Patents
Literature
33results about How to "Solve technical problems with potential safety hazards" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
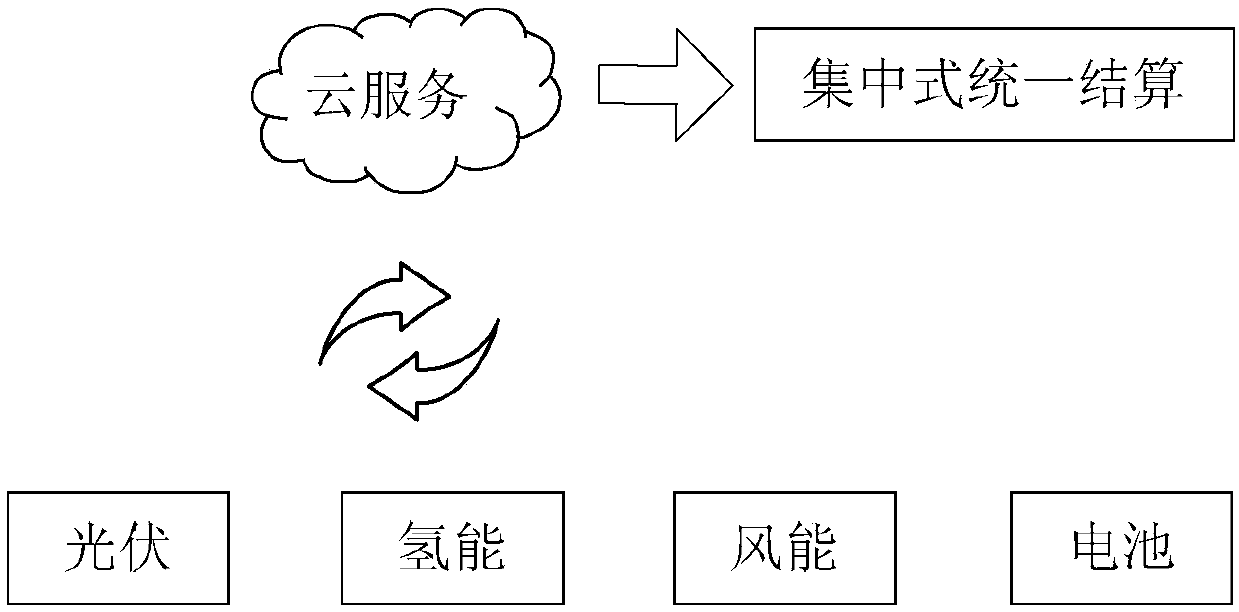
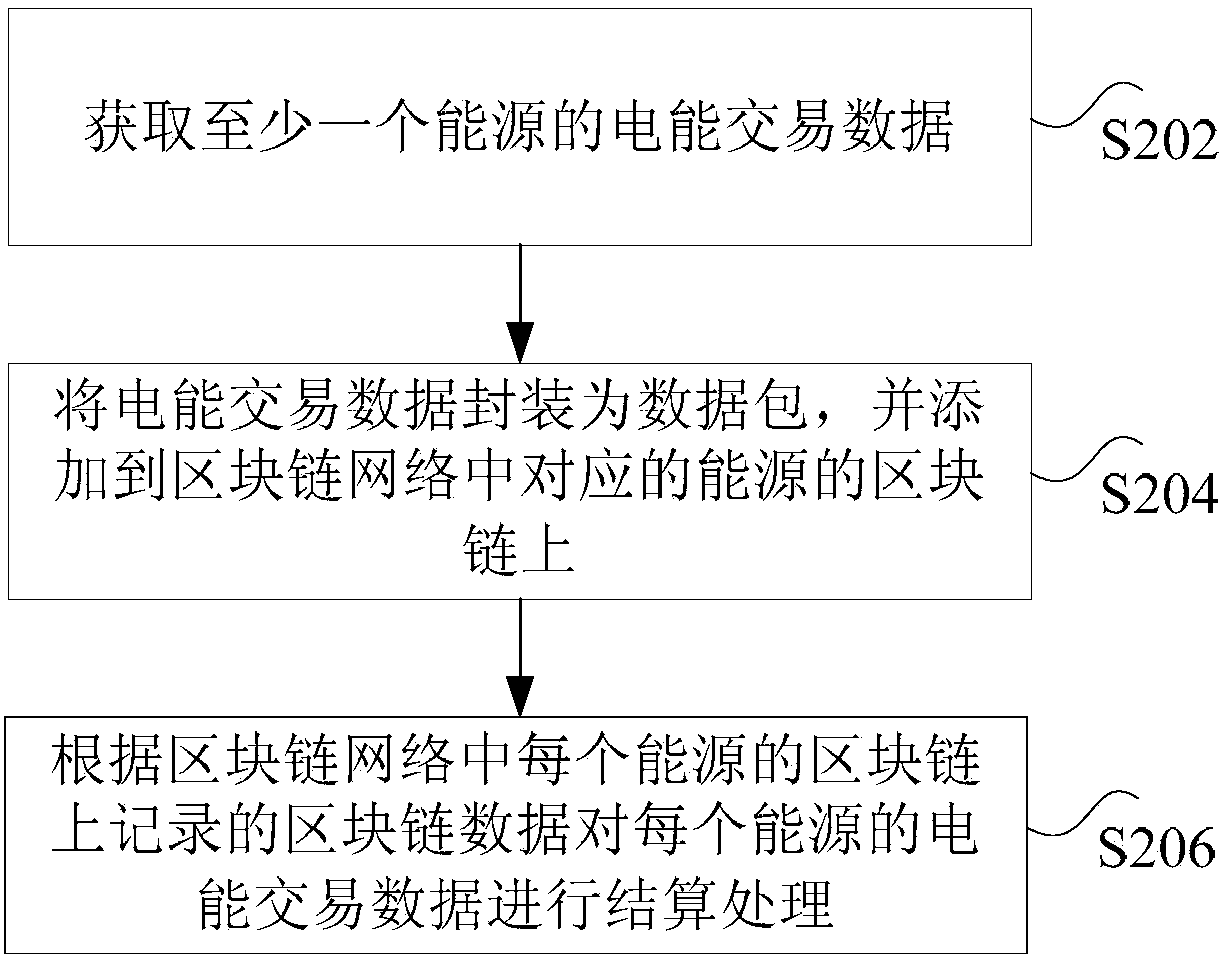
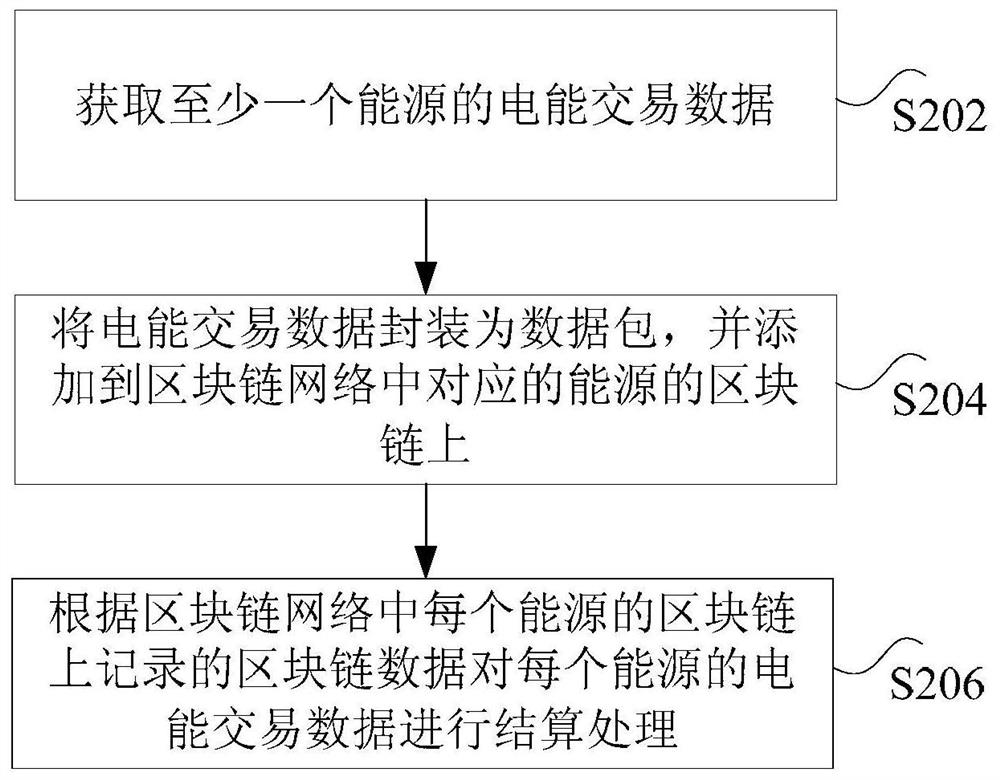
Energy settlement method, device and system
ActiveCN107909358AAchieve securitySolve technical problems with potential safety hazardsTransmissionProtocol authorisationBlockchainCentralized database
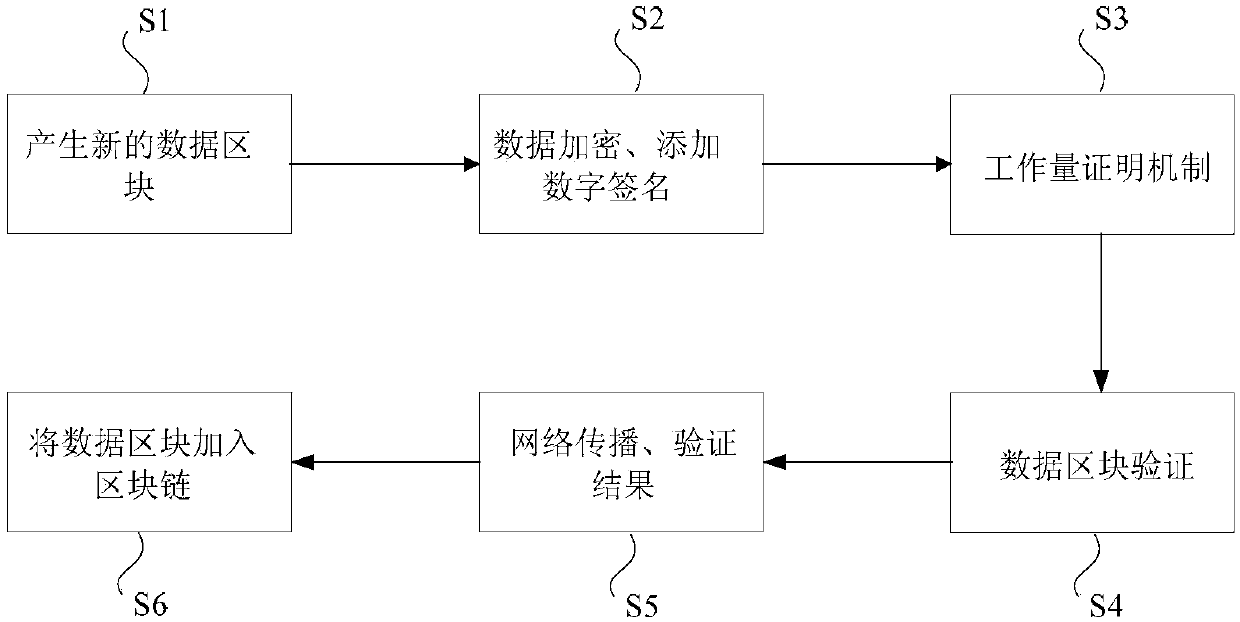
The invention discloses an energy settlement method, device and system. The method comprises the steps that energy trading data of any energy station within a blockchain network are acquired, whereinthe blockchain network is composed of at least one energy station; the energy trading data are sent to the blockchain network for verification, and a verification result returned by the blockchain network is received; and if the verification result is successful verification, the energy trading data are recorded on the blockchain of each energy station within the blockchain network, wherein blockchain data recorded on the blockchain of each energy station are used to settle the energy trading data of any energy station within the blockchain network. According to the invention, the technical problem of trading data security risks caused by a centralized database which is easily tampered in the prior art is solved, wherein the centralized database is used to settle the energy trading data ofa number of energy stations.
Owner:北京融链科技有限公司
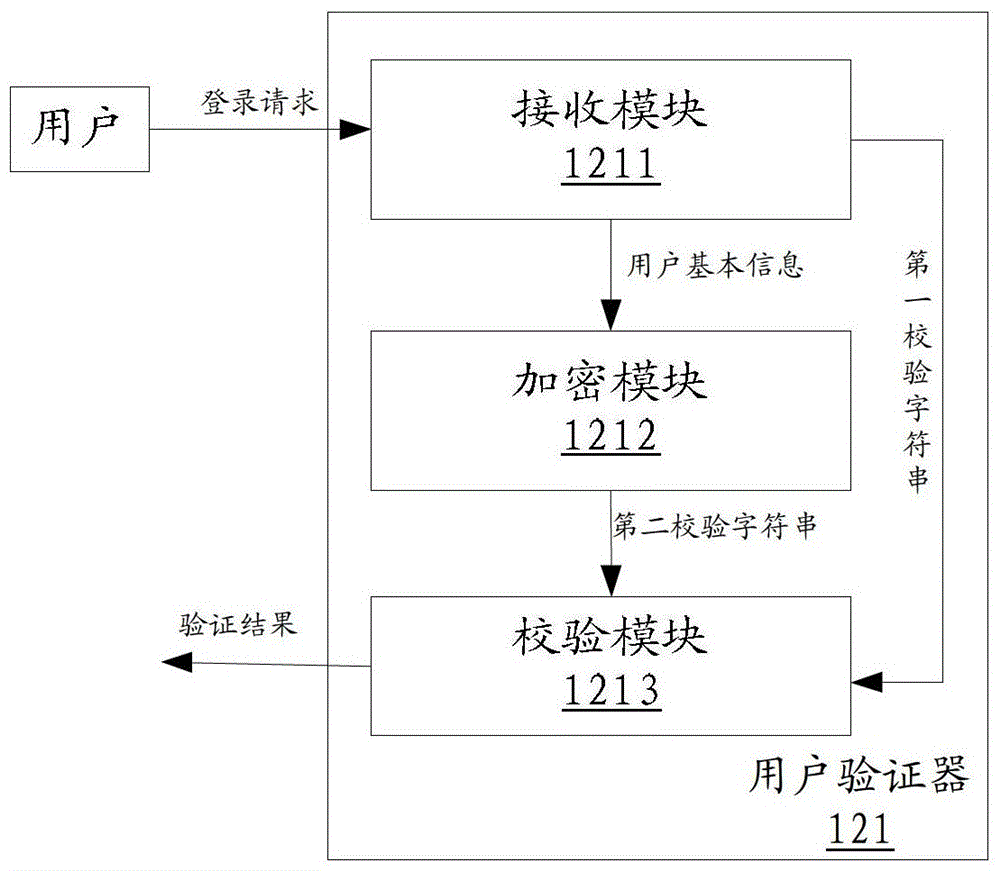
User authentication method and device
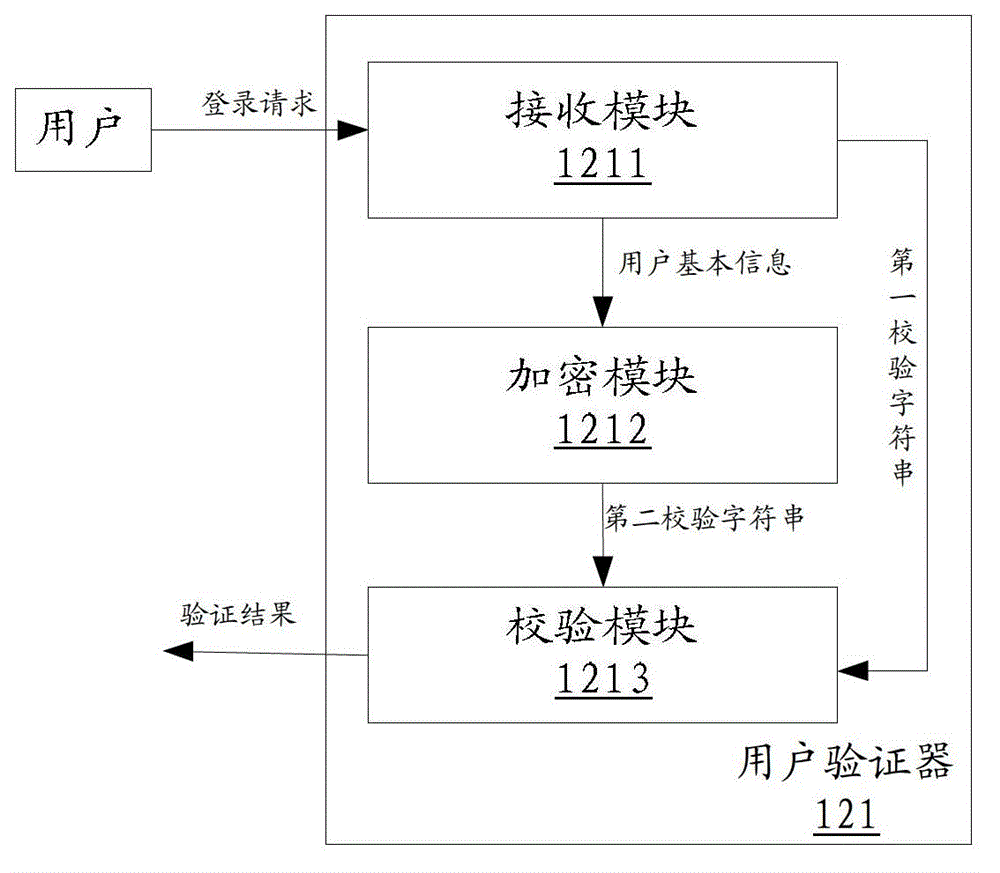
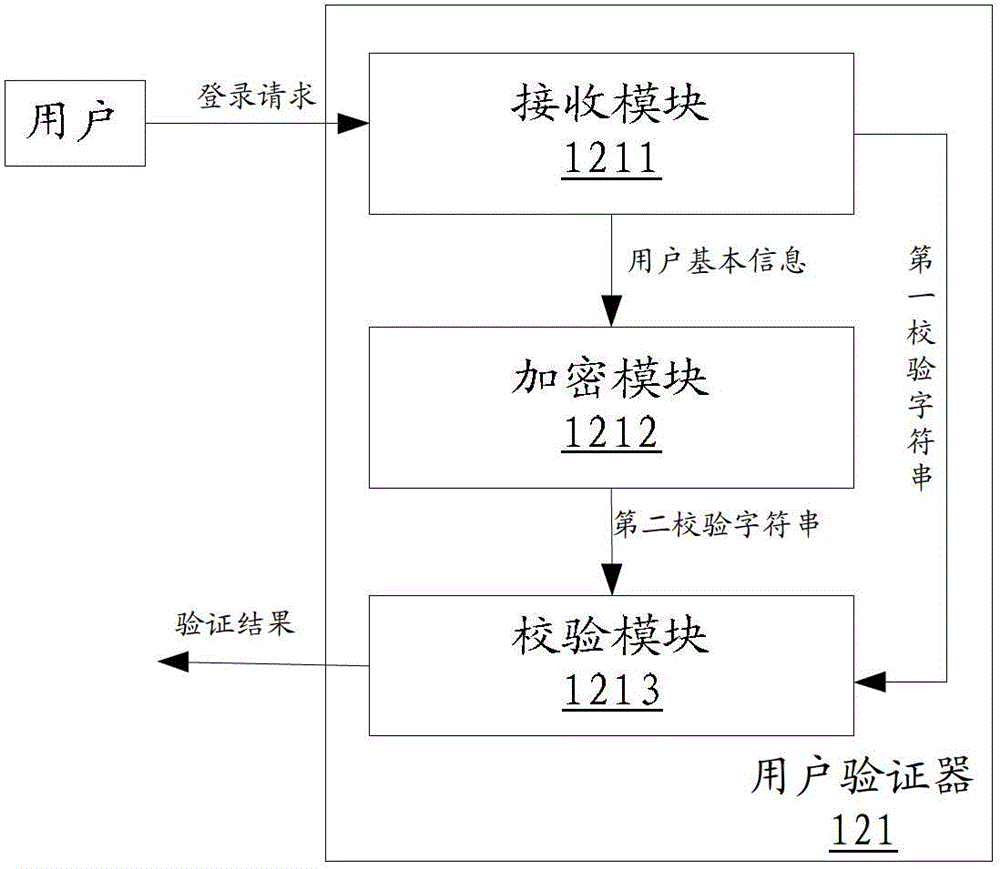
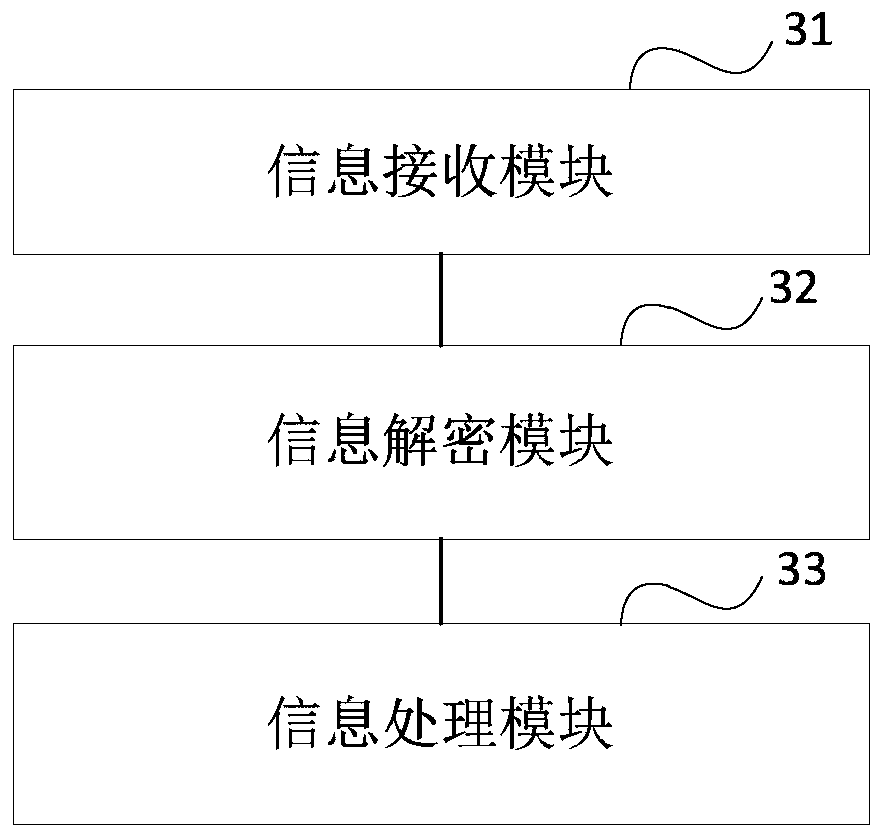
ActiveCN102946384ARealize self-checkingSolve technical problems with potential safety hazardsTransmissionUser authenticationForge
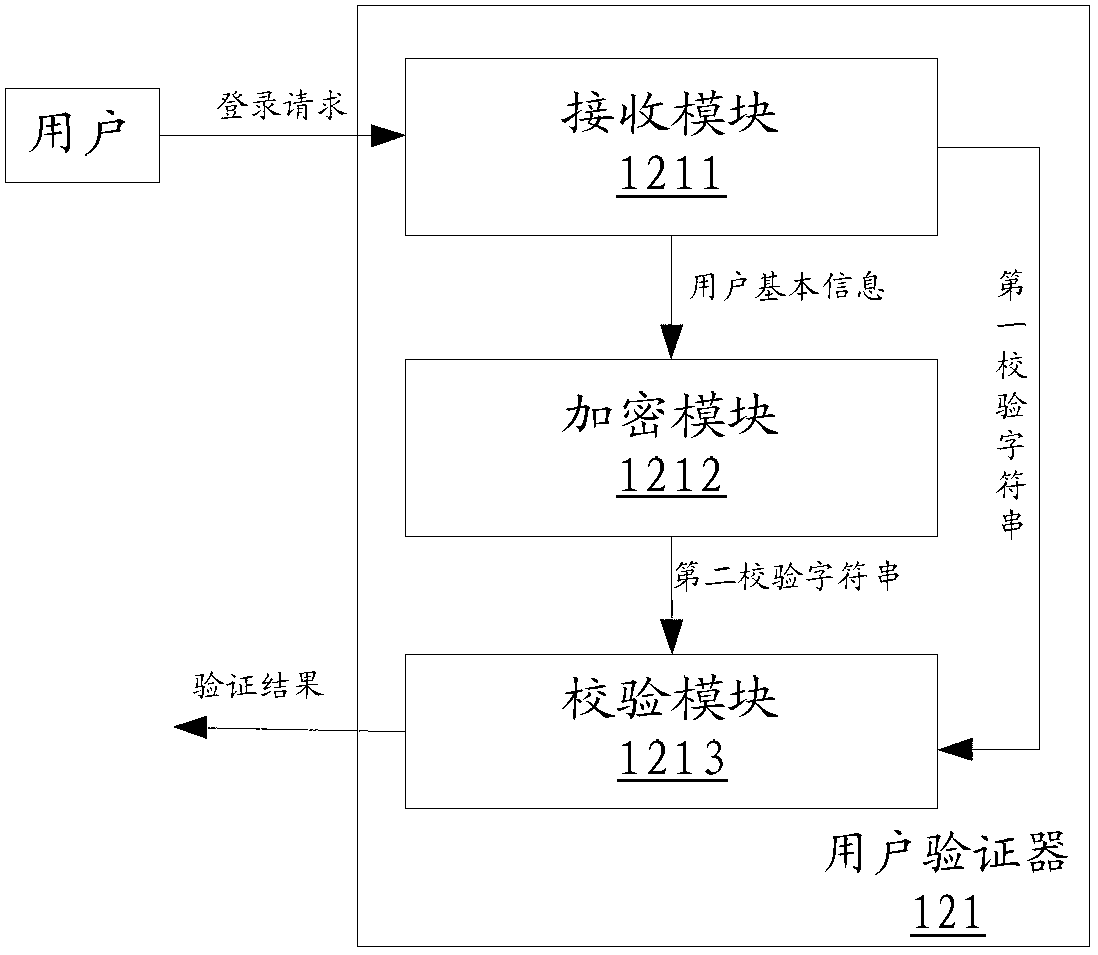
The invention discloses a user authentication device, which comprises a receiving module, an encryption module and an authentication module, wherein the receiving module is used for receiving a logging request including authentication information from a user; the authentication information comprises a first information part and a second information part; the first information part comprises basic information of the user; the second information part comprises a first verification character string generated after the basic information of the user is encrypted by a preset encrypting rule; the encryption module is used for encrypting the basic information of the user is encrypted by the preset encrypting rule to obtain a second verification character string; and the authentication module is used for determining whether the second verification character string is matched with the first verification character string or not, and the authentication is successfully if the second verification character string is matched with the first verification character string. By adopting the user authentication device provided by the invention, a technical problem of potential safety hazard of a system, which is caused by the fact that a malicious user forges cookie to log into the system, can be solved. The invention further discloses a corresponding user authentication method and system.
Owner:BEIJING QIHOO TECH CO LTD
Identity authentication method, device and apparatus and data processing method
InactiveCN109218269AIncrease attack difficultyImprove securitySpeech analysisDigital data authenticationLiving bodyAuthentication system
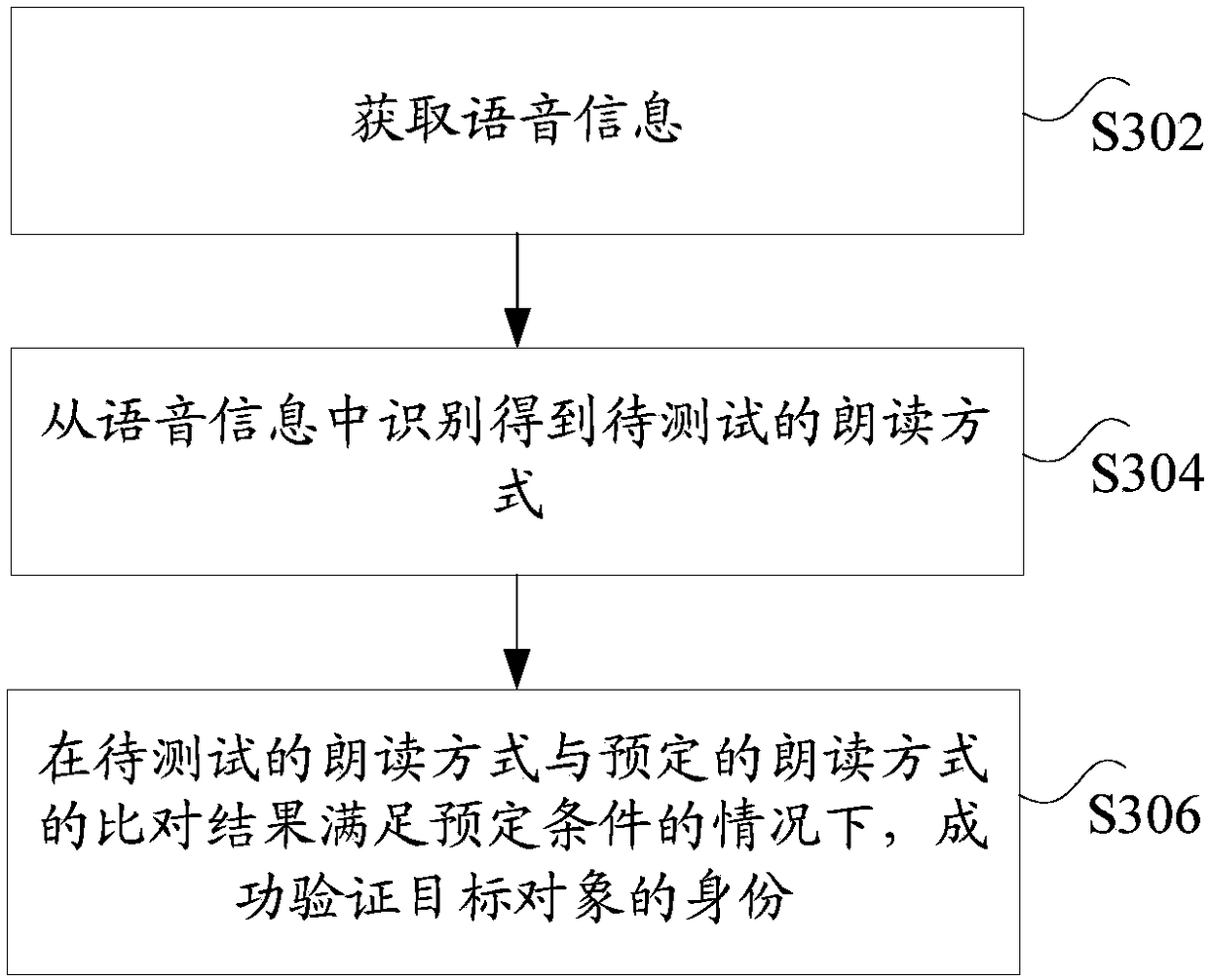
The present application discloses an identity authentication method, device and apparatus and a data processing method. The method includes: acquiring voice information, wherein the voice informationis information generated by a target object reading the predetermined content according to a predetermined reading mode; identifying a reading mode to be tested from the voice information; and when acomparison result of the reading mode to be tested and the predetermined reading mode satisfies a predetermined condition, successfully verifying the identity of the target object. The method solves the technical problem that the user information in an existing living body detection scheme is easy to imitate so that the security of the authentication system has a hidden danger.
Owner:ALIBABA GRP HLDG LTD
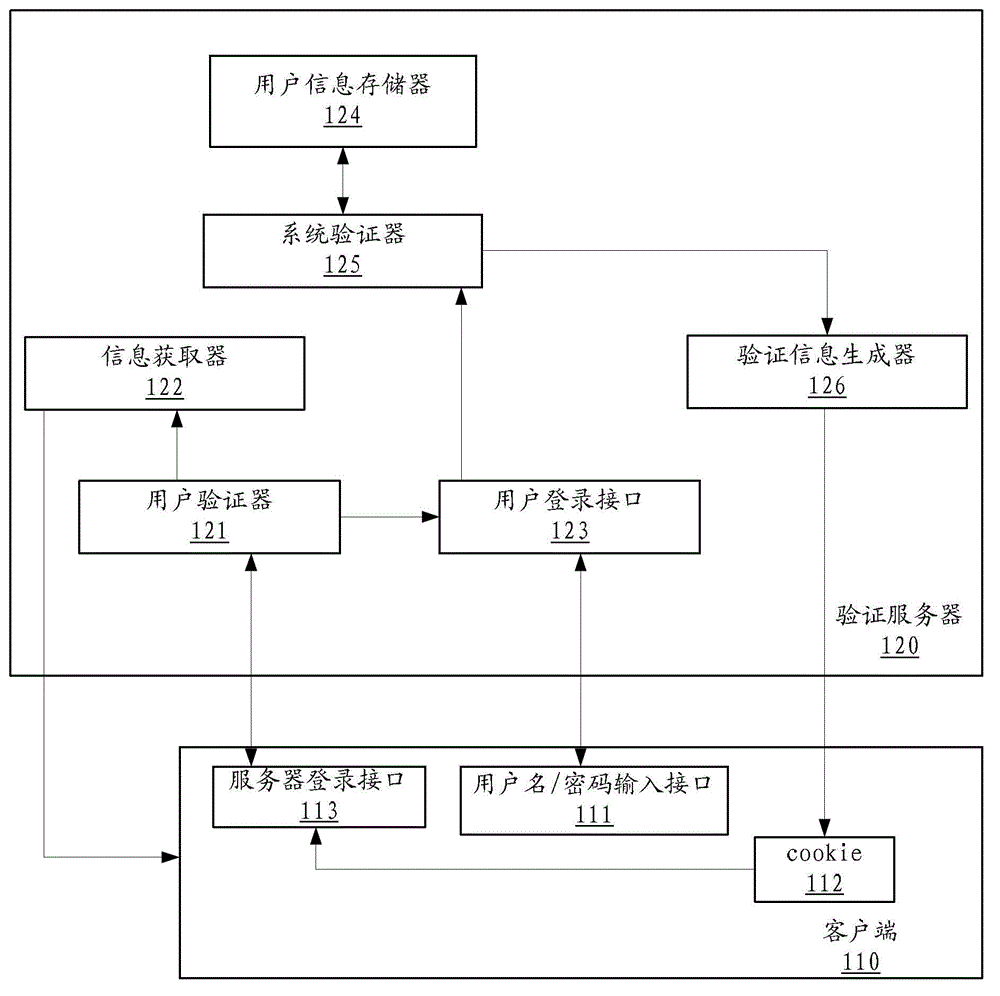
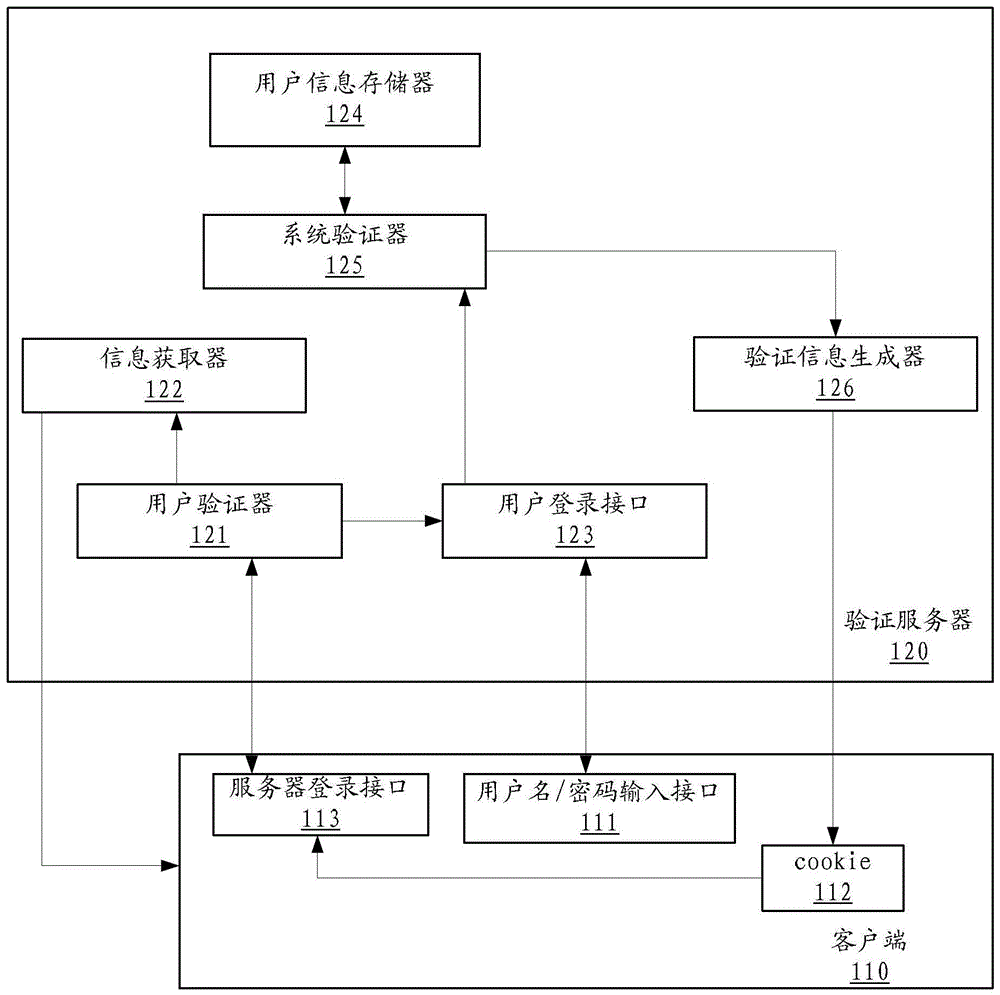
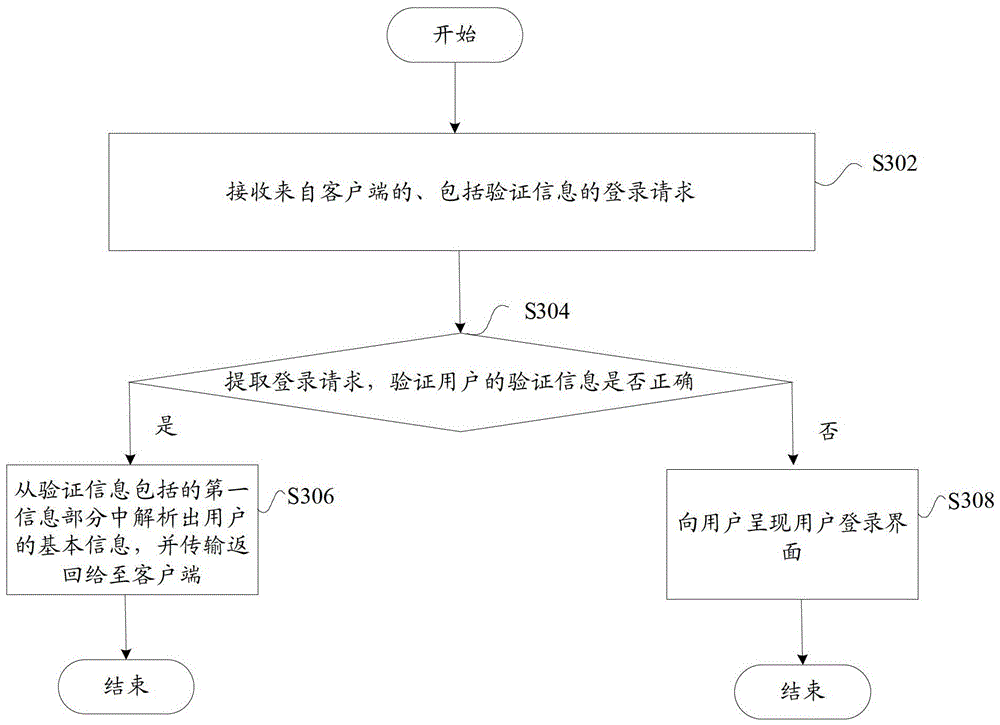
User verification method, user verification server and user verification system
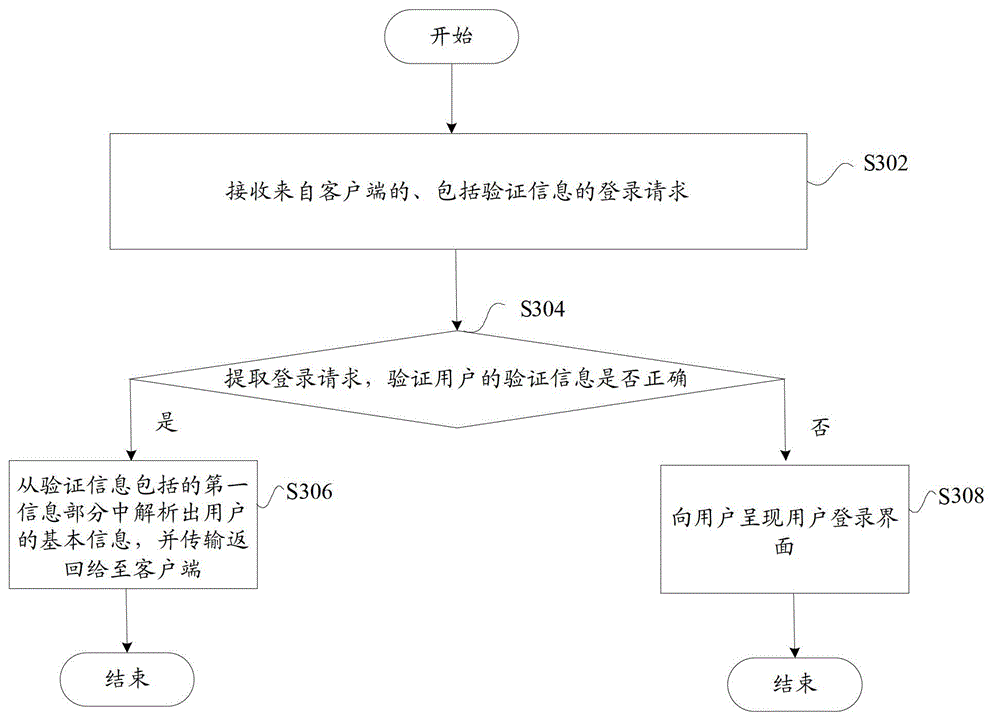
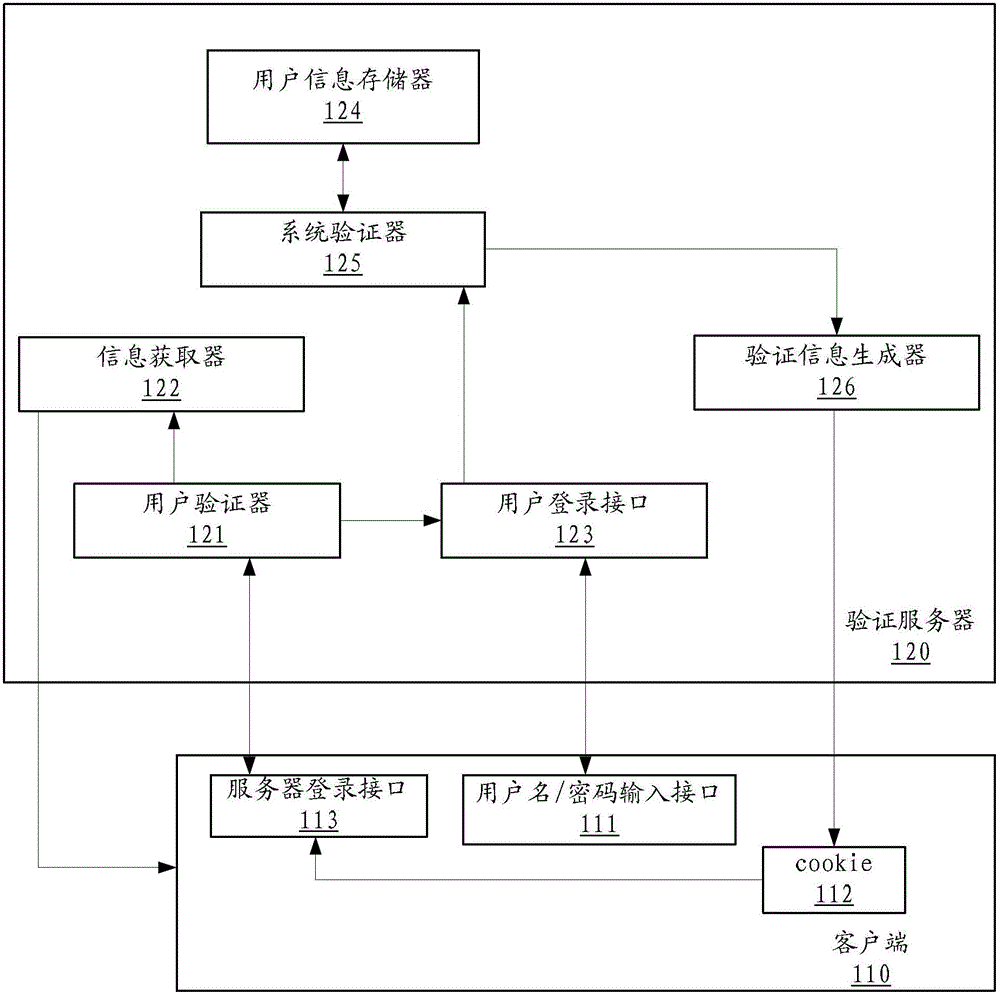
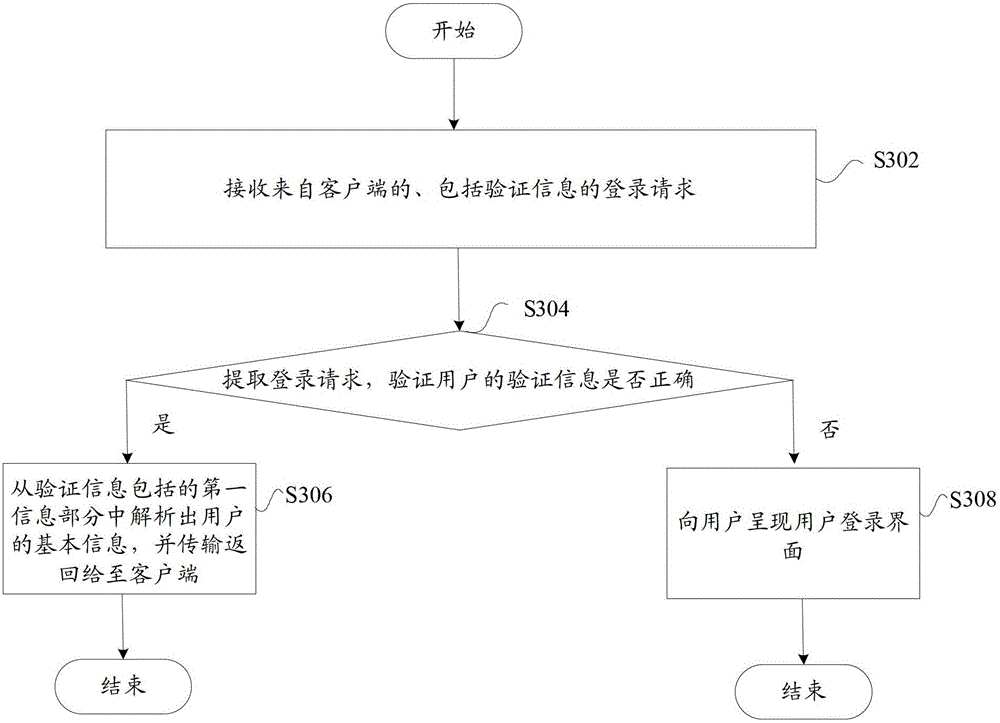
ActiveCN103001770ARealize self-checkingSolve technical problems with potential safety hazardsUser identity/authority verificationUser verificationUser interface
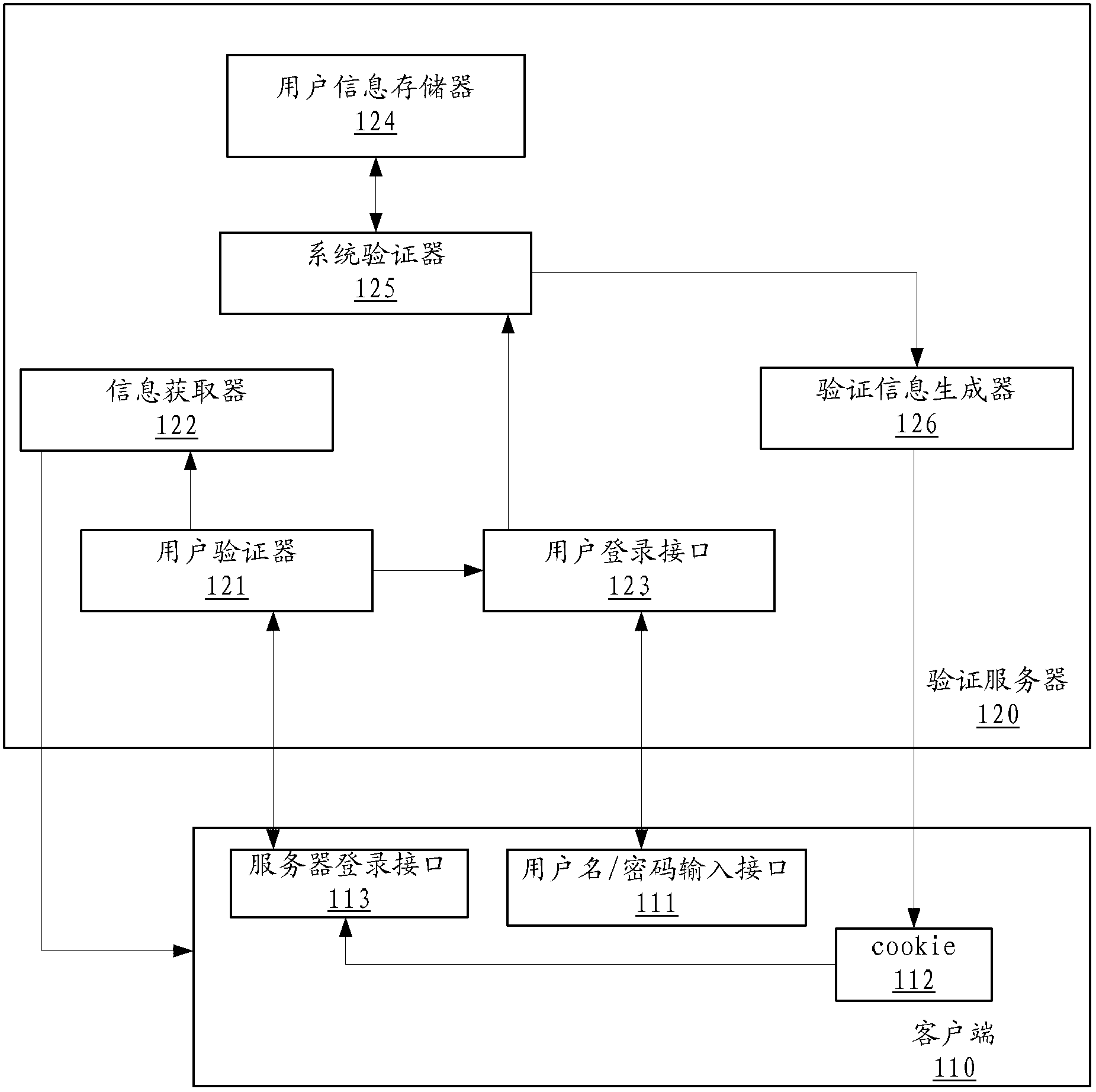
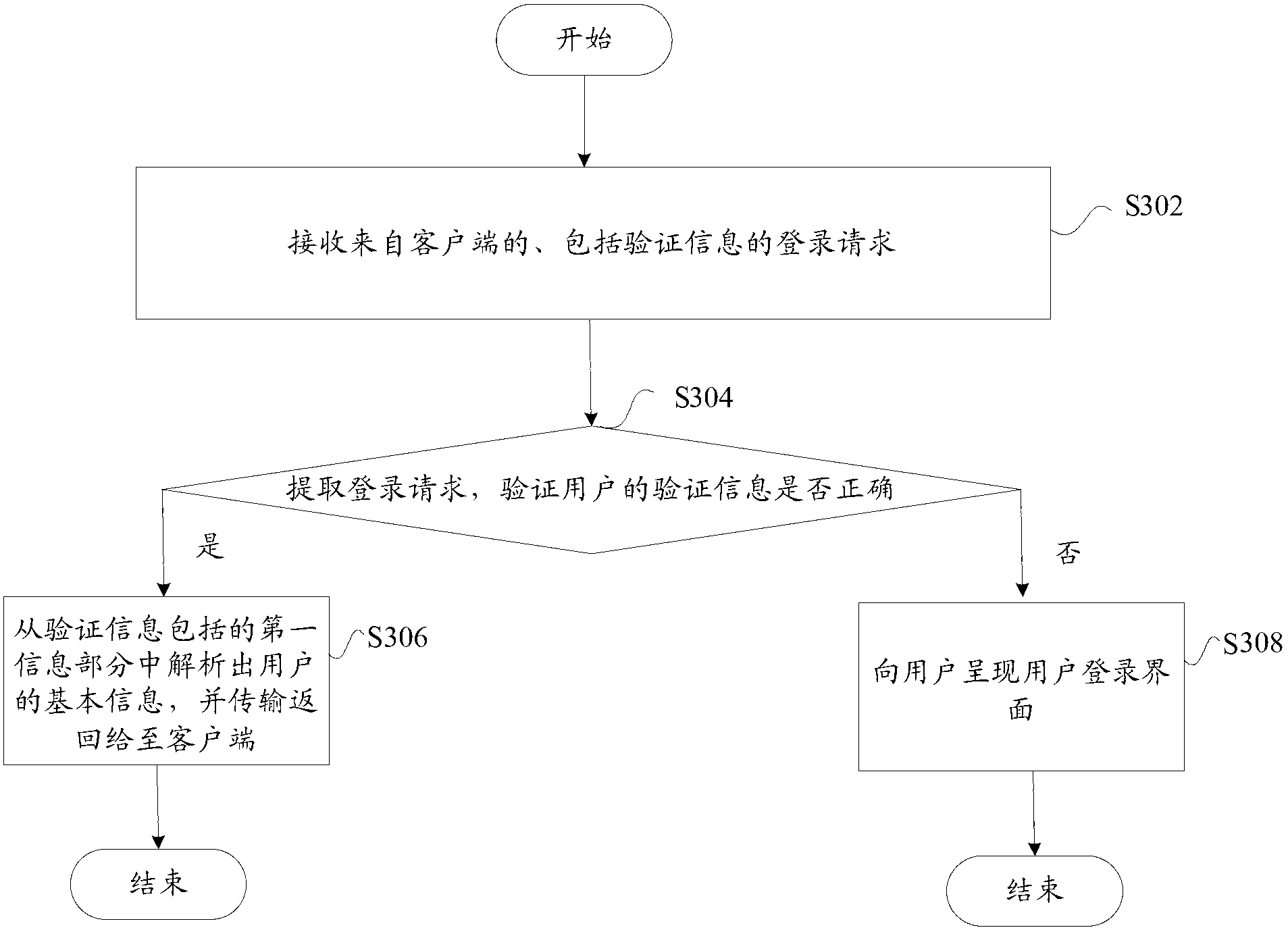
The invention discloses a verification server. The verification server comprises a user verifier, an information acquisition device and a user login interface, wherein the user verifier is used for verifying a login request, the information acquisition device is used for parsing basic information of a user and sending the basic information to the user when verification is successful, and the user login interface is used for presenting a user login interface to the user when verification fails. The user verifier comprises a receiving module, an encryption module and a verification module, wherein the receiving module receives the login request including verification information, a first information part of the verification information includes the basic information of the user, and a second information part includes a first check character string generated after the basic information of the user is encrypted by the aid of the predetermined encryption rule; the encryption module is used for encrypting the basic information of the user by the aid of the predetermined encryption rule to obtain a second check character string; and the verification module is used for determining verification to be successful if the second check character string is matched with the first check character string. By the verification server, the technical problem that system security risk due to the fact that a malicious user logins a system through a counterfeit cookie is solved. The invention further discloses a corresponding user verification server and a corresponding user verification system.
Owner:BEIJING QIHOO TECH CO LTD
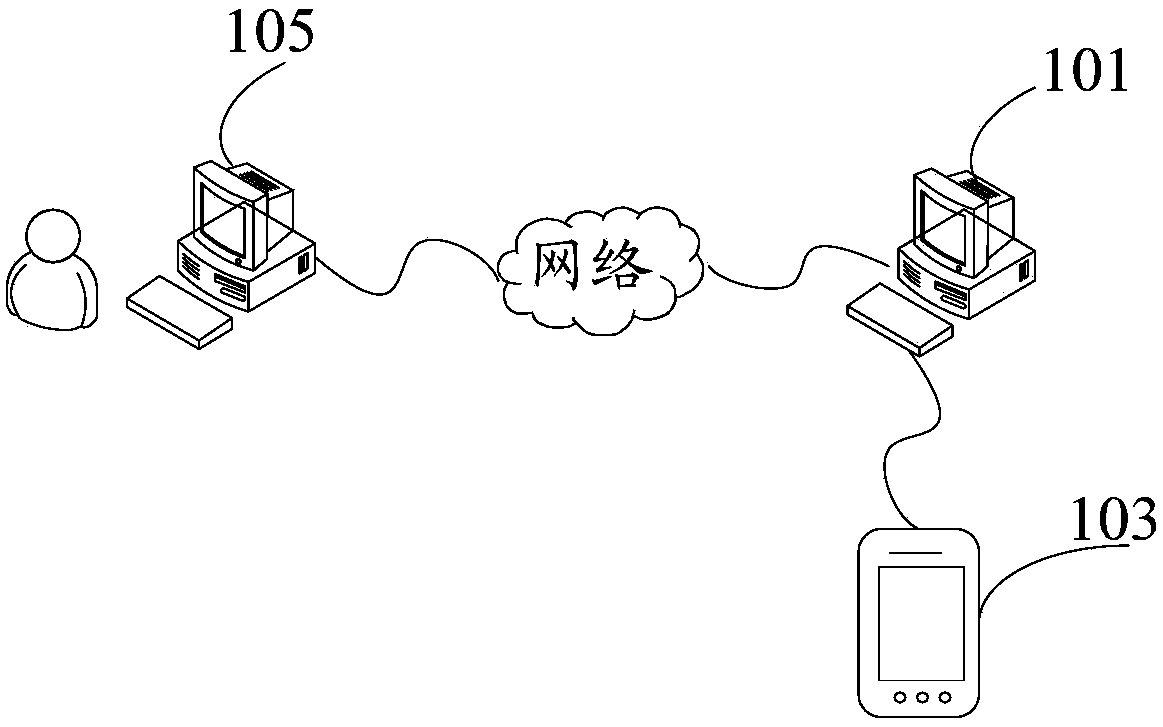
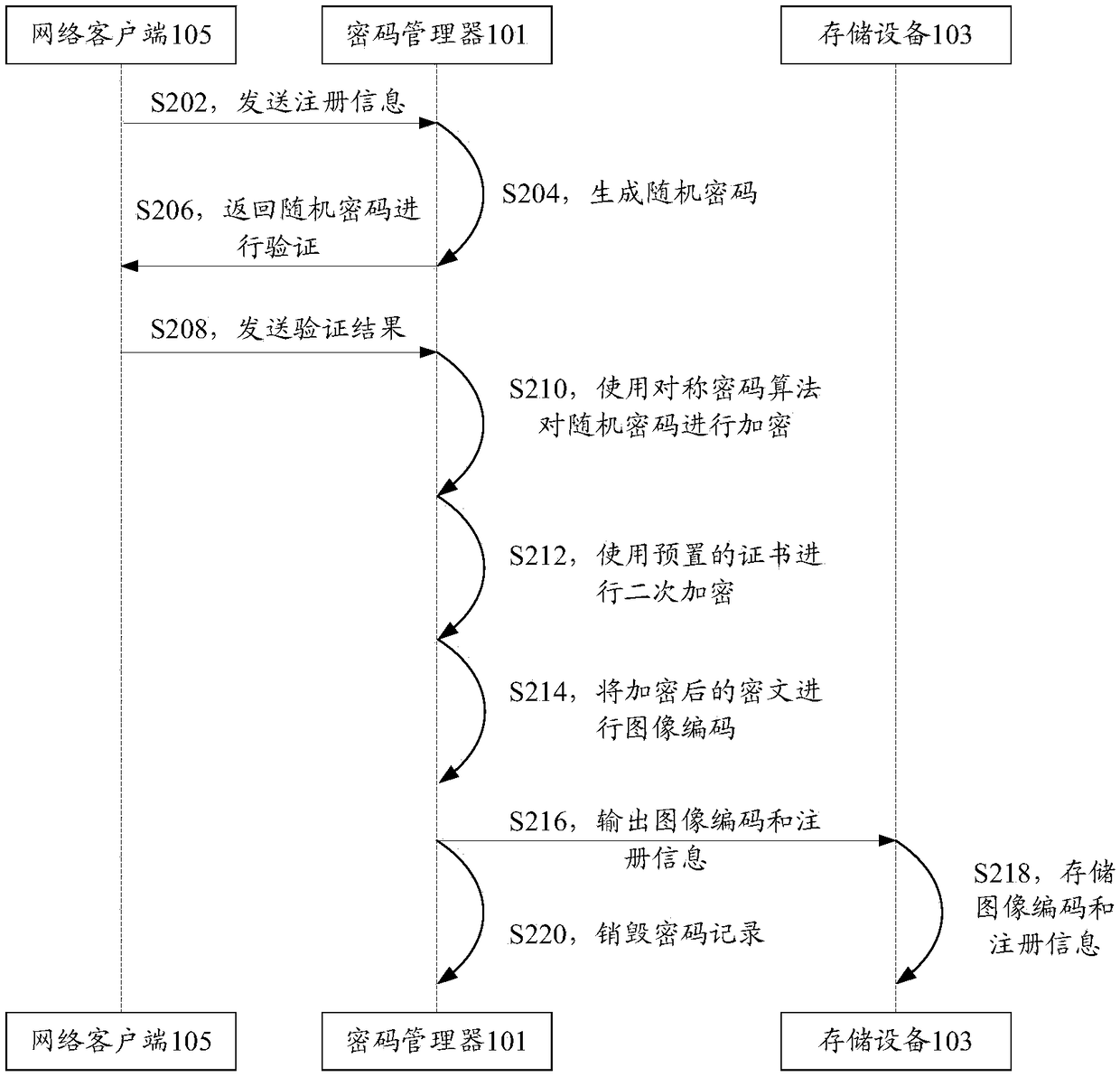
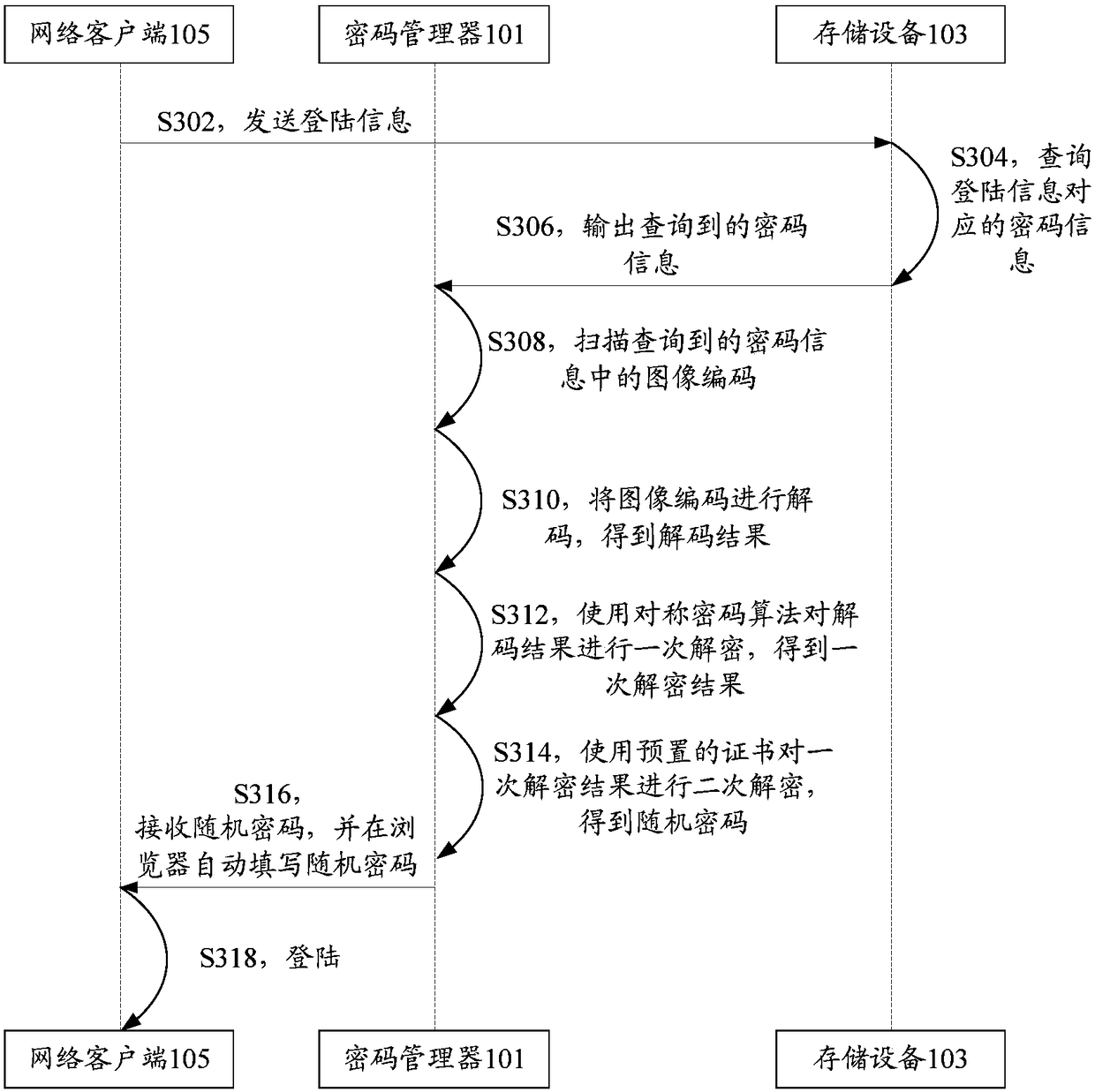
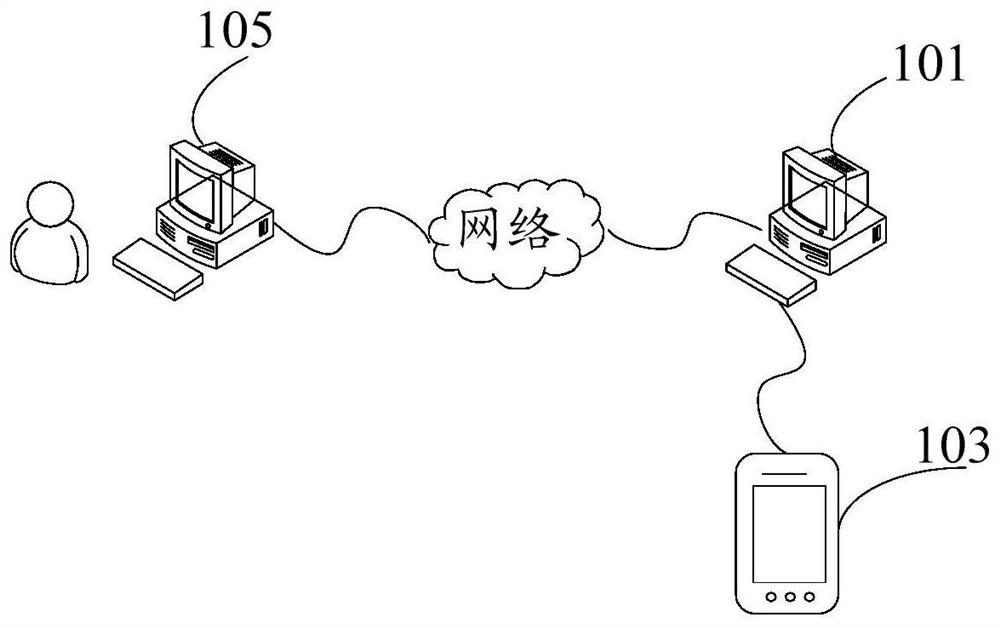
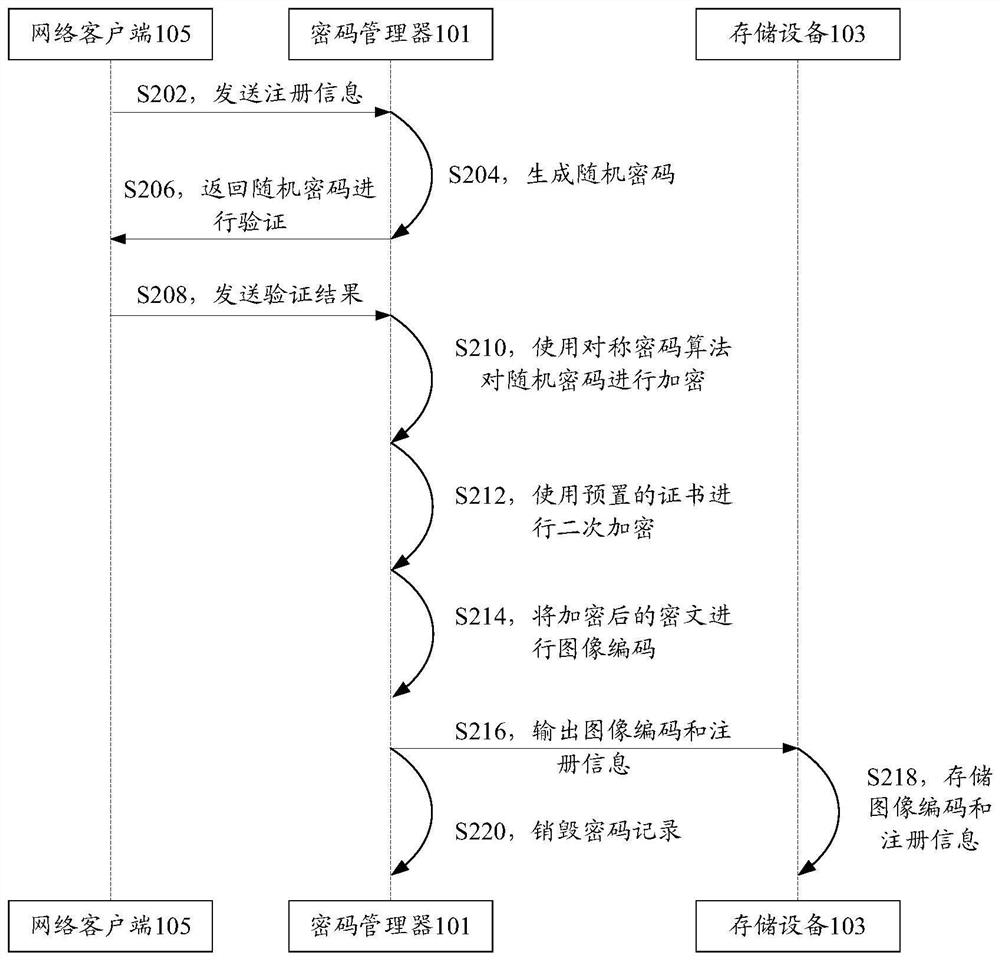
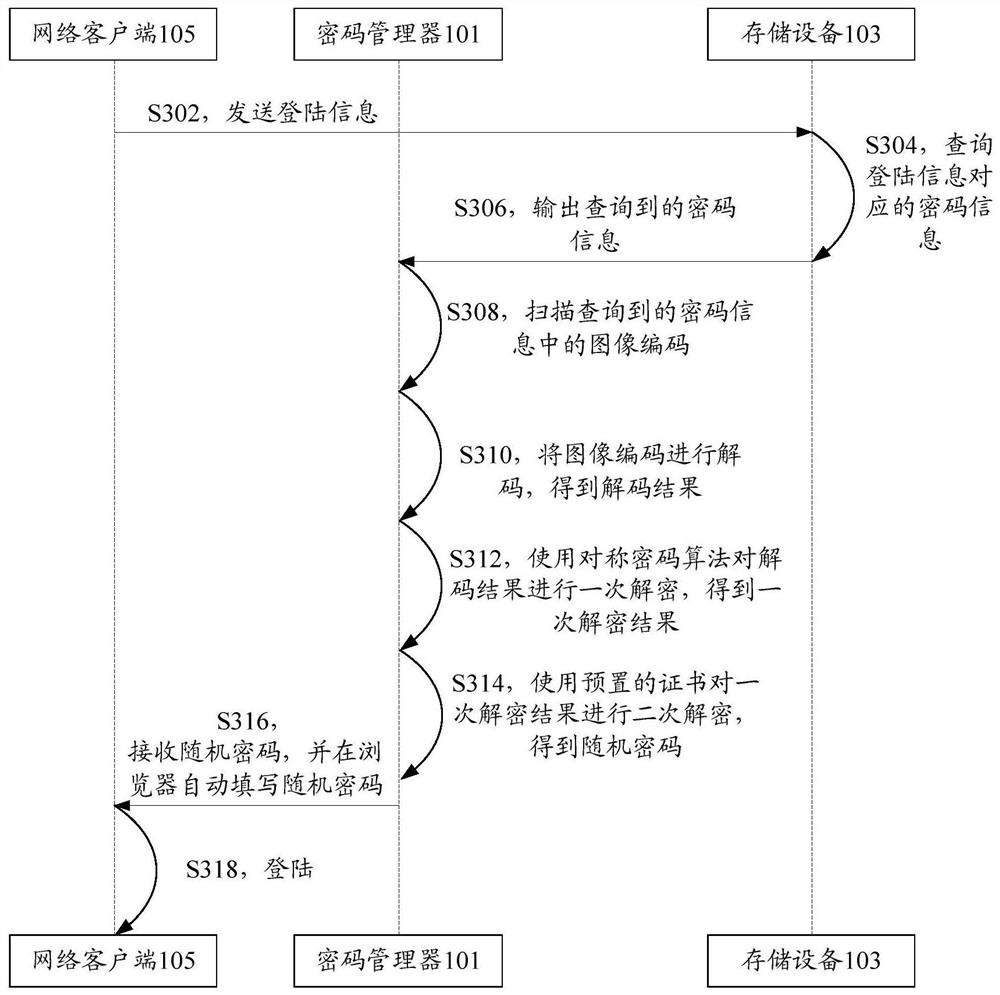
Password storing method, device, system and equipment
ActiveCN108737080AReduce time spent onlineStrengthen security managementKey distribution for secure communicationPassword managerPassword management
The invention discloses a password storing method, device, system and equipment. The password storing method comprises the steps that a password manager obtains registration information and generatescryptograph according to the registration information; the password manager synthesizes password information based on the registration information and the cryptograph; and the password manager sends the password information to the storing equipment, wherein the storing equipment is disconnected from the password manager after receiving the password information and stores the password information offline. According to the password storing method, device, system and equipment, the technical problem that potential safety hazards exist in an existing password storage scheme adopting a password manager is solved.
Owner:ALIBABA GRP HLDG LTD
Method and system for processing data
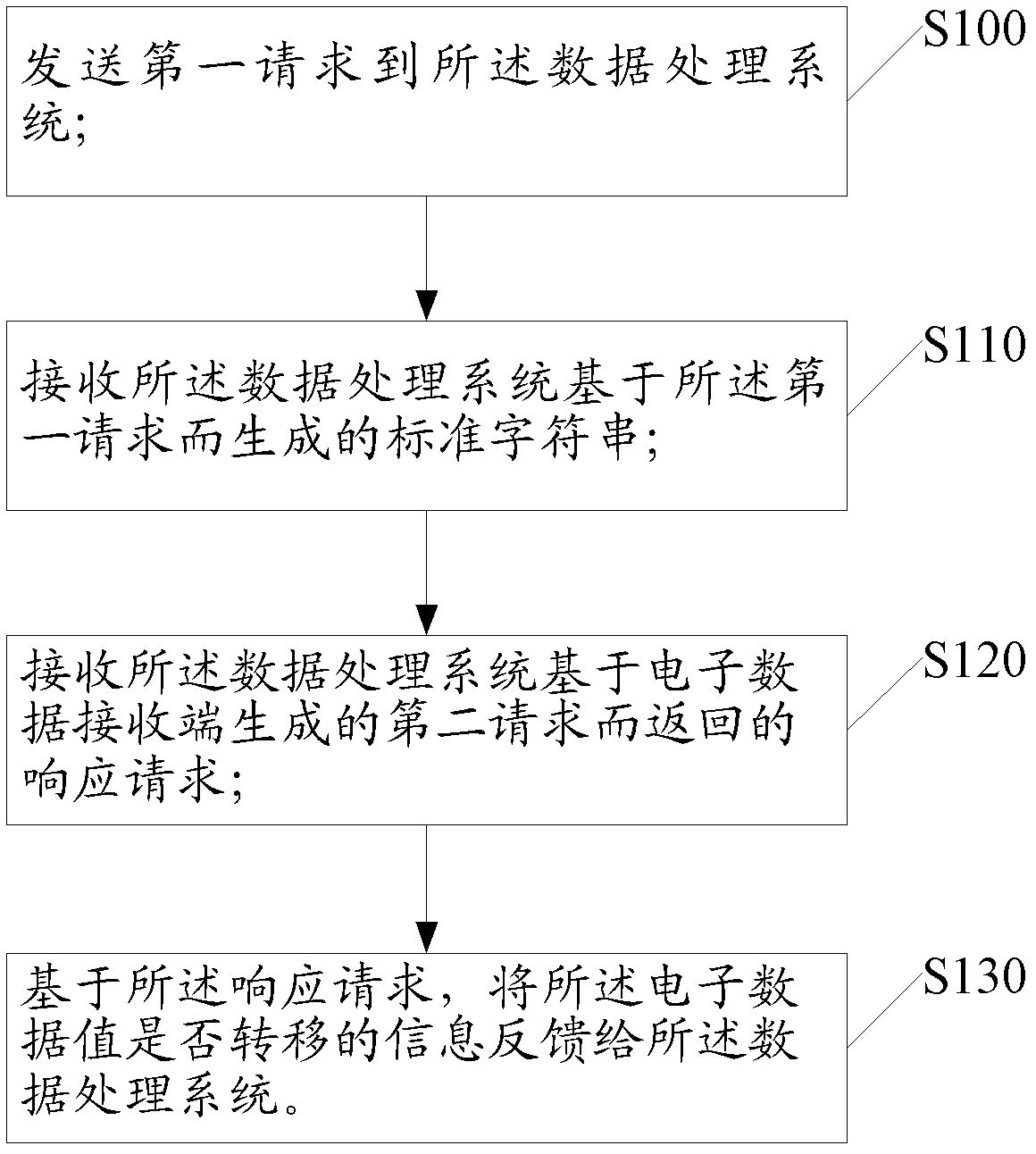
InactiveCN103295132ASolve the problem of money lossAchieve securityProtocol authorisationData processing systemClient-side
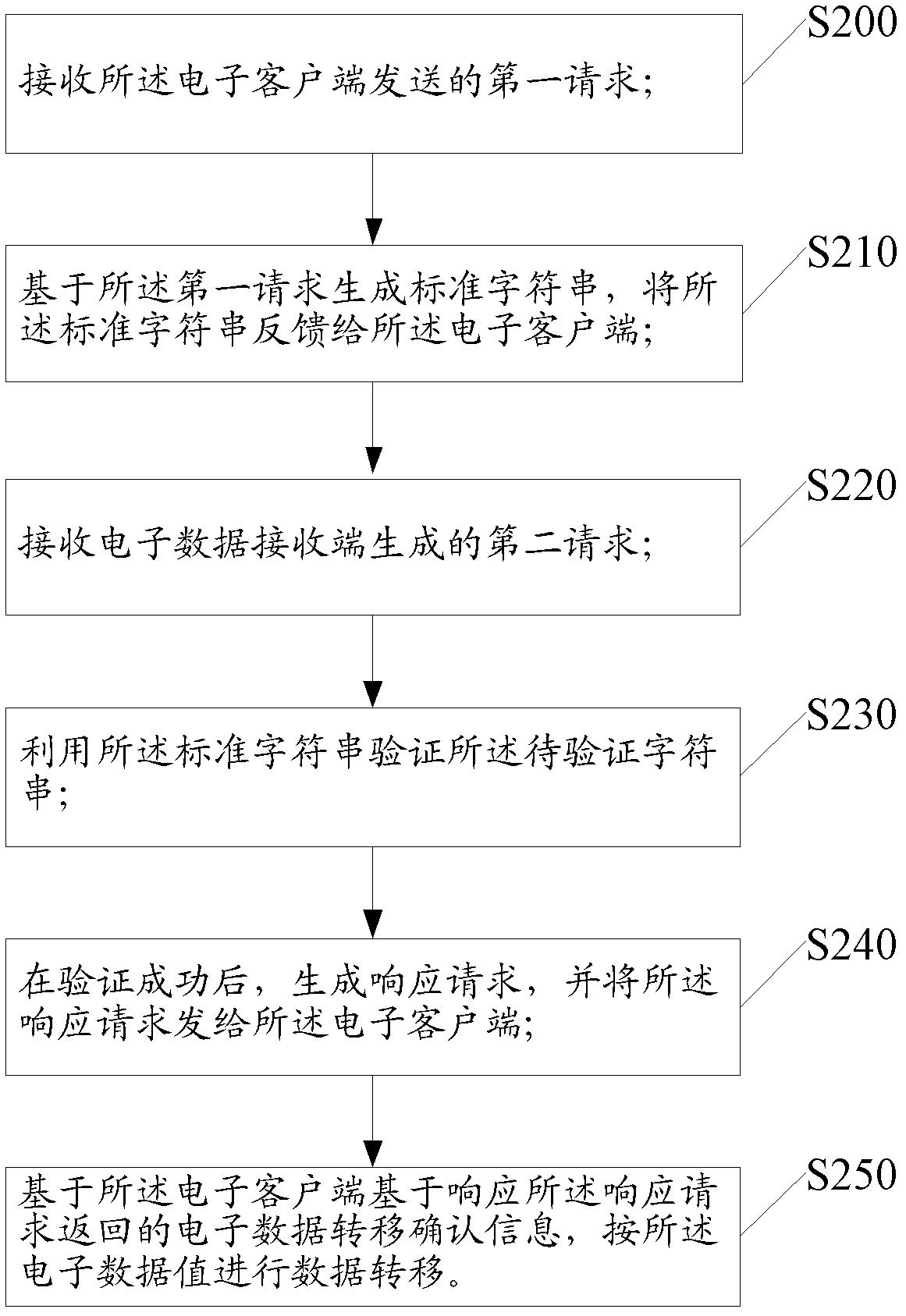
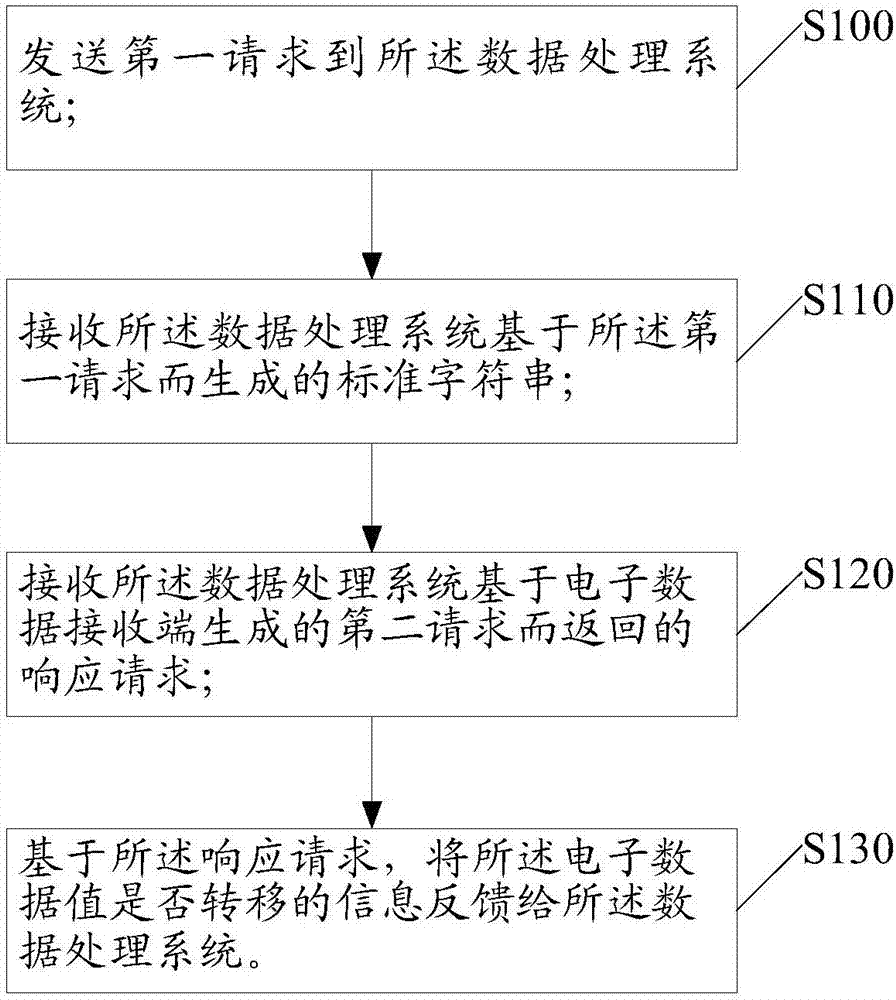
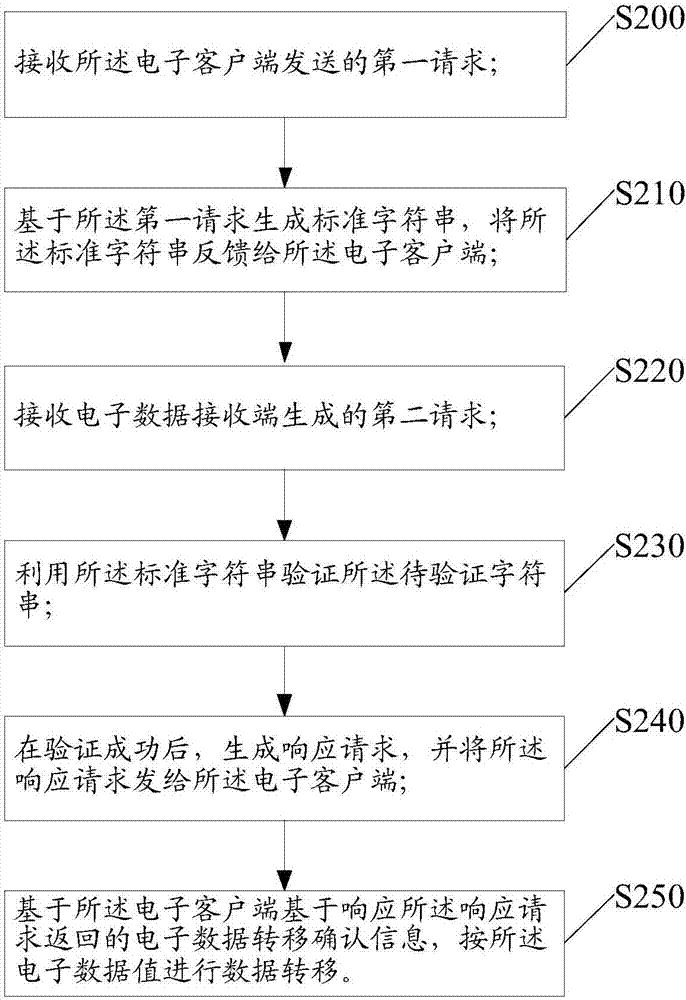
The invention discloses a method and system for processing data. The method is applied to an electronic client-side, wherein the electronic client-side achieves transferring of electronic data by being matched with a system for processing the data. The method includes the steps that a first request is sent to the system for processing the data, the first request data includes account information of the electronic client-side, a standard character string generated by the data processing unit based on the first request is received, the stand character string corresponds to the first request in a unique mode, a response request returned by a second request generated by the system for processing the data based on an electronic data receiving end, and the information about whether electronic data values are transferred or not is fed back to the system for processing the data based on the response request.
Owner:ALIBABA GRP HLDG LTD
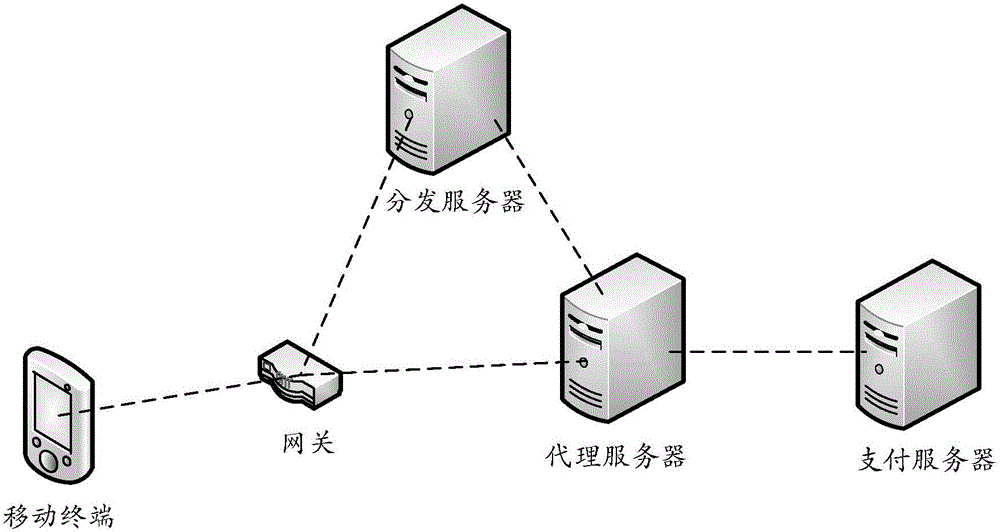
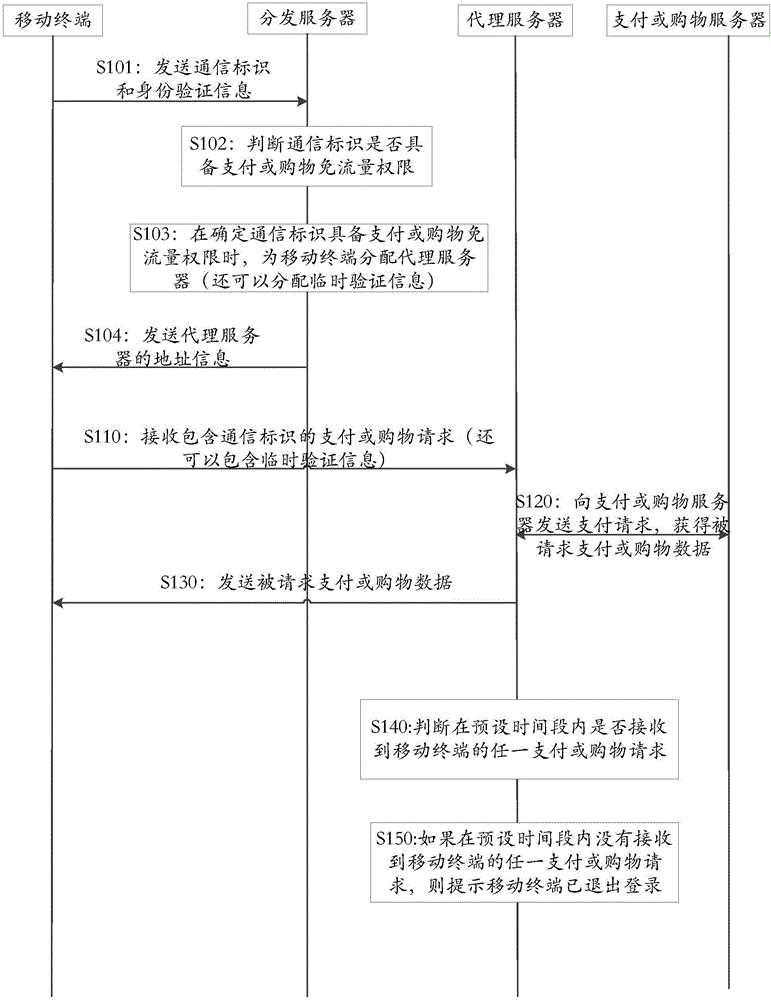
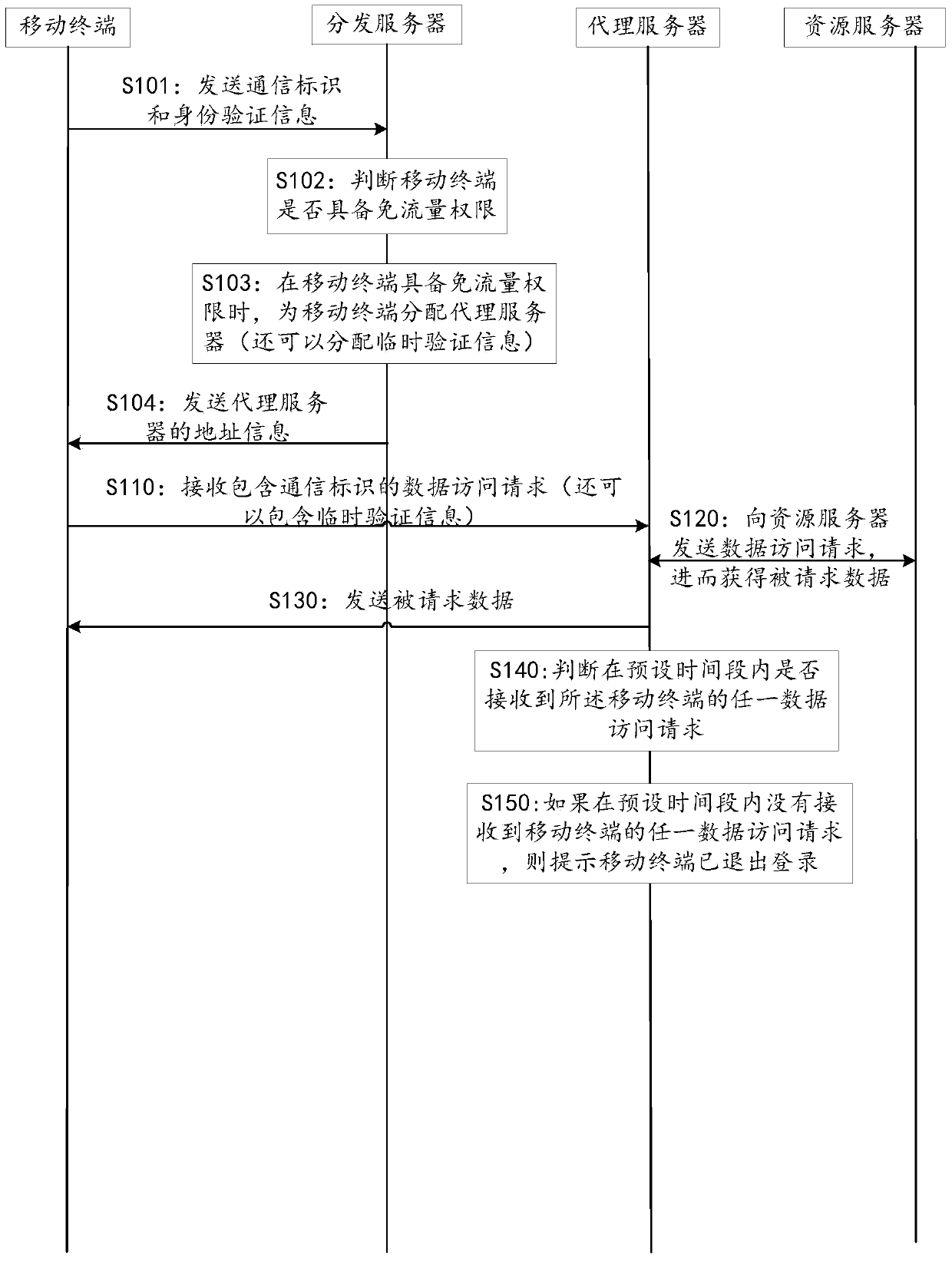
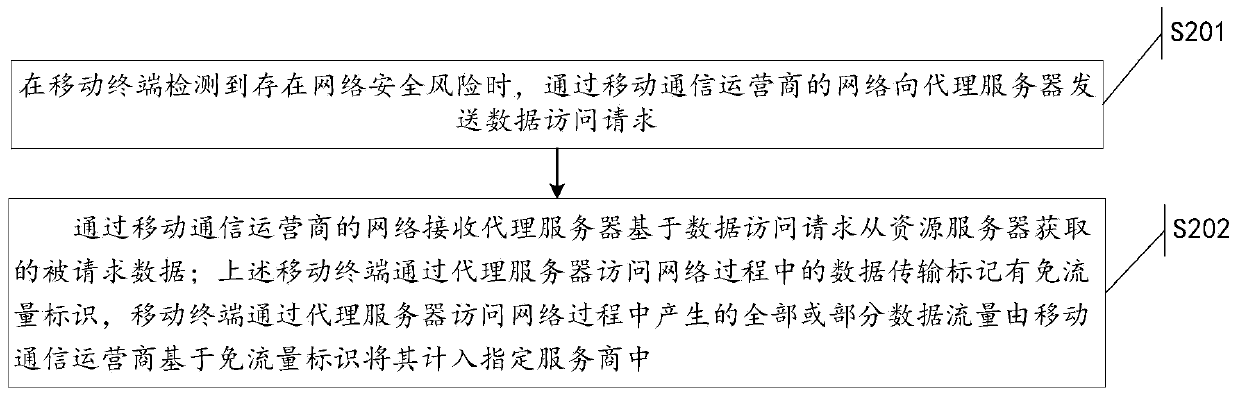
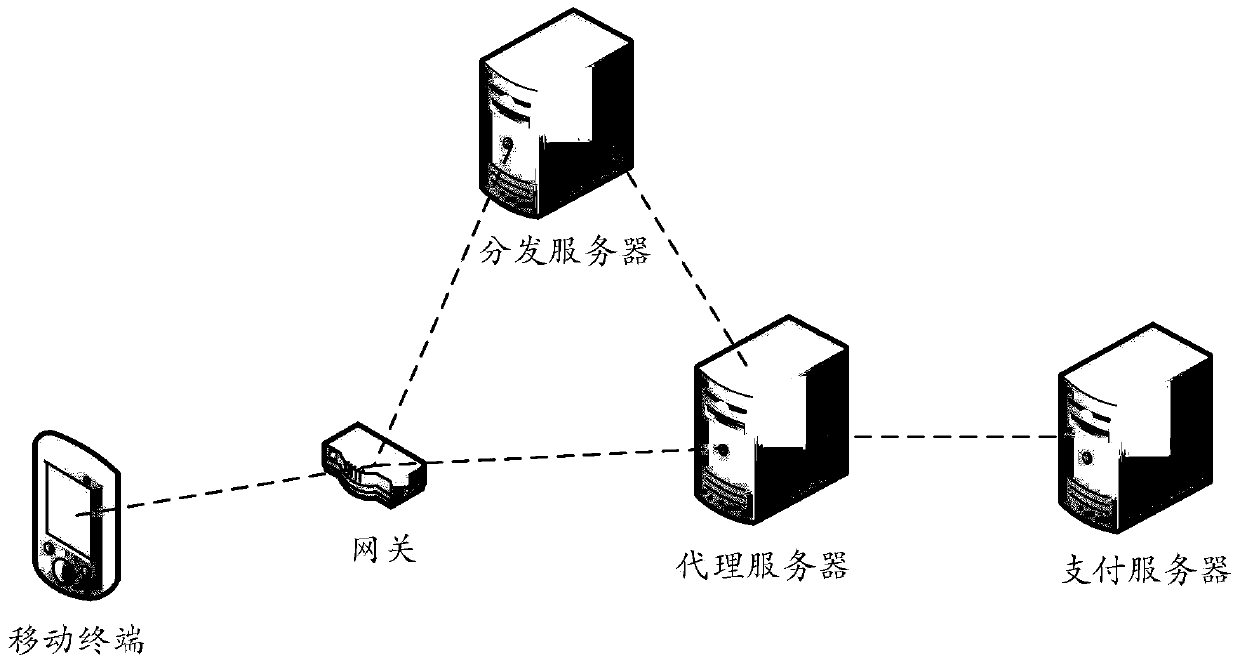
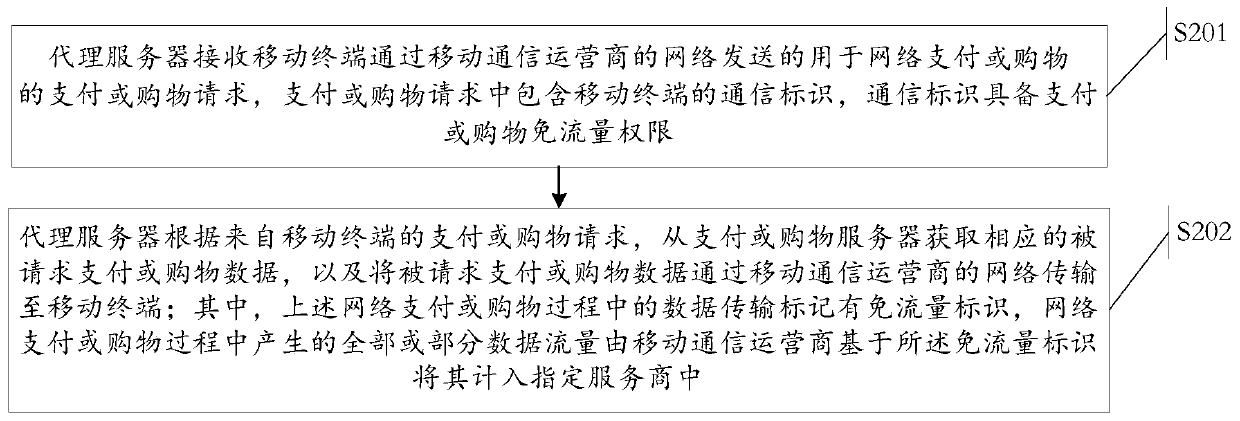
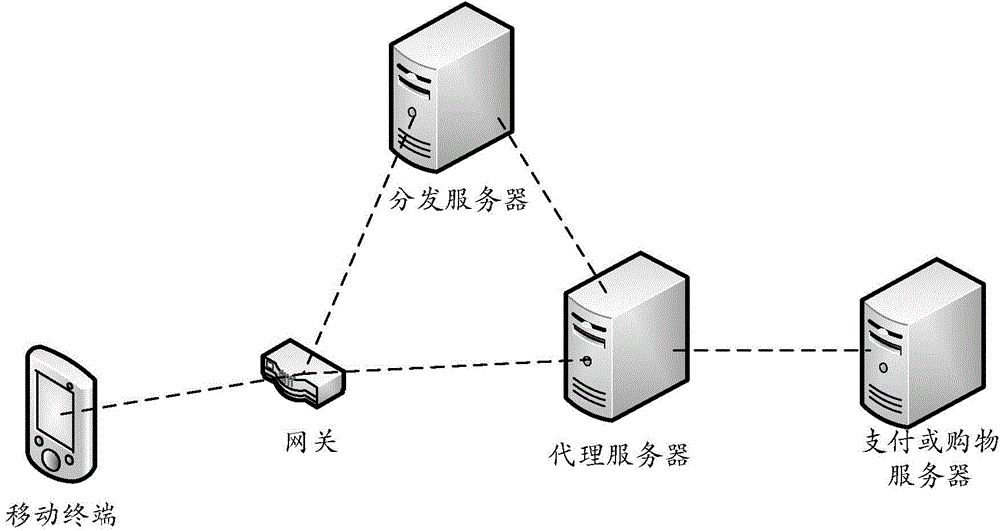
Traffic-free security takeover method
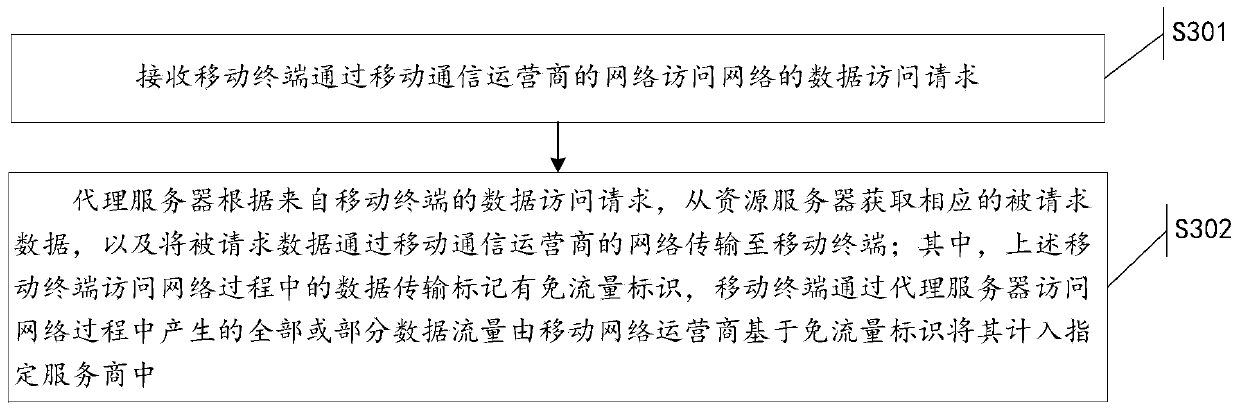
ActiveCN104902481AEnsure safetySolve technical problems with potential safety hazardsSecurity arrangementTraffic capacityData access
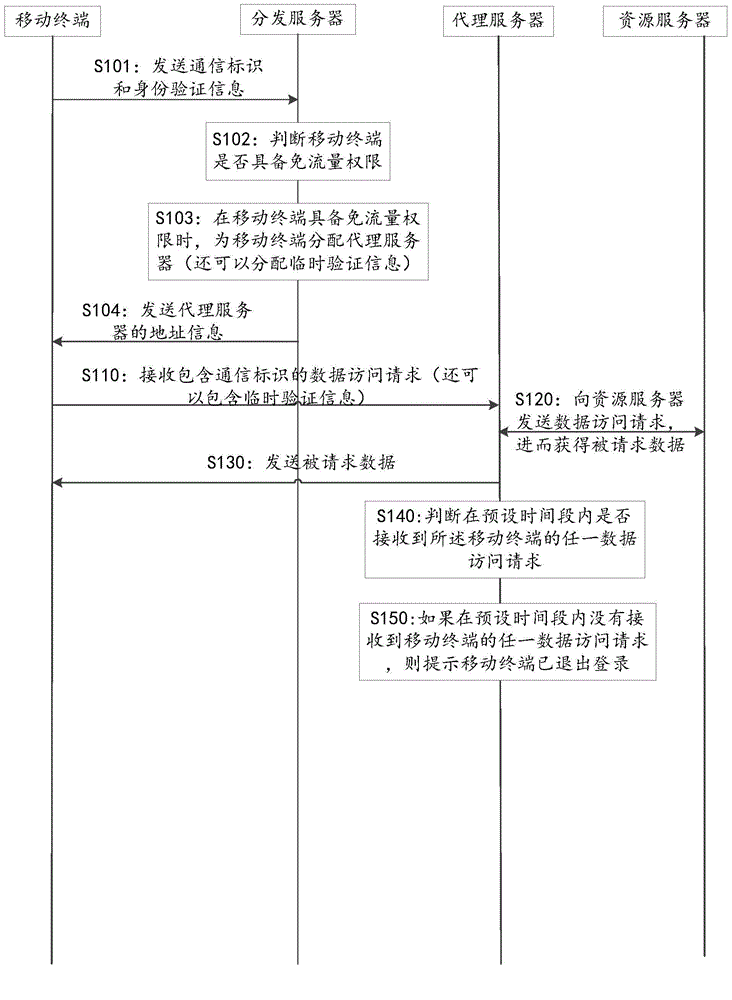
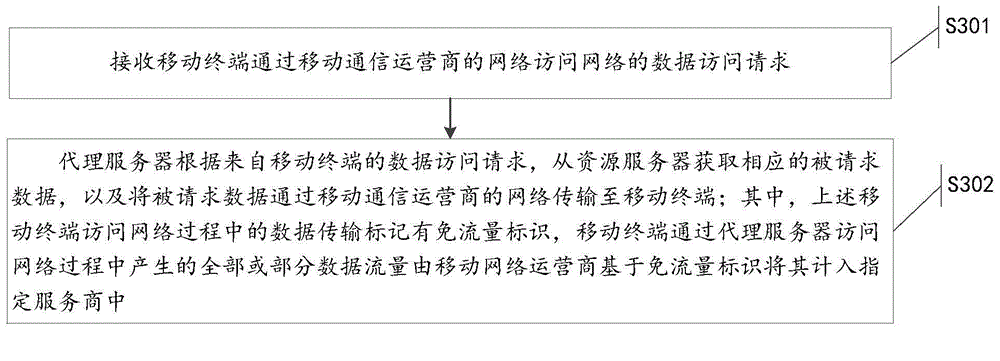
The invention discloses a traffic-free security takeover method. The traffic-free security takeover method comprises the following steps: when a mobile terminal detects that a network security risk exists, sending a data access request to a proxy server through the network of a mobile telecom carrier; receiving requested data which are acquired from a resource server by the proxy server based on the data access request through the network of the mobile telecom carrier, wherein a traffic-free mark is marked for data transmission in the network access process of the mobile terminal through the proxy server, and all or part of data traffics generated in the network access process of the mobile terminal through the proxy server are included in a designated service provider by the mobile telecom carrier based on the traffic-free mark.
Owner:北京鸿享技术服务有限公司
Data encryption and decryption method, data uploading end, data receiving end and system
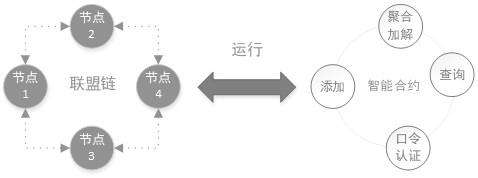
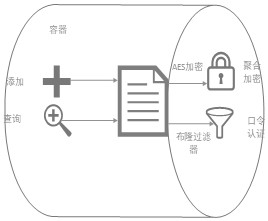
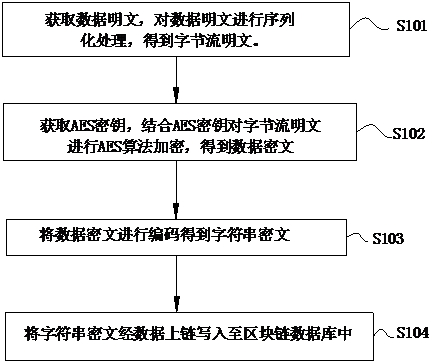
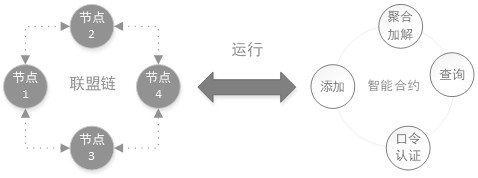
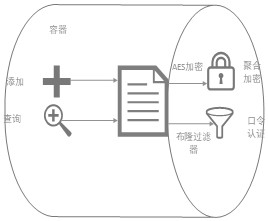
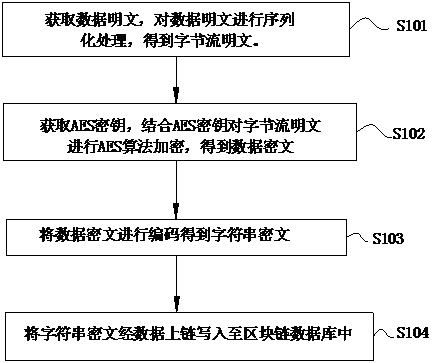
ActiveCN113343286ASolve technical problems with potential safety hazardsThreat to securityDigital data protectionPlaintextCiphertext
The invention provides a data encryption and decryption method, a data uploading end, a data receiving end and a system, the method comprises an encryption method and a decryption method, the encryption method comprises the following steps: acquiring a data plaintext and an AES key, and encrypting the data plaintext in combination with the AES key to obtain a data ciphertext; and encoding the data ciphertext to obtain a character string ciphertext, and writing the character string ciphertext into a block chain database. The decryption method comprises the following steps: acquiring a data ciphertext, a decryption password and a preset password, and authenticating the decryption password and the preset password; when the authentication is passed, outputting a data plaintext; and when the authentication is not passed, outputting the data ciphertext. According to the data encryption and decryption method, the data uploading end, the data receiving end and the system, different bloom filters can be set for verification for different groups of data through a password authentication mode without key distribution, differential verification of the data is realized, data security is ensured, and the problems are solved that in the prior art, an encryption algorithm needs to manage a key, and potential safety hazards exist in data security.
Owner:JIANGXI AGRICULTURAL UNIVERSITY
Hand stubble-cleaning return-to-field operation machine
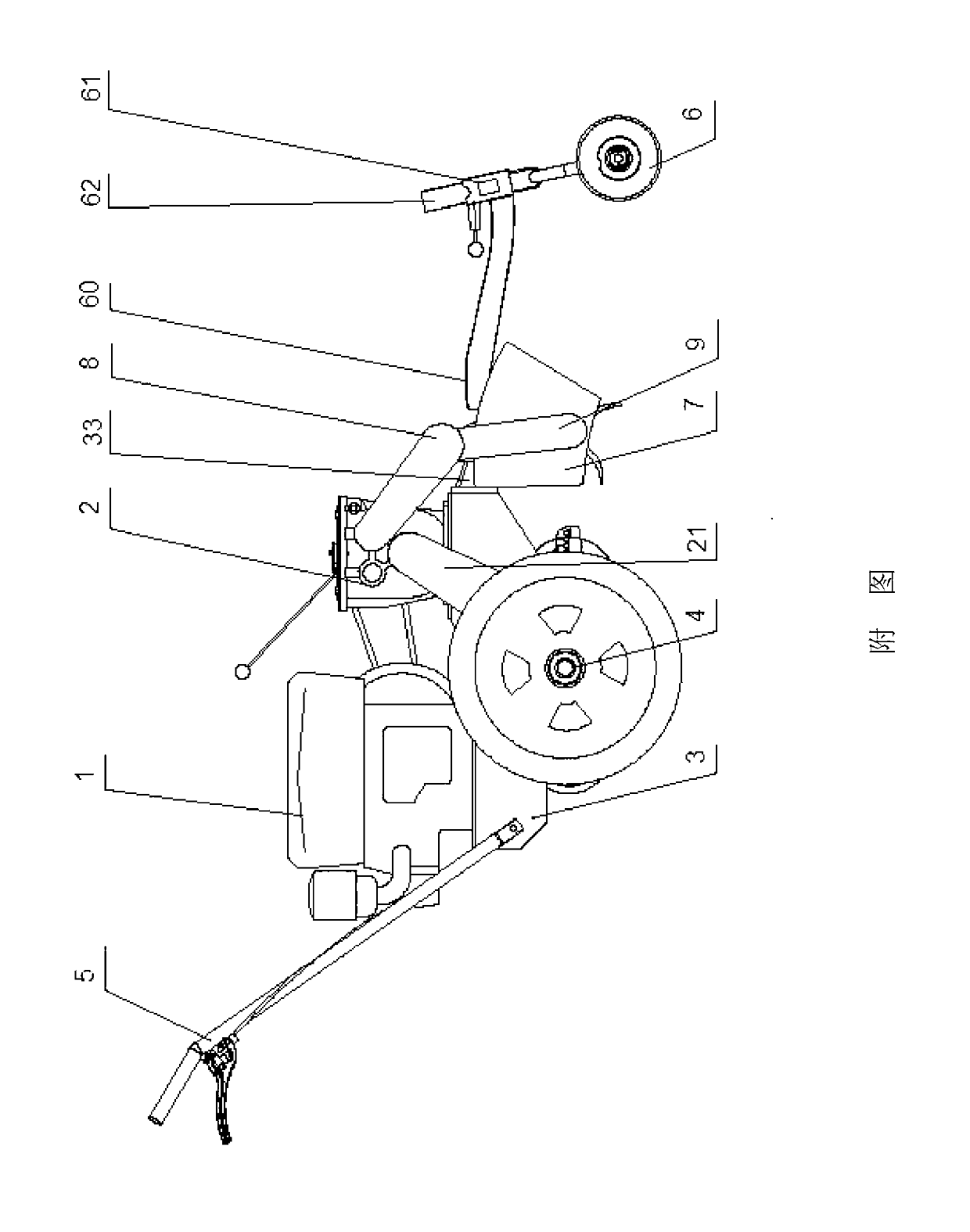
InactiveCN102726173ASolve technical problems with potential safety hazardsStable center of gravityCrop conditionersMowersAgricultural engineeringRidge
The invention provides a hand stubble-cleaning return-to-field operation machine. The operation machine comprises a power walking main machine and a stubble-cleaning assembly, wherein a transmission case in the power walking main machine is arranged on the front part of a machine frame; an engine is arranged on the rear part of the machine frame relative to the transmission case; a walking wheel axle is arranged on the lower part of the machine frame and is in transmission connection with a first output shaft of the transmission case; a ridge guide wheel and a bracket of the ridge guide wheel are arranged at the front end of the machine frame; and the stubble-cleaning assembly is arranged on an installation base, in front of the walking wheel axle, of the machine frame, and a second speed transmission output shaft of the transmission case is in reduction transmission connection with a stubble-cleaning hob shaft arranged in front of the walking wheel axle. The hand stubble-cleaning return-to-field operation machine has the technical advantages of low energy consumption, labor conservation, capability of cleaning stubbles on sloping fields and high safety.
Owner:张凤武
A user verification method, server and system
ActiveCN103001770BRealize self-checkingSolve technical problems with potential safety hazardsUser identity/authority verificationUser verificationUser authentication
The invention discloses a verification server. The verification server comprises a user verifier, an information acquisition device and a user login interface, wherein the user verifier is used for verifying a login request, the information acquisition device is used for parsing basic information of a user and sending the basic information to the user when verification is successful, and the user login interface is used for presenting a user login interface to the user when verification fails. The user verifier comprises a receiving module, an encryption module and a verification module, wherein the receiving module receives the login request including verification information, a first information part of the verification information includes the basic information of the user, and a second information part includes a first check character string generated after the basic information of the user is encrypted by the aid of the predetermined encryption rule; the encryption module is used for encrypting the basic information of the user by the aid of the predetermined encryption rule to obtain a second check character string; and the verification module is used for determining verification to be successful if the second check character string is matched with the first check character string. By the verification server, the technical problem that system security risk due to the fact that a malicious user logins a system through a counterfeit cookie is solved. The invention further discloses a corresponding user verification server and a corresponding user verification system.
Owner:BEIJING QIHOO TECH CO LTD
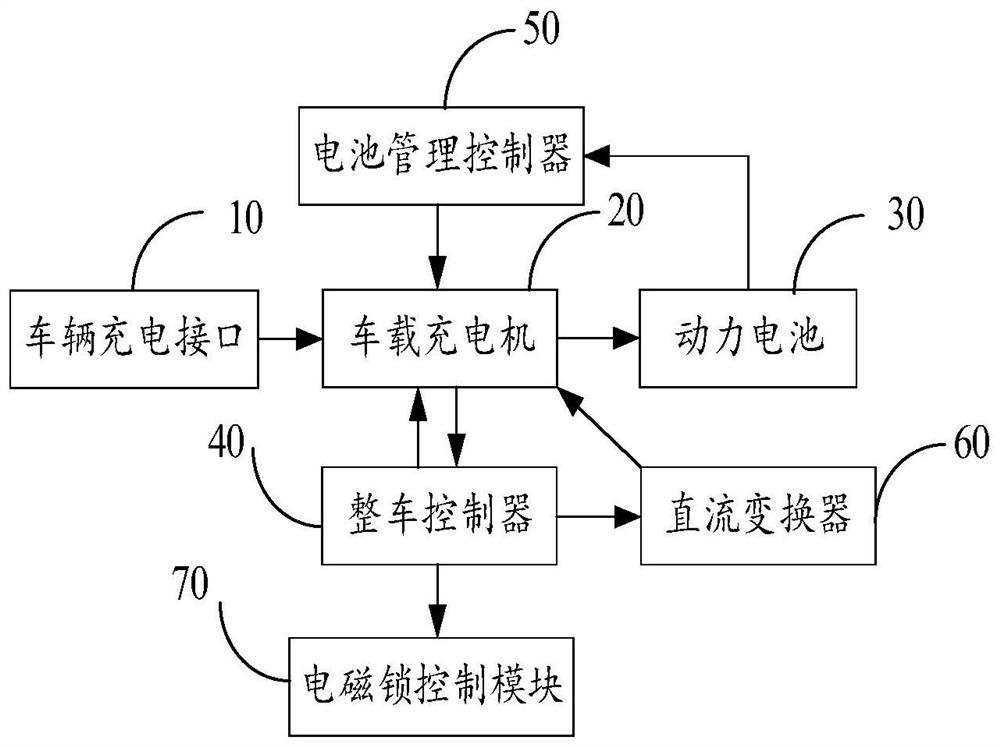
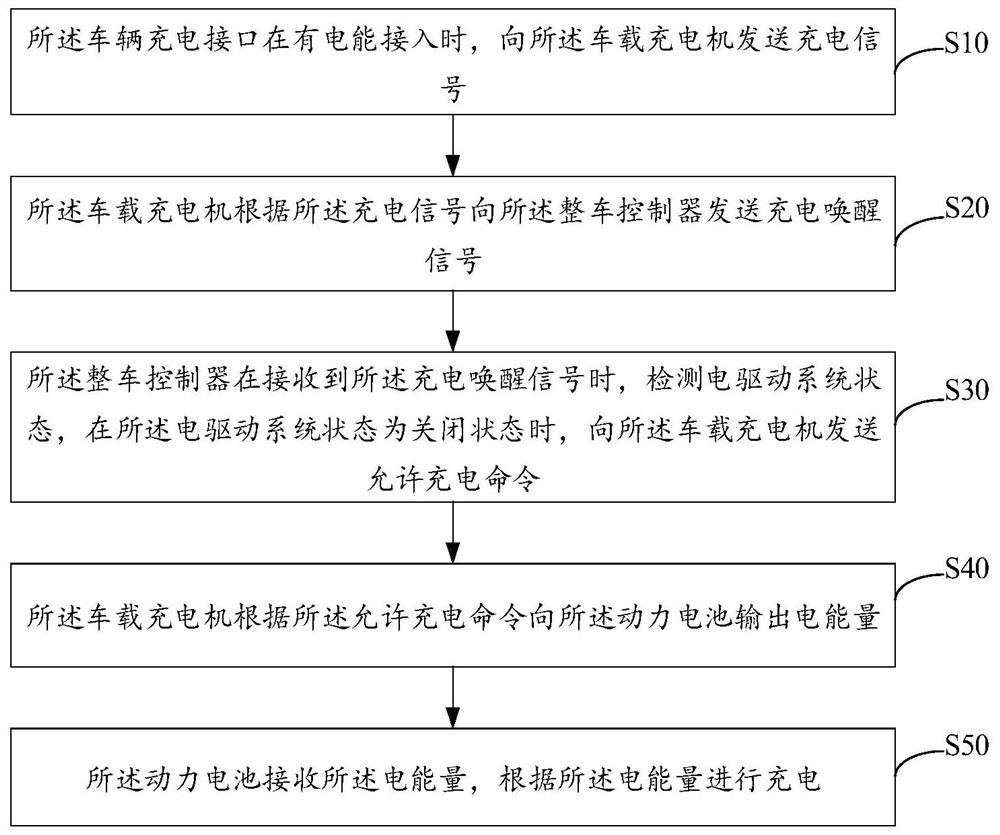
Vehicle-mounted charging system and method
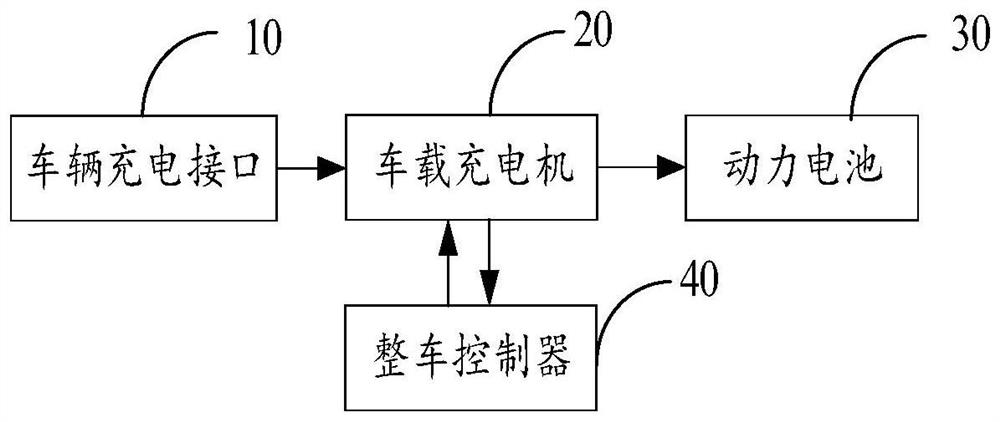
InactiveCN112428841AAvoid damageAvoid electrocutionCharging stationsElectric vehicle charging technologyPower batteryIn vehicle
The invention belongs to the technical field of electric vehicles, and discloses a vehicle-mounted charging system and method. The system comprises a vehicle charging interface, a vehicle-mounted charger, a power battery and a vehicle control unit, when electric energy is accessed into the vehicle charging interface, a charging signal is sent to the vehicle-mounted charger; the vehicle-mounted charger sends a charging awakening signal to the vehicle control unit according to the charging signal; the vehicle control unit detects the state of the electric driving system when receiving the charging awakening signal, and sends a charging allowing command to the vehicle-mounted charger when the state of the electric driving system is a closed state; the vehicle-mounted charger outputs electricenergy to the power battery according to the charging allowing command; and the power battery receives the electric energy and charges according to the electric energy. By means of the mode, it is ensured that a vehicle cannot enter a drivable state in the charging process or when a charging cable is connected, and damage to the vehicle-mounted charging device or electric shock danger is avoided.The technical problem that potential safety hazards exist in an existing alternating current charging device is solved.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
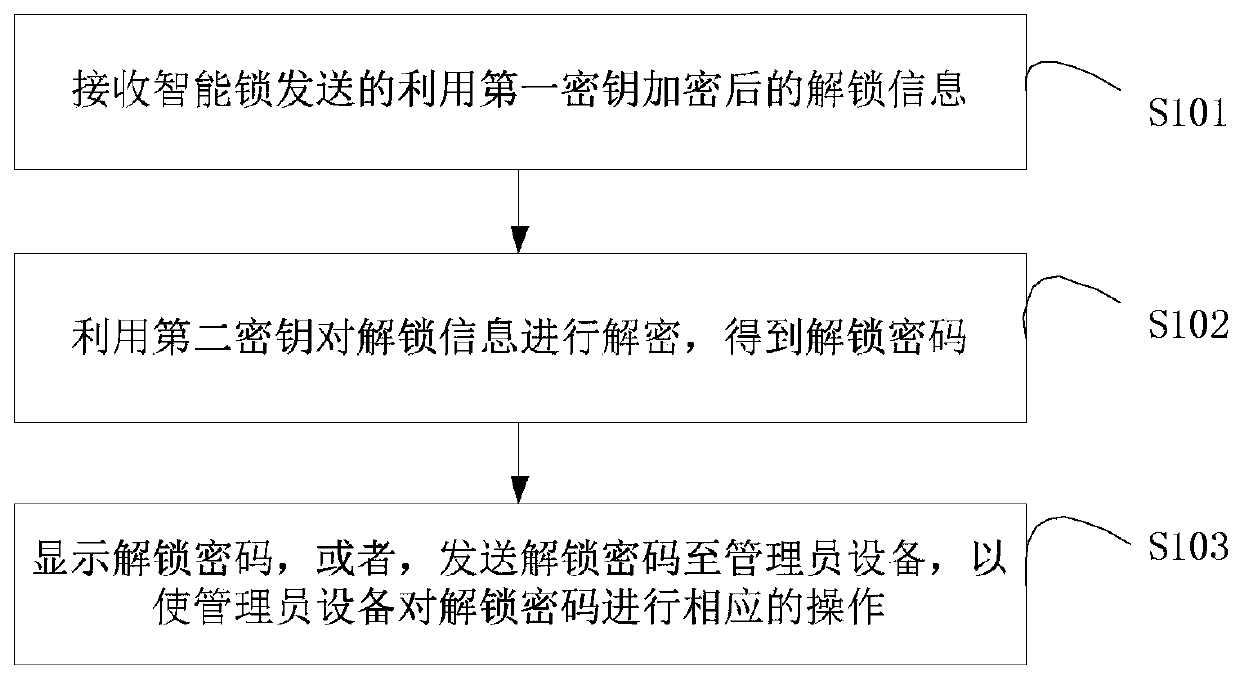
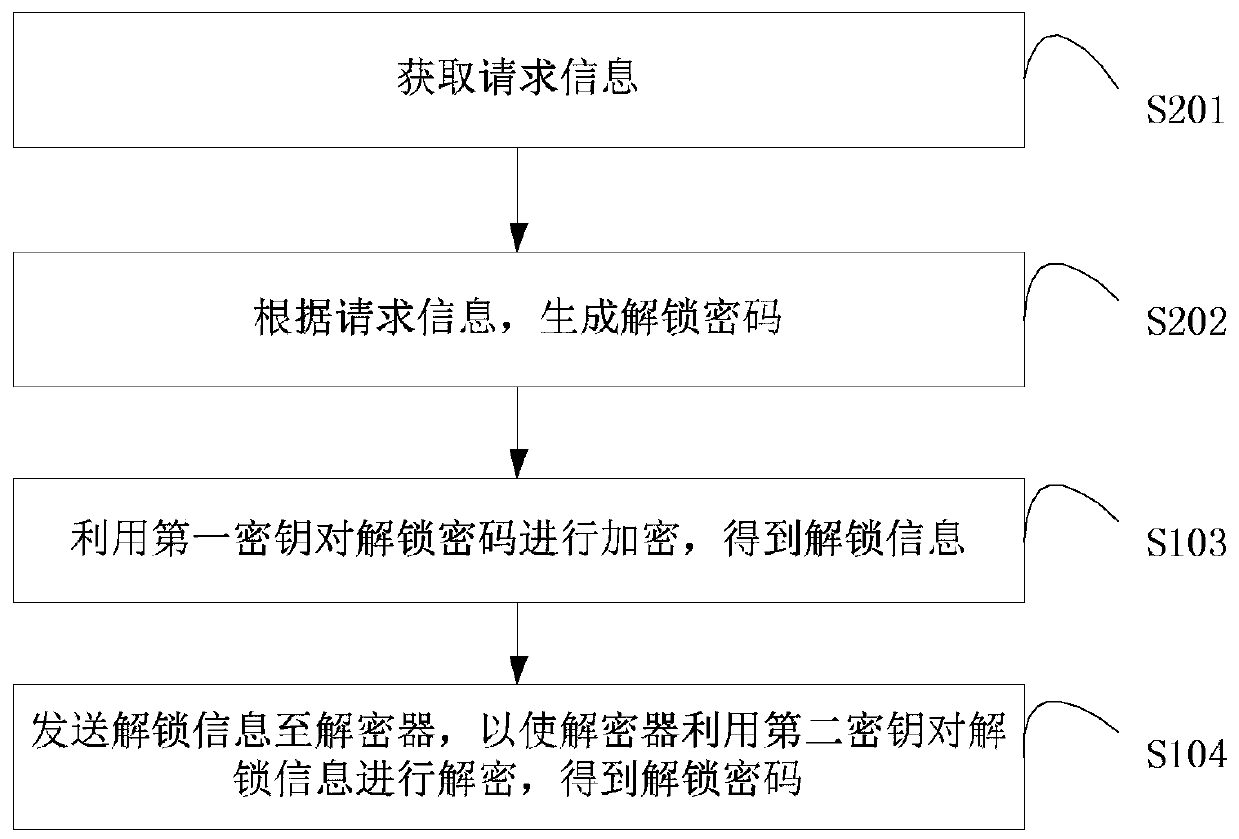
Control method, device and system for intelligent lock and storage medium
InactiveCN109872436AImprove securitySolve technical problems with potential safety hazardsIndividual entry/exit registersPasswordCipher
The invention discloses a control method, device and system for an intelligent lock and a storage medium. The control method for the intelligent lock applied to a decryptor comprises the steps of: receiving unlocking information which is sent by the intelligent lock and encrypted by utilizing a first key, wherein the unlocking information at least comprises an unlocking password; carrying out decryption on the unlocking information by utilizing a second key to obtain an unlocking password, wherein the first key is paired with the second key; and displaying the unlocking password, or sending the unlocking password to manager equipment, so that the manager equipment carries out a corresponding operation on the unlocking password. The encrypted unlocking information sent by the intelligent lock is decrypted by the decryptor to obtain the unlocking password, thereby solving the technical problem of potential safety hazard caused by a case that in the prior art, unlocking of the intelligentlock or password resetting is controlled by a server, and achieving the technical effect of improving use safety of the intelligent lock.
Owner:MICROARRAY MICROELECTRONICS CORP LTD
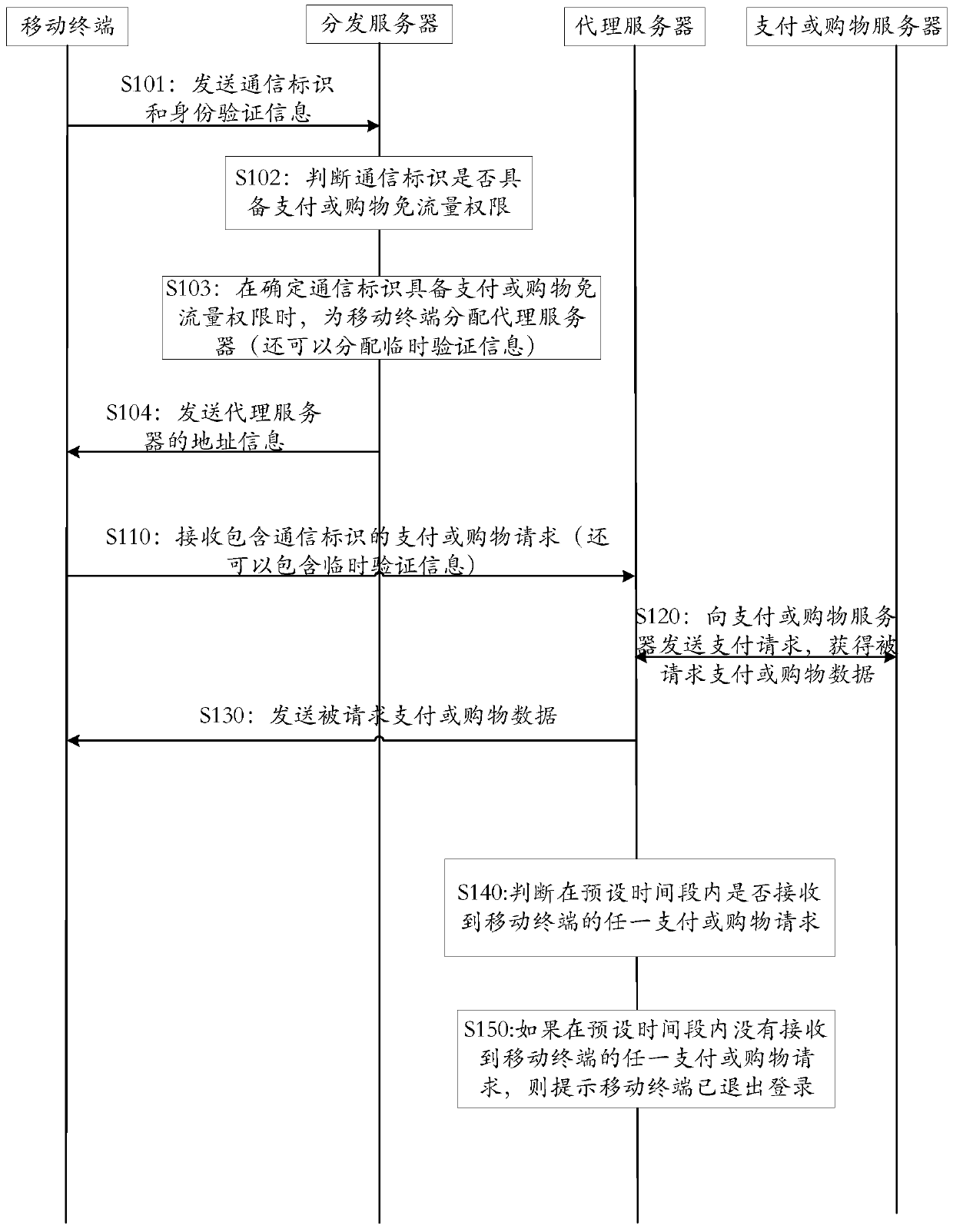
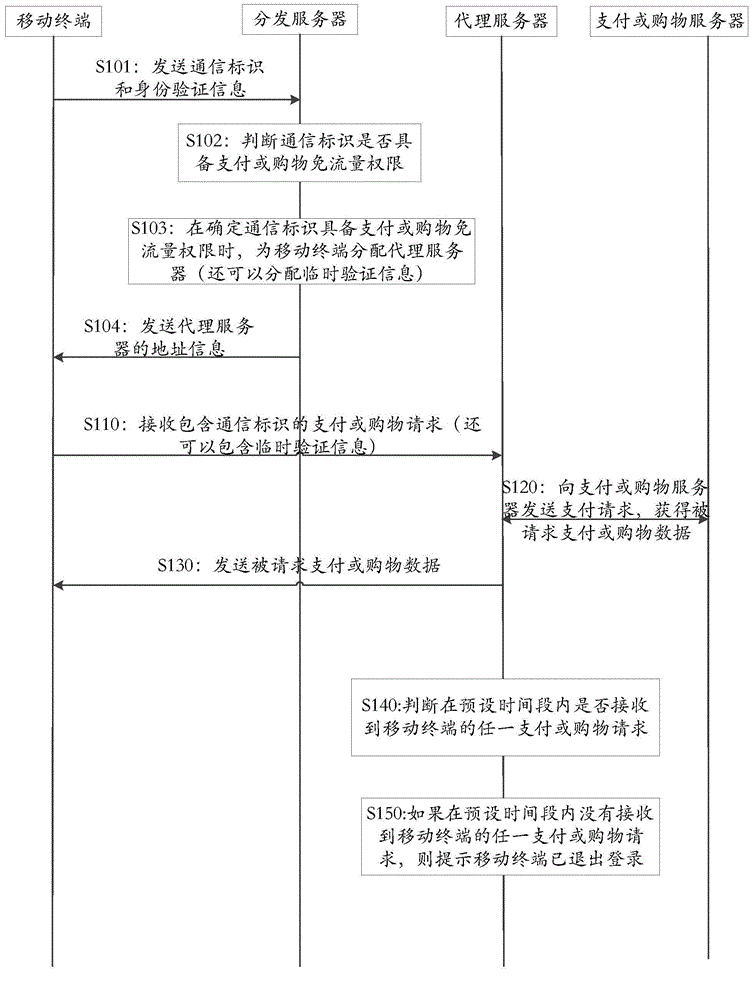
Traffic-free payment or shopping method
ActiveCN104992323ASolve technical problems of potential safety hazardsEnsure safetyPayment architecturePaymentData transmission
The invention discloses a traffic-free payment or shopping method. When a user performs payment or shopping operation, a payment or shopping request for network payment or shopping is sent to a proxy server through a network of a mobile communication operator; requested payment or shopping data which is obtained by the proxy server from a payment or shopping server based on the payment or shopping request is received through the network of the mobile communication operator; and data transmission in the network payment or shopping process is marked with a traffic-free identification, and all or partial data traffic generated in the network payment or shopping process is counted in an assigned service provider by the mobile communication operator based on the traffic-free identification. Therefore, the traffic-free network payment or shopping is achieved through the network of the mobile communication operator, and the beneficial effect that the expense of data traffic consumed in the network payment or shopping process cannot be undertaken is achieved under the precondition of ensuring payment or shopping safety.
Owner:北京鸿享技术服务有限公司
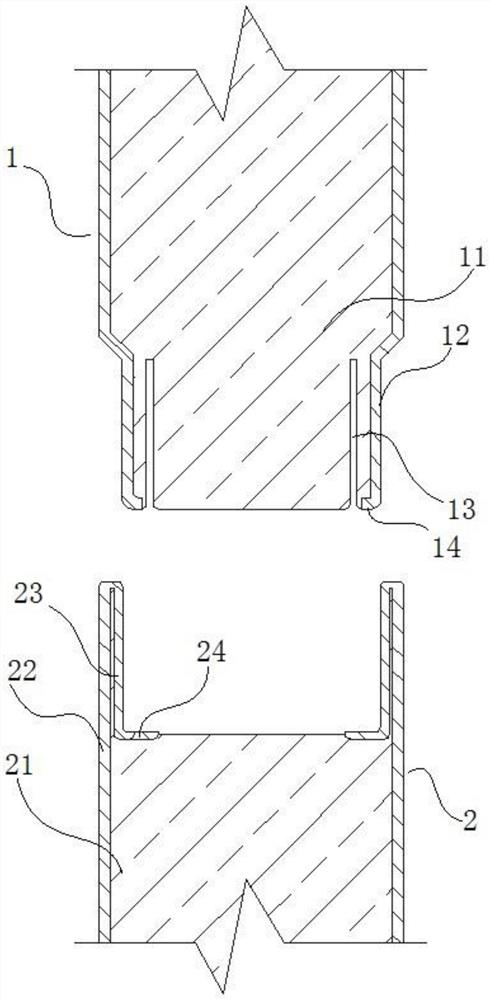
Installation and construction method of double-glass magnesium rock wool color steel plate
ActiveCN113982285AFirm and stable docking structureSolve technical problems with potential safety hazardsBuilding material handlingButt jointMaterials science
The invention discloses an installation and construction method of a double-glass magnesium rock wool color steel plate. The installation and construction method comprises the following steps in sequence: matching; oppositely assembling; and carrying out flush treatment. According to the opposite assembly step, when the matching step is carried out till the distance between a pressure groove and a pressure bearing end is 1-5 mm, the two double-glass-magnesium rock wool color steel plates are made to get close rapidly, the pressure bearing end impacts a hook end, the hook end extrudes a glass-magnesium rock wool layer A on the middle portion of the end of the glass-magnesium rock wool layer A, the open face of the pressure groove is closed, the pressure groove forms a closed air pressure cavity, and the air pressure cavity extrudes the color steel plate layer A towards the pressure on the two sides, so that a firm and stable butt joint structure is formed after the female joints are in butt joint; the technical problem that two double-glass magnesium rock wool color steel plates are reinforced and fixed by using a reinforcing plate through screws after being subjected to glue joint testing, and potential safety hazards exist is solved.
Owner:NO 1 CONSTR ENG CO LTD OF GUIZHOU CONSTR & ENG GRP
A data encryption and decryption method, data uploading end, data receiving end and system
ActiveCN113343286BSolve technical problems with potential safety hazardsThreat to securityDigital data protectionCiphertextPassword
The present invention provides a data encryption and decryption method, a data uploading terminal, a data receiving terminal and a system. The method includes an encryption method and a decryption method. The encryption method includes: obtaining data plaintext and an AES key, and combining the AES key to encrypt the data plaintext, Obtain the data ciphertext; encode the data ciphertext to obtain a string ciphertext and write it into the blockchain database. The decryption method includes: obtaining data ciphertext, a decryption password and a preset password, and authenticating the decryption password and the preset password; when the authentication is passed, outputting the data plaintext; when the authentication is not passed, outputting the data ciphertext. The above data encryption and decryption method, data uploading end, data receiving end and system, through password authentication, does not involve key distribution, and different Bloom filters can be set for different groups of data for verification, so as to realize the differential verification of data , to ensure data security, and solve the technical problem that encryption algorithms in the prior art need to manage keys, resulting in potential safety hazards in data security.
Owner:JIANGXI AGRICULTURAL UNIVERSITY
User authentication method and device
ActiveCN102946384BRealize self-checkingSolve technical problems with potential safety hazardsTransmissionUser verificationUser authentication
The invention discloses a user authentication device, which comprises a receiving module, an encryption module and an authentication module, wherein the receiving module is used for receiving a logging request including authentication information from a user; the authentication information comprises a first information part and a second information part; the first information part comprises basic information of the user; the second information part comprises a first verification character string generated after the basic information of the user is encrypted by a preset encrypting rule; the encryption module is used for encrypting the basic information of the user is encrypted by the preset encrypting rule to obtain a second verification character string; and the authentication module is used for determining whether the second verification character string is matched with the first verification character string or not, and the authentication is successfully if the second verification character string is matched with the first verification character string. By adopting the user authentication device provided by the invention, a technical problem of potential safety hazard of a system, which is caused by the fact that a malicious user forges cookie to log into the system, can be solved. The invention further discloses a corresponding user authentication method and system.
Owner:BEIJING QIHOO TECH CO LTD
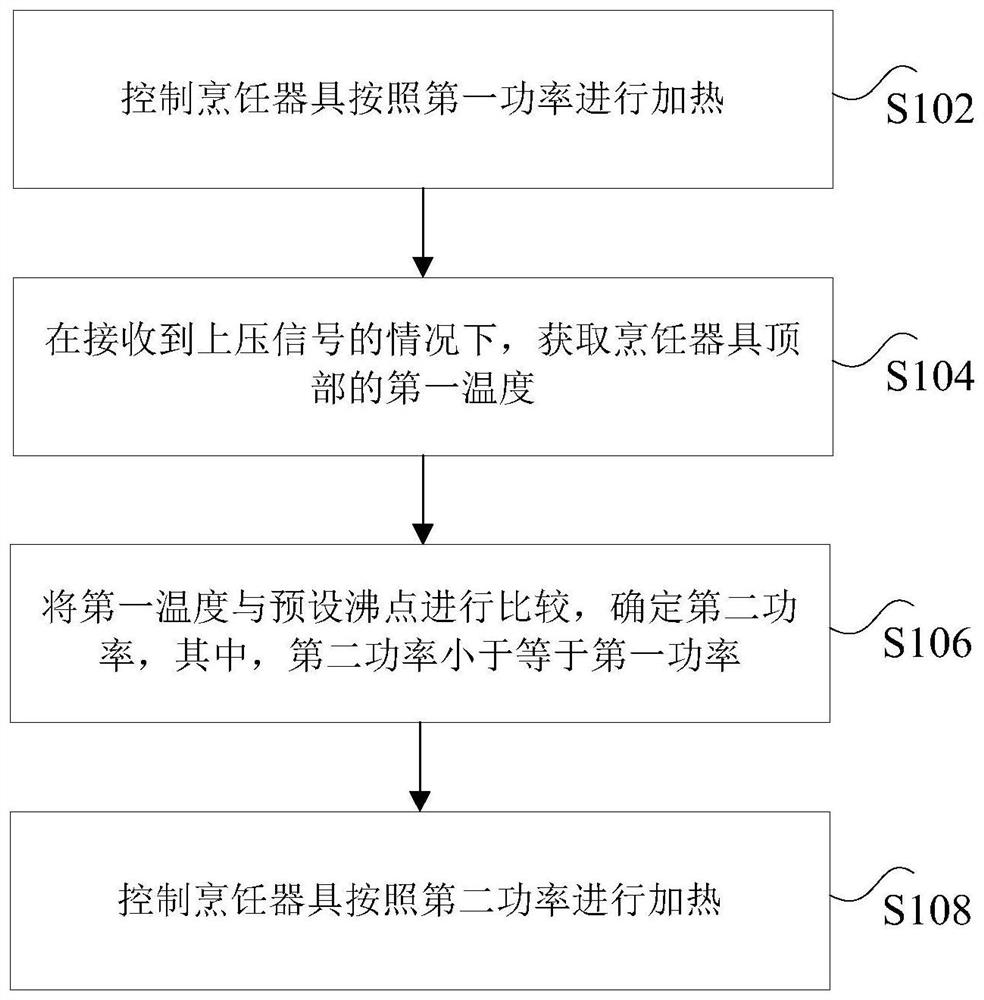
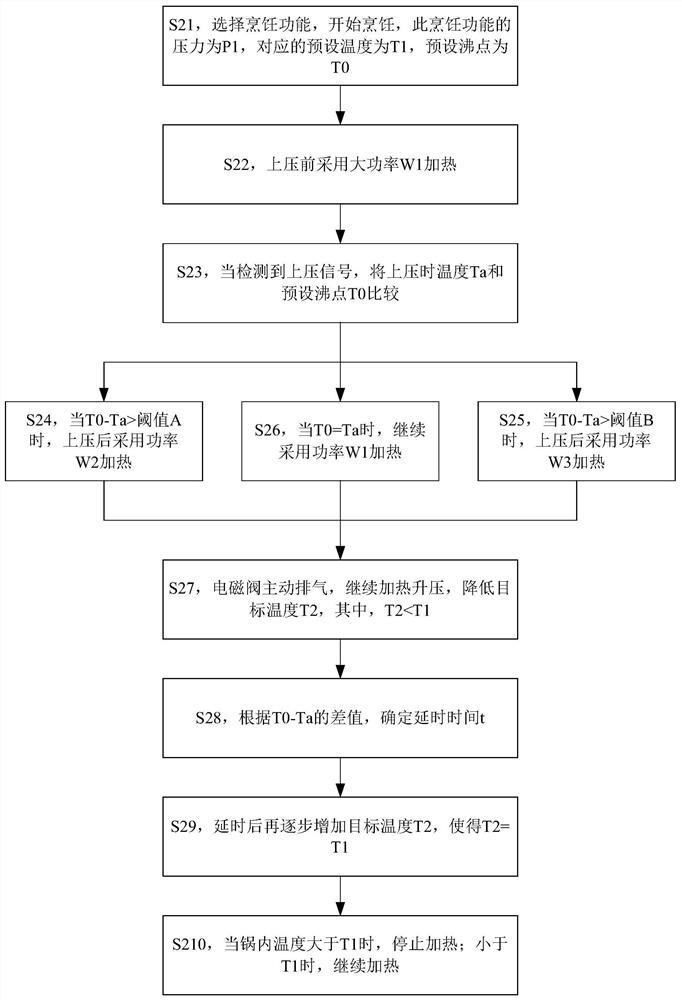
Cooking control method and device and cooking utensil
PendingCN113317687AImprove securitySolve technical problems with potential safety hazardsTime-controlled ignitorsProcess engineeringIndustrial engineering
The invention discloses a cooking control method and device and a cooking utensil. The method comprises the steps of controlling the cooking utensil to heat according to first power; under the condition that a pressurizing signal is received, obtaining the first temperature of the top of the cooking utensil; comparing the first temperature with a preset boiling point, and determining second power, wherein the second power is less than or equal to the first power; and controlling the cooking utensil to heat according to the second power. The technical problems that when the cooking utensil is pressed in advance in the prior art, due to temperature detection lag, the actual pressure is too high, and potential safety hazards exist in the cooking utensil are solved.
Owner:ZHEJIANG SHAOXING SUPOR DOMESTIC ELECTRICAL APPLIANCE CO LTD
A safe takeover method that can avoid traffic
ActiveCN104902481BEnsure safetySolve technical problems with potential safety hazardsData switching by path configurationSecurity arrangementInternet privacyData access
The invention discloses a flow-free safe takeover method, comprising: when a mobile terminal detects that there is a network security risk, sending a data access request to a proxy server through the network of the mobile communication operator; receiving a data access request through the network of the mobile communication operator. The requested data obtained by the proxy server from the resource server based on the data access request; wherein, the data transmission in the process of the above-mentioned mobile terminal accessing the network through the proxy server is marked with a traffic-free mark, and the process of the mobile terminal accessing the network through the proxy server All or part of the data traffic generated in the mobile communication operator will be included in the designated service provider based on the traffic-free identification.
Owner:北京鸿享技术服务有限公司
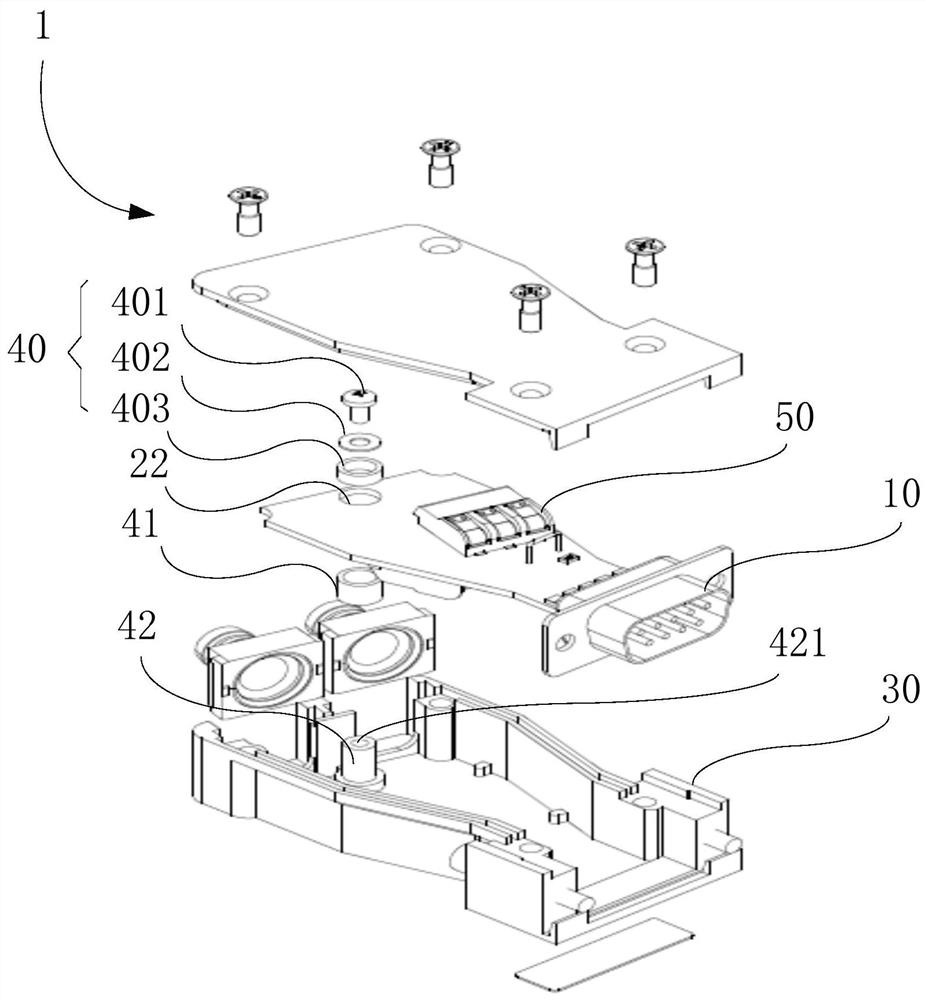
A db9 type bus connector
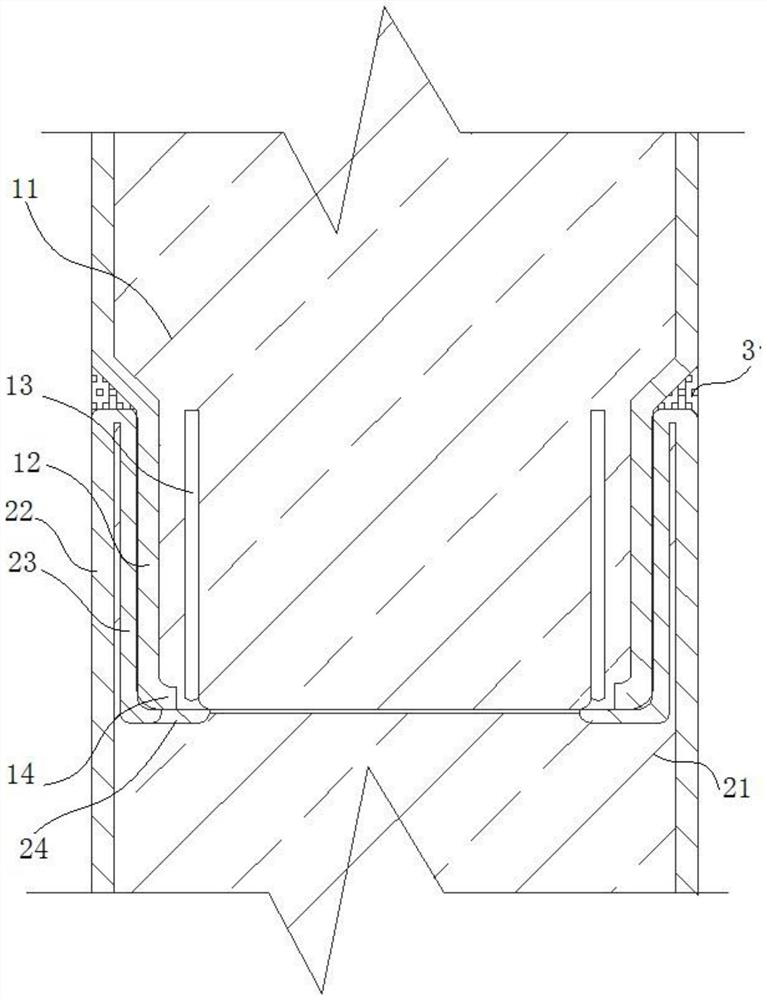
ActiveCN111384620BSolve technical problems with potential safety hazards in operationSolve technical problems with potential safety hazardsSecuring/insulating coupling contact membersStructural engineeringBoard structure
The present invention provides a DB9 type bus joint, comprising: a shell, a circuit board and a plug, wherein, the shell has an accommodating cavity, the circuit board is installed laterally in the accommodating cavity, and the circuit board and the The distance between the inner bottom wall of the accommodating cavity is equal to the distance between the circuit board and the inner top wall of the accommodating cavity; the plug is arranged on the shell, and one end of the plug is connected to the The circuit board is electrically connected. The DB9 bus joint provided by the present invention avoids contact between the wiring terminal and the inner wall of the joint shell by using a new type of terminal and redesigning the structure of the circuit board, and improves the safety performance of the DB9 bus joint.
Owner:CRRC DALIAN R & D CO LTD
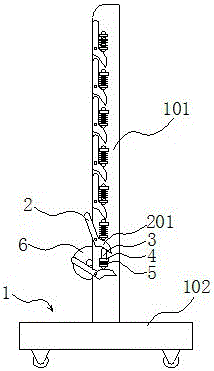
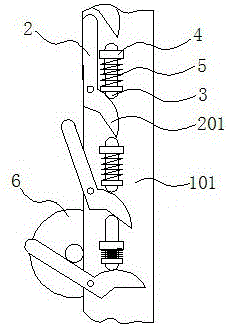
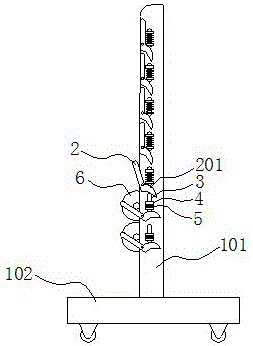
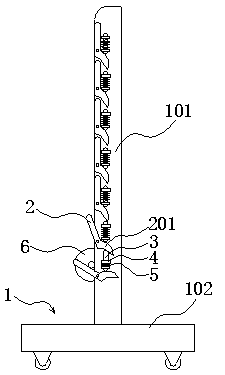
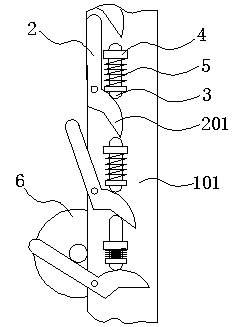
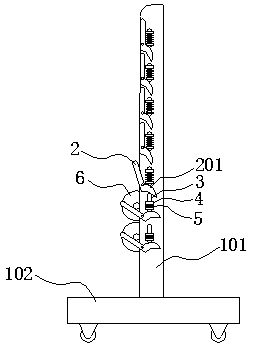
Coiled textile fabric storing rack
InactiveCN106516519ASolve technical problems with potential safety hazardsStorage devicesEngineeringMaximum size
The invention relates to a coiled textile fabric storing rack, and belongs to the field of textile machinery. The coiled textile fabric storing rack comprises two support plates which are arranged in parallel, wherein a rotating supporting arm is arranged on the outer side surface of each support plate along the length direction of the support plate; when rotating out of the corresponding support plate, one end of each supporting arm can form a V-shaped support port with the corresponding support plate, and the other end of the supporting arm is provided with a linkage bump; a spring telescoping assembly which is fixed to each support plate is arranged between every two adjacent supporting arms; when in an initial state, the supporting arm at the bottom of each support plate rotates out of the support plate by an angle, and other supporting arms do not rotate out of the support plate; each spring telescoping assembly is propped to the linkage bump of the supporting arm which is close to the lower part of the spring telescoping assembly, and each spring telescoping assembly is not propped to the supporting arm which is close to the upper part of the spring telescoping assembly; when the lower one of the adjacent supporting arms rotates out of the corresponding support plate and the V-shaped supporting port reaches the maximum size, the upper one rotates out relative to the corresponding support plate to form a pre-supporting port, and the supporting arm above the upper supporting arm does not rotate out of the corresponding support plate at the same tie. According to the coiled textile fabric storing rack with the abovementioned structure, the use safety can be improved.
Owner:吴江市惠风织造有限公司
A method of data-free payment or shopping
ActiveCN104992323BSolve technical problems of potential safety hazardsEnsure safetyPayment architecturePaymentProxy server
The invention discloses a traffic-free payment or shopping method. When a user performs payment or shopping operation, a payment or shopping request for network payment or shopping is sent to a proxy server through a network of a mobile communication operator; requested payment or shopping data which is obtained by the proxy server from a payment or shopping server based on the payment or shopping request is received through the network of the mobile communication operator; and data transmission in the network payment or shopping process is marked with a traffic-free identification, and all or partial data traffic generated in the network payment or shopping process is counted in an assigned service provider by the mobile communication operator based on the traffic-free identification. Therefore, the traffic-free network payment or shopping is achieved through the network of the mobile communication operator, and the beneficial effect that the expense of data traffic consumed in the network payment or shopping process cannot be undertaken is achieved under the precondition of ensuring payment or shopping safety.
Owner:北京鸿享技术服务有限公司
Terminal safety management and control method for rail transit cloud
ActiveCN110661747ASolve the problem of illegal accessSolve technical problems with potential safety hazardsTransmissionData streamInformation transmission
The invention discloses a terminal safety management and control method for rail transit cloud. The method comprises the steps: firstly deploying a safety gateway at the rail transit cloud, enabling aterminal to send a request message to the safety gateway, and enabling the safety gateway to transmit the request message to the rail transit cloud; deploying a terminal safety management and controlservice in the rail transit cloud, and performing safety coding verification on a request message forwarded to the rail transit cloud by the safety gateway through the terminal safety management andcontrol service; the method comprises the following steps: respectively carrying out information area coding on resource objects of rail transit cloud, carrying out information area coding verification through terminal safety management and control service, and shunting data according to the information area coding; the data is forwarded to the terminal in the form of data flow through the safetygateway, and the terminal does not cache the data flow. According to the invention, the information safety of the rail transit cloud is realized, and the technical problem that potential safety hazards exist in terminal access and information transmission in the rail transit cloud environment is solved.
Owner:NR ENG CO LTD +1
Cabinet air conditioner and air conditioner with same
PendingCN114576704ASolve technical problems with potential safety hazardsDucting arrangementsLighting and heating apparatusElectric machineEngineering
The invention provides a cabinet air conditioner and an air conditioner with the cabinet air conditioner, relates to the technical field of air conditioners, and is designed for solving the problem that potential safety hazards are easily caused by unreliable power failure of a motor when an air duct is disassembled. The cabinet air conditioner comprises an evaporator assembly, an air duct assembly and a connecting terminal, the air duct assembly is detachably and fixedly connected with the evaporator assembly, and the connecting terminal is configured to enable a motor of the air duct assembly to be electrically connected with a main control board of the cabinet air conditioner; the connecting terminal comprises a male end and a female end, one of the male end and the female end is installed on the evaporator assembly, and the other one is installed on the air duct assembly. When the air duct assembly and the evaporator assembly are relatively separated, the male end and the female end are disconnected; and when the air duct assembly and the evaporator assembly are mutually combined, the male end is matched with the female end. The air conditioner comprises the cabinet air conditioner. According to the cabinet air conditioner and the air conditioner provided by the invention, when the air duct is disassembled, the motor is reliably powered off.
Owner:NINGBO AUX ELECTRIC +1
Password storage method, device, system and equipment
ActiveCN108737080BReduce time spent onlineStrengthen security managementKey distribution for secure communicationInternet privacyCiphertext
The application discloses a password storage method, device, system and equipment. Wherein, the method includes: the password manager obtains the registration information and generates ciphertext according to the registration information; the password manager synthesizes the password information based on the registration information and the ciphertext; the password manager sends the password information to the storage device, wherein the storage device receives After receiving the password information, disconnect from the password manager and store the password information offline. The application solves the technical problem that the existing password storage scheme using the password manager has potential safety hazards.
Owner:ALIBABA GRP HLDG LTD
Data processing method and system
ActiveCN107507004ASolve the problem of money lossAchieve securityProtocol authorisationData processing systemClient-side
The present application discloses a data processing method and system. The method is applied to an electronic client, wherein the electronic client realizes the transfer of electronic data by cooperating with a data processing system. The method includes the following steps that: a first request is sent to the data processing system, wherein the first request contains the account information of the electronic client; a standard character string that is generated by the data processing system based on the first request is received, wherein the standard character string is uniquely corresponding to the first request; and a response request returned by the data processing system based on a second request generated by an electronic data receiving end is received, and information for indicating whether an electronic data value is to be transferred is fed back to the data processing system based on the response request.
Owner:ADVANCED NEW TECH CO LTD
Energy settlement method, device and system
ActiveCN107909358BAchieve securitySolve technical problems with potential safety hazardsTransmissionProtocol authorisationTransaction dataEngineering
The invention discloses an energy settlement method, device and system. Among them, the method includes: obtaining the electric energy transaction data of any energy site in the block chain network, wherein the block chain network is composed of at least one energy site; sending the electric energy transaction data to the block chain network for verification, and receiving The verification result returned by the blockchain network; if the verification result is verified, the power transaction data is recorded on the blockchain of each energy station in the blockchain network, where the block of each energy station The blockchain data recorded on the chain is used to settle the electricity transaction data of any energy station in the blockchain network. The invention solves the technical problem that in the prior art, a centralized database is used to settle the electric energy transaction data of multiple energy sites, and the transaction data has potential safety hazards because the centralized database is easily tampered with.
Owner:北京融链科技有限公司
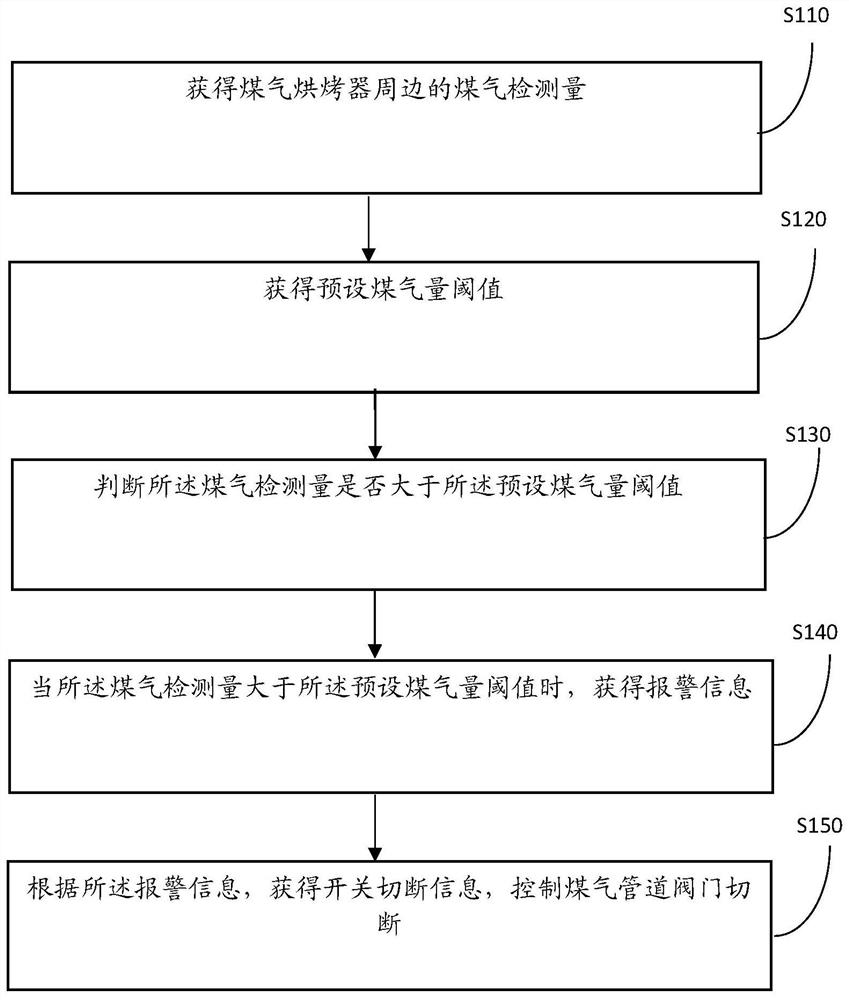
A gas leak detection system, method and device for a gas roaster
ActiveCN111009101BAchieve automatic shutdownSolve technical problems with potential safety hazardsEqualizing valvesSafety valvesInformation controlControl signal
The invention provides a gas leak detection system, method and device for a gas roaster. The system includes: a gas detection device, which is used to detect the gas volume around the gas roaster, and output gas volume information according to the gas volume; The control device is connected with the gas detection device, receives the gas quantity information output by the gas detection device, and generates control information output according to the gas quantity information; the execution device, the execution device is connected with the control device, receives the control signal sent by the control device and follows the Control signal for gas valve control. It solves the technical problem that there is a lack of effective means for on-site detection and control of the gas oven in the prior art and there are hidden dangers to personnel safety. It achieves the automatic closing of the gas valve of the roaster, prevents safety accidents, has the functions of gas leakage detection, alarm and safety action, high system reliability, and plays a technical effect of safety protection function.
Owner:JIANGSU YONGGANG GROUP CO LTD
A terminal security management and control method for rail transit cloud
ActiveCN110661747BSolve the problem of illegal accessSolve technical problems with potential safety hazardsSecuring communicationData streamInformation transmission
The invention discloses a terminal security management and control method of a rail transit cloud. Firstly, a security gateway is deployed in the rail transit cloud, and a terminal sends a request message to the security gateway, and the security gateway forwards it to the rail transit cloud; terminal security management and control is deployed in the rail transit cloud. Service, the security gateway forwards the request message to the rail transit cloud to perform security code verification through the terminal security management and control service; the resource objects of the rail transit cloud are respectively encoded in the information area, and the information area code verification is performed through the terminal security management and control service, according to The information area code divides the data; the data is forwarded to the terminal in the form of a data stream through the security gateway, and the terminal does not cache the data stream. The invention realizes the information security of the rail transit cloud, and solves the technical problem of potential safety hazards in terminal access and information transmission under the rail transit cloud environment.
Owner:NR ENG CO LTD +1
Roll Textile Fabric Storage Rack
InactiveCN106516519BSolve technical problems with potential safety hazardsStorage devicesMechanical engineeringMaximum size
The invention relates to a coiled textile fabric storing rack, and belongs to the field of textile machinery. The coiled textile fabric storing rack comprises two support plates which are arranged in parallel, wherein a rotating supporting arm is arranged on the outer side surface of each support plate along the length direction of the support plate; when rotating out of the corresponding support plate, one end of each supporting arm can form a V-shaped support port with the corresponding support plate, and the other end of the supporting arm is provided with a linkage bump; a spring telescoping assembly which is fixed to each support plate is arranged between every two adjacent supporting arms; when in an initial state, the supporting arm at the bottom of each support plate rotates out of the support plate by an angle, and other supporting arms do not rotate out of the support plate; each spring telescoping assembly is propped to the linkage bump of the supporting arm which is close to the lower part of the spring telescoping assembly, and each spring telescoping assembly is not propped to the supporting arm which is close to the upper part of the spring telescoping assembly; when the lower one of the adjacent supporting arms rotates out of the corresponding support plate and the V-shaped supporting port reaches the maximum size, the upper one rotates out relative to the corresponding support plate to form a pre-supporting port, and the supporting arm above the upper supporting arm does not rotate out of the corresponding support plate at the same tie. According to the coiled textile fabric storing rack with the abovementioned structure, the use safety can be improved.
Owner:吴江市惠风织造有限公司
Payment or shopping method
ActiveCN104933615ASolve technical problems of potential safety hazardsEnsure safetyPayment architectureBuying/selling/leasing transactionsPaymentThe Internet
The invention discloses a payment or shopping method, which comprises the following steps: a proxy server receives a payment or shopping request which is sent from a mobile terminal and is used for Internet payment or shopping; and the proxy server obtains corresponding requested payment or shopping data from a payment or shopping server according to the payment or shopping request from the mobile terminal and transmits the requested payment or shopping data to the mobile terminal through the network of a mobile communication operator, wherein data transmission in an Internet payment or shopping process is marked with a traffic-free identifier, all or parts of data traffic generated in the Internet payment or shopping process are numbered into an appointed service provider through the mobile communication operator on the basis of the traffic-free identifier. The payment or shopping method achieves the beneficial effects that traffic-free Internet payment or shopping is carried out through the network of the mobile communication operator so as to avoid from paying the cost of the data traffic consumed by the Internet payment or shopping on the premise that payment or shopping security is guaranteed.
Owner:360 TECH GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com