System and method for generating and managing secret key
A key generation and key technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
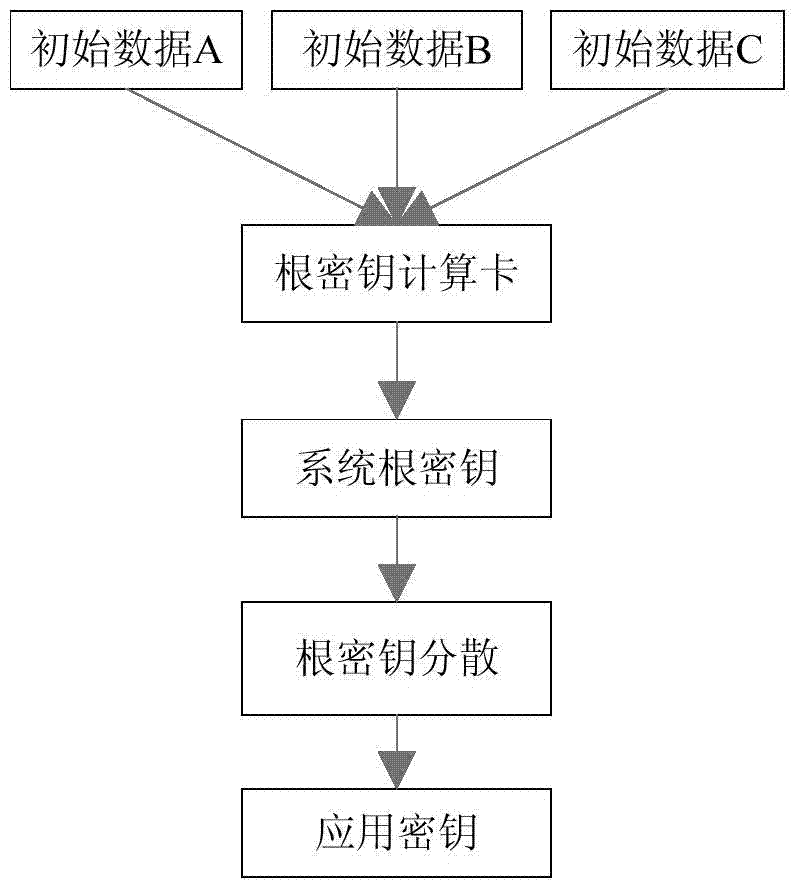
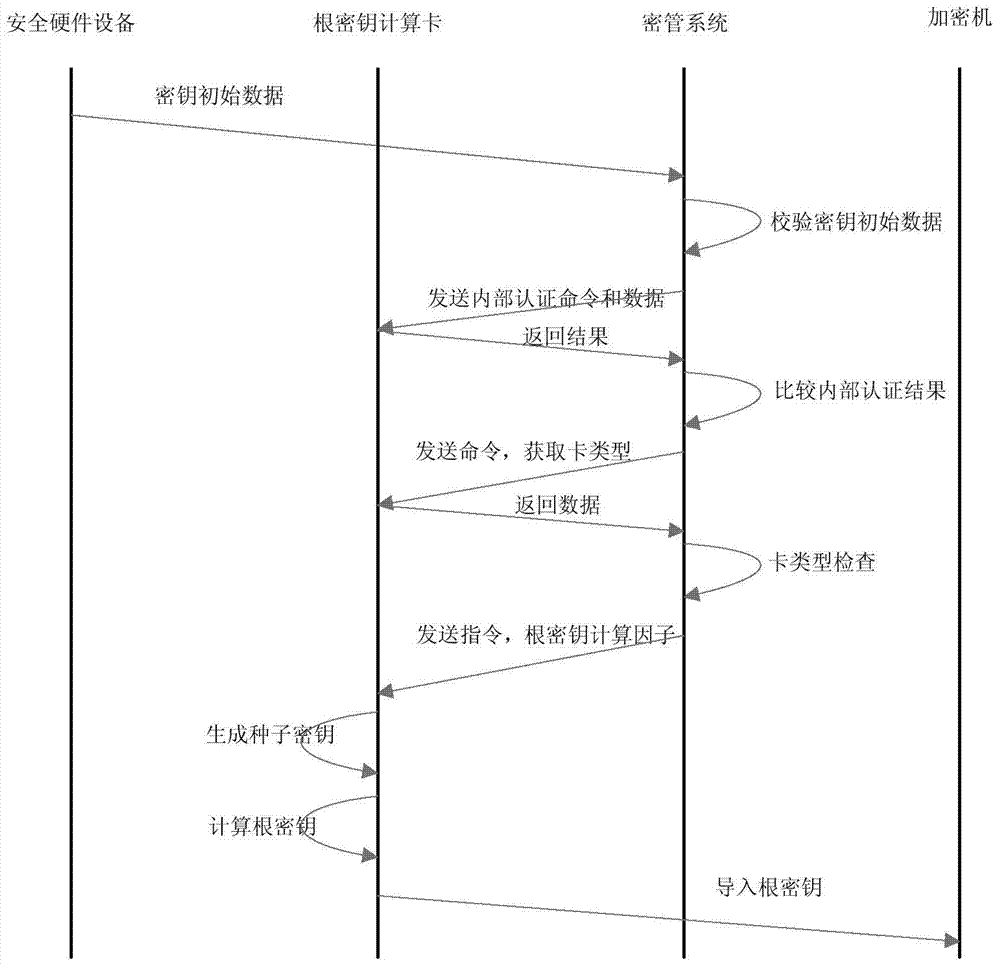
[0069] Embodiments of the present invention provide a method and device for a key management system. In this embodiment, a smart card is used as a secure hardware device, and the specific methods include:
[0070] When the system starts up, check whether the two card readers are connected correctly and whether the encryption machine is connected correctly, otherwise it will provide an error message and exit the system after providing the error message.
[0071] The configuration information of the encryption machine used in the system is stored in the database.
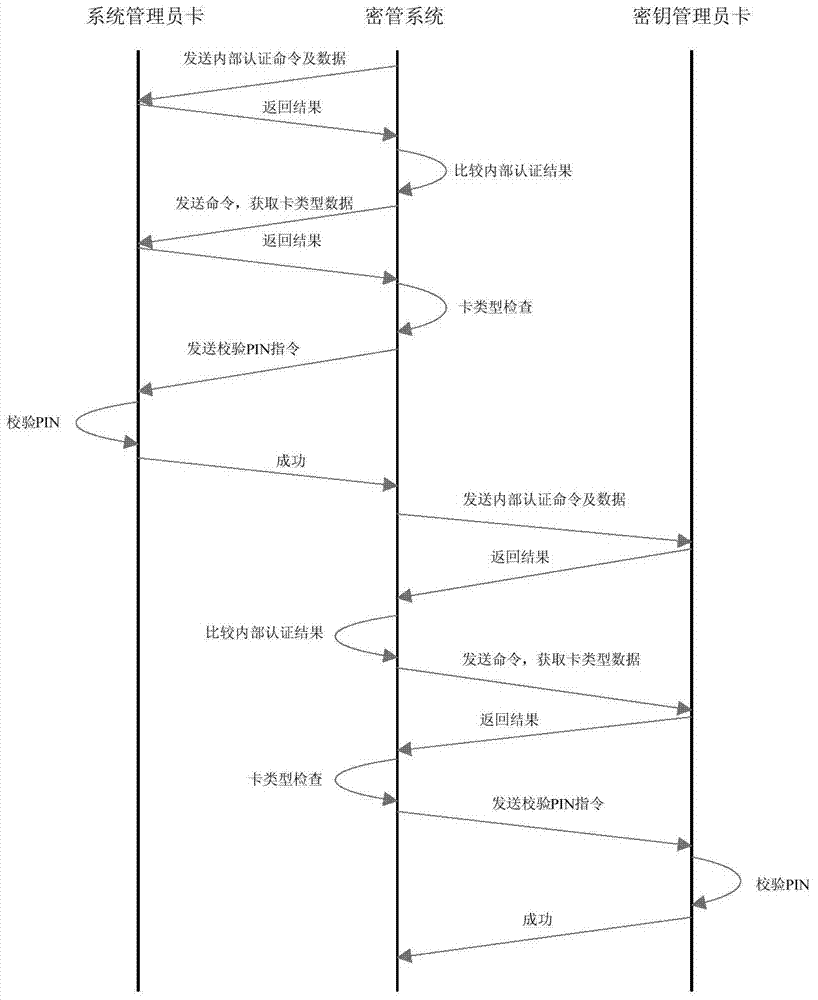
[0072] When the system starts, check whether the system administrator card is inserted in the card reader (including whether it is connected, whether it is the required card in the system, and whether the PIN has been locked), otherwise it will provide an error message and allow the operator to try again or not Exit system. During this self-test process, the following abnormal situations may occur:
[0073] (1) The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com