Server security defense method and system, communication equipment and storage medium
A server security and server technology, applied in the security field, can solve problems such as the vulnerability of servers to attacks, achieve the effects of improving security and service availability, improving user experience, and increasing the difficulty of attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] In order to solve the problem that the server's IP address and service port are open to all access terminals on the Internet, causing the server to be vulnerable to attacks, the embodiment of the present invention provides a server security defense method, which is used in a server security defense network system.
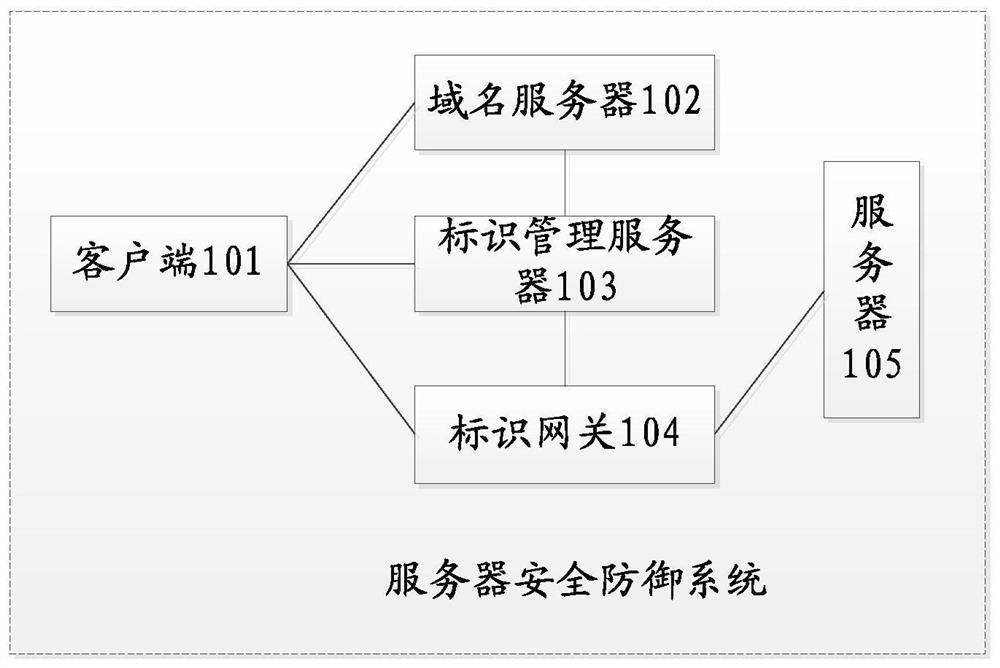
[0032] See figure 1 , figure 1 A server security defense system provided by an embodiment of the present invention. In the embodiment of the present invention, the server security defense network system includes: a client 101 , a domain name server 102 , an identification management server 103 , an identification gateway 104 , and a service server 105 . Wherein the identification gateway 104 is located between the client 101 and the service server 105, that is, the client 101 and the service server 105 are divided into different security areas, wherein the service server 105 is located in a high security area, and the identification gateway 104 provides sec...
Embodiment 2
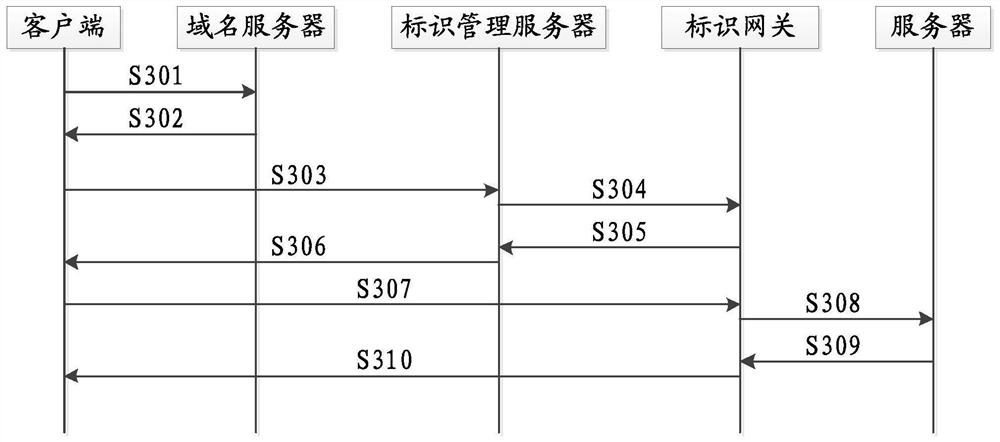
[0044] In order to solve the problem that the server's IP address and service port are open to all access terminals on the Internet, making the server vulnerable to attacks, image 3 Shown is a server security defense method provided by the embodiment of the present invention, including the following steps:
[0045] Firstly, the concept of service identifier is explained. The service identifier indicates the Internet service resource that the user wants to access, and is generally described by a uniform resource locator, which is composed of a server identifier and a content identifier, such as: www.example.com:80 / news / top. xml, where "www.example.com:80" is the server ID, specifically including the server domain name (www.example.com) port (80), where the server domain name can also be identified by the server's IP address, if the default port is used, you can Omit the port; " / news / top.xml / " indicates the specific content provided by the business service, and the combination ...
Embodiment 3
[0085] Figure 4 Shown is a flow chart of a server security defense method provided by the present invention. The client uses the service identifier to conduct service access, including the following steps:
[0086] S401: the client sends a domain name resolution request to the domain name server;
[0087] S402: The domain name server performs domain name resolution, and returns a domain name query response;
[0088] Wherein, the response information returned by the domain name server to the client includes at least one IP address identifying the management server. In the embodiment of the present invention, in the domain name server, the IP address configured by the server domain name is not the real address of the server, but the IP address of the identity management server. If there are multiple identity management servers in the network, multiple identity management servers can be configured for IP address, the domain name server selects at least one IP address of the id...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com