Patents
Literature
39 results about "Web programming" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Yunten's Web Application Methodology & Web Programming Language (YWAM & WPL)
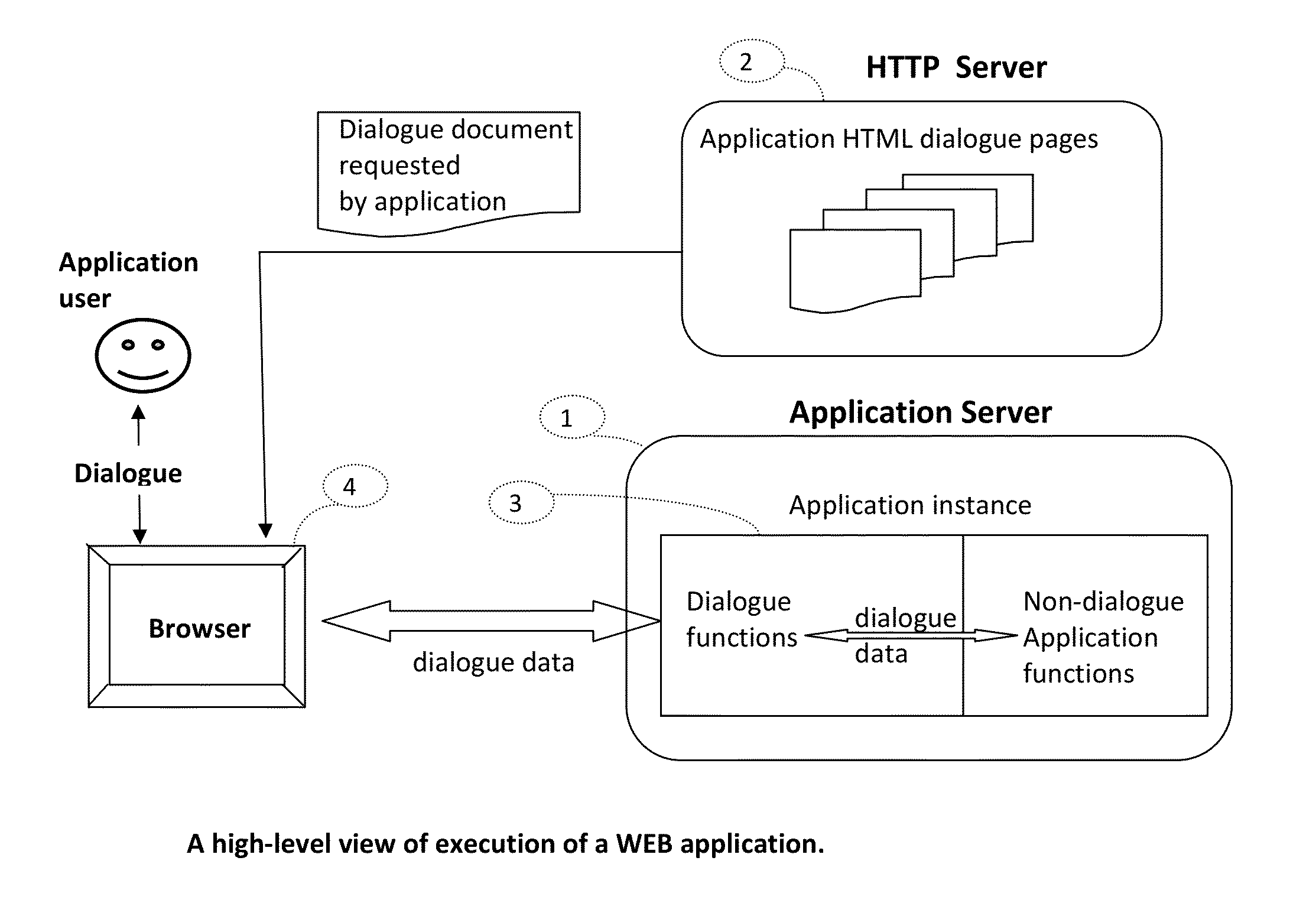
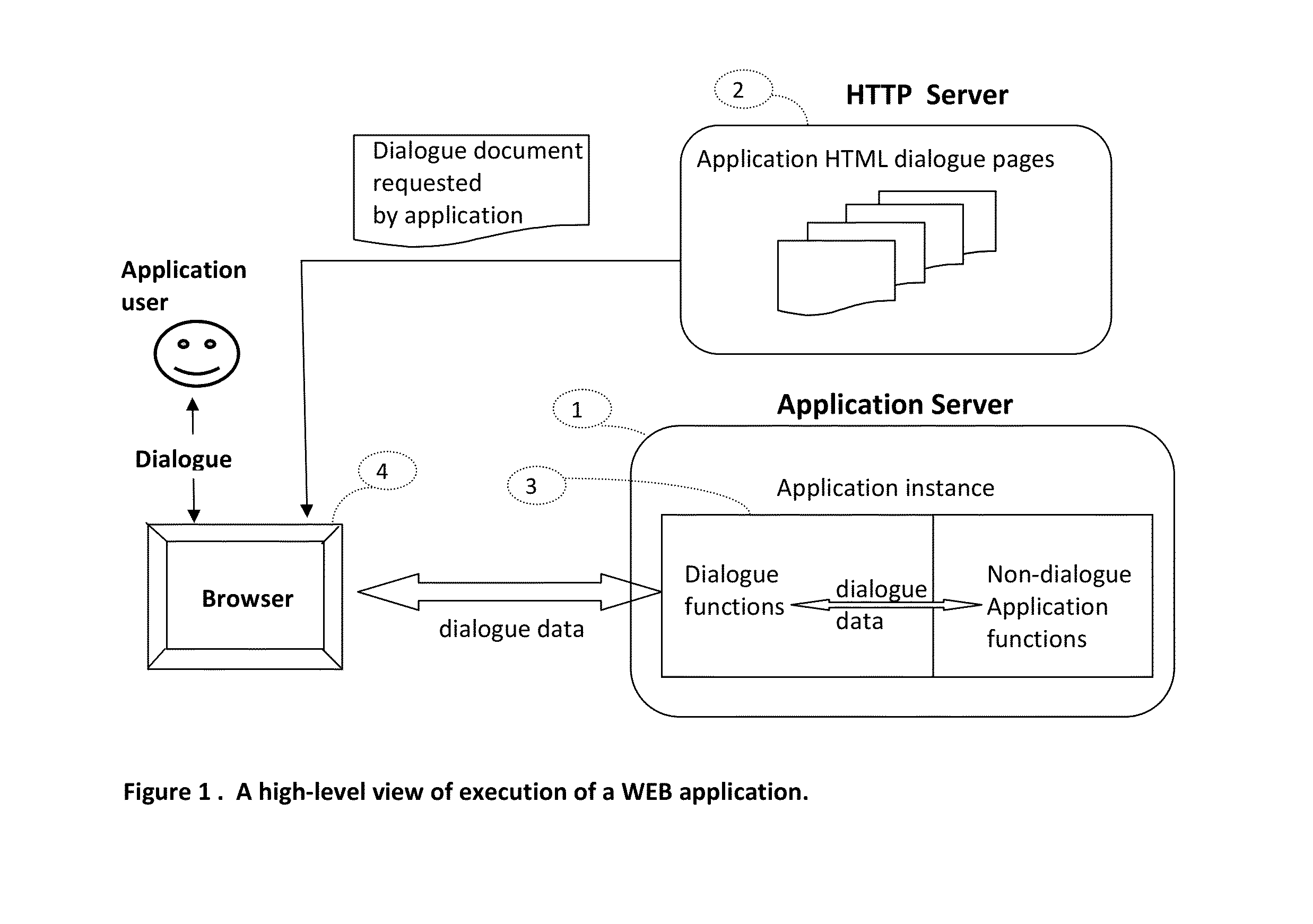
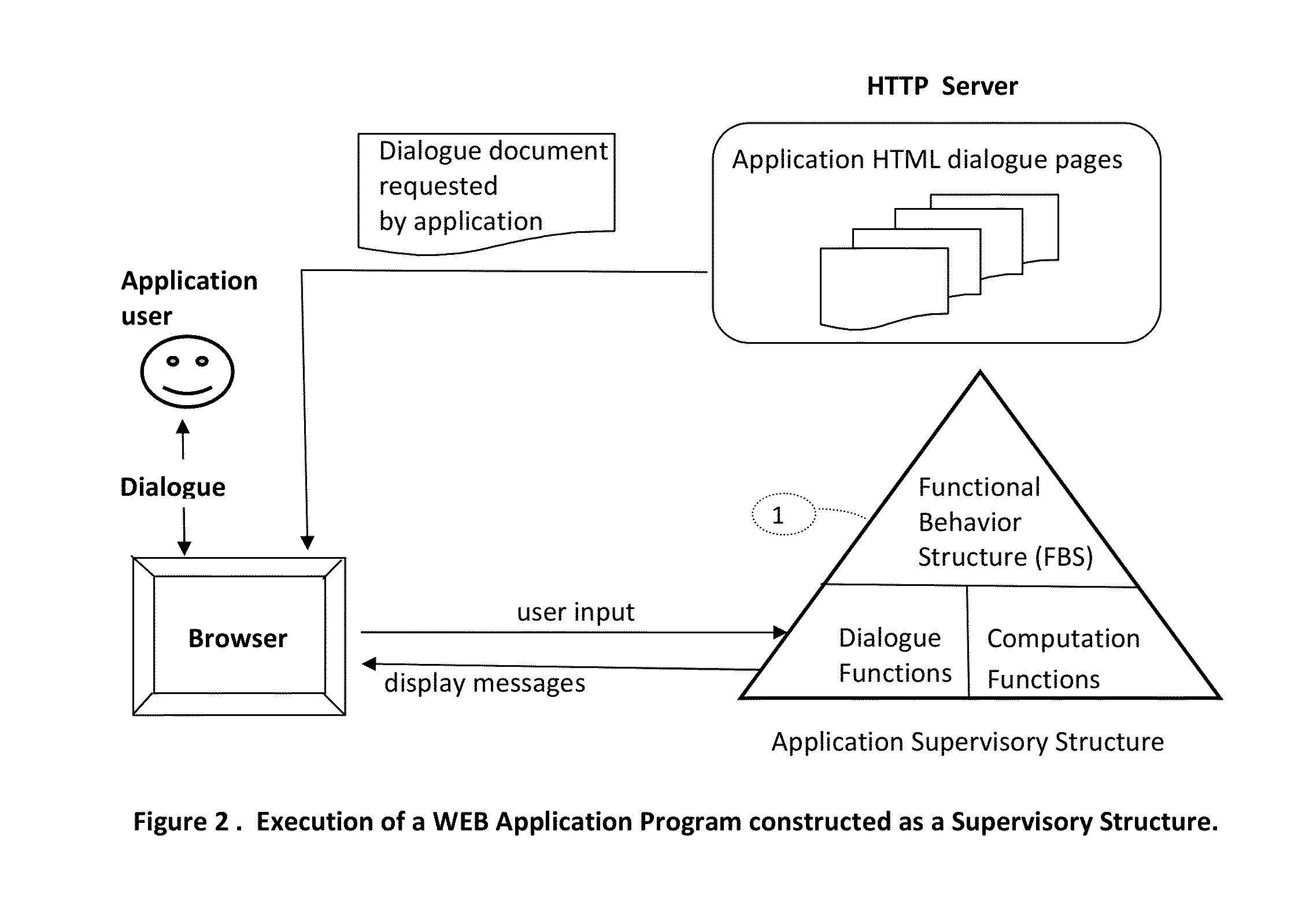
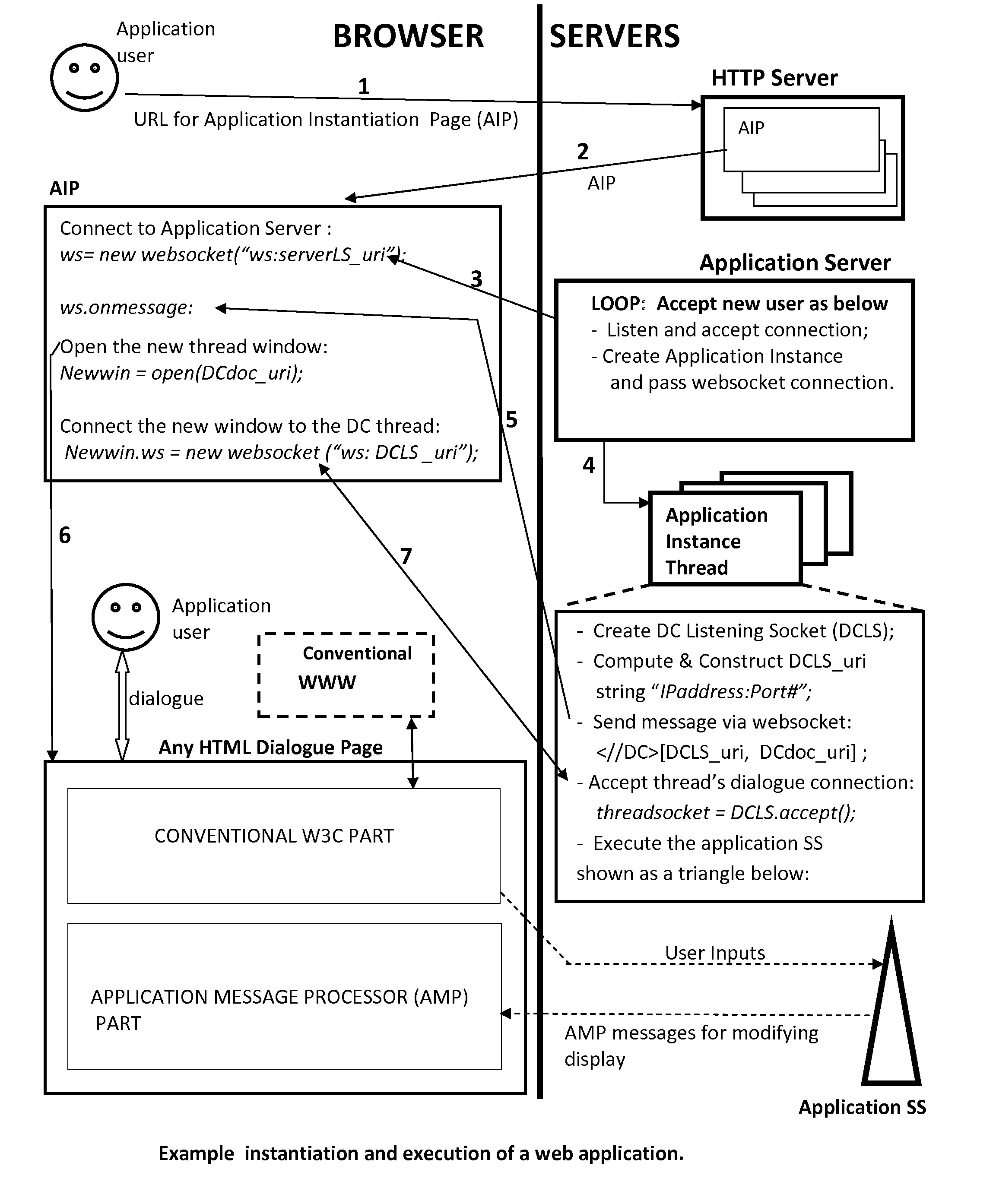
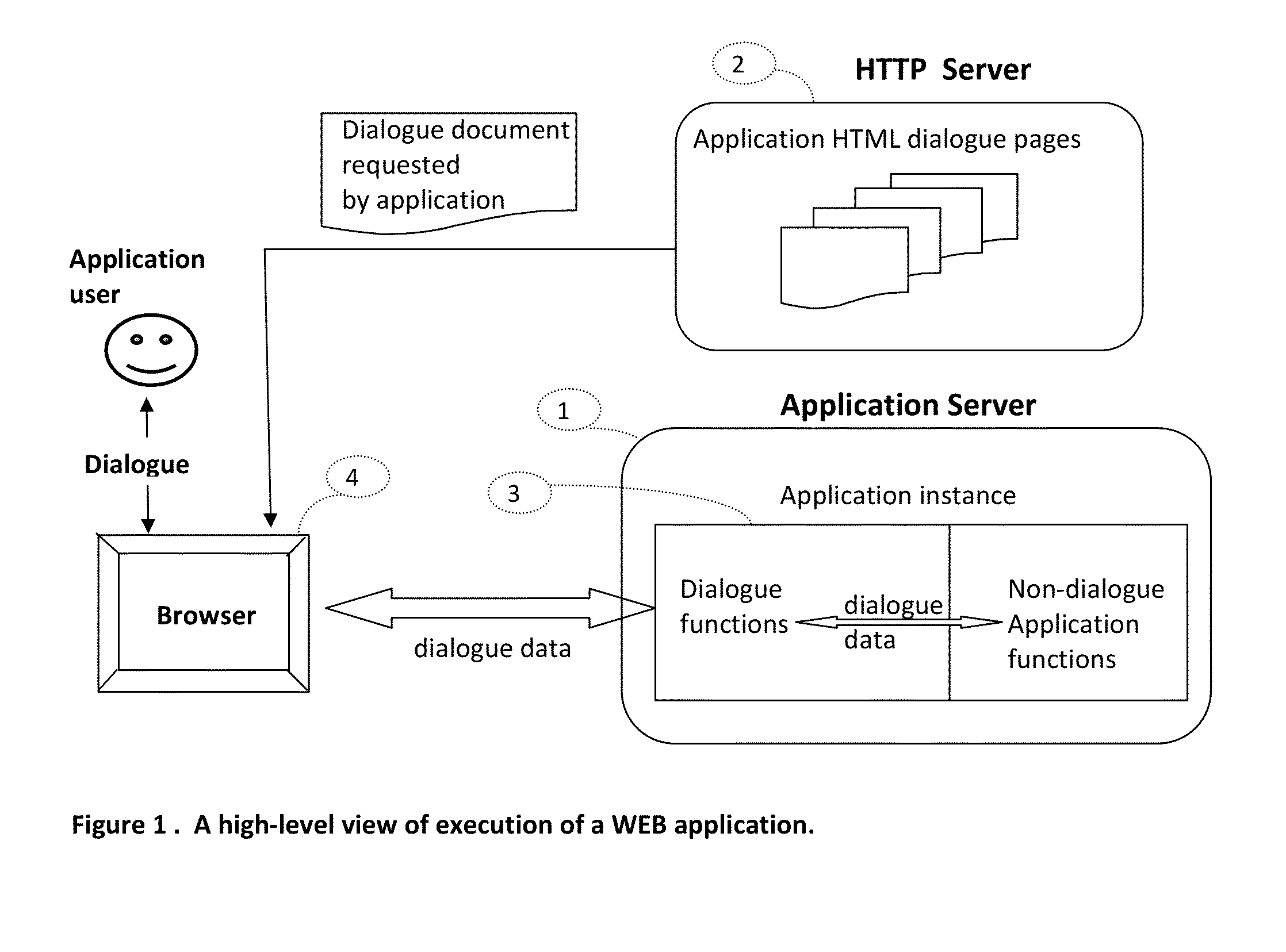
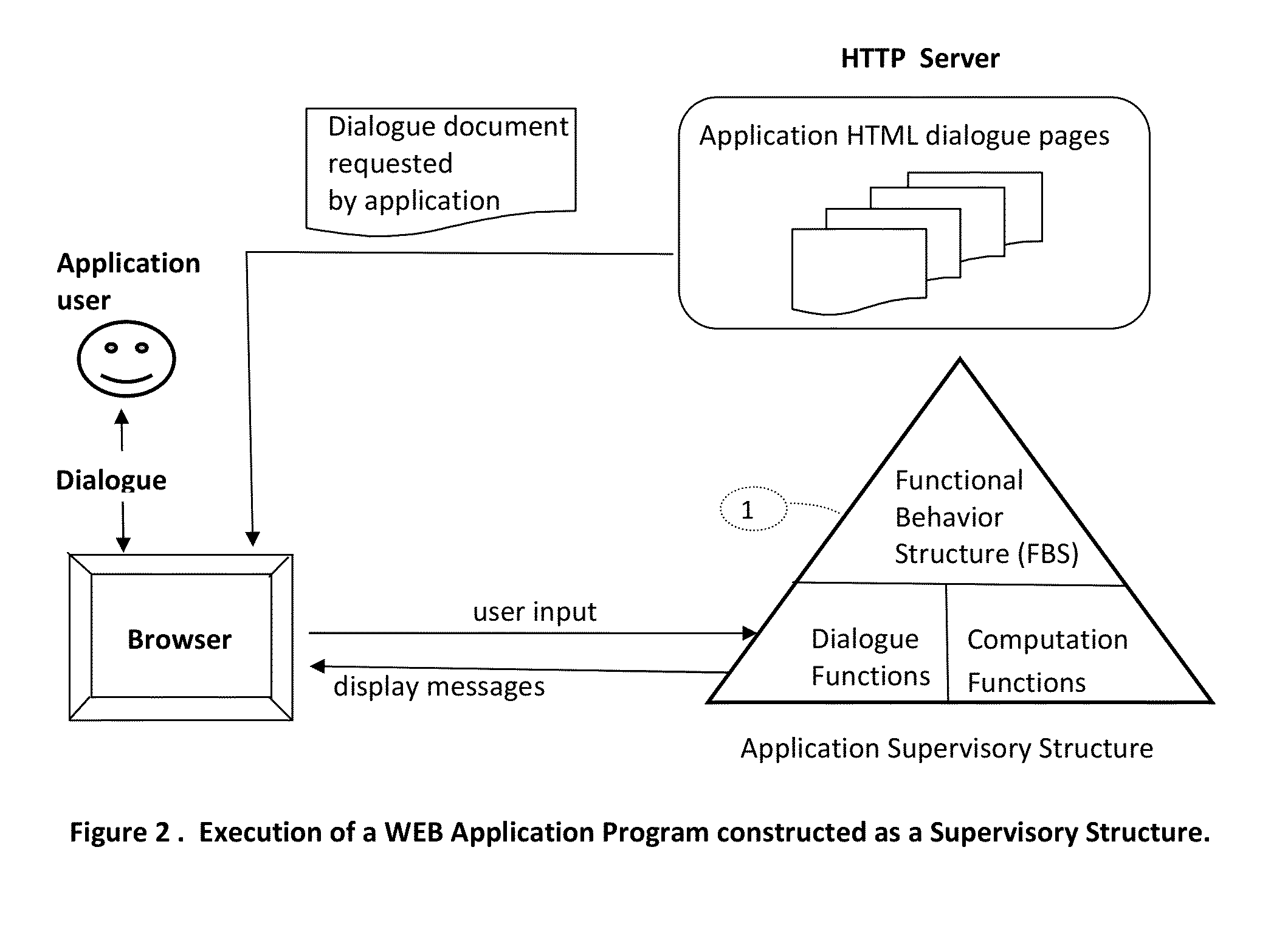
This invention introduces a structured software engineering methodology for developing interactive network application systems that use a web browser as a user-dialogue engine. The methodology uses two server types: Application Server(s) for instantiating and executing an application instance in binary code, and HTTP Server(s) for delivering to the user's browser the textual HTML+Javascript user-dialogue documents used by this application instance during its execution. An application is accessed by executing at the user's browser an Application Instantiation Page (AIP) which is a part of this invention. The methodology is built into a notational programming language.
Owner:YUNTEN TAMER
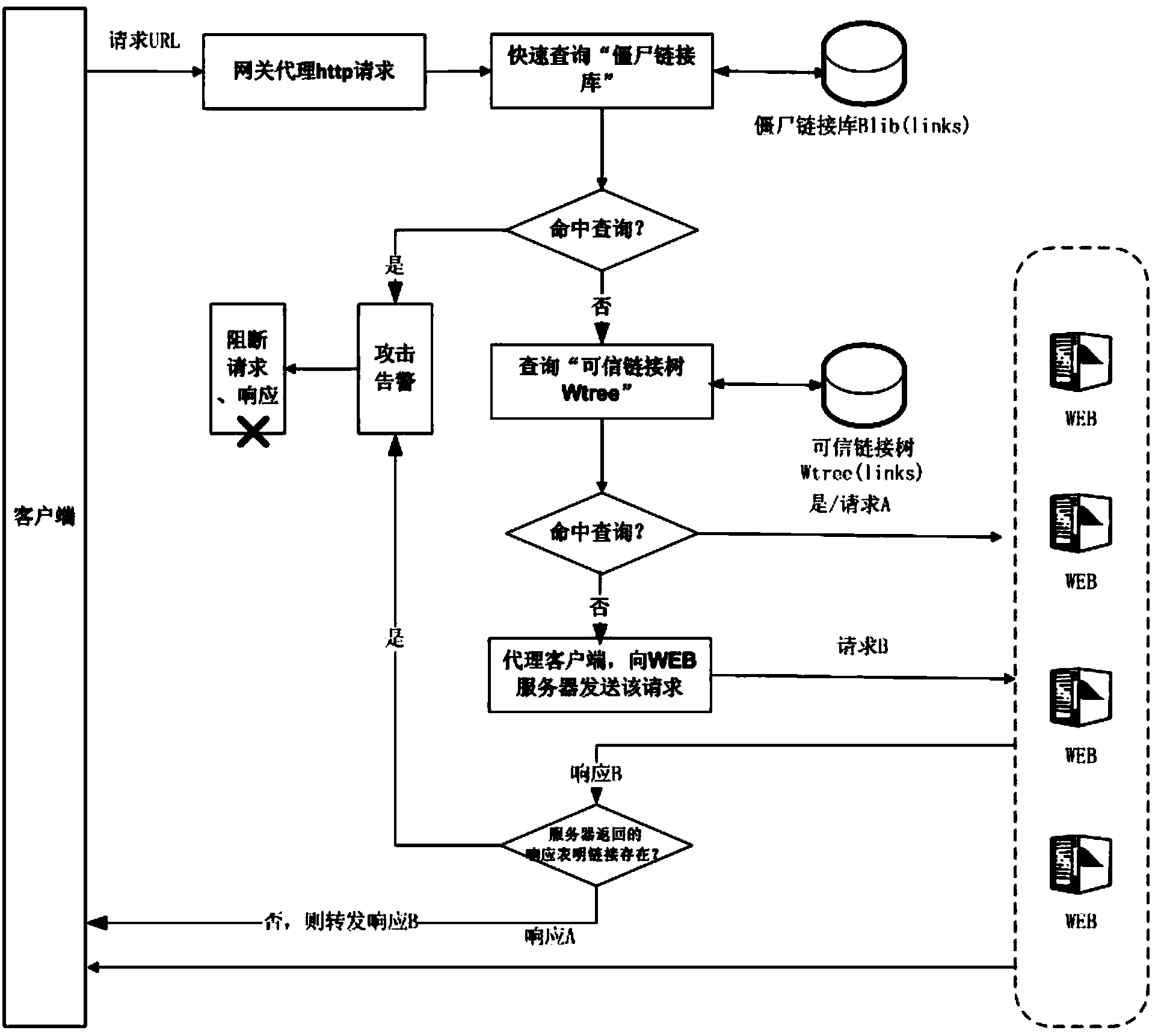
WEB backdoor detection method and system based on relevance tree
ActiveCN103561012AImprove relationshipSimplified link relationship tree associationTransmissionSpecial data processing applicationsWeb siteWeb application
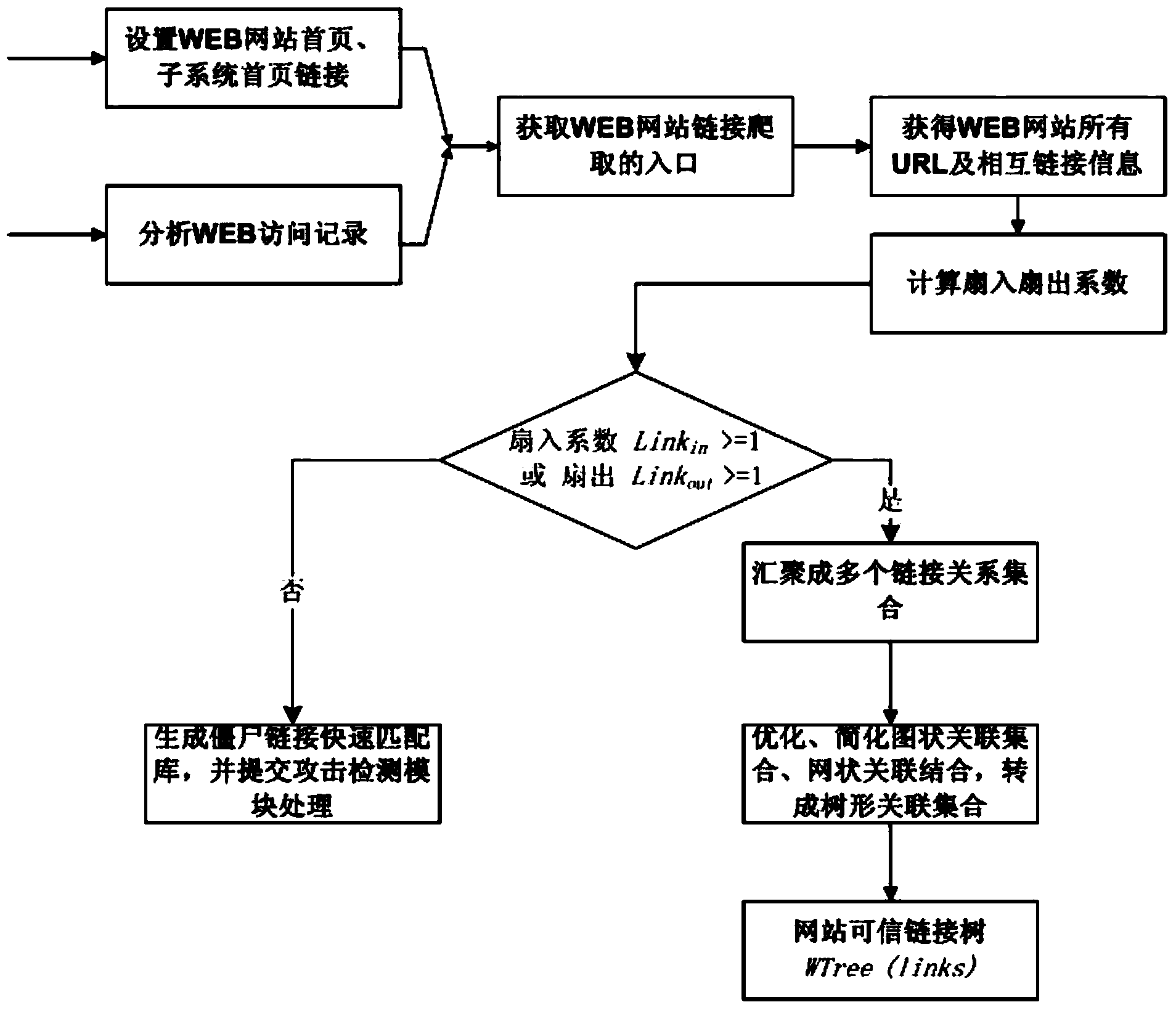
The invention relates to a WEB backdoor detection method and system based on a relevance tree. The WEB backdoor detection system comprises a link relevance tree generation module and an attack real-time detection module. The detection system does not depend on antivirus software or file feature detection software, instead, initiative crawling and access record collecting are conducted on WEB links first, a link set of all URLs of a WEB is established through analysis and process, and the link and skip relation of the URLs is marked in a computerized algorithm in a tree mode, so that a link relevance tree is formed. If a backdoor URL request does not exist in the link relevance tree, a security monitoring module of the system gives an alarm, and the attack request is stopped. By means of the detection method, the safety of WEB application is improved, the problem of WEB backdoor attack which can not be detected and prevented by security products such as the antivirus software and a firewall is solved, the university is good, there is no need to mount software programs on a WEB server, and the type of the WEB server, WEB programming languages, customer usage and the like are all made to be transparent.
Owner:INST OF INFORMATION ENG CAS
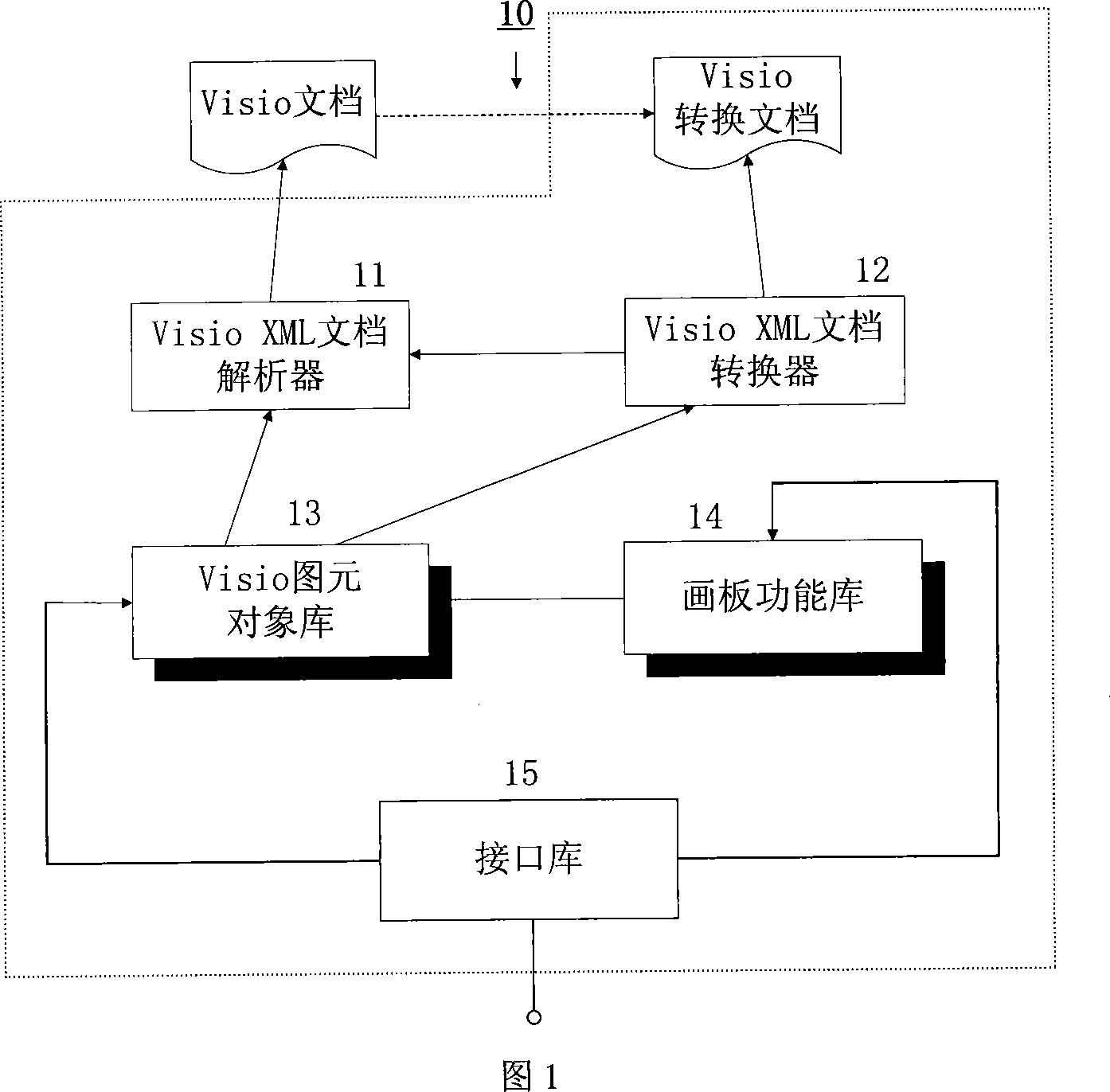
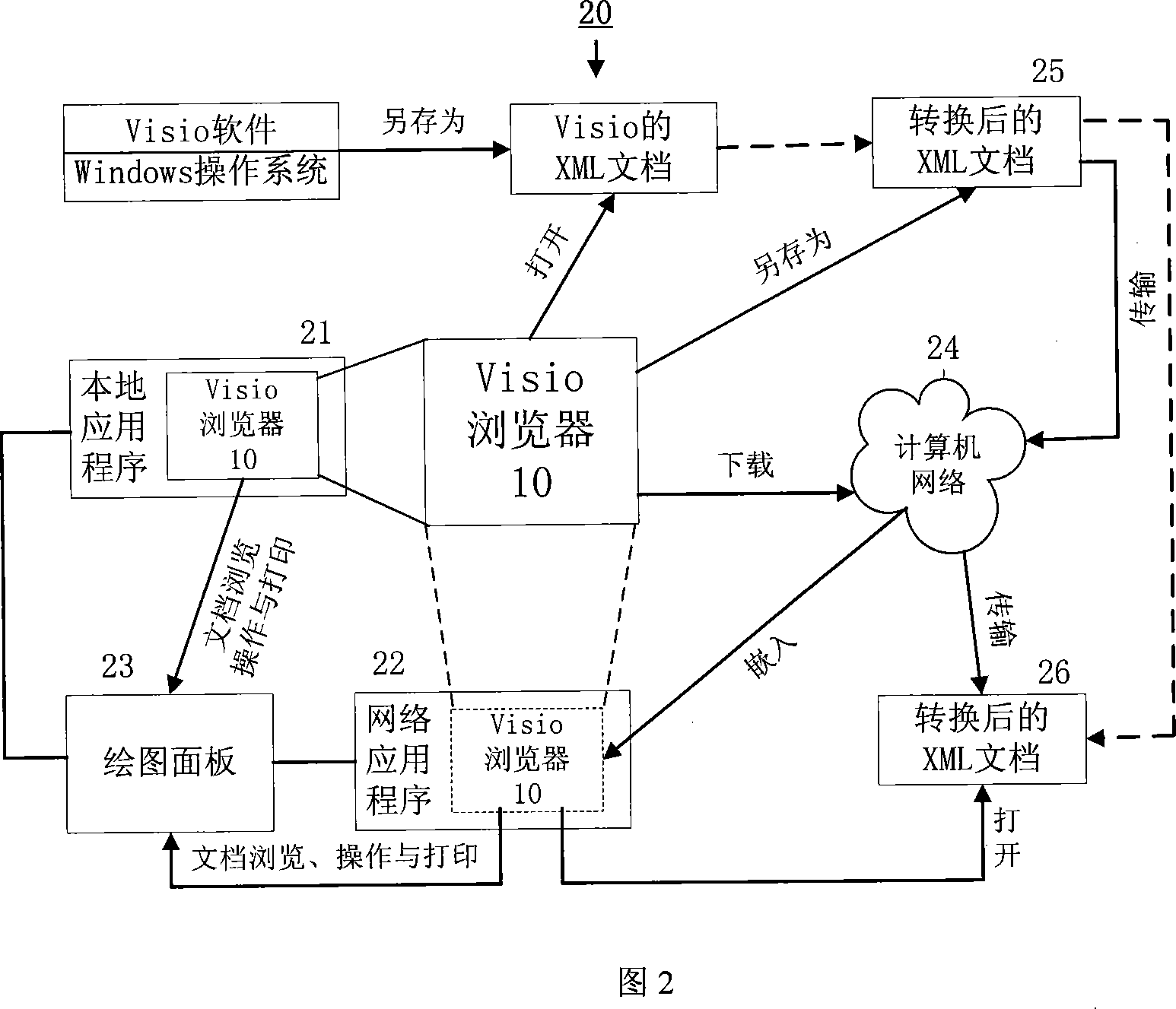
Visio file cross-platform network browser implementation method and software
InactiveCN101078989AAdd browsing functionRich graphics performanceSpecific program execution arrangementsSpecial data processing applicationsOperational systemSoftware engineering
The invention discloses a method to construct span flatform Visio document network browser with network programming language and uniform document marking language of spam flatform, which is characterized by the following: setting Visio document browser element as the core; comprising Visio XML document analyzer, Visio XML document converter, Visio image element object library, drawing board functional library and interface library; realizing relative function of the Visio XML document span flatform network browser; connecting to the other application program with static state or dynamic mode; basing on Java; combining to an integral body on logic and function through the interface library and the application program of the element.
Owner:阮俊杰
Communication Channel For Reconfigurable Devices
ActiveUS20180285295A1Dynamic configurationDigital data protectionBootstrappingProtocol for Carrying Authentication for Network AccessWeb programming
A communication channel for reconfiguration of a device, such as an FPGA, is described in various embodiments. One embodiment includes a physical input / output circuit, a dynamic layer, and a static layer. The static layer is programmed into the reconfigurable device to contain a configuration layer and a network layer. The configuration layer is able to receive additional layers, such as a virtual network layer and a virtual security layer and program them into the reconfigurable device. The virtual network layer can provide communication protocols, such as TCP / IP, and the virtual security layer can provide security protocols, such as TLS and IPSec. Various distributed applications can be programmed into the reconfigurable device over the network and configured to use the virtual network layer and the virtual security layer.
Owner:IBM CORP
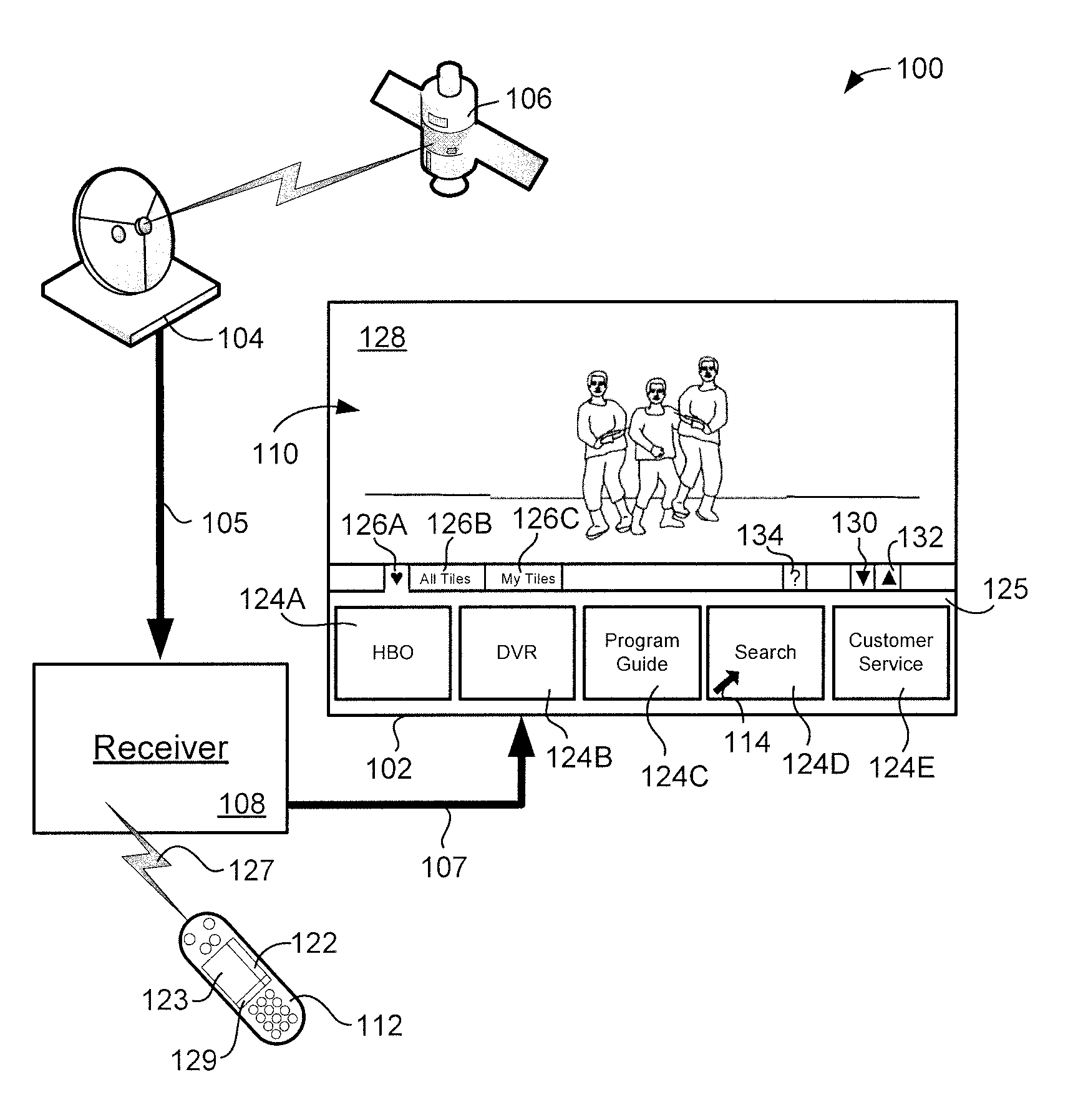
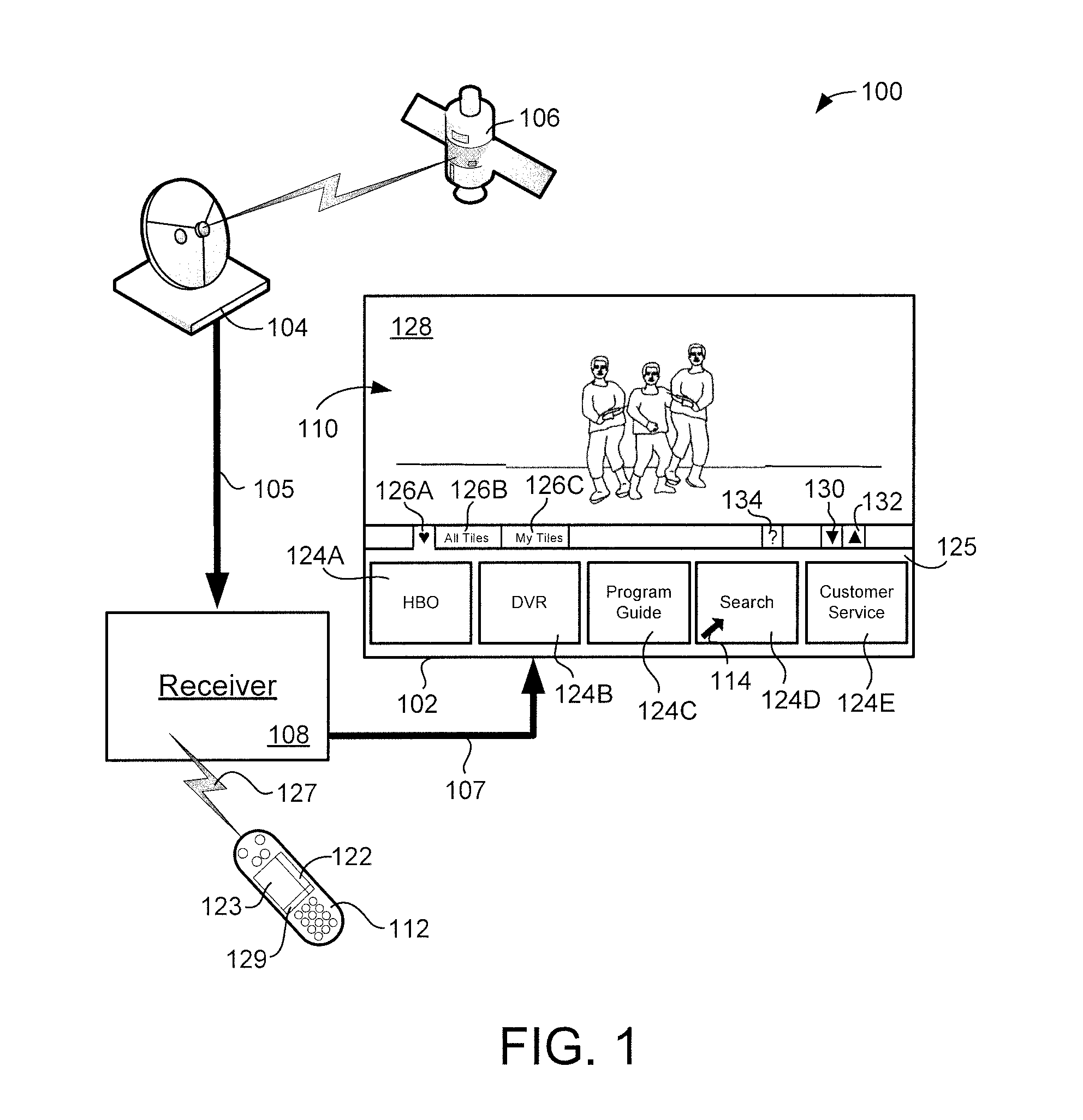
Systems and methods for providing customer service features via a graphical user interface in a television receiver
Systems and methods provide for graphically providing customer service features on a set top box (STB) or other television receiver in response to viewer instructions received from a remote control. Imagery including a customer service tile is presented on the display. A two-dimensional input is received from the remote control that indicates that the tile has been selected, and, in response to the received two-dimensional input, the customer service feature is provided. The customer service feature may provide information received from a remote source via a network, programming connection or other medium.
Owner:DISH TECH L L C
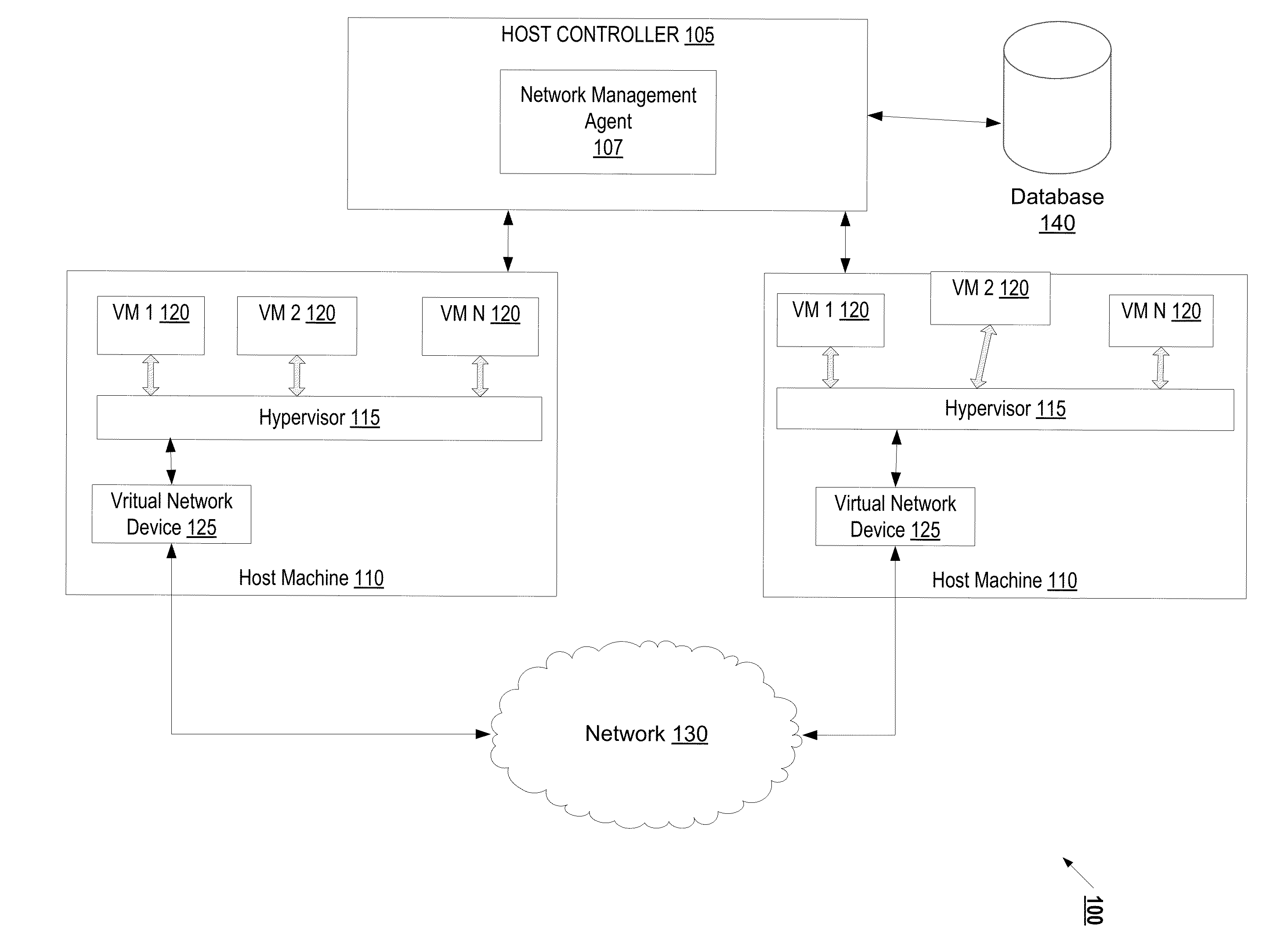
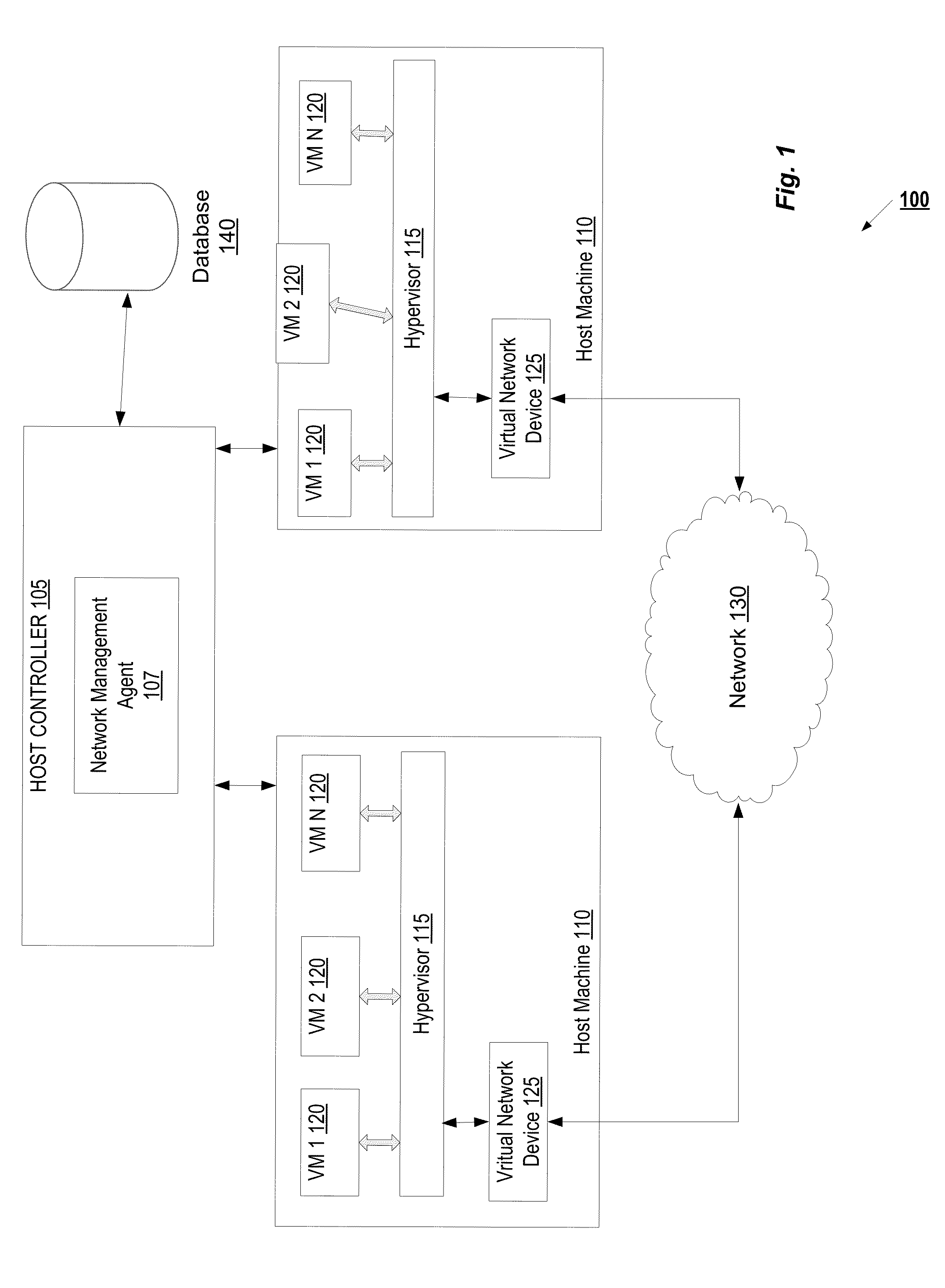
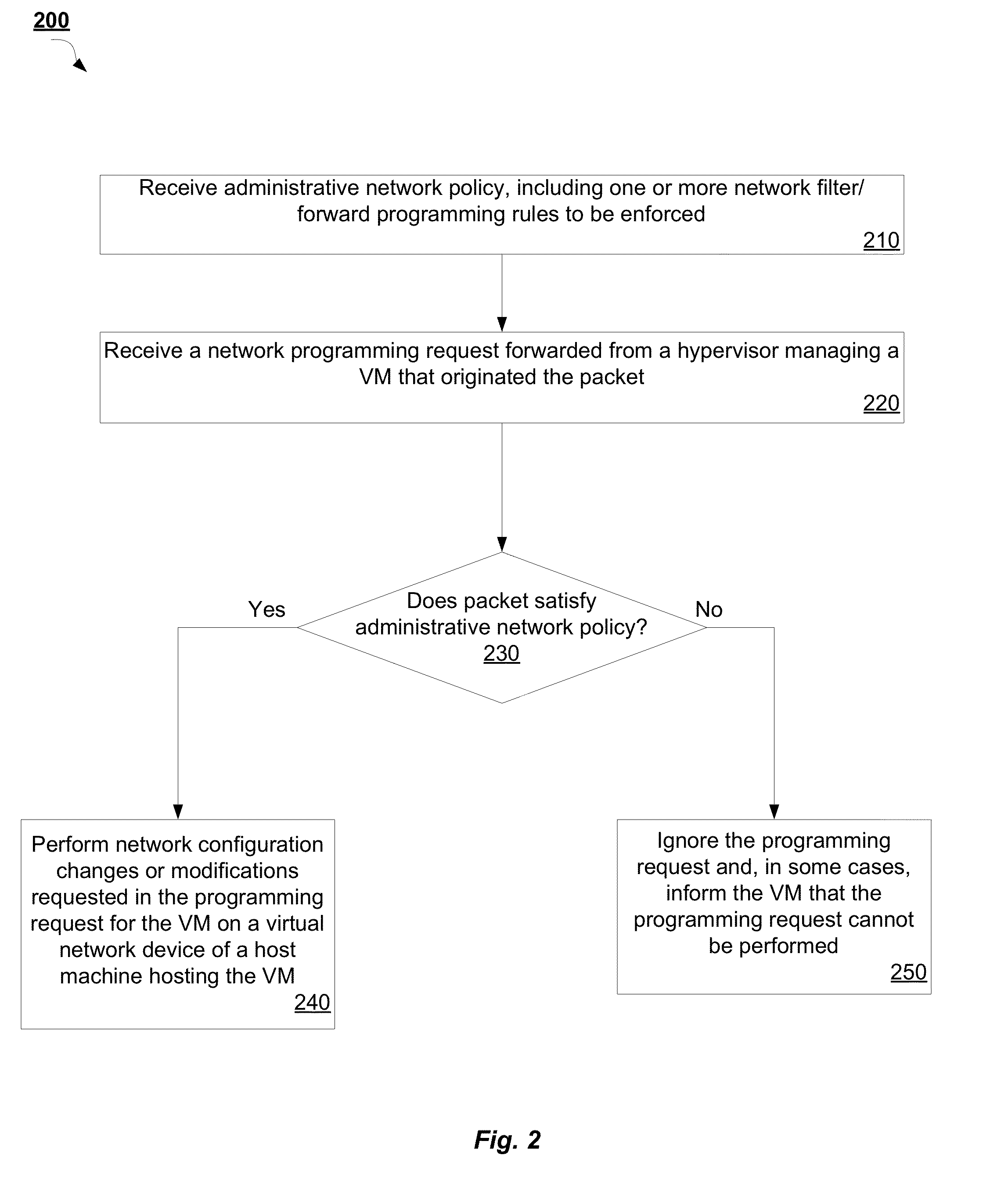
Mechanism for managed network filter/forward programming in a virtualization system
ActiveUS20130055242A1Multiple digital computer combinationsTransmissionWeb programmingVirtual machine
A mechanism for managed network filter / forward programming in a virtualization system is disclosed. A method of the invention includes receiving a network programming request from a hypervisor managing a virtual machine (VM), wherein the hypervisor intercepted the network programming request from the VM, determining whether the network programming request satisfies an administrative network policy, and updating network configuration settings as requested by the network programming request if the network programming request satisfies the administrative network policy, wherein the updating occurs without restarting the VM.
Owner:RED HAT ISRAEL
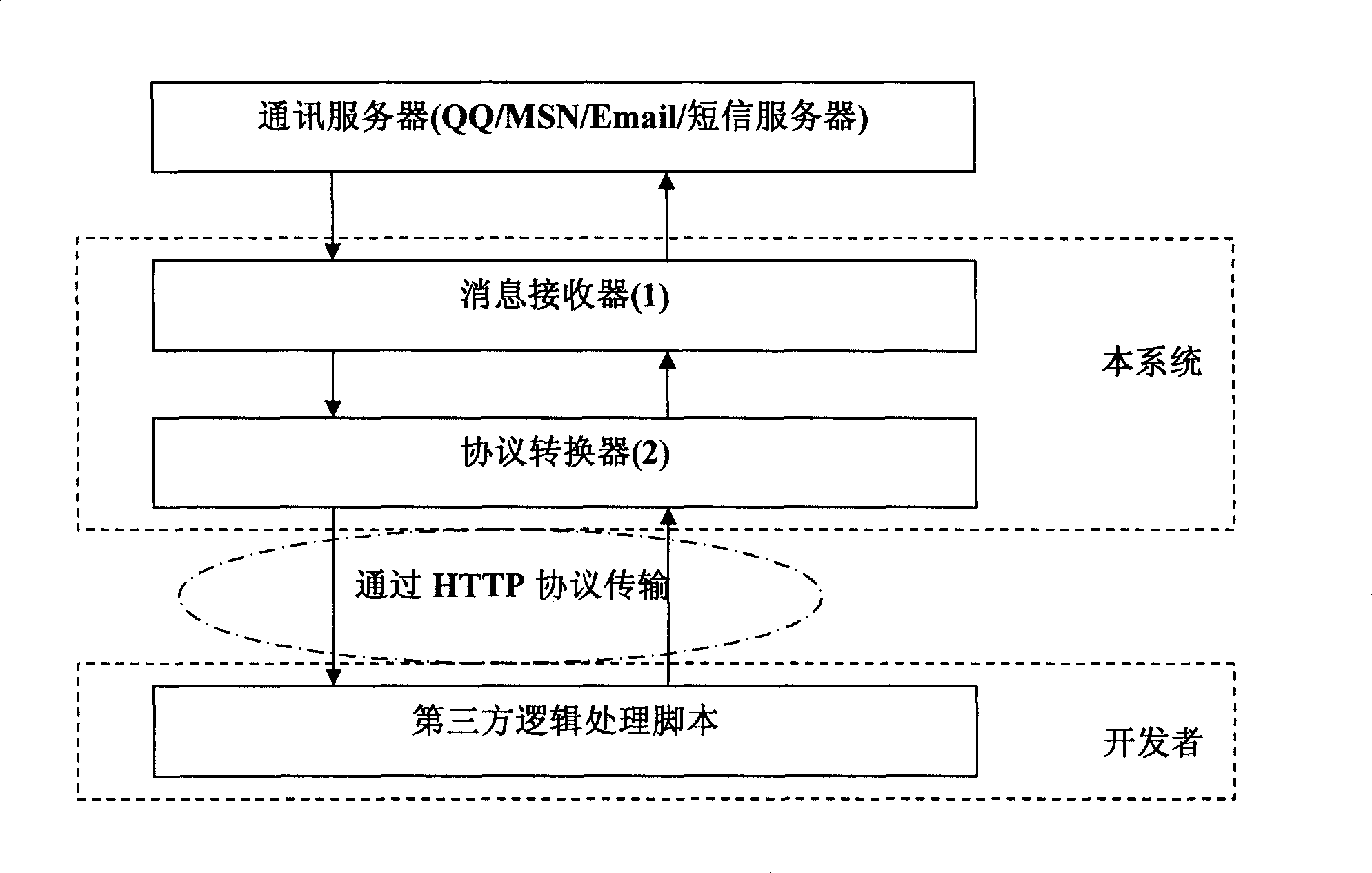
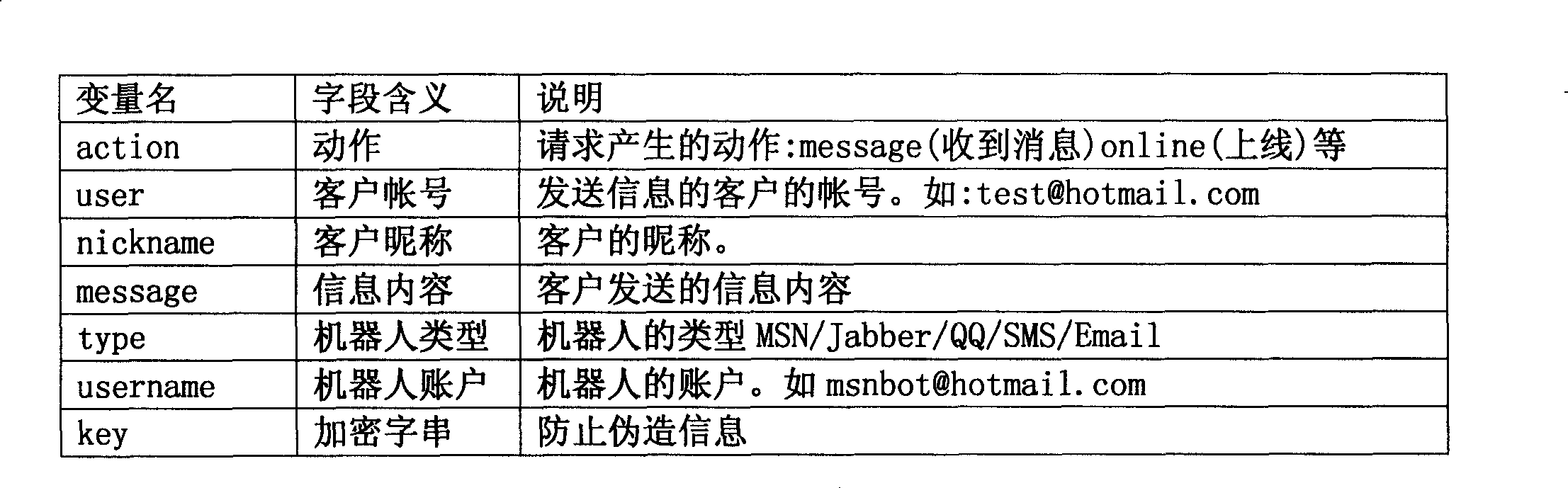
Communication robot protocol converting system
The invention describes a protocol conversion system for a communication robot. The system converts the protocol of different communication means to a universal HTTP protocol request; and a developer only needs to develop a dynamic web page to receive the HTTP protocol request, and carries out logical treatment according to parameters, namely the function of the communication robot can be achieved, thereby greatly reducing the difficulty in developing the communication robot. When information is received by the system, a standard HTTP request can be constructed, and sent to the logic treatment script of a third party; results are also returned by the script in an HTTP manner, and then the system reverts the results to a server. The developer only needs to use ASP, PHP and other Web programming language to compile the dynamic web page, namely the created communication robot. The developer only needs to pay attention to the logic treatment of the information, and does not need to pay attention to protocol difference among different communication tools.
Owner:陈正伟
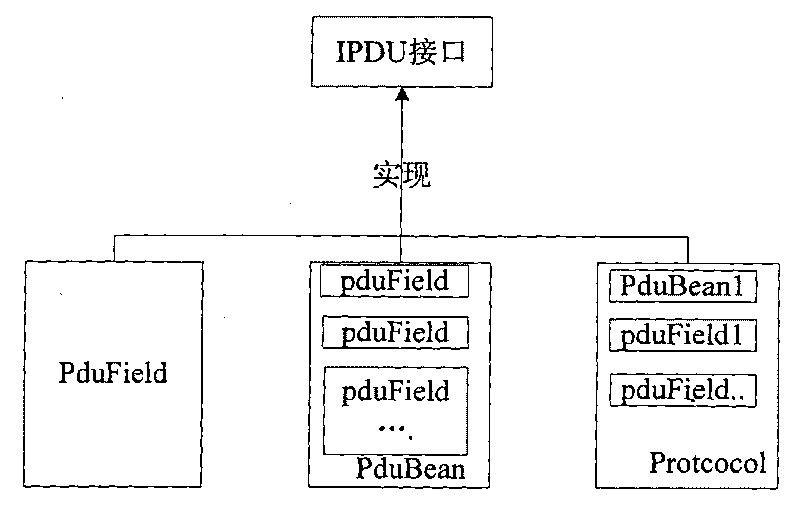
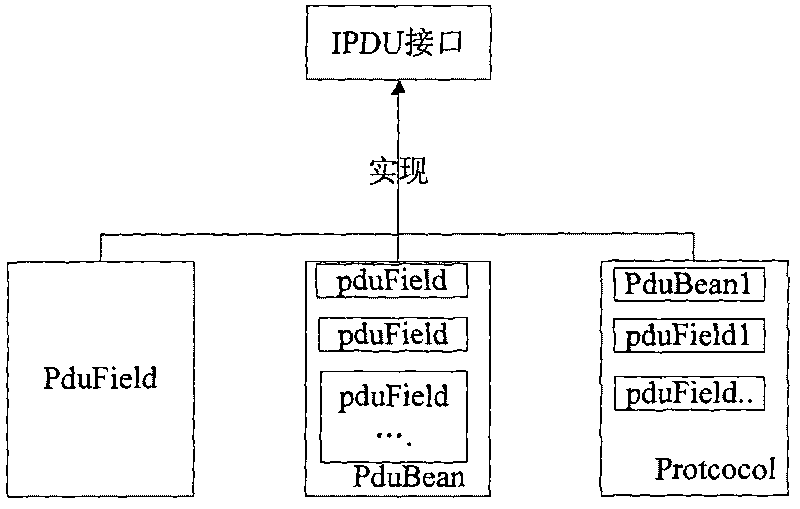
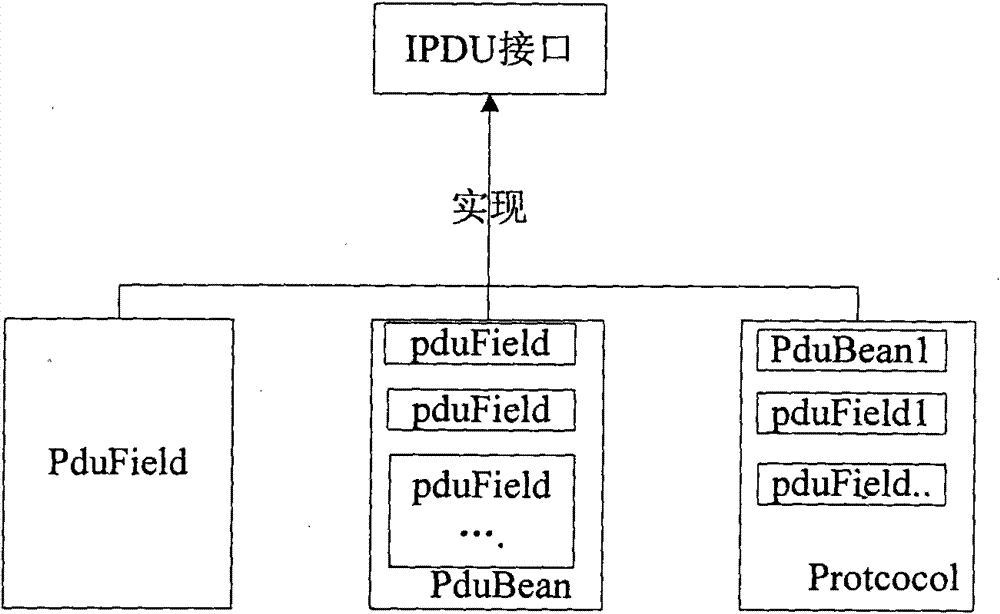
Method for implementing protocol data unit (PDU) used for packing and unpacking network bytes
ActiveCN101697546AImprove programming efficiencyEasy to packTransmissionTransmission protocolTraffic capacity
The invention discloses a method for implementing a protocol data unit (PDU) used for packing and unpacking network bytes, which comprises the following steps: firstly, defining an XML field configuration file of a needed transmission protocol; and then performing packing and unpacking, wherein the XML field configuration file comprises order, length and data type of fields in the transmission protocol. The method solves the problems of complex programming model and inconvenient protocol field change in the conventional network programming, improves the efficiency of network byte stream programming, facilitates packing and unpacking the network bytes, shields the difference of high-low bytes, and provides good debugging information and unified traffic monitoring.
Owner:WHALE CLOUD TECH CO LTD
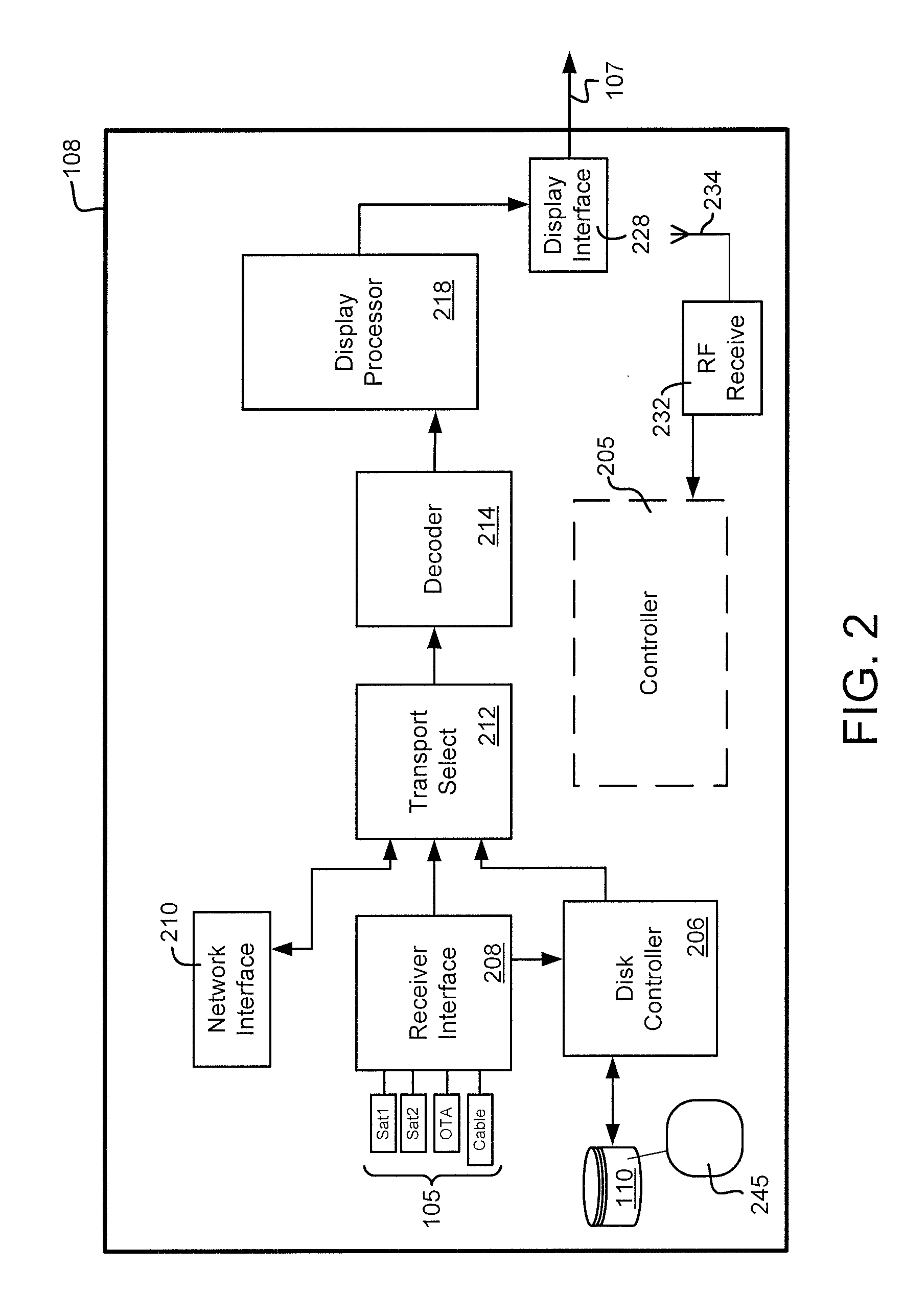
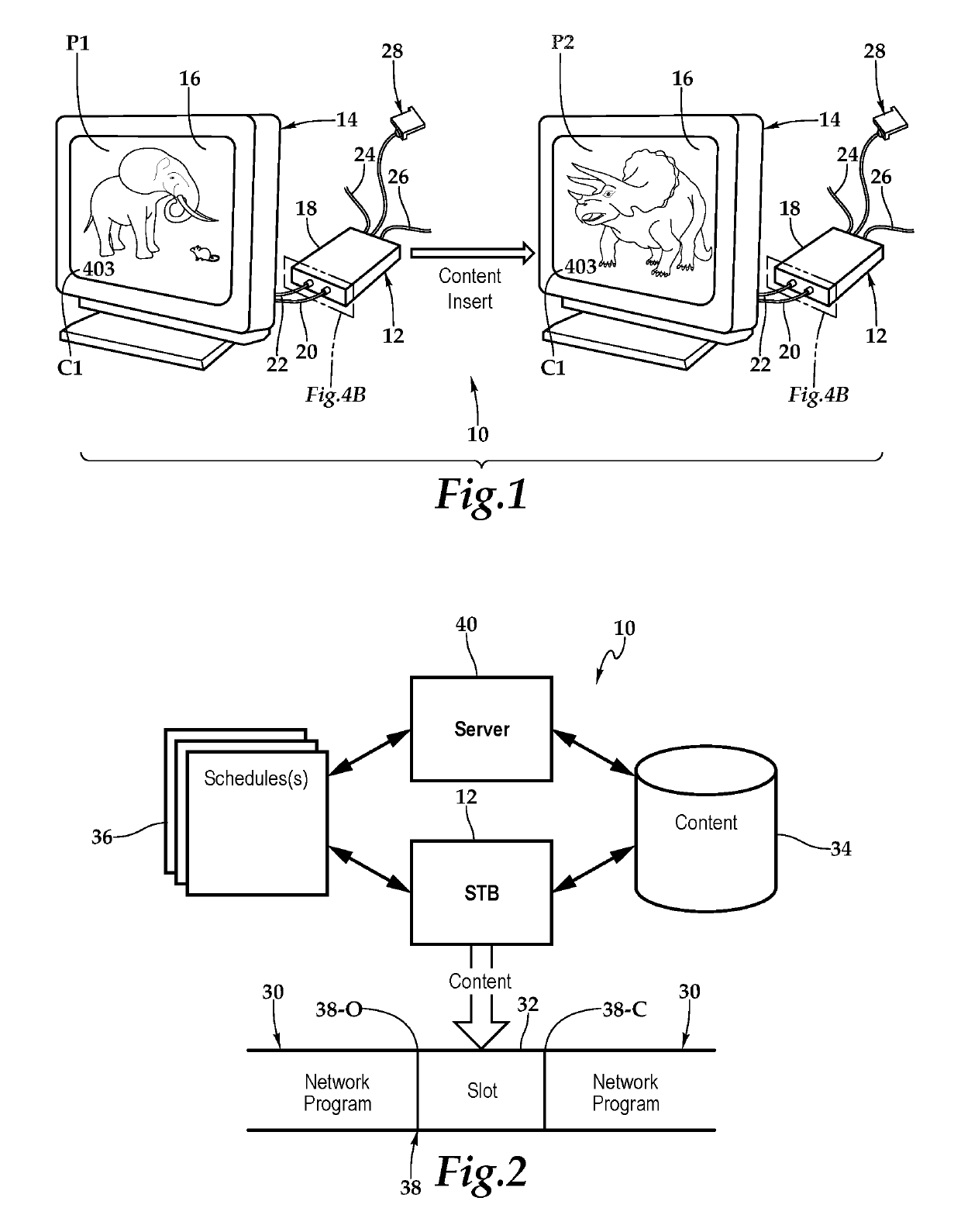
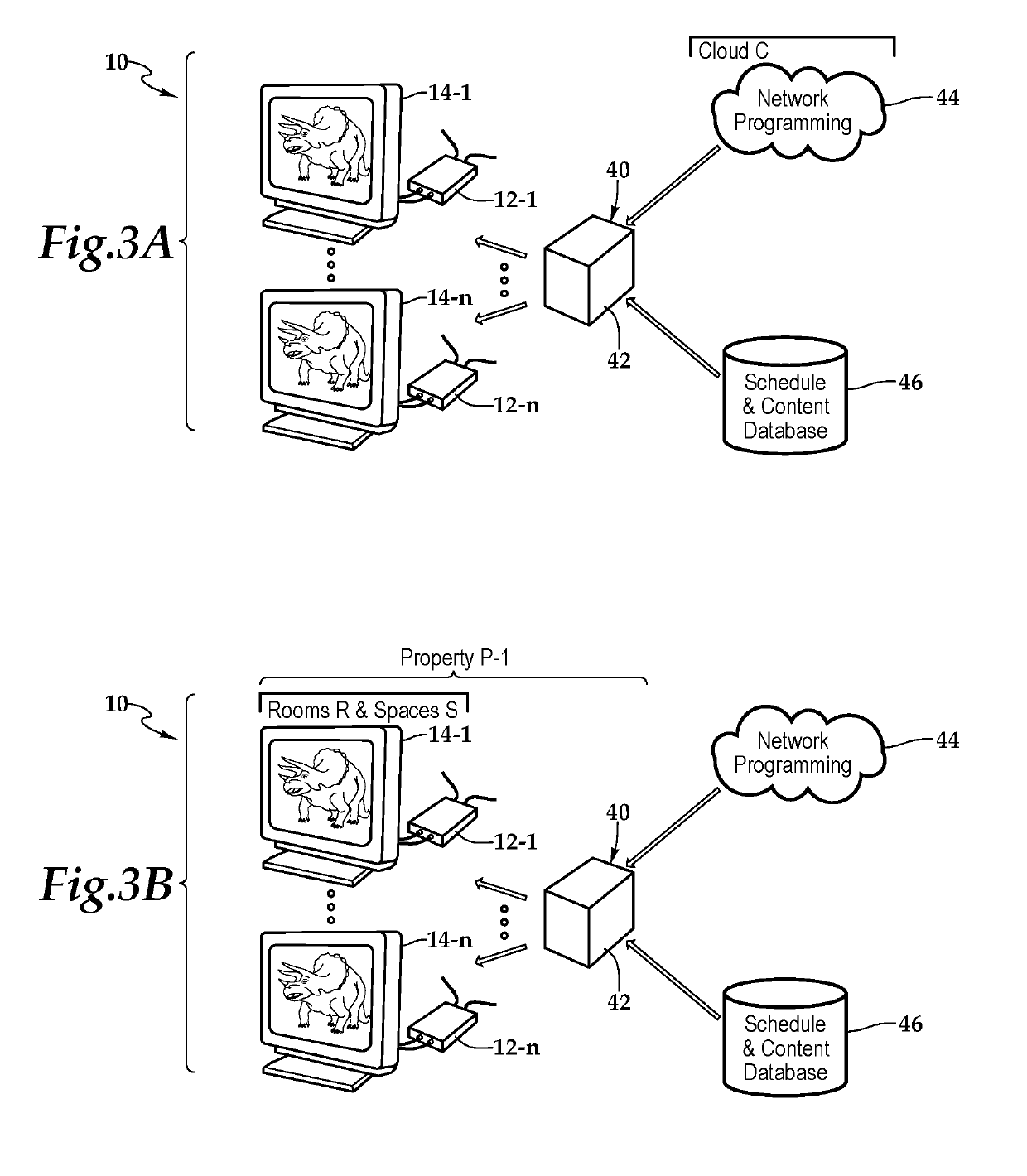
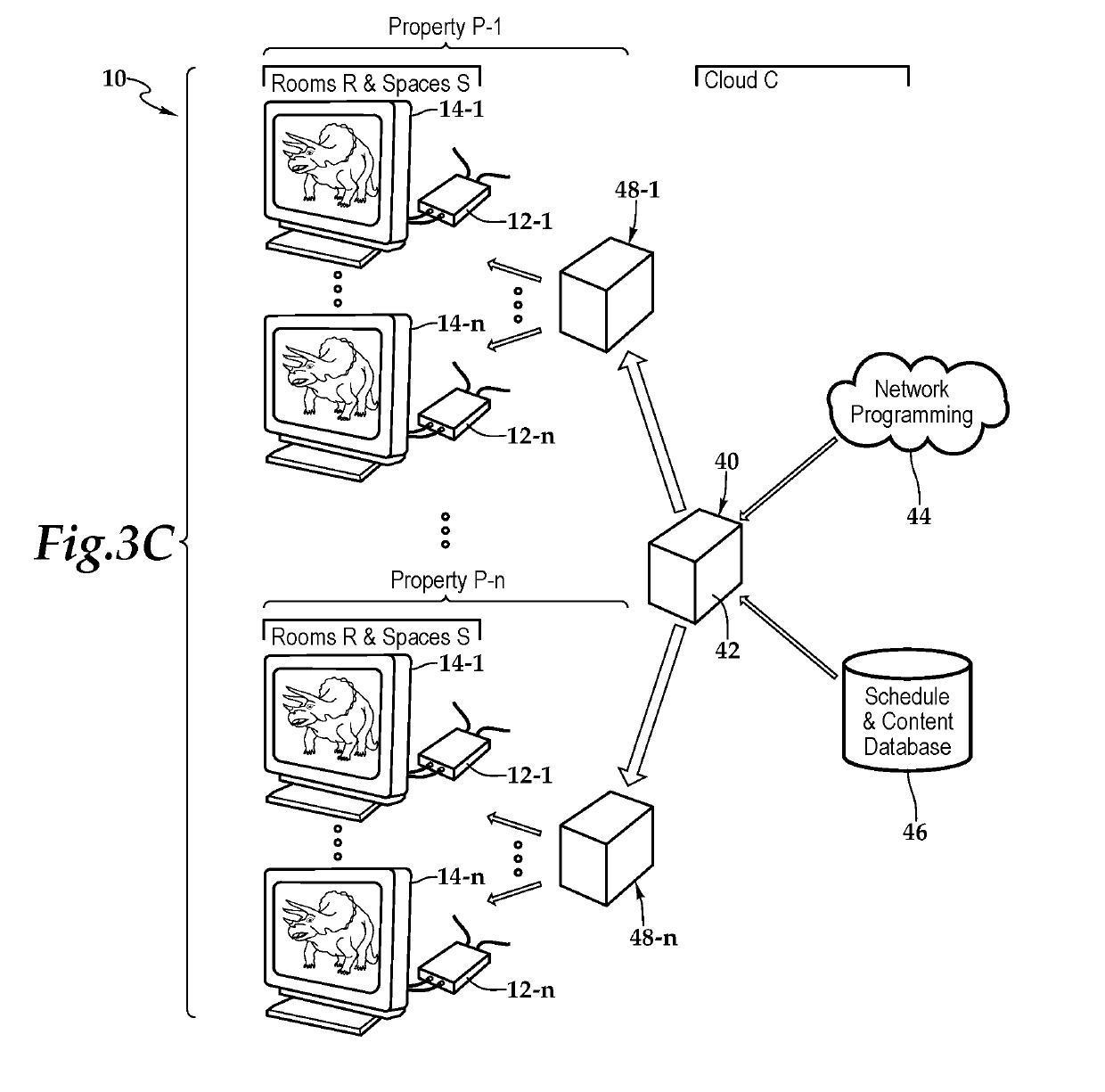
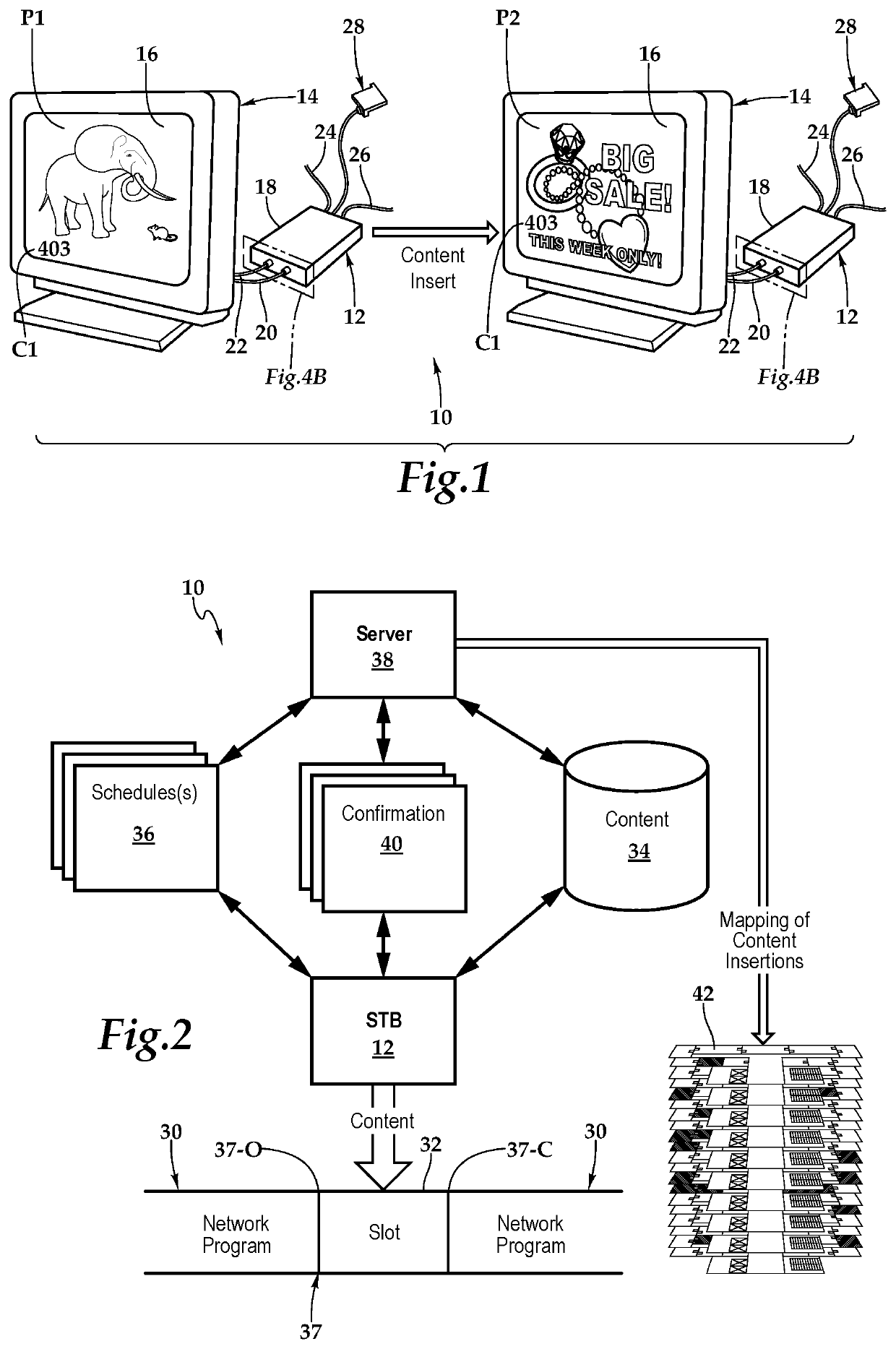
Set-Top Box with Enhanced Content and System and Method for Use of Same
A set-top box with enhanced content and system and method for use of the same are disclosed. In one embodiment of the set-top box, a signal input, a signal output, a processor, and memory are communicatively interconnected within a busing architecture in a housing. The signal input is configured to receive a source signal which includes a stream of network programming having time slots interposed therein. The set-top box detects signaling data indicative of a designated time slot within the network programming and responsive thereto, interposes content stored at the set-top box at the designated time slot within the network programming. The set-top box then forwards the interposed content to the display via the signal output. Following the forwarding of the interposed content, the set-top box returns to receiving network programming on the signal input and forward the network programming to the display via the signal output.
Owner:ENSEO LLC
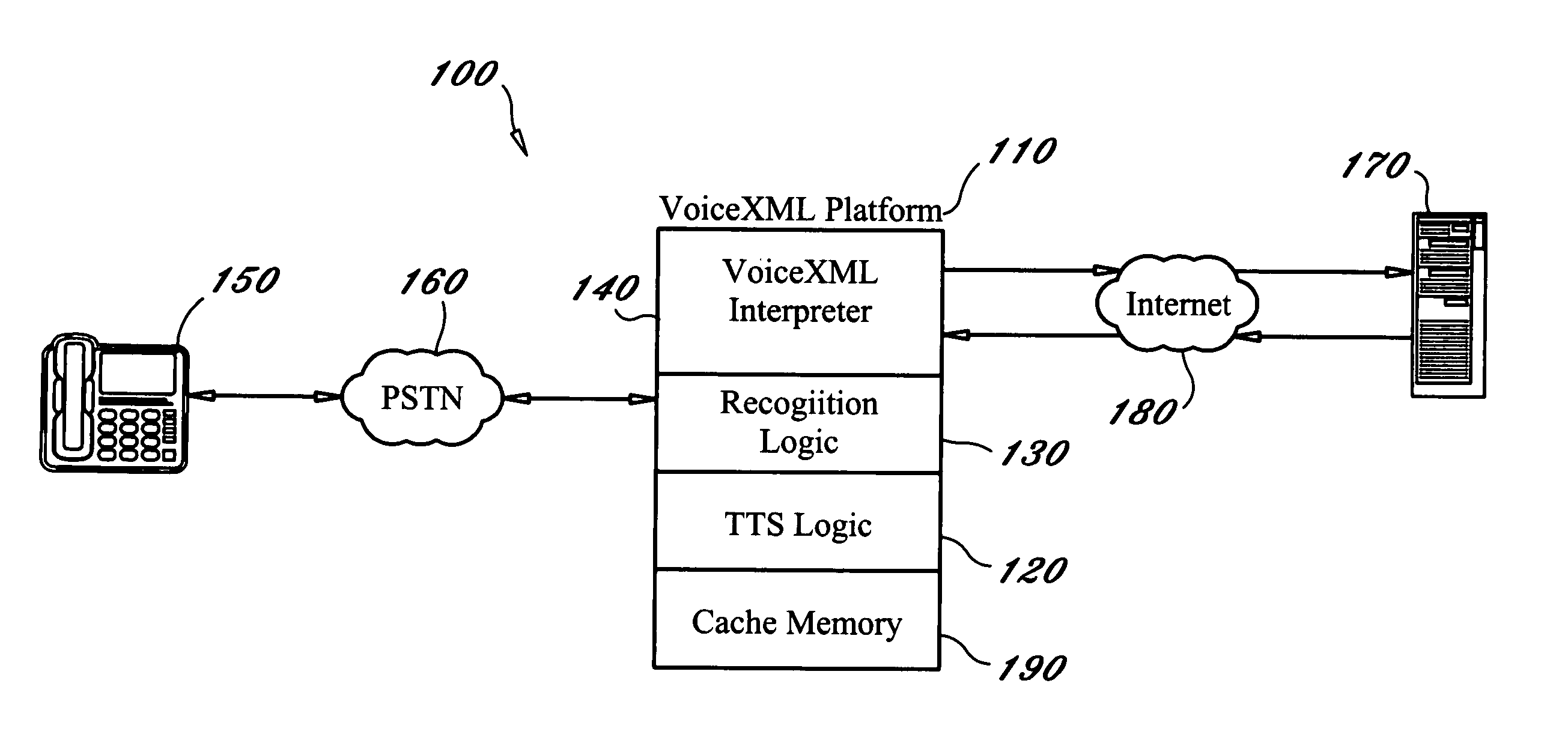
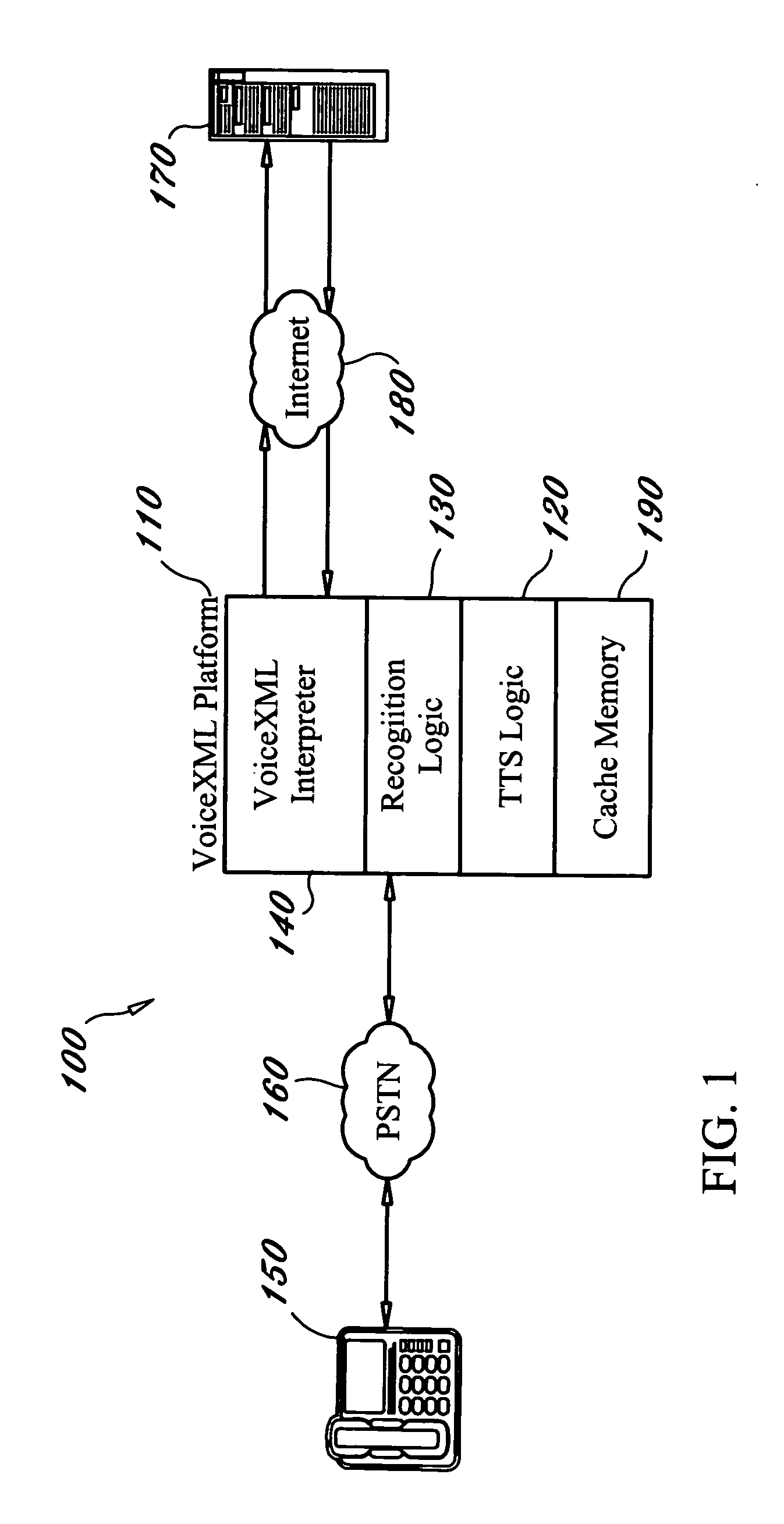
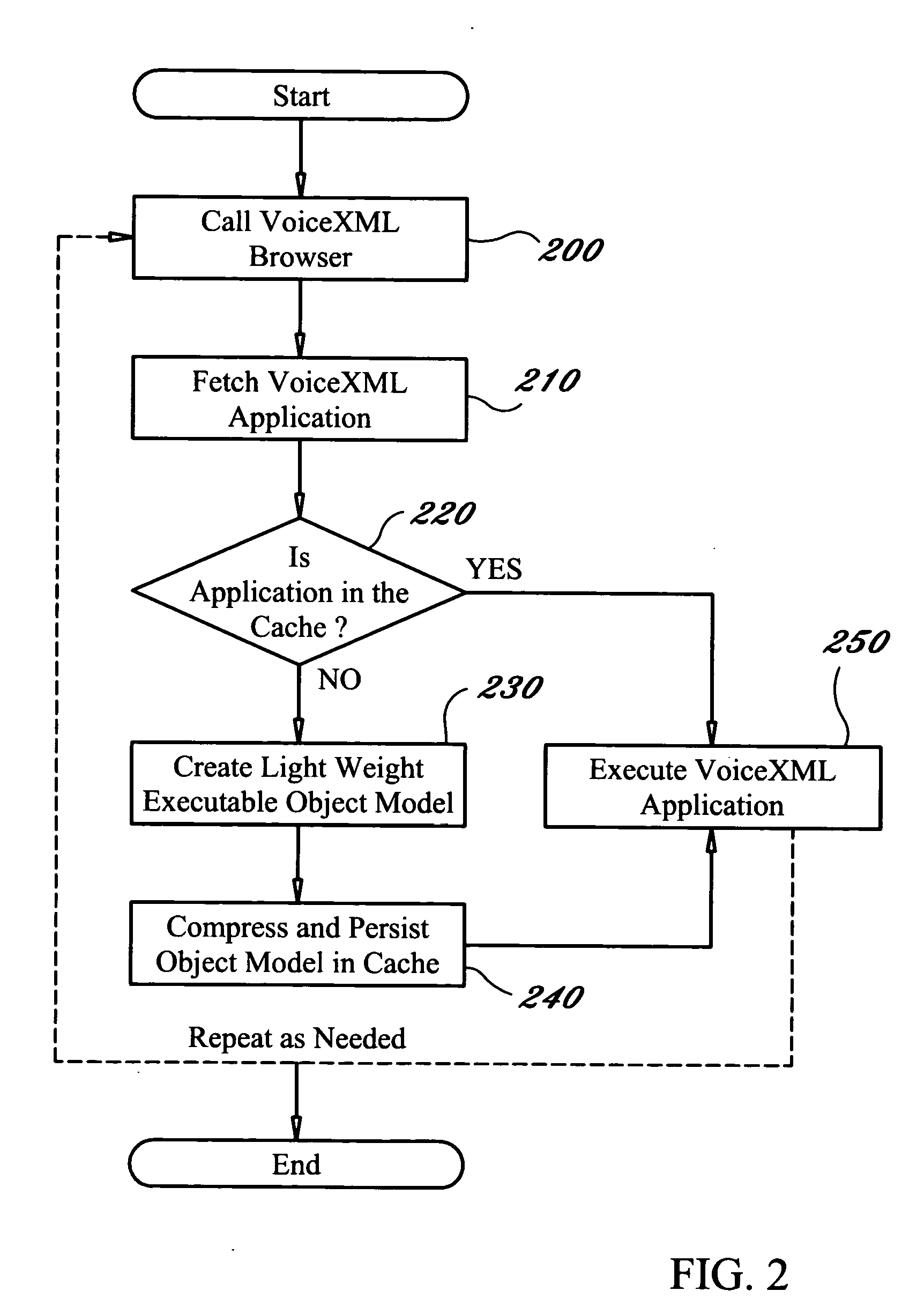
Method and procedure for compiling and caching VoiceXML documents in a Voice XML interpreter
InactiveUS20050135572A1Automatic call-answering/message-recording/conversation-recordingAutomatic exchangesSystem requirementsSmall footprint
A method and system of compiling and caching voice application documents in order to provide more efficient retrieval of resources in a web-programming model such as in the VoiceXML domain. The method and system of the present invention requires that a voice application resource such as a VoiceXML document first be transformed into a representative object model before it is stored in the system's cache memory, and that this model becomes the voice application resource that is ultimately executed by the VoiceXML interpreter. The representative object model contains all of the data of the original source document but in a compressed and optimized format therefore occupying a smaller footprint in memory. The representative object model also contains the code necessary to execute the data. Further, the compressed representative object model does not need to be compiled again before execution. Because the object model stored in cache contains a compiled representation of the original resource and not the original resource itself, it can be executed as a binary object, thus leading to greater efficiency during execution and the reduction of cost and hardware utilization.
Owner:LINKEDIN
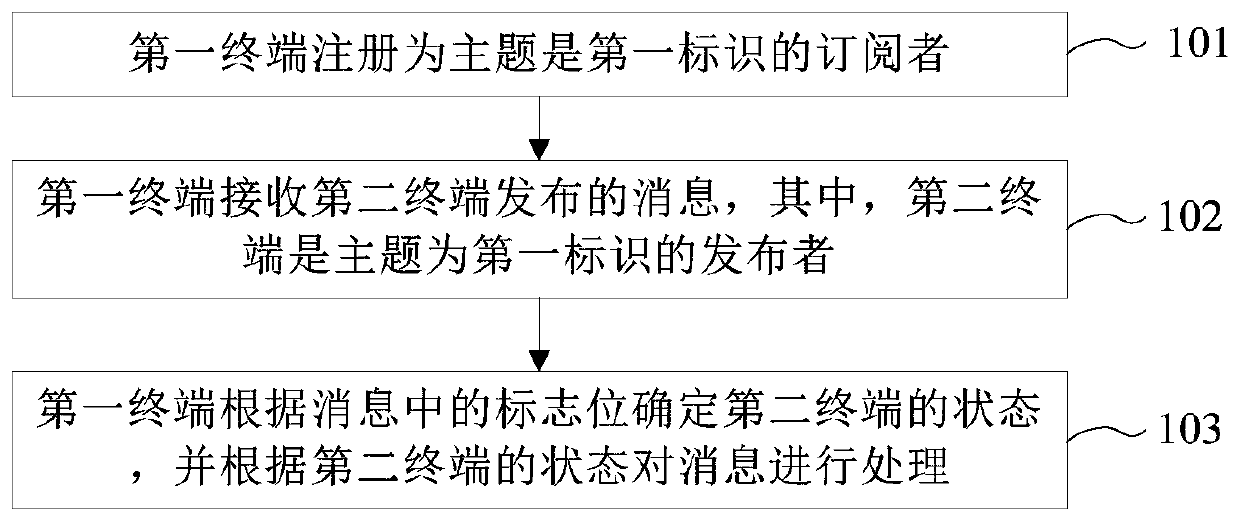
Method, device and equipment for achieving remote calling and computer readable storage medium
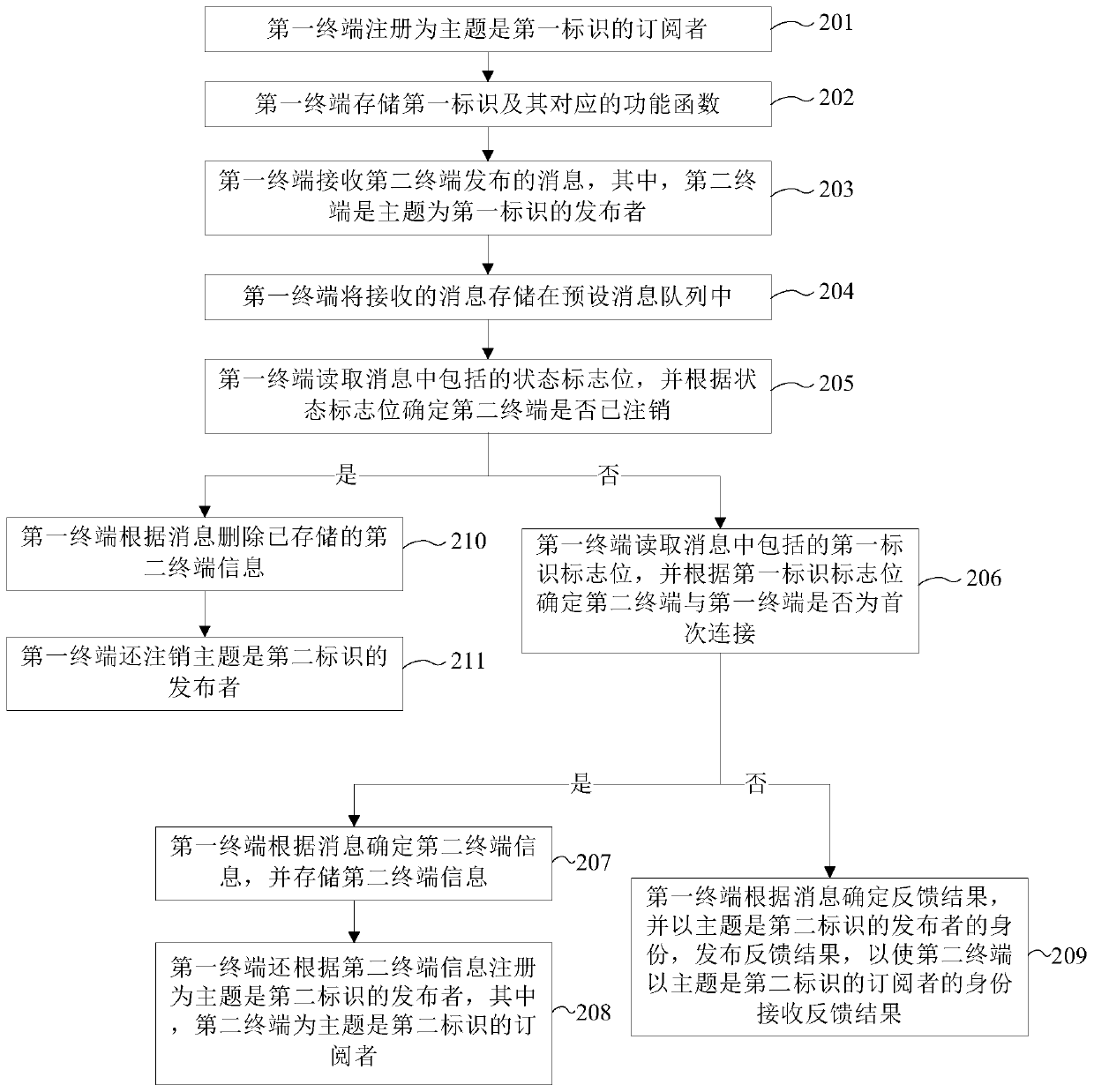
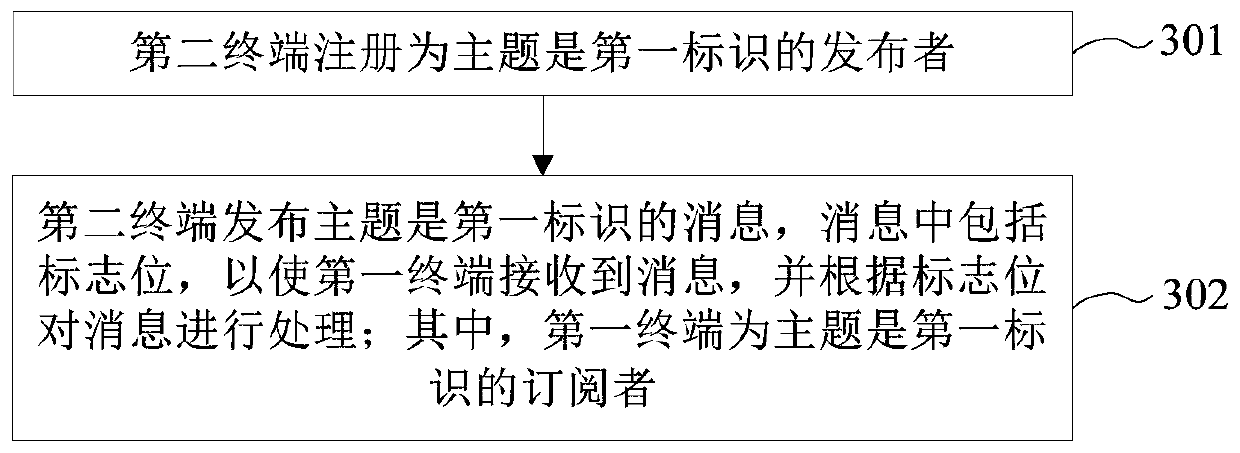
ActiveCN109857572AThe implementation process is simpleImprove flexibilityInterprogram communicationInformation transmissionWeb programming
The invention provides a method, device and equipment for achieving remote calling and a computer readable storage medium. The method comprises: registering a first terminal as a subscriber with the theme being a first identifier; the first terminal receiving a message issued by a second terminal, and the second terminal is an issuer whose theme is the first identifier; and the first terminal determines the state of the second terminal according to the flag bit in the message, and processes the message according to the state of the second terminal. Method provided by the invention, According to the device, the equipment and the computer readable storage medium, the RPC function can be achieved based on the MQTT protocol, information transmission is conducted through the identities of two terminals which are publishers and subscribers, and therefore the problem that in the prior art, an RPC scheme needs to be set up through a network programming mode is solved, and the scheme is simplerand more flexible to achieve.
Owner:APOLLO INTELLIGENT DRIVING (BEIJING) TECHNOLOGY CO LTD
HTTP request information processing method and device, medium and equipment
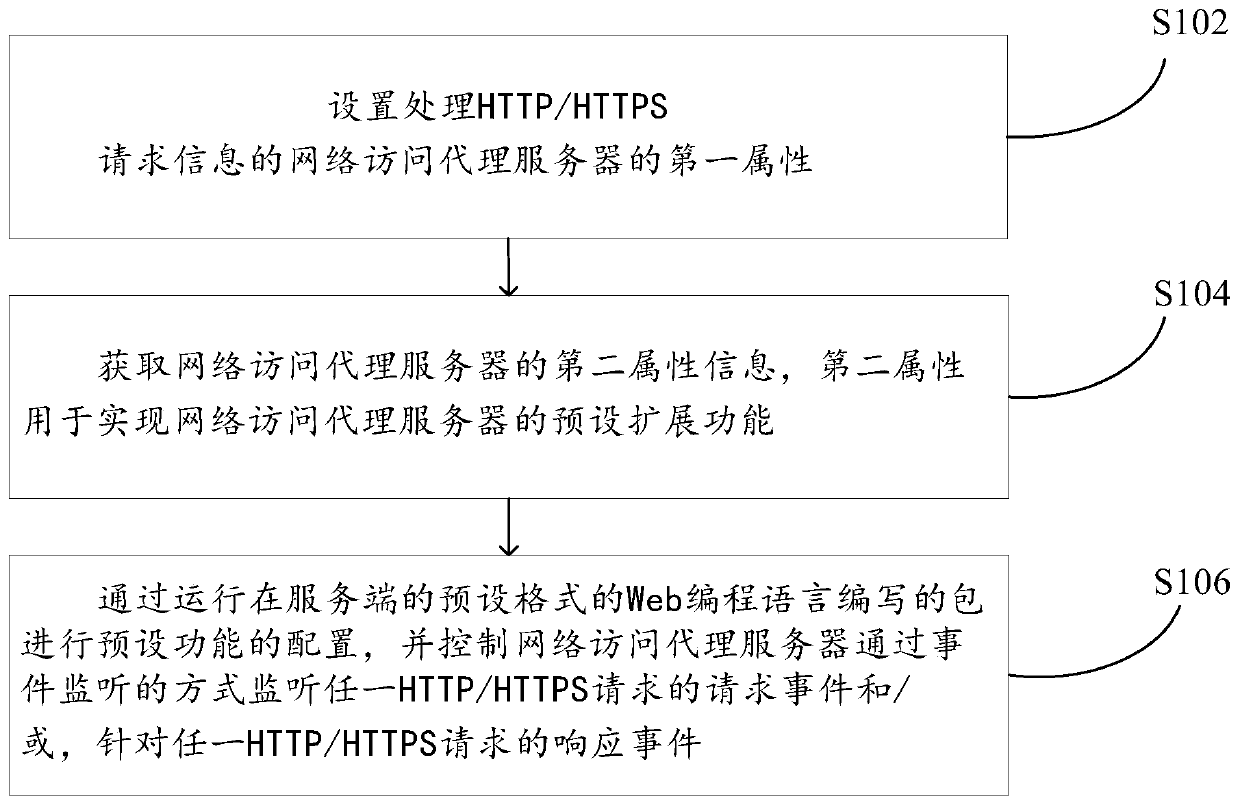
ActiveCN110493318ARich preset extension functionsMeet different needsTransmissionInformation processingHypertext Transfer Protocol over Secure Socket Layer
The invention provides an HTTP / HTTPS request information processing method and device, a medium and electronic equipment. The processing method comprises the following steps: setting a first attributeof a network access proxy server for processing the HTTP / HTTPS request information; acquiring second attribute information of the network access proxy server, wherein the second attribute is used forrealizing a preset extended function; configuring a preset function through a package compiled by a Web programming language running in a preset format at a server side; and controlling the network access proxy server to monitor a request event of any HTTP / HTTPS request and / or a response event for any HTTP / HTTPS request in an event monitoring mode. According to the method and the device, the preset function is configured through the package written by the Web programming language in the preset format and running on the server, so that the preset extended function of the network access proxy server can be continuously enriched to meet different requirements; and the process of configuring the preset function through the package compiled by the Web programming language in the preset formatis automatically completed, so that the existing excessively tedious function configuration process is simplified.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
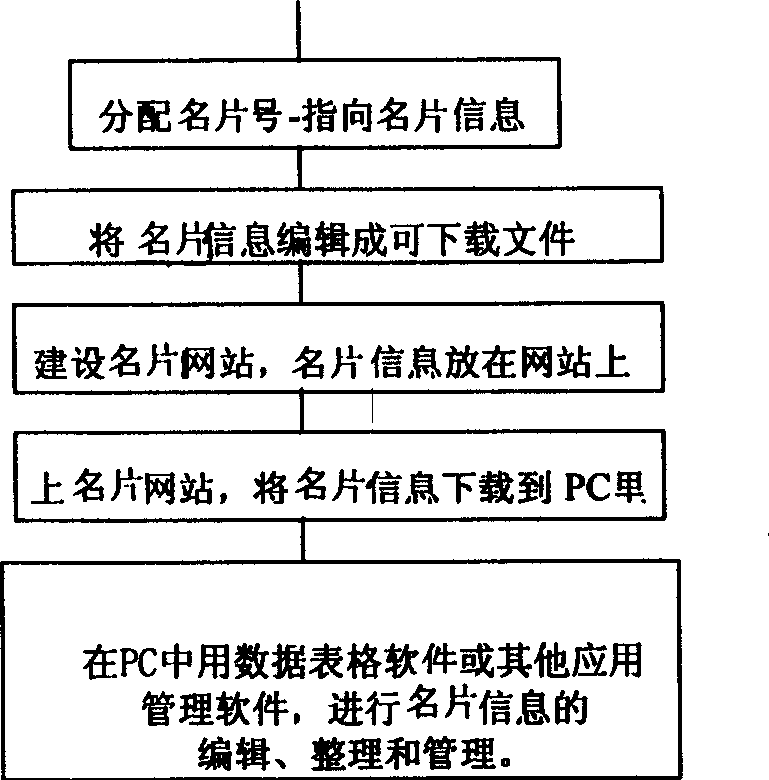
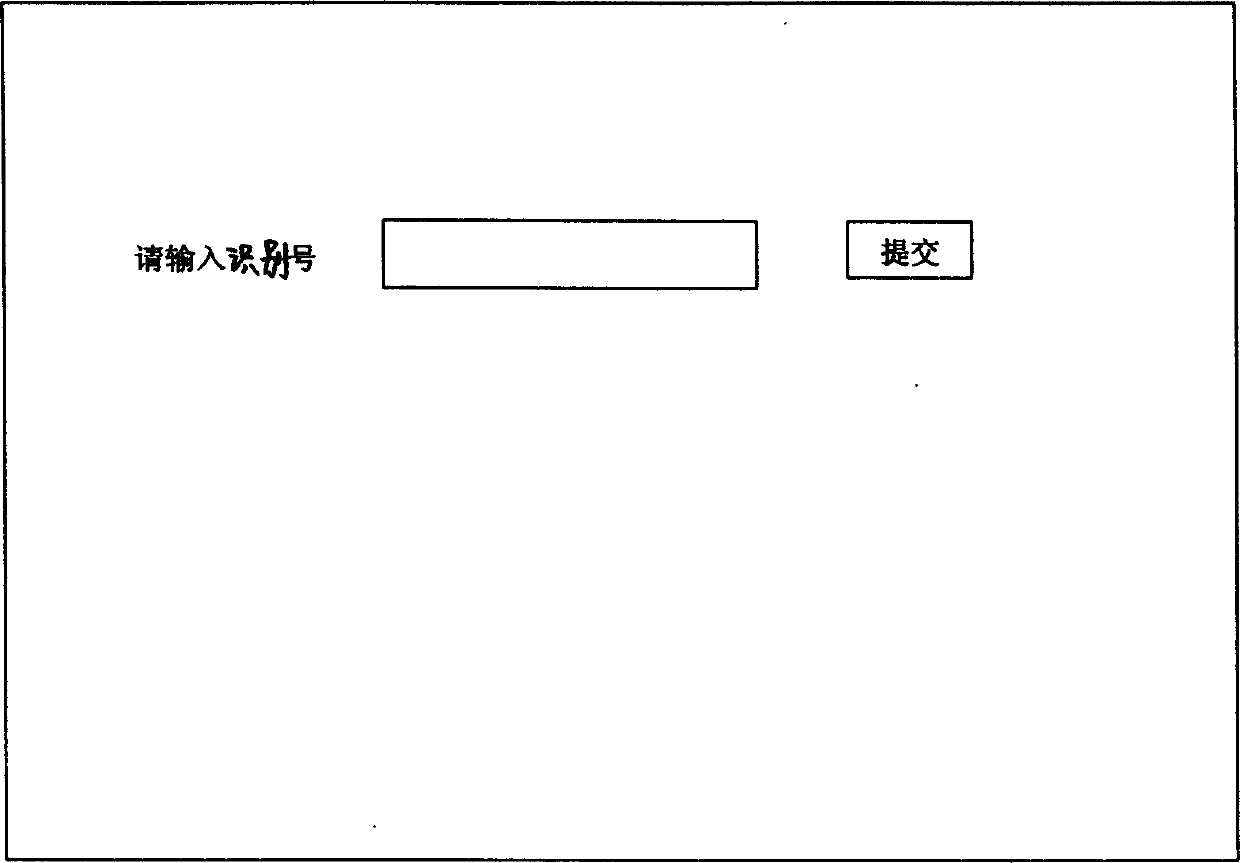
Establishment of visiting card information network and using method
InactiveCN1538314AEasy inputProgram control using stored programsMultiple digital computer combinationsWeb siteWeb service
The method includes following steps: (1) assigning an ID for person, who needs to build and down load information of name card on network; (2) personal information is input into computer terminal; (3) setting up dedicated web site based on Web programming language, storing down loadable files of information of name card under file directory in hard disk of Web server; (4) logging on the said web site to modify own information and down loading other's information of name cards. Comparing with the existing technology, the invention can update and down load information of name card at any time, keep information accurate. Moreover, multimedia information is allowed to add to information of name card.
Owner:赵磊
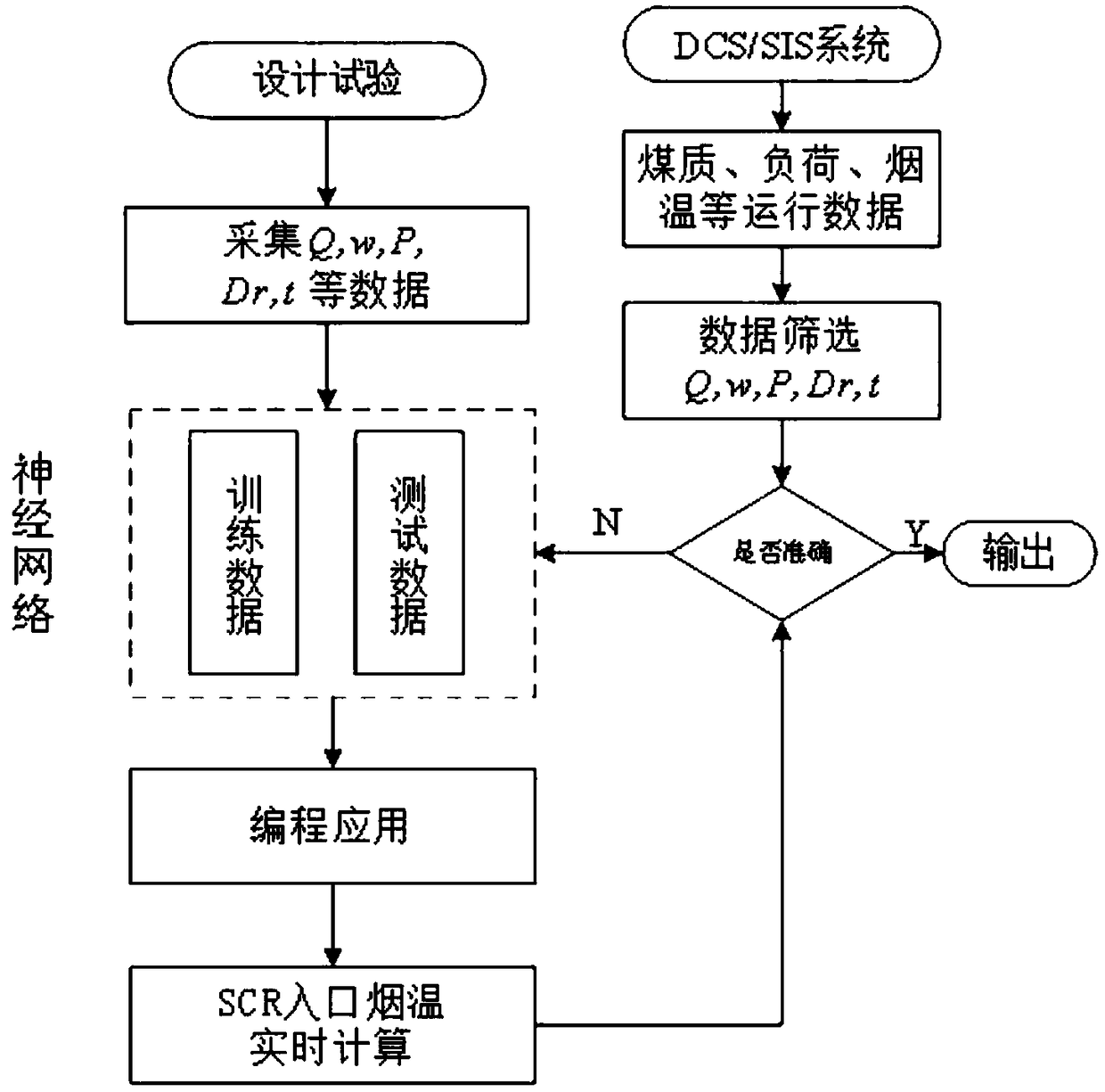
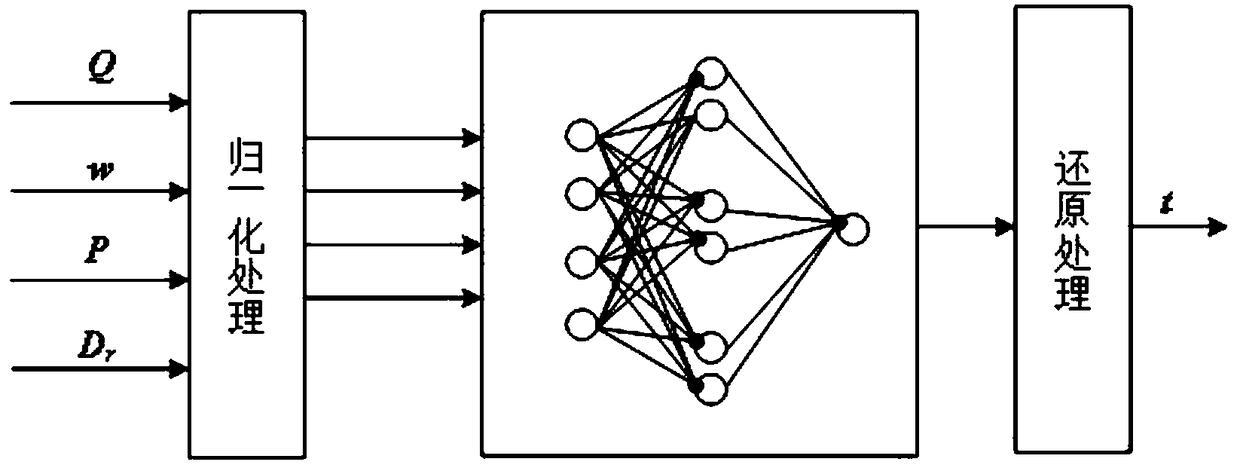
Combined heat and power generation unit SCR inlet smoke temperature online calculation method based on BP neural network
ActiveCN108647478ACorrect self correctAccurate determination of peak shaving limitsDesign optimisation/simulationNeural learning methodsCogenerationEngineering
The invention discloses a combined heat and power generation unit SCR inlet smoke temperature online calculation method based on a BP neural network. The method comprises the following steps of carrying out designing, carrying out multi-coal and multi-working-condition boiler thermal tests, obtaining test data of coal quality, load, heat supply steam extraction capacity and SCR inlet smoke temperature under different test working conditions, training the BP neural network through utilization of test data, and establishing an SCR inlet smoke temperature initial calculation model; issuing the smoke temperature initial calculation model in a form of an online website through utilization of a network programming technology, thereby realizing online determination of the SCR inlet smoke temperature under different operation conditions; and after the SCR inlet smoke temperature deviates, carrying out real-time online correction on the smoke temperature initial calculation model through combination of practical operation data of a thermal power generation unit. According to the method, related staff can calculate and predict the SCR inlet smoke temperature of a combined heat and power generation unit under different coal quality and different load rates in real time, the peak-load regulation limit of the set can be accurately determined, and when the boiler heat exchange condition is changed, the self-correction of a model can be realized.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +1
Method for summarizing data from a plurality of subordinate terminals to the same superior
InactiveCN105468773AUniqueness guaranteedAvoid confictSpecial data processing applicationsData needsApplication software
The invention discloses a method for summarizing data from a plurality of subordinate terminals to the same superior relating to the database management and network programming field. The method comprises steps as follows that: when the subordinate terminals are connected to the management application program of the superior, the management application program distributes unique three-digit terminal serial numbers to all connected subordinate terminals; the application programs of the subordinate terminals determine 9-digit terminal codes according to the terminal serial numbers; the front 6 digits of the terminal codes are local administrative division codes of the subordinate terminals; the rear three digits are obtained terminal serial numbers; the terminal application programs distribute recording tables according to the terminal codes and distributes unique data IDs to the data needed to be uploaded; the front nine digits of the data IDs are terminal codes; the rear digits are data serial numbers; the subordinate terminals upload the data and data IDs to the superior for being summarized and stored. According to the invention, the uniqueness of the data IDs is ensured without modifying the management application program of the superior; the data IDs are prevented from conflict; the operation process is relatively simple and is applicable to be popularized.
Owner:WUHAN OPENKER COMPUTING
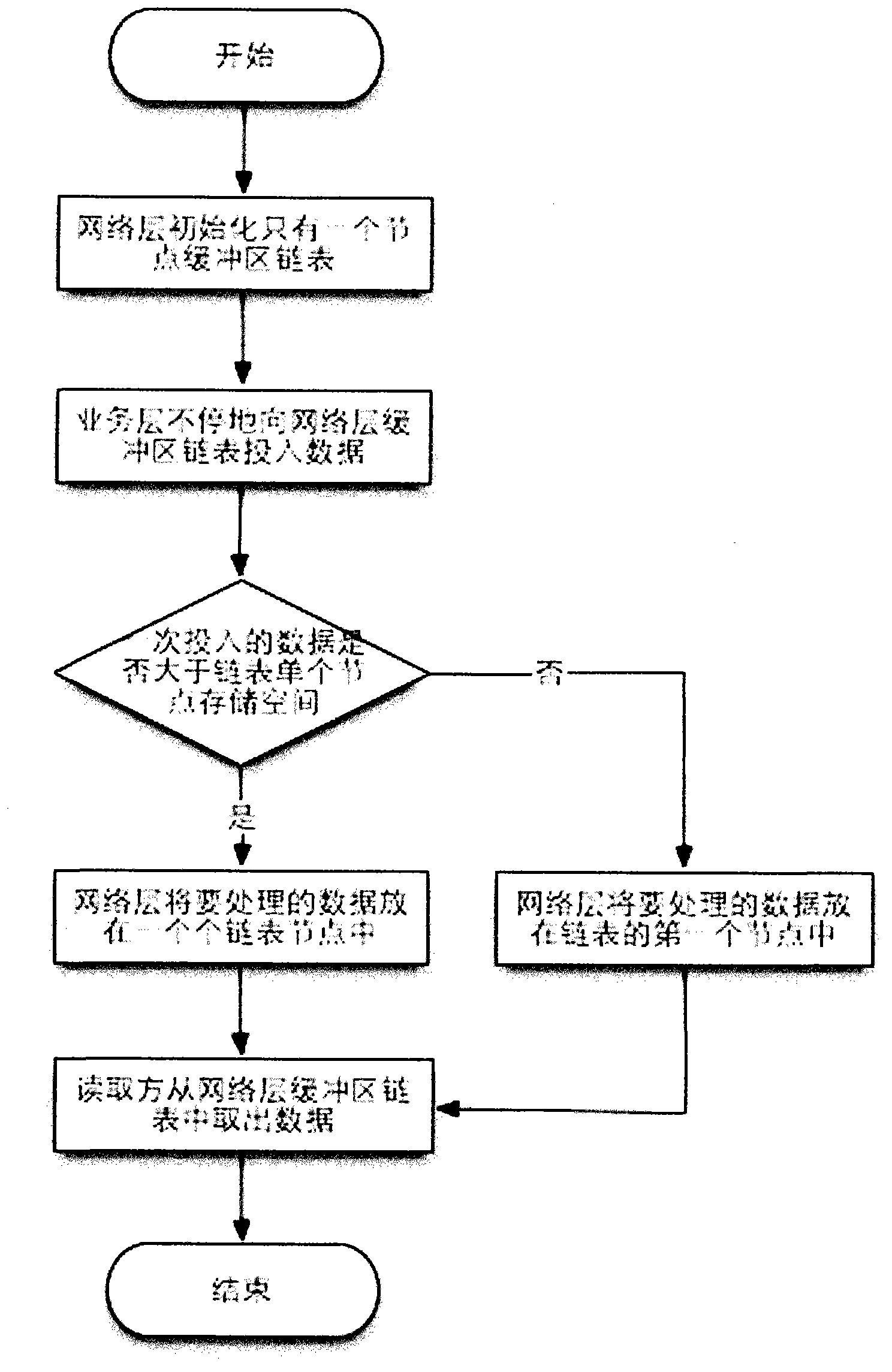
Design method for improving memory usage rate of buffer area in network programming
InactiveCN103259745AStrong addition and deletionSolve low usageMemory adressing/allocation/relocationData switching networksInternal memoryComputer network programming
The invention provides a design method for improving a memory usage rate of a buffer area in network programming, and relates to the field of network communication. A network layer processing message packet initializes a chain table of a buffer, and the chain table of the buffer area is only provided with one node of the buffer area and a distributed space for the node of the buffer area is 8KB. According to a service layer providing the source of the message packet, when the message packet is transmitted to the network layer to be processed, if the content of a message is smaller than 8KB, the message is placed on a first node of the buffer area of the chain table of the buffer area. A reading side taking out the data of the buffer area takes the data from the chain table of the buffer area of the network layer, and whenever reading of a buffer area is finished, the node of the buffer area is released from the chain table of the buffer area until the last buffer area. The design method for improving the memory usage rate of the buffer area in the network programming solves the problem that a usage rate is low due to the fact that an integrated continuous buffer area cannot retrieve part of internal memory.
Owner:EASTLAND DIGITAL CORP
Modularized self-help website building management system for intelligent websites
InactiveCN106294531AFast and convenient online constructionEasy and fast managementWebsite content managementSpecial data processing applicationsS systemArchitecture of Integrated Information Systems
The invention discloses a modularized self-help website building management system for intelligent websites. The self-help website building management system is an Internet-based Web technology, a B / S system structure, PHP and Mysql database construction are completely adopted, and operations transcending Unix / Linux / FreeBSD / Solaris / Windows (2000 / XP / 2003) systems can be realized. The modularized self-help website building management system is widely applied to online rapid building and daily management of various internet websites. By the management system, users do not need to download any software and master complex network programming technologies, and can quickly and conveniently build up and manage their own websites online only by typing. The website building management system overcomes defects of first and second generations of website building technologies, various necessary and common function modules for internet website building are enriched, and synchronization in website building and displaying is truly realized.
Owner:SHENZHEN RICH NETWORK TECH CO LTD
Yunten's web application methodology and web programming language (YWAM and WPL)
This invention introduces a structured software engineering methodology for developing interactive network application systems that use a web browser as a user-dialog engine. The methodology uses two server types: Application Server(s) for instantiating and executing an application instance in binary code, and HTTP Server(s) for delivering to the user's browser the textual HTML+Javascript user-dialog documents used by this application instance during its execution. An application is accessed by executing at the user's browser an Application Instantiation Page (AIP) which is a part of this invention. The methodology is built into a notational programming language.
Owner:YUNTEN TAMER
System simulation method
InactiveCN110233824AEffective research analysisOpen functionDesign optimisation/simulationTransmissionRemote controlWeb programming
The invention provides a system simulation method which is applied to a data transmission end, and the method comprises: the data transmission end generating an AFDX communication port configuration table through loading a configuration function in an upper application layer of a server side, then creating a sampling port, and completing the creation of an AFDX communication port; utilizing a network programming interface Socket socket to establish a server UDP port; receiving data of a remote controlled object through an AFDX communication port; and sending the remote controlled object data to a simulation control end through the server UDP port.
Owner:XIAN AVIATION COMPUTING TECH RES INST OF AVIATION IND CORP OF CHINA
Network programming framework system and method based on asynchronous IO model
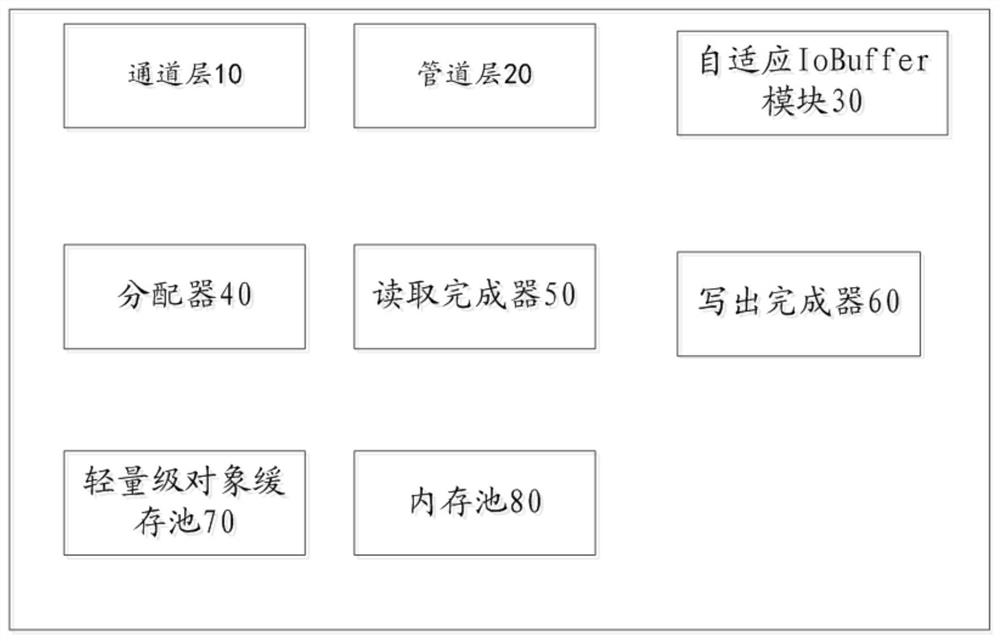
ActiveCN112230901AReduce coding difficultyGuaranteed uptimeResource allocationProgramming languages/paradigmsProcessor nodeOriginal data
The invention provides a network programming framework system and method based on an asynchronous IO model, and the system comprises a channel layer which is used for receiving to-be-processed original data; a pipeline layer which is used for reading the original data from the channel layer and operating the original data through a plurality of stored processor nodes; wherein the plurality of processor nodes are connected end to end through forward pointers and backward pointers to form a chain type processing model in a responsibility chain form, and each processor node is bound with a workerthread, so that the method of the processor node is executed in the bound worker thread. According to the embodiment of the invention, a single-thread running environment is provided for the processor node through the design of the context of the processor on the pipeline layer and the processor node, so that the coding difficulty can be reduced by giving the single-thread running environment toeach processor node, and the running performance can be improved by giving the possibility of serialization running of an overall responsibility chain mode.
Owner:厦门市易联众易惠科技有限公司
Content management system and method for use of same
ActiveUS10904640B2Selective content distributionElectrical cable transmission adaptationDisplay deviceEngineering
A content management system and method for use of same is disclosed. In one embodiment of the system, the set-top box is configured to receive a source signal which includes a stream of network programming having time slots interposed therein. The set-top box detects signaling data indicative of a designated time slot within the network programming and responsive thereto, interposes content stored at the set-top box at the designated time slot within the network programming. The set-top box then forwards the interposed content to the display. Following the forwarding of the interposed content, the set-top box returns to receiving network programming and forwarding the network programming to the display. The set-top box also provides confirmation of the displayed interposed content to a server, which may map the confirmation information.
Owner:ENSEO LLC
Method for realizing front-end cooperative debugging based on cloud computing and network programming
ActiveCN111367804AImprove collaboration performanceImprove collaborationInterprogram communicationSoftware testing/debuggingInterface (computing)Cooperative work
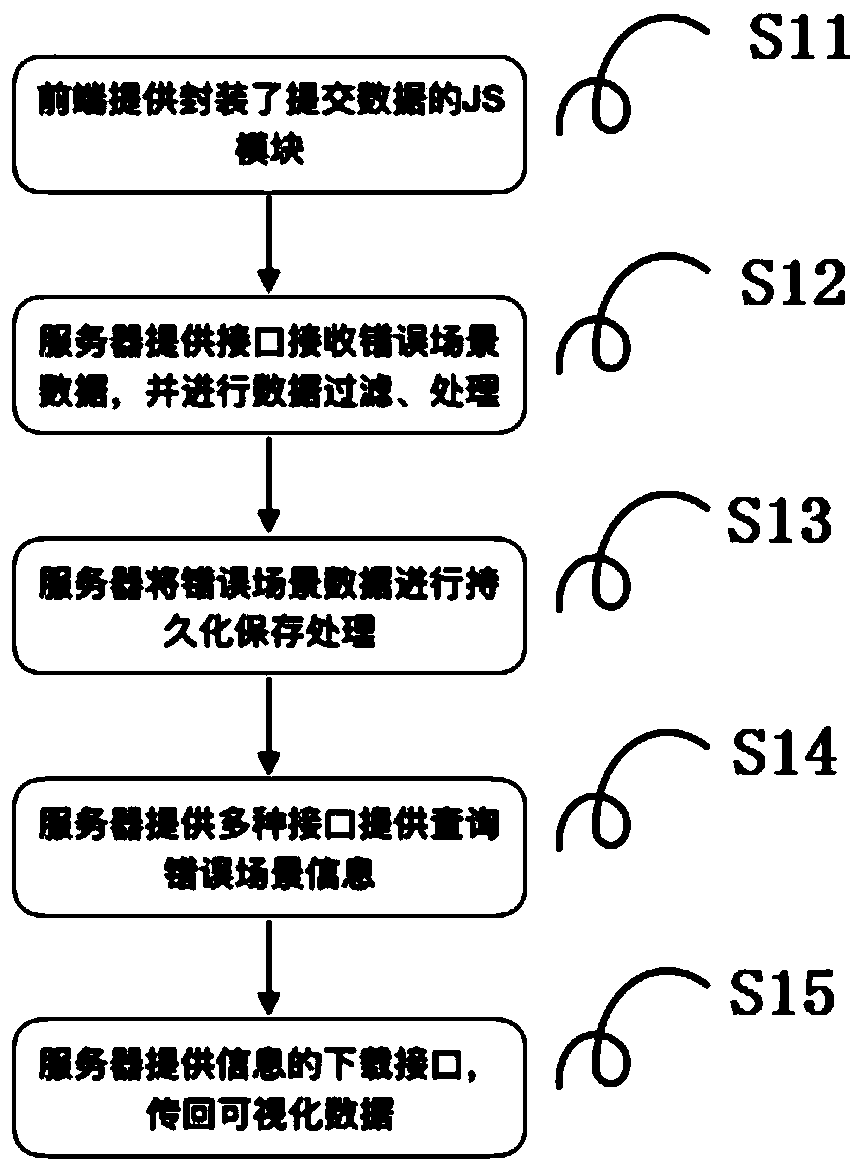
The invention relates to the field of computers, and particularly provides a method for realizing front-end cooperative debugging based on cloud computing and network programming, which comprises thefollowing steps of: S1, storing front-end error information into a database by utilizing a front-end error information storage model; wherein the front-end error information storage model comprises adatabase, a system server and a front-end transmission interface, the database is in interactive connection with the system server, and the outlet end of the front-end transmission interface is connected with the inlet end of the system server; s2, recovering an error scene by querying the error scene information transmitted in the step S1 in a database; through the steps of the invention, the cooperative work capability of front-end developers is enhanced. And the capability of an enterprise for emergently handling front-end product problems is effectively improved. And an error log system server is established, so that the capabilities of cooperative work and problem mutual troubleshooting of developers are effectively improved.
Owner:广州锦行网络科技有限公司
Point-of-cyber-access cyber system
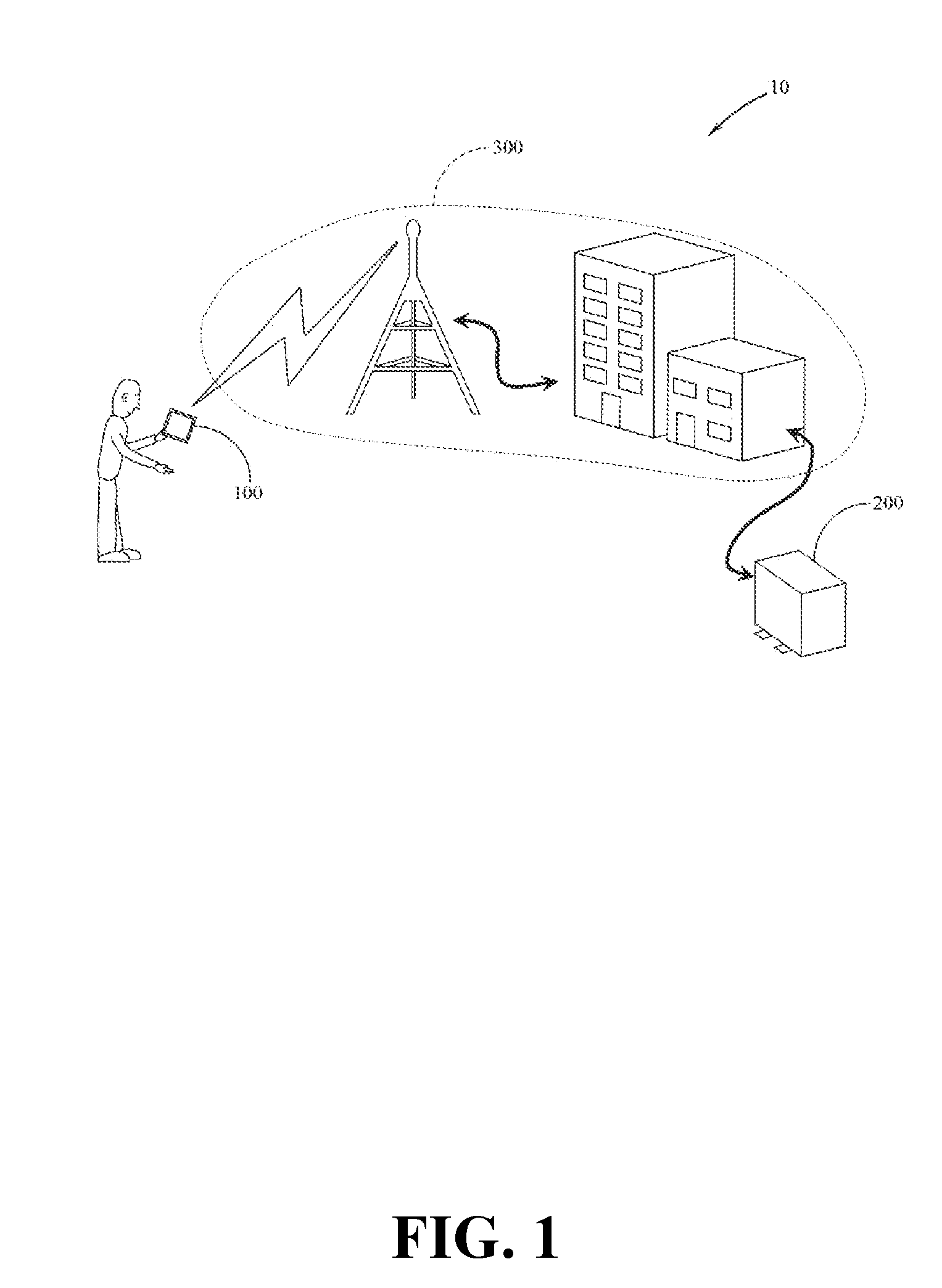
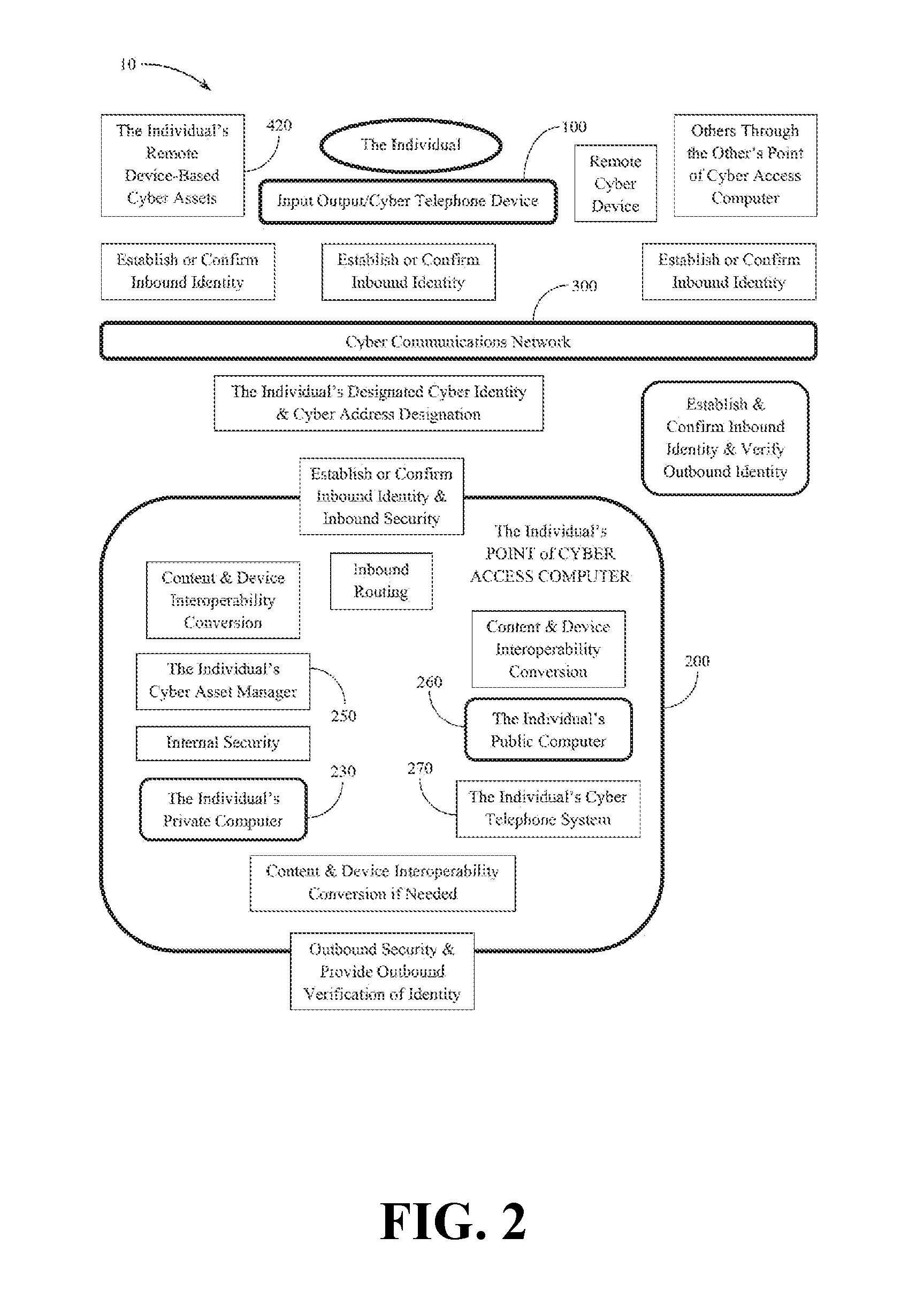
ActiveUS20160352740A1Minimize the numberDigital data protectionDetails for portable computersInternet privacyWeb programming
The system and system components of the present disclosure may be configured to provide individuals with both a safe and a secure cyber environment. Within this safe and secure cyber environment, each individual and each cyber device may be properly identified for all cyber interactions with others, and for all cyber interactions with the cyber devices of others. The system may also be configured to provide individuals with privacy for the individual's private cyber activities and cyber assets. Furthermore, the system may be configured to provide for environment-wide, interoperable use of any cyber device, cyber programming, and cyber content.
Owner:ARONSON JEFFRY DAVID
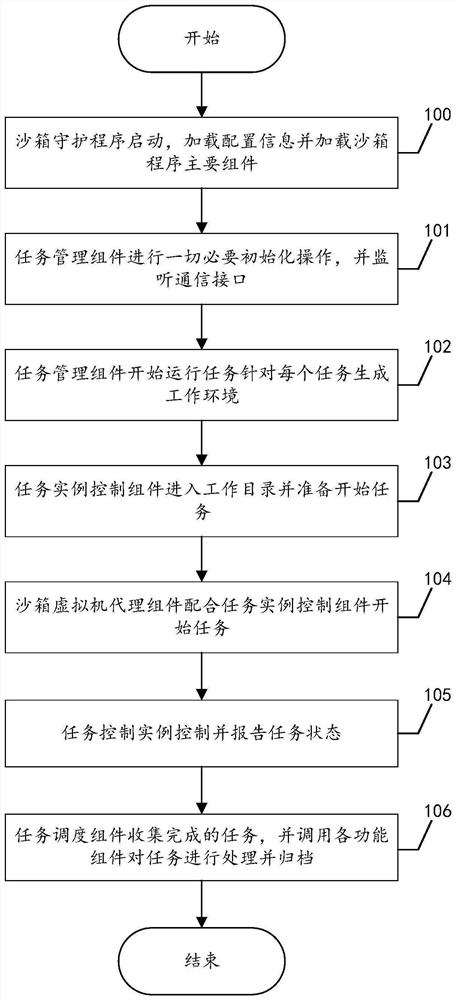
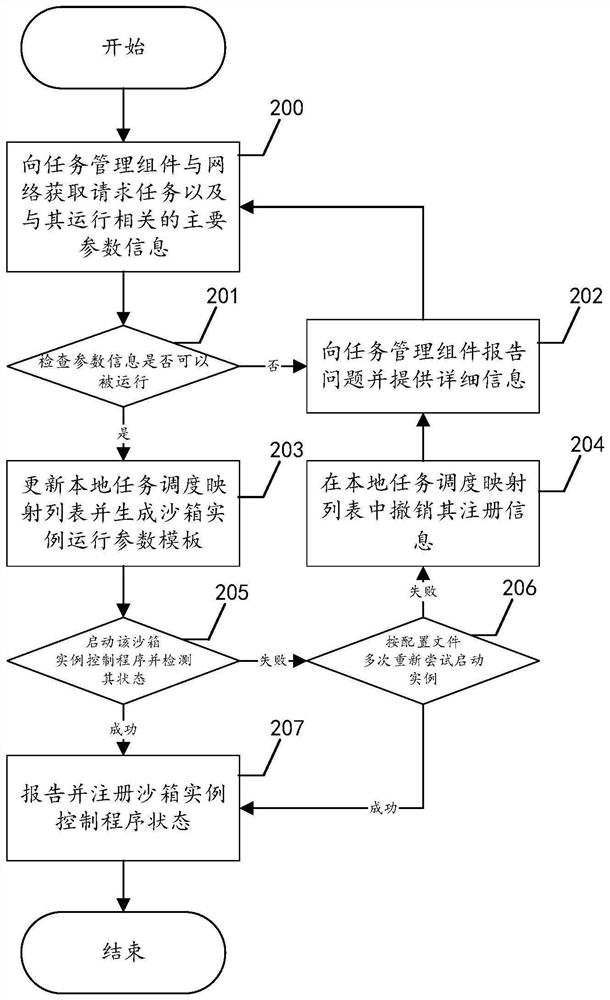
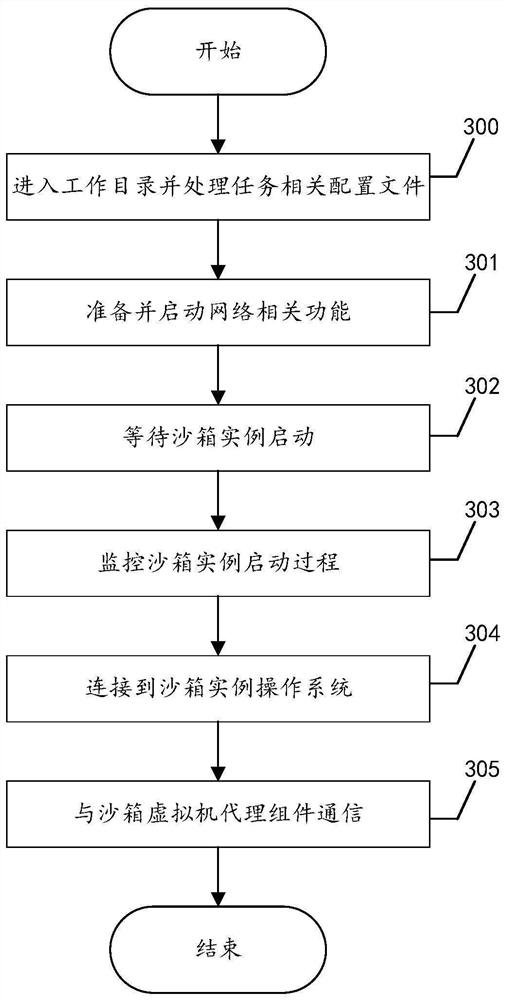
Sandbox-based malicious program behavior analysis processing method and system
PendingCN114491509AResolve interferenceStrong Analysis PerformancePlatform integrity maintainanceCommunication interfaceSoftware engineering
The invention provides a sandbox-based malicious program behavior analysis processing method and system, the method is executed in a network programming virtual execution environment, and the method comprises the following steps: starting a sandbox daemon, loading configuration information and loading a sandbox program main component; the task management component performs all necessary initialization operations and monitors a communication interface; the task management component starts to run tasks and generates a working environment for each task; the task instance control component enters a working directory and prepares to start a task; the sandbox virtual machine agent component cooperates with the task instance control component to start a task; the task control instance controls and reports a task state; and the task scheduling component collects the completed tasks, and calls each functional component to process and file the tasks.
Owner:UNIV OF JINAN
Remote dnc control method of numerical control system based on tcp/ip protocol and linux network programming
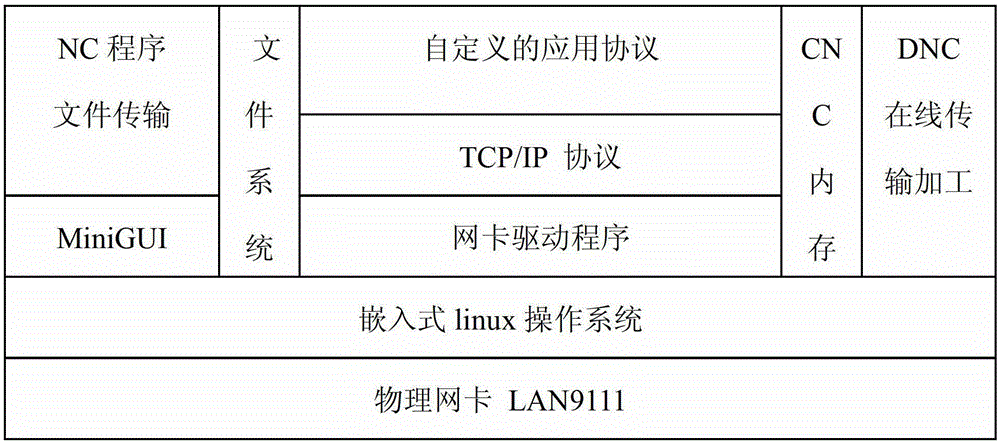
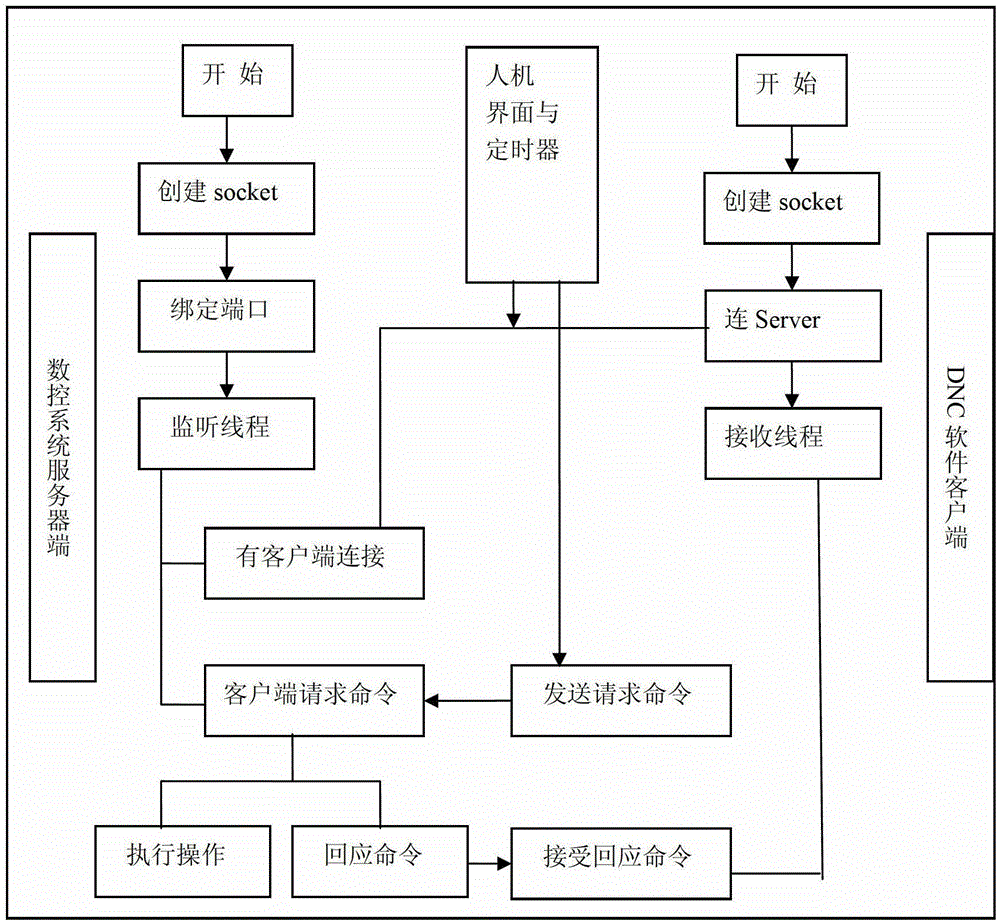
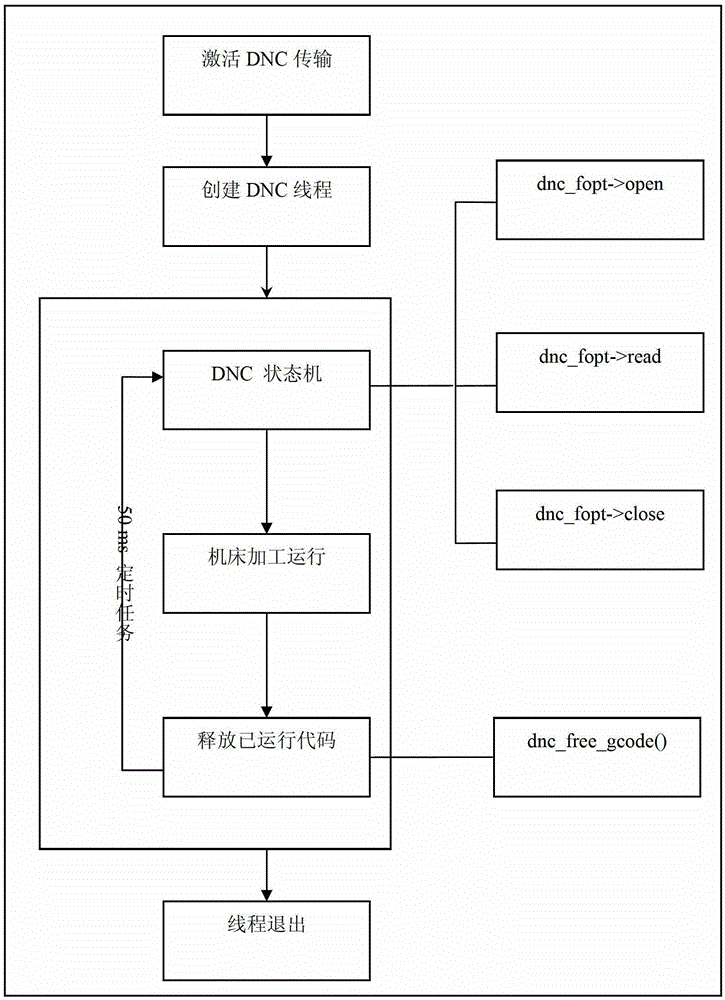
ActiveCN103064391BImprove transmission distanceAchieve sharingTotal factory controlProgramme total factory controlEngineeringCommunications media
The invention discloses a numerical control system long-distance direct numerical control (DNC) method based on a transmission control protocol (TCP) / internet protocol (IP) and a linux network program. The method includes the following steps: (1) starting a numerical system, creating a network thread, and binding a port and an IP; (2) monitoring all the time to know whether a client side is connected after the port and the IP are bound; (3) starting a timer and sending user-defined heartbeat packets to the numerical control system after the client side and the numerical control system are connected; and (4) a user listing network computer (NC) files, uploading NC programs, downloading the NC programs, deleting the NC programs, carrying out DNC transmission fabrication and stopping transmission fabrication on a user interface after the client side and the numerical system are connected. According to the method, the numerical system is used as a server, a user computer serving as the client side constructs a network environment with the TCP / IP as a bottom layer protocol and a twisted pair line as a communication medium, the TPC / IP is used as a communication protocol for sending information, data transmission rates and anti-interference capacity are improved, connection with an internet is convenient, and data sharing is achieved.
Owner:GSK CNC EQUIP
SDN network programming method and device and readable computer storage medium
PendingCN112732226ASupport online updateAvoid interruptionProgramming languages/paradigmsSoftware designService flowData pack
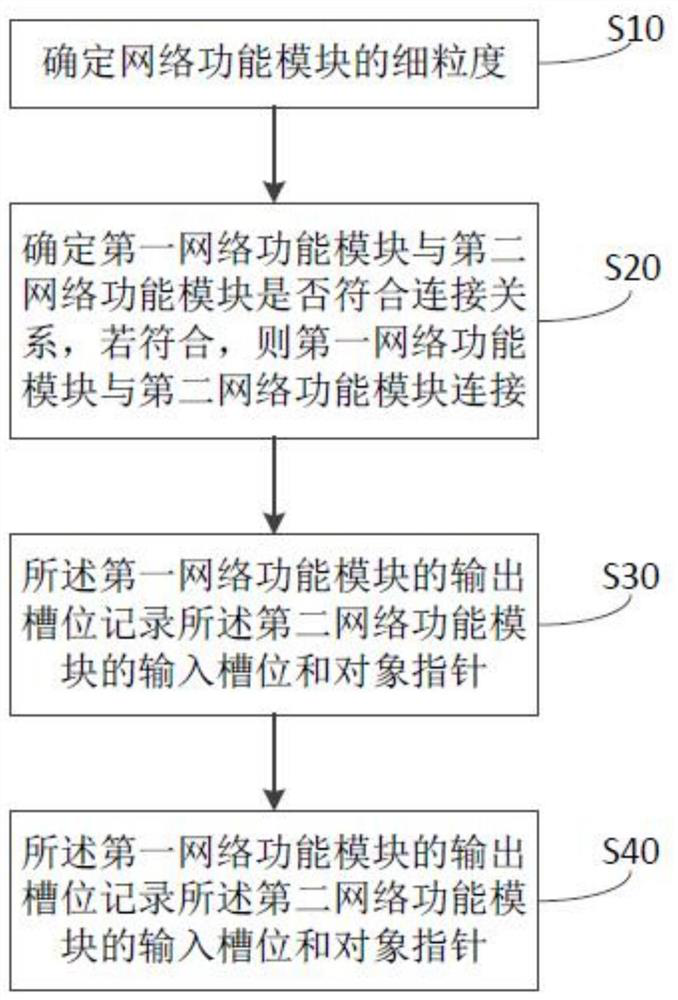
The invention discloses an SDN network programming method and device and a readable computer storage medium, and the method comprises the steps: determining the fine granularity of a network function module; determining whether the first network function module and the second network function module conform to the connection relationship, and if yes, connecting the first network function module and the second network function module; wherein the output slot position of the first network function module records the input slot position and the object pointer of the second network function module; the input slot position of the second network function module records the output slot position and the object pointer of the first network function module. According to the SDN network programming method, a network application is abstracted into a combination mode of a plurality of modules, and the combination mode between the modules is specified through a lookup table built in the modules, so that the next module for processing a data packet is flexibly selected by dynamically modifying the content of the lookup table, and therefore, online updating of the network application is supported, and interruption of the service flow is avoided.
Owner:PURPLE MOUNTAIN LAB
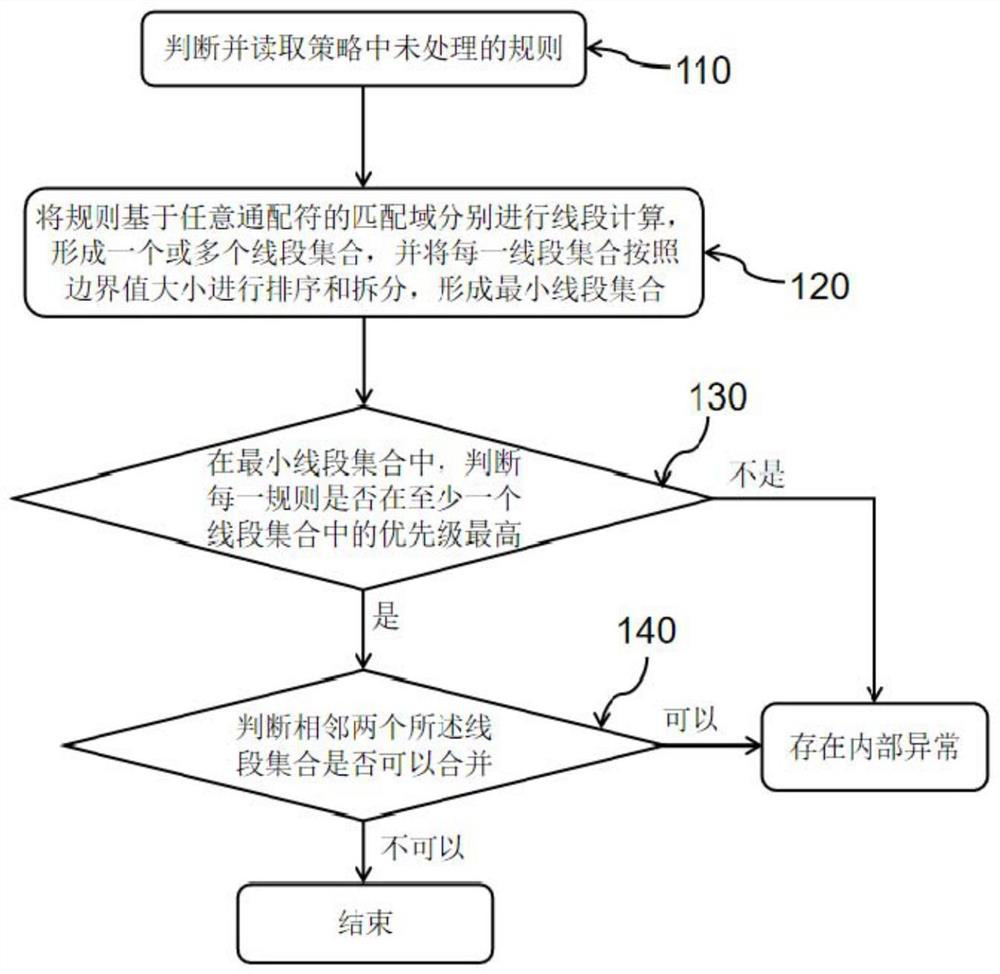
Policy anomaly detection method, system, device and storage medium for sdn network
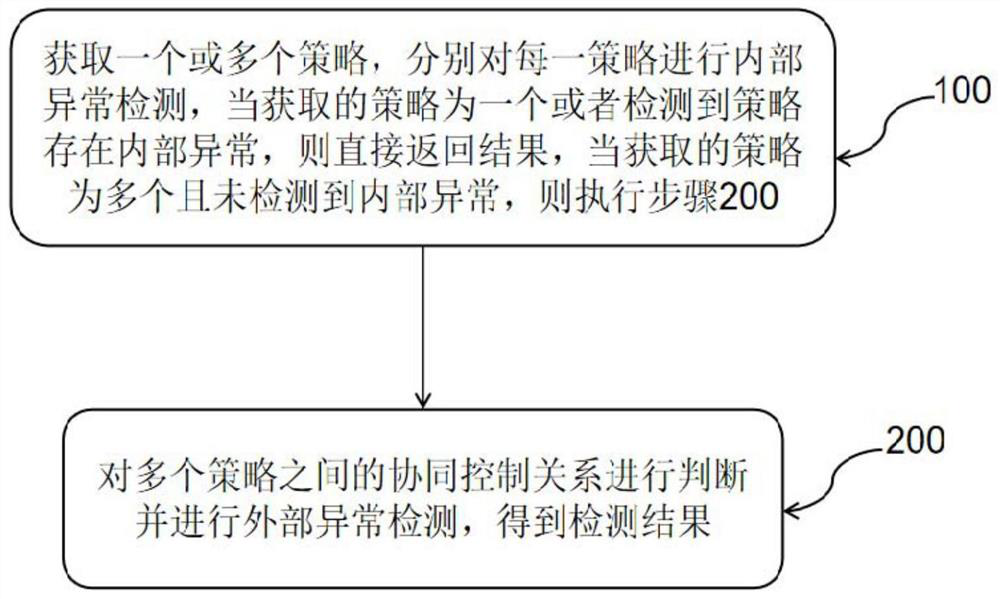
The present invention relates to a detection method, system, device and storage medium for SDN network policy anomalies, wherein the detection method includes: step 100, acquiring one or more of the policies in the SDN network, and respectively The above-mentioned strategies are used for internal abnormality detection. When the obtained strategy is one or an internal abnormality is detected in the strategy, the result is returned directly. When there are multiple obtained strategies and no internal abnormality is detected, step 200 is performed. ; Step 200, judging the collaborative control relationship between multiple strategies and performing external anomaly detection to obtain the detection result. The invention can ensure that in the programming process of the software-defined network (SDN), the function and efficiency abnormalities within and between SDN strategies can be quickly discovered and located, and can be fed back to network programmers in time.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method for implementing protocol data unit (PDU) used for packing and unpacking network bytes
ActiveCN101697546BSolve the problem of inconvenient changeImprove scalabilityTransmissionTransmission protocolTraffic capacity
The invention discloses a method for implementing a protocol data unit (PDU) used for packing and unpacking network bytes, which comprises the following steps: firstly, defining an XML field configuration file of a needed transmission protocol; and then performing packing and unpacking, wherein the XML field configuration file comprises order, length and data type of fields in the transmission protocol. The method solves the problems of complex programming model and inconvenient protocol field change in the conventional network programming, improves the efficiency of network byte stream programming, facilitates packing and unpacking the network bytes, shields the difference of high-low bytes, and provides good debugging information and unified traffic monitoring.
Owner:WHALE CLOUD TECH CO LTD
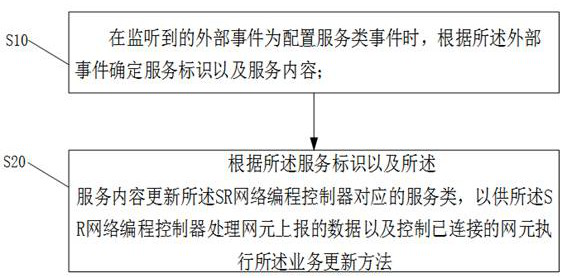
Service updating method and device and segmented routing network programming system
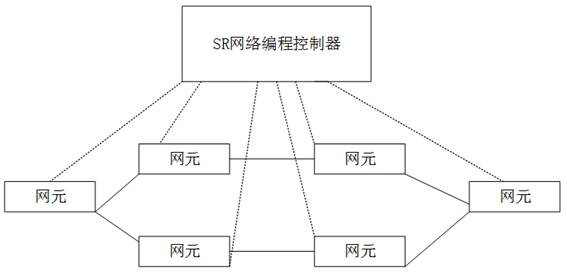
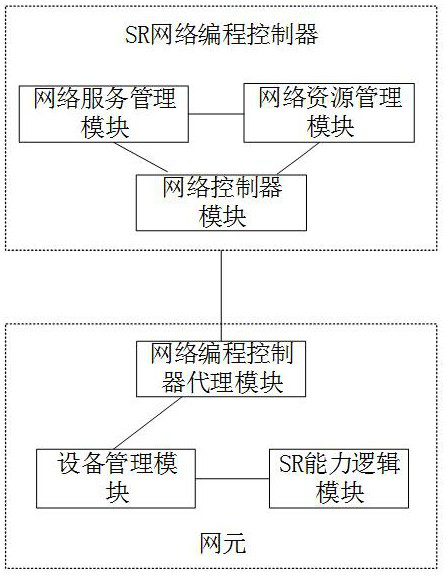
ActiveCN113411256AAvoiding Insufficient Scalability ProblemsData switching networksEngineeringWeb programming
The invention discloses a service updating method and device and a segmented routing network programming system. The method is applied to an SR network programming controller of the segmented routing network programming system. The method comprises the steps of: when a monitored external event is a configuration service event, determining a service identifier and service content according to the external event; and updating a service class corresponding to the SR network programming controller according to the service identifier and the service content, so that the SR network programming controller processes data reported by the network element and controls the connected network element to execute the service updating method. According to the method and the device, the service class corresponding to the SR network programming controller is updated by configuring the service class on the SR network programming controller, so that the problem of insufficient expansibility when the segment routing network programming system executes SR network programming is solved.
Owner:GUANGDONG COMM & NETWORKS INST
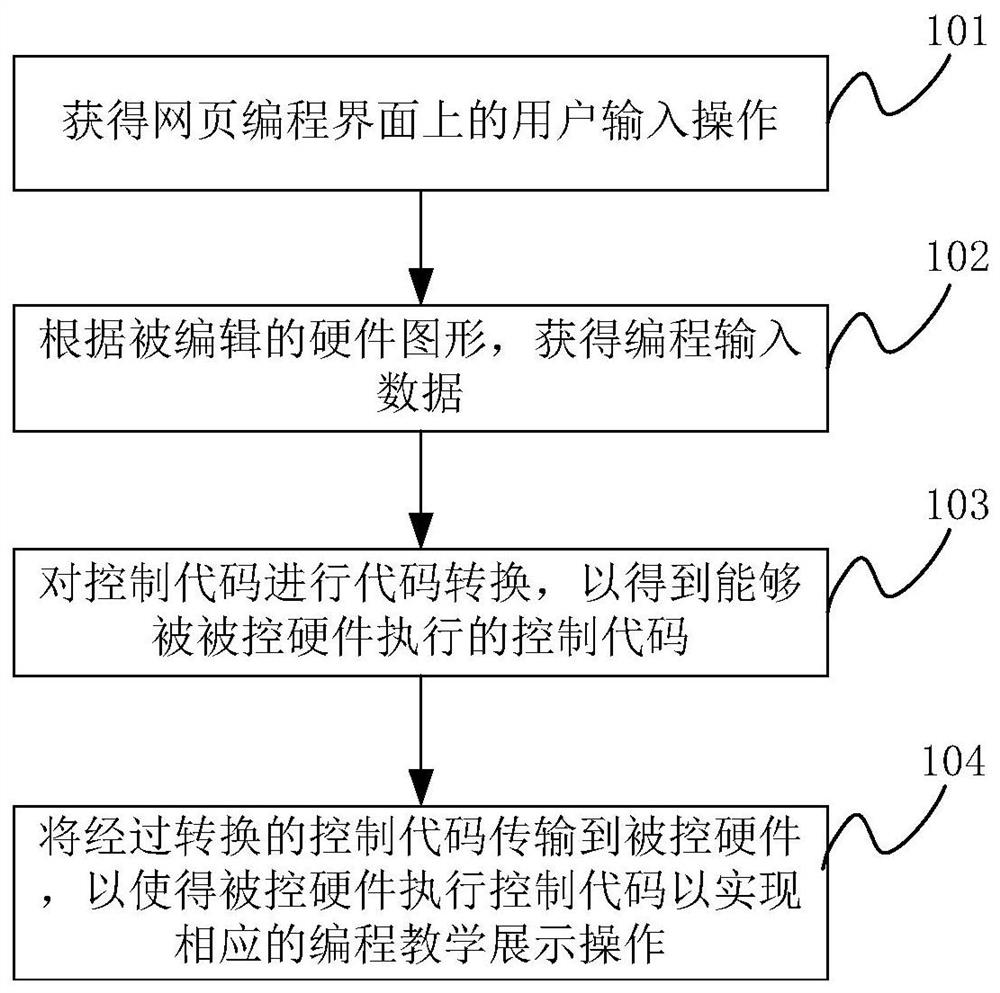
Control method, device and electronic equipment
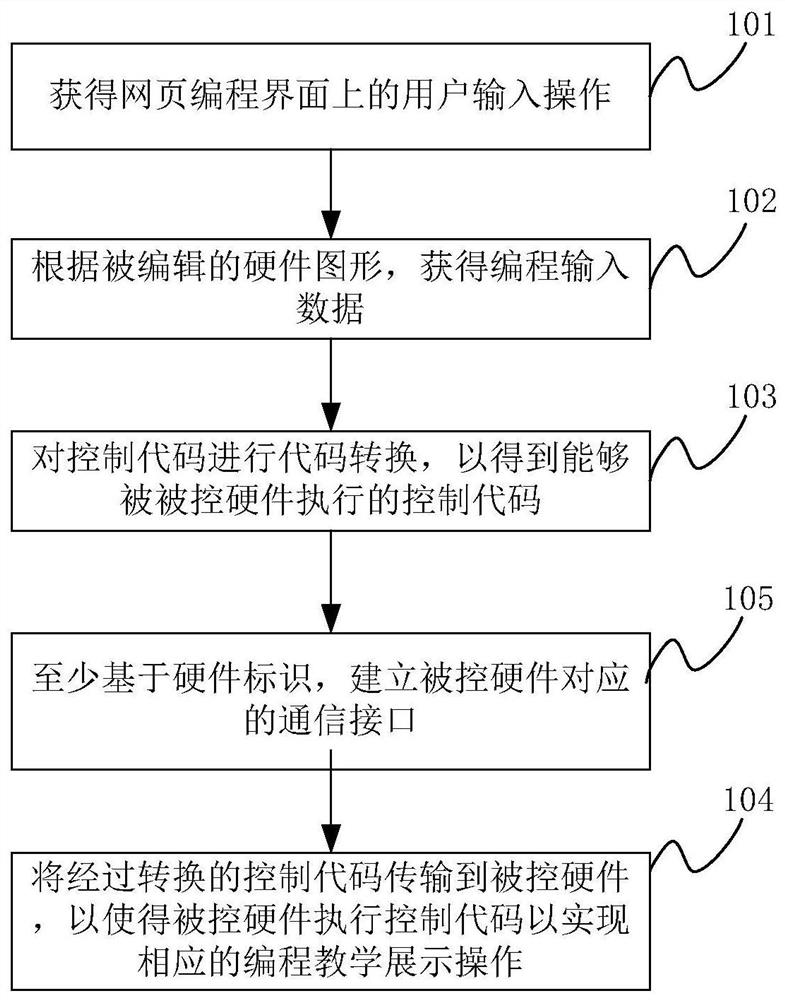
ActiveCN110795086BReduce the amount of codeEasy to controlVisual/graphical programmingCode compilationGraphicsUser input
Owner:LENOVO (BEIJING) LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com