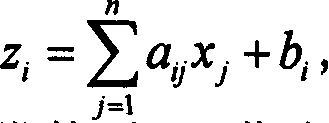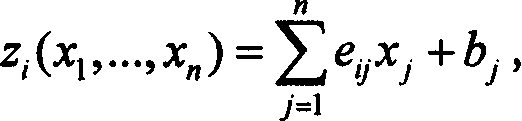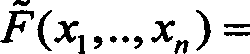Method for generating multiple variable commom key password system
A multivariable public key and cryptosystem technology, which is applied in the field of generating new multivariate public key cryptosystems and can solve problems such as insecurity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] 1. Internal Perturbation-Plus Method (IPP)
[0021] 1.1 Basic idea of IPP
[0022] Internal perturbation-plus is the name given to the first class of methods among the methods invented in the present application. The basic idea of IPP is now described, and subsequent subsections will show some specific examples of IPP applications, such as applied to the Matsumoto-Imai cryptosystem to generate the so-called internally perturbed Matsumoto-Imai-Plus cryptosystem (PMI+).
[0023] The reason why the word "disturbance" is used here is very similar to the physical meaning of disturbance, which means to intentionally "change" or add a small-scale "noise" to the system to see how the system changes, and thus derive new information about the system itself . The key point is that the perturbation must be done in a controlled manner so that the system itself is not fundamentally changed. Our method is indeed to "add" random "small" "noise" to the cryptographic system, so th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com