Method for realizing block cipher multiple S-boxes for resisting differential power attack
A differential power consumption attack and block cipher technology, which is applied in countermeasures against encryption mechanisms, encryption devices with shift registers/memory, digital transmission systems, etc., can solve the problem of reducing computing speed, increasing hardware consumption resources, and restricting security chips Development and other issues to achieve the effect of increasing difficulty and increasing attack difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
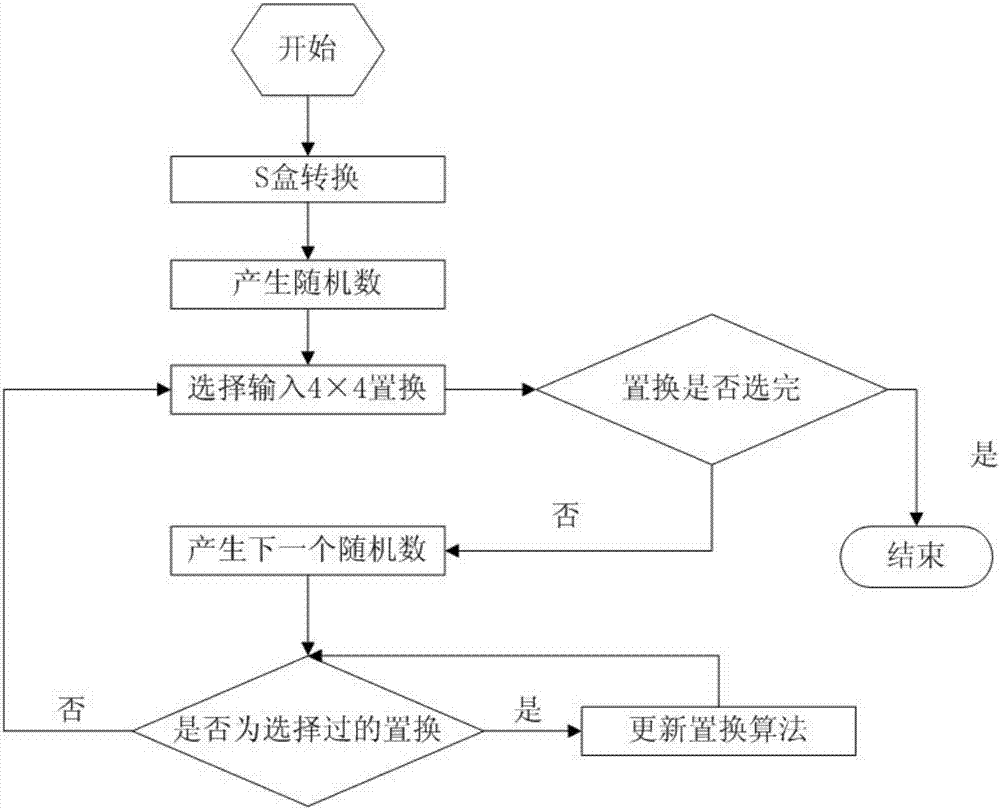
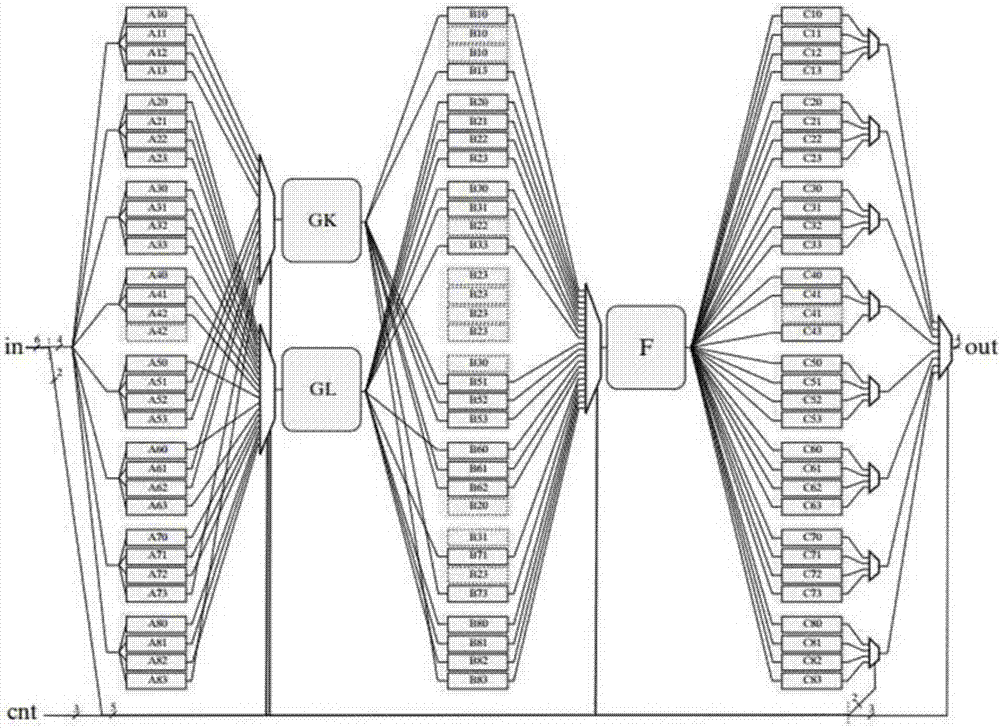
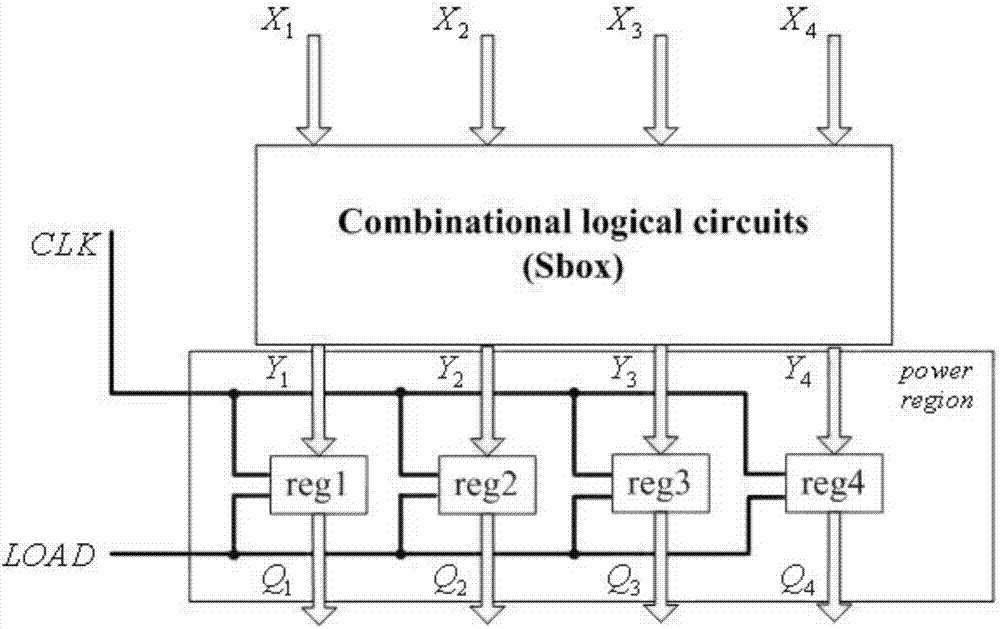
[0042] In order to improve the effective protection of the S box, the present invention provides a figure 1 The block cipher multi-S-box implementation method for resisting differential power consumption attacks shown above uses pipeline technology to add three-level registers in the middle of the multi-dimensional serial reusable S-box frame, so that the speed of cryptographic operations is lower than that of the original scheme. It will drop too much and improve efficiency.
[0043] Using the block cipher multi-S-box randomized input technology, the attacker of the differential power consumption attack cannot align the curve according to the relevant statistical difference method after obtaining the power consumption curve, thus resulting in the failure of the differential power consumption attack and improving the security of the block cipher implementation sex.
[0044] The specific plan includes the following steps:
[0045] Step 1: Select a block cipher algorithm, conv...
Embodiment 2
[0076] Taking the block cipher algorithm DES as an example, the present invention is further described in detail.
[0077] Although we know that the DES algorithm of the 56bit key has been proved to be insecure in many applications. But we know that Triple-DES is still widely used in the field of electronic payment, because it has a key of 112bits, so it is proved to be safe.
[0078] The DES algorithm is a symmetric cryptosystem in the cryptographic system, also known as the American Data Encryption Standard. It is a symmetric cryptosystem encryption algorithm developed by IBM Corporation in the United States in 1972. The plaintext is grouped by 64 bits, the key length is 64 bits, and the key is actually 56 bits to participate in the DES operation (the 8th, 16th, 24th, 32nd, 40th, 48th, 56th, and 64th bits are check bits, so that each key All keys have an odd number of 1) grouped plaintext groups and 56-bit keys that are replaced or exchanged bit by bit to form an encryption...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com