Public key cipher system private key escrowing system based on identification
A public key cryptosystem and cryptosystem technology, applied in transmission systems, electrical components, user identity/authority verification, etc., can solve problems such as USBKey cracking, and achieve the effect of ensuring security and increasing attack difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
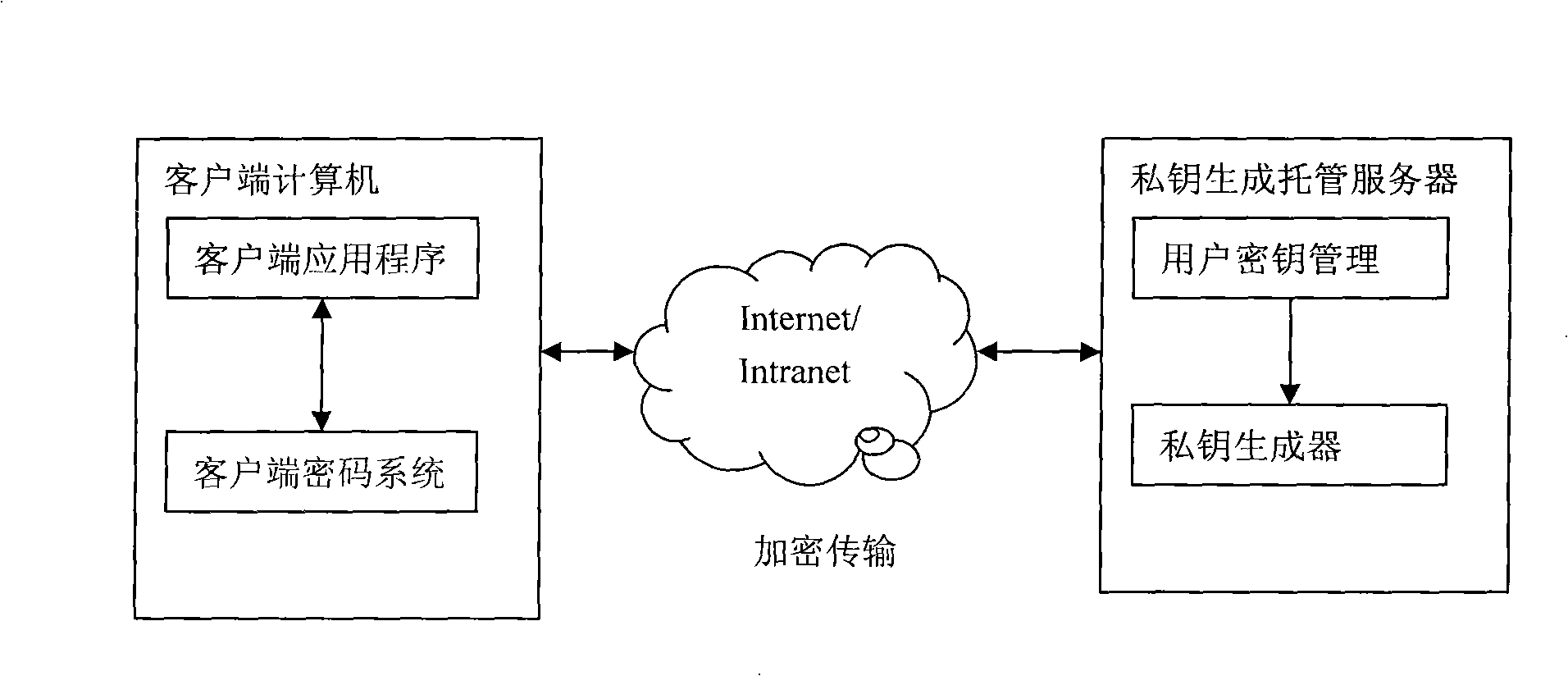
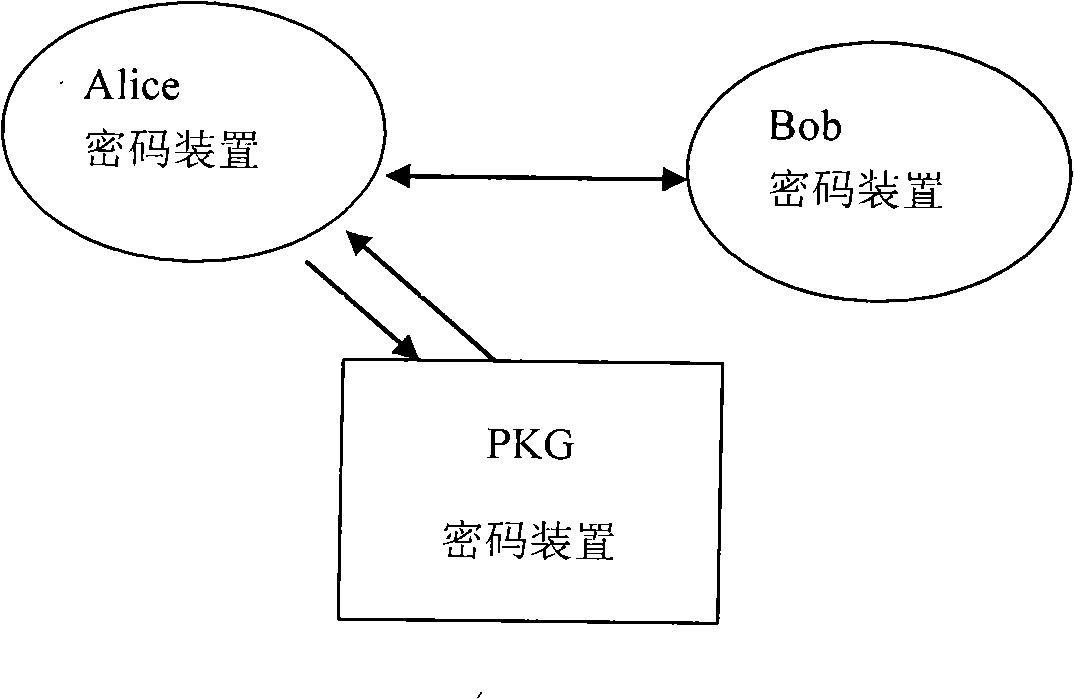
[0033] This system is deployed on the Windows operating system. To implement the system designed by the present invention, it is first necessary to establish a private key generator PKG. Since the user's authentication information is stored in the PKG, it should be stored in a safe environment and various security protections should be taken. measures to avoid attacks.
[0034] Each client needs to install a password device and issue a password for authentication to the user. The password can be given to the user by using a password generator or by printing.
[0035] One-time password authentication can also be changed to biometric authentication and other security authentication methods that support the star structure.
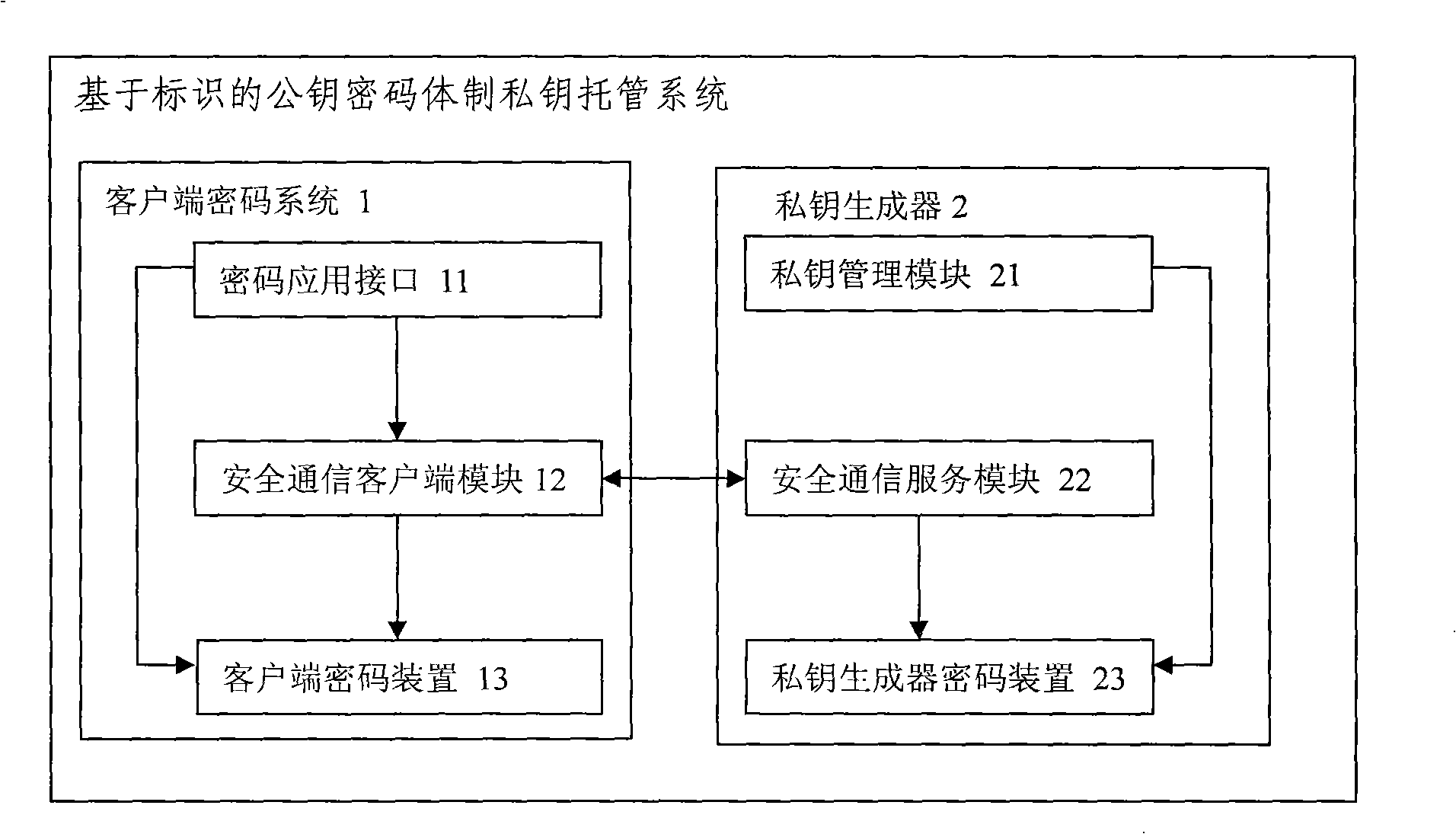
[0036] System implementation includes three parts. One is the tamper-proof identity authentication protocol, the other is the design of the cryptographic device, and the third is the private key acquisition process.
[0037] 1. Tamper-proof identity authent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com