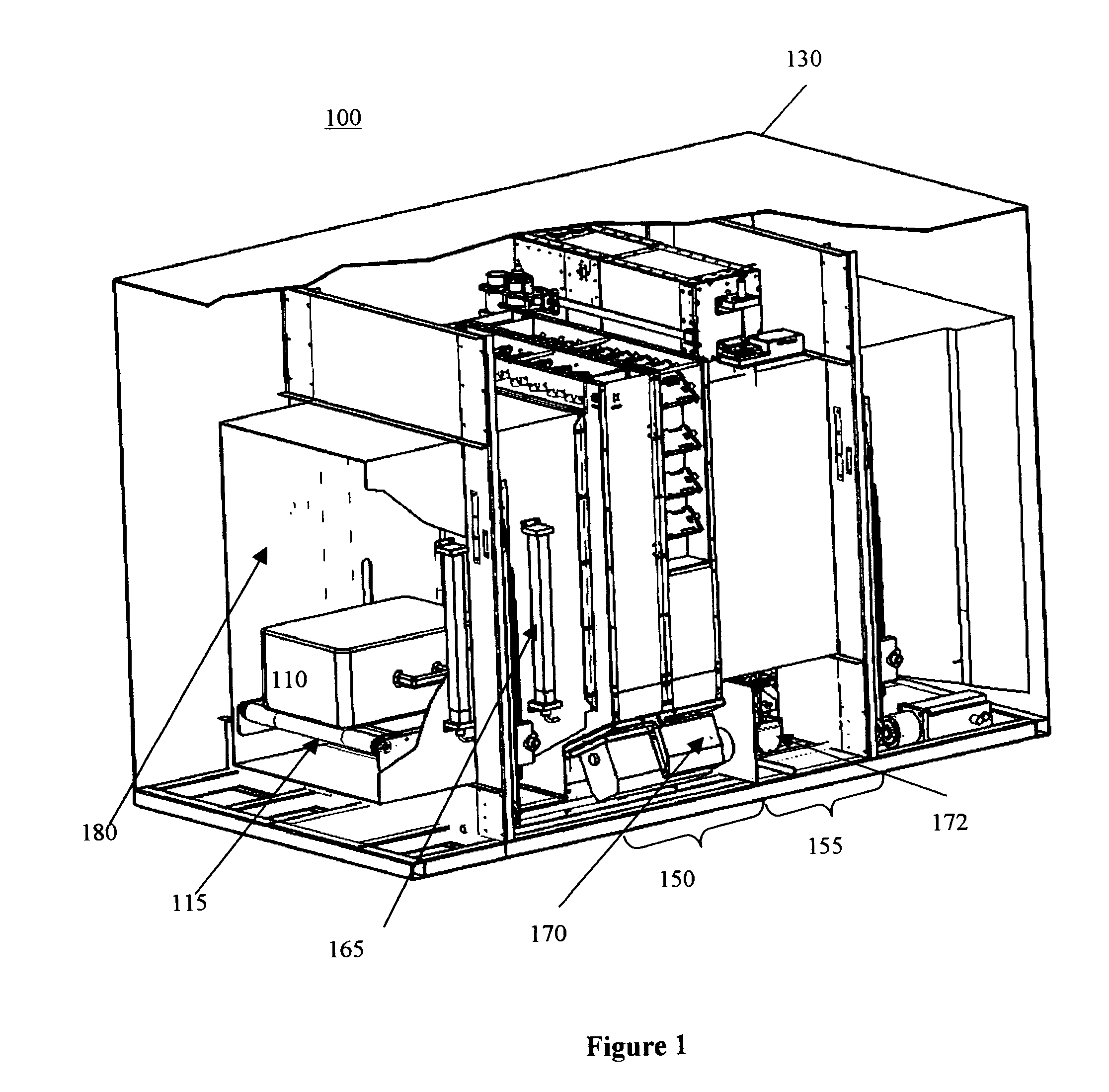
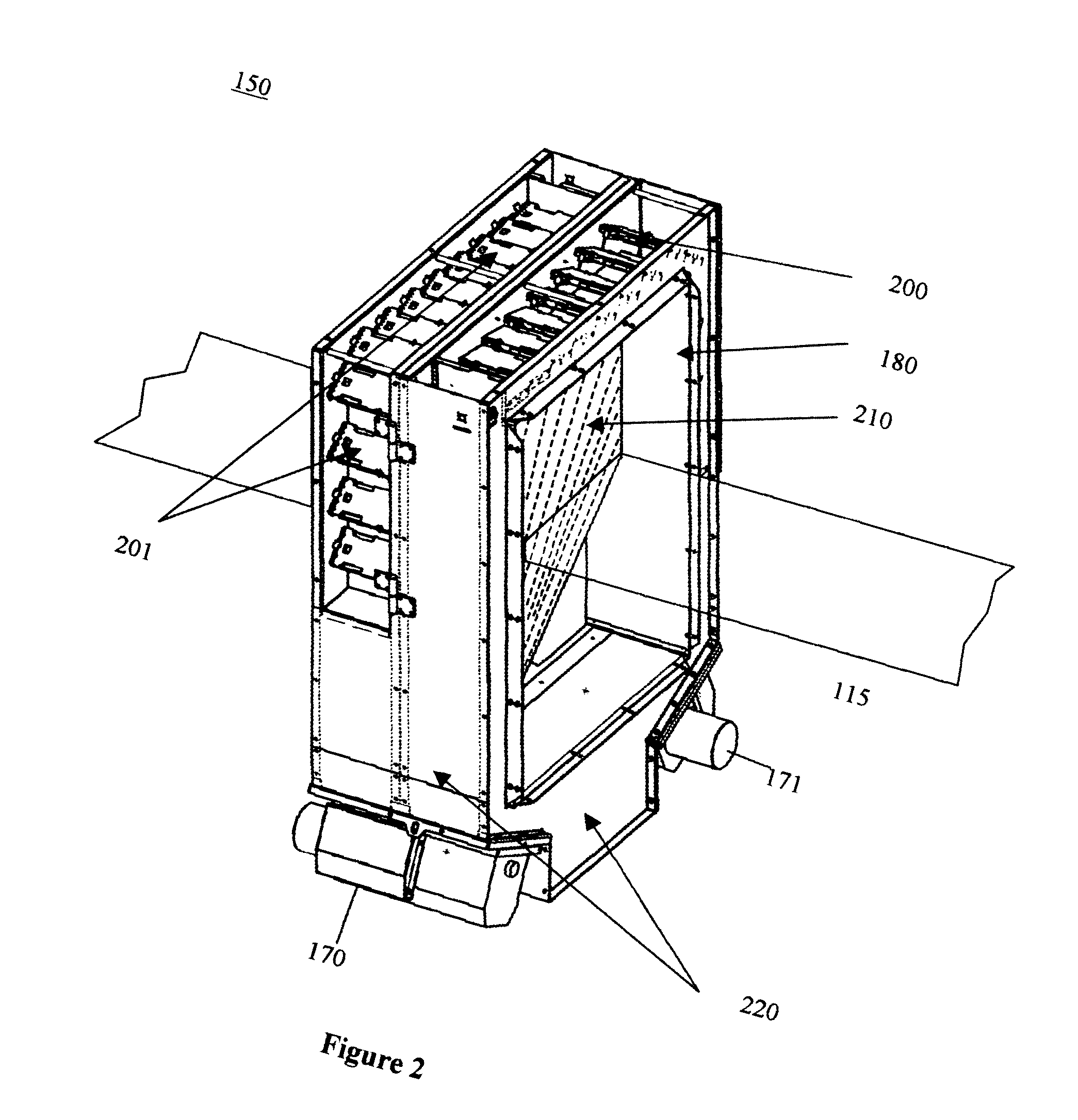
In a second embodiment, the transmission detector array functions as an imaging detector to provide precise attenuation data for certain areas in containers, like container wall areas, where contraband can be hidden. When the circular beam is centered on an edge of a container, the edge of the container can be imaged in good detail, and can help analyze the edges for concealed threats.
third embodiment
In a third embodiment, transmission detector measurements can be used to determine whether the inspection region is, in fact, the same target region previously identified in the first stage scan. If the transmission data correlates with X-ray characteristics different than those obtained in the first stage scan, the relative positioning of the second stage scanning system and the object under inspection may be modified until the transmission data correlates with the same material characteristics that was identified in the first stage scan.
fourth embodiment
In a fourth embodiment, transmission detector data are also being used to simplify the algorithm-training procedure of the system, as described below, in particular the collection of threat material properties with irregularly shaped threat samples, like sticks of dynamite.
It should be noted that it would appear because the scatter radiation path and transmission path differ downstream from the scatter volume, there would be inconsistencies in the data when scatter and transmission data are combined. This inconsistency is one example of a number of partial volume effects, solutions for which are addressed herein. However, the inconsistencies are not significant and can be tolerated without encountering significant performance degradation of the system as a whole. As shown, FIG. 4 is not an isometric schematic and, in reality, the scatter angle is preferably about 3 degrees, and the real path differences are comparatively smaller.
As previously discussed, the second stage scanning ...
PUM
| Property | Measurement | Unit |
|---|---|---|
| scatter angle | aaaaa | aaaaa |
| scatter angle | aaaaa | aaaaa |
| volume | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com