Identity authentication method, device and apparatus and data processing method
An identity authentication and identity technology, applied in the field of computer Internet, can solve the problems of easy imitation of user information and hidden dangers in the security of the authentication system, so as to solve the hidden dangers of security, improve the difficulty of attack, and enhance the effect of security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
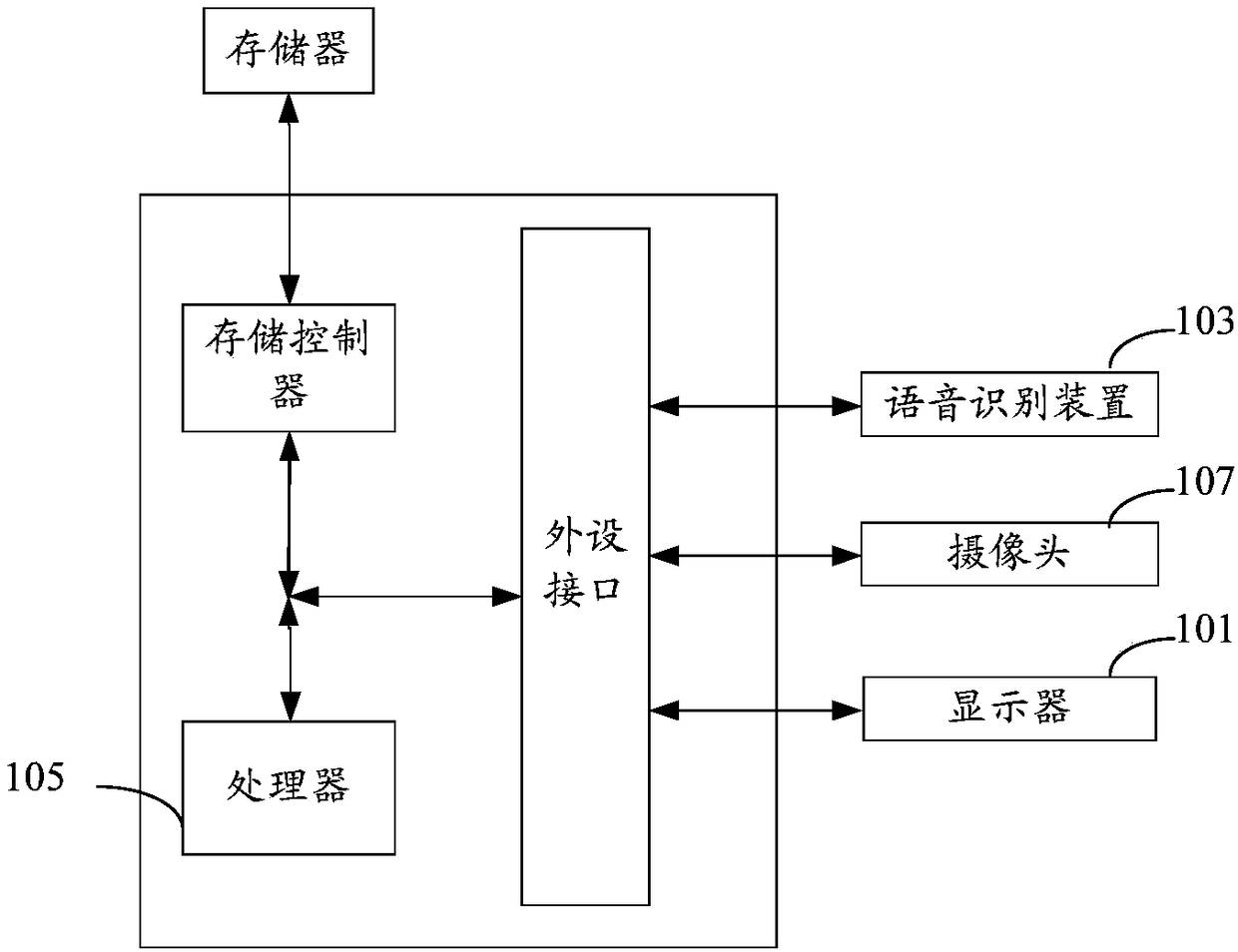
[0042] According to the embodiment of this application, an embodiment of an identity authentication device is provided. It should be noted that this embodiment can be applied to but not limited to registering or logging in to a website, online payment, consumer card swiping, access control, ATM machine withdrawal, time attendance, etc. Scenario, the device can be a smart terminal device such as a computer, a laptop, a tablet computer, or a mobile phone, or a terminal device that needs to be identified, such as an attendance machine, an ATM cash machine, or the like.
[0043] With the rapid development of electronics, computers, networks and communication technologies, people pay more and more attention to the security of electronic information. Traditional identity verification methods using passwords, passwords, keys, smart cards or certificates are prone to loss, theft and vulnerability. Replication problem. Due to the uniqueness and stability of human biological characteris...
Embodiment 2
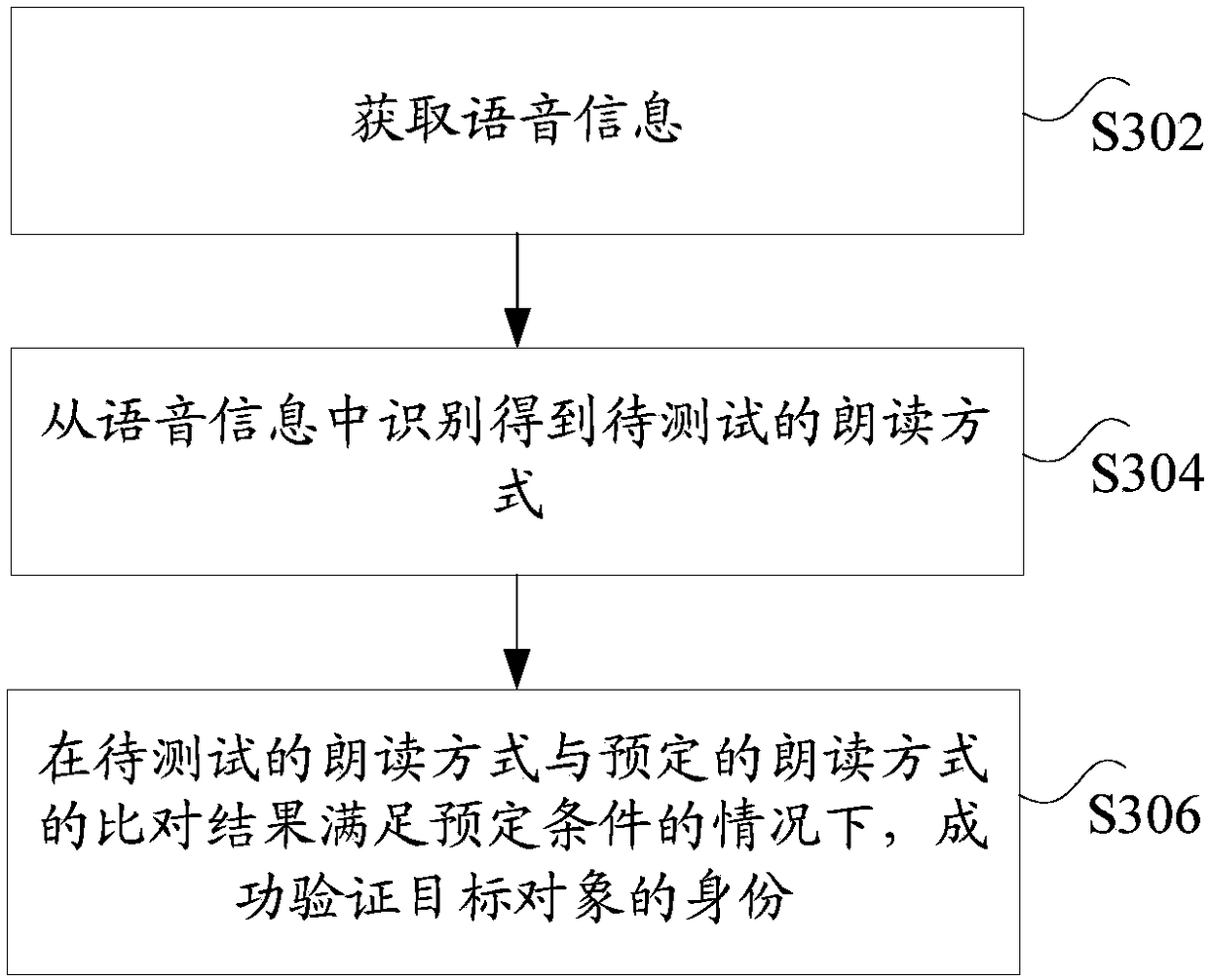
[0077] According to the embodiment of this application, an embodiment of an identity authentication method is also provided. The identity authentication method provided in this embodiment can be applied to any software and hardware products or systems that require identity authentication, as an optional implementation This method can be applied to identity authentication performed on the server in various applications or Web-based services. It should be noted that the steps shown in the flowcharts of the accompanying drawings may be performed in a computer system, such as a set of computer-executable instructions, and that although a logical order is shown in the flowcharts, in some cases, The steps shown or described may be performed in an order different than here.
[0078] Due to the existing living body detection scheme based on biometrics, the identity of the user is verified by prompting the user to make some facial movements or prompting the user to input a piece of voi...
Embodiment 3
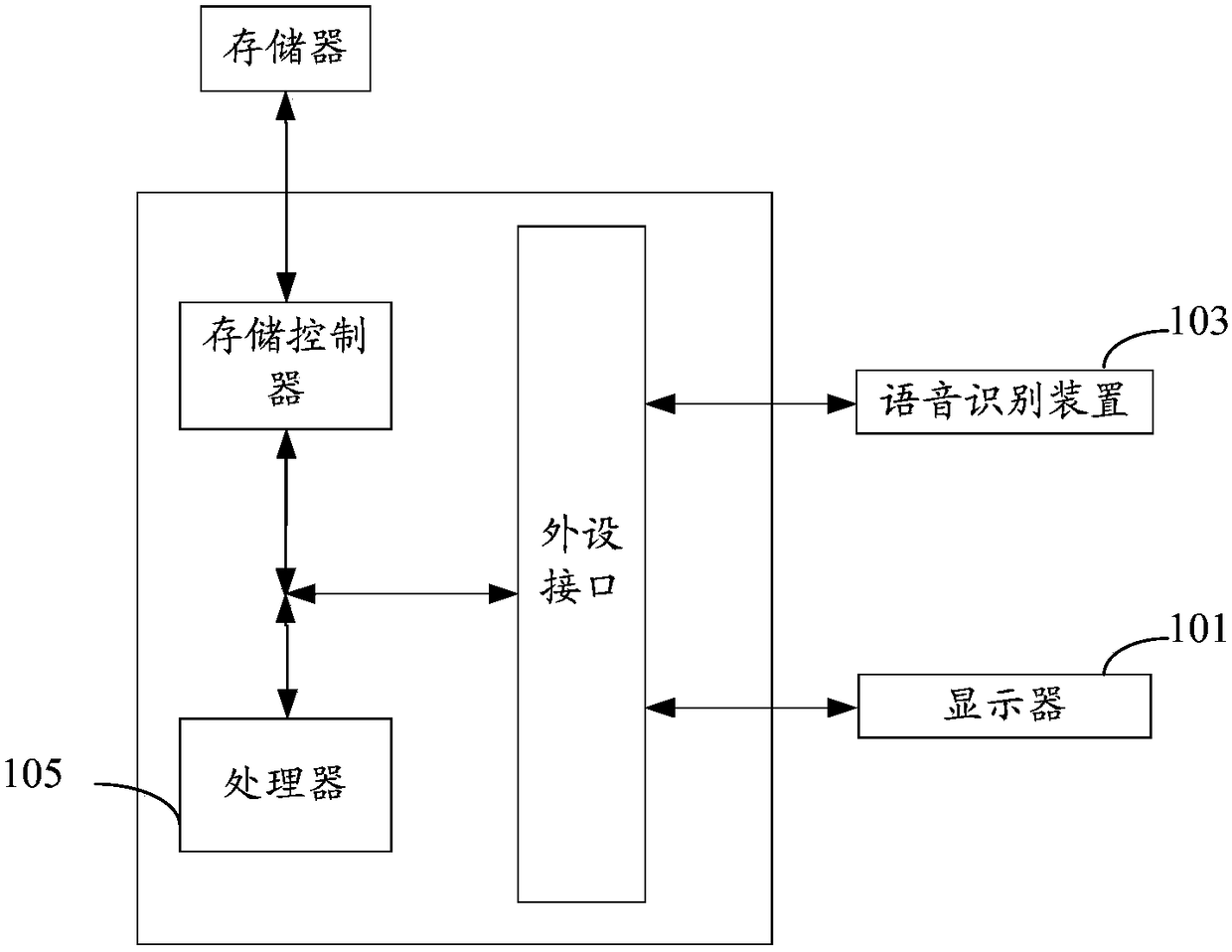
[0142] According to the embodiment of the present application, a device embodiment for implementing the above identity authentication method is also provided, Figure 11 is a schematic diagram of an identity authentication device according to an embodiment of this application, such as Figure 11 As shown, the device includes: a first acquisition unit 111 , a first identification unit 113 and a first verification unit 115 .
[0143] Wherein, the first obtaining unit 111 is used to obtain voice information, wherein the voice information is information generated by the target object reading predetermined content according to a predetermined reading method;
[0144] The first identification unit 113 is used to identify the reading method to be tested from the voice information;
[0145] The first verification unit 115 is configured to successfully verify the identity of the target object when the comparison result between the reading method to be tested and the predetermined read...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com