Method and system of file encipher share
A file and file sharing technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of insecure cost and inconvenient operation of file sharing methods, and achieve the effect of simple key management and cost reduction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The content of the present invention is described in detail below through a simple server-client model, but this does not constitute a limitation to the present invention.
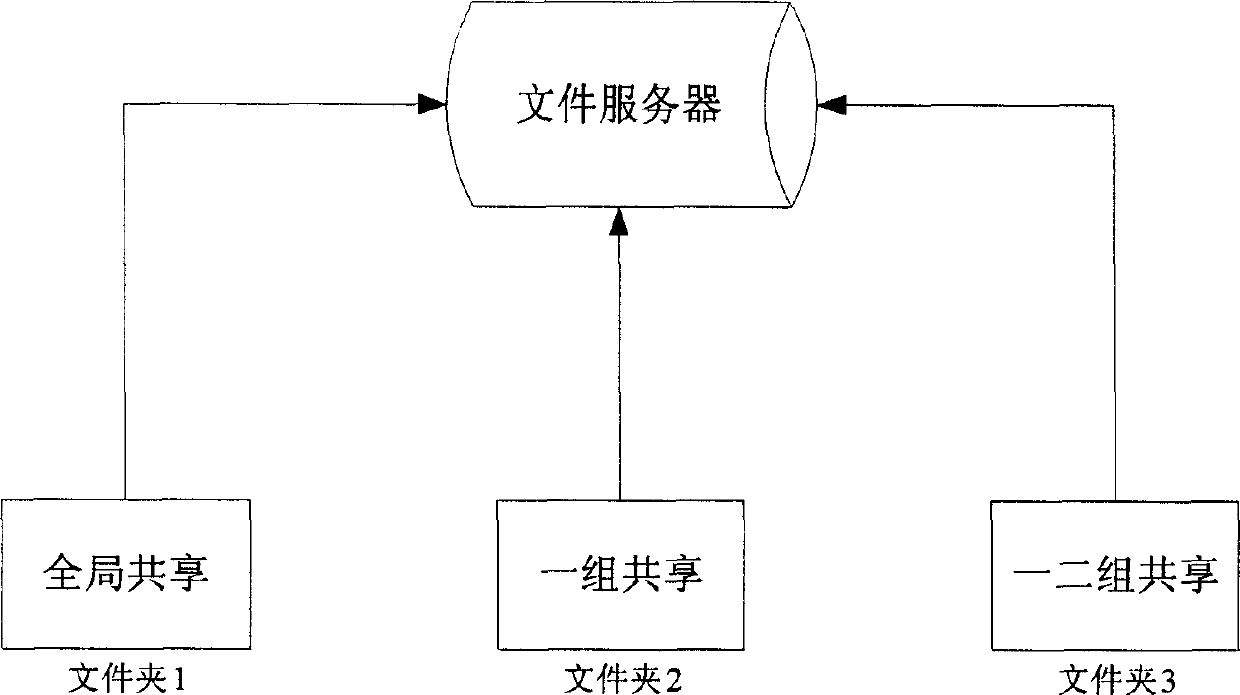
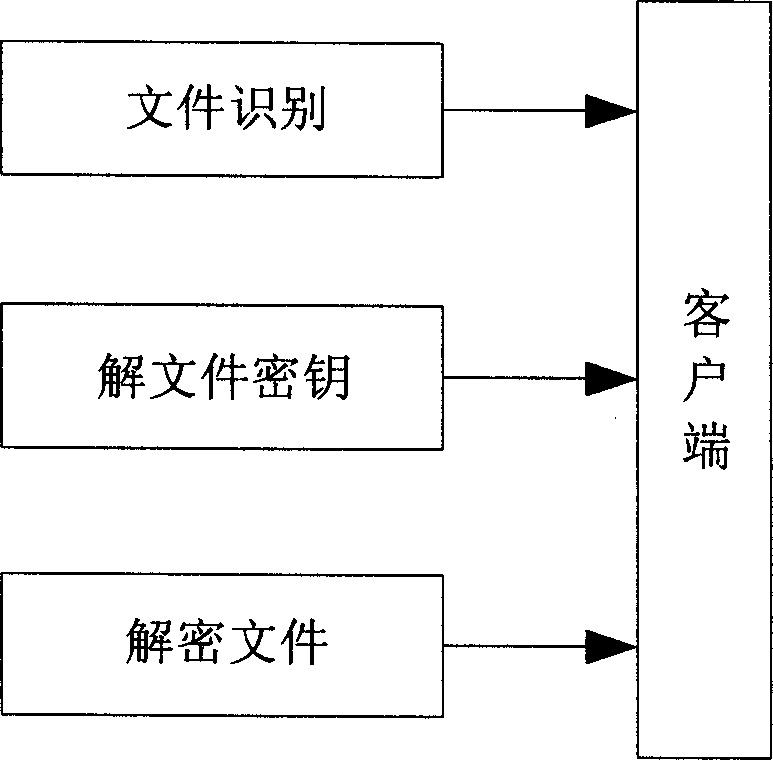
[0036] In this embodiment, the file encryption sharing system is composed of several file servers and computer terminals (clients), and all users are divided into three user groups. The file encryption process is in the file encryption server, and a file server can be randomly selected as the encryption file server, and the encryption monitoring service is installed on the file server. The file server holds global, group and user public keys. The decryption process is on the client, and the client host installs a decryption program. This can well ensure the rational use of computer resources.
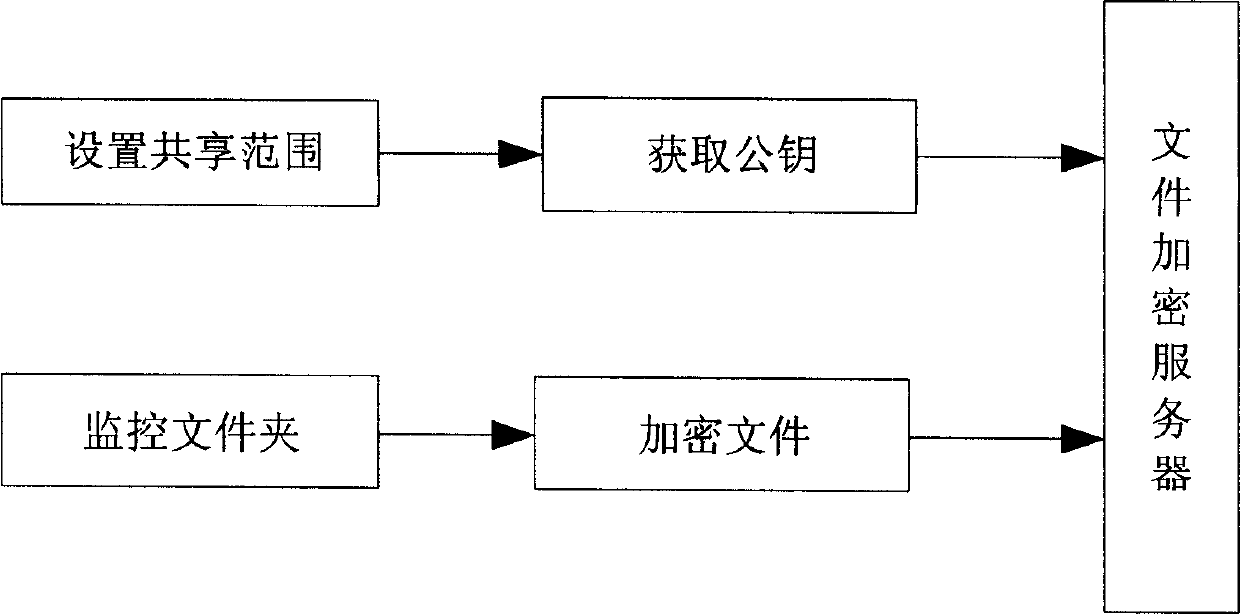
[0037] Wherein, the structure of the file encryption server is as shown in Figure 4, which includes: folder monitoring module, folder sharing range setting module, public key acquisition module and encrypti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com