Sandbox-based malicious program behavior analysis processing method and system
A technology for behavior analysis and malicious programs, applied in electrical digital data processing, instruments, computing, etc., can solve problems such as inability to ensure equipment security, lack of security design defects, etc., to improve compatibility, avoid interference problems, and strengthen analysis. performance effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] The purpose of this embodiment is to provide a sandbox-based malicious program behavior analysis and processing method.
[0055] A sandbox-based malicious program behavior analysis and processing method, which is executed in a network programming virtual execution environment, the method includes:
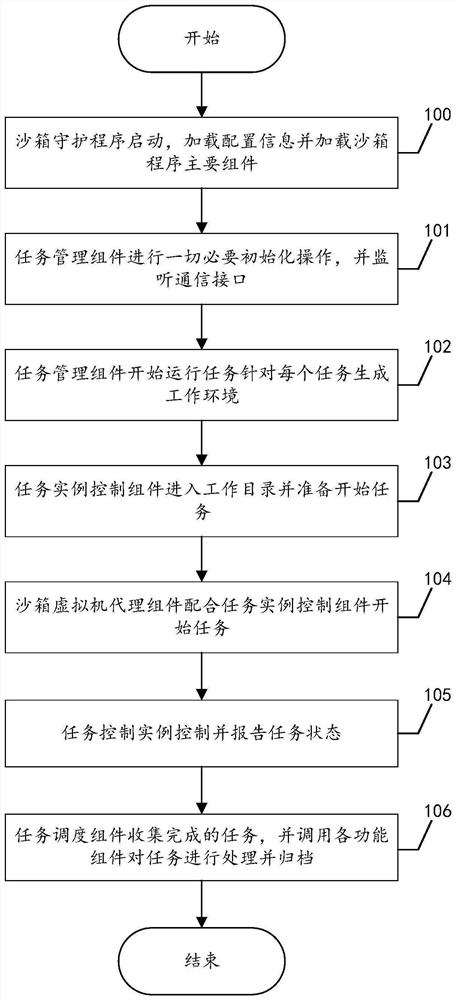
[0056] The daemon receives user instructions or according to configuration information, loads and starts the main components of the sandbox program;
[0057] Monitor the communication interface through the task management component, build a local task list and connect to the malicious sample database;
[0058] Run tasks from the malicious sample database according to the sandbox configuration file;
[0059] Use the task scheduling component to deploy relevant environments for the acquired tasks and generate configuration files, register and start the sandbox instance control component;
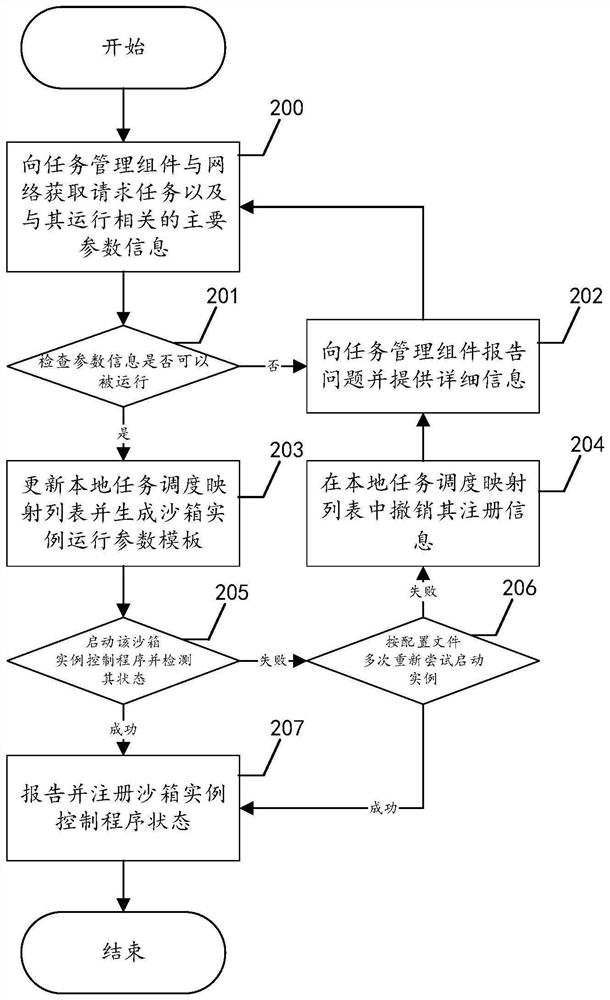
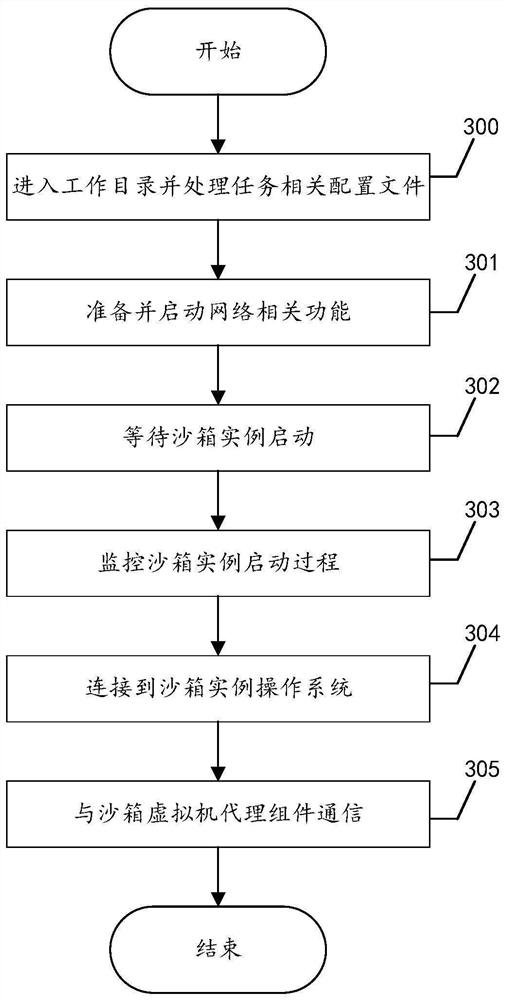
[0060] receiving the configuration file of the task scheduling component through the s...
Embodiment 2
[0295] The purpose of this embodiment is to provide a sandbox-based malicious program behavior analysis and processing system.
[0296] A sandbox-based malicious program behavior analysis and processing system, including:
[0297] The preprocessing module is used for the daemon program to receive user instructions or according to configuration information, load and start the main components of the sandbox program; monitor the communication interface through the task management component, build a local task list and connect to the malicious sample database;
[0298] Task malicious behavior analysis and processing module, which is used to run tasks from the malicious sample database according to the sandbox configuration file; through the task scheduling component, perform relevant environment deployment and generate configuration files for the acquired tasks, register and start the sandbox instance control component; Receive the configuration file of the task scheduling compone...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com