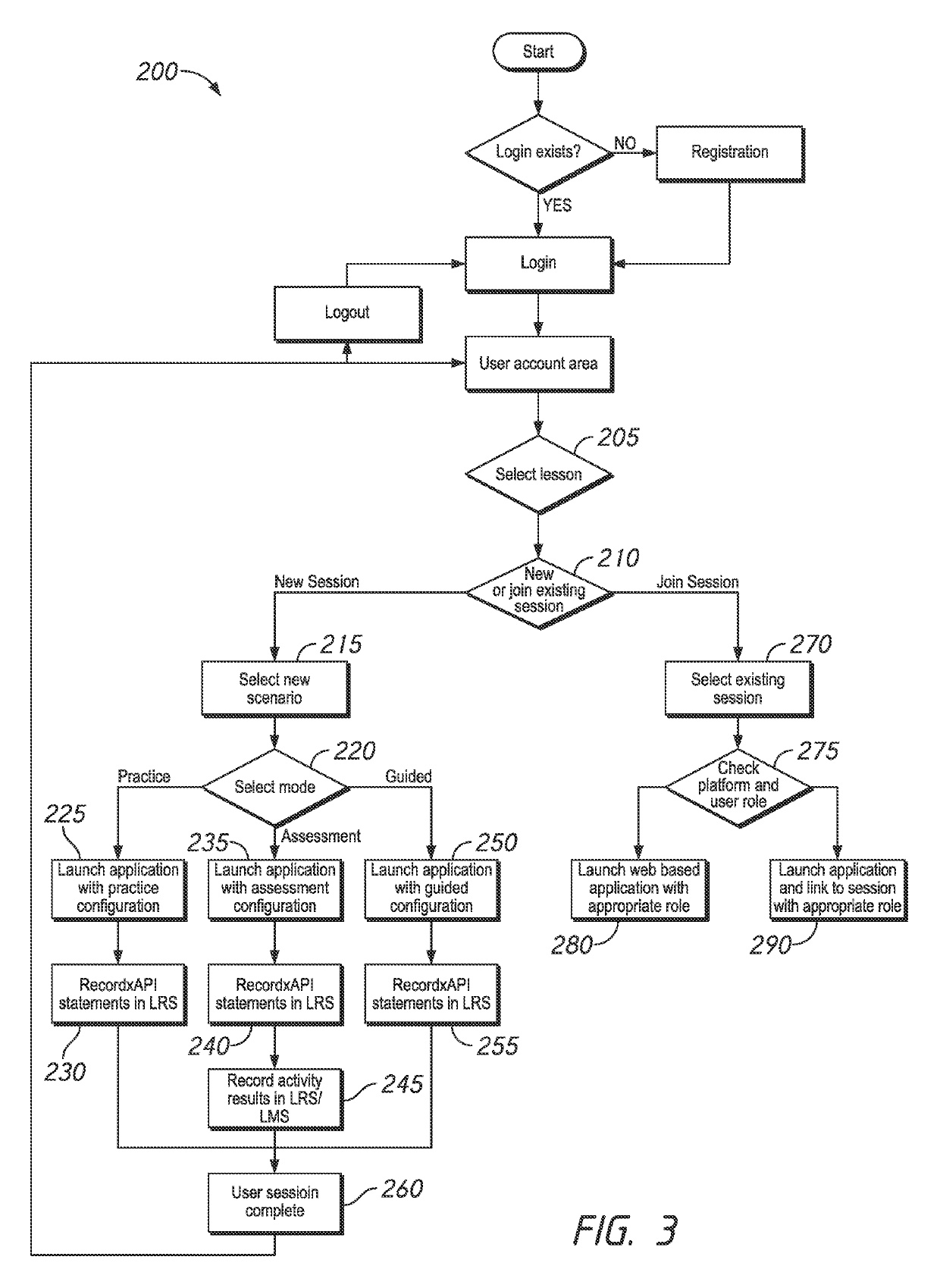
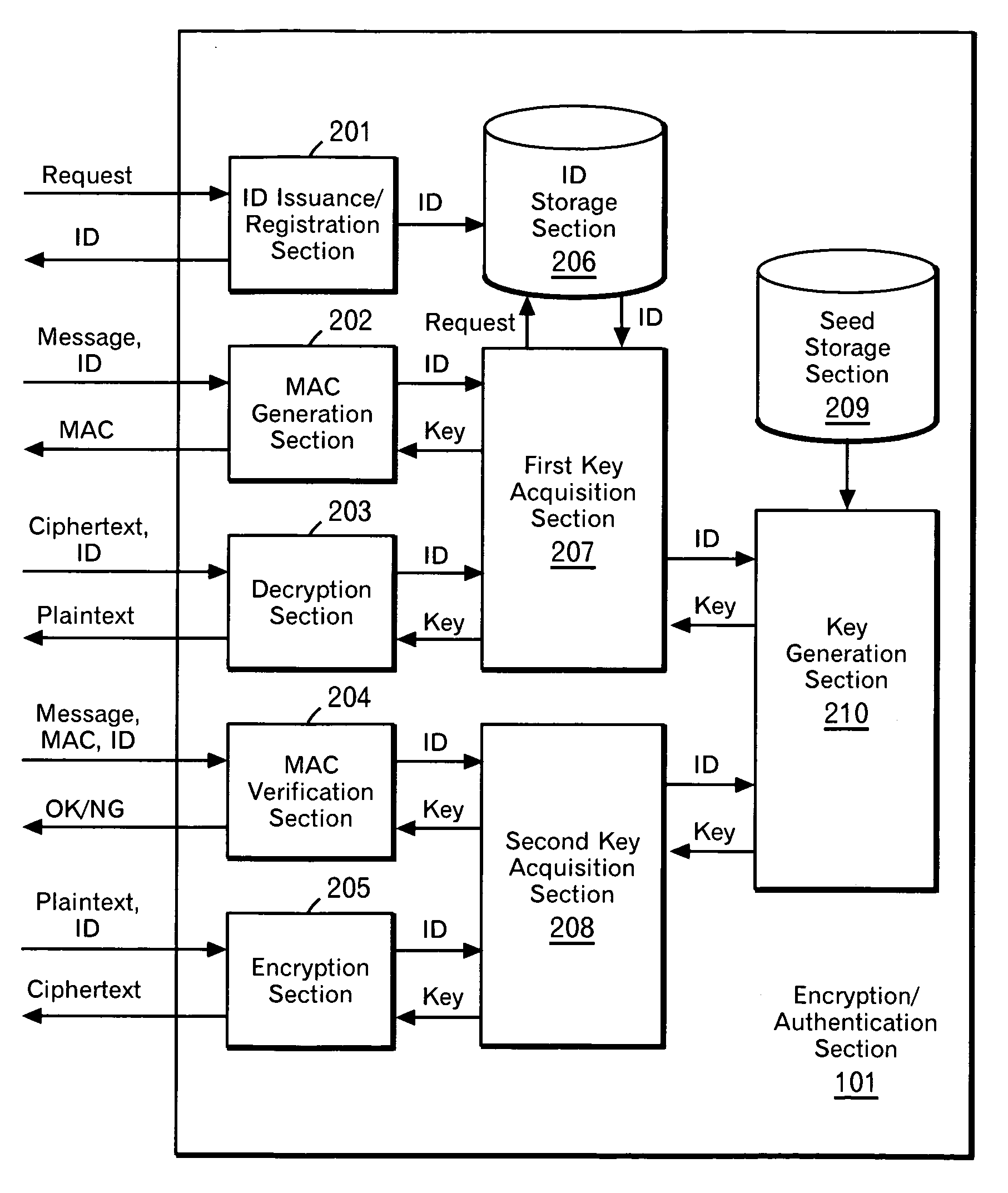
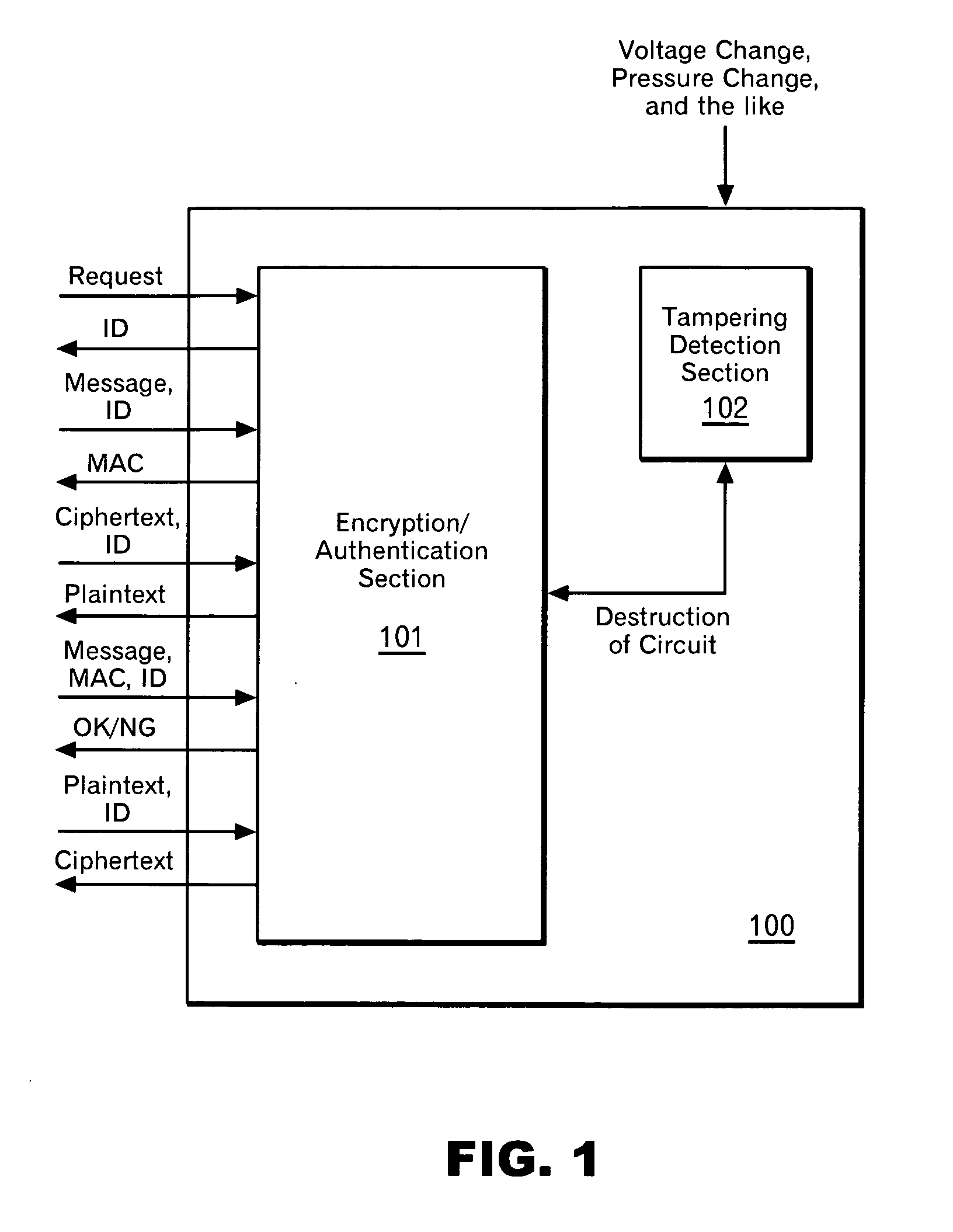
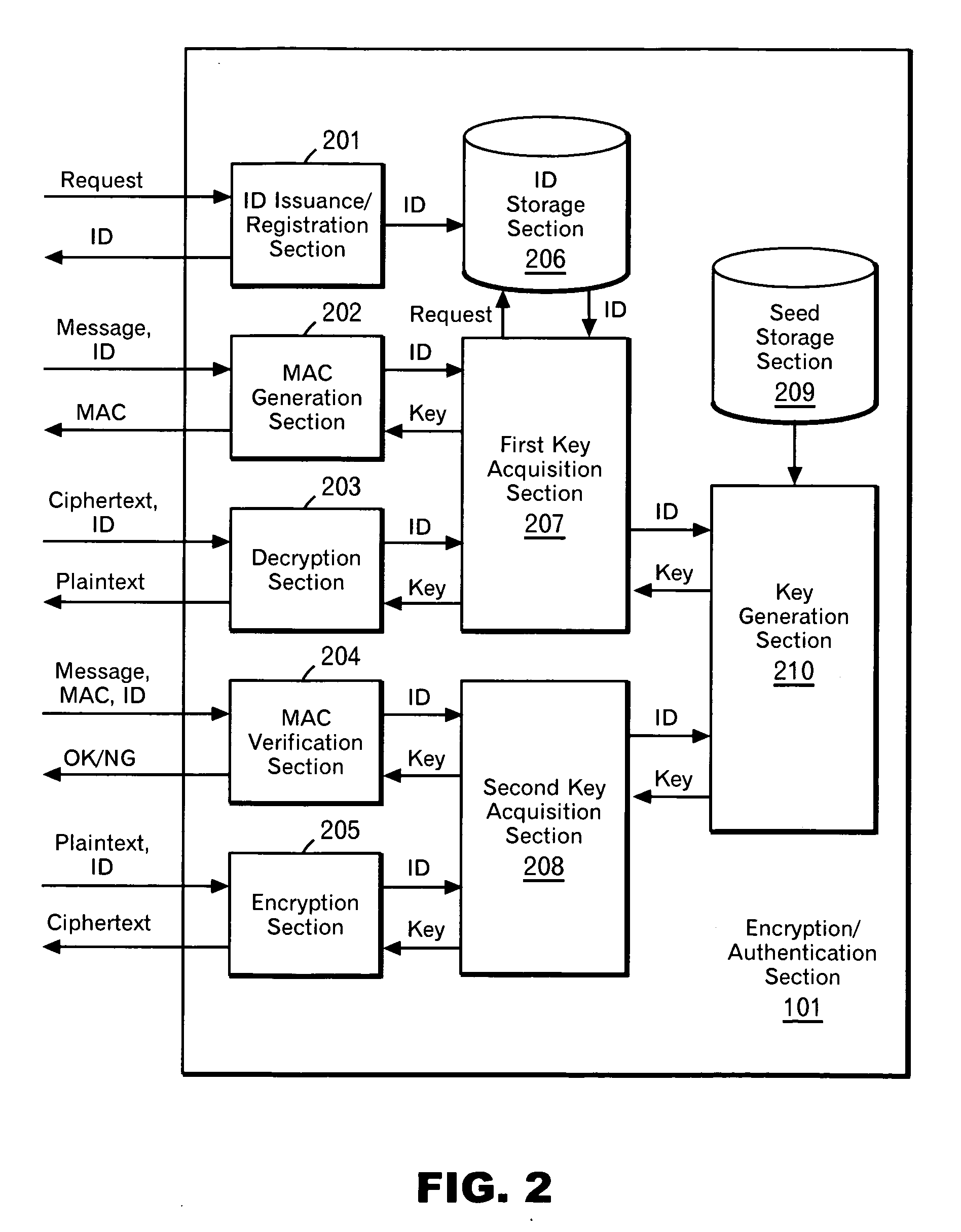
Patents
Literature
253 results about "Third person" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
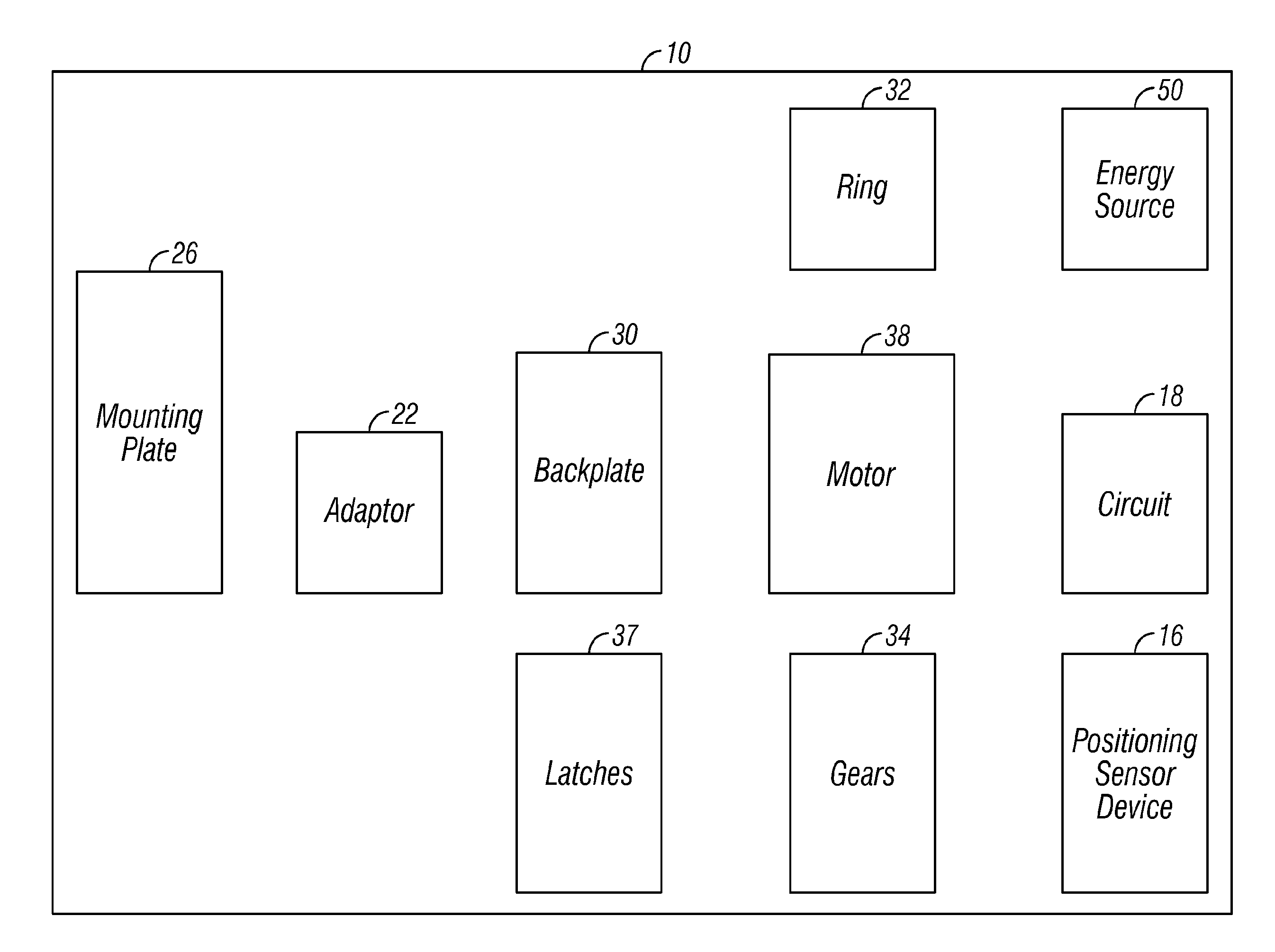
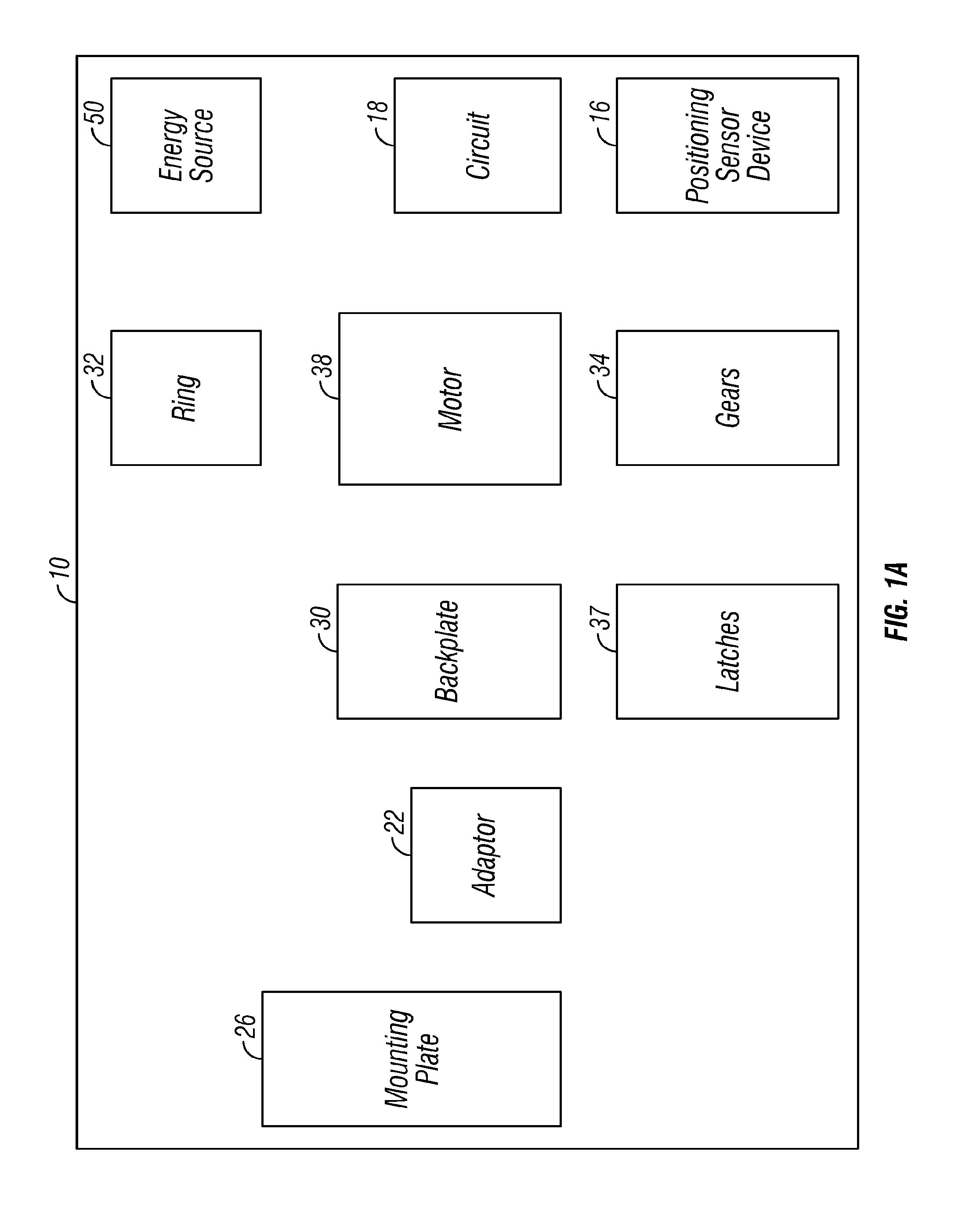
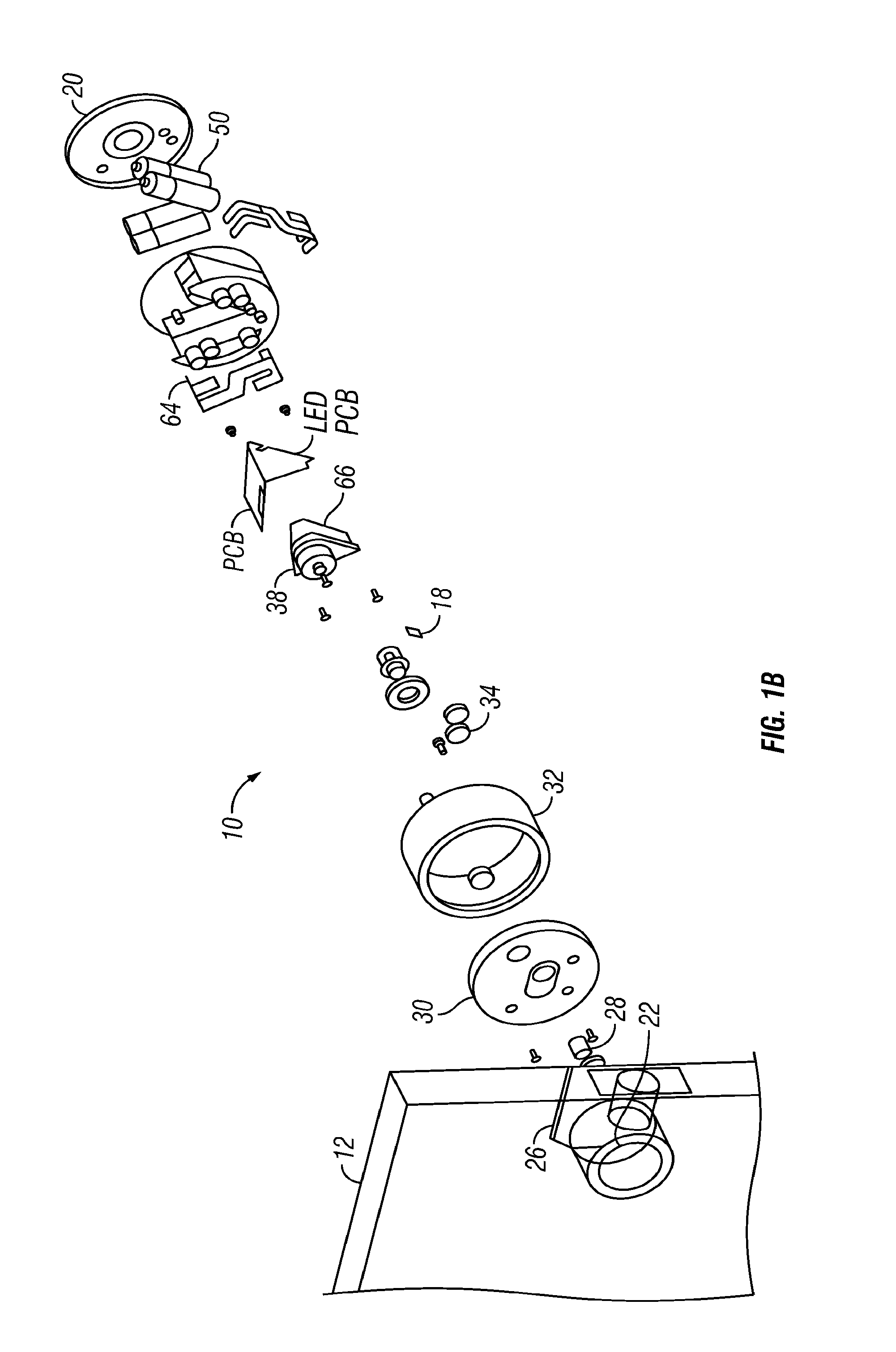
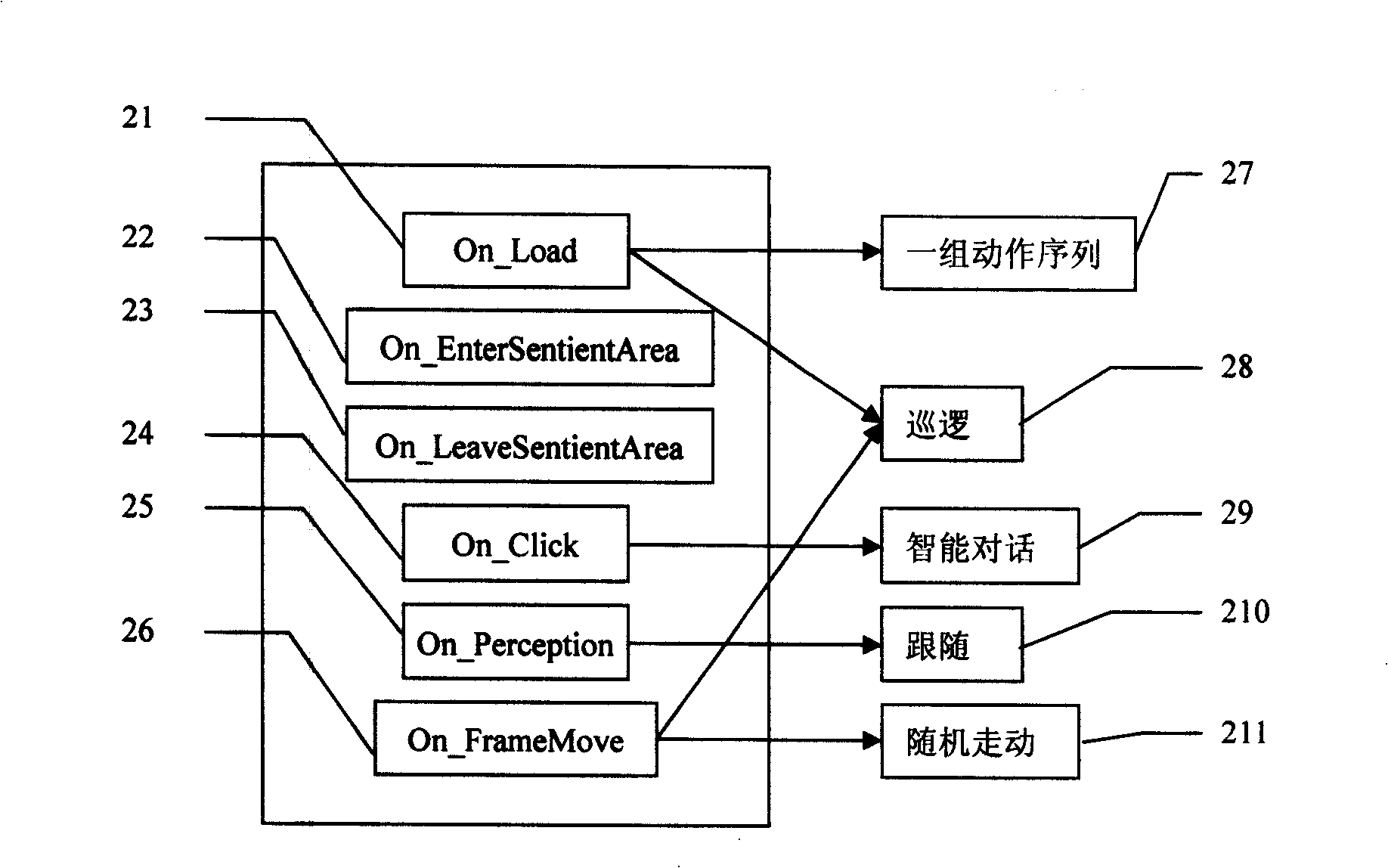
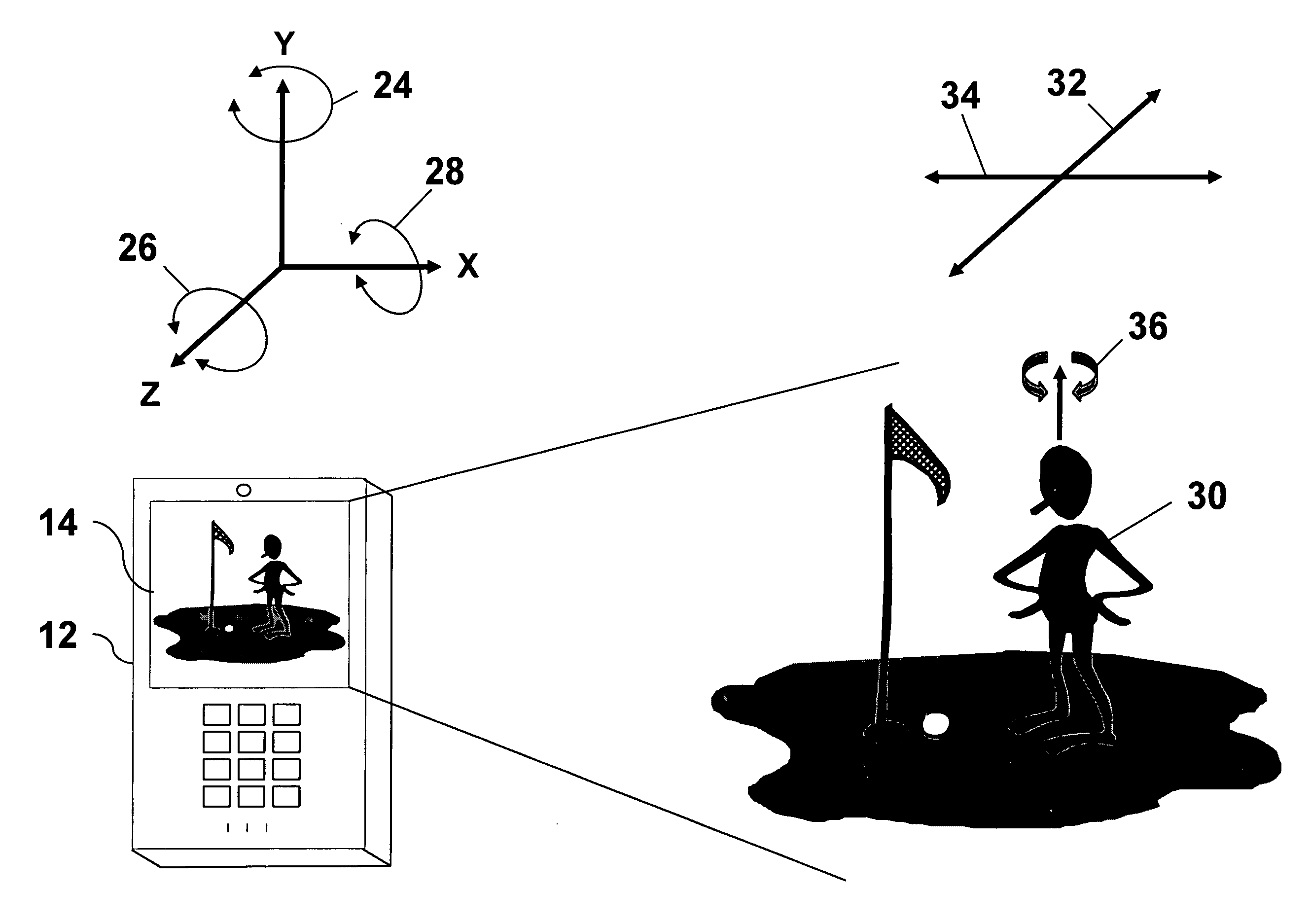
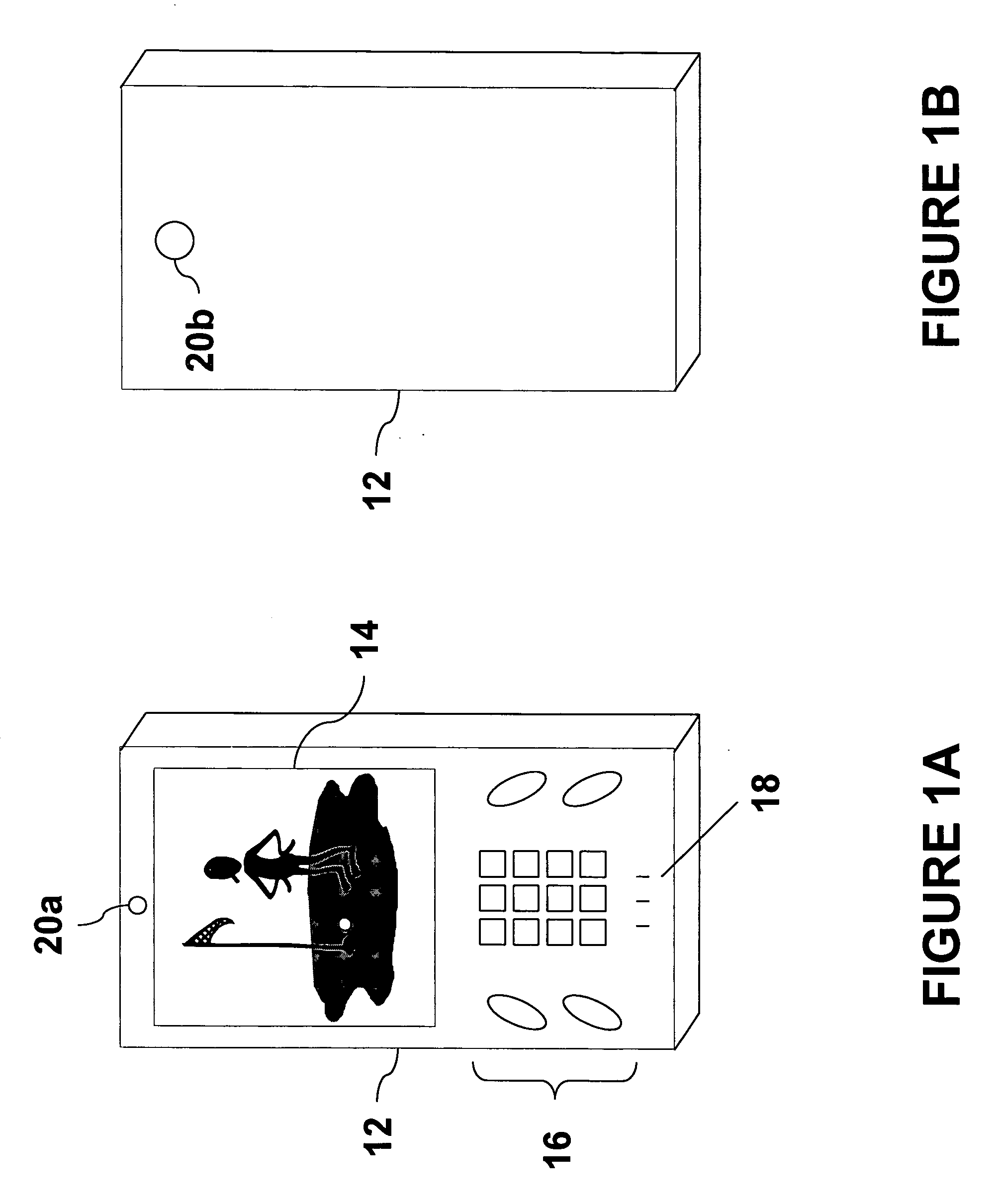
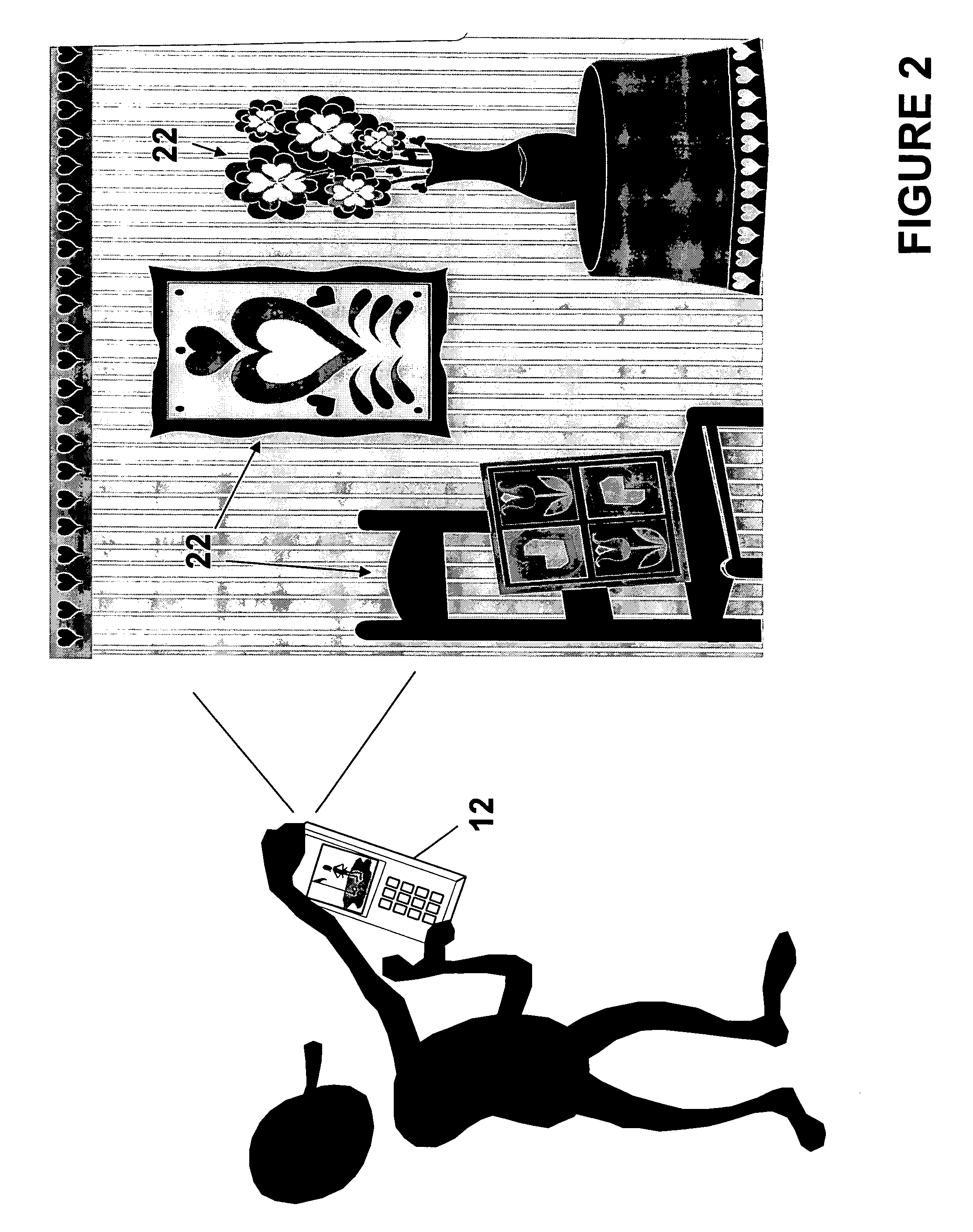
Digital mirror system with advanced imaging features and hands-free control
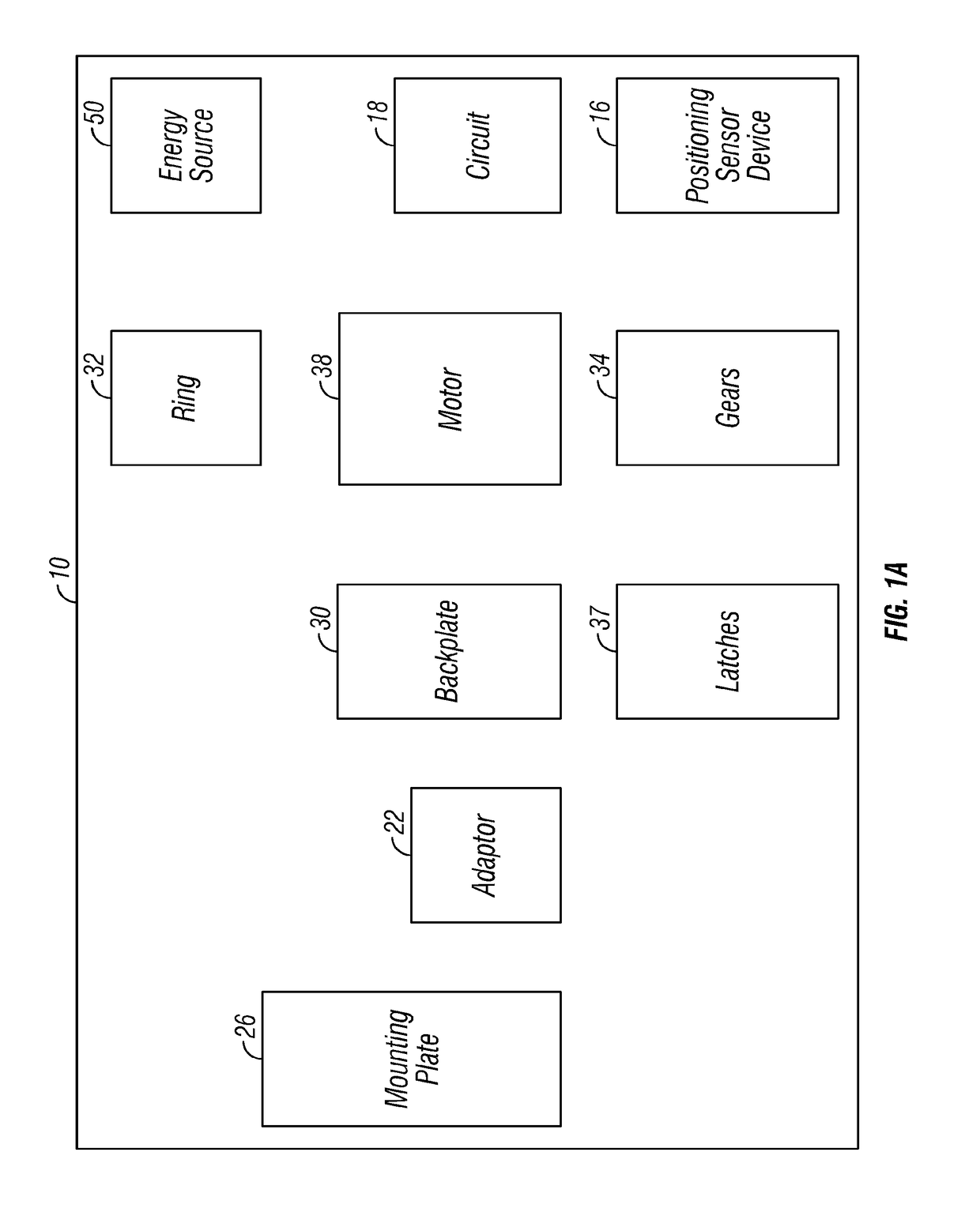
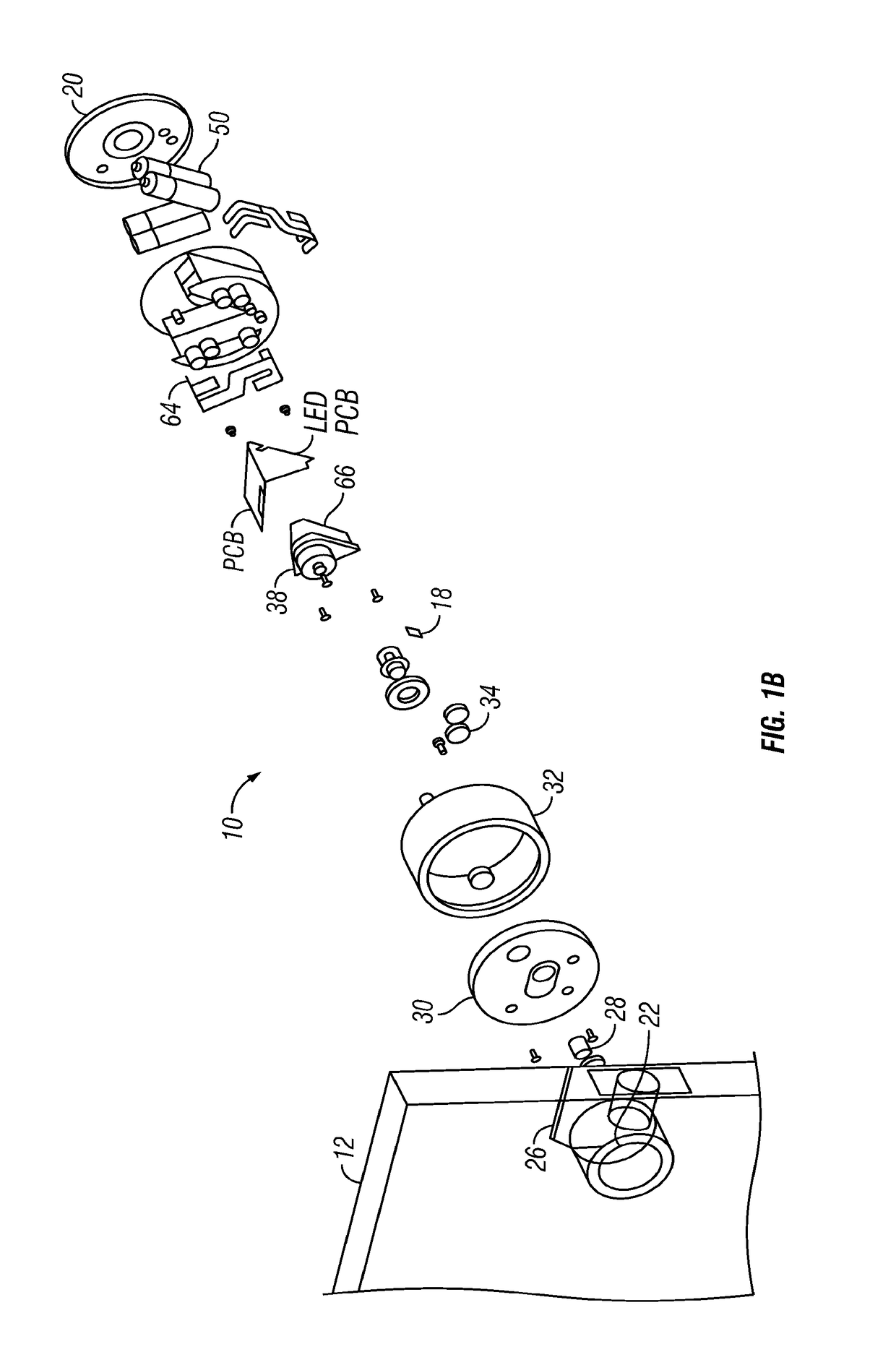
A digital mirror system is provided that emulates a traditional mirror by displaying real-time video imagery of a user who stands before it. The digital mirror system provides a plurality of digital mirror modes, including a traditional mirror mode and a third person mirror mode. The digital mirror system provides a plurality of digital mirroring features including an image freeze feature, an image zoom feature, and an image buffering feature. The digital mirror system provides a plurality of operational states including a digital mirroring state and an alternate state, the alternate state including a power-conservation state and / or a digital picture frame state. The digital mirror system provides a user sensor that automatically transitions between operational states in response to whether or not a user is detected before the digital mirror display screen for a period of time. The digital mirror system provides for hands-free user control using speech recognition, the speech recognition being employed to enable a user to selectively access one or more of the digital mirror modes or features in response to verbal commands relationally associated with those modes or features.
Owner:OUTLAND RES
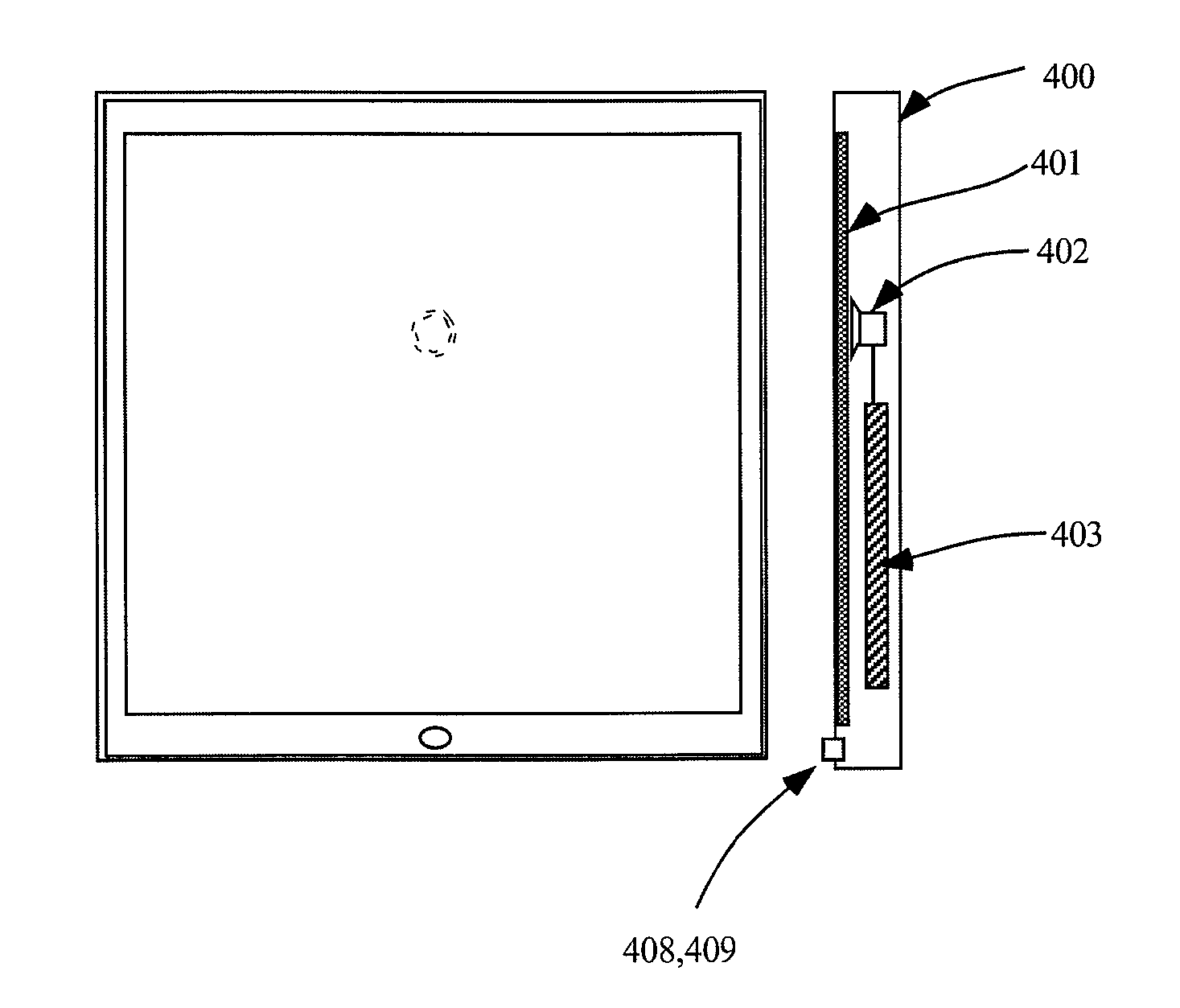
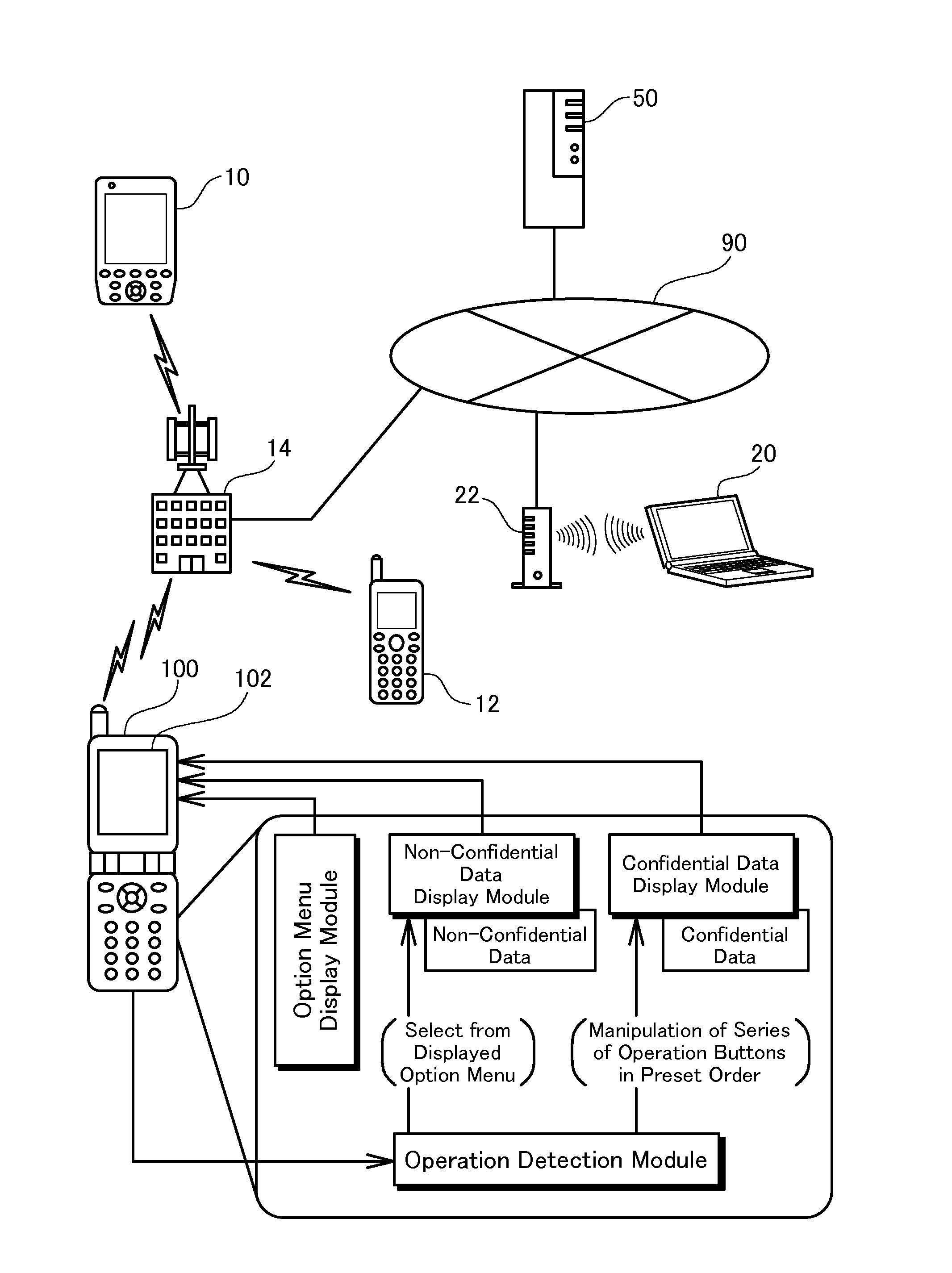
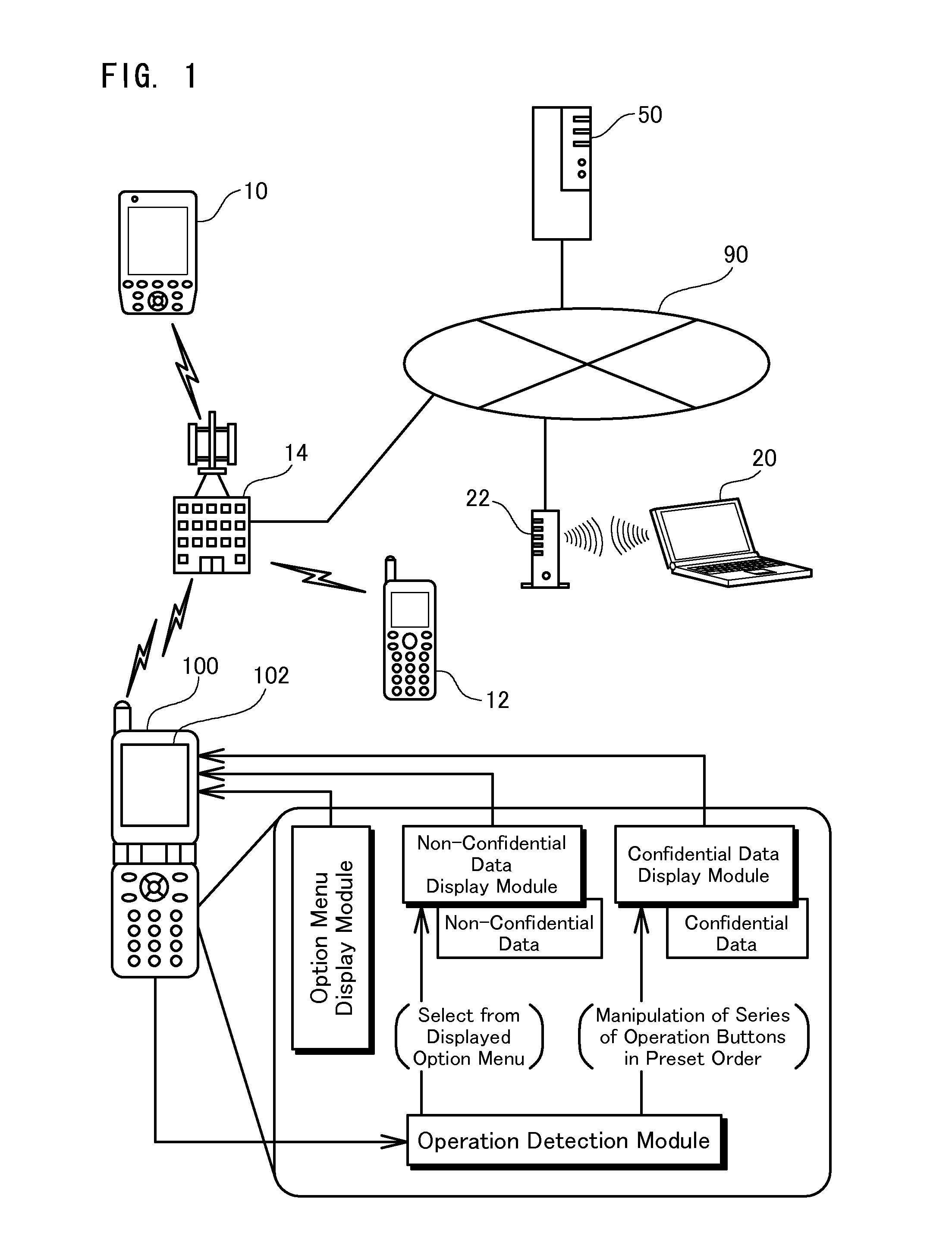
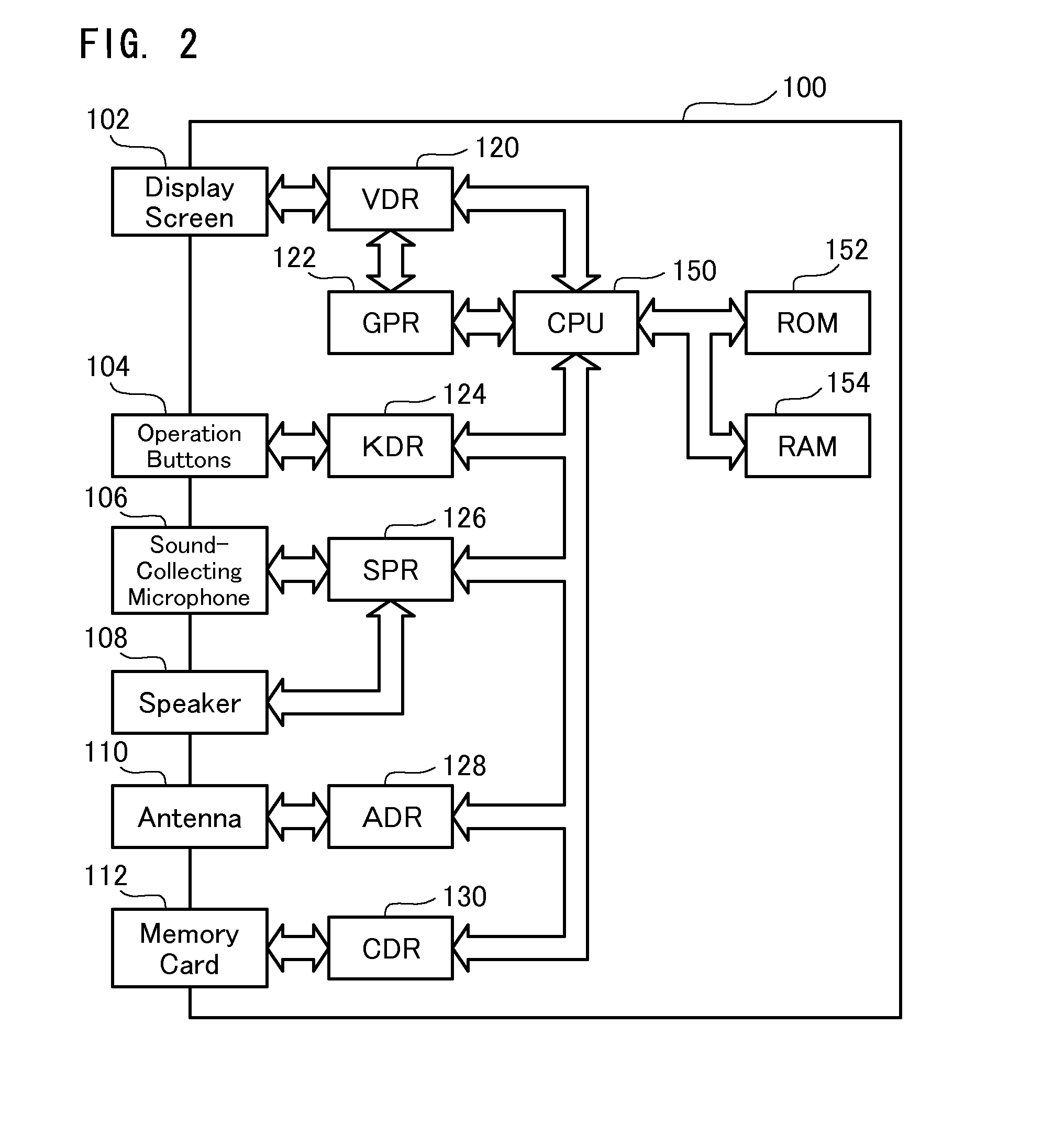
Information terminal device and character data display method
InactiveUS20070271608A1Safe and secure of confidential dataReduce the possibilityDigital data processing detailsUser identity/authority verificationData displayInternet privacy
The information terminal device of the invention has a first function of displaying non-confidential data in a selectable manner on its display screen and, in response to the user's selection of the non-confidential data, showing the details of the non-confidential data. The information terminal device also has a second function of displaying confidential data in a selectable manner and, in response to the user's selection of the confidential data, showing the details of the confidential data. The first function is given as one normally selectable menu option and is activated by the user's selection of the corresponding menu. The second function is, however, not given as a normally selectable menu option and is triggered only by the user's series of operations of an operation unit in a preset sequence. No operation-related display appears on the display screen of the information terminal device during the user's series of operations of the operation unit. The information terminal device of this configuration does not hint even the presence of confidential data to any third person and thus effectively prevents the third person from analyzing or decoding the data stored in the information terminal device and having illegal access to the confidential data. This arrangement of the invention desirably enables the safe handling of confidential data without the potential for leakage of the confidential data from the information terminal device.
Owner:SUNSOFT
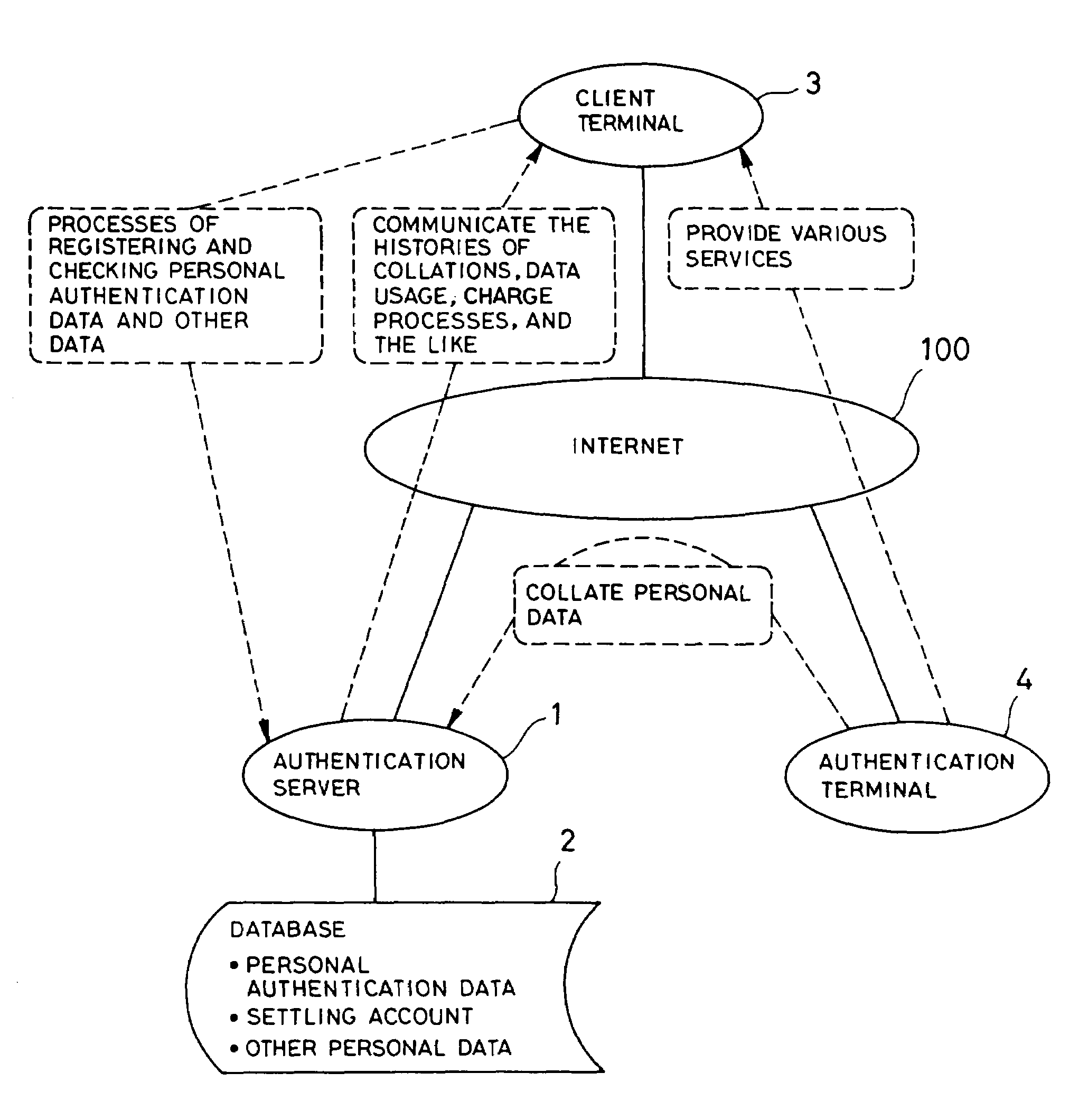
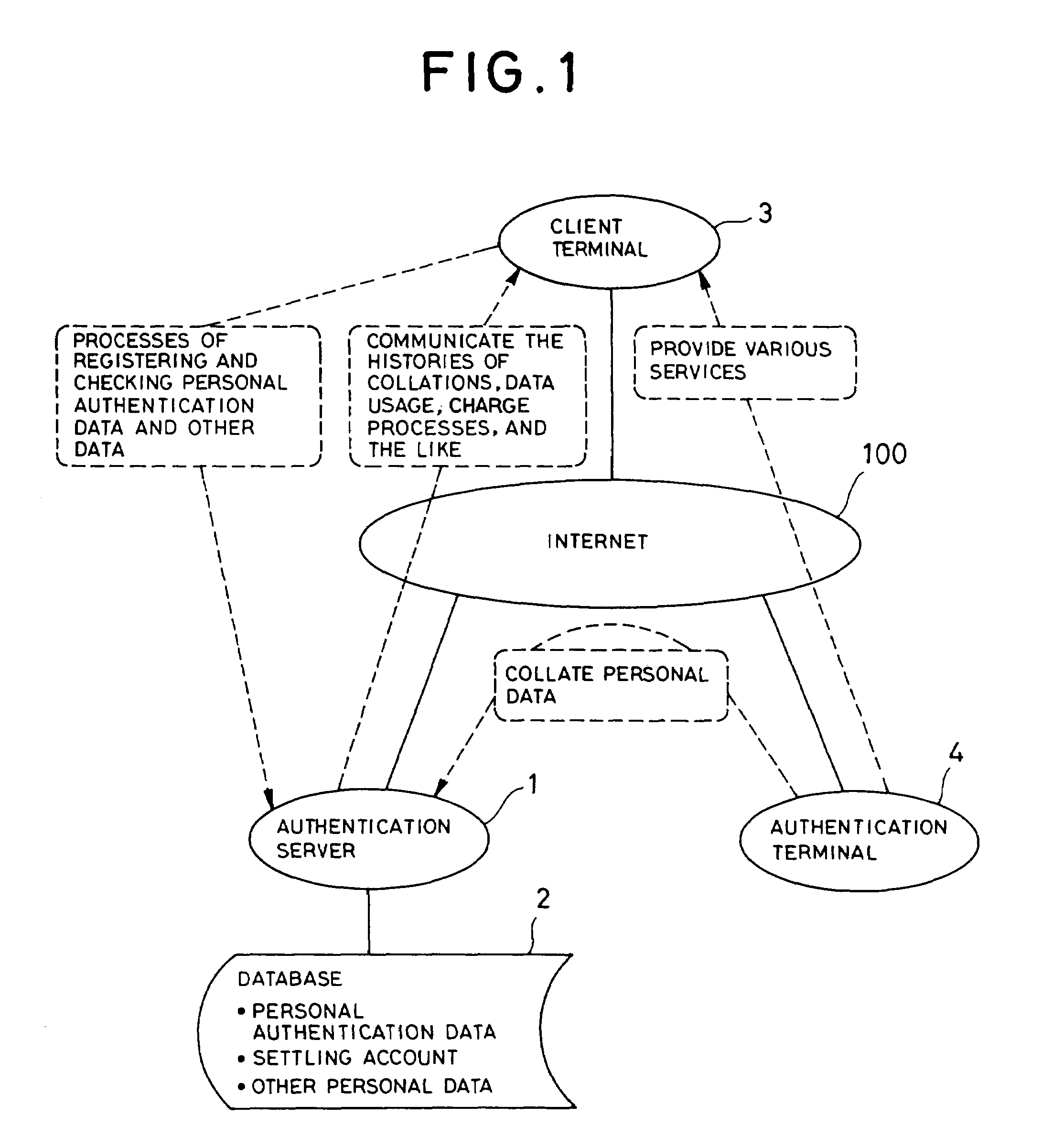
Personal authentication system, and personal authentication method and program used therefor
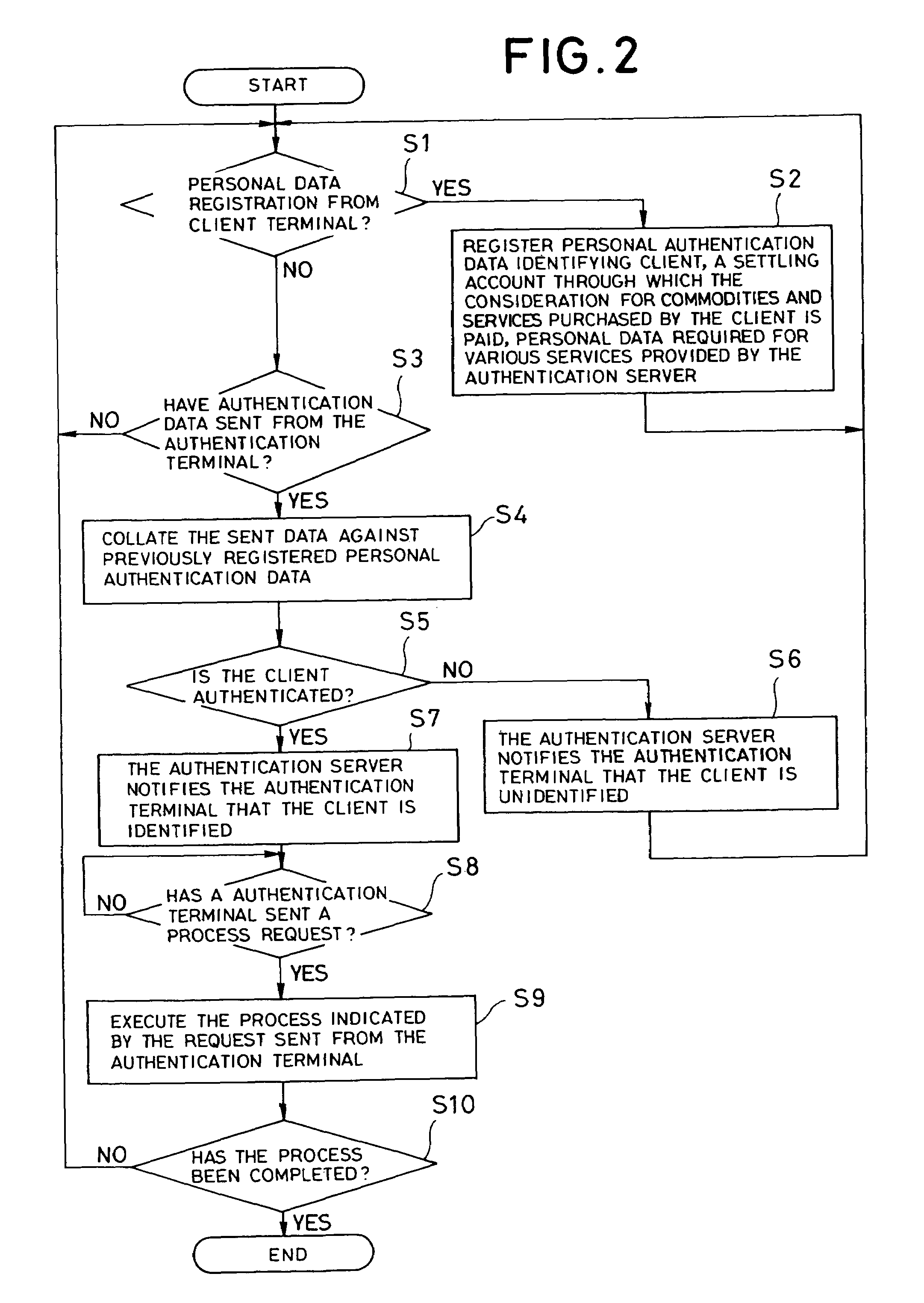
InactiveUS7028013B2Avoid Personal Information LeakagePrevent leakageTicket-issuing apparatusDigital computer detailsPaymentInternet privacy
To provide a personal authentication system that enables a client to receive services even if he fails to carry his card or the like with him or loses it, thus preventing the abuse of the card or the like by a third person and the leakage of the personal information. When data identifying a client are transferred to an authentication server using an authentication terminal, the authentication server collates the sent data against personal authentication data registered previously in a database to identify the client and sends the results of the identification to the authentication terminal. After the authentication, when the authentication terminal requests the payment of charges from a settling account registered previously in the database, the read and modification of personal data, or the like, the authentication server executes a process based on the sent request.
Owner:NEC CORP
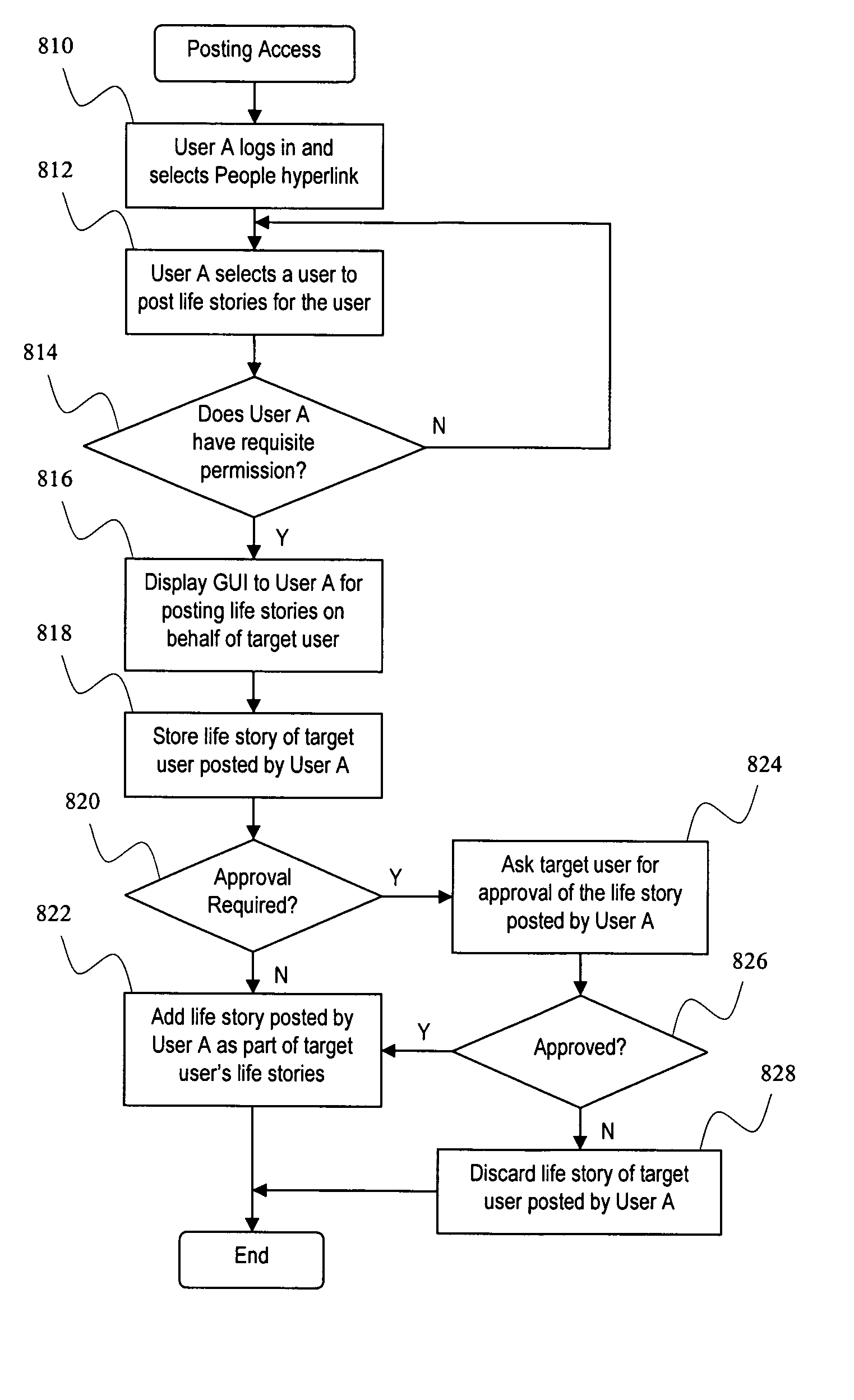
Collaborative system and method for generating biographical accounts
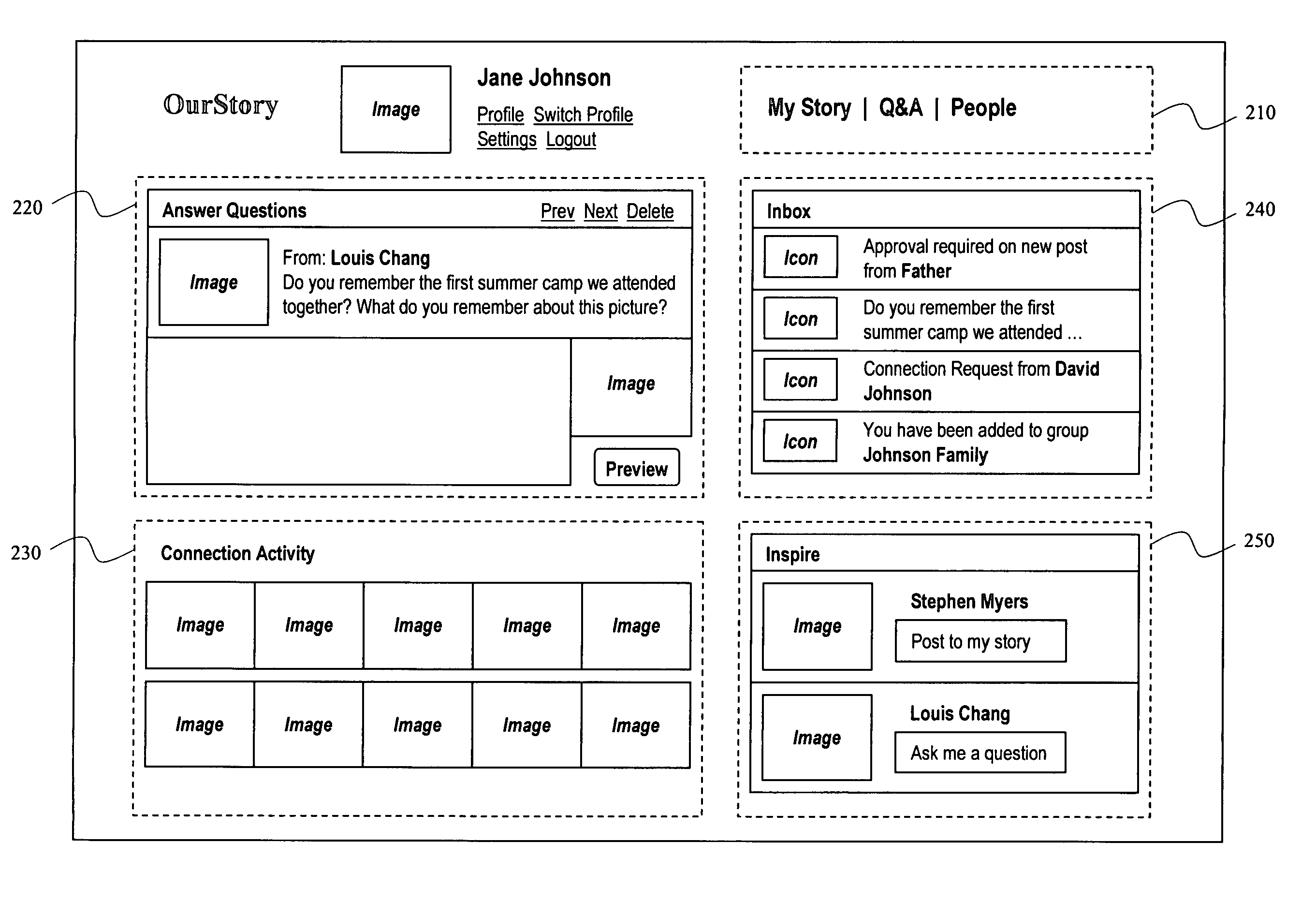
InactiveUS20070261071A1Improve relevanceHighly relevantAnalogue secracy/subscription systemsBroadcast information monitoringCollaborationThird person
A collaborative system and method are used to capture, organize, share and preserve life stories. Life stories can be expressed in first person or third person. In either case, the process of developing the life stories is carried out with collaboration with and contributions from other users. The collaboration among the users is desirable because it serves to encourage and prompt users to record their life stories and also increases the relevance of the recorded life stories, so that an online community of users containing highly relevant and meaningful content, that is also relatively permanent in nature, about the users can be created.
Owner:GOOGLE LLC
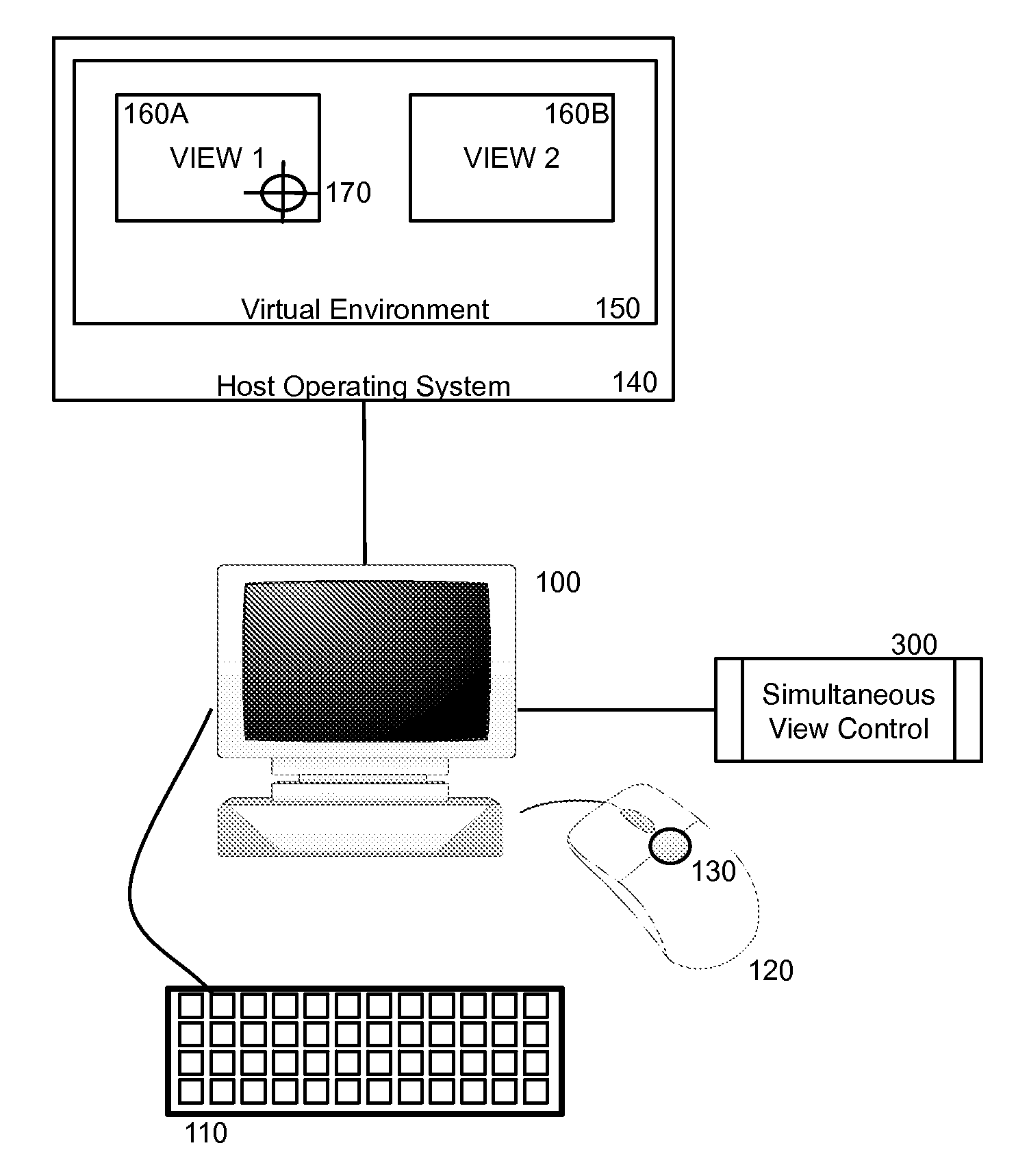
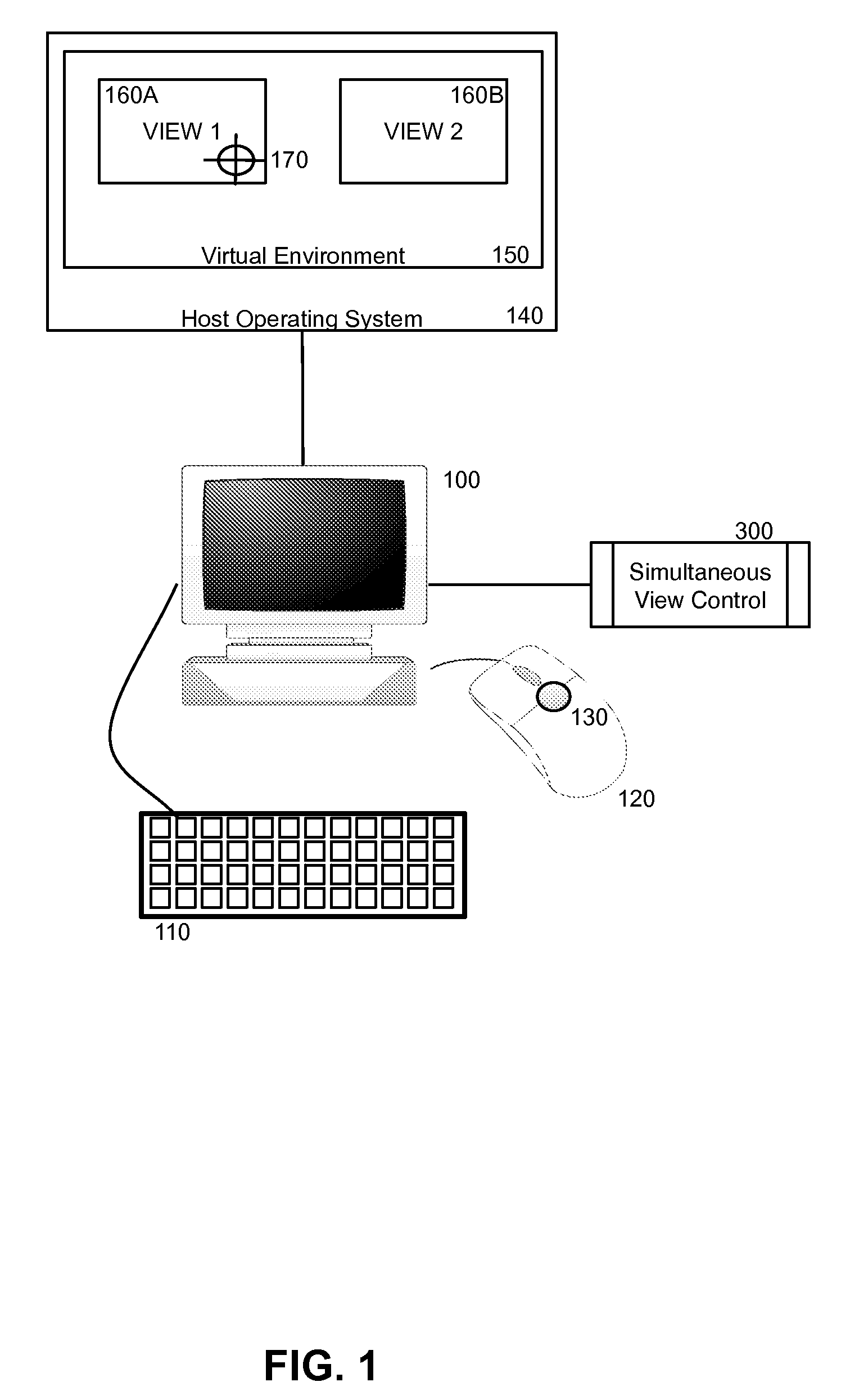
Simultaneous view and point navigation
Embodiments of the invention provide a method, system and computer program product for simultaneous view and point navigation. In a first embodiment of the invention, a single virtual environment interaction method can include maintaining first and second independent views corresponding to respectively different geometric planes in a single virtual environment, such as a flight simulator, first-person or third-person shooter game or avatar-driven adventure game. The method also can include independently changing the first view responsive to a first input directive from a first input device while concurrently changing the second view responsive to a second input directive from a second input device. Thereafter, the method further can include modifying a point of interest in one of the views responsive to a third input directive from one of the first and second input devices. Optionally, the devices can include an under-mouse sensor and trackpoint included as part of a dual-pointer mouse.
Owner:ACTIVISION PUBLISHING
Collaborative system and method for generating biographical accounts
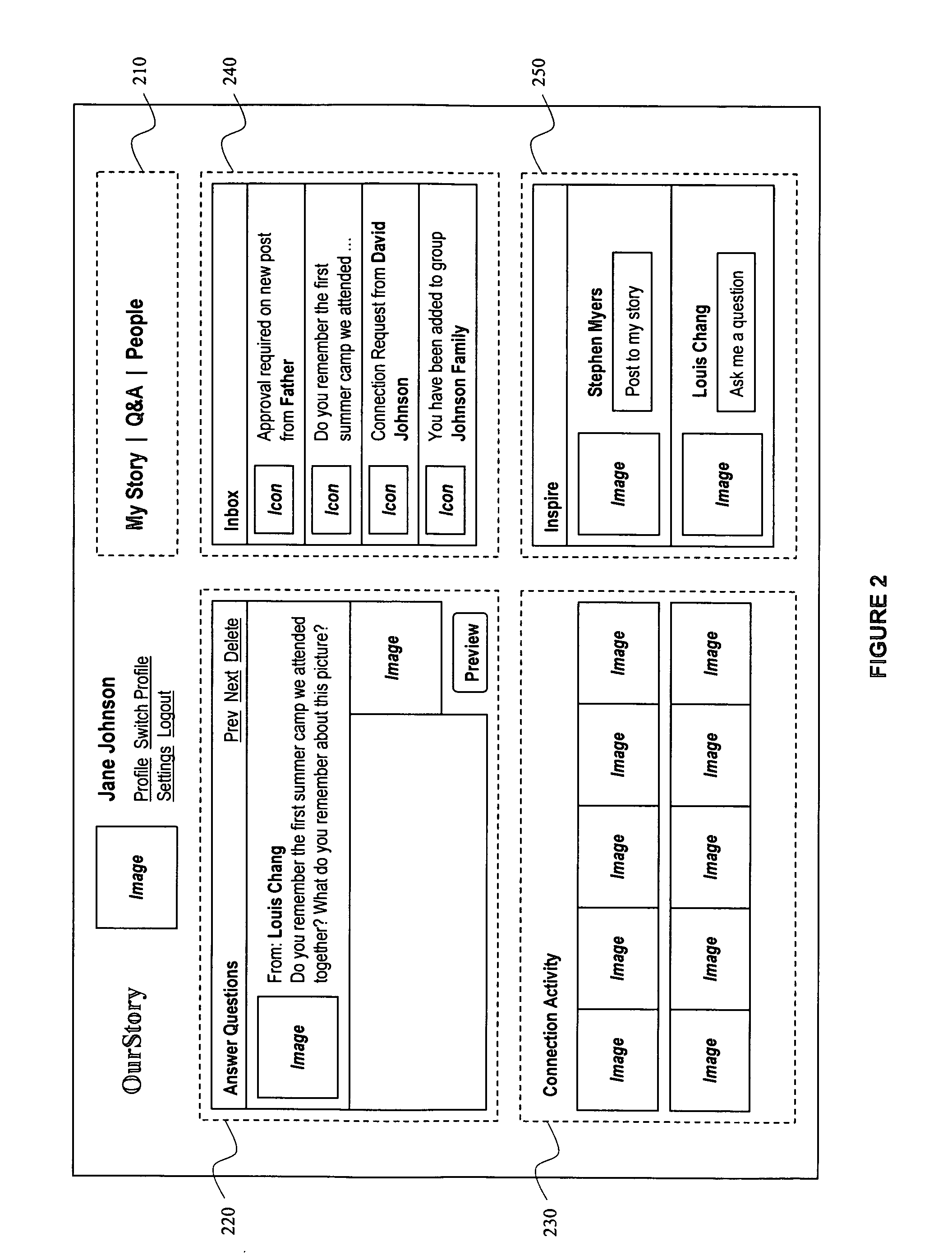
InactiveUS8103947B2Simple interfaceImprove relevanceAnalogue secracy/subscription systemsBroadcast information monitoringThird personCollaboration
A collaborative system and method are used to capture, organize, share and preserve life stories. Life stories can be expressed in first person or third person. In either case, the process of developing the life stories is carried out with collaboration with and contributions from other users. The collaboration among the users is desirable because it serves to encourage and prompt users to record their life stories and also increases the relevance of the recorded life stories, so that an online community of users containing highly relevant and meaningful content, that is also relatively permanent in nature, about the users can be created.
Owner:GOOGLE LLC
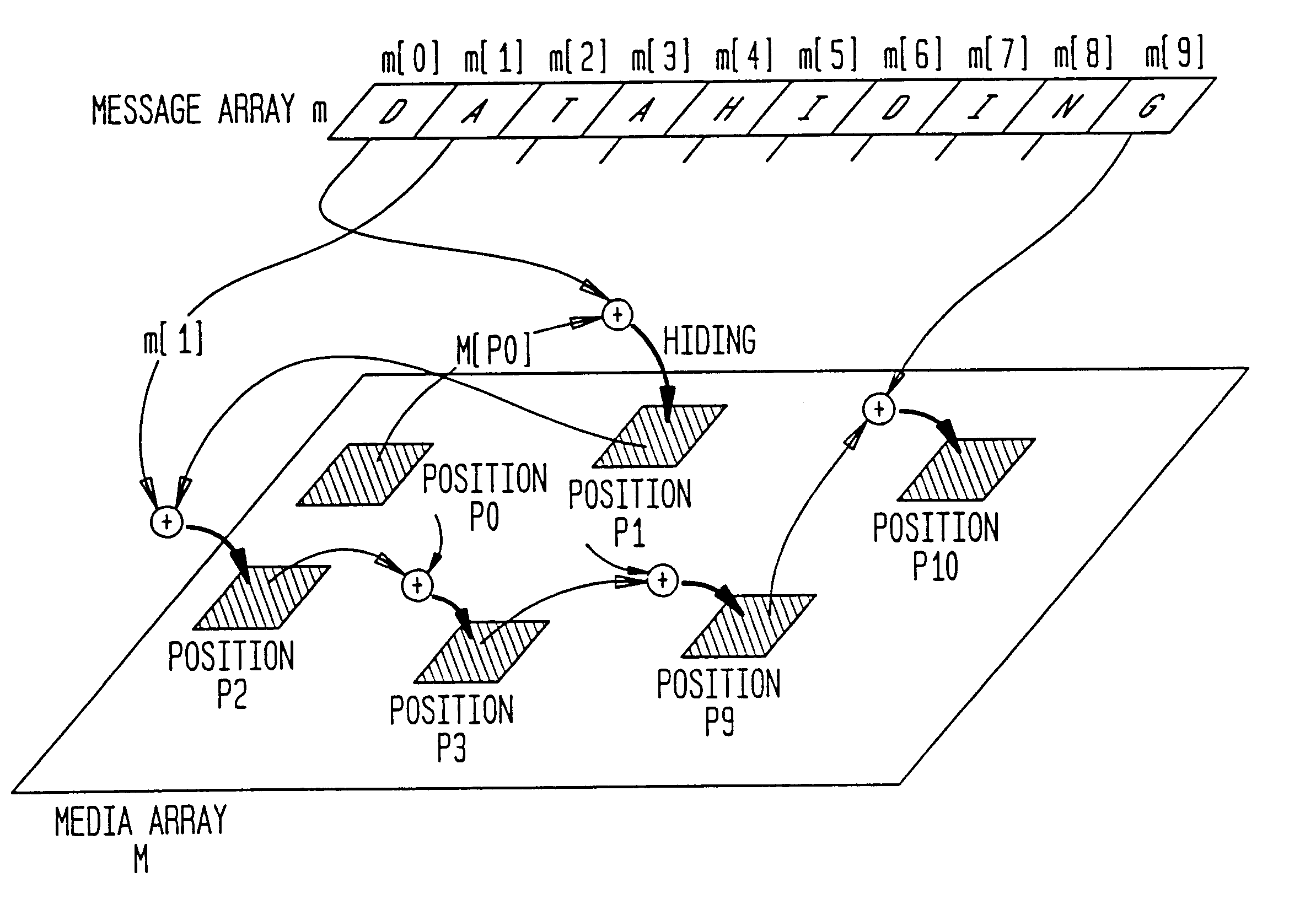
Data hiding and extraction methods
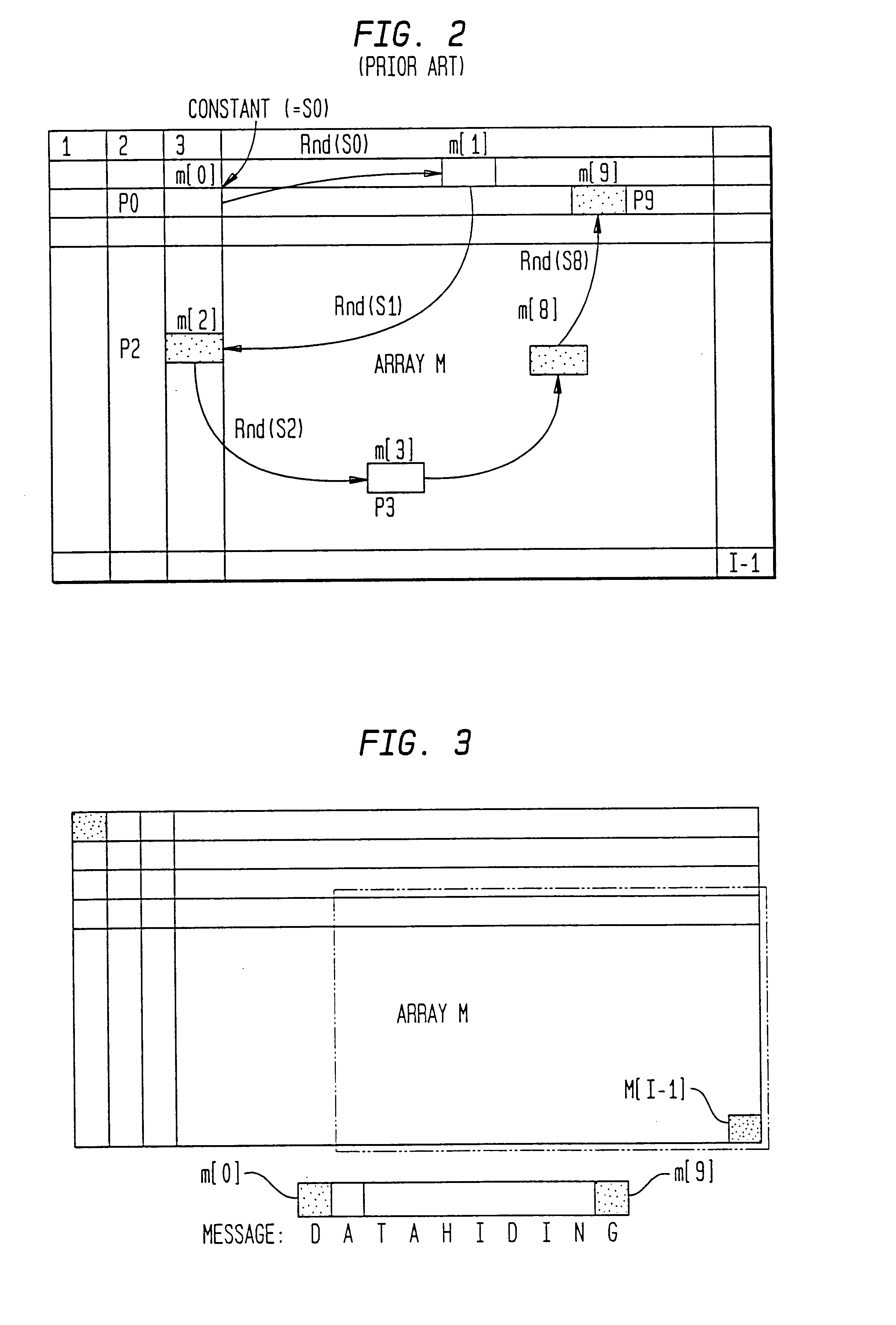
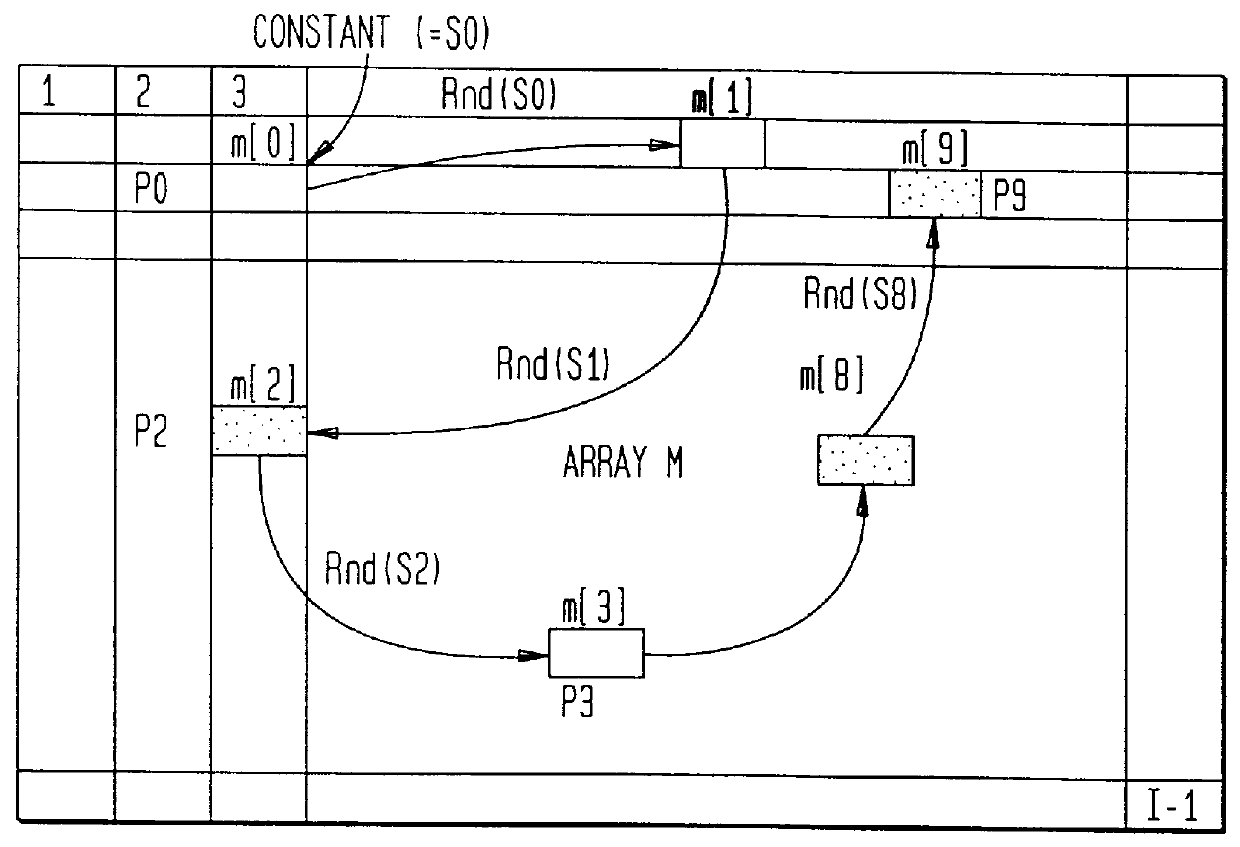
InactiveUS6512835B1Picture reproducers using cathode ray tubesPicture reproducers with optical-mechanical scanningComputer hardwareArray data structure
The present invention provides a data hiding method of hiding media data in message data and a data extraction method of extracting the hidden data wherein message data is dispersively hidden in media data such as an image or sound to prevent a third person from modifying the message data easily.More specifically, the present invention relates to a data hiding method in which media data is expressed as a media array while message data is expressed as a message array so that the array elements of the message array can be dispersively hidden in the message array based on a state values specifying a particular array element of the media array, comprising the steps of:(a) determining the j-th (j>=0) state value Sj;(b) determining (j+1)-th state value Sj+1 based on the j-th state value, the array element of the media array indicated by the j-th state value, and the array element of the message array; and(c) hiding data with respect to the array element of the media array indicated by the (j+1)-th state value Sj+1.
Owner:IBM CORP
Wireless communication device
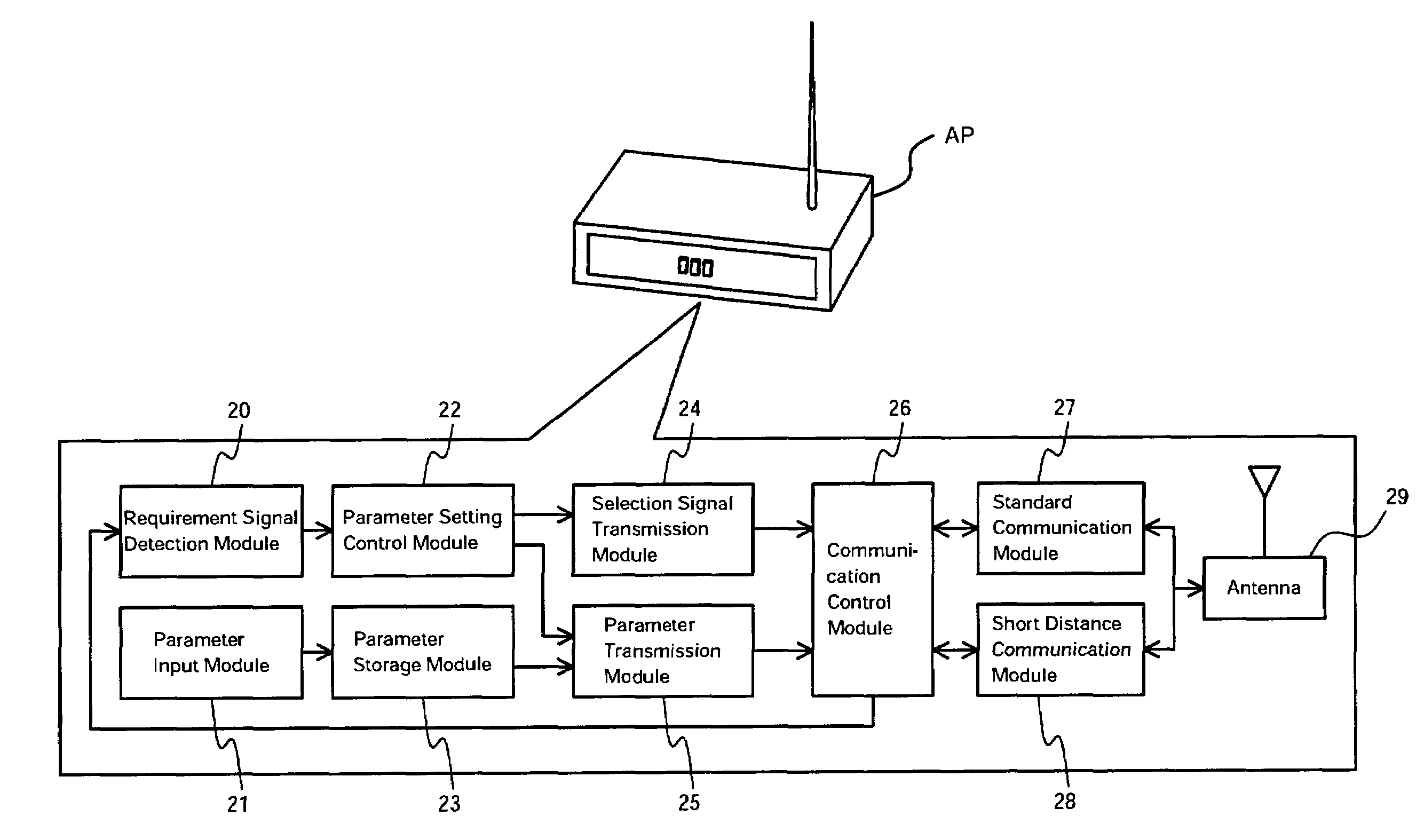
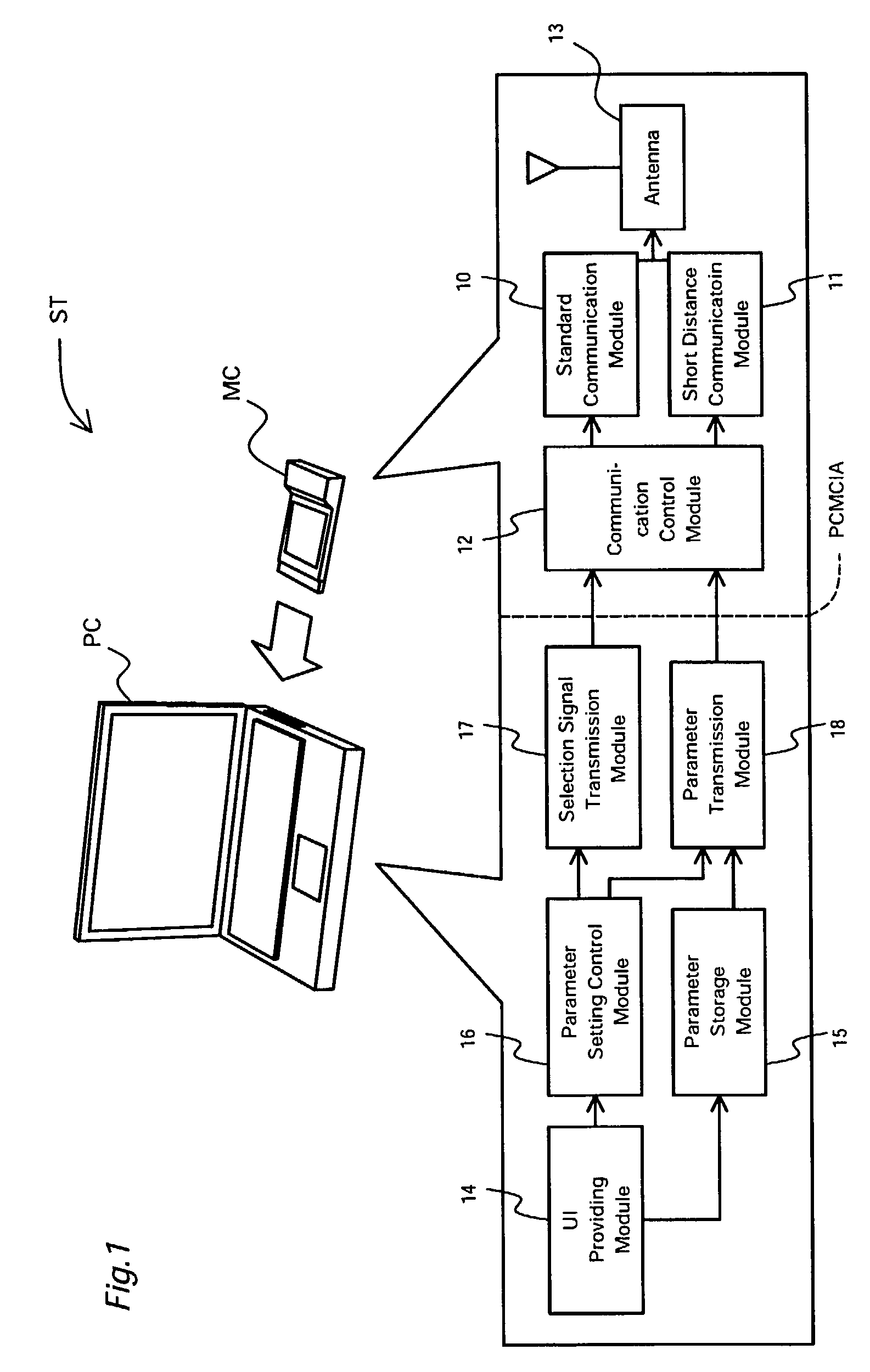
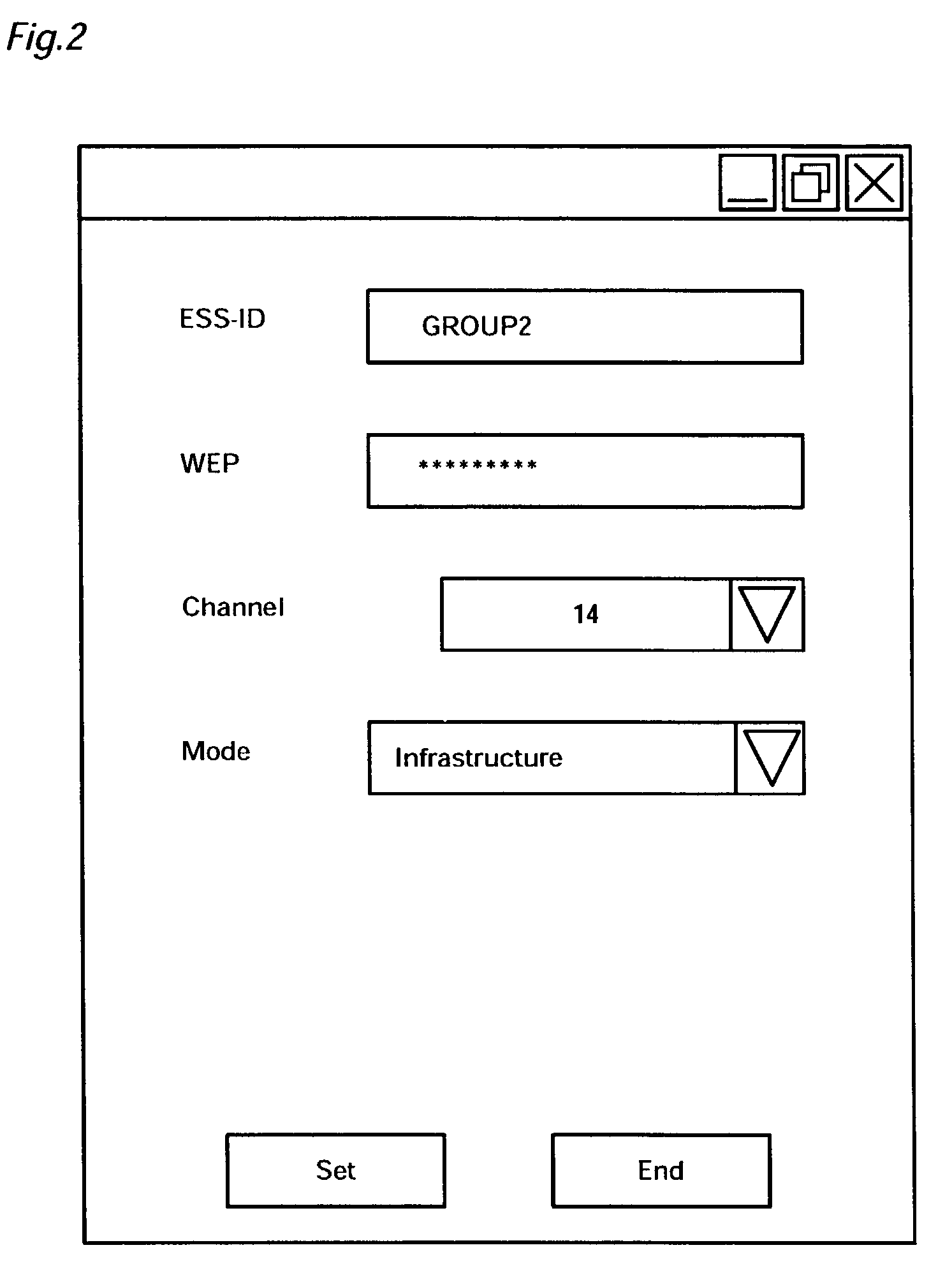
ActiveUS7174157B2Ensure security for settingEnsure safetyKey distribution for secure communicationNetwork traffic/resource managementShortest distanceCommunication control
A standard communication module establishes communication with another wireless communication device via radio waves. A short distance communication module utilizes weaker radio waves than the radio waves used by the standard communication module, in order to establish communication with another wireless communication device. A communication control module activates the short distance communication module to transmit setting parameters, which are used to change settings required for communication in another wireless communication device. This arrangement effectively prevents leakage of the setting parameters to any third person who is beyond the communicable range of the short distance communication module, thus ensuring security for settings in the wireless communication device in a wireless environment.
Owner:138 EAST LCD ADVANCEMENTS LTD
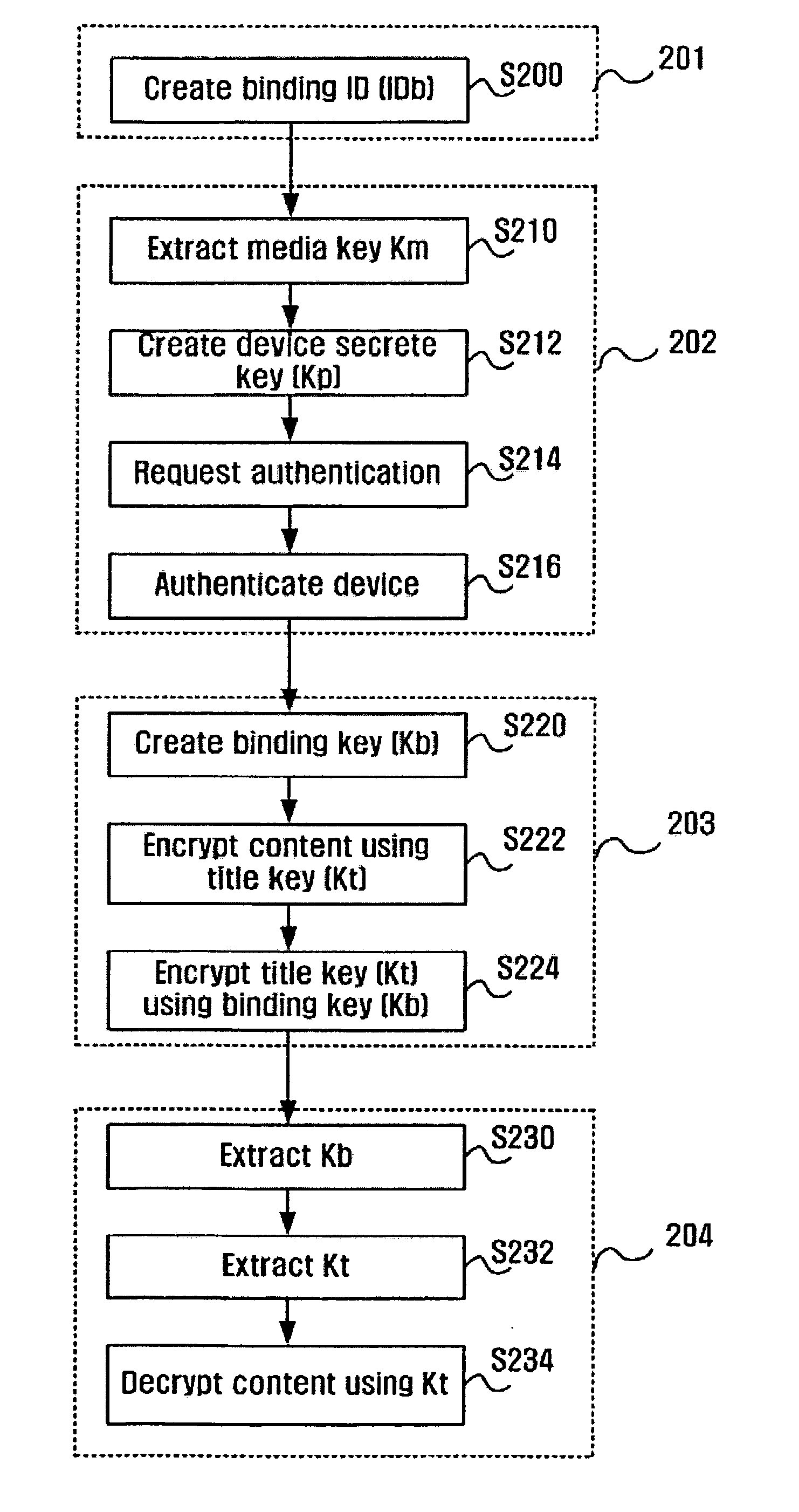
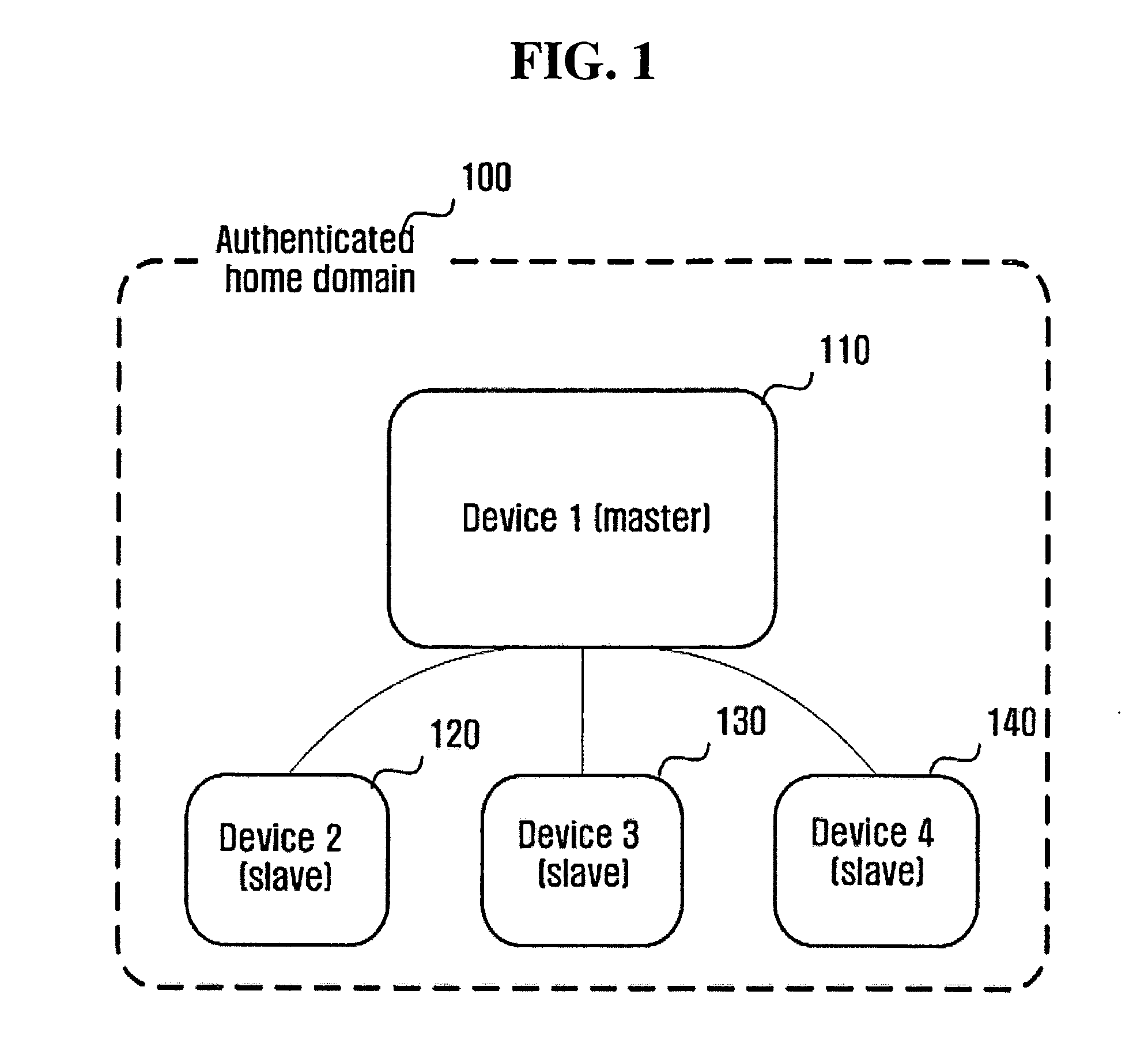
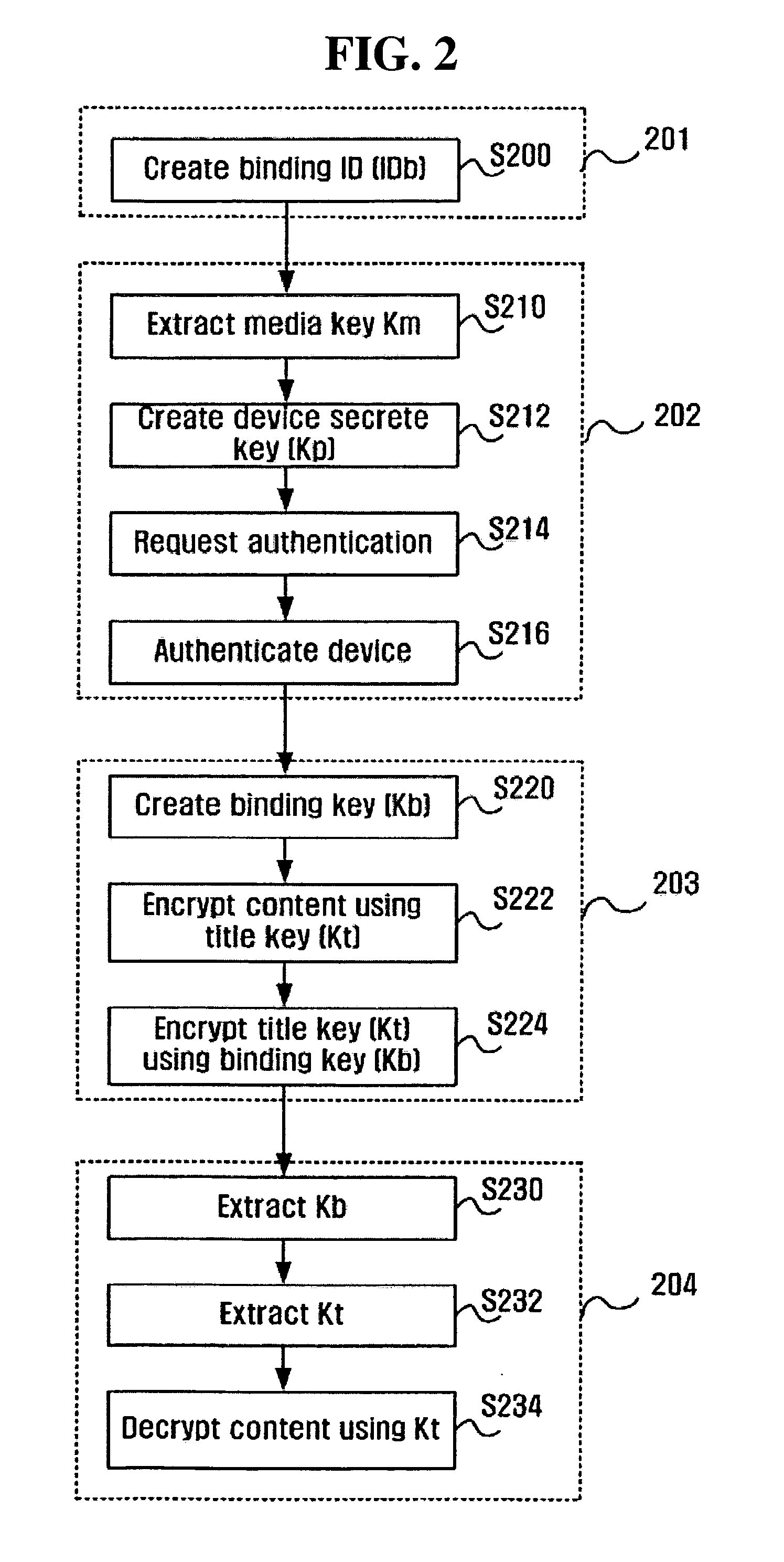
Method of constructing domain based on public key and implementing the domain through universal plug and play (UPnP)
InactiveUS20050086514A1Construction safetyPrevent illegal useDigital data processing detailsUser identity/authority verificationFamily networkNetsniff-ng
A method of constructing a unique domain for preventing content from being illegally used by an unauthorized third person in a public key-based architecture and applying the constructed domain to a home network using universal plug and play (UPnP). The method of the present invention includes selecting one of controlled devices that are operable as a master device and determining the selected device as the master device; performing device authentication in such a manner that other controlled devices receive a secret information block from the determined master device and create certificates; and determining slave devices by selecting one or more devices among the authenticated controlled devices.
Owner:SAMSUNG ELECTRONICS CO LTD
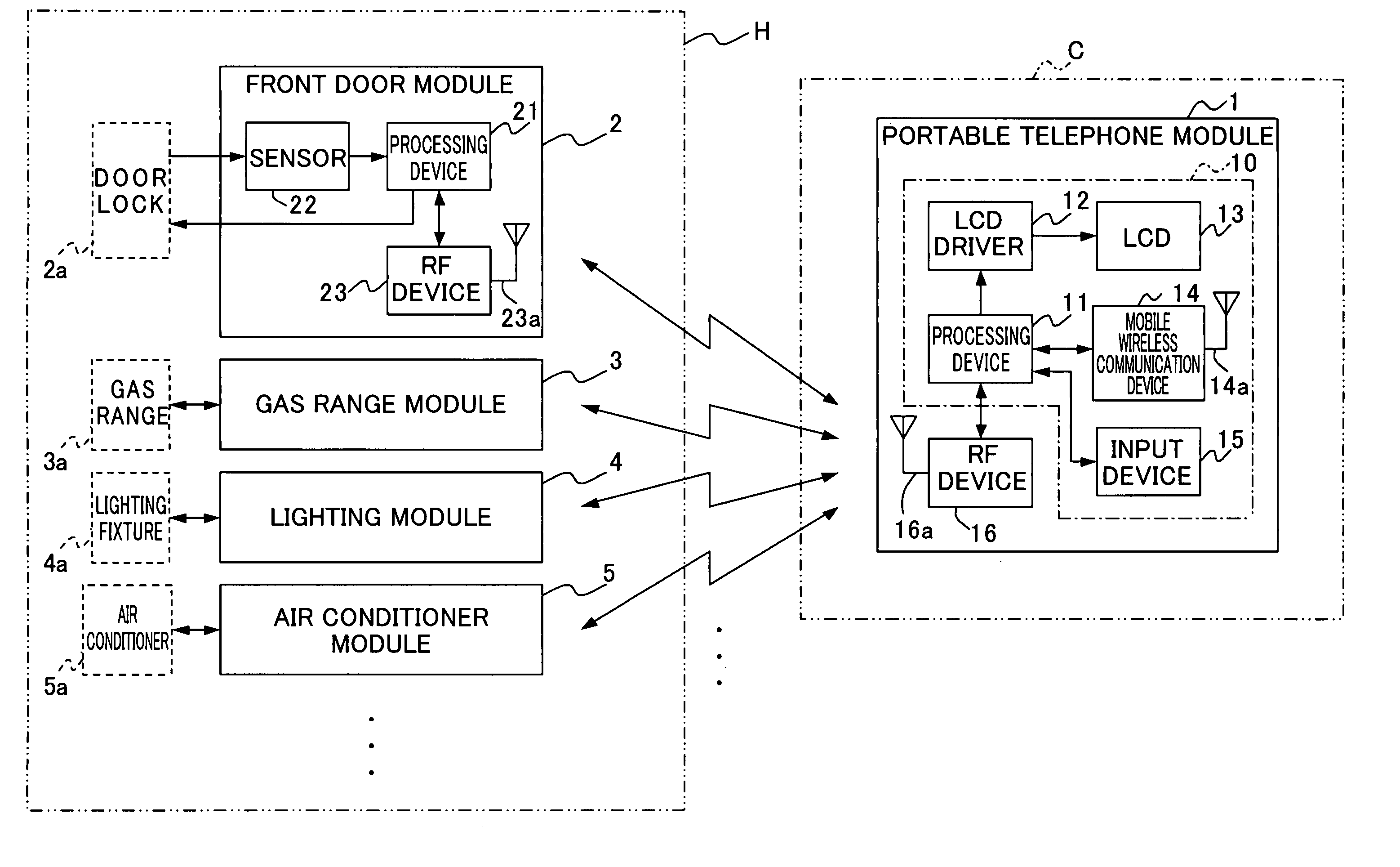
Home security system
InactiveUS20060109966A1Prevent unauthorized accessElectric signal transmission systemsFrequency-division multiplex detailsHome securityHome appliance
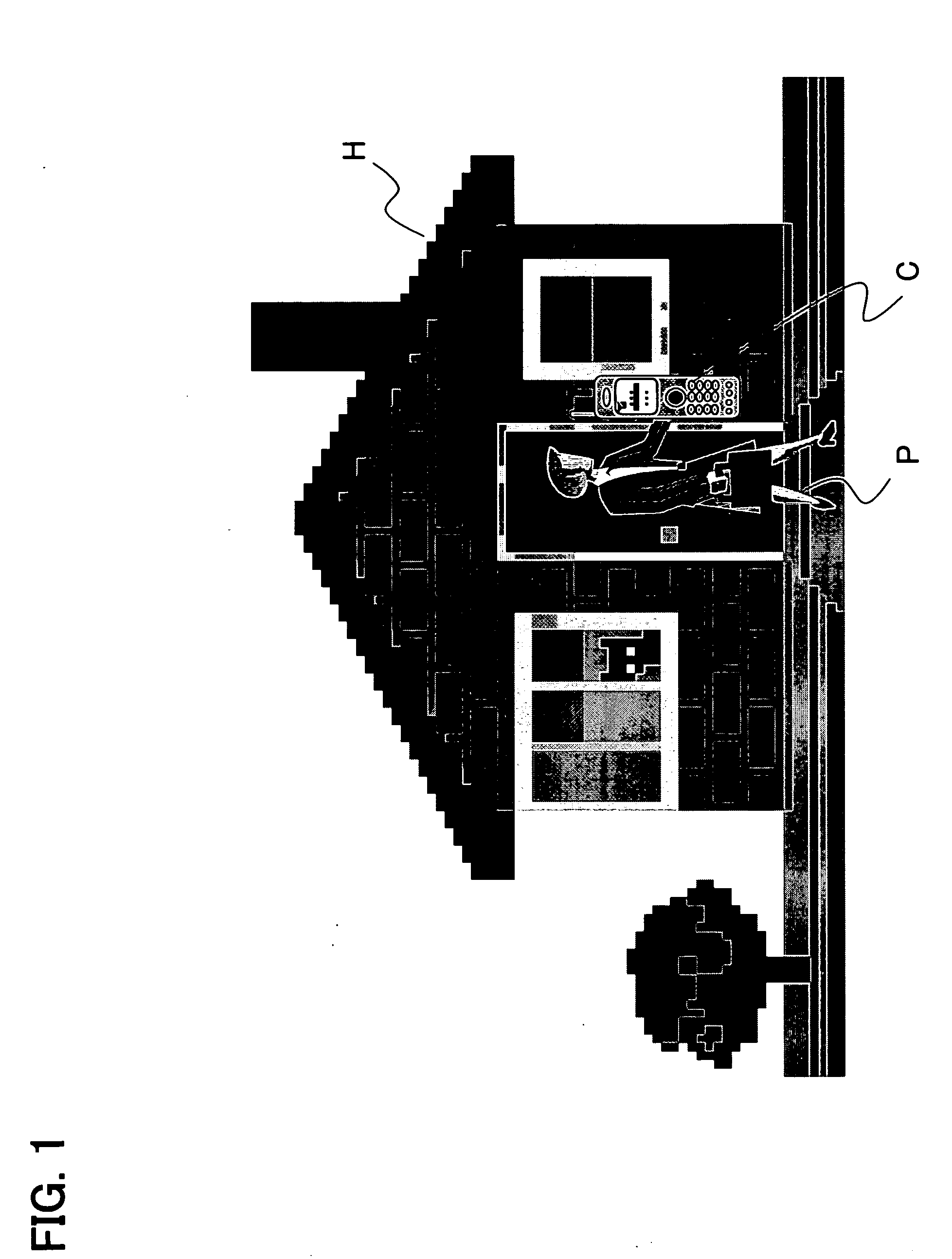
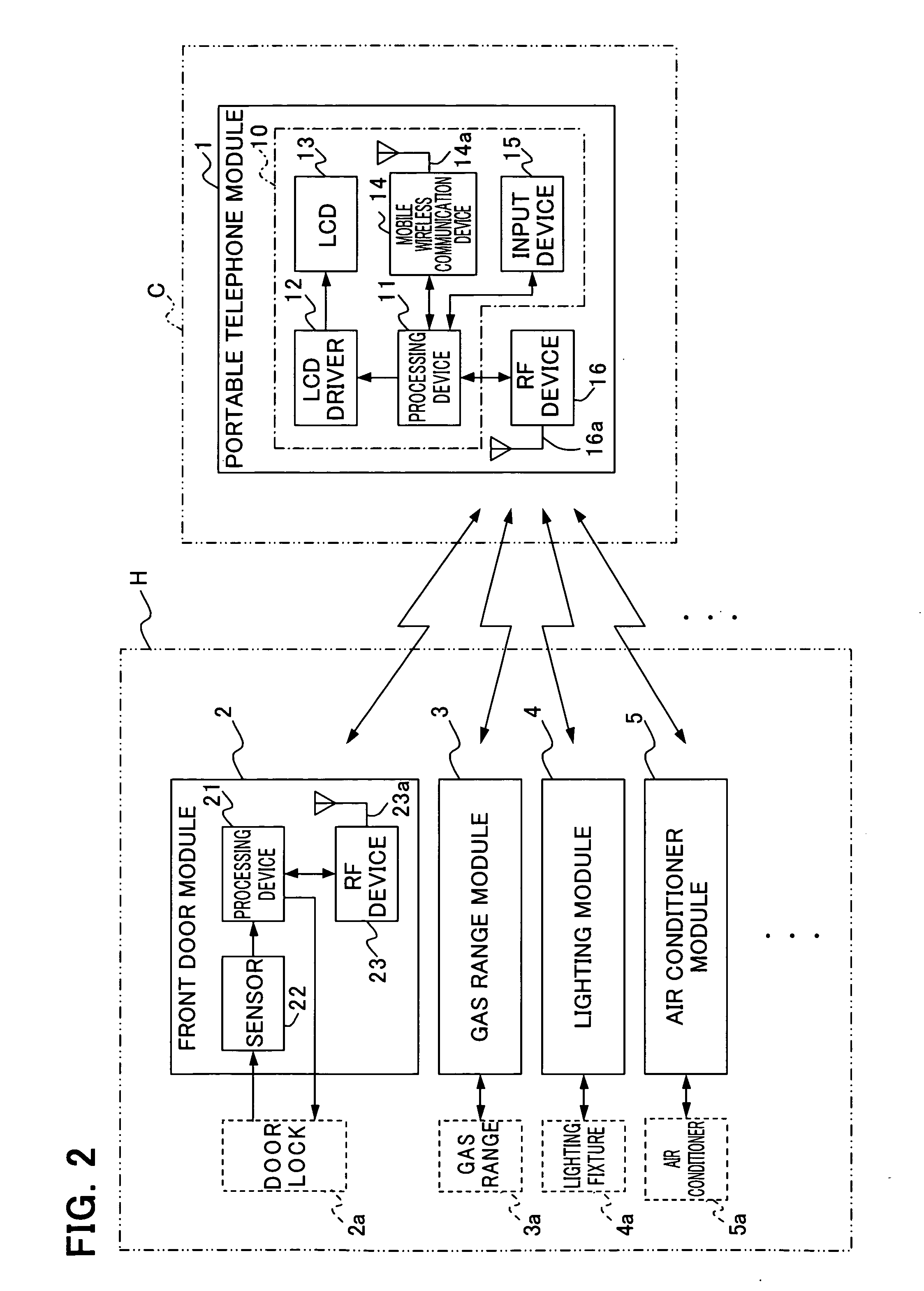
A security system capable of safely performing home device state check or operation. In the security system, a mobile telephone module of a mobile telephone transmits M-series data (call signal) to home device modules provided in home devices such as a door lock and home electric appliances. In response to this call, the home device module returns a home device ID to the mobile telephone module. The mobile telephone module authenticates the home device module according to the home device ID and after authentication, returns a mobile telephone ID and state check or operation command to the home device module. The home device module authenticates the mobile telephone module according to the mobile telephone ID. When this mutual authentication is complete, the home device module performs the home device state check or operation according to the command and returns the result to the mobile telephone module. Thus, the state check or operation is performed after mutual authentication and it is possible to prevent an unauthorized access of a third person.
Owner:FUJINOMAKI RYUJIN
System and method for hiding and extracting message data in multimedia data
The present invention provides a data hiding method of hiding media data in message data and a data extraction method of extracting the hidden data wherein message data is dispersively hidden in media data such as an image or sound to prevent a third person from modifying the message data easily. More specifically, the present invention relates to a data hiding method in which media data is expressed as a media array while message data is expressed as a message array so that the array elements of the message array can be dispersively hidden in the message array based on a state values specifying a particular array element of the media array, comprising the steps of: (a) determining the j-th (j> / =0) state value Sj; (b) determining (j+1)-th state value Sj+1 based on the j-th state value, the array element of the media array indicated by the j-th state value, and the array element of the message array; and (c) hiding data with respect to the array element of the media array indicated by the (j+1)-th state value Sj+1.
Owner:IBM CORP
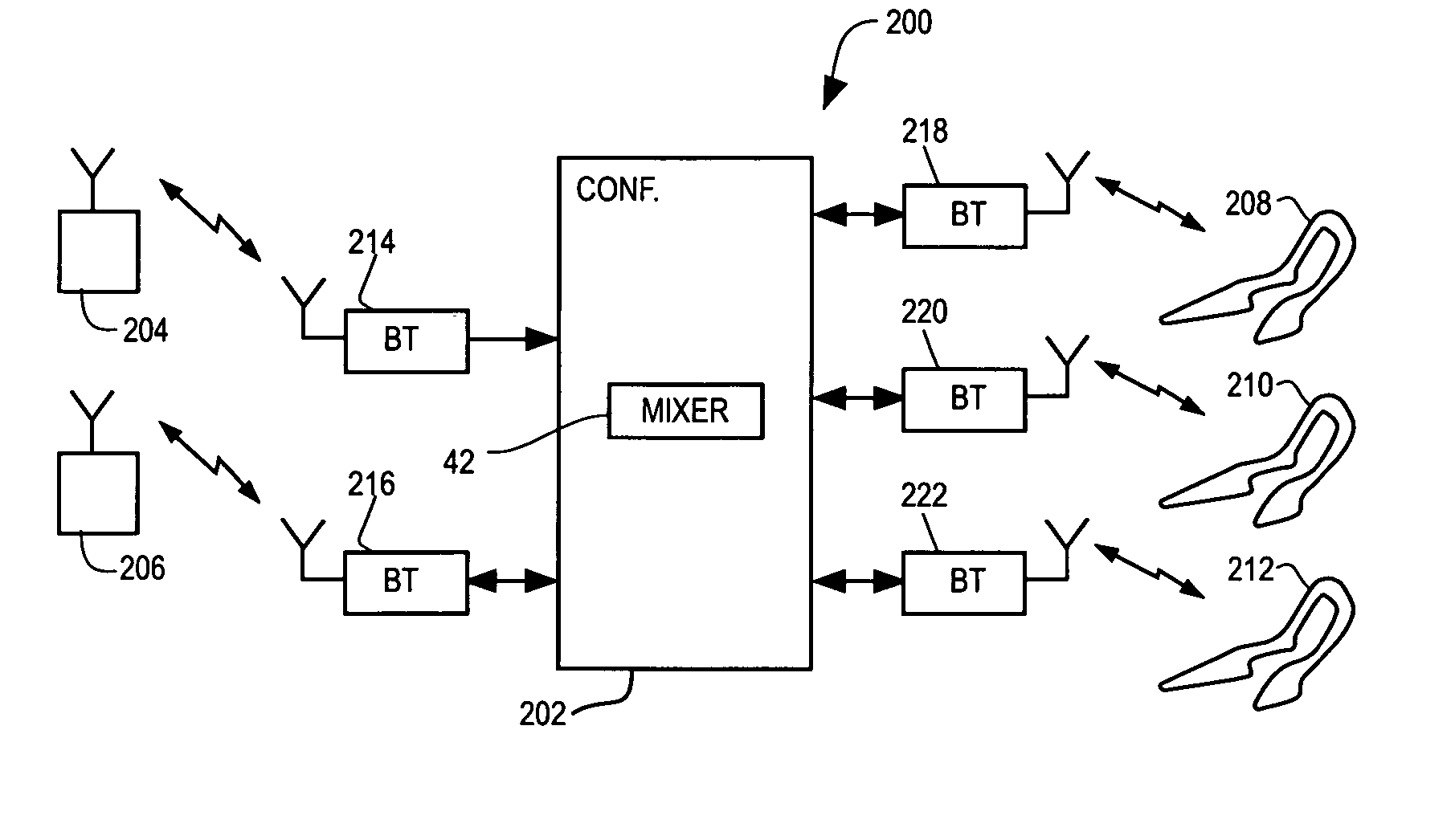
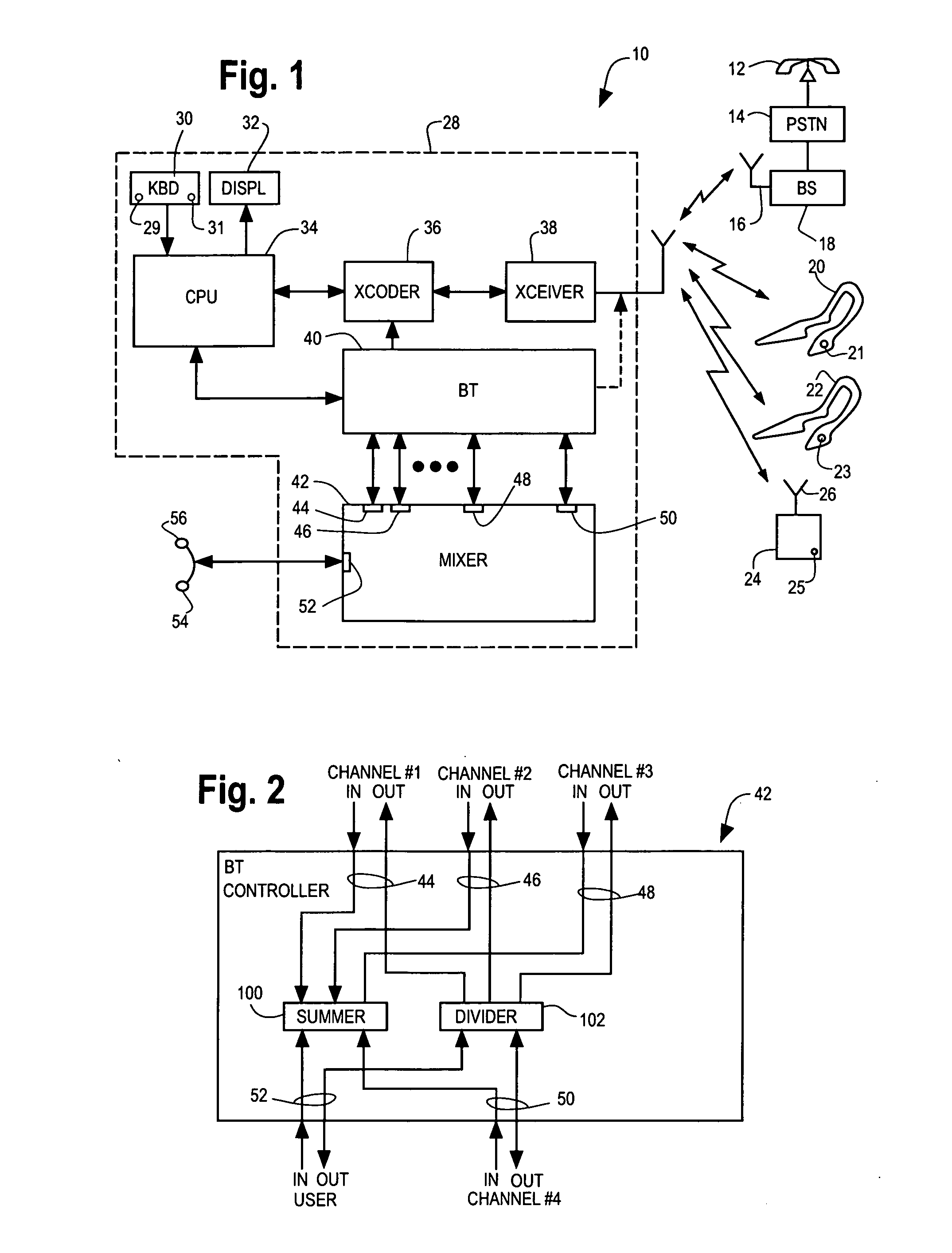
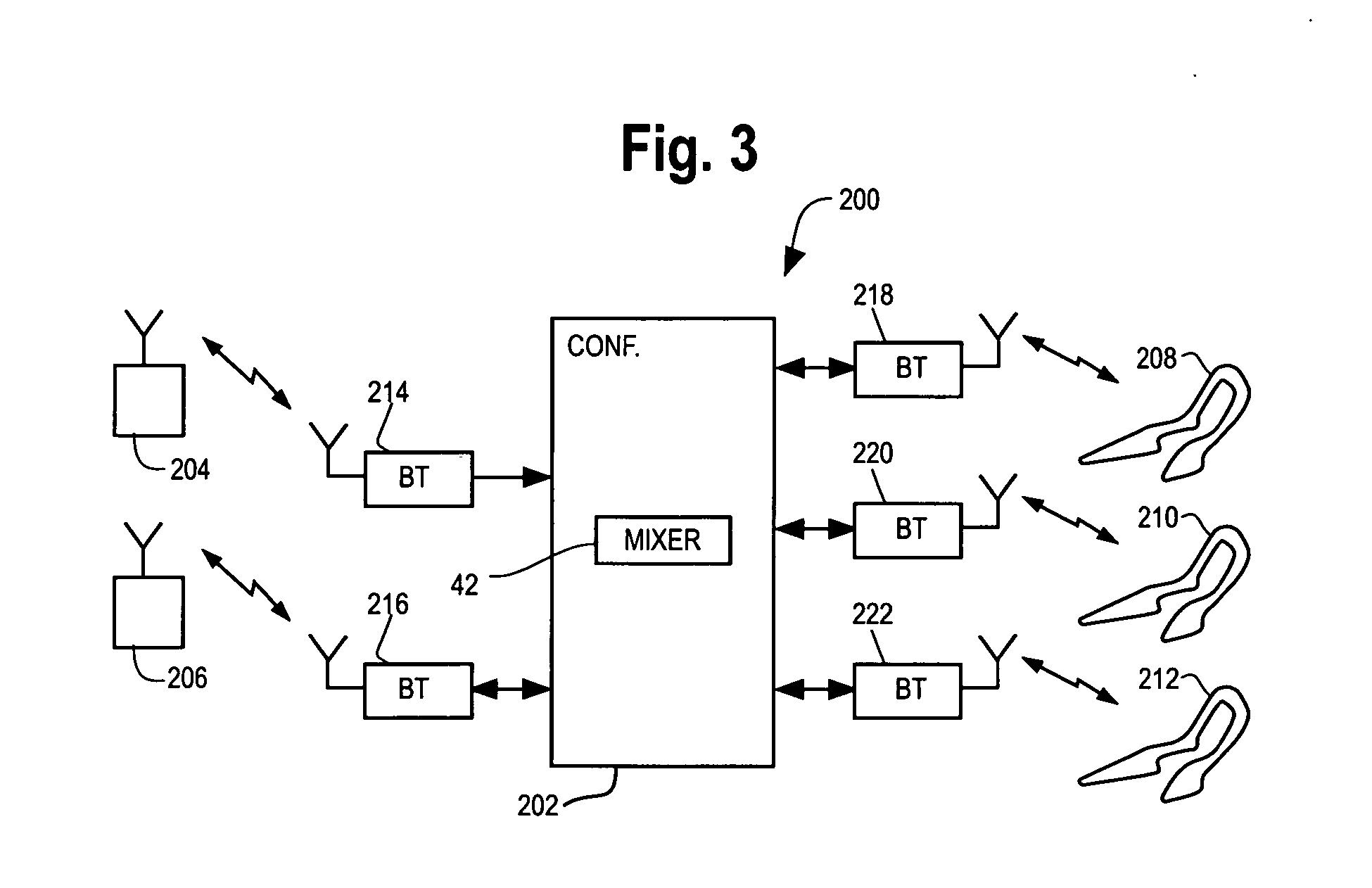
Mobile conferencing and audio sharing technology
A method and apparatus is provided for setting up a voice conference call or sharing audio content (e.g. music, news, voice / phone call). The method in respect to voice conferencing includes the steps of providing an audio mixer that receives an audio input from each of at least three audio interfaces of the conference call, mixes the audio inputs and provides an equalized audio output to each of the at least three audio interfaces, providing a first local wireless interface between a first audio interface of the at least three audio interfaces and a wireless headset of a first person of the conference call, providing a second local interface between a second audio interface of the at least three audio interfaces and a second person of the conference call and coupling a third audio interface of the at least three audio interfaces to a third party of the conference call through a base station of a cellular network, wherein the communication paths to the first, second and third persons are all different. The method in respect to sharing audio content is similar to voice conferencing, except the communication path between the audio interface and person is in one direction (i.e. no voice path), and if stereo audio is required the audio information is split into a left-ear and right-ear channel.
Owner:CALLPOD
Method and apparatus for controlling objects of a user interface
InactiveUS20110289423A1Input/output for user-computer interactionDigital data protectionHuman–computer interactionVisual perception
A method and apparatus for controlling objects of a user interface (UI) are provided. The method and apparatus simultaneously hide and move a selected object to a bottom of a UI when the object is encrypted, thereby not visually exposing the encrypted object to a third person, displaying, through the UI the encrypted object on a predetermined screen, directory or folder, and rearranging unselected objects to fill a space created when the selected object is hidden and moved.
Owner:SAMSUNG ELECTRONICS CO LTD
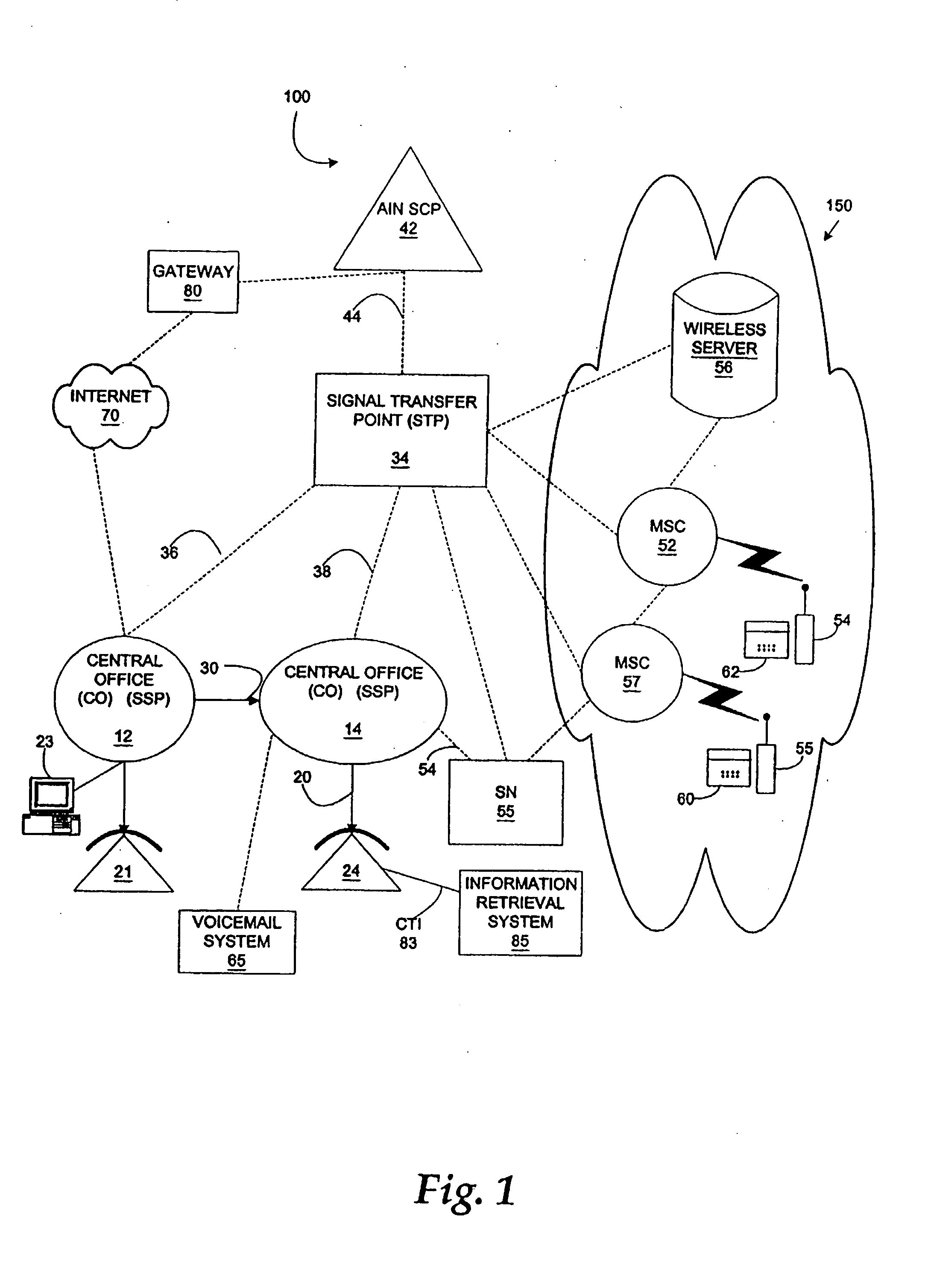
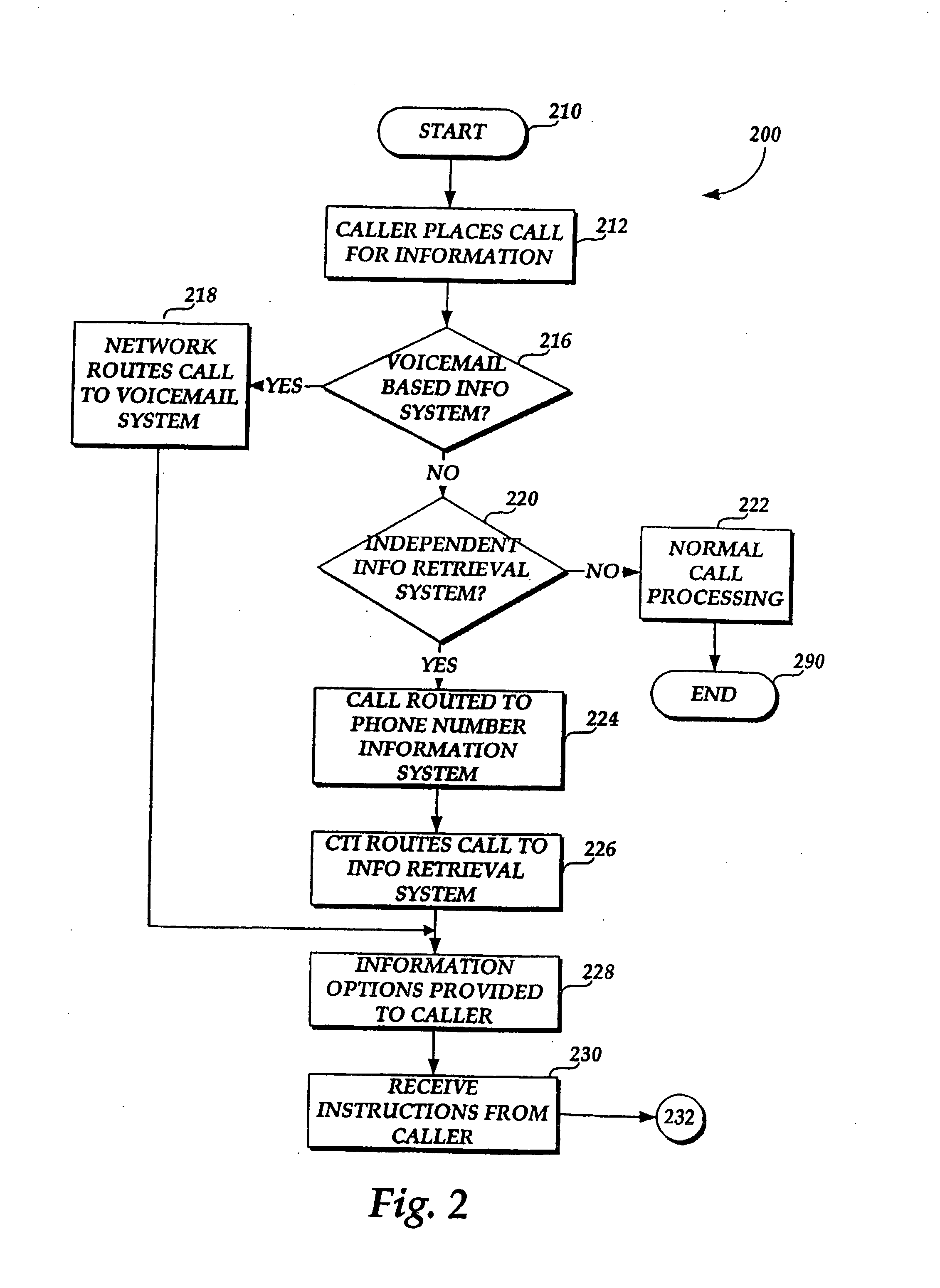
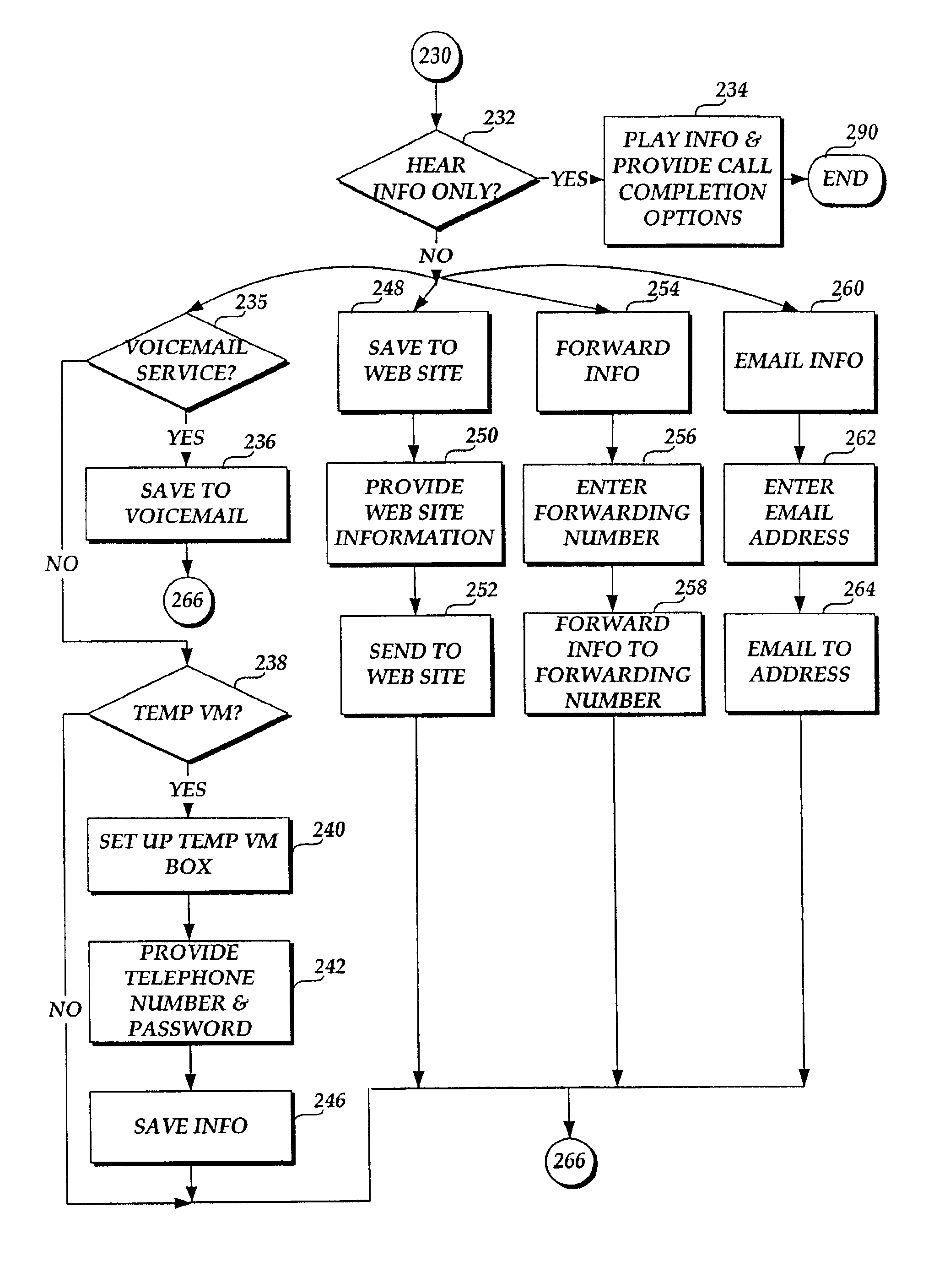
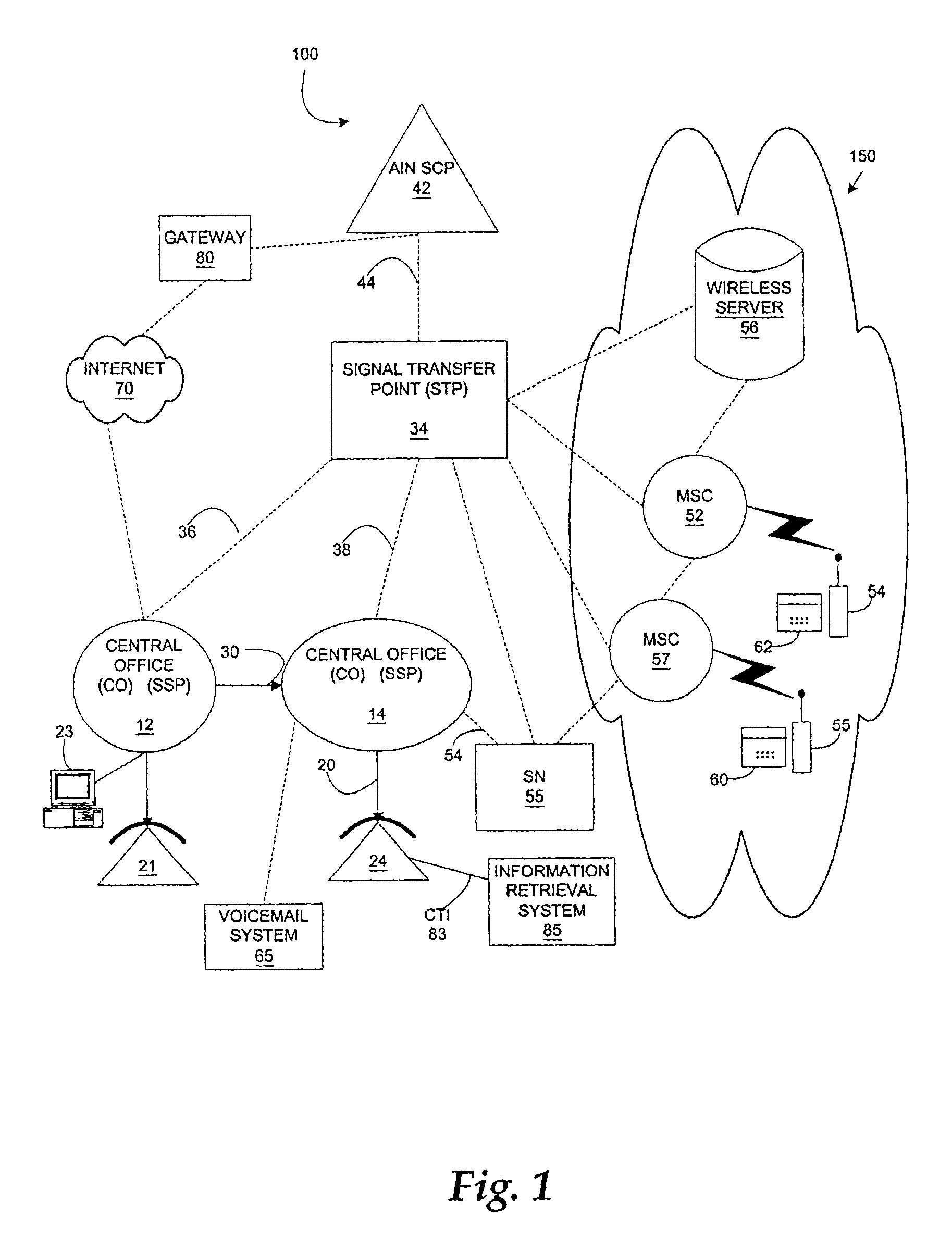
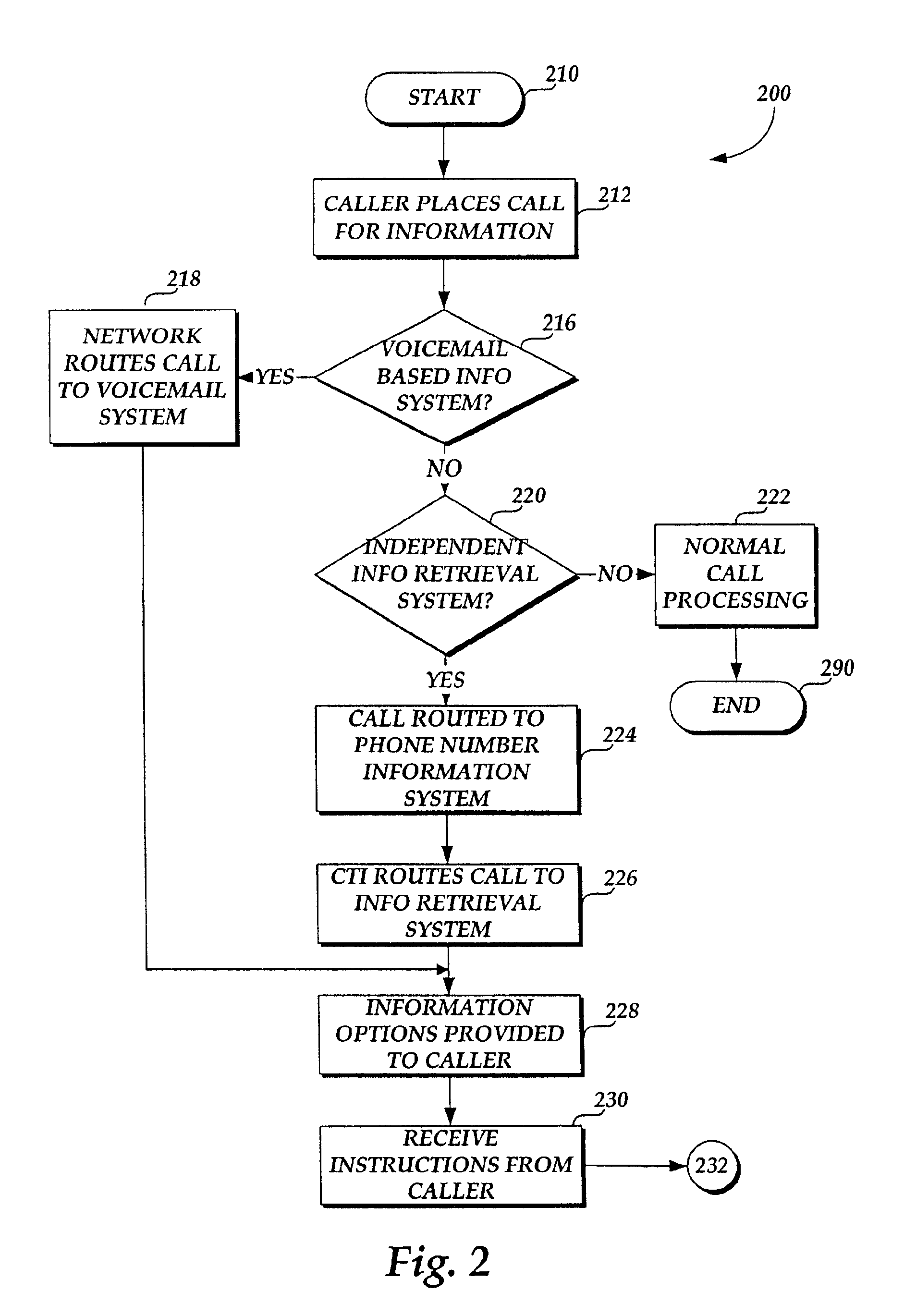
Saving information from information retrieval systems
InactiveUS20060171511A1Special service for subscribersAutomatic call-answering/message-recording/conversation-recordingReceiptThird person
A method and system for allowing a calling party to save information obtained from an information retrieval system. The caller may select options to save the information to a memory location, e.g., the caller's own network-based voice mail system or a temporary voice mailbox provided for the caller by the information provider, from which the caller can subsequently retrieve and review the information. The information may be saved to an Internet-based website from which the caller may subsequently retrieve the information. The information may be forwarded to a separate telephone directory number for receipt by a third person or for storing on a remote voice mail system. Additionally, the information may be electronically mailed to the caller's electronic mail address for subsequent retrieval. Discussions with a live attendant may be recorded and stored, as audio files or as converted to text, for access by or delivery to the caller.
Owner:BELLSOUTH INTPROP COR
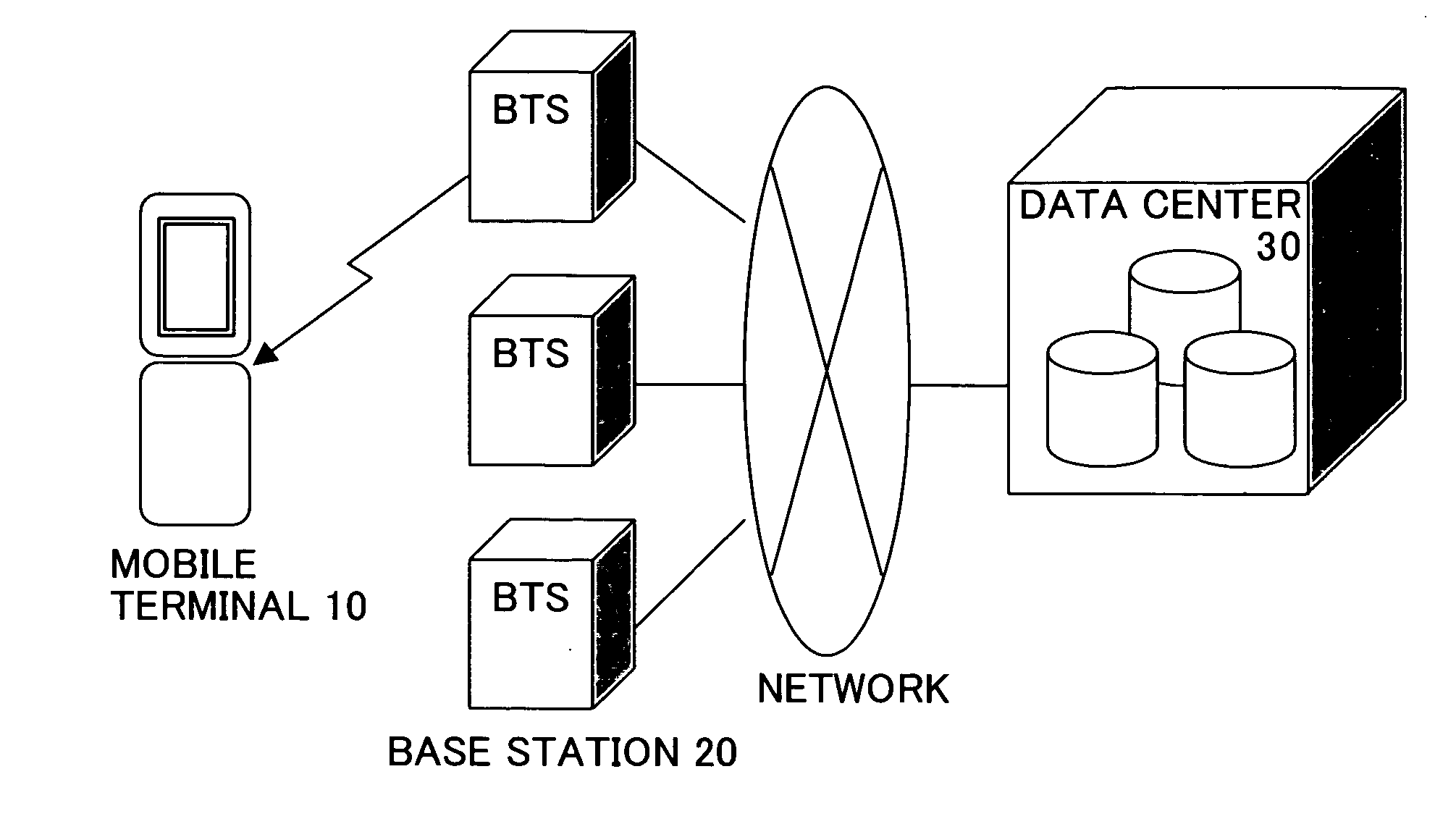
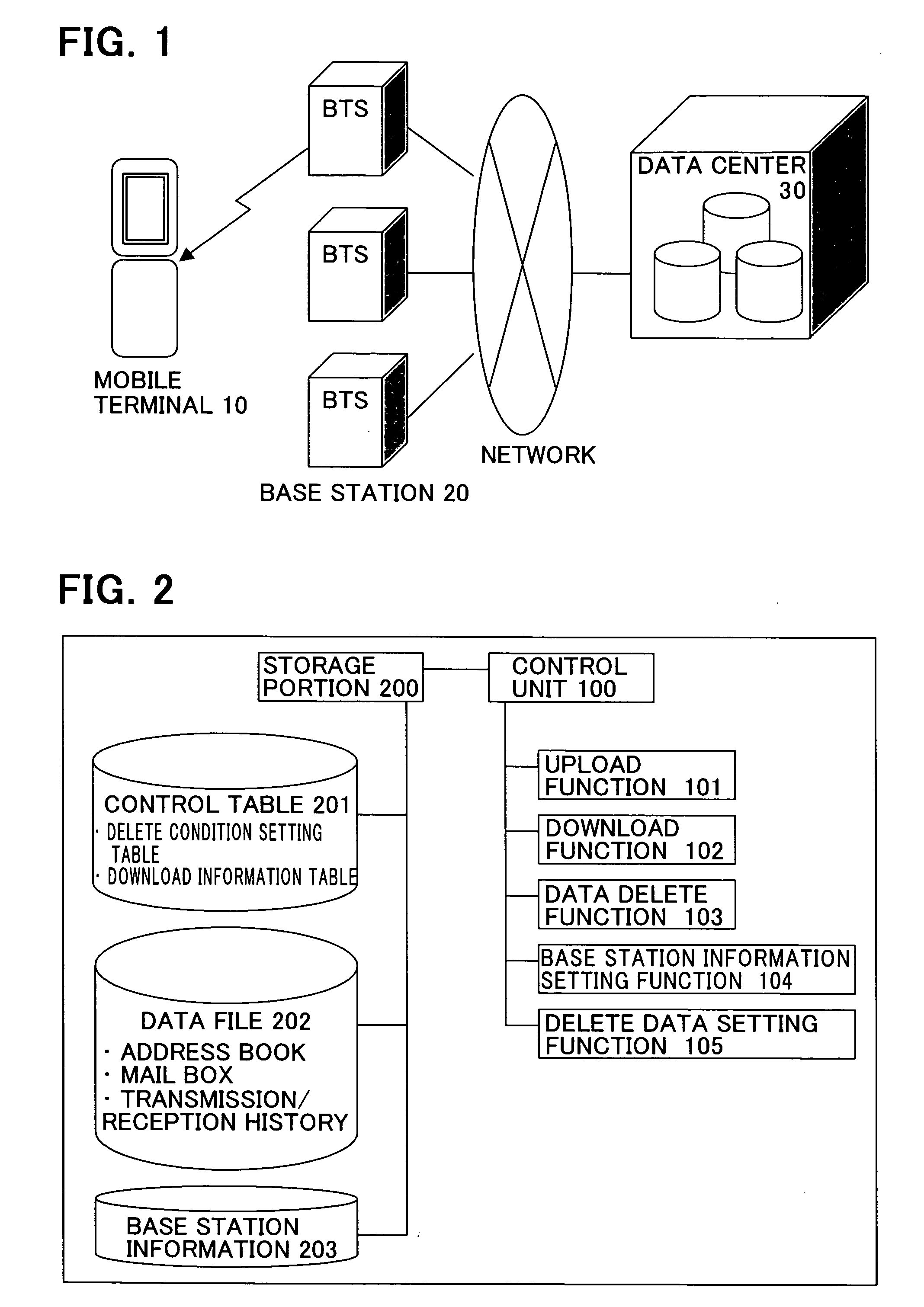
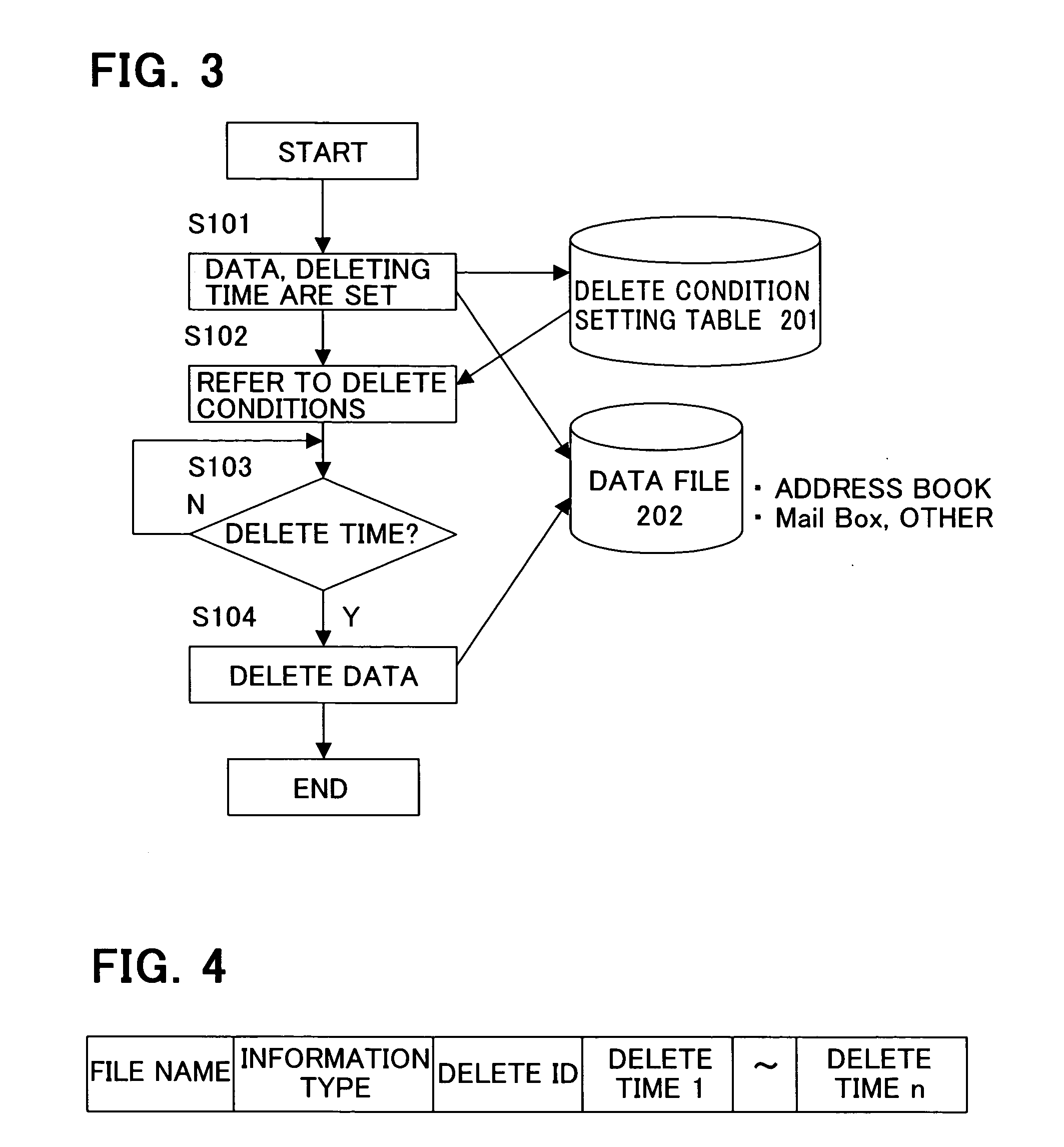
Mobile terminal with data delete function
InactiveUS20070077925A1Reduce riskPrevent leakageUnauthorised/fraudulent call preventionSpecial service for subscribersComputer scienceInformation leakage
To prevent information leakage due to the loss of a mobile terminal, when various delete conditions that are set in advance in the mobile terminal are satisfied, data is deleted by control performed by the mobile terminal itself. By allowing the mobile terminal to perform control of deleting data instead of allowing an outside system such as a network to perform the control of deleting the data, it is possible to reduce the risk that the information leaks out to a third person when the network cannot perform the control or during a period of time between when the mobile terminal is lost and when the loss of the mobile terminal is noticed. Moreover, by saving the data to be deleted in another computer device by uploading the data onto, for example, a server on the network so that the data can be recovered, leakage of the information from the mobile terminal can be prevented without hampering the convenience for the user.
Owner:FUJITSU LTD
Saving information from information retrieval systems
InactiveUS6888930B1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersTelecommunications networkEmail address
A method and system are provided for allowing a calling party to save for subsequent retrieval and review information obtained from an information retrieval system. A calling party places a call to either an interactive voice information retrieval system or to a telephone directory number that is associated with a telecommunications network-based voice mail system that provides interactive information to calling parties. The call is either routed directly to the general information retrieval system or via the telecommunications network to the network-based voice mail system. Once the calling party receives desired information, the calling party may select a number of options to save the information to a memory location from which the calling party may subsequently retrieve and review the information. The information may be sent to and stored at the calling party's own network-based voice mail system, or the calling party may have the information sent to and stored at a temporary voice mail box provided by the information provider. The information may be saved to an Internet-based website from which the calling party may subsequently retrieve the information. The information may be forwarded to a separate telephone directory number for receipt by a third person or for storing on a remote voice mail system. Additionally, the information may be electronically mailed to the calling party's electronic mail address for subsequent retrieval.
Owner:AT&T INTPROP I L P
Wireless access control system and methods for intelligent door lock system
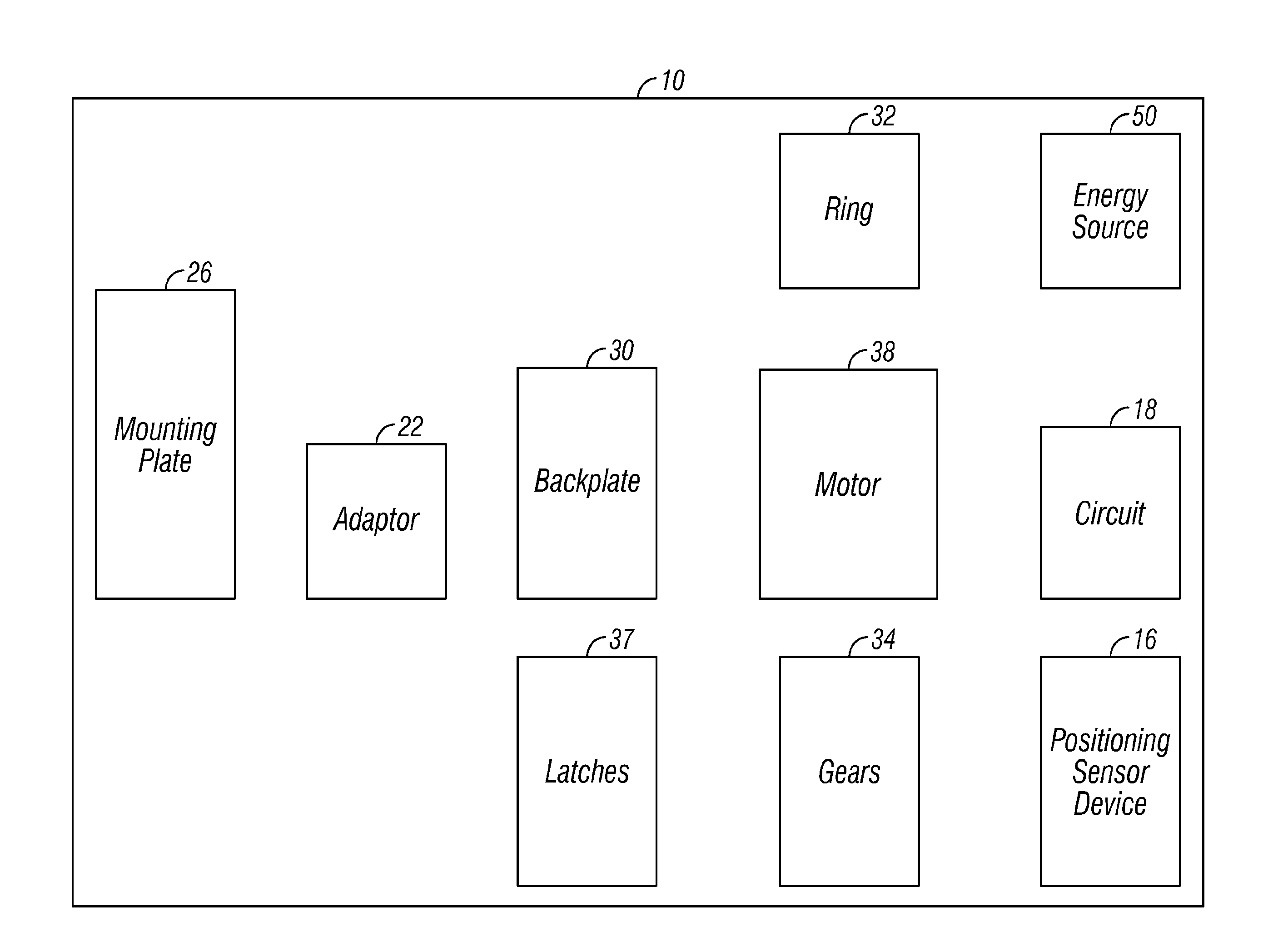
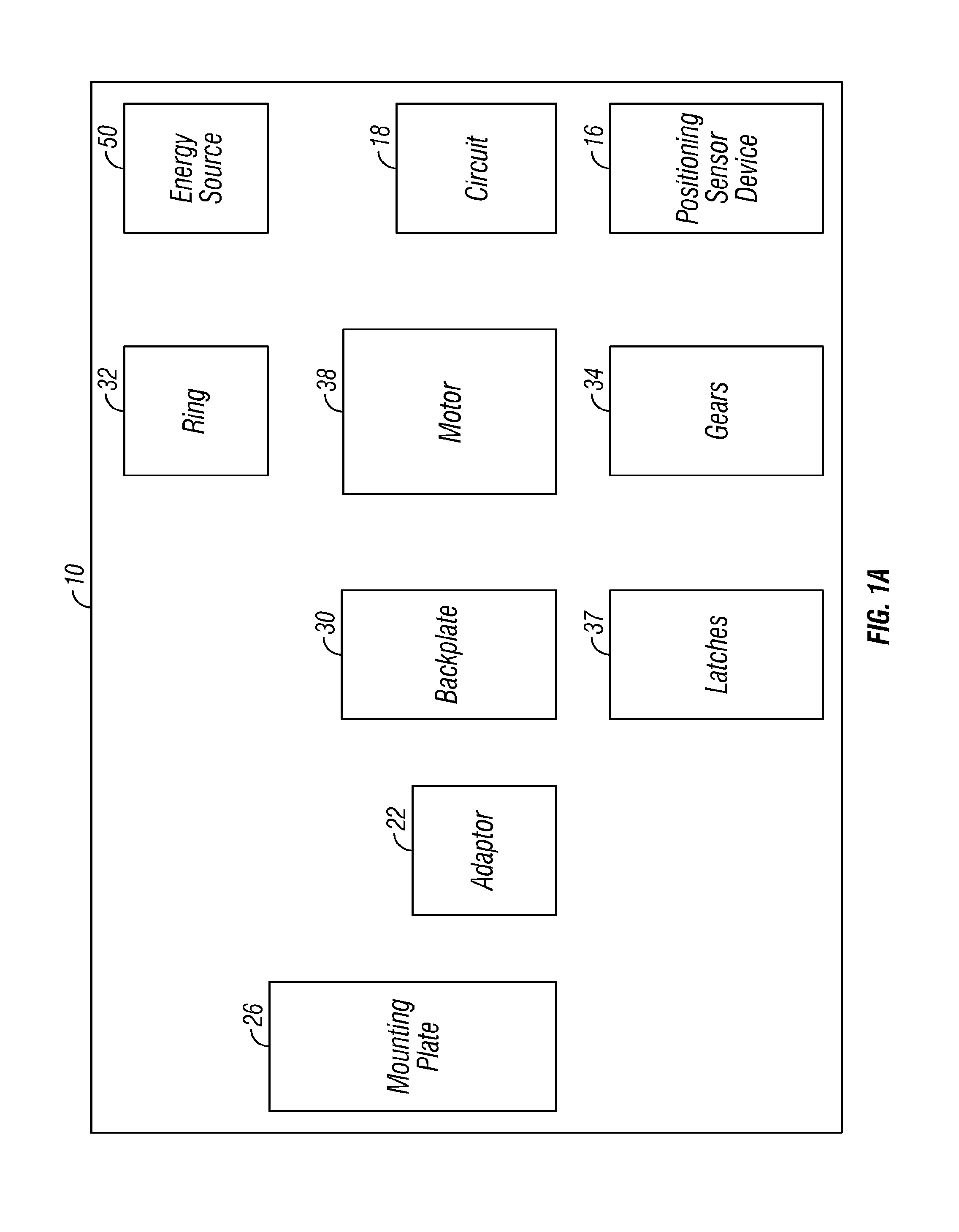
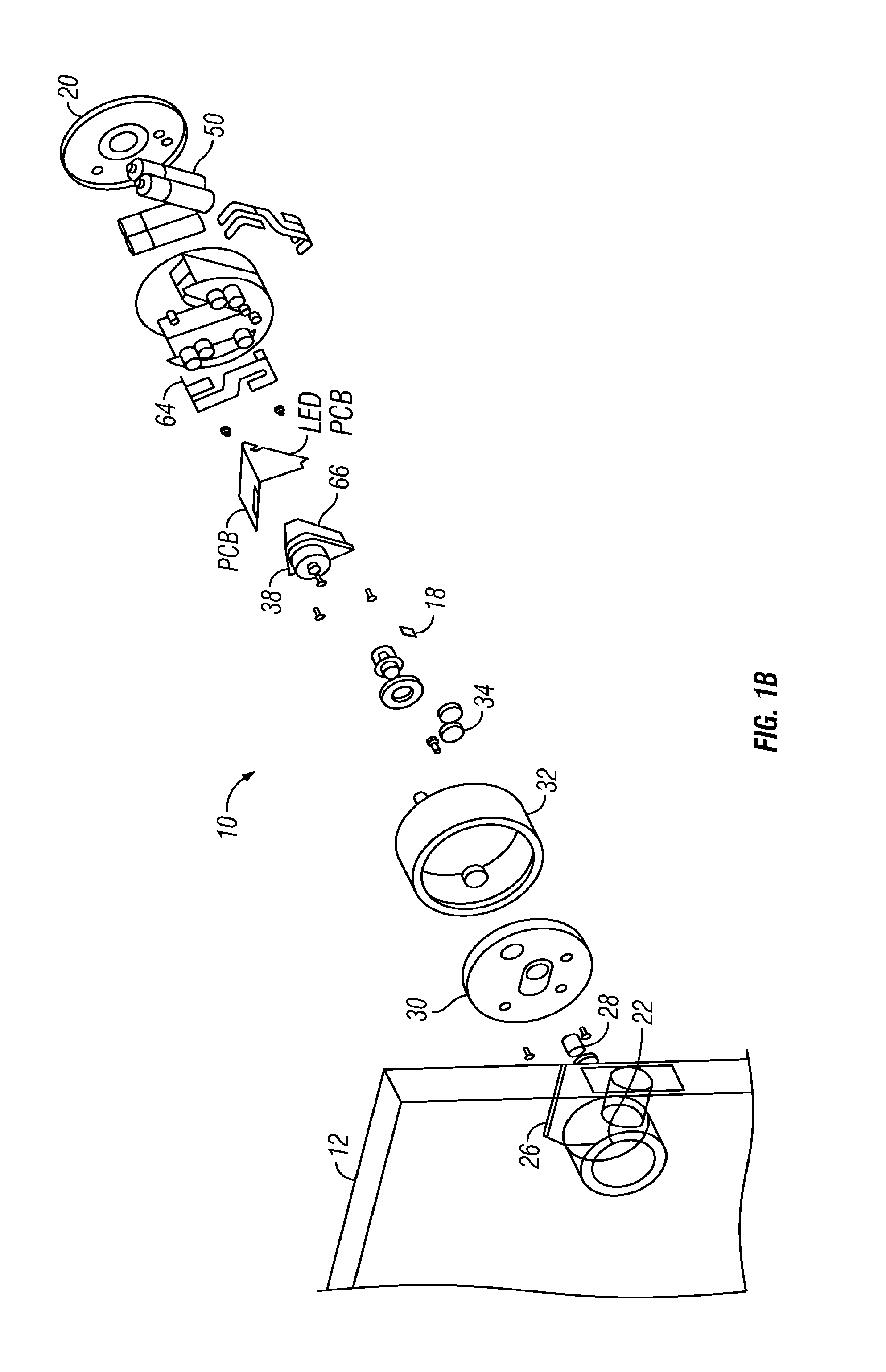
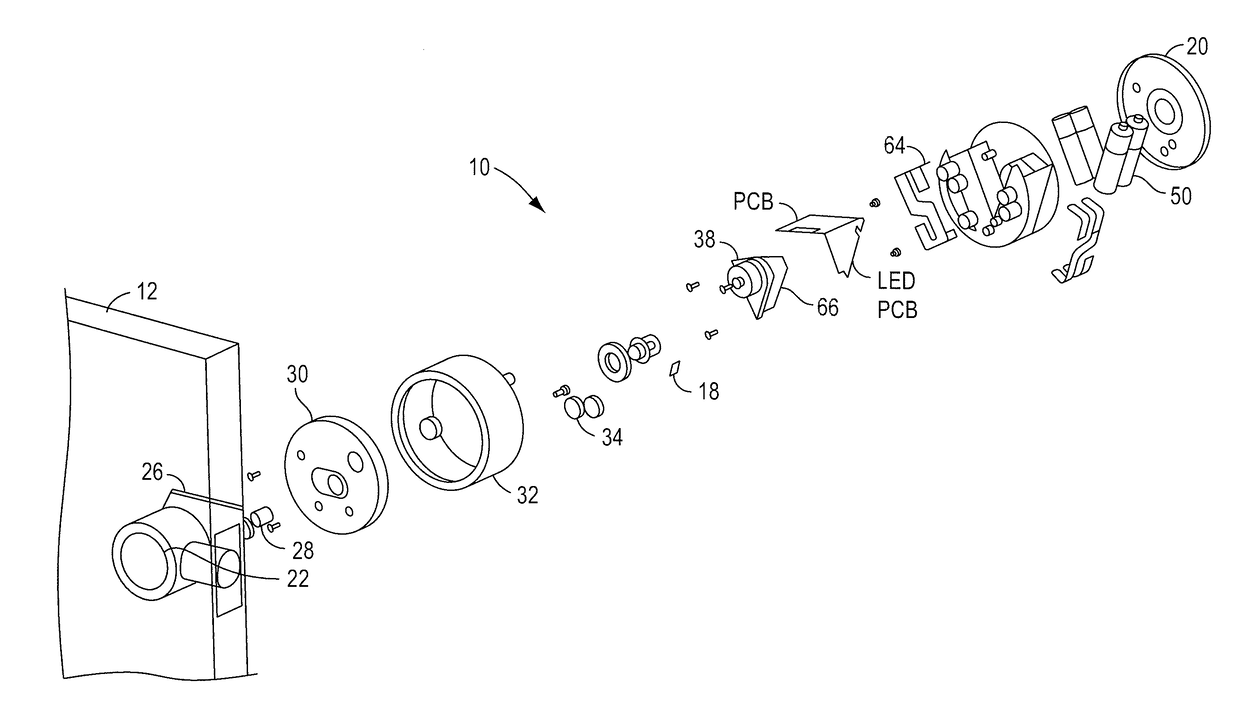
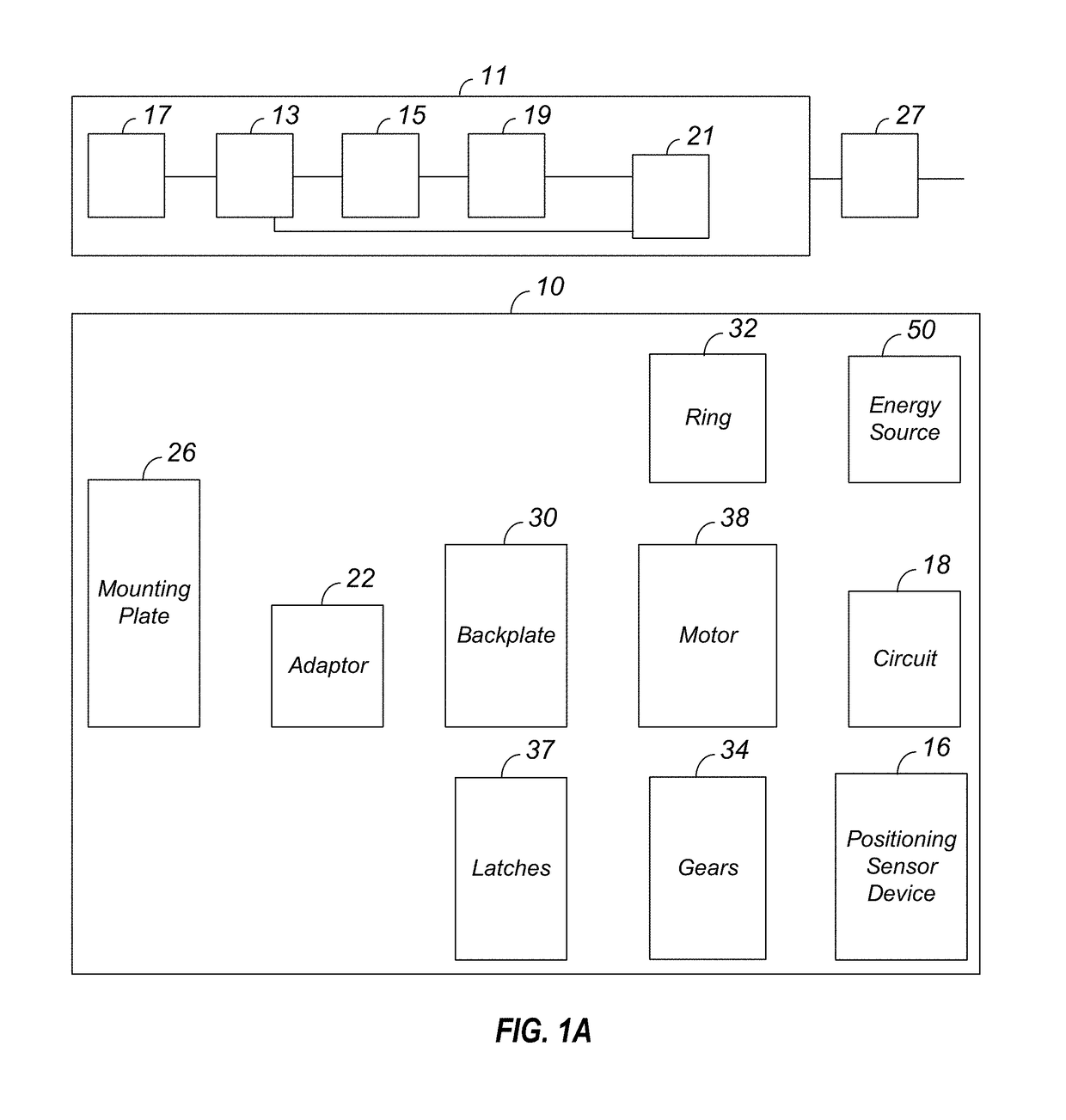
A wireless access control system to lock or unlock a first door at a dwelling of a user. A user remote access device transmits a first signal and a second signal. The user remote access device includes a vibration mode that provides an alert to the user of the remote access device. The user remote access device is configured to be in communication with an intelligent door lock system at the dwelling with the first door. The intelligent door lock system includes: a drive shaft, a circuit coupled to an engine configured to cause a rotation of the drive shaft, and an energy source coupled to the drive shaft, the user remote access device configured to provide the first signal to the intelligent lock system for locking or unlocking of the first lock, the intelligent door lock system configured to allow controlled access to the dwelling that includes an occupant of the dwelling as well as a designated third person granted access rights by the occupant. The user remote access device is configured to be in communication to a second lock at a vehicle of the user or at an office of the user. The user remote access device is configured to communicate with the second lock with the second signal to cause the second lock to lock or be unlocked. The remote access device has a controller for generating the first and second signals.
Owner:AUGUST HOME
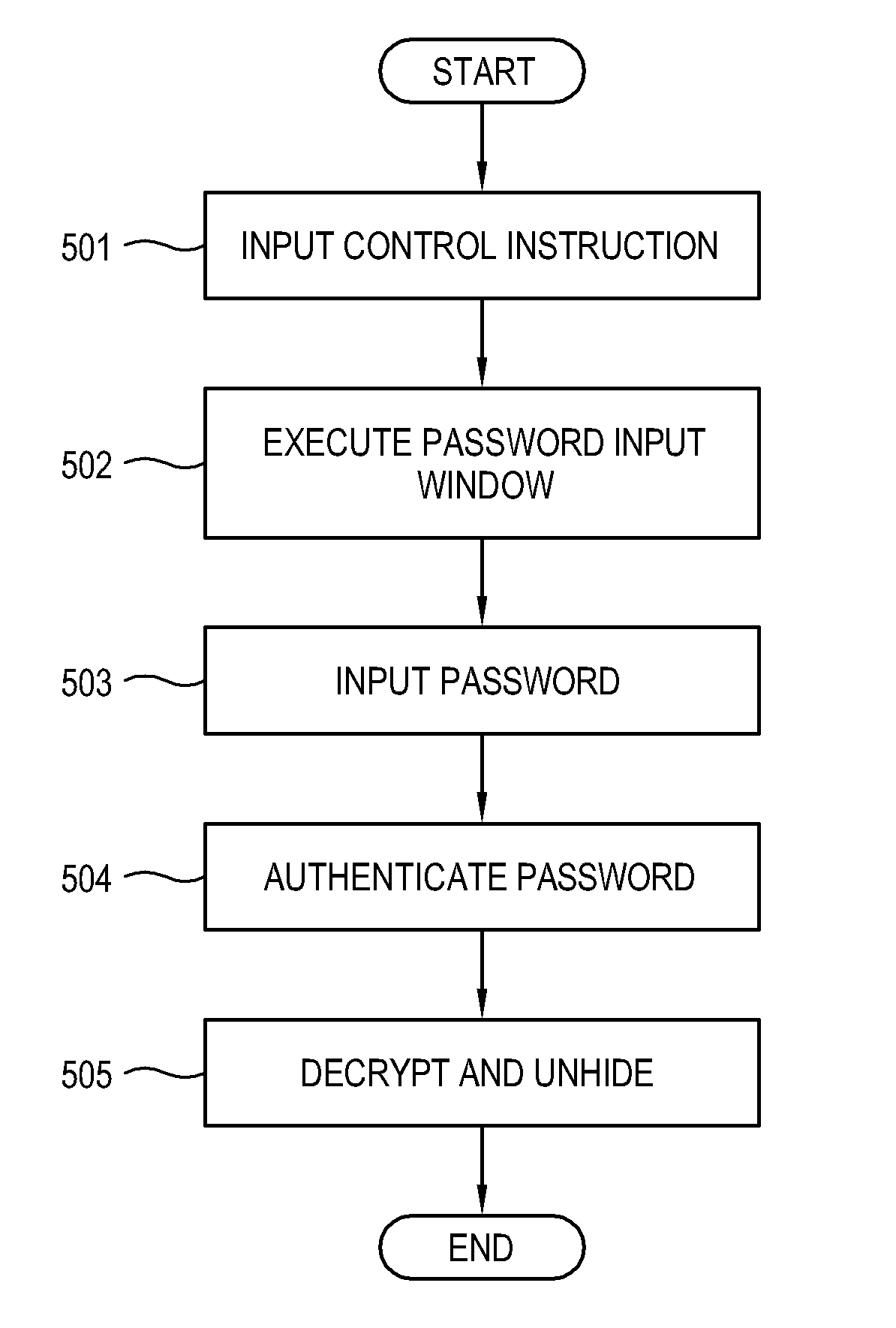
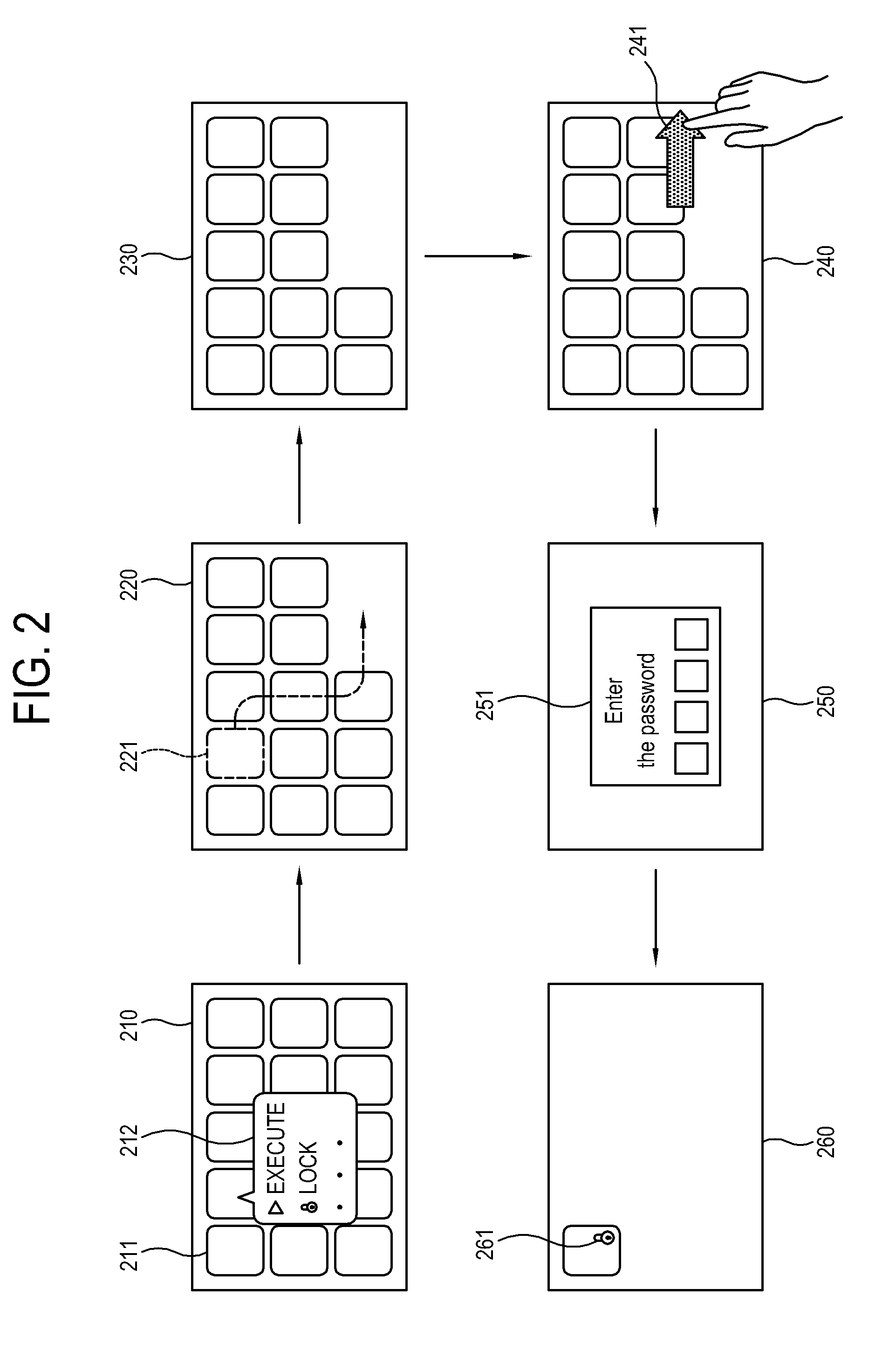
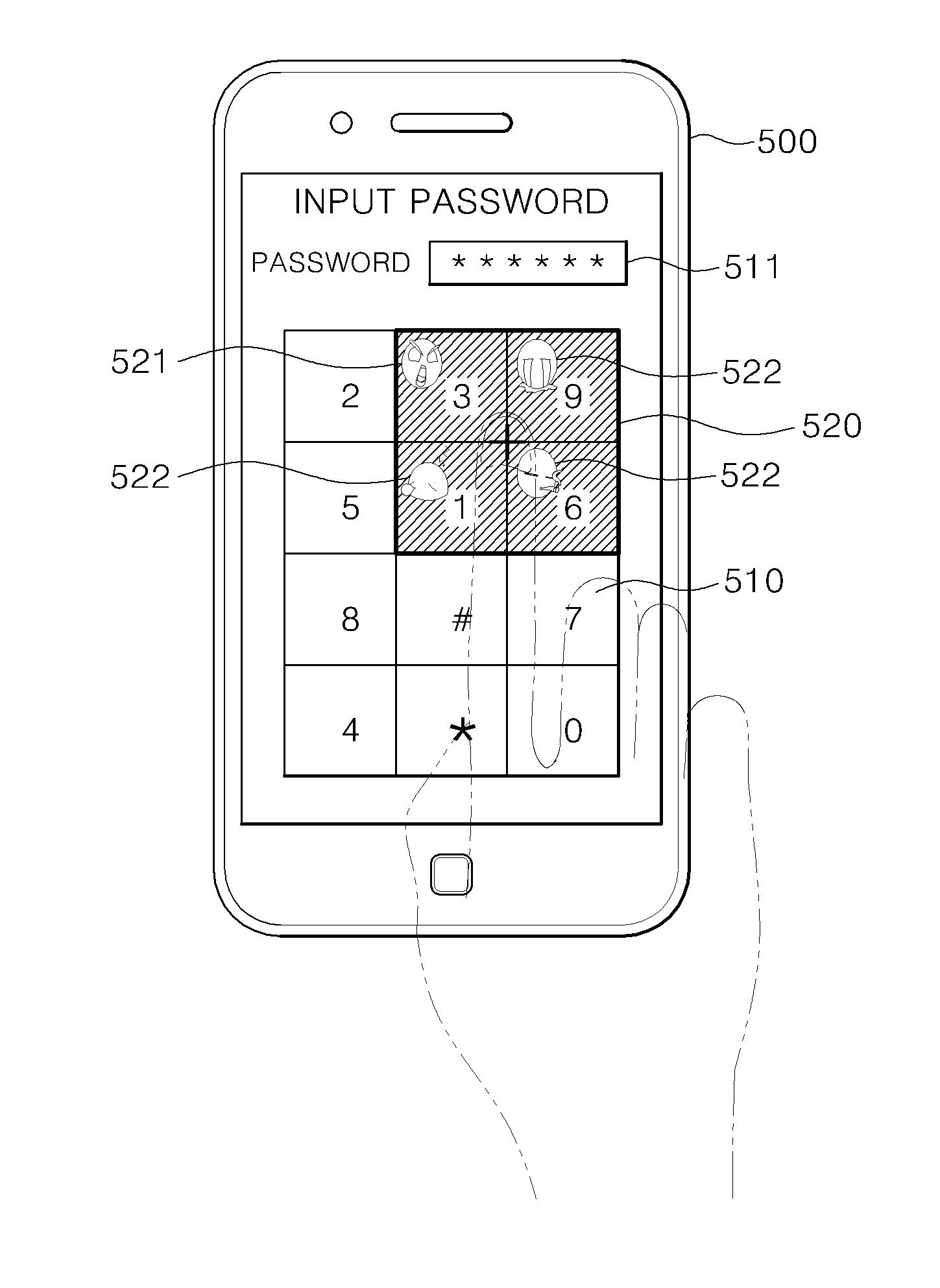
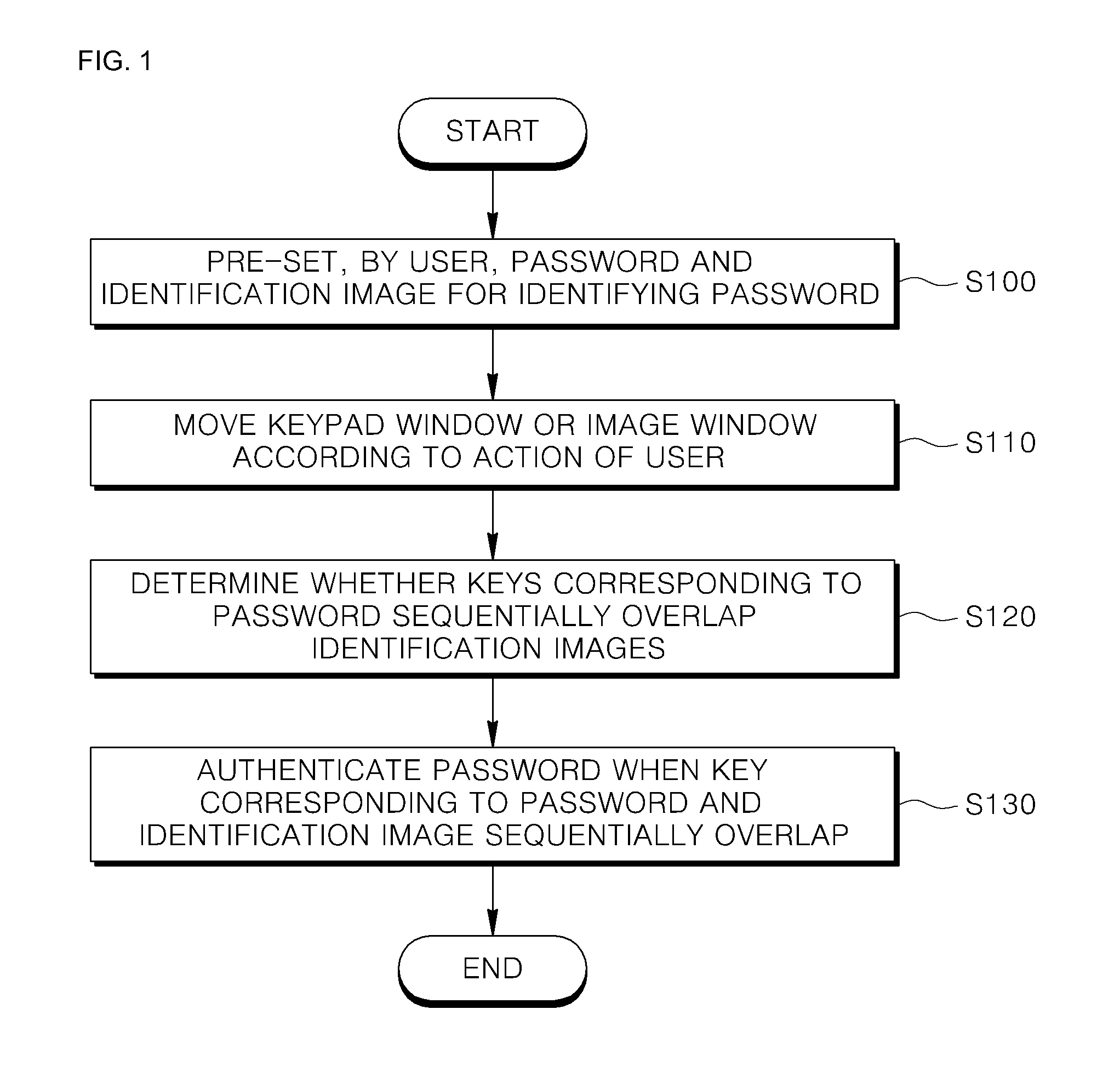
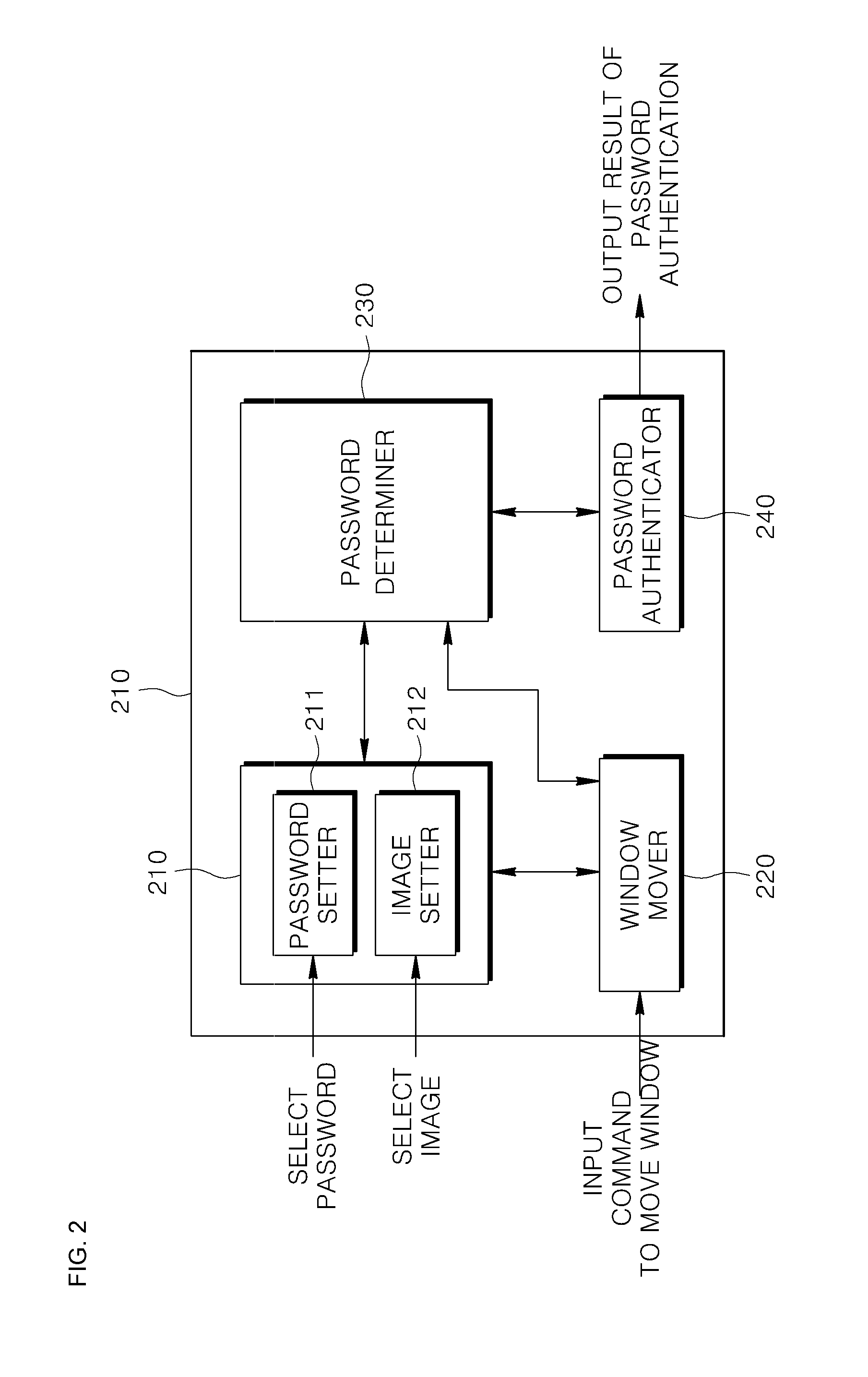
Method and apparatus for authenticating password of user terminal
ActiveUS20140201831A1Digital data processing detailsUser identity/authority verificationIndirect MethodThird person
Provided are method and apparatus for authenticating a password of a user terminal. The method includes: pre-setting, by a user, a password and an identification image for identifying the password; moving a keypad window or an image window realized on a screen of the user terminal according to an action of the user; determining, when a plurality of images included in the image window and a plurality of keys included in the keypad window sequentially overlap with each other, whether a plurality of keys and the identification image corresponding to the password sequentially overlap; and authenticating the password when the plurality of keys and the identification image corresponding to the password sequentially overlap. Accordingly, password information may be protected from a third person observation as the user inputs a pre-set password in an indirect method without having to directly input the pre-set password through an authentication interface.
Owner:FOUND OF SOONGSIL UNIV IND COOP
Close-contact counter-measure garment and method
A garment equipped with emitter, said emitter positioned on the garment such that the emitter can be a weapon, where said emitter can be fired by the wearer of the garment or fired remotely by a second person, an observer, or a third person, a monitor, an observer who is monitoring, where said emitter emits a means to mark an attacker by marking means, the position, identification of, and, alternatively, to immobilize or interfere with an attacker of the wearer of the garment. A method of defending an individual, including wearing by the individual a garment having contained upon, in, or proximal thereto a lethal, non-lethal, or less-than lethal weapon, and discharging or firing the weapon from the garment in the direction of an attacker.
Owner:RESNICK JOSEPH ANTHONY
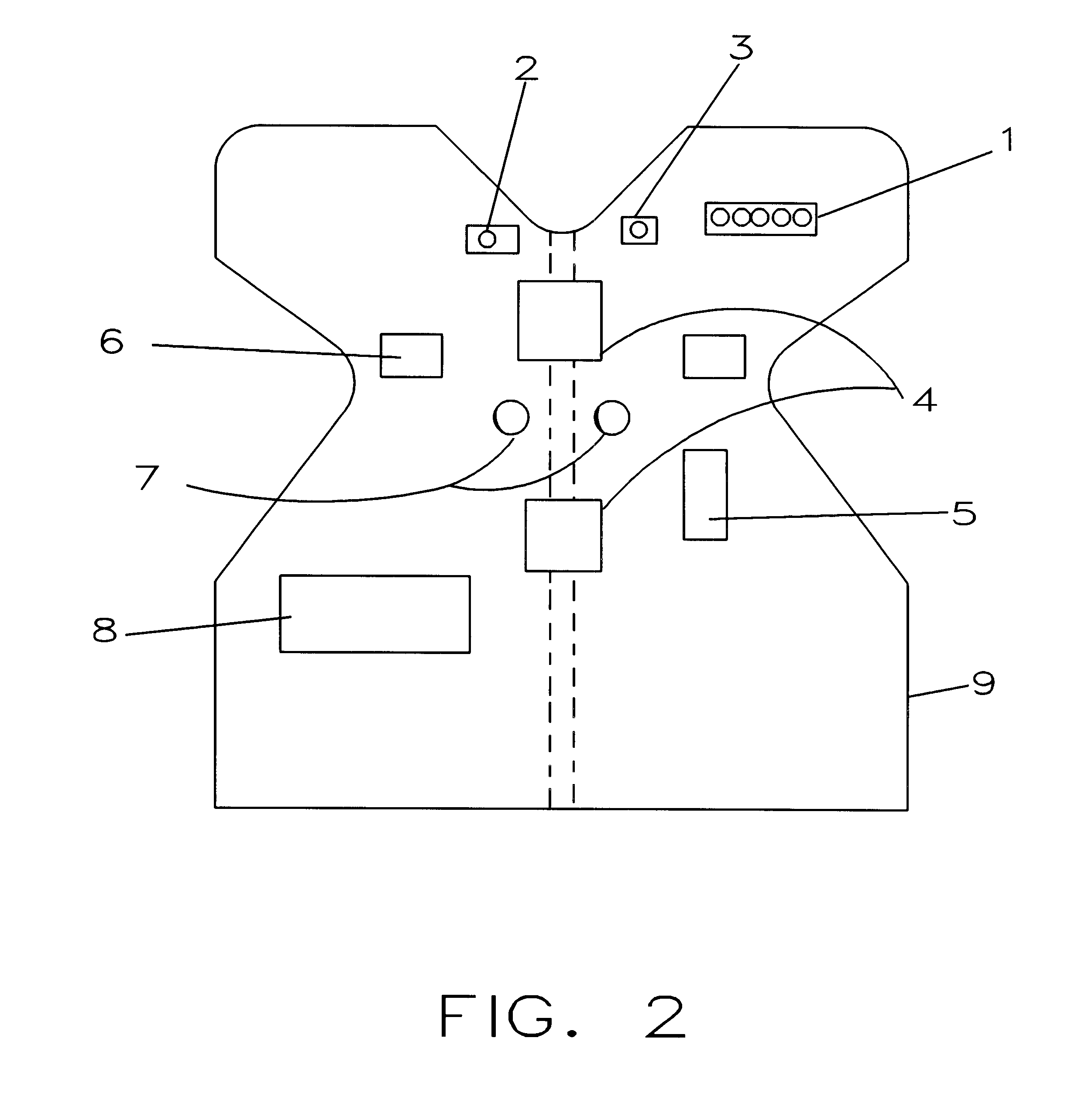
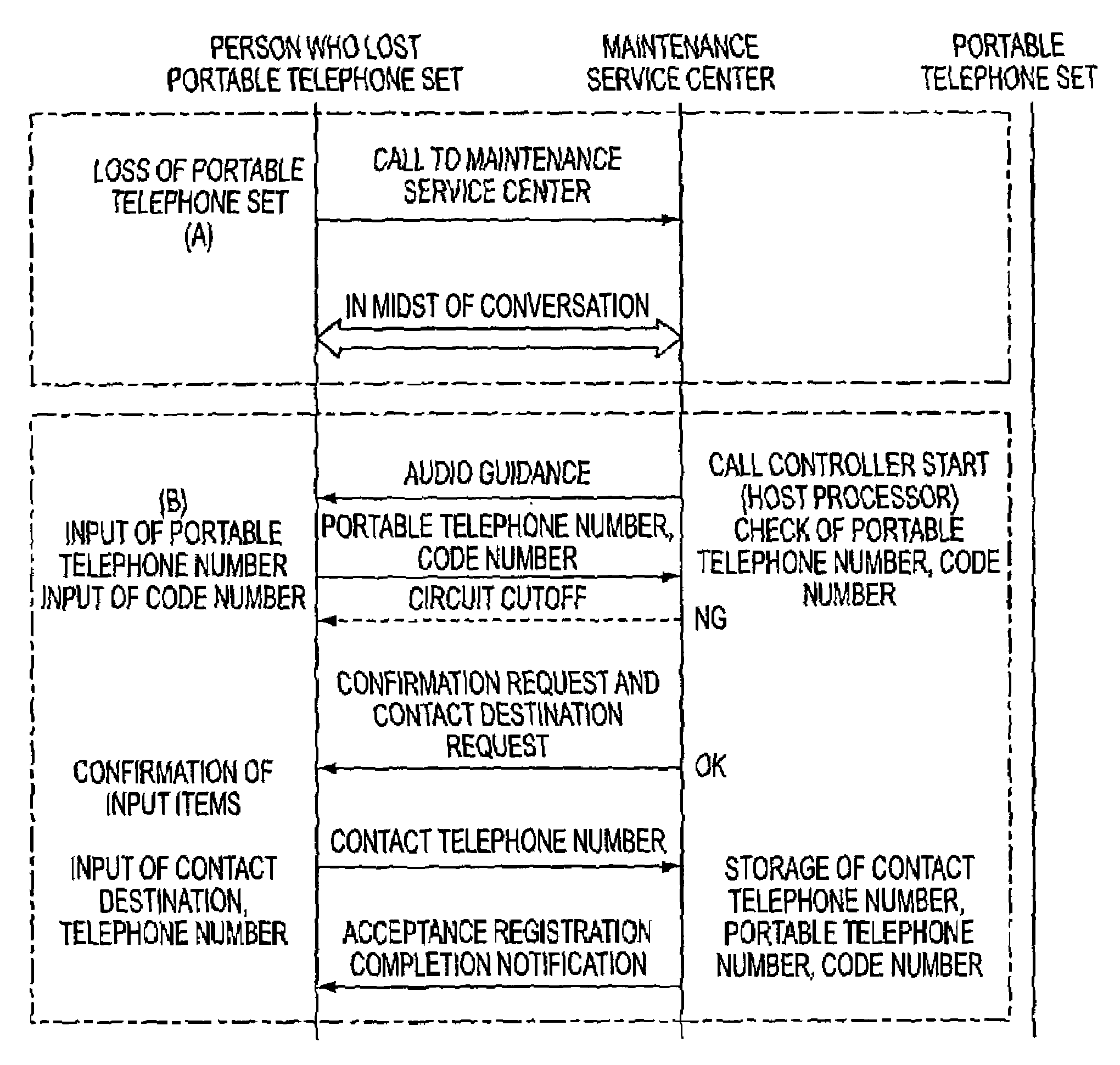
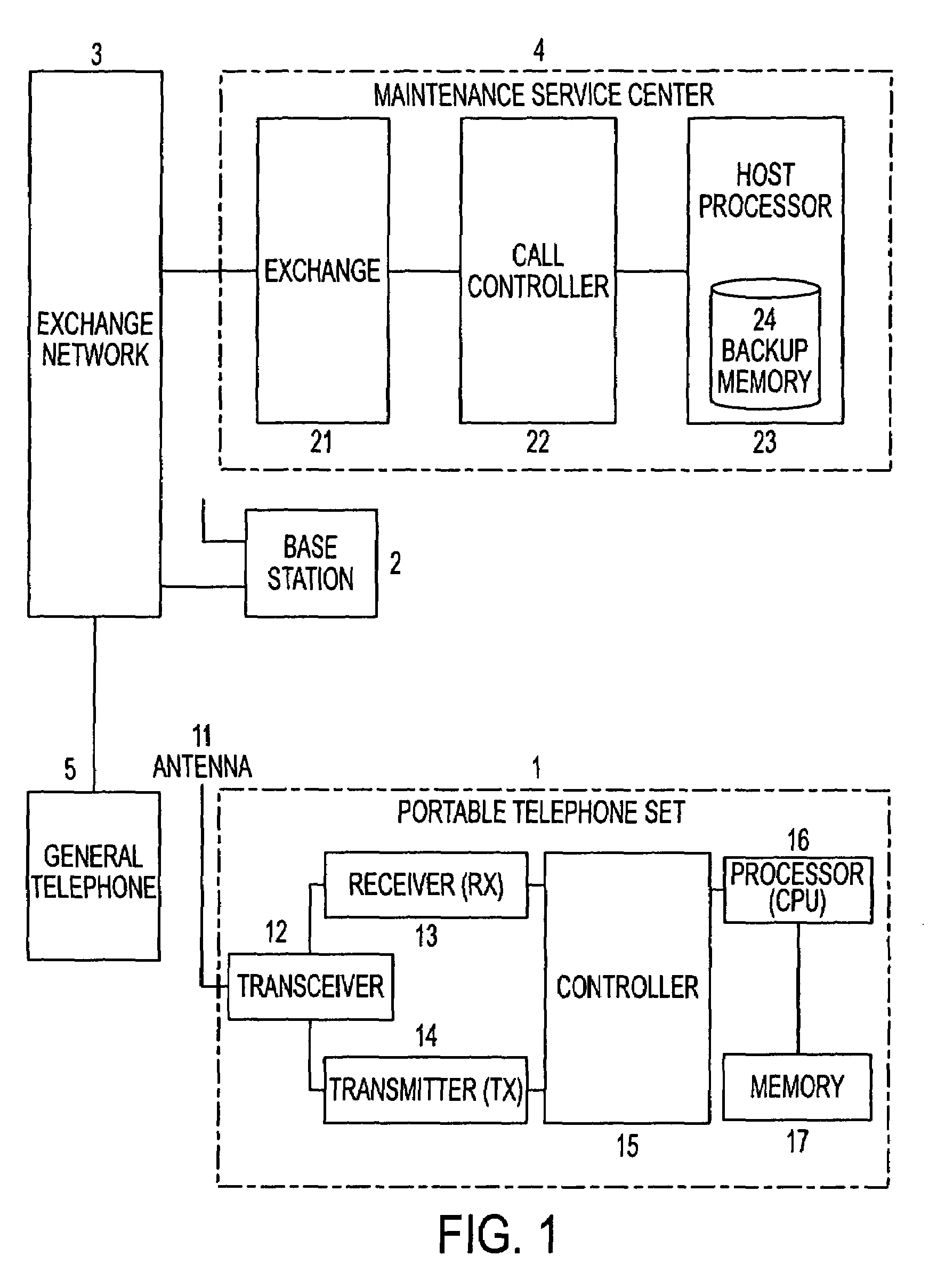
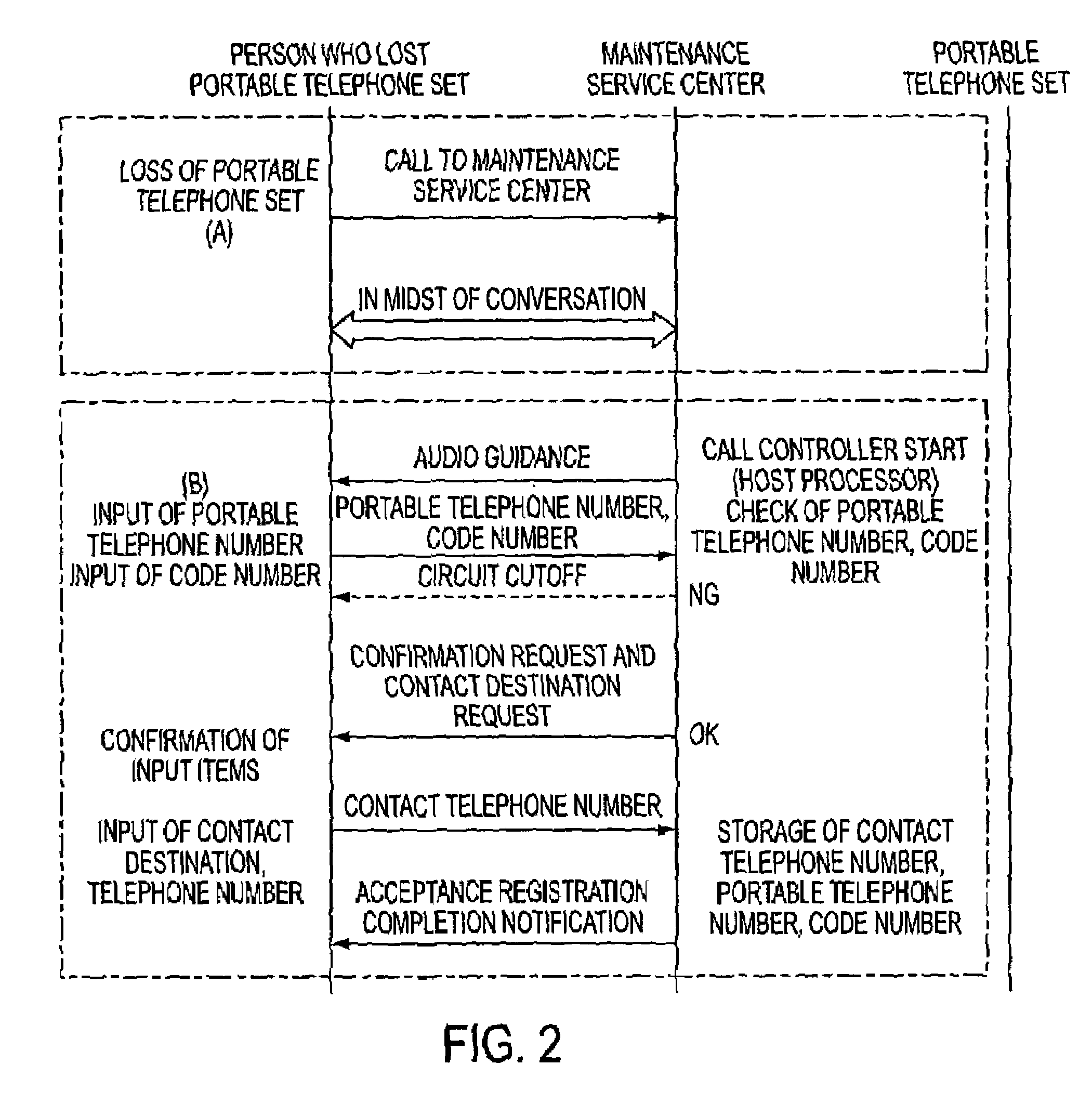
Portable telephone maintenance service system and maintenance service method
InactiveUS7200220B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsExchange networkThird person
A portable telephone maintenance service system and maintenance service method for backup control of a portable telephone set, to make it possible to prevent misuse by third persons and to perform data restoration service. A maintenance service center is connected to an exchange network and by a backup control request, that includes the portable telephone number and a code number from the person who lost the portable telephone set, dialing is done from the maintenance service center to the lost portable telephone set. Memory dial data, mail address data, and other data from the memory of the portable telephone set is saved to backup memory and the data in the memory of the portable telephone set is erased. Upon a backup control request when the portable telephone set is recovered, data is downloaded from the backup memory to the memory of the portable telephone set.
Owner:FUJITSU LTD
Paper money, coin, valuable instrument, certificates, tag, label, card, packing containers, documents, respectively installed with integrated circuit
InactiveUS20050141256A1Limited accessImprove reliabilityRead-only memoriesPayment architecturePaper documentDocument preparation
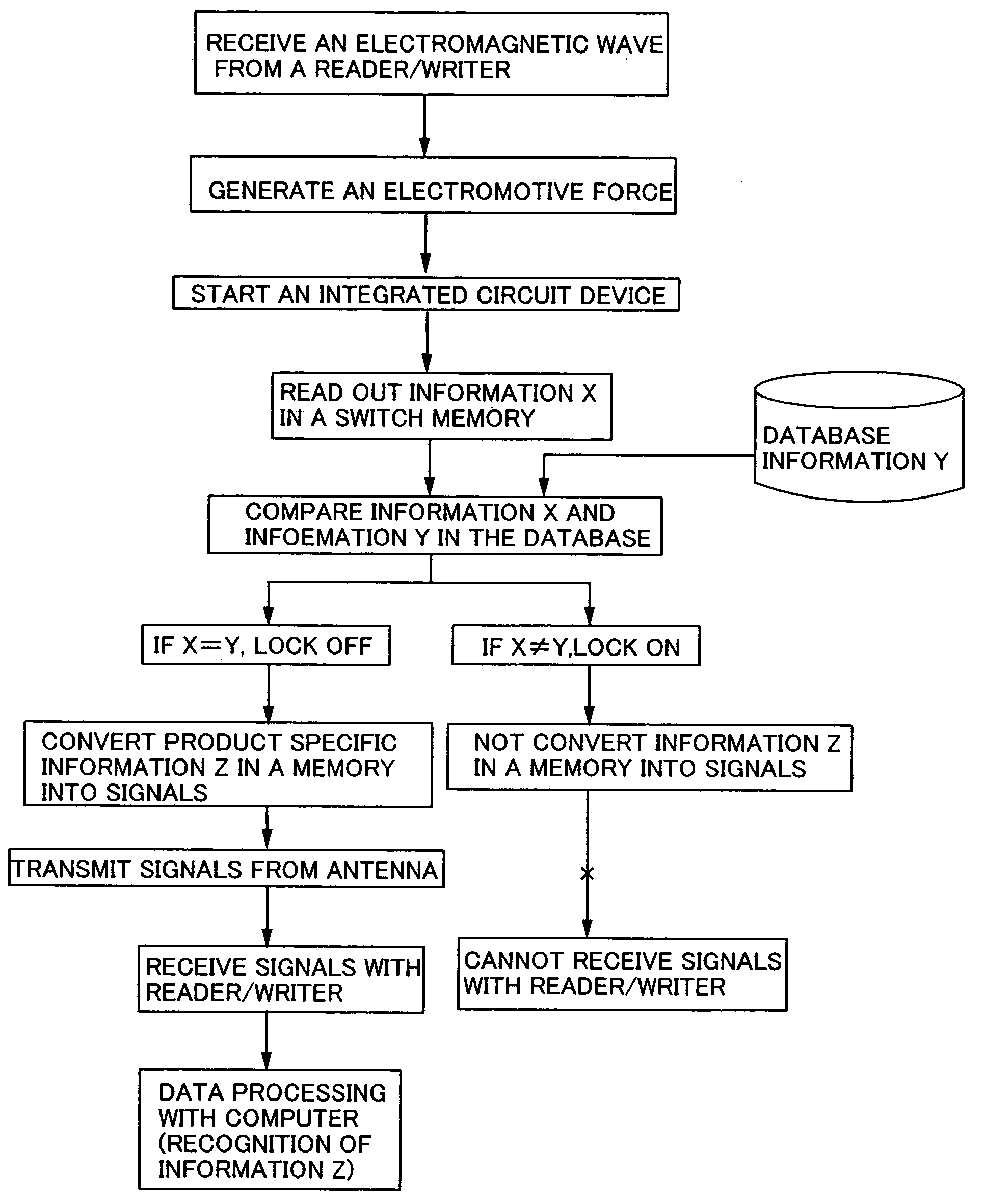
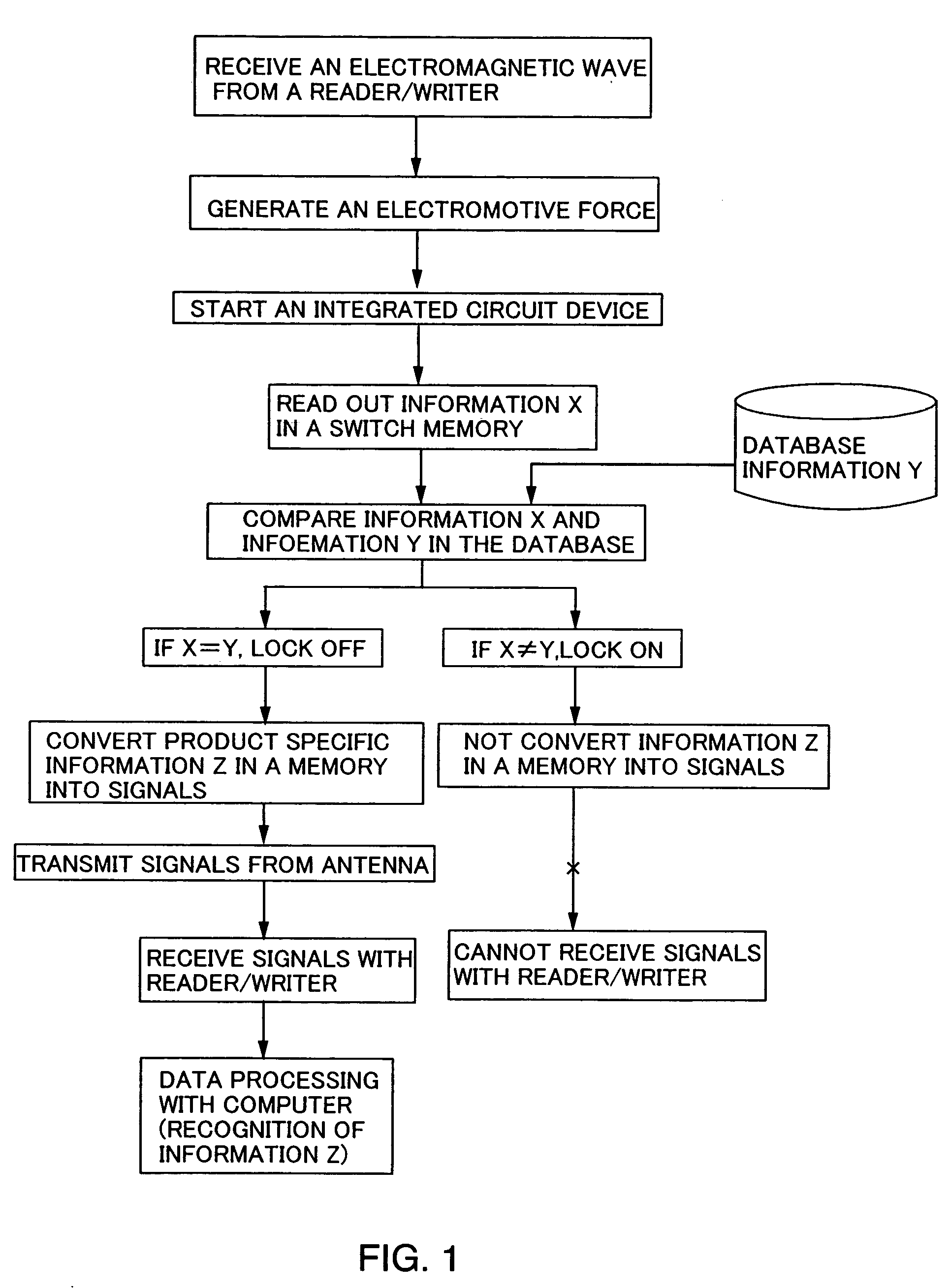
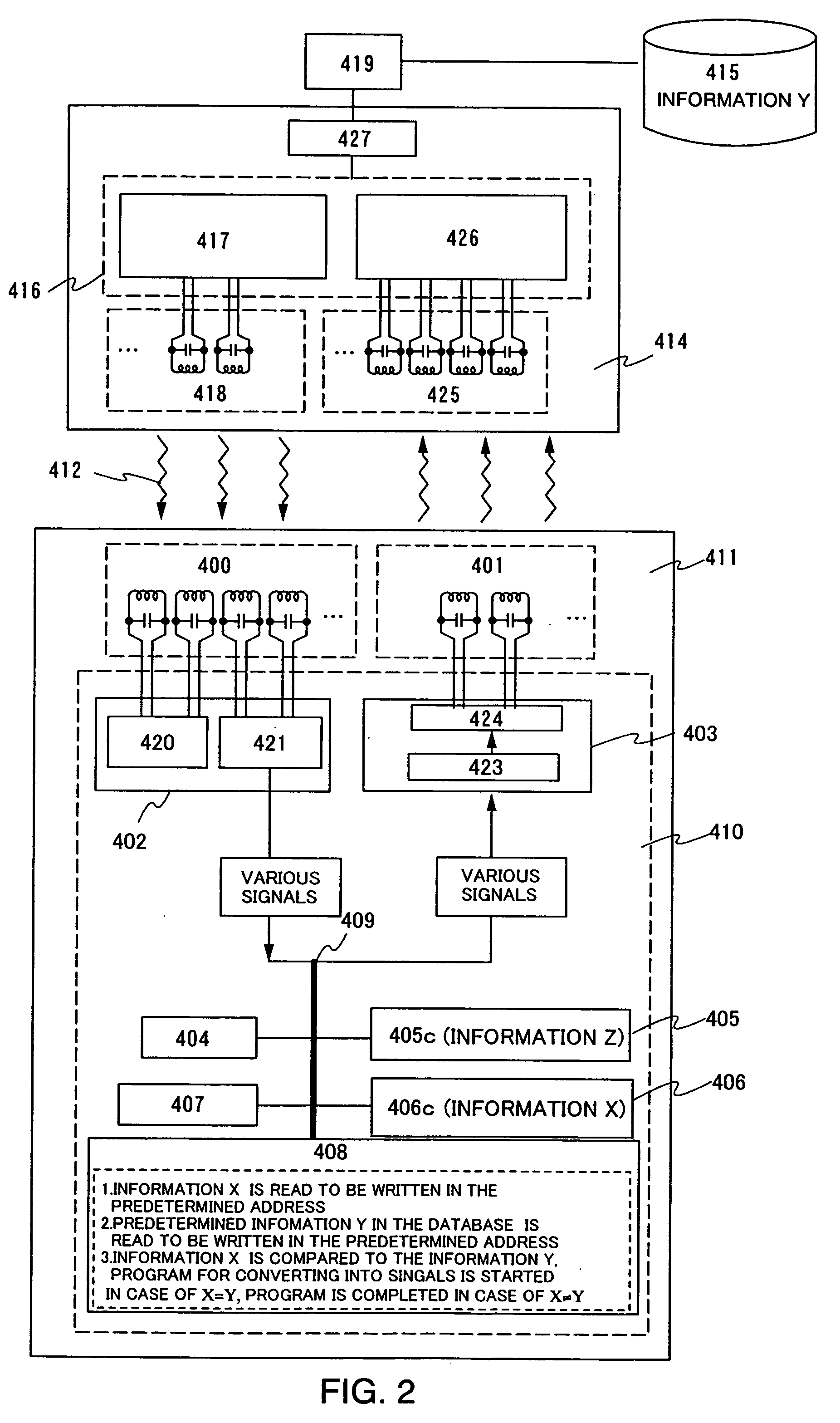
Although a product having such the IC chip has been diffused, information on the product may be capable of being perceived, abstracted, falsified, or the like by a third person with his external device during distribution of the product or after purchase of the product. Further, privacy may be seriously infringed. Paper money, various products, and the like are disclosed according to the present invention with an integrated circuit device having a switching memory for controlling reading and writing of information (lock / unlock of information) in order to protect the information recorded and stored in the integrated circuit such as an IC chip installed to the product or the like.
Owner:SEMICON ENERGY LAB CO LTD
System and method for producing and playing real-time three-dimensional movie/game based on role play
InactiveCN101247481AMaking immersiveThe production process is simpleTelevision system detailsColor television detailsAnimationSimulation
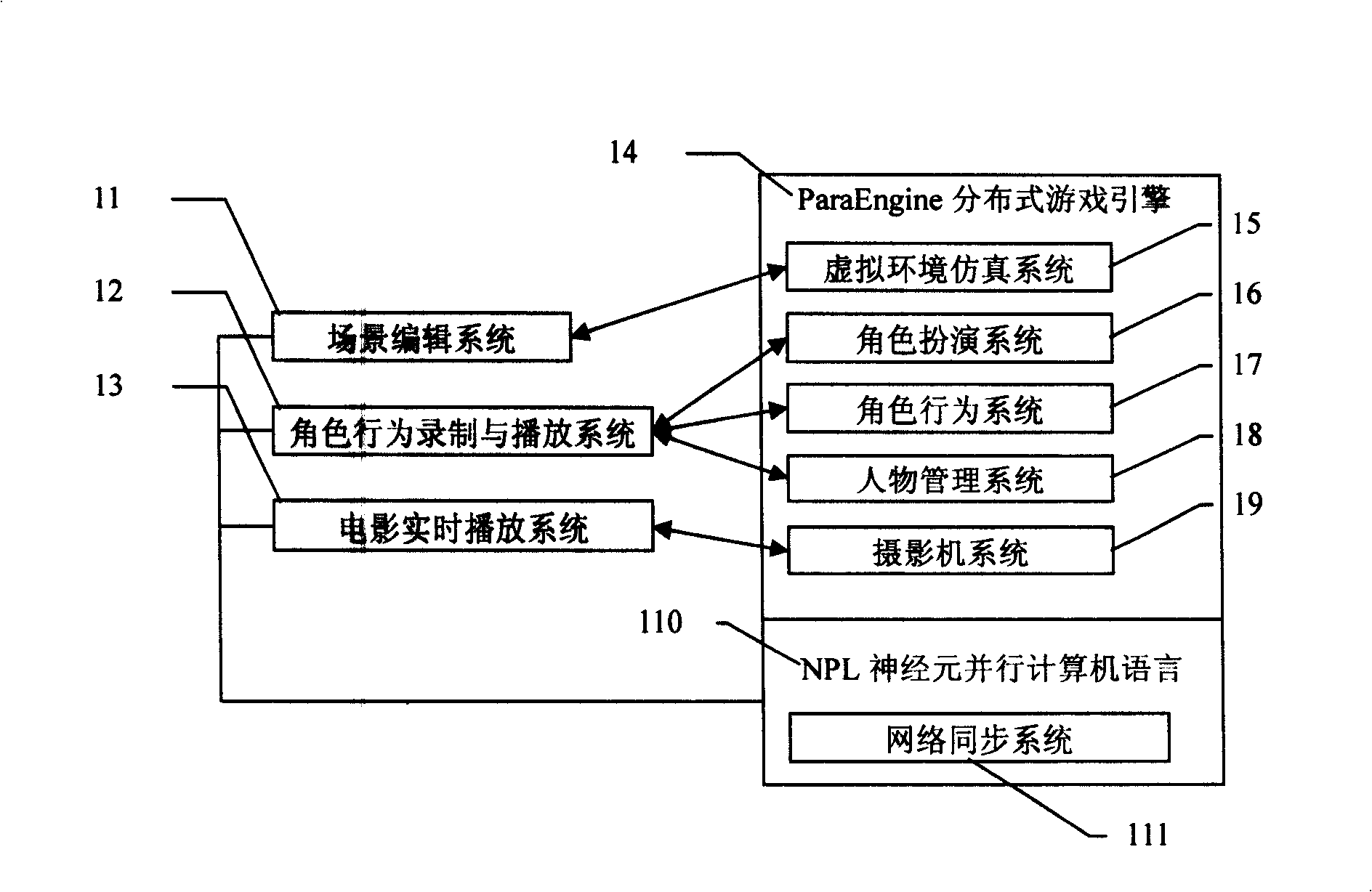
The present invention relates to a system for realizing real-time three-dimensional movie / game preparing and playing basing on the virtual role playing and a method thereof. In the invention the user operates the virtual role with a first or a third person visual angel, realizes the action of the role in the 3D movie / game, and shoots the lens in the virtual scene through acting as a director and operating the camber with a first person. Then a group of lens is series-connected and the real-time display of the 3D movie / game can be realized. The system for realizing the function comprises a role playing system, a virtual environment simulating system and the like. The invention takes the acting of the virtual role as the main facility of the 3D movie / game manufacturing. A majority of figure cartoons are automatically generated through the simulating of the virtual environment. The manufacturing to multiple-figure story polt is realized by time-sharing overlapping. The novel simplified 3D-movie manufacturing process flow is formed. The invention especially provides a platform to the manufacturing for the personal 3D movie / game.
Owner:李西峙
Personal Internet identity verification system
InactiveUS20050027672A1Limited extentSecure siteDigital data processing detailsPayment architectureInternet privacyThe Internet
An individual identification verification system is provided for persons to verify their identity to third persons who they meet in various internet sites in a safe, confidential manner and wherein the extent and manner of information are controllable by the person whose identity and background is being verified. The system provides the following improvements: control of the extent of disclosure by the individual being investigated, information is given on a secure site, unlimited access and referrals, updateability, and interoperability with other media including print and telephone dating services.
Owner:PERSONACHECK
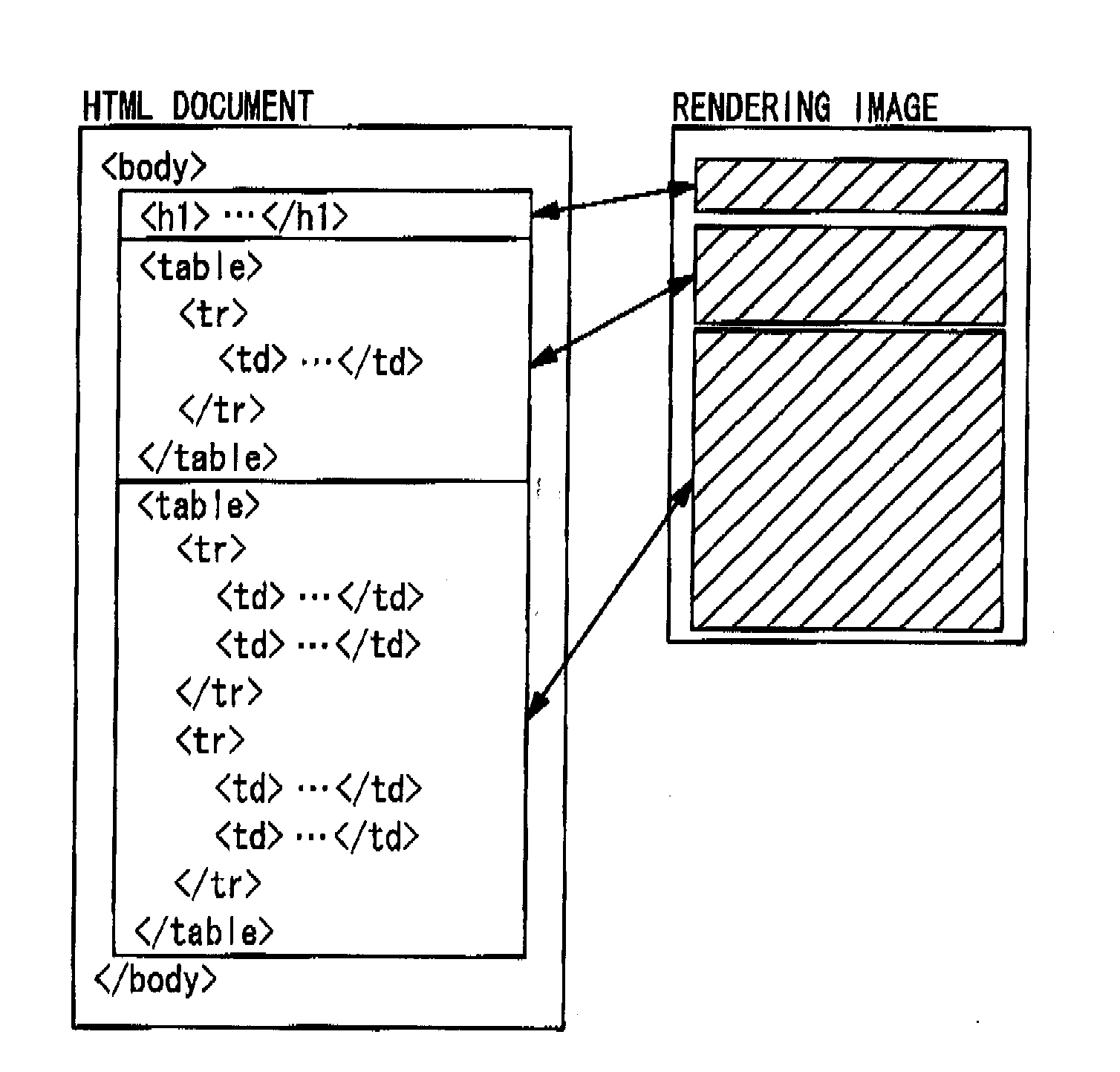
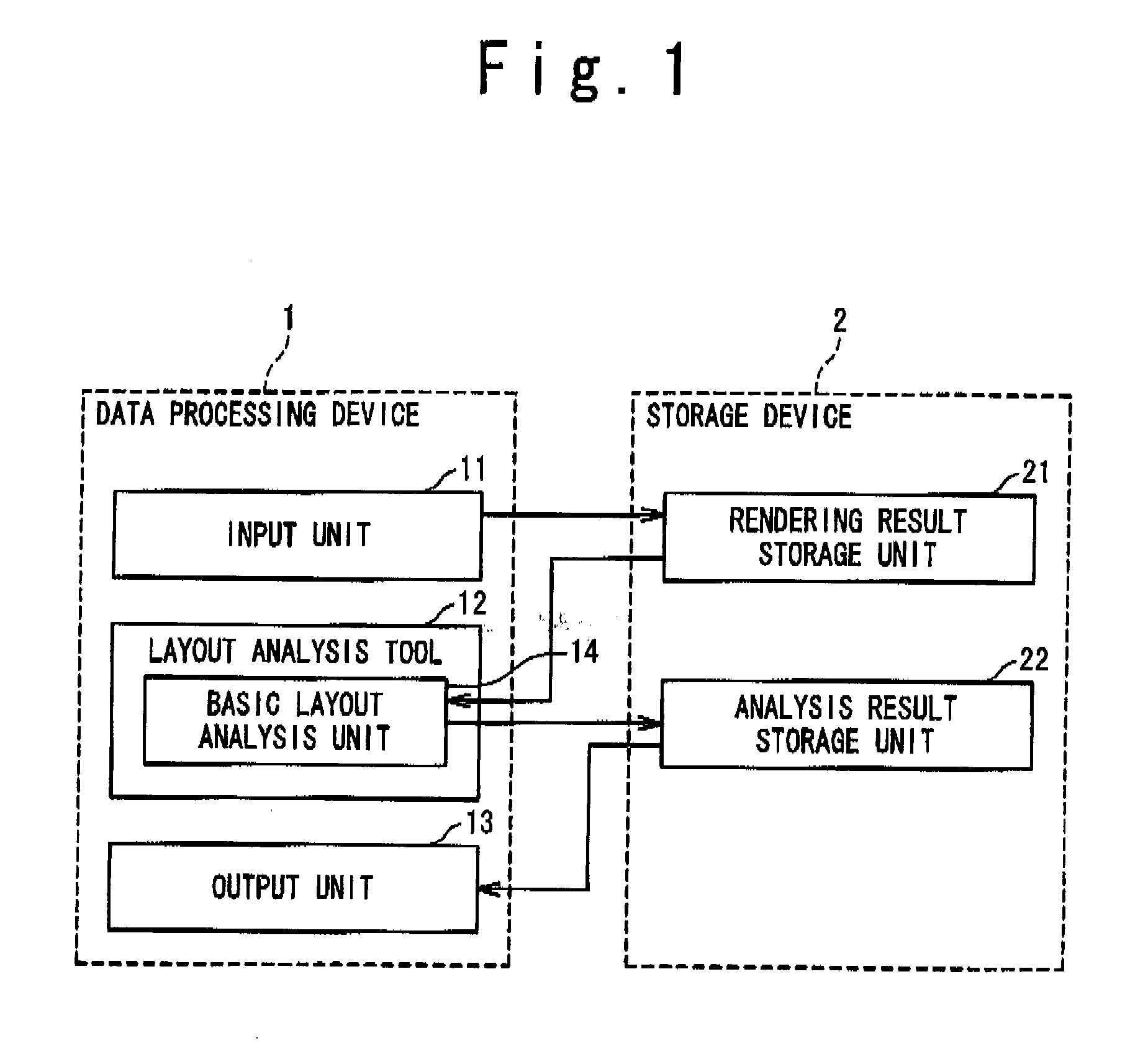
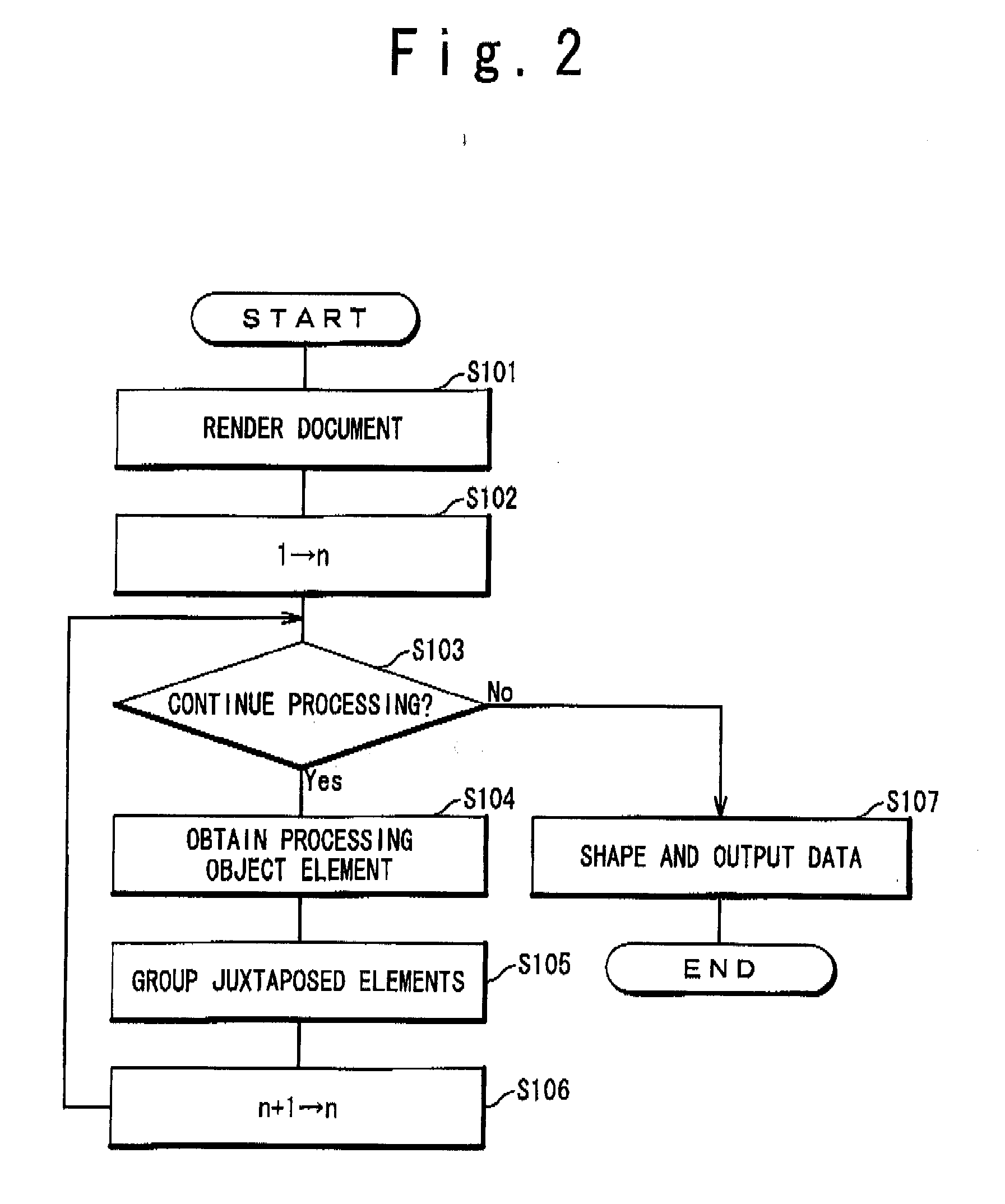
Document Analysis System and Document Adaptation System
InactiveUS20080148144A1Easy to analyzeEasy to useDigital data information retrievalText processingDocument analysisDocument preparation
A document analysis system which can execute a layout analysis intended by a document provider and an exhaustive title analysis and output the analysis result which can be used by a third person is provided by the present invention. The input unit (11) obtains a structured or semi-structured document and renders it. The basic layout analysis unit (14) obtains the rendering result and analyzes the layout by grouping document description elements juxtaposed in a determined direction by referencing an arrangement of the document description elements. The title analysis unit (15) obtains the rendering result and a title analysis rule from the title analysis rule storing unit (23) and analyzes the title by comparing the name, attribute, style or the content of the document analysis elements with the title analysis rule. The layout analysis unit (16) obtains the layout components and the hierarchical relationship thereof and the titles for generating a new layout by grouping the layout components. The output unit (13) obtains the layout components and the hierarchical relationship thereof, the relationship between the components and the titles, shapes them into a format having an expression which uses the reference to the document description elements and output them.
Owner:NEC CORP
Wireless access control system and methods for intelligent door lock system
A wireless access control system to lock or unlock a first door at a dwelling of a user. A user remote access device transmits a first signal and a second signal. The user remote access device includes a vibration mode that provides an alert to the user of the remote access device. The user remote access device is configured to be in communication with an intelligent door lock system at the dwelling with the first door. The intelligent door lock system includes: a drive shaft, a circuit coupled to an engine configured to cause a rotation of the drive shaft, and an energy source coupled to the drive shaft, the user remote access device configured to provide the first signal to the intelligent lock system for locking or unlocking of the first lock, the intelligent door lock system configured to allow controlled access to the dwelling that includes an occupant of the dwelling as well as a designated third person granted access rights by the occupant. The user remote access device is configured to be in communication to a second lock at a vehicle of the user or at an office of the user. The user remote access device is configured to communicate with the second lock with the second signal to cause the second lock to lock or be unlocked. The remote access device has a controller for generating the first and second signals.
Owner:AUGUST HOME
Systems and methods for multi-user virtual reality remote training
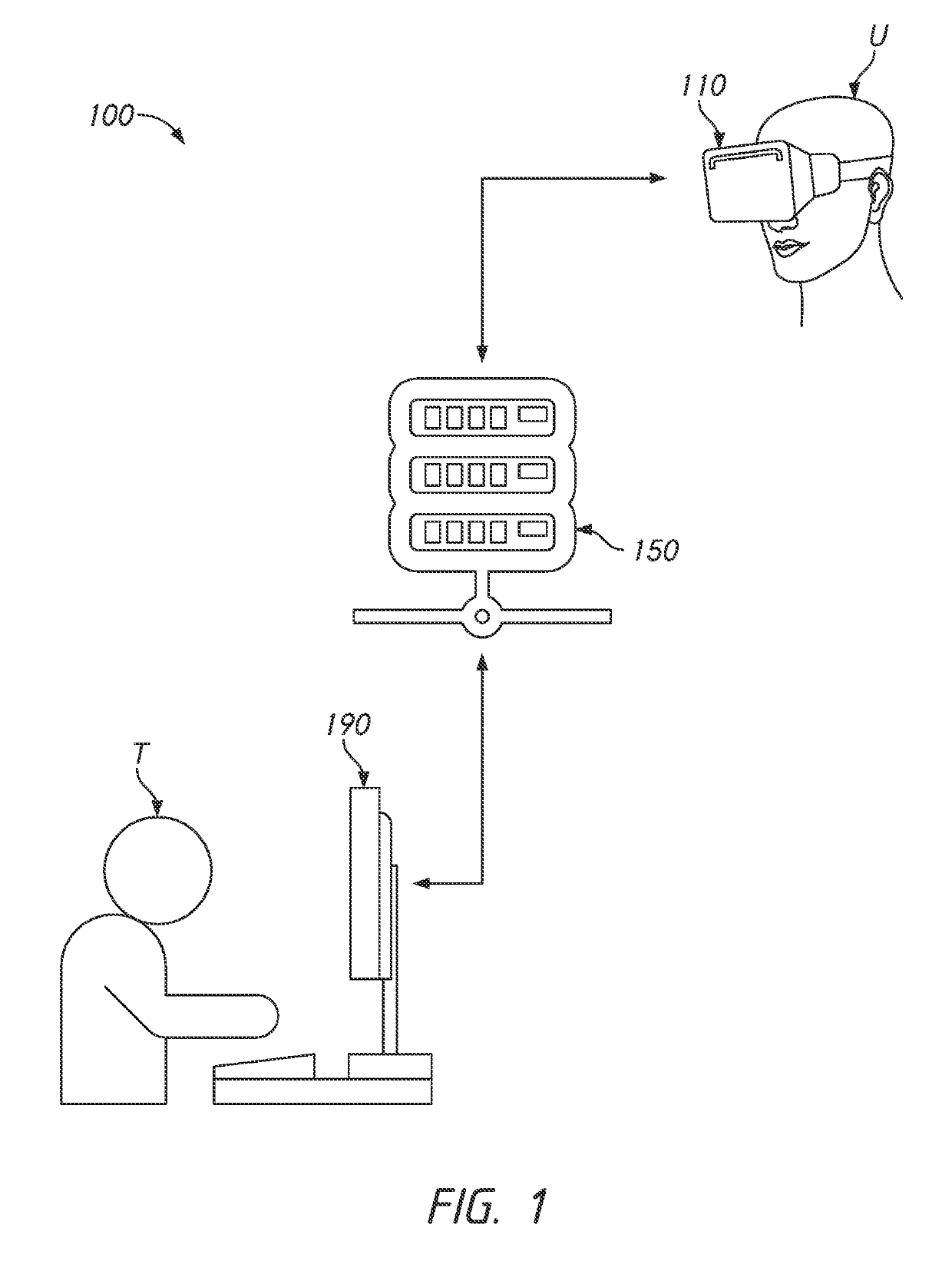
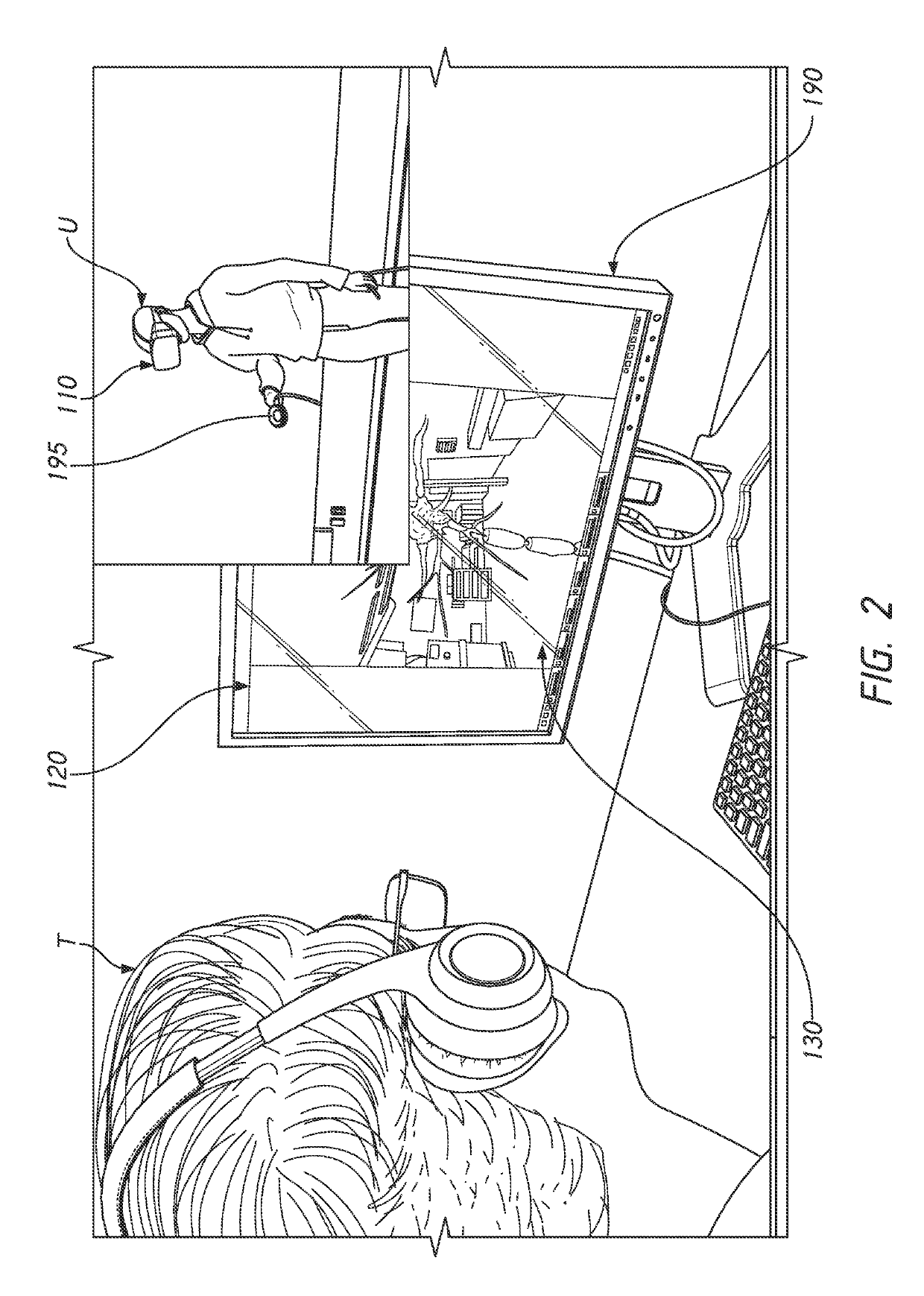
ActiveUS20190304188A1Cosmonautic condition simulationsImage data processingVirtual realityThird person
Aspects of the disclosure provide remote training in a virtual reality (VR) environment. Multiple users may engage in the session. For example, a trainee may practice or be evaluated in performing a virtual version of a training task. A trainer may join the trainee's session. Embodiments enable the trainer to switch from a third-person perspective viewing the environment to the trainee's first-person perspective to see what the trainee is seeing. Virtual objects may be highlighted to guide the trainee's steps. Some embodiments may configure the training module to be engaged at various points out of order. For example, a user may select a specific point in a training sequence and work from there, replay or forward the environment in time to other points so that the trainee can skip or practice parts of the procedure.
Owner:EON REALITY
Pseudo public key encryption
InactiveUS20070189517A1Low costCheap to achievePublic key for secure communicationSecret communicationComputer hardwareTamper proof hardware
According to the present invention, a secret key cryptosystem and tamper-proof hardware are used to realize a pseudo public key cryptosystem at a low cost. A trap-door one-way function is substantially realized with the use of tamper-proof hardware. Each user performs communication using equipment provided with hardware having the same capabilities described below. Such hardware retains association between an ID and a key. In response to a request from a user, the hardware issues and stores an ID, and it can perform decryption and generation of a MAC (message authentication code) with a key associated with the ID. A user publishes his ID. When performing encryption, a message sender encrypts a message using the published ID. A third person can perform decryption with the ID only by analyzing the mechanism in the hardware. However, the hardware has a capability of destroying itself when such an act is attempted.
Owner:IBM CORP
Camera based orientation for mobile devices
In an exemplary embodiment, an on-board camera is used as a controller for a hand-held game device. Control information is provided to a game application via video captured by the camera. As the hand-held device is moved, features of the captured video are tracked. The relative motion between the tracked features and the hand-held device is translated into control information for the game application. Aspects of the game application are rendered on a display of the hand-held game device in accordance with the control information. For example, from a third person perspective, viewing a game character from overhead, rotation of the hand-held game device can be translated into rotation of the character. From a first person perspective, seeing the game through the eyes of the game character, rotation of the hand-held game device can be translated into observing various challenges coming from different directions.
Owner:MICROSOFT TECH LICENSING LLC
Intelligent door lock system with audio and RF communication
A wireless access control system is provided to lock or unlock a first door at a dwelling of a user. A user remote access device transmits a first signal and a second signal. The user remote access device is configured to be in communication with an intelligent door lock system at the dwelling with the first door. The intelligent door lock system includes: a position sensing device configured to be coupled to a drive shaft of a lock device, the position sensing device sensing position of the drive shaft to assist in locking and unlocking the first lock of the lock device, an engine with a memory coupled to the position sensing device, the engine configured to execute software instructions relative to the positioning sensing device and an energy source coupled to the circuit. The user remote access device provides the first signal to the intelligent lock system for locking or unlocking of the first lock. The intelligent door lock system allows controlled access to the dwelling that includes an occupant of the dwelling as well as a designated third person granted access rights by the occupant. The user remote access device is configured to be in communication to a second lock at a vehicle of the user or at an office of the user. The user remote access device communicates with the second lock with the second signal to cause the second lock to lock or be unlocked. The remote access device has a controller for generating the first and second signals.
Owner:AUGUST HOME
Door lock system with one or more virtual fences
An intelligent door lock system is coupled to a door at a dwelling. A sensor is at the dwelling. The sensor is coupled to a drive shaft of a lock device to assist in locking and unlocking a lock of a lock device at the door. The lock device is coupled to the sensor and includes a bolt. An engine, an energy source and a memory are coupled together. A camera is coupled to or part of the intelligent door lock system. The camera is configured to define a safe zone in the dwelling in which an occupant, and a non dwelling occupant third person is allowed into the dwelling.
Owner:AUGUST HOME
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com