OA (office automation) data protection method and system based on OA flow
A data protection and data technology, applied in the field of OA data protection methods and systems, can solve problems such as inability to prevent intentional or unintentional offline expansion, inability to prevent printing, screenshots, network transmission, and inability to prevent screenshots, copy and paste, etc. , to achieve the effect of flexible means and time, protection and safety, and short cycle
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
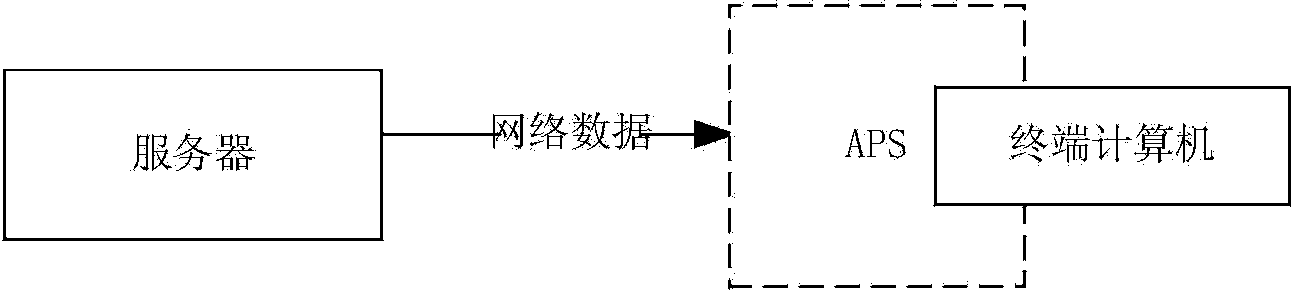
[0068] Embodiment 1 provides an overall architecture diagram for protecting OA data. attached figure 2 The system architecture of the present invention includes an OA server that manages OA data and OA processes, user terminals used by common users, and the APS (Application Protection System) proposed by the present invention.
[0069] APS implements the protection of information and data on terminal computers according to policies. This feature of the APS determines the deployment location of the APS. The figure below shows the protection scope and deployment position of APS in the entire information and data leakage prevention protection system, and is also a structural diagram of the entire APS system.
[0070] From this figure, it can be seen that the APS system can not only protect the network communication between the server and the terminal computer, but also protect the local data of the terminal.
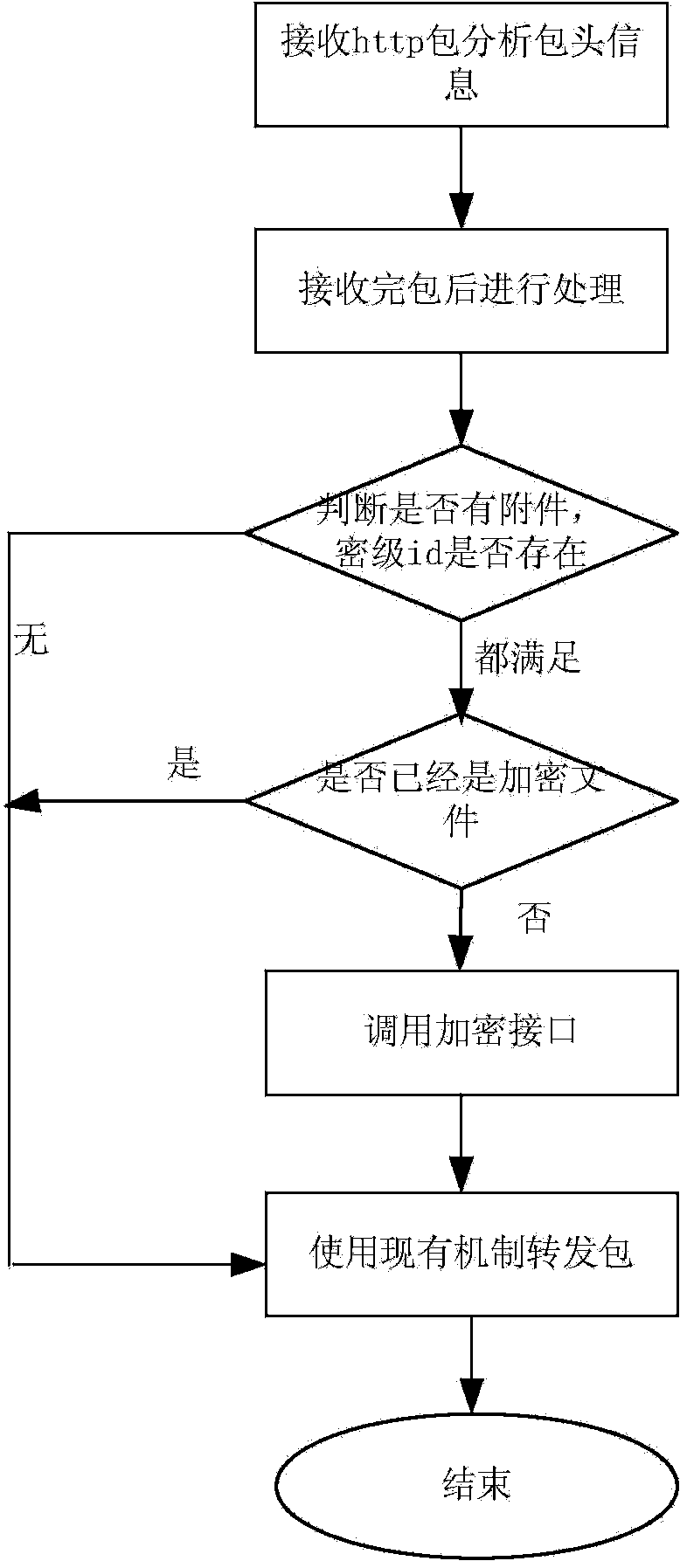
[0071] First of all, APS needs to encrypt and store the sensitive ...
Embodiment 2
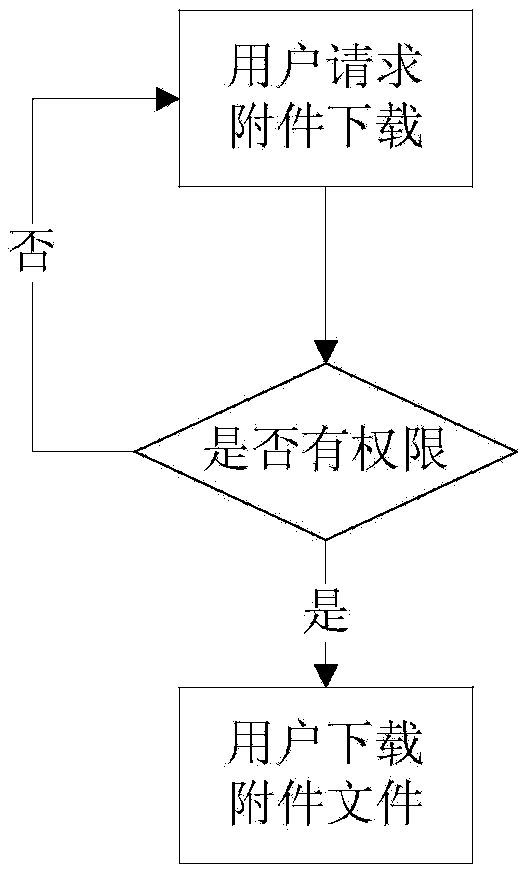
[0093] Embodiment 2 provides a flowchart of a data protection method.
[0094] Figure 4 It is a typical flow chart of OA attachment download, in which "encrypted attachment file process" is the module for APS to perform anti-disclosure processing. This flowchart describes how the data transferred from the server is protected.
[0095] 1) The user requests to download OA data;
[0096] 2) Determine whether the user has the download permission to download OA data;
[0097] 3) If the user has the download permission to download OA data, the user downloads OA data and jumps to step 5);
[0098] 4) If the user does not have the download permission to download OA data, return to step 1);
[0099] 5) Encrypt the downloaded OA attachment file;
[0100] 6) Download the encrypted OA attachment file to the user terminal;
[0101] 7) When the user opens and views the downloaded OA attachment file, the following functions are activated: prevent screenshots, prevent copying, prevent ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com