Mobile memory divulgence protection method and system
A mobile storage and key technology, applied in the field of data leakage prevention, can solve problems such as increasing the risk of information leakage, and achieve the effect of convenient management and data protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Hereinafter, the present invention will be described in detail through specific embodiments in conjunction with the accompanying drawings. In the description of this embodiment, the system for protecting against confidentiality of the mobile storage will be simultaneously reflected in the description of the method for preventing leakage of the mobile storage.
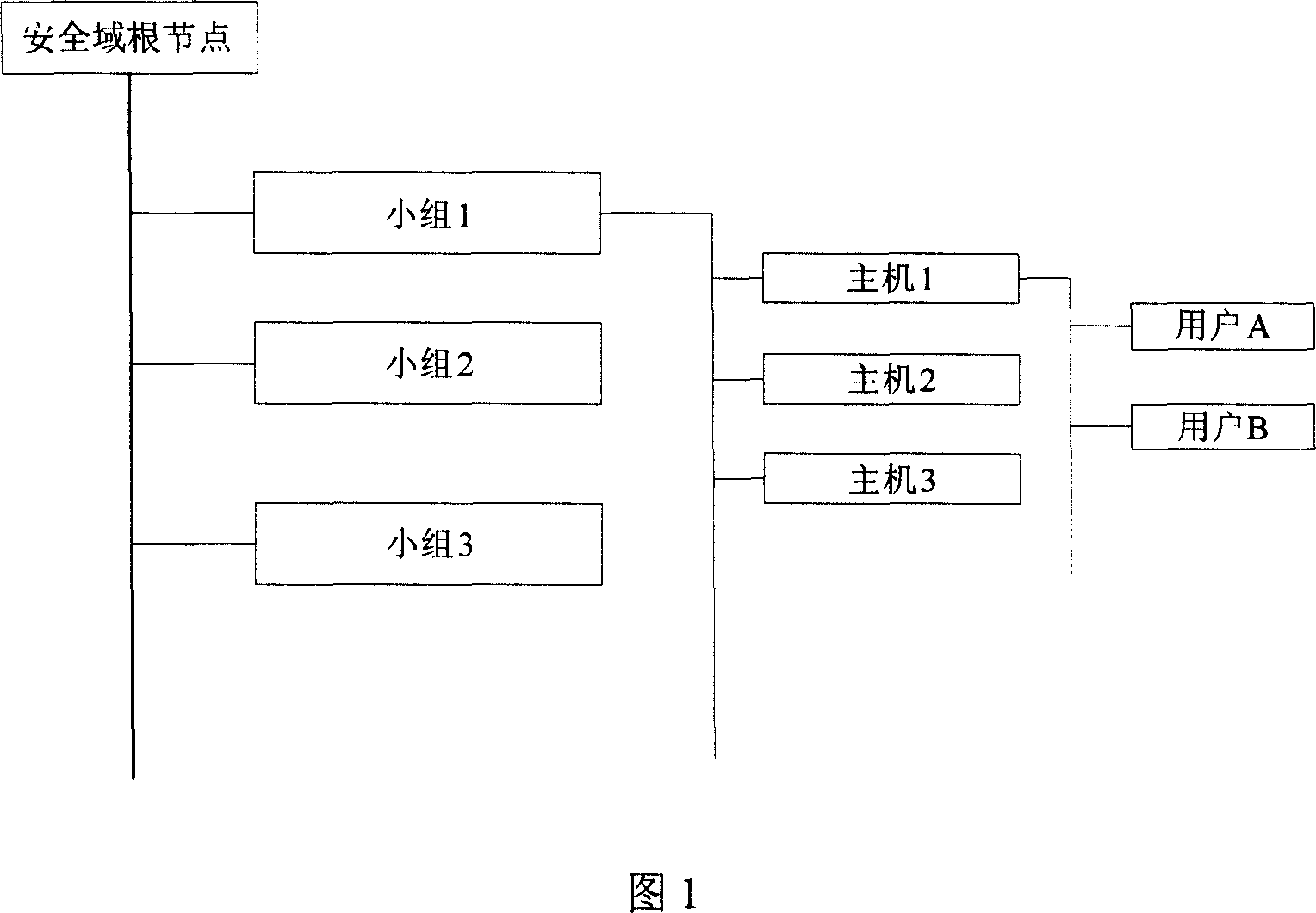
[0025] Taking the USB flash drive used by a certain unit as an example, first install a server and authorization center, and each host in the LAN installs a client to form a work security domain. The node organization structure diagram of this security domain is shown in Figure 1. Each node in has a global ID, group ID, user ID, and host ID.
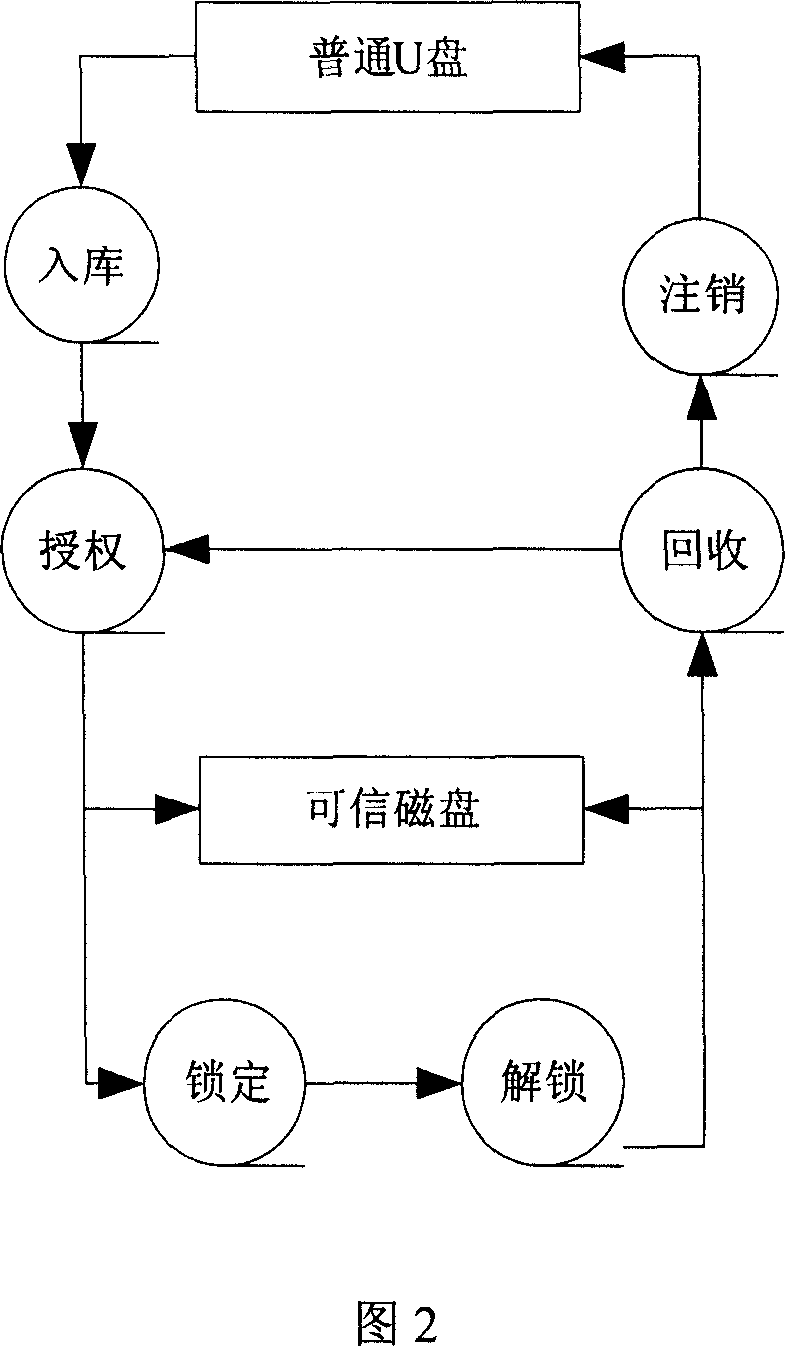
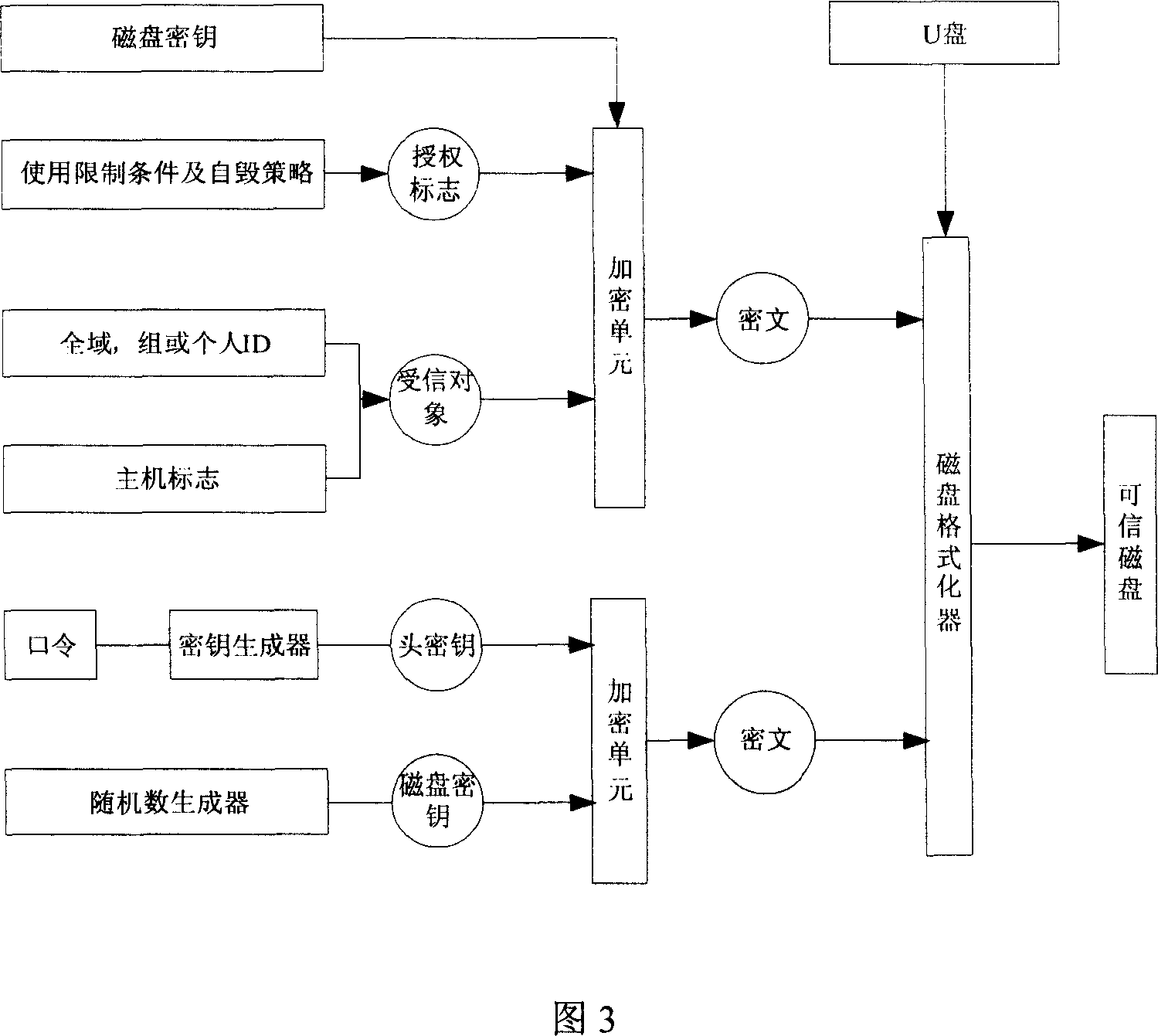
[0026] The mobile memory that prevents data from being leaked does not need to use a special disk encrypted at the hardware level, and only needs an ordinary mobile memory. As shown in Figure 2, after the ordinary U disk is registered in the warehouse, it will be authorize...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com