Achievement method of certificate-less public key cryptosystem without bilinear pairing operation
A public-key cryptosystem and bilinear pairing technology, which is applied in the field of information security, can solve problems such as solution breaches, forged signature attacks, and low computing efficiency, achieving the effects of strong security, high computing efficiency, and less resource occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
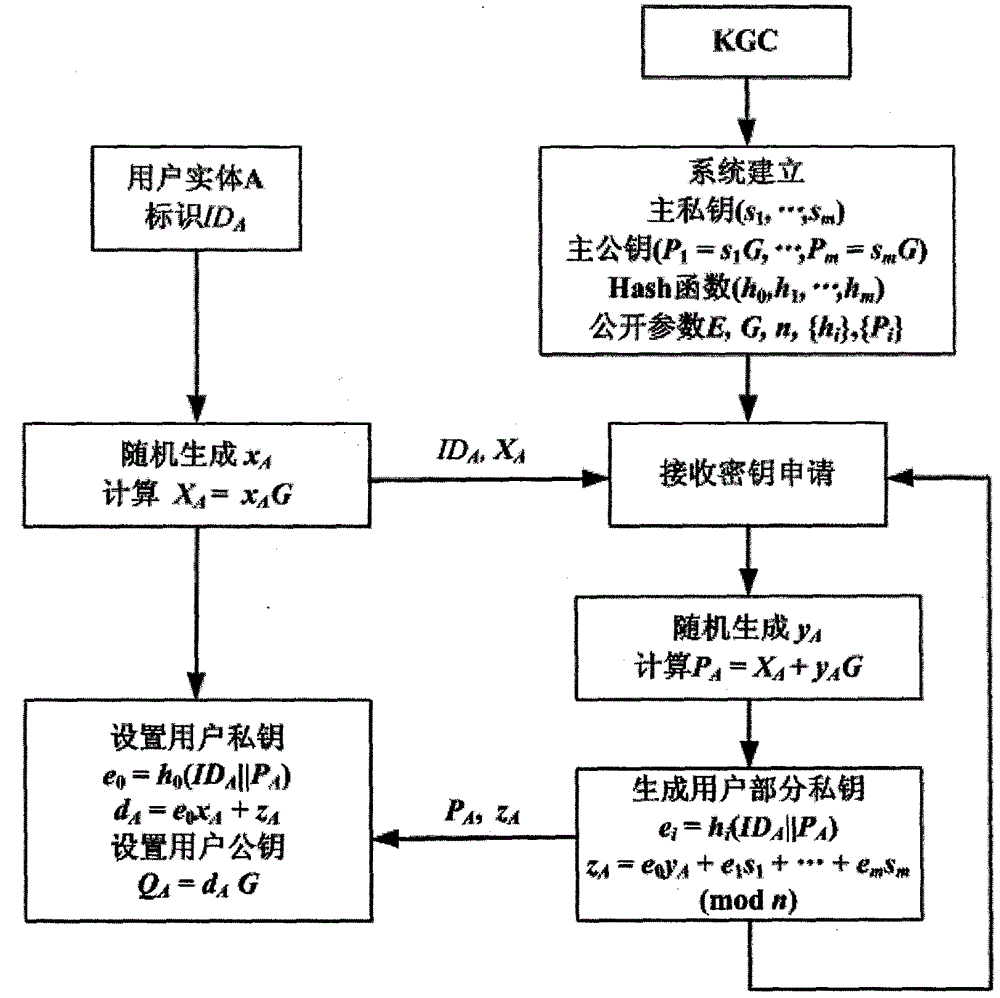
[0067] Phase 1: System Establishment
[0068]System establishment is completed by KGC.
[0069] KGC chooses the finite field F q The secure elliptic curve E on :y 2 =x 3 +ax+b, take an n-order point G on E as the base point, where n is a prime number. Then select a positive integer m≥1, and a set of {0, 1} * → [1, n-1] HASH function h 0 (), h 1 ( ), ..., h m (). General choice F q is a prime number field, and the number of bits of q and n is more than 192, for example, the elliptic curve parameters specified in the national SM2 standard can be selected. In the SM2 standard, both q and n have 256 bits.
[0070] KGC randomly selects m secret values As the system master private key, calculate the system master public key: P 1 =s 1 G,...,P m =s m g. KGC Confidentials 1 ,...,s m , public system parameters
[0071] Phase 2: User Key Generation
[0072] User key generation is jointly completed by KGC and users.
[0073] (1) The user entity identified as ID ran...
Embodiment 2
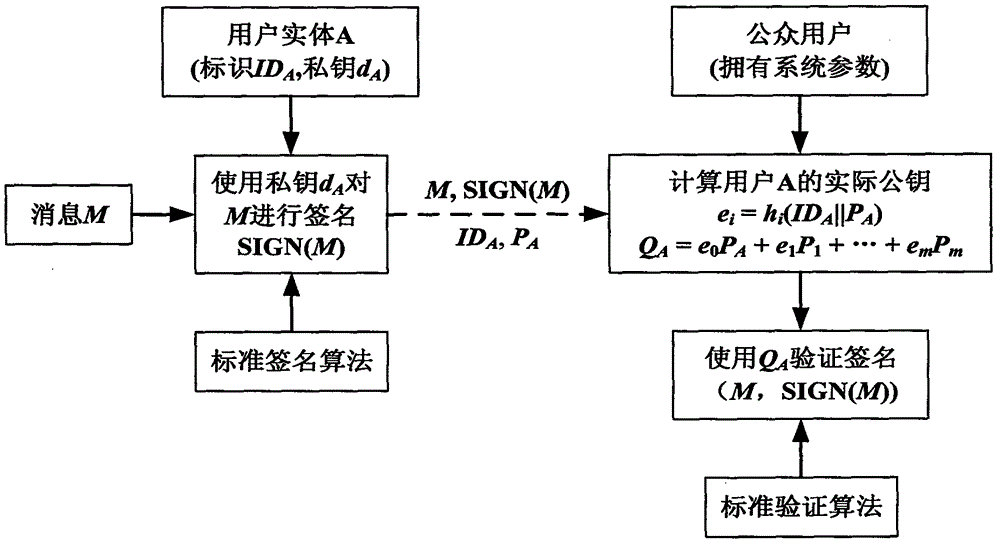
[0084] Select the elliptic curve as in Embodiment 1. Take m>1, h() is a {0, 1} * →[1,2 m -1] for the HASH function, the system public parameters are In the user key generation stage, the definition of x and y is as in embodiment one, let e=h(ID||P), and e is expanded by binary, recorded as e=(e 1 , e 2 ,...,e m ) 2 , where e i ∈ {0, 1}, i=1, . . . , m. The final generated user private key is d=x+y+e 1 the s 1 +…+e m the s m (mod n), the user's partial public key is P=xG+yG, and the user's actual public key is Q=P+e 1 P 1 +…+e m P m .
[0085] when e i = 0, the i-th item in the formula for calculating Q will not appear, so calculating the user's actual public key only needs to perform m / 2 times of point addition operations on average. When m2 (n), the time spent on calculating Q is much less than the time spent on one multipoint operation, so this method can obtain higher efficiency. In order to ensure safety, m≥128 is generally required in practical applicat...
Embodiment 3
[0087] Select the elliptic curve as in Embodiment 1. Take l, N is a positive integer, m≤2 N , h() is a {0, 1} * →[1,2 lN -1] for the HASH function, the system public parameters are In the user key generation stage, the definitions of x and y are as in Embodiment 1, let e=h(ID||P), expand e by binary bits, and each consecutive N bits form a word, and a total of l words are formed. Make e=(w 1 ,w 2 ,...,w l ) N , then let e i =w i (mod m)+1, then e i ∈[1,m], i=1,...,l. The final generated user private key is d=x+y+s e1 +…+s el (mod n), the user's partial public key is P=xG+yG, and the user's actual public key is Q=P+P e1 +…+P el .
[0088] In this embodiment, calculating the user's actual public key only requires one dot-add operation. To ensure safety, the number of combinations is required For example, when the number of bits of n is 256, N=8, l=32, m=128 can meet the requirements. In this case, lN=256, calculating the user’s actual public key only needs 32...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com