Anti-bypass attack algorithm and chip thereof
A side-channel attack and chip technology, applied in the field of information security, can solve the problem of ignoring the security of modulo reduction operations, and achieve the effect of increasing the difficulty of attack and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings, but the present embodiments are not intended to limit the present invention, and all similar structures, methods and similar changes of the present invention should be included in the protection scope of the present invention.
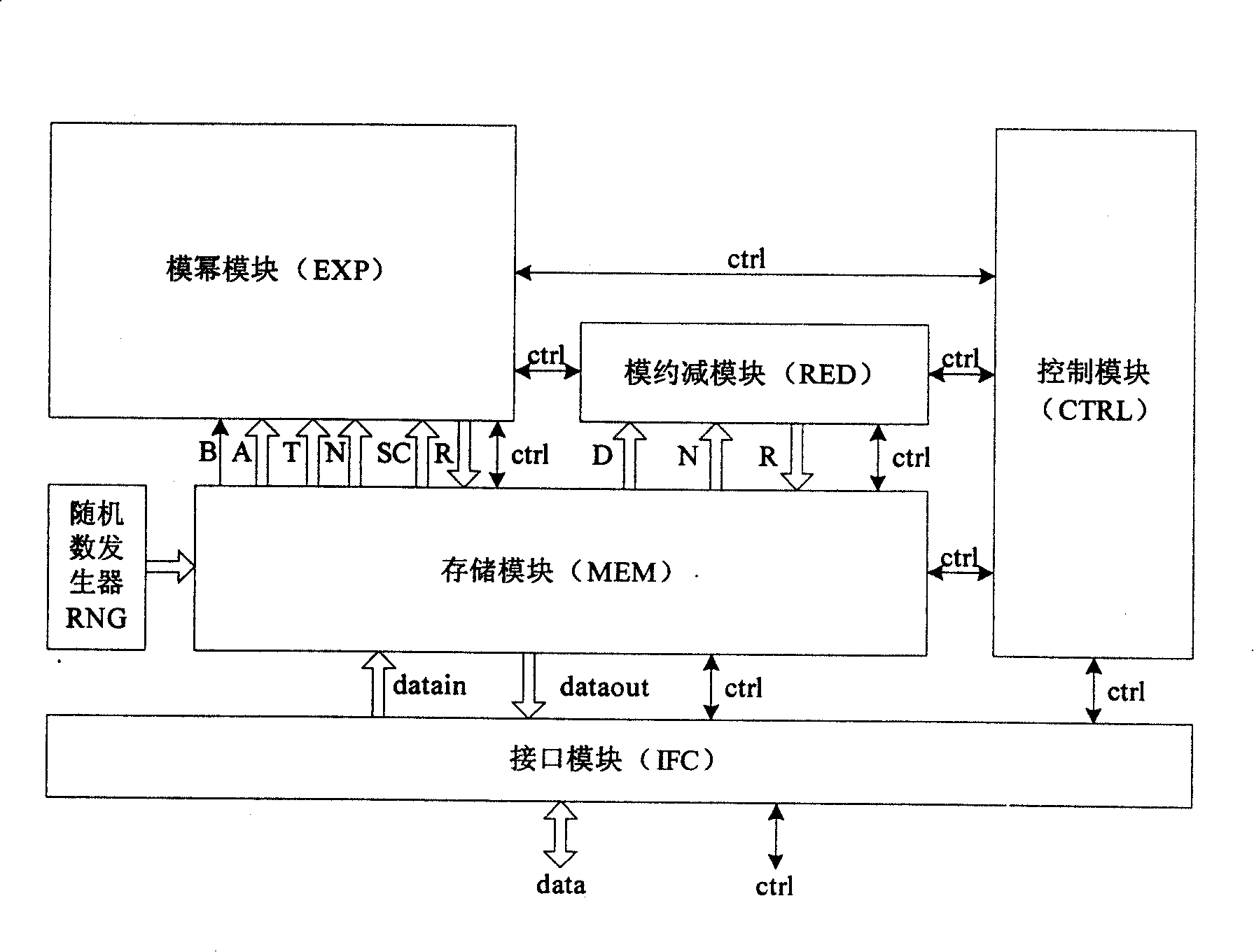
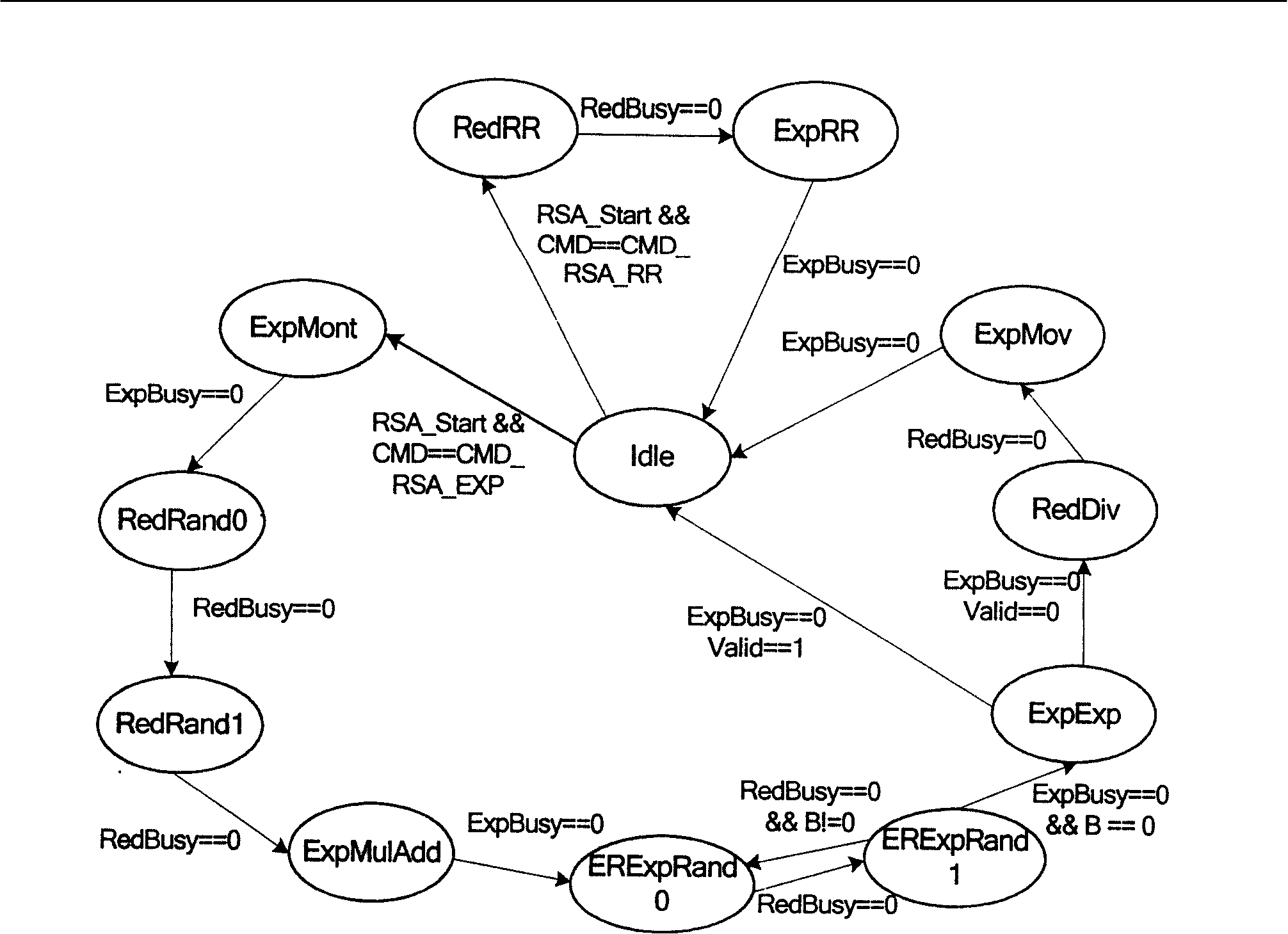
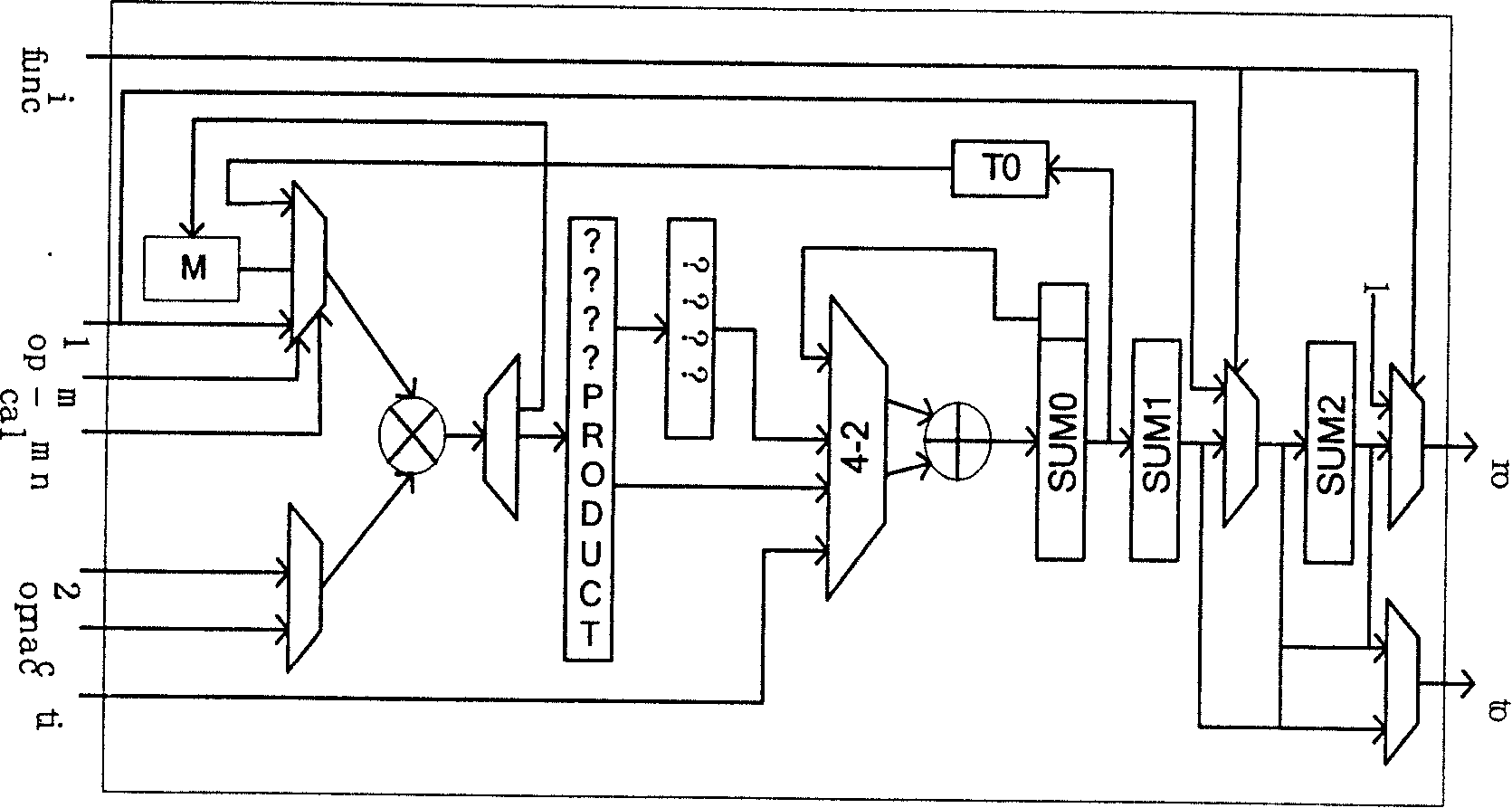
[0069] The invention proposes a more secure modular reduction algorithm RandRed by introducing random numbers. At the same time, combined with the MIST algorithm, a design method of RSA chip against side channel attack is given.
[0070] After the introduction of random numbers, the operand selection space fixed at one end of the subtraction operation is greatly increased, making the attacker need to determine the operand used for calculation in a large amount of data. To calculate E mod d, the algorithm is described as follows:
[0071] RandRed(E, d) {
[0072] Choose a random number rand;
[0073] d'=d×rand;
[007...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com