Data encryption and decryption method, data uploading end, data receiving end and system
A data decryption and data encryption technology, applied in the field of blockchain, can solve data security problems such as hidden dangers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
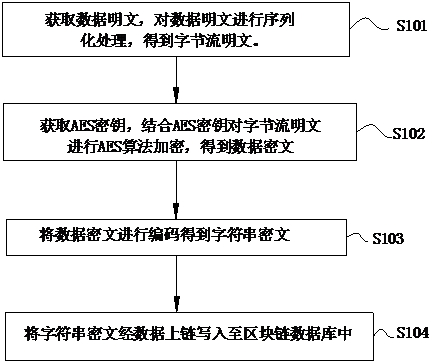
[0054] In the embodiment of the present invention, please refer to image 3 , image 3 It is a schematic diagram of the data encryption method in the embodiment of the present invention, such as image 3 As shown, the method includes step S101 to step S104:
[0055] S101. Obtain data plaintext, perform serialization processing on the data plaintext, and obtain byte stream plaintext.
[0056] First, serialize the data to be encrypted, where the data to be encrypted is the data plaintext, then use the AES key generated by the key generation algorithm to perform AES encryption on the serialized data, and finally encrypt the encrypted data with the k-v key Value pairs are stored in the state of the blockchain world.
[0057] S102. Obtain an AES key, and perform AES algorithm encryption on the byte stream plaintext in combination with the AES key to obtain data ciphertext.
[0058] In the data input phase, the data owner uploads the password of the data to be encrypted to the c...
Embodiment 2
[0090] An embodiment of the present application also provides a data upload terminal, including:
[0091] The data plaintext acquisition module is used to obtain the data plaintext, serialize the data plaintext, and obtain the byte stream plaintext;
[0092] The encryption module is used to obtain the AES key, and combines the AES key to perform AES algorithm encryption on the byte stream plaintext to obtain the data ciphertext;
[0093] An encoding module, configured to encode the data ciphertext to obtain the string ciphertext;
[0094] The writing module is used to write the string ciphertext into the blockchain database via data uplink.
[0095] To sum up, the data uploader in the above-mentioned embodiments of the present invention performs AES algorithm encryption on the byte stream plaintext obtained by serializing the data plaintext combined with the AES key to the data plaintext, and the obtained data ciphertext is uploaded to the In the blockchain database, when th...
Embodiment 3
[0097] Another aspect of the embodiment of the present application provides a data receiving end, including:
[0098] The data ciphertext acquisition module is used to obtain the data ciphertext sent by the blockchain database;
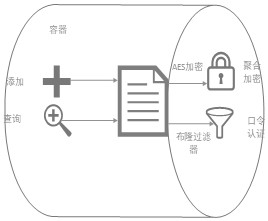
[0099] The authentication module is used to obtain the decryption password input by the user, and obtain the preset password from the Bloom filter of the blockchain database, and authenticate the decryption password and the preset password. The preset password is pre-stored before the data ciphertext is uploaded to the chain passphrase into the Bloom filter;
[0100] The first execution module, when the authentication is passed, decrypts the data ciphertext with the AES algorithm, deserializes the data ciphertext decrypted by the AES algorithm, obtains the data plaintext corresponding to the data ciphertext, and outputs the data plaintext;
[0101] The second execution module outputs data ciphertext when the authentication fails.
[0102] To sum up,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com