Method of authenticating identification based common key cryptosystem and encryption address in network
A technology of public key cryptography and identity, applied in the field of Internet technology mobile IPV6 communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
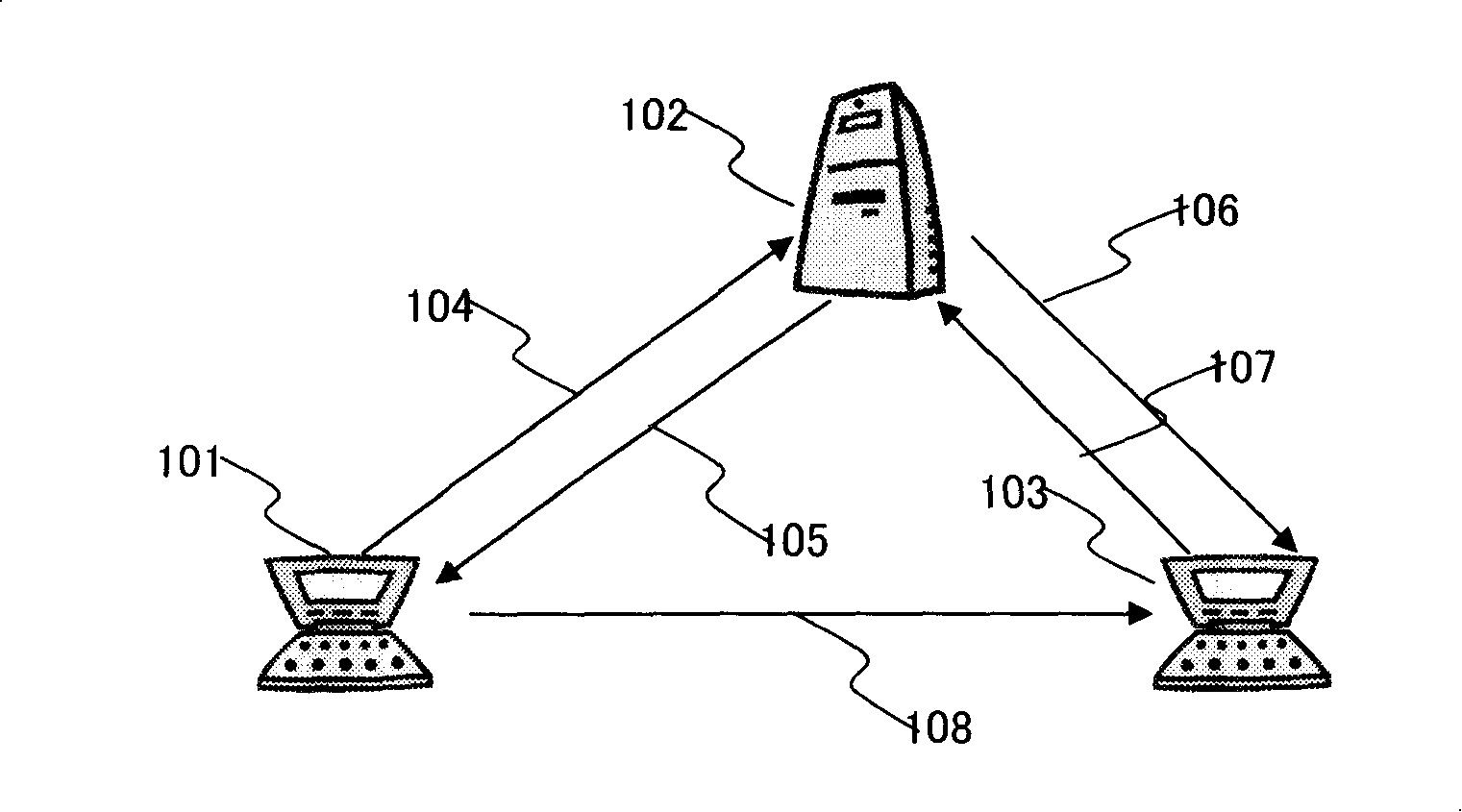
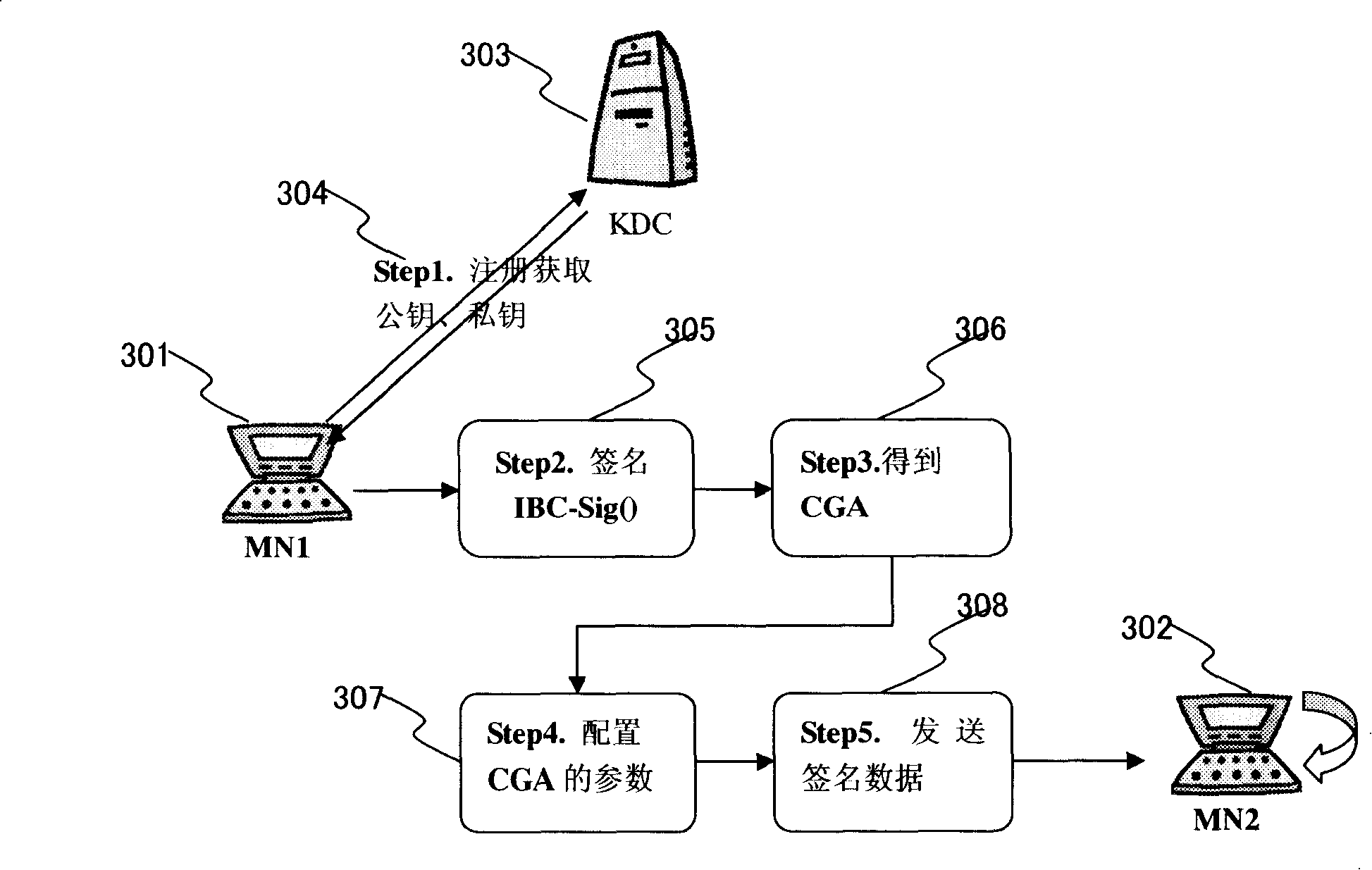
[0027] Figure 1 details the architecture of the identity-based public key cryptography system IBC, which includes the following parts:
[0028] Key Distribution Center (KDC), responsible for producing, issuing, backing up and managing the system parameters necessary for IBC system initialization and operation, as shown in Figure 1 at 102;
[0029] ●End entities, that is, users, applications or devices using system security functions, such as 101 and 103 in Figure 1;
[0030] ●The process of registration and key distribution between the terminal entity and the key distribution center, as shown in Figure 1 104, 105, 106, 107;
[0031] ●The message signature authentication process between terminal entities, as shown in 108 in Figure 1;
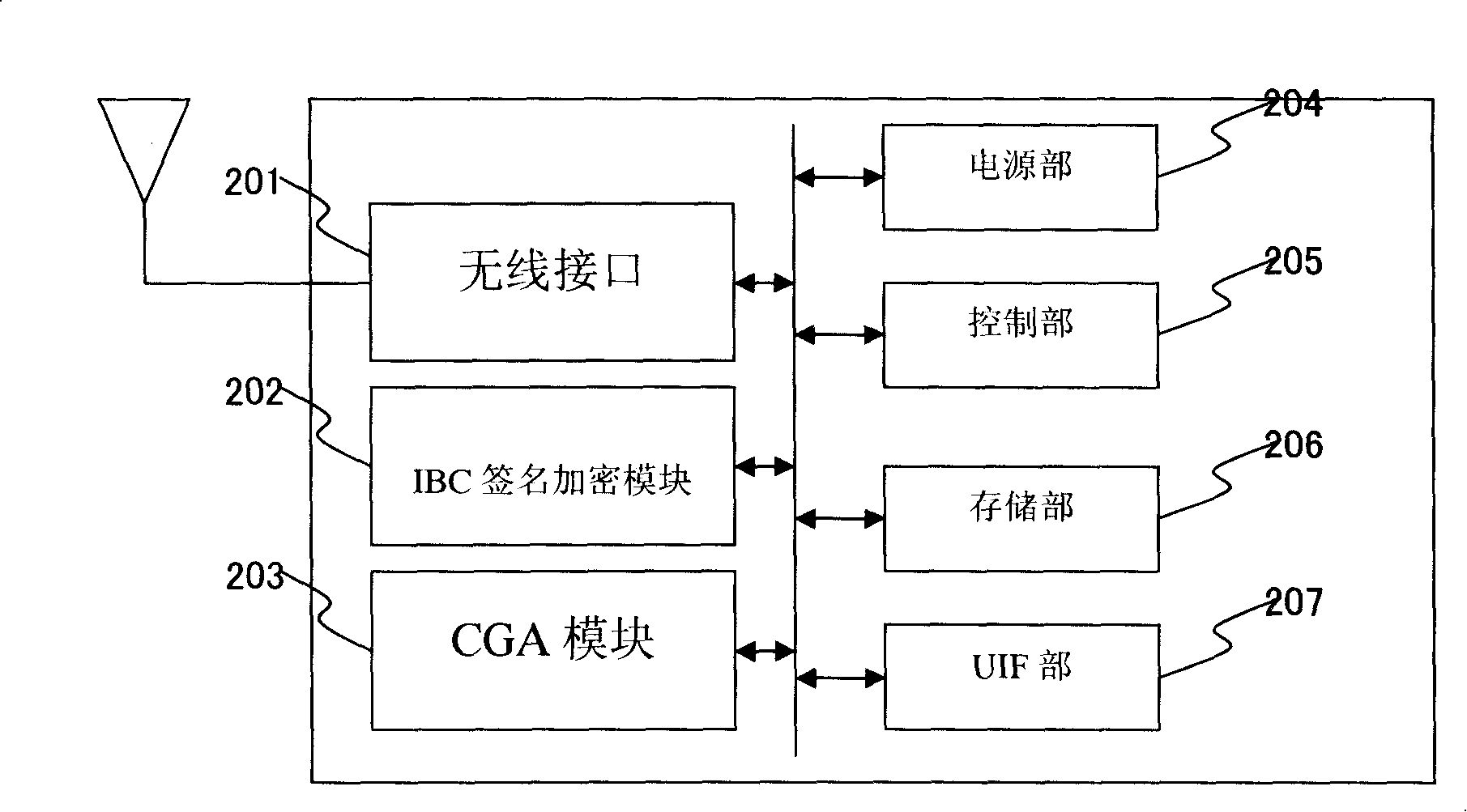
[0032] Fig. 2 is a schematic diagram of the module structure of the mobile terminal. In Fig. 2, 201 is a wireless network interface, 202 is a signature encryption module of the identity-based public key cryptosystem, 203 is a module that uses t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com